Senior Leaders Cyber Summit

CyberSecurity Woman of the World Gala

DDoS attacks on the increase
Protecting Microsoft 365 data

CyberSecurity Women Nominees
The elephant in the room
AICS 2023 Conference and Exhibition, Bahrain








Contents Dear Reader, Welcome to Cyber News Global, this collaborative publication has been brought together by the UK’s leading Energy Sector Publication OGV Energy and UK Cyber Security Specialists, OSP Group Limited. A combined wealth of experience, networks and specialists will ensure that CNG becomes a leading platform for the Cyber Sector in the UK, USA and Middle East. Thomas McCarthy CEO, Cyber News Global Kenny Dooley Director, OGV Energy If you have a contribution of relevant industry news please email media@cybernewsglobal.com Have an inspiring day and read on! 5 10 12 14 16 19 20 24 26 28 Senior Ladies Cyber Summit 5 things every company should consider DDoS attacks on the increase The battle for the digital supply chain Protecting Microsoft 365 data Cybersecurity Woman of the World Cybersecurity Women Nominees Safeguarding The Digital Future The elephant in the room Arab International Cyber Summit 2023 6 19 26 14 Cybersecirity Woman of the World Bahrain to Host the Second AICS Exhibition The Battle for the digital supply chain The Elephant in the Room Official Partner 3








CYBER SECURITY CONSULTANCY FOR INDUSTRIAL AUTOMATION AND CONTROL SYSTEMS IACS Consulting LTD, Balmoral Business Park Building 1, Aberdeen AB12 3JG info@iacsconsulting.com 01224 460212 UNDERSTANDING AND MITIGATING YOUR OPERATIONAL TECHNOLOGY SECURITY RISKS www iacsconsulting com ASSESSMENT | COMPLIANCE | SUSTAINMENT
Disclaimer: The views and opinions published within editorials and advertisements in Cyber News Global are not those of our editor or company. Whilst we have made every effort to ensure the legitimacy of the content, Cyber News Global cannot accept any responsibility for errors and mistakes.



Supply Chain Security








‘the weakest link in the supply chain’



Supply Chain Security Course – This course is aimed at staff who deal with third parties within their organisation’s supply chain. With this training you will improve awareness of the supply chain cyber risk and help to implement good practice.




This course includes:
• Understand the cyber risks to your supply chain


• Understand how to establish and maintain control of your supply chain
• How to check your arrangements for confidence in your supply chain
• Recognise how to encourage continuous improvement and build trust with suppliers.
This course makes recommendations based on NCSC best practice, implementing these recommendations will take time, but the investment will be worthwhile. It will improve your overall resilience, reduce the number of business disruptions you suffer and the damage they cause.
It will also help you demonstrate compliance with GDPR, the new Data Protection Act. Ultimately, these measures may help you win new contracts, because of the trust you have sought in the security of your supply chain.

CONTRIBUTORS OUR PARTNERS Editorial editor@cybernewsglobal.com Advertising marketing@cybernewsglobal.com Design office@ogvenergy.co.uk Events & Partnerships ceo@cybernewsglobal.com VIEW our media pack at www.cybernewsglobal.com or scan de QR code ADVERTISE WITH US
SCAN QR CODE ospcyberacademy.com 7
S E N I O R L E A D E R S
Date & Time: 31/08/23 09:00 - 17:00



Location: Robert Gordon University

Sir Ian Wood Building

Purchase your ticket here
Discussions Include:
Blueprints of Tomorrow - Empowerment & Opportunities

Should marketing within the Cyber Sector be Regulated


Demistifying Cyber Insurance & Quanitifying Cyber Risk





How to prioritise your Organisations Exposure Management

Risks associated with Emerging Technology

Educating the Board in their role in Cyber Women in Cyber Leading the Way
How do we test our OT Security
The Global Cyber Landscape - How do we Survive the Threats Public Authority Cyber Debate


Understanding the Threat Social Media brings to the Workplace
Thanks to our Sponsors & Partners

When the World Goes Wrong

M M I T A B E R D E E N A N E V E N T B Y I N P A R T N E R S H I P W I T H
C Y B E R S U







































 Carmen Marsh President & CEO United Cybersecurity Alliance
Dr Andrew Larner Chief Executive iESE Ltd Chief Executive CCoE
Sandip Patel KC FCIArb Legal Advisor OSP Cyber Academy
Simon Moore Senior Management Consultant CRMG
Euan Davidson Group Head of It KCA Deutag
Brad Brooks Chief Executive Officer Censys
Keith Chappell Chief Technical Authority CyberPrism
Cynthia Kaiser Deputy Assistant Director FBI Cyber Division
Karen Meechan CEO ScotlandIS
Sally Walker former Director of Cyber UK Ministry of Defence
Louise Beattie Chief Operating Officer i-confidential
Sophie De Ferranti Senior Managing Director Teneo
Joanna Goddard Partner BRIM
Saltanat Mashirova Advanced Cyber Security Architect Honeywell
Heide Young Manager Cyber Strategy & Engagement TONOMUS NEOM
Major General (Rtd) Martin Smith CB MBE DL MD CyberPrism
Rob Simpson Director of Business Services Aberdeenshire Council
Keith McDevitt Cyber Incident & Vulnerability Lead Scottish Cyber Co-ordination Centre
Malcolm Norman Group CISO Wood
Todd Wade CISO Advisor CRMG
Alan Greig CEO BRIM
Dougie Grant former Senior Coordinator NCSC MD Nihon Cyber
David Charters former MD Deutsche Bank former MI6 Intelligence Officer
Rois Ni Thuama PhD Tech100 Women Winner EU Cyber Woman of the Year
Maggie Titmuss MBE Advisor National Cyber Resilience Board
Emma Philpott MBE CEO IASME Consortium Ltd
Laura Irvine Head of Regulatory Law Davidson Chalmers Stewart LLP
Irene Coyle Chief Operating Officer OSP Cyber Academy
Amanda Finch CEO CIISec
Wanda Mizell Assistant Legal Attache FBI London
Nicholas Fyfe MA PhD FAcSS FRSA Vice Principal of Research & Community Engagement RGU
Conrad Trickett Chief Superintendent Police Scotland
Alex Woerndle GAICD CISO / Non-Executive Director
Cade Wells Business Development Director Censis
David Tutt Leader Eastbourne Borough Council
Chris McDermott Lecturer Human Centred Security RGU
Carmen Marsh President & CEO United Cybersecurity Alliance
Dr Andrew Larner Chief Executive iESE Ltd Chief Executive CCoE
Sandip Patel KC FCIArb Legal Advisor OSP Cyber Academy
Simon Moore Senior Management Consultant CRMG
Euan Davidson Group Head of It KCA Deutag
Brad Brooks Chief Executive Officer Censys
Keith Chappell Chief Technical Authority CyberPrism
Cynthia Kaiser Deputy Assistant Director FBI Cyber Division
Karen Meechan CEO ScotlandIS
Sally Walker former Director of Cyber UK Ministry of Defence
Louise Beattie Chief Operating Officer i-confidential
Sophie De Ferranti Senior Managing Director Teneo
Joanna Goddard Partner BRIM
Saltanat Mashirova Advanced Cyber Security Architect Honeywell
Heide Young Manager Cyber Strategy & Engagement TONOMUS NEOM
Major General (Rtd) Martin Smith CB MBE DL MD CyberPrism
Rob Simpson Director of Business Services Aberdeenshire Council
Keith McDevitt Cyber Incident & Vulnerability Lead Scottish Cyber Co-ordination Centre
Malcolm Norman Group CISO Wood
Todd Wade CISO Advisor CRMG
Alan Greig CEO BRIM
Dougie Grant former Senior Coordinator NCSC MD Nihon Cyber
David Charters former MD Deutsche Bank former MI6 Intelligence Officer
Rois Ni Thuama PhD Tech100 Women Winner EU Cyber Woman of the Year
Maggie Titmuss MBE Advisor National Cyber Resilience Board
Emma Philpott MBE CEO IASME Consortium Ltd
Laura Irvine Head of Regulatory Law Davidson Chalmers Stewart LLP
Irene Coyle Chief Operating Officer OSP Cyber Academy
Amanda Finch CEO CIISec
Wanda Mizell Assistant Legal Attache FBI London
Nicholas Fyfe MA PhD FAcSS FRSA Vice Principal of Research & Community Engagement RGU
Conrad Trickett Chief Superintendent Police Scotland
Alex Woerndle GAICD CISO / Non-Executive Director
Cade Wells Business Development Director Censis
David Tutt Leader Eastbourne Borough Council
Chris McDermott Lecturer Human Centred Security RGU
KEYNOTE SPEAKER
Malcolm Warr Chair CNI Scotland
KEYNOTE SPEAKER
SUMMIT CHAIR
5 things every company should consider when it comes to cyber security.
In today's digital age, cybersecurity has become increasingly important as businesses and organizations continue to rely heavily on technology and the internet to carry out their daily operations. While every organization is different, there are certain practices that every organization would benefit from implementing. In this short article, I included FIVE of the most important cybersecurity practices that every business and individual should implement to protect themselves from cyber threats:
1. Assess the risks:
Regular risk assessments can help identify potential vulnerabilities and threats to a company's systems and data. Companies should conduct risk assessments regularly and address any identified issues promptly.
2. Create a Cybersecurity Plan and Policy:
One of the essential things a company can do is to create a cybersecurity plan. A cybersecurity plan outlines the steps the company will take to protect its systems and data from cyber threats. The plan should include policies and procedures for system backups, data encryption, access control, and incident response.
The approved policy will ensure everyone in the organization is committed to maintaining the security of the organization and its assets.
3. It’s not about the technology, it’s about the people:
Your employees can either be your strongest or your weakest link when it comes to cyber security. In a world where 90% of all data breaches involve the human factor, it is vital educate employees on cybersecurity risks and best practices; this education is critical in protecting a company's data and systems. Regular training can help employees identify potential threats, avoid phishing scams, and keep sensitive data secure.
Awareness training is not a “one off” event. It should be a formulated ongoing process that will enable all employees to understand cyber risks and to identify them.
4. Expect the unexpected – create an Incident Response plan:
Even with the best cybersecurity practices in place, cyber-attacks can still happen. Companies should have an incident response plan in place to respond quickly and efficiently to any potential cyber-attack. The plan should outline the steps to take in the event of a data breach or cyber-attack and include procedures for notifying customers and authorities, negotiating with the attackers, and steps to recover lost data.
5. Implement Security best practices:
Technology can help reduce the risks of a cyber incident, here are a few crucial practices that every organization should implement to both minimize their chances of experiencing a cyber incident and reduce the impact of such an attack.

a. Implement a strong password policy
Although this changes as technology advances, a good password policy always includes the same principles:
• Use a long and complex password
• Do not use the same password in multiple services
• Change your passwords in a regular basis
These principles will reduce the chance of password guessing, and even if a single password is somehow exposed (by social engineering or by breaching a specific provider), the single password is not the “master key” to all assets in the Kingdome.
b. Add Multi-factor Authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security to accounts by requiring additional verification, such as a code sentas a text message or generated by an authentication app. It is advised to add MFA to all important accounts, including – social media accounts, financial accounts, email accounts etc.

c. Stay on top – update your assets
Hackers often target vulnerabilities in software and operating systems to gain access to a company's systems. Regular software updates and patches help address these vulnerabilities and improve overall system security.
d. Implement a “need to know” privilege policy
Not all employees need access to sensitive data, and restricting access to sensitive information is crucial. Implementing access controls, including permissions and user groups, can help prevent data breaches and leakage and limit the potential impact of a cyber-attack.
e. Be prepared - Backup your data
Regular data backups are crucial in case of a cyber-attack or data loss. Companies should ensure that they regularly back up their data and test their backup procedures to ensure they work as intended.
In conclusion, cybersecurity should be a top priority for every company in today's digital age. Implementing the items outlined above can help protect a company's systems and data from potential cyber threats, including hacking, data breaches, and cyber-attacks. By prioritizing cybersecurity, companies can protect their reputation, customers, and overall business operations.
5 things to consider... cybernewsglobal.com 10

The total number of DDoS attacks in 2022
increased by 73% worldwide
Media, banks, and payment systems became most affected segments
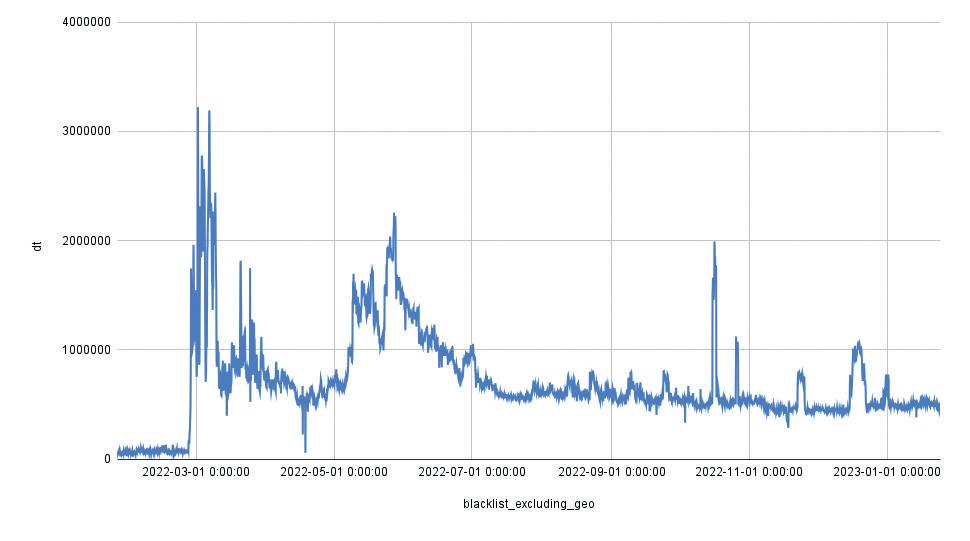
The year of 2022 was remarkable in terms of significant rise in the number of Distributed Denial of Service (DDoS) attacks and their intensity worldwide. The duration of DDoS attacks rose tenfold in 2022 compared to 2021, demonstrating increasing capabilities from the attackers in terms of their hardware.
Number of IP addresses involved in malicious activity in 2022


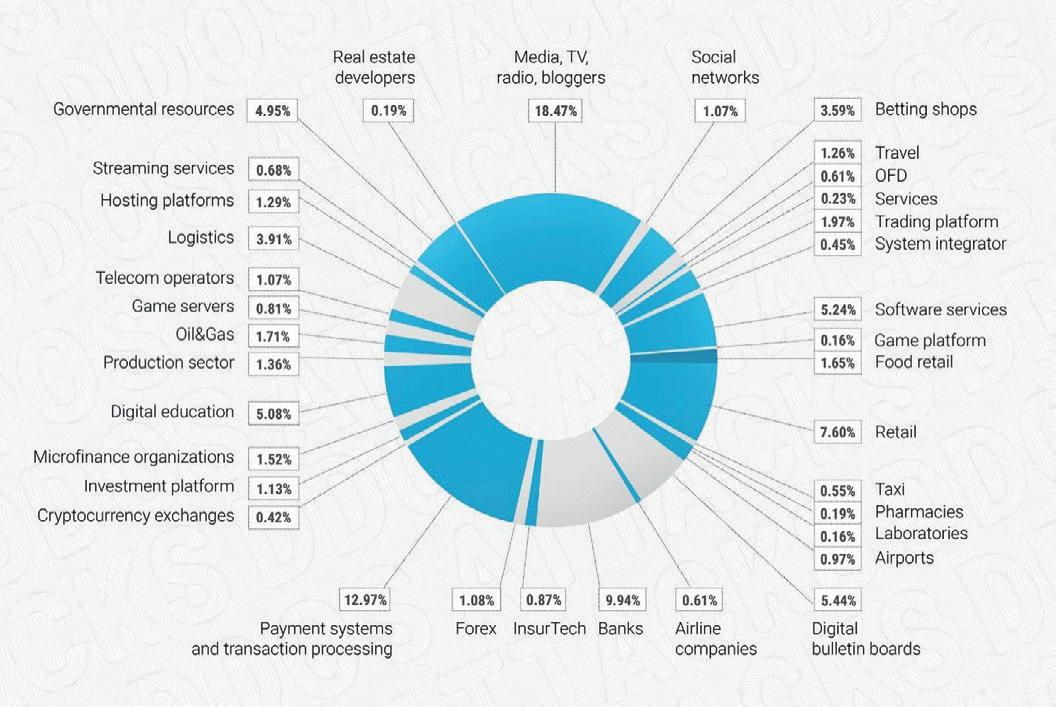
According to our recent survey, the total number of attacks in 2022 increased by 73.09% year-on-year. Cybercriminals mainly focused on media (18.5%), banks (9.9%), and payment systems (13%) with the latter two being the most profitable sectors, in terms of arranging cyberattacks.

Number of DDoS attacks by industry in 2022
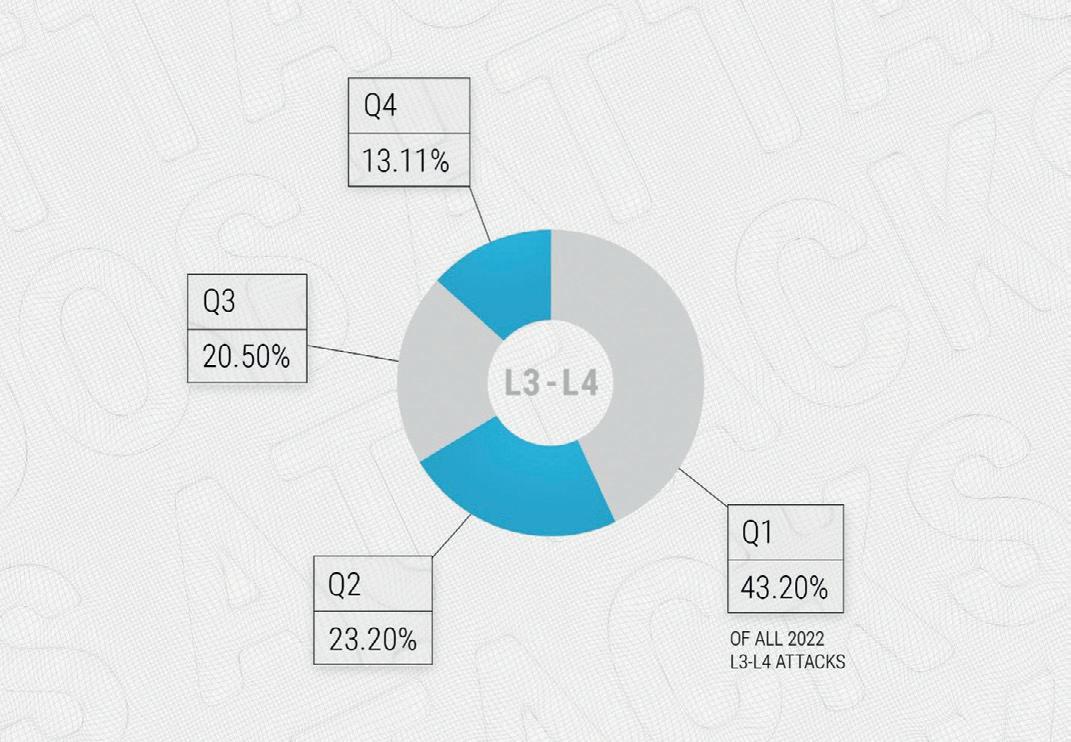
The largest share of attacks occurred in the first quarter of 2022 which was 43.2%, and it then began to decline in the second and third quarters to 23.3% and 20.5%, respectively. The fourth quarter observed just 13.11% of the annual number of attacks.
Quarterly distribution of DDoS attacks in 2022
The duration of DDoS attacks increased tenfold YoY. While in the first quarter of 2021, the maximum duration was 10 hours, in the same period of 2022, it was 10.5 days. In addition to the rise in intensity, starting from the fourth quarter of 2022, there was an increase in the complexity of attacks.
At the beginning of 2022, most attacks were simple. It wasn't until Q4 that we began to see a surge in their complexity. At a certain point, basic attacks were no longer effective: the industry had learned how to deal with them, and cybercriminals started to escalate the difficulty in order to get results.
cybernewsglobal.com
While attackers previously sought to optimize botnet usage time, they now have the resources to continue their attacks for weeks. The quantitative peak is over – unpretentious mass cyberattacks, which many web resources quickly and successfully «knocked down», have worked their way through.
Now, we expect a new stage in the competition between the armor and the projectile. Instead of mass, the attackers are tasked with achieving efficiency. The sophistication of attacks will grow, and methods of neutralizing them, which were effective yesterday, will most likely not work tomorrow.
In terms of the Internet threats, the top three will not dramatically change this year. DDoS attacks, phishing and hacking take up positions in the ranking of the most common threats on the Internet year by year, just exchanging their positions once in a while. Therefore, in 2023, we don’t expect emergence of fundamentally new types of threats.
The Way for Companies to Tackle the Challenges in 2023 Head On
In conclusion, two important tips for market participants on the ways to protect themselves and their customers from cyber fraudsters in 2023. Foremost, a company has to know the network and its services well. Services should be split into different baskets depending on their risk and severity level to the business (mission critical, critical, bulk, etc.). For each of these baskets, a risk assessment should be performed, and these risks should be managed (risk mitigation).
It is also important to deploy cyber defenses on a permanent basis (“always-on”). If there is no such a solution, it is required to conduct internal drills switching to incident-service in response to test attacks at least quarterly. In addition, network services should be reanalyzed at least twice a year: what the network consists of, what applications are in it, which of them are critical, and what are the risks for them. Such an approach will help to counter cybercrimes effectively and help the company services to stay up and running 24/7 increasing customers’ loyalty and maintaining a good business reputation as a reliable and honest service provider.
This pattern will become common for any services, both public companies and private businesses.
It’s actually hard to say if the infrastructure will be able to cope with such attacks, since this will be influenced by a large number of factors, one of which is the amount of investment in infrastructure. If the infrastructure development stops, it may cause huge risks in terms of its ability to successfully mitigate large amount of sophisticated attacks.
In 2023, we expect Application Layer DDoS attacks, with their traffic mimicking the behavior of ordinary users, to become more widespread. Such attacks are extremely challenging to detect and neutralize.


DDoS attacks on the increase 13
THE BATTLE FOR THE DIGITAL SUPPLY CHAIN
Why did Churchill say that? Well, the UK’s lifeline was dependent on the supply of goods, materiel, and people from North America. It was a tenuous but crucial supply chain across the sea — The United Kingdom and its Empire would not have survived without it.
There are lessons we can learn from history which can be applied now within the Cyber community especially as we move from traditional supply chain management to digital supply chain operations.
Fast forward to now.
The supply chain challenges that we are facing in the digital age are often relegated as low priority both by cyber professionals and by businesspeople. It is not glamorous. Yet it sits astride all part of business and society. The intricacy and tenuousness of the digital supply change can be difficult for the lay person to comprehend until problems occur.
Supply chain attacks often occur when a company’s data is compromised via the hacking of a third- party supplier which has legitimate access to its customers’ systems. Hackers can insert malicious code into trusted hardware or software at the source, compromising the data of its customers – and their customers –spreading infection throughout that chain.
Where traditional supply chains function in a linear fashion, digital supply chains function more like networks. And unlike traditional supply chains, digital supply chains can provide real-time visibility into the performance of each step along the chain. This visibility into supplier performance and customer needs, allows a business to develop more relationships with more suppliers, and better protects the company against disruptions when they occur.
Digital supply chains work by integrating internal systems and data with external information, both structured and unstructured. Using new technologies to collect, monitor, and analyse data, a digital supply chain can help you make much better predictions and recommend remedial actions in real- time.

However, this can place an unsustainable burden on a small company which simply does not have the resources or expertise to join the digital supply chain club.
So how do we deal with this?
Good supply chain management is about four things:
1. reducing complexity
2. reducing uncertainty
3. learning lessons
4. visibility of process and transactions across the whole supply chain built on trust.
At the heart of digitisation is the fundamental requirement to know who you are dealing with and to “track and trace” along the chain. The principles of good risk management drive the need to understand the risks inherent in both traditional and digital supply chains. A full understanding of the network of suppliers is crucial so that cyber risks can be managed efficiently, and that due diligence can be carried out effectively.
Digital identity
As previously discussed, maintaining, and safeguarding digital supply chains is made easier and more effective with new technologies. However, this can place an unsustainable burden on a small company which simply does not have the resources or expertise to join the digital supply chain club.
For small businesses already burdened with all sorts of business challenges, digital identity offers a good assurance.
Digital identity is information used by computer systems to represent an external agent – a person, organisation, application, device, or supply chain flow.

So, this can be applied to material, commodities and goods
Digital identities allow access to services provided by computers to be automated and make it possible for computers to verify relationships by identity proofing.
Identity proofing is the process of verifying a user’s identity: confirming that they are who they say they are. This may sound like ordinary authentication, the kind based on a username/ password combination, but identity proofing actually comes into play before users get their credentials to access an application or alongside the traditional authentication process.
Malcolm Warr OBE Former Chair TranZparency Group New Zealand

The aim of identity proofing is to ensure that a user’s claimed identity matches their actual identity: in other words, that their identity is real and not fictitious. An excellent first step on the digital high road.
In other words knowing exactly who you are dealing with.
In New Zealand, the Trust Alliance (TANZ) has pioneered a trusted data sharing arrangement for New Zealand’s agricultural industry. In practice it is a Supply Chain digital assurance approach applicable to all industries world-wide
As TANZ Executive Director Klaeri Schelhowe has said, “We found there was no easy mechanism for farmers and food producers to easily and directly input their farm’s data in a trustworthy way and into the agricultural food chain. The existing data exchange models were inefficient and time wasting, which is why we have acted now to create a smarter way of collecting and sharing this important data.” Their ‘digital compliance product passport’ is configured to an international standard, data sharing technology where everyone across the sector is able to securely contribute, control, collate and protect their crucial data.
The new OSP Cyber Academy course will raise awareness of supply chain cyber security. The course includes a segment on how businesses can make the transition to a digital supply chain, with a focus on how can they use the data generated to solve problems.
It talks about the need to get everyone else on board. This involves developing a supply chain message and assuring that it reaches everyone in the organisation.
The aim is to develop digital supply chain management strategies and practicalities that embeds the right technologies and digital protections for clients’ businesses.
To sum up
Digital identity is playing a foundational role in our digital economy. Start with easy goals and have a project plan which maps your approach and can be scrutinised. Remember a key component is proving that suppliers are who they say they are!
To sumarize with a quote from Winston Churchill, “Success is not final, failure is not fatal, it is the courage to continue that counts.”
Digital supply chain cybernewsglobal.com 14
Churchill said of the Battle of the Atlantic: “The only thing that ever really frightened me during the war was the U-boat peril…for a long time we could not track and trace our adversaries”

Protecting Microsoft 365 data in-line with NCSC guidelines.


In the digital age, data is the lifeblood of any organisation. It fuels business processes, decision- making, and customer engagement. With the rise of cloud computing, solutions like Microsoft 365 (M365) have become an integral part of daily operations in businesses around the globe. This paper examines the criticality and sensitivity of M365 data, the limitations of its native protection features, and how Acronis backup solutions help meet the essential recommendations provided by the National Cyber Security Centre (NCSC) of the UK.
1. The criticality and sensitivity of Microsoft 365 data
Microsoft 365, formerly known as Office 365, is a suite of cloud-based productivity and collaboration tools, including Outlook, Word, Excel, PowerPoint, and Teams. These tools process and store a wealth of valuable data, from confidential emails and detailed reports to strategic plans and personal customer information. The loss or compromise of such data could have severe consequences, including operational disruption, loss of customer trust, reputational damage, and regulatory penalties.
Despite the undeniable importance of this data, many organisations have misconceptions about the level of data protection offered by M365. While Microsoft provides a robust infrastructure and a variety of security features, it does not guarantee comprehensive data protection or offer an extensive backup solution. This is largely due to the ‘shared responsibility’ model that underpins cloud computing.

Shared Responsibility Model
In cloud computing, the shared responsibility model defines the roles and responsibilities of cloud service providers (CSPs) and their customers concerning security and compliance. In the case of M365, Microsoft, as the CSP, is responsible for securing the underlying infrastructure that supports the cloud services, known as ‘security of the cloud.’ This includes tasks like ensuring
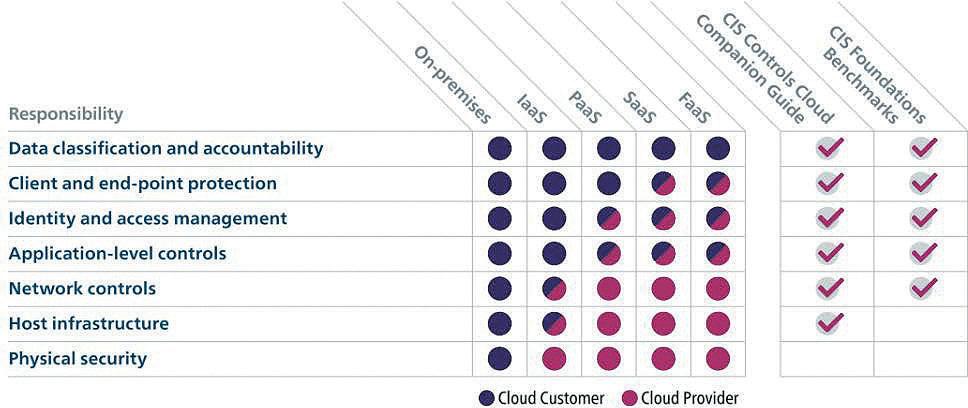
physical security of data centres, maintaining server infrastructure, and protecting the software that runs the cloud services.
On the other hand, customers are responsible for protecting their data within the cloud services, referred to as ‘security in the cloud.’ This includes safeguarding user accounts, managing data access permissions, and, crucially, protecting data through backup and recovery measures.
cybernewsglobal.com 16
Microsoft's Terms and Condititions
Microsoft's Services Agreement makes it clear that while they ensure the availability of their services, they do not specialise in data protection. They provide some native protection features, such as Recycle Bin for deleted items and versioning for SharePoint and OneDrive, but these measures have limitations, including finite retention periods and limited recovery options, especially for deleted items and users.
As a result, businesses that rely solely on M365's native protection features may find themselves unable to recover essential data in the face of accidental deletion, malicious insider activity, ransomware attacks, or other threats. The native features are designed to protect against service failures, not user errors or malicious actions, and thus do not provide a comprehensive backup solution.
The inadequacy of M365's native backup becomes even more apparent when considering the regulatory landscape. With laws like the European Union’s General Data Protection Regulation (GDPR) and the UK's Data Protection Act 2018, businesses are required to implement robust data protection measures, including regular data backups. Failing to meet these requirements could result in heavy penalties, not to mention the potential damage to a company's reputation.

Given these realities, it is essential for businesses to supplement M365's native protection with a robust third-party backup solution. This is where Acronis Backup for Microsoft 365 comes into play.
NCSC guidelines on data backup and protection
Recognising the importance of effective data backup and protection, the NCSC has issued guidelines to help businesses protect their valuable data. These guidelines include recommendations on data backup, understanding third-party protection measures, and legal responsibilities.
Data backup
At the heart of the NCSC's guidelines is the principle that organisations should regularly back up any data that is essential for their operations. This includes not only business data, but also configuration data required to operate systems. The guidelines also recommend following the '3-2-1' rule, which suggests having at least three copies of important data, stored on two different types of media, with one copy stored offsite
Understanding third-party protection measures
The NCSC advises organisations to understand what measures they can take to protect their data and what assurances they need to seek from third parties. This includes considering where they are relying on others to protect their data, such as in cloud services, in their supply chain, or on staff's personal devices.

Legal responsibilites
The NCSC also emphasises the need for organisations to understand their legal responsibilities. The guidelines reference the GDPR security outcomes guidance, developed jointly by the Information Commissioner's Office (ICO) and the NCSC. This guidance outlines a set of technical security outcomes considered appropriate for the protection of personal data under the Data Protection Act 2018.

Meeting NCSC recommendations with Acronis Backup for Microsoft 365
Acronis Backup for M365 is a comprehensive solution that aligns with the NCSC's guidelines and addresses the limitations of M365's native protection features. It offers automated backups of M365 data to secure Acronis Cloud Storage, with flexible recovery options and advanced security measures.
Understanding data protection responsibilities
Acronis takes its responsibilities as a thirdparty provider seriously. The company ensures the security of your data by storing it in data centres that adhere to rigorous industry standards, including ISO 27001 and ISO 9001. They provide clear information about their data protection practices and offer service-level agreements that provide concrete assurances about their commitment to safeguarding your data.
Compliance with legal responsibilities
The Acronis solution is designed with compliance in mind. It offers features that help organisations comply with data protection regulations like GDPR and the Data Protection Act 2018. These include the ability to define customisable retention policies, as well as data deletion and data export capabilities.
Backing up essential data
Acronis Backup for M365 goes beyond the native backup features of M365, offering regular, automatic backups of M365 data, including emails, contacts, calendars, SharePoint sites, OneDrive for Business accounts, and Teams data. These backups are stored in secure Acronis Cloud Storage, separate from the M365 environment, ensuring that they are protected even in the event of a compromise of the M365 account.
Following the '3-2-1' Rule
In line with the NCSC's guidelines, Acronis Backup for M365 follows the ‘3-2-1’ rule, storing backups in multiple locations to ensure data availability even if one copy is compromised. By default, backups are stored in the secure Acronis Cloud, but customers can also choose to store backups on local storage or another cloud storage of their choice, providing flexibility in their backup strategy.

Ensuring offline and restricted access backup
Acronis Backup for M365 ensures that backups are kept separate from the network, reducing the risk of them being compromised in the event of a network attack. In addition, access to the backup data is strictly controlled, with role-based access control and multifactor authentication options available to further secure the data.
Retaining backups for an extended period
Acronis allows organisations to define their backup retention policies, providing the flexibility to retain backups for an extended period. This ensures that organisations can recover their data even if an issue is not detected immediately, addressing one of the key limitations of M365's native protection features.
Testing backup and recovery
Acronis understands the importance of not just backing up data, but also ensuring that it can be restored effectively when needed. As such, they offer intuitive recovery options and encourage customers to regularly test their backups and restoration procedures.
Reducing the risk of re-infection
To help reduce the risk of re-infection when restoring data from backups, Acronis offers advanced security features, including built-in anti-malware protection. This feature scans files during the backup and recovery process, helping to ensure that any malicious files are detected and removed before they can cause harm.
Conclusion
In conclusion, to align with the NCSC recommendations and adequately protect your Microsoft 365 data based on the risks identified, it's necessary to go beyond native protection. Acronis Backup for Microsoft 365 provides a robust, comprehensive backup solution that addresses the areas of risk and responsibility highlighted by the NCSC and Microsoft's shared responsibility model. It ensures that organisations have the necessary protections in place to secure their M365 data, comply with regulatory requirements, and maintain business continuity.
Visit our website to get a 30-day free Acronis Trial
17
The Cybersecurity Woman of the World Edition 2023: Empowering Change, Building Stronger Defense and Shaping the Future
The field of cybersecurity has become increasingly critical as our world becomes more interconnected and reliant on digital technologies. In this dynamic landscape, women have emerged as influential leaders, innovators, and change-makers, contributing invaluable expertise and perspectives. To recognize and honor their remarkable achievements, the Cybersecurity Woman of the World Edition 2023 has been established as the highest honor and prestigious award for women in cybersecurity.
The brainchild of Carmen Marsh, the founder of the annual Cybersecurity Woman of the Year Awards at Black Hat, the Cybersecurity Woman of the World Edition aims to expand the reach and impact of recognizing women's contributions in the field. Carmen Marsh, a global cybersecurity leader and advocate, envisioned a platform that would shed light on women who have gone above and beyond to defend our digital landscape. By establishing this new and truly impactful award, Carmen and her team aim to celebrate the achievements of women in cybersecurity on a global scale.
The expansion of the Cybersecurity Woman of the Year Awards to the Cybersecurity Woman of the World Edition signifies the growing importance of gender diversity and inclusivity in the cybersecurity industry. Carmen Marsh recognized that acknowledging and honoring women's accomplishments is not only a matter of equality but also a strategic imperative. By bringing attention to the exceptional work of women in cybersecurity, this initiative aims to inspire and encourage more women to pursue careers in the field, addressing the gender gap and fostering innovation and creativity.
The Cybersecurity Woman of the World Edition is also a collaborative effort under the umbrella of the United Cybersecurity Alliance, OSP Cyber Academy and Cyber News Global. This alliance strives to bring together global experts, organizations, and individuals to build the strongest defense against cybercriminals. The nominees come from the 160 different women in cyber associations from across the globe including the past winners of the Cybersecurity Woman of the Year Awards. By recognizing and honoring the achievements of women in cybersecurity, the Cybersecurity Woman of the World Edition aligns with the alliance's mission of fostering collaboration, sharing knowledge, and advancing cybersecurity practices worldwide.

This prestigious award serves as a beacon of inspiration for aspiring professionals and challenges existing stereotypes. It recognizes excellence in cybersecurity and highlights the significant impact women have in defending our digital landscape.
By highlighting the extraordinary work of women who have made a significant impact in defending our digital landscape, the initiative aims to break down barriers, challenge stereotypes, and encourage more women to pursue careers in cybersecurity.

The Cybersecurity Woman of the World Edition is an event of global importance. It brings together cybersecurity experts, thought leaders, and industry professionals from around the world, providing a platform for networking, knowledge-sharing, and collaboration.
Ultimately, the Cybersecurity Woman of the World Edition is a testament to the power and influence of women in the cybersecurity field. By recognizing their achievements, the initiative challenges societal norms, encourages diversity, and underscores the essential role women play in shaping the future of cybersecurity. Through this prestigious award, Carmen Marsh and the United Cybersecurity Alliance aim to inspire, empower, and unite cybersecurity professionals worldwide to build a robust defense against cyber threats.
In conclusion, the Cybersecurity Woman of the World Edition 2023 represents the highest honor and prestigious recognition for women in cybersecurity. By shining a spotlight on women who have made extraordinary contributions, the Cybersecurity Woman of the World Edition paves the way for a more inclusive and secure digital world.


19
CYBERSECURITY



















Meet
cybernewsglobal.com 20
Meet some of the CYBERSECURITY WOMAN NOMINEES

















21
SCOTSOFT2023
28.09.2023 Edinburgh
create. innovate. collaborate.
For more than 30 years, leadership and technology have combined at ScotSoft.
Over 1000 guests join us from around the world, not just to learn during the day, but celebrate the incredible young talent emerging from Scotland’s universities.

The day is jam packed with more than 40 speakers across our Developer Conference and Leadership Forum, and topped off with our Young Software Engineer of the Year Awards dinner in the evening.
join us
We’re packed full of visionaries, technologists, business leaders and managers working in digital companies and end user businesses.
Join us and get inspired by our great line up of speakers at the longest running tech focussed conference in Scotland.
scotsoft.scot

Official Media Partner
CRIMINALS USING THE DARK WEB THINK YOU CAN’T
SEE THEM WITH SEARCHLIGHT CYBER, YOU CAN.
GAIN THE ADVANTAGE OVER THREAT ACTORS AND CRIMINALS
Illuminate threats with dark web intelligence

Pre-empt ransomware and cyberattacks
Defend your organization
TRUSTED GLOBALLY BY ENTERPRISE, LAW ENFORCEMENT AGENCIES, AND GOVERNMENTS

TO LEARN MORE, VISIT:

SC S O a S O AICPA SOC aicpa.org/soc4so SLCYBER.IO
CISOs Role in Safeguarding The Digital Future

 Mohamad Mahjoub
Mohamad Mahjoub
 CISO – Veolia Near and Middle East
CISO – Veolia Near and Middle East


It is no secret that Cyber Attacks are on the rise. The utilities market has been experiencing such kinds of attacks since 2015. Our Group’s size, international scope and the variety of its businesses make it all the more vulnerable to cyber risks and prone to be the target of cyber attacks. Moreover, as a world leader in utilities management, Veolia wishes to be ahead of regulations which are more and more enforced. Cyber threats are becoming more sophisticated and prevalent as we continue to rely on digital technologies to drive business growth. In today's digital age, the role of the Chief Information Security Officer (CISO) is more important than ever to secure the digital future of any organization.

As a CISO , my primary responsibility is to implement and oversee Veolia Near and Middle East cybersecurity program. This includes identifying potential cyber risks and ensuring that Veolia Near and Middle East is prepared to handle any cyber incidents that may occur. It is vital as well to align the cybersecurity program with the overall business objectives and strategy. By understanding the company's goals and objectives, I can ensure that the cybersecurity program is in line with them. By aligning cybersecurity and business objectives, CISOs can help the company achieve its goals and protect its digital assets.
Monitoring incident response activities is another critical responsibility. Cyber incidents can occur at any time, and we need to be prepared to respond promptly and effectively. By monitoring incident response activities, we can ensure that Veolia Near and Middle East is ready to handle any potential cyber incidents and minimize their impact on the company's operations.

Managing business continuity and disaster recovery is one of the most important areas for a CISO to manage. A cyber incident can cause significant disruptions to our company's operations, making it essential to have a plan in place to ensure that the company can continue to operate in the event of a disaster. I am responsible for developing and implementing a business continuity and disaster recovery plan that will enable us to recover from any cyber incidents quickly.
Cultivating a strong information security culture is another key responsibility. I have created an environment in which employees understand the importance of cybersecurity and its role in protecting the company's digital assets. This is a pre-requisite to pave the way to a cyber security awareness and training program, which is an essential task for any CISO. I try my best to ensure that all employees are trained on cybersecurity best practices and understand the potential risks associated with cyber threats. Topics include social engineering, how to identify phishing scams, how to avoid BEC attacks, and many more.
Safeguarding the Digital Future cybernewsglobal.com 24
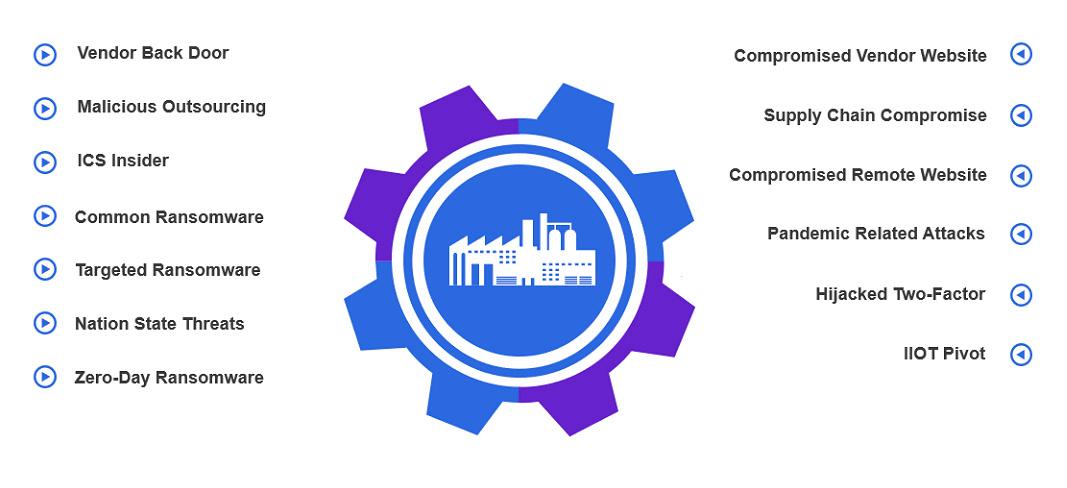
Everyone is fighting against a remarkable IT and OT threat landscape; Veolia Near and Middle East region is no different. As you may be aware, some threats identified in the diagram have the potential to evolve into disruptive and destructive capabilities, particularly the supply chain and ransomware attacks. On top of that, ransomware gangs are an emerging constant threat due to the fact that they share methods, infrastructure (C&C), and techniques.
Ransomware-as-a-Service (RaaS) has also emerged to be a common term where malicious ransomware packages are made available to other criminals, who can easily make use of them. Moreover, the majority of the industrial environment is vulnerable to newly known defects (ripple 20 and amnesia), misconfigurations, and inadequate maintenance, which is in turn assisting these threats to materialise. The main challenge is that we always need to be vigilant about new threat vectors for IT and OT environments.

We all know that risk can be reduced by implementing a well-maintained defence-in-depth approach, which is exactly what we are continuously working on. We believe that the governance umbrella, in addition to employee cyber awareness and having a defined and tested incident response procedure in place, is the cornerstone of this strategy. We are currently deploying OT vulnerability management solutions across the region, which will provide us with many security benefits. We believe that such initiatives go hand in hand with the need for digital transformation and corporate modernization. We are constantly working with our peers all over the world on securing our systems to meet these demands and, as a result, business needs, while taking into account the uniqueness of local and relevant cyber legislations.

OT security has always been a challenge to us, that being said, we are benchmarking global standards such as NIST CSF, NIST 80053, NIST 800-82, and ISO 27001:2022 and the seamless integration of GDPR in it, and ISA/IEC 62443 to building our internal “Security Framework” to help us provide a consistent language for the security community across Veolia, this will in turn assist us to analyse and effectively convey our security posture, away from the intricacies of frameworks and standards.
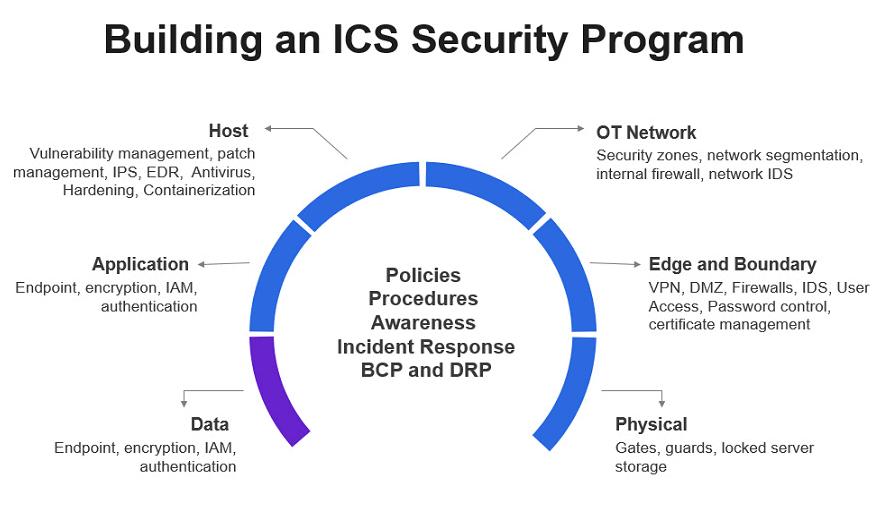
The rule of thumb is “Threats can be mitigated through a well-maintained defense in-depth strategy” . Industrial environments are no different. Data, application, host, OT network, edge and boundary, in addition to physical security layers must be carefully assessed before relevant security controls can be implemented. The most important factor is the governance aspect and management support, employee’s awareness, existence of solid policies procedures, in addition to having resilient incident response and business continuity plans. My advice to corporate cyber security teams is to go to their plants, understand the process well, learn the language of the OT people, and build relationship with them as this will help tackling cyber security concerns more efficiently.

Safeguarding the Digital Future 25
DNS: The Elephant in the Room - From Design to Ignored Consequences
By A J. Jenkinson

Domain Name System (DNS) serves as a critical backbone of the Internet, translating human-readable domain names into machine-readable IP addresses. Since its inception and acceptance by the Internet Engineering Task Force (IETF) in 1986, DNS has played an indispensable role in facilitating Internet communication. However, despite its vital importance, DNS has often been overlooked, leading to significant consequences in terms of security vulnerabilities, attacks, and potential disruptions. This article explores the journey of DNS from its design and acceptance to its utilization, and highlights key papers, government initiatives, compliance regulations, and notable attacks since 2011.
DNS Design and IETF Acceptance
The DNS protocol was introduced in the early days of the Internet to simplify the process of accessing resources by translating domain names into IP addresses. In 1986, the IETF officially accepted DNS as a standardized protocol, establishing its fundamental role in Internet infrastructure. The design principles focused on scalability, efficiency, and decentralized administration, making it a robust and essential component of the Internet. DNS was designed and invented by my associate and friend Dr Paul Mockapetris from 1983-1986. Paul is the first to confirm back in the heady days of moving from Arpanet to the Internet, that security was not really considered. More latterly, Dr Mockapetris and Dr Paul Vixie, another acknowledged DNS expert and fellow inductee of the Internet Hall of Fame both state; ''Over 95% of all cyberattacks, malware, and bots rely on DNS.'' Such attacks exploit exposed, insecure, and misconfigured DNS servers.

DNS Utilization and Government Involvement
Recognizing the significance of DNS, governments and organizations worldwide have delved into research and policy initiatives to optimize DNS utilization, however a lack of knowledge and competency ensures lax, suboptimal security due to DNS errors, oversights, and ignorance. The United States Government, through agencies such as the Cybersecurity and Infrastructure Security Agency (CISA) and the White House, has published numerous papers addressing DNS security, vulnerabilities, and best practices. The European Union (EU) Commission has also emphasized the importance of DNS and included it in various cybersecurity strategies. In January 2022 just days following the Russian Cyberwar launch on Ukraine, both The White House and EU Commission published their papers on Zero Trust Architecture and DNS Abuse. The two papers cited DNS vulnerabilities, manipulation, and abuse over 1,000 times.
The Ukraine government suffered numerous Internet Asset attacks as over 70 government websites were attacked, including DNS attacks.* The U.S. and UK governments were confirmed in revelations by Edward Snowden in 2013 as having exploited Internet Assets and DNS as part of their ongoing surveillance programmes. Now the tables were turned and the same vulnerable, exposed, and insecure DNS positions that the Intelligence Agencies had manipulated were now being manipulated and abused by cyber criminals whilst security professionals are forced to play Digital Whacka-Mole whilst trying to address symptoms whilst often overlooking the root cause and initial access. Cyber criminals have learnt how to exploit DNS from our own Intelligent Agencies only now for nefarious reasons as opposed to simply surveillance.
Emergency Directive M-19-01 and DNS Security
In 2019, the U.S. Government issued Emergency Directive M-19-01, emphasizing the criticality of DNS security and mandating federal agencies to enhance their DNS protections. The directive underscored the need for implementing security measures, monitoring DNS traffic, and adopting best practices to mitigate potential attacks. This directive highlighted the growing recognition of DNS as a vulnerable point in network infrastructure. The Emergency Directive was issued following numerous Federal Agencies suffering DNS Cyberattacks which took them offline for 33 days.
In 2023 several Federal Agencies suffered further cyberattacks and these were quite possibly further DNS attacks as the exposed vulnerabilities were simply left and not remediated despite the Emergency Directive. The systemic failure to address DNS by the Federal Agencies leaves the U.S. completely exposed to ongoing DNS Tampering and Abuse despite M-19-01.
DNS and Compliance Regulations
The Cybersecurity Maturity Model Certification (CMMC) framework, developed by the U.S. Department of Defence, addresses the inadequate security posture of the defence industry in the US. It emphasizes DNS security and compliance as essential components for safeguarding sensitive defence information. Compliance with CMMC requirements is meant to ensure that Government third party organizations have robust DNS protection in place to defend against potential threats and to mitigate their government and military clients. Should any of the third-party suppliers, including global companies such as Boeing, General Dynamics, BAE, Babcock International and the like fail to adhere to CMMC, or be given easy passage without due diligence to confirm compliance, the U.S government and military will remain vulnerable, exposed, and exploitable to third-party supply chain risks unnecessarily. Currently the framework and compliance regulations are simply failing to deliver the required assurances.
Notable DNS Attacks Since 2011
Since 2011, numerous high-profile DNS attacks have exposed the vulnerabilities and potential consequences of ignoring DNS security.
1) The Distributed Denial of Service (DDoS) attack on Dyn in 2016 highlighted the disruptive impact of targeting DNS infrastructure, leading to widespread service outages. This took major organisations offline across the U.S for the majority of the day resulting in major costs and losses.
2) The 2020 SolarWinds supply chain attack further underscored the DNS-related risks, as malicious actors manipulated DNS records to gain unauthorized access and compromise systems and gain access to over 18,000 SolarWinds clients including the U.S. government and U.S. Treasury. This attack is noted as the world’s largest cyberattack.
Header
* https://data.europa.eu/doi/10.2759/616244
cybernewsglobal.com 26
3) More recently the swathe of MOVEit related attacks that have traversed the globe is an interesting case of not every victim using MOVEit software, but all using the same third-party insecure DNS servers.
From early cyberattacks in the 2000's to date, many symptoms and flaws are subsequently and retrospectively discovered. However, due to a lack of competency and knowledge, the root cause and method of access is frequently completely overlooked - DNS security, or lack thereof. The continued oversight and ignorance of the criticality of DNS security will result in only one outcome. These outcomes we see and read about every single day.
The economic costs associated with the examples above are significant. Unfortunately, cyberattacks are deemed similar to playing the lottery as no one knows whether they are the next to be attacked: frustratingly, it is abundantly clear that the DNS side doors and back doors can be closed, and the risk reduced which requires experts and effort. Experts and effort that far too few have.
Ignoring DNS: Consequences and Future Outlook
Ignoring DNS security has far-reaching consequences that extend beyond temporary service disruptions. Exploiting DNS vulnerabilities can result in data breaches, unauthorized access to sensitive information, hijacking of traffic, Man in The Middle (MiTM), Distributed Denial of Service (DDoS), and even potential espionage or sabotage. By neglecting the criticality of DNS security, organizations and governments expose themselves to substantial risks, including reputational damage, financial losses, and compromised national security.
Conclusion
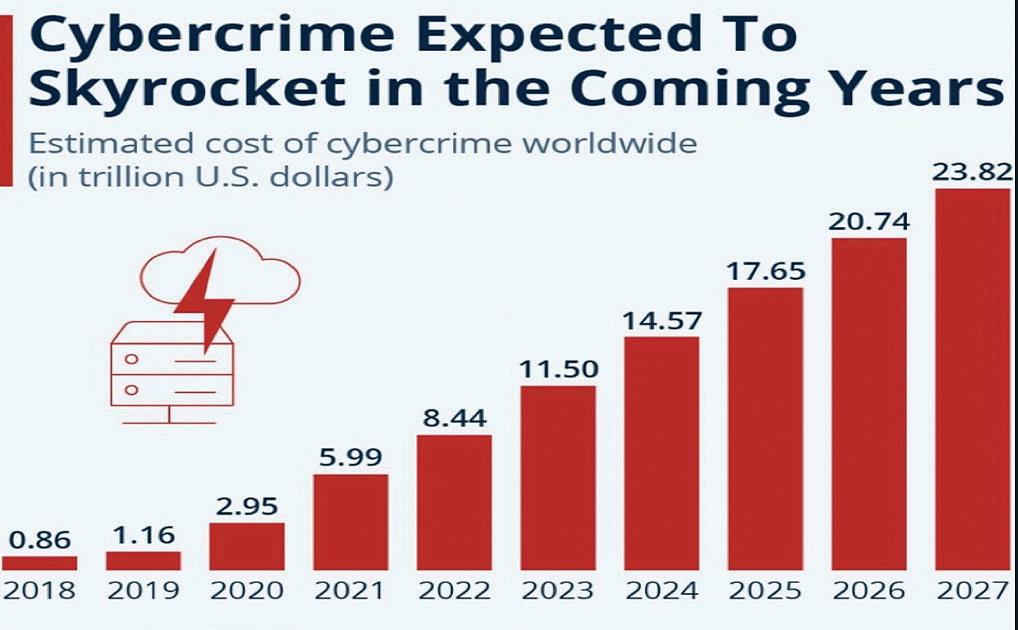
Today, losses to cybercrime are around 10 $trillion per annum, or around 10% of the world’s GDP. This is predicted to exponentially increase to reach circa 24 $trillion over the next few years. This represents around 25% of the world’s GDP making it larger than any country in the world. The amount of money spent on cyber defence is only 5% of the annual losses. This is simply not enough to combat the losses. Little to no attention addresses the elephant in the room. By continuing to ignore the criticality of the DNS problems, our economies, and democracies will continue to dramatically be eroded resulting in unthinkable and extremely unpalatable consequences.
DNS is by far the greatest, largest elephant in the room when it comes to security as the Intelligence Agencies have manipulated and abused DNS for decades as part of their ongoing surveillance programmes. However, now it demands not gazes being averted, but radical proactive measures if we are ever to see any stabilising, let alone reduction of cybercrime. With its vital role in Internet communication and the increasing sophistication of cyber threats, it is imperative to address DNS security congruently and comprehensively. Governments, organizations, and individuals must collaborate to implement best practices, strengthen DNS infrastructure, and prioritize investments in securing this foundational component of the Internet. Ignoring DNS risks, vulnerabilities, attacks, and potential disruptions, jeopardises the integrity and trust of the Internet globally. It is time to acknowledge and proactively safeguard the criticality of DNS to ensure a secure and resilient digital future.
 Andrew Jenkinson CEO Cybersec Innovation Partners, Fellow The Cyber Theory Institute. Author of three published Industry books: Stuxnet to Sunburst 20 Years of Digital Exploitation Ransomware and Cybercrime, Digital Blood on Their Hands Cited as Global DNS Expert Assisted Governments & Intelligence Agencies
Andrew Jenkinson CEO Cybersec Innovation Partners, Fellow The Cyber Theory Institute. Author of three published Industry books: Stuxnet to Sunburst 20 Years of Digital Exploitation Ransomware and Cybercrime, Digital Blood on Their Hands Cited as Global DNS Expert Assisted Governments & Intelligence Agencies
27
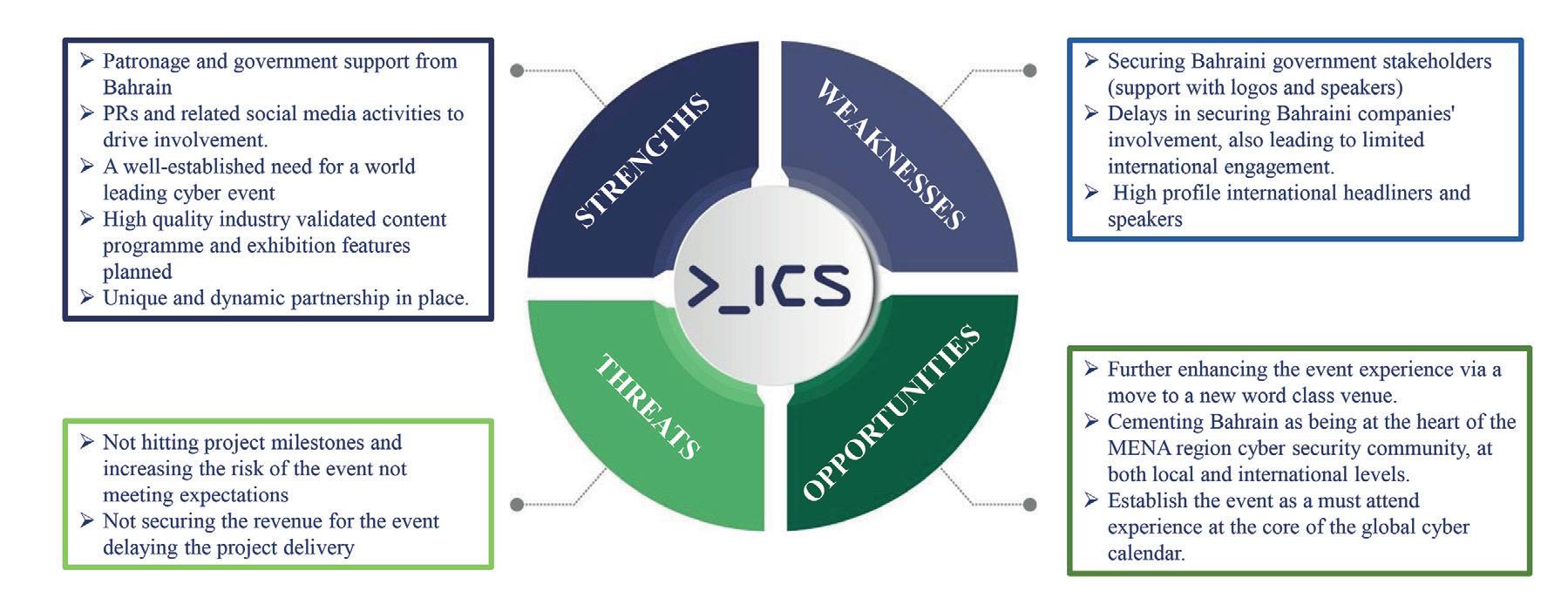
Bahrain to Host the Second Arab International Cybersecurity Conference & Exhibition (AICS)
Manama, Bahrain
Under the patronage of His Royal Highness Prince Salman bin Hamad

Al Khalifa, the Crown Prince, Deputy Supreme Commander of the Armed Forces and Prime Minister, the Kingdom of Bahrain is set to host the second Arab International Cybersecurity Conference & Exhibition (AICS). The event is scheduled to take place at the Exhibition World Bahrain from 5th to 6th December 2023.
The AICS is a premier annual event that brings together industry leaders, experts, and professionals from around the world to share their knowledge, experience and solutions to the challenges facing the cybersecurity sector. The event also provides a platform for networking and collaboration among the stakeholders in the cybersecurity sector.
On the occasion, National Security Advisor, Royal Guard Commander,
His Highness Shaikh Nasser bin Hamad Al Khalifa, emphasized that cybersecurity is a fundamental pillar of the kingdom's national security and economic development. He further added that Bahrain's security and prosperity depend on the existence of a secure information and communication technology infrastructure.
HH Shaikh Nasser also indicated that the AICS is in line with the National Cybersecurity Strategy and aims to meet the specific needs of exploring new technology, learning, and dealing with the evolving global cyberspace. The three-focus area of the event will demonstrate the ‘5 pillars’ of NCSC’, will provide a conducive environment for networking and engaging vendors, OEM and solution providers.

The AICS is not just an opportunity for experts in the field of cybersecurity to exchange knowledge, share experiences, and learn about the latest cybersecurity trends and

solutions, but also offers a range of activities such as technical sessions, keynotes, panel discussions, workshops, hackathons, and demonstrations for students and cybersecurity enthusiasts. The event will showcase the latest cybersecurity technologies and products from leading companies and organizations. Attendees will have the opportunity to network with industry experts and obtain valuable insights and best practices.
The Arab International Cybersecurity Conference & Exhibition aims to raise awareness of cybersecurity issues, key innovations and to build a strong foundation for the security of the digital world, providing an opportunity for attendees to learn, network and share their experience and knowledge in the cybersecurity domain. The event is a must-attend for anyone interested in the cybersecurity sector, and we look forward to welcoming participants from around the world to Bahrain in December 2023.

cybernewsglobal.com 28
Connecting Influencers and Thought Leaders
An event for cyber security speacialists and suppliers


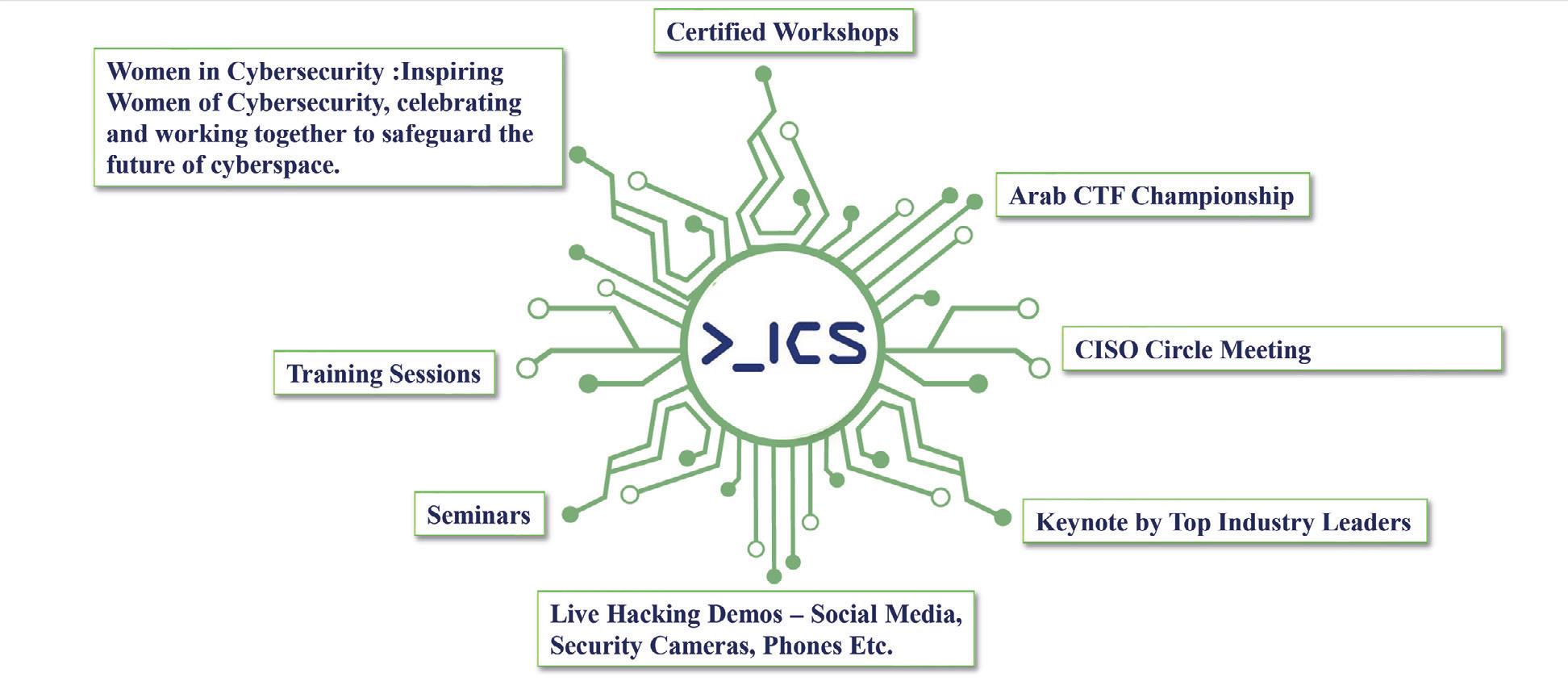
Potential highlights of AICS 2023 his highness shaikh nasser bin hamad al khalifa
in Cybersecurity 29
Empowering Global Cooperation































































Are your cyber defences FIT FOR PURPOSE? Sooner or later, you will let malware in. They only need to get it right ONCE. Cyber Centre of Excellence for Local Public Services From education & training, to detection, protection & response, we are the one-stop-shop for your cyber essentials. www.iese.org.uk/cyber-centre-of-excellence | enquiries@iese.org.uk An entirely new layer of cyber protection. Created by the sector, for the sector. Military grade defence, at high street prices. A unique combination of skills and solutions. Expert services that you can trust. Protecting your local community. elearning.ccoe.org.uk/elearning - enquiries@ccoe.org.uk


Be part of the event contact ceo@cybernewsglobal.com Official Media Partner


































































































































































 Mohamad Mahjoub
Mohamad Mahjoub
 CISO – Veolia Near and Middle East
CISO – Veolia Near and Middle East










 Andrew Jenkinson CEO Cybersec Innovation Partners, Fellow The Cyber Theory Institute. Author of three published Industry books: Stuxnet to Sunburst 20 Years of Digital Exploitation Ransomware and Cybercrime, Digital Blood on Their Hands Cited as Global DNS Expert Assisted Governments & Intelligence Agencies
Andrew Jenkinson CEO Cybersec Innovation Partners, Fellow The Cyber Theory Institute. Author of three published Industry books: Stuxnet to Sunburst 20 Years of Digital Exploitation Ransomware and Cybercrime, Digital Blood on Their Hands Cited as Global DNS Expert Assisted Governments & Intelligence Agencies








































