















This past year we celebrated our 20th year as CyLab with an anniversary panel at our October 2023 CyLab Partners Conference and 20th Anniversary Gala. CyLab founding director Pradeep Khosla, former CMU president Jerry Cohon (who sadly passed away in March 2024), and past and present CyLab leaders reminisced about the early days of CyLab and reflected on why CMU is the perfect home for CyLab. We continued our anniversary celebrations throughout the 2023-24 academic year, culminating in a summer picnic for our students, faculty, and staff, during which attendees tie-dyed their own unique CyLab 20th anniversary T-shirts. You can see the colorful results on the back cover.
Besides celebrating and looking back, we also spent a lot of time this year looking forward. Through our strategic planning process, we identified a need for a more coordinated effort to fill gaps in our security and privacy faculty. With support from the provost and deans, we launched a security and privacy priority hiring search to hire eight tenure-track faculty into CMU academic departments over the next few years. We posted a job announcement on our website and convened a search committee. We look forward to working closely with several departments to hire candidates that meet strategic needs of both CyLab and the hiring departments. Please help us spread the word to potential faculty candidates and encourage them to apply!
Of course, we spent most of our time this year doing what we do best: collaborating on innovative and impactful security and privacy research, working across departments, disciplines, and geographic boundaries. Our work has resulted in many CyLab papers being presented at the major conferences in our field. In November, we presented three papers at the ACM Conference on Computer and Communications Security (CCS 2023). In February, we presented five papers at the Network and Distributed System Security Symposium (NDSS 2024). In May, we presented six papers at the 2024 IEEE Symposium on Security and Privacy and 10 papers at ACM Conference on Human Factors in Computing Systems (CHI 2024). In July, we presented eight papers at the Privacy Enhancing Technologies Symposium (PETS 2024). And in August, we presented three papers at the Symposium On Usable Privacy and Security (SOUPS 2024) and eight papers at the 2024 USENIX Security Conference.
You can read more about this work in the following 42 pages and on our website, but I’ll whet your appetite with a few highlights here. One of our newest faculty members in the Software and Societal Systems Department (S3D), Riccardo Paccagnella, was on a team of researchers who uncovered a new side-channel attack, GPU.zip, that exploits software-transparent uses of graphical data compression. Sauvik Das, in the Human Computer Interaction Institute (HCII), and his team constructed a taxonomy of AI privacy risks by analyzing 321 documented AI privacy incidents. CyLab postdoc Karen Sowon, in collaboration with a team of researchers in Pittsburgh and CyLab-Africa, studied the role of useragent interactions on mobile money practices in Kenya and Tanzania and uncovered security and privacy issues that the team is now trying to address.
We’ve got lots more to share in the following pages. We also invite you to visit our website and subscribe to our email list for quarterly updates on CyLab news.

Director and Bosch Distinguished Professor in Security and Privacy Technologies, CyLab, FORE Systems University Professor of Computer Science and of Engineering & Public Policy
Privacy is a key principle for developing ethical AI technologies. But as technological advances in AI far outpace regulation of these technologies, the responsibility of mitigating privacy risks in goods and services that incorporate these technologies falls primarily on the developers of these goods and services themselves.
CyLab celebrates 20 years of cybersecurity leadership at its 2023 Partners Conference
CyLab celebrated 20 years of collaborating on cuttingedge research and educating the next generation of security and privacy professionals at its annual Partners Conference. 22 Carnegie Mellon celebrates CMU-Africa Week 2024
In its second year running, CMU-Africa Week welcomed students from the land of a thousand hills to the city of bridges. The annual event aims to build a stronger connection between the two College of Engineering locations and highlight the research happening in Kigali, Rwanda.

Ally Nisenoff is a Ph.D. student in Carnegie Mellon University’s Software and Societal Systems Department. She is also a talented artist, honing her skills in various forms of visual media ranging from photography and glass work to crochet and embroidering.
Ally’s visual artwork is often inspired by her expertise in usable security and privacy. In her time at Carnegie Mellon, she has embroidered many images that are familiar to her fellow CyLab community members, including logos from conferences that are frequented by CyLab researchers, the CyLab logo itself, and even CMU’s beloved Scottish terrier mascot.
We’ve included some of Ally’s embroidered images throughout this publication to highlight the groundbreaking work that CyLab’s researchers have shared throughout the past year. You can find more of Ally’s embroidered artwork at anisenoff.github.io/craft_galleries/gallery_embroidery. html
But as technological advances in AI far outpace regulation of these technologies, the responsibility of mitigating privacy risks in goods and services that incorporate these technologies falls primarily on the developers of these goods and services themselves. That’s a tricky proposition for AI practitioners, and it starts with tangibly defining AI-driven privacy risks in order to address them in the research and development stage of new technologies.
And while there is a privacy taxonomy that has a wellestablished research-driven foundation, it’s likely that groundbreaking AI technological advancement will bring with it unprecedented privacy risks that are unique to these new technologies.
“Practitioners need more guidance on how to protect privacy when they’re creating AI products and services,” said Sauvik Das, assistant professor at Carnegie Mellon University’s Human-Computer Interaction Institute (HCII)
“There’s a lot of hype about what risks AI does or doesn’t pose and what it can or can’t do. But there’s not a definitive resource on how modern advances in AI change privacy risks in some meaningful way, if at all.”
“Practitioners need more guidance on how to protect privacy when they’re creating AI products and services.”
Sauvik
Das, assistant professor at Carnegie Mellon University’s Human-Computer Interaction Institute (HCII)
In their paper, “Deep Fakes, Phrenology, Surveillance, and More! A Taxonomy of AI Privacy Risks,” Das and a team of researchers seek to build the foundation for this definitive resource.
The research team, which also features Carnegie Mellon University researchers Hao-Ping (Hank) Lee, Yu-Ju (Marisa) Yang, and Jodi Forlizzi, constructed a taxonomy of AI privacy risks by analyzing 321 documented AI privacy incidents. The team’s goal was to codify how the

AI practitioners, such as the developers of the technologies behind smart speakers, can use the taxonomy constructed by Sauvik Das (pictured) and a team of CMU researchers as a guide to help the practitioners protect privacy when they’re creating new AI products and services.
unique capabilities and requirements of AI technologies described in those incidents generated new privacy risks, exacerbated known ones, or otherwise did not meaningfully alter known risks.
Das and his team referred to Daniel J. Solove’s 2006 paper “A Taxonomy of Privacy” as a baseline taxonomy of traditional privacy risks that predate modern advances in AI. They then cross-referenced the documented AI privacy incidents to see how, and if, they fit within Solove’s taxonomy.
“If the incidents where we’re seeing the AI causing harm is challenging that taxonomy, then that’s an instance where AI has changed privacy harm in some way,” explained Das. “But if the incident fits neatly into the taxonomy, then that’s an instance where maybe it’s just exacerbated the existing harm, or maybe it hasn’t meaningfully changed that privacy harm at all.”
In examining the documented AI privacy incidents through the lens of Solove’s taxonomy, the team identified 12 high-level privacy risks that AI technologies either newly created or exacerbated, outlined in the table on the following page.
“We set a divide as it relates to products and services and in two ways that pipe into the taxonomy: the requirements of AI and the capabilities of AI,” said Das.

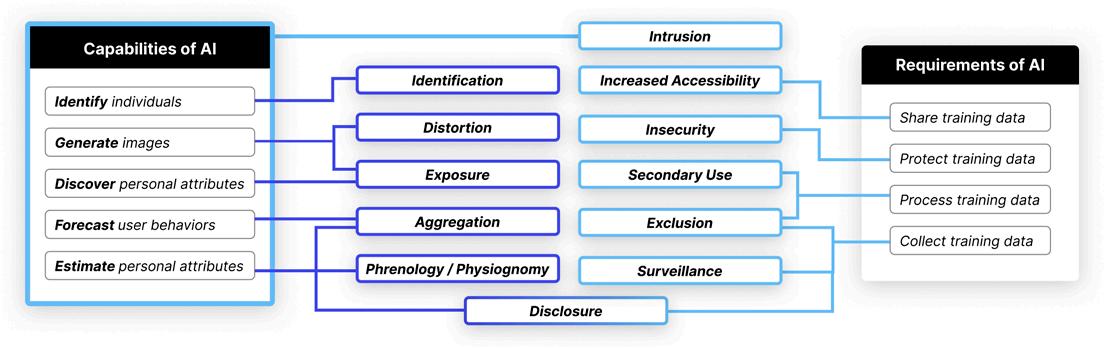
The researchers identified 12 privacy risks that the unique capabilities and/or requirements of AI can entail. For example, the capabilities of AI create new risks (purple) of identification, distortion, physiognomy, and unwanted disclosure; the data requirements of AI can exacerbate risks (light blue) of surveillance, exclusion, secondary use, and data breaches owing to insecurity.
Source: “Deepfakes, Phrenology, Surveillance, and More! A Taxonomy of AI Privacy Risks”
“The requirements of AI refers to ways that the data and infrastructural requirements of AI exacerbated privacy risks already captured in Solove’s taxonomy.
“The capabilities of AI refers to its ability to do things like infer information about users to predict where they’re going to go next or what they’re going to do next.”
Two examples of newly created privacy risks resulting from AI technologies that the researchers identified are physiognomy (the long debunked pseudoscientific art of judging one’s character from facial characteristics) and the proliferation of deepfake pornography.
“There’s a ‘distortion’ category in Solove’s taxonomy which addresses instances where information about you can be used against you, which at a general class would capture this use of deepfakes,” said Das. “But there’s something fundamentally new about the capability of AI to take information about you in one context and generate it to make photorealistic content about you in another context that information and computing technology wasn’t able to do in the past in a way that wasn’t obvious, or at least not without a lot of effort.
“It represents a new category of distortion risks that never existed in the past, and AI has fundamentally changed that.”
“The capabilities of AI refers to its ability to do things like infer information about users to predict where they’re going to go next or what they’re going to do next.”
Sauvik
Das, assistant professor at Carnegie Mellon University’s Human-Computer Interaction Institute (HCII)
Das and his team presented their findings in May at the Association for Computing Machinery’s (ACM’s) 2024 Computer-Human Interaction (CHI) Conference in Honolulu. And they hope to build on their current research to make it easier for practitioners and regulators to use their taxonomy to mitigate privacy risks when developing and managing these technologies.
“Soon, we’re going to have a web version of this taxonomy, so that should make it a little bit more accessible,” said Das. “Our hope is that this taxonomy gives practitioners a clear roadmap of the types of privacy risks that AI, specifically, can entail.”
CyLab celebrated 20 years of collaborating on cutting-edge research and educating the next generation of security and privacy professionals at its annual Partners Conference.
The conference, which was held October 3-5 at Carnegie Mellon University, highlighted the latest research in security and privacy with an interactive forum between faculty, students, industry, and government.
The hybrid event included three student poster sessions and a forum featuring more than 40 faculty and student presentations that focused on various aspects of seven topic areas, including:
• Generative AI and Machine learning
• System and hardware security
• IoT security and privacy
• Human factors in privacy and security
• Software security
• Blockchain and crypto
• Privacy

This year’s conference also included a special 20-Year panel, featuring CyLab leaders from throughout its twodecade history, sharing personal stories and memories of how CyLab grew from an idea amongst a few CMU faculty members into a worldwide leader in providing expertise on security and privacy issues.
“Looking back, I don’t think [CyLab] could have been created at any other place except CMU,” said Pradeep Khosla, founding director of CyLab. “I also think that the combination of actors was perfect, and it was the perfect time to do this.”

During the forum, Aaron Roth, the Henry Salvatori professor of Computer Science and Cognitive Science at the University of Pennsylvania, was officially recognized as CyLab’s 2023 Distinguished Alumni Award winner. Roth presented his latest research and received the award from his former advisee, Steven Wu, now assistant professor in CMU’s School of Computer Science.
“I really like the interdisciplinary nature of CyLab just as part of its existence.”
Tim Vidas, a principal engineer at Amazon Web Services
In addition to the forum, participants had the opportunity to tour CyLab’s Biometrics Lab, take part in demos on WiSE Lab and picoCTF, and network during the 20-Year Celebration Gala at the Heinz History Center.
CyLab partners who attended the event say the conference provides them with insight into the latest trends in cybersecurity and privacy and offers the opportunity to connect with colleagues and academics doing leading work in the field.
Continued on page 8


CyLab leaders from throughout its history gathered to share stories and memories of the institute’s growth during the 20-Year Panel. Jared Cohon, the eighth president of Carnegie Mellon University, died peacefully on March 16, 2024.
Left: Lorrie Cranor, CyLab director, address the audience at the 2023 Partners Conference.

CyLab helped start the SOUPS symposium in 2005 and the PEPR conference in 2019.

Continued from page 6
“One thing that I would say makes CyLab very different than a lot of the other research institutions is that most of the topics that they bring are the ones that we see successfully implemented in industry,” said Ilyas Iyoob, chief data scientist and global head of research at Kyndryl. “That gives us confidence to keep working here because we know whatever is built is going to see the light of day at the end.”
“It’s been great to not only meet the students and faculty but also meet the other partners and see that we’re part of an elite group — partners who are committed to not only the growth of CMU and CyLab but also the growth of these organizations as a whole, and to bringing security to the forefront of what we do,” said Jose Romero-Mariona, associate director of engineering at Raytheon Technologies.
“I really like the interdisciplinary nature of CyLab just as part of its existence,” said Tim Vidas, principal engineer at Amazon Web Services. “I think that that really influences the types of solutions that they seek, and their generally out-of-box thinking that doesn’t lean too hard on the traditional methods and procedures.”

“Looking back, I don’t think [CyLab] could have been created at any other place except CMU. I also think that the combination of actors was perfect, and it was the perfect time to do this.”
Pradeep Khosla, founding director of CyLab
“To me, if you are forward-thinking and you want to see the trends in the industry from a service perspective, this is the place to be because we have students who are working on things that we don’t think about on a dayto-day basis, and you get that research being done here by very smart people,” said Max Wandera, Director of Eaton’s Product Cybersecurity Center of Excellence.
CyLab’s partners include a wide variety of businesses and institutions, each united by a passion for creating a world in which technology can be trusted. To learn more about partnering with the Carnegie Mellon CyLab Security and Privacy Institute, contact Michael Lisanti, Director of Partnerships, at mlisanti@andrew.cmu.edu or 412-268-1870.
For over a decade, researchers at Carnegie Mellon University’s CyLab Security and Privacy Institute have been working to pioneer privacy nutrition labels, advocating for a quick and easy way to show tech users how their data is being collected and used.
In recent years, Apple has begun requiring app developers to disclose this type of information through privacy labels displayed in the iOS App Store. However, recent research has shown that app developers often struggle to create accurate privacy labels. “Little guidance, a laundry list of confusing terms, and a lack of privacy expertise among app developers often result in developers creating inaccurate labels,” said Norman Sadeh, co-director of CMU’s Privacy Engineering Program and head of the Usable Privacy Policy Project
“Inaccurate labels mislead users about the data an app might be collecting and how that app handles that data. In addition, it exposes app developers to regulatory penalties.”
To overcome this issue, Sadeh and his team have developed a new tool, Privacy Label Wiz (PLW), providing app developers with an easy-to-use, step-by-step resource to help effectively disclose their apps’ data practices.
“Privacy Label Wiz offers developers an efficient way to create accurate, user-friendly labels,” said Jack Gardner, a recent graduate of CMU’s Privacy Engineering master’s program and a key contributor to the tool’s development.
“Our tool not only generates a preliminary report based on its analysis of an app’s code, but also prompts developers for input to support the full consideration of their app’s functionality.”
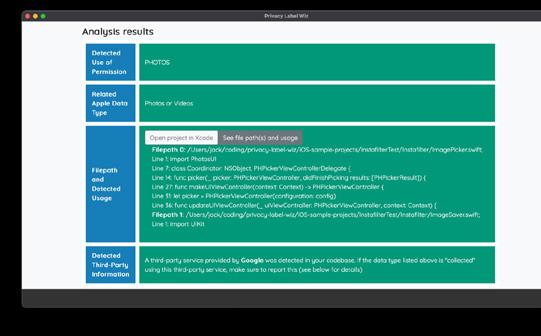
Once data collection and use practices have been determined, Privacy Label Wiz asks developers to confirm where the information will be sent and who will have access to it. Source:
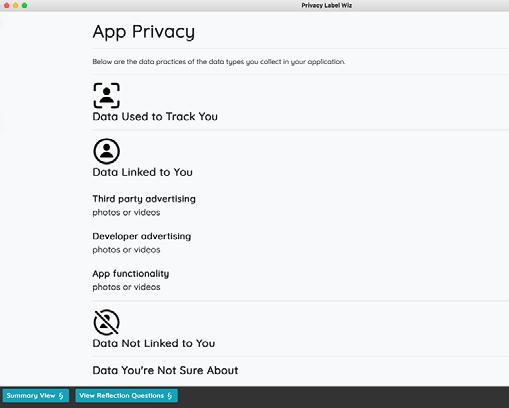

When the process is complete, Privacy Label Wiz generates a summary report for developers to review.
After installing the tool, developers are asked to load their apps’ static code. The code remains on their machine and is never shared with anyone. Privacy Label Wiz then analyzes the code to identify likely data collection and use practices, including whether the app records financial information, browsing history, the user’s location, or enables access to the device’s photos or camera, among others. The wizard also looks at whether sensitive data is shared with third parties such as advertisers or marketing companies, and more generally looks for other practices developers need to disclose in their iOS privacy labels.
Developers are then asked to review the tool’s analysis and confirm, modify, or supplement information about what data their app collects, how that data is handled and with whom it can be shared prompting app developers to answer additional questions as needed.
“In our research, we have found that developers often struggle with some of the terminology used by the iOS privacy labels and with the disclosure of a number of different data practices such as sharing sensitive data with third parties,” said Sadeh.
“Privacy Label Wiz is designed to systematically review a comprehensive list of questions with the developer and provide them with the support they need to more accurately disclose their app’s data practices.”
Privacy Label Wiz is now available for general public non-commercial use, with options for developers to commercially license the tool.
This summer, two CyLab papers that featured undergrads as lead writers were accepted and presented at major international conferences.

at CHI 2024.
“What is cool about this is, while undergrads frequently participate in research, undergrads being the lead authors is not that common,” said Dimitrios Skarlatos, assistant professor in Carnegie Mellon University’s Computer Science Department.
Skarlatos knows this firsthand, as he collaborated with two undergraduates in CMU’s Computer Architecture and Operating Systems (CAOS) group on a paper that was accepted at the 2024 International Symposium on Computer Architecture (ISCA).
The paper, “Perspective: A Principled Framework for Pliable and Secure Speculation in Operating Systems,” features CMU Computer Science (CS) undergrads Tae Hoon Kim and David Rudo as lead authors. Kim and Rudo presented this work in Buenos Aires, Argentina in June.
“We started this project in January of 2022. I first joined the group while looking for research mentors for the SCS research class 07-300,” said Kim, who is now a fifth-year
“I’m extremely grateful to have been given this opportunity; it was everything I had in mind and more.”
Dillon Shu, information systems undergraduate student, Carnegie Mellon University
CS master’s student. “Since then, this 2.5 year project has been a really challenging but rewarding journey. We are very grateful that it got accepted at ISCA, one of the top-tier conferences.”
In the paper, the research team proposes Perspective, a principled framework for building efficient, lightweight speculative execution defenses for operating systems against transient execution attacks.
“We show that there is a way of mitigating a wide net of malicious speculative attacks with minimal overhead,” said Rudo, a rising senior CS major with a security and privacy concentration. “And we specifically focus on the Linux kernel operating system because it is such an important piece of software that holds sensitive data attackers have tried to target in the past.”
“Our approach co-designs software and hardware so that it doesn’t require complex hardware. Another benefit of the software-hardware co-design is that we can obtain a highly pliable design by communicating our security goals through the software to the hardware,” said Kim. “So people can adapt it to their applications based on their security needs.”
While Kim and Rudo focused their research efforts on preventing cyber attacks, undergrads Claire C. Chen and Dillon Shu conducted consumer-facing research designed to empower customers to access reliable security and privacy information about Internet of Things (IoT) devices when making purchasing decisions.
Chen and Shu were lead authors on “Is a Trustmark and QR Code Enough? The Effect of IoT Security and Privacy Label Information Complexity on Consumer Comprehension and Behavior,” which Chen, a CMU School of Computer Science student, presented at the 2024 Association for Computing Machinery (ACM) Conference on Human Factors in Computing Systems (CHI 2024).


For the paper, Chen and Shu’s research team, working with faculty Lorrie Cranor and Yuvraj Agarwal, conducted an online survey with 518 IoT purchasers, through which they sought feedback on the labels that may someday accompany the official U.S. Cyber Trust Mark on IoT device packages to inform consumers about device security and privacy attributes.
The researchers examined survey participants’ comprehension and preferences for three labels of varying complexities, with and without an educational intervention.
“We designed labels with different levels of information and looked to see what difference that made for consumer purchasing decisions,” said Shu. “We learned that consumers preferred higher complexity labels, or labels with more information. Specifically, consumers almost unanimously did not like the labels with only the Trust Mark and QR code, which contained no privacy and security information on the label directly.”
Chen and Shu began working on the research as part of a class project in Cranor’s usable privacy and security course. After the semester was over, Cranor and Agarwal hired them as research assistants and they continued working on the project over the summer and submitted a paper for publication.
“We show that there is a way of mitigating a wide net of malicious speculative attacks with minimal overhead.”
David


Shu, an Information Systems student, said that the project helped him with his communication skills, and that he really appreciated the chance to work in a team research setting as an undergraduate student.
“I’m extremely grateful to have been given this opportunity; it was everything I had in mind and more,” said Shu. “On a personal level, I never considered research as a future path for me, but I felt since I was fortunate enough to have the opportunity I should see what it was like. It was a great chance to leave my comfort zone, and I figured this could be something that was a great fit for me that I simply hadn’t experienced yet.”
For Skarlatos, leading research on a major paper represents an invaluable growth opportunity for all undergraduate students, who gain experience and exposure to contemporary skills needed to tackle very challenging problems in the process of conducting their research. And it is an especially valuable résumé-builder for students who want to continue their academic studies beyond their undergraduate years.
“If you want to think about doing advanced studies, the earlier you think about conducting research, the better,” said Skarlatos. “Leading top tier research projects as an undergrad is a great pipeline to applying for advanced degree programs.”
This year, CyLab has awarded $400K in seed funding to 18 CMU students, faculty, and staff members representing five departments across three colleges at the university.
The funding was awarded on the projects’ intellectual merit, originality, potential impact, and fit towards the Security and Privacy Institute’s priorities. “This year’s funded projects represent and address a wide range of research competencies and challenges,” said Lorrie Cranor, director of CyLab, and professor in Carnegie Mellon’s School of Computer Science and Engineering and Public Policy Department. “These funds will address critical needs that will hopefully evolve into larger projects with additional external funding.”
“We are thankful to our partners for their support in empowering us to provide seed funding for these groundbreaking projects that have great potential for real-world application and positive societal impact,” said Michael Lisanti, CyLab’s director of partnerships. “Together, with our partners, we are driving innovation and shaping a more secure digital landscape for all.”
FUNDED PROJECTS:
Attacking LLM Watermarks by Exploiting Their Strengths
Wenting Zheng - assistant professor, Computer Science Department
Virginia Smith - Leonardo assistant professor of Machine Learning
LLMs for Code-injection Vulnerability Detection
Beidi Chen - assistant professor, Electrical and Computer Engineering
Limin Jia - research professor, Electrical and Computer Engineering
Corina Pasareanu - principal systems scientist, CyLab
Security Attacks and Robust Defense against LLMs
Lei Li - assistant professor, Language Technologies Institute
Daphne Ippolito - assistant professor, Language Technologies Institute
Steven Wu - assistant professor, School of Computer Science, Software and Societal Systems Department

Synergies and Trade-offs in Private Federated Learning
Gauri Joshi - associate professor, Electrical and Computer Engineering
Zhiwei Steven Wu - assistant professor, School of Computer Science, Software and Societal Systems Department
Amplifying Privacy and Scalability in Decentralized Learning
Osman Yağan - research professor, Electrical and Computer Engineering
Carlee Joe-Wong - Robert E. Doherty career development professor, Electrical and Computer Engineering
Mansi Sood - Ph.D. candidate, Electrical and Computer Engineering
ROSLock: Assuring Secure and Private Communications in ROS-based Robots
Claire Le Goues - professor, School of Computer Science, Software and Societal Systems Department
Christopher Timperley - systems scientist, Software and Societal Systems Department
Increasing Assurance in Verified Production Compilers
Fraser Brown - assistant professor, School of Computer Science, Software and Societal Systems Department
Bryan Parno - The Kavcic-Moura professor, Electrical and Computer Engineering
Practical, Software-Only Mitigations Against Frequency Side-Channel Attacks
Riccardo Paccagnella - assistant professor, School of Computer Science, Software and Societal Systems Department
CyLab’s Future Enterprise Security Initiative has announced its second round of funded proposals.
The 12 selected proposals will empower researchers and industry leaders to rethink security across enterprise ecosystems through innovations in artificial intelligence, computer science, engineering, and human-factors research.
Each project falls under one of the four FutureEnterprise@CyLab key research thrusts:
• AI-driven workflows to automate security management and data-driven decision-making to minimize the need for large human teams
• Collaborative capabilities for real-time global visibility for security decision making
• Foundations for understanding cyber risk and dependencies in complex ecosystems and supply chains
• Least-privilege-by-design infrastructure, including trustworthy outsourcing, remote work/ management, and deployable software-defined architectures
This year, Generative AI and Large Language Models (LLMs) were added as a technology of interest in all four research thrusts.
Funding for the projects is made possible by sponsorships from Amazon Web Services, Cisco, Microsoft, Nokia Bell Labs, PNC, and the VMware University Research Fund. Sponsors actively worked with FutureEnterprise@CyLab Co-Directors Lujo Bauer and Vyas Sekar on proposal requests and reviews.
During the execution of these projects, faculty will collaborate with FutureEnterprise@CyLab sponsors to develop a suite of novel foundations and technologies, re-imagining ways to achieve security in small- and medium-sized enterprise systems.
“The Future Enterprise Security Initiative brings lots of value to CyLab because we get to benefit from sponsors’ expertise — both their technical expertise and their understanding of which problems they’re struggling with most — so that we can direct our research energies towards solving the problems that really matter right now,” said Bauer.
SECOND ROUND OF FUNDED PROJECTS
Collaborative Capabilities
Adversarial Robustness and Unhardening Dynamics in Federated Learning
PI: Carlee Joe-Wong - associate professor, Electrical and Computer Engineering (ECE)

Evaluating Large Language Models’ Privacy Risks with Privacy Attacks
PI: Steven Wu - assistant professor, Software and Societal Systems Department (S3D)
Risk Assessment
Combining Program Synthesis and LLMs to Identify Code-Injection Vulnerabilities in Node.js packages
PIs: Ruben Martins - assistant research professor, Computer Science Department (CSD) and Limin JiaResearch Professor, ECE
ODO: Open Dependency Observatory for Software Dependencies
PI: Yuvraj Agarwal - associate professor, S3D and Rohan
Padhye - Assistant Professor, S3D
Harnessing LLMs for enabling fuzzing of high-level API properties
PI: Rohan Padhye - assistant professor, S3D
AI-Driven Workflows
Conversational AI to Simplify Wireless Enterprise Security
PI: Swarun Kumar - associate professor, ECE
LLM Self-Defense Against Adversarial Attacks for Coding Tasks
PI: Corina Pasareanu - principal systems scientist, CyLab and Limin Jia - Research Professor, ECE
Least Privilege by Design
Beyond Zero Trust Architectures for Enterprise Security
PI: Virgil Gligor - professor, ECE
Verus: Enabling Engineers to Develop Provably Secure and Performant Software
PI: Bryan Parno - associate professor, CSD and ECE
Adaptive Deployment of SDN/NFV Network Security
Infrastructure with SyNAPSE
PI: Justine Sherry - associate professor, CSD
Provable and Practical Defenses against Spatial Algorithmic Complexity Attacks
PI: Justine Sherry - associate professor, CSD
Enhancing Security and Portability with Lightweight Sandboxing using the WebAssembly Linux Interface
PI: Ben L. Titzer - principal researcher, S3D and Anthony Rowe - professor, ECE
The winning streak continues for Carnegie Mellon University’s competitive hacking team, Plaid Parliament of Pwning (PPP), who claimed first prize at the MITRE Embedded Capture the Flag (eCTF) competition for the third consecutive year.
This year’s team from PPP includes 13 students — undergraduates and graduates — enrolled in the departments of Computer Science and Electrical and Computer Engineering (ECE), as well as the Information Networking Institute (INI) master’s program. Students took a keen interest in this year’s competition, and some PPP members have participated multiple times in eCTF, allowing them to take on informal leadership and mentoring roles on the team.
Anthony Rowe of ECE, Patrick Tague of INI, and Maverick Woo of CyLab served as faculty advisors for the team.
The competition lasts the entire Spring semester and is broken into two phases: design and attack. Teams are evaluated for how well they cater to both functionality and security in their products.
Unlike many other capture the flag tournaments, MITRE eCTF focuses on embedded system security — which
“What we’ve observed is that if we don’t keep track of outstanding tasks, if we don’t have someone sketching out a timeline of what we need to get done and when, things don’t get done.”
Carson Swoveland, CMU ECE graduate
deals with protecting data and safety in field-deployed devices such as mobile phones and avionics equipment. This year’s theme was about securing a supply-chain solution for medical device manufacturers. During Phase 1, which began in January, PPP held weekly meetings

In addition to its MITRE win, PPP added to its legacy as the winningest team in DEF CON’s Capture the Flag competition history, clinching its third consecutive title in August, and earning its record eighth victory in the past 12 years.
PPP joined forces with CMU alumnus and University of British Columbia Professor Robert Xiao’s team, Maple Bacon, and hackers from CMU alumni startup Theori (The Duck), playing under the name Maple Mallard Magistrates (MMM).

to develop their product in accordance with the seven security requirements stipulated by the MITRE organizers.
“I learned a lot about how an embedded system can go wrong,” said Carson Swoveland, a recent ECE graduate.
“I don’t think any traditional courses focus on designing an embedded system with quite as much intensity and practicality as MITRE’s competition.”
According to Swoveland, one of the keys to PPP’s success was that everyone knew exactly what they were responsible for.
“What we’ve observed is that if we don’t keep track of outstanding tasks, if we don’t have someone sketching out a timeline of what we need to get done and when, things don’t get done,” said Swoveland, who will pursue a fifth-year master’s degree at CMU.
Phase 2, the attack phase, involves trying to find vulnerabilities in the embedded systems made by other teams. Swoveland says this stage also required considerable strategic collaboration. One group of teammates focused on exploiting a defect that several competing systems had in common, while the other group developed workarounds for separate issues. In this year’s competition, PPP’s system was one of a select few to not have any vulnerabilities successfully hacked by competing teams.
MITRE eCTF also mimics a commercial environment with its evaluation setup, splitting points between functionality, timeliness, and security. As Woo explains, rushing to turn in a product doesn’t guarantee a tournament victory — teams must resist the temptation to cave in to market pressure. In a commercial environment, the most effective and secure product will distinguish itself from the competition.
To help students perform at their best, CMU allows students to earn 12 course credits for participating in the eCTF. Students also have no financial obligations to participate in the tournament thanks to generous support from sponsors, who provide funding to purchase the hardware equipment necessary for the competition. This year’s team received funding support from Amazon Web Services, AT&T, Cisco, Infineon, Nokia Bell Labs, Rolls-Royce, and Siemens through the CyLab Partnership Program.
PPP’s success seems poised to continue. Woo believes that MITRE places a high premium on thoroughness, and he says that CMU students are well prepared because their courses teach them to do the right thing and not to compromise on the quality of solutions.
Additionally, several PPP team members hone their skills outside of MITRE eCTF by serving as problem writers for the annual picoCTF hacking competition, in which participants from middle schoolers and their teachers to undergraduate university students learn to overcome sets of challenges from six domains of cybersecurity including general skills, cryptography, web exploitation, and forensics.
Through writing for picoCTF, PPP team members gain a unique perspective on overcoming challenges by creating hacking challenges themselves. They also give back to the cybersecurity community by helping to educate the next generation of privacy and security professionals.
“I think our students are very driven to participate, and very entrepreneurial, so this activity suits them well,” said Woo.

Alina Oprea, professor in the Khoury College of Computer Sciences at Northeastern University, has been named CyLab’s 2024 Distinguished Alumni Award winner.
“I am truly honored and grateful to the CyLab community for this recognition,” said Oprea. “I would like to thank everyone in CyLab who supported my journey in cybersecurity, starting with my Ph.D. advisor Mike Reiter, the founding technical director of CyLab, and my wonderful colleagues.”
Nominated by Vyas Sekar, Oprea’s former CyLab classmate and now Tan family professor in CMU’s Department of Electrical and Computer Engineering, the award recognizes Oprea’s “foundational contributions to the theory and practice of trustworthy AI, including understanding the security and privacy risks of MLbased critical applications, and developing techniques to improve their resilience.”
Oprea was amongst the first CyLab students when CMU’s Security and Privacy Institute launched in 2003. She earned her Ph.D. in Computer Science from Carnegie Mellon University in 2007, where she was advised by Michael Reiter, CyLab’s founding technical director.
Oprea’s Ph.D. dissertation, “Efficient Cryptographic Techniques for Securing Storage Systems,” proposed new cryptographic approaches that provide rigorous security for networked storage systems and are efficient to implement in practice.
“At the time, several outsourced storage services for remote data backup were available long before cloud computing became widespread. However, the security of these services was not well understood,” said Oprea. “We developed new security mechanisms to protect this data, and that prepared me quite well for going to an industry research lab, where I started working more on cloud computing security.”
After graduating from CMU, Oprea spent nine years at RSA Labs as a principal and consultant research scientist. During this time, she conducted groundbreaking research on integrity protection for data stored in cloud systems, game theoretical modeling of cyber interactions, and utilizing AI to detect cyber attacks.
“We developed several techniques where we analyzed security logs, network logs, and web traffic in order to proactively detect anomalies and cyber attacks using machine learning,” said Oprea. “And some of these methods were actually deployed in an RSA product to protect organizations against cyber attacks. So that part was very rewarding to be able to see research incorporated into a real product, which is kind of rare for industry research.”
In 2016, Oprea joined Northeastern’s Khoury College of Computer Sciences as a tenure-track faculty member, where she has taught courses on cryptography, machine learning, and special topics courses on the security and privacy of machine learning. Currently, Oprea co-directs the Network and Distributed Systems Security Lab, which focuses on AI-enabled cyber defense, trustworthy AI, cloud security, and secure distributed systems. She is also a founding member of the Northeastern Cybersecurity and Privacy Institute.

“I am truly honored and grateful to the CyLab community for this recognition.”
Alina
Oprea, CyLab’s 2024 Distinguished Alumni Award winner
As the co-author of numerous journal and peer-review conference papers, Oprea has participated in a large number of technical program committees (IEEE S&P, NDSS, ACM CCS, ACSAC, DSN) and is a co-inventor of 30 issued patents. Opera served as co-chair of the flagship security conference, the IEEE Symposium on Security and Privacy, in 2020 and 2021, and she will serve as its general chair in 2025 and 2026. She currently sits as an associate editor for the IEEE Security and Privacy Magazine.
Oprea has been recognized for her work and contributions to the field of cybersecurity through a number of awards, including a Best Paper Award at the 2005 Network and Distributed System Security Conference, the Technology Review TR35 award for research in cloud security in 2011, and the Google Security and Privacy Award in 2019.
Oprea says that her current research focuses on the area of trustworthy AI, which aims to analyze the security and privacy of machine learning algorithms and systems.
“Recently, we have been looking at privacy techniques in AI,” said Oprea. “Generative AI models are trained on sensitive user data, like user chat histories or email messages, and we really want to protect the privacy of the users when we train these AI models.”
In the CyLab Distinguished Alumni Award’s fifth year, Oprea joins 2023 winner Aaron Roth, 2022 winner Michelle Mazurek, 2021 winner Yinglian Xie, and 2020 winner Elaine Shi.
Oprea will be presented with the award and give a talk on the security and privacy of generative AI at CyLab’s annual Partners Conference on September 25, 2024.
In celebration of International Privacy Day, Carnegie Mellon University teamed up with Carnegie Library of Pittsburgh (CLP) to host Data Privacy Day 2024.

The event took place on Sunday, January 28 from 11 a.m. to 1 p.m. at CLP-Main (Oakland) in the South Wing Reading Room on the 2nd floor.
Carnegie Mellon hosted its first Data Privacy Day in 2014 as part of an international effort to empower and educate people to protect their privacy and control their digital footprint. For its ninth installment, CMU collaborated with CLP to celebrate International Data Privacy Day by bringing practical advice on protecting privacy online to the general public, holding the event off the university’s campus for the first time.
“We wanted to take a more community-oriented approach this year,” said Hana Habib, associate director of Carnegie Mellon University’s Masters in Privacy Engineering program. “This event is centered on our Privacy Clinic, which involves CMU students and researchers who are experts in the privacy domain identifying topics of interest to the general public, and advising them on how they can take a more privacy-protective approach to how they use the internet.”
This year’s Privacy Clinic gave attendees an opportunity to learn strategies for protecting their privacy during their daily usage of digital technology. CMU’s information privacy and security students and

researchers provided information and answered questions about privacy risks and remedies concerning topics ranging from creating strong passwords and private browsing, to posting sensitive information and understanding iPhone app privacy reports.
For Habib, Data Privacy Day provides a great occasion for privacy practitioners to teach the community about tools that are often easy to overlook, but are crucial to empowering individuals to protect their data in a digital world.
“In the U.S., privacy protection largely falls on the hands of consumers, so it’s really up to end users to take the steps to protect their privacy,” said Habib. “A lot of people don’t have the time to do that, or the knowledge and skill set to use all of the different tools or settings that they could be, so this is an opportunity for us who work in privacy to help people learn about the ways that they can take action to protect their privacy.”
“We
wanted to take a communityoriented approach this year.”
Hana Habib, associate director of Carnegie Mellon University’s Master of Science in Privacy Engineering program

September 6, 2023
Arlen Cox
Researcher, Institute for Defense Analyses / Center for Computer Sciences

Program Analysis in the Face of Uncertainty

September 11, 2023
Srini Devadas
Webster Professor of EECS, Massachusetts Institute of Technology
PAC Privacy: Automatic Privacy Measurement and Control of Data Processing
September 25, 2023
Jody R. Westby, Esq.

CEO, Global Cyber Risk LLC, Managing Principal, Global Cyber Legal LLC
Why Content on Technology-Related Laws and Regulations Should Be Integrated in Interdisciplinary Curricula

October 16, 2023
Mark Seiden
Former Lecturer at the University of California, Berkeley How much trust can we put in ratings and reviews on the Internet? Based on a not very scientific study, not much
October 23, 2023
Eugene H. Spafford
Webster Professor of Computer Science, Purdue University

Looking at Cybersecurity Myths and Some Problems They Pose
November 13, 2023
Marshini Chetty
Associate Professor, Department of Computer Science, University of Chicago I Always Feel Like Somebody’s Watching Me: Privacy and Security Issues In K-12 and Beyond
January 22, 2024

Lei Li

Assistant Professor, Carnegie Mellon University Language Technologies Institute Is It Generated by AI? Attacks and Robust Watermarking for Generative AI
February 5, 2024
Nina Narodytska
Staff Researcher, VMware Research by Broadcom

Lemur: Integrating Large Language Models in Automated Program
Verification
February 12, 2024
Mike Hicks

Senior Principal Scientist, Amazon Web Services; Professor Emeritus, University of Maryland Cedar: A language for expressing fast, safe, and fine-grained authorization policies
February 19, 2024
Rahul Chatterjee
Assistant Professor in Computer Sciences, University of Wisconsin–Madison Privacy and Safety Issues of Smart Home Devices
April 1, 2024

Elette Boyle

April 12, 2024
Andrew Kongs

Senior Manager, Security Integration and Testing at Rivian Defending Modern Connected Vehicles
April 22, 2024
Riccardo Paccagnella
Assistant Professor, Carnegie Mellon

University Software and Societal Systems and the Department of Electrical and Computer Engineering Timing Attacks on Constant-Time Code
April 29, 2024
Dan Boneh Professor of Computer Science, Stanford University
Recent Developments in Succinct roof Systems and Their Applications

May 6, 2024

Rahul Telang Trustees Professor of Information Systems, Carnegie Mellon University’s Heinz College of Information Systems and Public Policy Merchants of Vulnerabilities: How Bug Bounty Programs Benefit Software Vendors
May 6, 2024
Tawfiq Alashoor
Assistant Professor of Operations, Information and Technology, IESE

Business School, University of Navarra
The General Relativity of Privacy: From Spacetime to Contextimes
Associate Professor and Director of Foundations and Applications of Cryptography (FACT) Research Center at Reichman University, Israel Zero-Knowledge Proofs on Distributed Data and Cryptographic Applications
Each year, CyLab recognizes high-achieving Ph.D. students pursuing security and/or privacy-related research with a CyLab Presidential Fellowship, covering an entire year of tuition.
This year’s CyLab Presidential Fellowship recipients are:

Ph.D. Student, Computer Science Department
Advised by Aayush Jain, Assistant Professor, Computer Science Department, and Riad Wahby, Assistant Professor, Electrical and Computer Engineering
Quang’s research focuses on ensuring the long-term security of zero-knowledge proof systems (ZKPs) through two primary avenues: formal verification of ZKP implementations, and post-quantum secure proof systems.
Ian McCormack
Ph.D. Student, Software and Societal Systems Department
Advised by Jonathan Aldrich, Professor, Software and Societal Systems Department and Director, Software Engineering Ph.D. program; and Joshua Sunshine, Assistant Professor, Software and Societal Systems Department

Ian’s research addresses the challenges of foreign function interfaces in Rust — a programming language that is generating a lot of excitement because it is fast and low-level while still providing guarantees of memory safety and race freedom, both of which are critical to the security of modern applications.

Ph.D. Student, Computer Science Department
Advised by Wenting Zheng, Assistant Professor, Computer Science Department, and Virginia Smith, Leonardo Associate Professor of Machine Learning
Qi’s research focuses on addressing the privacy and
security issues in machine learning (ML) systems by revealing new attack vulnerabilities (ADI and Watermark Attack) and developing efficient and secure ML systems using cryptographic and ML techniques (MPCDiff and BOLT).
Ph.D. Student, Software and Societal Systems Department
Advised by Yuvraj Agarwal, Associate Professor, Software and Societal Systems Department

Prasoon’s research focuses on developing an activity discovery system for unseen environments that optimizes the balance between model performance and user privacy protection. He aims to minimize the amount and sensitivity of data collected from users while maintaining highquality activity recognition. To achieve this, he proposes a multi-faceted approach that leverages innovative training methods and prioritizes user control over data sharing.
Ph.D. Student, Electrical and Computer Engineering Department
Advised by Akshitha Sriraman, Assistant Professor, Electrical and Computer Engineering Department
Sara’s research vision is to rethink the data center computing stack across hardware and software systems to enable demographic bias-free web systems that also preserve user privacy. Her proposed research makes a case for how web systems must consider demographic bias as a key systems concern (similar to performance or power).

From March 12–26, thousands of participants competed in the picoCTF competition hosted by Carnegie Mellon University’s CyLab Security and Privacy Institute.


The more than 18,000 participants ranged from middle schoolers and their teachers to undergraduate university students.
picoCTF’s first hacking competition took place in 2013, and featured around 6,000 participants. Eleven years later, it is now one of the most well-known hacking capturethe-flag competitions in the cybersecurity industry.
picoCTF includes challenges across several disciplines, including forensics, cryptography, reverse engineering, web security, and others. Challenges are designed by faculty, staff, and students from Carnegie Mellon University, many from the internationally acclaimed hacking team, the Plaid Parliament of Pwning.
Participants have to beat the challenge in order to find the answer, or “capture the flag,” and the challenges progressively become harder as the competition advances. All teams who manage to capture a challenge’s flag receive the same number of points in reward, regardless of how quickly it takes them to solve each individual challenge.
“Our goal is to encourage everyone, even new people with no background in it, to try cybersecurity,” said Megan Kearns, picoCTF Program Director.
“Our
goal is to encourage everyone, even new people with no background in it, to try cybersecurity.”
Megan Kearns, picoCTF program director
Because of its focus on inclusion, picoCTF is now more than just an annual competition. “picoCTF is a year-round cybersecurity program with a competition,” said Kearns. “There are more competitions appearing every year and it’s a great way to test your skills. What students need is a place to learn and build those skills at their own pace.”
After the 2018 competition season, participants reached out to Kearns asking for the challenges to be kept open so they could practice. This led to the picoCTF team developing picoGym, a noncompetitive space to practice hacking and cybersecurity techniques.
picoGym’s challenges consist of samples from previous years’ competitions, along with new challenges to solve. In addition, the picoCTF team hosts YouTube tutorials on cybersecurity practices for students and teachers.
The competition is an optional part of the picoCTF programming, and participants must register to compete in the weeks leading up to its launch. While this year’s competition involved an impressive 18,000 people, the platform as a whole boasts over 600,000 active users across the world throughout the year.
While most participants are based in the United States, picoCTF also serves a robust international community. Japan and Africa have their own regional leaderboards for the competition, which has helped to develop more robust young cybersecurity communities in these areas.
It’s easy to get involved, since signing up for an account on the picoCTF website is free and open to all. In order to stay accessible, the program mostly receives funding though sponsorships and grants.





According to Kearns, the expansion of picoCTF into a year-round program was “how we blew up to what we are today.” Now, picoCTF is well-known in the field: Kearns always finds engagement at conferences, and students make connections with prospective employers through their shared experiences of picoCTF. This has resulted in a community built around cybersecurity.
“picoCTF is established and widely known for its reputation as the place to begin learning about cybersecurity and capture-the-flag competitions,” said Kearns. “Come in anonymously, play at your own place, and build up skillsets.” And it grows every year as it succeeds in its mission to introduce cybersecurity to a new generation of programmers.
1st Place: enzocut
2nd Place: obafgkm
3rd Place: flocto

1st Place: smiley-face cartel



2nd Place: les amateurs

3rd Place: rip rhythm


1st Place: gheeeedra

2nd Place: UCSD SHS

3rd Place: Open Parenthesis Colon

In its second year running, CMUAfrica Week welcomed students from the land of a thousand hills to the city of bridges.
The annual event aims to build a stronger connection between the two College of Engineering locations and highlight the research happening in Kigali, Rwanda.


thirteen students traveled from CMU-Africa and joined 12 of their peers who have been studying in Pittsburgh for the semester through the global campus exchange program. Throughout the week, the students had the opportunity to experience CMU’s Pittsburgh campus through tours of the Tech Spark, Mill19, and the JPMorgan Chase & Co. AI Maker Space. They also had the chance to visit and tour companies like Google, explore the city, and attend a few events, including a Pittsburgh Pirates game.
“Welcoming CMU-Africa students to campus for the exchange program and this annual event is a wonderful experience for not only the visiting students, but the entire Carnegie Mellon community.” says Jennifer Spirer, director of graduate affairs in the College of Engineering. “Creating cross-cultural connections allows for a tremendous learning experience.”
On April 10, the CyLab Security and Privacy Institute and the College of Engineering hosted a day-long event for the Carnegie Mellon community with an agenda featuring African culture and engineering research spanning CMU-Pittsburgh and CMU-Africa. The day began with a series of research talks from faculty, including CMU-Africa’s Moise Busogi and George Okeyo. Students then led a poster session showcasing their research in fields such as agriculture, healthcare, cybersecurity, and policy development. Many projects highlighted the use of artificial intelligence, including in the automated detection of neonatal asphyxia, AIdriven precision farming, and livestock identification.


Following the poster session, students transitioned to a cultural event that included presentations about the diversity of the African continent. Students talked about the traditions, language, food, music, and art of their home countries. The audience joined in the fun through a series of quizzes and games about the presentations.
“CMU-Africa Week is an important tradition that gives faculty and students—who are normally located across the world from one another—the opportunity to engage in person,” said George Okeyo, associate teaching professor and director of academics at CMU-Africa. “The event gives greater visibility to the many ways that we can work together to solve global challenges through research and educational programs.”
As the presence of mobile phones becomes increasingly widespread in Africa, digital services have allowed for more financial inclusion among low- and middle-income countries within the continent.

Through a system known as mobile money (MoMo), users are able to make transactions through telephone companies, using their phone number as an account number as opposed to opening a traditional account at a financial institution.
Telephone companies rely on third parties known as “agents” to digitize physical cash and facilitate these transactions. However, although the convenience of this system allows a larger population base to be reached, it brings with it unique privacy and security challenges.
A group of Carnegie Mellon University researchers led by Karen Sowon, a postdoctoral researcher at CMU’s CyLab Security and Privacy Institute, investigated these issues and recently published a paper on “The Role of User-Agent Interactions on Mobile Money Practices in Kenya and Tanzania.” The work, which includes researchers from CMU’s Pittsburgh campus and Kigali location, was presented at the 45th Institute of Electrical and Electronics Engineers (IEEE) Symposium on Security and Privacy.
The paper presents data from 72 interviews with MoMo users in Kenya and Tanzania. The researchers discovered three primary insights related to the interactions between users and agents. First, they identified and categorized the many challenges users face when engaging with the MoMo system and the potential causes behind them. These included issues with know-your-customer (KYC) compliance, interface accessibility and usability, and privacy and security concerns with agents.
Subsequently, they were able to highlight the various workarounds that both users and agents utilize to circumvent these challenges and their associated risks, as well as identify reasons users would choose one agent over another.

“We found that factors like choice of agent were not just for convenience, but also because people thought it might mitigate some of the inherent privacy risks of MoMo or the ones the workarounds were creating,” said Sowon. “For example, some users, when transacting large amounts of money, would use an agent in another town or place where they are completely unknown instead of the agent they would normally use to create anonymity. But, of course, there are privacy and security risks with that, too.”
Following this study, Sowon and her team have a better idea of some of the considerations their future solutions must include. The difference between basic feature phones common in Africa and smartphones present the challenge of exclusivity and ensuring that the technical solutions they create are accessible to all users.
“In situations where people don’t have mobile money, they could potentially be left out of economic opportunities and exacerbate their economic status,” Sowon explained. “So, we need to be thinking of things like this in terms of inclusion and future solutions.”
Sowon and her team are now evaluating new MoMo protocols that could address some of the challenges identified in their study, such as allowing people to authenticate themselves to the MoMo system without having to share their personal information with an agent.
The team of researchers included Karen Sowon, Edith Luhanga, Lorrie Faith Cranor, Giulia Fanti, Conrad Tucker, and Assane Gueye. This research was made possible through the funding of the Bill and Melinda Gates Foundation.
CyLab-Africa researchers partner with mobile security provider for
Researchers from CyLab-Africa and the Upanzi Network recently partnered with the mobile security provider Approov to explore the security of common financial services apps used across Africa. After surveying 224 popular financial applications, the researchers found that 95 percent of these Android apps exposed secrets that can be used to reveal personal and financial data. Across these applications, approximately 272 million users have the potential to be victims of the security flaws.
The Carnegie Mellon University Africa team included alumni and a current student who are all working as researchers with CyLab-Africa in Rwanda: Theoneste Byagutangaza (MSIT ‘23), Trevor Henry Chiboora (MSIT ‘23), Joel Jefferson Musiime (MSIT ‘24), and Lenah Chacha (MSIT ‘17). The project was part of a summer collaboration experience where the CyLab-Africa researchers received guidance and mentorship from Approov. CyLab-Africa co-directors Assane Gueye and Giulia Fanti served as advisors for this project.
“Participating in this project was a rewarding yet challenging experience. It involved in-depth research into the consequences of secret key leaks, which

CyLab-Africa co-directors Assane Gueye and Giulia Fanti served as advisors for this project.


proved to be a formidable task initially. However, collaborating with a diverse team enriched my problem-solving skills, honed during my time as a student at CMU, and made the project a valuable learning opportunity,” said Byagutangaza.
The team selected and investigated Android applications from countries in North, Central, Eastern, Western, and Southern Africa and categorized the security threats into “high,” “medium,” and “low” severity. The majority of the threats fell into the high (18 percent) and medium (72 percent) categories. A high severity classification was used for vulnerabilities that could potentially lead to unauthorized access, data breaches, and compromised user privacy. Medium severity was used for secrets that if exposed, could potentially compromise the confidentiality of user data and application functionality.
“Being new in the field of mobile security, this project was a good learning experience as it gave me an understanding on the design and deployment of mobile apps from a security perspective,” said Musiime. “Collaborating with the experienced team at Approov in the field of mobile security greatly aided my learning process, as they were always ready and willing to offer guidance and support throughout the research.”
The work culminated in a report which draws comparisons between other regions and Africa, pinpointing trends, commonalities, and disparities pertaining to the exposure of secret keys in a mobile application’s binary package. For example, they found that apps deployed in West Africa were the most exposed in terms of high severity secret exposure (20 percent) and Southern Africa the least (only 6 percent).
“The project report holds significant value for a wide audience, including product owners, developers, and everyday users. It not only sheds light on security concerns related to secrets and API keys in Android packages but also provides valuable recommendations for mitigating these issues,” said Chiboora.
Despite advances, many research questions still need to be answered to ensure blockchain protocols and applications are ready for widespread use.

As the industry continues to see more consumer applications, such as decentralized finance (DeFi), securing the fundamental research elements of the technology, especially from a security, privacy, ethics, and societal impact perspective, is of utmost importance.
To address these research challenges, Carnegie Mellon University’s Secure Blockchain Initiative (SBI) brought together the foremost blockchain researchers and industry experts for the Second Annual Secure Blockchain Summit.
“Blockchain is an incredibly interdisciplinary area,” said Elaine Shi, co-director of the SBI, during her opening remarks at the summit. “Our cross-campus initiative spans multiple colleges across the university, and today’s programming will reflect that.”
Held April 16-17 on the Carnegie Mellon campus, the two-day event featured six sessions and more than 30 speakers and panelists across industry and academia who
presented groundbreaking research and best practices on topics such as cryptoeconomics, applied cryptography, programming languages, policy and regulation, formal methods, and more.
The agenda featured researchers from top universities, including Princeton, Stanford, and Duke, with areas of expertise ranging from computer science and economics to public policy and human-computer interaction.
The summit also featured presentations by leaders from a diverse range of nonprofit, corporate, and government organizations such as J.P. Morgan, Moody’s Ratings, and the Federal Reserve Bank of Philadelphia.
Carole House, executive in residence at Terranet Ventures and a nonresident senior fellow at the Atlantic Council, presented the keynote address on the topic of “Identity, Security, and Accountability: Critical Evolutions Needed for Trustworthy Blockchain Ecosystems.”
Matt Weinberg, associate professor at Princeton University, shared a feature presentation in which he revisited the primitives of transaction fee mechanism design. And a number of Carnegie Mellon Ph.D. students
Carnegie Mellon University’s Secure Blockchain Initiative (SBI) has announced its second round of funded proposals, providing $90K to three groundbreaking research projects that are exploring the security and privacy of distributed ledger technology.
Through research, the CMU SBI aims to revolutionize blockchain technology within enterprise ecosystems by tackling various challenges, including enhancing consensus mechanisms and scalability, exploring cryptocurrencies and markets, advancing cryptography, implementing formal verification, and addressing regulation, policy, and governance concerns.
Led by co-directors Nicolas Christin, Elaine Shi, and Ariel ZetlinJones, the multi-year CyLab initiative intends to develop a suite of novel foundations and technologies focused on three key research thrusts:
• Cryptoeconomics: Cryptography, Consensus, and Verification
• Applications and Implementations
• Cryptocurrencies, Tokenized Assets, and Policy

shared their most recent web3 research, including Hao Chung, Abhiram Kothapalli, Mingxun Zhou, and Ke Wu, who recently accepted a tenure-track faculty position at the University of Michigan.
In addition to the keynote, featured presentations, and lightning talks, Ariel Zetlin-Jones, co-director of the SBI, moderated a policy panel featuring Peter Van Valkenburgh of the Coin Center, Thomas Ruchti of the Office of Financial Research at the U.S. Department of the Treasury, and Chester Spatt of CMU’s Tepper School of Business.
The Secure Blockchain Summit also featured a dinner on day one, a networking reception on day two, and multiple breakout sessions throughout the event to give experts from around the world an opportunity to share their research and discuss the future of distributed ledger technology and its applications.
Each of the following researchers provided lightning talks previewing their funded research at the 2024 Carnegie Mellon University Secure Blockchain Summit: Analysis and Optimization of Resilience in Ripple Transaction Network
Osman Yağan - research professor, Electrical and Computer Engineering (ECE)
Modeling and Reasoning about Secure Multi-Party Computation (MPC) Deployment
Fraser Brown - assistant professor, Software and Societal Systems Department (S3D)
Eunsuk Kang -assistant professor, Software and Societal Systems Department (S3D)

“One of our goals for this conference was to bring together engineers, computer scientists, and economists who are all working in this space together to learn from each other,” said Zetlin-Jones during his closing remarks at the summit. “I found it inspiring and enlightening, and we want to thank all of the speakers and presenters for participating.”
The Secure Blockchain Summit was made possible thanks to the generous support of this year’s sponsors, the Algorand Foundation, Ripple, Jito Labs, and SoftLedger. Interested in supporting the Secure Blockchain Initiative? Reach out to Michael Lisanti, Director of Partnerships, at mlisanti@andrew.cmu.edu or 412-268-1870.

How Automated Market Maker (AMM) Reward Functions Can (Dis-)Incentivize Strategic Liquidity Providers
Giulia Fanti - Angel Jordan associate professor, Electrical and Chemical Engineering (ECE)
Funding for these projects is made possible by the following sponsors:


Ripple launched the University Blockchain Research Initiative (UBRI) in 2018 to foster collaborative partnerships with leading universities globally to support academic research, technical development, and innovation in blockchain, cryptocurrency, and digital payments.



In the five years since, Carnegie Mellon University faculty members, students, and alumni have made a big impact on UBRI’s diverse portfolio of blockchain research, technical development, and innovation.
“UBRI has been a cornerstone of our university-wide blockchain initiative, and their support has really catalyzed cross-campus blockchain research and curricular collaborations between faculty and students,” said Ariel Zetlin-Jones, associate professor of economics at Carnegie Mellon’s Tepper School of Business.
Zetlin-Jones, co-director of the CMU Secure Blockchain Initiative, was recognized as UBRI’s 2022 Educator honoree in the category of Courses, primarily for his work in the class “Developing Blockchain Use Cases,” which he co-developed and co-teaches with Elaine Shi and Mike McCarthy
Through the course, students have an opportunity to propose and develop applications or use cases for a campus blockchain. Along the way, they learn practical development skills in distributed ledger technologies (DLT) to understand blockchain programming and application development.
In addition to his teaching, Zetlin-Jones regularly presents to U.S. representatives as a DLT expert, and he was a featured speaker on the topic of Liquidity Provisions in DeFi Markets at last month’s UBRI Connect conference in Toronto.
“Economists well understand that when people have differences of opinion about the value of assets—such as cryptocurrencies—there might be gains to reallocating those assets to the people who most value them,” said Zetlin-Jones during his UBRI Connect presentation. “Our research provides a new, fundamental framework to
“Being at CMU gave me the room to really just play around with different ideas and get a better flavor for what research-oriented paths into the blockchain space look like.”
Eugene Leventhal, (HNZ ‘19), executive director of the Metagovernance Project

Eugene Leventhal (HNZ ‘19), executive director of the Metagovernance Project, received the 2023 UBRI Legend award.
“I was attracted to doing blockchain research because of the exciting technical challenges that lie at the intersection of cryptography, distributed systems, and economics.”
Elaine
Shi, associate professor, Computer Science Department, Electrical and
Computer Engineering
evaluate methods to create liquidity that supports this type of exchange natively on blockchains.”
Shi, co-director of the CMU Secure Blockchain Initiative, was similarly recognized in 2022 as the UBRI Innovator honoree as a professor for her breakthrough research in the sector. Shi’s renowned research in cryptography, game theory, algorithms and foundations, and blockchains was cited by UBRI during its presentation of the honor, particularly her work on scalable large-scale consensus and incentives.
“I was attracted to doing blockchain research because of the exciting technical challenges that lie at the intersection of cryptography, distributed systems, and economics.,” said Shi, professor in CMU’s Computer Science and Electrical and Computer Engineering departments.
As a featured speaker at UBRI Connect 2023, Shi presented “Unveiling the Future: From Theory to Transformation with Oblivious RAM.” During her presentation, Shi described how Oblivious Ram (ORAM) evolved from a theoretical concept to large-scale, realworld deployment, shared strategies for constructing ORAM, and talked about ORAM applications and challenges to deployment.
“Do you need trusted hardware? If you do, you likely need ORAM. It pretty much goes hand-in-hand with Intel SGX and other trusted hardware,” said Shi during her UBRI Connect presentation.
CyLab’s most recent honoree at the 2023 UBRI Awards is Eugene Leventhal (HNZ ‘19), a Master of Science in Public Policy and Management alumnus from CMU’s Heinz College of Information Science and Public Policy.
Leventhal was the recipient of the 2023 UBRI Legend award, presented to UBRI alumni that are currently working and thriving in the field of blockchain technology. This year’s awards were presented at Ripple’s annual UBRI Connect, and the judging panel saw over 35 nominations in only eight categories.
“It’s always just nice to be recognized for any kind of existing work,” said Leventhal. “It was a very unexpected thing and I received word of the honor on a very stressful day, so it was a nice little thing to put a smile on my face at the end of the day.”
Leventhal expressed an interest in blockchain and web3 technologies as a Heinz College student, leading the CMU Blockchain Group student club as its president. Upon completing his graduate studies in 2019, Leventhal began his career in the blockchain space as project and partnerships manager for CyLab, where he supported partnership discussions and events for the Secure Blockchain Initiative. He then moved on to the Smart Contract Research Forum (SCRF), a startup organization dedicated to advancing web3 through research and knowledge-sharing, where he served as its operations lead and, later, executive director.
Today, Leventhal serves as the executive director of the Metagovernance Project, an interdisciplinary research collective that builds standards and infrastructure for digital self-governance.
“Being at CMU gave me the room to really just play around with different ideas and get a better flavor for what research-oriented paths into the blockchain space look like,” said Leventhal. “It showed me a lot of the potential rigor toward going into this space from the right angles, and it was really exciting to get to build off of that.”
As a top-tier institution with renowned faculty and researchers, Carnegie Mellon University produces graduates who are poised to become leaders in their respective fields. CMU launched the CyLab Venture Network in June to provide a substantive program for startups looking to disrupt the security and privacy industry by connecting founders with venture investors, corporate partners, academics, and government officials.

Michael Lisanti, director of partnerships at the CyLab Security and Privacy Institute, said the program is a direct reaction to high industry demand to partner with CMU security and privacy startups, and that spotlighting these companies is an important part of CMU’s identity and social impact.
“Innovation and entrepreneurship are innate in the CMU DNA, and we are seeing a growing number of our computer science, engineering, and business startups succeed in the market,” Lisanti said. “The goal is to inspire even more students and faculty to explore creating cybersecurity startups, and to help existing startups in the Network become more successful.”
Partner sponsorship for startups in the Cylab Venture Network is reserved for early- and growth-stage companies. The Network launched with 20 startups across multiple sectors and stages, developing some

“The goal is to inspire even more students and faculty to explore creating cybersecurity startups, and to help existing startups in the Network become more successful.”
Michael Lisanti, director of partnerships, CyLab
of the most disruptive technologies in the security and privacy industry.
“For an early-stage startup like ours, the connections the CyLab Venture Network will enable can be gamechanging, particularly as we start to grow and hire more,” said Giulia Fanti, co-founder and chief scientist at Rockfish Data, a Venture Network startup.
“The CyLab Venture Network is an amazing opportunity for CMU faculty, students, and entrepreneurs,” added Vyas Sekar, co-founder and chief technologist at Rockfish Data. “For a growing startup like Rockfish, it is an incredible opportunity to tap into the broader CyLab network of academics and industry practitioners to work together to create industry-changing solutions.”
“The CyLab Venture Network is offering unparalleled access to a community of leading experts and potential collaborators,” said Fraser Brown, co-founder and CTO at Cubist, another inaugural Venture Network startup. “We can’t wait to see what it makes possible.”
“As a member of CyLab’s core faculty, I’ve seen firsthand the value that CyLab brings to its industry partnerships. So I am completely thrilled that Cubist is joining the CyLab Venture Network,” said Riad Wahby, co-founder and CEO at Cubist.
As part of this dynamic ecosystem, partners will receive exclusive invitations to participate in CyLab’s annual partners conference and engage in innovative programming developed in collaboration with CMU’s Swartz Center for Entrepreneurship.
Two VC firms signed on to be investor partners of the Venture Network. 412 Venture Fund supports technology and technology-enabled companies with ties to the Pittsburgh region, making CMU a fitting partner, especially since its leadership team includes several alumni.

















“We’re looking for the next Wombat Technologies,” said Ilana Diamond, Managing Partner of 412 Venture Fund.
“Norman Sadeh, Jason Hong, and Lorrie Cranor, cofounders of Wombat Security Technologies, spun the company out from a CyLab research project, attracting significant Venture Capital and eventually leading the company to a successful exit. With Norman joining 412 Venture Fund as a Limited Partner, he’s come full cycle as a successful CyLab founder using his expertise and resources to support a new generation of entrepreneurs from CMU and the Pittsburgh region.”
DataTribe, based in the Baltimore-Washington corridor, also features several Carnegie Mellon alumni in leadership roles, as it caters to the needs of seed-stage cybersecurity companies and encourages their growth. Startups in the DataTribe portfolio have been acquired by the likes of Microsoft, Synopsys, and ID Technologies.
“It can be tricky to turn deep academic research into successful products,” said John Funge, managing director of DataTribe. “That’s where active collaboration between the academic community, startups, and the investment community comes in.





“The CyLab Venture Network offers a resource to enable transformative ideas born at CMU to grow into successful startups and, in turn, maximize their positive impact. This aligns with DataTribe’s mission to co-build world-class startups centered around over-the-horizon technologies. We’re excited to be a part of this effort.”
The Venture Network will also provide significant value for current CMU faculty, research staff, and students by opening doors to internships and job opportunities, as well as direct exposure to corporate and startup partners. Getting a closer look at the ins and outs of founding a company will inspire the next generation of CMU entrepreneurs to join the Venture Network with their own companies.
“CMU embraces and celebrates creators, innovators, entrepreneurs, and game-changers,” said Lisanti. “The startup founders in the CyLab Venture Network embody this spirit, working towards a future where critical infrastructure resilience, enterprise security, and individual privacy thrive.”
Bridging the gap between academia and industry, the CyLab Partners Program aims to drive advancements in cybersecurity, enhance the preparedness of the cybersecurity workforce, and contribute to the development of effective and scalable security technologies.
CyLab’s partners include a wide variety of businesses and institutions, ranging from companies focused on developing advanced technologies to science and government agencies in the U.S. and international partner countries.
Through their participation in the CyLab Partners Program, organizations gain a comprehensive set of benefits that enhance their cybersecurity capabilities, strategic positioning, and overall business success. This collaborative approach not only helps partner institutions











stay ahead of emerging threats, but also ensures that the research conducted at CyLab has real-world applications and impact.
Our strategic focus initiatives include rethinking future enterprise security, laying the groundwork for secure distributed ledger technologies, and improving the cybersecurity of financial systems in emerging economies. By focusing on these initiatives, the CyLab Partners Program aims to address the most pressing cybersecurity challenges, foster innovation, and improve the overall security posture of both organizations and individuals.
If you’re interested in working together to develop a collaborative plan that benefits both your team and CyLab, please contact Michael Lisanti, Director of Partnerships, at partnerships@cylab.cmu.edu
















Security and privacy courses and degree programs are offered across several departments and institutes at Carnegie Mellon. CMU’s offerings include both undergraduate and graduate courses, as well as full-time and part-time programs.
UNDERGRADUATE LEVEL
• Minor in Information Security, Privacy, and Policy
> Engineering and Public Policy Department
> Software and Societal Systems Department
• Security and Privacy Concentration
> Electrical and Computer Engineering Department
> Computer Science Department
MASTER’S LEVEL
• Master of Science in Information Security (MSIS)
> Information Networking Institute
• Master of Science in Artificial Intelligence Engineering - Information Security
> Information Networking Institute
• Master of Science in Information Security Policy and Management
> Heinz College
• Master of Science in Information TechnologyInformation Security
> Information Networking Institute
• Master of Science in Privacy Engineering
> Software and Societal Systems Department
PH.D. LEVEL
While CMU does not offer any Ph.D. programs dedicated to security and privacy, there are several programs that enable students to focus on these areas of study, including: College of Engineering
Electrical and Computer Engineering, Engineering and Public Policy
School of Computer Science
Human-Computer Interaction, Language Technologies, Machine Learning, Software Engineering, Computer Science, Societal Computing
For a full list of security and privacy courses at Carnegie Mellon University, visit

The rapidly evolving landscape of technology-related security and privacy challenges requires an understanding of the business application and the ability to apply best practices to create solutions. From open enrollment to bespoke training programs, CyLab educators and researchers will empower you and your organization to solve critical challenges.
CyLab offers training in these topics and more:
• Artificial Intelligence (AI), Machine Learning, Security and Privacy
• Behavioral Cybersecurity
• Biometrics and AI
• Blockchain and Cybersecurity
• Cyber Workforce Development
• Dark Web, Security Economics, Crime, and Fraud
• Ethical Issues in AI and Cybersecurity
• Internet of Things (IoT) Connected Products Security and Privacy
• Privacy Engineering
• Social Cybersecurity and Social Network Analysis
• Software-Defined Security for Next Generation Networks
• Usable Privacy and Security
Interested in learning more about CyLab’s executive education offerings? Contact the CyLab partnerships team at partnerships@cylab.cmu.edu to learn more.


This year, Sarah Scheffler joined Carnegie Mellon’s Software and Societal Systems and Engineering and Public Policy Departments after earning her Ph.D. in Computer Science from Boston University and finishing her work as a postdoctoral research associate at MIT’s Internet Policy Research Initiative. Scheffler’s research interests lie in applied cryptography at the intersection of computer science, policy, and law.
Alessandro Acquisti
Trustee Professor of IT and Public Policy, Heinz College
Yuvraj Agarwal
Associate Professor, Software and Societal Systems Department (S3D)
Lujo Bauer
Professor, Electrical and Computer Engineering (ECE), S3D
Shawn Blanton
Associate Department Head for Research and Joseph F. and Nancy Keithley Professor, ECE
Fraser Brown
Assistant Professor, S3D
David Brumley Professor, ECE
Nicolas Christin
Department Head, S3D professor, Engineering and Public Policy (EPP), S3D
Lorrie Cranor
Director and Bosch Distinguished Professor in Security and Privacy Technologies, CyLab, FORE Systems University Professor, S3D, EPP
Sauvik Das
Assistant Professor, HumanComputer Interaction Institute
Giulia Fanti
Angel Jordan Associate Professor of Electrical and Computer Engineering, ECE
Mohamed Farag
Assistant Teaching Professor, Information Networking Institute (INI)
Matt Fredrikson
Associate Professor, CSD, S3D
Virgil Gligor Professor, ECE
Hana Habib
Assistant Teaching Professor, S3D, Associate Director, Privacy Engineering Program
Dena Haritos Tsamitis
Director and Barbara Lazarus Professor, INI, Founding Director, Education, Training and Outreach, CyLab
Hanan Hibshi
Assistant Teaching Professor, INI
Jason Hong
Professor, Human-Computer Interaction Institute
Aayush Jain
Assistant Professor, CSD
Limin Jia
Research Professor, ECE
Yorie Nakahira
Assistant Professor, ECE
Jema Ndibwile
Assistant Teaching Professor, CMU-Africa
Riccardo Paccagnella
Assistant Professor, S3D
Sam Pagliarini
Special Professor, ECE
Bryan Parno
Kavčić-Moura Professor, CSD, ECE
Corina Pasareanu
Principal Systems Scientist, CyLab
Joanne Peca
Associate Director, Associate Professor of the Practice, INI
Raj Rajkumar
George Westinghouse Professor, ECE
Norman Sadeh
Professor, S3D, Co-Director, Privacy Engineering Program
Marios Savvides
Bossa Nova Robotics Professor of Artificial Intelligence, ECE, Director, CyLab Biometrics Center
Sarah Scheffler
Assistant Professor, S3D, EPP
Vyas Sekar
Tan Family Professor, ECE
Elaine Shi
Professor, CSD, ECE
Asim Smailagic
Research Professor, ECE
Patrick Tague
Associate Teaching Professor, INI
Conrad Tucker
Director of CMU-Africa and Associate Dean for International Affairs-Africa, Professor, CMU-Africa, Mechanical Engineering
Riad Wahby
Assistant Professor, ECE
Steven Wu
Assistant Professor, S3D
Osman Yagan
Research Professor, ECE
Ding Zhao
Associate Professor, Mechanical Engineering
Wenting Zheng
Assistant Professor, CSD

Bernagozzi Student Life and Office Coordinator

Danyel Kusbit Administrative and Financial Coordinator

Beth Bucher Project Administrator

Michael Cunningham Communications Manager

Ashley Bon Business Manager

Abbey Rideout Administrative Assistant

Brittany Frost Senior Administrative Coordinator

Tina Yankovich Manager of Personnel and Student Services

Isabelle Glassmith Project Manager

Chief Morale Officer

Jason Griess Associate Director of Partnerships

Chief Information Paw-ficer

Kearns Special Projects Administrator


Michael Lisanti Director of Partnerships
Alessandro Acquisti
Inauguration of the Academic Year 2023-2024
Lezione Giorgio Fua’, Istituto Adriano Olivetti (ISTAO), Ancona (IT)
Lujo Bauer
From Pandas and Gibbons to Malware Detection: Attacking and Defending Real-World Uses of Machine Learning
Invited Talk, University of WisconsinMadison Distinguished Lecture, Madison, WI
From Pandas and Gibbons to Malware Detection: Attacking and Defending Real-World Uses of Machine Learning
Invited Talk, Distinguished Lecture, CISPA, Saarbruecken, Germany
David Brumley
Steering Clear of Danger: Decrypting the Realities of Remote Car Hacking
Invited Talk, RSA Conference 2024, San Francisco
Nicolas Christin
What I Learned from Spending a Dozen Years in the Dark Web
Keynote Talk, ACM International Conference on Web Search and Data Mining
It’s All About the Users: Analyzing Cryptocurrency Derivatives
Trading in the 2020s
Keynote Talk, International Symposium on Blockchain Advancements 2023, Singapore

Lorrie Cranor
From Password Requirements to IoT Cybersecurity Labels: Informing Public Policy With Research
Keynote Talk, ACM CCS 2023, Copenhagen
From Password Requirements to IoT Cybersecurity Labels: Informing Public Policy With Research
Invited Talk, Triangle Computer Science Distinguished Lecturer Series
The FCC’s Broadband Nutrition Labels
Panelist, Broadband Measurement Summit, Washington, D.C.
Giulia Fanti
Training Foundation Models from Private, Federated Client Data Invited Talk, Opportunities at the AI Research Frontier, The White House, Washington, D.C.
David Garlan
Humanizing Software Architecture Keynote Talk, 50th Annual Conference on Applications of Mathematics in Engineering and Economics, Sozopol, Bulgaria
Hanan Hibshi
Cybersecurity is Everywhere Keynote Talk, Global Conference for Educational Robotics (GCER), Augustine, FL
Rethinking What We Share Online Invited Talk, The Visiting American Professionals Program
Jason Hong
Helping Developers with Privacy Invited Talk, University of Wisconsin-Madison Distinguished Lecture, Madison, WI
Carlee Joe-Wong
Adversarial Robustness Unhardening: A New Type of Federated Learning Attack Invited Talk, Microsoft AI Community Outside Speaker Series
Making Homomorphic Encryption Feasible for Federated Learning Invited Talk, Adobe Research
Gauri Joshi
Heterogeneity-aware Algorithms for Federated Optimization
Keynote Talk, FedVision, Federated Learning workshop at CVPR
Swarun Kumar
From Wireless Sensing to Actuation Invited Talk, SIGCOMM Networking Channel
Pushing the Limits of mmWave Radar Invited Talk, NSF Workshop on Smart Sensing Systems
Pushing the Limits of Low-Power IoT Invited Talk, IIT Hyderabad
Lei Li
Empowering Responsible Use of Large Language Models
Invited Talk, JHU Center for Language and Speech Processing Seminar, Baltimore
Empowering Responsible Use of Large Language Models
Invited Talk, Nanyang Technological University, Singapore
Self-assisting and Cooperative Large Language Models
Invited Talk, Ohio State University
TDAI’s Foundations of Data Science and AI Speaker, Columbus, OH
Bryan Parno
Verus: Developing Verified and Performant Software
Invited Talk, Amazon Web Services
Formally Verifying the Rust Standard Library with Verus Invited Talk, The High Confidence Software and Systems Conference (HCSS), Annapolis, MD
Corina Pasareanu
Formal Verification and Run-time Monitoring for Learning-Enabled Autonomous Systems
Keynote Talk, NASA Formal Methods Symposium, Moffett Field, CA
Keynote Presentation
Keynote Talk, The 39th IEEE/ACM International Conference on Automated Software Engineering (ASE 2024), Sacramento, CA
Joanne Peca
U.S. Master’s Level Cybersecurity Programs: An Analysis of the Diversity of Content Paper Presentation, ACM SIGITE 2023: The 24th Annual Conference on Information Technology Education, Kennesaw State University, Marietta, GA
Samuel Perl
Advice for Graduates from the Field of Cybersecurity
Keynote Talk, The Lyell B. Clay Concert Theatre & Concert Hall inside of the WVU Canady Creative Arts Center, Morgantown, WV
Norman Sadeh
Privacy in the Age of AI and the Internet of Things
Invited Talk, Computer Science Seminar Series, UC Irvine
Privacy and (Generative) AI –Panelist, 5th IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications Atlanta, GA
Reflecting on 30 Years of AI Research in SCM
Keynote Talk, 2024 Supply Chain Analytics Institute Annual Conference, Rutgers
Nihar Shah
What can we do about NeurIPS Reviewer #2? Challenges, Solutions, Experiments and Open Problemsin Peer Review
Tutorial, Neural Information Processing Systems (NeurIPS) 2023, New Orleans
Mark Sherman
Should I Trust ChatGPT to Review My Program
Invited Talk, InfoSec World Conference, Orlando, FL
Using ChatGPT to Detect Vulnerabilities in Source Code
Invited Talk, INFORMS Annual Meeting, Phoenix, AZ
Carole J. Smith
Trustworthy By Design
Keynote Talk, ICSE 2024 - ACM/IEEE International Conference on Software Engineering, Lisbon
Ben Titzer
The WebAssembly Linux Interface Invited Talk, WebAssembly Workshop (WAW) at POPL 2024
Dena Haritos Tsamitis
Empowering women: The rise of female entrepreneurship
Moderator, IEEE Women in Engineering Forum USA East, Pittsburgh, PA
Is it me or my workplace? Change the culture, change the dynamic Keynote Talk, Navy Federal Women in Cybersecurity (WiCyS) Chapter Presentation
CyLab Partners Conference 20-Year Panel
Panelist, CyLab Security and Privacy Institute at Carnegie Mellon University, Pittsburgh, PA
Carol Woody
Establishing the Demand Signal for Good Software Assurance
Moderator, Software and Supply Chain Assurance Forum, sponsored by NIST, DoD, and GSA
Software and Cybersecurity
Keynote Talk, MBA Cyber Sprint, Mason Business School at William & Mary, Williamsburg, VA
Secure by Design as a Business Enabler
Panelist, SINETConnect Webinar


Lujo Bauer
Will serve as co-chair of USENIX Security ‘25
David Brumley
Received the 2023 USENIX Security Test of Time Award for ‘Remote Timing Attacks are Practical.’
Co-author: Dan Boneh
Lorrie Cranor, Lujo Bauer, and Andrea Gallardo
Received Best Paper Honorable Mention Award at the 2024 ACM CHI for ‘Interdisciplinary Approaches to Cybervulnerability Impact Assessment for Energy Critical Infrastructure’
Co-authors: Katya Le Blanc, Robert Erbes
Sauvik Das, Hao-Ping (Hank) Lee, Yu-Ju Yang, and Jodi Forlizzi
Received Best Paper Award at the 2024 ACM CHI for ‘Deepfakes, Phrenology, Surveillance, and More! A Taxonomy of AI Privacy Risks’
Co-authors: Thomas Serban von Davier
Giulia Fanti
Received the NSF Faculty Early Career Development (CAREER) Award
Served as co-chair of SIGMETRICS TPC
Elevated to rank of Angel Jordan Associate Professor of Electrical and Computer Engineering
David Garlan
Received Best Paper Award at the 17th European Conference on Software Architecture (ECSA) for ‘Supporting the Exploration of Quality Attribute Tradeoffs in Large Design Spaces’
Co-authors: Andres Diaz-Pace, Rebekka Wohlrab
Gihyuk Ko
Received Distinguished Paper Award at the 32nd USENIX Security Symposium for ‘BotScreen: Trust Everybody, but Cut the Aimbots Yourself’
Co-authors: Minyeop Choi, Sang Kil Cha
Swarun Kumar
Received the SIGMOBILE Rockstar Award 2024 at ACM MobiCom
Alexandra Nisenoff
Received Distinguished Paper Award at the 32nd USENIX Security Symposium for ‘A Two-Decade Retrospective Analysis of a University’s Vulnerability to Attacks Exploiting Reused Passwords’
Co-authors: Maximilian Golla, Miranda Wei, Juliette Hainline, Hayley Szymanek, Annika Braun, Annika Hildebrandt, Blair Christensen, David Langenberg, and Blase Ur
Rohan Padhye, Vasudev Vikram, Isabella Laybourn, and Ao Li
Received ACM SIGSOFT Distinguished Paper Award at the ISSTA 2023 Conference for ‘Guiding Greybox Fuzzing with Mutation Testing’
Co-authors: Nicole Nair, Kelton OBrien, Rafaello Sanna
Bryan Parno
Received an endowed chairKavčić-Moura Professor of ECE and CS
Corina Pasareanu
Named Association for Computing Machinery (ACM) Fellow
Samuel Perl
Served as guest editor for the ACM Journal DTRAP - Digital Threats Research and Practice, Special Edition on Cyber Incident Response
Guannan Qu
Received the NSF Faculty Early Career Development (CAREER) Award
Norman Sadeh
Developed and offered the first course at CMU on AI Governance
Mahmood Sharif
Received the Intel Rising Star Faculty Award
Elaine Shi
Named Association for Computing Machinery (ACM) Fellow
Mansi Sood
Named Schmidt Science Fellow
Akshitha Sriraman
Received the NSF Faculty Early Career Development (CAREER) Award
Received the Intel Rising Star Faculty Award
Joshua Sunshine
Received the NSF Faculty Early Career Development (CAREER) Award
Dena Haritos Tsamitis
Recognized as a Smart 50 Honoree by Smart Business Pittsburgh Magazine
Jingxian Wang
Received the SIGMOBILE Doctoral Dissertation Award at ACM MobiCom for ‘Blind Wireless Beamforming to Power, Heat, and Move’
Steven Wu
Received the NSF Faculty Early Career Development (CAREER) Award
Jonathan Aldrich, Yi Chen, Cristian M. Borcea, and Cristobal Cheyre
Continuous Reasoning with Gradual Verification
Funder: U.S. Department of Defense
Nicolas Christin
Google 2023 Security and Privacy Award
Funder: Google
Lorrie Cranor and Yuvraj Agarwal
IoT Security and Privacy Label Research
Funder: Craig Newmark Philanthropies
Giulia Fanti
CAREER: Theory and Practice of Privacy-Utility Tradeoffs in Enterprise Data Sharing
Funder: National Science Foundation (NSF)
Matt Fredrikson
Google 2023 Security and Privacy Award
Funder: Google
David Garlan
Resilient Systems through Adaptive Security Architecture
Funder: National Security Agency (NSA)
Towards Trustworthy
Autonomous Cyber Defense for Dynamic Intrusion Response
Funder: NSA
Hanan Hibshi
2024 GenCyber (for picoCTF Teachers Program)
Funder: NSA
Increasing Student Diversity in Cybersecurity Educations (picoCTF)
Funder: Cisco Systems, Inc.
Jason Hong, Motahhare Eslami, and Ken Holstein
Engaging End Users in Surfacing Harmful Algorithmic Behaviors in Large-scale AI Models
Funder: Notre Dame-IBM Technology Ethics Lab
Microsoft Research AI & Society Fellow
Funder: Microsoft
Swarun Kumar and Anthony Rowe
High-Resolution Imaging from a Compact mmWave Radar
Funder: Office of Naval Research (ONR)
Designing Ultra-Low Power Sensors for Distributed RF Surveillance
Funder: ONR
Lei Li
Apple Research Gift
Funder: Apple
Real-time robust simultaneous interpretation with few samples
Funder: Amazon Research Award
Brian Parno
Simplifying End-to-End Verification of High-Performance Distributed Systems
Funder: NSF
Industrial Scale Proof Engineering for Critical Trustworthy Applications
Funder: Defense Advanced Research Projects Agency (DARPA)
Corina Pasareanu
Proving the Absence of Timing Side Channels in Cryptographic Applications
Funder: Amazon
Guannan Qu
CAREER: Structure Exploiting MultiAgent Reinforcement Learning for Large Scale Networked Systems: Locality and Beyond
Funder: NSF
Norman Sadeh, Lorrie Cranor and Hana Habib
UsersFirst: Privacy and AI Threat
Modeling: A User-Focused Framework for Notice and Choice
Funder: PwC Digital Transformation and Innovation Center
Norman Sadeh
Operationalizing AI Threat Modeling and Mitigation
Funder: Block Center for Responsible AI
Mark Sherman
Improving API Security for the DoDs
Funder: Office of the Under Secretary of Defense for Research and Engineering (OUSD[R&E])
Dena Haritos Tsamitis
DoD CySP 2023-2024
Funder: NSA
DEFENSEWERX-IWX Cyber Security Tech Talks
Funder: DEFENSEWERX



Jay Bosamiya, Computer Science
Advisor: Bryan Parno
Thesis: ‘A Principled Approach Towards Unapologetic Security’
May 2024
Ángel Alexander Cabrera, Human-Computer Interaction Institute
Jason Hong and Adam Perer
Thesis: ‘Behavior-Driven AI Development’
April 2024
Yae Jee Cho, Electrical and Computer Engineering
Advisor: Gauri Joshi
Thesis: ‘Faster, Incentivized, and Efficient Federated Learning: Theory and Applications’
May 2024
Jenna Wise DiVincenzo, Software and Societal Systems
Advisors: Jonathan Aldrich and Joshua Sunshine
Thesis: ‘Gradual Verification of Recursive Heap Data Structures’
December 2023
Thomas J. Glazier, Software and Societal Systems
Advisor: David Garlan
Thesis: ‘Meta-Management of Collections of Autonomic Systems’
December 2023
Steven Jecmen, Computer Science
Advisors: Nihar B. Shah and Fei Fang
Thesis: ‘Making Peer Review Robust to Undesirable Behavior’
February 2024
Daisuke Kawai, Engineering and Public Policy
Advisor: Nicolas Christin
Thesis: ‘An Empirical Analysis of the Cryptocurrency Ecosystem toward Better Regulation and Supervision’
July 2024
Abhiram Kothapalli, Computer Science
Advisor: Bryan Parno
Thesis: ‘A Theory of Composition for Proofs of Knowledge’
May 2024
Kaiyuan Li, Electrical and Computer Engineering
Advisor: Limin Jia
Thesis: ‘Pangine Disassembler: Implementing and Evaluating Non-sequential Code Analysis with Non-chronological Backtracking’ February 2024
Keane Lucas, Electrical and Computer Engineering
Advisor: Lujo Bauer
Thesis: ‘Attacking, Defending, and Evaluating Machine Learning-based Raw-Binary Malware Detectors’ June 2024
Jielin Qiu, Computer Science
Advisors: Lei Li and Christos Faloutsos
Thesis: ‘On the Alignment, Robustness, and Generalizability of Multimodal Learning’ April 2024
Yoshiki Takashima, Electrical and Computer Engineering
Advisors: Limin Jia and Corina Pasareanu
Thesis: ‘Testing and Verifying Rust’s Next Mile’ March 2024
Yuhang Yao, Electrical and Computer Engineering
Advisors: Carlee Joe-Wong
Thesis: ‘Efficient Federated Graph Learning: Formulation, Algorithms and Applications’ May 2024

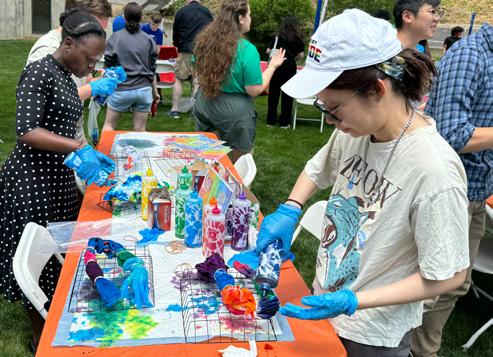
CyLab faculty, staff, and students beat the summer heat while making Tie-Dyed shirts featuring the CyLab 20th Anniversary logo.
Carnegie Mellon University students Rohan Viswanathan of CMU’s Information Networking Institute and Nisaruj Rattanaaram of the Heinz College of Information Systems and Public Policy successfully completed the 2024 National Security Agency Codebreaker Challenge, helping Carnegie Mellon finish seventh overall in the competition. The NSA Codebreaker Challenge provides students with a hands-on opportunity to develop their reverse-engineering / low-level code analysis skills while working on a realistic problem set centered around the NSA’s mission.

During CMU Carnival weekend, CyLab community members participated in the 2024 Random Distance Run, a fun CMU School of Computer Science tradition.
The Random Distance Run is a footrace whose length is determined by a randomized procedure. The length of the race is the sum of two dice rolls, times 400 meters (the length of the CMU track). Thus, the expectation of the race length is seven laps (2.8 km or 1.74 miles), while the maximum possible race length is 12 laps (4.8 km or 2.98 miles).
One giant, fuzzy die is rolled just before the race begins. As the leading runner is about to finish the number of laps rolled, a second die is rolled, and that many more laps must be run. All finishers run the same distance, and this year’s run was nine laps (3.6 km or 2.24 miles).



10.18.2023 On the tools that social media companies use to moderate false or extremist content:
“Unless you do content moderation consistently, for the same story across all the major platforms, you’re just playing Whac-a-Mole.”
Kathleen M. Carley, Professor of Computation, Organizations, and Society; Software and Societal Systems Department


11.2.2023 On the manipulability of new AI chatbots:
“One approach is to limit the instructions these models can accept, as well as the data they can access.
Another is to try to teach the models to recognize malicious prompts or avoid certain tasks.”
Matt Fredrikson, Associate Professor, Computer Science Department, Software and Societal Systems Department

9.11.2023 On how cyberattacks could affect smart cars:

“If the attacker finds a weakness, they can compromise a large number of connected cars simultaneously without much cost or effort.”
Vyas Sekar, Tan Family Professor, Electrical and Computer Engineering

10.31.2023 On Biden’s plan for ethical hacking for AI safety:

“Companies and policymakers need to shift their attention to the algorithms and data sources at the heart of the models, rather than the outputs.”
David Brumley, Professor, Electrical and Computer Engineering

1.16.2024 On the reliability of perception systems in autonomous vehicles:
“Their method of providing end-to-end safety guarantees is very important.”

Corina Pasareanu, Principal Systems Scientist, CyLab
10.15.2023 On why the U.S. government has $5 billion in bitcoin:
“The government moves generally very slowly to dispose of those assets because they’ve got to do a ton of due diligence, the cases are often complicated and there’s a lot of red tape.”

Nicolas Christin, Professor, Engineering and Public Policy, Software and Societal Systems Department; CoDirector of Carnegie Mellon University’s Secure Blockchain Initiative

3.12.2024 On the FCC’s Cyber Trust Mark program and consumer IoT labeling process:
“By having these labels, the hope is that it will raise the bar because companies are going be upfront about this.”

Lorrie Cranor, Director and Bosch Distinguished Professor in Security and Privacy Technologies, CyLab
FORE Systems Professor, Engineering and Public Policy, Software and Societal Systems Departments

3.19.2024 On the benefits and risks of open- versus closed-source software:
“If you open source, then you have an entire community of practitioners who poke holes and gradually over time build up patches and defenses.”

Sauvik Das, Assistant professor, Human-Computer Interaction Institute

AUGUST 23
Five unique cybersecurity challenges in Africa
Assane Gueye, associate teaching professor and co-director of CyLabAfrica, has identified five cybersecurity challenges that Africa faces on the path to a digital future.
SEPTEMBER 13
Researchers develop adversarial training methods to improve machine learning-based malware detection software
Professor Lujo Bauer and a team of researchers investigate the effectiveness of using adversarial training methods to create malware detection models that are more robust to some of the state-of-the-art attacks.
SEPTEMBER 26
Newly discovered side-channel attack side steps current defense mechanisms
Software and Societal Systems assistant professor Riccardo Paccagnella and fellow researchers uncovered a new type of side-channel attack, dubbed GPU.zip, which exploits software-transparent uses of compression.
OCTOBER 10
CMU’s Synergy Lab presents multiple papers on ubiquitous sensing at UbiComp
Researchers from Carnegie Mellon’s Systems, Networking, and Energy Efficiency (Synergy) Lab presented several multi-year studies on their work around ubiquitous sensing at the 2023 ACM International Joint Conference on Pervasive and Ubiquitous Computing (UbiComp) in Cancún, Mexico October 8-12.
NOVEMBER 9
CyLab receives a $250,000 gift from Craig Newmark Philanthropies to support research on IoT security and privacy labels
Craig Newmark Philanthropies announced a $250,000 gift to support CyLab’s research on privacy and security labels for IoT devices. The project seeks to standardize a usable security and privacy label for smart devices to help consumers make informed choices about Internet of Things device purchases, and to encourage manufacturers to disclose their privacy and security practices.
NOVEMBER 20

Niraj Tolia receives 2023 Parallel Data Lab Distinguished Alumni Award
Carnegie Mellon University’s Parallel Data Lab (PDL) recognized Niraj Tolia (BS ‘02, MS ‘03, Ph.D. ‘07), CEO and co-founder of Alcion, as the recipient of its 2023 Distinguished Alumni Award.
DECEMBER 21
Unplugging doubt
Smart speakers and other Internet of Things (IoT) devices often have always-on microphones to enable voicebased interaction. In a recent paper, CyLab faculty member Sauvik Das and a team of researchers propose a new concept of “intentionally powered” microphones that can only be powered using the energy harvested from intentional user interactions.
For more CyLab news, visit cylab@cmu.edu/news
MARCH 11
CMU faculty selected for UN-led working group on DPI safeguards Assane Gueye and Giulia Fanti were selected by the United Nations Office of the Secretary-General Envoy on Technology to be part of a working group for the DPI Safeguards initiative.
APRIL 15
Releasing private population analytics: How should we do it?
Population analytics is a concept that has important downstream applications, like determining funding allocations, but these analytics can leak sensitive data about individuals. A group of researchers led by Aadyaa Maddi (MS Privacy Engineering ‘23) tested the TopDown algorithm and synthetic data release to see which did a better job of responding to familiar queries (used to train the algorithm) and unfamiliar queries (new ones) with results that were as accurate as possible while adhering to privacy guarantees.
JUNE 5
picoCTF-Africa inspires participants to learn cybersecurity
As Africa grows into a digital future, it is vital that digital systems and infrastructure are kept safe from malicious attacks. Through picoCTF-Africa, the cybersecurity field is being introduced to young participants in the competition, who are encouraged to consider careers in the field to help address the skills gap that currently exists on the continent within the security and privacy sectors.


Stay Connected with CyLab
cylab.cmu.edu
linkedin.com/showcase/carnegiemelloncylab
@CyLab
https://www.facebook.com/carnegiemelloncylab/
bit.ly/cylab-newsletter
