

FALL 2022 LIBRARY OF CONGRESS ISSN 2833 0455
Highness Sheikh Mohammed
Al

11 UAE a Promising Global Investment Hub 41 Understanding Quantum 67 Standard Password Practices For Organizations 93 NATO Countries Hit With Unprecedented Cyber Attacks His
Bin Rashid
Maktoum UAE Vice President, Prime Minister And Ruler Of Dubai 6 of

131 Army SOF’s Expanding Role in Deterrence 157 Quantum Leadership Theory 177 Leading Strong in a Complex World195 Machine Learning & Development Operations The Forbidden City 111 of

“It’s the responsibility of a Technology Publication to share new ideas and challenge the status quo.

And when a Publication fails to include different experiences, beliefs, and ideas, they miss out on a true perspective of Our Global Environment.”
Linda Restrepo, Editor | Publisher
HIS HIGHNESS SHEIKH MOHAMMED BIN RASHID AL MAKTOUM
UAE VICE PRESIDENT, PRIME MINISTER AND RULER OF DUBAI


HIS HIGHNESS SHEIKH MOHAMMED BIN RASHID AL MAKTOUM UAE VICE PRESIDENT, PRIME MINISTER AND RULER OF DUBAI

BIN RASHID AL MAKTOUM
PRESIDENT, PRIME MINISTER AND RULER OF DUBAI
HIS HIGHNESS SHEIKH MOHAMMED
UAE VICE
His Highness Sheikh Mohammed Bin Rashid Al Maktoum is The Vice President And Prime Minister Of The United Arab Emirates And Ruler Of Dubai. In 2010 he launched the UAE Vision 2021 with the aim of making the UAE one of the best countries in the world. He is responsible for the growth of Dubai into a Global City. He is a true leader, and visionary. His quotes are presented below to inspire us to dream great dreams and have the courage to get up and take action. We thank his Royal Highness for his support, leadership, and wisdom.
Linda Restrepo
“The word impossible is not in the Leaders' dictionaries. No matter how big the challenges, strong faith, determination, and resolve will overcome them.”
“Dubai will never settle for anything less than first place.”

“An easy life does not make men, nor does it build nations. Challenges make men, and it is these men who build Nations.”
“Most people talk; we do things. They plan; we achieve. They hesitate; we move ahead. We are living proof that when human beings have the courage and commitment to transform a dream into reality, there is nothing that can stop them.”
“Those who neglect the new will remain at the back of the line; those who wait for luck to make things happen will be disappointed.”
“Time is limited and the dream is boundless; therefore I am always in a hurry.”
Sheikh Mohammed Bin Rashid Al Maktoum


UAE A PROMISING
GLOBAL INVESTMENT HUB

UAE BOASTS FIRST-CLASS INVESTMENT ENVIRONMENT AND INTEGRATED LOGISTICAL INFRASTRUCTURE.
Dr. Tomasz Zaleski Chairman of the Royal Office UAE
In 2020, it launched the UAE 50 Economic Plan in line with the UAE Centennial 2071 goals to boost national economy, increase the GDP, develop the local business environment, strengthen the position of UAE companies globally, and provide investors with access to markets across the world.
Key economic sectors in the UAE are witnessing a steady growth in the flow of investments, and several national companies are entering into partnerships with foreign firms. The country seeks to attract further investments into promising sectors such as advanced technology, artificial intelligence, research and development, and digital economy, which stimulate innovation and improve the performance of the economy.
UAE is One of the World’s Most Attractive Investment Hubs wherein the investment attractiveness of the UAE witnessed a steady increase over the past years. With its ability to attract substantial investments, the country enhanced its cumulative FDI inflows and became one of the most preferred investment destinations across the world. It was ranked the most attractive country for investments in West Asia, Middle East, and North Africa regions. Some of the key factors why the UAE stands out as a potential destination for investors is:
Effective Government Strategies
The UAE Government has ambitious strategic development objectives and realizes its vision through wise policies and initiatives that aim to drive the economy and foster happy societies. These development plans were accompanied by exceptional projects for more than half a century, even as it aspires for a more diversified, competitive and adaptable economy based on science and innovation.
The UAE’s future endeavors are spearheaded by inclusive strategies toward achieving a digital and knowledge-based economy.
Strategic Infrastructure and Location

The government has pumped investments and capital into major public transport and renewable energy projects that have become key pillars in the new economic milieu. The UAE has 10 major airports, 12 seaports, an unrivaled network of roads and bridges, and 6 national carriers connecting to over 200 cities worldwide. This enables 33% of the world’s population to reach the UAE within 4 hours, and 66% to access the country within 8 hours.
Ease of Doing Business
The UAE created a modern investment environment and set policies that facilitate and speed up the establishment of companies through electronic platforms, and promoted its attractiveness by issuing amendments to the Companies Law.
13


These efforts resulted in maintaining an advanced position in the ‘Ease of Doing Business’ index, ranking 16th out of 190 countries in 2019. The country also ranked 1st in terms of business efficiency, 2nd in terms of government efficiency, and 7th on the economic performance index.
The UAE is a Trustworthy Investment Hub

The UAE has also joined the top 20 countries considered trustworthy, ranking 15th in Kearney’s 2021 Foreign Direct Investment Confidence Index. The review of business environment laws such as the Commercial Companies Law has resulted in boosting investor appetite in the UAE and making it one of the destinations of choice for international investors.

Advanced Ratings by Global Agencies
In 2020, the UAE achieved a rating of “AA ” from Fitch Ratings Inc., thanks to government support and a decrease in public debt.

That same year which is looked upon as being the most challenging globally the UAE was also able to achieve a rating of “Aa2” with a stable outlook for the national economy from Moody’s Investors Service. Reflecting its robust sectors and economic stability, this is considered the highest sovereign ranking in the region.


Efficient Government Services
Government entities provide investors and entrepreneurs with smart, easy and interactive government services which can be availed at any time and from anywhere through their smartphones. The digital transformation that began more than a decade ago at the government level has been extremely successful and this is reflected in the investors’ satisfaction and the ease of establishing businesses. This digital transformation journey qualified the UAE government to rank 1st in the Arab world and 8th globally, in the Smart Services Index.

17
An Impartial Legal and Judicial System
The UAE prohibits monopolization and fosters competitiveness through an advanced system of modern and effective laws and legislations that ensure a safe investment environment, where regulations that enhance economic stability are implemented.

Moreover, it ensures fair market competition and impartiality to all parties, be it investors, inventors, authors, innovators, owners of intellectual property rights, trademarks or agencies. The UAE also maintains a fair judicial system that guarantees rights and the rule of law.

A Regional Hub for Global Companies

The UAE hosts the largest number of regional headquarters in the Middle East, and is constantly looked upon as an ideal country for engaging in commercial and investment activities. The nation’s advanced infrastructure, cutting edge communications, and

government support make it a fitting environment for international companies to manage their regional offices from the UAE. The country has long constituted an ideal window from which global corporations can oversee their business activities.

19


An Open, Multi-Cultural Society

A safe place to reside and conduct business activities and a preferred tourist destination, the UAE embodies tolerance, mutual respect, multi culturalism, and diversity. The country firmly embraces freedom of belief and
religion, hosting close to 200 nationalities and ensuring the wellbeing of all its residents by providing exceptional healthcare services, and an educational system that caters to various academic curricula.

A Global Hub for Start-Ups
The UAE has emerged as a prominent hub for start-ups. The government supports innovative entrepreneurship and offers business accelerators, financing services, and sponsorship programs to entrepreneurs from around the world. The Small and Medium Enterprise (SME) sector in the UAE is witnessing notable development and growth, and various small companies established here have evolved into remarkably successful businesses within a short span of time, many of which have also been acquired through multi billion dirham deals.
Talent and Skilled Labour Incubator
The UAE has skilled, multicultural and diverse talents and workforce. Arabic and English are the main languages at work, and the UAE looks forward to becoming the first incubator for highly skilled professionals and talented
workforces across all dynamic economic sectors. While UAE is poised to become the world’s best country in all aspects as part of the centennial 2071 plan some of the basic facts about UAE are:
Population ≈ 9.8 million people in 2021 Area 71,023.6 km²
Location
The UAE overlooks the Arabian Gulf and borders the Kingdom of Saudi Arabia to the South and West and the Sultanate of Oman to the Southeast.
Time
The UAE time is 4 hours ahead of GMT.

Currency
The Emirati Dirham is the official national currency. The US dollar is exchanged for the UAE Dirham at a rate of 3.67, and credit cards are widely accepted.
Climate
The UAE has a warm and sunny weather most of the year, recording an ideal temperature from October to May.
23
Official Language
Arabic is the official language and English is widely spoken in public, markets and restaurants.
200 Nationalities
The UAE hosts large foreign communities and all residents enjoy freedom of civil rights and practice of religion. Security and Safety
The UAE was ranked the third safest country in the world in 2020, offering residents and visitors highest levels of safety.
Some of the Promising Sectors for Investments in the Future are:
Healthcare, Agritech, Retail & E Commerce, Education, Smart Cities and Autonomous, Entertainment Streaming & Gaming, Manufacturing, ICT sector, Space, Logistics, Fintech, Tourism and Renewable Energy.
And Some Unique Opportunities for Promising Foreign Investments Sectors are:

Agritech, Transport infrastructure, Senior Housing & Care
organizations, Health care Facilities, Therapeutics & Devices, Renewable Power Generation / Water supply, E healthcare / E pharma, Cyber security, Artificial Intelligence, subscription based products / digital content, Fintech, E commerce platforms, Artificial reality / virtual reality, Blockchain, Renewable Energy, Carbon capture technology, 5G infrastructure, Smart buildings, 3D printing, Robotics, Consumer companies, IoT and sensors, Sustainable transport, Sustainability in food consumption and Edtech.
Strategies for a Future-Based Economy
UAE Centennial 2071 HH Sheikh Mohammed bin Rashid Al Maktoum, Vice President and Prime Minister of the UAE and Ruler of Dubai, launched ‘UAE Centennial 2071’ in 2017 as a roadmap to make the UAE the best country in the world, by the year 2071, when celebrating the Centennial of its establishment.
The Centennial is based on four key pillars: future focused government, excellent education, diversified knowledge based economy and a happy and cohesive society. Under the axis ‘the best economy in the world’, the UAE aims to become a global hub for attracting the best minds, ideas and talent, together with offering the best business opportunities, a stable environment and an advanced infrastructure. Steadily increasing investments in artificial intelligence, biotechnology, nanotechnology, cognitive sciences and multi-dimensional cumulative manufacturing continues to strengthen the UAE’s position as a global leader in various sectors.
The Fifty Economic Plan –Roadmap to the Future
The Ministry of Economy launched the Fifty Economic Plan for building a future focused economy in the UAE in December 2019.
As part of the ‘Towards the Next 50’ strategy, this serves as a roadmap for economic undertakings during the coming decades.
The strategy includes five key pillars: integrated economy, entrepreneurship and SMEs, tourism, foreign direct investment and exports, and attracting and retaining talent. The plan aims to achieve a quantum leap in the national economy by the year 2030 and support GDP growth by creating a flourishing local business environment and enabling UAE companies to excel and lead worldwide. The pillars of this future-focused economy include sectors such as space technologies and digital entertainment, alongside opening new markets and establishing a progressive legislative landscape that serves economic aspirations. Simultaneously, the Ministry is facilitating greater ease of doing business, supporting family businesses, and protecting and incentivizing investment.

25
The Emirates Blockchain Strategy

The Emirates Blockchain Strategy was launched in 2018, with the objective of harnessing, utilising and capitalising on advanced technologies to the benefit of society.

Further, the efficiency of government performance is being enhanced by transferring all UAE government transactions to blockchain platforms. The strategy is based on four key themes: the happiness of citizens and residents, improved government efficiency, advanced legislations that qualitatively transform federal government operations, and the UAE’s international leadership in the field of information security and transfer.
This will build the capabilities of individuals, institutions and government leaders, save time, effort and resources and qualify the UAE to emerge as one of the most globally advanced nations ready to embrace transformation.


27


The UAE’s Green Growth Strategy

The UAE’s Green Growth Strategy aims to achieve sustainability in economic, social and environmental sectors, as opposed to relying on oil resources. The UAE seeks to become a global leader in green economy, a center for the export and re export of green products and technologies, and to create a sustainable environment that endorses long-term economic growth. The strategy encompasses a set of programmes and policies spanning the fields of energy, agriculture, investment and sustainable transport, coupled with new environmental and urban policies that strive to improve the country’s quality of life. This strategy consists of 6 key streams: green energy, government policies promoting investment in a green economy, green cities, dealing with the effects of climate change, green lives, and green technologies.
UAE Strategy for the Fourth Industrial Revolution
The UAE Strategy for the Fourth Industrial Revolution aims to strengthen the country’s position as a global hub for the next industrial revolution and contribute to a competitive national economy that is based on futuristic applications that merge material, digital and biological technologies. This is in addition to harnessing technologies and tools to serve community members and achieve public happiness. The key pillars of this strategy include the adoption of various plans and of genomic medicine and medical genomic tourism, and strengthening economic security by embracing a digital economy. The strategy also involves developing advanced technologies, from artificial intelligence and nanotechnology to the internet of things and 3D printing, to support economic growth.


31
UAE Circular Economy Policy

The Circular Economy Policy provides direction towards the sustainable management of the economy, and optimal and efficient use of natural and environmental resources through the adoption of the best methods and technologies of sustainable consumption and production. This is to ensure a high-quality lifestyle for current and future generations, improve the efficient consumption of natural resources, and minimise wastage. The policy also aims to boost environmental health and encourage the private sector to adopt cleaner industrial production techniques and technologies, together with realising the UAE vision of becoming a leader in green development. The most important outcomes of the policy include generating considerable economic proceeds for the country, mitigating environmental pressures, ensuring the supply of raw
materials, increasing competitiveness, promoting innovation, strengthening economic growth and creating job opportunities.
National Program for Artificial Intelligence 2031
The UAE is one of the most prepared nations to tackle technological change, especially in light of its extensive efforts for providing a future centric and highly advanced infrastructure that is capable of improving the quality of life for individuals and communities. In line with the objectives of the UAE Centennial 2071, this strategy is considered the first of its kind on a global level, and consists of eight strategic objectives, five themes and a set of initiatives targeting the utilisation of artificial intelligence in developing the country’s vital sectors such as education and the economy. It also aims to improve government performance, achieve social
(Continued on page 36)

33

H.H. SHEIKH AHMED BIN FAISAL AL-QASSIMI
H.H. Sheikh Ahmed Bin Faisal Al Qassimi as member of the Royal family of Sharjah & Ras Al Khaimah from the United Arab Emirates, one of the most prominent Royal Families in the UAE.

After graduating from the Royal Military Sadhurst College in the United Kingdom in 2003, he being a big fan of sports and football in particular supported the Youth in sports. In 2012 he joined his brother H.H. Sheikh Mohammed Bin Faisal Al Qassimi in the real estate business acquiring hotels in the United Kingdom and the United States.
He received his first international award when he was selected as “Young Global Leader in 2008” by the World Economic Forum. In April 2010, He was awarded the prestigious young CEO of the year by Former French Prime Minister Dominique De Villepin. It is under his patronage and guidance that the Private Office is destined to lead future investments to the next level and beyond.
happiness, create a new and promising regional market that is of high economic value, support private sector initiatives, and boost productivity. Targeted sectors include transport, health, space, renewable energy, water, technology, education, environment and traffic.
UAE Energy Strategy 2050


The UAE launched its ‘Energy Strategy 2050’ in 2017, and the country’s unified energy plan balances production and consumption with global environmental commitments. The strategy fosters an attractive and conducive economic environment that catalyses the growth of all sectors and aims to increase the efficiency of individual and corporate energy consumption by 40%. It also seeks to increase the share of clean energy in the total energy mix from 25% to 50%, saving the equivalent of AED 700 billion by the year 2050.
The UAE is scheduled to invest AED 600 billion until 2050 in order to meet growing energy demands and fulfil sustainable growth of the economy. According to the strategy, the energy mix is set to be as follows: 44% from clean energy, 38% from gas, 12% from clean coal and 6% from nuclear energy.
With these strategies for the future based economy and with a time bound implementation plan UAE is determined to reach a world class investor friendly country in the near future and we look forward to more and more people to come and experience this beautiful country.
 Dr. Tomasz Zaleski Chairman of the Royal Office UAE
Dr. Tomasz Zaleski Chairman of the Royal Office UAE


His Excellency Tomasz Zaleski is a member of parliament, and Chairman of the Royal Office owned by His Royal Highness Sheikh Ahmed Bin Faisal Al Qassimi member of the Ruling Family of Sharjah (UAE)

UNDERSTANDING QUANTUM
41
“

believed my love would be reciprocated because it was pure. But it wasn’t.
I
Reaction to every action? It doesn’t work that way with a human heart. Human minds resemble the quantum world. Always uncertain. Beyond any explanation.” -AbhaidevQUANTUM QUANTUM QUANTUM 43

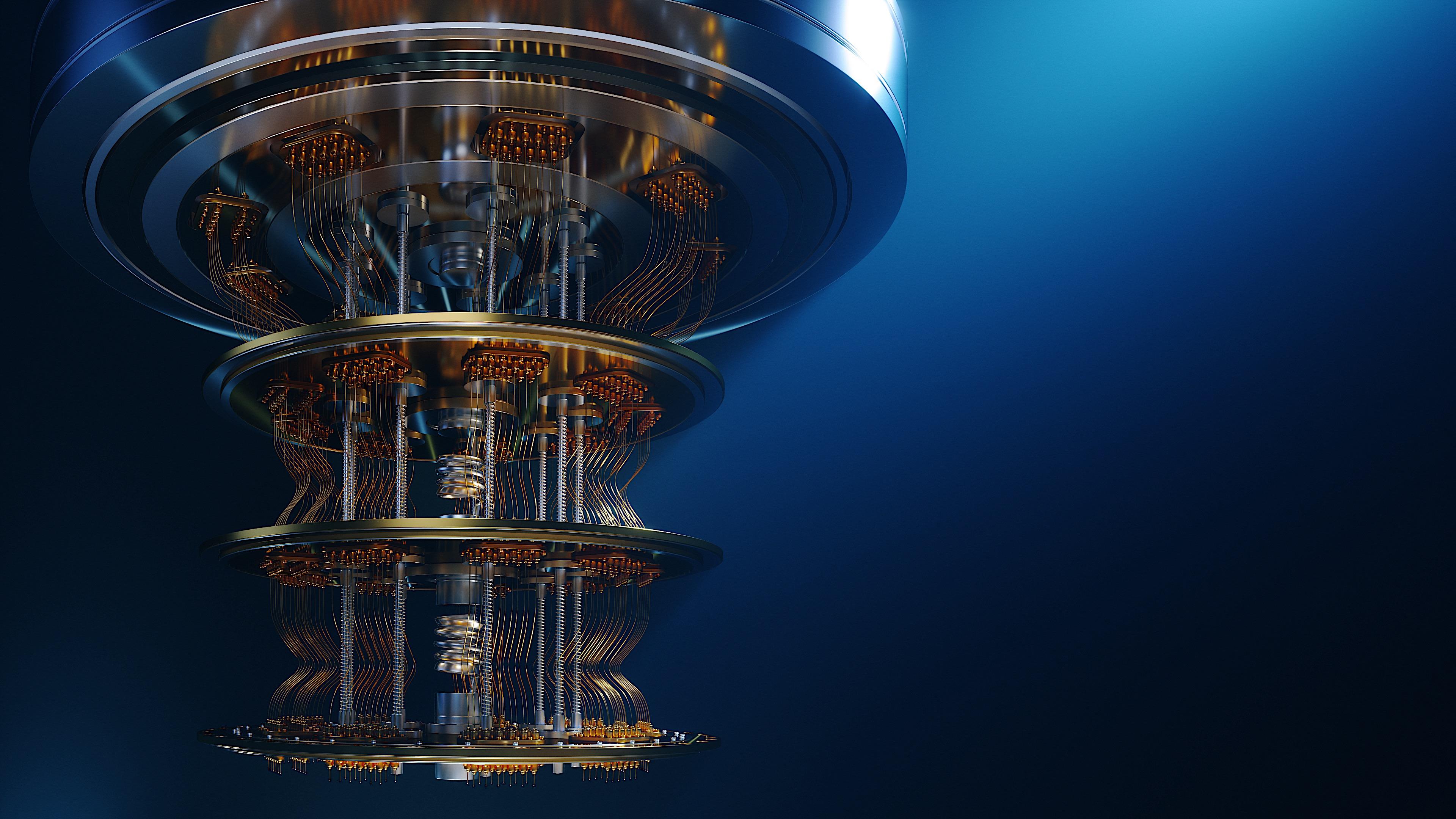
QUANTUM TECHNOLOGY
Quantum Technology
has an intimidating reputation but really it’s just kind of a mental barrier that keeps us from learning. We try to fit it into a model of the World that we understand but that’s not going to work. Understanding basic Quantum concepts is not really difficult it's just odd and we have to keep an open mind. Have no qualms Quantum is here to stay, it will impact your life, career, and future. Quantum Technology reinvents almost everything and if you don’t contribute to the input you cannot complain about the output. Those who do not understand technology will be left behind. We must go to Goliath because Goliath will not come to us. Estimates are that Quantum Computing Market will surpass $64,988.3 Million by 2030.
QUANTUM QUANTUM QUANTUM 45
Quantum computing is an area of computing focused on developing computer technology based on the principles of quantum theory.
Quantum technology is a place where everything goes awry, “universal” laws don’t apply and nothing makes sense. Quantum computing offers exponentially faster speeds than classical computing. The most exciting thing about a quantum enhanced world, however, is that no one yet knows what it will bring.

The building of quantum computers works on three underlying principles. The FIRST is quantum theory; the SECOND is that of superposition. This could mean that the quantum bit, also known as the qubit, can be a one or a zero, or pretty much anything in between. For example, if you have a coin you have heads or tails, it’s binary, it is either a head or a tail but if you spin that coin, then it can be both heads and tails at the same time. ENTANGLEMENT is the THIRD one. With entanglement, if you have two coins that are spinning, the result of one impacts and changes the result of the other.

In a nutshell entanglement, superposition, and quantum theory are the foundation of quantum computing.
Keeping an open mind bring — — in the cat. Schrodinger’s cat was perhaps the most famous cat of all time. Born in Vienna Schrodinger was awarded the Nobel Prize in Physics in 1933. His research discusses the possibility that a cat can either be dead or alive when it is in a state of SUPERPOSITION.
Spinning the coin is the point in its superposition. When you stop the coin from spinning and you look at it, that’s when you can determine which state it’s ultimately in, it is heads or tails?

Quantum Computers are a totally new way of processing data. Just like a lightbulb is not a more powerful candle, a regular computer is not like a quantum computer.
You cannot build a better lightbulb by making more candles and you cannot make a Quantum Computer the same way you make a regular Computer. Classic computers work in a binary status: true or false; yes or no, left or right. They are based on “bits’ a binary Number System which is a small amount of data that a computer can hold. A bit can hold only one of two values: 0 or 1.
Quantum Computers also have bits but they are called Quantum bits or Qubit which refers to a basic unit of quantum information. Qubits can also function in a state of one to zero like classical computers.

A ZERO OR A ONE HEADS OR TAILS HEADS TAILS ZERO ONE 49
Quantum Computers also have bits but they are called Quantum bits or Qubit which refers to a basic unit of quantum information. Qubits can also function in a state of one to zero like classical computers . But the magic in Quantum Computer Qubits is that they can represent multiple combinations of 0 and 1. It can actually represent 0 and 1 at the same time, furthermore, they can be 0 and 1 simultaneously moving around in different directions.
Head Tails
Zero One SUPERPOSITION
It can exist in a superposition, a combination of zero and one.
Due to the phenomena of superposition, “qubits” can exist in more than one space at exactly the same time. Qubits can have a value of both “1” and “0” simultaneously but when the qubit is observed, it collapses to “1” or “0”.
In Quantum Computation qubits represent the probability that their observed state will be either “1” or “0” and because there is an infinite range of probabilities between “1” and “0”, this means that a qubit can represent a far larger range of data values than a classical bit.
Qubits can also become entangled which means that the state of one qubit is tied to the state of another. No matter how far apart the two qubits may be.
Many people are turned off by risks, it is safer and more comfortable to sit back in a safe zone. But, risk is what distinguishes the doers from the dreamers.
Risk takers are more likely to be successful because they refuse to limit themselves and put their energy into the unknown.
All life is a chance!
51
So let’s do some gambling and take a risk against a classical computer!
But before we do I’ll make a disclaimer, remember the warning in Kenny Rogers's famous song: You can’t go home again. “Will you ever learn, Will you ever see, Will you just keep moving on?
Every Cowboy knows how the story goes when you’re running out of dreams. You can mend your ways, you can walk for days, But you can't go home again.”
Quantum is going to make it impossible for anyone to go home again, it is an emerging technology that will change the world.
Every industry will be affected by quantum computing. Quantum computers are able to process much larger data sets and perform much more complex computations than even the world's most powerful supercomputers relying on classical computing.

53
Let’s play a game, a coin game heads or tails, with a regular computer.
We start with a coin showing heads.
The computer plays first it chooses to flip the coin or not But you do not know what its choice is So now it's your turn you can also flip the coin or not, and since we all like to play fair, your move will not be revealed to your opponent, the computer and its move is not revealed to you.
The

coin is revealed. Computer plays Computer plays You play H T YOU WIN H Computer Wins
In an ideal world, but not so realistic world, the hypothesis is if your competitor is honest and the coin is fair, you both have a fifty percent chance of winning in this scenario. This happens because the regular computer is using Bits 0 and 1 for data and processing. Example 4 bits in a row can represent a bunch of numbers: 4 bits 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100

Etc. and you can keep on going So “one by one” the regular computer inputs the numbers to find what the correct response is. This is also the manner in which cybersecurity hackers currently function, they will definitely try to crack your password using all the bits. Going back to our original batch he will utilize all of the numbers individually until he comes across the correct number.
How do I destroy thee? Let me count the ways… On average, it takes a hacker about two seconds to crack an 11 character password that uses only numbers. Throw in some upper and lower case letters, and it will take a hacker one minute to hack into a seven character password.
55
Let’s bet against a computer again except this time it will be a Quantum Computer.
Now quantum Bits (Qubits) are also 0 and 1 BUT they can also be zero and one at the same time! Remember the phenomena of superposition.
For example a coin can either be heads or tails, Zero or one
But when you toss it in the air it can either be heads or tails at the same time, it does not make sense until the coin lands and you can see what it

The coin is revealed. is, perfectly recovering heads so that you lose every time Computer plays Computer plays You play H T x H Computer Wins



0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 0000 0001 0010 0011 0100 0101 0110 0111 Regular computer one number at a time Quantum computer all of the numbers – all of the time 57
CYBERSECURITY
While the promise of quantum computing is speeding up conventional computing it goes deeper by delivering an exponential advantage for certain classes of problems. With cybersecurity breaches on the rise, academia, companies, the government, and institutions more than ever need to be concerned about protecting digital resources from cybercriminals.

QUANTUM
QUANTUM QUANTUM
While the concept of quantum computing was presented in 1980 and has received a lot of attention during the last few decades, quantum cybersecurity is still in its infancy.
Quantum computers can easily become one of the most significant problems for internet safety in the near future. With the ability to transform cybersecurity it can also emerge as a solution. As with all emerging technologies quantum cybersecurity can be utilized for the betterment of cybersecurity threats as well as a threat.
So now let’s see how a cybersecurity hacker could function, he will definitely try to crack your password using all the bits. In a regular computer and going back to our original batch he will utilize all of the numbers individually until he comes across the correct number.
4 bits
0000 0001 0010 0011
0100 0101 0110 0111
1000 1001 1010 1011
1100
Etc. and you can keep on going
So now cybersecurity hackers will use a Quantum computer with Quantum bits. Remember a Quantum Bit is both a zero and a one (heads and tails). This means that the quantum bits are all of the numbers, all at the same time. So in order to find the password, the Quantum bits put into a Quantum Computer can analyze all of the numbers at the same time.
A grovers operator can sweep away all the wrong answers/passwords at the same time and give you the right one. So a quantum computer can evaluate every solution in the universe and give you the absolutely correct one.
59
ARTIFICIAL INTELLIGENCE
Now what about AI who has the ability to reprogram itself. But like a regular computer it has to go through trial and error to find out what is the best possible solution.
in Quantum Computing AI can track every single possible program, and circuit design to find the right one to make itself the best. This can be done in a second with a quantum computer.
UTILIZING QUANTUM TECHNOLOGY IN THE REAL WORLD
Regular coins do not exist in combinations of heads and tails. We do not experience the fluid quantum reality in our everyday lives.
First of all quantum uncertainty can be used to create private keys for encrypting messages sent from one location to another so that hackers could not secretly copy the key perfectly because of quantum uncertainty. We have always utilized encrypted messages as far back as World War II. In the early part of World War II, the enemy was breaking every military code that was being used in the Pacific. This created a huge problem for strategizing against the enemies. The Code Talkers and their native American Navajo language were utilized to convey messages by telephone and radio, a code that was never broken by the Japanese.
In order to hack quantum private keys, Hackers would technically have to break the laws of quantum physics to hack the key. Banks are already testing this kind of unbreakable encryption.
QUANTUM QUANTUM QUANTUM
61
When Albert Einstein met Charlie Chaplin in 1931, Einstein said, “What I admire most about your art is its universality. You do not say a word, and yet the world understands you.”

“It’s
Replied Chaplin, “but your fame is even greater. The world admires you, When no one understands you.”
“The
true.”
future is fundamentally uncertain Will we be or will we not be?” LindaRestrepo Editor|Publisher

Linda Restrepo is Director of Education and Innovation Human Health Education and Research Foundation. She is a recognized Women in Technology Leader Cybersecurity and Artificial Intelligence. Restrepo’s expertise also includes Exponential Technologies, Computer Algorithms, Research, and Implementation. Management of Complex Human machine Systems.
Global Economic Impacts Research. Restrepo is President of a global government and military defense multidisciplinary research and strategic development firm.
EDITOR|PUBLISHER
She has directed Corporate Technology Commercialization through the U.S. National Laboratories. Emerging Infectious Diseases, Restrepo is also the Chief Executive Officer of Professional Global Outreach. Restrepo has advanced degrees from The University of Texas and New Mexico State University.

LINDARESTREPO
SECURITY ALLIANCE
QUANTUM


Dr. Merrick S. WATCHHORN DMIST, QIS, QSA Program Chair 67

STANDARD PASSWORD PRACTICES Author: Dr. Albert H. Carlson, QSA Chair Encryption & Entropy ORCHID: 0000-0002-0087-6066 Technical Reviewer and Editor: Dr. Keeper L. Sharkey, QSA Chair Quantum Applied Chemistry ORCHID: 0000 0002 3767 6261 POC: Dr. Merrick S. Watchorn, DMIST, QIS, QSA Program Chair ORCHID: 0000 0003 2460 8689 FOR ORGANIZATIONS: Relative Theory and Recommendations
I. EXECUTIVE SUMMARY
In June 2022, several emerging cybersecurity threats were reported, which were: 1) a phishing campaign targeted U.S. organizations in military, software, supply chain, healthcare, and pharmaceutical sectors to compromise Microsoft Office 365 and Outlook accounts and 2) the FBI, National Security Agency (NSA) and CISA
announced that Chinese state-sponsored hackers targeted and breached major telecommunications companies and network service providers since at least 2020.
As part of a quantum security public service announcement, the Quantum Security Alliance (QSA) was asked to explore plausible approaches to help out with individuals that were the target of these types of attack and others.

69
The QSA was established in December 2018, and has been working rapidly to provide context to the emerging security landscape for Quantum Computing. In the last several months of activity, the QSA has worked on numerous efforts including aiding the Cloud Security Alliance (CSA), Quantum Tech Congress, and the National Defense University (NDU) in building a working knowledge-sharing model that includes the University of Maryland, University of Phoenix, and Purdue Global Online University.
“Cybersecurity methods are riddled with new technologies such as Artificial Intelligence, Machine Learning, Natural Language Processing and Operational Technologies (OT, IoT, SCADA, CPS, etc.), cloud computing, blockchain and Quantum Information Systems (QIS)” [1]. Recently, the QSA identified the need to enhance the knowledge share around password standards. All organizations need consistent security standards in order to have practical

procedures and to set logical user expectations. An important security philosophy is one that follows the axiom, “Keep the bad guys out [of your equipment, facility, and company]” [2]. Passwords are one of the most effective ways to electronically secure software, networks, and computers.
Like all security measures, the measure must not be weak, otherwise it provides an attack
vulnerabilities is often the purview of the organization. The Quantum Security Alliance (QSA) is dedicated to promoting effective security measures. In that vein, the following measures for passwords are presented as the minimum level standards for password protections by briefly describing entropy, Shannon redundancy, unicity distance, and random number generator (RNG) unicity distance. Subsequently, we list actionable items and recommendations. vector that is easy for an attacker to exploit. Managing risks and

II. BACKGROUND
A. Entropy, Shannon Redundancy, Unicity Distance, and RNG Unicity Distance
Entropy is a general scientific concept originally specified for use in physics and chemistry, and is a measurable physical property commonly associated with a state of disorder, randomness, or uncertainty. Although applied to different items in those fields, the math is similar. In information theory entropy is measured in bits, making base 2 natural for the measurement. In other fields the base may be different, resulting in a different look for the equation. However, the base in the equation may be converted to any other base using the base conversion equation: log c (a)
where a is the base of the desired log, b is the number of the target log, and c is the original log. At this point the standard representation for quantum information is still being decided upon. When accepted, the equation will be adjusted to reflect that base.
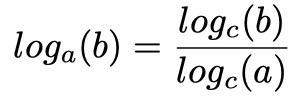
Entropy related to information is the amount of “surprise” and was first defined by Hartley [3] in the early 1920’s where Shannon adapted it to his new study of Information Theory [4] when working on cryptography [5]. Using the principles of Abstract Algebra [6] and Topology [7], which says that if two problems share the same mathematics, then what works for one problem will work for the other; the two problems that we focus on herein are cryptography and password (p) control. In both cases, it is important to maximize entropy in the
data to resist an attacker reconstructing the information. Therefore entropy becomes important for password usage and security protocols. At the core of the theory, entropy is a probabilistic function that is defined as:
which leads to the unicity distance (n), or amount of information required to unambiguously recover the original data. Shannon calculated this to be
where k is the number of symbols and pr(xi ) is the probability of the selected symbol xi appearing at that location in the block; i.e. the location in a password.
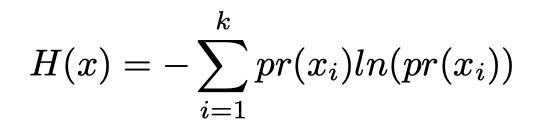

Maximizing the entropy associated with a password, is required for creating strong security and is denoted as Hmax(x). For a unique language (L), the Shannon redundancy (RL) relates the entropy of repeated symbols used in a language to how many possible symbols in the language, and is given as:
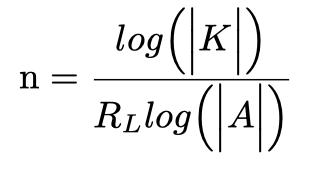

where K is the key space, (|K|) is the size of the key space, and |A| is the size of the alphabet for a particular language L. The goal of determining the unicity distance is to be able to assess how much data is needed to amass enough information to be able to know the underlying plain text data for an encryption. Nevertheless, passwords are not typically encrypted data. However, RNGs have a measure that is similar to in purpose to the unicity distance. This number is known as ρ and tells how much information is required to pattern the RNG.

73
This data can then be used to assess the loss of entropy over its use and help set the time that a selection routine or password is safe. The time is known as the time to live (TTL) for the function.
B. Sharding
Breaking a message into smaller submessages involves a process known as “sharding.” It was so named because of the comparison to throwing a rock through a pane of glass on which a message is written. The result is irregular size and shaped fragments with part of the message on each piece of broken glass. Shards are used to control the information available in the shard and keep it below the unicity distance for the data. The size of a shard is determined by the TTL associated with the information accumulation and content of the shard. log c (a)
C. Polymorphic Encryption

Recent advance in cryptography has resulted in a concept known as “polymorphic” encryption. This type of encryption is best characterized by its most extreme example; the “One Time Pad” (OTP) [8,9]. In the OTP example, each character is encrypted by a randomly selected cipher/key pair. Carlson [10] showed that selecting a new cipher/key can be done for a shard rather than a character while retaining the same security. Further, using the concepts of abstract algebra [6], it can be shown that the mathematics of passwords are equivalent to those of encryption. Random numbers are necessary to keep the selection process safe from attack [11,12], requiring a regular injection of entropy in order to maximize the ρ and unicity distance of the password.

Sharding with the effective use of TTLs provide the frequent, and irregular injection of entropy into the password and password selection process.
III. BRUTE FORCE ATTACK ON PASSWORDS
Assume the time needed to verify whether or not a password works is given by tv. Also, assume that the possible number of characters that can be used in an

alphabet is |A|. Characters in the alphabet can be composed of [A z], [0 - 9], spaces, and special characters found on the keyboard. This means that there are from 90 - 102 symbols that can be used in the password. Extending this to multi-character passwords, the a password of B characters where B is the number of bits to encode the characters in the language, the number of possible passwords (|K |) are given by:
[13]. Unlike the combinations that are found in language [10], all possibilities are possible. For each of these password sizes from the lower bound of the key size (lb) to the upper bound (ub) the number of combinations is given by:
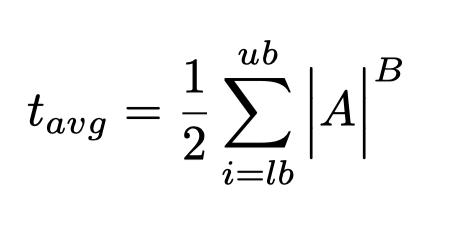
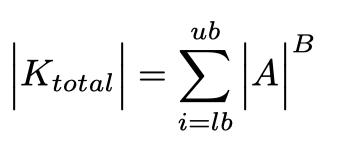
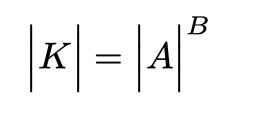
Using Brute Force Attack [14] to break the password requires attempting to decrypt half of the possible passwords [15]. Now, adding the time it takes to evaluate a password, the time to evaluate the information indicates that, on the average, a password will be discovered in about:

75
While this is average, there is a 50% chance that the time will be shorter. So, pick some time fraction that the security analyst wants to remain below (p), and calculate the time that this fraction represents. Then the time to break (tb ) becomes:
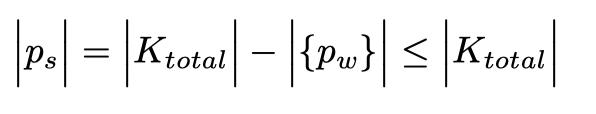
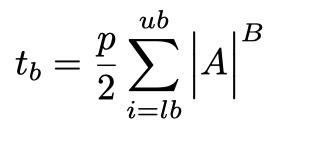
The value of tb gives the maximum number of possible passwords, and should represent the highest available security for passwords. However, some passwords are known to be weak - that is, they are easily guessed or cracked by password crackers, such as John the Ripper [16]. Some cracking tools also include “rainbow tables” which consist of commonly used passwords that can be rapidly searched.
log c (a)

While it is desirable to maximize the search space the drawback of possibly using weak keys, which are normally checked first by attackers. Unfortunately, there is no way to know how many keys are weak and should be removed from the key corpus. To date there is no conclusive list of weak keys for even small password sizes. Still, the addition of more possible passwords can increase the key corpus even when weak keys are removed. If this set of weak (w) passwords is represented by {pw} then the total number of strong (s) passwords (|ps|) is given by:
Many of these weak passwords consist of patterns, especially those which comprise words, phrases, sequences, or patterns.
As the password size increases, the numbers of patterns and sequences falls off quickly. Carlson, et al, show that by the time the password is 6 characters (48 bits) the number of meaningful sequences is less than .003% of the total combinations [10,17]. This indicates that removing sequences and words from the password corpus does not majorly affect the corpus size and avoids rapid password cracking.
The same argument also applies to having a large password. In general, the larger the password the better the security because of the multiplicative explosion that occurs as the password size increases. Even with the sequences and patterns removed the number of possible passwords will monotonically increase.
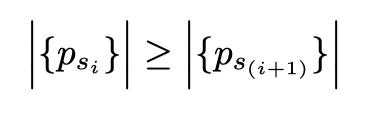
Randomly selected passwords are hard for humans to create and remember. Therefore, the selection and administration of passwords should be automated to both speed password selection and to enforce the rules for password selection. Rules should be library based and enforced. A history of at least the last 10 passwords needs to be kept in order to allow the system to compare the next selected password to those recently used. There are many ways to compare the new password with those previously used. If a new password happens to be too similar to older passwords an attacker can gain an advantage in breaking the new password. The algorithm for comparing passwords a and b consists of a “distance metric” (d⟨a,b⟩) for deciding that similarity. Since there are many different types of similarity, it is likely that multiple distance metrics should be applied.

77
The relationship between the two passwords is the minimum of the applied distance metrics. Approval of the new password assumes that the minimum is at least five (5) degrees of separation between the passwords. It would be best to have a library of distance metrics available for calculations.
Along with the size and closeness metrics, the time to live for the password is important. Verification of the TTL should be done in parallel with the use of the password. Normally, this is done by using password cracking software in an attempt to ensure that an attacker is not using the same software to break into the protected system. By running that testing the protected organization assures itself the fastest notification and warning that a particular password may be compromised.

If potentially broken via this testing, the password should be immediately replaced with a new password, following the established procedure for regular password updates.
The quality of the password does depend on all of the rules for passwords being followed by the user. Deviations from consistent use of the rules often comes from laziness, desire to simplify the process, or lack of knowledge. However, some of the rules are constraints on combinations of letters. For example, enforcing the rules about including upper case letters, numbers, and special characters while eliminating character sequences eliminate those passwords from the corpus.
These constraints on the passwords have a small effect on the corpus size and the gains outweigh the loss of weak passwords.

79
IV. Recommendations
As a standard for the Quantum Security Alliance, the following recommendations for password use should be followed:




• Allow variations in password size Passwords should have a range of lengths (sizes) from a minimum to a maximum size. Typically, this condition is given as “the password must consist of at least c number of characters.”
• Use a large password size with a minimum of 32 characters and using as standard keyboard set of characters (102) A password size of 32 characters gives a password space of 102 32 ≈ 1.88 × 10 64 possible passwords. At this size it would require a computer to attempt a minimum of 1657 password checks and the number of verification per second to break in that time period. This is highly unlikely, given the need to communicate to the server and process that data before a reply is given. If a larger password is used, that password space will rise accordingly.
• Change passwords at a maximum of every 30 days - A longer period for change quickly erodes security by allowing the attacker more time to work on the password and potentially break it.
• Vary the time between password changes (avoid a schedule with constant time schedule for changing passwords) Do not change the password on a regular schedule. If possible, change the password on a randomly selected schedule with a minimum number of 5 days that a password remains constant. The minimum time for using the same password is dictated by convenience for the organization.
• Require the presence of at least one character from every set of characters for humans, remove this for computers that can be forced to do real RNG selection This forces an 83

• attacker to try more obscure passwords and makes them harder to guess.
• A dictionary should be used to disallow passwords composed of words, dates, and phrases along with sequential numbers - Patterns are commonly used in human selected passwords. Such patterns are found in rainbow tables and are normally tried early in the cracking process. That makes passwords with patterns much more likely to be broken and should be avoided.
• Passwords should be generated by the machine, independent of human influence Human biases are avoided if the machine is used to select the new password.
• A password history should be employed so that a password cannot be repeated for at least ten (10) passwords in a row -
• Password history requirements prevent the same password, or closely related passwords, are avoided. When passwords that are previously used the attacker can make use of this fact to begin when the attack left off for the last use of that password.
• A password checker that evaluates the distance between the selected password and those in the history file. The distance metric [18] used is critical and should be of at least the quality of Euclidean distance [15] Passwords that are close variations of other recently used passwords allow the attacker to continue prior attacks and greatly cut down on the time required for cracking the password. By measuring the relatedness of passwords, those that would allow an attacker that had cracked a part of password to

• leverage that prior work to decrease the time to break the password.
• Employ the best in class RNGs, specifically polyRNGs Password composition is highly dependent on the underlying RNG. The higher the quality of the RNG, the more diverse passwords will become. Newer RNGs are using polymorphic compositions are becoming available. These higher quality polyRNGs are the most like IRVs and are the most difficult to pattern and predict. They have the largest cycle and produce the most diverse output sequence and, consequently, passwords.
• Transmission for the sharing of new passwords should be done using sharding and polymorphic encryption when passwords are shared
• over electronic media, the password should use the polymorphic principles of sharding and encryption so that the password will be kept secret for much longer than its period of use.

• A password cracker should be used on the selected password in use that includes rainbow tables. If the password is cracked, it must be immediately replaced - This is the parallel check that can determine if the password is weak and can be easily cracked. Immediately replacing the weak password is an important practice to protect the system and purge the weak password as quickly as is possible.
Maintaining these practices will limit successful attacks on a system or critical equipment.
85
V. CONCLUSION
We present a standard approach for password practice, which is one small aspect in security. The background mathematics and theory are presented in order to develop confidence in organizational procedures related to password security at all levels of the stack. These practices are equally applicable to classical computing and in the post quantum environment (PQE).
The mathematics of passwords do not change because of the platform of which they exist. This maxim is further explored in a recently published white paper [19] which relates the theory of quantum chemistry virtualization to security protocol for additional threat detection, demonstrating this cross platform applicability.

Governing Board
All rights reserved. All content in this document is protected by Quantum Security Alliance (QSA) copyrights and other protective laws.

Quantum Security Alliance was formed to bring academia, industry, researchers, and U.S. government entities together to identify, define, collaborate, baseline, standardize and protect sovereign countries, society, and individuals from the far reaching impacts of Quantum Computing.
Dr. Merrick S. Watchorn Mr. John Marshall Mr. J. Aaron Bishop
61 87

Dr. Merrick S. Watchorn, DMIST current research is focused on quantum information science, cloud computing, cybersecurity, and open-source intelligence technologies.

He is a pragmatic subject matter expert, blending his academic success with nearly three decades of government and commercial experience. He also provides a myriad of services within the Cybersecurity industry based on his sixteen years of active service in the United States Navy (USN) and the last several within the United States Government (USG). His work background included formal training in semantic ontologies, Big Data analytics, machine learning and artificial intelligence methods, theories, and cognition. As a cofounding member of the Quantum Security Alliance (QSA), he serves as Chair for the Security Reference Architecture (Q SRA). He has expansive computer and systems experience; including business systems development, complex networking, database management, and advance programming
requirements in classified and unclassified programs. He has proven experienced team leader, supervisor, and resource manager; with extensive inter-agency experience, while acting as a senior military liaison for all branches of the Department of Defense; including Senior North Atlantic Treaty Organization personnel. He is a former U.S. Military Service member with several years of work in and around the Department of Defense (DoD), Department of Commerce (DoC), Intelligence Community (IC), and Pentagon Force Protection (PFP). He has broad experience as a government certified Automation Data Protection Officer (ADPO), Information Security Systems Officer (ISSO), and Information Security Systems Manager (ISSM), and acted as a directorate level Security Officer for the DoD.
DETERRENCE DETERRENCE DETERRENCE REFERENCES [1] M. Watchorn, J. Bishop, H. Mumm, and C. Brooks. Cybersecurity legal elasticity antecedent resilience (clear) system. LinkedIn, https://www.linkedin.com/posts/quantum security alliance_ qsas view on a clear system activity 6867932751069356032 KgKj?utm_source=linkedin_share&utm_medium= member_desktop_web, 2021. [2] Albert H. Carlson. Defense in depth: Perspectives on utility security from a military intelligence viewpoint. In The 6th Western Power and Delivery Conference, 2009. [3] Paul Garrett. The Mathematics of Coding Theory. Pearson/Prentice Hall, Upper Saddle River, 2004. [4] Thomas Cover and Joy Thomas. Elements of Information Theory. John Wiley & Sons, Inc, New York, 2nd edition, 2005. [5] Claude Shannon. Communication theory of secrecy systems. Bell System Technical Journal, 28:656 – 715, 1949. [6] John B. Fraleigh. A First Course in Abstract Algebra. Addison Wesley, 7 th edition, 2003. [7] John Kelley. General Topology. D. Van Nostrand Company, Princeton, 1955. [8] Uli Maurer. A universal test for random bit generators. Journal of Cryptography, 5(2):89 105, 1992. [9] Albert Carlson, Bob Le Blanc, and Carlos Gonsalez. One time pad matrix, 2016. [10] Albert Carlson. Set Theoretic Estimation Applied to the Information Content of Ciphers and Decryption. PhD thesis, University of Idaho, 2012. [11] John Kelsey, Bruce Schneier, David Wagner, and Chris Hall. Cryptanalytic attacks on pseudorandom number generators.
DETERRENCE
DETERRENCE
[11] John Kelsey, Bruce Schneier, David Wagner, and Chris Hall. Cryptanalytic attacks on pseudorandom number generators. In Fast Software Encryption, Fifth International Workshop Proceedings (March 1998), pages 168 188. Springer Verlag. [12] John Earl Haynes and Harvey Klehr. Venona: Decoding Soviet Espionage in the United States (Yale Nota Bene). Yale University Press, 1999. [13] Matthew Bishop. Computer Security: Art and Science. Addison Wesley Professional, Boston, 2003. [14] Bruce Schneier. Applied Cryptography: Protocols, Algorithms, and Source Code in C. John Wiley and Sons Inc., New York, 2nd edition, 1996. [15] R. Lyman Ott and Michael T. Longnecker. An Introduction to Statistical Methods and Data Analysis 7 th edition. Cengage Learning, 2016. [16] John the ripper password cracker, 10 July 2008. [17] Albert H. Carlson, Garret Gang, Torsten Gange, Bhaskar Ghosh, and Indira K. Dutta. Evaluating true cryptographic key space size, the sixteenth international conference on systems and networks communications, icsnc 2021. 2021. [18] Patrick Combettes. The foundations of set theoretic estimation. Proceedings of the IEEE, 81(2):182 208, 1993. [19] A. Carlson, H. Mumms, K. L. Sharkey, and M. Watchorn. Quantum chemistry for detecting cybersecurity threats to information system. LinkedIn, https://www.linkedin.com/posts/quantum security alliance_ q chem for detecting cybersecurity threats activity 6951226103449489408 jPMu?utm_source=linkedin_share& utm_medium=member_desktop_web, 2022. 91



NATO COUNTRIES HIT WITH UNPRECEDENTED CYBER ATTACKS
Montenegro, Estonia and new NATO applicant Finland are just three of the countries being hit hard by sophisticated cyber attacks. What’s happening and who’s next?
Dan Lohrmann Award winning CISO | Bestselling Author
A headline this past week from Balkan Insight read: “Montenegro Sent Back to Analog by Unprecedented Cyber Attacks”, Here’s an excerpt:
“The digital infrastructure of a major part of Montenegro’s public administration has been offline since August 22 following a ransomware attack that security sources
have told BIRN may have been an ‘inside job,’ uploaded directly from a computer connected to a government server.
“The government of the tiny Adriatic republic, a member of NATO, has reported an unprecedented series of cyberattacks on government servers and says it is working to contain the damage.

CYBER ATTACKS CYBER ATTACKS CYBER ATTACKS
“Sources say the servers were hit with ransomware, a type of malware attack in which the attacker locks and encrypts the target’s data and important files and then demands a payment to unlock and decrypt the data.”

The Associated Press, meanwhile, covered the U.S. response to help our NATO partners:
“A rapid deployment team of FBI cyber experts is heading to Montenegro to investigate a massive, coordinated attack on the tiny Balkan nation’s government and its services, the country’s Ministry of Internal Affairs announced. . “The announcement came as the government’s main websites — including the ministries of
defense, finance and interior remained unreachable. Officials said they were offline ‘for security reasons.’
“The ministry called the FBI assistance ‘another confirmation of the excellent cooperation between the United States of America and Montenegro and a proof that we can count on their support in any situation.’”
One more on this story. Security Affairs offered this: “‘Coordinated Russian services are behind the cyber attack,’ the ANB said in a statement. ‘This kind of attack was carried out for the first time in Montenegro and it has been prepared for a long period of time.’
CYBER ATTACKS CYBER ATTACKS CYBER ATTACKS
95
NATO comprises 30 nations. Their primary role is to protect its member states by political and military means. The alliance allows European and North American members to discuss security concerns.

Article 5 of the North Atlantic Treaty provides that if a NATO Ally is the victim of an armed attack, each and every other member of the Alliance will consider this act of violence as an armed attack against all members and will take the actions it deems necessary to assist the Ally attacked.

NATO HACKED
“‘I can say with certainty that this attack that Montenegro is experiencing these days comes directly from Russia,’ said Dusan Polovic, a government official. “However, a cybercriminal extortion gang has claimed responsibility for at least part of the attack, the systems at a parliamentary office were infected with a variant of Cuba ransomware.”
OFFICIAL U.S. EMBASSY
STATEMENT
The U.S. Embassy website for Montenegro posted this update on Sept. 1, 2022:
Event: A persistent and ongoing cyber-attack is in process in Montenegro. The attack may include disruptions to the public utility, transportation (including border crossings and airport), and telecommunication sectors.

Actions to Take:
Be aware of your surroundings.
Limit movement and travel to the necessities.
Review your personal security plans.
Have travel documents up to date and easily accessible.
Monitor local media for updates.
§
§
§
§
§
CYBER ATTACKSCYBER ATTACKSCYBER ATTACKS
Coverage by The Hill elaborated on other recent cyber attacks that countries around the world are facing:
“Earlier this month, both Finland and Estonia were victims of a cyberattack, though Estonian officials said they successfully thwarted the attack that targeted the country’s public and private institutions.
“The attack followed the removal of a Soviet war monument from an eastern Estonian city bordering Russia.
“Killnet, a Russian-backed hacking group, claimed responsibility for the attempted attack against Estonia, Reuters reported.”

Event: A persistent and ongoing cyber attack is in process in Montenegro. The attack may include disruptions to the public utility, transportation (including border crossings and airport), and telecommunication sectors.
Back in July of this year, these cyber threats were anticipated: “Cyberattacks are increasingly endangering regions such as the Western Balkans, Europe and broader global areas following the Russian attack on Ukraine, according to a former American general who heads a cybersecurity company contracted by the Albanian government.
§ Actions to Take: Be aware of your surroundings.
§ Limit movement and travel to the necessities
§ Review your personal security plans.
§ Have travel documents up to date and easily accessible.
“James Jones was invited to parliament on Monday, days after a sophisticated cyber attack crippled online government infrastructure bringing all digital services and government websites offline.
§ Monitor local media for updates.
CYBER ATTACKS CYBER ATTACKSCYBER ATTACKS 99
NATO budget
For 2022, NATO’s military budget is set at $1.77bn (1.56 billion euros). Member countries contribute to the budget based upon a cost sharing formula derived from the gross national income of each country.

NATO’s military expenditure
In 2020, the U.S. spent $778bn on its military –the largest military spender in the world –according to the Stockholm International Peace Research Institute (SIPRI), accounting for 3.7 percent of its gross domestic product (GDP). Among NATO members, the UK is the second highest military spender with $59.2bn spent on its military in 2020, accounting for 2.2 percent of its GDP.

“NATO member countries must increase efforts in the face of cyber threats as well as cooperation between intelligence agencies, which is nowhere more urgent than in this region,’ he said.”

And back in April, Balkan Insight reported that cyber attacks hit Romanian websites and the Czech Republic.
The Wall Street Journal reported earlier this year that Finland and Sweden were also being hit by cyber attacks: “Authorities in Sweden and Finland have raised alert levels for cyberattacks, concerned they face increased hacking risks because of the war in Ukraine and the two Nordic countries’ subsequent applications to join NATO.
“Since Russia invaded Ukraine in February, cybersecurity officials in Sweden and Finland haven’t seen an increase in attacks targeting critical infrastructure, though they say the countries are becoming more interesting targets for hacking groups with Russian ties.
“The two Nordic countries applied to join the North Atlantic Treaty Organization on Wednesday, after decades of neutrality.”
BACK TO THE U.S.
In February of this year, 60 Minutes offered the following look at the vulnerability of the U.S. power grid to a cyber attack: https://youtu.be/GlGI643vUIg
CYBER ATTACKS CYBER ATTACKS CYBER ATTACKS
Earlier this year, Transportation Security Administration (TSA) directives took effect which required cyber preparations for rail owners and operators following its imposition of similar requirements on airports and airlines. The key points of those directives included:
§ “(Last) December, the Transportation Security Administration (TSA) issued a pair of Directives establishing cybersecurity measures for high risk freight rail, passenger rail, and rail transit owners and operators. These directives went into effect December 31, 2021. Specifically, owners and operators must: (1) name a cybersecurity coordinator;
(2) report any cyber incidents within 24 hours to the Cybersecurity and Infrastructure Security Agency (CISA);
(3) develop an incident response plan; and (4) complete a cybersecurity vulnerability assessment.
§ “At the same time, TSA issued an Information Circular recommending that lower risk rail owners and operators and over-the-road bus owners and operators implement the above requirements voluntarily.
§ “TSA had previously directed airports and airline operators to: (1) name a cybersecurity coordinator; and (2) report cyber incidents within 24 hours to CISA.

CYBER ATTACKS CYBER ATTACKS CYBER ATTACKS
103

CYBER ATTACKSCYBER ATTACKS CYBER ATTACKS § “The resulting deadlines for applicable rail owners and operators are the following: ü January 7, 2022 Designate a cybersecurity coordinator ü March 31, 2022 Conduct cybersecurity vulnerability assessment ü June 29, 2022 – Implement a cyber incident response plan” I have been covering the cybersecurity focus on protecting our critical infrastructure throughout this year, and here are two of those blogs looking at our situation in the U.S.: ü “Cyber Attacks Against Critical Infrastructure Quietly Increase” ü “Will Voluntary CISA Cyber Goals Be Enough to Protect Critical Infrastructure?” "This article is used by permission and was originally published at: https://www.govtech.com/blogs/lohrmann on cybersecurity/nato countries hit with unprecedented cyber attacks"
ATTACKS
FINAL THOUGHTS
You may be wondering: Why the focus on cyber attacks against global countries?

The answer is that these attacks continue to ratchet up. There are also various cyber attacks occurring in Africa, and Costa Rica underwent a series of major cyber attacks that were crippling.

Australia has been actively engaged in many global cyber battles over the past few years as well. I found this report entitled, “‘May the best spy win’: Australia’s intelligence chiefs open up on cyber threats and feminism,” to offer a rare glimpse into nation state battles within three letter agencies.

 ATTACKS
ATTACKS
ATTACKS
ATTACKS
CYBER ATTACKSCYBER ATTACKS CYBER ATTACKS
CYBER
CYBER
CYBER
105
These are stories that rarely get reported in the mainstream press here in the U.S.
While fear-mongering is certainly not a good thing, it is also not good to cover up (or not report) what is actually happening globally. It is important for public and private sector leaders to be aware of what is happening globally.

I continue to think that more cyber attacks will impact U.S. critical infrastructure in the future. We need to stay informed of what is happening and take the appropriate steps with a sense of urgency.
For actionable specifics, you can start by visiting: https://www.cisa.gov/shieldsup.
CYBER ATTACKS
CYBER ATTACKS
CYBER ATTACKS

Lohrmann led Michigan government’s cybersecurity and technology infrastructure teams from May 2002 August 2014, including enterprise wide Chief Security Officer (CSO), Chief Technology Officer (CTO) and Chief Information Security Officer (CISO) roles in Michigan. He works with cybersecurity technology companies to provide insights and long term strategic support. Dan is a Senior Fellow with the Center for Digital Government and a contributor to Government
Technology magazine. He has advised senior leaders at the White House, National Governors Association (NGA), National Association of State CIOs (NASCIO),


U.S. Department of Homeland Security (DHS), federal, state and local government agencies, Fortune 500 companies, small businesses and non profit institutions. He began his career with the National Security Agency. He worked for three years in England as a senior network engineer for Lockheed Martin (formerly Loral Aerospace) and for four years as a technical director for ManTech International in a U.S./UK military facility.
Lohrmann holds a Master's Degree in Computer Science (CS) from Johns Hopkins University in Baltimore, Maryland, and a Bachelor's Degree in CS from Valparaiso University in Indiana.
Daniel J. Lohrmann is an internationally recognized cybersecurity leader, technologist, keynote speaker and author.

THE FORBIDDEN CITY A Perspective


CHINA'S SECURE CONTRIBUTION TO PEACE IN UKRAINE

In recent hours, Chinese Foreign Minister Wang Yi has comprehensively outlined China's position and proposal on the resolution of the current crisis in Ukraine, which can be summarised as four six-point commitments.
Giancarlo Elia Valori
President International World Group
Dialogue and peace are to be promoted through four steps that must adhere to the purposes and principles of the United Nations’ Charter; respect and protect Ukraine's sovereignty and territorial integrity; adhere to the principle of indivisibility and security; and accommodate the parties' concerns about their own national security.
The People's Republic of China - a recent friendly neighbor of Russia - insists on dialogue and negotiations to resolve disputes by all peaceful means. For China, it is important to focus on the long-term stability of the region and to build a balanced, effective and sustainable European security mechanism.

113
Diplomacy
The Ukrainian issue lies in complex and special historical situations.
Only by addressing them firmly and considering the legitimate security concerns of the parties concerned in a
thoughtful, rational and proper manner can the sacred rights of each country's sovereignty and territorial inviolability be effectively safeguarded and progress be made in bilateral dialogue and

Diplomacy
negotiations, so as to resolve the current crisis on the basis of achieving long-term stability for the region, with the construction of a balanced, effective and sustainable European security mechanism.
Considering the unique complexity of the Ukrainian issue, the People's Republic of China is encouraging direct negotiations between Russia and Ukraine and a fair exchange of views between the United States, NATO, the European Union and Russia,

115
urging the international community to provide the necessary strategic "patience" and continued cooperation until the two sides have jointly taken concrete actions to firmly restore the international system with the United Nations at its core. China believes that, in the process of resolving the current Ukrainian crisis, the UN and the parties involved

should take coordinated and effective action based on international law, with the short term aim of promoting a diplomatic solution to the ongoing war.
Sanctions have never been a fundamental and effective solution to a problem. When the parties’ legitimate security concerns are not addressed,
recklessly putting strong pressure with large-scale sanctions is tantamount to adding fuel to the fire and only affecting the populations.
As Foreign Minister Wang Yi stressed, the concept of common, comprehensive, cooperative and sustainable security needs to be upheld, while relinquishing the idea of
exclusive and absolute security for one side and insisting on ending conflicts through negotiation. It is imperative to strengthen mutual trust and build a world of lasting peace together. The Chinese Six Point Initiative is aimed at preventing a large scale humanitarian crisis in Ukraine.

117



Minister Wang Yi has stressed that the top priority in the Ukrainian crisis is to alleviate the situation on the ground as much as possible, to prevent the conflict from escalating or even spiralling out of control. The Six-Point Initiative, proposed by the People's Republic of China for this purpose, demonstrates the country's clear position, and the global mindset of China's diplomacy.
Avoiding the politicisation of humanitarian issues and not turning it into propaganda for one side only is important to ensure the safe, timely and smooth development of humanitarian operations.
With a view to reaching this goal, the Six-Point Initiative emphasises in a comprehensive and

balanced manner that all parties concerned must adhere to the principles of neutrality and impartiality in the conduct of humanitarian operations, and that the United Nations should play a key coordinating role in the humanitarian sphere to assist Ukraine, so as to facilitate the development of humanitarian operations, through the deployment of efficient channels that point in the right direction.
The different groups most affected by the situation in Ukraine and most in need of humanitarian assistance have different practical concerns, which determine the different priorities of response strategies, based on the actual needs of representative groups such as displaced persons, civilians and foreigners in Ukraine.

On the Chinese side, Minister Wang Yi solemnly announced that the Chinese Red Cross Society would provide Ukraine with emergency humanitarian aid as soon as possible. The intense commitment shows China's humanitarian concern and is a clear example of China's continuing efforts to overcome the humanitarian crisis.
Safeguarding national interests through pro-people diplomacy. Protecting national interests has always been the fundamental task of China's foreign affairs. Since the establishment of diplomatic relations between China and Ukraine in 1992, Ukraine has become China's third largest trading partner in Eurasia after Russia and Kazakhstan, and China has also become Ukraine's largest trading partner.


The two parties have achieved fruitful cooperation in the fields of science and technology, education and culture, and have maintained close exchanges of personnel. As the situation in Ukraine has changed, China's Ministry of Foreign Affairs has immediately activated the emergency consular protection mechanism and has maintained close communication with all sides. It has also coordinated with both sides and has taken multiple measures to try to initiate a peace dialogue. Firstly, Minister Wang Yi immediately held a phone call with the Ukrainian and Russian Foreign Ministers, proposing a peaceful path to resolve all parties’ concerns through dialogue and negotiation.


123
Secondly, various agencies of the Chinese Foreign Ministry cooperated closely and comprehensively assessed the changes in the situation. Based on various options, they immediately formulated a feasible plan to assist the voluntary safe evacuation of Chinese and non Chinese citizens from Ukraine, activated the emergency consular protection mechanism and opened and unblocked some security channels.

Not wasting time and seizing the right time windows that we are struggling to open in the current war situation are ways to better organise emergency evacuation operations, and provide every possible help to those who have not been evacuated yet. Behind such efficient relocation operations, which have also involved the governments of China,
Moldova, Romania, Poland, Hungary, Slovakia and Belarus, there are the dedication of diplomats and people’s common desire for peace around the world, as these countries and others have provided security and evacuation structures.
Minister Wang Yi clearly and vigorously expressed China's open, transparent and consistent basic position on the Ukrainian issue, saying that the vast majority of countries oppose the "new cold war" and the division of the world. Minister Wang Yi said that in the face of a turbulent and changing world, the People's Republic of China has always represented stability and positive energy, and has always positioned itself in the right direction of historical progress. China will continue to take its responsibilities, to hold high the banner of peace,
development, cooperation and benefit for everyone, to promote the construction of a new type of international relations and contribute to building an international community with a future shared by all mankind.
We are certain that only the People's Republic of China has the possibility of making Russia see reason and leading it, first of all, to the cessation of hostilities, and to the organisation of a "Helsinki 2" Conference that would ensure to everyone as forty seven years ago - respect for the security of one another.


125

Professor Giancarlo Elia Valori is a world-renowned Italian economist and international relations expert, who serves as the President of the International World Group.
In 1995, the Hebrew University of Jerusalem dedicated the Giancarlo Elia Valori Chair of Peace and Regional Cooperation. Prof. Valori also holds chairs for Peace Studies at Yeshiva University in New York and at Peking University in China.

Among his many honors from countries and institutions around the world, Prof. Valori is an Honorable of the Academy of Science at the Institute of France, as well as Knight Grand Cross and Knight of Labor of the Italian Republic.
Giancarlo Elia Valori
 Edificio Valori at Peking University
Edificio Valori at Peking University

Giancarlo Elia Valori

Giancarlo Elia Valori
Army SOF’s Expanding Role In

DETERRENCE

Dr. Robert TOGUCHI Chief, Concepts Division, Force Modernization Directorate
Introduction
The recent war between Russia and Ukraine emerged in an unprecedented fashion in scope and scale since the Second World War.
On February 24th, 2022, Russia launched a five-prong military invasion of Ukraine with large scale conventional forces. Although Russian President Vladimir Putin called it a “special military operation,” the roots of this large-scale conflict go back to 2014 when Russia invaded and annexed Crimea while Russian supported separatist forces seized parts of the southeastern Donbas region.

In 2022, conventional deterrence experienced challenges. In the wake of the Russian invasion, the U.S. military recognized the foundational importance of strengthening deterrence at the strategic and operational levels to prevent future wars of aggression. In the emerging operational environment, deterrence cannot be limited to
operational forces only designed for high-end military conflict. Today, deterrence may come in many forms to include the application of Special Operations Forces through irregular warfare to ensure that all elements of national power are implemented to the fullest capacity prior to the next large scale invasion.

133
Framing Army SOF’s Expanding Role in Deterrence
In an era of competition between Great Powers, the premise of this evolving concept is that the focus must now be on deterrence. Where multiple threats are altering the global security environment to the extent that prevention is no longer an option; shaping or spoiling actions, or at a minimum preventing threat actions from escalating beyond our strategic depth and ability to respond is an emerging requirement. Our underlying hypothesis can be summarized as follows:

In the emerging security environment, deterrence, must expand beyond preventing something from happening, but also about preventing something from escalating beyond U.S. strategic depth or capability to respond, in a manner consistent with our National values.

135
In a world characterized by increased volatility, an evolving concept of deterrence recognizes the need to expand deterrence thinking beyond high-end conventional or nuclear capabilities, and consider threats to national security
across the spectrum of conflict. Although the pre conflict space of global competition will continue to be led by the Department of State, National guidance suggests DoD support to a broader approach is needed. The DoD possesses unique capabilities to assess, sort, form a response, and rescale security threats long before they escalate beyond the Nation’s strategic depth and ability to respond.

In consideration of security threats and capabilities across the operational continuum, deterrence can be defined as the prevention of adversary action through the signaling or use of credible physical, cognitive and information

capabilities that raise an adversary's perceived cost to an unacceptable level of risk relative to the expected benefit.
With an emphasis on pre-conflict force posture and readiness, this article will explore five broad conceptual lines of effort to strengthen deterrence which include:
137
the

Rethinking Strategic Power and Reframing Power Projection Expanding
Strategic Start Point
1. Expanding the Strategic Start Point

The totality of the security challenges facing the U.S. and its Allies and the evolving character of these threats require an operational framework to win early to prevent these challenges from scaling beyond the Nation’s strategic depth and ability to respond. Such an operational framework begins with an earlier Strategic Start Point for campaigning. The framework for this approach centers on forward basing in and around the people with deep knowledge of the environment to generate decisive situational awareness to better inform the proper strategic start point for campaigns where the “Win” can occur at a much lower level of effort.
An earlier “Strategic Start Point” requires new thinking about the traditional military Phase 0 and new thinking about when “Left of Phase 0” campaigns can begin. Re-framing the Strategic Start Point requires us to consider how we assess, sort, form a response and rescale security challenges to win early and preserve strategic depth and decision space for our national decisionmakers. An example of this approach can be seen in the early investment of U.S. SOF trainers and advisors over many years to ensure the relative combat effectiveness of Eastern European SOF formations and employment of advanced technology capabilities.
DETERRENCE DETERRENCE DETERRENCE 139
DETERRENCE
2. Rethinking Strategic Power and Reframing Power Projection

Traditional considerations of power projection generally center on long range stand off or rapid expeditionary capabilities. Rethinking strategic power to address security challenges emanating from the Gray Zone, below the level of armed conflict, considers power beyond traditional warfighting capabilities to examine the full range of national, allied, partner, and population based power. Reframed power projection envisions leveraging bi-lateral capabilities through a focus on extant partner and populationbased power in and around the operational area, in support of persistent campaigns below armed conflict, to mitigate threats early in their development and risk profile.
In an era of persistent unrest and global insecurity, the application of indigenous mass is a fundamental component of power projection. The effectiveness of recent Ukraine defenses comprised of both military, security forces, and population based defenses attest to the power of these approaches. (a) Partner Based Power. Partner based power is a vital component of Army SOF’s (ARSOF) emerging role in deterrence and centers on leveraging persistent forward presence to shape, develop, enable, and integrate indigenous governments, militaries, and security forces into a broad framework of strategic power.
DETERRENCE DETERRENCE
DETERRENCE DETERRENCE DETERRENCE
Partner-based power focuses on developing and accessing host nation capabilities to produce credible power in the operational area to achieve relative superiority over the physical, cognitive, and information security environments of key populations and locations. At its core, partner based power is centered on operating “with and through” foreign governments, militaries, security forces, and non governmental organizations1 to support local, regional, and global deterrence efforts. Operations in Northern Iraq, Colombia, El Salvador, and the Philippines offer compelling examples of effective partner based power.
(b) Population Based Power. Population based power is also a vital component of ARSOF’s emerging role in deterrence and centers on persistent influence to shape, develop, enable, and integrate local perceptions, attitudes, behaviors, decision making processes, and actions that support a broad framework of strategic power. Population based power relies upon influence over time to address trends in competition and to achieve relative superiority over the physical, cognitive, and/or information security of key personas, groups, and populations. Population based power includes actions and/or messaging to encourage desired behavior in targeted populations,

141


DETERRENCE DETERRENCE DETERRENCE
DETERRENCE DETERRENCE DETERRENCE


such as support to legitimate government, counter malign activities, etc. In semi permissive or denied environments, population based power leverages select populations to facilitate a resistance movement than can deny adversary regime objectives and policies, or in extreme cases, to facilitate regime change. Population based power enhances resilience. It also focuses operating “with and through” relevant persons and populations, both of which are designed to create indigenous mass forward in the operational area to support local, regional, and global deterrence efforts.

143
Gaining

an Information Advantage Rethinking Asymmetric Approaches
DETERRENCE DETERRENCE DETERRENCE
3. Gaining an Information Advantage
An information advantage is key to deterrence in the Gray Zone. ARSOF require persistent forward presence working with partners and allies to establish and improve U.S. placement, access and influence. ARSOF must have the ability to converge all-domain effects to coordinate, synchronize, and campaign globally in the Gray Zone.
Transregional Fusion Headquarters

To coordinate special operations across geographic, political, and military boundaries, ARSOF may need a transregional C2 capability that can fuse all-domain capabilities to achieve U.S. deterrence objectives.
The purpose of a transregional fusion headquarters is to facilitate the rapid and continuous integration and convergence of capabilities in all domains, the electro magnetic spectrum (EMS), and information environment. This enables the joint force to optimize effects and raise an adversary’s estimate of the perceived cost of action to an unacceptable level of risk across human imposed boundaries it eliminates gaps and seams across the operational space. The special operations component commander would have a tool to employ Special Forces, Civil Affairs, and Psychological Operations capabilities from across all geographically oriented
145
DETERRENCE DETERRENCE DETERRENCE
SOF commands partnered with capabilities from cyber, space and other JIM partners.
(c) Cognitive Targeting as an Enabler

Cognitive Targeting consists of employing culturally aware and regionally attuned ARSOF to influence the perception and behavior of relevant audiences through the low-signature application of lethal and nonlethal actions. ARSOF coordinates actions and messaging with DoD and other JIM partners to accomplish U.S. strategic objectives. For example, ARSOF may leverage personal relationships and messaging influence over an adversary’s troops to remain in their barracks prior to a joint forcible entry operation.
Cognitive targeting may also entail an information plan to influence religious leaders to condemn ethnic cleansing by an adversary government.
4. Rethinking Asymmetric Approaches
Joint Publication 1 02 defines asymmetry in military operations as “the application of dissimilar strategies, tactics, capabilities, and methods to circumvent or negate an opponent's strengths while exploiting his weaknesses.”2 In a competitive environment, asymmetric approaches can be advantageous to optimize forces, capabilities, and relationships to achieve a relative positional advantage over our toughest adversaries.
DETERRENCE DETERRENCE DETERRENCE
(d) SOF Cyber Space Triad as an Asymmetric Approach

One form of asymmetry is the recent emergence of the converging capabilities and effects of SOF, Cyber and Space in the competitive security environment. As we move into the future, the combinations of these particular capabilities orchestrated in a holistic fashion with relevant C2 will ensure greater redundancy, resilience and influential power previously unseen on the battlefield. Together this Triad of capabilities will offer new options for deterrence that will be compelling both in competition and conflict and could manifest in ways that were previously unseen
and unanticipated by our adversaries. An integrated Cyber, Space and SOF Triad could certainly achieve greater strategic and operational impacts through campaigning for deterrence and preparing the environment for Joint Force action in crisis and conflict. The Triad components would be inherently trans regional and collectively could better see, sense, understand, stimulate, and provide options to strike and assess across the physical domains synchronized with the information and cognitive dimensions. In employment, an interoperable SOF Cyber Space Triad cross functional team empowered with appropriate resources
147
DETERRENCEDETERRENCE

DETERRENCE
authorities, and permissions could foreseeably converge cyber, space, and special operations capabilities to achieve unique trans regional multi domain effects to impose costs on and create dilemmas for our toughest adversaries.



DETERRENCEDETERRENCEDETERRENCE
Expanding


Technology Solutions for Irregular Warfare Force Modernization
DETERRENCE DETERRENCE DETERRENCE
5. Expanding Technology Solutions for Irregular Warfare

Forward presence and proximity with populations is paramount to maintaining a competitive advantage in Irregular Warfare. To that end, technology-based deterrence solutions have long been a key element in the national security calculus. During the Cold War deterrence required a new level of technological sophistication to counter the former Soviet Union and roll back the spread of Communism. In the 1970s, Secretary of Defense Harold Brown and Under Secretary William Perry implemented a plan to emphasize advanced technology solutions to deter the
former Soviet Union and gain technical superiority, but this time focused on stealth capabilities, precision strike weapons and improved command, control, communications, computers, intelligence, surveillance, and reconnaissance (C4ISR).3
The emerging operating environment requires technology solutions for Irregular Warfare. Social, political, informational, and economic trends in international competition are converging among state, non state actors, and others for relative superiority over key populations. Such technologies may include enhanced cyber enabled collection and analytical capabilities leveraging open source information
151
DETERRENCE DETERRENCE DETERRENCE
and a robust reachback to subject matter expertise to conduct social media exploitation and analysis, AI enabled data fusion, human terrain mapping, sentiment analysis, trend analysis, pattern-of-life analysis, and predictive analytics.

CONCLUSION
State and non-state actors are increasingly employing combinations of conventional, irregular, and hybrid strategies across the conflict continuum to achieve their objectives. Russia’s actions in Eastern Europe, China’s activities in the South China Sea, and the rise of non-state actors are contemporary examples that suggest a need to relook deterrence thinking and to
define what a “Win” looks like in the Gray Zone.
ARSOF’s role in deterrence considers deterrence across the entire operational continuum to confront low and high end competitors in the early 21st Century security environment. It offers a way to address the escalation of many security challenges we face earlier in their development and risk profile. In doing so, it will broaden strategic options in terms of time, decision space and approaches for our national decision makers.
1 The U.S. Army defines mass as: “Concentrate the effects of combat power at the decisive place and time, “ FM 1 02, Operational Terms and Graphics, September 2004, 1 121. 2 Joint Publication 1 02, DOD Dictionary of Military and Associated Terms 08 November 2010, as amended through 15 November 2014, http://www.dtic.mil/doctrine/dod_dictionary/index.html. 3 Robert Martinage, "Toward a New Offset Strategy: Exploiting U.S. Long Term Advantage to Restore U.S. Global Power Projection Capability," (PowerPoint Presentation), Center for Strategic and Budgetary Assessments, 2014, 5.


Chief, Concepts Division, Force Modernization Directorate U.S. Army

COL Robert M. Toguchi, Ph.D., U.S. Army retired, is a senior concept developer at ARCIC. He previously served as chief, Strategic Plans, J 5 Directorate, and Deputy Director, J 8 Directorate, U.S. Pacific Command. He also has served as a war plans officer in the War Plans Division, Army G-3, Department of the Army Staff.
Responsible
Army
United States Military Academy at West PointChief, Concepts Division, Force Modernization Directorate U.S. Army



for concept development for all assigned U.S.
Special Operations Command capability areas. Extremely knowledgeable of advanced military technologies in multiple sectors.
QUANTUM
LEADERSHIP

THEORY
BRIAN LENAHAN
 Founder & Chair of the Quantum Strategy Institute
Founder & Chair of the Quantum Strategy Institute
Abstract Quantum technologies, given their complexity, dynamism and disruptive nature demand a type of leadership never before required in human history. Based in the theories and experimentation of Einstein’s light quanta and ‘spooky action at a distance’, Heisenberg’s uncertainty and Feynman’s ‘if you think you understand quantum mechanics, then you don't’ environment, it is with little wonder that organizational leaders approach quantum technologies with caution. Layer on predictions of usefulness years distant, making investments in such technologies, let alone applying them commercially could be construed as folly.
However, this approach would be in error, as incremental, iterative progress is being made in the field achieving early stage results. In this article, I establish a set of principles on which the practice of quantum leadership can be explained. Such a system of ideas to explain a general theory of quantum leadership (QLT) holds significant importance for consuming organizations as quantum technologies advance rapidly around the world. The QLT introduces a holistic perspective for organizational leaders to follow in integrating quantum technologies now and in the future.

159
Introduction
The development of a generalized theory of quantum leadership imbues an assumption of uniqueness of the field’s technology, its characteristics and implications relative to other classical, conventional or traditional technologies based on either analog or digital foundations.
For individual leaders to enable their organizations to assess, compare, invest, implement, monitor and measure quantum performance, they must not only understand the underlying fundamentals of quantum mechanics and physics to some degree, but, as a result, the wide variety of quantum solutions that exist in an environment without convergence.

This article addresses the set of principles required for the relatively new field of quantum technology and its inherent leadership. Five principles are identified within this paper composing the elements of the QLT.

History of Leadership Theory
Leadership theorists of the 20th and 21st century include McClelland, Fiedler, Hersey and Blanchard, Mintzberg and Kotter. Starting with ‘trait’ theory in the early 20th century to today’s focus on collaboration and agility, leadership theory has evolved in generally the following order. Trait theory suggested only people born with certain leadership traits would be successful.
161
QUANTUM LEADERSHIP THEORY

Brian Lenahan
Contingency theory suggested different situations required different leadership styles. Leader-Member Exchange theory focused on the quality of relationships between the two parties. Situational leadership occurred where leaders selected a style appropriate for the maturity of the follower. Servant leadership incorporated 10 key compassionate characteristics including listening, empathy and healing. Transformational leadership focused on the engagement of the individual interacting with
others where motivation and morality are raised on the part of both the leader and followers. Marsh defined the transition in leadership theory between 2000 and 2020 as “Leadership has shifted in the last twenty years away from an autocratic style and towards a more collaborative approach, fostering greater teamwork, productivity, innovation and creativity.” Leadership themes of collaboration and agility prevail in 2022. Jordan, Wade and Yokoi argue
“There have been many calls for leadership approaches to shift to meet the demands of a fastchanging, unpredictable world.” Stanton states in 2022, “Success will be determined by those who can swiftly adapt, shift, monitor and adjust.
Constant change is the norm, and the sooner accepted, the better equipped we are to ensure our teams are poised for growth. Internally, people are looking to their leaders to provide direction, guidance and support.”
Quantum Leadership Principles

To address this agile environment coupled with a rapidly maturing technology (quantum), the following five leadership principles are incorporated into a quantum leadership theory.
1Principle 1: Quantum, being different from any other prior technology, must be treated as unique.
As noted in the abstract, quantum mechanics and quantum physics, based in the smallest units of nature, atoms, molecules, electrons, photons and ions, have been studied at least since Einstein’s miracle year of 1905 where he theorized light existed not just in waves but also in particles he called ‘light quanta’. The resulting 117 years have been a race to understand the dynamics of elements (i.e., silicon, barium, ytterbium) composed of these small units to take advantage of their characteristics of superposition and entanglement.
163
Digital technologies are based on finite bytes (bits) of 1’s and 0’s. Quantum bits or qubits are in superposition of 1 and 0 where superposition is defined as the ability of a quantum system to be in multiple states at the same time until it is measured. Qubits also have the ability to entangle at close and great distances offering the ability to exponentially accelerate quantum algorithms. Given the notable differences between digital and quantum technology, a traditional approach will be ineffective.

2Principle 2: Quantum dynamism, the speed at which breakthroughs occur, must be a foundational element of any quantum roadmap.
Technology, and increasingly mainstream, media share articles, blogs, posts, and papers touting the latest breakthrough in the field of quantum technology and such breakthroughs occur on at least a weekly basis around the globe. Cybersecurity risk represents the first highest need application for quantum technology as classical systems like RSA are expected to be broken as early as within a few years of this article. Multiple forms of protection in the form of post quantum cryptography, quantum key distribution, quantum random number generation and others have been under development for the better part of the last decade and already exist in market in smartwatches, secure communication networks
QTL
and some of the largest corporate organizations. Other application areas such as optimization, navigation, simulation and sensing are underway in research, development and commercialization. The obvious challenge for today’s leaders is the lack of awareness of first quantum, followed by the speed of breakthroughs, followed by the implications of each. Quantum technologies are advancing so rapidly they represent a unique environment for leaders to address.
Principle 3: Leadership principles which rely on a broadly distributed hierarchy are ineffective in a quantum technology environment.

For thousands of years, the traditional hierarchy or
or pyramid of workers, supervisors, managers and leaders has held sway as the method of research, production, sales and marketing, dividing up the skills by role. The new challenge represented by quantum is one of deeper understanding by Chief Executive Officers (CEO’s), as well as their technology teams. Today, there are at least ten different quantum modalities or hardware types. Even if one were to remove a consuming organization from the underlying hardware and base software levels of a quantum stack, the decisions required on cloud suppliers, algorithm developers/development, hybrid comparisons, roadmap development and more demand CXO’s retain
QTL
QTL
3
165
and keep current a deep understanding of such levels in order to enable reasonable quantum decisions. In the face of already overwhelming considerations, adding a complex subject such as quantum can be daunting and challenging to work into an organizational strategy. Relying on a hierarchy of employees, committees, vendors or councils will extend the timeline for quantum integration during periods where the technology is advancing so quickly, new opportunities are arising and competition is leaping ahead.
Thus, leaders need to commence and accelerate quantum research and initiatives now with risk focused yet agile teams who understand the technology and its potential.
Principle 4: Global communities of quantum fields will be indispensable for quantum technology success. One unique characteristic of the quantum space, unlike its most recent technology relative artificial intelligence in its recent era (2010 through 2020), was the rapid adoption of quantum communities and collaboration around the world.
The sharing of ideas, breakthroughs and results is widespread through conferences, consortiums, social media, podcasts, videos and more. Wise leaders accelerate their education through short bursts of learning through these methods. Sourcing and developing scarce quantum talent occur as much as through word of mouth and coaching as through traditional recruiting and training.

4
Access to information though regional, national and global communities form a fundamental foundation of quantum education now and in the future, and quantum leadership demands such access.
5Principle 5: The uncertainty of quantum and the certainty of organizational procedures need to be bridged. As a former executive in a large financial institution, policies guidelines, rules, contracts and other
illustrations of approximating relentless certainty in order to reduce risk and costs of inefficiency remain the order of the day. In quantum leadership, uncertainty will be added
to the certainty of the digital world in a hybrid environment, extracting the best of both worlds. Uncertainty in several senses. In that once quantum advantage occurs (i.e., exceeding the processing capabilities of any classical computer or super computer on a given task), how will quantum output be validated? How will the evolving discoveries in quantum be integrated?
How will an organization keep up-to-date with quantum technology advances? How will unexpected opportunities from quantum be leveraged? Existing comfortably in the realm of uncertainty and making that realm part of the organizational culture and skill sets will be fundamental to ongoing success.

 Brian Lenahan
Brian Lenahan
Summary
The five principles incorporated into the Quantum Leadership Theory address the uniqueness of quantum technologies, the speed at which QT advances, the need for shifting hierarchal structure, the importance of leveraging a formidable quantum community, and finally, the need to be comfortable in an environment of uncertainty.
Quantum,
Copyright 2022 Aquitaine Innovation Advisors All rights reserved Comments: General Quantum Leadership Theory (General QLT) 2022 Subjects:
Business Version 1.0 169



Brian Lenahan is Founder & Chair of the Quantum Strategy Institute, an international think tank devoted to the acceleration of the adoption of quantum technologies. Brian is a global pioneer in quantum leadership theory and the commercialization of quantum technologies, consulting to large corporates. He is a six time author of books dedicated to the commercial advance of artificial intelligence and quantum technology including his latest “Quantum Excellence: How Leading Companies Are Deploying the Transformational Technology”. A former North American financial services executive, Brian integrates that business experience with advanced technologies, regularly speaking at conferences around the world.
Sources: 1. Sources: 2. https://hsm.stackexchange.com/questions/11839/what is the source of einsteins quote spooky action at a distance 3. https://scienceexchange.caltech.edu/topics/quantum science explained/uncertainty principle 4. https://www.bbvaopenmind.com/en/science/leading-figures/richardfeynman-the-physicist-who-didnt-understand-his-own-theories/ 5. Superposition is the ability of a quantum system to be in multiple states at the same time until it is measured. Because the concept is difficult to understand, this essential principle of quantum mechanics is often illustrated by an experiment carried out in 1801 by the English physicist, Thomas Young. https://www.techtarget.com/whatis/definition/superposition 6. https://scienceexchange.caltech.edu/topics/quantum science explained/entanglement 7. https://www.t three.com/thinking space/blog/leadership 2000 2020 8. Finding the Right Balance and Flexibility in Your Leadership Style, Jennifer Jordan, Michael Wade, and Tomoko Yokoi. January 11, 2022. Harvard Business Review. https://hbr.org/2022/01/finding the right balance and flexibility in your leadership style 9. T1 - Current Trends in Practicing Leadership: Evidence From the 10. Harvard Business Review. DO 10.4018/978 1 5225 8088 1.ch008. 11.
1. 2. https://www.researchgate.net/publication/338305959_Current_Trends _in_Practicing_Leadership_Evidence_From_the_Harvard_Business_Revi ew/citation/download 3. https://www.forbes.com/sites/forbestechcouncil/2022/03/17/fiveleadership trends you should care about in 2022/?sh=646e1e056e13 4. https://bmjleader.bmj.com/content/leader/5/1/3.full.pdf 5. https://www.academia.edu/41096171/A_short_history_of_leadership_ 6. theories 7. https://www.t three.com/thinking space/blog/leadership 2000 2020 8. https://toughnickel.com/business/The History of Leadership Studies and Evolution of Leadership Theories 175


LEADING STRONG IN A


COMPLEX WORLD Brigadier General Scott F. “Rock” Donahue (U.S. Army, Retired)
“The world is spinning and so are we whether we like it or not. It is more complex and unpredictable than we can see. Technology is at the forefront of the chaos; it affects everything, from our daily existence, our careers, and the way we make decisions. … In today’s environment, we are all willing to work longer, and harder but the big question that arises is whether corporations are willing to retain us in positions that match our skills. There is currently a mismatch between the skills people have and the skills that are required to go forward. Those who do not understand technology will be left behind”.


Dr. Linda Restrepo, CEO Professional Global Outreach
F. “Rock”
179 Brigadier General Scott
Donahue (U.S. Army, Retired)



“We are all afraid for our confidence, for the future, for the world. This is the nature of the human imagination. Yet every man, every civilization, has gone forward because of its engagement with what it has set itself to do. The personal commitment of a man to his skill, the intellectual commitment and the emotional commitment working together as one, has made the Ascent of Man”.
Jacob Bronowski TheAscentofMan , 1973
United States security is inextricably linked to global security requiring agile, adaptive, and authentic leaders in all professions to effectively operate within complex and often volatile, uncertain, and ambiguous environments: 1 shaped by an increasing range of threats including terrorism, insurgencies, transnational groups, rogue states, non-state actors, criminal organizations, and near peer competitors; 2- exacerbated by the transcendence of globalization, urbanization, persistent conflicts, protracted competition, pandemics, strained economies, civil unrest, energy crises, the tyranny of transparency, and cyber warfare; and 3 perplexed by astounding innovations in biotechnology, robotics, drones, and quantum enhanced systems.1

Consequently, our rapidly transforming world requires a corresponding transformation of lifelong leader growth to enable high performing organizations (i.e., cohesive teams comprised of winning subordinate teams) to thrive in this new strategic landscape. Moreover, because there are no predetermined solutions, leaders at all levels now more than ever in our history – must be equipped with an innovative mind, a willingness to execute decisively with precision and to accept prudent risk in unfamiliar or rapidly changing situations, an ability to adjust based on continuous assessment, and the courage to lead necessary change to turn daunting challenges into desirable opportunities.2
The author posits effective transformative lifelong leader growth occurs across the five continuous interdependent domains of learning (what to know), training (what to do), education (how to think), development (when to act), and assessment (where to grow) encompassing a proven enterprise operating philosophy framed by the four foundational rallying principles of Teamwork, Execution, Attitude, and Mission

“T-E-A-M”
183
Depicted in Figure 1, the T-E-A-M operating construct and leader growth model is grounded in the empowering three core attributes of inspired leadership, disciplined execution, and superior performance, which are enriched through the three shared ethical elements of values, trust, and accountability. Moreover, the leader growth model is engaged by the following four foundational rallying points:
Teamwork: promoted through connection, communication, and collaboration;
Execution: fostered by engagement, empowerment, and excellence;


Attitude: characterized by the Level 5 leadership qualities of personal humility, professional will, and positive determination; and
Mission: accomplished through resolve, renewal based on the strategic/operational environment, and results.
4 2 1 3
TEAM
Together, the fusion of the interdependent empowering core leader attributes, shared ethical elements, and foundational rallying points produce principled leaders of character strengthening their professions, and who embody the enduring qualities of being relevant, respected, responsive, and resilient.


Relevant Respected Responsive Resilient 185
AND
GROWTH MODEL
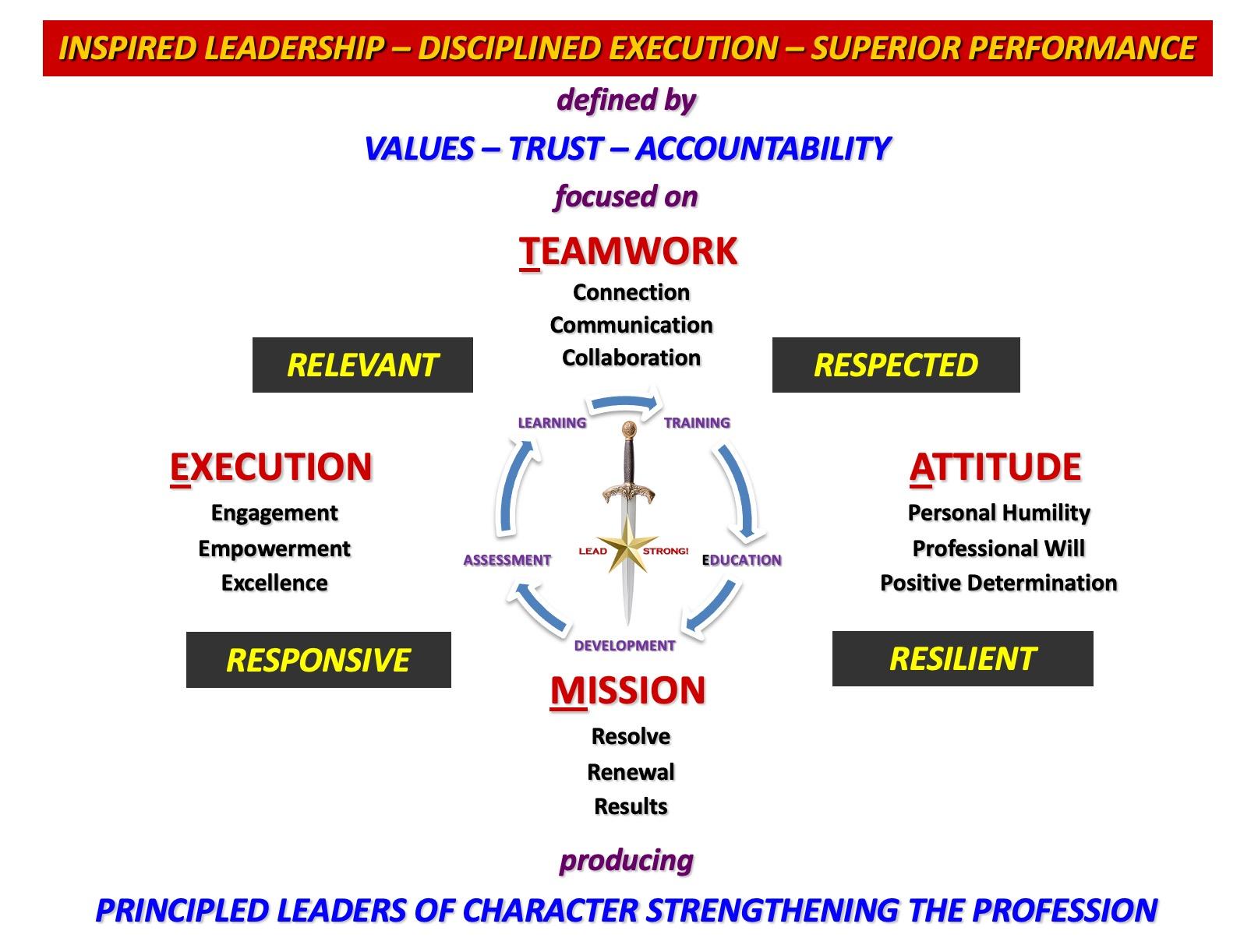


ENTERPRISE OPERATING PHILOSOPHY
LEADER
Figure 1
Leadership ability is the lid that determines a person’s level of effectiveness. The lower an individual’s ability to lead, the lower the lid on his potential. The higher the leadership, the greater the effectiveness.

John C. Maxwell
The21IrrefutableLawsofLeadership,1998
As highlighted in red and gold at the top of Figure 1, the T E A M enterprise operating construct with the embedded model of five continuous domains of transformative lifelong leader growth is predicated on the empowering three core attributes of inspired leadership, disciplined execution, and superior performance. As learned, developed, and practice through my nearly forty years of continuous personal and professional learning, training, education, development, and assessment in the United States Army as well as in the public sector – these three core attributes can be defined and put into decisive action as follows:
187
1. Demonstrate
Inspired Leadership:
a) Set the moral and ethical climate of your organization; strive to build cohesive winning teams of teams.
b) Treat everyone with dignity and respect; lead, inspire, and mentor disciplined, values-based, servant leaders.
c) Maintain a positive, upbeat attitude and approach to doing business.
d) Encourage and reward initiative, innovation, creativity, and risk taking.
e) Develop yourself and those around you; conduct effective, meaningful performance counseling routinely.
2. Discipline Execution of Primary Duties and Responsibilities
a) Develop disciplined people, thought, and action.
b) Do what’s right legally, morally, and ethically every day in all you do.
c) Engage and empower subordinates and hold them accountable; always underwrite honest mistakes.
d) Discipline social networking and information management; communicate using the 4C’s: clear, concise, cogent, and complete.
e) Address areas of concern before they become points of friction, and resolve points of friction before they become points of conflict.

3. Deliver Superior Performance:

a) Make a positive impact; say what you’ll do and always do what you say.
b) Maintain truth, trust, transparency, and accountability.
c) Develop systems of internal controls to do routine things routinely.
d) Plan, prioritize, and coordinate continuously; challenge assumptions.
e) Know the difference between efficiency (doing things correctly) and effectiveness (doing the right things); strive for both.
In summary, being an effective leader is not about giving orders, rather it’s about earning respect, demonstrating inspired leadership, disciplining execution in all you do, and building high performing winning teams to promote excellence and deliver superior performance.
Your success will be measured by your personal commitment to continuous learning, training, education, development, and self assessment, as well as your passion for team members and teams you’ll train, teach, coach, mentor, and lead.
189
1
Along the way you will no doubt make honest mistakes, and face difficult decisions and dilemmas. But stand firm and do not waver as this is inherit in the process of learning the art of leadership and LeadingStrong . Above all, you must display unimpeachable integrity and uncompromising character, and remain truthful in word and deed, as this is the underlying premise of always Leading Strong – and serving with courage – in a complex world.

Lieutenant Colonel Scott F. Donahue, Assessing Leadership Potential for the Army’s Future Force, (United States Army War College Strategy Research Project: Carlisle Barracks, Pennsylvania, March 19, 2004), 1 2. 2 Ibid., 3 7. Maxwell, John C. The 21 Irrefutable Laws of Leadership: Follow Them and People will Follow You. Nashville: Thomas Nelson, Inc., 1998.
Georgia Military College (GMC) was established in 1879 by act of the Georgia General Assembly.
In 1950, the United States War Department designated the institution a “Military Junior College.” Today GMC is one of only five Military Junior Colleges in the United States.


191

Since March 2022, Brigadier General Rock Donahue has served as Georgia Military College Senior Vice President and Chief Infrastructure & Sustainability Officer (CISO). Previously, from mid October 2014 to February 2022, he served as Executive Director of Georgia Military College’s new campus in Fayetteville, GA; and beginning September 1st, 2017 he assumed executive oversight of all four Georgia Military College campuses in the Atlanta Metropolitan Region including the Fairburn and Stone Mountain Campuses, as well as GMC’s Extension Center in the City of Zebulon; then in January of 2022 he assumed executive oversight of the Madison Campus as well.
directing high performing units and functioning in complex environments in the United States and abroad, including command at the company, battalion, brigade, and division levels, as well as combat operations in Panama, Kuwait, Afghanistan, and Iraq.

General Donahue is the recipient of numerous prestigious awards and honors including the Distinguished Service Medal; two awards of the Defense Superior Service Medal; four awards of the Legion of Merit; two Bronze Star Medals; two Defense Meritorious Service Medals; and four Meritorious Service
Prior to joining Georgia Military College, General Donahue retired from the United States Army in 2013 after more than 30 years of active federal commissioned service. During his military career, he served in a wide range of Army, coalition, and joint command and staff positions
Medals. He is also the recipient of the United States Army Corps of Engineers Silver Order of the deFleury Medal; and he earned the US Army’s Master Parachutist Badge, Pathfinder Badge, Ranger Tab, Sapper Tab, and Army Staff Identification Badge.
193

MATTEO TESTI
CEO & Founder Deep Learning Italia M. Ballabio

Machine Learning
ML Ops
Dev Ops
Data Engineering
A machine learning (ML) model is a “compiled” software of data [1][2]. The term "MLOps" is used when this DevOps process is specifically applied to machine learning [3]. Different from traditional software, the quality of a ML model (e.g., accuracy, correctness, and robustness) is often a reflection of the quality of the data, model choice, and optimization of the hyperparameters. MLOps aims to measure and improve the quality of ML models and release into production [4].
MLOps was born from different fields: ML, Development and Operations (DevOps), and data engineering (Fig. 1). DevOps had the biggest impact on MLOps development because it’s a method of practice [5] that aims to introduce the concepts of continuous integration (CI) and
 Figure 1: MLOps develops upon Machine Learning, DevOps, and data Engineering [18]
Figure 1: MLOps develops upon Machine Learning, DevOps, and data Engineering [18]
continuous delivery (CD), which allow software to be produced with short time to market, ensuring that it can be reliably released at any time.






When we look at how the current literature describes an ML project pipeline, a picture like the one illustrated in Fig. 2 (below) is often shown. In many companies, model development and operations are carried out manually and without implementing MLOps without a standardization of a workflow or pipeline.
Figure 2: Traditional workflow of ML (top) vs. MLOps workflow (bottom)[18]
 Training Validation Testing
Design Model Development Operations
Training Validation Testing
Design Model Development Operations
197
One of the most important point is that ML models have zero Return on Investment (ROI) until they can be used [7][8], time to market should be the first metric to look at and optimize for any ML project.
The only way to improve the release and continuous use of ML solutions in the industrial environment is to take great care of the part following the development of the model, in particular the interface between the ML solution and
Machine Learning Development and Operations
the existing Information and Communication Technologies (ICT) system. In fact, the most timeconsuming step in releasing an ML solution into production is Operations (Fig.2 ).

Thus, the life cycle of a machine learning project consists of many complex phases, such as data preparation, model selection, and deployment [8]. The focus of the academic world is attracted to the early life machine learning project life cycle is often overlooked
although they are critical to the success of such models in industrial applications. Precisely, in recent years, the problem of how to deploy and scale machine learning models have been
simplified by automatic learning models such as Seldon Core (Cox et al., 2018), KFServing (KFServing, 2019), Kubeflow (Kubeflow, 2018), and MLFlow (Zaharia et al., 2018).
One of the big challenges in MLOps is to design systems that can monitor in real time the performance of the model and generate alerts when the performance of the pattern is changing (Diethe et al., 2019)[9]. Therefore, we try to identify the activities key to the success of an application of ML: 199
Business Problem Understanding
Establishing an understanding of the business and the criteria of success to solve the problem [10].
Data Acquisition
During data acquisition, the goal is simply to collect enough data to train the ML model to get the first solution [11]. The tasks for data acquisition can be summarized as follows:
Data extraction: select and integrate data relevant to the ML business.
Data analysis: exploratory analysis of the data.
- Data Preparation: identify the data preparation and feature engineering required for the model.
ML Methodology
After data acquisition, selecting the best ML algorithms to solve the problem is a key part of the ML project. Usually, the data science team studies the state of the art for the specific problem and tries a bottom up approach to solving it.
ML Training And Testing
The process of training and optimizing a new ML model is an iterative process in which data scientists test several algorithms, features, and hyperparameters. Once the best ML models have been chosen, they are re trained and tested. The models are evaluated using different validation methods such as: Holdout validation, Cross-validation, Bootstrap validation.
2 1 3
4
Continuous Integration (CI)
Is about testing, and convalidation code, data sets, data schemas, and models [12][13]. The validated model is deployed in an environment to prepare the functions for previews or classification. This distribution can be one of the following: Microservices with REST APIs. - A model embedded in a preferential or mobile device. Part of a batch prediction system.
Continuous Delivery (CD)
The objective of the pre production testing phase is to assess the reliability of a model for the production implementation [6]. The goal of the deployment phase is to enable a seamless and uninterrupted implementation with the possibility to implement new models with as little risk as possible. Best practices in Continuous delivery of software services requires the use of secure deployment techniques, such as A/B testing.

5 6
201
Continuous Training (CT)
During Continuous Training, we must continue to set up the dataset in the same way we train our model [14]. This means outlier detection to understand when the data distribution diverges from the training data. CT was in charge of retraining automatically the data and serving the models.
Continuous Monitoring (CM)
The main objective during the monitoring phase is to manage the risks of models in production by monitoring the various metrics and performance [15] and alerting an operator to the progress of the model
.
Explainable AI
.
The explainability of the model concurs with the customer to create confidence in the predictions/classifications made by the ML system, improving the transparency and reliability of such systems [16]. The user can verify which factors have contributed to certain predictions/classifications, introducing a level of accountability.
Sustainability: Carbon Footprint
If this growing trend continues, Deep Learning could become a significant contributor to climate change [17]. This trend can be mitigated by exploring how to improve energy efficiency in the DL models. Hence, data scientists need to know their energy and carbon footprint, so that they can actively take steps to reduce them whenever possible.
7 10
9
8
 MLOps
MLOps
MLOps MLOps








MLOps MLOps Figure 3:Proposed MLOps workflow [18] Business Problem Understanding ML Methodology ML Training & Testing Data Acquisition Continuous Integration Continuous Training Continuous Delivery Continuous Monitoring Sustainability Explainable AI
CONCLUSION
In conclusion, implementing ML models in production is difficult and especially does not mean just deploying the model with APIs. Further, it means implementing an ML pipeline that automates the training and implementation of new models. Setting up a CI/CD system allows you to automatically test and deploy new pipeline
implementations automatically. CM allows you to always have an evaluation in terms of metrics to evaluate and explainability helps you better understand how the model is thinking.
MLOpsMLOps MLOps 205

MATTEO TESTI is currently pursuing a Ph.D. degree in computer engineering with the Medical Statistic and Molecular Epidemiology Unit, University of Biomedical Campus, Rome, Italy. He is also an entrepreneur with a strong background in data science with a focus on deep learning. He founded Deep Learning Italia the biggest e learning platform in the artificial intelligence area in the Italian language. He was one of the technical writers for the Artificial Intelligence Italian white paper. Since 2019, he has been an Adjunct Professor with the University of Rome Tor Vergata, Rome.
CEO & FOUNDER DEEP LEARNING ITALIA

MATTEO BALLABIO was born in Carate Brianza, Monza and Brianza, in January 1999. He received the B.Sc. degree in Biomedical Engineering from Bergamo University, Italy, in December 2021, where he is currently pursuing the M.Sc. degree in management engineering. He has been a Collaborator at Deep Learning Italia since September 2021. He is the Contributor of the dataset ‘‘DBB Distorted Brain Benchmark’’ (BrainLife.io) used in the publication ‘‘DBB A Distorted Brain Benchmark for Automatic Tissue Segmentation in Paediatric Patients’’ published on NeuroImage Journal. He received the B.Sc. thesis entitled: ‘‘Creation of an open dataset for the evaluation of the segmentation of MRI images in the case of patients with severe distortions of brain anatomy’’ in collaboration with the Research Center Fondazione Bruno Kessler (FBK), Trento (IT). He is coauthor of scientific paper called “MLOps: A Taxonomy and a Methodology” (2022) with Matteo Testi.
1. References: [1] A. Karpathy. Software 2.0. https://medium.com/@karpathy/software-2-0-a64152b37c35, 2017. [2] L. Bass, I. Weber, and L. Zhu. DevOps: A software architect’s perspective. Addison Wesley Professional, 2015. [3] S. Alla and S. K. Adari. What Is MLOps? In Beginning MLOps with MLFlow, pages 79 124. Springer, 2021. [4] C. Renggli, L. Rimanic, N. Merve Gurel, B, Karlas, W. Wu, C. Zhang. A Data Quality Driven View of MLOps, 2021 [5] I. Karamitsos, S. Albarhami, and C. Apostolopoulos, ‘‘Applying DevOps practices of continuous automation for machine learning,’’ Information, vol. 11, no. 7, p. 363, Jul. 2020. [6] J.-P. Correa-Baena, K. Hippalgaonkar, J. van Duren, S. Jaffer, V. R. Chandrasekhar, V. Stevanovic, C. Wadia, S. Guha, and T. Buonassisi, ‘‘Accelerating materials development via automation, machine learning, and high performance computing,’’ Joule, vol. 2, no. 8, pp. 1410 1420, Aug. 2018. [7] J. Mizgajski, A. Szymczak, M. Morzy, Ł. Augustyniak, P. Szymański, and P. Żelasko, ‘‘Return on investment in machine learning: Crossing the chasm between academia and business,’’ Found. Comput. Decis. Sci., vol. 45, no. 4, pp. 281 304, Dec. 2020 [8] Testi, M., Ballabio, M., Frontoni, E., Iannello, G., Moccia, S., Soda, P., & Vessio, G. (2022). MLOps: A Taxonomy and a Methodology. IEEE Access. [9] J. Klaise, A. Van Loovern, C. Cox, G. Vacanti, A. Coca. Monitoring and explainability of models in production, 2020 [10] A. F. V. Maya, ‘‘The state of MLOps,’’ Tech. Rep., 2021
[11] Y. Li, X. Yu, and N. Koudas, ‘‘Data acquisition for improving machine learning models,’’ 2021, arXiv:2105.14107. [12] J. Bosch, ‘‘Continuous software engineering: An introduction,’’ in Continuous Software Engineering. Cham, Switzerland: Springer, 2014, pp. 3 13. [13] M. Leppänen, S. Mäkinen, M. Pagels, V. P. Eloranta, J. Itkonen, M. V. Mäntylä, and T. Männistö, ‘‘The highways and country roads to continuous deployment,’’ IEEE Softw., vol. 32, no. 2, pp. 64 72, Mar. 2015. [14] B. Liu, ‘‘Lifelong machine learning: A paradigmphfor continuous learning,’’ Frontiers Comput. Sci., vol. 11, no. 3, pp. 359–361, 2017 [15] J. G. Moreno Torres, T. Raeder, R. Alaiz Rodríguez, N. V. Chawla, and F. Herrera, ‘‘A unifying view on dataset shift in classification,’’ Pattern Recognit., vol. 45, no. 1, pp. 521 530, 2012. [16] Y. LeCun, Y. Bengio, and G. Hinton, ‘‘Deep learning,’’ Nature, vol. 521, no. 7553, pp. 436 444, Nov. 2015. [17] L. F. W. Anthony, B. Kanding, and R. Selvan, ‘‘Carbontracker: Tracking and predicting the carbon footprint of training deep learning models,’’ 2020, arXiv:2007.03051. [18] Testi, M., Ballabio, M., Frontoni, E., Iannello, G., Moccia, S., Soda, P., & Vessio, G. (2022). MLOps: A Taxonomy and a Methodology. IEEE Access. 211



TECHNOLOGY IN THE MAKING VECTOR N360 ™ © INNER SANCTUM Linda Restrepo | Publisher - Editor
TECHNOLOGY IN THE MAKING
DISCLAIMER: This Magazine is designed to provide information, entertainment and motivation to our readers. It does not render any type of political, cybersecurity, computer programming, defense strategy, ethical, legal or any other type of professional advice. It is not intended to, neither should it be construed as a comprehensive evaluation of any topic. The content of this Presentation is the sole expression and opinion of the authors. No warranties or guarantees are expressed or implied by the authors or the Editor. Neither the authors nor the Editor are liable for any physical, psychological, emotional, financial, or commercial damages, including, but not limited to, special, incidental, consequential or other damages. You are responsible for your own choices, actions, and results

Linda Restrepo | Publisher - Editor
