ZYOUD

Senior Information Security & Risk Management , Government Entity, Financial Department

ZYOUD

Senior Information Security & Risk Management , Government Entity, Financial Department
"If digital transformation journey does not align with solid cybersecurity strategy, it will be a gateway to attract more cyber risks and threats."/18-20.









A warm welcome to all readers to the August issue of The Cyber Sentinels.
We are entering H2 of 2022 – the busiest and probably the most action-packed time for business worldwide. Specially, for the MEA region H2 is always synonymous to major events, trade shows, and multiple networking summits and awards. For Global CIO and CISO Forum, The World CIO 200 2022 Roadshow is the biggest head-turner for H2. The 40-country tour will be bringing on board over 3000+ delegates in a span of 4 months. The Grand Finale, to be held on November 23-24 in Pattaya, Thailand will be home to over 300 top technology decision makers flying in from these 40 countries. The event will also be the launchpad for The CISO 100 2023 tour (April-June) wherein we shall be inviting CISOs from our country chapters to take part in our exclusive panel session on Leading Security through Transformation and Disruption.
ANUSHREE DIXIT

Anushree@gecmediagroup.com
To make a start, to begin somewhere is inevitable. There is no growth until a seed is sown.
This issue of Cyber Sentinels, and the upcoming ones, is a preshow edition to the launch of this mega event. We have featured leading CISOs from the GCC who are voicing their opinion on the challenges faced by CISOs in modern enterprises and how they are still finding it difficult to fund critical cybersecurity initiatives. “Even though data breaches can be damaging when they occur, it remains challenging to fund critical cybersecurity initiatives sufficiently. Furthermore, there is a significant shortage of skilled cybersecurity professionals due to the rapid increase in demand outpacing the available talent pool. As international data regulations continue to develop, they are becoming more complex” says Abdullah AlShehry, CISO, Advisor, and Risk Expert., Semi-Government Environment Sector Entity. CISOs have also put forward some crisp and interesting remarks on what they expect from the security vendors and solution providers.
Shahab Ud Din, Group – IT Infrastructure & Security Manager, Ittihad International Investment LLC says, “Partners and consultants must be on the customer side, and they must understand the real problems of clients by conducting multiple sessions with the security team as well as the business to identify challenges and propose the best solution to protect users, applications, data, and infrastructure.”
And, last but definitely not the least, our cover story features Bader Husni Zyoud , Senior Information Security & Risk Management ,Government Entity , Financial Department who has put forward his thoughts around the myths and notion of digital transformation in security and the importance of aligning the transformation journey with a solid cybersecurity strategy.
The bottom line is still the same, start small to grow….. BUT start!
We hope you enjoy reading all the stories as much as we did in compiling them for you.
See you at the events!
Stay Safe.
MANAGING DIRECTOR
Tushar Sahoo tushar@gecmediagroup.com
CEO
Ronak Samantaray ronak@gecmediagroup.com
GLOBAL HEAD - CONTENT AND STRATEGIC ALLIANCES
Anushree Dixit anushree@gecmediagroup.com
ASSISTANT EDITOR
Rehisha PE rehisha@gecmediagroup.com
SALES
Richa S richa@gecmediagroup.com
Anuradha Basu anuradha@gecmediagroup.com
Ines Ben Rejeb ines@gecmediagroup.com
Ph: + 971 555 120 490
Production, Circulation, Subscriptions info@gecmediagroup.com
COMMUNITY COMMUNICATIONS
Gurleen Rooprai gurleen@gecmediagroup.com
Jennefer Lorraine Mendoza jennefer@gecmdiagroup.com
OPERATIONS LEAD
Omair Khan omair@gecmediagroup.com
DIGITAL TEAM
IT MANAGER
Vijay Bakshi
DIGITAL CONTENT LEAD
Deepika Chauhan
CREATIVE LEAD
Ajay Arya
DESIGNER
Rahul Arya
ASSISTANT DESIGNER
Vikas Chandra
DESIGNED BY
PRINTED BY Al Ghurair Printing & Publishing LLC. Masafi Compound, Satwa, P.O.Box: 5613, Dubai, UAE
SUBSCRIPTIONS info@gecmediagroup.com
# 203 , 2nd Floor
G2 Circular Building , Dubai Production City (IMPZ) Phone : +971 4 564 8684
31 Foxtail Lan, Monmouth Junction, NJ - 08852 United States of America Phone No: + 1 732 794 5918
A PUBLICATION LICENSED BY International Media Production Zone, Dubai, UAE @copyright 2013 Accent Infomedia. All rights reserved. while the publishers have made every effort to ensure the accuracyof all information in this magazine, they will not be held responsible for any errors therein.
Strategically taking place before COP27, ADIPEC is the global platform for leaders to reinforce commitments that will drive the industry towards reducing emissions, meeting decarbonisation goals, and providing a realistic view on short- and long-term energy outlooks.

The long-term impacts of geopolitics on the global economy and energy industry
The road to COP27
An industry transitioning: adapting to the new fundamentals of supply, low carbon and new energy solutions
and the energy transition: pioneering a new era of technology development
The new management agenda: future workforce and the leaders of tomorrow
BADER HUSNI ZYOUD

Senior Information Security & Risk Management , Government Entity, Financial Department
18-20
COVER FEATURE
CYBER SECURITY AS A TOP PRIORITY IN DIGITAL TRANSFORMATION
SECURITY, PRIVACY THREAT, AND REGULATORY COMPLIANCE LANDSCAPE OF INDUSTRY 4.0
TRANSFORMATION
CYBERSECURITY: ORGANIZATIONS BRACE FOR EFFECTIVE CYBER THREATS
THE JOURNEY OF A SECURITY OFFICER IN THE AGE OF DIGITAL TRANSFORMATION
A NEW STANCE OF CYBERSECURITY IN THE CONNECTED WORLD

OVERCOMING THE AGITATION AROUND SECURITY RISKS
HOW SECURED IS YOUR BUSINESS FROM CYBER ATTACKS?
HOW SECURED IS YOUR BUSINESS FROM CYBER ATTACKS?
EXPERT BYLINE
12-13
CYBER SECURITY IN AN INCREASINGLY DIGITALIZED WORLD
14-16
THE RISE & RISKS OF OBSERVABILITY DATA
44-46
SIMPLIFYING SOFTWARE
SECURITY: VERACODE
ENHANCES FRICTIONLESS EXPERIENCE FOR DEVELOPERS
48-49
Q2 2022 DDOS ATTACK TRENDS
50-51
NETWORK MODERNIZATION: THE KEY TO THE FUTURE OF HEALTHCARE
Security threats and data breaches are increasing due to the introduction of new technologies and procedures in the businesses.
Please describe your job role?
l Ensuring that the Mashreq IT systems and Operational teams /processes and procedures comply with all relevant data privacy, protection law, regulation, and policy (including concerning the retention and destruction of data).
l Working with designated privacy law attorneys across the Mashreq offices and, where necessary, outside counsel to help advise on local data privacy law issues.

l Promoting effective work practices, working as a team member, and showing respect for co-workers.
l Assists in the development and implementation of Data Privacy strategic initiatives. Leads all Privacy related tasks with effective monitoring and protection of information security assets.
What are the most important and critical aspects of your job role?
Data protection is the most important plan, sets up, and enforce frameworks to protect data, safeguard sensitive information and personal data against hackers targeting or misuse of data. Ensure that specific data is available according to organizational requirements.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
l CISOs face threats both inside and outside of the company, ranging from common tasks like employee management, retention, and training to sophisticated threats from external sources. They also handle the challenges of managing budgets, ongoing business priorities, and communicating well with senior stakeholders.
l I believe the CISOs' biggest concern in these days and coming days is hacker's privileges vs. security controls implementation on information and information assets. For example, yesterday’s organization held its assets on-premises and today it's hosting on the cloud which is available for everyone, plus the security for the on premise is revers and less supported.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
l Strong IT skills and knowledge including hardware, software, and networks
l Meticulous attention to detail
l Ability to use logic and reasoning to identify the strengths and weaknesses of IT systems
l A forensic approach to challenges
l A deep understanding of how hackers work and ability to keep up with the fast pace of change in the criminal cyber-underworld
l Ability to seek out vulnerabilities in IT infrastructures
l Required Certificate like: CISM/CISSP etc.
How do you define digital transformation?
Digital transformation is the process of using digital technologies to create new or modify existing business processes and customer expe-
riences to meet changing business and market requirements. This reimagining of business in the digital age is digital transformation.
According to you, how does digital transformation affect the security posture of any business?
Digital transformation leads to the adoption of new technology/new integrations/exposure to the third party to facilitate Business. But at the same time it also increased the threat landscape and an unknown risk/challenge can come up due to the landscape of business party’s data exposure, etc.
How is digital transformation impacting the job role and department responsibilities?
l Assuring that digital changes are successful and safely address consumer and management objectives. This requires adapting the organizational culture, which will have a big impact on those connected to your business such as your employee and customers.
l The changes will have an influence on the availability of resources in two ways. First, an organization needs to give existing employees new roles and responsibilities and make sure they are properly trained to drive the digital transformation forward. Secondly, in order to hire experts in digital transformation, the firm should first involve the HR department in redefining roles, responsibilities, and job descriptions. To properly accomplish a Digital Transformation objective, both alternatives will need a significant investment in both money and employee time to overcome the challenge of digital transformation.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
l Security issues are getting worse as businesses continue to adopt new technologies and business procedures and transition digitally. In fact, 85% of CISOs claimed that the commercial effect of security vulnerabilities during the digital transition ranged from "slightly" to "very
big." Likewise, the attack surface and the number of entryways into a network have significantly risen as a result of the quick adoption of new technologies, particularly IoT and multi-cloud scenarios.
l As a result of the digital transition, compliance standards and privacy protections have been strengthened. Regulators have set stricter laws and guidelines to secure consumer data and personally identifiable information as cyberattacks have gotten more harmful and sophisticated (PII). In order to maintain a sufficient level of risk management, firms must take compliance standards into account and resort to bestin-class products, processes, and qualified employees. In the crucial areas of threat management and operations, businesses are facing security challenges, such as Polymorphic assaults, DevOps, and Lack of visibility.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
Protecting critical digital systems, networks, communications, applications, data, devices, and endpoints (computers, laptops, tablets, smartphones, etc.) from unauthorized external and internal access, use, disclosure, destruction, modification, or disruption is the ongoing practice of cybersecurity. Cyberattacks can take many different forms, including (Malware, Viruses, Phishing, Ransomware, Password Breaches, Unauthorized Data Collection, Insider Threats, Endpoint-delivered Attacks, etc.), and cybersecurity solutions range in how well they defend against the threats and incidents
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
Cybersecurity breaches have gone mainstream, rising in frequency and severity, making headlines in media, and striking fear in the hearts of business managers and owners everywhere. Simply put, the need to secure organization data against security breaches. Delivering cybersecurity solutions to existing customers broadens offering, targets their biggest worry, and reduces churn.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
l Patches update and vulnerability test for your servers.
l Install antivirus for all your servers.
l Ensure to compline with the policy & regulation of Data protection.
l Have data protection stander.
l Build the right & strong password policy.
l Separate customer data from the main infrastructure.
l Conduct access review and limit unauthorized access to your data.
l Build/ implement strong security tools for customer’s personal data, and sensitive data.
l Ensure having high quality of security policy on database solution.
l Strong advisory practices narrow the attacker’s advantage.
l Prepare your disaster recovery plan and test.
l Involve yourself in BCP & DR test with your business owner to have a better understanding of their infrastructure when it connects to your solutions.

l Ensure that you have a Backup process with high-security tool of data storage.
l Availability of Support team 24/7.
l Update the High-security resources against cybersecurity threats in place.
l Conduct awareness sessions and update your customers with the latest threats.
l Share the limitation of your solution to get appropriate support from your business owners. ë
Increase in video meetings in 20201
Grow th of UC meetings with video from 2019 to 20202
11% 400% 71% 274%
Information workers who rarely or never use video in meetings3
Information workers who use video at least once a day3
Superior Audio and Video: A video bar engineered for midsize rooms, featuring a motorized PTZ lens, adaptive beamforming mics, support for two


Flexible D eployment Options: Run meetings in appliance mode without a computer for Microsof t Teams, Zoom, GoTo, Pexip, or RingCentral Or, connect to a computer or laptop and use with any sof tware
Simple Setup and Cable Management: Place on a table or credenza, or add a wall or TV mount for a sleek space-saving set up Integrated cable management keeps connections tight

Easy to monitor, manage, and suppor t: Stay informed and ahead with metrics like people count
MAKE EVERYONE LO OK AMA ZING.
My role as a cybersecurity senior involves assisting the organization to develop, maintain, and evaluate cybersecurity controls, policies, and procedures. As part of my responsibilities, I work closely with the engineering and operations teams to ensure that system controls meet security requirements. As part of my responsibilities, I oversee the results of security audits and follow up on them. Additionally, this role involves identifying the most effective methods of protecting the system, networks, software, data, and information systems from potential threats. Additionally, I have been responsible for providing professional supervision and guidance to the teams responsible for security and information technology on several occasions as well as in the creation of secure architecture, an essential component of any IT project.
It is not true that every organization has a top-level executive in charge of cybersecurity. However, it is fortunate that the Saudi National Cybersecurity Authority requires all public and semi-public organizations to hire a Chief Information Security Officer and elevate the role to the position of the top executive. To succeed as a chief information security officer, he/ she must learn to translate cybersecurity threats into business cases and communicate effectively like a business leader. CISOs face this challenge on a daily basis.
Keeping up with emerging risks is challenging in today's rapidly changing environment. Most organizations believe that they can overcome this challenge by throwing more money at the problem and implementing
ABDULLAH ALSHEHRY vCISO, Advisor, and Risk Expert., Semi-Government Environment Sector Entity
“CISOs should be able to communicate the challenges in simple terms to colleagues while understanding the impact their functions have on the organization”.
various security measures. As a cybersecurity leader, I believe that my primary responsibility is to assist my organization and team in securing information assets and to educate my colleagues through workshops and other awareness programs.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
It is essential for CISOs to communicate efficiently and effectively with senior stakeholders concerning top priorities and high-needs issues when it comes to CISO role challenges. To name a few, several developments have taken place in the past few years in relation to the rapid expansion of connected devices and other things (thanks to the Internet of Things). When combined with the use of personal devices by employees, their ability to bring their phones to work, and their use of personal devices to work from home, hackers have been given an infinite number of ways to penetrate an organization's network.
Even though data breaches can be damaging when they occur, it remains challenging to fund critical cybersecurity initiatives sufficiently. Furthermore, there is a significant shortage of skilled cybersecurity professionals due to the rapid increase in demand outpacing the available talent pool. As international data regulations continue to develop, they are becoming more complex. In the context of data handling, you may be required to adhere to multiple different protocols, such as NIST, ISO 27001, and CIS controls, based on the nature of the business. Regarding local controls and guidelines, the NCA, SAMA, and NDMO are most important for CISOs to comply with.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
A successful chief information security officer is one who maintains his or her technological expertise, learns about new technology and threats so that he or she remains up-to-date with an ever-evolving threat landscape, and becomes a strong leader and collaborator who communicates technical issues to stakeholders who don't have a need or desire to know details of the technology. CISOs should be able to communicate the challenges in simple terms to colleagues while understanding the impact their functions have on the organization.
How do you define digital transformation?
In recent years, many enterprises have implemented initiatives using digital technologies as an enabler due to the growing demand from customers for value-added products and services. As a result, digital capabilities have exponentially increased, which has created endless challenges. The concept of digital transformation, however, is not clearly defined. Many authors define digital transformation as the adoption of new digital technologies in order to facilitate significant improvements in business operations (such as enhanced customer experience, streamlined operations, or the creation of new business models). To remain competitive and survive, enterprises must implement appropriate digital transformation strategies.
According to you, how does digital transformation affect the security posture of any business?
As a result of the increased adoption of digital transformation, cybersecurity has undergone a significant change. In order to achieve new business models and enhance customer experiences, businesses are increasingly adopting more digital technologies in various areas of their industry to prevent cyberattacks, data breaches, and other cyber incidents in general.
How is digital transformation impacting the job role and department responsibilities?
The job role and department responsibilities change as a result of digital transformation adoption, which is influenced by factors such as process, people, and technology. The roles and responsibilities of individuals must be redefined to align them with the organization's transformation objectives in order to clarify the roles and competencies required.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
Our first challenge is the generation of too much information from IoT, cloud, and mobile devices. All activities are now being logged with a detect and respond mindset. It is necessary to know what we are looking for to be able to detect and respond. The problem
is made worse by ad hoc solutions and weakly managed systems, Networks and Web applications. When logging is conducted in isolation, the problem does not disappear. On the positive side, digital transformation is facilitating innovation, creating efficient capabilities, and disrupting traditional industries through new management, business, and detection models.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
As the needs of the future evolve, existing operational cybersecurity capabilities and technologies will no longer meet the needs and be enough. New approaches and a new skilled workforce will be required to mitigate threats and respond to incidents independently, however, collaboration with other solutions providers is needed.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
Due to the increase in demand for robust security defenses, the market for cybersecurity technology has been growing, as well as the number of solutions available. It is important to emphasize, however, that cybercriminals are usually successful not due to their sophisticated attack methods that can bypass security solutions, but rather due to fundamental security issues that remain unresolved in organizations.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
I cannot overstate the importance of hiring experienced professionals to lead vendor project implementation because inexperienced graduates with little or no IT hands-on experience will not help you build your success story. Unfortunately, I encountered service providers and partners who were unfamiliar with Saudi Cybersecurity requirements. It is necessary for them to understand the NCA's controls and to align the company's products and services with the NCA's requirements. Finally, the most critical indicators of the success of your brand are customer satisfaction and quality of service. ë
The drive towards digitalization has long been an ambition of organizations across the world. The transformational potential of digitalization is seemingly limitless.

With the expansion of remote working models and ongoing migration to cloud-based services, the environment for attackers has become increasingly target-rich. As more and more devices are expected to be connected to remote networks, there’s a need to create new identities. However, each of these identities offers a potential weak point for bad actors to exploit the system.
JITHIN JOY ABRAHAM, DirectorSales & Client Relations Middle East, CYBERARK
With a rise in impersonation & spearphishing attacks and targeted attacks to steal high-value identity credentials, it is essential for leaders to foster a change in their approach and culture. The importance of understanding the management of access and privilege rights must become second nature across teams and departments.
The protection of credential identities must be considered paramount in defending against
malicious intent. Many organizations are still assigning and tracking identities manually. Passwords and keys remain unchanged for a longer period and even when employees or users no longer require access, they are retained needlessly. This practice increases identities to data breach or attack. Dormant accounts can be exploited and used as an entry point. If non-human credentials such as applications, DevOps Secrets, RPA bots etc., are not continually monitored and secured, they pose similar risks. Critical data and systems are only as safe as their weakest link. An accelerated transformation and digital business require a holistic, risk-based approach to secure human and nonhuman identities.
CyberArk solutions can help organizations by ensuring potential gaps in the security are closed. CyberArk can help to reduce the surface of attack by working to address risks in legacy IT services and infrastructure, managing credential security & supply chain risk, and

ensuring successful adoption of cloud-based services, therefore, guaranteeing delivery of safe and effective processes.
CyberArk can help to reduce the surface of attack, ultimately ensuring safe and effective processes can be delivered:
l CyberArk’s DNA discovery and audit tool provides valuable insights into an organization’s exposure to risk, identify systemic weaknesses, help in quantifying the risk level & DNA highlight areas where a potential breach may occur and therefore, point towards ways to mitigate risks.
l Cloud identity entitlements and Privileges are managed and maintained across AWS, Google Cloud Platform, and Microsoft Azure. Risk reports using CyberArk AI discover, isolate, and record risky behavior for control, audit, and output in the entity’s Security Operations Centre (SOC).
l CyberArk’s Privileged Access Management (PAM) capability delivers secure management of Privilege throughout the entire life cycle of identity by reviewing and certifying access and ensuring segregation of duties. Sitting in front of either an existing legacy or modern Cloud architecture, CyberArk integrates “anything and everything”, creating an air gap between end user and asset.
l Infuse privilege controls to help isolate and stop attacks. Give humans and machines access to everything they need, at just the right time, while protecting critical assets.
l Manage the lifecycle of identities and take control of excessive permissions to enforce the least privilege.
l Secure all credentials and secrets used by non-human users. Eliminate hard-coded credentials in applications. Rotate credentials based on policies.
l Authenticate applications and containers using native application attributes and role-based access controls. Record key events with tamper-resistant audit.
l Zero Trust third-party privileged access: Provide external vendors with fast, easy, and end-to-end encrypted privileged access to critical internal systems.

For more than two decades CyberArk has been in the vanguard of information security and identity management. Its Remediation and Red Team have been instrumental in helping organizations recover from some of the most serious security breaches during this century. Widely recognized as the leader in Privileged Access Management, CyberArk solutions are used by nearly 7000 customers in 110 countries, including more than 50% of Fortune 500 companies and across a broad spectrum of both public and private sector organizations. CyberArk is the global leader in Identity Security. Centered on privileged access management, CyberArk provides the most comprehensive security offering for any identity — human or machine — across business applications, distributed workforces, hybrid cloud workloads, and throughout the DevOps lifecycle.
To Know more about CyberArk Identity Security, Visit https://www. cyberark.com/identity-security/
Spire Solutions is the Middle East & Africa’s leading value-added distributor (VAD), with exclusive distribution rights for some of the world’s best-known cybersecurity vendors (OEMs) that offer niche solutions and services. Spire engages, empowers, and enables channel partners across Middle East & Africa via various partnership models and partner success programs. Driven by a strong dedication to customer success and solving problems without creating new ones, Spire Solutions has built a reputation of being the preferred security partner to CISOs of several government organizations and enterprises in the region. For more information, visit www.spiresolutions.com or our LinkedIn page. ë

Over the last two years, the increasing complexity of modern distributed systems and application architectures has expanded the security surface area of every enterprise. It has also highlighted the limits of legacy detection and response approaches. Detection and response tooling, like XDR and SIEM, remains fixated on collecting and reporting alerts, burying teams in low-value work doing triage and potentially missing critical breaches. Applying observability principles to today’s security environments allows teams to boost the signal in a sea of noisy data and see more of what’s happening across their environments, without the limits imposed by legacy methods and products.
Observability comes from industrial control theory in the 1960s. The idea is, that if you have enough data, you can infer the internal state of a system from its outputs. This takes a fundamentally different approach than monitoring’s alert-based methods; it allows you to ask questions about a system that digs deeper than the pre-defined thresholds from your monitoring and alerting systems. Observability isn’t a replacement for monitoring, however, each plays a role. The reality is you need both observability and monitoring for full insight into your environment.
NICK HEUDECKER, Senior Director of Market Strategy
Observability gives you greater flexibility for coping with unknowns, while monitoring offers reliable processes for dealing with the expected.
Observability requires collecting massive amounts of data from systems, networks, and applications to feed its discovery process. As systems and applications become more complex, figuring out what went wrong and why becomes much more challenging. Collecting logs, metrics, events, and traces from different sources such as firewalls, agents, containers, and syslog servers, then sending these huge volumes of data to various destinations such as your SIEM tools or data analytics platforms can create an unnecessary financial and technical burden on your organization’s infrastructure. Most enterprises have 20 to 30 monitoring tools, each with its own dedicated agents, resulting in disconnected silos of information. With increasing demands to retain and monitor all forms of data traversing a company's network, security cannot simply discard excess data, so the path forward becomes streamlining data processing.
Coping with this data challenge requires a new way of thinking about
observability data. Companies are adopting specially-designed pipelines to connect the sources and destinations of observability and security data. These pipelines allow companies to route data to multiple destinations, enrich data in flight and reduce data volumes before ingestion. The term 'observability pipeline’ addresses a very specific problem that arises from data and tool sprawl.
An observability pipeline is a strategic control layer positioned between the various sources of data, like networks, servers, applications, and software agents, and the multiple destinations in today’s IT and SecOps environments. Instead of relying on siloed point-to-point
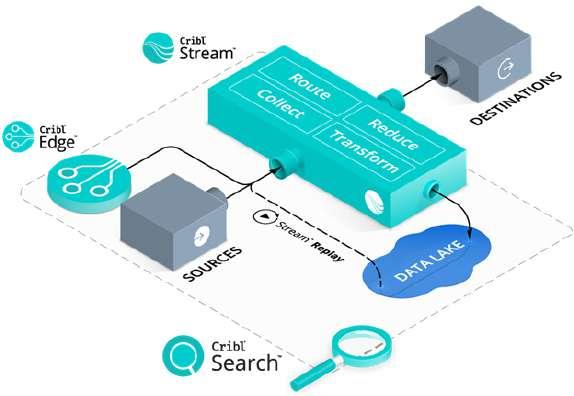

connections, an observability pipeline centralizes all of your observability data processing, giving your teams full control over every aspect of your data.
Abstracting the sources and destinations of observability data offers massive benefits to IT and SecOps teams. For example, it can provide a single point for governing data and applying consistent rules for data redaction, access control, and sharing. It can also help reduce the amount of redundant data flowing into downstream systems like logging analytics, SIEM, and SOAR platforms, or accelerate the onboarding of new tools by sharing data from one source with multiple destinations.
The observability market is maturing whilst continually opening new doors for opportunities and growth of data management and insight. As the amount of data and toolsets increase, organizations want to keep an eye on the management and complexity involved in architecting and orchestrating at a continually increasing scale. Learn more: https://cribl.io/resources/what-is-observability/
Cribl is a company built to solve customer data challenges and enable customer choice. Our solutions deliver innovative and customizable controls

to route security and observability data where it has the most value. Our solutions help slash costs, improve performance, and get the right data, to the right destinations, in the right formats, at the right time. Cribl helps you instrument everything, so you can analyze more and pay less. Join the dozens of early adopters, including leaders such as TransUnion and Autodesk, to take control and shape your data. Founded in 2017, Cribl is headquartered in San Francisco, CA. For more information, visit www. cribl.io or our LinkedIn, Twitter, or Slack community.
Spire Solutions is the Middle East & Africa’s leading value-added distributor (VAD), with exclusive distribution rights for some of the world’s best-known cybersecurity vendors (OEMs) that offer niche solutions and services. Spire engages, empowers, and enables channel partners across Middle East & Africa via various partnership models and partner success programs. Driven by a strong dedication to customer success and solving problems without creating new ones, Spire Solutions has built a reputation of being the preferred security partner to CISOs of several government organizations and enterprises in the region. For more information, visit www.spiresolutions.com or our LinkedIn page. ë
BADER HUSNI ZYOUD
Senior Information Security & Risk Management , Government Entity, Financial Department

Due to the increase in connectivity and technological development, cybercrimes, data breaches, and identity thefts are steadily increasing. Our Cover Story this month features a transformational security leader, Bader Husni Zyoud, who asserts that, if the digital transformation journey did not align with solid cybersecurity strategy and enterprise risk management it will be a gateway to attract more cyber risks and threats.
How does your organization or how do you define digital transformation?
It’s the journey and the related functions of how we utilize people, processes, technology, and data in producing new business models and new revenue streams, driven by changes in culture and customer expectations around products and services.
According to you, how does digital transformation affect the security posture of any business?
The digital transformation journey will introduce new technologies, new processes, new vision, new business, new culture, and new products. If this journey did not align with solid cybersecurity strategy and enterprise risk management it will increase the cyber risks and threats landscape as we will face skillset gap, lack of awareness, legal and governance restrictions, visibility, and privacy issues …etc.
How is digital transformation impacting your job role and department responsibilities in the organization?
Digital transformation changes the way an organization operates. Systems, processes, workflow, and culture are all part of this process. This transformation affects each level of an organization and brings together data across areas
to work together more effectively. This also requires the security and risk management to work on proactive base to provide security assurance to the organization.
Please describe your job role in the organization?
l Work with executive management to develop and maintain security programs and security functions that address specific risks and security requirements in all the organization transactions.
l Define and monitor critical success factors and key performance indicators (KPI) for the cybersecurity process & functions in the organization.
l Responsible for maintaining the enterprise vision, strategy, and program to ensure information assets and technologies are adequately protected and leading the security posture of the department based on innovative and solid KPIs.
l Develop and maintain the information security governance framework based on ISO 27001:2013, ISO 27035, NIST, PCI-DSS, NESA, OWASP, ISO 22301:2010, GDPR, and Privacy. This involved the development of security policies, procedures, and guidelines based on the results of planned gap analysis and security risk assessments. In addition, responsible for designing the security management system and advising executive management on the implementation process.
What are the most important and critical aspects of your job role for your organization?
l End-to-End Security Operations
l Compliance and Governance
l Cybersecurity Awareness & Training
l Cyber Maturity Management & KPI Management
l Digital Security Transformation, Resilience Security & Risk Management
l Third-party & Vendors Cyber Risk Management
l Cyber Security Consultation and Advisory
l Cyber Security and IT Technical Audit (On-premise and Cloud)
l Development of security plans and design of security controls
l Budgeting of Security Management
l Cyber Security and IT Projects Management
l SOC & CDC Design Management and Development
What are the typical challenges faced by a chief security officer in large and medium enterprises?
l Lack of power, decision making, and authority.
l Lack visibility into the total security program’s effectiveness.
l Organizations defragmentation and resistance against the change.
l Lack of the proper projects management and enterprise strategic planning.
l The gap between cybersecurity strategy and the organization’s vision and goals.
l The weakness of the alignment between solid enterprise risk management and cyber risks management.
l Third-party risks and weaknesses.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
With the growth of the digital world, we have seen growth in cyber threats:
l Traditionally, CISOs have come more from the technical side and perhaps did not have to understand the whole business.
l To focus on the business and managing the environment.
l Communicating how security is important to company success.
l They should have a relationship with both the CEO and the Board.
l Manage the risks to an acceptable level.
l A good CISO is also a good leader, and communicator with strategic thinking.
l In short, the role has evolved from a specific function to a vital part of a company’s management.
l Someone who can influence the organization to be able to drive towards the outcome of ensuring security and availability of systems.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
Opportunities: Simplification of the security process and technology, adopting new strategies and flexibility to adopt security, enables future digital growth, increasing operational efficiency, limiting human error, encouraging collaboration and improving communication, and enabling high-quality user experience big data feeds.
Challenges: Third Party visibility and storage security, implementing automation securely, boosting staff cybersecurity skills, poor project design and management, new culture and change resistance, privacy concerns, legal and law requirements and restrictions, governance and compliance, misconfiguration of security, the balance between user experience and data protection.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
Currently, organizations get confused with the number of solutions and the increase in cyber threats. In fact, the more technology we develop and apply, the more money we spend on cybersecurity defense resulting in a greater increase in cybersecurity breaches. And those breaches are only the ones we a) know about and b) are reported.
The upside is that cyber security solutions realized that the main concern of the solutions which they started like XDR which include the below features:
l Improved protection, detection, and response capabilities.
l Improved productivity of operational security personnel.
l The lower total cost of ownership for effective detection and response of security threats.
l Automating processes to investigate threats more effectively and efficiently. The downside can be that “Today’s cyber warfare has proven no vendor can detect zero-day malware from reaching your network, no one of the vendors can protect us 100% and no one is perfect in the cybersecurity solutions”.
At present, what are your expectations from cyber security solution vendors, channel partners and consultants?
There will be more focus on:
l Security automation
l Privacy and data protection frameworks
l Cloud Security solutions
l Zero Trust models
l Third–party risks
l Penetration test automation
l Industry based security solutions
l AI or Biometric solution for cybersecurity defense
l 5G will provide any attacker with instant access to vulnerable networks
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
l I recommend that security vendors, and channel partners focus more on industry based security solutions, culture based security solutions, and frameworks.
l Focus more on simplification and centralization of security by reducing a number of products and increasing the features to have more visibility across the digital infrastructure.
l Having long-term security solutions strategy.
l Consultants to work more on research and collaboration between the universities and the security industry.
l Starting cybersecurity as a journey, starting small then growing and putting strategic goals to achieve. ë





With the overwhelming traction seen in Industry 4.0 proceedings across the globe, new security & privacy threat landscape has emerged which have become a big challenge for IT & Security Leaders. As the Industrial 4.0 ecosystems are built with a variety of Cyber-Physical Systems (Mechanical, Electrical, and Electronic Devices) that are connected through IoT. Many of these systems are already legacy in nature which tends to have compatibility, and interoperability issues.
The Cyber-Physical Systems connected in the Industry 4.0 ecosystem will increase the connectivity of systems and humans which has drastically changed the security & privacy threat landscape of Industry 4.0 ecosystems. Industry 4.0 ecosystems and the cyber-physical systems in these ecosystems are experiencing a significant increase in cyber-attacks targeting them. This will include attacks such as ICT Supply Chain Attacks, IoT Attacks, Malware Attacks, Ransomware Attacks, IP Theft, and compromise of Data Privacy. As per a recent survey Ransomware is found as a top threat for companies. Ransomware attacks increased by 239% since 2019. The cost to recover from an attack has increased by 228%. Key cybersecurity agency has warned that manufacturing environments are at higher risk of being targeted by hackers during the COVID-19 pandemic. Recent research has found that 1-in-5 manufacturing environments in the U.S. and U.K were victims of cyberattacks over the last twelve months during the Covid 19 pandemic.
As mobile devices, wearables, and other connected devices integrated into the Industry 4.0 ecosystem collect an enormous amount of personal information and the privacy threat landscape is also emerging strongly for Industry 4.0 ecosystems. People have a common tendency of not reading any of the privacy policies provided for every device purchased/used by them in an Industry 4.0 ecosystem. Even if they would like to read, most of those privacy policies would be written with an overwhelming amount of legal terms which can’t be understood by an average person. These policies generally will have unintelligible terms & conditions with mandatory arbitration clauses that will force them to give up their rights to fight their case in the courts of law. As a result, the privacy of consumers can be compromised significantly in Industry 4.0 ecosystems.
Cyber-Physical Systems (CPS), Cloud-assisted Manufacturing, Mobile Computing, Augmented Reality, Big Data, and Artificial Intelligence kind

IoT Attacks
Physical Attack
Software Attack Network Attack
Node Tampering
RF Interference
Node Jamming
Malicious Node Adware
Physical Damage
Social Engineering
Sleep Deprivation Attack
Malicious Code Attacks Injection on the Node
Traffic Analysis Attacks
RFID Spoofing
RFID Cloning
RFID Unauthorised Access
Sinkhole Attack
Man in the Middle Attack
Denial of Service
Routing Information Attacks
Sybil Attack
IoT Attacks
of new age digital technologies are expected to play a key role in the Industry 4.0 Transformation which is very much vulnerable to a variety of cyber-attacks.
In Industry 4.0 ecosystem, systems will be built around physical devices or machines controlled by Industrial Control Systems connected to the Internet such as smart devices, and sensors which are considered the Internet of Things (IoT) Ecosystems. IoT is considered to be the critical technology element in achieving the Industry 4.0 Transformation as it will help in connecting various Cyber Physical Systems (CPS) into a single platform. There is a number of limitations and challenges in managing IoT-driven Industry 4.0 transformation which can result in a variety of Cyber-attacks and privacy compromises. Being a new age disruptive technology IoT has its threat landscape. The following weaknesses present in an IoT ecosystem can be successfully exploited by adversaries:
l Improper Platform Usage
l Insecure Data Storage
l Insecure Communication
l Insecure Authentication & Authorization
l Ineffective Cryptographic controls
l Weakness present in hardware components
l Weakness present in software components
l Poor Code Quality
l Code Tampering
l Design & Code Reverse Engineering
l Extraneous Features
l Weakness present in protocols and procedures
l RF interference on RFIDs is extensively used in the IoT ecosystem
l Lack of security awareness of users of the IoT ecosystem
Encryption Attack
Virus and Worms
Spyware and Malicious Node Adware
Trojen Social Horse
Malicious Scripts
Denial of Service
Side Chanel Attacks
Cryptanalysis Attacks:
a) Cliphertext Only Attack
b) Known Plaintext Attack
b) Chosen Plaintext or Cliphertext Attack
Man in the Middle Attack
l Human errors in developing and maintaining the IoT ecosystem
The above diagram depicts the threat landscape of IoT Attacks.
The devices connected to an IoT ecosystem will gather Personally Identifiable Information (PII) elements such as Names, National ID, and Medical Information, the compromise of which will jeopardize the privacy of the individuals. Wearable devices used by us collect all our critical health-related information which is a significant risk from a data protection and privacy point of view. The biggest privacy challenges in these days are ubiquity and invisibility. IoT Systems connect a variety of Cyber-Physical Systems in mass numbers today and transmit data without the knowledge of device owners. The IoT ecosystem is made up of technologies from various vendors which will eventually make the tracking of collection of Personally Identifiable Information (PII) elements a very difficult task.
l IoT infrastructure has to be built based on Secure & Privacy by Design principles. Building security controls into the IoT ecosystem in the early stage will be cheaper than adding them later when the vulnerabilities that exist in the system becomes public.
l Multiple cycles of system and integration testing should be performed to ensure the reliability of IoT devices that will drive Industry 4.0 Initiatives.
l Appropriate automation tools need to be identified and implemented for managing and administrating the various devices that will bridge the connected ‘things’ in an IoT ecosystem into Internet Infrastructure.
l The IoT System Architecture must consider data that should reside on the edge, and data that should be in the cloud.
l Segmenting the network architecture should be considered by having a SDN architecture built will support this.
l Multi-layered Access & Authentication Controls need to be built into an IoT ecosystem supported by Need to Know, Least Privilege, and Separation of Privilege principles.
l Appropriate authentication mechanisms such as MFS solutions need to be implemented as required.
l Subsystems connected in an IoT ecosystem should be isolated using firewalls.
l Firewalls with advanced capabilities such as deep packet inspection need to be implemented.
l Knowledge and behavior-based Intrusion Detection Systems (IDS) need to be implemented.
l Anti-Malware and Endpoint Protection Solutions such as EDR and XDR need to be considered for implementation.
l Application Whitelisting, Flow Whitelisting kind of controls need to be considered as appropriate and as required.
l Strong Cryptography controls need to be integrated into the data flow channels to prevent data leakage and privacy issues. This will help in protecting the privacy and integrity of data traveling between different network nodes of an IoT Ecosystem.
l Integrity Monitoring Solutions need to be considered for implementation as appropriate and as required which will help in ensuring data privacy and integrity.
l Data anonymization techniques need to be implemented as required to preserve the privacy of data elements.
l Periodic Security Awareness Training need to be provided for users of IoT-driven Systems.
As a new technology arrival into the modern world, IoT technology lacks defined regulatory standards and guidelines like other industrial
systems have now. However international security and privacy standards, frameworks, and laws such as US National Institute of Standards and Technology (NIST) standards, International Organization for Standardization (ISO) standard ISO 27002, North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP), Federal Information Security Management Act (FISMA), and the EU General Data Protection Regulation (GDPR) should be considered for implementation as appropriate and as required.
Security standards and frameworks such as the Global System for Mobile Communications (GSMA), International Electro technical Commission (IEC), and NIST should be implemented to improve the security posture of IoT devices. IoT Consortiums and Standards can help overcome the connectivity and interoperability issues faced in Industry 4.0 initiative driven by IoT ecosystems.

Implementation of Data Privacy Standards (ISO 27550, ISO 27552, ISO 27701, ISO 29100, ISO 29134, ISO 29151, ISO 31700, GDPR, HIPAA, CDPA, CCPA, DPA-UK), Privacy by Design Guidelines as appropriate and as required will be useful in ensuring Data Privacy in Industry 4.0 Initiatives.
With the presence of integrated mechanical, electrical, and electronic devices such as next-generation sensors, edge computers, PLCs, and other industrial equipment, the attack surface of Industry 4.0 is considered to be significantly large. Industrial Cyber Security & Operational Technology Security Solutions shall provide a solid approach to mitigate the various risks of Industry 4.0 transformation which will unleash innovation and lead to the transformation of industrial equipment and processes. With such a huge transformation wave, Industry 4.0 ecosystems are expected to trigger different security and privacy concerns around the collection, aggregation, or transmission of data over the network.
We should identify robust Industrial Cyber Security, Operational Technology Security, and Privacy Controls and implement them as required. Acceleration of investments in security solutions bolstering Industry 4.0 is expected to increase in the forthcoming period. With the way how Industry 4.0 is expected to shape up the industrial sector in the future, IT & Security Leaders should work in a proactive manner in identifying the appropriate security and privacy controls and implementing them in a fool proof manner. ë
10TH OCT 2022

LOCATION: SHANGRI-LA DUBAI, SHEIKH ZAYED ROAD, DUBAI-UAE
VENUE: AL NOJOOM BALLROOM

FOR MORE VISIT
WWW.EC-MEA.COM/GEC-AWARDS-2022/
Please describe your job role?
I currently work as a Cybersecurity and Privacy Officer (CSPO) in Huawei Portugal, meaning that my role scopes both internal cybersecurity and privacy compliance and risk management, while making sure all cybersecurity and privacy regulations and legislations are fulfilled at a country level. Our CSPO role is vital to make sure all legal and customer cyber and privacy requirements are embedded into our overall global services and products, making sure we fulfill a completely customercentric approach, thus ensuring Huawei provides the most trustworthy service and product possible.
What are the most important and critical aspects of your job role?
Without any doubt, making sure we keep our customer’s data safe and secure while maintaining the requirements we have not only with them but with laws and regulations. We strive for delivering world-class service and products while demonstrating full transparency in our operations.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
The role of a CISO is extremely challenging in today’s worldwide digital environment. Enterprises face constant digitalization and business transformation, which inevitably introduces a high pace to keep up with, while multiple threat vectors are simultaneously created. The overall complexity of the risk landscape with the ever-evolving threats associated with multiple interconnected ecosystems within the organization. This turns the CISO role into a role that needs to be able

“Cybersecurity vendors and consultants will have to step up their game and provide more effective and efficient capabilities”.
NUNO TEODORO Cybersecurity and Privacy Officer, Huawei Portugal
to shape itself, adapt, and be fast-paced enough to keep up with the business while maintaining a strict approach of holistic risk and threat managing and business enabler at the same time.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
Ability to adapt to constant changes and be a very effective communicator with the entire organizational spectrum while putting itself in a position of supporting the business and while maintaining a clear vision for managing risks in the organization.
How do you define digital transformation?
Digitalization is better defined as the improvement of customer and employees’ engagement, operations services, and product optimizations through the use of digital technologies.
According to you, how does digital transformation affect the security posture of any business?
Digital transformation potentially introduces new attack surfaces as the introduction of digital capabilities relies upon the introduction of technologies, which is prone to cyberattacks. All organizations, independently of this transformation should introduce zero

trust and security by design concepts that allow the introduction of new technologies to run smoothly and with a controlled risk to the business.
How is digital transformation impacting the job role and department responsibilities?
I don’t believe there is a big impact on the job role of a CISO and his department responsibilities. The fact is that the CISO role is an evolving role with the need for adaptation while performing continuous risk management for the business, striving for supporting the organization in complying with all security requirements.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
Organizations will tend to understand and have a clearer perspective that technology is present in most business-critical operations. With that, cyber resilience will have a bigger relevance for most organizations, thus creating a whole set of new opportunities for the CISO role to be present and relevant.
In general, looking at the present and future technol-
ogy landscape, what are the upside and downside of cyber security solutions?
Cybersecurity solutions will tend to be more relevant as with the increase in the threat landscape and the evolution of complexity of cyberattacks, efficiency, and automation provided by these tools will have a big impact in scaling the security capabilities to maintain cyber-resilient capabilities within the organization.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
Cybersecurity vendors and consultants will have to step up their game and provide more effective and efficient capabilities to pragmatically respond to the current threat landscape within the new technological space.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
Understand the organization’s requirements and its technological ecosystem in order to provide services or solutions that bring a real ROI and support the security team to deliver value to the business in a more efficient and effective way. ë
Please describe your job role?
l Developing and implementing security measures for the organization.
l Research security measures and concerns to develop effective strategies to mitigate security risks.
l Develop systems and techniques to handle sensitive information in a confidential way.
l Minimize security threats by examining infrastructure and devices, and identifying security flaws.
What are the most important and critical aspects of your job role?
l Analyzing existing security procedures and
Ministry of Interior
“Increased compliance standards and a focus on privacy concerns are additional results of digital transformation”.
ZAHEER KADIR KAZI Information Security Senior Specialist,
suggesting changes to upper management for increased efficiency and extra security.
l Present findings to managers and recommending new technologies or policy modifications.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
Cyberattacks are Becoming More Common
The pervasiveness of cyberattacks is generally CISOs' top concern and the driving force behind the majority of their day-to-day efforts. Few other threats pose a greater risk to a company’s, brand value, general operational capacity, and revenue stream.
As CISOs are responsible for all aspects of IT risk management, they will almost undoubtedly be held accountable even if an employee acts recklessly. Because of the large disparity between the lack of control and the excessive risk, the possibility of employee errors is always near the top of a CISO's list of top concerns.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
l Substantial business management experience, as well as a working knowledge of information security risk management, cybersecurity technologies, and strategy
l Familiarity with industry security standards
l Must be capable of understanding and communicating the business and profit impact of information security operations on the organization
l Security architecture definition and development
l Practices and methods of security architecture, enterprise architecture, and IT strategy
l Must have a highly-developed analytical sense
l Adaptability is one of the most essential traits of being a successful information security manager
Since digital transformation will differ considerably for each company, it can be harder to identify a universal definition. In
general, digital transformation can be defined as the integration of digital technology into all areas of a business, resulting in significant developments in how businesses operate and deliver value to customers. Beyond that, it's a cultural shift that necessitates organizations to constantly challenge the status quo, experimenting frequently, and become comfortable with failure. This sometimes entails abandoning long-standing business processes on which companies were founded in favor of relatively new practices which are still being characterized.
According to you, how does digital transformation affect the security posture of any business?
It has transformed Security into a business imperative, not an afterthought while increasing the use of maturing machine learning technologies and prioritizing AI ethics and governance.
Increased compliance standards and a focus on privacy concerns are additional results of digital transformation. Regulatory organizations have set stricter laws and guidelines to secure consumer data and personally identifiable information as cyberattacks have gotten more devastating and sophisticated. In order to maintain a sufficient level of risk management, firms must be aware of compliance standards and resort to best-in-class, certified products, procedures, and personnel.
How is digital transformation impacting the job role and department responsibilities?
There has been a huge change in the current career path and educational platforms which the new generation prefers to opt for such as Big data analytics, Machine learning, Cloud computing, Change management, and Cybersecurity. Keeping up with the current technology and trends whilst mastering the basics is the key skill required for any job role.
In order to focus on the people component of most digital transformation projects, human resource professionals have a clear role to play. This entails putting a priority on learning, development, and upskilling initiatives that enable workers to efficiently acquire skills necessary for a job in the future.
Specifically, what are the challenges and opportunities created by digital trans-
formation including IoT, cloud, and mobility, for chief security officers?
Even while data-driven decision-making, cloud usage, mobility, and the expansion of the Internet of Things (IoT) are all having a huge impact on technology, digital transformation extends beyond simply adopting new solutions. In order to foster innovation and produce better business results, organizations must also reevaluate their current business structures and procedures. The key is in combining the use of digital technologies and data processes to reimagine the firm for future growth.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
The upside may be cyber security solutions that help to maintain the confidentiality of your personal information and helps protect your business. This allows people to work in a relaxed environment. It keeps up the efficiency as well. This also results in the mechanization of numerous vocations and transforms the way you organize data and information.
The downside would be that Cybersecurity is a never-ending process that is sustained through continuous upgrades and improvements. Regarding cybersecurity, you can't just set it and forget it. It takes years to plan and put into action. The security systems in place must also be continuously monitored and updated. You must keep making investments in cybersecurity if you want to benefit from it.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
Would enjoy working with vendors who have a complete understanding of the solution they provide whilst understanding our requirements rather than a vendor who just wants to achieve their business targets.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
With almost 20 years in this industry, I have just one thing to say “OFFER SOLUTIONS, NOT PRODUCTS”. ë
Please describe your job role?
I am a prominent GRC & Cybersecurity professional in the MEA region with more than 12 years of experience in managing Cybersecurity transformation programs. My leadership ability enables a paradigm shift in an organization's cyber security posture.
I have solid experience in managing and delivering various large-scale transformation and security management projects in big enterprises. My expertise is in consulting for leadership insights and best practices in technology strategies, Enterprise Architecture, and implementation of Risk Management, Information Security, Business Continuity Management, and Cyber compliance frameworks.

What are the most important and critical aspects of your job role?
My day-to-day job entails Cyber Strategy & Governance | Security Architecture & Development Frameworks | Identity & Access Management |
Security Engineering | Threats Assessment | Vulnerability Management | Cloud Security | Perimeter security | SOC | Enterprise IT & Cybersecurity Operations | Penetration Testing | Information Security Audits | Application Security | Leadership | Project Management | Compliance/Frameworks: NIST ISO 27001, CIS, CES+.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
Role of a Chief Security officer is quite arduous in the contemporary world.
One of the prominent challenges is the limited security budget which is required to accomplish any endeavor.
Additionally, Cloud and other outsourcing model are transforming the organization’s infrastructure in a dramatic space. Covering cyber hygiene for ever-changing threat landscape is a never-ending race.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
One of the most indispensable skills is communication. Strong communication skill is the cornerstone of any Cybersecurity program.
“Articulating cyber risk in business language and persuading the top gun in the organization is a valuable and essential art”.
VARUN VIJ Head of Information Security, Government entity
Articulating cyber risk in business language and persuading the top gun in the organization is a valuable and essential art.
Secondly, adaptability and flexibility skills are required to assimilate with the business culture.
Let’s first eliminate the common fallacy that many organizations perceive as digital transformation. Digitizing existing business services is not a digital transformation. Digital transformation is a journey of strategic, organizational change which generates a culture of digital innovation that enables an organization to transform the business culture by leveraging the technology in a seamless manner.
Organizations that will not embrace the digital revolution will be on the brink of extinction by end of this decade. For example, Kodak wanted to embrace but they were too late. So Digital transformation is not a choice but a necessity.
Nevertheless, not integrating cyber security strategy with digital transformation can have serious repercussions for the organization. World economic forum sees an astounding 10 trillion dollars’ worth of cybercrime damages
every year which is ironical twice the benefit of the ICT industry. This implies that cyber are causing more harm than good.
How is digital transformation impacting the job role and department responsibilities?
Every organization on the planet is somewhat becoming a technology-driven company. This is bringing a paradigm shift in roles and responsibilities for everyone. Block chain technology, for instance, has got business use cases for almost all operational aspects of the business. Thus, we can expect every business employee to get more exposure and acquaintance with the evolving technology.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
One of the biggest challenges created by digital transformation is data management. By 2025, worldwide data will grow by astounding 175 zettabytes. Do we have the capacity to handle and analyze this much amount of data?
In terms of opportunity, digital transformation cultivates a more connected world than ever before which is efficient, effective, and productive.

In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
Cyber security solution sales have become 35 times in the last 2 decades and speak volumes. New Artificially intelligent solutions like SOAR, Breach Attack Simulation, and Network Behavioral anomaly solutions are saving a lot of headaches for security professionals as automation was the missing recipe.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
In today’s time, many security solutions have overlapping features which confound the organization and results in having numerous dashboards, all working in silos. Additionally, it results in a broken and siloes view of cyber security. Therefore, solutions rendering a unified, holistic overview of security can make a world of difference for the organizations.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
Organizations can spend a billion dollars on cyber security without affecting the bottom line. We all know that there is no silver bullet in the organization. Thus, security solutions like EDR, SOAR, and DLP must be showcased by first understanding the organization’s threat profile as there is one size fit for all. ë
Security techies need to align with the business to ensure our tech is protecting the right assets in optimized costs and efforts.”
VIKALP SHRIVASTAVA Vice President – Information Security and Technology (Global CISO), Kerzner International
Please describe your job role in the organization. Cybersecurity and regulatory compliance are never an easy deal; however, my primary focus is to protect the brand reputation, and this takes a lot of my energy to implement the best in breed solutions along with a cutting edge information security framework. We are one of the top brands in the luxurious hospitality sector in the world and it’s never easy to keep it safe from those bad cyber criminals.
What are the most important and critical aspects of your job role for your organization?
I would say coordination among the general staff, tech geeks, and CXOs of the company to ensure everyone understands the risks and provides support to protect the brand appropriately. I am a great fan of IT governance, and every large multinational organization must
practice good information security governance. This drives the smooth implementation of the latest technologies and framework to protect the brand and communication as the key.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
There are several moving pieces and bringing them all together, including the human factor of staff education, is the most difficult element. CISOs need to educate end users along with the board and CXOs in their own language and analogies, and technology can be adopted and implemented appropriately. But an insider can open a door for the hacker by just clicking on a link or exposing trade secrets loosely in public unknowingly. Alongside security techies need to align with the business to ensure our tech is protecting the right assets in optimized costs and efforts.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
The CISO owns the overall responsibility to implement the right security framework and practice the appropriate communications that upstream and downstream, in my opinion, the CISO needs to be a techie as well as a great communicator. This is a role where one needs to be a bridge between the IT tech teams and the top management like in the world of CEO/CFO/ CMO. At the same time in my opinion a CISO can be effective if he/she knows the industry well enough to tackle the business problems and align the security framework with business objectives.
How do you define digital transformation?
Digital transformation is inevitable, the world is moving towards more and more digitally
connected systems, and every segment of the business turning to more and more automation hungry. This is the new world we are living in; does it increases cyber security risk? Well, yes! But there are evolving technology and framework to mitigate or minimize at the same time.
According to you, how does digital transformation affect the security posture of any business?
One isolated lockdown computer with lots of physical volts and Z-grade security, without any connection, without any open physical or virtual port, is definitely safer than a computer connected to the internet. However, that’s not possible in the current super-connected world. Security experts need to adapt to the change and align the strategy to protect along the journey of digitization, this is always a moving trajectory and security teams need to align the framework well in advance to cover the exposed risks; risk assessments – risk treatment – pen testing – repeat.
How is digital transformation impacting the job role and department responsibilities?
With the digital transformation, information security is not only the IT department’s responsibility anymore, but this is also a shared responsibility to protect the system, data, and eventually the brand reputation. Every department and staff handles or deals with information and digital footprints of data to own the responsibility to follow the best practice.
Specifically, what are the challenges and opportunities created by digital trans-
formation including IoT, cloud, and mobility, for chief security officers?
We came a long way into offshore data/system hosting. I can recall those days of the late 90s when everyone started talking about the cloud and CISOs were too paranoid about the concept of keeping the super sensitive data at a place which you don’t see or control, being in a highly regulated industry like casinos and banks even I was opposing the migration to cloud in those days. However, around 20002005 it was very clear that the cloud is the way to go and connect with remote data centers as the future and bring physical security risks and available risks down. Now the cloud providers are doing more than what an organization does, which has a different business focus on security to protect the data and communication. All the major cloud providers are practicing the best frameworks like NIST/SOC2/ISO27001 etc. and it makes CISOs’ life a bit easier.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
There is a great focus on AI and ML these days, which is very good in terms of detecting and preventing the crafted attacks following a pattern. It’s also good for systems to learn the new behavior and act upon it, and there are always false positives and false negatives that will improve over time. The biggest issue I see is the coding practice in software development teams, and there are several companies that are very hungry to build a business quickly by creating apps or software. But they often forget to follow the best secure coding practice, which creates several back doors and vulnerabilities,
and these need to be regulated and controlled better in my opinion.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
I always suggest security vendors to understand the business industry before proposing a solution, and if solutions are customized to the industry needs they would perform better. The security vendors own a bigger responsibility to provide the solutions according to the industry risks as they can be very unique from industry to industry.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners and consultants?
Vendors should align their R&D based on CISO’s feedback, vendors should talk to CISOs and industry experts to understand the pinpoints better. There should be a communication channel among the vendor community and security professionals, and any product’s success depends on the way it is configured and placed in a framework/network. For channel partners/consultants I would suggest being closely aligned with their customers to understand actual operation issues/challenges, the more they listen more they will learn about the daily operational issues. Often company stops the use of one product due to a lack of operation knowledge rather than the technical deficiency of the product, if the staff is trained well and gets quick support, they would gain confidence in the product or solution. ë

AL NOJOOM BALLROOM, SHANGRI-LA DUBAI, SHEIKH ZAYED ROAD, DUBAI-UAE




BROUGHT TO YOU BY

Please describe your job role in the organization. To establish and provide cybersecurity services to G42 cloud customers to improve their cybersecurity posture.
What are the most important and critical aspects of your job role for your organization?
To improve our customer’s cybersecurity posture by providing a fit for purpose solutions that deliver value.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
The rapid continuous change in the cybersecurity threats and opportunities landscape, implementing the mitigation/ remediation controls at speed along, and the continuous challenge of skillset shortage globally. Also, the old challenge of embedding the required cybersecurity basics.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
Broad understanding of business needs, with the focus to deliver value rather than technology, up to date with emerging threats and opportunities, effectively manage the cybersecurity spending to enable business and respond to the cybersecurity threat.
How do you define digital transformation?
It’s the means of effectively delivering business value in the most cost-effective and secured manner that enable the service receiver a faster time to market, removing waist and optimizing business processes while miniating the right level of governance.
According to you, how does digital transformation affect the security posture of any business?
Any technology comes with its cybersecurity
challenges and threats and the more we enable technology to improve efficiently the more we introduce complexity and increase the cyber threats landscape that could cripple the organization for good in some cases. Therefore, for any digital transformation, a secure by design approach must be the default approach to ensure the right security requirements around (People, Process, and Technology) are already implemented within the digital transformation roadmap.
How is digital transformation impacting the job role and department responsibilities?
Digital transformation should enable the business to be more effective by automating more low-level tasks. Moreover, your expensive resources start to focus on what really matters and how they can optimize and deliver business value rather than sink into the day-to-day operational tasks that could be automated or delivered through suppliers as a commodity service.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
l The organizations will realize that cloud investments drive better company performance, agility, and resiliency. Cloud adoption will continue to accelerate, the cloud migration services market is expected to grow to $515 billion by 2027, and by 2025 the cloud providers will store 100 Zettabytes or 50% of the world’s data.
l The IoT market is due to reach 75 billion IoT devices by 2025, according to Cisco. IDC expects that number to reach 200 billion by 2031. Intelligent devices such as sensors, lights, and meters are indirectly connected to critical infrastructure. Experts predict that over 25% of all cyberattacks against businesses will be IoT-based by 2025, and more kill ware against self-driving cars, medical devices, and other smart devices will be developed.
l There are nearly 5.3 billion unique mobile phone users in the world today. And most of the leading e-commerce software and platforms are accessible through mobile platforms. Cybercriminals see this as an opportunity to target mobile users and use
“Experts predict that over 25% of all cyberattacks against businesses will be IoT-based by 2025”.
mobile devices as attack vectors. 2021 saw an incredible increase in the detection of Android banking malware by 200% and more zero-day attacks on iOS are observed than ever before. This makes mobile devices as ideal targets as they travel almost everywhere with their owners, this creates an extraordinary opportunity for cybercriminals.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
The upside, that global spending on cybersecurity protection to reach $1.75 trillion cumulatively from 2021 to 2025 with a growing demand for more integration and a single view of technical and vulnerability risk information will grow. Moving away from siloes security risk management to an integrated and proactive approach.
The downside, the technology to mitigate/ remediate cybersecurity threats are still lagging behind especially around AI and ML. More investment is required to accelerate the development of cybersecurity capabilities that will
deliver the edge and the means to counter the emerging and future threats.





At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?







To help the organization in addressing the fundamental cybersecurity basics, to partner with the organization rather than a supplier/customer approach, to help the organization to mature the cybersecurity capability rather than focus on selling new technology, help to realize the value delivery rather than silo technology, help reducing complexity rather than adding to it, and finally be a trusted advisor rather than a salesperson.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners and consultants?

The cybersecurity sector is faced with huge challenges in the coming years, as









cybercrime and especially state-sponsored actors are increasingly targeting the most vulnerable part of both the public and private sectors.
Threats will expand both in complexity and in scope, and therefore the need for greater cybersecurity collaboration of Data and Intelligence in the industry goes beyond economics or profitability and has become a matter of national security.
Organizations must be ready and prepared by building a fit-for-purpose cybersecurity capability through a cohesive strategy around People, Processes, and Technology that address threats and leverage opportunities.
Whether the “Big One” is an earthquake, war, or another natural or man-made disaster, the information technology community is not prepared for a massive prolonged outage. In such a circumstance, the world will experience its first long-term internet outage that the world is not prepared for. The question is best not asked in hindsight, “do we have the tools necessary to prevent, protect or avoid such a cyber-calamity?”
The question we must answer is no more “Are we going to be breached?”, rather “How fast and effective are we to recover a breach?” ë













Please describe your job role?
I am responsible for the planning and development of the overall Cybersecurity strategy for Ittihad International Investment LLC, oversite, and managing all security assurance and security governance activities within the organization. I am also responsible for reporting the information security program to the stakeholders and executive committee efficiently and effectively, developing and reporting the information security key performance indicators and oversite the information security operation.
What are the most important and critical aspects of your job role?
My role ensures that the organization’s information and assets are protected from a variety of technology attacks, threats, theft, or corruption from outside and within the organization. My duty is also to ensure effective Cybersecurity awareness program, and the development and implementation of Corporate Security Policies and Risk Mitigation and Compliance Posture including legal laws of UAE.

What are the typical challenges faced by a chief security officer in large and medium enterprises?
Based on my professional experience in UAE, a chief security officer faces many challenges like staff retention, training to threats from external sources, and with respect to business I must
“The upside of cybersecurity solutions is the availability of many tools and utilities to protect corporate and personal digital footprint.”
mention poor communication and planning adds more hurdles to security team targets.
What are the key skills required for an ideal chief security officer in this age of digital transformation?
A CSO with the skill to design security programs to mitigate threats before they become a real problem for an organization.
How do you define digital transformation?
I would say digital transformation is all about change of organizational culture to embrace the latest technologies and solutions, those technologies can assist to achieve organizational vision, and goals.
According to you, how does digital transformation affect the security posture of any business?

Corporate commitments and pressure from management on CIOs to achieve digital transformation as soon as possible bypassing standard security practices, while onboarding new business solutions which has an extremely large impact on the organization’s security.
How is digital transformation impacting the job role and department responsibilities?
Department must be agile and collaborative by using modern IT infrastructure and cloud environments which demands new roles that require the subject matter experts and professional people to deliver technical solutions and services to support business with a better user, and customer experience.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud,
and mobility, for chief security officers?
The rapid adoption of digital transformation, especially the adoption of IoT, mobility, and cloud environments, has increased the attack surface and the number of entryways into a network. This is especially true if organizations do not have integration across their security solutions and incomplete visibility into users, applications, data, and network behavior.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
The upside of cybersecurity solutions is the availability of many tools and utilities to protect corporate and personal digital footprint.
The downside of this is to find the right solution to protect the corporate digital landscape without adding unnecessary or parallel solutions with minimum risk acceptance.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
As a corporate Cybersecurity person, I expect vendors to focus on evolving their solutions by creating and joining ecosystem instead of staying in silos they must come together to learn and share findings from their customers or prospects. Partners and consultants must be on the customer side, and they must understand the real problems of clients by conducting multiple sessions with the security team as well as the business to identify challenges and propose the best solution to protect users, applications, data, and infrastructure.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners and consultants?
I would like to recommend emphasize on automation, there is huge demand for automated cybersecurity solutions to assist cybersecurity professionals by helping them with automatic actions on threats and attacks with minimum involvement of human intelligence and support. ë
“The emerging threats and an everchanging infrastructure landscape due to digital transformation have made it critical to prepare for an
ZAHEER SHAIKH Chief Information Security Officer, Al Maryah Community Bank LLC
Please describe your job role?
My role as a founding Chief Information Security Officer (CISO) is to develop and refine the Information and Cyber security strategy, objectives, policy, regulatory compliance, risk identification, mitigation and maintain cyber hygiene and awareness with internal and external stakeholders.
What are the most important and critical aspects of your job role?
The bank is the UAE’s first digital bank completely hosted on the cloud, ongoing basis applies risk-based thinking which enables the units to make the right security decision and set the priorities. Additionally, identifying the gaps in the design and operational effectiveness in the security architecture, implementing controls, and recommending changes or enhancements as desired.
What are the typical challenges faced by a chief security officer in large and medium enterprises?
This is my viewpoint and not my organization’s, the observations noted so far while meeting other chiefs and heads on the field -
l Strategic aligning the cybersecurity efforts with the business strategies to support the organization’s objectives
l Leadership buy-in, organization culture, setting the tone and the cadence for embracing the security
l The digital transformation has triggered the ongoing change in the attack surface hence continuous evaluation of new cyber threats and data breaches is needed to develop effective security controls
What are the key skills required for an ideal chief security officer in this age of digital transformation?
l Strong foundation and in-depth technical knowledge of security engineering, protocols, authentication, network security, and cryptography for on-prem and cloud setup
l Technically qualified solutionist to assess threats, vulnerabilities, and security laws and regulations
l Familiarity with industry-standard
security frameworks and professional security certifications
l Understand the types of cyber-attacks, threats, and subsequent threat modeling
How do you define digital transformation?
My perspective of digital transformation on “Transforming culture enabled by Technology” is that a new sustainable system has a competitive advantage not just going digital but as the digital innovators. These are the strategic planned organizational change that empowers the team to create new methods to create a highly responsive strategy and fearless culture of innovation.
According to you, how does digital transformation affect the security posture of any business?
The emerging threats and an ever-changing infrastructure landscape due to digital transformation have made it critical to prepare for an emergency due to deterring the security posture which involves Products, Channels, Customers, Operations, and Employees. Hence it is essential to review the organization’s risk profile, automate the monitoring functions, upskill the security team and build a strong partnership as collaboration is crucial for resilience.
How is digital transformation impacting the job role and department responsibilities?
The pandemic has triggered a huge interest in business and digital transformation, which has exposed organizations to increased levels of cybersecurity threats. Whilst the mundane business process was automated for the Straight Through Process (STP), the ripple effect mandated the security decision-makers to automate many of the security operations enabling employees to participate successfully in transformation without exposing the organization to threats.
Specifically, what are the challenges and opportunities created by digital transformation including IoT, cloud, and mobility, for chief security officers?
“In the middle of every difficulty lies opportunity”, whilst the digital evolution has carried the various challenges like access, data security, and cross border comminution which has increased in the attack surface the digital innovative geeks. The organization has unearthed the possibilities of automating the operations with the disruptive technologies like Artificial Intelligence (AI), Machine Learning (ML) and Low-Code/No-Code (LC/NC) which has given the security unit an upper edge in mitigating the risk to a large extent.
In general, looking at the present and future technology landscape, what are the upside and downside of cyber security solutions?
As the threats and vulnerabilities are growing with the transformation and so are the risk, the upside here is the security solutions are innovating with the necessity of the hour, however, the downside is the supply vs demand for the right skill set in the market supporting the solution which every organization is struggling with.
At present, what are your expectations from cyber security solution vendors, channel partners, and consultants?
A subtle product or off-the-shelf solution which is easy to implement, maintain, and customized as per the business requirement or the use case. Easy to communicate on the open APIs with the up and downstream integration systems or partners. Doing more with less to increase compliance on efficiency and security posture management.
At present, what advice or feedback or recommendation would you give cyber security solution vendors, channel partners, and consultants?
Don’t overkill the organization or the chief security officer with a range of products or solutions that don’t fit all their strategy/ objectives. Study the prototype of the organization and the relevant uses case and basis that build the business case or data sheet for the review and assessment. ë

Cloud-native Platform Provides Expanded Integrations, Software Bill of Materials, and Additional Language and Framework Support
Veracode announced the enhancement of its Continuous Software Security Platform with substantial improvements to its integrated developer experience. New features include extended integrations to support software composition analysis (SCA), a software bill of materials (SBOM) Application Programming Interface (API), and additional language and framework support for static analysis, further enhancing developers’ ability to secure software in the environments where they work.
Brian Roche, Chief Product Officer at Veracode, said, “Modern applications are mostly assembled, not written from scratch. Open-source code makes up a significant proportion of audited code bases—for example, 97 percent of the typical Java application is made up of open-source libraries—increasing security risk and the need to identify supply chain risk. Our SBOM API, is designed to make it easier for developers to inventory their code base, including third-party components, allowing them to act quickly if new vulnerabilities emerge. Since the launch of our Continuous Software Security Platform in May, we have introduced additional capabilities that meet developers right where they work: in the integrated developer environment (IDE), code repository, and command line interface. These innovations are designed to drive adoption by making the platform even more developer friendly.”
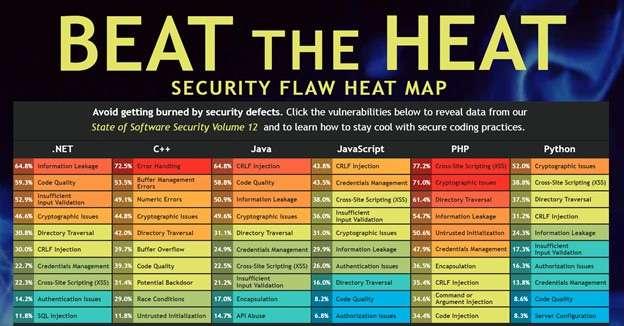
Veracode’s platform supports 100+ languages and frameworks, including those for cloud-native application development and older languages used with legacy assets, like COBOL. Large enterprises have applications across myriad languages and being able to deploy a continuous security testing solution across them simplifies the process, while providing consistent results. The company’s latest State of Software Security (SoSS) 12 research analyzed the most common flaws by language and revealed that a prevalent flaw for one language may not be of any concern for another.
For example, cross-site scripting (XSS) is the most common flaw for PHP, at 77 percent, but doesn’t even make the top 10 for C++*. Moreover, flaws change constantly, meaning that even if a flaw isn’t prevalent in a programming language, practitioners should still take active steps to prevent it from impacting their code. Since remediation tactics vary by flaw and programming language, having a broad array of language support in one place makes developers’ jobs easier by freeing up their time to focus on meeting tight deployment deadlines.
Peter Evans, Engineering Director at QAD Precision GTTE, said, “Veracode brought a complete platform for us to build security tools into our development pipelines, as well as helped us grow our knowledge to keep getting better at security. Veracode was also a good fit because the platform can scan Java code in the Spring framework where we develop our software. We’ve gone from reviewing code to integrating continuous scans into our daily pipelines. Security threats don’t stand still and Veracode provides us the tools to keep up with the latest vulnerabilities and rules.”
Notable updates to the Veracode Continuous Software Security platform include:
SBOM FOR SCA
l With government regulations driving standards for securing software supply chains, having an SBOM is increasingly important for organizations. Veracode’s SBOM API in SCA enables developers to easily generate an SBOM in CycloneDX JSON format—one of the approved formats for compliance with the U.S. Executive Order. This helps confirm the code they’re using, or building, is free from vulnerabilities.
To make software security a seamless experience, Veracode continues to introduce integrations that meet developers where they work.
l The Veracode Azure DevOps Extension has a new “SCA Flaw Importer” to automatically import SCA flaws into Azure DevOps Boards and Work Items
l The soon-to-be-released Veracode for Visual Studio Code extension provides detailed information on vulnerabilities, licence risks, and recommended versions of open-source libraries and transitive dependencies so developers can rapidly respond to any risks

l The company is committed to keeping up with the latest language and frameworks with which developers work, adding support for
Rails 7.0, Ruby 3.x, and PHP Symfony
Roche concluded, “As a pioneer of application security, we are uniquely positioned to combine unrivalled experience with the latest innovations in cloud development. Unlike on-premise vendors, our SaaS solution is both scalable and elastic, meaning customers are always prepared to meet unexpected demand. Powered by nearly two decades of cumulative data, our platform provides detailed comparative historical reviews against industry benchmarks and peers—a level of insight highly relevant for leadership teams and the board. Our platform also saves developers time by delivering highly accurate results and enabling them to find and fix vulnerabilities in minutes, meaning they can ship code quickly with the confidence that it is secure.” ë

Q2 has witnessed some of the largest attacks the world has ever seen including a 26 million request per second HTTPS DDoS attacks that Cloudflare automatically detected and mitigated. Furthermore, attacks against Ukraine and Russia continue, whilst a new Ransom DDoS attack campaign emerged.
The Russian and Ukrainian Internet
l The war on the ground is accompanied by attacks targeting the spread of information.
l Broadcast Media companies in the Ukraine were the most targeted in Q2 by DDoS attacks. In fact, all the top five most attacked industries are all in online/Internet media, publishing, and broadcasting.
l In Russia on the other hand, Online Media drops as the most attacked industry to the third place. Making their way to the top, Banking, Financial Services and Insurance (BFSI) companies in Russia were the most targeted in Q2; almost 45% of all application-layer DDoS attacks targeted the BFSI sector. Cryptocurrency companies in Russia were the second most attacked.
l We’ve seen a new wave of Ransom DDoS attacks by entities claiming to be the Fancy Lazarus.
l In June 2022, ransom attacks peaked to the highest of the year so far: one out of every five survey respondents who experienced
BASHAR BASHAIREH, Managing Director, MiddleEast & Turkey, Cloudflare
a DDoS attack reported being subject to a Ransom DDoS attack or other threats.
l Overall in Q2, the percent of Ransom DDoS attacks increased by 11% QoQ.

l In 2022 Q2, application-layer DDoS attacks increased by 72% YoY.
l Organizations in the US were the most targeted, followed by Cyprus, Hong Kong, and China. Attacks on organizations in Cyprus increased by 166% QoQ.
l The Aviation & Aerospace industry was the most targeted in Q2, followed by the Internet industry, Banking, Financial Services and Insurance, and Gaming / Gambling in fourth place.
l In 2022 Q2, network-layer DDoS attacks increased by 109% YoY. Attacks of 100 Gbps and larger increased by 8% QoQ, and attacks
lasting more than 3 hours increased by 12% QoQ.
l The top attacked industries were Telecommunications, Gaming / Gambling and the Information Technology and Services industry. l Organizations in the US were the most targeted, followed by China, Singapore, and Germany. This report is based on DDoS attacks that were automatically detected and mitigated by Cloudflare’s DDoS Protection systems.
Commenting on the report, Bashar Bashaireh, Managing Director, Middle East & Turkey, Cloudflare says, “Cloudflare’s mission is to help build a better Internet. A better Internet is one that is more secure, faster, and reliable for everyone — even in the face of DDoS attacks. As part of our mission, since 2017, we’ve been providing unmetered and unlimited DDoS protection for free to all of our customers. Over the years, it has become increasingly easier for attackers to launch DDoS attacks. But as easy as it has become, we want to make sure that it is even easier — and free — for organizations of all sizes to protect themselves against DDoS attacks of all types.”
There’s no denying that Covid-19 had an irreversible impact across every industry, perhaps most notably the healthcare sector. Two years ago, healthcare providers and facilities had to make huge changes in order to adjust to the influx of Covid patients. Many of these changes involved digitization, as between the initial uncertainty of Covid transmission and on-and-off lockdowns, digital services went from optional to mandatory overnight.
As healthcare organizations continue to introduce IoT devices to their operations, their digital success stories depend on one fundamental component – a reliable network. Resilient and secure connectivity must underpin every institution’s digital roadmap, upholding and progressing the convergence of IT, patient care and operational efficiencies. So, just how do they achieve this?
Many legacy networks that IT teams in the healthcare sector are pushed to work with were designed during a pre-Covid time where applications were static. These outdated networks not only create their own roadblocks, but trying to adapt them to support today’s demands can also result in huge operational issues. An IT team tasked with scaling their network up to support a surge in users and devices across various locations would be faced with having to manually process every connection type and device if a network hasn’t been modernized.
Fast forward to 2022 and the aforementioned shift towards personalized healthcare and increased dependence on mobile devices and applications means that this type of process is simply no longer sustainable. In order to support the surge of IoT devices, and unlock the opportunities they bring around autonomous, predictive and analytical capabilities – healthcare organizations must firstly upgrade and modernize their networks.
Here, organizations should consider opting for a

cloud-centric network architecture solution, as whether it is consumed in the cloud or on-premises, this will provide organizations with much needed agility for future scale and connectivity.
On top of this, networks based on traditional VLAN architectures will struggle to accommodate huge amounts of IoT devices, so modernizing WAN solutions with SD-WAN should be seen as the next step for healthcare organizations. Offering greater efficiency and cost savings, hospitals and clinics can also opt for an approach that doesn’t involve the wholesale replacement of their current infrastructures, but rather look for options that coexist with current architectures. Here, healthcare organizations can introduce network overlays such as EVPN/VXLAN alongside existing infrastructure to learn how to adapt these protocols to current and future environments.
As all these IoT devices churn out large quantities of health information, automation merged with other smart technologies such as machine learning can help turn into actionable insights that healthcare organizations can use to build new solutions.
Here, simplified workflows can also help alleviate administrative burdens and redeploy precious time so that staff can focus on patient care. From apps that help patients manage their care themselves, to online symptom checkers and e-triage AI tools, virtual agents that can carry out tasks in hospitals, or a bionic pancreas to help patients with diabetes, adding AI to your technology arsenal can greatly enhance patient care. Of these AI applications, some help improve healthcare operations by optimizing scheduling or bed management, others aid population health by predicting the risk of hospital admission or helping detect specific cancers early enabling intervention that can lead to better survival rates; and
others even help optimize healthcare R&D and pharmacovigilance. All of this can go a long way to help hospitals make better use of their resources in an age where they’re more stretched than ever. But it takes a strong and secure network to support this.
While a modern network and the IoT devices and AI solutions it can support have the potential to transform healthcare in practice, the growing use of connective devices also poses increased risk for healthcare organizations.
The key to a secure network is visibility. This means that everything, from sensors to visitors phones, needs to be individually identified, secured and monitored. By ‘fingerprinting’ every de-vice this way, any vulnerability can be spotted and addressed immediately before it is exploited. This level of nuance is also particularly vital in healthcare. In life-or-death environments critical-care devices that need to run continuously can’t be treated the same way as those which can be disconnected if needed. Instead, Zero Trust architectures ensure that all devices and users trying to access the network are identified and authenticated, before providing the least amount of ac-cess required through a predefined security policy.
The digital transformation of our healthcare system is being driven by the benefits of a truly IoT-device connected environment. However, in order to unlock the promises of this future, it is fun-damental that organizations have a network in place to support this. By deploying a modern and secure network and leveraging automation, healthcare organizations can drive operational effi-ciencies, redeploy employee time and ultimately enhance patient care. ë

WHERE TECHNOLOGY IS BORDERLESS, AMBITIONS ARE FEARLESS, AND LEADERSHIP IS LIMITLESS
Algeria
Bahrain
Botswana
Egypt
France
Germany
Ghana
Hong Kong
India
Italy
Ivory Coast
Kenya
KSA
Kuwait
Mauritius
Malaysia
Morocco
Netherlands
Nigeria
Oman
Pakistan
philippines
Qatar
Singapore
South
Spain
40 COUNTRIES 4000 C-LEVEL EXECS 300+ SESSIONS
Africa

Switzerland
200+ EXHIBITORS
Tanzania
Thailand
Tunisia
Turkey
UAE
Uganda
UK
USA
Vietnam
BROUGHT TO YOU BY