
December 2022/January 2023 New Zealand Security Magazine Terror Plot: A wake up call for New Zealand’s crowded places www.defsec.net.nz CyberCon2022: Selected cyber wisdom from famous speakers Retail Security: Why thieves target some items and not others

LoktronicLimi t e d sraey03 s’ZNgnicivres S e c u r ity Industry REGISTERED COMPANY ISO 9001:2015 Certificate No. NZ1043 Loktronic Limited Unit 7 19 Edwin Street Mt Eden Auckland P O Box 8329 Symonds Street Auckland 1150 New Zealand Ph 64 9 623 3919 • Fax 64 9 623 3881 • 0800 FOR LOK mail@loktronic.co.nz • www.loktronic.co.nz Three great brands that stand for QUALITY and VALUE from Loktronic Limited SERVICE and SUPPORT drive us.


ABLOY® BEATHigh Security Bluetooth padlocks designed for critical infrastructure protection www.assaabloy.com/nz • Bluetooth High Security Padlocks • Easy to use mobile application • Manage keys, locks and access rights on the go with ABLOY Cloud-based management system • Full Audit trails • Super Weather Proof Padlock (SWP) IP68 approved Scan for more
From the Editor
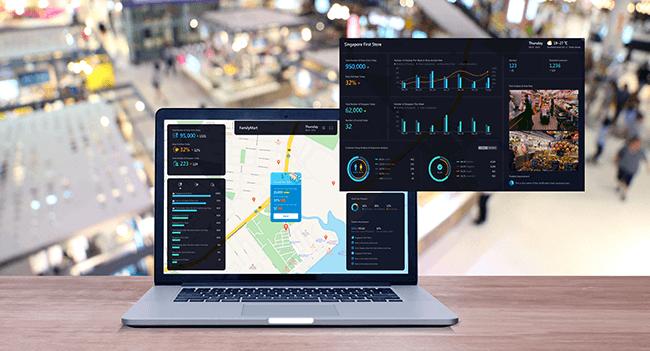
Never drop the ball on instore customer experience: how smart video can help
New From Provision-ISR – Brought To You Exclusively By Security Wholesale....................................................... 10
Planned Auckland terror attack a wake-up call say crowded places security experts
Leading supermarket chain Lidl adopts 2N access system in the UK 14 We’re risk takers, and that’s making cyberattacks more costly 16
New Public Safety Network to improve emergency services communications

What next after resilience? Wisdom from AISA CyberCon2022
Security licensing requirements for the install, servicing and selling of security systems


23
ICT updates Geutebrück G-Core integration to support V6 24
Violence and organised crime up: annual retail security survey 26


The Wisdom of the Crowds coming through loud and clear at CyberCon2022
Gallagher named Security Software Manufacturer of the Year at Security & Fire Excellence Awards
New Zealand Security Association CEO’s November Report


NZIPI Update
31
‘Hot Products’: Why stolen goods are CRAVED 38


Finding pragmatic, proportionate and effective physical security solutions 40
Multi-million dollar package to tackle retail crime and reoffending
4 NZSM December 2022/January 2023 www.asis.org.nz www.nzipi.org.nz
www.security.org.nz www.skills.org.nz www.masterlocksmiths.com.au 12 38 26 0800 367 565 www.loktronic.co.nz * Three leading brands from
Industry Associations
.......................................................................................................................................................................
6
......................................................
8
............................................
12
.......................................................
18
................................................................................
20
.....................................
...................................................... 28
................
......................................................................................
32
.........................................................................................................................................................................
36
...........................................................................
18 ISSN Print 1175-2149 • ISSN Online 2537-8937 CONTENTS
46








Welcome to the December 2022 – January 2023 issue of New Zealand Security Magazine!
It’s our annual retail security issue, and inside you’ll find some fantastic retail-focused features. Retail security has been a hot issue this year with ram raids, smash and grabs, and violence against store operators placing theft under the media spotlight.
The 2022 edition of the National Retail Federation’s Retail Security Survey indicates more and more retailers in the US are turning to smart tech to reign in $100 billion worth of losses. We take a look at some of the key takeaways of this year’s survey. We also explore the specific reasons why offenders target so-called ‘hot products’. There’s an acronym for it!
Still on retail, Hikvision’s Andrew Martin discusses how smart video can deliver a real-time view of customer needs in store and support faster, more responsive service. We also learn how 2N delivered a centralised access control system to Lidl supermarket distribution centres in the UK to meet the demands of 24-hour vehicle access while offering centralised remote system maintenance and audit.
In addition to retail, this end-of-year issue of NZSM features a line-up of weighty cybersecurity features, including a double-barrel round-up of Melbourne’s CyberCon2022 from correspondent and IFSEC champion global influencer Jennie Vickers.
I also chime in on the cybersecurity front, arguing that businesses appear to be addicted to gambling on their cybersecurity, or at least engaging in a degree of moral hazard. It seems that our big appetite for cyber risk is now being called out by insurers, government... and criminals.
Also in this issue of NZSM, I’m excited to welcome ICARAS Security Consultants’ Chris Philp as a contributing author. In his excellent article, Chris combines theory with practice to acquaint us with the building blocks of assessing security risk and identifying an effective security solution.
Some great updates as well from the NZSA, the New Zealand Institute of Professional Investigators (NZIPI), and the Crowded Places Security Advisory Group (CPSAG).
There’s plenty more in this December-January issue of NZSM! To ensure you don’t miss out on any of the news and analysis we publish, subscribe to our email newsletters via our website, and follow us on LinkedIn via the address listed on this page. As always, feel free to get in touch to find out about how your business can benefit by being part of New Zealand’s premier security, risk and resilience publication in 2023!
Wishing you a safe and secure festive season!
Nicholas Dynon Auckland
NZ S M
Contact Details:
Chief Editor, Nick Dynon
Phone: + 64 (0) 223 663 691 Email: nick@defsec.net.nz
Publisher, Craig Flint
Phone: + 64 (0)274 597 621 Email: craig@defsec.net.nz
Postal and delivery address: 27 West Crescent, Te Puru 3575, Thames, RD5, New Zealand
Upcoming Issue
Feb-Mar 2023 – Banking, Insurance and Finance, Loss prevention, industry training
facebook.com/defsecmedia twitter.com/DefsecNZ


linkedin.com/company/ defsec-media-limited
 Nick Dynon Chief Editor
Nick Dynon Chief Editor
Nick has written for NZSM since 2013. He writes on all things security, but is particularly fascinated with the fault lines between security and privacy, and between individual, enterprise and national security.

Prior to NZSM he clocked up over 20 years experience in various border security and military roles.
Disclaimer:
The information contained in this publication is given in good faith and has been derived from sources believed to be reliable and accurate. However, neither the publishers nor any person involved in the preparation of this publication accept any form of liability whatsoever for its contents including advertisements, editorials, opinions, advice or information or for any consequences from its use.
Copyright: No article or part thereof may be reproduced without prior consent of the publisher.
6 NZSM December 2022/January 2023
THE EDITOR
New Zealand Security Magazine
FROM
DEFSEC New Zealand’s National Defence, Fire and Security Publishers of: Line of
Defence, FireNZ, New Zealand Security Magazine

Never drop the ball on instore customer experience: how smart video can help
With a huge array of online and in-store shopping options available, stores need to deliver great customer experiences to stay ahead. To do that, they need to take advantage of key technologies – such as smart video – which provides a real-time view of customer needs in store and supports faster, more responsive service, says Andrew Martin, Retail & Logistics Lead at Hikvision UK and Ireland.
Massive growth in online retail has led to the commoditisation of all kinds of products, from furniture and phones to groceries and printer paper. In many cases, the last bastion for differentiation is customer service – whether customers buy online or in store.
But although great customer experiences are absolutely central to success in today’s markets, delivering them remains a major challenge for retailers for a number of reasons.
First, many supermarkets are moving towards semiunattended or totally unattended environments, which makes it harder than ever to provide the personal, faceto-face service experiences many customers still want. Additionally, fewer staff in all kinds of retail stores means it’s increasingly difficult to balance customer care with day-today tasks such as admin, inventory, and shelf filling.
In this environment of stiff competition, increasing online and hybrid shopping options, and changing retail staffing models, technology solutions can greatly enhance a store’s ability to deliver great customer service. In particular,
the latest generation of AI-enabled smart video solutions provide new ways to enhance customer experiences, without the high costs and complexity of manual processes.
Five ways smart video gives you the edge on customer service
Smart video is able to boost customer experiences and deliver new competitive advantage for retailers in five important ways:

1. Understand and meet customers’ needs in store, in real time
Smart video makes this possible by providing ‘realtime awareness’ of customers’ journeys through the store. For example, smart cameras can be used to count customers entering and leaving the store, ensuring that enough staff are available to serve them. Staff can also be diverted to the checkout when queues get too long and return to routine shelf-filling and other tasks during non-peak times when fewer customers are in the store.
8 NZSM December 2022/January 2023
2.
For customers, having access to the right product in the right place at the right time is the cornerstone of a great experience. Smart video can help by registering the availability (or otherwise) of goods on shelves, and by triggering alarms to ensure products are restocked and always available.
Additionally, video data analytics provides new insights into which products are the most popular, helping stores to place them in ‘hotspots’ where customers can find them quickly and easily. This ensures that the shopping experience is as quick, efficient, and satisfying as possible.
3. Deliver great service in unattended retail environments
As an increasing number of retailers roll out unattended stores (or stores with very few staff), smart video is taking a leading role. It’s possible, for example, to identify customers who are struggling at the self-service checkout, and to send a member of staff to assist them.
Additionally, smart video offers multiple, high-value security applications for unattended environments, from traditional video security to AI algorithms that detect shoplifting. These capabilities ensure that customers feel safe, while also helping to minimize shrinkage from the inventory.
4. Provide pleasant, multi-channel shopping experiences
Smart video can help retailers provide far better multichannel shopping experiences in store based on an
in-depth understanding of customer journeys. For example, analysis of video data can ensure that kiosks for online ordering and product pickups are located in the right areas of the store to minimize congestion and speed up service. Likewise, smart video solutions at the distribution center can ensure that customer orders are picked and packed correctly, as well as ensuring that customer queries and disputes are answered faster.
5. Keep stores safe and clean for customers
With smart video, store managers and maintenance teams can get alerts in real time to ensure the store is always safe and clean. In particular, AI-powered cameras can detect liquid spills or obstacles in the aisles automatically, allowing staff to react more quickly to ensure that these issues never compromise the customer experience.
Why partner with Hikvision on in-store customer experience
Many leading brand retailers are partnering with Hikvision to enhance their in-store experiences with help from our smart video solutions and our ecosystem of retail technology partners. Our solutions not only give managers a real-time view of how many customers are in the store, and the ideal staffing levels to look after them. Hikvision smart video can also ensure that products are always available when and where customers want them – and that multi-channel customer journeys are optimized.
To find out more about Hikvision’s solutions for better customer experiences, please visit the www.hikvision.com/ au-en/. Alternatively, please contact us today via salesnz@ hikvision.com or 09 217 3127.
NZSM 9 December 2022/January 2023
Ensure that the right products are available –when and where customers want them
New From Provision-ISR –
Brought To You Exclusively By Security Wholesale
Provision-ISR is a fast-growing Israeli company founded in 2007 to meet the demand for highquality products in the medium segment of the CCTV market. Our wide range of products includes IP and HD technologies able to respond to the market’s diversified demand. Advanced CCTV software and APPs developed by our Israeli engineers intend to keep the user experience intuitive and straightforward.
DETECT | ACT | DETER
Discover the new Provision-ISR’s active deterrence cameras.
Unlike “standard” security cameras, which are commonly used to investigate an event after it happened, active deterrence cameras notify the intruder that his presence has been detected and drive him out of the premises. For this reason, they can be compared to real alarm systems.
Provision-ISR’s Smart Alert cameras integrate active deterrence mechanisms (such as strobe light and speaker) into compact security devices.

Provision-ISR enhances the cameras’ performance by enriching them with advanced artificial intelligence (DDA Video Analytics –Object Recognition Technology).
Available in the Turret / Dome and Bullet versions, with 4MP resolutions, Provision-ISR’s Smart Alert cameras include more exciting features such as the possibility to upload a customized audio message.
Provision-ISR’s active deterrence cameras are widely used in private
properties’ perimeter protection and industrial or commercial areas. They are also used to prevent unauthorized access to restricted areas, parking lots, or pedestrian zones.
Let Provision-ISR’s Smart Alert cameras be your security guard!
Highlights:
• Integrated strobe light
• Customisable audio
• Advanced A.I.
WHAT COLOUR IS THE NIGHT?
Provision-ISR launches the new Rainbow colour night-vision cameras. Provision-ISR’s Rainbow cameras, equipped with CNV (Colour Night Vision) technology, return sharp and superior quality colours even in poor light conditions, providing visual detail that significantly contributes to the identification of people or objects.

Available in the Turret/Dome and Bullet versions, with 4MP resolutions, the cameras are equipped with a built-in warm LED light source, F1.0 super-wide aperture lens, and state-of-the-art sensors, which are more sensitive to light than those of traditional infrared technology. Crimes such as theft, drug violations, simple assaults, robbery, or vandalism are known to be more likely to occur at night. The
Provision-ISR’s Rainbow cameras can provide authorities with crucial information, such as people’s clothes or car colour. The 4MP Rainbow cameras are equipped with the most talked-about A.I. feature: DDA Video Analytics. Thanks to advanced artificial intelligence algorithms, the cameras accurately detect and distinguish people, two and fourwheeled vehicles.
Highlights:
• Full-colour image at night
• Excellent detail visibility
• Better contrast
Visit the NZ Provision-ISR website at www.provision-isr.co.nz.
Provision-ISR is exclusively distributed in New Zealand by Security Wholesale Ltd – www.swl.co.nz
10 NZSM December 2022/January 2023
NDAA Compliance
The John S. McCain National Defense Authorization Act (NDAA) for the Fiscal Year 2019 was passed on August 13, 2018. The law, specifically Section 889, prohibits federal agencies, their contractors, and grant or loan recipients from procuring or using “Telecommunications and video surveillance equipment or services” from specific Chinese companies as a “substantial or essential component of any system, or as critical technology as part of any system.” The NDAA ban includes telecommunications equipment produced by Huawei Technologies Company or ZTE Corporation and video surveillance and telecommunications equipment produced by Hytera Communications Corporation, Hangzhou Hikvision Digital Technology Company, or Dahua Technology Company.

Provision-ISR Statement


With headquarters in Israel and manufacturing facilities located in Shenzhen, China, Provision-ISR supports NDAA compliance across its product line and is committed to complying with all government and international trade regulations. Provision-ISR is committed to providing NDAA Section 889-compliant products and does not have OEM, ODM, and JDM relationships with the named vendors in the NDAA. Provision-ISR cameras and network video recorders (NVRs), which do not use or deploy critical components, including SoCs produced by NDAA-banned component vendors, comply with the NDAA. The Provision-ISR compliance product list will be regularly updated on Provision-ISR’s website.

Discover NDAA compliant products
Exclusive to: Security Wholesale Ltd | Auckland | Wellington | Christchurch | www.swl.co.nz Security Wholesale Limited
Planned Auckland terror attack a wake-up call say crowded places security experts

The Crowded Places Security Advisory Group says recent teenage terror plot presents important learnings for hospitality, retail, entertainment, and event venue operators.
It emerged in early November with the recent release of court documents that a radicalised teen had planned to carry out an Islamic State-inspired attack in Auckland, including compiling a list of around 80 potential target locations. Restaurants, shopping malls, transport hubs, and entertainment hotspots such as Spark Arena, SkyCity, and Auckland Town Hall, were among the targets.
“It’s no surprise that the individual considered these locations as potential targets,” said Chris Kumeroa, Chair of the Crowded Places Security Advisory Group. “These ‘crowded places’ have
been shown internationally to be prime targets for terrorists due to the fact that they can accommodate large numbers of people, they have predictable patterns of use, and that an attack in such premises can effect maximum casualties and terror.”
A voluntary security industry body, the Crowded Places Security Advisory Group (CPSAG) was formed after the New Zealand Police sought assistance from the New Zealand Security Association to identify how the industry might contribute its expertise to the protection of crowded places. It came hot on the heels of the September 2020 publication by police of Protecting Our Crowded Places from Attack: New Zealand’s Strategy. The strategy had a quiet launch at a time when COVID was front and centre.
“The crowded places strategy contains a suite of six documents that provide guidance to venue owners and operators on a range of topics from recognising threats to detecting hostile reconnaissance,” said Chris Kumeroa.
“One of the things that the coverage of the Auckland terror plot tells us is that owners and operators of crowded places need to understand how they can put in place measures to prevent wouldbe terrorists from gathering intelligence about their venue online and from conducting hostile reconnaissance in and around their venue in the weeks or months prior to a planned attack.”
Knowing the signs of attack planning
“The threat of an attack on a crowded place is something we’ve known about in New Zealand since the Christchurch terror attack,” said CPSAG member Dr Bridgette Sullivan-Taylor. “With the tourism and hospitality sectors getting back to business post-COVID, we’re seeing more cruise ships, more concerts, and more sporting events, so it’s critical we’re vigilant and taking a joined-up approach.”
Tourism, hospitality and event venues are ‘soft targets’. They can’t be fortresses. They need to be open enough to be welcoming to visitors and patrons, and their staff equipped enough to be able to identify the terrorist from the tourist. How do you know what a terrorist looks like?
“It’s about being proactive and identifying unusual activity or behaviour that might be possible indicators of attack planning and rehearsing, such as an individual loitering in the vicinity of the venue, displaying unusual interest in a venue’s security measures, or wandering into restricted or work areas,” said Dr Sullivan-Taylor. “Staff need to be equipped to identify, report, manage and respond to any concerns.”
From her research and involvement in the UK multiagency approach and from recent events in New Zealand
12 NZSM December 2022/January 2023
Chris Kumeroa, Chair of the Crowded Places Security Advisory Group
such as the Christchurch attack, Dr Sullivan-Taylor has identified that we need to take a multi layered approach to situational awareness via a combination of vigilance on the ground and on cyber platforms.
“In addition to recognising suspicious activity, disrupting the preparation of an attack also means being careful not to place information on a venue’s website or social media accounts, such as detailed floorplans, that may inadvertently assist an attacker in their planning,” said Dr Sullivan-Taylor. “For many venues this will require a rethink of what their security means.”
Knowing the signs of violent extremism
The teen, now 20, at the centre of the Auckland terror plot had been radicalised online after taking an interest in Middle East conflicts. In his bedroom police found one of the
ingredients used to make an explosive compound. His Google Cloud account included folders titled “Terror plot Recons” and “ISIS supporter-recruit”.
“We live in a world in which dismisinformation is increasingly rife, providing ideal preconditions for those looking to radicalise vulnerable people and set them down a path towards violent extremism,” said Chris Kumeroa. “Mental health, social isolation, economic failure, and political grievance are just some of the potential factors that might make an individual more susceptible.”
“The question is, how can you identify when a person may be exhibiting the indicators of violent extremism? Trusting your instincts is important, but there are some good resources out there, including Know the signs: A guide for identifying signs of violent extremism, which was recently published by the New Zealand Secret Intelligence Service.
“New Zealand is a relatively safe country, but events in the recent past remind us that we are not immune from attacks. The government’s intelligence and law enforcement agencies are doing a great job, but we all have a part to play, and owners and operators of crowded places particularly should be on the front foot.”
According to the Ipsos 2022 National Security Public Survey published in April, ‘Terrorist attack / violent extremism in NZ’ ranked 8th in a list of threats, with 71% of respondents indicating they felt that it was a real threat of happening in the next 12 months (well ahead of the global country average of 62%).
The CPSAG is establishing a register of New Zealand security consultants qualified in the provision of crowded places protective security advice to organisations on how to better protect their venues and events.

NZSM 13 December 2022/January 2023
Leading supermarket chain Lidl adopts 2N access system in the UK
Lidl is one of Europe’s leading food retailers. When they began planning the construction of more than 50,000 m2 of new distribution centres across the UK, they needed highly secure premises with efficient haulage traffic throughput. They needed a centralised access control system that could meet the demands of 24-hour vehicle access in all the regional DC’s, whilst being flexible enough to provide remote system maintenance and auditing from a central control point.
Specifically, Lidl looked for a solution that provides:
• A scalable IP access control system
• Products that can withstand the most demanding weather conditions
• Easily integrated with the existing central phone system
• Simple installation and administration
The distribution centres gained a reliable IP access control system using the call button modules and integrated cameras,

achieving a greater level of security and traffic efficiency. The intercom system includes an anti-vandal solution with the highest durability according to IP69K and IK10 standards.
The integrated 2N access solution is simple to use –access authentication is done via intercom video calls to security, reception and logistics officers. The system provides additional options for further access technologies that can be added in the future, e.g. Bluetooth module, Fingerprint Reader module or the 2N® Mobile Video application, so the system can grow with the business.
Not only can 2N intercoms be set up remotely via 2N® Access Commander, but the security agency can also monitor the distribution centres in real time. In addition, the administrator can access all devices remotely via a secure cloud connection.
Working directly with the Lidl GB Network & Security Team, the 2N partner provided a network of IP-connected intercom systems for each distribution site, including: 2N® IP VERSO: Each site features multiple vehicle and pedestrian access locations, some on ‘gooseneck’ stands – at dual heights for both haulage vehicles and staff cars – and some single-height units at door/gate access points. Access validation is done via intercom video calls from 2N® IP Verso audio-visual intercoms featuring a colour camera and an additional 5 Call Button Module.
14 NZSM December 2022/January 2023
2N® IP FORCE: 2N® IP Force intercoms were installed at the areas with higher-than-normal ambient noise levels, using the 4 Call Buttons and integrated camera. The wideangle HD camera monitors events around the intercom and has 135° wide viewing with a night vision model. It is the toughest IP intercom on the market with its anti-vandal design.
2N® ACCESS COMMANDER: The simple integration to the existing central phone system allowed the 2N® IP intercoms to provide flexible communication with incoming and remote door/gate openings. The configuration and management of the complete system are via the 2N® Access Commander.



“This was a very large project to undertake. When we were reviewing the options, our focus was on finding an already proven, reliable solution with excellent usability. 2N was certainly able to provide that and exceeded our expectations in terms of service via the distribution partner and the efficiencies they were able to deliver.” Lidl, GB
To find out how 2N can add simple and secure access control to your warehouse or distribution centres, please contact:
Mike Clark
Physical Security Manager, Sektor Ltd


E: mikec@sektor.co.nz
M: 021 588 334
Clint Morris Sales Manager, Axis Communications
E: clint.morris@axis.com
M: 021 906 194
NZSM 15 December 2022/January 2023 AWARD WINNING IP INTERCOMS & ACCESS CONTROL AVAILABLE NOW AT SEKTOR sektor.co.nz/Brands/2n | 0800 735 867 Residential single-unit or spartments Commercial Gated entrances . Lifts access control . Parking buildings . Mobile access technology Distributed in NZ by Sektor Ltd
We’re risk takers, and that’s making cyberattacks more costly
Businesses are addicted to gambling on their cybersecurity, writes Nicholas Dynon. But our big appetite for cyber risk is now being called out by insurers, government… and criminals.

2022 has been a good year for those engaged in cybercrime. With media reporting recently that businesses are willing to pay almost double what they were prepared to pay last year in ransom to stop a ransomware attack, there are spoils to be had.
Research by McGrathNicol Advisory has found that in the event of an attack four in five businesses chose to pay the ransom to the tune of an average $1.01 million+. The average amount that businesses would be willing to pay almost doubled from $682,123 in 2021 to $1,288,608 this year.
And it seems that businesses can’t give their money away to those holding them to ransom fast enough. The research reveals the timeframe for ransom payments has shortened, with 44% of businesses paying within 24 hours (up from 23% in 2021).
Unsurprisingly, businesses are also willing to pay more for cyber insurance. Premiums for cyber insurance collected by US insurance carriers last year, for example, grew by 92% from the previous year. In Australia, a Marsh study has found that cyber insurance premiums have surged up to 80% in the first half of last year, with claims numbers also increasing by 50%.
So, the pay-outs for these cyberattacks are increasing. Whether it’s ransom payments – where the attack is already in progress, or cyber insurance – which is based on the inevitability of an attack, businesses are
digging deeper into their pockets to pay for cybercrime either (i) as it occurs or (ii) with the assumption it will occur.
This begs the question, are businesses adequately investing in their cybersecurity to prevent and prepare for attacks ahead of time?
Reactive: We address fallout not threats
NIST’s Incident Response Process provides an established framework for understanding the four major phases involved in managing cyber incidents: (i) preparation, (i) detection and analysis, (iii) containment, eradication, and recovery, and (iv) post-incident activity.
The Preparation phase is all about setting the organisation up to be able to better deal with an incident if it were to happen. It is during preparation, states NIST’s venerable Computer Security Incident Handling Guide, that “the organization also attempts to limit the number of incidents that will occur by selecting and implementing a set of controls based on the results of risk assessments.”
Actions like paying ransoms and taking out cyber insurance policies are not aimed at minimising the risk of a cyberattack occurring. They are more about containment and recovery, which places them in the third phase of NIST’s process, i.e. post-incident.
According to a range of experts, businesses in New Zealand and Australia are just not doing enough to get on the front foot in relation to cyberattacks. Poor security hygiene, a lack of basic controls, and the absence
16 NZSM December 2022/January 2023
Nicholas Dynon is chief editor of NZSM, and a widely published commentator on New Zealand’s defence, national security and private security sectors.
of risk assessments are creating wide gaps for cybercriminals to exploit.
In a recent 7news report, Professor Sanjay Jha, Chief Scientist at the University of New South Wales Institute for Cybersecurity, said that companies should be doing more to protect data, saying they have to lift their game and “spend a bit more on cybersecurity.”
“I’m just wondering why some simple things like [multifactor authentication] are not being done in companies that should be easy to fix,” he said.
It’s a good question. Why aren’t businesses doing the simple things? Why aren’t they investing in prevention and preparation? Factors like complacency and culture may provide part of the explanation, but, according to behavioural economics, an underlying reason may well be that when it comes to security human nature dictates that we are risk-takers.
Speculative: We bet on losing big Prospect Theory is a behavioural economics model for describing how people make decisions between alternatives that involve uncertainty, or risk. Daniel Kahneman, one of the economists behind the theory, won a Nobel Prize in Economics for his work, so as far as theories go it’s pretty sound.
According to the theory, for most people a small yet certain gain is more attractive than the prospect of a less certain larger gain, but when it comes to losses, the reverse holds true: most
people will risk the prospect of a greater loss rather than incur a guaranteed smaller one.

In one study, participants were presented with two choices: the choice between a certain gain of $500 and a 50% chance of gaining $1,000, and the choice between a certain loss of $500 and a 50% chance of losing $1,000. 84% chose the certain $500 gain over the riskier one, while 70% chose to risk a $1,000 loss over settling for the smaller certain one.
In other words, human nature dictates that we’ll take a sure gain over a less certain bigger one, yet we’ll risk a bigger loss just to avoid a certain smaller one. We are hard-wired to be risk-takers when it comes to security; it’s part of the human condition.
Businesses prepared to gamble on their security are more likely to expose themselves (and their customers’ data) to greater risk, yet they are less likely to put in place adequate controls to minimise their risk. When combined with cyber insurance, this predilection for risk leads to moral hazard.
It’s no wonder the price of ransoms and cyber insurance premiums are skyrocketing. But in addition to rising costs, businesses can also expect that insurers will require them to comply with increasing security requirements as barriers to obtaining and retaining coverage.
According to a recent report by Duncan Cotterill, over the past two
years “the local [New Zealand] cyber insurance market has undertaken a significant adjustment,” with a new baseline being set in relation to “premium, deductible levels, coverage availability, capacity, and underwriting rigor.”
Baseline criteria to obtain cyber cover, include the use of anti-malware software, regular data backups, the use of Multi-Factor Authentication, ensuring software updates are actioned regularly, and updating default credentials.
“Some businesses may need to make some changes to how they operate in order to obtain cyber insurance cover,” states the report, “and businesses may see an increase in the premium they pay for cover.”
You can also bet on cybersecurity becoming an increasingly regulated space, and we’re already seeing this in relation to privacy, and across the Tasman with the recent toughening of the Australian Security of Critical Infrastructure Act. As cyberattacks increase in severity, governments are identifying the need to legislate in order to compel better security behaviours.
Ultimately, while the risk of cyberattack itself may have never provided businesses a strong incentive for better cybersecurity, rising insurance costs and regulation will drag us kicking and screaming towards it –and that’s a sure bet!
NZSM 17 December 2022/January 2023
New Public Safety Network to improve emergency services communications
The Public Safety Network will deliver emergency services with a single secure digital radio network and greatly improved mobile broadband access. Together the technologies will help meet the ever-increasing data and information needs of frontline staff as they are out and about serving the community.
“This infrastructure investment is significant and is what New Zealand’s frontline workers deserve. It will help keep them and the public safe by giving them reliable and secure coverage in urban, state highway and rural areas,” said Chris Hipkins in a 10 November media release.
“New Zealand’s Emergency Services are made up of approximately 35,000 staff and volunteers who attend over five million calls for help every year. They need to be able to respond at any time, and in any part of New Zealand, and for that they need accurate and timely information.
Progressing the Public Safety Network to this build phase has required a significant collaborative effort among the four emergency services. The new network will serve our front line emergency responders for decades to come.
It will be used by Police, Fire and Emergency NZ, Hato Hone St John, and Wellington Free Ambulance and gives them the ability to communicate with each other more effectively

during emergency incidents to keep people safe, protect life and property, maintain law and order, and deal with health events. It could be expanded for other government users in the future.
The network will have two key components: a digital land mobile radio network, which allows emergency services to reliably communicate with each other and prioritised cellular services and roaming, which will increase connectedness to mobile broadband for responders, especially at times when mobile networks are congested or degraded.
We also know first-hand the significant challenges posed by earthquake and climate-related emergencies. This infrastructure investment will support our emergency services to work together more effectively in this challenging environment.
New Zealand’s emergency services have done an incredible job in often very challenging circumstances.
The new network will give them a modern network to replace a critical communications system that’s getting past its best.
The successful bidders who will build the Public Safety Network are a Tait Communications and Kordia joint venture, and Hourua (a Spark and Vodafone NZ (One NZ) joint venture). It’s extremely pleasing to see New Zealand companies and the economy will benefit from this important and skilled work,” said the minister.
Delivery of the Public Safety Network will see the investment of $1.4 billion over 10 years to build and operate the network, roll out new devices to emergency services staff, stations and vehicles, and decommission the existing network.
Emergency services will start transitioning to Cellular Services from mid–2023 and Land Mobile Radio as a regional roll out from 2024. More information about the Public Safety network can be found on the NGCC website: www.ngcc.govt.nz.
18 NZSM December 2022/January 2023
Police Minister Chris Hipkins announces new digital communications network for emergency service workers to roll out from next year.
Photo courtesy of NGCC












SECURITY TECHNOLOGY RELIABILITY Loktronic Limited Unit 7 19 Edwin Street Mt Eden Auckland P O Box 8329 Symonds Street Auckland 1150 New Zealand Ph 64 9 623 3919 Fax 64 9 623 3881 0800 FOR LOK mail@loktronic.co.nz www.loktronic.co.nz For expert advice and assistance with your security locking needs, trust in Loktronic, call us on 0800 367 565 fire door holding electromagnets *Standard terms & conditions of sale apply. GUARANTEE A) B) C) FDH40S unbreakable universal mounting • Low power consumption - low operating temperature • One product suits floor and wall mounting • Universal armature - offsets to 55º to suit doors opening past 90º • Wall mount extensions available • 12 & 24 VDC selectable • Push off button with no residual magnetism • Oversize armature for easy alignment • Emergency release button • Electroless nickel plated armature and electromagnet • Stainless fastenings • Full local support and back up FDH40S/R Surface and Recess mounting This device enhances an outstanding range of unbreakable products which conveniently hold open fire doors. When a smoke/fire alarm is activated the magnet instantly releases the door to the closed position to prevent the spread of smoke and fire. These units feature a choice of 3 covers for optimum aesthetic appeal and durability. The installer can utilise one device for surface mounting or for recess mounting. unbreakable! 21556/1/18 10 YEAR GUARANTEE* 10 YEAR GUARANTEE* Designed, tested and produced in New Zealand to AS4178 A) Wall mounted,126mm extn. tube (overall 202mm) B) Wall mounted, 156mm extn. tube (overall 232mm) C) Wall mounted, 355mm extn. tube (overall 431mm) Satin Aluminium Gloss Black Gloss White 12 & 24 VDC selectable Option A – Surface Mounted GUARANTEE Option B – Recess Mounted Standard, floor mounted, wall to door distance 114mm NZ made
What next after resilience? Wisdom from AISA
CyberCon2022
NZSM correspondent Jennie Vickers attended @CyberCon2022 in October, gaining wisdom from some of the most inspirational speakers on the planet. She shares her big takeaways from the Australian Information Security Association’s flagship event.
Remember when you were eleven and you got back to school after the holidays and saw friends and shared experiences? You may recall the din and the excitement. That was how it was at @ CyberCon2022 in Melbourne, after two long years away.
I vaguely recall that the school return thrill, lasted less than a day, but I can report that the electricity of reconnecting continued for the full three days.
The theme of the event was “Resilience in the Cyber World”. A good theme and a topic we continue to grapple with.
An event attracting thousands is able to bring in big global speakers,
and AISA did not disappoint. To wrap up 2022 and maybe to help frame our resolutions for 2023, here is a selection of thoughts, ideas, and soundbites from a selection of these globally recognised speakers.
Captain Chesley ‘Sully’ Sullenberger
Ric Elias of North Carolina was a passenger in Row One on Flight 1549 which crash landed 13 years ago on the Hudson River in New York City. This experience of having no control over his next 3.5 minutes, and having his life in someone else’s hands, changed his life.

He was not a speaker at @ cybercon2022 however, the pilot that day was Captain Chesley ‘Sully’ Sullenberger. and he was the closing speaker of this event.
Jennie Vickers is CEO of Zeopard Consulting and the inaugural IFSEC Global Security Influencer of the Year.

20 NZSM December 2022/January 2023
US Airways Flight 1549. Image from Wikipedia
Within minutes of commencing, Sully stressed that this Hudson River miracle required the efforts of a whole team, including the first officer, Jeffrey Skiles, the crew, the passengers, and everyone on the ground. That success was as much a result of teamwork and adherence to procedure as it was of skill and coolness under pressure.
Sully pointed out that they had just 3.5 mins to find a solution that was not in the checklists or manuals, but behind those 3.5 mins was a lifetime of learning.
He explained that approximately 45 years ago, aviation safety changed with the introduction of a raft of new ideas around the role of people. The focus came onto the idea of “turning a team of experts into an expert team”. They recognised that compliance alone is a necessary but not a sufficient condition for safety.
“We also had to have the resilience and other systems and knowledge to be able to handle things we hadn’t trained for or envisaged,” Captain Sullenberger told his audience.
Another set of changes involved reducing the flight hierarchy between the captain and the rest of the crew. They made it psychologically safe for the most junior member of a team to approach a captain about an issue. They made it “about what is right not who is right”. There was a dual right to speak but also the responsibility to speak up.
Jumping back to recall his air force days and being a fighter pilot working in fast speed low altitude formations, he pointed out that the real learning from rapidly unfolding events and experiences, occurred at the post flight debriefs, where leaders and followers held each other to account.
Those brutally honest exchanges about what worked or didn’t and why made the difference. The lessons learned process is why aviation has been so safe for many years, and this is an essential part of an airworthiness system.
During the Q&A session the obvious parallels to cyber events were drawn and it was clear that too few in the audience saw this approach paralleled in their organisation, but many clearly thought it should.
Erin Brockovich
Earlier in the event the keynote speaker was Erin Brockovich, known to many thanks to the movie starring Julia Roberts, and now to many millions more as an environmental activist and passionate advocate for protecting water as a fundamental human right.
Erin was quick to identify that she was not in the room to talk about cybersecurity but was there to share her thinking which was relevant to security. Her big opening volley was around the need to go back to listening to our instincts, using intuition, and being connected to our environment, to people, and to ourselves. With a rare suggestion, she identified an unexpected benefit of COVID-19 to the world in that it sat us down, triggered a reboot and reset, and forced us to be more awake to our environment.
Published during COVID-19, her book Superman’s Not Coming’ is about US water and infrastructure issues but has relevance to everyone concerned about security issues in their organisation or life. “Whatever we do, we keep looking for someone else to give us the answers when the answer lies within the person in the mirror,” she said.

eCLIQ - Rethink the Key
eCLIQ is uncomplicated and reliable, without compromising on security. Each key is individually programmable, offering; password protection, authentication and audit trails.
With its extensive range of different cylinder types, the eCLIQ system is designed for every kind of use, from the company entrance gate, to securing the alarm systems, lift doors and cabinets.

www.assaabloy.com/nz

An electronic contact between the key and cylinder transmits power and data.

Programmable, water resistant key with LEDs.
Erin introduced a term unknown to most of us in the room, the word “Sticktuitiveness”. Yes, it is a real word, and it means dogged persistence and perseverance. “This humanistic sense
Fast and easy battery replacement. Programmed with flexible access rights and time schedules.
Cylinders are easy and quick to install, no cabling is needed.

NZSM 21 December 2022/January 2023
New, future-proof CLIQ ® chip generation with AES encryption and rapid processing speed with efficient energy management.
is all about using intuition, to follow what does not feel right.”
On leadership, Erin’s philosophy is that it is not about being up the front but about seeing the quality in another and pulling them in to work with you. “I want to come in and work with you, how do we collectively get something done?” If you are worried about cyber “you ask questions, you plan, you be prepared, you implement an action.”
Erin admitted she was freaking out a little about speaking to a cyber community, so she went to her bank and asked them whether it was a “big thing”. The Manager said cyber is all they do and shared a story of a fraud. The skills that caught it before it was too late were all those she talks about.

“Be you, be present, if something does not feel right, if you are uncertain, step out of that box,” she said. “Never be afraid to activate your own instincts, rely on them, work with them, believe them.”
Answering a question about how to get people to listen to hard truths about security risks, her advice was to allow space for people to process and give them facts but recognise that people struggle to believe truths if they are driven by fear.
Steve Wozniak
Steve Wozniak (Woz) is a rare speaker who can provoke a large auditorium full of people to smile and keep smiling. He was his authentic self and did not talk in sound bites. Sharing stories of Apple’s history, he reminded us that the iPhone was the greatest product introduction ever. “I’ve got more power than Superman with my iPhone…” (we possibly need to connect him with Erin Brockovich!).
My favorite thing he said has resonance for everyone going into the holidays and thinking about the person they want to be in 2023. His consistent message for the past decades (see his interview in The Guardian from 2016) is: “Everything you do should have an element of fun in it. Happiness to me is smiles minus frowns (H=S-F). Increase your smiles, do a lot of fun things, enjoy entertainment, talk with people, make jokes. That’s creativity.” No more frowning in 2023!
Ric Elias
Finally, back to Ric Elias. Apart from cofounding Red Ventures, a portfolio of digital companies in North Carolina in 2000 that has grown to 3,000 employees across several countries, he a survivor of aforementioned Flight 1549.
These days, as a result of his near miss experience, he runs a portfolio of tech brands with a strong social focus. His four-minute TedTalk from TED2011 is worth a quick listen. It is entitled “3 things I learned while my plane crashed”. Sully’s wisdom comes from the cockpit, from a position of leadership and a place of control. Ric’s wisdom comes from the back end of the plane, where there’s a complete absence of control.
Wisdom from Ric includes:
• Live with purpose, on purpose;
• This moment is the only one that’s guaranteed;
• If we live each day like we are running out of time, making every second count, we will live with no regrets;
• Compete only against who you were yesterday. There will always be someone who is smarter, stronger, or luckier - but what matters most isn’t winning.
• Give your best to the work that’s worth doing, so you can earn the right to keep doing it.
Leader or follower, this combined wisdom has something for everyone.
22 NZSM December 2022/January 2023
Security licensing requirements for the install, servicing and selling of security systems
The following statement has been jointly produced by the Master Electricians and NZSA, and is intended to provide guidance on the application of legislation covering registration and licensing and ensuring that customers are provided with consistent and appropriate advice and service.
Security services provided by an electrician or electrical company:
• A Registered Electrician is exempt from requiring a Certificate of Approval (CoA) as a Security Technician for the install or service of security systems including intruder alarms, access control and camera systems.
• Where a registered electrician for valuable consideration enters a premise not owned by himself/herself or his/ her firm for the purpose of selling or attempting to sell a security system or to advise the owner or occupier of the premise on the desirability of having a security system installed, they are deemed to be acting as a Security Consultant and must hold a Certificate of Approval in the category of Security Consultant.
• Where an electrical company has an employee whom is acting as a Security Consultant and is required to hold a Certificate of Approval as a Security Consultant, it follows that the company must also hold a Company Security Licence under the Security Consultant category.
• It is recommended that where an electrical company or a registered electrician is required to hold a company security licence or Certificate of Approval under the Security Consultant category, that they also licensed under the Security Technician category.
Definitions:
• The term Security Technician is defined in Section 6 of the Private Security Personnel and Private Investigators Act 2010: https://legislation.govt.nz/act/ public/2010/0115/latest/DLM1594499.html
• A Registered Electrician is covered within Section 22(d) of the Private Security Personnel and Private Investigators Act 2010:
• https://legislation.govt.nz/act/public/2010/0115/latest/ DLM1594521.html.
Security services provided by a security employee or security company:
• Where a technician installs or services a security system (intruder alarm, access control or camera system) they must hold a Certificate of Approval under the Security Technician category.
• Where an employee of a security company for valuable consideration enters a premise not owned by himself/ herself or his/her firm for the purpose of selling or attempting to sell a security system or to advise the owner or occupier of the premise of having a security system installed, they are deemed to be acting as a Security Consultant and must hold a Certificate of Approval in the category of Security Consultant.
• Note: In those situations where the sales process is conducted from a site owned or occupied by that party, there is no requirement for the individual to hold a Certificate of Approval or the company to hold a security licence (e.g Bunnings, on-line sellers etc).
• Where a company has an employee whom is required to hold a Certificate of Approval as a Security Consultant, it follows that the company must then hold a Company Security Licence under the Security Consultant category.
• Where a company provides the installation or servicing of security system’s they must hold a Company Security Licence under the Security Technician category.
Definitions:
• The term Security Technician Employee is defined in Section 14 of the Private Security Personnel and Private Investigators Act 2010.
• The term Security Consultant Employee is defined in Section 15 of the Private Security Personnel and Private Investigators Act 2010.
NZSM 23 December 2022/January 2023
ICT updates Geutebrück
G-Core integration to support V6
Access control manufacturer ICT announces feature enhancements are now available to support v6.1 of the Geutebrück G-Core VMS within Protege GX.
When integrated, the Protege GX Geutebrück Video Service provides a comprehensive sync between Protege GX and the G-Core NVR server. Camera feeds are seamlessly embedded into fully customisable Protege GX status pages or interactive floor plans, delivering complete oversight of any property.
This integration enables operators to confirm alarms or events in real time and view live and historical video footage without the need to leave the platform.
This bi-directional exchange of information enables the communication of PTZ triggers and alarm interfaces back to the NVR for actionable site security.
“Aligning with ICT enables us to provide a unified solution for security personnel, said Alan Johnson, General Manager of Geutebrück. “A core value at Geutebrück is intuitive usability, which I am happy to report continues with this update”.
Temperature and humidity notification and detection events are now actionable within Protege GX alongside an associated/linked camera, allowing operators to monitor or customize alarms based on the end-user requirements. Sensor audio alarms are now also manageable as events within the system to strengthen the monitoring capabilities of operators.
This upgrade continues to support License Plate Recognition (LPR) via a Geutebrück server-based and/or camera-based LPR algorithm, enabling Protege GX to detect and assign license plate credentials to users for access control such as gate entry.
Richard Hawker, Chief Revenue Officer for ICT says, “Geutebrück offers a great solution, we’re delighted to be able to extend our support to v6.1 of G-Core and look forward to implementing future improvements”.
Protege GX feature support for G-Core 6.1 also enables operators to:
• View historic and archived video footage.
• View live or archived video footage directly from an event associated with a camera.
• Automatically launch a camera view window when specific types of events occur.
• Send pre-set PTZ commands to the VMS in response to a Protege GX event filter.
• View HLI events directly in Protege GX such as motion detection, low disk space, excess body temperature detected, license plate detected, sound detected, camera online/offline and camera physical on/off.
Geutebrück G-Core manages video images and is the base for an optimally customisable complete solution. The system can be used as a stand-alone unit or expanded to any size and complexity by linking several G-Core systems. The range of features is customised to meet any specific requirements via selectable options.
As an open platform, G-Core provides access to a large number of integrations with leading manufacturers such as ICT. G-Core is especially easy to use and intuitive to operate which complements the Protege GX platforms similar ethos for usability.
Note: Protege GX version 4.3.298 or higher is required, valid Protege camera licenses and version 6.1.0.392 of Geutebrück G-Core are needed.
24 NZSM December 2022/January 2023


Loktronic Limited Unit 7 19 Edwin Street Mt Eden Auckland P O Box 8329 Symonds Street Auckland 1150 New Zealand Ph 64 9 623 3919 Fax 64 9 623 3881 0800 FOR LOK mail@loktronic.co.nz www.loktronic.co.nz Loktronic for Sales, Service and Support LoktronicLimi t e d sraey03 s’ZNgnicivres S e c u r ity Industry
Violence and organised crime up: annual retail security survey

The 2022 edition of the National Retail Federation’s Retail Security Survey indicates more and more retailers in the US are turning to smart tech to reign in $100 billion worth of losses
One rapidly ballooning issue is retail shrink, a nearly $100 billion problem for the industry, according to the National Retail Federation’s (NRF) 2022 National Retail Security Survey (NRSS).
The National Retail Federation’s Retail Security Survey is an annual survey of retail loss prevention professionals that covers retail security issues such as inventory shrink, employee integrity and organised retail crime (ORC). This year’s report includes a closer look at the impact of ORC on the retail industry.
Overall, the study found that –consistent with the last five years – the average shrink rate in 2021 was 1.4%. When taken as a percentage of total retail sales, the shrink represents $94.5 billion in losses, up from $90.8 billion in 2020.
Responses indicated that retail shrink is primarily driven by external theft (37%), including theft attributed to ORC, with employee/internal theft accounting for 28.5%.. Retailers, on average, saw a 26.5% increase in ORC incidents in 2021.
Violence
Eight in 10 retailers surveyed reported that the violence and aggression associated with ORC incidents increased in the past year. Over half reported that mass violence and gun violence had also risen in recent years.
Labour shortages, challenges with employee retention and hiring, and issues related to enforcing COVID precautions, contributed to the risks of violence and hostility. The climate in the US of active assailants and gun violence added to retailers’ concerns around keeping employees and customers safe.
The majority of those surveyed (81.2%) reported that ORC offenders are “somewhat more” or “much more” violent when compared to just one year ago. Over one third (35.9%) reported that ORC offenders were “much more” violent when compared with one year ago.
COVID-19
COVID-19 has had profound implications for the retail risk landscape, not least in relation to
security. A staggering 89.7% of respondents, for example, reported that COVID-19 had resulted in an increase in the risk of violence within their organisation.
The majority of respondents also reported that overall risk had increased since COVID-19, as well as the risk of shoplifting, ORC and employee theft. In contrast, 60.1% of respondents said that COVID-19 had no impact on cargo theft risk at their organisation.
Other areas where respondents reported that the COVID-19 pandemic had impacted their risk included: (1) labour-related challenges; (2) increased violence and hostility; (3) and issues related to masking and maintaining COVID-19 precautions.
Labour shortages and turnover have had significant effects on retailers,
26 NZSM December 2022/January 2023
including serious implications for loss prevention. “Retailers may not have sufficient employees in the store to provide informal guardianship, that is, to simply deter retail crimes with their presence,” stated the report.
“Employee turnover can also reduce retailers’ ability to maintain trained staff and develop their workforce –for example, if an employee develops experience controlling loss and mitigating risks within a store and then leaves, the retailer must then train another employee to do so.”
Technologies
Retailers are allocating significant resources to prevent the victimisation of their employees, customers and organisations. Almost one third of retailers surveyed have established a dedicated ORC team, and those that have tend to record more apprehensions and prosecutions.
Many have boosted their budgets for loss prevention and technology. 52.4% increasing their budgets specifically for capital and equipment, including such technological solutions as artificial intelligence-based video analytics at
self-checkouts, self-service locking cases, autonomous security robots and licence plate recognition.
With increasingly sophisticated risks, retailers are turning to new strategies and technologies. Retailers reported that they were implementing or planning to implement such systems as RFID (38.6%); AI-based pointof-sale (POS)/self-checkout (SCO) video analytics (29.8%); License plate recognition (19.3%); and/or self-service locking cases or lockers (17.5%), AIbased perimeter surveillance (14%); advanced weapon detection (12.3%); facial recognition (12.3%).

“RFID has many uses throughout retail, from managing and tracking inventory in the supply chain to maintaining up-to-date in-store inventory records, or identifying and recovering stolen products,” stated the report. “AI-based POS/SCO video analytics can help detect crimes such as ticket- or product-switching, or sweethearting.”
“Ticket- and product-switching involves retail offenders using the barcode from a less expensive item in place of the barcode for a more expensive item while scanning
products, while sweet hearting includes a variety of offenses at the POS involving an employee and a “sweetheart” – someone to whom they are giving “favourable” treatment.”
According to the report, many of the technologies that retailers are implementing are designed to provide greater threat awareness. “For example, licence plate recognition systems, perimeter surveillance, facial recognition and multi-sensor parking lot surveillance towers/units can all help retailers detect when a potential threat has arrived on the premises, as well as gather information about suspects who entered/exited the store and/or the parking lot.”
In addition to the tech investment, the majority of respondents reported needing greater analytic and investigative skills.
Interestingly, the report indicated that retailers are wanting stronger ORC legislation, as well as better law enforcement, increased penalties for theft, and a reduction in crime thresholds. 70.8% of respondents reported increases in ORC in areas where crime thresholds had been increased.
NZSM 27 December 2022/January 2023
The Wisdom of the Crowds coming through loud and clear at CyberCon2022
In this second part of her despatch from CyberCon2022, NZSM correspondent Jennie Vickers delivers a bumper harvest of collective wisdom with the best bits of the event’s speaker presentations.
Back in 2004, James Surowiecki published the book The Wisdom of Crowds: Why the Many Are Smarter Than the Few and How Collective Wisdom Shapes Business, Economies, Societies and Nations.

Ideas around the benefits of collective wisdom ring true at conferences and tradeshows where line-ups of technical experts converge to share their thoughts and ideas. With over 30 topic streams and hundreds of speakers, there was more than enough on CyberCon’s agenda to provoke new ideas and build a plan of action for 2023.
But, one can’t be everywhere, so I’ve carefully identified a number of themes inspired by several of the speaker presentations, which will be of interest to security professionals when they wind back up after a well-deserved summer break.
‘Cyberworthiness’: Adopting a philosophy from aviators
In his presentation, Squadron Leader Arjun Xavier of the Royal Australian Airforce introduced the idea of ‘cyberworthiness’. The “-worthiness” concept is familiar to many in the context of air and sea, but this extension into cyber provides a useful framework.

It is, in essence, a risk management and continuous improvement
framework, enabling the Australian Defence Force to effectively manage risk in cyberspace as they execute their mission. An underpin is “Don’t get chained to compliance.”
Arjun explained that cyberworthiness is not just about security. Traditional cybersecurity is focused on activities designed to ensure the confidentiality, integrity, and availability of systems. Cyberworthiness, on the other hand, “is rooted in survivability – business continuity, in corporate terms – and assurance of our mission.”
For all of us, our future cyberworthiness governance framework needs to be scoped across three key pillars – people, processes, and technology [the reflections of ‘Sully’ Sullenberger (refer to my other article in this issue of NZSM) around airworthiness changes from 45 years ago would indicate that many
organisations have a long way to go understanding the people side of this puzzle.
Group Efforts, Partnerships and Collaborations
A confession. I am hooked on a Netflix Korean drama called “Vincenzo”. It is about a Korean-born mafia consigliere in Seoul. The point of this reference is that the series demonstrates the many ways in which the mafia and other crime groups (pre-cyber) around the world have always collaborated and worked in partnership, where it is of value to them to do so.
A number of speakers at Cybercon2022 alluded to the importance of the good guys (us) getting as good at collaboration as the hackers. Many of them recognised that we’re still not as good as we need to be.
The idea of being out-played in this regard was reinforced when speaker
28 NZSM December 2022/January 2023
SQNLDR Arjun Xavier
Glenn Maiden
Glenn Maiden explained the work of Fortinet as part of the World Economic Forum’s (WEF) Cyber Atlas Project.
“Defeating global cybercriminal organisations requires a global group effort with strong, trusted relationships among cybersecurity stakeholders,” says the WEF. “Criminal enterprises function almost exactly like corporations. Once attackers start to quit out of fear of being exposed and arrested or feel the profits aren’t worth the risks, then cybercrime may begin to recede.”
Several different speakers from Accenture shared this view of the need for better collaboration, recognising that “visibility across enterprises and government agencies is also essential to allow common goals, training and governance to be implemented, and to reduce duplicated efforts.” The reality is that CaaS (Cybercrime as a Service) is growing faster than SaaS!
Continuing Cyber ignorance
Paula Januszkiewicz is a rockstar MS Security Enterprise Expert, who both delivered a keynote and ran half day workshops. Interviewing Paula, we got around to a key dilemma facing executives embracing Digital Transformations and IOT where the risks are rising.

Paula’s view is that if we apply strict security rules, no one will be able to get any work done, so a balance needs to be struck between safety, usability, and practicality. If executives do not understand the underlying technology, striking that right balance is hard.
Cyber focus at a government level
In her opening speech, Hon Clare O’Neil MP, Australia’s Minister for Home Affairs and Minister for Cyber Security said that the “new Government in Australia has made the decision to have a cyber security minister because we want to elevate this issue to the level of importance that it so clearly is for Australia business, for Australia citizens and very much for our nation.
“Cyber is everything and it is everywhere,” she told the CyberCon2022 audience. “A resilient cyber ecosystem is going to be
fundamental to our country’s future.”
We need a champion of Cyber from Government here in New Zealand.
2023: Try telling a different cyber story
Mina Zaki from KPMG ran a useful session on how to use storytelling to change the narrative. She made the case for well-reasoned, relevant, and problem focused case studies along with a better understanding of the way a story engages brains.
Elevate security issues to boardlevel concerns and language
Talking about changing the narrative, Michael Shepherd from Accenture commented that “essentially it boils down to catalysing the business relevance, capturing the strategic picture of cyber security with the right scorecard, and speaking the language of business impact in all cyber security communications to the Board.”
Thales ANZ, reminds us that “It’s not about compliance, it’s about survival in a dangerous and complex world.”
Persia Navidi of Hickmans lawyers noted – with thoughts heavily laden with animal references – that “when it comes to board directors, it goes without saying that cyber events are no longer “black swan” events, but despite this they’re still very much treated as the elephant in the room.”

Securing Critical Infrastructure
Amy Ormrod and Zoe Thompson from PwC were joined by colleagues from Europe for a global perspective. A few key takeaway thoughts included:
Ormrod
• If you can’t map your asset interdependencies, you have no way of understanding what is critical.
• You need a security by design lenses across the entire organisation.
• Internal silos are more of a threat than the external threats.

• Manage expectations, spend is never going down.
• Where is CI data? Is there a war coming near your data?”
Is it time for your Board’s Committees to play a greater role?
Ashwin Pal of RSM Australia is a friend of New Zealand, having previously spoken at the New Zealand Defence Force / New Zealand Defence Industry Association’s IDEAS2020 event. He presented on the role of ARCs (Audit and Risk Committees of Boards). Ashwin’s summary points are a useful list:
• Cyber security is a key business risk and must be treated as such.
NZSM 29 December 2022/January 2023
Mina Zaki
Michael Shepherd
Jason Brown Principal Advisor, Security and Risk to the Board of
Amy
• As a result, Board / ARC members’ responsibility for cyber security is increasing.
• Board / ARC members MUST ask the right questions of management and THEMSELVES to be able to discharge their duties.
• Cyber risk needs to be quantified so it can be managed.
• A methodical program is necessary to stay on top.
• You cannot control what you cannot measure.
“Boards and Executives must treat cyber risk as a high priority business risk,” he said in closing. “It

must be part of the Enterprise Risk Management framework with risk appetite clearly defined and cyber risk mitigated to an acceptable level. Unless this methodical approach is taken, breaches will continue to increase.”

Data: How about we go with effective de-identification for now?
Dr Ian Oppermann, the NSW Chief Scientist, delved into the vexing issue of personal information and the failures of de-identification attempts. Enter stage left, the PIF Project Tool. This project is a collaboration between the Cyber Security CRC, CSIRO’s


Data 61, the Australian Computer Society (ACS), and the NSW and WA Governments.
“The Personal Information Factor (PIF) Tool measures the risk associated with releasing a dataset,” explained Dr Ian. “When risks are high, an AIenabled tool analyses attack vectors and transforms the data, using provable privacy perturbation techniques, making it suitable for publication.”
Procurement: How to pick the right security horse
Mark Hofman, CTO of CyberCX caused a few OMG moments. I never say OMG, but in this case, Mark shared the results of a Gartner report from July 2022 which found that 56% of organisations said they had a high degree of purchase regret over their largest tech-related purchase in the last two years. This is shocking but credible.
Mark had screeds of good advice (article to follow in 2023) but to vendors he said, “get better at articulating both your licensing model and the problems you actually solve; and to buyers the usual entreaty to get better at articulating requirements but also ensure a whole cross organisation team is involved in the procurement.”
Final Thoughts: We need more sessions on convergence
It really is time for events in 2023 to get better at combining OT and IT and talk convergence across the whole spectrum. The events organised by associations are better placed to make this happen… and it needs to, as a matter of urgency.
30 NZSM December 2022/January 2023
Ashwin Pal
Dr Ian Oppermann
Mark Hofman
Gallagher named Security Software Manufacturer of the Year at Security & Fire Excellence Awards

Security manufacturer Gallagher has been awarded the Security Software Manufacturer of the Year accolade at the UK’s 2022 Security & Fire Excellence Awards.
Taking place at the London Hilton on Park Lane on Wednesday 23 November, winners of the annual awards came from all across the industry. Among them was New Zealand’s Gallagher.
The Security Software Manufacturer award category was created to celebrate the efforts of a security software vendor who has gone above and beyond in the areas of innovation; marketing; commitment to high physical, integration and cybersecurity standards; being a great employer, and building products that meet or exceed the latest environmental and energy usage standards.
“We’re absolutely delighted to be named ‘Security Software Manufacturer’ of the year and to be recognised for the all-round excellence of our Gallagher Security Command Centre software,” said Gallagher’s Regional General Manager for the UK and Europe, Richard Huison.
“Our customers are at the forefront of what inspires our innovation and I believe that our ability to consistently deliver such a high standard of product and service is a direct reflection of the outstanding levels of knowledge and skill held by our employees.
“This culture of innovation and excellence ensures that Gallagher
remains a market leader and creates the enduring and successful partnerships we experience with our customers.”
Command Centre is the software at the heart of Gallagher’s integrated security solutions, a centralised platform that delivers control of every aspect of a site. Fully scalable and supported by continuous investment in research and development, Command Centre supports future growth and changing security requirements.
The platform provides perimeter solutions, intelligent access control and building management for critical sites with some of today’s highest security requirements.
Now in their twenty-third year, the Security & Fire Excellence Awards highlights the very best people, projects
and processes that the security and fire sectors have to offer across a total of 25 award categories.
“Many congratulations to all of this year’s winners and finalists including those NSI approved companies amongst them, who work tirelessly in keeping people, property and places safe across the UK,” said Richard Jenkins, National Security Inspectorate Chief Executive.
“The Security & Fire Excellence Awards is a long standing and respected event in the industry calendar and it never fails to remind us of the significant contribution and outstanding dedication of those who work in the private security sector to collectively make the UK a much safer place.”
NZSM 31 December 2022/January 2023
New Zealand Security Association CEO’s November Report
NZSA CEO Gary Morrison talks “Saved a Life” Awards, Fair Pay Agreements, review of industry training qualifications, Countering Terrorism and Violent Extremism Conference, and more.
In opening, congratulation to all of our finalists and award winners for the annual New Zealand Security Awards event held at the Hilton Hotel during September.

It was a fantastic event where we had the chance to recognise and celebrate the efforts of who work in the industry and in particular, the twenty award winners who have excelled in their roles.
owned companies such as Crosbies Security who were awarded the Outstanding New Product or Service Award for their Smart Solar Towers product.
I’m pleased to advise that the 2023 NZ Security Awards will be held on the 15 September at the newly opened Te Pae Convention Centre in Christchurch – make sure the date is in your diary!
Gary Morrison is CEO of the New Zealand Security Association (NZSA). A qualified accountant, Gary was GM of Armourguard Security for New Zealand and Fiji prior to establishing Icon Security Group.

As is normal, many of the 250 plus attendees were bought to tears listening to the acts of bravery and the humility of those being recognised. The event also highlighted the real diversity that exists within our industry across gender, ethnicity and age (where those recognised ranged from their early 20’s to our supreme award winner who is in the later stages of his career).
It was also great to see a range of companies represented across the categories, including smaller privately
NZSA “Saved a Life” Awards Commencing in the New Year, the NZSA will launch a new award programme that recognises and celebrates those workers within our industry who have saved a life, or lives, through their actions.
This follows on from the wellreceived and very successful Covid Guardian award programme that we ran during the lockdown periods.
Nominations can be submitted at the time and with recipients recognised within each newsletter. Recipients will
32 NZSM December 2022/January 2023
receive a certificate and trophy to be retained and will also be recognised at the annual awards event through a roll call.
We are also hopeful of receiving ongoing media coverage for the awards. Look out for more details in the next month or two.
Update re Fair Pay Agreements
(FPAs)
This is a very important issue that may have significant implications for those providing physical security services such as guards, patrols, cashin-transit and possibly monitoring/ communication centres.
The Fair Pay Agreements Bill has passed its final reading and will likely come into force at the end of November with applications for a “Fair Pay” Agreement (FPA) able to be lodged from early December.

The Bill means that Unions will be able to start (initiate) sector-wide negotiations with employer associations (such as NZSA) to create mandatory agreements that set minimum terms and conditions for all employers in a sector, not just for a single employer.
It is important to note however that even though we expect the Security Sector to be amongst the first industries to be initiated, in a practical sense there is nothing that our members need to do immediately to prepare for this change in employment relations.
As the peak body for the security sector, the NZSA has sought expert guidance and consulted with key stakeholders such as MBIE to ensure that we can provide our members, and all industry employers, with the necessary governance, systems and processes should we be required to represent and support them.
We will keep you informed on developments over coming weeks and also remind our members that more information can be found under the FPA tab on our website (provide link).
Review of industry training qualifications
With the new WDCs (Workforce Development Councils) now resourced and operational, one of their first actions has been to review qualifications on the NZQA
framework to identify those which are being used and to ensure that they retain relevancy to industry.
The security industry is represented by two WDCs – Ringa Hora (Service Industry) for the physical security sector and Waihanga Ara Rau (Construction and Infrastructure) for the electronic security sector.
We, and a number of our members and industry stakeholders, have been fully involved in the review process and we are pleased to advise that we fully support the outcomes to date.
The next stage of the review process will commence in 2023 and involves looking at the Unit Standards that make up each qualification. From experience, this can become a long and drawn-out process but given the unit standards across both physical security and electronic security are fairly recent there is a degree of confidence that we can conclude this reasonably quickly and start to move onto the qualification development phase, including a Level 5 for the NZ Certificate in Security.
As a general comment, the move from Training Organisations to the
NZSM 33 December 2022/January 2023
WDC’s has caused a significant hiatus in industry training over the last two years however there is cause for optimism in that we can now start to look at delivering training in a manner that can achieve the best outcomes for industry and our workers.
CATE Conference (Careers and Transition Education Association) I’m sure that most of our members will agree that the greatest challenge they face currently is in attracting sufficient staff to meet service requirements. This issue isn’t unique to the physical security sector, with almost all electronic security providers experiencing extreme staff pressures as well.
Whilst it is very difficult to quantify exact numbers, we estimate that the wider security industry is currently short of at least 2,500 workers.
One of the challenges for the industry is the lack of understanding by the general public of the diverse range of services and roles that fall within the scope of the security industry. We have developed a very comprehensive website (www.securitycareers.co.nz) that includes an in-depth overview of roles and pathways but need to better educate those seeking employment, and particularly school leavers, on the opportunities that exist within the security industry.
One initiative we have implemented is to create greater awareness of our industry, and the Security Career website resource, across all school career advisors. As part of this, I will attend and man our stand for three days at the CATE Conference in Christchurch in late November. This event brings the majority of school career advisors together on an annual basis and provides the ideal opportunity to sell our industry and career options.
Countering Terrorism and Violent Extremism Conference
I’m pleased to be attending the Whenua Taurikura Hui 2022 being held in Auckland at the start of November. The focus of the hui will be on all of society approaches to preventing terrorism and violent extremism in New Zealand.
I have previously provided representations to government working groups on the capability and capacity of the private security sector and how we can contribute towards improving our national resilience towards terrorism and violent extremism.
It is also worth highlighting that the New Zealand Security Intelligence Service and within the last week published a document “Know the signs – A guide to identifying the signs of violent extremism”. The guide aims to
raise awareness of indicators of violent extremism and to help people identify some of the key warning signs.
I would certainly recommend that employers should read this document and consider distribution or promotion to their staff and customers. The document can be downloaded from the NZSIS website.
Master Electricians – licensing requirements
Several years ago, the NZSA and Master Electricians produced a joint release that provided clarity with regards to the licensing requirements that pertain to electricians when selling, installing or servicing security systems including alarms and cameras.
In very simplified terms, an electrician who is registered with the EWRB is exempted from the need to hold a CoA as a Security Technician when installing or servicing security systems. Should that electrician however be involved in selling or giving advice on that security system, they need to hold a CoA under the Security Consultant category.
We are currently working with the Master Electrician Association on updating the joint release and expect to be able to promote and distribute the document within the next few weeks.
Virtual Reality (VR) Training
The use of the e-learning and virtual reality training platform for the delivery of the CoA training continues to grow and is now part of the accepted delivery model for a number of security businesses.

The VR platform is also being used for attracting workers to our industry with MSD hosting a series of Virtual Reality Job Expos around the country. The expos provide a safe and welcoming environment where attendees get to experience what it is like to work in an industry using the VR headsets. There are 12 industries represented and to date, security has been one of the most popular with the attendees.
As always, we welcome all comments and feedback on NZSA or industry issues and activity.
Keep safe and well.
34 NZSM December 2022/January 2023


Loktronic Limited Unit 7 19 Edwin Street Mt Eden Auckland P O Box 8329 Symonds Street Auckland 1150 New Zealand Ph 64 9 623 3919 Fax 64 9 623 3881 0800 FOR LOK mail@loktronic.co.nz www.loktronic.co.nz Loktronic for Quality and Value backed by Guarantees LoktronicLimi t e d sraey03 s’ZNgnicivres S e c u r ity Industry
NZIPI Update
NZIPI Website to Include Different Categories of PI
Along with the recent name change and amended rules, NZIPI has invested in creating a new website, check out www.nzipi.org.nz. Now members of the public are able to search for professionals by region and by category of licence. The object being to differentiate between, (1) Private Investigators, (2) Health and Safety Investigators and (3) Auditors and Forensic Accounts. The change comes about from PSPLA. After some time deliberating, obtaining comment and hearing submissions from interested parties, on 30 September 2022, the PSPLA issued formal Decisions regarding the two latter categories. The PSPLA found that the work performed by both employment investigators and forensic accountants did require the companies and individuals performing the work to hold a Private Investigators Licence and/or COA. Certain exceptions applied. The Decisions are [2022] NZPSPLA 030 and [2002] NZPSPLA 031. The NZIPI website will be a work in progress as more individuals in all three categories join.
AGM
NZIPI held its AGM online on 24 November 2022 with a new Executive Committee being elected, they are; Chair - Bruce Couper Vice Chair - Machelien Sherry Treasurer - Megan Ruby (independent accountant) Committee - Sue Kelly Committee - Russ Mincher Committee - Karl Ruby
At the AGM three long term members of the executive stood down Ron McQuilter, Phil Roigard and Rob Nicholl. Topics covered at the AGM were varied with the new Chair outlining his proposed vision.
Ron McQuilter (outgoing chair) updated the members on the Institute’s application to renew the member’s 241
access to the Motor Vehicle Register, a task that took considerable time, effort and assistance from a Barrister. Access to this Register requires a stringent regime to be in place with member training, the checks being made via Infolog and regular random audits of checks. Access can only be for approved purposes, domestic work is for example one of the excluded purposes. The outcome is Gazetted and all new members must also be approved by NZTA before they have access.
Life Membership(s) Awarded
At the AGM, Life membership of the NZIPI was awarded to Ron McQuilter and Phil Roigard, bringing the total number of Life members to three. To be awarded life membership, the membership must vote and there must be a consensus of no less than 65% of all the current financial members voting in favour.
Both Ron and Phil are founding members of NZIPI and both have served on the executive for that many years, it almost impossible to count. The fact that the members vote in excess of 65% speaks volumes of the esteem held by their peers for Ron and Phil.
Ron McQuilter
In May 2023 Ron will have been a PI in New Zealand for 40 years since arriving from Scotland in 1983. Nine years ago, Ron moved from Auckland to Mount Maunganui and continues to run Paragon NZ and associated entity.
Ron has been the Chair of NZIPI for the past 17 years straight and arguably the voice of Private Investigators in New Zealand for many years. It was not because no one wanted the job, each year Ron would offer to stand down, but he was continually re-elected. In the role of Chair, Ron has also assisted the PSPLA in considering complaints against investigators, able to offer a real world expert opinion on
what is reasonable and necessary. He has always been available to answer media enquiries, though Ron’s motto has been always to speak positively and if a problem crops up, to focus on the solution.
A couple of years ago, Ron wrote “Busted” a book containing real life stories demonstrating the work New Zealand PI’s perform. He did it to educate others and to dispel the often misguided perception that PI’s work mainly divorce cases. Busted went mainstream, so well that “Busted Again” is also in bookstore stores now.
Ron has no intention of slowing down anytime soon and will continue to assist NZIPI or the profession whenever asked. He has been a Justice of the Peace for New Zealand for over 20 years and is married to Gillian.
Phil Roigard
Phil has been a member of the NZIPI since its incorporation and has served as an Executive Committee member for many years, including several years on the Ethics Committee. (In fact, he formed the Institute’s predecessor organisation, the NZ Association of Private Investigators in 1981).
Phil is a career Investigator having worked in both the public and private sectors his entire working life. His brief work history is as follows:

36 NZSM December 2022/January 2023
• New Zealand Police. Graduated first in his Cadet Wing receiving the Minister’s Prize for General Excellence
• Resigned from the Police after 10 years’ service with the rank of Detective Sergeant
• Private Investigator. Created one of the first Professional Private Investigation companies in N.Z. and helped create the business wave for such services upon which many followed and rode

• Serious Fraud Office. One of five investigators appointed as inaugural members of the NZ Serious Fraud Office (SFO). Worked in a multidisciplined investigative team with accountants and solicitors investigating serious and complex
fraud cases. Became a Senior Investigator with responsibilities for SFO security and screening complaints for qualification under the SFO Act
• Private Investigator & Security Consultant. Transferred investigative skills back to the private sector and after a course of study in Security Risk Management became involved in Security Risk Reviews for multiple corporate clients. He has conducted 200 such reviews over the last 20 years
• ASIS International (ASIS). Phil has been a member of ASIS for over 30 years. In 2003 he obtained the Certified Protection Professional (CPP) designation, one of the security profession’s highest recognition of practitioners
• World Association of Detectives (former member)
• International Association of Arson Investigators (former member)
Phil is now semi-retired and based in Christchurch. He is still a current member of NZIPI & ASIS.
Looking to the Future – New NZIPI Chairman
Bruce Couper
Bruce Couper is the General Manager of Bespoke Security. He spent 11 years in the New Zealand Police
service initially working in a variety of uniformed roles. He spent the last four years of his service as a Detective in the Criminal Investigation Branch (C.I.B) in the areas of serious crime squad, car squad and robbery squad and participated in a range of major investigations including kidnapping and homicides.
Bruce has been a licensed Private Investigator since 1992 and member of NZIPI for much of that time.

Bruce wants the Institute to grow and be more representative of its members. He views representation with government agencies and informing licensing authorities as a priority.
Bruce is a current member of ASIS International and the ASIS New Zealand Chapter. He is a Life member of the NZSA, former Chairman of ASIS New Zealand and a former Chairman of the NZSA.

NZSM 37 December 2022/January 2023
‘Hot Products’: Why stolen goods are CRAVED
Jewellery, alcohol, sportswear, and medicines are just a few of the items favoured by ram raiders and shoplifters. There are specific reasons why offenders target these socalled ‘hot products’, writes Nicholas Dynon.
Ronald Clarke’s seminal paper Hot products: Understanding, anticipating, and reducing demand for stolen goods, was published in 1999 by the UK Home Office as part of a Police Research Series. Over two decades on, and as many countries – including New Zealand – grapple with cost of living crises and a ballooning of ram raids, retail theft, and property crime, Clarke’s paper is as relevant as ever.
of crimes. The rewards of crime are heavily dependent on the careful choice of targets
In other words, some products are more likely to be targeted by offenders than others because they are easier or less risky to steal, or their value or attractiveness makes them a more rewarding target. To describe what makes hot products hot, Clarke came up with the acronym CRAVED:
Concealable
Nicholas Dynon is chief editor of NZSM, and a widely published commentator on New Zealand’s defence, national security and private security sectors.

What makes it such an important work is that it introduced the idea that crimes don’t just tend to predominate (or repeat) in particular places (crime ‘hotspots’) or in relation to particular people (repeat victimisation), but that they often tend to focus on particular items (‘hot products’).
‘Hot spots’, which is a geographic concept, refers to locations that have a high rate of reported crimes or calls for police assistance. It’s a concept that’s been helpful, states Clarke, in identifying places with concentrations of ‘street crime’, disorder and drug dealing. “Repeat victimisation, on the other hand, focuses on people or places that suffer a series of crimes in a relatively short period of time.”
‘Hot products’ is the term Clarke gives to those consumer items that are most attractive to thieves. They are one of a number of ‘choice structuring properties’ that affect offender calculations of the ease, risks and rewards of committing particular kinds
These are things that are small enough to quickly hide or those that may be taken without attracting attention. Those that cannot be concealed afterwards, or that are easy to identify later are also less likely to be stolen,” states Clarke.
This attribute helps “explain why car thieves do not generally steal Rolls Royce cars for their own use. Leaving them parked outside their homes would attract too much unwelcome attention.”
Removable
Removable items are things that are easy to carry or are themselves mobile. “For instance, shoplifters are severely constrained in the number of bottles of whisky or packets of cigarettes they can steal without being noticed, but a ‘commercial burglar’ operating after hours may be able remove many cartons of alcohol and tobacco.”
Available Availability refers to things that are more likely to be abundant and
38 NZSM December 2022/January 2023
accessible in one way or another. It also explains why thefts of items can often occur in ‘waves’. According to Clarke, the introduction of attractive new products, such as mobile phones or laptop computers, quickly establish product-specific illegal markets.
At the most basic level, availability can also simply refer to how visible an object is at the point of theft.
Valuable
This refers to items that are valuable, particularly when thieves intend to sell them. “For example, one reason that cars that are around five years old are more at risk of theft is because the value of their parts is greater than that of the whole stolen vehicle,” states Clarke. Value is also reflected in the tendency of Juvenile thieves to select goods that are valued in the youth culture, whose ownership confers status.
Enjoyable
These are things that are enjoyable as opposed to things that are more functional (e.g., refrigerators). The fact that ‘enjoyable’ items are more attractive to thieves than ‘functional’ items “may reflect the pleasure-loving lifestyle of many thieves and the people who buy from them.”
Disposable
Disposable items are things that are easy to trade, sell for cash, or that can be used immediately without risk. Since many items are stolen to be sold to others, thieves will tend to select things that will be easy to sell.
Which goods are CRAVED?
According to the US Department of Justice guide Understanding Theft of ‘Hot Products’ (Bowers and Johnson), items that have more CRAVED characteristics are more likely to be stolen. According to the authors of the guide, this is primarily because these items are “optimal targets for offenders who want to minimise the time and effort required to commit crime (e.g., the availability/accessibility and removability of items), and minimise risk of negative consequences (i.e., concealability), while maximising the benefits of any given offense (e.g., value, enjoyment and disposability of items).”
When Clarke wrote his report in 1999, the consumable goods commonly targeted for theft included alcohol, tobacco, food items, personal care products such as razors and shampoo, medicines, fuel, batteries, and entertainment media (DVDs, etc).
Clarke also cited a study of losses for three categories of merchandise—food; health and beauty products; and beers, wines, and spirits—at three large U.K. supermarkets, which revealed that in the case of food, fresh meat is far more likely to go missing (particularly beef and chicken), and milk and strawberries are at a high risk of shrinkage when compared to drinks or sandwiches.
“For alcohol, spirits go missing with a higher frequency than wine and liqueur, and overwhelmingly it is name-brand products that go missing,” he writes.
“For health and beauty products, commonly stolen items include pain

relief, baby products, cosmetics, face creams, oral health products, and perfume. What was most telling was thieves’ preference for particular brands, and even within brands, particular products.”
Two decades later, the top categories identified in the 2022 edition of the US National Retail Federation’s Retail Security Survey as being targeted by Organised Retail Crime offenders closely aligns with Clarke’s findings. These categories included apparel, health and beauty, electronics/ appliances, accessories, food and beverage, footwear, home furnishings and housewares, home improvement, eyewear, office supplies, infant care, and toys.
“Still CRAVED, but perhaps with some difficulties to overcome are bicycles (which can be difficult to conceal but, once taken are highly removable); disposable razors (which are more functional than enjoyable, and not particularly valuable, although they are expensive for a disposable product); and larger household goods, such as televisions, microwaves, and desktop computers (which are harder to conceal and remove),” states the survey report.
According to Clarke, offender decisions around what items to target ultimately come down to how easily they can be sold or traded on. “While each of the elements of CRAVED may be important in explaining which products are stolen, how much they are stolen may depend critically on just one attribute — the ease of disposal.”
NZSM 39 December 2022/January 2023
Finding pragmatic, proportionate and effective physical security solutions
Security Risk Advisor
ICARAS Security
Most people understand that physical security control measures, such as security alarms, access control and CCTV systems, are a necessary evil in this day and age. However, when it comes to what security measures to install, and to what extent, everyone has a different view.
Nobody wants to “undercook” their physical security and risk insufficient protection of their people and assets. But neither does anyone want to throw money away on extensive and expensive systems that are unnecessary.
In this article, I will lay out a basic process that can be used to help you determine a pragmatic, proportionate and effective physical security solution for your organisation. I will start by looking at threat and risk, followed by how to apply threat and risk assessments to your organisation’s physical security environment.
I will then look at some of the principals of physical security and how these apply to different physical security control measures. Finally, I’ll pull everything together to present a high-level process for determining an appropriate physical security solution for your business.
It’s probably worth noting that the language and terminologies used in this article have been deliberately simplified so that it can be understood by everyone and not just the technical experts!
Part 1 – Threat and Risk
Understanding threat and risk is the fundamental building block to achieving the pragmatic and proportionate aspects of a physical security solution. Most organisations regularly deal with risk assessments in the health and safety domain, but often don’t take the same approach in the security domain.
By identifying the threats to your organisation and the associated risks they present, you can determine where your vulnerabilities lie. However, there is often a lack of understanding of the difference between threat and risk.
While there are many standards, handbooks and guides on threat and risk, we will try and boil it down to a magazine article-sized summary below.
What are threats and risks
A threat identifies an action or event that leads to a negative outcome and incorporates who or what perpetrates that action or event. For example, a threat may be a petty criminal breaking into a storage shed and stealing some tools.
Common threat categories used within government circles are shown in Table 1 below. These are fairly broad and some may be more relevant to your organisation than others.
Terrorism International extremists Domestic extremists
Disruptive activity
Protestors, activists or issue motivated groups Fixated or acutely disaffected persons
Sabotage / unauthorised Insiders disclosure of information Hostile intelligence activity
General crime
Violence, theft and vandalism Organised criminal activity
Economic crime Cybercrime
Table 1 - Common threat categories
Identifying what may go wrong on its own is not that helpful, so threats also consider the likelihood of that action or event occurring. For example, if your site is in an industrial area with a high crime rate and your shed is secured with a low grade lock, you may determine there is a fairly high chance that someone might steal your tools.
Risk takes this a step further and considers the impact or consequences. Identifying instances of how these threats
40 NZSM December 2022/January 2023
Chris Philp,
at
Consultants, combines theory with practice to acquaint us with the building blocks of assessing security risk and identifying an effective security solution.
Figure 1 – Threat and risk relationship (Source: National Security Journal).
could occur and assessing the impact or consequences of these occurrences results in a set of risks.
For example, if the tools were low value and used only for routine maintenance, the impact of them being stolen might be low. However, if the tools were a critical part of your operations and difficult to replace, the impact of them being stolen might be very high.
Another way of looking at the relationship between threat and risk, and how to determine them, is shown in Figure 1. This is the process used by the Combined Threat Assessment Group (CTAG) when setting the national terrorism threat level.
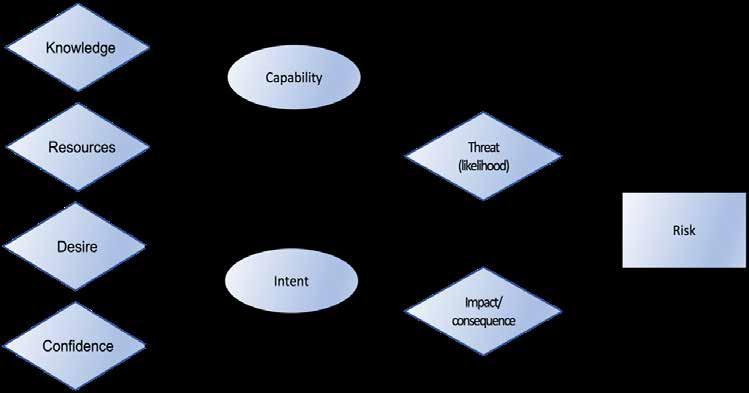
To provide context, threats and risks are usually assigned a level. This could be low/medium/high or a scale of one to five, or whatever system works for you. From Figure 1 we can see that the risk level is usually the combination of the Likelihood and Impact or Consequence.
A common approach is to use a numerical scale, then output a colour coded high/medium/low rating, an example of this is shown in Table 2. However, the purpose of a risk rating is to help you understand the significance of a risk to your organisation, both absolutely and relative to other risks, so use any system that provides the relevant information and works for you.
So far, we’ve looked at threat and risk, covering the highlevel concepts in identifying the physical security risks to your organisation. This next part looks at how to use that risk assessment.
Part 2 – Applying risk assessments
So far, I’ve looked at threat and risk, covering the high-level concepts in identifying the physical security risks to your organisation. This next part looks at how to use that risk assessment.
Balancing detail
Threats and risks can be expressed broadly (for example, the current assessed threat of terrorism in New Zealand is ‘Medium’). A broad threat and risk analysis will, however, yield broad results, which may be less helpful when looking at specific risk mitigations.
Defining threats and risks in more detail can be beneficial – the more specific the risk, the more specific the risk mitigation. However, on the flip side, too much detail can become overwhelming and counterproductive.
Table 2 – Physical Security Risk Rating
A good place to start is to focus on the threats that are most relevant to your organisation. The categories in Table 1 cover a wide gambit of threat sources and it is likely only a few will be particularly relevant to your organisation. Likewise, similar risks can sometimes be grouped together.
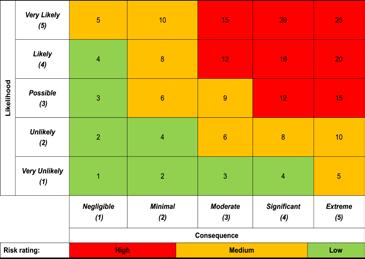
NZSM 41 December 2022/January 2023
Handling risks
Risks can be either tolerated, terminated, treated or transferred.
• Tolerate: Accept the risk without mitigation (or further mitigation). This may be employed when the risk consequence is assessed as being very low or the cost of mitigation is disproportionate to the risk rating. For example, just accept that tools will sometimes be stolen and need to be replaced. Tolerate is also employed once mitigations are applied to a risk to lower the rating to a level that is within the organisation’s risk appetite.
• Terminate: Remove the object of the risk – for example, stop undertaking the work that requires tools to be stored at high crime sites.
• Transfer: The risk is transferred to a third party. For example, the financial component of the risk of stolen tools can be transferred to an insurance company through an insurance policy.
• Treat: Develop one or more options to mitigate the risk. This is usually the most appropriate option when it comes to physical security risks and is where physical security control measures come into play.
Determining where your organisation’s risk tolerance level, or risk appetite, sits is a key component of the risk assessment process. It gives a clear picture of what risks can be tolerated without mitigation and what physical security measures are needed to bring the other identified risks down to an acceptable level.
A risk can be mitigated by either reducing the likelihood of a threat action or event occurring, or by reducing the consequence or impact on your organisation should the threat action or event occur. Risk mitigation measures will generally operate on one or both of these risk aspects.
For example, storing tools in a more robust shed with a high grade lock will make it harder to access the tools, thus reducing the likelihood they will be stolen. Ensuring a second set of tools is available at another site means work can continue even if one set of tools is stolen, thus reducing the impact of the tools being stolen.
Part 3 – Physical security concepts and principles
Having looked at threat and risk, and applying a risk assessment to your organisation, I’ll now take a small sidestep and look at some of the key concepts and principles in physical security and physical security control measures.

Deter, Detect, Delay and Respond
Physical security measures can mitigate risks through one or more of deterring, detecting, delaying, or responding to threat actions:
42 NZSM December 2022/January 2023
• Deter. The aim of deterrence is to stop or displace an intrusion before it has taken place. This is the primary goal of the whole physical security system – the best outcome is always to stop a threat action from happening when possible. For example, a sign stating an area is under CCTV surveillance may make a criminal think twice before breaking into a shed to steal tools.
• Detect. The primary purpose of detecting a threat action or event occurring is to initiate a timely response, which may reduce the impact of the event. For example, a fence alarm may detect an unauthorised intruder entering your site, prompting a security guard response which may disrupt an attempt to break into the shed to steal the tools.
• Delay. Measures that are put in place to delay, or slow down, the intrusion. This decreases the chances of the intruder reaching their target before being apprehended or giving up. For example, a high quality lock on the storage shed may be beyond the capability of many criminals to defeat or take a determined criminal some time to bypass.
• Respond . The response to an intrusion should ensure that the incident is stopped or, at a minimum, cannot progress any further. Also, a post-incident response can provide information that enables additional control measures to be employed that reduces the risk of the incident occurring again. For example, the arrival of a security guard on site will likely cause a criminal to cease their attempts to break into the storage shed and leave as quickly as possible.
It is important to understand what domains a security measure operates within to determine how effectively it will mitigate a specific risk, if at all. For example, a CCTV camera will deter but not delay an intruder, a mechanical lock will delay but not detect an intruder, an alarm system will detect and instigate a response but not delay an intruder.
Crime Prevention Through Environmental Design (CPTED)
CPTED provides a framework for incorporating crime prevention within quality urban design by focusing on reducing the opportunity to commit crime, therefore lessening the motivation to offend. The natural and built environment can help or hinder physical security.
While the origins of CPTED are in urban design, there are elements that are applicable to many other types of site. There are four key overlapping CPTED principles:
• Surveillance. People are present and can see what is going on. For example, ensuring your storage shed is well lit and visible to passers-by on the street will increase the chances of a criminal trying to break into that shed being seen
• Access management. Methods are used to attract
people and vehicles to some places and restrict them from others. For example, closing off your site carpark to vehicles after hours will discourage people from congregating, which may in turn reduce the risk of opportunistic targeting of your storage shed.
• Territorial reinforcement. Clear boundaries encourage community ‘ownership’ of the space. For example, a clearly marked boundary around your site will discourage people from entering and loitering, which may in turn reduce the risk of opportunistic targeting of your storage shed.
• Quality environments. Good quality, well maintained places attract people and support surveillance. For example, a poorly maintained storage shed suggests a lack or care or concern for it, which in turn may lead to a potential criminal believing their risk of being caught is reduced.
Security in depth
‘Security-in-Depth’ involves layering multiple security measures to make unauthorised access difficult. These measures should complement and support one another. A visual representation of this is shown in Figure 2.
Each individual layer represents a set of security controls or obstacles that any threat or attacker would need to breach in order to compromise the asset(s), with the layers operating cumulatively towards the total effective protection. Layers of security controls also provide redundancy, reducing the risk of compromise should a single layer fail.
For example, a criminal may need to pass through multiple layers, include a perimeter fence, security lighting, a robustly constructed storage shed and a high quality lock, before getting access to the tools in the shed to steal them.
Part 4 – Pragmatic and proportionate physical security control measures
In this part, we bring the threads of what we’ve covered so far together to determine effective physical security controls to address the identified risks, guided by the relevant concepts and principles.
Firstly, your risk assessment and organisational risk tolerance should highlight the key physical security areas that need mitigation measures. By focusing on the highest risk areas you ensure you are expending effort and resource in the areas where it is most needed to provide a proportionate solution.
Next, determine which physical security controls will provide suitable and effective mitigation against those risks. Before looking at direct controls, think about how the principles of CPTED and using the natural and built environment can be used to your advantage. Then consider each of the direct physical security controls in terms of how they fit into the deter, detect, delay and response framework – which aspects of the framework are required to effectively mitigate the risk and what controls can be applied to each of those aspects.
NZSM 43 December 2022/January 2023
Figure 2 – Layered approach to physical security
While most controls will span more than one aspect, it is unlikely only one control will give full coverage to mitigate a risk. Which brings us to security-in-depth – think about the process of the threat action or event and how it “interacts” with each security control along with any potential interdependence between controls (for example, a guard force response requires an alarm or other prompt to initiate it). Ensure you have multiple layers and try and avoid single points of failure.
Once you have mapped out proportionate and effective physical security controls, find the common ground. It is likely many of the controls will overlap different risks and these can be consolidated into a single control specification that covers all the relevant risk mitigation requirements. This provides a pragmatic deployment solution for each control.
Alongside this, undertake a gap analysis with your existing physical security controls – look at what you might already have in place that can provide effective mitigation and may reduce the additional controls that need to be installed. This provides a pragmatic deployment solution across all controls.
Finally, take your list of the additional physical security controls required to mitigate your identified risks and develop a deployment plan, looking to link the control and management systems of each control together wherever possible to enable them to work together and to reduce the management burden.
Worked example
Lets bring it all together, based on the very basic example used throughout this article.
The identified risk is petty criminals breaking into a storage shed on site, stealing tools that are essential to the
operation of the business. As the site has minimal existing physical security controls and the loss of the tools would have a significant impact on business operations, the risk rating is assessed to be high.
There is an overgrown hedge around the site that blocks the view of the shed door from the road. By trimming this hedge, the door can be seen from the road, is better illuminated by the streetlights and makes the site look tidier and well kept (natural surveillance and quality environments).
While the door to the shed is reasonably robust, it opens inwards and is prone to a solid kick or shoulder charge. By converting it to an outwards opening door with hinge bolts, it presents a much tougher target requiring more time to defeat (delay), in full view of the street (deter).
Installing a monitored security alarm in the shed will provides a notification of attempted unauthorised access (detect) and allow a response from the security guard force (respond).
A locked internal cabinet or storage cage can also be installed, providing an extra layer of physical barrier but also providing an additional delay factor after the alarm detection to give the guard force time to respond.
This is just a basic example and there are many other options available to mitigate this type of risk – one of the simplest being to move the tools to a more secure location. However, hopefully this have given you an idea of the process to determine a pragmatic, proportionate and effective physical security solution for your organisation that is a little more robust than just glossy brochures and good ideas.
This article was originally published as four blog posts at www.icaras.nz.
44 NZSM December 2022/January 2023
REACH NEW HEIGHTS in
Professional Excellence
ASIS accredited certifications can help you reach your career goals.
Validates your ability to conduct security investigations through the effective use of surveillance, interviews, and interrogations. Designed for those with 5 years of related experience.
WH Y EARN THE PCI DESIGNATION?
• Provides independent confirmation of your specialized skills in security investigations

• Gain global recognition by your peers and industry
• Get a competitive edge in the marketplace
• Enhance your career and earnings potential
• Enjoy personal satisfaction and professional achievement
Be one of the many ASIS board certified practitioners who are leaders, mentors, and trusted strategic partners, serving both their organizations and the profession.
Visit www.asis.org.nz

“PCI is an important element in the ASIS C ertification programme, dovetailing into both CPP a nd PSP for a comprehensive understanding of broader security industry objectives. An effective and reliable investigation depends on objectivity, thoroughness, relevance, accuracy and timeliness. PCI helps identify critical investigative outcomes, including evidence collection, case management, and the process of offender detection, iden tification, interview and prosecution. Good physic al security designs, together with robust policies and procedures are key elements in a successful investigation. The PCI certification p rov ides an insight into how these pieces interrelate."
- D avi d H orsburgh, MSc CPP PSP PCI

WHY SHOULD AN EMPLOYER HIRE ASIS CERTIFIED PROFESSIONALS?
• Build a strong, dedicated team committed to high standards and continuing professional development
• Promote ongoing education of critical job knowledge and skills
• Feel confident that your staff are using best practices
• Recruit the most qualified professionals
• Reinforce or elevate your organization’s reputation and credibility
Increase the competency level of your staff by supporting your security professionals in their certification journey.
NZSM 45 December 2022/January 2023
Multi-million dollar package to tackle retail crime and reoffending
As retail crime continues to send shockwaves into communities, the Government announced on 28 November an extended package of measures to combat it, with new initiatives to partner with small businesses and local councils.
Fog cannon subsidy scheme
The Government will establish a new fog cannon subsidy scheme open to all small shops and dairies in New Zealand who want a fog cannon installed.
“Funding of $4,000 will be available for each shop who will be able to have the fog cannon installed through an approved supplier, meaning they can access them directly without an onerous process. Additional details will be released shortly,” Jacinda Ardern said.
“Despite global supply chain issues, Police has been successful in ordering an extra 455 fog cannons, which are expected to arrive before Christmas,” said Police Minister Chris Hipkins. “This adds to the 270 fog cannons that are currently in the country and have been allocated to affected shops.”
“More challenging will be the time it takes to install them. The 1,000 fog cannons that are already installed took
four years, and despite Police doubling the number of local contractors that will do the work to six, it’s expected it will take till the second quarter of next year for the number of installations to start to ramp up.”
The fog cannon fund was set up in 2017 after aggravated robberies of commercial premises had doubled from 2015 – from 599 to 1170. It was expanded in 2018 and 2019, and 1000 fog cannons were installed by the end of 2021.

Local crime prevention boost
New funding of $4 million will be made available to local councils to assist with crime prevention measures.
This will be made up of $2 million for Auckland, $1 million for Hamilton and $1 million for the councils in the Bay of Plenty to match on a dollar for dollar basis by Councils for local crime prevention measures.
Partnerships are likely to be focused on Crime Prevention through Environmental Design (CPTED) measures, such as street lighting, CCTV cameras and planters, in areas where small retailers are commonly targeted.
“Conversations have been had already between Police and government officials and Auckland Council, Hamilton Council and Bay of Plenty Councils to identify opportunities that can get started soon,” said Chris Hipkins.
“We’re also announcing today that we will make funding available for all small shops and diaries to install fog cannons, adding to the 1,000 that have already been installed as part of the fog cannon initiative.
Extension of the Retail Crime Prevention Fund
The $6 million Retail Crime Prevention Fund was set up for small shops and dairies in early 2022 as offending shifted to ram raiding, and eligibility tis now being expanded to aggravated robbery committed over the last year.
“Police are making progress on the number of stores accessing the fund,” said the police minister. “More than 100 shops now have installations approved, with 431 security measures allocated and underway. This includes 93 fog cannons, 78 security sirens, 57 alarms, 63 CCTV systems, 43 bollards and 36 roller doors.”
46 NZSM December 2022/January 2023


Loktronic Limited Unit 7 19 Edwin Street Mt Eden Auckland P O Box 8329 Symonds Street Auckland 1150 New Zealand Ph 64 9 623 3919 Fax 64 9 623 3881 0800 FOR LOK mail@loktronic.co.nz www.loktronic.co.nz Loktronic for ex-stock availability LoktronicLimi t e d sraey03 s’ZNgnicivres S e c u r ity Industry

































































































































































































































































































































































































































































































21620 Loktronic Limited Unit 7 19 Edwin Street Mt Eden Auckland P O Box 8329 Symonds Street Auckland 1150 New Zealand Ph 64 9 623 3919 Fax 64 9 623 3881 080 0 FOR LOK mail@loktronic.co.nz www.loktronic.co.nz Battery Load Tester Ref. 730-101 ViTECH, strong, lightweight aluminum case, 5, 15 and 30 amp battery load tester for fire and alarm use. Weight: 500gms, Size: 165mm x 90 x 70mm. STI-13B10-NW Ref. 720-092 Surface mount, horn and label optional 206mm H x 137mm W x 103mm D STI-6518 Ref. 720-060 Flush mount, no horn 165mm H x 105mm W x 49mm D STI-13000-NC Ref. 720-090 Flush mount, no horn 206mm H x 137mm W x 69mm D Fire Brigade Alarm: (Closed/Open) Ref. 730-231 ViTECH branded Type X (730-230) and Type Y (illustrated) models with temperature compensated pressure transducers with digital display showing pressures for defect, fire and pump start. STI-1100 Ref. 720-054 Flush mount with horn 255mm H x 179mm W x 86mm D Anti-Interference Device Ref. 730-400 series ViTECH AID for sprinkler valve monitoring; fits all ball valve sizes. STI-13210-NG Ref. 720-093 Surface mount, horn and label optional 206mm H x 137mm W x 103mm D LOKTRONIC’s expansive product range has just become even wider with these first class EGRESS and FIRE PROTECTION DEVICES and PROTECTIVE COVERS. fired up protection All STI ‘Stoppers’ are made of tough, UV stabilised polycarbonate. Many can be supplied with or without a 105 dB horn. Other models and sizes available including weather resistant options. • Approved to EN54-11 • Current Rating: 3 Amps @ 12-24V DC, 3 Amps @ 125-250V AC
Material: Polycarbonate
with Clear Cover
2 x SPDT switches
•
• Comes
•
• Positive activation that mimics the feel of breaking glass.
• Visible warning flag confirms activation.
• Simple polycarbonate key to reset operating element - no broken glass.
ViTECH products are designed and produced in New Zealand. STI-1130 Ref. 720-102 Surface mount with horn and spacer 255mm H x 179mm W x 135mm D NEW
Ref. 720-051G Available in White, Green, Blue & Yellow.
Mini Theft
use of equipment.
when
construction.
cabinets and display cases or
freestanding equipment.
Compact
25mm
Ref.
Available in
Blue &
Ref.
Cover
Flush
Available.
Ref.
Also available
NEW NEW 21620/1/18
• Dimensions: 87mm Length x 87mm Width x 23mm Depth (Flush Mount) & 58mm Depth (Surface Mount)
STI-RP-GF-11/CN
STI-6255 Ref. 720-042
Stopper discourages inappropriate
Sounds a powerful 105 dB warning horn
activated. Tough, ABS
Reed switch activation for
unique clip activation for
Does not interfere with use of protected fire fighting equipment.
design 85mm H x 85mm W x
D. STI-RP-WS-11/CN
720-052W
White, Green,
Yellow. STI-RP-RS-02/CI
720-058
included.
Mount
STI-6720 Ref. 720-047 Break Glass Stopper. Keys under plexiglas. Protects emergency keys from inappropriate use. Keys remain visible. Fast, easy installation. Simple, inexpensive plexiglas. 3 year guarantee against breakage of the ABS housing within normal use. STI-WRP2-RED-11 IP67
720-062R
in White.









































































































































































































































































