A New Era of Cyber Defense

Ensuring Security is Built-in by Design and by Default in IoT Devices
How Zero Trust Architecture Can Help Organizations Adapt for the Future
Implementing a Realistic and CostEffective Cyber Defense Strategy
Making IT Security
Auditing More Effective and Efficient with Automation

Threats continue to evolve. New technologies are introduced. Stakeholders push for further digital transformation. As progress marches on, it can be a challenge for any organization to adapt to the ever-changing landscape, but especially small- and medium-sized enterprises. Luckily, there are resources available to help these organizations prepare for the future.
Maintaining the MSISAC’s Strong Sense of Community as Membership Grows
A PUBLICATION FROM
Ad Placement Work more securely in the cloud Microsoft Windows 10 and 11 in Azure Marketplace LAUNCH NOW
Cybersecurity
Fall 2023 Volume 7 Issue 3
Editor-in-Chief
Michael Mineconzo
Supervising Editor
For questions or information concerning this publication, contact CIS at info@cisecurity. org or call 518.266.3460
© 2023 Center for Internet Security. All rights reserved.
Laura MacGregor
Copy Editors
David Bisson
Autum Pylant
Staff Contributors
Jay Billington
Stephanie Gass
Carlos Kizzee
Kathleen Moriarty
Charity Otwell
Aaron Perkins
Natalie Schlabig
Karen Sorady
Valecia Stocchetti
Fall 2023 i Contents Featured Articles Building Community Within the ISAC Membership How the ISACs are ensuring that the sense of community among our members remains strong as we continue to grow 3 Whole of State Takes a Village: How Zero Trust Enables a Secure IT Ecosystem Effectively using zero trust architecture to help government agencies adapt to new technologies and workforces 6 Embedded IoT Security: Helping Vendors in the Design Process Insights on how IoT vendors can ensure security is built-in by design and by default, rather than an after-the-fact add-on 10 Essential Cyber Hygiene: Making Cyber Defense Cost Effective A real-world view into how realistic and cost effective it can be to achieve essential cyber hygiene. 14 Advancing Operational Excellence through Automated IT Security Auditing How introducing automation to the IT security auditing process can improve efficiency and effectiveness 19 Quarterly Regulars Quarterly Update with John Gilligan 1 News Bits & Bytes 2 Cyberside Chat 18 ISAC Update 21 Event Calendar 22
Quarterly is published and distributed in March, June, September, and December. Founded MMXVII. Published by Center for Internet Security, 31 Tech Valley Drive, East Greenbush, New York 12061
Ad Placement Your governance, risk, and compliance toolbox. LEARN MORE Save up to 20% on a new Membership with code AUDIT2023
QuarterlyUpdate with John
Gilligan
Fall has finally arrived. For many of us, this is a welcome relief from what was generally a very warm summer. Unfortunately, while the weather has cooled, the rate of cyber incidents has not. We are pleased to present the fall issue of Cybersecurity Quarterly, which provides some recommendations on how to protect your organization from cyber attacks.
In recent months, our attention has focused on the impacts of artificial intelligence in the cyber world. The potential of leveraging artificial intelligence tools like ChatGPT to develop malware and to dynamically modify attack profiles to defeat cyber defense systems has received quite a bit of attention. These trends certainly are cause for concern in the cyber defense world. Fortunately, there is an increasing number of cyber defense tools with artificial intelligence capabilities to look for unusual patterns and anomalous events that might indicate a new attack vector. What is certain is that we are entering a new era of cyber protection and defense – one that requires a much nimbler response to evolving threats and that is making it harder for smalland medium-sized organizations to adequately protect themselves against cyber attacks. We are seeing this play out in increasing attacks on schools and hospitals. However, we are also seeing even larger organizations succumbing to ransomware attacks. The cyber defense world will continue to be hot for the foreseeable future.
As a part of its effort to assist small- and medium-sized organizations, the Multi-State Information Sharing and Analysis Center (MS-ISAC) has initiated an effort to work with segments of the critical infrastructure sector that operate from public organizations. One of the articles in this issue describes the initial efforts to establish communities of interest for some of these critical infrastructure areas (e.g., K-12 schools, utilities, judicial organizations) that will foster better collaboration and sharing of cybersecurity best practices. In August, the MS-ISAC held their annual meeting in Salt Lake City with over 800 attendees. Karen Sorady, CIS’s Vice President of MS-ISAC Member Engagement, reflects in another article about how the MS-ISAC is doubling down on
lessons learned to create an environment that provides even more value to MS-ISAC members in the future.

Further expanding on the theme of helping smalland medium-sized organizations, Valecia Stocchetti, Information Security Audit Manger at CIS, has authored a piece on the CIS Controls Implementation Group 1 (IG1) and the costs and benefits of implementing IG1 to achieve essential cyber hygiene. Representing an emerging minimum standard of information security and outlining actions that every enterprise should take to defend against the most common cyber attacks, IG1 is an ideal starting point for small- and medium- enterprises.
Kathleen Moriarty, our CTO, has provided an article that summarizes work that her team has done to provide guidelines for embedding security into the design process for Internet of Things (IoT) systems. This work is especially helpful in evaluating the relative strengths of features and different standards being used for IoT systems, certain to be an area of concern as IoT devices continue to expand their prevalence in our world.
Rounding out this quarter’s issue, Tamer Baker and David Cagigal from our CIS CyberMarket partner Zscaler have contributed an article on utilizing zero trust architectures to better enable a whole-of-state cybersecurity ecosystem. Elizabeth Wu, President of Cybersecurity Auditing Technologies, has provided a piece on the advantages of using automation in the performance of IT auditing. Finally, for our regular CISO column, Stephanie Gass, Director of Governance, Risk and Compliance, discusses how to keep staff aware of the changing threat landscape through effective security training.
Please enjoy this quarter’s issue, and have a great fall!
Best Regards,
Fall 2023 1
John M. Gilligan President & Chief Executive Officer Center for Internet Security
“We are entering a new era of cyber protection and defense –one that requires a much nimbler response to evolving threats.”
CIS Launches Strategic Collaboration with Microsoft to Strengthen Cybersecurity for State and Local Governments

CIS and Microsoft have entered a strategic collaboration aimed at bolstering cybersecurity measures for U.S. State, Local, Tribal, and Territorial (SLTT) government organizations, marking a significant step in providing multi-cloud security compliance solutions to help fortify digital defense capabilities against cyber threats to the public sector.

“Our joint efforts with Microsoft will further assist us in collectively addressing the unique challenges faced by the traditionally cyber-underserved organizations in the public sector and will ultimately further protect SLTTs against pervasive cyber threats,” said Gina Chapman, CIS Chief Operating Officer.
CIS Named to PCI Security Standards Council 2023-2025 Advisory Board

CIS has been selected as one of 52 board members to join the Payment Card Industry (PCI) Security Standards Council (SSC) in its efforts to secure payment data globally. The Board of Advisors represents PCI SSC Participating Organizations worldwide and works to ensure global industry involvement in the development of PCI Security Standards and programs. As strategic partners, board members bring industry, geographical, and technical insight to PCI SSC plans and projects. For the first time, PCI SSC Board of Advisor members will participate by voting on new standards and major revisions to standards prior to their release.
CIS and CREST Join Forces to Secure Organizations Globally

CIS and CREST, an international not-for-profit accreditation and certification body, are launching the CIS Controls Accreditation program to provide organizations a way to show that their cybersecurity posture meets the best practice guidance set forth in the CIS Controls. CIS Controls Accreditation offers CIS SecureSuite Members that provide CIS Controls implementation, auditing, and/or assessment services with the ability to demonstrate that their implementation of security best practices is guided and externally assessed in accordance to the rigorous standards defined by two renowned authorities in cybersecurity.
CIS Critical Security Controls Featured as Recommended Safeguard
in Verizon’s 2023 Data Breach Investigations Report
The CIS Critical Security Controls® (CIS Controls®) have been featured once again as a recommended path to cyber defense in the Verizon 2023 Data Breach Investigations Report (DBIR). The Verizon 2023 DBIR is widely recognized across the cybersecurity industry for its comprehensive analysis of the global threat landscape; it’s based on real-world data from actual security incidents and breaches. The Verizon DBIR serves as an authoritative source of information for organizations seeking to enhance their cybersecurity defenses and make better informed risk management decisions.
This year’s report recommends implementating specific CIS Controls and CIS Safeguards to defend against top attack patterns such as system intrusion, social engineering, and basic web application attacks – a focus which showcases the effectiveness of using the CIS Controls to protect against global threats for all industries.
Learn more about our collaboration efforts, as well as key findings from the 2023 Verizon DBIR by watching our recent webinar.
2 Cybersecurity Quarterly
NewsBits&Bytes
Building Community Within the ISAC Membership
By Carlos Kizzee
The Multi-State Information Sharing and Analysis Center (MS-ISAC®) and the Elections Infrastructure Information Sharing and Analysis Center (EI-ISAC®) have undergone and are continuing to undergo significant growth. By the time of publication, the MS-ISAC organizational membership strength is expected to be at 16,000 organizations and growing.
Within this growth, we have consistently heard from members that the ability to network with peers in clearly defined segments of practice or areas of interest is a key reason why people join and participate in the MS- and EI-ISACs. This networking enables members to identify peer practices that they can emulate to solve problems as well as to reduce cost and time associated with the implementation of solutions to common problems.
In addition to identifying and applying peer best practices, networking within communities of practice or interest enables members to commit time to focusing on specific issues and concerns that they have in common with their peers. The ISAC community is committed to enabling and enhancing these valued opportunities, especially given the challenge and complexity of the public-sector cybersecurity environment and the fact that cyber threat actors continue to target these environments.
What Do These Communities Look Like
MS-ISAC K-12 members come in all shapes and sizes. Some are States; some are Local governments. We also have both Tribal and Territorial government organizations with K-12 cybersecurity interests. The MS-ISAC maintains a K-12 working group that meets monthly to discuss topics of interest in K-12 cybersecurity. The group often receives presentations from SMEs and ISAC peers who share their lessons learned in developing and implementing security programs and tools.
As it is not feasible for approximately 4,500 K-12 members in the ISAC to join this Working Group or its monthly calls, the K-12 membership of the MS-ISAC Executive Committee and the K-12 Working Group leadership are exploring effective methods for enabling, engaging, maintaining, supporting, and informing what this growing K-12 Community should be.
Without doubt, the resulting K-12 Community of Practice will be the largest community within the MS-ISAC environment. Their best practices, knowledge, and key security guidance will be able to inform not only the ISAC K-12 network environment but also the rest of public sector K-12 organizations across the nation.
The K-12 members of the MS-ISAC Executive Committee and the K-12 Working Group leadership are engaged in a variety of coordination activities at the national and regional levels. These activities are designed to inform public policy and resource decisions that affect the cybersecurity of K-12 schools across the nation. The coordination activities include meetings, presentations, and workshops; participants in these activities include representatives from the White House, FEMA, CISA, and relevant trade associations.
Fall 2023 3
As MS-ISAC membership continues to grow, it’s crucial that we make extra effort to foster collaboration among peer groups to maintain our sense of community.
We have consistently heard from members that the ability to network with peers in clearly defined segments of practice or areas of interest is a key reason why people join and participate in the MS- and EI-ISACs.
Historically, many of our public-sector higher education organizations have connected with their peers in K-12 as well as with government officials in other areas of practice. The Center for Internet Security® (CIS) has heard a crescendo of interest from the approximately 900 public higher education organizations in ISAC Membership that they would benefit from greater coordination and networking among this segment of ISAC membership. Many responded to a recent call to action from one of their peers to form a recurring security discussion session group. They have identified key areas of security and risk management in the higher education environment around which they wish to network . They also see value in periodically publishing the perspectives and best practices from their dialogue to the rest of the community. Many have expressed interest in leveraging their community to identify key topics of interest for sessions in the 17th MS-ISAC Annual Meeting scheduled in June 2024.
What Additional Community Opportunities Are There?
In addition to communities based on areas of practice like K-12 and higher education, there is also opportunity for communities based on common topics of interest, such as cloud adoption, CIS Critical Security Controls (CIS Controls) implementation, and smart cities. The MS-ISAC has maintained a series of training and educational sessions on topics such as these. ISAC members who have registered for and attended these sessions are likely among those in the ISAC environment who are “subjectmatter interested” in topics and would benefit from periodic discussion sessions and other similar networking opportunities to share lessons learned and best practices in particular areas of common interest.
We have also heard from ISAC membership that there is common interest in user group communities to use or implement a particular type of technology/tool or even a specific solution to further reduce cost, decrease time to value, reduce time to full implementation, and enhance the use and tuning of specific security tools in an organization’s security stack.
What’s Next on the Community Roadmap?
The MS-ISAC is continuing to conduct “Community 411” sessions for ISAC communities of practice related to jurisdictions and areas of critical infrastructure.

The ISAC hosts sessions to present cyber threat intelligence, incident response best practices, and self-assessment insights to specific communities of practice. These communities include local governments, public utilities, state and local judiciary, and other segments of the ISAC membership.
These sessions also explore how organizations in these communities can address their vulnerabilities using products, services, and capabilities from the MS-ISAC, CISA, and the Center for Internet Security that are available at a reduced or no cost.
These sessions also enable communities to form themselves as communities of practice and communities of interest within the MS-ISAC environment, identifying leadership at the national level and within each of the 10 CISA regions to further support collaboration and mutual assistance where and when needed among that community.
CIS will continue to leverage member interest and input to support opportunities for communities of practice and communities of interest to develop among the ISAC membership. If you are interested in leading or supporting the development of a community or working group, please contact your Regional Engagement Manager or express your interest in an email to info@ cisecurity.org for further coordination.
Carlos P. Kizzee is the CIS Senior Vice President for Stakeholder Engagement Operations. In that position, Kizzee is accountable for the engagement, account management, and training and education activities associated with MS-ISAC membership as well as key programs assessing and enhancing the security maturity of state, local, tribal, and territorial government agencies and activities. Previously, Kizzee served with the Retail & Hospitality Information Sharing and Analysis Center (RH-ISAC) as Vice President of Intelligence, building and supporting retail and hospitality industry security collaboration; and with Defense Security Information Exchange as Executive Director, promoting threat intelligence sharing and collaboration within the defense industrial base and actively supporting the development and establishment of the National Defense ISAC.
4 Cybersecurity Quarterly

Whole of State Takes a Village: How Zero Trust Enables a Secure IT Ecosystem
As all levels of government adapt to new technologies and working conditions, maintaining a secure IT environment can be a challenge. Zero trust architecture can provide an effective means to balancing security and accessibility.
By Tamer Baker and David Cagigal
COVID left its permanent mark on the public sector, from necessitating the need for a hybrid workforce to constituents accessing services online to more applications and data appearing in the cloud. It was a heavy lift to make these significant changes in culture, process, and application delivery, but agencies did it and demonstrated agility and resilience during a time of great uncertainty.
Now government continues the digital transformation journey with IT modernization to better reflect this new reality and the need for improved security posture. Cybersecurity mandates and guidelines require changes to legacy systems and infrastructure to keep up with sophisticated cyber threats. It’s not just mandates, either. It’s also the work-from-anywhere requirement to access government applications from any device in any location for continuity of operations and delivery of citizen services.
Zero trust architecture (ZTA) provides a path forward that not only improves the user experience and cyber threat protection but also enables collaboration across the public sector to maximize collective cybersecurity resources. Zscaler’s multi-tenant architecture facilitates this approach to whole of state while maintaining independent policies at each individual agency.
Whole of State Challenges
Transformation is never easy; it puts increased pressure on IT and security leaders to lead not only a technical evolution but a cultural one, as well. Much of the hard work of mindset change has occurred, with work from anywhere on any device now a common occurrence.
Local government is a critical piece of the cyber threat protection puzzle, and state and local government can
collaborate while maintaining independence in cyber policies. In fact, the modernization of IT from the White House to the suburbs requires that the government work together to overcome challenges that have historically affected forward progress.
Culture
Transformation requires a mindset change. Yet the thing about change is it creates discomfort, and then inertia holds us back. IT leaders are the ones who have to drive forward this IT change. The CIO, CTO, and CISO work together to enable innovation; provide fast, reliable, and cost-effective connectivity; and manage agency risk with better cyber and data protection. They also lead the cultural change to collaborate across levels of government to improve security and resilience.
Resources
Governments are often resource-challenged due to limited budgets and competing priorities for funding. In agencies where resources are scarce, investments in security may be difficult, making them easier to target
6 Cybersecurity Quarterly
Zero trust architecture (ZTA) provides a path forward that not only improves the user experience and cyber threat protection but also enables collaboration across the public sector to maximize collective cybersecurity resources.
for cyber attacks. Whether it be funding or expertise and skills, resources are often a significant constraint to a whole-of-state strategy.
Technology
The traditional security network is built to silo data centers and restrict collaboration. In a single-tenant architecture, the hardware and its resources are exclusively dedicated to one tenant, requiring costly dedicated resources, isolated tenant data with private infrastructure that cannot be shared, and operator maintenance burden. Further, legacy security firewalls and VPNs extend and expose your network to the internet, enabling unwanted users and bad actors to discover them.
Whole of State Ecosystem
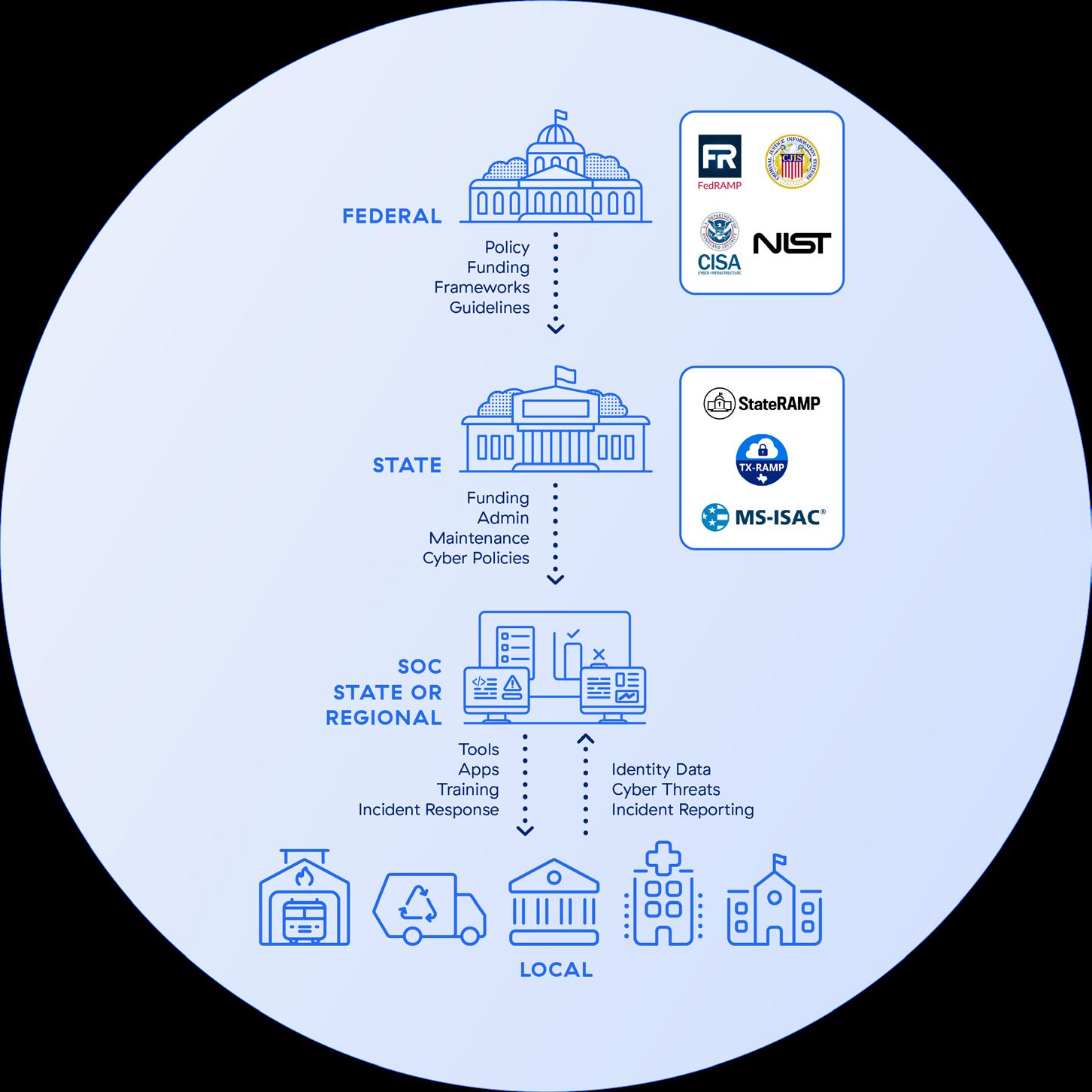
With ZTA, Zscaler is able to help government organizations build a whole-of-state ecosystem for cybersecurity. This symbiotic relationship between federal, state, and local government strengthens security to protect and serve constituents as well as preserve national security for our country. Let’s look at the contributions of each level of government in this ecosystem.
• Federal Government – Creates federal level policies, frameworks, and guidelines as well as funding for programs.
• State – Receives federal funding and passes through to local government; also, develops state-level cyber policies and guidelines.
• Local – County, city, and municipality determine local policies and manage public services for constituents.
• SOC – A state or regional security operations center (SOC) sits in between the state and local levels. The state provides the administration of tools, applications, training, and incident response, while the local level provides identity data, cyber threat notification, and incident reporting. Together, the state and local governments are able to leverage federal funding and frameworks without
compromising independent policy setting and data bifurcation.
Zero Trust Enables Whole of State
Secure digital transformation requires a zero trust architecture. Legacy architecture comes with increased cost, complexity, security risk, and compromised user experience. The legacy network-centric architecture has served us well for 30+ years, but with our applications moving everywhere, our users becoming more mobile, and adversaries modernizing, this architecture no longer works. That’s where the zero trust architecture comes in, and that’s the architecture that Zscaler pioneers. Let’s dig deeper into why and how.
Traditional Architecture Doesn’t Work Anymore
Over the past 30 years, organizations have built hub-andspoke networks, connecting cloud, branches, employees, constituents, and all locations to a few data centers. The network was secured by building a perimeter around the ever-growing network. Inside the perimeter, everything was trusted; outside was untrusted.
Fall 2023 7
The architecture that’s based on firewalls and VPNs protecting a perimeter is like a bridge. Once the bridge opens, traffic starts flowing, and you can go east, west, north, south. Your network is exposed to the internet, and attackers are allowed to find a way in and move laterally. In today’s borderless environment where data is stored and accessed from various locations and devices, a perimeter network cannot be secured.
Traditional cybersecurity architecture is often reactive, meaning that it only responds to threats after they occur. This approach is no longer sufficient, as threats can now spread rapidly and cause significant damage before they are detected and mitigated. A more proactive, comprehensive, and adaptive approach to cybersecurity architecture is needed to protect against the growing threat of cyber attacks.
Zero Trust Network Architecture – A Switchboard vs. a Bridge
Contrast legacy architecture that functions like a bridge with zero trust architecture, pioneered by Zscaler, that functions like a switchboard. A user connects with a switchboard, and based on the policy, that user gets connected to a particular application and that application only – not to the network.
In zero trust architecture, your applications are merely destinations – applications managed by you in your data center, public cloud, or SaaS and the internet. How do users and devices connect? You do not need a trusted network connecting everything to everything. You simply have every party connecting to the internet, and ZTA sits in the middle like a switchboard.
With ZTA, the traffic comes to us, and the first thing we do is say: “Stop, who are you?” Once we have verified identity, we ask, “Where are you going?” This is app-specific policy; you can restrict people to go to certain applications. ZTA checks a whole host of other policies and potential risks, such as device posture, and only when everything looks good is the go/no-go decision made to pass the user through the switchboard to their requested destination.
For external applications, we can connect simply to the internet and SaaS with a normal outside-in connection that starts from your end device. For internal applications that are managed by you, we have a unique technique: an inside-out connection using a piece of software called a connector. This connector makes that connection only after all these policy criteria are met. By doing so, we are actually doing a number of things for you.
First, by completing SSL inspection of all traffic, we are providing better cyber and data loss protection. Adversaries are smarter now and encrypting their payloads that pass right through firewalls and VPNs.

Next, by connecting users to applications only – not to the network – we are preventing lateral threat movement. Stolen user credentials is the number one attack vector. By removing users from the network and removing the ability for an attacker to utilize those credentials (VPN login), agencies will see huge risk reductions.
Lastly, by opening an inside-out connection, we minimize your attack surface because your applications go invisible. If they can’t find you, they can’t attack you. Or as we like to say, “If you’re not reachable, you’re not breachable.”
This is zero trust architecture at Zscaler, which closely follows the NIST model.
How ZTA Enables Whole of State with Multi-Tenant Architecture
8 Cybersecurity Quarterly
Traditional cybersecurity architecture is often reactive, meaning that it only responds to threats after they occur. This approach is no longer sufficient, as threats can now spread rapidly and cause significant damage before they are detected and mitigated.
Zscaler’s purpose-built multi-tenant architecture supports shared services, multi-agency environments, and local governments. In a multi-tenant environment, customers share the same application, operating environment, hardware, and storage mechanism. This is distinct from virtualization, where every application runs on a separate virtual machine with its own operating system.
A multi-tenant cloud is commonly likened to an apartment building. Residents have keys to their own separate apartments, but they all share the infrastructure that delivers water and power. The provider sets overarching rules and performance expectations for customers, but the individual customers have private access to their data.
Utilizing multi-tenant architecture in a state or regional SOC allows for each agency to set their own security policies and data privacy while sharing the infrastructure cost, burden, and administration with other agencies. Multi-tenant clouds take advantage of their underlying architecture to achieve efficiency, flexibility, and scalability; achieve cost savings; and maintain independent security policies to protect against cyber threats. This is whole of state with ZTA.
Next Steps
You’ve done the hard work to transform from an on-premises workforce and service delivery model to one that better reflects the remote and digital nature of our post-COVID world. Continue your transformation by shifting from legacy network infrastructure to a zero trust model that will improve your security posture and user experience. Continue the shift to whole of state with technology that enables a collaborative ecosystem while empowering government at all levels to shape their cyber policies based on independent requirements. Continue to protect your people, your constituents, and your data
with a whole-of-state strategy because the most effective cyber threat protection strategy truly takes a village.
Download Zscaler’s whole of state white paper for more detailed information about how our Zero Trust Exchange can support digital transformation for your agency.

With more than 15 years of experience in cybersecurity, Tamer Baker has worked with a variety of organizations across industries to help them achieve their security and business goals through technology. As Chief Technologist at Zscaler, Baker is responsible for assisting healthcare organizations, state and local governments, and educational institutions with their digital transformation efforts, modernizing their infrastructure to save money on operational costs, and increasing productivity and security – all while reducing risk by leveraging a zero trust architecture. Prior to Zscaler, Baker spent almost a decade at Forescout, where he provided global customers with strategic direction and architected solutions to meet specific requirements for national defense, government, healthcare, finance/banking, and other industries. Before moving to the private sector, Baker served in various roles within the public sector as well as an officer in the United States Air Force. Baker has a B.S. in aerospace engineering from Embry-Riddle Aeronautical University (ERAU) in Daytona Beach, FL.
David Cagigal currently serves as CXO Advisor at Zscaler and is a seasoned executive with over 25 years of experience in information technology visioning, strategic planning, and management. He is experienced in converging business strategies with ever-changing and innovative information technologies. He also identifies and implements the appropriate change management processes and risk-mitigating strategies for each unique culture. Cagigal has held executive IT positions at Alliant Energy, DeVry University, DePaul University, Maytag, and Amoco that cross multiple industries and business functions. Cagigal was appointed Wisconsin’s CIO in late 2012 after several decades in the private sector, including stints at the oil giant Amoco, appliance manufacturer Maytag, and Midwestern power utility Alliant Energy. During his tenure as the CIO of Wisconsin, he oversaw the process of consolidating all the data centers into one facility that serviced 50 agencies.
Fall 2023 9
Embedded IoT Security: Helping Vendors in the Design Process
As connected devices continue to permeate through our everyday life, it is becoming increasingly crucial that security becomes an embedded part of the design process, rather than an add-on after the fact.
By Kathleen Moriarty
The number of Internet of Things (IoT) devices is increasing at a pace where owners can’t keep up with device updates and secure configurations. Statista reports that the total number of IoT devices is expected to reach 30.9 billion units in 2025. That’s more than double the 13.8 billion devices that were connected in 2021.
Simultaneously, there is a lack of skilled expertise when it comes to securing IoT. This is changing…but slowly and partially. Documentation resources for IoT security, such as moving toward labels and other guidance for the enterprise, are increasing. However, when the Center for Internet Security (CIS) surveyed the market resources available, there was no guide aimed at vendors for embedding IoT security.
Given this discrepancy, we decided we wanted to assist vendors with decisions on which protocol stack makes the most sense for their product and what their security options are within that protocol stack. As a result, we created the white paper, Internet of Things: Embedded Security Guidance
In this article, I’ll describe the purpose of the white paper, go over what it contains, and discuss how you can use it.
IoT Security Built-in and By Default
Embedded IoT security is increasingly important. Attackers target IoT because it’s a possible entry point into corporate (and home) networks. While a gateway can help to protect devices, attackers can bypass the gateway in many instances. Additionally, embedding security as part of the design process reduces the need for add-on or bolt-on security products and approaches. In the very least, this makes it more difficult for cyber threat actors (CTAs) to conduct an attack. It’s no surprise that the White House’s Executive Order 14028, “Executive Order on Improving the Nation’s Cybersecurity,” and its follow-on documentation identified security that’s built-in by design and by default as an important theme for IoT devices.
To achieve embedded IoT security, vendors need resources that help them understand the necessary security requirements and how they can meet them. Take the design phase of an IoT product, for instance. The team has certain constraints that require consideration and that drive a decision to one of many protocol stacks to support those constraints. Since there are upwards of 10 protocol stacks, vendors would need to perform significant research to find what’s most applicable. They would also need to spend time researching the security capabilities that are either intrinsic to the protocol or available as optional extensions.
This is unrealistic. There has to be a better way.
Two Defining Characteristics of Our White Paper
Developed and vetted by industry experts, Internet of Things: Embedded Security Guidance aims to provide a resource to IoT vendors to ease the process of building
10 Cybersecurity Quarterly
Adopting zero trust is a journey toward better cybersecurity rather than a destination – one that may take multiple years to fully adopt but for which every organization should aim.
in security by design and by default. It does this with the four different IoT communication and data-sharing patterns in mind.
Our white paper stands out in two ways:

• Prescriptive recommendations – It includes recommendations for security options to better scale management and shift it left to the vendor when possible. (CIS members along with small- and medium-sized businesses are particularly interested in scale to reduce resource requirements.) We conducted significant research to develop these recommendations and lessen the burden
on individual developers from having to perform it themselves.
• Vetted research – It pulls from IoT industry experts engaged with vendors, standards work, and government to better understand the potential set of protocols that can be used. Additionally, it details the security options available within each of those protocol stacks. The research and verification takes an effort that many development teams do not have the time for when building a product and meeting timelines. This also brings forward all of the security options to ease that process for vendors. They might select a different protocol stack with different
Fall 2023 11
security options by having the ability to easily compare these options.
Get the Conversation Going
Our aim is to maintain this as a resource if it is found to be beneficial. As a reader, you can learn about options to enable security management at scale, such as the Manufacturer Usage Description (MUD) documented in RFC 8520 as well as the resources available to implement MUD. You can also use it to advocate for greater levels of IoT security in your organization and countless others.
what supplemental resources might aid in improving security to provide meaningful resources that assist in the “shift-left ” security movement.
If security is built in, enabled by default, and managed at scale by the vendor, the overall security landscape will improve. While there is always a way in for an attacker, measures to build in security increase the costs to the attacker and may help shift attackers away from the cyber under-resourced.
You can download a copy of Internet of Things: Embedded Security Guidance at https://www.cisecurity. org/insights/white-papers/internet-of-things-embedded-securit y-guidance

If you’re an organization, you can begin the conversation with your vendors on embedded IoT security requirements for your products. You can specifically use this document as an educational tool and potentially provide it as a guide for the vendor. Currently, the burden for IoT security fully rests with you, where it’s your responsibility to add on security to protect products and services using resources such as the CIS Controls v8 Internet of Things Companion Guide. By embedding security and changing the expectations for security to be built in, we may be able to reduce the overall costs for security as well as reduce the distributed management burden.
We want to hear from the community and understand if this white paper is helpful. We’re also interested to learn
Kathleen Moriarty, Chief Technology Officer at the Center for Internet Security has over two decades of experience. Formerly as the Security Innovations Principal in Dell Technologies Office of the CTO, she worked on ecosystems, standards, and strategy. During her tenure in the Dell EMC Office of the CTO, Moriarty had the honor of being appointed and serving two terms as the Internet Engineering Task Force (IETF) Security Area Director and as a member of the Internet Engineering Steering Group from March 2014-2018. She is a 2020 Tropaia Award Winner for Outstanding Faculty at Georgetown University School of Continuing Studies and was recognized in the book, “Women Know Cyber: 100 Fascinating Females Fighting Cybercrime,” published by Cybersecurity Ventures. Moriarty has over twenty years of experience driving positive outcomes across information technology leadership, IT strategy and vision, information security, risk management, incident handling, project management, large teams, process improvement, and operations management in various roles with MIT Lincoln Laboratory, Hudson Williams, FactSet Research Systems, and PSINet. She holds a Master of Science degree in Computer Science from Rensselaer Polytechnic Institute, as well as, a Bachelor of Science degree in Mathematics from Siena College.
12 Cybersecurity Quarterly
If security is built in, enabled by default, and managed at scale by the vendor, the overall security landscape will improve.

Essential Cyber Hygiene: Making Cyber Defense Cost Effective
Developing an effective cyber defense strategy sounds like a monumental and resource-intensive task; our new guide illustrates that it can actually be realistic and cost effective, regardless of your organization’s size and resources.
By Valecia Stocchetti
Strengthening your cyber defenses can be a daunting task. Where do you start? Which tools do you use? How much will it cost? And what do you risk losing if you do nothing? It’s not always easy to answer these questions, but in the absence of definitive answers, you may struggle to grow your cybersecurity maturity and leave yourself exposed to cyber attacks.
The CIS Critical Security Controls (CIS Controls) team has published a guide, The Cost of Cyber Defense: Implementation Group 1 (IG1), to help you answer those questions. The purpose of the guide is to provide enterprises such as yours with a real-world view into how realistic and cost effective it can be to achieve essential cyber hygiene, as embodied in Implementation Group 1 (IG1) of the CIS Controls. This information will help individuals with any level of expertise to make informed and prioritized decisions for strengthening cyber defense. Several different audiences can benefit from this guide, too, including members of the executive team (e.g., CEO, CFO, CISO, CIO) and IT administrators.
What You Risk if You Do Nothing
The risk of a cyber attack on an enterprise is greater than ever before. Devices are constantly being added to networks, increasing the digital footprint and providing more opportunities for an attacker to exploit weaknesses in those devices. Enterprises of all sizes are at risk of a cyber attack; however, small- and medium-sized enterprises (SMEs) often have more risk due to small budgets and limited resources. According to a 2021 report published by Accenture , 43% of cyber attacks target small businesses, yet only 14% of SMEs are prepared to defend against an attack.
Depending on the severity of a cyber attack, recovery costs can range from thousands to millions of dollars. The damages depend on the nature of the attack, including the breadth and depth, as well as how long the attacker remained on the network (e.g., days, months, years). For some enterprises, the cost of recovery from a cyber attack might be a significant portion of their budget, if not their entire annual revenue. Some enterprises have even gone out of business after experiencing a cyber attack. According to a report published by Cisco, “60% of small- and medium-sized businesses go out of business within six months of a cyber attack.”
Where You Can Start: Essential Cyber Hygiene at a Reasonable Cost
Every enterprise wants a reasonable starting point at a reasonable cost for cybersecurity. The CIS Controls are a prioritized set of actions that you can implement to create an effective cyber defense program. The key word here is prioritized.
14 Cybersecurity Quarterly
The purpose of The Cost of Cyber Defense: Implementation Group 1 (IG1) is to provide enterprises such as yours with a real-world view into how realistic and cost-effective it can be to achieve essential cyber hygiene, as embodied in Implementation Group 1 (IG1) of the CIS Controls.
CIS recommends starting with IG1 of the CIS Controls, as this subset constitutes what’s known as “essential cyber hygiene” for any enterprise. It includes a ‘“must do”’ list of actions that you can use to build a foundation for implementing more complex countermeasures later on. For example, larger enterprises that face more sophisticated adversaries and protect more sensitive data or services can move on to implement Safeguards in Implementation Group 2 (IG2) and/or Implementation Group 3 (IG3).
Tools to Help You Along the Way
IG1 consists of 56 actions, which are called Safeguards. This does not mean you need to deploy 56 individual tools in order to implement IG1. In fact, you can accomplish many of the Safeguards using one or a few tools. To pare down the Safeguards in IG1 into a digestible format, we chose 10 categories (e.g., Asset Management, Data Management) to represent the 18 Controls. From there, we created a set of generic tool types along with the policies needed to support them and mapped them to IG1 Safeguards. These tools are not vendor-specific; they’re general in that they group Safeguards together that require similar tooling. For example, obtaining an “Enterprise and Software Asset Inventory Management Tool” can be used to satisfy Safeguards 1.1, 1.2, 2.1, 2.2, 2.3, 9.1, and 12.1.
Your enterprise may already have the tools in place (or can easily add on to pre-existing platforms) to implement some of the Safeguards in IG1. For example, if you’re using Microsoft products, you may already have the built-in or added capabilities (e.g., BitLocker, Active Directory) to achieve many of these actions.
Enterprises may also consider other factors during tool selection, such as whether the implementation process is manual or automated. For example, an enterprise may choose to use a spreadsheet to track enterprise assets and software. However, as that enterprise grows, they may make the decision to move to an automated tool for inventory, adding to the cost
All tools come with a cost. If an enterprise chooses to select all no-cost or open-source software, they may be spending more on vulnerability management or labor to ensure that the software is safe to use. On the other hand, if an enterprise chooses to use a commercially-supported tool, they may be spending more on renewal costs, support costs, or integration costs. It is important not to get distracted with the tool and instead, focus on the activity. Enterprises can then find the tool that best fits their needs.
How Much It Will Cost You

When it comes to dollars and cents, the industry as a whole has made many attempts to calculate the cost of a cyber attack. The same can’t be said about estimating the costs of implementing cyber defenses. But there’s value in knowing both of those metrics. Knowing what an enterprise can spend to prevent an attack is helpful when you know what they’re willing to spend to recover from an attack. For example, if the cost of recovering from a cyber attack is $1.25 million but an enterprise can spend only $1 million on implementing a set of robust cyber defenses, which one should they choose?
To estimate the cost of IG1 Safeguards, we looked at the cost of licensing commercial versions of the tools that an enterprise needs to implement each of the 10 categories. Tools are priced in many ways, the most common being the following: by number of employees, users, workstations/servers, and/or by usage (e.g., megabyte, gigabyte, hours). To try and simplify this pricing and also
Fall 2023 15
To estimate the cost of IG1 Safeguards, we looked at the tools that an enterprise needs to implement them... Our estimate shows that obtaining and deploying commerciallysupported versions of the tools should be less than 20% of the Information Technology (IT) budget for any size enterprise.
provide deeper insight for enterprises of different sizes, CIS created IG1 Enterprise Profiles to help streamline the process of calculating costs.
Our estimate shows that obtaining and deploying commercially-supported versions of the tools should be less than 20% of the Information Technology (IT) budget for any size enterprise. Even with adding in the overhead of implementing the necessary policies to support them, IG1 Safeguards can provide a reasonable, necessary, and effective starting point for cybersecurity by any enterprise. Our findings reinforce what we already thought to be true – an enterprise can implement the Safeguards in IG1 for a relatively low cost, and the Safeguards constitute a foundational and achievable set of security actions for even the smallest of enterprises.
How to Use Our Cyber Defense Guide
This guide has five main sections.
1. The first section describes our methodology for estimating the cost of implementing IG1 for enterprises of different sizes.
2. The second section briefly discusses the Safeguards themselves.
3. The third section outlines the IG1 Enterprise Profiles.
4. The fourth section identifies the types of tools needed to implement the Safeguards.
5. Finally, the fifth section estimates the cost of deploying the tools for the three different IG1 Enterprise Profiles.
Practitioners can find valuable information in the appendices of this guide that help to further break down the cost for each tool as well as provide some insight into several considerations while procuring these tools. Additionally, a spreadsheet is available for users to download if they wish to use it for budgeting and/or implementation purposes.
This guide is a starting point to answer many questions that enterprises want answered when implementing defenses. The most important thing is that enterprises start now. Do not wait to become a victim of a breach or incident. Use the information in this guide to help make informed and prioritized decisions to get the defenses in place before an incident occurs.
Ready to see how cost-effective it is to implement IG1?

Download our new guide, The Cost of Cyber Defense: Implementation Group 1 (IG1), at https://www.cisecurity. org/insights/white-papers/the-cost-of-cyber-defensecis-controls-ig1
Valecia Stocchetti is the Information Security Audit Manager at the Center for Internet Security, Inc. (CIS®), where she evaluates and manages the control implementation within CIS and measures compliance to internal standards and best practices. Previously, she was a Senior Cybersecurity Engineer on the CIS Controls team where she worked with various attack models and other datasets, including MITRE ATT&CK, to help validate and prioritize the CIS Controls. There, she led and contributed to multiple projects including the CIS Community Defense Model (CDM), the CIS Cost of Cyber Defense: IG1, and the Blueprint for Ransomware Defense. Stocchetti also led the Computer Incident Response Team (CIRT) at the MultiState and Elections Infrastructure Information Sharing and Analysis Centers (MS-ISAC® and EI-ISAC®), spearheading multiple forensic investigations and incident response engagements for the MS- and EI-ISAC’s state, local, tribal, and territorial (SLTT) community. Stocchetti came to CIS from the eCommerce field where she worked complex financial fraud cases. She holds multiple certifications, including GIAC Certified Forensic Examiner (GCFE), GIAC Certified Forensic Analyst (GCFA), and GIAC Security Essentials Certification (GSEC). Stocchetti earned her Bachelor of Science degree in Digital Forensics from the University at Albany, State University of New York. She is currently pursuing a master’s degree in information security at Champlain College.
16 Cybersecurity Quarterly

CybersideChat

Security Training and Awareness…and You!
By Stephanie Gass, Director of Governance, Risk & Compliance, CIS
With Cybersecurity Awareness Month nearly here, it is time to think about training and awareness programs for your teams and organization. Most malicious attacks and threats require an element of human interaction. In an ever-evolving threat landscape, it is crucial to understand the overall requirements that organizations need to establish a robust security training and awareness program that can keep your employees on top of the latest threat vectors and vulnerabilities.
Training and awareness need to be ongoing activities for organizations, as they complement a complete protection plan for your organization’s “crown jewels,” such as data and
the systems and networks in which it resides. The training program creates awareness for individuals on what is important to the organization, individuals’ roles and responsibilities, and their duties in identifying potential threats and escalation procedures. There are many ways to incorporate training and awareness throughout the year using module-based training, phishing campaigns, role-based training, newsletters, town halls, and, if you are in the office, the use of visual aids. When training and awareness is ongoing, it fosters the growth of a security culture and illustrates the importance at all levels of the organization.
Equally important is for the individuals of your organization to realize this training not only aids them in their jobs but also in their home life. No one wants to believe they will be a victim of cybercrime, but the reality is we are surrounded by constantly evolving technology and ever-present connectivity. Focusing on the greater benefit of cybersecurity awareness in all aspects of life will help to contextualize training towards practical application of cybersecurity best practices.
Some topics worthy of consideration for security awareness training should include security culture, authentication, public Wi-Fi, social engineering, security while traveling, malware and
current threats, privacy, and device security. Protecting against cyber threats is critical. By creating training that is engaging, requires interactions, and utilizes real-world scenarios to effectively influence security behaviors, your organization minimizes risk and builds upon the ideal of a strong security culture.
Be mindful that security training and awareness does not need to cost a lot of money to be effective. Free resources in this training space that your organization can utilize are plentiful. As an example, you check out some excellent resources curated by CISA here: https://www.cisa.gov/ resources-tools . Newsletters and communication campaigns should be used as short segments of best practice guidance to serve as a reminder. Town halls need a security advocate and evangelist to speak to the importance of security and security culture. Advocacy does not need to rely solely on cybersecurity team members; encourage champions from other parts of the organization to go out and speak to their teams and business units about what security means to the organization.
At the end of the day, it is important for everyone at an organization to understand that security is everyone’s responsibility.
18 Cybersecurity Quarterly
Training and awareness need to be ongoing activities for organizations, as they complement a complete protection plan for your organization’s “crown jewels,” such as data and the systems and networks in which it resides.
Achieving Operational Excellence by Automating IT Security Auditing
Completing a thorough IT security audit can be a time-consuming and resourceintensive task. Integrating automation into the process can help make auditing faster, easier, and more effective.
 By Elizabeth Wu
By Elizabeth Wu
In today’s complex business landscape, IT audits often cause frustration, resentment, and high-pressure situations within organizations due to their disruptive nature. Preparing for IT audits requires collecting and creating policies and processes, referencing each control of the audit framework. Working closely with IT auditors, every control is meticulously followed to achieve compliance. The result, after months of effort, is a certification suggesting the organization is secure at the time of verification. However, this raises the critical question: Does an IT audit and its security compliance certification effectively prevent data breaches?
Despite these certifications, data breaches continue to plague organizations, as evidenced by staggering statistics. Approximately 85% of businesses with fewer than 1,000 employees and 60% of larger corporations still fall victim to cyber intrusions . Even with extensive IT staff and thorough audits, it becomes clear that these measures are often insufficient in preventing data breaches.
In the ever-evolving tech landscape, a transformative shift is underway that’s revolutionizing the core of IT security audits. Led by the next generation of IT auditors, this paradigm shift embraces technology to create an automated baseline of security status across 600 data points within just 24 hours after deployment. This shift is pivotal in the ongoing battle to prevent and avoid data breaches, a challenge where previous software solutions have failed, as it points to exactly where the vulnerabilities are.
The Evolution of IT Security Auditing
To comprehend the significance of this transformation, it’s essential to recognize how IT security auditing has not evolved in the last 60 years. Traditional IT audits are labor-intensive, requiring months of preparation and cooperation across various departments. Employees from IT and other business units were often burdened with creating and documenting policies and processes. The painstaking process of aligning every control with these policies was a time-consuming endeavor.
The outcome of these efforts was a snapshot of compliance at the moment of verification. However, this static approach to IT auditing posed significant limitations. It couldn’t adapt to the rapidly changing threat landscape where new vulnerabilities emerge daily. Consequently,
Fall 2023 19
This raises the critical question: Does an IT audit and its security compliance certification effectively prevent data breaches?
organizations certified as secure at one point in time remained vulnerable until the next audit.
The Rise of Automated IT Security Auditing
The integration of an automated IT security auditing process establishes a baseline either at one location or all locations displayed in a dashboard in near-realtime. This automation empowers IT auditors to engage in proactive, fact-based dialogues with business units that are fueled by faster, measurable, and accurate data insights.
The Broader Paradigm Shift
While the technical advancements of automated IT security auditing are remarkable, its impact transcends IT departments. Companies that embrace this paradigm shift position themselves at the forefront of technological advancement. They foster a culture of proactive engagement with business units, enabling swift and accurate vulnerability remediation.

One of the most significant advantages of automated auditing is how it fosters transparency between IT and business units. Resource allocation becomes more efficient, and the organization gains peace of mind knowing that its security posture is continuously monitored.
The Ripple Effect of Benefits
The benefits stemming from this paradigm shift are extensive and encompassing:
1. Cost Savings: Automated auditing drastically reduces the time and resources required for assessments, channeling these savings toward initiatives that foster growth and innovation.
2. Elevated Stakeholder Confidence: The embrace of automated continuous compliance fosters unwavering confidence in the perpetual safeguarding of an organization’s digital assets, extending trust to investors, partners, and customers.
3. Empowered System Administrators: Automation liberates system administrators from the burden of routine checks, allowing them to focus on optimizing systems, enhancing performance, and responding to critical incidents without the encumbrance of manual audit tasks.
4. Competitive Edge: Organizations that adopt automated auditing distinguish themselves by showcasing their commitment to cutting-edge technology
and robust cybersecurity practices, thereby establishing themselves as industry leaders.
The Path Forward
The revolution in IT security auditing, driven by automation and continuous compliance, has opened new frontiers for organizations seeking to fortify their IT ecosystem. To thrive in this age of technological evolution, companies must embrace this paradigm shift as a strategic imperative.
You can start by evaluating your organization’s readiness to oppose the status quo of pre-existing model solutions and activities in exchange for automated auditing based on internal data facts. Engage with the system administrators in the field to understand how this evolution can benefit your specific operations. By taking proactive steps now, you can lay the foundation for stability, security, and a prosperous future in the digital landscape.
The time for action is now; the age of technological transformation awaits your command. Embrace automated IT security auditing, and you will not only protect your organization against data breaches but also position yourself as a leader in the ever-evolving digital realm.
Elizabeth Wu is a Canadian entrepreneur who is Founder and CEO of Cybersecurity Auditing Technologies Inc. (CAT Inc.). After 20 years of experience in IT security auditing and consulting working on behalf of the business, Wu and her team have created the only automated IT security auditing platform that continuously measures the vulnerabilities of an IT ecosystem. CAT’s mission is to reduce the number of data breaches by empowering business leaders with IT auditing facts and improve accountability and transparency in their IT departments. With their platform, organizations are able to avoid up to 80% of cyber attacks and turn cyber risk into cyber confidence.
20 Cybersecurity Quarterly
ISACUpdate

Reflecting on the 2023 Annual ISAC Meeting
By Karen Sorady, Vice President of Stakeholder Engagement, MS-ISAC
In August, MS-ISAC members gathered in the beautiful city of Salt Lake City, Utah, for the 16th Annual MS-ISAC Meeting. Surrounded by the Wasatch Mountains, this was the biggest and best-attended Annual Meeting to date, comprised of a variety of sponsors and 810 attendees representing all 50 states, 10 CISA regions, and 18 different SLTT sectors, including elections, K-12, higher education, public utility, health, transportation, public safety, judiciary, and more.
This year’s meeting included eight networking opportunities and 83 sessions covering a myriad of topics, including document analysis, incident response, how to collaborate with other state entities, cyber hygiene, how to get the most out of the MS-ISAC membership, and many others. There was a little something for everyone, no matter the size of the organization, the sector, or whether their role is technical or non-technical. Attendees were treated to a historic retrospective of the MS-ISAC by some of the membership’s founding members. Everyone had the opportunity to celebrate the 20th anniversary of the MS-ISAC’s foundation and the fifth anniversary of the EI-ISAC.
Incorporating feedback from last year’s attendees, we were able to create a unique, engaging, and informative experience. Feedback revealed that attendees wanted more opportunity to make real connections and
build new relationships with peers within their state and across the nation, so many of this year’s sessions were peer-focused. We wanted to give members the opportunity to network and hear from their peers, so we ensured there were many presenters from the SLTT community.
The popular Regional Sessions returned this year, giving attendees the opportunity to network with others in their own and neighboring regions. We also incorporated more opportunities to engage with our federal partners in the Regional Sessions, providing attendees with the opportunity to connect with the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA) Joint Cyber Defense Collaborative, National Institute of Standards and Technology, and the Integrated Operations Division.
We also brought back service rooms, which afforded attendees the opportunity to have one-on-one meetings with ISAC, CISA, and CIS representatives to ensure that members are getting the most out of their membership. We also hosted additional sector-based community sessions, including K-12, tribal, and state Chief Information Security Officers to allow members to share best practices and connect with peers who are facing many of the same challenges in other parts of the nation.
Additionally, we hosted a Women in Cyber event, which was well received by those who attended.
The Annual ISAC Meeting is more than an opportunity for attendees to hear from CIS and keynote speakers – it’s an opportunity to connect and share real-world stories and valuable information with cybersecurity peers in similar organizations and roles who experience similar challenges. The 2024 Annual Meeting, scheduled for June 24-26, is already in the works. In the meantime, we’ll continue to search for networking and community opportunities for our members. We encourage members to share feedback to continue to add value and improve the overall experience of the Annual ISAC Meeting. We have already started building out an agenda based on our members’ suggestions, both from survey data collected following the event and from polling at the August monthly call. We will touch on topics including emerging technologies, assessing risks, and improving purchasing power through collaboration and even more sector-specific tracks.
If you’d like to be involved in the content planning, let us know by emailing us at info@cisecurity.org and spread the word about next year’s annual meeting to your colleagues!
Fall 2023 21
UpcomingEvents

October
October 3
LogicalNet is hosting the 2nd Annual Cybersecurity Symposium at Rivers Casino & Resort in Schenectady, New York. The event will bring together leading national security experts to share concrete advice on protecting your business. Attendees will learn about industry standard best security practices, how to obtain the best cyber insurance at competitive pricing, and new threats like AI-driven voice hacking. Learn more at https://logical. net/cyber2023/.
October 3 - 4
The State of Montana will host the Montana Local Government IT Conference in Missoula, Montana. The event will bring together local government IT leaders and professionals from across the state to learn about important topics of interest and network with peers. MS-ISAC Director for Cybersecurity Advisory Services Jason Emery will lead a session on cybersecurity resources for local government.
October 4
Cyber Security Summit: Charlotte will take place at The Westin Charlotte in Charlotte, North Carolina. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. CIS Senior Cybersecurity Engineer Eric Pinnell will lead a panel discussion at the event on ransomware. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ charlotte23/.
October 4 - 5
The Harrisburg University of Science and Technology will host the Harrisburg University Cybersecurity Summit at its campus in Harrisburg, Pennsylvania. Hosted in partnership with the Commonwealth of Pennsylvania, County Commissioners of Pennsylvania, and Central Susquehanna Intermediate Unit 16, the event will bring together security leaders and experts from state and local government, federal agencies, K-12 school districts, higher education, and the private sector to learn about and discuss current topics and issues in the cybersecurity industry. MS-ISAC Regional Engagement Manager Megan Incerto will speak at the event and discuss cybersecurity resources for SLTT entities. Learn more at https://summits.harrisburgu.edu/ cybersecurity/.
October 5
MassCyberCenter will host its 3rd Annual Massachusetts Municipal Cybersecurity Summit at Mechanics Hall in Worcester, Massachusetts. The event aims to help municipal leaders and other officials from the Commonwealth’s 351 municipalities improve their cybersecurity programs. This year’s event will focus on the theme “Be a Cybersecurity Hero” to highlight the importance of building a culture of cybersecurity. The MS-ISAC team will be at the summit sharing their no-cost and low-cost cybersecurity resources for local government. Learn more at https://masscybercenter. org/2023-massachusetts-municipalcybersecurity-summit .
October 8 - 11
The National Association of State Chief Information Officers (NASCIO) will host the NASCIO 2023 Annual Conference at the Hyatt Regency Minneapolis. The event will bring together state CIOs, their staff, and other state technology officials from across the country to consider the future of technological innovation in state government. Attendees will network with their peers, learn about the latest topics of interest from industry experts, and collaborate with partners. Learn more at https:// www.nascio.org/conferences-events/ annual-conference/.
October 9 - 13
The Association of County and City Information Systems (ACCIS) will host the 2023 ACCIS Fall Conference at the Kitsap Conference Center in Bremerton, Washington. The event will bring together Chief Information Systems Officers and other local government IT leaders from counties and municipalities from across the State of Washington to connect with peers, share their knowledge and experiences, and learn about pressing issues and topics from industry thought leaders. MS-ISAC Regional Engagement Manager Michelle Nolan will lead a session at the event on cybersecurity resources for local governments. Learn more at https://www.accis-wa.org/.
22 Cybersecurity Quarterly
October 19 - 20
Colorado State University Pueblo will host the Southern Colorado Regional Cybersecurity and IT Conference at its campus in Pueblo, Colorado. The event will bring together government IT leaders and professionals from across the state to learn from industry leaders, network with peers, and discover new solutions to strengthen their cybersecurity programs. MS-ISAC Regional Engagement Manager
Michelle Nolan will lead a session at the conference on cybersecurity resources for local government and the benefits of participating in the Nationwide Cybersecurity Review (NCSR).

October 20
The Connecticut Education Network (CEN) and the Connecticut National Guard will host Cyber Nutmeg 2023 at Central Connecticut State University in New Britain, Connecticut. The one-day event is designed to help state, local, and education leaders heighten their awareness of cybersecurity threats and learn about defenses they can deploy to protect their organizations. MS-ISAC Regional Engagement Manager
Elijah Cedeno will lead a session on cybersecurity resources for state and local governments and K-12 schools. Learn more at https://ctedunet.net/ engagement-events/
October 20
Cyber Security Healthcare & Pharma Summit will take place virtually. It will bring together business leaders and cybersecurity professionals in the healthcare industry to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ healthcare23/.
October 25 - 27
The Michigan Association of Educational Data Systems (MAEDS) will host the 2023 MAEDS Annual Fall Conference at the Grand Traverse Resort and Spa in Acme, Michigan. The conference will offer attendees from the state the opportunity for professional growth, networking with colleagues, and learn about new resources. MS-ISAC Regional Engagement Manager Heather Doxon will lead a session at the event and discuss cybersecurity resources for K-12 schools. Learn more at https://www.maeds.org/index.php/ fall-conference/.
October 25 - 27
The International Information System Security Certification Consortium (ISC)2 will host the 13th Annual (ISC)2 Security Congress at the Gaylord Opryland Resort in Nashville, Tennessee. It will bring together cybersecurity professionals in every phase of their career – from (ISC)2 Candidates to seasoned CISOs – through engaged learning that builds the competence and confidence to lead. Attendees will experience industry-leading education, five visionary keynotes, exclusive networking, new career resources, exhibitor showcases, and more. Learn more at https://www.isc2. org/professional-development/events/ congress-2023
October 27
Cyber Security Summit: Columbus will take place at The Renaissance Columbus Downtown Hotel in Columbus, Ohio. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. CIS Senior Cybersecurity Engineer Eric Pinnell will lead a panel discussion at the event on ransomware. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ columbus23/.
Fall 2023 23
November
November 1

Cyber Security Summit: Scottsdale will take place at The Phoenician in Scottsdale, Arizona. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. CIS Cybersecurity Engineer Justin Brown will lead a panel discussion at the event on ransomware. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ scottsdale23/.
November 7 - 8
The Florida Municipal Electric Association (FMEA) will host the FMEA Energy Connections Conference and Trade Show at the DoubleTree by Hilton Hotel Orlando at SeaWorld in Orlando, Florida. The event will bring together technical personnel and leaders from the state’s public power organizations to network with peers, learn about trending issues in the industry, and discover new solutions to improve their operations. The MS-ISAC team will be at the event sharing our no-cost and low-cost cybersecurity resources for public utilities. Learn more at https://www.flpublicpower.com/ events/energy-connections-conference.
November 10
Cyber Security Summit: Dallas will take place at the Sheraton Dallas Hotel in Dallas, Texas. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. CIS Cybersecurity Engineer Justin Brown will lead a panel discussion at the event on ransomware. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ dallas23-nov/.
November 14
Cyber Security Summit: Boston will take place at The Westin Copley Place in Boston, Massachusetts. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. CIS Chief Technology Officer Kathleen Moriarty will lead a panel discussion at the event on ransomware. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/boston23/.
November 15 - 17
The Kentucky Association of Counties (KACo) will host the 49th Annual KACo Conference and Exposition at the Central Bank Center in Lexington, Kentucky. The event is the premiere conference for county officials in Kentucky. It will feature keynote speakers, breakout sessions, and ample opportunities for networking with county colleagues. The MS-ISAC team will be at the conference sharing our no-cost and low-cost cybersecurity resources for local governments. Learn more at https://conference.kaco.org/.
November 16 - 18
National League of Cities (NLC) is hosting the NLC City Summit at the Georgia World Congress Center in Atlanta, Georgia. This event allows attendees to connect with local leader peers from across the country, policy experts, and industry professionals to gain knowledge and expand their network. It is a great opportunity to make new connections, access resources, and gain knowledge that will help you and your municipality thrive. Learn more at https:// citysummit.nlc.org/.
November 17
Cyber Security Summit: New York will take place at the Sheraton New York Times Square Hotel in New York City. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. CIS Senior Cybersecurity Engineer Eric Pinnell will lead a panel discussion at the event on cloud security. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ newyork23-nov/.
November 30
Cyber Security Summit: Los Angeles will take place at The Beverly Hilton in Beverly Hills, California. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ losangeles23/.
24 Cybersecurity Quarterly
November 26 - December 1
AWS re:Invent will take place in Las Vegas across multiple venues along the Las Vegas Strip. The event brings cloud enthusiasts together from around the world to hear the latest cloud industry innovations, meet with AWS experts, have fun, and build connections. The week-long event will give attendees the opportunity to gain knowledge from over 2,000 interactive, expert-led sessions, learn about innovative solutions from hundreds of solution vendors, and network with peers at dozens of fun activities and events. On Wednesday, November 29th at 10:30 a.m. PT, CIS Product Manager for Cloud and Benchmarks Mia LaVada and Qualys Vice President of Product Management Nayeem Islam will deliver a Lightning Talk in the Security Zone on the expo floor in which they’ll discuss how to securely configure AWS workloads. Additionally, the CIS team will be at Booth 1678 in the Security Zone, where they’ll share our security resources for working in AWS environments. Learn more at https://reinvent. awsevents.com/.
November 29 - December 1
The Tennessee Educational Technology Association (TETA) will host the 2023 Annual Tennessee Educational Technology Conference at the Embassy Suites by Hilton in Murfreesboro, Tennessee. The conference will feature administrative, technical, and curriculum tracks specifically designed by educators from both public and independent schools in Tennessee. The MS-ISAC team will be at the conference sharing our no-cost and low-cost cybersecurity resources for public schools. Learn more at https:// www.teta.org/37196.
December
December 6
Cyber Security Summit: Jacksonville will take place at the Sawgrass Marriott Golf Resort and Spa in Ponte Vedra Beach, Florida. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https:// cybersecuritysummit.com/summit/ jack sonville23/.
December 7
Cyber Security Summit: Houston will take place at the Westin Houston Memorial City in Houston, Texas. It will bring together business leaders and cybersecurity professionals to learn about the latest cyber threats. Through our partnership, SLTT entities can receive free admission. Contact the CIS CyberMarket team for more details. Learn more at https://cybersecuritysummit.com/ summit/houston23/.
December 10 – 13
The Georgia Association of Voter Registration and Election Officials (GAVREO) will host the GAVREO Annual Conference at the University of Georgia in Athens, Georgia. The conference is designed to improve election administration and voter registration among municipal, county, and state election officials. It will offer sessions to provide election officials with guidance and best practices on how to navigate a successful election. Senior Director of the EI-ISAC Marci Andino will lead a session on the threat landscape for the 2024 elections and no-cost cybersecurity resources for election agencies. Learn more at https://cviog.uga.edu/ training-and-education/conferences/ elections-officials-and-voterregistrars.html.

Fall 2023 25

Interested in being a contributor? Please contact us: cybermarket@cisecurity.org www.cisecurity.org 518.266.3460 CIS CyberMarket cisecurity.org info@cisecurity.org 518-266-3460 Center for Internet Security @CISecurity TheCISecurity cisecurity




















 By Elizabeth Wu
By Elizabeth Wu




