Overcoming the Chaos, Concern and Fear of Ransomware with Seceon aiXDR

Demand for ransom in exchange for something valuable, captured forcefully, is an age old vice that has found its parallel in the digital world several years ago. Cyber criminals have resorted to extortion, preying on individuals and organizations (enterprises, businesses, institutions) by encrypting files on personal computers, workstations, tablets and mobile devices. In order to salvage the situation, helpless user would be coerced to
pay up a ransom, in return for the recovery key. While the ransom could vary from a couple of hundred dollars to thousands, depending on perceived value of the data and asset, there is also a high probability that parts of the data (personal, confidential or business oriented) may be sold on the dark web, if the demand remains unfulfilled by the stipulated deadline.
Welcome to the dark world of old and new ransomware – from WannaCry, Ryuk, Petya, and Maze to Darkside, REvil and Epsilon Red. While attack techniques and tactics could vary, perpetrators are mostly elusive, as with any complicated crime scenario, and cyber sleuths have negligible success at reversing the situation.
That leaves us with only a few options –
a.) Self-Awareness to avoid any trap
b.) Software based early detection
c.) Rapid response to minimize damage or eliminate threat.
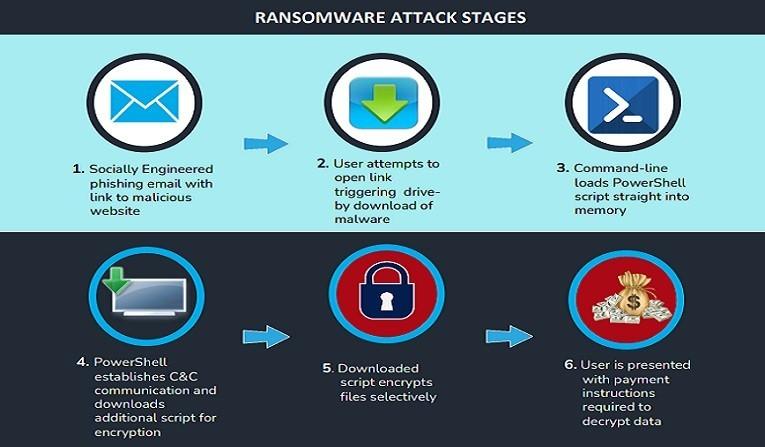
Almost all ransomware attacks originate from an email phishing campaign or drive-by download (accessing a blacklisted site or hijacked site). Seceon aiXDR quickly swings into action, correlating logs from email server with endpoint activities, identifying access to blacklisted site (with gathered Threat Intelligence) and applying behavioral patterns to find traces of unusual or suspicious process spawned on the endpoint. The picture below depicts attack stages that are commonly seen.
Let us consider the attack scenario that unfolded at Colonial Pipeline, with business servers being critically impacted by Darkside Ransomware. Does aiXDR, the XDR Solution from Seceon, stand up to the challenges posed by tactical maneuvers from Darkside?

Here is what we’ve learned about Darkside’s modus operandi…
1.Scours information from the victim’s computer – OS type, version, username, hostname, disks, language etc. Any computer with Easter European or Russian language was left unaffected.
2.Selectively chooses which files to encrypt, based on directories, file names and extensions. This is intended to save time and keep the system in working condition so that contact information related to ransom payment can be conveyed.
Seceon aiXDR monitors File Access, particularly recursive access to directories is seen as suspicious activity – Threat Indicator is generated and no. of instances (recursive activity) are counted. Also, Seceon aiXDR with FIM capabilities come in handy.
3. For anonymity, attacker instructs designated website (for payment arrangement) can be accessed using TOR browser.
Using netflow/J-flow/IPFix data, IP Address of destination can be extracted despite use of TOR browser
4. Critical strings are encrypted using XOR Encryption to avoid detection. Also, main configuration is encrypted using base64 encoding.
Seceon aiXDR can decrypt XOR Encrypted strings to identify type of activity. Also, any process associated with base64 encoding or any other encryption/decryption (e.g OpenSSL) method is identified by aiXDR and flagged as a Threat Indicator.
5. Dynamically calls WinAPI by hashed names and encrypted names instead of referring to the import table of APIs, to avoid detection and revelation of purpose.
Any WinAPI call results in a process with an unknown hash that gets picked up by aiXDR’s Machine Learning algorithm.
6. Pulls up a list of Shadow Copy backups and gets rid of them, so the user can’t restore files.
It is quite a common behavior for ransomware to hijack the windows program vssadmin.exe that manipulates volume shadow copies of a file system. Seceon’s aiXDR instantly catches this attempt –generally as a combination of command-line “vssadmin delete shadows” and WMI command “wmic shadowcopy delete”. This malicious behavior and threat indicator is considered very risky and the alert is elevated to severity level “Major” or “Critical”. Note, vssadmin requires “Administrator” privilege to execute and is
commonly used by other ransomwares like Ryuk and WannaCry to wreak havoc. Hence, privilege escalation by the malware is also detected by aiXDR as a serious Threat Indicator.
7. Tries to disable various backup solutions.
Seceon aiXDR detects any attempt to disable a service on the host/endpoint and creates a Threat Indicator.
8. Uses both symmetric and asymmetric key encryption, so that an intercepted public key cannot be solely used for restoring access to data.
As noted earlier, any process associated with encryption or decryption is promptly discerned by aiXDR and tagged as potentially suspicious, subject to other evidences.
In summary, an advanced XDR solution like Seceon aiXDR relies on comprehensive set of information streaming in from network, events, endpoints (EDR), threat intelligence and vulnerability scan to assign appropriate threat indicators. The AI engine correlates these indicators and applies behavioral aspects to conclude “Ransomware” attack in progress, while immediately escalating alert severity to “critical/major” with a high degree of confidence. In fact, aiXDR goes a step further by empowering the Security Analyst to take rapid action through auto-remediation or semi-automated remediation built into the solution. Affected endpoint/host can be isolated from the network or specific processes can be eliminated promptly to block further damage.
To learn more about Seceon aiXDR, check out these resources:
• End-to-end Cybersecurity with aiXDR
•Seceon aiXDR
tanu (Shaan) Bagchi ctor, Pre-Sales Solutions eon Inc. s:// www.linkedin.com/in/sha anbagchi/ Santanu (Shaan) Bagchi has 20+ years of experience in Software Industry, leading through Product Management, Pre-Sales/Solutions Architecture, Consulting and Product Marketing roles for Product Vendors, MSSPs and System Integrators in North America. As someone who has expertise in multiple tracks of Cyber Security – Advanced SIEM, Data Loss Prevention, Endpoint Security, Vulnerability Management, Threat Intelligence and Identity and Access Management – he brings versatile perspective to product innovation and customer centric solutions. Before joining Seceon, he worked as Practice Director (Cybersecurity and Risk Services) for Wipro. Previously, he held Product Management positions at Secureworks (MSSP), Novell (Virtualization and IaaS), Digital Guardian (DLP) and Hitachi Data Systems (Cloud Storage-aaS). Shaan received MBA degree from Babson College (Wellesley, MA) and Bachelor of Engineering from IIEST (formerly Bengal Engineering College, India)

