

SUSTAINABLE SUPPLY CHAINS TO SERVE AMERICA







VADM William A. Brown, USN (Ret.) President & CEO
COL Craig Hymes, USA (Ret.)
Senior VP, Operations
Claudia Ernst Director, Finance and Accounting
Lee Matthews VP, Marketing and Corporate Development

Membership Manager
Executive Assistant to the President & CEO
For a listing of current Committee Chairpersons, Government Liaisons, and Chapter & Regional Presidents, please visit the Association website
The editorial objectives of the Defense are to advance knowledge and science in defense logistics and transportation and the partnership between the commercial transportation industry and the government stimulates thought and effort in the areas of defense transportation, logistics, and distribution by providing readers with:
News and information about defense logistics and transportation issues
New theories or techniques
Information on research programs
Creative views and syntheses of
Articles in subject areas that have significant current impact on thought and practice in defense logistics and transportation
Reports on NDTA Chapters
Defense Transportation Journal is designed as a forum for current research, opinion, and identification of trends in defense transportation and logistics. The opinions expressed are those of the authors and not necessarily of the Editors, the Editorial Review Board, or NDTA.
rchives are available to members on , Managing Editor, DTJ
50 South Pickett Street, Suite 220 Alexandria, VA 22304-7296
703-751-5011 • F 703-823-8761
The National Defense Transportation Association Foundation recognizes our most special donors for their gracious financial support to academic scholarships supporting our future logistics and transportation leaders.
Contribution over $100K
Contribution $25K - $49,999



Reliable, Sustainable, and Safe!










February 2025 • Vol 81, No. 1
PUBLISHER
VADM William A. Brown, USN (Ret.)
MANAGING EDITOR
Barbara Parus | bparus@ndtahq.com
CIRCULATION MANAGER Leah Ashe | leah@ndtahq.com
PUBLISHING OFFICE
NDTA
50 South Pickett Street, Suite 220 Alexandria, VA 22304-7296 703-751-5011 • F 703-823-8761
GRAPHIC DESIGN & PRODUCTION MANAGER
Susan Hill
ADVERTISING SALES DIRECTOR Bob Schotta bschotta@cjp.com
ADVERTISING & PRODUCTION
Carden Jennings Publishing Co., Ltd. Custom Publishing Division 375 Greenbrier Drive, Suite 100 Charlottesville, VA 22901 434-817-2000 x330 • F 434-817-2020
Defense Transportation Journal (ISSN 0011-7625) is published bimonthly by the National Defense Transportation Association (NDTA), a non-profit research and educational organization; 50 South Pickett Street, Suite 220, Alexandria, VA 22304-7296, 703-751-5011. Copyright by NDTA. Periodicals postage paid at Alexandria, Virginia, and at additional mailing offices.
SUBSCRIPTION RATES: One year (six issues) $40. Two years, $60. Three years, $75. To foreign post offices, $45. Single copies, $6 plus postage. The DTJ is free to members. For details on membership, visit www.ndtahq.com.
POSTMASTER: Send address changes to: Defense Transportation Journal
South Pickett Street, Suite 220 Alexandria, VA 22304-7296

VADM William A. Brown, USN (Ret.) NDTA President & CEO
Greetings and Happy New Year!
One thing is certain: 2025 will be filled with decidedly interesting developments— economically and geopolitically. Change management will be essential for adapting to technological advances, market dynamics and customer expectations. This idea led us, in coordination with the Defense Travel Management Office and General Services Administration, to adopt our 2025 GovTravels theme, “Change Management: Challenges & Solutions in Government Travel.” Without managing change, organizations will be playing “catch up” as new waves of technology, regulations, and culture come into play.
This issue of the DTJ will explore how effective change management can improve efficiency, reduce costs, and transform our approach to challenges within the military, government, and travel industry. My strong advice is that in times of rapid change across a plethora of factors affecting business and technology, we should communicate effectively and often to ensure trust remains strong across our transportation and logistics enterprise—remembering, of course, that our mission is in support of national security.
Cybersecurity and cyber hygiene continue to be woven into basic business processes. Bad actors continue to steal information and treasure from honest businesses and individuals. Also, in this issue of the DTJ, we are highlighting two articles on DoD’s final version of the
Cybersecurity Maturity Model Certification (CMMC) Program, which small businesses need to implement by the third quarter 2025.
Regarding national security and U.S. interests on the world stage, the complexity of geopolitical issues and relationships is likely at an inflexion point. We have several years’-long conflicts raging and the risks of swift escalation could come in the form of a pandora’s box full of potential surprises. For example, we were caught off guard by the Houthis’ control of a strategic choke point. Being prepared to react effectively to these types of situations will be the key.
We often hear the adage: “We don’t want to fight a fair fight—we want to overwhelm any adversaries—on multiple fronts.” This will take the will of our nation to accomplish as we have been winding our way further behind as a nation. The challenges will be significant as we rebuild our U.S.-flagged fleet, as an example. An optimistic and strong economy will be essential to tackle these challenges. A strong
CHAIRMAN’S CIRCLE
• Global Critical Logistics
• UPS (Upgrade)
PRESIDENT’S CIRCLE
• Geodis Transportation Solutions
• GMR Transport LLC
SUSTAINING
• Applied Research Associates
• HV Logistics
• Hylant
• Island Hospitality Management
• Lansdowne Coach LLC
• Synergy Global Housing
• VisionSafe
UNIVERSITIES
• John D. Odegard School of Aerospace Sciences
• McKendree University
• Purdue University WELCOME
and optimistic NDTA family is essential as part of the solution. Our engagement and encouragement as an influential association affiliated with progress, engagement, ideas, and solutions are needed now, more than ever in our 80-year history.
Wishing you great success in staying the course while you navigate this year of change at home and globally. Please feel free to reach out to me or the NDTA staff at any time! DTJ


A recognized industry
provides safe, secure, reliable transportation services delivered by our unique network of independent agents and capacity providers.
• One of the industry’s largest van and platform selections with over 85,600 truck capacity providers in network
• Expedited cargo vans, straight trucks and tractor-trailers
• More than 18,000 pieces of trailing equipment
• 9,000 owner-operators leased to Landstar with over 1,250 stepdecks and 970+ flatbed trailers
• Drop and hook services
• Specialty trailers ranging from beam, blade and Schnabels to double drop, stretch and multi-axles
• Secure, dedicated government services with more than 350 AA&E secret cleared teams
• Hazmat certified owner-operators
• Unit moves with on-site carrier representative







By Tabatha Ward, Executive Vice President of Growth, ROGERCO, Inc.
The Defense Industrial Base (DIB) has long been a cornerstone of national security, ensuring the United States maintains a competitive edge in global defense capabilities. As a critical component of the DIB, defense transportation contractors are pivotal in mobilizing and sustaining military operations.
The Cybersecurity Maturity Model Certification (CMMC) 2.0, finalized in October 2024, is a comprehensive tiered framework that integrates industry-standard best practices, including National Institute of Standards and Technology’s (NIST) NIST 800 and NIST 800-172, to safeguard data within the defense supply chain. In fact, CMMC certification and compliance is a mandatory requirement for defense contractors seeking to do business with the Department of Defense (DoD).
But, more than a compliance requirement, CMMC also is a strategic business enabler that strengthens the position of defense transportation contractors. It ensures that contractors adopt a risk-based
approach to cybersecurity that can open potential business opportunities by differentiating them from competitors who may not be compliant.
CMMC certification provides defense transportation contractors with tangible advantages that strengthen both operations and business outcomes by:
Protecting supply chain security. Transportation contractors manage logistics systems, shipment tracking, and supply chain operations. A breach in these systems could lead to delayed deployments or compromised missions.
We know the security of the supply chain is only as secure as its weakest link. As threat vectors increasingly overlap operational technology (OT) and information technology (IT) operations, even the largest contractors can be affected by incidents targeted at the least sophisticated suppliers.
Organizations that invest in robust cybersecurity see a 27% reduction in down-
time following cyber incidents, according to a Ponemon Institute study. CMMC compliance means contractors can secure these operations against cyber threats, ensuring uninterrupted service.
Strengthening stakeholder confidence. The DoD relies heavily on contractors to maintain operational readiness. CMMC certification demonstrates a contractor’s commitment to cybersecurity, strengthening trust and increasing the likelihood of securing future contracts. As Katie Arrington, former Chief Information Security Officer (CISO) for the Office of the Under Secretary of Defense, states, “CMMC is about ensuring our national security by protecting the information that underpins our warfighter’s capability.”
Integrating CMMC with active situational awareness through participation in the Surface Transportation Information Sharing & Analysis Center (ST-ISAC: www.st-isac.com) and the National Defense Information Sharing & Analysis Center (ND-ISAC: www.nd-isac.org),
while fostering a culture committed to maintaining these standards, leads to a stronger and more secure industry.
Improving operational efficiency. Obtaining the certification isn’t enough. Dedication to ongoing implementation of CMMC’s best practices leads to improved processes and stronger internal controls. Examples include better network segmentation, enhanced encryption protocols, and streamlined incident response plans, contributing to greater efficiency and resilience.
Reducing financial and operational risks. Non-compliance with CMMC can result in disqualification from DoD contracts. Additionally, cybersecurity incidents—such as ransomware attacks—can lead to significant financial losses and operational downtime. Compliance minimizes these risks by establishing a proactive approach to cybersecurity.
A study by IBM Security found that organizations with mature cybersecurity frameworks, like those aligned with CMMC, experience 45% lower breach costs.
Cybersecurity breaches extend beyond IT systems. In the transportation sector, the consequences of cyberattacks ripple through supply chains, disrupt logistics, and jeopardize national security. Due to the interconnected systems within companies in this sector, the account first compromised often enables access to additional systems resulting in many of the attacks seen in the industry, including ransomware attacks and business email compromise (impersonating known partners for unauthorized activity).
• Frequency of cyberattacks: Transportation companies experienced a 45% increase in targeted attacks year-overyear, according to Verizon’s 2023 Data Breach Investigations Report.
• Financial impacts: The average cost of a ransomware attack on transportation firms, including downtime, data recovery, and reputational damage, is estimated at $4.7 million, according to IBM’s 2022 Cost of a Data Breach Report.
• Double attack risks: Studies reveal that 20% of companies targeted by ransomware experience a second attack within a year.
• Business closures: The National Cyber Security Alliance reports that 60% of small businesses go out of business within six months following a significant cyberattack.
of understanding of intricate security standards, and the time and energy required to establish and manage mandatory security practices and processes.
The costs of CMMC compliance vary based on factors like the size of the company, level of certification required, and any necessary consultations. For small and medium enterprises (SMEs), the initial investment can average $15,000 to $100,000, depending on infrastructure upgrades, personnel training, and consulting services. For smaller companies, annual maintenance costs can range from $5,000 to $25,000. A National Defense Industrial Association (NDIA) report states that over 70% of SMEs find these costs manageable when weighed against the long-term benefits.
Despite these upfront costs, the return on investment is significant. Non-compliance can result in lost contract opportunities, penalties, and increased vulnerability to cyberattacks, which can have far more significant financial repercussions. CMMCcertified contractors may be able to offset certain associated expenses, such as qualifying for cyber insurance discounts.

While the CMMC is a commendable initiative for defense contractors to enhance cybersecurity, certification and compliance present several challenges for smaller defense contractors, particularly due to the complexity of the standards and requirements involved.
According to Expert Insights, only 38% of companies in the transportation sector implement multi-factor authentication, compared to 88% in the technology sector. This one change can block over 99.9% of account compromised attacks.
Check out these other mind-boggling stats from recent reports.
There are significant direct and indirect costs linked to implementing security controls, preparing for audits, and the certification process itself. These costs can be weighty, particularly for businesses operating on limited budgets. Other hurdles include limited resources, like the absence of dedicated IT security personnel, a lack
While achieving compliance is essential to safeguarding sensitive data and maintaining eligibility for Department of Defense (DoD) contracts, defense transportation contractors, especially SMEs, may find compliance challenging due to limited resources. CMMC 2.0 offers a streamlined, risk-based approach, such that contractors with less sensitive contracts do not require as robust a certification level as contractors supporting the most critical contracts, reducing barriers while ensuring an industry-wide improved security posture.
Taking a practical, three-pronged strategic approach can help contractors overcome hurdles:
Partner with third-party experts. Engaging Managed Security Service Provid-

ers (MSSPs) or consultants can streamline compliance. These experts can conduct gap analyses, implement necessary controls, and prepare contractors for third-party assessments. The NDIA estimates that contractors using MSSPs achieve compliance 30% faster than those relying on their internal resources.
Leverage DoD resources. The DoD has provided guidelines and resources to support contractors, including the CMMC Assessment Guide and cybersecurity templates. Leveraging these tools can reduce the complexity of compliance.
Plan incrementally. Contractors can adopt a phased approach to compliance, addressing high-priority requirements first and gradually implementing additional controls. This approach ensures continuous progress without overwhelming the organization.
Achieving CMMC compliance is not just about meeting technical requirements but about fostering a cybersecurity culture. Organizations with a strong cybersecurity culture are half as likely to experience a significant breach as those focusing solely on technical solutions (SANS Institute). This can be accomplished with:
• Employee training. Ensuring all personnel understand their role in main-
taining cybersecurity. Even the most advanced technical controls are ineffective without a workforce that understands its role in cybersecurity.
• Leadership engagement. Securing buy-in from executives to leadership is essential in reinforcing a cybersecurity culture by prioritizing strategic initiatives, such as implementing comprehensive security policies and fostering open communication about cyber risks. Research by PwC shows that organizations where leadership prioritizes cybersecurity see a 60% higher ROI on security investments than those where it is viewed as an IT-only issue.
• Continuous improvement. Cyber threats evolve constantly. Regularly updating systems and processes to address emerging threats supports a culture focused on proactive measures.
• Collaboration. A cybersecurity culture is optimized through industry collaboration. When the Final Rule was published last October, the DoD highlighted how CMMC is “perpetuating a collaborative culture of cybersecurity and cyber resilience,” underscoring the program’s role in enhancing collective security efforts.
Over time, this culture becomes a strategic asset, enhancing the organization’s overall resilience and competitiveness. CMMC is a strategic opportunity for de-
fense transportation contractors. By enhancing trust, mitigating risks, streamlining investments, and building a culture of security, CMMC positions contractors for success in an increasingly complex and competitive landscape.
While compliance costs may seem significant, the long-term benefits—including securing contracts, reducing risks, and improving operational efficiency— make it a worthwhile investment. For defense transportation contractors, embracing CMMC is not just about meeting DoD requirements, but positioning themselves as reliable, resilient, and competitive partners in the DIB. DTJ

Tabatha Ward is an executive with over 15 years of experience across federal and commercial sectors, with a special interest in intersectional IT/ OT threat vectors and surface transportation. As EVP of Growth at ROGERCO, Inc. (powering the Surface Transportation Information Sharing Analysis Center), Tab excels in cultivating partnerships and building agile teams to achieve big goals. Tabatha holds a BBA in Business Law and an MBA in Project Management. She is based in Peachtree City, Ga.

Obtaining compliance with CMMC Level 2 is a critical requirement for organizations in the Defense Industrial Base (DIB) that process, store, or transmit Controlled Unclassified Information (CUI). Central to this compliance journey is the implementation of the cybersecurity standards outlined in NIST Special Publication 800-171 Rev. 2. These standards are structured across 14 Security Requirement Families, covering 110 cybersecurity requirements (or controls) designed to protect CUI from unauthorized access.
To ensure that these controls are effectively implemented, NIST Special Publication 800-171A offers an assessment guide that breaks these controls down into 320 detailed assessment objectives. These objectives provide a precise framework for evaluating your organization’s adherence to the necessary cybersecurity protocols and readiness for a CMMC Level 2 assessment.
Third-party assessments were authorized to begin in December 2024. Another rule to implement the program will be released by mid-2025, and we will start seeing CMMC requirements in solicitations for DoD contracts. This phased rollout by the DoD is designed to ensure the appropriate transition for contractors and contracting agencies.
Note: Organizations that have not sought to pursue a self-assessment by the first half of 2025 will start missing out on valuable opportunities. Those subject to a Level 2 Third-Party Assessment should begin preparation now and engage with a qualified C3PAO to plan for an assessment well before one of their contracts requires it.
For more details about implementation, read “CMMC Is Here. What’s Next?” by CMMC expert Eric Crusius, Partner, Knight & Holland, on page 12.
By Eric Crusius, Partner, Holland & Knight LLP


For a long while, the question was whether contractors (including businesses in the transportation industry) doing business with the Department of Defense (DoD) would ever have to comply with the Cybersecurity Maturity Model Certification (CMMC). With the issuance of the programmatic rule that kicked off certifications by certified assessors, the question now is not “if,” but “when.”

This article will examine the CMMC timeline and identify the requirements and expected pitfalls. It is important to note that the rules are hundreds of pages long, so we will not be able to cover all the nuances in this article. I recommend reaching out to your government contracts attorney to discuss your own unique situation with them.
Before getting into the specifics, it is important to review the basics of the CMMC program. The CMMC program
will categorize each contract into one of three levels:
Level 1 will be a self-certification based on the 15 controls already required by Federal Acquisition Regulation (FAR) 52.20421. This is applicable when contractors manage Federal Contract Information (FCI) as part of its work under the contract.
Level 2 will be a self-certification or a third-party certification, based on the 110 controls in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 revision 2. DoD estimates that the vast majority of contractors falling in this category will be required to get a third-party certification (76,000 versus 4,000). Level 2 is appropriate when contractors manage Controlled Unclassified Information (CUI) in the performance of their contract. Third-party assessments will be conducted by Certified Third-Party Assessment Organizations (C3PAOs), which are accredited by the Cyber Accreditation Body (the Cyber AB).
Level 3, which will only be attainable after a contractor obtains a Level 2 thirdparty certification, will be based on about two dozen controls in NIST 800-172. Contractors falling in this category are required to obtain a third-party certification for those two dozen controls from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). DoD has said that this will be required for especially sensitive CUI.
It is important that for Levels 1 and 2, CMMC is merely a verification of existing requirements, though the majority of contractors handling CUI have not instituted the 110 controls under NIST 800171. Further, the program is widespread and applies through the supply chain with the exception of Commercial off-the-Shelf (COTS) products sellers and to all nonCOTS contracts valued at over $10,000 (the micro-purchase threshold).
CMMC is here. But it also isn’t. Let me explain:
There are two separate rules that make CMMC come to life. The first, under CFR Part 32, establishes the CMMC program. The second, under CFR Part 48, puts the CMMC requirement into contracts. The Part 32 rule is final and in effect while the Part 48 rule will be released in final form in
"So, while the program exists, it is not in any contracts yet. That does not mean contractors, or their supply chains, should wait. The effort to get into compliance takes some time – especially if a company has not attempted to do so before."
– Eric Crusius
a few months. So, while the program exists, it is not in any contracts yet. That does not mean contractors, or their supply chains, should wait. The effort to get into compliance takes some time – especially if a company has not attempted to do so before.
The Part 32 rule lays out the timing for CMMC once the Part 48 rule is finalized. On the effective date of the Part 48 rule, all new solicitations will have CMMC in it. Even so, there is a rollout period.
• Phase 1 (immediate) will require contractors to self-certify compliance for Level 1 (if they have FCI) and Level 2 contracts (if they have CUI).
• Phase 2 (one year after Phase 1) will require all contractors to obtain a thirdparty certification (with some limited exceptions) if they have CUI.
• Phase 3 (one year after Phase 2) will require all contractors with sensitive CUI to obtain a certification from the DIBCAC. Under this phase, thirdparty Level 2 certifications may also be required at option years for existing contracts not previously covered.
• Phase 4 (one year after Phase 3) will institute the requirement for all three CMMC levels for all new contracts and options (for contracts where CMMC has not been required).
Under certain circumstances, contracts that began prior to CMMC may eventually require a certification. That may allow contractors to seek a price adjustment.
More specifically, Phase 1 of the final rule permits DoD to accelerate adoption and requires third-party assessments by C3PAOs as part of Phase 1. That means CMMC may be a requirement in prime contracts as soon as the issuance of the DFARS rule expected in the first half of this year. While
it is not expected this will be widespread, contractors holding or creating particularly sensitive information should be prepared to comply under an accelerated timeline.
Companies seeking a self-assessment or a third-party assessment will need to first figure out the scope of the assessment. There is no requirement for any assessment to cover an entire organization and, in fact, it often makes more sense to limit the scope of where the information will be stored (and what will need to be assessed).
Next, companies will need to determine how they will institute the controls. Do they need to build a bespoke system, or can they rely on the ecosystem of Managed Service/Security Providers (MSPs)?
MSPs often have a cost advantage and, by picking the right one who understands the space, a company can make compliance more affordable. Some other important strategies and pitfalls of note:
An organization seeking a certification may disagree with an assessor’s review that certain controls were not met (which could prevent the organization from obtaining a certification necessary to perform a contract). In those circumstances, the organization can appeal that determination within the C3PAO. And if that is unsuccessful, the organization can appeal to the Accreditation Body. Beyond that, there is no right of appeal to DoD or elsewhere written into the rule. Whether the courts can be an avenue once the administrative appeals are unsuccessful remains to be seen because the Accreditation Body is a private nonprofit entity.
DoD IS WEDDED TO NATIONAL INSTITUTE FOR STANDARDS AND TECHNOLOGY (NIST) SPECIAL PUBLICATION (SP) 800-171 (REVISION 2) FOR NOW.
During the CMMC rulemaking process, NIST released an updated version (Revision 3) for SP 800-171. While this
newer version has fewer controls, it has a greater number of assessment objectives and includes additional supply chain controls not previously found in NIST SP 800-171. For now, DoD has committed to utilizing Revision 2 here and in DFARS 252.2047012. DoD stated in the final rulemaking that implementation of Revision 3 will be the subject of further rulemaking which we should expect in about a year.
CMMC
requirements apply to small business and international companies just like their large and domestic counterparts.
Assessments under Level 2 occur every three years. That date may be sooner, however, if the contractors change the scope of the system through non-routine upgrades or through merger and acquisition activities.
FROM THE COMPANY MUST BE FILED REGULARLY.
The new CMMC regime creates a huge new False Claims Act risk because contractors will be required to file regular affirmations, at a minimum, after the completion of an assessment and annually. These affirmations from a company official must certify that the controls are still in place and the system has not changed.
CMMC requirements apply to small business and international companies just like their large and domestic counterparts. Of course, the cost to some small businesses may be less if the environment is smaller.
There is concern that CMMC will drive smaller businesses and businesses that do not rely on the DoD supply chain for a lot of their revenue from the Defense Industrial Base (DIB). There are some things that companies can do for their supply chain to ease or erase the burden.
First, avoid flowing down information
that will trigger an assessment. Think carefully about what the supply chain needs to know and limit information, if possible.
Second, when that is not possible, consider utilizing a virtual desktop system where lower-tiered contractors can access but not download information. This is specifically contemplated for in the rules.
Third, larger contractors should consider offering support to their supply chain and engage with them regularly to find out if there are pain points.
And, of course, pre-award protests are always an option if there is a disagreement with the level designation by a contracting officer. Before going down that path, contractors should engage with the agency as permitted (such as during the Q and A phase).
CMMC represents a compliance sea of change for transportation contractors in the DoD space and the above merely represents just the beginning. Because there are a lot more contractors than C3PAOs, contractors that will seek a Level 2 thirdparty certification from a C3PAO would be wise to prepare immediately and avoid a bottleneck. Even if CMMC changes with the new administration, the underlying compliance with NIST SP 800-171 is unlikely to be altered, and time and money getting into compliance will not be wasted. Begin by contacting an attorney, C3PAO, or MSP today and get started. DTJ

Eric Crusius draws on his previous experience representing internet-based companies across the globe and focuses on cybersecurity issues particular to government contractors, including counseling contractors regarding cybersecurity compliance obligations, specialized breach response requirements required by various federal agencies (including the DoD), and certifications such as the Cybersecurity Maturity Model Certification (CMMC) and Federal Risk and Authorization Management Program (FedRAMP). He is an industry thought leader with respect to these issues, appearing on Government Matters, Federal News Network and featured at conferences to provide insight to the greater contractor community.
The Department of Defense developed the Cybersecurity Maturity Model Certification (CMMC) to ensure contractors and subcontractors implement cybersecurity controls and processes that adequately protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) residing on Defense Industrial Base (DIB) systems and networks. CMMC certification is mandatory for all entities doing business with the DoD. By achieving CMMC compliance, your organization will meet DoD requirements and significantly strengthen its overall security posture.
If you need any assistance with steps 1-3, contact your attorney, C3PAO or MSP to help you prepare.

Understand CMMC & NIST 800-171 Rev 2
• Research and gain a comprehensive understanding of the model and security standard
• Familiarize yourself with the domains outlined in the model
Identify your CMMC level
• Level 1 [Foundational]: Applicable to defense or aerospace contractors bidding on DoD contracts handling FCI. All contractors in Level 1 must implement 17 basic cybersecurity practices to safeguard FCI. If the FAR 52.204-21 Requirement is in your current contracts, you are most likely in the CMMC Level 1 category.
• Level 2 [Advanced]: Applicable to defense or aerospace contractors bidding on DoD contracts handling:
– CUI
– CTI
– ITAR or export-controlled data that is CUI
All contractors in Level 2 must implement 110 security controls from NIST 800-171. If the DFARS 252.204-7012 requirement is in your current contracts, you are most likely in the Level 2 category.
• Level 3 [Expert]: Applicable to defense or aerospace contractors bidding on DoD contracts handling Critical CUI. Level 3 security requirements are expected to contain a subset of NIST SP 800-172. If the DFARS 252.2047012 requirement is in your current contracts and you have had a DIBCAC assessment, you are most likely in the Level 3 category.
Identify your in-scope assets
• Federal Contract Information (FCI): Information provided by or generated for the government under contract not intended for public release
• Controlled Unclassified Information (CUI): Information requiring safeguarding or dissemination controls pursuant to and consistent with laws, regulations, and governmentwide policies, excluding information that is classified under Executive Order 13526, Classified National Security Information, December 29, 2009, or any predecessor or successor order, or Atomic Energy Act of 1954, as amended
• Level 1 asset types:
• Process – FCI that can be accessed, edited, entered, generated, or printed by an asset
• Store – Inactive or at-rest FCI on an asset
• Transmit – Transferred FCI from one asset to another
• Level 2 asset types:
• CUI assets – Processes, stores, or transmits CUI
• Security protection assets – Provides security functions or capabilities to the contractor’s CMMC assessment scope
• Contractor risk managed assets – Assets that can, but are not intended to, process, store, or transmit CUI because of security policy, procedures, and practices in place and are not required to be physically or logically separated from CUI assets
• Specialized assets – May or may not process, store, or transmit CUI i.e. government property, Internet of Things (IoT) devices, Operational Technology (OT), Restricted Information Systems, Test Equipment, etc.
• Level 3 asset types: To be announced later
Identify gaps in CMMC compliance
• Perform a gap assessment to identify gaps
Develop an implementation plan
• Based on findings from your gap assessment, address vulnerabilities to meet the control objective requirements
Develop required documentation
• Complete System Security Plan, diagrams, inventory lists, etc.
Prepare for C3PAO assessment
• Ensure your team is prepared to provide needed evidence and answer interview questions with the C3PAO
• Readiness assessment can help your organization validate your readiness through a C3PAO mock audit to ensure you move into the CMMC assessment with confidence
Choose a certification body
• Choose a quality audit partner that aligns their goals with yours
• Ensure certification body is accredited to certify for CMMC
• Check references with other companies certified by the body
Undergo C3PAO assessment
• Designate a team member as the point of contact for auditors to streamline communication
• Undergo assessment with interviews of key personnel and review of documentation
Remediate follow-up actions
• Schedule a meeting to discuss audit findings with the internal team
• Plan for immediate, short-term, and long-term actions based on the audit report
Understand future practices and required assessments
• Level 1 – Annual self-assessment
• Level 2 – C3PAO assessment every three years for critical national security information; annual self-assessment for select programs
• Level 3 – Government-led assessment every three years
Establish continuous improvement team to oversee progress
Integrate CMMC compliance metrics into regular management reviews

A travel management company can help ensure the safety and security of employee business travelers
By Marlene Gray, Director, Government Services, Omega World Travel
Taveler safety and security should be a top priority for companies. Employees on business travel are business assets and their safety and well-being should be part of the company’s objective for that mission. The concept of duty of care is more than just employee itinerary tracking and safe accommodations. A “duty of care program” is a set of policies and procedures implemented by an organization to actively protect its employees, particularly when traveling for work, from foreseeable harm by taking reasonable steps to ensure their safety and well-being, fulfilling a legal obligation to act responsibly and minimize risks.
Travel managers are focused on developing, communicating and enforcing travel policies and procedures needed to prioritize employee safety during business trips and help them perform their due diligence. Travelers will rely on travel managers before and during their trip, so it’s important for them to stay up to date with global events, travel advisories and potential risks at any destination employees might visit during work trips, as well as any other duty of care guidelines the company might have. By being proactive and vigilant, travel managers can make sure employees are well-prepared and supported throughout their journey.
There are key points to developing an effective duty of care program, and your travel management company could help lead the way. Just as having a complete and up-do-date traveler profile is key for a positive travel experience, a company’s travel policy is the key to developing a successful duty of care program. A company’s duty of care program should contain a statement of its commitment to care for its employees and how far that extends. Its travel policy should prioritize traveler safety and outline your company’s guidelines for how employees should manage their business travel, from booking travel accommodations and approval processes to procedures on how to prepare for a business trip and handling emergencies while traveling.
Your travel management company can help develop a policy that provides guidance on risk assessment, travel restrictions, safety briefings, and emergency procedures to ensure the safety and security of employees during business trips.

Companies should consider doing travel risk assessments that identify potential threats their travelers could face while on official travel. Whether local or abroad, understanding what potential threats employees might encounter while traveling is key to your duty of care program. The first step is to identify potential hazards. For instance, political and civil instabilities, natural disasters, health and environmental conditions, crime and theft protection are risks that should not be overlooked. Ranking the severity of these hazards—and who they might impact and how—is equally important in your assessment plan. Creating a plan of action for implementing these processes is necessary. Knowing how to respond is equally important. Lastly, it is imperative to review these steps often to make updates when necessary.
Never underestimate communication and training for employees. “Know before you
go” is a very practical safety tip to include in your general safety advice for employees. Therefore, providing training to prepare and educate travelers about the potential risks they may face while on travel is imperative. It’s not as simple as knowing a country’s entry requirements or local breaking news that should be reviewed prior to travel by employees and travel managers. It is beneficial to provide travelers with checklists that educate them on health precautions, local customs and even how to report incidents and other protocols to follow before, during and after travel. Travel guides can help the traveler focus on adhering to company policy as well as their personal safety.
Training employees in situational and cultural awareness is crucial as it is important to prepare travelers with the knowledge and skills to navigate different environments when traveling. Understanding current events or political tensions in travel is also important. Learning local customs


The US Department of State issues detailed travel advisories for every country, based on the security situation, risks, and potential threats, such as civil unrest, natural disasters, health concerns, or terrorism.
Travel advisory levels: The Department of State uses a system with levels ranging from Level 1 (Exercise Normal Precautions) to Level 4 (Do Not Travel).
How to check: You can check the travel advisories for any country on their official website, which provides up-todate information on current safety conditions, entry requirements, and tips for travelers. Go to US Department of State – Travel Advisories at https://travel.state. gov/content/travel/en/traveladvisories/ traveladvisories.html/

The CDC provides health-related travel advisories and alerts for travelers that cover potential outbreaks, vaccination requirements, and other health-related risks (e.g., COVID-19, malaria or polio). This is a great source for understanding the health risks associated with international travel.
Health alerts: The CDC issues disease alerts that may affect travelers, including travel health notices that are color-coded based on the severity of the situation.
How to check: Visit the CDC’s website to find health notices and advisories for specific destinations at CDC Travel Health Notices: https://wwwnc.cdc.gov/travel
Your travel management company can offer travel advisory alerts and notifications that include the level of impact expected at a particular airport, city or country. Your travel management company also can identify specialized vendor partners to elevate your risk management plan with medical and security services like medical evacuation, on-site medical assistance, security consultants to provide training and briefings and a 24/7 emergency hotline. Travelers can keep themselves informed about safety alerts and potential risks for global travel through several reliable resources and tools. Below is a checklist of eight ways for travelers to find out if a country has a safety alert or advisory.

WHO monitors global health trends and issues advisories, safety alerts and updates for travelers on epidemics, pandemics and health risks in specific regions or countries.
Health alerts: WHO issues health alerts for infectious diseases, such as outbreaks of Ebola, Zika virus, or cholera, which can affect travelers.
How to check: Access WHO’s travel health recommendations and safety alerts at WHO Travel Health: https://www.who.int/ health-topics/travel-health

Travelers can check the official websites of their country’s embassy or consulate in the destination country for safety alerts and travel advisories. Embassies often issue emergency alerts or updates in response to local crises, such as political instability, natural disasters, or civil unrest.
How to check: Visit the website of your country’s embassy or consulate in the country you are traveling to. For example, the US Embassy’s website provides important local information for US citizens abroad. Go to US Embassies: https://www.usembassy.gov/

Many travel insurance companies provide safety alerts or risk assessments as part of their services. They often partner with global risk management companies that offer detailed reports and updates on safety conditions in specific destinations.
How to check: Travelers can contact their travel insurance provider or check their online portals to see if they offer real-time safety alerts or travel warnings for specific countries.

International SOS is a company that provides global health and safety solutions for travelers. It offers medical alerts, security alerts, and evacuation services to businesses and travelers worldwide.
How to check: You can subscribe to their alerts or visit their website for up-to-date information on security and health risks in various countries at International SOS: https:// www.internationalsos.com/

The US Department of State runs the STEP Program, which allows US citizens to register their travel plans. By registering, travelers receive email updates and emergency notifications about safety conditions, travel alerts, or emergencies in their destination country.
How to Register: US citizens can sign up for the STEP program to receive personalized travel alerts at https://mytravel.state. gov/s/step

Sometimes the easiest, simplest and most tried-and-true ways are best for learning what is happening in your destination area right now.

and etiquette when traveling abroad could help avoid negative encounters. Respecting gender roles in different cultures is of equal importance. Being aware of the potential risks related to gender-based violence should not be minimized as a potential travel risk. Your travel management company can assist with traveler training and other educational resources to keep travelers informed.
Travel disruptions vary and can have a significant impact on travel plans. Travelers are facing more than simple inconveniences, such as a last-minute gate change
or a delayed flight due to airline staffing shortages or mechanical failures. Travel disruptions can be severe and leave travelers stranded in the most unlikely places but there are technology platforms to help travel managers understand and plan for travel disruptions using predictive analytics. Travel managers can use software to mitigate travel disruption risks and consider alternate options to save travel costs or even a travel mission.
Your travel management company can offer travel advisory alerts and notifications that include the level of impact expected at a particular airport, city or country. (See the list of Handy Resources for Travel Safety Alerts and Advisories on page 18.)
Your travel management company can also identify specialized vendor partners to elevate your risk management plan with medical and security services like medical evacuation, on-site medical assistance, security consultants to provide training and briefings and a 24/7 emergency hotline.
Of course, tracking business travelers is necessary in a duty of care program so ensuring your travel data is complete with accurate itinerary information is extremely important. Changes to ticketed itineraries that occur outside of your travel management company can become a problem for traveler tracking if there is no process to bring that information back into the travel
program. Companies need reliable information when activating a plan of action and your travel management company can get this data straight from the source to ensure the data is accurate and complete. The ability to communicate directly with employees during a travel crisis or disaster is crucial. There are many tools that allow travel managers to send push notifications via email or SMS messaging to employees on travel and your travel management company can help you identify the right system to meet your company needs.
In review, your travel management company can assist your organization with planning and managing employee travel to ensure positive outcomes in the following ways:
• Assisting you with creating a robust duty of care program by helping to identify potential risks, current travel conditions
and safety information that is based on your company’s travel destination list.
• Implementing travel safety guidelines and processes to ensure employee compliance with your duty of care program.
• Providing training sessions on safety awareness and best practices.
• Offering services that include monitoring travel in real time and proactively communicating with your travelers during critical situations.
• Providing emergency assistance for immediate medical support.
• Facilitating communication with local authorities, other vendor partners and company decision makers.
Traveler safety and security are a necessary and fundamental aspect of every travel program. Identifying the right travel management company with the necessary resources to help administer your duty of care program by understanding your company’s unique
needs and challenges is important to your employees’ travel health and well-being. A good travel management company can significantly improve employee experience during business travel by securing better rates, streamlining booking processes, managing risks, providing 24/7 support, and ensuring safety and security, ultimately allowing employees to focus on their work rather than travel logistics, leading to increased satisfaction and productivity. DTJ

Marlene Gray is the Chair, of the NDTA Government Passenger Travel Advisory Council's Travel Management Companies Committee, and the Director of Government Services at Omega World Travel in Jacksonville, NC. She has 25 years of travel industry experience and earned her BA from Pfeiffer University in Misenheimer, NC.
Join the National Defense Transportation Association’s global association of transportation, logistics and passenger travel professionals.
Experience competitive benefits, rewarding professional development courses, exciting networking opportunities, and create a strong, efficient transportation system for the United States.
Visit https://www.ndtahq.com/events/sfpc for more details.

June 10-12, 2025
“Challenging the Joint Force Deployment Status Quo –Improving the Large-Scale Deployment Model”
The 2025 SFPC will feature:
• Meetings and Breakout Sessions –Meet, network and join the discussion with government and industry leaders covering topics on inland waterways, port readiness, Joint Logistics Over-the-Shore (JLOTS) Operations, strategic seaports, threat protections, and the Joint Transportation Management System (JTMS).
• Keynote Speakers – Listen and engage with our six senior government, military and industry keynote speakers as they
discuss large-scale deployment operations, protecting our ports, power projecting through strategic seaports, unmanned aerial systems policy, delivering commercial capacity, and embarking Marines.
• Panels – Learn from our three panels as their moderators guide the discussion on optimizing transportation networks, command and control of deployments and cybersecurity and counterintelligence.
Together, we can build relationships, identify challenges, discuss solutions, and find ways to improve readiness and capacity.
Together, we can build relationships, identify challenges, discuss solutions, and find ways to improve readiness and capacity.


By Barbara Parus, Managing Editor, DTJ and The Source
he May 7, 2025, deadline for states to comply with REAL ID requirements for driver’s licenses and ID cards is quickly approaching. Do you know how to obtain a compliant REAL ID?
The time has come! In 2025, travelers in the United States will need a REAL ID or another form of federally accepted identification to board domestic flights, enter federal buildings and nuclear power plants, and access other federal services that require identification. The REAL ID Act will take effect May 7, 2025. In the event the REAL ID Act does go into effect on this day, it’s best to get your enhanced driver’s license sooner rather than later to avoid any potential backlogs as the date nears.
The REAL ID concept is not as new as you may think. The vision emerged almost 24 years ago in the wake of the Sept. 11, 2001, terrorist attacks when the 9/11 Commission recommended that the federal government establish standards for driver’s licenses and identification cards. This prompted the enactment of the bipartisan REAL ID Act in 2005 with an initial dead-
line of May 2008 for the ID provisions of the law. Among the security standards required by the law are anti-counterfeiting technology, measures to prevent insider fraud, and the use of documentary evidence and record checks to validate that a person is who they claim to be.
A REAL ID is a state-issued driver’s license or identification card that meets federal standards for security and identity verification. It looks like an ordinary driver’s

license, except it will display a star or other emblem in the upper right corner.
US travelers must be REAL ID-compliant to board domestic flights. Travelers who do not present a REAL ID-compliant
license or acceptable alternative beginning May 7, 2025, will not be permitted through the airport security checkpoint. The REAL ID does not replace a passport for international travelers, and they can still use a passport for all domestic flights within the US. For related information, visit tsa.gov.
The application process is easy. Simply visit your state’s Department of Motor Vehicles (DMV) or equivalent agency, and bring certain documents (such as proof of identity, proof of Social Security number, and proof of residency) to apply for a REAL ID. To avoid longer wait times, gather your appropriate documents and get your REAL ID well before the May 7, 2025, deadline.
REAL ID cards cannot be used for border crossings into Canada, Mexico or other international travel.
Here is some general information about passport requirements for international travel in 2025. Currently, there haven’t
been any widely discussed global changes to passport requirements specifically in 2025. However, some trends and developments are worth noting:
Many countries require that a passport be valid for at least six months beyond your planned date of entry. This rule is already in place, but travelers should always check the specific passport validity rules for your destination before travel.
Countries around the world are continuing to implement electronic passports (epassports), which contain a digital chip to store biometric data. This trend will continue in 2025, as many countries already require or encourage the use of e-passports for smoother, more secure border crossings.
Some countries may introduce changes to their visa requirements or travel documentation rules due to security, health, or immigration policy updates. Take these countries, for example:
The European Union is set to roll out the ETIAS (European Travel Information and Authorization System) for visa-exempt travelers starting in 2025. ETIAS is like the US ESTA system, requiring travelers from visa-exempt countries to apply for travel authorization before entering EU member states.
Once granted ETIAS travel authorization, travelers will be able to enter participating countries multiple times for shortterm stays—usually up to 90 days—over a 180-day period. The ETIAS is valid for up to three years, but if your passport expires, a new ETIAS travel authorization will be required.
The expansion of the Electronic Travel Authorization (ETA) program will impact US and European travelers headed to the United Kingdom. Starting Jan. 8, 2025,
Adult passengers 18 and older must show valid identification at the airport checkpoint to travel. In coordination with its DHS counterparts, TSA has identified acceptable alternate identification for use in special circumstances at the checkpoint.
• Driver’s licenses or other state photo identity cards issued by Department of Motor Vehicles (or equivalent)
- Beginning May 7, 2025, if you plan to use your state-issued ID or license to fly within the US, make sure it is REAL ID compliant. If you are not sure if your ID complies with a REAL ID, check with your state department of motor vehicles.
• State-Issued Driver’s License or StateIssued ID
• US passport
• US passport card
• DHS trusted traveler cards (Global Entry, NEXUS, SENTRI, FAST)
ETA registration will be required by inbound travelers so that UK authorities can screen visitors before arrival, which was modeled after the US Electronic System for Travel Authorization (ESTA) system to reduce potential security risks and make border entry more efficient.
The ETA is valid for multiple entries into the UK within a two-year period.
Though not yet operational, the European Union’s European Travel Information and Authorization System (ETIAS), which has been postponed multiple times, is expected to take effect in May 2025. US passport holders who previously traveled to Europe without a visa will now need to apply for authorization through the ETIAS platform before visiting.
• US Department of Defense ID, including IDs issued to dependents
• Permanent resident card
• Border crossing card
• An acceptable photo ID issued by a federally recognized Tribal Nation/Indian Tribe, including Enhanced Tribal Cards (ETCs)
• HSPD-12 PIV card
• Foreign government-issued passport
• Canadian provincial driver’s license or Indian and Northern Affairs Canada card
• Transportation worker identification credential
• US Citizenship and Immigration Services Employment Authorization Card (I-766)
• US Merchant Mariner Credential
• Veteran Health Identification Card (VHIC)
Here’s some good news for airline travelers. In April 2024, the Department of Transportation announced that new rules would be rolled out requiring airlines to automatically give cash refunds to passengers for canceled and significantly delayed flights, even if they opt not to take a rebooked flight.
Prompt flight refunds or re-bookings. Effective Oct. 28, 2024, the new rules— which require prompt refunds—are the biggest expansion of passenger rights in the department’s history. Travelers now can easily receive automatic refunds if they opt not to take a rebooked flight due to significant disruptions, making the refund process much more hassle-free than before. The DOT rules lay out that passengers will be “entitled to a refund if their flight is canceled or significant-

ly changed, and they do not accept alternative transportation or travel credits offered.” (This doesn’t mean travelers can get both a refund and a new flight; the regulation only covers one or the other.)
Refunds for delays. Airlines can no longer decide how long a delay must be before a refund is issued. Under the new DOT rules, the delays covered would be more than three hours for domestic flights and more than six hours for international flights, the agency said. This includes tickets purchased directly from airlines, travel agents and third-party sites such as Expedia and Travelocity.
According to DOT, most US airlines have committed to providing benefits, such as hotels for overnight delays or meals for passengers, during significant delays and cancellations that are caused by issues within the airline’s control. You can view those benefits at flightrights.gov.
Refunds on bag fees. Travelers also are eligible for refunds on bag fees if a bag is delayed for over 12 hours (or 15-30 hours for international flights), refunds on ancillary paid services that don’t work such as Wi-Fi, and 24/7 live customer service support channels. Before this new ruling, when an airline misplaced a bag, it was up to the airline whether they would provide reimbursement for the bag fee paid.
Under DOT regulations (for domestic travel) and international treaties (for international travel), airlines are now required to compensate passengers if their bags are damaged, delayed, or lost. Improved customer service. Airlines are now required to provide live customer service communication channels around the clock, whether through live chat or phone support. The big advantage here is that travelers will receive immediate confirmation—from a human—and receive hassle-free and timely seven business-day refunds back to your credit card, or 20 calendar days for other forms of payment. DTJ
NOTE: The following sources were used to compile this article: transportation.gov, tsa.gov and dhs.gov
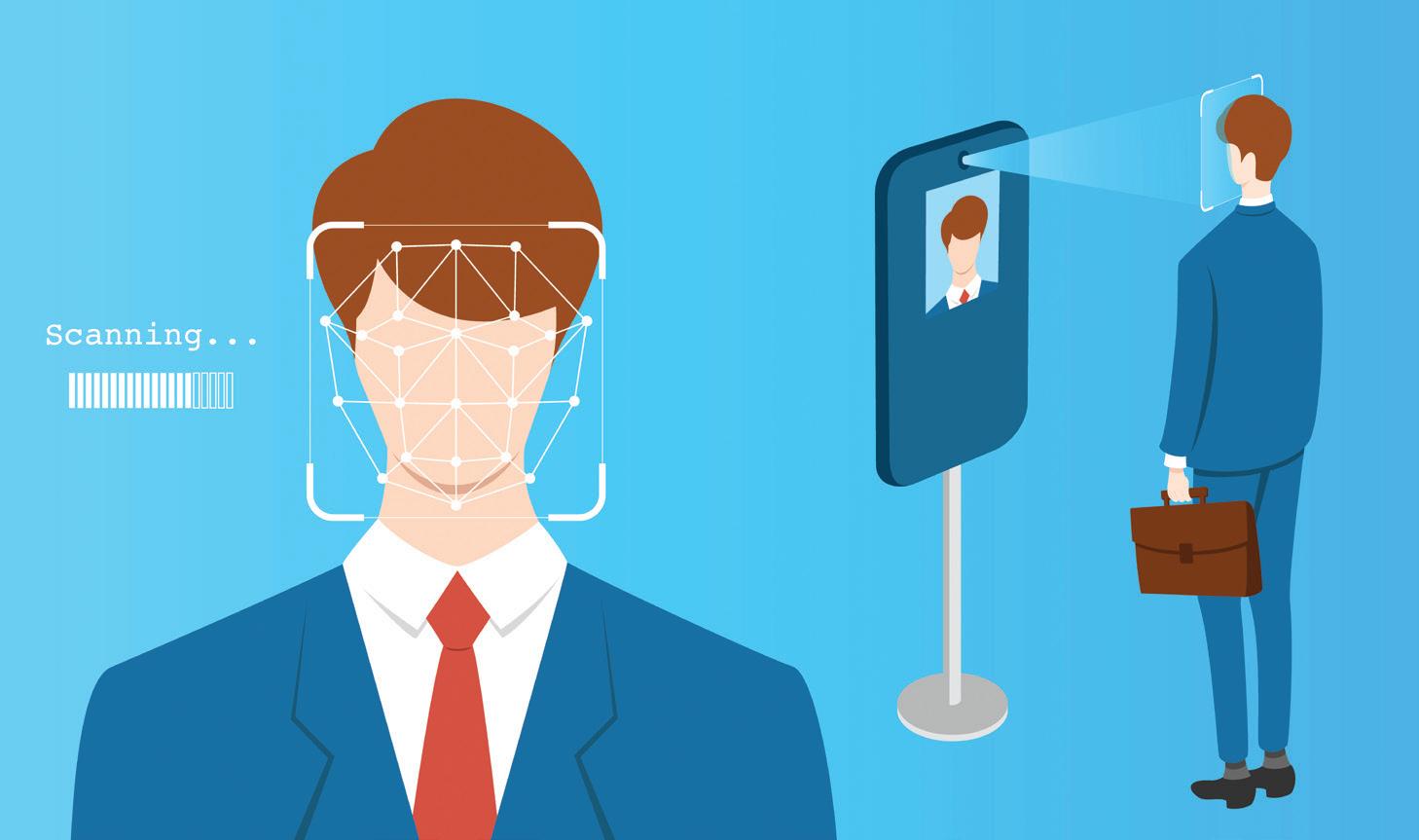
Airports around the world are using facial recognition to improve security, expedite passenger flow, and enhance the travel experience.
By Barbara Parus, Managing Editor, DTJ and The Source
Facial recognition technology has been used in major US airports for over a decade, though it’s only become more widespread in the past few years. In the mid-2010s, major airlines and airports began to adopt facial recognition for more streamlined security processes, like boarding and passport control.

Boston Logan International Airport (BOS)
Charlotte Douglas International Airport (CLT)
Chicago O'Hare International Airport (ORD)
Dallas/Fort Worth International Airport (DFW)
Detroit Metropolitan Airport (DTW)
Hartsfield-Jackson Atlanta International Airport (ATL)
Houston George Bush Intercontinental Airport (IAH)
John F. Kennedy International Airport (JFK)
Los Angeles International Airport (LAX)
Miami International Airport (MIA)
Minneapolis-Saint Paul International Airport (MSP)
Newark Liberty International Airport (EWR)
Orlando International Airport (MCO)
Phoenix Sky Harbor International Airport (PHX)
Salt Lake City International Airport (SLC)
San Francisco International Airport (SFO)
Seattle-Tacoma International Airport (SEA)
Washington Dulles International Airport (IAD)
NOTE: Not all terminals at these airports may have facial recognition deployed yet. It may be limited to specific flights or programs, like Global Entry or Mobile Passport Control.
By the late 2010s and into the 2020s, facial recognition technology became more common across international airports. It speeds up processes, such as check-ins, baggage drop-off and boarding by creating a seamless, contactless experience for travelers. Many airports across the globe, including London Heathrow, Dubai International, and Atlanta Hartsfield-Jackson, now use facial recognition for international arrivals and departures, often in conjunction with other security measures, such as fingerprint scanning, iris scanning, and retina scanning.
The Transportation Security Administration (TSA) uses facial recognition technology to ensure the person standing at the checkpoint is the same person pictured on their ID credential, such as a REAL ID or passport. (For more forms of identification, see “Get Real. A REAL ID, That Is” on page 22.) TSA uses second-generation Credential Authentication Technology (CAT-2) scanners as travelers enter the screening process. This technology assists
Transportation Security Officers (TSOs) in verifying the traveler’s ID, their flight status and vetting status. The CAT-2 units are currently deployed at nearly 84 airports nationwide, and will expand to the more than 400 federalized airports over the coming years.
Time-saving convenience. At some airports, passengers can use facial recognition to check in for flights instead of going through traditional check-in counters. They can scan their face at kiosks or selfservice terminals, speeding up the process. Facial recognition helps to expedite checkin, security, and boarding processes, potentially reducing wait times significantly for passengers.
• Security screening. Facial recognition allows passengers to be matched against their flight data and boarding passes without manually presenting documents. This technology can improve security by ensuring that the person
presenting the identification matches the person on record, reducing the risk of identity fraud.
The accuracy rate of facial recognition technology varies depending on several factors, including:
• Lighting. Facial recognition works best in well-lit environments where the camera can clearly capture distinct facial features.
• Angle and pose. The passenger’s face should be in full view and not partially covered with a mask, glasses, or a hat.
• Age, gender, and ethnicity. Facial recognition systems are less accurate for certain demographic groups, including older adults, women, and individuals with darker skin tones. Some countries and organizations are setting standards for accuracy. In the United States, the National Institute of Standards and Technology (NIST) tests and ranks facial recognition systems to assess their performance. They have discovered that the best-performing systems have significantly reduced error rates for people in the 18- to 60-year-old age group with lighter skin tones.
• Database quality. An up-to-date system that has been trained on a wide range of faces will have a high accuracy rate. High-quality systems, especially those used by major airports and law enforcement, can achieve accuracy rates of 99% or higher under ideal conditions. False positives are rare but can happen, especially in crowded or less controlled environments.
Less advanced systems, like those used in some mobile phones or public security cameras, may have lower accuracy rates in the 85% to 95% range. This happens when the system fails to recognize a person’s face because it is partially obstructed, or there are drastic changes to a person’s appearance (e.g., cosmetic surgery, significant weight loss, different hair style, or aging).
While high-quality facial recognition systems can have an accuracy rate of 99% or
higher under prime conditions, it’s important to note that even small errors can have serious consequences in high-stakes environments like airports or security settings. This is why facial recognition technology is often used in conjunction with other security measures, such as biometric-based security systems like fingerprint scanning, iris scanning and retina scanning.
Although facial recognition technology raises concerns about privacy and security, airports are increasingly using it to verify passenger identities. It is considered a key component for ensuring passenger safety by quickly matching a traveler’s face to their ID documents, identifying and preventing potential security risks, and expediting the check-in process at security checkpoints.
Traveler safety is paramount as underscored by TSA’s predicted expansion to 400 federalized airports in the coming years to provide a secure and pleasant flight experience. DTJ

Your service matters to us. It always has. It’s in the Enterprise name, a salute to our founder, Jack Taylor, and the World WarII aircraft carrier he served on. It’s in his legacy that continues to guide us. We know exceptional service matters to you, too. That’s why we’re committed to supporting active military, government employees and veterans with convenient locations, special car rental rates and personal service that stands out.
These corporations are a
AAR
AAT Carriers
Accenture Federal Services
Agility Defense & Government Services
Air One Aviation
Air Transport Services Group (ATSG)
AIT Worldwide Logistics, Inc.
Alamo City Engineering Services Inc.
Amazon
American President Lines, LLC
American Roll-On Roll-Off Carrier
Atlas Air Worldwide Holdings
Bennett Family of Companies
BRW
C5MI
Carlile Transportation Systems, LLC
Chapman Freeborn International Ltd.
Corporate Travel Management (CTM)
Crowley
Deloitte
DHL Express
Enterprise Mobility
Fairwater Holdings Inc.
Federated Maritime, LLC
FedEx
Freeman Holdings Group
Global Critical Logistics
Hapag-Lloyd USA, LLC
AEG Fuels
HomeSafe Alliance
International Auto Logistics, LLC
JET Infrastructure
Kalitta Air, LLC
KGL
Landstar System, Inc.
Liberty Global Logistics LLC
Maersk Line, Limited
Matson
Naniq Government Services, LLC
National Air Cargo, Inc.
Omni Air International, LLC
Patriot Maritime
Port of Corpus Christi
SAP
Schuyler Line Navigation Company LLC
Sealift, Inc.
SEKO Government, Space and Defense
Sixt Rent a Car LLC
Southwest Airlines
The Pasha Group
TOTE Group
Tri-State Motor Transit Co.
United Airlines
UPS
US Marine Management
US Ocean, LLC
Waterman Logistics
Air Charter Service
Berry Aviation, Inc.
BNSF Railway
Boeing Company
Choice Hotels International
CSX Transportation
CWTSatoTravel
Echo Global Logistics
Geodis Transportation Solutions
Global Logistics Providers
GMR Transport LLC
ICAT Logistics
LMJ International Logistics, LLC
National Air Carrier Association
Norfolk Southern Corporation
Ocean Shipholdings, Inc.
PayCargo LLC
SAP Concur
Sikich
The Port of Virginia
Transportation Institute
Union Pacific Railroad
U.S. Bank
Western Global Airlines
Wyndham Hotels & Resorts, Inc.
ALL OF THESE FIRMS SUPPORT THE PURPOSES AND OBJECTIVES OF NDTA
3Sixty
Able Freight
Admiral Merchants Motor Freight, Inc.
Aimbridge Hospitality
All Aboard America Holdings
American Bureau of Shipping
American Maritime Officers
American Trucking Associations
Applied Research Associates
ArcBest
Army & Air Force Exchange Service
Arven Services, LLC
ATS Secure
Avis Budget Group
Baggett Transportation Company
Beltway Transportation Service
Benchmarking Partners, Inc.
Boyle Transportation
Bridgeway Connects, Inc.
Bristol Associates
BTX Global Logistics
BWH Hotels
C5T Corporation
CGI Federal
Coleman Worldwide Moving
Construction Helicopters, Inc. (d/b/a CHI Aviation)
Council for Logistics Research
Cypress International, Inc.
D&G Support Services
Dash Point Distributing, LLC
Delta Air Lines
Drury Hotels Company, LLC
Duluth Travel, Inc. (DTI)
EMS Shipping & Trading GmbH
Ernst & Young
Europcar Mobility Group
Everts Air Cargo
Gallantry Global Logistics
GeoDecisions
Amyx
Apex Logistics International Inc.
CakeBoxx Technologies, LLC
Cartwright International
Dalko Resources, Inc.
Delaware River Stevedores, Inc.
Global Secure Shipping
GMT Resources, LLC
Green Valley Transportation Corp.
Groundswell
Hilton Worldwide
Holland & Knight
HV Logistics
Hyatt Hotels
Hylant
IHG | IHG Army Hotels
Intermodal Association of North America (IANA)
International Association of Movers
International Longshoremen’s Association (ILA)
Interstate Moving | Relocation | Logistics
Isaac Instruments
Island Hospitality Management
J.B. Hunt Transport, Inc.
Jacksonville Port Authority (JAXPORT)
Keystone Shipping Co.
Lansdowne Coach LLC
Leidos
LMI
Marine Engineers’ Beneficial Association
Mayflower Transit
McCollister’s Global Services, Inc.
Mercer Transportation Company
mLINQS
National Van Lines, Inc.
Nika Corporate Housing
Northern Air Cargo, LLC
Omega World Travel
One Network Enterprises, Inc.
ORBCOMM
Paxton Van Lines
Perfect Logistics, LLC
Pilot Freight Services, a Maersk Company
Plateau GRP
PODS Enterprises LLC
Port of Beaumont
Port of San Diego
Preferred Corporate Housing
Prestera Trucking, Inc.
Enterprise Management Systems
Gridiron Forwarding Co., Inc.
HLI Government Services
Holland & Knight
JAS Forwarding
Lineage
Lynden, Inc.
Move One
Priority Worldwide
Prosponsive Logistics
PTS Worldwide
Radiant Global Logistics
Red Roof Inn
Sabre
SAIC
Savi
SeaCube Containers
Seafarers International Union of NA, AGLIW
Sealink International Inc.
Selsi International Inc
Signature Transportation Group
Sonesta International Hotels
SSA Marine
St. Louis Union Station Hotel a Curio Hotel
Collection by Hilton
StarForce National Corporation
Steam Logistics, LLC
Stevens Global Logistics, Inc.
Synergy Global Housing
Taft Law
The Hertz Corporation
The MITRE Corporation
The Suddath Companies
Thinklogical
TMM, Inc.
Toll Group
Trailer Bridge
Travelport
Triton Container International Limited
TTX Company
Uber for Business
UNCOMN
United Van Lines, Inc.
US1 Logistics
VisionSafe
Wertz Motor Coaches
Women In Trucking Association, Inc.
World Fuel
XLG Transportation Inc.
Xwing Air, Inc.
NorSea Denmark A/S
Overdrive Logistics, Inc.
PITT OHIO
Port Canaveral
Port of Port Arthur
Prime Trip Support
Trans Global Logistics Europe GmbH
UNIVERSITIES
Christopher Newport University
John D. Odegard School of
Aerospace Sciences
Maine Maritime Academy
McKendree University
Purdue University
Saint Louis University
SUNY Maritime College
University of Missouri - St. Louis






We celebrate those who always strive: to rise higher, push through every boundary, and overcome every obstacle