Report
Title: Vulnerability scanning on https://seiumatrimony.com/
Open source information gathering:
IPv4 address:103.50.160.62
Reverse DNS md-in-70.webhostbox.net
Forward DNS
www.bharatiyayojana.hatchacode.com, forestgallery.onesolutionraipur.com, ebax.in, mail.dedipyachittifunds.com, autodiscover.mysunlifecare.co.in, ...
Routing
103.50.160.0/24 via PUBLIC-DOMAIN-REGISTRY, US (AS394695)
OS
Red Hat Enterprise Linux 7
Server Apache
Services (23)
21/FTP, 22/SSH, 25/SMTP, 26/SMTP, 53/DNS, 80/HTTP, 110/POP3, 143/IMAP, 443/HTTP, 465/SMTP, 587/SMTP, 993/IMAP, 995/POP3, 2077/HTTP, 2078/HTTP, 2082/HTTP, 2083/HTTP, 2086/HTTP, 2087/HTTP, 2095/HTTP, 2096/HTTP, 2222/SSH, 3306/MYSQL
Subdomains
cpanel.seiumatrimony.com
103.50.160.62
cpcalendars.seiumatrimony.com 103.50.160.62
nmap enumeration
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
26/tcp open rsftp
53/tcp open domain
80/tcp open http
110/tcp open pop3
143/tcp open imap
443/tcp open https
465/tcp open smtps
587/tcp open submission
993/tcp open imaps
995/tcp open pop3s
2222/tcp open EtherNetIP-1
3306/tcp open mysql
Vulnerabilities
i)Session hijacking:
Session hijacking involves an attacker using captured, brute forced or reverse-engineered session IDs to seize control of a legitimate user’s session while that session is still in progress. In most applications, after successfully hijacking a session, the attacker gains complete access to all of the user’s data, and is permitted to perform operations instead of the user whose session was hijacked.
Impact
Session hijacking is a severe threat to website security and can cause irreparable damage to your users and your website.
Session hijacking is dangerous because attacker can steal Unauthorized access to user information, loss of sensitive data, possible fraud transaction.
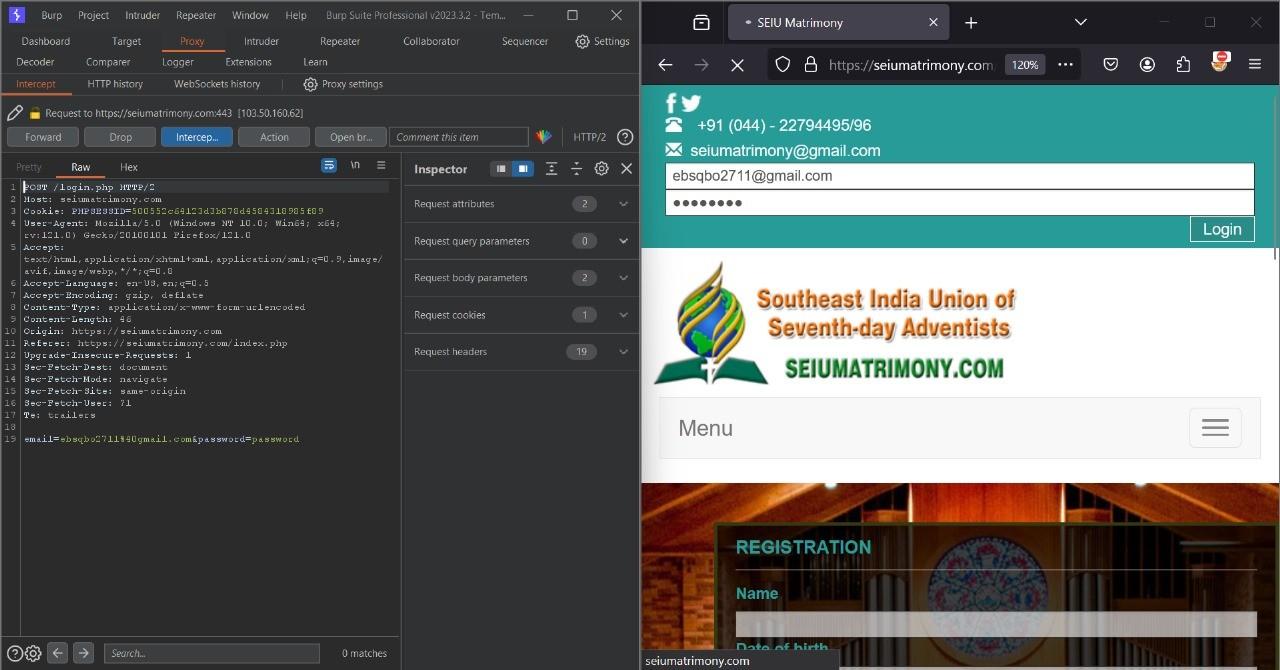
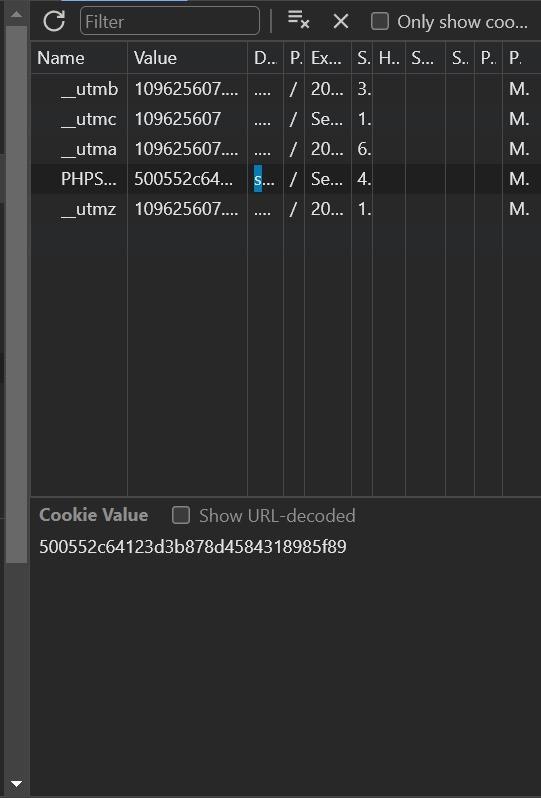
when you entered your email and password and there are man n the middle who can access the transmission of your data or capture your traffic the person can steal sessionID. for this scenario sessionID is: PHPSESSID=500552c64123d3b878d4584318985f89
Man in the middle steal the sessionID and save it for further use and forward the request for accessing the content.
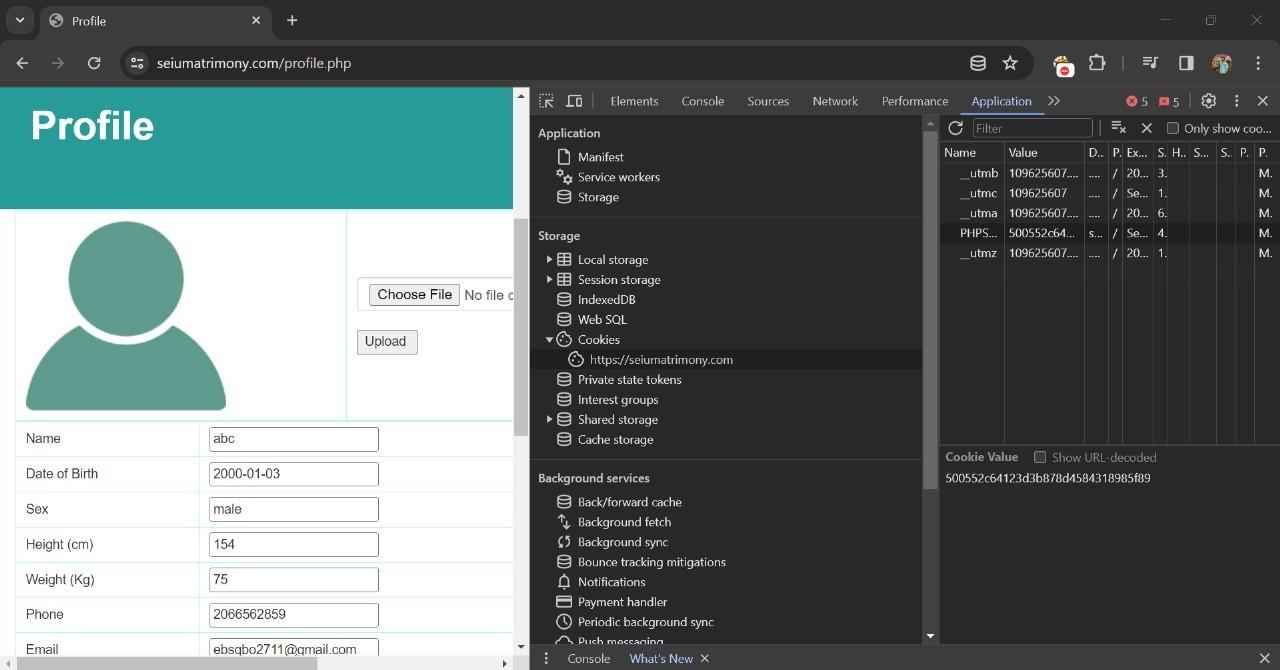
Now attacker open their browser and try to access the session of the main user.
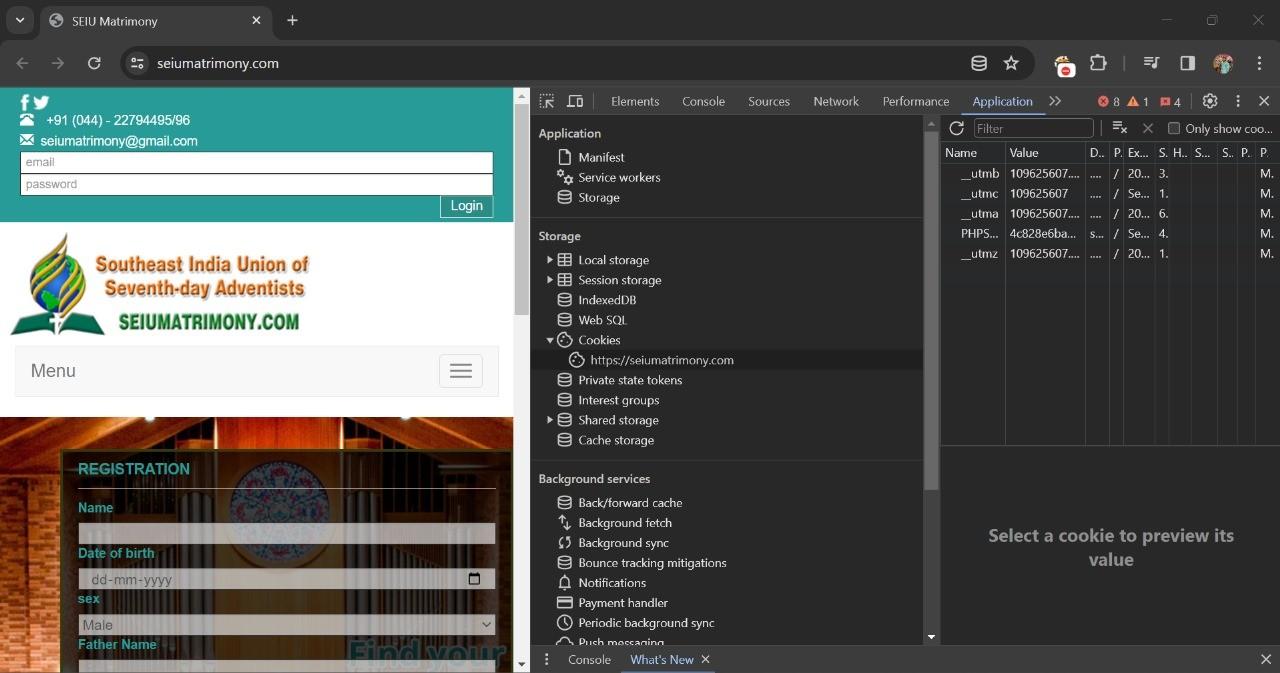
Attacker change the sessionID from 4c82 to the new session id which is captured during the analysis phase.
Now refresh the page and go to the profile page you can see the previous user login details you can use the user credentials of that user to make theft.
ii)SQLi attack
SQL injection (SQLi) is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. This can allow an attacker to view data that they are not normally able to retrieve. This might include data that belongs to other users, or any other data that the application can access. In many cases, an attacker can modify or delete this data, causing persistent changes to the application's content or behaviour.
Impact
A successful SQL injection attack can result in unauthorized access to sensitive data, such as:
Passwords.
Credit card details.
Personal user information.
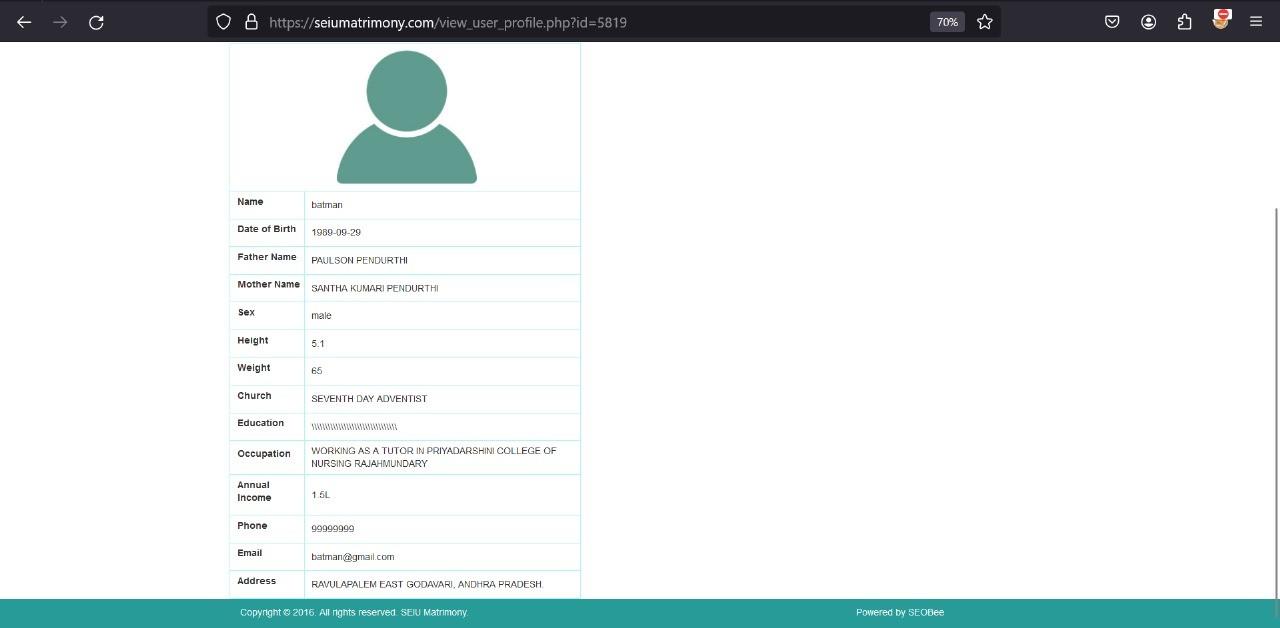
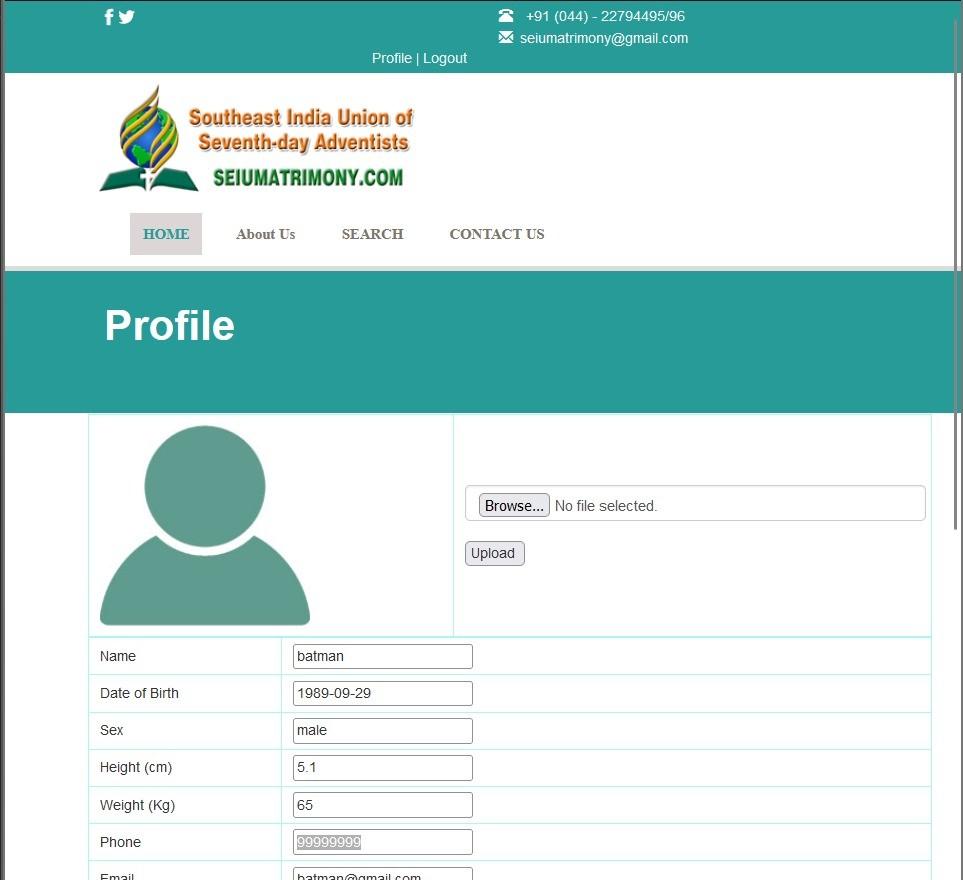
You can use email address to login as a batman user.
I don’t have password for the user batman but the password field is sql vulnerable.
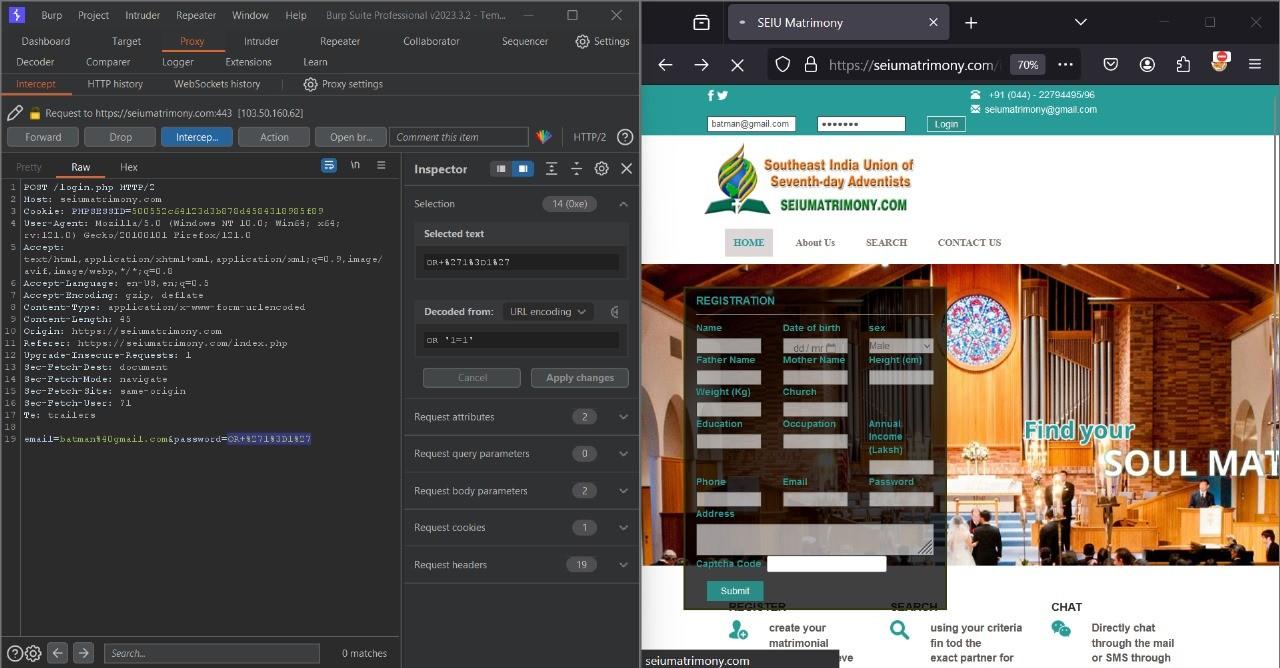
We just temper the SQL query and get login into the user batman and also able to acess whole profile of the user batman