This meteoric rise of NVIDIA in the past few years driven by its domination of the AI chips market is a success that is unparalleled in the industry. With the company nearly holding 88% market share in the GPU market, NVIDIA looks poised to lead the way towards relentless innovation in the AI market.
As of today, most technology leaders have signed up strategic partnerships with NVIDIA and its GPUs are powering the infrastructure of the large cloud providers and enterprises. NVIDIAs GPUs have become the default processors for AI workloads and are driving innovation across domains from deep learning and neural networks to autonomous vehicles and data centres.
While NVIDIA has moved to occupy center-stage in the AI computing era, it has come a long way from its origins as a GPU manufacturer primarily focused on gaming and entertainment. Over a decade back, NVIDIA played second fiddle to Intel as a GPU chips provider for Intel powered laptops and PCs. While Intel continues to lead in the PC Microprocessor market, it hasn’t yet made significant strides in the AI market vis-à-vis NVIDIA. NVIDIA laid the path to its current success with the prescient unveiling of its CUDA platform back in 2006 that could be used by developers for general purpose parallel computing and speed up applications. Riding on its unprecedented success, NVIDIA has become one of the leading technology stocks with a dramatic surge in the past couple of years and is likely to outpace most stocks in the next few years.
There could be some competition along the way ahead. Some nascent AI startups could develop alternative architectures and cheaper AI chips or perhaps some of the bigger technology companies may come out with breakthroughs. Apart from Intel, AMD could also be one of the contenders as it has adapted its GPUs for executing AI workloads in the data center and increased its focus on the AI business. While NVIDIA seems to be far ahead, yet the contenders may gain ground in the next few years.
RAMAN NARAYAN
Co-Founder & Editor in Chief narayan@leapmediallc.com Mob: +971-55-7802403
Sunil Kumar Designer
R. Narayan Editor in Chief, CXO DX
SAUMYADEEP HALDER
Co-Founder & MD saumyadeep@leapmediallc.com Mob: +971-54-4458401
Nihal Shetty Webmaster
MALLIKA REGO
Co-Founder & Director Client Solutions mallika@leapmediallc.com Mob: +971-50-2489676














14 » ENHANCING CONNECTIVITY
D-link has over the years played a key role in addressing network infrastructure requirements of mid-market Business enterprises over the years
22 » ADVOCATING A HOLISTIC APPROACH TO CYBERSECURITY
Ram Narayanan, Country Manager at Check Point Software Technologies ME discusses the need for an integrated approach to cybersecurity
24 » TOWARDS STRONGER DATA SECURITY
Naji Salama, CEO, IT Max Global discusses the need for data insurance in the face of cyberattacks
28 » THE AI REVOLUTION: FROM SCIENCE FICTION TO SMART FACTORIES
Andrew Burton, Global Industry Director Manufacturing discusses how AI empowers manufacturers to optimize processes, enhance product quality, and streamline operations
30 » ONLY A HOLISTIC APPROACH TO CX WILL DRIVE CUSTOMER LOYALTY
Ahmad Rodolph Khoury, MDDubai & Northern Emirates, Avaya discusses the need to evolve a holistic approach to CX
32 » THREE THINGS YOU SHOULD KNOW ABOUT AI APPLICATIONS
23 » HIDDEN CHAMPIONS: BEHIND THESE POPULAR APPLICATIONS ARE HARD DRIVES
Rainer W. Kaese, Senior Manager Business Development Storage Products at Toshiba Electronics Europe says that wherever large volumes need to be stored at low cost, you need hard drives
26 » TRANSFORM MEETING SPACES TO BOOST ENGAGEMENT
Ekta Puthran, Head of Sales APAC & MEA - Collaboration, Barco discusses how Video bars have emerged as a cornerstone of modern meeting spaces, seamlessly blending in-person and remote collaboration
Lori MacVittie, F5 Distinguished Engineer discusses key aspects to understand when defining an AI strategy
34 » HOW TO DEAL WITH UNMANAGED DEVICES AND SECURITY
Implementing zero trust involves adopting a comprehensive philosophy across all security operations opines Richard Sorosina, Chief Technical Security Officer EMEA and APAC, Qualys



Omnix’s latest offering accelerates AI deployment, cuts costs, and enhances customer interaction across diverse sectors

Omnix International, a leader in digital transformation and innovative technology solutions, announced the launch of its newest service, Conversational AI-as-aService. Part of Omnix's state-of-the-art Hyper Automation suite, this service simplifies the deployment of conversational AI for enterprises, significantly reducing both the time and cost traditionally associated with such implementations.
Conversational AI-as-a-Service from Omnix provides a pre-built, scalable solution that can be deployed in its own environment. This removes the burden on enterprises to set up infrastructure, procure licenses and software, and hire professional services, thus enabling the utilization of conversational AI at a fraction of the usual cost and time. This versatile service can be implemented across various industries.
“Our Conversational AI-as-a-Service is a game-changer for enterprises aiming to leverage AI technology without significant upfront investments. By offering a pre-built, scalable solution, we eliminate the complexities and high costs associated with AI infrastructure, making it accessible and affordable for businesses of all sizes. Our solution is designed to streamline operations and enhance customer interactions,” said Walid Gomaa, CEO of Omnix International
Omnix places a high priority on security and customer data protection, leveraging local Microsoft Azure's robust security features and additional external security measures to ensure the highest level of data security and compliance with all regulatory requirements.
The Google Cloud offices in Kuwait will serve as a hub for collaboration and innovation
Google Cloud announced the opening of its new offices in Kuwait licensed by Kuwait Direct Investment Promotion Authority (KDIPA) at an event attended by His Excellency Omar Saud Al-Omar, Minister of Commerce and Industry and Minister of State for Communication Affairs. This expansion further signifies Google Cloud's commitment to supporting Kuwait's national digital transformation journey, including the modernization of government services and the advancement of economic development.
In January 2023, Google Cloud announced a national alliance framework agreement with the Kuwaiti government to develop a roadmap for a comprehensive digital transformation program across government entities and key state-owned enterprises. The partnership will bring Google Cloud's cutting-edge technology, data expertise, and AI capa-

bilities to government agencies and key state-owned entities, enhancing their operations and cybersecurity.
Abdul Rahman Al Thehaiban, Managing Director of Google Cloud in the Middle East, Turkey and Africa said at the event: “Opening Google Cloud offices in Kuwait is yet another step to meet the demand for our services and expertise in Kuwait to support the New Kuwait
Vision 2035 vision which aims to transform the country into a digital society and diversify its economy. We are working with the government of Kuwait towards digitizing citizen services and increasing the productivity of government employees, in addition to participating in the implementation of several digital transformation initiatives in healthcare, education, disaster recovery, and smart living.”
New capabilities empower customers to run data-intensive workloads like GenAI and VMware environments more easily
NetApp unveiled new capabilities designed for strategic cloud workloads including GenAI and VMware. These enhancements to NetApp data and storage services reduce the resources and risks for customers to manage these strategic workloads across increasingly complex hybrid multi-cloud environments.
Pravjit Tiwana, SVP and GM, Cloud Storage at NetApp said, “NetApp is helping customers take back control of their data with intelligent data infrastructure that leverages unified data storage, integrated data services, and automated cloud operations. Even when they are up against specific and nuanced technology requirements, NetApp gives them the tools they need to optimize and simplify their data operations in their environments across the hybrid multicloud.”
The new capabilities include:
• NetApp BlueXP Workload Factory – for
AWS: This intelligent data infrastructure service uses defined industry best-practices to automate the planning, provisioning, and management of cloud resources and services for key workloads.
• NetApp GenAI Toolkit – Microsoft Azure NetApp Files Version: Customers can now include private enterprise data stored in Azure NetApp Files in their RAG workflows.
• Amazon Bedrock with Amazon FSx for NetApp ONTAP Reference Architecture: AWS and NetApp have released a joint reference architecture which provides guidance for customers on implementing RAG-enabled workflows that bring proprietary data stored on Amazon FSx for ONTAP into their GenAI data pipelines.
• Amazon FSx for NetApp ONTAP Enhancements: AWS announced the next-generation Amazon FSx for ONTAP cloud storage service with enhanced capabilities
• NetApp BlueXP Disaster Recovery Support for VMFS: The BlueXP disaster

Mohammed Amin President, CEEMETA, Dell Technologies recovery service, for VMware workloads across both on-premises and cloud environments, has been expanded to support VMFS datastores for on-premises to on-premises disaster recovery.
Generative AI usage more than triples in 12 months
Netskope, a leader in SASE published new research showing that regulated data makes up more than a third of the sensitive data being shared with genAI applications—presenting a potential risk to businesses of costly data breaches.
The new Netskope Threat Labs research reveals three-quarters of businesses surveyed now completely block at least one genAI app, which reflects the desire by enterprise technology leaders to limit the risk of sensitive data exfiltration. However, most are behind in adopting the advanced DLP solutions needed to safely enable genAI.
96% of businesses are now using genAI—a number that has tripled over the past 12 months. On average, enterprises now use nearly 10 genAI apps, up from three last year, with the top 1% adopters now using an average of 80 apps, up from 14. With the increased use, enterprises have experienced a surge in proprietary source code sharing within genAI apps, accounting for 46% of all documented data policy violations.
There are positive signs of proactive risk management in the nuance of security and data loss controls organizations are applying: for example, 65% of enterprises now implement real-time user coaching to help guide user interactions with genAI apps.
The regional HQ reaffirms IFS’ focus on optimizing local resources and driving sustainable industrial innovations in the kingdom

IFS, a global cloud enterprise software company, has announced the inauguration of its regional headquarters in Riyadh. The strategic move reiterates IFS’ commitment to strengthen its position in the region and accelerate the Kingdom’s ongoing digital transformation journey.
“Establishing our regional headquarters in the largest economy in the MENA region reinforces our commitment to support the region’s growth by providing industrial technologies to key sectors here. We look forward to building a strong foundation with our partners and expand our footprint in Saudi Arabia and the neighboring countries, driving inno-
vation and excellence. This achievement symbolizes our dedication to becoming an integral part of the Kingdom’s ambitious vision and dynamic future.” said Vincent Carvalho, Regional President, APJ, ME&A, IFS.
The regional headquarter establishment reaffirms IFS’ focus on optimizing local resources and driving sustainable industrial innovations in the kingdom through its latest digital solutions. It will help local key industry players benefit from the latest technological advancements as IFS continues to innovate and drive operational efficiency in business processes.
New premium offerings enable enterprises to improve platform performance, save operational costs, and establish financial governance
Cloudera, the hybrid platform for data, analytics, and AI, announced two new offerings for Cloudera Observability Premium designed to simplify and automate platform administration. These premium tier features provide a single source of observability across all cloud-based and on-premises data centres, even for the most secure enterprises.
Cloudera’s expanded Cloudera Observability suite empowers enterprises with highly secure networks to operate observability entirely within their data centres or on the public cloud.
Cloudera’s two new solutions in its Cloudera Observability suite include:
● Cloudera Observability Premium On-Premises allows customers with highly secure networks to run observability entirely within their data centres. This solution ensures optimal monitoring, troubleshooting, financial governance, data
observability, and automated actions, even in air-gapped configurations.
● Cloudera Observability Premium for Public Cloud Data Hub extends all the advanced premium capabilities to public cloud users, including real-time monitoring, advanced financial governance, automated actions, and data observability.
With the addition of both these offerings, enterprises can now leverage high-value features such as real-time monitoring for Data Hub clusters, jobs, and queries, financial governance with new cost factors and capacity forecasting, workload views, alerts, and automated actions, along with data observability with hot and cold table analysis.
"Cloudera's new premium observability offerings provide Middle East organisations with unparalleled insights into their data operations. With real-time monitor-

ing and advanced financial governance, enterprises can optimise performance, reduce costs, and ensure compliance with regional data privacy regulations,” said Ahmad Shakora, Group Vice President of Emerging Markets (META), at Cloudera.
This marks a significant milestone in Mindware’s AI solutions portfolio
Mindware signed a strategic distribution partnership across the META region with DDN, a global leader in artificial intelligence (AI) and multi-cloud data management solutions. Under the agreement, Mindware will help DDN accelerate the adoption of its products and services, designed to support data-intensive environments and applications, by leveraging its expansive channel ecosystem in the region.
Alexandre Boutin, AI Director at Mindware commented, “As an AI Value-Added Distributor and trusted advisor, we felt the need to incorporate a vendor with a distinctive value proposition to meet various requirements, one of them being an Nvidia certified ecosystem partner for large SuperPOD projects, within and outside the realms of conventional AI/ HPC applications. With this new partnership with DDN, Mindware will offer solutions that accelerate AI and HPC apps at any scale,
that are geared towards enabling organizations to manage large volumes of data efficiently, and to derive actionable insights from that data, ensuring high performance and reliability across various use cases.”
DDN's storage and management solutions make deployment, management and scaling simple for even the largest AI applications, from edge to data centre to any cloud.
Ankur Arora, Senior Regional Director for MEA at DDN, says: "The data storage market has globally been experiencing significant growth driven by Large Language Models (LLM), Generative AI and other AI applications. Infrastructures need to be adapted to cope with the increasing compute capabilities and workload requirements. DDN’s unique value proposition is centred around its ability to deliver high-performance, scalable and reliable data storage solutions tailored for

complex, data-intensive workloads and environments. We are thrilled to announce our partnership with Mindware to bring DDN solutions and services to the META region.”
The collaboration aims to provide Saudi students with advanced training programs and certifications

Dell Technologies, Aramco, and the National IT Academy (NITA) have signed a collaboration agreement that aims to provide Saudi students with advanced training programs and certifications and will help develop a skilled and readily employable technology talent pool in the Kingdom.
The agreement was signed by Nabil
Al-Nuaim, Senior Vice President, Digital & Information Technology, Aramco, Majed S. Al-Ghassab, Executive Director, NITA, and Mohammed Amin, Senior Vice President, Central Eastern Europe, Middle East, Turkey, Africa (CEEMETA), Dell Technologies.
As per the agreement, the four-monthlong program “ITXcelerate” is designed
to equip recent Saudi graduates in computer engineering, computer science, and IT with Dell Proven Professional Certification across areas such as storage management, data science, and AI. It also includes hands-on experience with on-site job shadowing and mentoring opportunities. This immersive program aims to go beyond theoretical concepts and arm local talent with the skills and knowledge required to excel and thrive in today’s data-driven world.
It aligns with Saudi Arabia’s vision to foster a vibrant tech ecosystem and equip its workforce with the skills necessary to contribute to the nation's technological advancement and economic prosperity. The collaboration signifies a shared commitment to fostering a competent and future-ready IT workforce in Saudi Arabia.
Report highlights opportunity for leaders to transform enthusiasm into productivity gains
Microsoft’s fourth annual Work Trend Index (WTI) Report, titled “AI at Work Is Here. Now Comes the Hard Part” conducted in partnership with LinkedIn, provides a comprehensive view of how AI is not only reshaping work, but also the labor market more broadly. It revealed that three in four employees (75%) are already using AI at help them tackle their daily workloads; the use of Generative AI at work specifically has doubled over the past six months.
The report also found that despite 79% of business leaders agreeing that their company needs to adopt AI to stay competitive, a lack of clear AI vision and pressure to showcase immediate ROI is stalling plans for widespread adoption. As a result, a significant number (78%) of employees, unwilling to pass over the many benefits of utilizing AI,
are bringing their own AI tools to work. However, more than 50% of AI users say that they don’t want to admit to using the technology at work for fear that their employers might think of them as “lazy” or “replaceable”.
Zubin Chagpar, Senior Director and Business Group Leader, Modern Work and Surface Devices, Microsoft CEMA, said, “The biggest challenge now is for business leaders to take on a more agile approach when it comes to implementing AI to empower their employees, many of whom are struggling to keep up with the pace and volume of work today. Failure to do so will result in employees continuing to utilize their own AI solutions without the benefits that come from an organization’s strategic use of AI at scale such as enhanced cybersecurity and data privacy.”

Zubin Chagpar Senior Director and Business Group Leader, Microsoft CEMA
Unveils 2023 Sustainability Report and validation by SBTi of ambitious CO2e reduction targets affirmed

As Axis Communications, a leader in network video marks its 40th anniversary milestone, it has announced the publication of the Axis Sustainability Report 2023 and confirmed its ongoing commitment to reduce the impact of its own operations and its value chain on the environment. This is being done with validation by the Science Based Targets initiative (SBTi) of its total global greenhouse gas emissions reduction targets.
"Reaching this significant anniversary is testament to our relentless commitment to innovation, quality, and sustainability," said Ettiene Van Der Watt, Regional Director, Middle East & Africa of Axis Communications. "But this is not just about celebrating the past 40 years of achievements, it is also about demonstrating our uncompromising commitment to realising over the years
and decades to come our sustainability goals. Collectively, the scope of these initiatives means every aspect of our business – from the raw materials used in component manufacturing to energy consumption and the approach to recycling products at their end-of-life – will need to demonstrably contribute to the achievement of emissions reduction targets. Put simply, we are committed to our sustainability agenda to ensure the next 40 years are as rewarding as the last.”
Axis signed the UN Global Compact 2007, and its strategies and operations are aligned with these universal principles on human rights, labor, environment, and anti-corruption. Axis also supports the 17 Global Sustainable Development Goals (SDGs) of the UN 2030 Agenda, which act as a blueprint for peace and prosperity for people and the planet.

2024 marks the commercial launch of 5G-A, with leading operators in the Middle East already deploying 5G-A networks
Huawei made a significant impact at the Mobile World Congress (MWC) Shanghai 2024, highlighting its advancements in 5G-Advanced (5G-A) technology and artificial intelligence (AI) integration. Under the theme "Advancing the Intelligent World," the company presented a comprehensive vision for the future of mobile networks and services.
The year 2024 marks the commercial launch of 5G-A, with leading operators in the Middle East already deploying 5G-A networks. Huawei showcased its latest products and solutions supporting both 5G-A deployment and AI devices required for the mobile AI era.
Huawei's Executive Director David Wang emphasized how 5G-A and AI devices will be key to making intelligent services ubiquitous, transforming human-machine interaction, content production, and mobile devices. Wang noted that the number of global 5G users has exceeded 1.8 billion, with many operators seeing the first wave of benefits. The company highlighted that nearly 20 mobile phone models currently support multi-carrier aggregation, with some activating the feature by default. Multiple operators in the Middle East and China have started deploying 5G-A three-carrier component (3CC) aggregation networks at scale, targeting 5 Gbit/s downlink rates.
In a significant industry initiative, Huawei launched the 5G-A Pioneers Program, reaching six consensuses with pioneering global operators, including UAE's du, Oman Telecommunications, China's "big three", and HKT. These consensuses aim to maximize the value of advanced 5G-A capabilities, promote its development, and further advance the industry through various focus areas, including Pioneer Operators, Pioneer Cities, Business Model Upgrade, High-quality Networks, Service Innovation, and Thriving Ecosystems.
Huawei also unveiled plans to bring AI to networks, focusing on building an ecosystem of RAN Intelligent Agent in collaboration with operators. This initiative aims to increase network productivity by reshaping network operations and maintenance (O&M), experience, and services. Towards this end, Huawei introduced AI-powered copilots and agents to support role-based chatbots and scenario-based solution automation, significantly improving efficiency in areas such as field maintenance and network optimization.
Huawei also introduced the Open Gateway initiative to help carriers monetize their 5G investments. Huawei's Chief Marketing Officer, Dr. Philip Song, presented successful use cases of global operators that have improved customer services and lowered time to market.
Breaks down IT/OT silos with industry’s first fully managed Edge AI solution, enabling advanced AI use cases for industrial and manufacturing
NTT DATA, a leading IT infrastructure and services company, unveiled its new Edge AI platform to accelerate IT/ OT convergence by bringing AI processing to the edge. By processing data when and where it is generated and unifying diverse IoT devices, systems and data, this unique, fully managed solution enables real-time decisions, enhanced operational efficiencies and secure AI application deployment across industries to drive advanced Industry 4.0 technologies.
While the spotlight has been on GenAI and Large Language Models (LLMs), these technologies are impractical for industries requiring real-time and local decision-making. NTT DATA’s Edge AI solution addresses this challenge by processing massive data sets on compact computing platforms, using smaller, more efficient machine learning models to deliver real-time AI insights.
NTT DATA’s Edge AI is an all-inclusive managed service platform that includes all the systems, tools and capabilities required for AI at the edge. It addresses data discovery, collection, integration, computation power, seamless connectivity and AI model management.
The Edge AI platform, supported by NTT DATA’s consulting data scientists, managed services and global technical resources, addresses the shadow IoT challenge and AI infrastructure requirements. It does this by auto-discovering, unifying and processing data from IoT devices and IT assets across the organization, simplifying AI deployment and management.
Designed to support industry-specific requirements, the Edge AI platform leverages lighter, cost-effective AI models, enabling it to run within a small compute

box. Edge AI will perform specific tasks, such as supporting safety or operational efficiency, by collecting data from disparate devices across a network environment, enabling instantaneous and secure data processing and analytics.
Manufacturing operations could benefit from improved predictive maintenance by accessing IT/OT data from sensors, machinery, cameras and applications to plan and address failures. In addition, NTT DATA’s Edge AI can monitor and optimize energy consumption in real time, predicting energy spikes and optimizing machine usage, reducing costs and CO2 emissions with renewable energy.
“Our Edge AI platform represents a significant leap forward in driving AI at the edge securely and cost-effectively,” said Shahid Ahmed, Group Executive Vice President of Edge Services at NTT DATA. “By harmonizing data from disparate sensors and devices with lightweight AI models, powering all kinds of
automation use-cases, NTT DATA’s Edge AI is pioneering industrial AI adoption as the first fully managed offering, helping organizations modernize with tailored, industry-specific solutions.”
NTT DATA’s Edge AI deployment approach allows clients to take advantage of a free 30-day discovery and diagnostic of their IT and OT environment. The software auto-discovers assets with its vast library of pre-built OT interfaces. After this initial stage, Edge AI software generates a comprehensive diagnostic report inventorying assets and data streams, including identifying security risks and vulnerabilities.
NTT DATA’s managed services for Edge AI offer a unified view and management of devices, sensors and assets. With expert support and advanced technologies, NTT DATA helps businesses simplify complex processes, drive cost savings, enhance performance and accelerate digital transformation.
85% of UAE respondents anticipated a cybersecurity incident disrupting their business within the next 12 to 24 months in Cisco’s recent Cybersecurity Readiness Index
Cisco unveiled key insights into the evolving cybersecurity threat landscape, emphasizing the need for a united front between technology companies and governments. As cyber threats become increasingly sophisticated, Cisco advocates for the development of advanced AI detection systems to ensure a safer online environment for all.
Despite ongoing efforts from both public and private sectors to detect and mitigate the effects of AI-powered disinformation, the consequences are no longer theoretical. This was evident in Cisco’s recent Cybersecurity Readiness Index, where 85% of UAE respondents anticipated a cybersecurity incident disrupting their business within the next 12 to 24 months. Additionally, 52% of those affected by such incidents reported costs of at least $300,000. The urgency of leveraging AI capabilities has never been greater.
"As the volume of data generated continues to increase, the threat of AI-driven disinformation escalates. With larger data sets enhancing AI accuracy, it is imperative for companies developing AI technologies to act with utmost responsibility," says Fady Younes, Managing Director for Cybersecurity at Cisco Middle East & Africa. "Cisco, a leader in cybersecurity technologies and responsible AI practices, is committed to upholding transparency, fairness, accountability, reliability, security, and privacy—principles that benefit organizations and governments alike."
Companies and governments should aim to tackle complex societal challenges and counter the growing menace of AI-enabled disinformation. With AI advancements making it easier and cheaper to manipulate digital content on a massive

Fady Younes Managing Director, Cybersecurity, Cisco MEA
scale, it is imperative for those developing, using, and regulating the technology to collaborate effectively. This collective effort is essential to achieve the potential benefits of AI while managing the new risks it introduces.
In the near future, substantial progress will be made to address these dual challenges. Organizations will prioritize the development of reliable AI detection systems and risk mitigation strategies. Comprehensive new AI solutions will protect against cloned voices, deepfakes, social media bots, and influence campaigns. AI models, trained on extensive datasets, will achieve enhanced accuracy and effectiveness. Furthermore, new authentication and provenance mechanisms will foster transparency and accountability.
Detecting AI-generated written content remains challenging, with current AI detection tools often yielding low accuracy and false positives. To counter AI-based subversion, tech companies are expected to invest further in improving detection mechanisms and developing content authentication and provenance systems to verify the authenticity and source of AI-generated content.
Cisco anticipates a significant increase in public-private interactions aimed at combating the misuse of AI-generated content, including potential sanctions against those responsible for digital disinformation campaigns. Businesses will need to enhance data protection and threat detection to prevent damaging impacts, requiring constant vigilance, regular vulnerability assessments, diligent security system updates, and thorough network infrastructure auditing.
AI’s dual role in both exacerbating and mitigating AI-powered disinformation necessitates transparency and a broad approach to protecting democratic values and individual rights. This involves rethinking IT infrastructure, with business leaders recognizing that their technical infrastructure is integral to their operations. Early detection through monitoring and observability over complex infrastructure, network components, application code, and user experience is crucial. It is essential to identify potential outcomes and connect them to an effective, efficient response.
Carefully developed, strategically deployed technology and regulations can help mitigate these risks, but only with shared responsibility.
D-link has over the years played a key role in addressing network infrastructure requirements of mid-market Business enterprises

Sakkeer Hussain Director - Sales & Marketing, D-Link MEA
D-Link over the past two decades and more continues to be at the forefront of technology, playing a key role in helping shape the future of networking and internet connectivity across both consumer and enterprise markets. When it comes to the Business segment, especially in the region, D-link has over the years played a key role in addressing network infrastructure requirements of mid-market Business enterprises.
Sakkeer Hussain, Director - Sales & Marketing, D-Link Middle East & Africa says, “As D-Link, we've played a critical role in building the network infrastructure for mid-market businesses in this region. Over the years, we’ve witnessed firsthand the unique challenges faced by these enterprises. They often juggle rapid growth with constrained budgets, demanding solutions that are both cost-effective and scalable. That’s where we come in. Our focus has always been on delivering reliable, high-performance networking equipment without breaking the bank. We’ve meticulously crafted a product portfolio spanning switches, routers, wireless access points and beyond, ensuring there’s a solution tailored to every business need.”
He adds, “It's not just about the hardware. Our strong local presence and dedicated support teams are integral to our success. We believe in being there for our customers, offering timely assistance and building lasting relationships. We're proud of our role in empowering mid-market businesses to thrive. By providing affordable, scalable, and reliable networking solutions, we’ve helped countless enterprises optimize their operations and achieve their goals.”
While the pandemic years of 2020 and the early part of 2021 were a disruptive phase for all Businesses, there were also opportunities driven by the digital acceleration of the transition to remote work. Since then, things have returned to normal, but with more flexibility in terms of working on site and also working from anywhere. D-Link as a networking solutions provider came out with several new products that enhanced remote working connectivity. The vendor saw a surge in demand and had to ramp up production to meet the exploding demand.
Sakkeer says, “The COVID-19 pandemic was undoubtedly a seismic shift for businesses worldwide, and the technology sector was no exception. The abrupt transition to remote work placed unprecedented demands on network infrastructure. Initially, the surge in demand for home networking equipment was overwhelming. Overnight, residential Wi-Fi became the backbone of offices, schools, and entertainment centres. We had to rapidly scale our production to meet this unprecedented surge while maintaining our commitment to quality.”
Simultaneously, D-Link recognized the need to adapt its product portfolio. Features like Wi-Fi range extenders, powerline adapters, and robust security solutions became essential. D-Link invested heavily in research and development to enhance these offerings and introduce new products that catered specifically to the remote work environment, for example its Nuclias range of solutions.
“As the world gradually transitions to a more balanced hybrid work model, we see a convergence of office and home networks. This trend requires versatile solutions that can seamlessly support both on-site and remote employees. We're responding by developing products that can adapt to these changing work styles, offering features like seamless roaming between networks and advanced security protocols to protect sensitive data.The pandemic tested our agility and resilience. We emerged from it with a deeper understanding of our customers' needs and a product line that is better equipped to handle the complexities of the modern workplace.”
D-Link has an equal focus on consumer and business range of solutions. The vendor offers a sizable range of solutions in both segments and continues to be a popular choice among consumers and Business users.
“For D-Link, we have been a strong player in both consumer and business segments. The split is 50-50, as both categories are growth drivers for us. The consumer segment focuses on products like home routers, Wi-Fi extenders, and IP cameras for residential use. This segment is driven by price sensitivity, ease of use, and brand recognition. The business segment caters to enterprises, SMBs, and government organizations. This segment demands a different product portfolio, emphasizing reliability, scalability, security, and advanced features. Products include managed switches, enterprise routers, and surveillance solutions etc,” says Sakkeer.
“We're proud of our role in empowering mid-market businesses to thrive. By providing affordable, scalable, and reliable networking solutions, we’ve helped countless enterprises optimize their operations and achieve their goals.”
In the Business segment, D-Link has several product lines including Ethernet Switches, Wireless Access Points, Routers, NAS devices etc that meet all network connectivity needs of mid-market Businesses as well as enterprises. D-Link has enhanced its offerings across all these product lines in recent years.
In the ethernet switches range, D-Link offers stackable and modular switches for larger enterprise deployments. D-Link has managed switches in its portfolio with advanced features like VLANs, QoS, and Layer 3 routing. D-Link also offers PoE (Power over Ethernet) switches to simplify network deployments.
According to Sakkeer, stackable switches have emerged as a critical component of network infrastructure in the region, driving a significant demand across various sectors.
He elaborates, “This demand is primarily fueled by the increasing complexity and scale of network deployments. The demand for stackable switches is driven by several factors: expanding data center operations requiring high performance and scalability, the need for high-speed connectivity and redundancy in large enterprise campus networks,the growth of SMBs seeking flexible and cost-effective solutions, the optimization of network performance for cloud-based applications, and the increasing data demands of IoT and smart city initiatives. As businesses continue to expand and adopt new technologies, the importance of stackable switches is likely to grow further.”
In the wireless access points range, D-Link offers high-density Wi-Fi systems for large-scale deployments. Through its solutions, D-Link offers integration of advanced wireless technologies like 802.11n, 802.11ac, and 802.11ax. The manufacturer has been offering Wi-Fi 6E access points to support the growing demand for high-speed wireless connectivity, for both indoor and outdoor use cases. D-Link's comprehensive portfolio of indoor and outdoor access points addresses diverse wireless connectivity needs across various industries. Indoor access points provide reliable Wi-Fi coverage within buildings, with business environments demanding high performance, security, and scalability.
Sakkeer says, “D-Link offers a diverse range of indoor APs to cater to various business needs, including cost-effective options for SMBs with basic features, high-density APs for large organizations with advanced capabilities, and specialized solutions for specific industries like healthcare, education, and hospitality, featuring tailored functionalities like voice over Wi-Fi, guest access management, and location-based services.”
He adds, “Outdoor access points are crucial for businesses operating in environments with limited indoor coverage or requiring wireless connectivity outdoors. These D-Link APs are robust, weatherproof, and provide reliable coverage in challenging conditions.”
Key applications for outdoor access points include campus networks demanding extensive outdoor coverage, retail and hospitality enhancing customer experience with outdoor Wi-Fi, and industrial environments requiring APs built for harsh conditions. In routers, D-Link offers enterprise-grade routers with advanced
routing protocols and VPN capabilities. Firewall and security features are integrated into these routers for enhanced network protection. D-Link also offers SD-WAN (Software-Defined Wide Area Networking) routers to support hybrid network architectures.
In the Network Video Surveillance segment, D-LINk offers an impressive array of IP cameras suiting diverse requirements from indoor to outdoor surveillance. Its product ranges include high-resolution cameras with advanced features like PTZ (Pan, Tilt, Zoom), WDR (Wide Dynamic Range), and low-light performance. These cameras also feature Integration of video analytics and AI capabilities for intelligent surveillance.
Sakkeer says, “Surveillance solutions, particularly IP cameras, have become a significant growth segment for D-Link in the business sector. The increasing emphasis on security, both for businesses and individuals, has driven a robust demand for reliable and efficient surveillance systems. D-Link's focus on developing high-quality, feature-rich IP cameras, combined with our strong brand reputation in networking, positions us well to capitalize on this growing market. By offering integrated solutions that combine surveillance with network infrastructure, we are working on further strengthening our position as a comprehensive security solutions provider.”
D-Link through its centralized network management platform enables efficient configuration and monitoring. The platform includes cloud-based management tools for remote network management. Further, it also includes AI-driven network analytics for proactive troubleshooting and optimization.
Sakkeer says, “The Nuclias network management solution has undergone continuous improvement to address the evolving needs of SMB and mid-market businesses. Some of the enhancements include expanding cloud-based management capabilities for remote access and centralized control, integrating AI and machine learning for optimized network performance and troubleshooting, strengthening security features to combat cyber threats, supporting IoT device management, and improving the user interface for enhanced usability.”
He adds that the Nuclias solution offers significant advantages to SMBs and mid-market businesses by simplifying network management through centralized control, enhancing security with advanced features to protect sensitive data, improving network performance with AI-driven optimization, accommodating business growth with scalability, and ultimately, saving costs by streamlining network management and reducing downtime.
“By continuously enhancing Nuclias, we position ourselves as a preferred choice for businesses seeking efficient and secure network management solutions.”
Staying in sync with the latest industry trends, D-Link has continued to introduce new products. A typical example is Wi-Fi 6 where the vendor introduced a range of products that leverage this technology. D-Link expanded its Wi-Fi 6 product line to
include routers, access points, and extenders, catering to both residential and commercial markets. Likewise, it continues to be a leader in the 5G space.
Sakkeer says, “D-Link's products emphasize features like OFDMA, MU-MIMO, target wakeup time, and increased capacity to deliver faster speeds, lower latency, and improved network efficiency. Recognizing the growth of IoT devices, we have integrated Wi-Fi 6 into products designed to support a large number of connected devices. We have ensured that our routers and gateways are compatible with 5G home internet connections, allowing users to leverage high-speed internet for better Wi-Fi performance. D-Link has developed products that can effectively utilize 5G as a backhaul for Wi-Fi networks, improving coverage and capacity in areas with limited wired infrastructure.”
He adds, “By aligning our product strategy with the advancements in Wi-Fi 6 and 5G, we have positioned ourselves as a leader in providing reliable and high-performance wireless networking solutions to meet the evolving needs of consumers and businesses.”
D-Link intends to unveil Wi-Fi 7 access points soon along with several new product launches as it continues to be an innovation leader in networking technologies.
Sakkeer says, “We are looking to introduce several new products before the year's end. Building on Wi-Fi 6 and 6E success, Wi-Fi 7 access points will be launched soon for enhanced speed and capacity. AI-driven network management solutions, such as expanded Nuclias capabilities, will enhance automation and troubleshooting. To address the evolving threat landscape, advanced cybersecurity products like firewalls and intrusion prevention systems will be released over the next few quarters. In line with growing IoT and smart home demands, we will also expand our IoT product line.”
With its focus on affordable solutions, ease of use, quality, innovation, global reach as well as a strong partner strategy, D-Link continues to be a formidable player across its target segments. A sustained focus on enhancing solutions across all product lines of focus with new technologies also continues to be among the significant strengths of D-Link.

D-Link's G530 5G NR AX3000 Wi-Fi 6 router empowers users to harness the full potential of 5G technology by using a mobile carrier’s SIM card to deliver high-speed 5G connectivity through a robust Wi-Fi 6 network. Engineered with the renowned MIT (Made in Taiwan) quality assurance, the G530 provides a fast, reliable, and flexible networking solution ideal for homes, offices, remote sites, and temporary setups where traditional wired connections are limited or unavailable.
DXS-3410 Series L3 Stackable Switches:

The DXS-3410-32XY and DXS-3410-32SY, with advanced Layer 2 and Layer 3 functionalities are 10G Layer 3 Stackable Managed Switches. Designed specifically for SMB/SME core network infrastructure, these switches meet the exponential growth of business network demands, delivering unmatched performance, flexibility, and security. Ideal for medium to large businesses or campuses requiring high levels of security protection and maximum uptime, these switches help build reliable and scalable networks.

From safeguarding against ransomware attacks to protecting against data breaches, organizations must prioritize cybersecurity as a core component of their strategic planning.
As a critical aspect of an organization’s infrastructure, cybersecurity has to be a top priority in any IT strategy roadmap. In a digitally interconnected world with exponentially growing attack surface area, vulnerabilities, and risks, protecting the data assets of an organization against various cyber threats has become critical to sustaining smooth business operations. Evolving strategies that are aligned with business objectives and are capable of tackling emerging threats is central to the set of responsibilities that lie with IT security decision-makers in their respective organizations.
Nisha Rani, CISO at Emirates Leisure Retail says, “The cybersecurity landscape today is rapidly evolving, driven by the increasing sophistication of cyber adversaries, the widespread adoption of emerging technologies, and the ever-expanding attack surface. In an increasingly digital world where cyber threats are becoming more sophisticated and frequent, protecting sensitive data and ensuring the integrity of systems is essential. Organizations must integrate cybersecurity at every level of their IT strategy, from network security and data protection to threat detection and incident response.”
“By prioritizing cybersecurity, companies can mitigate risks, ensure compliance with regulations, and maintain the trust of their customers, partners, and stakeholders. A proactive and comprehensive approach to cybersecurity is not just a necessity but a competitive advantage in today’s business environment,” she adds.
Faisal Khan, Associate Director – Information Security & Compliance, IT Security and Compliance, DWTC says the rapid pursuit of digitization and digitalization is intensifying the complex-
ity of the cybersecurity landscape with more sophisticated threats increasingly posing a huge cybersecurity challenge.
He adds, “Often CISOs are on the brink of a breakdown considering the speed of the evolving technology and in-turn protect their environment with appropriate counter mechanisms, which are bound by available budgets and still don’t guarantee 100% protection. However, these counter mechanisms do give them some sort of assurance that they have reduced the risk at their best to safeguard and strengthen their organizational security. While Ransomware still tops the charts, phishing attacks and insider threats are mainly the primary focus areas for top emerging threats, with the rise of AI based technology, now it is imperative for them to also focus on AI based attack prevention practices to further secure their environment.”
Nisha shares her insights about some of the top cybersecurity threat trends including Ransomeware, supply chain attacks, phishing as well as AI driven attacks.
“Ransomware continues to be a significant threat, particularly as cybercriminals evolve their tactics, targeting not just IT systems but operational technology and critical infrastructure. The hospitality sector, which often relies on continuous operations, is especially vulnerable to these disruptions. Supply chain attacks, where adversaries infiltrate through third-party vendors, have become increasingly common and devastating. Phishing and social engineering attacks are becoming more sophisticated, tricking even seasoned professionals into compromising security. Further as AI and machine learning are leveraged for defensive measures, cybercriminals are also using these technologies to automate at-
tacks, enhance spear-phishing campaigns, and discover vulnerabilities more efficiently.”
Cybersecurity as a strategy has to be in the foreground as far as Businesses are concerned in this digital era. The importance of aligning cybersecurity strategy with the overall business objectives cannot be understated as it is seen as business enabler.
Faisal says, “The overall business objectives are often neglected when creating a cybersecurity strategy, however, is an integral part on how the organization functions and the risk it is subjected to due to the evolving threats. This alignment ensures that security measures are not just seen as an IT responsibility but as a strategic component that contributes to the overall success of the organization. Supporting business goals and objectives and most importantly it’s assets (information and people) should be the core focus with a risk-based approach which in turn effectively protects the organization’s brand and reputation.”
Nisha elaborates that a cybersecurity strategy that aligns with business goals contributes to operational efficiency by preventing disruptions that could impact services and also helps with innovation strategies.
“It’s not just about preventing breaches—it’s about ensuring that systems run smoothly, allowing the organization to deliver the best possible experience to its customers. Integrating cybersecurity into innovation processes allows organizations to explore new technologies and business models with confidence, knowing that security considerations are built into their approach from the start.”
Compliance requirements are also driving the need for a robust cybersecurity strategy at organizations. Regulations such as GDPR, HIPAA, NIST mandate strict controls over data privacy, security, and breach reporting.
According to Nisha, “With regulations like GDPR, and more jurisdictions adopting similar laws, compliance has become a significant concern. Failing to protect customer data can lead to severe penalties and damage to brand reputation. In addition, whether intentional or accidental, insider threats also pose a serious risk. Therefore, I emphasize the importance of cultivating a culture of security awareness within the organization.”
Cybersecurity frameworks help guide organizations in building a structured approach to cybersecurity that helps identify, assess, and manage cybersecurity risks and prioritize resources and investments where they are most needed.
Ankit Satsangi, Director - Enterprise Development, BEEAHGROUP says “Selecting the right cybersecurity frameworks and standards is crucial for protecting an organization’s digital assets and ensuring compliance with legal and regulatory requirements. The NIST Cybersecurity Framework (CSF) offers a strategic approach to managing cyber risks, helping align security efforts with business goals. ISO/IEC 27001 is essential for global organizations, providing a comprehensive system for safeguarding

sensitive information and fostering a security-conscious culture.” Further, he adds, “The UAE’s Personal Data Protection Law (PDPL) establishes a comprehensive framework to protect individuals' personal data, requiring explicit consent for data processing and granting rights such as access, correction, and deletion of personal information. It mandates the appointment of a Data Protection Officer for organizations handling significant amounts of sensitive data and regulates cross-border data transfers to ensure adequate protection.”
According to Faisal, “An organization should adapt a Risk Management Framework such as NIST, ISO/IEC 27001, and CIS Controls to assess, and prioritize risks across the organization. International Data Security Regulations and UAE Data Privacy Laws such as GDPR, PDPL should also be complied to protect sensitive data and avoid legal penalties. Continuous monitoring, regular risk assessments, a strong incident response plan, and user awareness sessions will be some key essential elements that contribute to maintaining a robust security posture.”
Ankit says that frameworks like HIPPA, MITRE ATT&CK etc are not just about compliance; they are a strategic approach to cybersecurity that prioritizes data protection, builds trust with customers, and ensures the organization’s resilience against evolving cyber threats. Integrating these tools into the security strategy helps create a robust and proactive defense, essential for longterm success.
“In healthcare, HIPAA ensures the confidentiality and security of patient data, which is vital for maintaining trust in healthcare ser-

Faisal Khan
Associate Director – Information Security & Compliance, IT Security and Compliance, DWTC
vices. The MITRE ATT&CK framework helps organizations understand cyber adversaries’ tactics and techniques, enabling them to proactively address potential vulnerabilities. Complementing this, MITRE D3FEND provides practical defensive measures, allowing organizations to build targeted defenses against identified threats, ” he adds.
An incident response plan is crucial to any cybersecurity strategy as breaches and attacks are almost inevitable in today’s world. A well-defined incident response strategy helps minimize damage, reduce recovery time, and helps maintain business continuity.
Ankit elaborates, “No matter how strong your defenses are there’s always a chance that something will slip through the cracks. When that happens, having a well-prepared incident response plan can be the difference between a manageable situation and a full-blown crisis. The plan ensures that your team knows exactly what to do, who to contact, and how to contain the damage quickly and effectively.”
To ensure an incident response plan is effective, it needs to be more than just a document sitting on a shelf, quips Ankit and goes on to elaborate.
“Regular testing through simulations or drills is essential, as it helps the team stay sharp and identifies any gaps or weaknesses in the plan. The plan should be reviewed and updated regularly to keep up with the evolving threat landscape and changes within the organization. Clear communication channels and roles should
be established so that everyone involved knows their responsibilities should an incident occur. In an active incident, speed and clear communication are crucial and having a well-practiced, up-to-date response plan is vital for minimizing damage and enabling a quick recovery.”
The emergence of Zero Trust Architecture (ZTA) has redefined the approach to cybersecurity in the era of pervasive digital connectivity and work from anywhere, where traditional cybersecurity approaches including perimeter defense are no longer enough. ZTA ensures every user, device, and application must be authenticated, authorized, and continuously validated before being given access to data or resources.
Faisal says, “While the Zero Trust Architecture is the new buzzword in the security world today and provides robust security benefits by emphasis on not trusting anyone by default, a careful assessment and a balanced approach needs to be taken by the CISOs as it is a complex process that requires a significant overhaul of existing IT infrastructure provides. As earlier stated, an alignment to the organization’s objectives and goals need to be ensured as they can potentially pose the business an impact to their productivity.”
Zero Trust Architecture has become increasingly relevant for organizations today, reflecting a shift in how we approach cybersecurity.
Nisha says, “Traditional perimeter-based security models are less effective in a landscape where threats can come from both inside and outside the organization. ZTA operates on the principle of "never trust, always verify," which helps mitigate risks from both external and internal threats. ZTA is designed to secure access to resources regardless of where users or systems are located, ensuring that security is enforced at all access points.”
Further, ZTA helps tackle the increased Complexity of IT Environments which has a mix of on-premises, cloud, and hybrid systems.
“ZTA helps manage this complexity by applying security controls consistently across all environments and minimizing trust assumptions. ZTA helps organizations meet data protection and regulatory requirements by enforcing strict access controls and ensuring that sensitive data is only accessible to authorized users. By implementing least-privilege access and segmenting the network, ZTA limits the scope of potential breaches.”
ZTA emphasizes continuous monitoring and verification of user and device identities, which provides better visibility into who is accessing what resources and how. This enhanced visibility helps in detecting and responding to suspicious activities more effectively.
Zero Trust Architecture is seen as a necessary evolution in cybersecurity strategy that helps organizations stay ahead of emerging threats and keep a more resilient security posture.
A Security Operations Center (SOC) must be a cornerstone of any organization’s cybersecurity strategy because a SOC provides
continuous monitoring of an organization’s IT infrastructure, enabling the detection of malicious activities and potential breaches before they can cause significant damage. However, there are options for a SOC strategy. Organizations can either choose to have their own in-house SOC or they can look at outsourcing SCO Managed services and in some instances a hybrid approach.
Faisal says, “Having 24/7 eyes on the glass is extremely important for an organization’s defence systems which protect and prevent external and internal threats in turn enhancing their security landscape. However, the decision to have an in-house SOC or Managed SOC Service depends on the organization's size, resources, and specific needs. An in-house SOC offers more control but requires significant investment while Managed SOC Services provide access to specialized expertise and can be more cost-effective, specially for mid-small organizations.”
While a SOC is crucial to enabling an organization’s ability to protect sensitive data, maintain customer trust, and ensure business continuity in the face of evolving cyber threats, whether to go for a managed SOC or an in-house SOC depends on the evaluation of the organization’s security needs, budget, regulatory requirements.
Nisha says, “Whether organizations should maintain their own Security Operations Centers (SOCs) or use SOC managed services depends on various factors, including their size, budget, and specific security needs. The decision between an in-house SOC and SOC managed services should be based on the organization’s specific requirements, budget, and strategic goals. Smaller organizations or those with limited resources may find managed SOC services to be a more practical and cost-effective solution. Larger organizations with complex needs and sufficient resources might prefer the control and customization of an in-house SOC. In some cases, a hybrid approach that combines elements of both options can also be effective.”
The emergence of AI and ML technologies has created opportunities and challenges. These technologies are being to enhance cybersecurity responses but at the same time in the hands of adversaries, the enable more sophisticated attacks.
Ankit says, “AI is making a big impact on cybersecurity by quickly identifying threats and patterns that would take people much longer to detect, allowing for faster responses to potential attacks. However, cybercriminals are also leveraging AI to create more advanced attacks, like highly convincing phishing schemes and rapidly exploiting security vulnerabilities. Deep fakes, which use AI to produce fake videos or audio that seem real, add another layer of risk by deceiving people into believing false information. While AI is useful in spotting these kinds of threats, it’s not foolproof, so we need to stay vigilant and keep refining our security measures.”
Finally, assessing the security posture of an organization requires a set of key metrics that provide insights into both the effectiveness of security controls and the organization's overall risk exposure.

Ankit Satsangi Director - Enterprise Development, BEEAHGROUP
Nishan mentions some of the key metrics.
“Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), Average time to identify a security incident (MTTD), Average time to contain and remediate an incident after detection (MTTR), tracking the total number of security incidents over a specific period are some metrics to consider. Phishing Success Rate looks at the percentage of employees who fall for phishing attempts that indicates the effectiveness of security awareness training. Vulnerability Management Metrics include Patch Management Compliance which looks at the percentage of systems with up-to-date security patches Vulnerability Remediation Time which determines the time taken to fix identified vulnerabilities.”
Further, Security Awareness Training Completion Rate looks at the percentage of employees who complete mandatory security training required to ensure that employees are informed about security best practices. Unauthorized Access Attempts as a metric helps track attempts to access sensitive systems or data without authorization to identify potential security weaknesses and insider threats.
In addition, Security Audit and Compliance Scores, the number of DLP incidents, Third-Party Risk Scores as well as Penetration Test Results are key metrics that help provide insights into the security posture.
Needless to say, a holistic cybersecurity strategy must encompass the latest AI/ML technologies, robust incident response strategies, Risk Management and compliance and the principles of Zero Trust Architecture, along with the required metrics to continually assess and enhance cyber security resilience.
Ram Narayanan, Country Manager at Check Point Software Technologies Middle East discusses the need for an integrated approach to cybersecurity
Discuss your focus on an integrated approach to cybersecurity Enterprises need to adopt a whole platform approach with the consolidation of various security solutions rather than deploying point solutions. Point solutions for specific requirements is an approach that worked in the past but the need of the hour for CIOs and CISOs is to look at an integrated platform approach to cybersecurity to combat the enhanced threat landscape.
Check Point’s Infinity architecture brings together different point solutions and then aggregates them together. Infinity Portal is a comprehensive SaaS management solution that provides administrators with a centralized console to manage Check Point Infinity Portal services. With its range of capabilities, the Infinity Portal simplifies security management, improves visibility, and enhances security across the enterprise. We have onboarded more and more services on this platform. We already have our email and collaboration services endpoint solution and mobile security on board the platform. It is a unique value proposition for customers or enterprises in the region, where they get the best-of-breed technologies and consolidation. It is hosted out of the UAE data center.
Please elaborate on how you have included AI in the Infinity platform.
With the platform approach, we have brought in AI as well. We call it AI-powered, cloud-delivered kind of SaaS model. We have had AI engines in the backend that power the intelligence to correlate across different sensors to help identify the new malware and start to block them.
We are now bringing Gen AI to solve customers’ business issues. I can highlight two aspects. The Infinity Co-Pilot can help reduce up to 90% of the time needed to perform common administrative tasks with a GenAI security solution that harnesses automation and collaborative intelligence. For instance, to execute certain admin tasks, you can type like in Google Chat. In the backend, the Copilot calls the APIs and then executes for them. It could be about adding a new access policy or certain users to the group or validating certain things. From an analysis perspective, they can check, for example, if there is a new vulnerability or an attack, whether they have been a target, analyze the logs, and then get some insights. This is how we've been able to use AI to help solve operational issues.

Ram Narayanan Country Manager, Check Point Software Technologies ME
The second aspect is related to Infinity Playblocks that help move the threat scenario from detection to prevention in the fastest time. Today, enterprises have many solutions, which will detect and alert them about an attack or incident but somebody manually has to look at it and take some preventive action. Infinity Playblocks help automate it and once identified as critical, we can even move over to prevention. But, of course, it's fully configurable. We let the customer know that there was an incident like this that we moved into prevention and this is the outcome. They can verify it. We already have close to 40 predefined templates. We are trying to make it easier for the SOC operations team to deal with cyber-attacks. This is how we have been able to put AI into action.
How do you look at the challenges of using GenAI in security? There's a context of how Check Point can use AI or AI can be used in security. As we spoke, we can use it in the backend and you can use it in the front end. We are also seeing enterprise customers using AI for their business processes. And that introduces new vectors of attack. It introduces vulnerabilities into the ecosystem, so you need to have solutions with guardrails which means that the solution has certain parameters within which it would work and outside those parameters, you place certain controls. For enterprises, we will be adding that layer of security. On an industry level, we're collaborating with Microsoft and Nvidia to better see how we can collaborate together because they have the largest computational power to help address the barriers. When it comes to operations, automation and orchestration, GenAI needs to be used. There will always be a point in time when GenAI cannot decide whether to block or allow certain things, and there will be a need to have human intervention, and you need to have that layer. I believe we're just moderating it in the right way but it is going to have its own iterations. I don't think it has taken its final shape, but we have done the first iteration and feel it's safe to use.
If you are going to detect something as malicious or not malicious, based on one or two parameters, the false positive rate increases. We employ 10 to 20 different engines, and each one gives their verdict. Then you assemble the feedback of all which helps you decide the overall score. If that is going to be about 90 or 95 percent, then you say the confidence level is more. In a report that came out at the beginning of the year to understand the efficacy of the product, where all the competing products were put together for testing for known and unknown malware, Check Point again scored an accuracy of 99.8%. That is the kind of accuracy that we get, partly because of the number of agents that we run plus the threat intelligence that we feed into which makes it much more comprehensive.
Do you have a focus on OT security?
There is a convergence of IT and OT security. OT has its own specific protocols. We offer the Check Point ICS security solution that offer a proactive strategy, minimizing risk across both environments, blocking threats before critical assets are affected, and enhancing industrial operations seamlessly.
As far as OT security is concerned, we do two tasks. One is discovery of OT assets risk, attack vector and baseline behavior, which we do with the help of third parties, and in certain instanc-
es do it ourselves. And then we do the protocol enforcement, because we understand the SCADA protocol and specific OT protocols and inspect those protocols. These are critical use case scenarios like a Metro service, water plant, electricity and utility plant etc where incidents can be extreme when parameters are changed. We can limit the kind of parameters that can be changed and the thresholds monitored.
The Quantum Rugged 1595R security gateways deliver industry-leading threat prevention, integrated AI security, secure 5G connectivity and more to protect ICS for manufacturing, energy, utilities, and transportation industries.
As far as IoT is concerned, we have an add-on module on our firewall platform, which detects all those IoT devices, because nobody has control of what kind of IoT devices are connected and there is no inventory of IoT devices deployed. And they just keep increasing. On the network layer, we are able to see, based on the traffic, what kind of devices that exist. And then we automatically create an IoT policy for them and ensure that they come under secure access control. This helps prevent unauthorized access to and from IoT devices with zero-trust segmentation, locks IoT malicious intents with threat prevention security services, 300+ IPS signatures and on-device run-time protection.
As a region, we have been growing for the last few years. The plan is to grow even more aggressively in the near future because Check Point now has a large portfolio of solutions. Increasing our sales revenues, getting closer to customers and enhancing our partnership with the channel ecosystem are our priorities. At the same time having partnerships with some key government entities is a focus area for us. Having the Infinity portal within UAE and by expanding our team, we are able to take the message of prevention, the platform approach and the consolidation story to our partners and customers.
“With its range of capabilities, the Infinity Portal simplifies security management, improves visibility, and enhances security across the enterprise. We have onboarded more and more services on this platform.”
Naji Salama, CEO, IT Max Global discusses the need for data insurance in the face of cyberattacks and also addresses the impact of AI/Ml technologies in strengthening cybersecurity
With data security being a global issue and concern, what do you think is the value of UAE spending on data security in 2024 and how does this compare from last year (2023)?
There's a much stronger focus on data security spending here in the UAE. In fact, projections show the UAE will reach around US$1.8 Billion dedicated to data security in 2024. That's a significant jump, with a growth rate of about 15% compared to last year.
There are a few key drivers behind this increase. First, there's a heightened awareness of cyber threats. Businesses are more aware than ever of the potential damage cyberattacks can cause. Regulatory requirements are also playing a role,with stricter data protection laws coming into effect. And finally, don't forget the ongoing digital transformation across many sectors. As companies move more of their operations online, the need for robust data security becomes even more critical.
Overall, the increase in data security spending reflects a strong commitment from UAE Government and businesses to safeguarding their digital assets. It's a positive trend, and it shows that companies are taking the cyber threat seriously.
What is the value of cybercrime losses suffered by companies in the UAE every year? Unfortunately, it's difficult to pinpoint an exact figure. There are so many factors at play, and many cyber incidents go unreported. However, based on industry reports, estimates suggest cybercrime losses could be in the billions of dirhams annually. One recent estimate we’ve seen is US$1.4 billion. This highlights the importance of robust cybersecurity measures.

Naji Salama CEO, IT Max Global
What are the most prominent fraudulent schemes targeting UAE employees dealing with financial documents? In the UAE, we find that employees dealing with financial documents are increasingly targeted by sophisticated phishing and Business Email Compromise (BEC) schemes. Phishing is a deceptive practice where attackers impersonate legitimate entities. Business Email Compromise (BEC) is when cybercriminals fake (spoof) an email’s sender address to pose as executives or trusted partners, instructing employees to transfer funds or share confidential data. One recent case we’ve had to deal with was for a large enterprise where cybercriminals posing as the CEO had managed to get someone in finance to wire north of 500,000 AED to their account. We’ve also noticed that
ransomware attacks have become more prevalent, where malicious actors encrypt crucial financial documents and demand a ransom for their release. That’s why, on top of the robust security countermeasures provided to our customers, we also provide interactive security training for personnels. We believe that educating employees about these schemes is essential in mitigating these risks.
What are the best directions of data insurance services in UAE 2024?
Data insurance is certainly evolving rapidly, and we're seeing some exciting developments here in the UAE. One of the key areas I see is a move towards more comprehensive coverage. In the past, data insurance might have just focused on data breach notification. But today's businesses need protection from a wider range of threats. We're talking ransomware attacks, business disruptions due to cyber incidents, and even privacy violations. So, the best data insurance products will offer that broader shield.
Another important trend is the integration with cybersecurity solutions. Imagine a world where your data insurance seamlessly connects with your existing security posture. Maybe you get discounts for having strong security in place, or perhaps some insurers even bundle insurance with security services. This joined-up approach can really strengthen a company's overall cybersecurity.
Of course, with the rise of cloud computing, data insurance needs to adapt too. We're seeing a growing demand for solutions designed specifically for cloud environments.
Rainer W. Kaese, Senior Manager Business Development
Storage
Products at Toshiba Electronics Europe
says that wherever large volumes need to be stored at low cost while being accessed online, there is no alternative to hard drives
So, the digital age has nothing to do with hard drives anymore? Whoever believes that is mistaken. Even if the hard drive is not the first thing that comes to mind for many people when it comes to digital applications, that does not mean that they have no points of contact with classical memory – quite the opposite. In fact, they probably use digital services that depend on hard drives daily: No other storage medium that allows direct access provides such high storage capacities at such low costs. Toshiba names five popular applications of the digital age in which the hard drive plays a crucial role in the background:
● Video streaming: Streaming services such as Netflix, Disney+, and similar, as well as the multimedia libraries of the TV channels or YouTube, hold thousands of videos, often in high resolution, that require an enormous amount of storage capacity. For cost reasons, these volumes of data in the petabyte range can only be stored on hard drives; otherwise, the providers would not be able to refinance the services. This is particularly the case because the videos are not only stored on a central system, but copies are also stored on systems in different regions to enable users in any part of the world to access them quickly.
● Online shopping: It is not just at Christmas or Easter time that online shopping is enjoying ever-increasing popularity. However, countless images, product descriptions and product data require plenty of storage capacity, ideally costing as little as possible so as not to further reduce the tight margins in many retail sectors. This
is why the bulk of the data is stored on hard drives. Only certain types of temporary data required for quick purchase transactions, such as the shopping cart and payment information, are temporarily stored on all-flash based storage.
● Map services: Anyone can go travelling digitally today. With their zoom functions, Google Maps and similar opens up highly detailed views of every corner of the world. In large cities, views of the buildings are also available for many streets – older images are even available in some cases, meaning that users can even take a trip back in time of several years. The numerous satellite images, aerial photos and photos of streets require an enormous volume of storage capacity and are therefore held on hard drives in cloud data centres. Google even receives the aerial images from government authorities, research institutes and commercial suppliers on hard drives.
● Online memories: Cloud-based memory services such as Dropbox, iCloud or OneDrive are practical for backing up important data or synchronising it across multiple devices. Practically all cloud services store large volumes of data on hard drives at low cost. Special software-defined architectures are used here: These combine a large number of drives in storage pools, delivering much higher performance than individual drives and handling a large number of simultaneous read and write access operations by users and devices.
● Social media networks: More than five billion people use social media networks,

Rainer W. Kaese Senior Manager Business Development Storage Products, Toshiba Electronics
and the figure is increasing daily. The number of photos, videos and audio files uploaded 24/7 seems almost incomprehensible. For Instagram alone the figure is over 1,000 photos per second, and for YouTube more than 500 hours of video material per minute. The network operators would not be able to cope with these volumes of data without hard drives.
Wherever large volumes need to be stored at low cost while being accessed online, there is no alternative to hard drives – regardless of whether it be popular consumer services such as video streaming, modern enterprise applications for ERP and CRM, or digitally monitored and controlled production systems. Whereas many people use smartphones and tablets on a private basis, hard drives - except NAS systems in the home - are now mainly used in data centres, where they bear the main burden of data processing in the digital age. This is why millions of drives continue to be sold year after year, which will remain unchanged over the coming years.
Ekta Puthran, Head of Sales APAC & MEA - Collaboration, Barco discusses how Video bars have emerged as a cornerstone of modern meeting spaces, seamlessly blending in-person and remote collaboration

Ekta Puthran Head of Sales APAC & MEA –Collaboration, Barco
In today’s hybrid work environment, attending remote meetings can be tedious and tiresome. Imagine transforming these meetings from mundane to extraordinary. It’s time to bid goodbye to boring cameras and say hello to video bars. These powerful allin-one collaboration devices give you the peace of mind and efficiency you need to drive engagement and efficiency.
Video bars have emerged as a cornerstone of modern meeting spaces, seamlessly blending in-person and remote collaboration. These devices which integrate high-quality audio and video capabilities, are increasingly popular for their ability to transform traditional meetings into dynamic, interactive experiences.
As organizations adapt to the demands of a hybrid workforce, video bars provide a streamlined, user-friendly solution that enhances engagement, simplifies IT management, and ensures everyone is seen and heard, regardless of their location. This surge in popularity underscores the critical role of innovative technology in fostering effective communication and collaboration in today's flexible work environments.
Video bars are all-in-one devices that integrate collaboration, audio, and video functionalities, into one streamlined solution for hybrid meetings. They come with benefits like reduced costs, simplified management, and sustainable design, making them a smart investment for any organization.
Video bars streamline meeting room efficiency and reduce installation costs and complexity. By combining audio, video, and collaboration features into a single device, fewer cables and less hardware are needed, minimizing installation time and cost. This simplicity also translates into fewer points of failure, which results in less downtime and lower maintenance costs.
For IT managers, this ease of installation and reduced need for ongoing technical support means more efficient use of resources. Video bars offer a straightforward, cost-effective solution that provides a significant return on investment in the long run.
Investing in video bars is a decision that pays off over time. These
devices are designed to be scalable and future-proof, with regular firmware updates ensuring they remain at the cutting edge of technology without additional costs. They integrate seamlessly into existing networks, providing robust security and stability.
Technology brands often provide comprehensive service packages, offering extended warranties and support, which further reduces long-term costs. In this way organizations can get the most out of future-proof investments that grow with their changing business needs.
In hybrid meetings, clear communication is crucial. Video bars excel in providing high-quality audio and advanced video capabilities, ensuring all participants feel seen and heard, regardless of their location.
First and foremost, clear audio is essential for effective communication. Audio degradations like background noise or clipping can significantly affect viewers’ satisfaction with video content. Video bars address these concerns with features like multiple microphones with beamforming technology, real-time noise removal, and acoustic echo cancellation. These capabilities ensure that voices are captured clearly, and background noise is minimized, enhancing the overall meeting experience.
In addition, video bars typically feature high-resolution cameras with wide fields of view and AI-powered framing options, ensuring that all participants are visible and well-framed during meetings. When video bars support dual-screen setups, they allow remote participants to be displayed alongside shared content for better interaction and more meeting inclusivity.
Advance features like these help remote workers to see and engage with in-room participants effectively, making hybrid meetings more dynamic and collaborative.
Video bars can facilitate seamless, wireless conferencing, allowing participants to join meetings quickly without the hassle of cables. Interactive features such as touchback, blackboarding,
and annotation enhance collaboration even further by enabling real-time interaction with shared content.
We’ve found collaboration tools like the ClickShare video bars, make it easy for remote participants to contribute as actively as participants in the room, fostering a more dynamic, interactive meeting environment.
Managing multiple meeting room devices can be challenging for IT departments. Video bars simplify this process with remote management capabilities. Using cloud-based tools, IT professionals can configure, monitor, and update devices from anywhere, ensuring maximum uptime and performance.
These management tools additionally provide key system health statistics, device usage insights, and meeting behavior data, helping IT professionals optimize meeting experiences and improve the return on investment for the technology. This remote management capability reduces the need for on-site technical support, allowing IT teams to focus on other critical tasks.
Video contribute to your sustainability goals with energy-efficient designs and eco-friendly materials. Check if the video bars are made from recycled plastics and feature recycled packaging. Additionally, passive cooling systems can reduce energy consumption, making these devices a greener choice for meeting rooms.
Choosing energy-efficient technology not only supports environmental goals but also enhances an organization’s reputation and appeal to eco-conscious clients and partners.
By investing in all-in-one video bars, organizations can create more dynamic, inclusive, and efficient meeting experiences, a ultimately leading to better communication, collaboration, and productivity. For IT managers, these devices represent a significant step forward in simplifying technology management and ensuring seamless, high-quality hybrid meetings.
Andrew Burton, Global Industry Director Manufacturing discusses how AI empowers manufacturers to optimize processes, enhance product quality, and streamline operations

Andrew Burton Global Industry Director Manufacturing
The manufacturing industry has been going through a rapid period of transformation, utilizing digital technology to improve its core operations, reaping significant efficiency and operational benefits in return. However, with the dawn of more advanced technologies and initiatives such as Industry 4.0, data transformation and smart factories, Artificial Intelligence (AI) stands as the technological force that will truly reshape the industry from the ground up.
No longer confined to science fiction, the addition of AI is seamlessly integrating itself into the industry, ushering in a new era of smart manufacturing. Driven by powerful algorithms and data analytics, AI empowers manufacturers to optimize processes, enhance product quality, and streamline operations.
In this blog, we will delve into specific use cases, highlighting how AI is revolutionizing manufacturing and exploring its profound impact on how we create, assemble, and deliver products to the world. As manufacturers journey further into the era of AI, they will find themselves equipped with powerful tools to enhance productivity, reduce costs, and ensure the highest standards of quality. Embracing these innovations and recognizing the importance of quality data will be key to thriving in the ever-evolving landscape of modern manufacturing.
Generative AI is driving the development of sophisticated digital twin models. These digital replicas of physical manufacturing systems allow for real-time simulation, monitoring, and optimization. By leveraging these digital twins, manufacturers gain the ability to test and refine their processes virtually, reducing downtime, and enhancing overall efficiency. Generative AI continuously updates these models, ensuring they stay accurate and reflect the ever-changing production environment.
Courtesy of the digital twin, manufacturers can gain valuable insights and adapt to changing market demands. By leveraging AI within supply and demand forecasting, scheduling, and planning
optimization, manufacturers can streamline their operations for maximum efficiency. Moreover, with ongoing challenges around increasing labor costs, raw materials costs and supply chain issues, AI has the potential to help manufacturers overcome economic headwinds and gain competitive advantage.
Demand forecasting is a crucial component of modern manufacturing. When combined with external data feeds and AI-powered insights, it will undergo a significant transformation. The integration of AI with demand forecasting offers a wide range of possibilities, improving predictive accuracy.
For example, customers whose sales are dependent on weather conditions – such as the food and beverage industry – can expect an increase in forecast accuracy of up to 78% compared to existing demand planning models. Event-driven demand prediction, fueled by external factors such as weather patterns, utilizes the power of AI to anticipate changes in demand that might be otherwise overlooked. By taking these factors into account, manufacturers can prepare for shifts in the market with greater effectiveness.
Supply Chain Management is a complex ecosystem in which AI will play a transformative role. With its advanced algorithms and data analysis capabilities, AI helps optimize this intricate web by predicting demand patterns, managing inventory levels, and designing efficient logistics routes. By taking a proactive stance, AI ensures that manufacturers remain agile and minimize delays or overstock situations. This makes the supply chain process more efficient and effective overall.
Industrial manufacturers face many operational challenges, and one of the biggest is managing complex scheduling lines. However, the integration of AI presents a range of opportunities for optimization and improvement. By utilizing IFS’s Planning and Scheduling Optimization module manufacturers are already benefiting from AI-powered Visual Production Planning and Predictions.
Furthermore, AI's reach extends into Resource and Location Forecasting, a critical element for achieving manufacturing efficiency. By using AI, manufacturers can facilitate Process Optimization, employing advanced algorithms to scrutinize data and pinpoint areas for improvement, ultimately driving increased efficiency, reduced waste, and energy conservation.
AI is more than just a technology tool – it is an exciting accelerator that transforms manufacturing into a more efficient, sustainable, and secure sector. For example, AI's advantages extend to autonomous vehicles and forklifts, which can control material handling and take shop floor operations to new heights. AI also simplifies the creation of Asset Maintenance Checklists and provides invaluable insights into Asset Performance Management (APM), enabling a shift from planned to truly predictive maintenance.
Minimizing industrial waste while still ensuring remains a persistent challenge; industrial manufacturing waste accounts for at least 50% of the waste generated on a global scale. To tackle this issue, AI has emerged as a promising solution to strike a delicate balance between quality control and waste reduction by enhancing our ability to make crucial, intricate, high-volume decisions. With AI-powered systems, manufacturers can now optimize their operations and make more informed decisions, leading to reduced waste and improved efficiency.
For example, a pivotal application is in Quality Control, where AI-driven computer vision systems take the lead. These systems consistently scrutinize products, thus upholding a standard of high-quality production while simultaneously reducing the need for labor-intensive manual inspections. Ultimately AI extends into Product Lifecycle Management (PLM), guiding the entire lifespan of products, informing product design and manufacturing processes, resulting in iterative enhancements and higher-quality outputs.
Process Monitoring is another area which lends itself to AI application, offering real-time oversight of manufacturing processes. Through constant vigilance and swift adjustments, AI ensures that quality remains uncompromised while efficiency is consistently optimized. This dynamic, real-time control enhances the overall production process.
In the realm of anomaly detection, generative AI shines as a self-learning sentinel. It continuously analyzes data streams, identifies normal patterns, and evolves its understanding of what constitutes anomalies. This self-learning capability allows it to proactively detect and alert operators to emerging issues, empowering manufacturers to take corrective action before they impact production.
With all these AI use cases becoming available, their relevance varies among manufacturers, and how they want to use it.
So, how do you start?
1. Acknowledge the paramount importance of quality data, as it underpins informed decisions, process optimization, and product quality. Then put in place measures to keep the data accurate.
2. Assess your processes and craft a strategic plan, prioritizing those with the highest potential return on investment from AI integration.
3. Identify bottlenecks best for AI anomaly monitoring, providing invaluable insights into their root causes and enabling their reduction.
Rodolph Khoury, Managing Director - Dubai & Northern Emirates, Avaya discusses the need to evolving a holistic approach to customer experience (CX) - one which integrates CX with employee experience (EX) and business growth

Rodolph Khoury Managing Director –Dubai & Northern Emirates, Avaya
Having a great product is no longer enough to guarantee loyalty and keep customers coming back. Even brands known for their loyal followings based on their great products, are seeing customers ‘switch sides’, or move to completely different brands. But there is one thing that can drive both loyalty and business growth – a holistic approach to outstanding customer experience.
The level of competition is strong no matter the industry, and there is an ever-increasing number of brands entering markets to stake their claim. Add to the mix the impacts of unpredictable global challenges, such as rising inflation and economic uncertainty, and it’s clear why winning and retaining customers – many of whom are tightening their purse strings – is incredibly complex.
Then there’s the ever-evolving criteria which inform customers’ buying decisions. Corporate social responsibility (CSR), sustainability commitments and humanitarian causes are just some of the influential factors everyday citizens research before committing to a brand, whether it’s a bank, insurer, retailer, airline, or fastfood restaurant.
This plethora of variables makes customer service imperative. A report found 97% of consumers feel customer service interactions correlate directly with their loyalty to a brand, and 60% have switched to other brands on the back of a bad experience. The data correlates with a separate report which indicates 81% of consumers are likely to become repeat buyers following a positive customer service experience. In addition, more than 70% of Middle Eastern businesses understand the significance of service availability and reliability.
But customer service isn’t easy; customers are demanding and can be fickle, and come with a broad range of preferences that businesses must constantly adapt to. Where once politeness and a smile may have appeased customers, today’s expectation is for organisations to accommodate the expectation for completely personalised experiences that can vary day to day.
This is especially true now that brand interactions are becoming more digital. In the UAE and Saudi Arabia, the average percent-
age of users choosing to interact through digital or remote channels has shot up to 78%. Customers want to self-serve, talk to AI bots, or speak with real people on their own terms, and don’t just expect responses almost instantly, but demand brands to anticipate their queries.
Among the biggest challenges in delivering customer service that meets these requirements is bridging the gap between current capabilities and these evolving customer expectations while mitigating the risks associated with overhauling business communications infrastructure and the costs that come with it. Other contributing factors are the continuing difficulty in finding and retaining top talent, alongside the imperative to drive revenue and growth amid competitive pressures.
Overcoming them relies on a holistic approach to customer experience (CX) – one which integrates CX with employee experience (EX) and business growth. The formula for Enterprise CX, CX + EX = BG (business growth), reflects a symbiotic relationship whereby organisations are committed to investing in fulfilling customer needs to ensure every interaction is meaningful and contributes to brand loyalty, regardless of a customers’ preferred method of communication.
One part of that commitment means constantly evolving and refining employee training and upskilling programs. The other part is adapting and enhancing communications and engagement strategies to keep up with customer demands.
However, the prospect of making an abrupt change from existing communications infrastructure carries high risks for businesses, including disruptions to operations and customer service continuity. It’s instability that can not only hurt the CX brands offer today, but also cause consequences to future innovation and new business outcomes.
That’s precisely why any such transformation doesn’t need to happen overnight. On the contrary, a pragmatic, step-by-step strategy enables organisations to forge ahead into new territories, introduce new services and channels, and explore advanced capabilities such as generative AI without compromising existing strengths.
It’s about building upon what already works – leveraging familiar processes, systems, and technologies as a foundation for introducing new innovations. For most companies, the safest route to innovation is identifying specific functions or departments primed for change, and uphauling those before a new service is rolled out across the whole organisation.
This approach is especially pertinent for implementing AI, which, while far from a new concept, is still an early-stage vision when it comes to customer service.
Companies looking to supercharge their employees’ productivity while removing cumbersome administrative tasks have the opportunity to test a large language model (LLM) within a specific team, evaluate the outcomes, and make necessary amendments to ensure the final product that other teams gain access to won’t create disruption or demand steep learning curves.
This method is equally valuable for chatbots; research shows 94% of leaders believe AI can enhance customer self-service, but before all customers are asked to engage with a chatbot, it must be trusted to handle complex and unexpected enquiries.
CX, can make or break a brand in a world where customers are more willing to jump ship than ever before. By adopting a holistic approach to CX, rather than being tempted by a rapid overhaul that only solves for one part of the equation, organisations and their teams will be geared to meet the expectations of customers without exposing their existing successes to high-risk disruption.

Lori MacVittie, F5 Distinguished Engineer discusses
key aspects to understand when defining an AI strategy
There are probably more than three things you should know, but let’s start with these three and go from there, shall we?
First, it’s important to note that AI is real. Yes, it’s over-hyped. Yes, entire portfolios are being “AI-washed” in the same way everything suddenly became a “cloud” product over a decade ago. But it’s real according to the folks who know, which is to say decision makers in our 2024 State of AI Application Strategy research.
While most organizations (69%) are conducting research on technology and use cases, 43% say they have implemented AI at scale. That’s either generative or predictive.
Somewhat disconcerting is the finding that 47% of those already implementing AI of some kind have no—zero, nada, zilch—defined strategy for AI. If we’ve learned anything from the rush to public cloud, it should be that jumping in without a strategy is going to cause problems down the road.
To help you define that strategy—especially when trying to understand the operational and security implications—we’ve put together a list of three things you should consider.
1. AI applications are modern applications
It shouldn’t need to be said, but let’s say it anyway. AI applications are modern applications. While the core of an AI application is the model, there are many other components—inferencing server, data sources, decoders, encoders, etc.—that make up an “AI application.”
These components are typically deployed as modern applications; that is, they leverage Kubernetes and its constructs for scalability, scheduling, and even security. Because different

Lori MacVittie F5 Distinguished Engineer
components have different resource needs—some workloads will benefit from GPU acceleration and others just need plain old CPUs—deployment as a modern application makes the most sense and allows for greater flexibility in ensuring each of the workloads in an AI application is deployed and scaled optimally based on its specific computing needs.
What this means is that AI applications face many of the same challenges as any other modern application. The lessons you’ve learned from scaling and securing existing modern applications will help you do the same for AI applications.
Leverage existing knowledge and practices for application delivery and security but expand to include approaches that recognize that different components of AI applications may have varying resource needs, such as GPU acceleration for compute-intensive tasks or CPU resources for less compute-intensive workloads. Modern application deployments allow for flexibility in allocating resources based on the specific requirements of each component, optimizing for performance and cost efficiency.
Yes, I know I just hammered home the “they are modern applications” point but there are differences that impact architecture, operations, and security.
First, AI applications exchange unstructured data. Those prompts have no format, no length or data type requirements, and the eager adoption of multi-modal LLMs only adds to the chaos that is a “request.” In the sense that most AI applications wrap a prompt and response in a JSON payload, I suppose you could say it’s structured, but it’s not because the actual payload is, well, undefined.
Second, AI applications communicate almost exclusively with a model via an API. That means bot detection solutions that use “human” or “machine” as a base criterion for access are not going to be as helpful. Security services helping to weed out “bad bots” from “good bots” are going to be an important part of any AI strategy. The reliance on APIs is also why, in our 2024 State of Application Strategy research, we found that the top security service planned for protecting AI models is API security.
Lastly, interaction patterns for AI applications are often dynamic, variable, and unpredictable. Generally, today’s security services watch for anomalies in mouse click and typing rates per page, because the services can infer “bot” behavior based on deviations from established human average standards. That doesn’t work when someone is using a conversational interface, and may type, retype, and submit questions on a highly irregular basis. Given that many security solutions today rely on behavioral analysis—including API security—that means some adjustments will be necessary.
You will need additional security capabilities to properly govern AI applications. Rethink traditional security approaches that may not adequately capture the nuances of conversational interactions. Explore innovative approaches such as real-time monitoring of interaction patterns and adaptive access control mechanisms based on contextual cues. Recognize the critical role of APIs in facilitating communication with AI models. Invest in robust API security solutions to protect against unauthorized access, data breaches, and malicious attacks.
Like the eventual reality that is multicloud, it’s highly unlikely organizations will standardize on a single AI model. That’s because different models can be a better fit for certain use cases.
That’s why we are unsurprised to learn that the average enterprise is already using almost three (2.9) distinct models, inclusive of open-source and proprietary models. When we look at the use of models based on use cases, we start to see a pattern. For example, in use cases which rely heavily on sensitive corporate data or ideas—security ops and content creation—we see significant trends toward open-source models. On the other hand, looking at a use case for automation, we see Microsoft gaining use, largely due to its ability to integrate with the tools and processes already in use at many organizations.
This is important to understand because the practices, tools, and technologies needed to deliver and secure a SaaS-managed AI model is different than that of a cloud-managed AI model is different than that of a self-managed AI model. While there are certainly similarities—especially for security—there are significant differences that will need to be addressed for each deployment pattern used.
Analyze the use cases within your organization and identify patterns in the adoption of different AI models. Consider factors such as data sensitivity, integration capabilities, and alignment with existing tools and processes. Tailor your approach to deployment and security based on the specific characteristics of each deployment pattern.
There are a lot of considerations for building, operating, and securing AI applications, not the least of which is all the new requirements for model security and scalability. But many of the lessons learned from deploying modern applications across core, cloud, and edge for the past decade will serve organizations well. The core challenges remain the same, and applying the same level of rigor to scaling and securing AI applications will go a long way toward a successful implementation.
But forgoing attention to the differences and leaping in without at least a semi-formal strategy for addressing delivery and security challenges is bound to lead to disappointment down the road.
Implementing zero trust involves adopting a comprehensive philosophy across all security operations opines Richard Sorosina, Chief Technical Security Officer EMEA and APAC, Qualys

Richard Sorosina Chief Technical Security Officer EMEA and APAC, Qualys
Over the past three years, the position of zero trust and access control has become more and more important to CISOs. According to the annual Leadership Perspective Survey published by Gartner peer community company, Evanta, in 2024, the category of User Access, IAM and Zero Trust is now the number one functional priority for CISOs, taking over from cloud security. However, while many CISOs want to adopt a zero trust mindset and embrace better security for their operations, getting to this goal is much harder than they imagine.
CISOs want to implement zero trust because it reduces the likelihood of a breach and the potential impact of any breach that does occur. It also makes it easier to take a proactive risk management approach across the organisation. As part of this, it focuses on unmanaged devices. The Zero Trust Security Architecture model states that no assets (inside or outside the perimeter) should be automatically trusted.
The issue around zero trust is that it is not a technology project. Instead, implementing zero trust involves adopting a comprehensive philosophy across all security operations, encompassing network configuration, impact limitation and micro segmentation processes, in order to deliver that improved security posture for the organisation.
Getting this change in culture in place is difficult. It needs careful leadership, development of links across the organisation, and sustained support to make the change stick. However, there is a fundamental issue that many CISOs still need to address if they want to make zero trust effective. That is how many companies still have assets that they don’t know about.
According to our research, 69 percent of organisations experienced at least one cyber attack due to an unknown or unmanaged asset. While traditionally unmanaged assets might be thought of as rogue endpoints or additional servers in the data centre, today these assets can include a wide variety of IT services, including software installed, cloud-based workloads, user accounts that have not been properly managed, and connected Internet of Things (IoT) devices too. Each of these assets can either get onto the corporate network or connect to it, and then represent a potential route for an attack.
In our work with companies, we found that CISOs had to add on average 34 percent more assets to their asset lists. This represents a huge additional overhead for companies around their IT, increasing management costs and potential risks for the future, if not addressed.
To address these issues and make zero trust a reality, we first have to admit where the problems are. Some of these may surprise you.
The first issue is whether we recognise that there is a problem around IT asset management at all. After all, while you can’t secure what you don’t know about, how many of us put this at the top of our to do lists? If your asset list is incomplete, then you are not able to make accurate decisions on what to prioritise across cloud workloads, containers, IoT systems, mobile devices, remote endpoints, and Operational Technology (OT) deployments. In turn, this can affect all your assumptions on risk modelling and how secure you really are. We may end up being massively over-confident about how much risk the business is exposed to.
The second issue we have to admit is that we may not address asset management as a critical competency. Instead, it is often delegated or passed around the team, and treated as a chore. It also relies on multiple teams to carry out the work involved. Without executive attention, it is hard to keep any asset list up to date, current and accurate. When it is treated as a critical task, then it will get the investment and concentration needed.
Alongside senior level support, we have to recognise that existing enterprise software tools cannot illuminate every platform. While we might have an accurate view of the cloud, say, we might not have that same level of accuracy and insight for IoT devices. Using any one tool to get the information we need is not reliable enough when there are so many platforms in place. Instead, we have to collaborate and use different methods to get all the data that we need, then organise it effectively. This includes blending a
range of different technologies, from active and passive scanning techniques and security agents to API-based discovery tools.
This combination will establish a comprehensive inventory of all your IT assets and keep it up to date in real time. This record should allow your team to automatically distinguish between trusted and untrusted assets and make decisions on how to handle those assets effectively. In turn, this makes it easier to apply zero-trust principles across all your devices.
Once you can see all your assets, you can make more accurate and informed decisions around risk. With companies having a third more IT assets on average than they expect, that category will include a range of different assets that will vary from inconsequential and forgotten devices through to critical applications that suffered from what Douglas Adams called the “Somebody Else’s Problem Field” issue.
Knowing about those assets is the first step to improving security across a diverse device landscape. Based on this information, you can set out a zero trust strategy and then concentrate your resources on those devices, applications and workloads that are critical to the business. This approach reduces the potential impact of any breach, shrinks the potential attack surface and makes risk management programs more effective. Unmanaged devices represent a significant risk to security programs, but getting insight into all the devices that might enter your network is not impossible. It just needs prioritisation.
“CISOs want to implement zero trust because it reduces the likelihood of a breach and the potential impact of any breach that does occur. It also makes it easier to take a proactive risk management approach across the organisation.”

Toshiba Electronics Europe GmbH (Toshiba) announced the release of its MG10-D Series, a family of air-filled conventional magnetic recording (CMR) HDDs supporting SAS and SATA interfaces and capacities of up to 10TB. Crafted with precision engineering and over 50 years of Toshiba experience, the MG10-D Series delivers improved performance and power efficiency over prior generations. With sanitize instant erase (SIE) and self-encrypting drive (SED) options, valuable data is safeguarded by a storage solution known for its robust performance and unwavering dependability.
Built for the increasing application demands of enterprise server and storage solutions, the MG10-D Series delivers a new level of performance. For example, compared with the previous model, the new 10TB MG10ADA10TE provides an approximately 13% better maximum sustained transfer speed of 268MiB/s and doubles the cache buffer size to 512MiB. It also reduces power consumption in active idle mode by approximately 21%, to 5.74W. Architected to deliver improved total cost of ownership (TCO), the new MG10-D Series fits seamlessly into a wide variety of business-critical applica-
Asus ProArt P16 is the ultimate creative companion for the studio and on the move. Its OLED touchscreen ensures precise color accuracy for flawless proofing, while versatile I/O ports seamlessly connect all your peripherals. This NVIDIA Studio-validated laptop packs a GeForce RTX 40 Series Laptop GPU, providing powerful graphics and 321 TOPS AI performance. Additionally, it features up to a 50 TOPS AMD Ryzen AI 9 HX 370 processor, delivering exceptional processing power. With AI-enhanced creative features, military-grade toughness, and a long-lasting battery, ProArt P16 transforms any setting into your studio.
ProArt P16 is your on-the-go studio. It breezes
tions, such as email, data analytics, data retention, and surveillance.
“Toshiba’s MG10-D Series delivers exceptional performance to meet the demands of growing business critical applications. The new cutting-edge design of the MG10-D Series is engineered for sustainable enterprise environments and fits seamlessly into existing infrastructure reducing TCO,” said Larry Martinez-Palomo, Vice President, Head of Storage Products Division at Toshiba.
Highlights:
• The MG10-D Series is a 5-disk CMR standard 3.5-inch, 7200 RPM airfilled platform.
• Available capacities are 2TB, 4TB, 6TB, 8TB, and 10TB for both SAS and SATA. SATA is also available in a 1TB drive.
• The series supports 6Gb/s SATA or 12Gb/s SAS interface options in Advanced format 512e and 4Kn.
• A 512n option is available on the 1TB, 2TB, and 4TB offerings to support legacy systems with native 512 byte block sizes.
• Designed for 24x7 enterprise reliability, the MG10-D Series has a workload rating of 550TB, an AFR of 0.44% and an MTTF/MTBF of 2M hours.
through tasks with professional ease. Advanced thermal design guarantees sustained peak perfor mance. Meanwhile, the lightning-fast RAM and SSD slash loading times, elevating your projects to masterpieces wherever you go.
Boasting 50 TOPS of NPU processing power, it delivers AI-enhanced efficiency. With dominant single-core and multi-core performance, importing and rendering demanding 4K footage is a breeze. The Ryzen AI-powered NPU accelerates AI-driv en tasks in Adobe Premiere Pro, streamlining processes like speech-to-text transcribing, auto se quence-framing, and scene-edit detection. Focus on storytelling, not workflow.

Acer expanded its TravelMate series with new AI-enhanced models. Powered with the latest generation of processors with built-in NPUs, the new laptops offer next-level performance, productivity, and mobility, in addition to enhanced security and connectivity features.
AI is transforming the way we do business, presenting new opportunities for increased productivity, personalized experience and power efficiency. These revolutions are causing a ripple effect in the PC market, offering significant benefits to both vendors and their partners. In essence, AI improves efficiency, drives business performance, and helps boost output.
The Acer TravelMate series unlocks all the AI advantages that enhance productivity through high-powered processors, fast-charging batteries, premium connectivity options, and dedicated AI apps; plus, support from TravelMateSense™, Windows 11 Pro, Copilot, Teams, and professional, hardware-grade security. This translates into 42% faster completion of workloadsa, 58% drop in security incidentsb and 68% improvement in quality of workc.
Along with a host of essential network reliability features, both new switches in the series also support an external redundant power supply to ensure business operations continue unimpeded.
Highlights:
• Acer TravelMate P6 14 (TMP614-73) is powered by the latest Intel Core Ultra 7 processors with Intel vPro, built-in Intel Graphics and Intel AI Boost to unlock new AI experiences, performance, and power efficiency in the premium device.


• The Intel Evo edition business laptop has up to 32 GB of LPDR5X memory2, and up to 1 TB M.2 PCIe SSD2 for long-lasting battery life and fast response even when handling large workloads.
• A stunning 14-inch WQXGA+ OLED (2880 x 1800) panel with a touch option, paired with a 16:10 aspect ratio, narrow bezels, and DTS audio delight users with immersive audio and visual experiences.
• Cinematic colors and motion clarity can be experienced when watching videos with 100% DCI-P3 color gamut support and VESA HDR TrueBlack 500 certification.
• The TravelMate P6 14 also comes with Wi-Fi 7 and Bluetooth 5.3, and a large availability of essential ports that support Thunderbolt 4 for seamless connectivity and convenience during business travels
Effortlessly tackle tasks with AI-enhanced multitasking prowess of Microsoft next level AI PC & Copilot.
Make your daily computing more efficient and fun with great new NPU-powered features such as Recall, Live Captions, Cocreator, Studio Effects, without the need to be always online.
powerful performance to handle demanding and resource-intensive projects anywhere you go
Create anywhere, lightweight at 1.85kg and 14.9 mm thin designed for uncompromised mobility.
Strictly tested US military-grade durability to meet diverse outdoor environment
A major challenge for organizations arises in justifying the substantial investment in GenAI for productivity enhancement
At least 30% of generative AI (GenAI) projects will be abandoned after proof of concept by the end of 2025, due to poor data quality, inadequate risk controls, escalating costs or unclear business value, according to Gartner, Inc.
Rita Sallam, Distinguished VP Analyst at Gartner said, “After last year's hype, executives are impatient to see returns on GenAI investments, yet organizations are struggling to prove and realize value. As the scope of initiatives widen, the financial burden of developing and deploying GenAI models is increasingly felt.”
A major challenge for organizations arises in justifying the substantial investment in GenAI for productivity enhancement, which can be difficult to directly translate into financial benefit, according to Gartner. Many organizations are leveraging GenAI to transform their business models and create new business opportunities. However, these deployment approaches come with significant costs, ranging from $5 million to $20 million (see Figure 1). “Unfortunately, there is no one size fits
all with GenAI, and costs aren’t as predictable as other technologies,” said Sallam. “What you spend, the use cases you invest in and the deployment approaches you take, all determine the costs. Whether you’re a market disruptor and want to infuse AI everywhere, or you have a more conservative focus on productivity gains or extending existing processes, each has different levels of cost, risk, variability and strategic impact.”
Regardless of AI ambition, Gartner research indicates GenAI requires a higher tolerance for indirect, future financial investment criteria versus immediate return on investment (ROI). Historically, many CFOs have not been comfortable with investing today for indirect value in the future. This reluctance can skew investment allocation to tactical versus strategic outcomes.
Earlier adopters across industries and business processes are reporting a range of business improvements that vary by use case, job type and skill level of the
worker. According to a recent Gartner survey, respondents reported 15.8% revenue increase, 15.2% cost savings and 22.6% productivity improvement on average. The survey of 822 business leaders was conducted between September and November 2023.
“This data serves as a valuable reference point for assessing the business value derived from GenAI business model innovation,” said Sallam. “But it’s important to acknowledge the challenges in estimating that value, as benefits are very company, use case, role and workforce specific. Often, the impact may not be immediately evident and may materialize over time. However, this delay doesn’t diminish the potential benefits.”
By analyzing the business value and the total costs of GenAI business model innovation, organizations can establish the direct ROI and future value impact, according to Gartner. This serves as a crucial tool for making informed investment decisions about GenAI business model innovation.
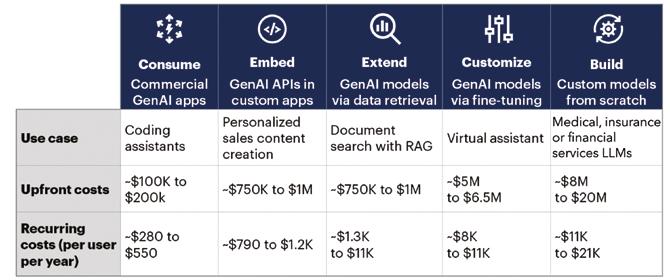
Source: Gartner (July 2024)