
37 minute read
SOLUTIONS SHOWCASE
SOLUTIONS SHOWCASE AGILENCE
Retail 20/20—Blurring the Line between Exception Reporting and Business Intelligence
Anyone who works in retail loss prevention knows what exception-based reporting (EBR) is. After all, it has been the industry standard for a few decades now. In their prime EBR programs were beneficial in helping to prevent future losses at the point-of-sale (POS), but even the best tools were difficult to use. They required a basic knowledge of structured query language (SQL). They would take weeks to return data, if you were lucky. And they did not generate actual reports, producing only spreadsheets of data that the user had to manually sort through.
Emerging Tools
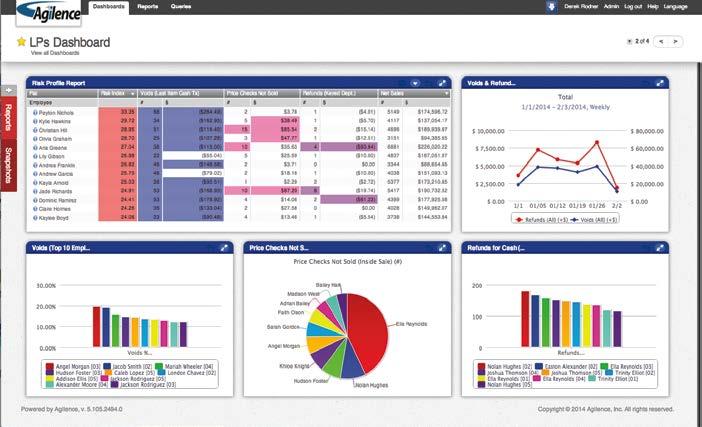
Enter the 21st century and the emergence of business intelligence (BI) tools. BI programs allow users to examine the business as a whole by collecting data from all possible inputs, then reporting on that data. These advanced tools tend to be highly personalized and colorful. The former is vital because it allows the user to see exactly what they want on their own
terms, but the latter can be just as important. This is because color allows certain figures to pop off the screen, quickly drawing your attention to the items that need immediate attention.
While each of these tools serves its own purpose, the separation of the two can leave loss prevention professionals in the dark. This is where Retail 20/20™ comes in—the next-generation reporting solution. Retail 20/20 blurs the line between EBR and BI by taking the best features from both and creating something that truly works for loss prevention professionals. Below are a few key features that allow Retail 20/20 to stand out from the traditional exception-reporting tools.
Automated Compliance. ACT™, Retail 20/20’s automated compliance tool, enables retailers to create workflows that automatically triage and report on alert triggers that can be based on individual events, summary data, or KPIs. ACT is also built to make chain-wide compliance simpler by allowing retailers to attach action plans and recommended resolutions to specific causes. The system then reports back to district managers and corporate-level users indicating which issues have been resolved, and if there are still open items that need to be addressed.
Chain-Wide Data Integration. Much like you, we know that losses can occur beyond the POS. This is why Retail 20/20 has the unique capability to collect data from almost any source, including loyalty programs, alarms and access control, inventory, human resource data, and much more. Collecting and reporting on all of this data simultaneously allows you to spot trends and track employee behavior more efficiently, helping you to stop fraud faster.
Reports That Actually Report. With all of this data coming in, you need reports that improve the process without adding to it. Retail 20/20’s reports run continually, eliminating the need for overnight jobs, and can be personalize using the drag-and-drop report builder—no knowledge of SQL required. The reports produced by Retail 20/20 use bright, colorful charts and graphs that allow outliers and trends to stand out. Click-to-drill-down then allows you to easily investigate issues all the way down to the item level. Advanced Queries without SQL. Creating a query in traditional EBR tools can feel like solving a calculus problem. If you do one thing wrong, you’ll never get the desired results. But Retail 20/20 is different. Creating queries has never been easier because you can use the language that your organization is familiar with. After just a few minutes with our query builder, you will be able to create queries delivering actionable insights that previously took you a full training session to nail down.
Future Ready
At Agilence we know that the technology being used today may not be the technology that is used tomorrow. To help you stay ahead of the curve we keep our ears to the ground and continually develop Retail 20/20 to be compatible with new technologies as they come across the horizon. Whether it is the next-generation EAS or RFID tag, a unique mobile POS system, or even wearable technology, rest assured that we are working to keep Retail 20/20 future ready.
SOLUTIONS SHOWCASE ALPHA
Arming Retailers for the Battle
Shoplifting is as old as shopping. Over the years this problem has escalated into a major battle that costs retailers more than $112 billion globally according to the Global Retail Theft Barometer. Growing concerns keep loss prevention high on the agenda of retailers. “Companies are keen to invest in effective and proven loss prevention methods by collaborating with technology companies and specialists for loss management solutions to diminish these shrink problems,” states Euromonitor International.
For more than forty years, Alpha’s primary goal has been to partner with retailers and provide innovative solutions to help win the war against shrink. Here’s a look at Alpha’s newest weapons for the retailers’ arsenal.

VersaLok™. Versatility and Flexibility
The challenge—Create an effective security solution that will fit on boxes or other odd-shaped merchandise not easily secured by Keepers® or Spider Wraps.
The solution—VersaLok is a reusable alarming module that when used in tandem with a clear, disposable trace provides security options that are nearly limitless. The compact size of the module helps maximize merchandise sets and minimize storage space. VersaLok’s ease of application and removal cuts labor costs. Visually, it sends a clear “alarm secured” message. VersaLok is proving extremely successful in protecting ink toner, electronics, and other packaged merchandise in major office supply stores.
S3™ Attack and XL Spider Wraps® . Both New and Improved
The challenge—Increase the ROI and best-in-class performance with ongoing improvements. Responding to one of the biggest shrink challenges faced by retailers, in 1996 Alpha created the Spider Wrap to protect six-sided boxes. The Spider Wrap pioneered a new era in security and is used by more than 500 retailers globally.
The solution—After engaging customers for candid feedback, Alpha’s newest generation, the 2 Alarm Attack Spider Wrap, allows for faster application and removal, features an even stronger locking mechanism, a smaller body for improved merchandising, and dual EAS technology. Storage is made more efficient with less exposed cables that won’t tangle. The newest addition to the Spider family, the 2 Alarm XL Spider Wrap has a longer cable length of 132 inches to protect even the largest boxed merchandise. A push-button release makes it intuitive to use and allows for quicker application and removal. Alpha’s new and improved Spider Wraps lead the way in flexible, alarming security and provide retailers with a proven return on their investment.
S3verify™. A Single Key; A Unique Store Code; Your Security Advantage
The challenge—Counterfeit, stolen, or unlawfully acquired detachers are being used to open and steal protected merchandise.
The solution—S3verify is a system utilizing new and advanced S3verify Keys and security devices that are programmed with a unique, store-specific code. Once programmed, attempts to open S3v devices with anything other than Alpha’s proprietary S3v Key will result in an alarm. S3verify is programmed to “erase” the store code if the S3v Keys are stolen or removed from the docking station. New S3v security devices include S3v-compatible versions of Alpha’s popular alarming series of CableLoks®, Spider Wraps, and Keepers. S3verify is the “key” to a unique advantage against theft.
Innovation That Never Stops
Alpha is committed to solving challenges and providing the solutions required to arm retailers for this ongoing battle. Strategic thinking combined with our investment in innovation will continue to result in new solutions that target shrink and out-of-stocks while improving merchandise availability and profits. For more information on these or any of our other solutions, please go to alphaworld.com or call 888-257-4272.
SOLUTIONS SHOWCASE AXIS COMMUNICATIONS
Meeting the Challenges of Modern Retail
Retailing today is no simple task and store owners face many challenges. The most obvious of these are theft and inventory shrinkage, which eat into your stores’ profits.
Retail surveillance using network video solutions, such as IP cameras, is an excellent tool in the efforts to protect your business. By deterring crime, it reduces loss and creates a safer environment for staff and customers.
With one of the broadest product portfolios on the market, Axis Communications offers a multitude of intelligent security solutions. From network cameras to encoders and physical access control, we think beyond surveillance and set the standard. With an open platform and collaboration with our partners, it allows us to create intelligent, proven solutions to deter loss and put money back to your bottom line.
For years the retail industry has been abuzz about the possibility of video analytics, and now it’s starting to
become a reality. Through these intelligent algorithms you can spot atypical customer behavior that when viewed by the LP department might suggest potential loss activity.
Historically, video analytics have been used for marketing and merchandising needs. But these analytics aren’t just tools for marketing and merchandising anymore. If you look at four of the most common video analytics used by retailers today—heat mapping, dwell time, people counting, and facial cataloguing—you’ll quickly see how intelligent video analytics can make the difference for loss prevention.

A Quick Glance at Video Analytics for LP
Heat Mapping allows retailers to visualize customer traffic patterns through the store over time. The analytic uses color overlays to denote hot spots of activity and cold spots with little or no foot traffic. From an LP perspective, heat mapping is especially useful in static environments where the floor layout remains the same. You can establish a good baseline of activity, which makes it easier to judge spikes and anomalies.
Dwell Time lets retailers see which areas of the store catch a customer’s eye and keeps their attention. The analytic is designed to detect a person remaining stationary in a particular location beyond a set period of time, a parameter designated by the retailer. The application uses a graphic overlay on the video to pinpoint the location where the dwell threshold has been exceeded. For LP a dwell-time alert can be a red flag that someone might be looking for an opportunity to conceal a product or scoping out the location for an organized retail theft sweep. People Counting helps retailers keep track of how many shoppers are entering the store or even a specific area of the store. The algorithm is designed traditionally to be one-directional so that it doesn’t count people leaving the premises. The information is generally presented in a graph broken down into units of time. When LP studies people-counting statistics, they’re looking to find a connection between customer density and returns. By familiarizing themselves with the baseline, they can spot inconsistencies that might indicate fraudulent rather than honest returns.
Facial Cataloguing is one of the newest analytics gaining attention and traction in retail. The algorithm is designed to gather the gender and approximate age of a shopper based on facial geometry. It can also predict general mood by analyzing facial expressions. The analytic helps LP identify repeat offenders or known retail crime members as they enter the premises by sending an alert to staff, who can then respond according to store policy and local laws.
Increasing Value for Loss Prevention
Today, LP professionals are beginning to see the value of using these analytics. As algorithms integrate into standard operating procedures, their cross-functional value is becoming even more apparent. When LP applies this intelligence to its own surveillance toolbox, the ability to anticipate and avert loss increases significantly as does the retailer’s overall return on investment.
For more information, visit axis.com/retail or retail-surveillance.com.
SOLUTIONS SHOWCASE INTELLIGENT LOSS PREVENTION
J-Plug’s Unique Audio Lock Secures Any Electronic Device with an Audio Jack

Introducing J-Plug display security from Intelligent Loss Prevention (ILP). J-Plug is changing the way demo devices are displayed through unrivaled security, style, and simplicity. The differentiating factor is J-Plug’s use of the common feature of all consumer electronics—the 3.5mm audio jack. J-Plug features a unique pin that locks into an audio socket.
This audio lock provides universal and future-proof security for any electronic device with an audio socket, such as tablets, smartphones, speakers, PCs, laptops, MP3 players, and more. In addition to the mechanical audio lock, J-Plug offers charging and alarming versions.
Clean, clutter-free design ensures that shoppers can fully interact with display products secured by J-Plug. This unique audio lock replaces the need for claw-style, adhesive, or bulky security devices that can detract visually or experientially. Slim design and 360-degree rotation ensure unhindered product interaction.
J-Plug solutions feature robust, aircraft-grade steel cables. Testing determined that retractable and coiled tethers deteriorate at a much higher rate than J-Plug’s wound steel cable. Alarming J-Plug solutions contain a “tripwire” that is woven into the cable as an additional layer of defense.
J-Plug’s sleek and durable stand, which works in conjunction with the J-Plug alarm, positions display products with magnetic precision. In addition to the audio lock solutions, J-Plug offers the smallest-profile camera security on the market and a stylish loop security solution that can be used with handbags, headphones, home goods, and more. J-Plug’s cohesive line allows users to maintain a consistent aesthetic across all product categories.
In addition to physical security, the J-Plug Pro App can be used alongside or independently of the J-Plug line security range. App features include siren from device, full system lockdown with geo fence technology, web-based dashboard, email notifications, content control, and uninstallation protection.
Intelligent Loss Prevention will be showcasing J-Plug at the NRF Loss Prevention Expo in Fort Lauderdale, Florida, from June 11–12. Demonstrations of the app will be available as well as the opportunity to view J-Plug securing mobile phones, tablets, speakers, headphones, cameras, and more.
While J-Plug is new to the U.S., it is no stranger to the European market. J-Plug is the creation of London-based Multplx whose customers include Microsoft, Jawbone, T-Mobile, Samsung, Dell, Griffin, Nokia, and HTC among others. Intelligent Loss Prevention is the exclusive U.S. distributor of Multplx’s J-Plug product line.

About Intelligent Loss Prevention (ILP)
Intelligent Loss Prevention is the consultative security division of Southern Imperial, Inc.—a leading manufacturer of retail displays and fixtures for over fifty years. ILP helps brands and retailers safely merchandise high-theft products in shopper-friendly formats that drive sales. For more information about J-Plug or our other solutions, please call us at 800-747-4384 or visit intelligentlossprevention.com.
SOLUTIONS SHOWCASE CORRECTIVE EDUCATION COMPANY
Leading the Change in Managing Petty Theft
To many, shoplifting is considered a victimless crime—not really hurting anyone. But in fact, shoplifting contributes to billions of dollars in losses for retailers each year and translates into higher prices for the average consumer. Other hidden costs can include overloading of the criminal justice system since low-level theft makes up a large percentage of these case loads. And for communities at large, neighborhood business may be forced to close due to lost profits, further inconveniencing the general public.
According to numerous surveys from a variety of different organizations, most incidents are “opportunistic shoplifting,” which describes thefts that are not pre-planned and are committed by individuals stealing for personal use, not for profit or resale. It is believed that approximately 73 percent of shoplifters don’t plan to steal in advance.
Providing a structured approach through corrective education programs can help alleviate the burden this type of crime places on retailers, law enforcement, prosecutors, and society as a whole.
Corrective Education Company (CEC) understands the challenges facing retailers, courts, prosecutors, and law enforcement agencies due to retail theft. The company works with all parties, as well as security firms, parents, and schools, to provide a successful, equitable, and more efficient alternative to judicial prosecution.
A pioneer in the industry, its approach to this societal problem has been to implement programs that balance the need for justice and restitution. Their team is comprised of seasoned professionals with years of experience in the areas of retail, education, and technology.
“By combining the latest in technology with media-rich educational programs, we deliver a holistic approach to restorative justice,” stated Darrell Huntsman, CEO and founder of Corrective Education Company. “Our education programs and proprietary incident intake and management system ensure that retailers receive the restitution and justice they deserve; while offenders recognize their mistakes and are given the support and tools they need to correct their mistakes and change the course of their lives.”
By the Numbers
A study conducted by the Loss Prevention Research Council (LPRC) found retailers’ apprehension costs without CEC solutions ranged anywhere from $42 to $240. When using CEC, that cost dropped to the $11 to $18 range due to time savings for the LP associate. With thousands of potential apprehensions per year, significant savings can be realized in a short time period.
Beyond the cost savings behind apprehensions, recidivism studies on the impact of CEC’s education programs have found that recidivism rates without an education program can be as high as 80 percent. With some education, the rates dropped to 35 percent. Recidivism rates for individuals that experience CEC’s program are consistently below 5 percent. Less administrative time shows a 34 percent gain in LP associate productivity. In an environment where retailers are constantly asked to do more with less, the gain in productivity alone can be a significant boost to the bottom line.
Finally, customer surveys show a 50 to 80 percent increase in financial restitution when deploying a CEC program.

Complete Suite of Solutions
CEC provides retailers with a complete suite of tools with its CEC Connect™ solution:
Mobile Case Management—Quickly launch a mobile app enabling clients to create, view, and edit incident reports on the go.
Increased Restitution—Users can now be more confident in the amount of restitution they receive for every case processed through CEC Connect.
Single Mobile Platform—No need to buy extra equipment because CEC Connect allows the swift launch of current service apps and programs at no cost using CEC’s device.
Predictive Analytics—Prevent theft before it happens with
CEC’s out-of-the-box predictive analytics, exception reporting, and dash boarding tools.
Geo-Tracking—The CEC Timestamp™ feature allows the end-user to run real-time location and time card stats by date, stores, region, and employee.
Time Savings—Decrease the processing time for a petty theft shoplifting case to 25 minutes.
Primary Benefits
CEC’s solutions offer a number of benefits to users: Reduces Time and Costs—The technology reduces costs for retailers to prosecute offenders and eliminates 90 percent of the time it takes to process an offender through the justice system. Increases Financial Recovery—Because offenders are held responsible for damages, improved offender data improves civil demand recovery. Completely Offender Funded—The offender pays for CEC’s program, and there is no cost to the retailer for the technology, online database, education program components, or implementation.
Components of the Program
There are three primary components of the CEC program: Mobile Devices, including iPads and Fingerprint Scanners— These technology solutions are deployed at every retail location to capture offender information. Cloud-based Analytics and Reporting Tools—Information captured on the mobile devices are stored in a secure, cloud-based database. At any time retailers can access the analytics and create reports to better understand in-store loss prevention and CEC program effectiveness. Online Education Program—CEC has developed a proprietary, proven online cognitive restructuring and life-skills course that takes offenders up to eight hours to complete. Retailers can track offender progress through the online database and reporting tools.
How the Program Works
Step 1. Once the offender is apprehended, he or she is qualified for the program. Qualification standards are established by the retailer and may include items such as age, repeat offense, value of merchandise, and other criteria. If the offender does not qualify for the program, the retailer follows its standard retail theft protocols.
Step 2. If the offender qualifies for the CEC program, an incident report is created and the offender is shown a video about the diversion program. The offender is then offered the program under free will, and, if rejected, then the retailer follows its standard retail theft protocols.
Step 3. If the offender accepts the offer, CEC contacts the offender immediately with details about the diversion program, including program structure and costs. If the offender cannot or chooses not to pay, the retailer then follows its standard retail theft protocols.
Step 4. When the offender pays for and completes the program, his or her information is stored in the online database and monitored for repeat offenses. Retailers can track offenders’ program progress through CEC’s cloud-based analytics and reporting tools.
Win-Win for Everyone
Shoplifting has been around since the beginning of retailing and will continue to exist as time goes on. Petty crime continues to present enormous challenges for retailers, the criminal justice system, law enforcement, and society. Unfortunately, the most common methods of dealing with these crimes are expensive for retailers, add additional pressures to the already overburdened criminal justice system, and can be life altering for individual offenders.
In the words of one senior vice president of loss prevention for a major retailer, “This is a program that is a win-win for everybody—the retailer, law enforcement, and the offender. I see no reason not to utilize CEC as part of any retailer’s LP program.”
Finding alternate ways to deal with offenders that is fair and equitable to all parties involved is the mission of Corrective Education Company. To learn more about the company and its solutions, visit correctiveeducation.com or call 877-318-0983.
Visit CEC at the NRF Loss Prevention Conference & Expo in booth 1023 and be sure to catch the session “Restorative Justice—The Impact on Retail Efficiency, Recidivism, and Shrink” on June 11 at 3:45 p.m. in room 315-316.
SOLUTIONS SHOWCASE TYCO RETAIL SOLUTIONS
Mobility Empowers Retailers to Deliver an Enhanced Customer Experience
By Nancy Chisholm
In today’s mobile era shoppers are moving at a rapid speed and have little patience for cumbersome shopping experiences. Retailers understand consumers’ need to quickly get in, find the products they want, and get back out the door. To keep their customers satisfied, many retailers are making it a priority to streamline their own operations, making shopping experiences quick, easy, and stress-free, while still keeping their valuable assets protected.
When it comes to a positive in-store experience, a fast and easy checkout plays a big part. If shoppers are stuck in the checkout line for a long period of time, they can become irritated and impatient. This dissatisfaction can then translate into a substantial loss in retailers’ sales—impacting their top-line growth and customer retention rate. And while some things that create an unpleasant checkout situation cannot be avoided, there are certainly many that can.

Nancy Chisholm
Vice President & General Manager Tyco Retail Solutions
Rapidly Changing Landscape
The retail landscape is constantly evolving, and so are the technologies needed to help retailers succeed. RIS News 2014 annual “Store Systems Study” cites mobile technology for associates among the top store systems priorities for retailers, causing them to completely rethink the way associates interact with customers. Research indicates the growth of mobile devices for store associates confirms how mobility has become part of retailing’s DNA.
Just as shoppers are utilizing mobile technology to be more productive and efficient in their everyday lives, retailers are doing the same in their stores. A number of research studies offer compelling insights on how equipping associates with mobile devices positively impacts productivity, profits, and customer service. In fact, according to RSR Research’s recent benchmark report “Mobile in Retail,” retailers recognize associates are unable to spend enough time assisting customers even though customers want assistance, making assisted selling the number one use of mobile devices for employees among the majority of retailers.
First-to-Market Solution
Leveraging emerging technology, we designed a solution to help associates checkout customers faster, more accurately, and more efficiently—while keeping assets secure and employees safe. First to market, Tyco Retail Solutions’ mobile handheld integrated deactivation solution enables associates to easily and accurately scan and deactivate acousto-magnetic (AM) electronic article surveillance (EAS) labels in one sweep for a quicker—and safer—checkout experience. This rapid one-step scan and label deactivation also reduces nuisance and false alarms that are responsible for causing unnecessary customer inconvenience.
This handheld’s lightweight yet durable design ensures reliable operation in spite of everyday usage and exposure to dust and liquids. Together with a compatible scanner, it becomes an all-in-one portable device retailers can use to free up valuable counter space and avoid having to install the deactivation system in or under the checkout counter. This new mobile, in-aisle checkout gives store associates the flexibility to scan and deactivate
all items in the shopping cart, including merchandise too heavy or bulky to lift onto the counter—a “must have” for reducing lifting-related injuries due to store associates taking heavy, bulky items out of the shopping cart and on to the checkout belt.
Additionally, since labels can only be deactivated after associates scan them for purchase, this device helps retailers tackle theft. By having this level of deactivation intelligence, retailers are helping prevent internal theft, scan avoidance or “sweethearting,” and merchandise switching.
Our handheld integrated device allows general merchandise, Do-It-Yourself (DIY), or other retailers that typically sell large, bulky products to improve employee productivity, reduce shrink, and enhance overall customer satisfaction. Now armed with Tyco’s breakthrough technology, our retail customers can seamlessly advance their mobile strategies, creating a satisfying and more profitable customer experience.
Tyco’s mobile deactivator enables retail associates to easily and accurately scan and deactivate in one sweep.

SOLUTIONS SHOWCASE PALMER, REIFLER & ASSOCIATES
Civil Recovery—The Original Restorative Justice Program
By Natt Reifler
State legislatures in all fifty states have already decided how to address employee theft, shoplifting, and other forms of retail theft. Alabama is a great example. Codified into its civil recovery statutes, Alabama provides clear legislative intent:
Section 6-5-270: Legislative findings.
The Legislature finds that shoplifting and employee theft have reached near epidemic proportions and that efforts to control these criminal offenses through traditional methods have proven unsuccessful and costly to both the general public and to business.
The existing criminal justice system is overcrowded and burdened thereby causing unreasonable delay. Continual use of the criminal justice system for shoplifting and employee theft offenses creates a further strain on an already overcrowded criminal docket, thereby requiring more tax revenue to pay for a continual expansion of the criminal justice system.
The continuous growth of shoplifting and employee theft cases in the face of traditional efforts to control these offenses represent added cost to retailers which, in turn, is passed on to the consumer in higher prices. Additionally, the merchandise lost to theft is not converted to profit in the form of sales for the retailer which results in millions of dollars in tax revenues lost.
Therefore, the Legislature deems that the utilization of an alternative form of deterrence to eliminate shoplifting and employee theft which avoids the stigma of a criminal record is more desirable than the present system. (Acts 1993, No. 93-676, §1.)
Clearly in matters of shoplifting and employee theft, Alabama considers civil recovery as the ideal civil method to settling claims with a desirable outcome, benefitting all parties involved. Alabama is not alone, although in most states, civil recovery is a supplemental civil remedy that can be pursued in addition to criminal prosecution as a parallel process. Civil recovery is, after all, the product of careful deliberation by fifty state legislative bodies attempting to balance the property rights of retailers and interests of consumers and society at large, with the need to punish and deter individuals from committing acts of retail theft.
Retailers experimenting with new restorative justice programs should be mindful that, in our litigious society, all too often it seems no good deed goes unpunished. In light of recent legal challenges to private-sector, for-profit alternatives to criminal prosecution, retailers are wise to pilot new programs carefully. Particular attention should be paid to the implementation details, not only verifying the support of the local prosecuting authorities while deciding along with advice from in-house counsel whether members of the shoplifting or employee theft community will truly understand the distinction between the education program offered to them as an alternative to criminal prosecution and future requests for statutory civil damages (civil recovery or civil demand).
Consideration should also be given to whether the people who fail to pay for the education program, or even those who do, will be more or less likely to sue retailers and/or their agents under state unfair/deceptive trade practices acts by arguing they didn’t understand the “pay for theft education instead of being prosecuted” agreement. Pioneering creative ways to tackle society’s theft epidemic is both noble and admirable, but may come with unacceptable risks inherent in relatively untested legal concepts.
As retailers explore new frontiers, it may be helpful to remember the long road to today’s civil recovery landscape. It didn’t happen overnight and without numerous legal challenges. The approved practice of civil recovery law by lawyers has been court tested and forged by landmark court decisions, amended by state legislatures, reviewed by Attorneys General, and proven effective for over twenty-five years. This process produced the important precedent that because the underlying claim to a civil theft demand is a tort and not a consensual consumer debt, attempts to collect civil demands are not considered attempts to collect debts and do not fall under the scope of various consumer protection legislation as well as other protections for retailers.
Today, in addition to pursuing a socially responsible policy, retailers are confident that a properly implemented civil recovery program is also a sound risk management decision.
NATT REIFLER, Esq. is a partner at Palmer, Reifler & Associates. His responsibilities include the overall supervision of the legal department and the team of dedicated collectors. Reifler also consults on compliance issues, serves as a legal liaison to clients, and advises on the firm’s day-to-day activities.
SOLUTIONS SHOWCASE PROTOS SECURITY
Isn’t It Time for the Guard Industry to Receive an Upgrade?
By Tim Shipman, LPC
Those of us in the loss prevention industry at times find ourselves in need of a security guard service for either a temporary or permanent assignment. Finding the right partner or provider can be a challenge. There have been times when some of us have thought this to be a four-letter word—something that we would just as soon not have to deal with.
Managing a security vendor can be overwhelming from the perspective of tracking their attendance, monitoring if the guard reports on time or leaves early, as well as the quality of the guard provided. Most security guard companies come in with the best intentions of providing quality guards who will report on time and follow the post orders provided by the client. At the end of the day, though, many of the companies give the lowest bid possible—hoping to create additional volume for their company so as to increase their revenue while cutting costs—but do not have the infrastructure in place to properly monitor and manage the service on a quality, time, attendance, and professional basis.
You also may have seen what I have experienced, where a guard company is billing you for hours that were not worked or covered. When confronted they say, “It was just an honest mistake.” If you have been in the industry as long as I have, you have seen many guard companies come and go because they over-commit and over-extend themselves and could not produce the professional services promised.
A Paradigm Shift in Guard Service
Last year, before deciding to leave a company I had been with for twenty-three years and start my own consulting company, I was called on by Patrick Henderson, vice president with Protos Security. He shared their approach with respect to security services. When Henderson initially told me that they were a security company but did not have security guards working for them, I was a little confused to say the least. He went on to tell me that they actually had developed comprehensive software that provides their clients with many layers of efficiencies that result in reducing the overall costs of any security guard program.
They have also developed a network of more than 2,000 security providers throughout the U.S., Canada, and Puerto Rico that have been put through a rigorous vetting process related to the quality of guards, service, and professionalism they provide. Once the vetting process is complete, Protos utilizes these companies to provide the needed services for their clients. Protos completely manages that process using the technology they’ve developed—creating one-stop, one-point of contact for service and billing.
At this point I am sure you are thinking the same thing I was thinking: “No way. This is too good to be true.” I decided to make a trip to Protos Security’s office and operations center in Roanoke, Virginia, to conduct onsite interviews. There I was met by their management team, consisting of Chris Copenhaver, president; Sally McGuffin, director of operations; and Jerry Scott, national accounts manager; in addition to Henderson.
It was obvious from the very beginning of the meeting that they were all very passionate about their business and the security industry as a whole. Copenhaver and Henderson actually started the company focusing on the technology side of the house because they both recognized the need to elevate the security guard industry while providing clients with a clear and accurate view of their overall security program.
In companies that utilize security guard services, many find this to be the largest single line item within their budgets; yet they do not have the labor or technology in place to properly manage billing, time, attendance, tracking, real-time incident reports, tardy alerts and notifications, quality assurance, and risk mitigation. Protos’s creative and fresh approach could and should take the security guard industry (reported to be a

$21 billion-a-year business) to a whole new and professional level—adding much-needed accountability for both the solution provider and the client.
Creating a Partnership, Not Just Another Vendor to Manage
It became very apparent that Protos not only wanted our business, but also had a very strong desire to become a true partner with us. After careful consideration, I made the decision to proceed, giving Protos an opportunity to provide the services they had described.
I checked back with Terry Hoal, loss prevention manager of distribution for Delhaize America, who manages the security guard services for both distribution and retail at Delhaize America. Following is what he had to say.
“Protos Security is the only guard company I have worked and partnered with where I am constantly receiving compliments on the level of service they provide. Their response time to temporary or permanent assignments is unmatched compared to other companies I’ve used. The technology they bring to the table is also outstanding as it relates to reports and time and attendance. We have experienced a 5 percent savings in our budget because of the accuracy of time worked being properly billed and reported,” said Hoal.
Obviously, using the management software Protos provides imposes accountability on the solution provider. At the same time, the client is paying only for the actual time worked instead of the scheduled time.
During the research for this article, I talked with several of Protos’s current clients, who provided the following statements.
“Protos Security is great to work with,” stated Sara Moccardine, NAS customer support manager for Protection 1. “They have always delivered what they say they will deliver. When we call for a last-minute situation where we need service, they constantly communicate with us until the request is filled. Compared to our previous provider, they are great communicators. I have and would highly recommend them to anyone in need of a very professional and caring guard company.”
Andrew Barborak, CFI, senior manager of LP at Gander Mountain, stated, “Protos gives us a single point of contact for requesting security guard coverage in all of our stores, as well as the ability to communicate with the onsite officer. We can also follow up using various reporting tools, which greatly enhances our ability to manage and be informed of our guard activity. They have truly found a way to add value to an age-old solution.” “At Advance Auto we have been doing business with Protos Security for eight years,” said Jeff Carr, asset protection solutions engineer for the auto parts retailer. “I have found Protos to be quick to respond to last-minute needs and always there to respond to our needs in the moment. The management tools they have developed provide us with real-time reporting and accurate billing, which is a cost and labor savings for our company. Protos Security is unlike any other security company I have ever done business with.”
I could find no one who had anything but positive things to say about Protos Security. Protos is quickly establishing itself as the one-stop, choice destination for contract security guard and management solutions. They are constantly looking for ways to raise the bar for their clients and are in the process of scheduling a security guard management summit of current and potential clients to solicit what additional visions, desires, and needs retailers may have related to contract security guard management tools.
I encourage you to contact Patrick Henderson at Protos Security at patrickh@protossecurity.com or 866-403-9630 ext. 105 to learn more about the solutions they provide or to participate in their upcoming summit.
Terry Hoal, Delhaize America
Andrew Barborak, CFI, Gander Mountain
TIM SHIPMAN, LPC is president of The Shipman Group, LLC, a loss prevention, emergency management/ disaster recovery, and risk management consulting firm based in Raleigh, North Carolina. He can be reached at 919-756-8033.
SOLUTIONS SHOWCASE THE RETAIL EQUATION
Big Data—Turning the Tide on Fraud and Shrink
The phrase “big data” turns up frequently in the trade press. This ill-defined term loosely describes the ocean of bits and bytes pouring into IT systems daily, as well as the complex analysis being applied to the sea of information. The data can be marshalled into neat rows and columns or can be completely unstructured.
Retailers want to use it to understand customers better or otherwise benefit corporate executives and marketing departments, but loss prevention doesn’t need to take a back seat. Recent studies by The Retail Equation (TRE) show the big impact of big data on fraud and shrink.
Volume and Speed
Retailers collect data from many sources, including store sales transactions, store video, traffic counters, alarms, merchandise movement, loyalty programs, e-commerce click paths, and much more. A large retailer collects millions of transactions and hundreds of millions of line items per day. To that they add 30 to 60 gigabytes of video per store per day. For a 1,000-store retailer, this could total 22 petabytes per year (the equivalent of 23,068,672 gigabytes).
Conventional systems like exception-based reporting and data-mining systems uncover direct relationships that occurred in the past. Big data analytical tools take analysis to a new level by, for example, detecting the connections among seemingly unrelated events to reveal underlying forces. This happens as the Verify-3® return authorization solution from The Retail Equation snaps into action to prevent fraud and abuse in real-time during the return process, not the day after. This type of response is not possible with conventional systems because they simply cannot pose the complex queries and deliver accurate answers fast enough to decline a transaction in process.
Many companies and solution providers have approached the data size or analytics problems by investing in bigger, faster hardware. This works up to a point. However, the massive amounts of data building up in the system and the complex analytical methods required to unearth the information is more resource-intensive than most companies can devote to loss prevention.
TRE achieves its big data high-processing speeds by using the Hadoop platform to split data into thousands of chunks and distribute the load. Additionally, TRE has custom software to operate in this environment to tackle very tough analytical challenges. Further, TRE utilizes several IBM PureData (formerly Neteeza) data warehouse appliances for added throughput. This architecture decreases processing time by sometimes more than 90 percent versus more traditional hardware/software deployments. A query that may take five hours to process using SAS on a conventional system takes only minutes on a Hadoop or PureData architecture. In the field, a return authorization completes in milliseconds.

Knowing Precisely What to Look For
Verify-3’s predictive algorithms and statistical models rely on big data tools to quickly improve the shopping experience and reduce return fraud and shrink simultaneously. TRE processes the data from all the transactions in the chain and identifies suspicious behavior indicative of any form of return fraud/abuse, including renting/wardrobing, returning stolen merchandise, receipt fraud, price arbitrage, price switching, double dipping, organized retail crime (ORC), check fraud, and tender fraud.
When an individual attempts to make a return, the system performs calculations, and, in less than a second, predicts the likelihood that the return is fraudulent. While the vast majority of consumers (about 99 percent) are approved, those whose actions are highly suspicious are warned or denied. This is an important point to notice—the system allows and supports generous return policies so that profitable consumers enjoy a fast and pleasant return process, including those who make many, many returns. In fact, the most valuable consumers tend to have a very high number of returns, which is why Verify-3 does not rely solely on simple return-velocity calculations, but rather uses big data to identify fraudulent patterns of behavior in real-time.
Hidden Connections Indicating Fraud
99.31% Return Rate
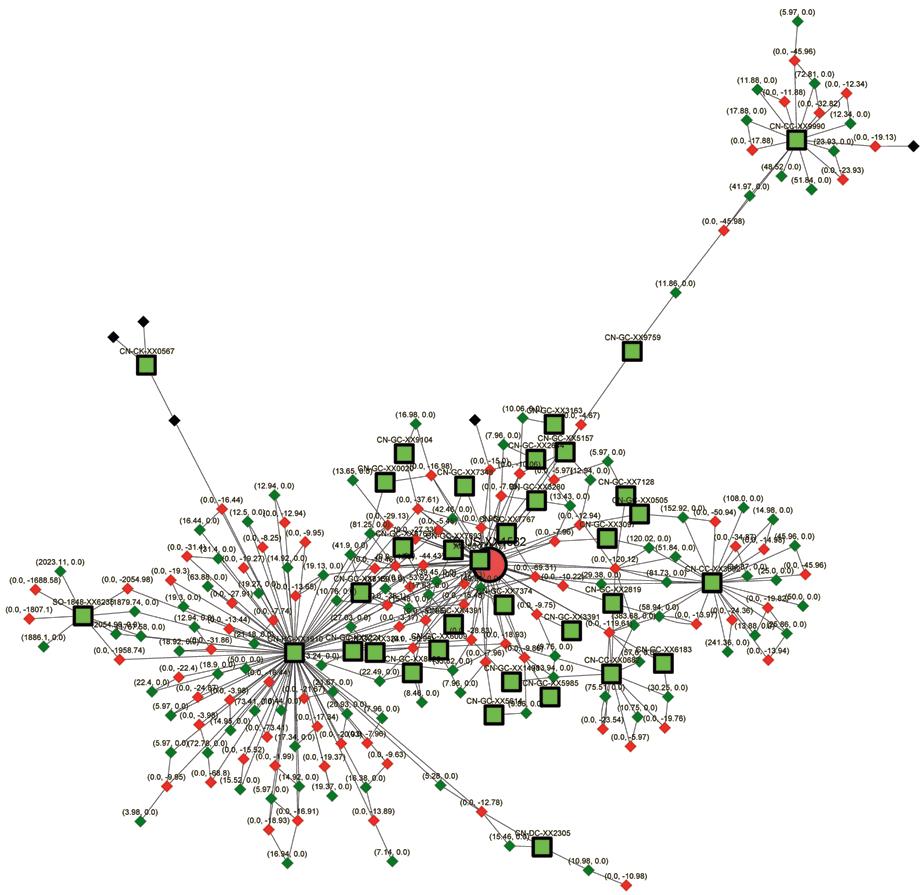
Verify-3 uses complex queries to identify ORC rings and fraudulent returners by linking seemingly independent events. The diagram above shows a cluster of suspicious purchase and return events.
At the center of each dandelion-like cluster is one person (or one ID). The thin lines connecting the clusters show a “hidden” connection, such as a gift card being passed among conspirators. On their own the clusters may appear to be legitimate (high-volume buyers often return many items), but the value of the returns is very close to the value of purchases, and the connections indicate probable fraud by a group or an individual using multiple identities. Verify-3 halts the group’s returns immediately, and special reports can provide investigators with the information necessary to pursue a case. The big data tools allow TRE to maintain and update the linked identities on more than a billion linkages each day.
The amount of return-related fraud is staggering—$9 to $16 billion problem according to the 2013 Consumer Returns in the Retail Industry report released in January 2014 by the National Retail Federation and TRE. Many of these losses are preventable using the technology available today.
Fraudsters depend on system delays and lapses in judgment by the cashiers and associates on the front lines. However, when big data analytics replace subjective decisions, fraud and shrink diminish substantially. Verify-3 reduces return rates by an average of 8.2 percent and shrink by 12.95 percent. A $2 billion retailer would see about $15 million in savings per year, and retailers will see a steep decline in return rates beginning immediately after the system is live.
About The Retail Equation
The Retail Equation, headquartered in Irvine, California, optimizes retailers’ revenue and margin by shaping behavior in every customer transaction. The company’s solutions use predictive analytics to turn each individual shopper visit into a more profitable experience. This yields immediate financial payback, increasing store comps by as much as 2 percent, with significant return on investment. The software-as-a-service applications operate in more than 27,000 stores in North America, supporting a diverse retail base of specialty apparel, footwear, hard goods, department, big box, auto parts, and more. For more information, visit theretailequation.com.





