8 minute read
Obstacle Avoiding Robot
Software Engineering & Web Applications Obstacle-avoiding robot
EMMA HARRISON | SUPERVISOR: Dr Ingrid Vella COURSE: B.Sc. IT (Hons.) Artificial Intelligence
Advertisement
When assisted by obstacle avoidance techniques, an autonomous mobile robot could navigate itself around an unseen space without any human intervention.. Such a robot would interpret information acquired by its sensors to detect obstacles in its way and navigate around them.
This project employed a Lego Mindstorms EV3 kit to build a wheeled differential drive robot, i.e., a mobile robot whose movement is controlled by two separately driven wheels. Since the robot is required to avoid obstacles without bumping into them, the robot was fitted with an ultrasonic and an infrared sensor at its front to measure the distance from any obstacles.
Initially, Bug2 algorithm was investigated for obstacle avoidance. In this case, the robot followed a goal line representing the target path and whenever it encountered an obstacle, it followed the obstacle’s perimeter until it encounters the goal line to follow once again. This process was repeated until the robot reached the desired target location. The vector field histogram (VFH) algorithm was also investigated. This algorithm works over three distinct steps. Firstly, using the robot’s sensors, it constructs a 2D histogram grid which is continuously updated in real time. Secondly, it constructs a 1D polar histogram around the robot’s current location in order to reduce the histogram grid. Finally, candidate valleys are selected and, once the centre of the selected direction would be determined, the robot’s orientation is steered to match it.
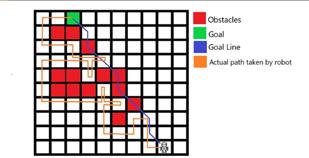
The algorithm was tested using a 10x10 grid as the robot’s environment. The grid included a goal location, and different obstacles were randomly placed in the grid in order to deliberately interfere with the path that the robot was planning to take. In each of the ten tests carried out, the robot reached its goal without ever colliding with obstacles.

Figure 1. The final version of the robot
Figure 2. The Test 10 path taken by the robot when programmed with the Bug2 algorithm
Auto-mobile Control Area Network security issues involving fuzzing
DAMIEN SPITERI BINETT | SUPERVISOR: Dr Clyde Meli | CO-SUPERVISOR: Dr Colin Layfield COURSE: B.Sc. IT (Hons.) Software Development
The Controller Area Network (CAN) bus protocol is used to network computerised car systems. Security was not a priority when the protocol was designed, as it was initially meant to connect a small number of electronic control unit (ECU) devices in a closed system. Modern cars now have their CAN bus accessible through a diagnostic port and ECUs that communicate wirelessly to outside devices, such as remote keyless entry systems and over-the-air updates to software systems and telematics systems. These systems ‒ combined with the importance of computerised systems in cars, especially in vehicles with self-driving capabilities –would help minimise any security risks that may lead to serious issues spanning from theft of the automobile to injury and possible loss of life. The software-testing method of fuzzing, which is the generation and input of unexpected inputs to a system, has been shown to be a viable attack on devices on the CAN network.
For the purpose of the experiment involving the CAN network, an attack device was developed. This comprised a Raspberry Pi and an MCP2515 module, which allowed the device to communicate with a CAN network. Once connected to the CAN network, the device could monitor all traffic on the network. The resulting data would be used to fuzz messages and send them to the network in order to attack devices on the network. The data could then be viewed, and attacks would be orchestrated through a web interface accessed by connecting to the devices transmitted Wi-Fi network.
In order to test the attack device itself, a testing device that would emulate the dash system of a car was developed. This device would receive CAN messages and process them with a view to changing instrument values and logging all messages and instrument changes. The testing device consisted of an ESP8266 microcontroller, an ILI9341 LCD screen, an MCP2515 module, and an SD card module.

Figure 1. The attack device Figure 2. The testing device

Software Engineering & Web Applications Procedurally generating crowd simulations with human-like behaviours
DANIEL JAMES SUMLER | SUPERVISOR: Dr Sandro Spina COURSE: B.Sc. (Hons.) Computing Science
The presence of crowds of people is becoming increasingly commonplace in areas such as gaming, where simulations are typically used to procedurally generate crowds [1]. The interactions within these crowds are key to adding an extra layer of immersion and realism. The method used to model these interactions will generally affect the expressiveness and scalability of these simulations.
This study sought to address these issues by proposing a framework that would simulate realistic crowds, in which the actions of an entity would not directly influence the actions of another entity, as well as adding personal decision-making, which is not commonly seen in other simulations.
The chosen approach was to create a framework that uses deterministic finite state automata (DFSA) to model the behaviour and interactions of each individual. The simulation area contains a multitude of different objects (such as benches and shops) which are represented as systems ‒ and each with its own DFSA. Once an entity enters a system’s range, they are to decide whether to transition to the system’s DFSA. Each system contains instructions in the form of a DFSA, which the entity would follow. The systems are independent of every other system, thus allowing new systems to be added without affecting others.
The simplicity of how the framework was set up allows people with little or no technological background knowledge to be able to create a custom environment for their own simulation. The choice of creating a framework for such simulations allows for continuous re-use to model various types of situations.
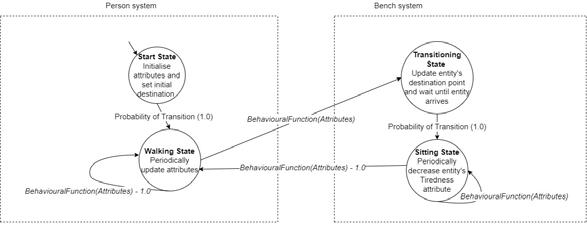
In order to determine whether an entity would decide to transition to a system’s DFSA, each entity contains its own attributes, which alter its decision-making process throughout the duration of the simulation. Attributes such as Hunger and Tiredness will help an entity decide whether to go to rest on a bench, buy something to eat at a shop or keep walking. Over time, each of these attributes will change depending on the action a person is taking, such as the action of walking, which increases the sense of tiredness and hunger. Figure 1 explains further how this process functions.
The framework described above was evaluated by testing its scalability and expressiveness. Scalability was measured by the complexity and size of the generated environments alongside the number of simulated people in the scene, together with the amount of time it would take to create and run a simulation. On the other hand, expressivity was measured by the unique number of simulation environments that could be modelled, including the extent to which environments can be customised by the user. This includes being able to model a simulation environment in which one may customise the internals of a building, such as a shop.
This project attempts to deliver a working solution to the situation outlined above. The proposed solution would allow users to create their own simulation for various situations, without having to create an entire interaction model from scratch.
Figure 1. A ‘person’ DFSA is extended when within the range of a ‘bench’ system – this allows more transition options from the ‘person’ system, thus allowing the entities to interact with other systems.
REFERENCES
[1] Xu ML, Jiang H, Jin XG et al. “Crowd simulation and its applications: recent advances”. JOURNAL of COMPUTERSCIENCE and TECHNOLOGY 29(5): 799-811 Sept. 2014.
Procedurally generating game content with the use of L-Systems
MIGUEL VELLA | SUPERVISOR: Dr Clyde Meli | CO-SUPERVISOR: Dr Michel Camilleri COURSE: B.Sc. IT (Hons.) Computing and Business
Modern-day game projects rely on teams of highly skilled, multidisciplinary teams, which include story writers and graphic designers. These projects also present a number of problems during development, such as issues relating to the budget, quality of the game and scheduling [1]. Bearing in mind the resulting pressure that game developers generally experience, this project seeks to contribute towards alleviating some of this pressure.
The proposed solution is largely based on the application of procedural content generation (PCG) through L-systems. PCG is a technique used to generate game content algorithmically, rather than generating this content manually. L-Systems were introduced by Aristid Lindenmayer as a method of simulating the growth of multicellular organisms, such as plants. Its applications have been extended to other areas, including gamecontent generation, in view of the string rewriting nature of L-Systems.
The approach chosen for this project was to develop a two-dimensional rogue-like dungeon game that utilises L-Systems as a framework to generate the level design of the dungeon in the game, creating a main path and a number of branching paths. The main path would lead to a boss room, which is the only way to finish the game. However, the branching paths may offer power-ups that would benefit the player throughout the game. The rooms in either path option would need to be generated such that every room would be accessible through at least one other room. The rooms of the main path should be connected to one another meaning that, should they choose to, players could ignore the sub-paths generated by the algorithm, and head straight to the boss room.
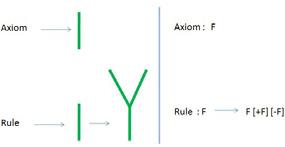
Figure 1. String-rewriting nature of L-Systems [3]

Figure 2. A tree generated in Unity3D using L-Systems [2]
REFERENCES
[1] F. Petrillo, M. Pimenta, F. Trindade, and C. Dietrich, “What went wrong? A survey of problems in game development,” Comput. Entertain., vol. 7, no. 1, pp. 1–22, Feb. 2009, doi: 10.1145/1486508.1486521.
[2] P. Fornander, “Game Mechanics Integrated with a Lindenmayer System,” Blekinge Institute of Technology, 2013
[3] “Enhancing Computational Thinking with Spreadsheet and Fractal Geometry: Part 4 Plant Growth modelling and Space Filling Curves” – Scientific Figure on ResearchGate. Available from: https://www.researchgate.net/figure/Rule-Interpretation-of-Bracketed-L-System-Witha-use-of-the-rule-we-obtain-an-order-of_fig11_258652653










