SPRING 2023
LIBRARY OF CONGRESS
ISSN 2833-0455



65 CONTENTS TABLE OF 7 The Day Before The Day After of Putin’s Years Let China Sleep 85 41 Digitalization of Ukraine In a Full-Scale Invasion Softwar Cyberspace and Artificial Intelligence 109

Orbital Cyber Warfare Statisticians Managing Business A Recipe for Disaster Classic vs Quantum Computing Thinking Technology: RA01 System Quantum Computing 181 139 161 199 227 QML Algorithm Financial QBITS 245

We all ask ourselves why does life have to be so complicated, why can’t anything be straightforward instead of the constant forking path into the dark? Society itself is comprised of fleeting moments, an ever-shifting interplay of errors and rejuvenation. The notion of a frictionless, idealized existence is but a mirage, for such a state is unattainable in reality.
In this publication, we take great pride in presenting a collection of diverse topics and perspectives, some of which may resonate with you while others may not. Yet, this is the essence of a truly free society, where a multitude of opinions can coexist and flourish. Sometimes you need to be broken before you can be whole.

5
- Linda Restrepo -
THE DAY
BEFORE
Spasms of an Empire
 By Patrick Pascal
By Patrick Pascal
THE DAY AFTER


On December 25, 1991, Mikhail Gorbachev signed his resignation as President of the USSR. In this premature winter night of Moscow latitudes, the Soviet flag flying over the Kremlin was taken down and replaced by the tricolor one of Russia. The dissolution of the Soviet Union was ratified the next day by the Supreme Soviet. USSR, which was experiencing a final spasm after the abolition by the Congress of Deputies, in the spring of 1990, of Article 6 of the Constitution on the ‘leading role’ of the Communist Party, after the putsch of August 1991 and the creation of a Commonwealth of Independent States (CIS), on December 8, 1991, by Russian President Boris Yeltsin and his counterparts from Belarus and Ukraine, had it really disappeared?

9
The question may be asked in the Day After, but the Day Before was mainly the considerable work of Mikhail Gorbachev, who changed the world by breaking down internal mechanisms of the system, breathing in a wind of freedom, regardless of the risks to power in the short and medium term, and setting himself the rule of abolishing the Brezhnev Doctrine on so-called ‘limited sovereignty’ and the peaceful settlement of external disputes.
En route to ‘Russia House’
On August 19, 1991, tanks rolled into Moscow while Mikhail Gorbachev, on vacation with his family in the Crimea, saw his resort transformed into a residence under surveillance. I am still in New York, awaiting my departure for Russia, observing from a distance this event of worldwide dimension, a considerable jolt in the evolution of a weakened Soviet Union, which is now confirmed to be in its death throes.
The information in the first hours is fragmentary. The televisions first broadcast images of an empty and gloomy Soviet capital, whose pale lighting, which gives a glimpse of armored means in the darkness, gives an even more sinister aspect.

The emerging coup appears to be a conservative reaction from within the system. The Army, the KGB, the Ministry of the Interior - the so-called ‘force structures’ (siloviki) - seem in the initial confusion to have sided with the coup plotters, who are given a chance to win.
I read the diplomatic correspondence from our post in Moscow, which, I imagine, requires a great deal of composure and even courage in these circumstances when it comes to observing the street right up to the White House, that is to say, the Parliament, which is one of the epicenters of the crisis.
In the disorder of the end of the Soviet Union, in counterpoint to the frozen world it embodied, it is very difficult to know what is really going on, at least in the first days, and on which side the scales will tip. The complexity of the affair is such that, years later, the thesis will circulate that Mikhail Gorbachev himself, noting the failure of his policy of openness and reform, would have been the instigator of the coup, to then carry out a recovery that he would have premeditated.

In the heat of the moment, our chargé d'affaires on the spot in the absence of the ambassador, took the risk of estimating - because there was a need to provide an analysis to Paris as soon as possible‘that basically, the man in the street is no doubt content with what is similar to an imposition…'. This judgment will ultimately prove to be totally erroneous, but, in the meantime, France cannot remain silent and President Mitterrand has decided to speak on television. He would later be reproached for
having implied in the name of necessary state-to-state relations, especially with a country of such importance, that a dialogue was possible with the new self-proclaimed Soviet authorities. Honesty and historical truth require that this criticism be substantially corrected.
The President of the French Republic had at the time of his public intervention only incomplete information, including the analysis of the embassy. Mikhail Gorbachev, under house arrest in Foros in Crimea, could not communicate with the outside world. It is necessary to review the televised performance of the President of the Republic.
The latter, quite boldly, believes that the movement for freedom, initiated in 1985, will not stop here, whatever happens, and he clearly condemns the putsch. The main concern he expressed was for the security of Mikhail Gorbachev - and at that time also of Boris Yeltsin - and this may explain why he proceeded to read
11
out live on television, for which he was particularly reproached, a letter from the leader of the putschists, Gennadi Ianaev (see State Committee for the State of Emergency), affirming that he would continue with the policy initiated by Mikhail Gorbachev. Everyone knows what happened next. The ‘man in the street’ did not accept it and Boris Yeltsin was the incarnation of the resistance, perched on a tank in front of the White House, in a posture reminiscent of Lenin in Petrograd in 1917.
At that time, it was not easy to make sound judgments in the context of a Soviet Union that one felt was about to disappear. This would be replaced a few months later by the bubbling of a new Russia engaged in what was called a 'period of transition’, which is probably not finished.

As for the attitude of France in the first hours of the removal of the legal president of Russia, Mikhail Gorbachev himself publicly estimated years later that François Mitterrand probably did not have the right information and that in any case he had always considered him as his friend.
The embassy's chargé d'affaires managed to be on the plane that brought Mikhail Gorbachev and his family back from Foros to Moscow, while Kryuchkov, the head of the KGB, Iazov, the Minister of Defense, and Lukyanov, the Chairman of the Supreme Soviet, were under arrest at the bottom of the plane.
As for the thesis of a pact concluded between the Russian leader and the coup plotters, it developed especially when the affair turned out badly for the frondeurs.
Sixteen years later, in October 2007, I accompanied a French minister to Mikhail Gorbachev's home in the premises of his Foundation, together with the French ambassador. I made the mistake of telling him that I had arrived in his country for the first time a few days after the putsch against him was launched. He blushed, could not say a word, and finally turned on me, proof that his imprisonment in Foros remained a traumatic event. Did his feelings at the time remind him of the tsar and the imperial family in Yekaterinburg?
The paroxysmal moment of the putsch, which was over by August 22, had passed when I arrived in Moscow on September 12. I understood that my task was no longer to observe the Soviet Union as a fairly predictable actor in international relations in the context of an East-West opposition that had its codes and rules. The reference points became blurred when one had no direct knowledge of the country.

Would Erich Honecker's East Germany, where I had been stationed some ten years earlier, provide keys to understanding the great sister country, or would it have been nothing more than a lesson administered by a Germany obsessed above all by the development of interGerman relations in the perspective of reunification?
What did we expect from this huge country that was wobbling on its foundation? Didn't we hope too quickly that it would come closer to our European values? Didn't the fascination that Russian culture and arts had always exerted in Europe, and especially in France, contribute to create the illusion of proximity and of a rapid rapprochement? Were we ready to get out of the mental patterns of the Cold War and to accept, if need be, that there could be a way between the failure of communism, which was obvious in many respects,
13
and the excesses of capitalism, to which, moreover, all the peoples of the so-called free world did not necessarily adhere? Were we able to abstain from the geopolitical reflection, towards which Russia by its multiple dimensions and its own permanent fundamental questioning on its Eastern or Western destinyinherited from an old debate opposing since the 19th century slavophiles and Westernists - always leads us? The daily life of a population having to operate an incredible mental revolution, to rebuild most of the economic and social structures and to live simply without the anaesthetizing protection brought by communism, facing new hardships of the existence, largely responsible for the fall of Mikhail Gorbachev, would it not be finally the main emergency of the 90’s?
The classical recipes for approaching and understanding the end of the USSR were inoperative at the time. It was difficult to define a method, without reference points, without contacts while new heads were emerging.
A country of 22 million km2 was undergoing a prolonged earthquake. The physical impression was that the ground was shaking under our steps and was going to restore, at the end of a ‘Brezhnevian glaciation’, decades of buried energies. My first free time in Moscow was used to go and look for bullet holes on the walls of the White House. It would be even worse during the so-called transition period with the battle of the Parliament in October 1993, not to mention the first war in Chechnya, which would also mark a break with Mikhail Gorbachev's policy.
And yet, he had provided us with a compass when our compasses were going haywire. On December 7, 1988, in New York, before a UN General Assembly transformed into a rock star concert, where groupies were sitting on the floor and on the stairs because of lack of space, he announced the reduction of the Soviet armed forces by 500,000 men

in two years, including 50,000 in East Germany alone, the end of the Brezhnev doctrine on limited sovereignty and the end of the leading role of the Communist Party. Some people could not believe their ears and thought they heard Teilhard de Chardin talking about the omega point, but this was the roadmap that the last Soviet leader followed. In the movie theaters of New York, one could see The Russian House with Michelle Pfeiffer and Sean Connery while the Gorbachev concept of a ‘common European house »’ was being developed. Michelle Pfeiffer alone helped to remove the last reluctance. It was time to leave for Moscow.
A dramatic transition before and after the Putsch

The sequence of events during the last two years of the Soviet Union is known. We can briefly remember it.
The spring of 1990 was marked by the first death of Soviet communism: Mikhail Gorbachev was paradoxically ‘elected’ president of the USSR by the Supreme Soviet, while a short time earlier Article 6 of the Constitution on the ‘leading role’ of the Communist Party had been abolished by the Congress of Deputies on the proposal of the same Gorbachev, endorsed by the plenum of the Central Committee. In perfect keeping with the Soviet tradition of contrition and confession, it is the Communist Party itself that has allowed it to be put aside for good, but it will continue to exist as a dead star.
In the same way, and we are skipping a few steps here, it will be the Supreme Soviet of the USSR - which had been nothing but a shadow theater for months - that will formally ratify the end of the USSR on December 26, 1991.
In November 1990, Mikhail Gorbachev was attacked in the Supreme Soviet by conservatives.
15
He probably made the mistake of dismissing liberals who supported him in favor of them. In the new Security Council, six of the nine members, including Kryushkov, the head of the KGB, Pugo, the Minister of the Interior, Iazov, the Minister of Defence, and Janaev, the future head of the State Emergency Committee, would be putschists in August 1991. Mikhail Gorbachev was criticized by the West for a conservative turn, while Boris Yeltsin questioned his ‘dictatorial’ power and Shevardnadze, the foreign minister, resigned.
In January 1991, Lithuania was the first republic to want to leave the Union. Gorbachev said of this crisis that it was a ‘provocation behind his back to bind him in blood’. On March 17, he had a referendum on the maintenance of the Union ('renewed Federation of sovereign and equal republics’) adopted - in a way in response. Boris Yeltsin proposed to include in the same consultation the election of the Russian president by universal suffrage and he was actually elected on June 12.

The day after the putsch, the picture was bleak: the party was a defunct constellation; the presidential dyarchy was weakening the state; the state had even been brought down by the August 19 coup; the Union was disintegrating and Mikhail Gorbachev was desperately trying to save it with a new stillborn Treaty on the Union, scheduled for August 20, which would be precisely a major trigger for the putsch; the economy was in ruins and the population was disoriented, plagued by anxiety about the future that had replaced the reign of fear and terror.
Igumnov House at Zamoskvoreche
It was in this context that I arrived in Moscow from New York, but the Soviet ensemble could be another New World, in its own way, in a land of ancient culture and civilization. On that late autumn day, after the outburst of resistance around the White House a few weeks earlier, Gorky Street, since
renamed Tverskaya, led directly to the Kremlin. The dominant tan and ochre color of the season is also that of the walls of its enclosure. The citadel, although on a mound like all the Kremlins in the country, seemed to be buried, contrasting with the verticality of the American cities, as if to hide and resist the repeated flows of barbarians and conquerors who had wanted to dominate it. A cold dampness announced an early winter and a first impression of lethargy emerged. This slowed down time gave to the whole a very oriental tone.
The neighborhood of the French Embassy had various layers and architectures. The street that bordered the Igumnov House, the French residence, and led to the October Square from which Lenin's stature was never removed, was called Dimitrova after the Bulgarian communist leader. It would soon be renamed Yakimanka to recall that the district had been in the 19th century that of rich merchants, including Igumnov.
The latter had built a magnificent residence in the so-called Russian style, of which only a few remains in Moscow. And behind the embassy, adjoining the French Residence, which was an ochre stone building in Brezhnevian style, itself surrounded by the impressive building of the Ministry of the Interior adjacent to October Square, a charming historical district developed.
It was dotted with gardens and crossed by alleys, it housed many churches as well as the Tretiakov Gallery, a cenacle of Russian art with the most famous icons of Andrei Rublev, including the famous Trinity. One could have gotten lost, in the good sense of the word, if it had not also been crossed by straight streets, legacy of an ancient urban planning project. Such was the case with the Bolshaya Polianka or the Bolshaya
Ordynka, which was said to have been laid out so that the tsarinas could go directly from the Kremlin to the Novodevichy Monastery,

17
where the Metropolitan officiates today.
This district, one of the most fascinating in Moscow from the historical point of view, is called Zamoskvoretche, i.e. ‘beyond the Moskva’, from the center which is the Kremlin.
In 1991, the neighborhood was even more isolated from the hustle and bustle of the huge capital than it has remained relatively today. Stores or restaurants were rare and the general slump hit them. During my first weekend in Moscow, I experienced a food supply problem. The only bakery on the avenue was delivered on Sunday afternoon and a queue formed immediately. The only choice was between white and black bread and the quantities were quickly exhausted. As soon as this was the case, the curtain of the store was drawn while a queue persisted on the sidewalk.
Such was the daily life at the end of the Soviet Union, made difficult by the uncertainties of economic policy.
This failure was attributed to the country's leadership and contributed greatly to Mikhail Gorbachev's unpopularity and downfall. The ‘they pretend to pay us, we pretend to work’ could no longer find any counterpart in minimal state protection. The situation was serious everywhere. For example, families had to feed their relatives who were hospitalized and, even more, to provide medicines that had become rare and very expensive. Finally, Soviet people did not understand that the dismantling of the communist system did not immediately bring them the supposed benefits of capitalism. This expectation, legitimate after so many years of frustration, even deprivation, fed the political and social tensions of the so-called ‘transition period’ (Переходный период) of which the battle of the Parliament in October 1993 - which also had other causeswas a violent and paroxysmal moment.
My main responsibility at the embassy was to follow the internal changes underway, in tandem with

a colleague who was particularly in charge of what had been called ‘kremlinology’ until then. The latter, a French diplomat of Russian origin, was much more at ease than I was in this environment where his family still had ties. Thanks to his connections, his previous experience in the post and his mastery of the Russian language, he had facilities that colleagues from other embassies did not, which enabled us to attend, inside the Kremlin, sessions of the Supreme Soviet of the Soviet Union or debates in the new Parliament. The new stars of political life, such as Chokhin and Chubais, were performing there and we could approach them without any formality.
The strong impression I had was that I was living in the eye of a cyclone, about to disrupt the world and its international relations, and at the same time evolving in a sidereal void.

The expectation of our analyses coming from our central administration at the Quai d'Orsay
was legitimately great, but its counterpart, the MID or Ministry of Foreign Affairs, which was traditionally an entry point for foreign diplomats, was of no help to us.
Our Soviet colleagues, in fact, did not escape the turmoil that affected not only their daily life, but also their institution. How could they have helped us to understand what they themselves did not master and which surprised them at every moment? Moreover, they did not have vocation to deal with internal questions. The decay of the MID was felt like that of all the institutions of a regime in the process of collapsing. It was not until the appointment in 1996 of Evgeny Primakov as head of the Ministry of Foreign Affairs that this prestigious administration, which had always been full of first-rate talent, was raised, following the example of the deputy ministers Vitaly Tchourkine, in charge of questions of the former Yugoslavia,
19
or Sergei Lavrov, at the head of the Department of the United Nations and International Organizations.
I was soon to be put to the test. One morning in October 1991, my ambassador rushed into my office in a state of excitement that was not usual for him. He quickly explained to me that Mikhail Gorbachev, on his way back from the Madrid Conference on Middle East, would be received the same day in Latche in the Landes by President Mitterrand. I had only a few hours to take stock of the country's economic and social situation. Having arrived in the post a few weeks earlier, in the context described, I had the feeling that I was facing a Himalaya that would be difficult to climb. I tried at least to be clear, which was not the most difficult thing to do, since my knowledge was limited, and to be educational.
The picture I painted was bleak enough for me to advocate emergency aid, including food aid, through channels that could be those of what was then called the European Community. It seems that our Head of State paid attention to our analysis. Moreover, at the end of the talks, he publicly declared that ‘we had to help the Russians because they were Europeans’. This orientation seemed to me to be correct, in the measure of the difficulties of the Soviet Union at the time; on the other hand, I judged that the European character of Russia, a great question never decided by the Russians themselves, remained open.
If the period was marked by the decomposition of an old system, it was also that of a reconstruction all azimuths of many structures that we were going to discover with the ambassador one after the other. This great transformation took place at first rather calmly.

The putsch was behind us and the passage from the Soviet Union to Russia seemed to be done without apparent clashes. Nevertheless, Boris Yeltsin's leadership would soon become restless.
It is somewhat provocative to say, at least for an outside observer, that the end of the Soviet Union and the beginning of the transition were an exceptional and euphoric moment. Fear had disappeared with the gradual disappearance of the repressive apparatus and real contacts became possible. The climate would change with the ‘wild’ capitalism of the Yeltsin years, heralded by the ‘shock therapy’ of the Minister of Finance and then Prime Minister, Egor Gaïdar, and above all the policy of privatization, which in
reality led to the private appropriation of most of the national wealth by a few, later called ‘oligarchs’.

The homo sovieticus revealed good sides: a form of carefree attitude guaranteed until then by the society, a taste for culture, indifference to money, authenticity in human relations. As mentioned, Moscow was quiet with its disproportionately large Stalinist avenues, which were almost empty of traffic.
An underground society was beginning to reveal itself cautiously. I remember taking part in a dinner organized in a communal apartment by a Russian woman who was fond of contemporary art. She had collected the best of the country's pictorial production all her life. In the room where we were, hundreds of works of art were piled up and she began to exhibit them with caution. We were thinking that she was probably allowed to do so.
21
In any case, she later opened a gallery in New York that has since become very famous. Some social ascensions, for the most audacious and the most skillful, were thus lightning.

Seeds for change
In the political sphere, new faces would also quickly appear and impose themselves. I remember a dinner at the embassy in early October 1991, only two weeks after my arrival.
The people around me were complete strangers, but the host of the evening, the Deputy head of the embassy, had done a good job and had more than a flair for it.
To my left was a young man, both shy and fiery, who was working in an economic institute at the time. His. name was Egor Gaïdar.
Opposite me sat a man, also very young in appearance, who was also active in an economic and social research center. His name was Lopoukhine and he was to become head of the Ministry of Energy, a considerable responsibility, while Gaïdar would become Minister of Economy before being chosen at less than forty years old, in the land of gerontocracy, to become the head of Boris Yeltsin's government.
Two other more mature people were also our guests: Vladimir Lukin, who would become a member of Parliament in the Duma, Russian ambassador to Washington and rapporteur for human rights in Russia (ombudsman); Evgeny Saburov, who was already part of the short-lived post-putsch ‘government structure’ (NB: Committee for the Operational Management of the Soviet Economy headed by Ivan
Silaev) and would later be the de facto prime minister of Crimea even before its return to the Russian fold. All of them stood up, just after dinner, citing ‘work’ to be completed, but without indicating that they would be called to high office a few days later. The new Russia seemed to be made of both improvisation and a certain romanticism that would not last.
Boris Yeltsin must be credited not only with the courage to have resisted the putschists in Moscow - as did Mikhail Gorbachev, who refused to submit in the isolation of Foros - but also with the audacity of having chosen a Russian government whose average age was no more than forty years. The new ministers sometimes had the reverse side of their qualities by appearing somewhat disconnected from the deep realities of the country. Egor Gaïdar, for example, was an intellectual, the son of a great historian, who spoke in technocratic Russian to an often dazed audience of members of Parliament, as if he had used Harvard or Princeton English,

23
which he mastered also very well. He would have got a great success in American universities, but this provoked a particularly marked culture shock in this Duma. This bet on Russian youth was well founded. From the beginning I was impressed by the adaptability of the Russian youth and by the multitude of talents in a country with a high level of school and university education. This was an achievement of Soviet communism that must be recognized and facilitated the adaptation to a brutal transition. I was fascinated, for example, by the emergence of the banking system where young professionals were operating with the help of disciplines that were new to them, including a massive use of computers that seemed to me to be even ahead of those of practices in our societies. The steps were taken and skipped cheerfully.
This positive development was not free of serious obstacles inherited from the burdens of the previous system and the conditions of transition. In the end, Yeltsin faced the same obstacles as Gorbachev, but he approached them differently. His liberals were more focused on economic policy than on philosophical convictions; the conservatives were the same, but even more radicalized, understandably so, because of the shock therapy. Relations with the opposition gradually degenerated into direct confrontation.
In December 1992, the Parliament finally refused to grant confidence to Prime Minister Egor Gaïdar, whom Boris Yeltsin was unable to maintain; the President's second choice was the Secretary of the Security Council, Yuri Skokov, also without success.

Only Viktor Chernomyrdin, who had spent part of his career with the state-owned Gazprom and was looking like a Soviet apparatchik, was finally acceptable to the Duma. Chernomyrdin, who was only a third choice, remained Prime Minister from 1992 to 1998, i.e., for almost the entirety of Boris Yeltsin’s presidency. The first transition was thus embodied by a man who had responsibilities in the country's immobility.
 Patrick Pascal
Patrick Pascal
25
Former Ambassador in Moscow for Russia,Ukraine and Belarus
The opposition, even confrontation, of the executive and legislative branches was exacerbated by a serious constitutional crisis. Strangely enough, the constitution still in force in the new Russia was the Soviet constitution of 1977. It allowed the Duma to systematically challenge presidential decrees by legislating differently on the same issues.
I remember accompanying the President of the French Constitutional Council to the house of the President of the Parliament, the Chechen Ruslan Khasbulatov. Robert Badinter gave his interlocutor, himself a graduate of the Moscow Law Faculty, a masterly lecture on constitutional law. The debate was no longer legal, but political. Yeltsin's own vice-president, the very popular Alexander Rutskoi, a former hero of Afghanistan as a fighter pilot, sided with the opposition to the
executive of which he was a leading figure.
This was probably too much for the president, who, in October 1993, after an interminable and paralyzing crisis, solved the problem by calling in the tanks of the Department of the Interior's Special Forces. For a whole day, under my windows, the tanks poured their shells on the White House, causing gaping holes. The insurgents surrendered at the end of the day, but all night the building burned. The building was quickly wrapped - as Christo could have done - and several hundred Turkish workers were urgently called in to remove all traces of the confrontation within a few weeks.
How many victims were there? We will probably never know, but probably more in Moscow than during the civil war in the early years of communism.

The embassy doctor, a remarkable woman who had experienced Chernobyl, offered the authorities blood donations. She could not see any injured people as if there were none. The West practically turned a blind eye to this episode, which in the end was a form of acquiescence, if not encouragement, to the use of violence. It is not forbidden to think that the first war in Chechnya was part of this spiral.
The ‘Near Abroad’

Serious tensions arose beyond this part of Russian territory, in what was called the ‘near abroad'. The Abkhazian conflict in Georgia degenerated under Yeltsin's presidency. There were at least three identified decision-making centers in Moscow: the MID had appointed an ad hoc ambassador who was at the same time the president's special envoy; the
army had its own interests in the Black Sea area where high-ranking officers had holiday homes (NB: there are sometimes petty reasons for big stories). The arbitrations of the presidency, despite Ambassador Kazimirov’s efforts, with whom we were in regular contact, were never clear. Ukraine became a major problem as soon as the CIS was established on 8 December 1991. It seems that Ukrainian President Kravchuk was then willing to return Crimea to Russia, a possibility that Boris Yeltsin would not have seized in the euphoria of his rival Gorbachev's ouster. But there was almost more important than that in the relationship with Ukraine. The difficult dialogue with Kiev included the question of sharing the Black Sea fleet and the issue of millions of mixed families.
27
As Moscow was the heir to the Kievan Rus, the internal rift was considerable and would never be overcome. The vice-president Rutskoy had an article published one day on the front page of the daily press with a huge title: ‘I, Russian officer, of Ukrainian mother’. Everything had been said.
Not even Central Asia, which Mikhail Gorbachev had tried at all costs to keep in the bosom of the Soviet Union, supported in particular by President Akaev of Kyrgyzstan and even more so until the last days of his power by President Nazarbaev of Kazakhstan, has moved away from the center of empire. Since 1991, the French ambassador tried to meet, as much as he could, political leaders of the Central Asian republics when they were in Moscow. In addition to domestic politics, I was supposed to cover evolution of these republics and the ambassador introduced me in the

autumn of 1991 to President Islam
Karimov of Uzbekistan, underlining all the interest we had in his country which was to become independent. President Karimov (NB: at that time still president of the Supreme Soviet of his republic) pointed an almost vengeful finger at me, but he was actually talking to Russia, saying:
‘Come to Tashkent, you will see the real Uzbek realities and not the turpitudes that are described in the Soviet press!’. The tea towel was already burning.
I did visit Uzbekistan several times in the following months, but in a private capacity. Almost twenty-five years later, President Karimov, a few months before his death, came on an official visit to the Central Asian country where I was ambassador. In accordance with protocol, I had to greet him and could then exchange a few words.
I reminded him of the meeting at the embassy in Moscow so many

years earlier without mentioning the quoted phrase in full, and told him that I had visited his country several times as he had urged me to do. In the evening, after the state dinner, he broke with protocol and came towards me to thank me effusively for my visits, proof if it were still needed of the strength of an exacerbated Uzbek national feeling. In the case of Uzbekistan, it was necessary to take into account the fact that the main demographic weight and focus of Islam in Central Asia had been suppressed under Soviet communism.
New Russia and Far West/East
The Day Before probably did not end with the departure of Mikhail Gorbachev, but rather during Boris Yeltsin’s first years of the transition period. Faced with the same problems as his predecessor, but with a different temperament and different principles, the president of Russia enjoyed greater support
29
from the Western world. Mikhail Gorbachev, desperate because of the failure of his economic policy (see ‘500 Days Program’), was bitter when he realized at the G7 meeting in London, where he was invited in June 1991, that it was easier for President Bush Sr. to finance his Gulf War than to help Russia. Margareth Thatcher, who had always supported Mikhail Gorbachev since 1984, as well as President Mitterrand, had tried to weigh in on his behalf, but largely unsuccessfully.
There had been Western economic advisers in the Russian ministries. They had encouraged a policy of free trade and thus a lifting of customs protection. Such a policy turned out to be disastrous, as Russia, lagging behind in many technological developments, was not able to face international competition. This contributed to the collapse of its industrial production.
This was the view of French experts, including a former CEO of Renault, who had been a consultant in connection with the privatization of the ZIL factories (Завод имени Ленина or Lenin factories) known for their trucks and huge black official limousines. The latter had told me:
‘The Russians did not listen to us a year ago, but now they have understood’. It was late, but it is true that Boris Yeltsin had been able to draw shortterm benefits from his opening to the West. He was immune to criticism from outside and benefited from billions of dollars from the IMF and other Western aid, without which his re-election in 1996, against the communist Gennady Zyuganov, would probably not have been possible.
Even more seriously, during the campaign for his re-election in 1996, Boris Yeltsin was led to conclude a ‘Faustian’ pact

with those who began to be systematically called ‘oligarchs’. Privatization, in the sense of the appropriation of national wealth by a few, was then completed. From then on, there was effectively no more Soviet Union, but no more state capitalism, which would have been preferable for the community. There was almost nothing left of the Gorbachev years, a parenthesis between two systems.
The Day After began and it is not over yet. Russia will one day have to question itself in depth, ‘rehabilitate’ in a way Mikhail Gorbachev and beyond that continue its duty to take stock. The banning of the NGO Memorial inquiring on
crimes of Stalinism era at the end of 2021 is a worrying signal in this respect. Albert Camus wrote in L'Homme révolté that the end does not justify the means you resort to. On the contrary, the nature of the means often determines the end.

31
As for us, don't we have our responsibilities in what Russia has become? Have we not been too complacent about internal political violence that can never lead to democracy? To have relativized a war, like the one in Chechnya, could only facilitate another one, and even others.
Mikhail Gorbachev was uncompromising on principles, and this is above all what makes him great. Criticism of the state, which is paradoxically sometimes weak compared to forces superior to it, is not enough. Who actually governs Russia? After ten years spent in the country, in one capacity or another, I personally could not answer with certainty.
Isn't the problem of Russia first and foremost that of a Republic to be built - in the sense of a more balanced distribution of wealth - before thinking of a full democracy?
Depending on

the answer that is given, the nagging question of Russian history about the Western or Eastern nature of the country will be resolved by itself. These are the stakes of The Day After.
The third disappearance of Mikhail Gorbachev
Mikhail Gorbachev died politically in Russia the first time for not having succeeded in transforming the Soviet system, which under Boris Yeltsin became a predatory oligarchy replacing the communist state. The recent Putin years, characterized by a marked opposition to the West, which culminates today with the war in Ukraine, are at the antipodes of Gorbachev's conception of international relations. Mikhail Gorbachev was also struck down by these events, and the day of his death, which affects us deeply, was not the day of his rehabilitation in his home country.
But let’s hope that Russia is not only violence, autocratic power, servile submission and even political crime in the tradition of a ‘classical’ mode of devolution of power. The personality and work of Mikhail Gorbachev alone are enough to show this. The last president of the USSR was accused of weakness in relation to the West in his own country, and the turn that he took in favor of the persistent conservative current - which provoked the resignation of his foreign minister, Eduard Shevardnadze - and of personalities who were to be found among the coup plotters of August 1991, also fueled criticism of his supposed naiveté.
Mikhail Gorbachev in fact came up against the resistance of the system, he had to face drastic transformations but he freed himself from what Barack Obama, years later, had called for
the President of the United States the ‘Washington playbook’ leading inevitably to external interventions. He rejected a ‘Moscow playbook’ of rules for the systematic use of internal repression and the control of centrifugal forces outside. If any Nobel Prize has been deserved, it is the one awarded to Mikhail Gorbachev.
François Furet, the great historian of the French Revolution, wrote Le Passé d'une illusion (The Past of an Illusion), a major work on the communist movement in the 20th century. The years of Mikhail Gorbachev's power could be characterized as the ‘Past of a Normality’. Indeed, during the very last phase of the Soviet Union - and this was undoubtedly the major fact of the Gorbachev ‘era' - fear had disappeared in society. Many of those who benefited from it blame him

33
for the fact that it also gradually disappeared for Russia's external partners as a result of a peaceful coexistence that was no longer a matter of mere ‘declaratory’ diplomacy, as in the good old days of the USSR.
Mikhail Gorbachev was never a czar in his politics, and he retained the almost dull appearance of a Politburo member, right down to his provincial accent from the grain-growing region of Stavropol. But the relapse came quickly and abruptly, and Boris Yeltsin did not cease to mention, during his presidency, his country's aspiration for ‘normality’, which was probably again cruelly lacking.
Mikhail Gorbachev thus demonstrated that another Russia than the one with the hideous face of revenge, hatred and aggression is possible. Yes, Russia, which is the largest country in the world in terms of size, from the immense plains of the continent to
the shores of the Pacific, can have a European destiny. In fact, it has no other if it wants to be a significant player on the international scene, or even a power, an aspiration from which it has never detached itself in its history. But Russia will have to make choices, an introspection on its identity that has been postponed for too long, from imperial autocracy to the anachronistic one of Putin's power, without forgetting to proceed to a real ‘de-Stalinization’, of which the 20th Congress of the Communist Party of the Soviet Union in 1956 had only been a camouflage.
Like the communism analyzed by François Furet, Gorbachev's policy also consisted of an ‘illusion’ of the transformation of the Soviet system. As for the ‘normality’ - and this is a contradiction in terms - so rare in the world of autocracy, it will have been a reality, even if it was an ephemeral parenthesis.

«

will have been
builder, will have opened a door, even if it is a thin gap, not only in the imposing wall of the Kremlin, but also in the minds of people who will finally escape amnesia ». PP
35
The question is whether this forgotten mark will become a reference again, whether Mikhail Gorbachev
a bridge-
PATRICK PASCAL
Former Ambassador, Former President of ALSTOM Group in Moscow, Founder and President of "Perspectives Europe-Monde" Knight of the National Order of Merit. ALSTOM President in Moscow for Russia, Ukraine, and Belarus. PASCAL’S diplomatic career has focused on strategic issues, East-West and NorthSouth, the UN, the Arab world, Europe, and Central Asia, during his postings in Berlin, Rome, New York, Moscow, Riyadh, Damascus, London, and Ashgabat.
• Ministry of Foreign Affairs, Political Affairs Division, United Nations and International Organizations.
• Permanent Mission of France to the United Nations, New York.
Cabinet of the Minister of Foreign Affairs, Paris.
• Ministry of Foreign Affairs, Political Affairs Division, United Nations and International Organizations.

• Embassy of France to the GDR, East Berlin.
• Ministry of Foreign Affairs, Directorate of Political Affairs, Strategic Affairs and Disarmament.
Publications :
- Journal d’Ukraine et de Russie, les crises and l’évolution du système international, VA Éditions, 2022.

Academic background:
- Sciences Po Paris, Institut National des Langues et Civilisations Orientales, Sorbonne, Universität des Saarlandes, Rheinische


Friedrich-Wilhelms-Universität Bonn.










Inspiration
Einstein theorized that mass is swappable with energy. Assuming, he’s right, this would imply that nations could one day learn how to swap some of their mass-based (i.e. kinetic) defense systems with energybased (i.e. non-kinetic defense) systems for applications related to physical security and national defense. Modern militaries already utilize both cyber and electronic defense systems, but perhaps there is some other type of defense technology that could combine electric and cyber defense systems together into an electro-cyber form of defense technology. If true, then perhaps one day society will learn how to utilize this special type of technology as a “soft” form of warfare to resolve international policy disputes, establish dominance hierarchies, defend property, rebalance power structures, or even mitigate threats associated with “hard” warfighting, such as nuclear escalation.

"We cannot abolish war by outlawing it. We cannot end it by disarming the strong. War can be stopped, not by making the strong weak but by making every nation, weak or strong, able to defend itself. If no country can be attacked successfully, there can be no purpose in war”
-Nikola Tesla-
43
Electro-cyber warfighting is not a new idea; it's at least 123 years old. In 1900, Nikola Tesla hypothesized that society would eventually develop such destructive kinetic power that humanity would face a dilemma and be compelled out of existential necessity to fight their wars using human-out-ofthe-loop "energy delivery" competitions. He believed humans would eventually invent intelligent machines that would engage in electric power competitions to settle humanity's disputes, while humans observe from afar. Other titans of the American industrial revolution had complementary ideas about using electricity to mitigate the threat of war.
In 1921, Henry Ford (while reportedly standing with Tesla's rival, Thomas Edison) claimed society could eliminate one of the root causes of warfighting by learning how to create an electric form of currency that bankers couldn't control.
Both Tesla and Ford saw potential in the idea of using electricity to either eliminate a root cause of warfare

or eliminate a root cause of warfare's associated destruction and losses. However, neither were successful at building the technology required to test or validate their hypotheses. This could have been because both theories predated the invention of "intelligent machines" a.k.a. general-purpose, storedprogram computers.

Both Tesla and Ford's theories predate the popular theoretical framework we call "computer science" and the development of the abstraction we call "software."
This thesis was inspired by the following question: what if Tesla and Ford were both right, and they were both describing the same technology? What if Ford's theory is valid, and it is indeed feasible to mitigate a root cause of warfare by converting electricity into monetary and financial information? What if Tesla's theory is valid, and the future of warfare does indeed involve “intelligent machines” competing
45
against each other in human-out-of-the-loop energy competitions? Would this technology not reduce casualties associated with traditional kinetic warfighting? If it did, would this technology not be worth every watt? Assuming Tesla's theories were valid, then what might "soft" warfighting technology look like? How might this technology impact or re-shape agrarian society's social hierarchies and power structures after spending well over 10,000 years predominantly fighting "hard" or kinetic wars? If Tesla's "intelligent machines" are in fact computers, then wouldn't their power competition be dictated by a computer program? Maybe humanity's "soft" and futuristic form of electro-cyber warfare would take the form of an open source "softwar" computer protocol. And because nothing like it has ever been seen before, maybe nobody would recognize it. This concept is illustrated in Figure 2.

A "softwar" protocol could theoretically utilize society's internationally-dispersed, global electric power grid and existing internet infrastructure to empower computers to impose severe, physically prohibitive costs on other computers in, from, and through cyberspace. It could combine Tesla's and Ford's ideas together and serve as both a "softwar" protocol and a monetary network. There's no logical reason to believe it couldn't serve both functions simultaneously, considering how the development and expansion of all technologies need financing - especially defense industrial complexes.
Here's an even more compelling idea: Maybe "softwar" technology already exists and nations are already starting to adopt it.
Maybe this new form of power projection technology is already demonstrating how it can empower every nation, weak or strong, to physically secure their interests like never before, thus fulfilling Tesla's prediction.
Perhaps this electro-cyber warfighting technology is hiding in plain sight, but people don't recognize it yet because they are mistaking it for a peerto-peer electronic cash system.
Finally, perhaps all it will take for society to recognize that they're entering a completely new and transformational paradigm of non-lethal warfighting is simply a different point of view.
To that end, the author presents this thesis.
47
This image illustrates the bottom line of this thesis, which is that Bitcoin isn’t strictly a monetary protocol. Instead, Bitcoin appears to be emerging as a cyber power projection tactic for the digital age. While most software can only logically constrain computers, Bitcoin can physically constrain computers and impose severe physical costs (as measured in watts) on belligerent actors in, from, and through cyberspace. Bitcoin’s global adoption could therefore represent a revolutionary approach to cyber security and could dramatically reshape how modern society secures their most valuable digital resources.
There are five different ways that machinery can be used to impose severe physical costs on others in, from, and through five different domains. The image at the bottom shows the specialized machinery that is currently being used to keep special bits of information called “Bitcoin” secure against belligerent actors.
Figure: Five Ways to Impose Severe Physical Costs on Attackers in Five Different Domains

Bitcoin could represent a strategically vital national security technology for the digital age. However, the American public may not understand why Bitcoin has the potential to be so strategically important because they don’t appear to understand the complexity of (1) the computer theory behind the design concept called “proof-of-work,” (2) modern power projection tactics, (3) the function of militaries, or (4) the profession of warfighting. If the theories presented in this thesis prove to be valid, then the American public’s lack of understanding about these core concepts could jeopardize US national strategic security.
The future of US national strategic security hinges upon cyber security, and Bitcoin has
demonstrated that “proof-ofwork” functions as a new type of cyber security system.
Nations appear to be waking up to the potentially substantial strategic benefits of Bitcoin and learning that it could be in their best strategic interest to adopt it (hence Russian’s recent 180-degree pivot to supporting Bitcoin). Another cold war could be kicking off, except instead of a space race, it could be a cyber space race. As is often the case with the emergence of any new power projection technology, speed of adoption may be critical.
If the US does not consider stockpiling strategic Bitcoin reserves, or at the very least encouraging Bitcoin adoption, the author believes the US could forfeit a strategically vital power projection technology lead to one of its greatest competitors and set itself back in global power dominance.

The current approach that US leaders are taking to analyze the potential risks and benefits of proof-of-work technologies like Bitcoin could therefore represent a threat to US national security. It is particularly concerning that US policymakers have arbitrarily chosen to categorize Bitcoin as “cryptocurrency” and tacitly allow institutions with conflicts of interest to claim to be experts in proof-of-work technology. These institutions could use their misperceived expertise to influence public policy making efforts for their own benefit, compromising US national strategic security in the process.

Computer scientists have been researching proof-of-work protocols for over 30 years –that’s more than twice as long as Bitcoin has existed. Since the beginning of this research endeavor, it was hypothesized that proof-of-work protocols could serve as a new type of
cyber security system that could empower people to keep computer resources (namely their most valuable bits of information) secure against hacking and exploitation simply by imposing severe physical costs (in the form of computer power) on belligerent actors trying to access or interfere with that
51
information. In other words, computer scientists rediscovered what military officers have known about physical security for thousands of years: to stop or deter bad guys from doing bad things, make it too physically expensive for them to do those bad things.
While academia theorized via formal academic channels about how proof-of-work could work, software engineers and “doers” like Adam Back, Hal Finney, and Satoshi Nakamoto designed, built, and deployed several operational prototypes via informal, non-academic channels. Today, Bitcoin has emerged as by far the most globally-adopted proof-of-work cyber security system to date.

Bitcoin is so physically powerful in comparison to other open-source proof-of-work protocols that a popular mantra has emerged, initiated by technologist Michael Saylor (MIT ’87): “There is no second best.”
But what could Bitcoin possibly have to do with warfare? To understand this connection, one must recall the primary function of militaries.
Sovereign nations have a fiduciary responsibility to their people to protect and defend access to international thoroughfares (e.g. land, sea, air, space) to preserve freedom of action and the ability to exchange goods with other nations. When a nation intentionally degrades another nation’s freedom of action or ability to exchange goods across these thoroughfares, that activity is often considered
to be an act of war. Militaries exist explicitly to protect and defend people’s access to these thoroughfares. The way militaries accomplish this is by imposing severe physical costs on those who try to deny access to these thoroughfares or impede a population’s ability to exchange goods across them.
Military branches are categorized based on the thoroughfare they assure access to and preserve freedom of action in. Armies assure access to land. Naval forces assure access to the sea. Air forces assure access to the sky. Space forces assure access to space. Regardless of the domain to which access is secured, each service effectively works the same way: preserve the nation’s ability to utilize each thoroughfare by imposing severe physical costs on anyone who impedes or denies access to it. Physical power is used to stop and deter belligerent activity in, from, and through these thoroughfares.

The more physically powerful, motivated, and aggressive a military is, the better it usually performs. The more a military service can utilize technology to project power in clever ways, the more effective it is at its primary value-delivered function.
One of the most strategically important thoroughfares of the 21st century is colloquially known as “cyberspace.” It is of vital national strategic Interest for every nation to preserve their ability to exchange a precious resource across this thoroughfare: valuable bits of information. Just like they already do for land, sea, air, and space, sovereign nations have both a right and a fiduciary responsibility to their people to protect and defend their access to this international thoroughfare called cyberspace. If a nation were to intentionally degrade another’s freedom of
53


action or ability to exchange valuable bits of information in cyberspace, that activity would likely be interpreted as an act of war, as it would in any other domain.

Until Bitcoin, nations have not had an effective way to physically secure their ability to freely exchange bits of Information across cyberspace without resorting to kinetic (i.e. lethal) power.
This is because they have not had access to technology which enables them to Impose severe physical costs on belligerent actors in, from, and through cyberspace.
This appears to have changed with the discovery of open-source proofof-work technologies like Bitcoin – a complex system which empowers people to physically restrain belligerent actors. This technology works, and adoption has already scaled to the nation-state level. Thanks to proof-of-work protocols like Bitcoin, nations can now utilize special machinery to impose severe
physical restrictions on other nations in, from, and through cyberspace in a completely nondestructive and non-lethal manner. This capability has the potential to transform cyber security by enabling computer networks to
run computer programs which don’t give a specific group of users special or unimpeachable permissions over the computer network and entrusts them not to exploit those permissions.
With the ability to impose severe physical costs on users through cyberspace, zero-trust computer
networks (and a new type of internet) can now be designed where users can have their special permissions physically revoked if they abuse or exploit them. The first computer network to prove this design concept appears to be the network of computers utilizing Bitcoin. Bitcoin is proof that proof-of-work works.
At its core, Bitcoin is a computer network that transfers bits of information between computers using a zero-trust physical security design.
As previously mentioned, bits of information can represent any type of information, including but not limited to financial information that might be used to support international payments and financial settlements. It makes perfect sense that a proof-ofwork computer network’s first use case would be to physically secure the exchange of vital financial bits of information, but that is clearly not the only

use case. This technology could have far wider-reaching applications, as there are many other types of precious information that society would want to physically secure in the information age.
To that end, Bitcoin could represent the dawn of an entirely new form of militarygrade, electro-cyber information security capability – a protocol that people and nations could utilize to raise cyber forces and defend their freedom of action in, from, and through cyberspace.
The bottom line is that Bitcoin could represent a “softwar” or electro-cyber defense protocol, not merely a peer-to-peer electronic cash system. The author believes proof-of-work technology could change the future of national strategic security and international power dynamics in ways that we have barely started to understand.

Copyright © [2023] Jason Lowery. All rights reserved.

LOWERY BEST SELLING AUTHOR OF SOFTWAR
MAJOR JASON P.

MAJOR JASON P.
LOWERY is a Department of Defense (DoD) sponsored US National Defense Department of the Air Force Fellow, MIT System Design and Management Fellow, Astronautical Engineer, and active-duty field grade officer in the US Space Force (USSF).
Prior to attending MIT, Jason served as the Director of Operations for the USSF Second Space Launch Squadron. Before that, he was a founding member of the cadre of officers who stood up USSF, serving as the Deputy Chief of the Commander’s Action Group for USSF Space Operations Command and US Space Command (USSPACECOM) Combined Force Space Component Command (CFSCC).
Jason transferred into USSF from the US Air Force (USAF), where he served as an allsource intelligence analyst and subject matter expert in electronic warfare, blast and ballistics effects, and space weapon system design.
Jason has a decade of experience serving as a Technical Advisor for US senior officials, to include the Office of the President of the United States (OPOTUS), Office of the Secretary of Defense (OSECDEF), and the Office of the Director of National Intelligence (ODNI). He has a Master’s Degree in Astronautical Engineering from Air Force Institute of Technology, Ohio and a Bachelor’s Degree in Mechanical Engineering from Baylor University, Texas.

We at Inner Sanctum Vector N360™ want to express our deep admiration and respect for the courage and determination that the people of Ukraine have shown in the face of adversity. We know that you are facing immense challenges every day and you have shown incredible resilience in the face of political, economic, and social turmoil. We want to assure you that we stand with you in solidarity and support. We are committed to using our platform to amplify your voices, share your stories, and raise awareness about the struggles that you are facing. We believe that by working together, we can build a brighter and more prosperous future for all. In the midst of darkness and uncertainty, we see hope and possibility. We know that the people of Ukraine have the strength and determination to overcome any obstacle, and we are proud to stand with you on this journey.

 Linda Restrepo Editor | Publisher
Linda Restrepo Editor | Publisher


63
DIGITALIZATION OF


THE SOCIAL SPHERE OF UKRAINE CONTINUES EVEN IN THE CONDITIONS OF A

FULL-SCALE INVASION
Kostiantyn

Koshelenko Uliana Tesliuk
Digitalization of the social sphere of Ukraine continues even in the conditions of a fullscale invasion
Over the past 20 years, Ukraine has been trying to digitize social services and the social sphere in general in an unsystematic way. Over two decades, there have been 3 attempts to unify all registers and databases, but organizational, budgetary and technical difficulties have prevented this from being successfully implemented three times.

Only with the beginning of the wave of digitalization within the country with the election of President Volodymyr Zelensky and Vice Prime Minister Mykhailo Fedorov and the adoption of the Social Sector Digitalization Strategy in 2021, a citizen-oriented systematic digitalization of social services and benefits was launched. This direction is now being developed and implemented by the digital team of the Ministry of Social Policy, headed by Kostiantyn Koshelenko as CDTO - Deputy Minister for Digital Development, Digital Transformation and Digitalization.
In 2021, the development and implementation of the Unified Information System of the Social Sphere (hereinafterUISSS) was launched. UISSS provides extraterritoriality and automation of service provision. As a result, citizens can apply online or in person to any social protection department regardless of their place of registration, which they could not do before because they were linked to the districts of their place of registration. In other words, we are changing the philosophy of providing social benefits and services, making them more accessible, transparent and effective.
On slide 1, you can see on the left how the social sphere worked before the UISSS implementation, and on the right how it is already starting to work now.
At the beginning of 2022, we approved an annual plan for the digital transformation of the social sphere, where we identified the most popular social benefits that were
prioritized, but due to Russia's full-scale invasion of Ukraine, we had to change the focus of digitalization. Due to the large number of internally displaced persons, we needed to provide IDPs with the necessary services, such as obtaining an IDP certificate and financial assistance for living from the state. We also had to do everything possible to ensure that Ukrainians in need of support could get help not only from the state, but also from international humanitarian organizations and benefactors from around the world.
In April 2022, we were able to stabilize the situation and resolve urgent issues, which allowed us to gradually return to the approved action plan.
In this article, we will talk about some of the most significant results of the digitalization of the social sphere of Ukraine.

Interaction of the UISSS with the unified portal of public services Diia provides Ukrainians with effective remote access to social services.
In particular, the opportunity to apply for IDP housing assistance through the 67


Diia app has been implemented, which has been used by more than 1.4 million Ukrainians since the beginning of the full-scale invasion. We also introduced a service for quick change of residence and deregistration of IDPs online. During the first day of the service, more than 20,000 people used the Diia app to change their temporary residence address or deregister as IDPs.

All this was realized thanks to information exchanges between UISSS and Diia. For citizens, this means that the appointment, accrual and
assistance for IDPs are carried out centrally and consistently all over Ukraine. In turn, for the state, the human factor has been reduced, processes have been automated, and corruption risks have been decreased. The second important block was the digitalization of some adoption services, as a large number of children were left without parental care due to the war. It was important for us to speed up the adoption mechanism. We cannot shorten the adoption process, because there are quite important aspects, such
as training for future adoptive parents. However, we were able to speed up the process of submitting documents. On the Diia portal, it is possible to apply for an adoption consultation, an application for candidacy for adoptive parents, and more. With these services, citizens do not need to stand in lines and get one document to get another - all the necessary documents can be obtained or uploaded to Diia.
We continue to bring services to the portal and the Diia app. For example, we are currently betatesting four benefits for families with children. These include assistance to parents who have adopted a child, persons caring for a sick child, persons with childhood disabilities and parents of children with disabilities, and single mothers or fathers who are not married. Therefore, thanks to digitalization, we are making social services more modern and convenient online, but we are keeping them accessible to those who wish to apply offline.
The eDopomoga platform as a response to humanitarian challenges.
Since the beginning of Russia's full-scale invasion, Ukrainians have been forced to move to safer places, hiding from missiles, shelling and the actions of the Russian occupiers to save the most important thing - their lives, the lives of their children, parents and relatives. Many people lost their homes and all their property from rocket and hail strikes. Some have lost their jobs. It's really hard to lose everything you have in one moment, to lose your points of support, your own home, to leave your hometown, and for some people to start building everything from scratch.
While working on programs to support people affected by the war, the Ministry of Social Policy of Ukraine faced a request from volunteers to help conveniently and easily from any country in the world.

71
Therefore, the Ministry of Social Policy, with the support of the Ministry of Digital Transformation, the United Nations Development Program (UNDP) in Ukraine, with financial support from Sweden and the World Bank, created the humanitarian platform eDopomoga https://edopomoga.gov.ua/.
First, eDopomoga was launched as a volunteer platform where anyone can support Ukrainian

families from any country in the world. Later, the platform received two more areas: financial assistance from the state (eDopomoga state) and payments from international organizations (eDopomoga international). Each direction has the task of helping people cope with the challenges of today, namely to receive support both in cash and in kind - food, medicine, hygiene products, clothing, fuel, etc.
The eDopomoga Volunteer platform has changed people's perceptions of charity and created a habit, even a need, for most of the platform's donors to help others on a regular basis. When you don't just transfer a percentage of your income to a charity, you choose whom you want to help and decide how and how much you want to help on the platform. We are in no way encouraging you to refuse to make donations to charities whose work is important, but we suggest that you try to help through eDopomoga online and
and feel that it is a completely new experience in charity.
First, for a person in need, it is an opportunity to submit an application online and receive support in the form of a certificate (similar to a gift certificate) for medicines, food or fuel. The certificate is sent online in the personal account on the platform and via SMS, and the person can choose the product they need today in partner retailers. For example, if an applicant on the platform asked for help with cereals and oil, but received a certificate only a week later, when he or she needs other products, he or she can buy meat, eggs, etc. The person can choose what they need. We preserve their dignity and leave them the right to choose the right product.
Secondly, for the benefactor, it is an opportunity to choose whom and how to help and choose the amount of assistance. And after the person uses the certificate, they receive a check from the partner network, which is a report on the use of charitable assistance.
The statistics are stored in the benefactor's own account, and for those who want to see the whole picture, there is analytics. Transparency, targeting, and accountability for benefactors are ensured.

Thirdly, it is an opportunity not only to support people in need, but also to support the entire supply chain, starting with the producers of goods.
eDopomoga volunteer in numbers as of March 27, 2023 looks like this:
● 4,708 donors, including 642 foreign donors living in 50 different countries. The top 10 benefactor countries include the United States, the United Kingdom, Germany, Canada, Latvia, Poland, France, Finland, Sweden, and Australia.


75


77
● more than 175 thousand certificates for online assistance paid by benefactors, which allowed 27 thousand families to receive assistance in the amount of more than $206 thousand.
eDopomoga international is also a new culture of aid for both Ukraine and most humanitarian organizations. It emerged as a solution to a number of problems of international organizations in providing financial assistance to Ukrainians.
eDopomoga international has strengthened the interaction of the state with international organizations and provided a convenient mechanism for collecting applications, verifying the data and deduplicating payments. This was made possible through information exchanges between eDopomoga and the Unified Social Information System, which is the foundation for the digitalization of social services. It is this area of financial assistance from
international organizations that has ensured the receipt of a large number of applications from people in need of support and powerful targeted financial assistance from organizations.
.
eDopomoga international in figures as of March 27, 2023 looks like this:
• 10,000,000 applications from Ukrainian citizens were collected in the first 3 months,
• 3,189,864 people were included in the lists for the payment of financial assistance to international organizations,
• more than $158 thousand was paid according to the lists submitted to international organizations. Therefore, eDopomoga volunteer and international directions are designed to provide targeted support and to be a transparent and reliable government link between the benefactor and the beneficiary of financial assistance.

.
By the way, on the eDopomoga International platform, we have launched a dashboard that allows international organizations to see the analytics of financial aid receipt in the context of many filters.
eDopomoga state is one of the three areas of the platform that provides step-by-step information on how to get help from the state. It has been useful for more than 1.5 million people looking for information on how to register as internally displaced persons and receive accommodation allowance; how to receive unemployment benefits; how to report damaged property due to Russia's military aggression, etc. We were able to collect up-to-date information from the state on the most popular benefits in one place. .
By the way, the platform's significance has been recognized internationally, with eDopomoga receiving the Go Global Awards 2022 from the International Trade Council in the category of Technology Innovation of the Year. PaySpace Magazine Awards 2022 in the nominations Best Fintech Startup and Best Techfin Project. Resilience Award Ukraine 2022 from Mastercard. Ukrainian Fintech Awards in the nomination Fintech New Product of The Year 2023. For our team, these awards have become a confirmation of the right direction of our efforts and a reason to increase attention to Ukraine and Ukrainians. Join us in supporting Ukraine in any way you can! Join our future victory and peace building!

“People don't really believe in words. Or rather, people believe in words only for a stretch of time. Then they start to look for action” .
“It's a victory when the weapons fall silent and people speak up. ” Volodymyr Zelensky


KOSTIANTYN KOSHELENKO is a Deputy Minister of Social Policy of Ukraine for Digital Development, Digital Transformations and Digitalization. He has over 15 years of professional experience in public service, retail, banking and fintech.
While working at the Ministry of Social Policy, he focused on the implementation of the new Unified Information System of the social sphere, which replaces the disparate systems that have been in operation for decades.
During the full-scale invasion, he initiated the development and implementation of the Ukrainian humanitarian platform eDopomoga, which is used for: providing monetary assistance to internally displaced persons from the state (state eDopomoga); receiving and providing volunteer assistance (eDopomoga volunteer); and financial assistance from international organizations (eDopomoga international) for vulnerable categories of the population.


ULIANA TESLIUK is a 3rd year bachelor's student at the Educational and Scientific Institute of International Relations Taras Shevchenko National University of Kyiv, working as a junior marketer at the Information and Computing Center of the Ministry of Social
Policy of Ukraine State Enterprise. Successfully completed an internship at the Ministry of Social Policy of Ukraine in the summer of 2022. Since September 2022, she has been working on promoting the eDopomoga platform.


China Has Woken By Linda Restrepo





HAS BECOME A REALITY

About 200 Years ago Napoleon Bonaparte warned the World when he said: “China is a sleeping Giant, Let her sleep. For when she wakes, she will shake the World”.



China's rapid rise as an economic superpower and its growing influence in global affairs have caused apprehension among many democratic nations. In recent years, there has been a growing debate about whether China has the ability to replace the United States as the world's dominant superpower. While there is no consensus on this issue, it is clear that China is seeking to expand its influence and reshape the global order to better serve its interests.
To an extent China has emulated the three key factors which enabled the United States to lead the post-World War II international order.
These factors were the ability to convert economic might into political influence, the maintenance of an innovation advantage, and the capacity to shape international institutions and set the rules of global conduct.
political influence, is something China has already pursued for several years. China has emerged as a significant economic power in recent years, and its economic growth has been accompanied by increased political influence.
China has used its financial leverage to shape global institutions and promote its interests, such as the Belt and Road Initiative, which seeks to build a network of infrastructure projects across Asia, Africa, and Europe.
The second factor, maintaining an innovation advantage, is also where China has invested heavily. China has made significant strides in artificial intelligence, quantum computing, and biotechnology. The Chinese government has made research and development a priority. It has invested heavily in education and technology infrastructure to support innovation.

The first factor, the ability to convert economic might into
The third factor, the capacity to shape international institutions and set the critical rules of global conduct, is perhaps the most challenging for China.
The current global order was primarily shaped by the United States after World War II, and the United States has played a crucial role in maintaining and enforcing the rules of the international system. China, on the other hand, has been a more reluctant participant in many of these institutions and has been critical of some of the rules and norms that have been established.
However, China has been taking steps to increase its influence within existing institutions and to establish new institutions that reflect its priorities and values. For example, China has been seeking to expand its voting power in the International Monetary Fund and the World Bank and promoting establishing new institutions such as the Asian Infrastructure Investment Bank.

TECHNOLOGY
Giancarlo Elia Valori, School of International Studies in Beijing, China, and President of the International World Group, gives
us a World Exclusive insiders look into AI in the Forbidden City. According to Valori, “AI has reached the peak of China's national strategy and has shown the need to learn from the advanced Western countries’ research practices to discuss, launch and implement the national plan.”
“A large number of repatriated experts sent by China to study AI abroad have become the cornerstone and the academics of research and development on the subject and are also extremely important for the industrial application and training of a new generation of teachers and professors.”
- Giancarlo Elia Valori -
Both China and the United States are leaders in technology and AI, and it is difficult to say which is ahead. Both countries have made significant investments in these fields and have developed some of the world's most advanced technologies.
95
In certain areas, such as AI research and development, China has made rapid progress and is rapidly closing the gap with the United States. Chinese companies such as Baidu, Tencent, and Huawei are now at the forefront of AI research and development and are making significant contributions to the field.
However, the United States continues to lead in other areas of technology and innovation, such as semiconductors, software, and the Internet. The country also has a well-established ecosystem that supports innovation, with a strong network of universities, research institutions, and venture capital firms.

Ultimately, China and the United States have strengths and weaknesses in different areas of technology and AI. It is inaccurate to say that one is definitively ahead of the other.
The competition between the two countries will likely continue to be intense. Both will play essential roles in shaping the future of technology and AI.
WARFARE
China is developing AI capabilities for military applications. The Chinese military is investing in developing autonomous weapons systems which use AI to make decisions about targeting and engagement. These systems can operate independently and are designed to be faster and more accurate than human operators.
China is also investing in unmanned aerial vehicles (UAVs) and ground-based robots that can be used for a range of military applications, including reconnaissance, surveillance, and logistics. In addition to these applications, China is also developing AI capabilities for cyber warfare.
China has been accused of engaging in cyber espionage and cyber attacks against other countries, and AI can be used to make these attacks more sophisticated and harder to detect.
China is also applying AI and other technologies to enhance the performance of its soldiers and warfighters. For example, it is developing wearable technology that can monitor soldiers' vital signs, track their location, and provide real-time feedback on their performance. It is also exploring the use of exoskeletons and other advanced prosthetics to enhance soldiers' strength and mobility systems which use AI to make decisions about targeting and engagement. These systems can operate independently and are designed to be faster and more accurate than human operators. China is also investing in unmanned aerial vehicles (UAVs) and ground-based robots that can be used for a range of military applications, including reconnaissance, surveillance and logistics. China is now the world's second-largest military spender after the United States.
HUMAN CLONING
China has been at the forefront of human cloning research and has made significant progress in this field in recent years.
However, it is important to note that human cloning is a highly controversial area of research, and many countries have banned it or placed strict limits on its use.
In 2018, a team of Chinese scientists at the Institute of Neuroscience at the Chinese Academy of Sciences in Shanghai announced that they had successfully cloned two macaque monkeys using a technique called somatic cell nuclear transfer.
This was the first time that primates had been cloned using this method, which involves transferring the nucleus of a somatic cell into an enucleated egg cell.
In 2019, Chinese scientists announced that they had created five cloned gene-edited macaque monkeys using the same somatic cell nuclear transfer technique. The monkeys had been genetically modified to disable a gene that is linked to sleep disorders, and the researchers stated that their work could help to develop new

97
treatments for human sleep disorders.
In 2015, Chinese researchers at the Sun Yat-sen University in Guangzhou published a study in which they reported successfully cloning human embryos using the somatic cell nuclear transfer technique. However, the researchers noted that the cloned embryos only survived for a few days and did not develop into fully-formed embryos.
The cloning of human embryos is highly controversial and is subject to strict ethical and legal restrictions in many countries.
While some scientists argue that human cloning could have important medical applications, others have raised concerns about the potential risks and ethical implications of this technology.
CHEMICAL WEAPONS
There have been allegations and reports that China has conducted chemical experiments that could be utilized in warfare.

However, it is difficult to verify the accuracy of these claims as they are often based on limited or unreliable information.
The use of chemical weapons in warfare is prohibited by international law, and China is a signatory to the Chemical Weapons Convention (CWC), which bans the production, stockpiling, and use of chemical weapons. China has stated that it is committed to fulfilling its obligations under the CWC and has reportedly destroyed its chemical weapons stockpiles.
However, there have been concerns that China may be developing new chemical agents not covered by the CWC. For example, in 2019, the US Department of State accused China of violating the CWC by conducting experiments on animals with "toxic" chemicals that could be used in chemical weapons. China denied the allegations and stated it is committed to complying with its international obligations.
There have also been reports of China conducting research into the use of non-lethal chemical agents for crowd control and other military applications. For example, in 2020, Chinese researchers published a study on the use of a chemical compound that could incapacitate people without causing lasting harm.

Some experts criticized the study as raising concerns about the potential for using chemical agents in violation of international law.
“Regardless of the source, allegations should be validated before making any decisions or forming any opinion”.
SPACE China has been using AI in space exploration and space-based applications. For example, in 2020, China successfully launched an experimental AI-controlled spacecraft that can operate without human intervention.
- Linda Restrepo99
The spacecraft uses AI to make decisions about orbit adjustments and other tasks, which can help reduce the workload for groundbased controllers and make space operations more efficient.
China is also developing AI capabilities to support its spacebased intelligence and surveillance for ground-based controllers and make space operations more efficient.
China is also developing AI capabilities to support its spacebased intelligence and surveillance and reconnaissance
(ISR) capabilities. China's military is investing in advanced satellite technology and data analytics to improve its ability to collect and process ISR data, which can be used for a range of military applications, including missile defense and monitoring of other countries' military activities.
RUSSIAN UKRAINE WAR
There are many who believe that China can influence the Russian Ukraine War. China has several ways to potentially influence the ongoing conflict between Russia and Ukraine. However, the extent to which it can do so remains a matter of debate and speculation.
One fundamental way China could influence the conflict is its position as a permanent United Nations Security Council member. As such, China can veto any resolution or action put forward by the Security Council, including those related to the conflict in Ukraine.
While China has traditionally taken a more neutral stance on the conflict, it could use its veto power to block resolutions it sees as unfavorable to either side.
China could influence the conflict through its economic and political ties with Russia. China has been a key partner and ally of Russia in recent years, with the two countries engaging in significant economic and trade relations.

“IS CHINA SPYING ON US? AFFIRMATIVE!”
As such, China could use its leverage to pressure Russia to deescalate the conflict or take other actions promoting peace and stability in the region.
At the same time, China has also sought to maintain good relations with Ukraine and has expressed support for the country's territorial integrity and sovereignty. This could potentially put China in a position to play a mediating role in the conflict, bringing the parties to the negotiating table and facilitating diplomatic efforts to find a peaceful resolution.
China has reiterated its calls for a political settlement to the Ukraine conflict on the one-year anniversary of Russia’s invasion, as Beijing comes under increasing pressure from the United States and its allies over its growing partnership with Moscow.
In a position paper China’s Foreign Ministry called for a resumption of peace talks, an end to unilateral sanctions, and stressed its opposition to the use of nuclear
weapons.
https://www.fmprc.gov.cn/mfa_e ng/zxxx_662805/202302/t2023022 4_11030713.html
It is worth noting, however, that China's ability to influence the conflict is constrained by a range of factors, including its own domestic political considerations, its relationships with other global powers, and its complex and evolving dynamics. As such, the extent to which China can shape the conflict's outcome remains uncertain.
BARRIERS
There are ideological barriers to the Chinese leadership. The tensions surrounding China’s rise do not simply result from clashing economic and geopolitical interests. China's rapid rise as an economic superpower and its growing influence in global affairs has caused apprehension among many democratic nations.
Tensions surrounding China's rise goes beyond the clashing economic and geopolitical

101
interests and stem from a more profound, inherent distrust that conflicts between democratic governments and robust authoritarian regimes.
The ideological differences between Beijing's political values and those of the world's democracies have created a significant barrier that inhibits international cooperation and creates friction. This article delves into the ideological wall between the Chinese leadership and the rest of the world and its implications.
AUTHORITARIANISM AND DEMOCRACY: INHERENT DISTRUST
Democratic governments and authoritarian regimes have inherent differences in values, governance, and human rights. Democratic Governments operate on the principle of transparency, accountability, and the rule of law.

At the same time, authoritarian regimes depend on secrecy, suppression, and coercion. The stark difference between these two systems creates a deep mistrust and unease that often hinders international cooperation.
China's authoritarian governance and lack of transparency have fueled the distrust between the Chinese leadership and democratic nations. The lack of access to information, restrictions on freedom of speech, and the media make it difficult for the international community to gauge China's intentions, creating a sense of unease and suspicion. The ongoing human rights violations in China, including the suppression of dissent, the persecution of religious and ethnic minorities, and the curbing of fundamental rights, have further deepened the mistrust between China and the democratic world.
IMPLICATIONS FOR CHINA'S GLOBAL ROLE
The ideological barrier between China and the rest of the world
significantly affects China’s global role. Despite China's growing economic and military might, the lack of trust and unease has made it challenging for China to secure cooperation and support from democratic nations.

Concerns about China’s intentions and authoritarian governance have also prompted several democratic governments to push back against China's expanding influence. China has been aggressively expanding its global footprint in recent years with initiatives such as the Belt and Road Initiative, Made in China 2025, and the Digital Silk Road. However, the inherent distrust has made several countries hesitant to participate in China's initiatives, fearing that they may be subject to China's influence and coercion.
The lack of trust has also challenged China to manage its relations with neighboring countries, particularly those in the Indo-Pacific region.
103
China's territorial claims in the South China Sea and the East China Sea have led to tensions with several countries in the region, including Japan, Vietnam, and the Philippines.

The lack of trust has made it difficult for China to build cooperative relationships with these countries, making it challenging to manage the geopolitical dynamics in the region particularly those in the Indo-Pacific region.
Napoleon’s alleged famous quote "Let China sleep, for when she awakes, the world will shake" has proven to be prophetic.
China's remarkable rise over the past few decades has transformed the global economic landscape, and its growing military power has given it a significant presence on the world stage.
Napoleon's words have stood the test of time, and they serve as a reminder that the world is constantly evolving and changing.
The challenge for all nations will be to adapt to these changes and to find ways to work together for the greater good of humanity.
The fear of Napoleon Bonaparte has become a reality, China sleeps no more, she has woken up to be a major global hegemon.

Some have said that the devil’s greatest trick is convincing the World that he doesn’t exist.
105
- Linda Restrepo -

LINDA RESTREPO
is Director of Education and Innovation Human Health Education and Research Foundation. She has been a recognized Women in Technology Leader Cybersecurity and Artificial Intelligence. Restrepo’s expertise also includes Emergent Technologies Management, Computer Algorithms, Global Economic Impacts Research. Restrepo is President of a global government and military defense multidisciplinary research and strategic development firm. She has directed Corporate Technology Commercialization through the U.S. National Laboratories. Research in Emerging Infectious Diseases, Restrepo is also the Chief Executive Officer of Professional Global Outreach. Restrepo has advanced degrees in Computer Technologies from The University of Texas And New Mexico State University.

107
CYBERSPACE AND

Giancarlo Elia Valori
ARTIFICIALINTELLIGENCE

While trying to understand the prerequisites for the epic clashes for the conquest of spacetowards which Artificial Intelligence today stands as an alternative of sharing responsibility for the downward curve of resources still available on planet Earth - I am reminded of a book written more than twenty-five years ago by Paolo Cortesi, in which he analysed the real aims of the space race that started in the late 1950s.
At that time everyone was convinced (or at least they let it be understood) that a new era was opening up for mankind by reaching beyond the Earth's atmosphere and onto the Moon. Everyone declared that the conquest of the Moon would have decisive consequences in the cultural and technological evolution of our planet.

Decades after that day, we can verify how inaccurate the emphatic predictions of that time were. Unfortunately, mankind has not changed for the better, if not for the worse, and evolution has not taken any sudden turns except in the technological sphere. The Moon has become remote again, and between the 1960s and the early 2000s, it has been of much less interest than it was a hundred years ago.
The affair of the so-called conquest of spacespace is quite another thing - is emblematic of the entire history of astronautics. It was an infatuation, an intoxication as intense as it

111
was swift, instigated by the two hegemonic powers, the United States of America and the Soviet Union, which spent enormous amounts of money on it. The USA alone spent $24 billion on the programme that ended with the Moon landing. Just think that NASA's budget for 1962 was set at $1.784 billion - and at the same time, the US aerospace agency had as many as 21,422 employees.
That dizzying investment was justified by scientific needs. As propagated, man was entering space. The era was beginning in which mankind would leave - at least ideally - the planet on which it had always been confined and astronautics would lead mankind to its full maturity. The reality of facts, however, was not like that at all.
Instead, the space race was an extension of the Cold War, but in the 1960s and 1970s saying so would have been seen as medieval blasphemy.
It was preferred to present (sometimes impose) the heroic version of the Promethean man who wanted to wrest his dominion from the sky, the ultimate conquest of outer space. Westerners under the pretext that liberalism and capitalism would lead to everybody’s happiness; Socialists on their way to the bright future, the so-called sol dell’avvenire, from Heaven on Earth.

The truth was much sadder: Russian satellites were spying on the United States which, with the highly secret Corona project - the existence of which was only revealed in the late 1990s - had launched highly sophisticated photographic devices that observed the Soviet Union from above, etc. All scientific rockets and launchers were conceived, designed and used for military purposes.
Space became disturbingly crowded: on 30 April 1969, there were as many as 3,950 satellites in orbit. The Russian Cosmos satellites were launched as part of a vast new “space research” programme: this was what TASS declaredofficially and very vaguely - on the occasion of the first launch (16 March 1962).
Nevertheless, if we consider the international political climate of the days when the Cosmos satellites were launched, we could discover very significant coincidences. The first Cosmos satellites were put into orbit when the Cuban crisis was breaking out and when it was tragically developing. In 1968, the monthly average of launches increased in conjunction with the SinoSoviet crisis.
In March 1969 as many as six launches took place, and it was in that month that the bloody clashes between the Soviets and the Chinese along the

113
Ussuri River for the conquest of Zhenbao Dao Island (Russian: Damansky) took place. In the following months, launches became routine, but in June, when there were clashes on the Western border of the People's Republic of Mongolia, there was a close launch of five Cosmos missiles. When talks began between Kossighin and Zhou Enlai, the number of satellites put into orbit decreased to only two per month.
The parallelism between satellites and international events was too timely to be a coincidence. As has always happened in technocratic civilisation, the external, journalistic, popular aspects are filtered by an oligarchy of politicians and military to conceal the real aims - i.e. control, conquest, preparation for war, orders placed to friendly companies.

In the pioneering years of space travel, military spending was a bottomless pit that swallowed up rivers of money: in 1962, $121 billion of the time was invested worldwide in armaments; in 1967, the amount rose to $197 billion and in 1970 to $240 billion. The arms-astronautics intertwining was indivisible.
In 1961 the US Air Force signed a contract with Raytheon for the wartime use of globular lightnings (high-energy spherical plasmoids). Besides this shady flip side of the coin, there is another secret story of astronautics. It is the story of unreported tests, of hidden and denied failures, of top-secret flight anomalies, of reticence and absurdities. Even today many truths are unknown to us. Despite the great changes that have taken place in recent years, the two superpowers’ archives are still far from being open and transparent.

115
Nevertheless, we can now less naively reinterpret an era that is our closest past, but which now seems almost alien to us, absolutely remote and sometimes incomprehensible.
The militarisation of space, however, has an older history than Moon landing. From 4 October 1957 to the summer of 1964 - that is, in just seven years - 235 artificial satellites were launched into space, 95 of which were still in orbit in July 1964: 74 American, 18 Soviet, two British and one Canadian. In addition to these devices, 328 fragments of rockets and spacecraft were orbiting the earth, almost all of them US-made.

A large part of that space fleet was made up of military satellites, about which the strictest secrecy was kept, with all due respect to the usual idealists who believed that technological progress was for the benefit of mankind. In fact, at least half of the rockets and satellites that were launched in the early years of space travel were intended for an unhumanitarian purpose, i.e. to spy on the enemy and to put into orbit nuclear warheads capable of crashing on targets which, in that case, were not barracks or forts, but cities populated by hundreds of thousands of defenceless human beings.

117
In the 1960s, the two superpowers’ military spending was colossal: in the US budget for 1964/1965 it amounted to $55,211 million. (Note that the total expenditure was $97,900 million and therefore the military budget was well over half of the entire national budget)1 . The “defence” item affected the US public finances according to the following figures, expressed in millions of dollars:
1962/1963: $52,800 million
1963/1964: $55,300 million
1964/1965: $55,200 million.
Of these amounts, the spending for the space race was the following:

1962/1963: $2,600 million
1963/1964: $4,400 million
1964/1965: $5,300 million.
As can be seen, investment was steadily increasing. The noble thirst for pure knowledge alone would obviously not be enough to justify and impose such substantial funding. Space was the new “battlefield” on which the two hegemonic blocs were confronting each other. We have not yet official figures available on Soviet space expenditure. A figure provided by the West is very eloquent: the Sputnik programme alone cost the Soviet Union 48 billion dollars each year (1961 data).
For more than a decade space travel was the large use of public money for the obsessive “national security reasons” that replaced scientific purposes, thus making astronautics a truly perfect example of what governments mean by the magic word technology. It is no coincidence that all the first astronauts, namely Gagarin, Glenn, Titov, Cooper, Carpenter, Leonov and White were officers of their countries' armed forces.

119
In the early 1960s secret satellites were like a swarm of midges orbiting the Earth. It goes without saying that the word “secret” here is synonymous with “military”. The United States (about which we have more information) launched those satellites from the Vandenberg base in California. Almost all the launchers used in those years were Thor-Agena, a 19-metre high missile that developed over 68,000 kilos of thrust. Between 30 October 1963 and 8 October 1964, there were six secret US satellites. Much more hectic activity took place in the first four months of 1966.
Between January 1 and 26 April 1966, 36 spacecrafts were launched, 13 of which were secret US satellites. They were very often spy satellites, which had the task of photographing military installations of the Soviet Union and of other countries considered “unfriendly”.
There were, however, also several satellites that carried radioactive material on board, both for batteries and for undeclared uses. These real nuclear bombs wandered around the Earth, posing a real danger not only to spaceships but also to life on the planet: a radioactive satellite crashing to the ground is not much less devastating than a nuclear warhead. But the delusional imagination of militarised technicians went even further, designing apocalyptic scenarios of real war in space, with apparent lucidity and rigour. President Reagan's Space Shield or Star

Wars (Strategic Defence Initiative-SDI) was only the subsequent step.

As early as 1959, the American De Seversky wrote: “Air power and space power are synonymous. Space above the Earth is the natural domain of the air force, which shall conquer the air and space domain in any future war by a well-coordinated and carefully conducted offensive by means of aircraft, missiles and, where necessary, satellites and spacecraft”.
In 1961, the French “Revue militaire générale” wrote that
after the first phase of the warlike use of satellites, as observers to spy on the enemy's moves, “a possible fight that takes place entirely in space may soon follow”. Bearing this in mind, for instance, the US “Air University Quarterly Review” of the summer of 1959 dealt with the Moon's military potential in a series of articles. The articles mentioned a US Air Force officer, Homer A. Boushey, who - as early as 1958 - had argued for "using the Moon as a missile base from which a retaliatory strike against the Soviet Union could possibly be launched". General Boushey's most demonstrative and convincing points were as follows:
"From the power viewpoint, it should be recalled that we must remember that 1/5 or 1/6 of the power required to perform the reverse operation is sufficient to launch a projectile from the Moon to the Earth.
121
The Moon has the advantage that whoever is in the highest position has, according to old military tradition. A missile launched towards the Earth from the Moon can be observed and guided from the moment of its departure until the moment of impact. The opposite is not true.
A missile attack launched from the Earth can be observed from the Moon 48 hours in advance of the missiles' arrival, which allows for a response. The Moon is a base of unparalleled value for retaliatory operations. If we had a base on the Moon, both in the event that the Soviets launched a powerful nuclear attack from Russia against the Moon two or two and a half days before attacking US territory (and such attacks would not escape observation), and in the event that the Soviets attacked the US directly, Russia could not escape our sure and massive

retaliation that would reach it 48 hours later.” That Dr. Strangelove-style proposal was appropriately commented by physicist, Prof. Lee DuBridge, who recalled a very important platitude that - in his eagerness to line up nuclear warheads at the edges of lunar cratersGeneral Boushey had missed: "If you dropped a bomb from the Moon on an Earth target, the bomb would take five days to reach the Earth. It would probably arrive when the war is already over”.
Then the following statements were made to try to remedy this: “It is therefore possible to consider elements of Moon potential in terms of psychological and technological warfare, as well as the development of new military doctrines. It is also possible to think of the Moon as a site for limited wars. The unconventional considerations made in this article are encouraging, as they may suggest a good investment of capital”. Fortunately, at that time there was not (nor is there now) sufficient capital to finance the establishment of even a small terrestrial military base on the Moon.
Military astronautics projects are a good illustration of certain mental paths: science and technology are docile servants of political expediency, which very rarely agree with the welfare and well-being of the peoples in whose interests they purport to rule.

123
The Able Project of 1966 is a fine example of this. The Marshall Space Flight Centre in Huntsville, Alabama, developed a missile programme that aimed to put a 600-metre diameter mirror into orbit. That huge reflective surface would be positioned and tilted in such a way as to constantly reflect the sun's rays onto Vietnam, to deprive the Vietcong guerrillas of the cover of darkness and make them easy targets at all times. Moreover, that “unlimited artificial day” would have destabilising psychological consequences on the enemy. The Able Projectwhich today appears to us as the ridiculous nonsense it waskept Marshall's engineers hard at work for months, under the direction of Edward Gray, a senior NASA official. NASA is a non-military government agency. The fact that it has been involved in wartime projects, such as the Able Project, says a lot about the alleged separation of civil and military bodies.
The early years of space travel are among the most mysterious of our century. Secrecy was the constant factor of tests, the military component of which was played down in a contrived atmosphere of scientific pioneering, fine words and bursts of science fiction bliss. Even the United States of America, which presented itself as the champion of freedom of information, crowded space with secret satellites. It was easier for the Soviet regime to work without being accountable to the public.

Many of the Soviet space launches were never officially declared, and some rare news of them was learnt from the US intelligence services. In June 1963 NASA released a document based on observations collected by the North American Aerospace Defense Command (NORAD). That document listed some space failures that the USSR had never admitted.
A spacecraft, launched into orbit on 25 October 1962, exploded and shattered into 24 metal fragments that orbited the Earth.
The first of those wrecks disintegrated by friction in the atmosphere on 29 October. The last fragments continued to gravitate around the Earth until 26 February 1963. On 12 September 1962 (still according to US sources), the Soviets launched a PHI 1-7 satellite, which, however, fell back to Earth only five days later. A BXL 1-5 spacecraft was launched on 4 November 1962 and disintegrated sometime between 5 November and 19 January 1963. On 4 January 1963 three artificial satellites were launched from a Soviet missile base, the first of which remained in orbit for only a few hours and the other two until 11 January 1963. These episodes can never be part of the “official” history of space travel, because they never existed officially.
As much as it repulses the public today, the missile tests of thirty years ago were

125
conceived and conducted without the slightest actual control by the citizens who paid out of their own pockets for the huge expenses of the space race. Scientists and the military - and they were often one in the same - designed tests without regard for their ethical aspects. Is it morally acceptable to intervene on the entire planet just because you have the technical means to do so? Is it lawful (or only reasonable) to alter the balance of the planet by compromising it for tens of years or perhaps centuries? In a delusion of technological omnipotence, magicianscientists imagined reshaping the Earth, like - for examplecertain Soviet scientists who, in early 1961, planned to create a belt of potassium particles around the globe. They were to place 1.75 million tonnes (sic!) of potassium, at an altitude of 1200 kilometres, between 70° and 90° north latitude. That potassium cap would serve to “increase the solar intensity on Earth”.
Soviet scientists evidently assumed that the planet's evolution was incomplete or inaccurate, if they believed to be entitled to create something that had not been missed over billions of years. Fortunately, some projects were so megalomaniac as to be unworkable. Others, unfortunately, were not: we have already seen the case of the stratospheric nuclear explosions in the United States of America.

Speaking of nuclear explosions, it is interesting to examine one which, although it does not directly concern space travel, is a fine example of how little the experts’ certainties are reliable and how gigantic the imbecility of power can be.
In the autumn of 1968, the United States of America detonated a thermonuclear bomb called the “earthquake bomb,” the most powerful it had ever made. Its destructive power was equal to that of 1,200,000 tons of TNT, i.e., 60 times more powerful than the Hiroshima bomb. The device was detonated in a cavity dug 1,200 metres deep in the Nevada desert. Experts had predicted that the seismic wave produced by the explosion would propagate within a radius of 400 kilometres. Instead, it exceeded 600 kilometres and was felt with terror as far as Salt Lake City, Utah, where skyscrapers

swayed as if under invisible colossal hammer blows. Seismographs jumped as far as Los Angeles, and twelve “natural” earthquake tremors followed the tremendous explosion, which left a crater 90 metres in diameter and 20 metres deep. It would be interesting to know the purported reasons for that explosion, which cost several million dollars, whose only consequences were the devastation of the deep soil and its radioactive contamination. In the 1960s, however, technocrats and the military believed they were finally all-powerful.
Like spoiled, paranoid children, the new sorcerer apprentices had convinced themselves they were improving the world. In order to do this, they put Dr. Mabuse-style tests into practice.
127
On 9 May 1963 an Atlas-Agena rocket left Point Arguello, California, and its mission was described as secret. Only later would the USAF reveal that it placed 400 million copper needles in orbit around the Earth, forming a belt 40,000 miles in circumference at an altitude of about 2000 miles.
As the usual experts assured us, that planetary cloud of copper needles would be used for world-scale communications tests. The duration of the belt was expected to be about five years, after which it would dissolve without a trace. To date, we do not know if, how and when the needle mass was destroyed. However, knowing the so-called technicians’ infallibility, we could honestly have some doubts about the planned outcome of the test.
Nowadays, while - on the one hand - the technological
advances recorded during the so-called scramble for outer space have ensured that the superpowers can spy on each other without many problems, on the geopolitical scene we are witnessing a transition from the bipolarism defined by the Cold War to the multipolarism of the current international space community.
As discussed in the book
“Cyberspazio e Intelligenza
Artificiale fra Occidente ed Oriente” (Cyberspace and Artificial Intelligence between East and West), which was presented on 2 March at La Sapienza University in Rome
(https://youtube.com/live/7uVU5p3xfI?feature=share), interest in reaching the Moon not only through human missions but also through stations equipped with robotic means has had a revival with the new millennium.

Their promoters include not only States, individually or jointly, but also private entrepreneurs, especially in the United States of America.
Since 1969, with the presence of many players intent on demonstrating their technological capabilities, space has become an economic, political, military and perhaps even purely scientific centre of gravity, whereas in the early days - as examined above - science was only an incidental optional.

Considering the above, the following can be inferred: technological independenceunderstood, in this case, as having a comprehensive space programme available - is a sign of international prestige and an element to assert one's political and economic leadership. High technological development is a driver of economic development, solidity, dynamism and industrial competitiveness.
The US leadership in the space sector is currently witnessing a surge in the People's Republic of China through very fast technological development and the use of reverse engineering. Many Chinese missions show the high level of development achieved by China through a mix of cooperation and competition. Some believe that while, on the one hand, China has often reaffirmed its propensity for cooperation, on the other it also demonstrates that it turns the technical-national benefits of its space programmes into geopolitical influence.
We can add some convincing ideas to the above points I have tried to highlight in my recent book: space is the new element of competition and States’ interest in the sector could give rise to a reorganisation of international relations on a global level.
129
The new role of international cooperation is defined, since if we have to look for new energy resources, we cannot make them come after a star war that first defines a winner-take-all, not least because in the event of a war very little would remain of our planet. New mechanisms of collaboration and division of the raw materials that are up there shall therefore be developed. Hence space diplomacy is certainly already in place, beyond the European terrestrial conflicts that concern issues that could have been settled long before. Nevertheless, the faint-hearted and fearful EU that had a duty to take action has done nothing about it except for hollow words and arms sales.
Let us go back to what we were discussing.
The renewed call for the “reconquest” of the Moon is obviously associated with the identification of the old

protagonists, new States, national space agencies and international organisations, and new players that we will examine later.
The so-called privatisation of space is present in the US reality and is linked to budget restraint, which has forced NASA to outsource rocket and probe design to independent laboratories linked to it, as well as universities and companies with recognised know-how in the sector. Private companies operating in the aerospace sector are also present in other countries, but in the United States of America the capabilities and skills have been strengthened to such an extent that it is capable of developing its own space programme, including Elon Musk's SpaceX, Richard Branson's Virgin Galactic, Jeff Bezos's Blue Origin, Robert Bigelow's Bigelow Aerospace and Eric C. Anderson's Space Adventures Anderson.
In any case the return to the Moon is the first step on a path to explore other parts of the solar system. At the moment the Moon appears to be closer, apparently only three days' journey from the Earth. For the sake of comparison, Mars is almost a year away - just to say that Man's “conquered” space is nothing compared to real space, but it is much in proportion to the raw materials we can extract from it.
The Moon provides an excellent base for truly scientific tests and should serve as a stimulus for advancing the technological and engineering capabilities of the nations involved.
Furthermore, the additional incentive for space exploration is the possibility of mining on the Moon and on various celestial bodies in the solar system to obtain fundamental minerals and other raw materials. It is hence easy to infer that the advocates of commercial space exploration
consider mining a key factor for future missions.
We also need to consider the concrete feasibility of the aforesaid exploration given the very high costs of reaching the Main Asteroid Belt, extracting resources and transporting them to Earth, considering that the largest of them, Ceres, can be reached in about 28 days (259,195,741 kilometres at the closest point), using the fastest unmanned spacecraft ever built, which has reached about 400,000 km/h.

131
The incentive for investment and projects must also come from the legal instruments defined by some countries, i.e. the creation of an international space law, a new terra nullius, which is even better regulated than what has been instead developed for Antarctica. Hence the new space race is really interested in the aspect of developing adequate regulation to facilitate the establishment of a climate of co-partnership, from a commercial and entrepreneurial viewpoint, among the players who would like to move towards the new frontier. The potential exploitation of space resources therefore opens up issues that require an agreed solution within the international community as soon as possible. The aforementioned legal instruments - which we hope will give rise to a well-defined regulatory regime - could,
however, stimulate the emergence of national regulations which, in the regime of freedom granted by the Outer Space Treaty - UN General Assembly Resolution 2222 (XXI) of 16 December 1966 - would end up triggering a dangerous race towards more favourable regimes for private investment and initiatives. Hence the need for a true international space law! Moreover, given its proximity to the Earth, the Moon is well suited to become an experimental laboratory - but a laboratory to which every country can have access, and not only superpowers or private individuals with a lot of money. There are renowned scientists not only from the United States, Russia and China, but also from many other countries that have the right - and we have the duty - to ensure that they draw on these technological resources.

A laboratory as a place where to live and prepare missions for the colonisation of Mars, the exploration and exploitation of the Main Asteroid Belt, and human missions to reach even more remote areas.

We must not forget that the Moon could be a source of water and oxygen extraction, as well as minerals such as titanium, aluminium, iridium and even some rare earth elements such as neodymium, although the most important lunar resource seems to be helium-3.
This gas produced by the solar wind and accumulated on the Moon's surface over billions of years is present in very large quantities. It would be a good clean fuel for nuclear fusion reactors, as its use would produce a negligible amount of radioactive waste. In this regard, we should recall the complex regulatory framework in place for the exploitation
of lunar resources, which provides for exploitation only for the benefit of mankind, and includes a whole series of limited activities to be carried out on the soil of our satellite.
In spite of the many failures of some missions not only to the Moon, but also directed elsewhere, and the awareness that the enterprise is not easy, the main reasons that drive the United States of America, the People's Republic of China, and some countries of the international community to attempt a return to the Moon
133
in the near future are apparently - and hopefully in reality - technological and scientific in nature. The challenge is the development of technologies that - repeating what happened in the past - will accompany the advancement of new architectures to keep a nextgeneration space station in orbit that facilitates less expensive exploration than in the past. Moreover, as pointed out above, the presence of the station on the Moon would also facilitate missions to Mars. Finally, returning to the Moon could contribute to a better and more comprehensive understanding of the development of the entire solar system.
The previous shelving of lunar missions and the development of public-private partnerships in this sector have given rise to the so-called new space economy in the United States of America. It will see a greater presence of private players, more so in the United States, as
in China and Russia these activities are controlled by the respective States. By supporting and financially backing lunar missions, these private players will reduce the costs borne by the public administration, as was the case in the 1960s and 1970s examined above. Furthermore, the sector will witness the development of startups and venture capital enterprises engaged in this field. Finally, space resources are attractive to the private sector. We refer to those present on the Moon, as well as asteroids.
The new era of exploration - Moon exploration, at first, and later space exploration in its entiretyneeds to be enhanced and made known to the general public properly and adequately so that the global community realises the positive impact these missions have on everyday life.
Artificial Intelligence will handle all this, including trips to the solar system with non-human but robotic crews.



PROFESSOR GIANCARLO ELIA
VALORI is a worldrenowned Italian economist and international relations expert, who serves as the President of the International World Group.
In 1995, the Hebrew University of Jerusalem dedicated the Giancarlo Elia Valori Chair of Peace and Regional Cooperation. Prof. Valori also holds chairs for Peace Studies at Yeshiva University in New York and at Peking University in China.


Among his many honors from countries and institutions around the world, Prof. Valori is an Honorable of the Academy of Science at the Institute of France, as well as Knight Grand Cross and Knight of Labor of the Italian Republic.
Dear Professor & President Giancarlo VALORI, “Genuinely, thank you. . . for your longterm support, kindness, and friendship with our School. I would also love to avail myself of this opportunity to express my deepest respect for your zealous effort and great contribution to promoting peace, solidarity, and mutual understanding among diverse cultures and peoples”.

 Edificio Valori at Peking University
Edificio Valori at Peking University


Introduction

In recent years, the increasing competition between major world powers for dominance in the space domain has raised concerns about the possibility of a space war.
In light of these concerns, former US Air Force Major Even “Jolly” Rogers established True Anomaly, Inc., a company aimed at addressing the challenges posed by orbital warfare.
Orbital Cyberwarfare our next frontier in cybersecurity ?
According to a recent filing with the US Federal Communications Commission, True Anomaly is preparing for its first orbital mission.
The mission, called Demo-1, will involve the launch of two Jackal spacecraft aboard a SpaceX rocket. The Jackals are equipped with thrusters, radar, and multispectral cameras, allowing them to maneuver
close to other satellites and gather intelligence. In the event of a successful first mission, Rogers envisions deploying thousands of autonomous spacecraft controlled by both human operators and AI to support the US military in its defense efforts.
While True Anomaly’s website does not explicitly state the development of offensive weapons, Rogers has hinted at the importance of being able to disable enemy spacecraft in the event of conflict. He has stated that tactically disabling enemy spacecraft could be crucial in determining the outcome of a battle.
Some scenario's
When considering the possibility of cyber warfare in space, it is important to consider the various scenarios that may arise and the possible outcomes from both a societal and legal perspective.
so
Scenario 1: State-sponsored cyberattacks on military satellites. In this scenario, a state-sponsored group launches a cyberattack on a military satellite, potentially disrupting communication and navigation systems. The outcome of this scenario could be a loss of confidence in the security of military systems and the escalation of tensions between the affected state and the state responsible for the attack.
Scenario 2: Jamming of commercial satellite communications. In this scenario, a state or non-state actor jams the communications of commercial satellites, potentially disrupting services such as GPS and television broadcasting. The outcome of this scenario could be economic loss for the affected state and private

companies and a decrease in trust in the security of commercial satellite systems.
Scenario 3: Cyberattacks on civilian space missions. In this scenario, a state or non-state actor launches a cyberattack on a civilian space mission, potentially compromising sensitive data and endangering the lives of astronauts. The outcome of this scenario could be a decrease in public support for space exploration and a decrease in investment in the space industry.
A spy balloon? Or is this a prelude to orbital conflict? The recent deployment of the Chinese "spy balloon" flying at a high altitude and gathering intelligence above the USA could be a potential trigger for the initiation of a space conflict.
141
The presence of such a device could be seen as a threat to national security, potentially leading to a response from the affected state.
Nope it's a dry run: Balloons called top ‘delivery platform’ for nuclear EMP attack
High-altitude balloons, such as the one China has floated over mountain state military bases recently, are considered a key “delivery platform” for secret nuclear strikes on America’s electric grid, according to intelligence officials. Take a dive and read this report to learn more Source intelligence
In September 2018 (source Chinese media) a similar platform was tested to launch hypersonic missiles

In the most stunning evidence of China's military use of stratospheric balloons, Chinese media including the military channel of state broadcaster CCTV reported
in September 2018 that a high-altitude balloon tested hypersonic missiles. Video footage carried by CCTV and reposted on social media app Douyin at the time, but now deleted, showed a balloon visually identical to the one over the US recently, carrying what looked like three different kinds of warheads.
According to Chinese media reports and a related Chinese Academy of Sciences research paper, they were models for "wide speed range" hypersonic vehicles, which can fly both below and above the speed of sound.
China's research on LTA vehicles belongs to two institutes at the Chinese Academy of Sciences, one of which is exclusively dedicated to high-altitude balloons. But in line with Beijing's "military-civil fusion" policy, which calls for civilian or commercial
 hi resolution capture of the wheather balloon sure... Check the dome camera's and computers.
hi resolution capture of the wheather balloon sure... Check the dome camera's and computers.
technology developments to be made available for military use if necessary, those efforts are closely integrated with those of the PLA, its research institutes and the militaryindustrial complex, and as such subject to secrecy.
Pentagon shot down this balloon with a F22
President Joe Biden ordered the action on Wednesday, but it was delayed until the balloon was over water off the coast of South Carolina to ensure no Americans on the ground were harmed.
"The balloon, which was being used by the PRC in an attempt to surveil strategic sites in the continental United States, was brought down above U.S. territorial waters," Austin said. Source
Once Twice Three Four times the same mistake ?

It's possible that the balloons you saw were not intentionally out of control.
There could be various reasons for the balloons to drift, such as changes in wind patterns or malfunctions in the equipment.
It's also possible that the balloons were intentionally made to appear out of control for some reason, but without more information, it's difficult to say for certain. See the camera's computers and sensor arrays... In my personal opnion this is just a prelude to more trouble ahead.
Sources: https://amp-cnncom.cdn.ampproject.org/c/s/a mp.cnn.com/cnn/2023/02/12/p olitics/lake-huron-highaltitude-object/index.html (object shot down last sunday)
https://www.dailystar.co.uk/ news/latest-news/breakingcanada-shoots-downunidentified-29194484
Spot the difference between a wheather balloon and intel based spy device
"We are aware of the PRC statement. However, the fact is we know that it’s a surveillance balloon, and I’m not going to be able to be more specific than that," Pentagon spokesman Brig. Gen. Patrick Ryder said during a Friday briefing. Source
Force majeure...
"China strongly disapproves of and protests against the U.S. attack on a civilian unmanned airship by force," the Foreign Ministry said. "The Chinese side has, after verification, repeatedly informed the U.S. side of the civilian nature of the airship and conveyed that its entry into the U.S. due to force majeure was totally unexpected.
Greenfield in legal regulations

From a legal perspective, the lack of clear norms and regulations regarding the use of cyber warfare in space raises questions about the accountability of actors involved in such conflicts. It is crucial for states to engage in discussions to establish clear rules and norms for the use of cyber capabilities in the space domain to prevent the escalation of conflict.
This is only the beginning China's growing interest in space exploration and its potential military applications is well-known. The country has made significant strides in developing its space program over the past few years, including launching its own space station, sending probes to the Moon, and developing advanced missile and antisatellite technology.
145

War in Orbit AI enabled graphics
© Copyright 2023
by Igor van Gemert
However, it is unclear what that incident was or how it relates to China's alleged desire to dominate the orbit area.
The reference to weather balloons and low orbit satellites suggests that China may be interested in disrupting or disabling these systems as part of its military strategy.

The statement implies that the Chinese balloon incident might have revealed something about China’s intentions in space that was previously unknown.
147

Credit Paul Szymanski


War in Orbit AI enabled graphics
© Copyright 2023
by Igor van Gemert
Weather balloons are used for a variety of purposes, including atmospheric research, meteorology, and communication, while low orbit satellites are used for Earth observation, communication, and navigation.
If China were to dominate this area of space, it would have significant implications for global security and technology. It would enable China to control access to critical satellite-based services, potentially giving it an advantage in military and economic spheres. This would be a cause for concern for other nations, particularly those with strategic interests in space.
What is next ? The Spaceforce escelation ladder
The ladder consists of different phases and sub-phases, each of which describes the escalation of the conflict and the type of action taken.
Phase 0: Pre-War Buildup (Shape) involves a range of activities, including overt weapons testing and deployment, treaties, saberrattling, and space alliances. During this phase, there may also be normal space surveillance, tracking, and reconnaissance activities, as well as satellite close inspections.
Phase 1: Deployment / Deterrence (Deter) is the transconflict phase and involves the deployment and deterrence but false attacks, demo attacks, and alternate country attacks.
Blockades, major covert SOF attacks, terrorist attacks, and the seizure and sequestering of suspected terrorists may also occur. Anti-satellite systems may be alerted, and satellite self-defense mechanisms may be armed. Allied astronauts on the International Space Station may also be armed.

151

Space Wars AI enabled graphics by Igor van Gemert © Copyright 2023
Each phase and sub-phase of the escalation ladder corresponds to a specific weapon type or weapon category, including overt weapons testing and deployment, diplomatic requests and demarches, economic actions, embargos, legal actions, administrative actions, transmitting propaganda broadcasts, jamming propaganda broadcasts, increased spying and surveillance, and unusual increases in space surveillance and tracking activities.
The escalation ladder highlights the increasing severity of the conflict and the corresponding escalation of the type of action taken.
As the conflict progresses, there may be an increased likelihood of major covert SOF attacks, cyber attacks, and the employment of lethal force against one's citizens.
Phase 0: Pre-War Buildup (Shape)
During this phase, countries may engage in a range of activities designed to shape the conflict environment and deter potential adversaries. This may include overt weapons testing and deployment, the negotiation of treaties and alliances, and normal space surveillance and reconnaissance activities. There may also be satellite close inspections, where one country inspects the satellites of another country to determine their capabilities and potential vulnerabilities.
Phase 1: Deployment/Deterrence (Deter)
During this phase, countries may deploy and position weapons in space as a means of deterrence. This phase may involve provocative actions

153
such as demo attacks, alternate country attacks, and blockades, as well as covert actions, such as cyber attacks and political disruptions. Countries may also mobilize their forces and increase their military alert level. Satellite self-defense mechanisms may be armed, and anti-satellite systems may be alerted. In addition, allied astronauts on the International Space Station may be armed to defend against potential attacks.

Phase 2: Conflict
During this phase, the conflict has escalated to the point where weapons are used to achieve military objectives. This may include the use of kinetic weapons, such as direct-ascent ASAT, coorbital ASAT, hit-to-kill ASAT, and rendezvous and proximity operations (RPO), as well as non-kinetic weapons, such as electronic warfare, cyber attacks, jamming, spoofing, dazzling, hacking, GPS disruption, EMP, RFI, and laser weapons.
These weapons may be used to destroy or disable satellites, disrupt communications and navigation systems, and create debris in space. This phase of the conflict is characterized by significant military activity and can have serious consequences for space exploration and for the civilian use of space-based technologies.
Phase 3: Post-Conflict
During this phase, the conflict has ended, and efforts are made to mitigate the damage caused by the conflict. This may include debris cleanup efforts, such as satellite servicing missions, robotic systems, ground-based lasers, tethered nets, electrodynamic tethers, and harpoons, as well as diplomatic efforts, such as negotiations, treaties, agreements, confidence-building measures, and dispute resolution mechanisms.
This phase may also involve efforts to enhance space situational awareness, transparency, and confidence-building measures to reduce the risk of future conflicts. The postconflict phase is focused on repairing the damage caused by the conflict and restoring stability and security in space.

Overall, the space escalation ladder serves as a useful tool for understanding the potential escalation of a conflict involving space warfare and the corresponding actions that may be taken at each phase of the conflict.
The consequences for our information society
A military conflict in high orbit has the potential to cause serious disruptions that could have far-reaching consequences on society. There are several ways in which such a conflict could impact our daily lives, including:
1. Debris: A conflict in high orbit could generate significant amounts of debris, both from destroyed satellites and from the use of anti-satellite weapons. This debris could remain in orbit for years, posing a threat to other satellites and space missions. The debris could also re-enter the Earth's atmosphere and cause damage on the ground. This could lead to serious disruptions to critical infrastructure, such as communications and transportation systems.
2. Disrupted Communications: The use of electronic warfare, cyber attacks, jamming, and spoofing in a high-orbit conflict could disrupt satellite-based communications systems. This could impact everything from cell phone and internet access to GPS navigation and weather forecasting. In today's interconnected world, these disruptions could have farreaching
155
consequences on commerce, emergency services, and daily life.
3. International Relations: A high-orbit conflict could have serious implications for international relations, particularly if it involves major powers such as the United States, Russia, and China. It could escalate tensions and trigger a wider conflict, including on the ground. This could have major geopolitical consequences, as well as economic and social repercussions.

4. Space Exploration: A highorbit conflict could also impact space exploration efforts, both in terms of current missions and future ones. It could delay or disrupt ongoing missions, and it could make it more difficult and expensive to launch future missions.
This could impact scientific research, commercial opportunities, and international cooperation in space exploration.
Overall, a high-orbit conflict could have serious and longlasting consequences for society, impacting critical infrastructure, disrupting communications, straining international relations, and impacting space exploration efforts.
It is important to develop norms of behavior and international agreements to prevent such a conflict from occurring and to manage any conflicts that do occur in a responsible and safe manner.

Space Wars AI enabled graphics by Igor van Gemert © Copyright 2023

IGOR VAN GEMERT
is a prominent figure in the field of cybersecurity and disruptive technologies, with over 15 years of experience in IT and OT security domains. As a Singularity University alumnus, he is wellversed in the latest developments in emerging technologies and has a keen interest in their practical applications. Apart from his expertise in cybersecurity, van Gemert is also known for his experience in building start-ups and advising board members on innovation management and cybersecurity resilience. His ability to combine technical knowledge with business acumen has made him a sought-after speaker, writer, and teacher in his field.
Overall, van Gemert's multidisciplinary background and extensive experience in the field of cybersecurity and disruptive technologies make him a valuable asset to the industry, providing insights and guidance on navigating the rapidly evolving technological landscape.

STATISTICIANS BUSINESS Analytics Officers

MANAGING
A RECIPE FOR
DISASTER
Alfred Hall
Jim Kyung-Soo Liew,, PhD

I think it’s essential to outline up front! People are led, and things are managed: Attack Processes and Engage People Pattens (APEPP).
In this article, we argue that to optimize organizational efficiency, business analytics[1] officers should manage statisticians rather
than the other way around. We begin by understanding both positions functions, which may initially appear very similar to the untrained eye. Both positions are staffed with people who can manage, process, analyze, and derive insights from diverse data types. Also, business analytical and statistical training allows
for the in-depth understanding of past “descriptive” data. the ability to make future “predictive” forecasts, and the capability to synthesize and recommend “prescriptive” actions. But the critical difference between the positions, as will be further elaborated upon below, is that the business

analyst is trained to understand the big picture and the details. In contrast, the statistician often focuses only on the details, therefore risking not extracting maximum business value. Typically, both positions’ workflow consists of ingesting historical data, munging it to a usable form, and attempting to understand the input data’s underlying behavior; with this

gleaned knowledge, both attempt to construct applicable complex models that ingest high dimensional data. They will also hope to find, at times, non linear patterns that, if robust enough, will yield helpful, unbiased predictions. These predictions are used to solve business problems or, at a minimum, provide
evidence that a problem exists. To fund this work, stakeholders evaluate whether the present value of the costs associated with it is less than the present value of the benefits it will yield. However, results have been mixed, and there are as many projects that flounder comparable to those that reap wild success.
163
This article hypothesizes that a crucial component of whether a given data project will become successful hinges on reporting lines’ subtle organizational structure. We examine closely the following: Is a data project’s outcome success affected by who is in the management role: business analytics officer or statistician?
While there are many overlapping components aforementioned between what a business analytics officer and a statistician may do, there are several significant differences, which we illustrate with an example.

Hypothetical Scenario: Chow Time!
In this scenario, we examine a question the business owner wants to explore in determining the optimal food to serve in a military chow line so that soldiers can minimize time away from battle positions.
In this case, we have data on the types of food per day, compositional breakdown of current food choices, food computation per day, the mess tent’s capacity, queue rates for the lines, everything about the soldiers’ characteristics, etc.
Statistician Leads

How would a statistician begin this project? The statistician would start by looking at aspects of the data’s integrity: Is it clean? Are there any missing values? What are the features’ distributional characteristics, and are the joint relationships visually apparent in scatter plots? From there, the biases within the data set will be investigated. If assured that biases are limited, then modeling would commence. What should we attempt to model? Would it be a binary supervised learning model to predict if a given soldier would eat “chili mac” or “not chili mac”? or some latentvariable-based recommendation system to attempt to predict the food choices of each soldier?
Note that there are many different vectors that a statistician could traverse. Given all those years of data modeling and possibly academic research training,
their prior experiences would arm him with a vast and complex box of statistical tools to apply to this data set. Once the analysis has been completed, a model is constructed, and results are typically captured in a final report. The final report culminates with an intense presentation to senior brass, a formal write-up submission containing all the lessons learned, and the engagement ends. At this point, the statistician would be off to the following data project, where he would commence the dataproject equivalent of the “hotwash, rinse, and repeat.”
All parties have been satisfied, and the project concludes. But what just really happened? A research project was commenced, funded, and completed, led by our technically competent statistician. Unfortunately, let us assume for argument’s sake that he does not have any business EQ, so this project, in 165
fact, just added another nonsensical extra data set to be maintained that adds little to no business value. The results were not implemented into production since it was just an intellectually exciting research project that did not ultimately impact the chow line’s business.
Now consider if the same people that worked on this project, led by the statistician, have since moved on. What is left for the managers of the chow line to keep? Note that the business of serving food to soldiers has remained the same, so any lessons learned have yet to be implemented into serving food. Any data that supported this project would have very little business value, and the knowledge of this project would have been lost when all those that attended the final meeting retired. How many projects have been proposed, funded, and completed leaving the maintenance of these “data
puddles” from previous projects? While interesting from a research perspective, such “data puddles” provide no real value to the business lines, rendering no business impact. Yes! The data was employed. Yes! Intelligent technical people were involved, and the job was outstanding as everyone worked well together, producing impeccable work, but the business outcome or operational effect fell flat.
Business Analytics Officer Leads.
In the same scenario, the Business Analytics Officer approaches the problem fundamentally differently: her first task is understanding the chow line’s business. Some questions may include: how does the food get there, and is a robust supporting supplychain system or distribution network in place? What are the potential conflicts of interest in the data collection process in the chow Line’s business?

Once the data capture process has been vetted, the business analyst will want to understand which prediction models would help with the more significant mission outcome. What is the big picture concerning the chow line business, and what outcome would drive the most business return on investment (ROI)? Ideally, the future state should have improved business processes and led to better outcomes than the current state process associated with feeding our soldiers given proper Business Process Reengineering activities been implemented, which is a discipline inside the Business Analytics Officer’s job jar. To think strategically about the cost-benefit of the work and the movement from the current state to the future, the goal of improvements will be at the forefront of the business analyst officer’s mind. Rather than getting caught up by the “shiniest” tool in the statistical toolbox, she will think carefully about improving the business process.
Moreover, when the project finishes, the value-added would be put into the production process for sustaining, improving, and testing the chow hall experience. All the lessons learned will be captured in the organization’s business. Therefore, the “newly” constructed data sets are directly linked to the business process improvements, resulting in minimal excess “data puddles” that have little or no value added to the deluge.
While the statistician would take the data as given, the business analytics officer would attempt to understand how everything fits together e.g., the mess hall, the food, the soldiers, the duty location, and the mission. Upon panning out the view, she realizes that the mess hall is on a ship. Did we know this data was taken onboard a vessel on the ocean? What about food supplies being limited and only available when the ship docks at a port?

These are crucial details about the business problem uniquely considered by the business analytics officer. Business Analytics professionals are trained to deeply understand the chow line’s business implications and the interactions between the business functionalities, even within the existing constraints, to understand them. This understanding is critical to optimizing the sub- and supermissions. Furthermore, the nature of business analytics lends itself to this more profound understanding of business problems, as all business professionals are taught to listen and understand the human nature of businesses. As part of their training, they value humancentered design and are mindful that the customer experience is crucial in any business improvement. Therefore, the business analytics officer brings arguably much more to the table since she possesses the requisite data science

understanding and effectively communicates chow-line enhancements and product lines to its customers.
Iron Sharpens Iron
Finally, the business analyst’s ability to effectively communicate to all levels within an organization will allow her to invite and include others in the conversation, thus incorporating diverse viewpoints and ideas that minimize blind spots. Challenging business processes and ideas results in an even better process, as “iron sharpens iron.” In reality, many technical statisticians do not have the thick skin to objectively listen to feedback about how their work does not add a business or operational value. Upon hearing negative criticism, statisticians tend to anchor into a defensive stance rather than make effective changes to improve the business process.
Herculean Challenge
The point here is that the business component of analytical work is essential but needs to be noticed by senior leadership. Since statisticians, and for that matter academics, tend to get caught up in the weeds of the data and the minutiae of the technical analysis, they can easily smoke-screen brass with confusing terms that appear to be the “silver bullet” solutions to the overwhelming data deluge. In reality, these projects may only result in more “data puddles” that do not improve the business processes and merely contribute to the ever-growing nonsensical data sets. Arguably, we are now sitting on a culmination of decades of these “failed” business projects, so the additional task of sorting out the data that possesses business value versus those that do not is in itself a Herculean challenge.
169


171
Value-Add Data Framework - Hull and Liew Model
Below is a framework we provide so that readers can better visualize workflow differences between a statistician and a business analytics officer. The framework shows that statisticians are typically only concerned with the modules in the red circle, whereas the business analyst officer would be taking in the purple picture.
The Hull and Liew Framework will follow ten phases to transform intellectual capital into decisive capabilities:
• PHASE I. BUSINESS Understanding. What does the business want to achieve?
• PHASE II. ANALYTIC Approach. Which analytics approach is appropriate for the business problem?
• PHASE III. DATA REQUIREMENTS. What data is required, and what are the provisioning processes?
• PHASE IV. DATA COLLECTION. Engineer the data pipelines: target (source) and tap (destination)
• PHASE V. DATA UNDERSTANDING. What is the current state of pipelined data?
• PHASE VI. DATA PREPARATION. Determine the approach for organizing the data.
Value-Add Data FrameworkHull and Liew Model

• PHASE VII. MODELING. Which modeling technique is appropriate for the business problem?
• PHASE VIII. EVALUATION. Validate the best-fit model for meeting the business objectives.
• PHASE IX. DEPLOYMENT. How do customers access deployed model results?

• PHASE X. FEEDBACK. Utilized Human-Centered Design techniques to enhance customer experience. Unlike statisticians, who may be only looking at the data for a particular use case, Business Analytics Officers, on the other hand, work directly with clients and business stakeholders to better handle how these sources of data can be used on the problems businesses are seeing in the trenches.
Some people argue that business analytics should primarily rely on descriptive rather than predictive methods because decision-making is not so much a reasoning process as it is an opportunity to implement prior strategic decisions.
Others maintain that it provides managers with the information required to make informed decisions. Both types of analysis should be combined. The structural analysis provides an interactive, analytical environment for a user to examine an enterprise from multiple perspectives. An approach is not unlike On-Line Analytical Processing (OLAP) but analyzes the enterprise’s qualitative or structural aspects.[2] In this view, once all the relevant data has been diagnosed, a company should maximize its efficiency by implementing strategies that maximize the available information.
173
IN CLOSING
In conclusion, when a statistician is the project manager and stays squarely within their functional lane, focusing exclusively on the weeds, this results in a lower value yield for an organization’s data projects. As the information being processed and various business operations continue to scale due to the fourth industrial revolution’s real-time business intelligence requirements, data stewards must see the data centers through the data. While this colossal shift challenges everything, all is not lost for the statistician, as seeking business training is always an option and, in a sense, converts them into big-picture thinkers, as is a requirement for the business analytics officer.

References:
1.Chintan Bhatt, Tadrash Shah, & Amit Ganatra. (2014, July). BUSINESS ANALYTICS-Applications and Practices for Continuous Iterative Exploration. ResearchGate; unknown. https://www.researchgate.net/publication/264497181_BUSINESS_ANALYTICSApplications_and_Practices_for_Continuous_Iterative_Exploration

2.Leung, Y. T., & Bockstedt, J. (2009). Structural Analysis of a Business Enterprise. Service Science, 1(3), 169–188. https://doi.org/10.1287/serv.1.3.169
Authors:
Alfred D. Hull, M.B.A.: Alfred Hull | LinkedIn Jim Kyung-Soo Liew, Ph.D.: Jim Kyung-Soo Liew, Ph.D. | LinkedIn
Placing our own bias aside, we recommend applying to Johns Hopkins Carey Business School for all those statisticians who are interested in converting!
175

ALFRED HULL is the


HQDA Data Policy & Governance Branch Chief/Senior Data Scientist, and previously led Artificial Intelligence & Machine Learning efforts for the Navy Program Executive Office Manpower, Logistics, and Business Solutions. He earlier led Data Science, Engineering, and Systems Development & Sustainment teams at Naval Information Warfare Command, supporting PMW150: Business Management Systems Portfolio.
He spent seven years in fortune 500 companies doing Operations Research and Decision Science work at Amazon.com, Target Corporation, and Dollar Tree Corporate Headquarters. Alfred holds an MBA from George Washington University and two undergraduate degrees in Decision Science and Maritime & Supply Chain Management from Old Dominion University.


DR. JIM KYUNG-
SOO LIEW is President and Founder of SoKat.com, and Associate Professor of Finance at Johns Hopkins Carey Business School. He has published pioneering research at the intersection of social media and big data, cryptos/blockchain, and financial markets. He currently teaches Big Data and Artificial Intelligence:



Extracting Business Value, Crypto-Currencies and Blockchain, and Leading Entrepreneurship and Innovation at the Johns Hopkins Carey Business School. He also serves as ACT-IAC's Co-Chair of the AI Curriculum Committee and Chair of the Data Readiness for AI Committee.


Brian Lenahan


When so few people understand what quantum computing means (is entanglement and superposition part of your everyday language?), how can they understand the implications of the new technology?
Consider the people evolution impact of AI. Today’s workforce is reeling from the impact of technologies like artificial intelligence. Whether it’s speed of progress, privacy issues, ethical use, or Terminator-type predictions, AI’s benefits and risks continue to be explored and certainly remain only partially known.
Job candidates must deal with robot resume filters and interviewers. Radiologists compete with AI-powered systems with greater and greater precision and reliability.
Yoga instructors either augment their practice or compete with tools that hyperaccurately analyse their clients’ movements and recommend improvements. Prognosticators have predicted for years that there will be millions of job losses while others suggest AI will augment existing jobs (much like previous industrial revolutions have resulted in more net new jobs).
Then along comes quantum computing or QC. A technology based on the smallest particles of our universe — atoms, photons, and electrons and the way they interact creating vast new ways to compute.
So, if you are one of the billions of people in today’s workforce or soon to be entering it, do you need to worry? Or is this technology merely in the realm of academia or the laboratory?

How can business leaders achieve a reasonable level of comprehension on such a complex subject? While the timing of commercialized quantum computing may be in question, the eventuality is not.

With every industrial revolution, humans have leveraged the newly available technology to pursue and solve new problems. So too with quantum computing. And human interaction will not fade, thus requiring people to continue to interact with others. Healthcare jobs, for example, are exploding around the world (occupations “according to the US Dept of Labor) even as technology takes new leaps.
As with AI, being creative and innovative is as important as the tools with which to explore opportunities and
challenges. Those are human elements. Dr. Jaclyn Lee of Singapore University of Technology and Design (SUTD) describes the future of jobs in her 2020 book “Accelerating Organisation Culture Change Through Digital Tools”. She contends “…more jobs will move from physical manual labor to work that is creative and innovative” and goes further to predict that “skills that will be in demand will be the ability to work across disciplines, being creative and innovative, and possessing good communication and people skills.” In that vein, instinct, judgment and empathy are vital skills or capabilities yet to be replicated by advanced technology. So, the employee of the future needs to leverage humanity and advanced technology in combination.
183
Boeing executive Jay Lowell, Chief Engineer, Disruptive Computing and Networks, believes that it’s not enough to be simply an expert in quantum computing. You need something else – another skill set or two – to bring to the team. In Boeing’s case that might be mechanical or electrical engineering. In other businesses it might be some other domain knowledge. And learners need to be quick at understanding and adapting to the science of quantum computing. Project groups need a spectrum of individuals. In fact, at Boeing in the Disruptive Computing and Networks team, quantumtypes are in the minority, reflecting the belief that team members can be trained to learn the quantum component.
Getting the Team Quantum Ready
One of the leading voices in quantum today is Carl Williams, Deputy Director of the National Institute of Standards and Technology (NIST) Physical Measurement Laboratory (PML). He has been involved in the technology world for decades and understands the dynamics impacting the quantum evolution. According to Mr. Williams, “what I learned, way back in 2002, is that when that ship leaves port, you have to have a team who understood the technology and understood your business model. You have to have both of those together technology and business model to see if this will affect your bottom line.”

According to numerous sources, there is a serious lack of non-technical talent in the quantum workforce. People with functional backgrounds like operations, marketing, HR and sales who have gained insight into quantum technology offer good value to quantum companies rich in technical talent yet lacking in establishing or driving a business forward.

The Advanced Technology Academic Research Center or ATARC, headquartered in Virginia, hosted a session covering quantum's future impact. The 2021 session covered many fields including how use cases like multivehicle routing problems can be applied to people, assets, vaccine and other distribution optimization challenges with a demo by D-Wave Systems Inc. Representative Jim Langevin
(US) attended the meeting and reaffirmed the importance of a sustained quantum literacy investment in people talent going forward. The head of the Quantum Economic Development Consortium (QEDC) – whose mission is to “grow a robust commercial quantum-based industry and associated supply chain in the United States” concurred that a diverse talent mix is needed and that the challenge is a global one.
I attended a presentation by the UK Quantum Simulation and Computing Hub (17 Universities and 25+ Commercial Partners) titled “Quantum Computing & a Diverse Workforce” discussing their organization's focus on equality, diversity and inclusion and the UK quantum ecosystem.
185
What struck me was the myriad of factors the organization had to consider in managing such a workforce in the 2020’s. Then add in quantum skills and crossover to business demands. IBM suggests that “building a quantum workforce requires interdisciplinary education and the promise of real jobs”. IBM states there’s a five-step process: Designating knowledgeable employees as “quantum champions”, identifying use cases, experimenting with solutions for actual problems, creating a roadmap for next steps, and embracing flexibility because the technology is rapidly evolving. Does every employee of the future need to be a PhD? Does one need to have started to learn about QC at an early age?
Can one learn at least something about the field from YouTube or free education platforms like edX? The answers are no, no and yes. I am an avid user of both of YouTube and edX platforms to learn about advanced technology including QC, each time learning about a new research development or use case at no extra cost.
Developers should apply their efforts in the real world, trying the IBM Quantum Lab where one can get “cloud access to the most advanced quantum computers available…to learn, develop, and run programs.” Your programs. Or Microsoft’s Quantum Development Kit samples. The options are significantly vaster than just a few years ago.

The Approach to Innovation
In 2021, one might imagine that companies all over the world are charging down the door to innovate given the preponderance of new technologies at their disposal. That seems not to be the case, however. Boston Consulting Group's "Most Innovative Companies 2021: Overcoming the Innovation Readiness Gap", determined while 75% of companies are making innovation (a top three priority), only 20% selfdeclared being fully ready to deliver the innovation they argued was crucial to their organizational performance. Certainly, the pandemic has forced organizations to rethink their strategies for the future, pivoting in some cases into
whole new businesses. Innovation in service, product, and technology are now high on the list of organizational priorities and quantum computing should be considered within such strategies when the business problems align.

187
BCG contends that the top innovation companies exhibit innovation ambition, governance, culture and domains while ensuring their ideas fit with the marketplace, performance management and internal ecosystems. Some of their top 10 include quantum computing vendors like Alphabet (Google), Amazon, Microsoft and IBM, yet a company does need to be ‘Big Tech’ any longer to benefit from quantum computing within their innovation strategy, though it’s better if you have some key people to lead that effort.
The CIO Role & Quantum

Forbes’ 2021 Top 50 Innovative Technology Leaders list includes CIO’s from a broad range of industries.
As a CIO in this era, staying on top of technological evolution is a greater challenge than ever. Forbes says compiling the list highlights “how the CIO role has evolved from its traditional focus on serving other corporate functions to one that emphasizes broad innovation and collaboration. Technology leaders are using data and machine intelligence to help identify new business opportunities and then cocreating products and services with their C-suite peers to take advantage of these.” Not only have CIOs had to deal with the impact of the pandemic (think work-from-anywhere and ecommerce tech solutions) on their organizations, but also with the challenge of making key decisions with limited budgets on a technology that is yet to proven on a widespread basis, like quantum computing.
CIO’s recruit and engage talent within their organizations to fill skills, knowledge and operational gaps, yet when it comes to quantum, supply is scarce. Universities are only gradually establishing programs, other than those at a PhD level which have been around for years. Companies must work with vendors pending an in-house solution, if at all. New roles emerge as technology evolves. It happened in the last decade with artificial intelligence and machine learning. It will happen with quantum computing. Yet before a CIO goes about hiring an army of data scientists (like many organizations have done), they may want to consider a different role to start their quantum journey.
The Quantum Business Strategist Organizations need to start considering the value of quantum technology and the talent they need to populate their teams. With billions of dollars being invested globally both publicly and privately, industry players racing to new discoveries and solutions, and prospective clients desperately trying to understand the potential for their organizations, never before has there been a greater need for the Quantum Business Strategist.
The Quantum Business Strategist (QBS) represents a fundamentally new way to address quantum technology implementation and evolution within organizations.

189
The quantum ‘quarterback’ (the QBS) leads the discussion between C-Suite and IT leaders in organizations and as an external consultant with client companies.

Requiring a broad set of skills and knowledge, the QBS should have deep business acumen, some knowledge of quantum physics and mechanics, and insights into the global quantum ecosystem (its’ players, its’ trends, its’ cost structure, its’ options, and more).
The QBS need not be a PhD, or lifelong quantum technology industry participant. Organizations, whether government, industry or academia, consistently argue they need talent with sales, marketing, and
operational experience as well as quantum knowledge, insight and experience and the QBS role is ideally suited for these challenges.

Inspiring long-run organizational quantum success, the QBS supports the development of a quantum mission, vision, goals, strategies, KPI’s and tactics for the organization in near, mid and long-term. By staging quantum activities within the organization, its’ leaders (at various hierarchical levels) and employees acclimatize themselves to this complex, relatively immature technology, its myriad of options, and permit investment decisions to be prioritized alongside business goals. Leveraging quantum opportunity assessments, (QA),
quantum implementation templates (QIT), and quantum strategy roadmaps (QSR), the Quantum Business Strategist must have a business and customer-first approach to the technology . Quantum computing provides great potential yet must be appropriately aligned with the goals of the business (not simply a shiny new piece of tech). Through analysis of the QA and QIT, leadership, employee and customer input, and industry insights, the QBS can develop a roadmap to enhance the success potential of quantum technology within an organization. Through the QBS’ roadmap, organizations gain greater comfort combatting concerns of falling behind the competition, or behind a rapidly advancing technology.
191
Providing resources, outside industry use cases, vendor contacts, and commonlanguage recommendations, the QBS offers leadership a valuable quantum industry professional.
New roles are being created daily in the world of quantum computing. Quantum hardware engineers, quantum algorithm developers, quantum full stack developer are roles that appear on Indeed and other recruiting sites regularly now. The role of Quantum Business Strategist will soon join these other functions in their contribution to a successful quantum implementation and roadmap.

BRIAN LENAHAN
BESTSELLING
Copyright © [2023] Brian Lenahan. All rights reserved.

3X AMAZON
AUTHOR



3x Amazon Bestselling Author, MITtrained, former executive, recognized speaker, consultant and mentor in the field of Artificial Intelligence and Quantum Computing. Brian has authored four books on AI including "Artificial Intelligence: Foundations for Business Leaders and Consultants", and "Deep Health: Using Artificial Intelligence to Live Longer and Healthier" which illustrates the power of AI in analyzing vast amounts of data about one person: you.
Brian's fifth book, his second Amazon Bestseller, "Quantum Boost: Using Quantum Computing to Supercharge Your Business", offers insights into the world of quantum computing and its myriad applications for business. His sixth book, "Quantum Excellence: How Leading Companies Are Deploying the Transformational Technology" shares examples from 50 leading companies from around the world.
Brian's latest book "On the Shoulder's of Giants: 10 Quantum Pioneers of the Past" launches April 14, 2023 (World Quantum Day) and shares the stories of scientists from India, Ukraine, US, Indonesia, Japan and more.
Brian is the founder and chair of the Quantum Strategy Institute (QSI), a collaboration of quantum experts and enthusiasts from around the globe enabling business to understand the technology, its potential and its practical applications. With directors and managers from multinational corporations already in place, QSI launched Sept. 15, 2021.

Brian is an AI & Quantum Advisor at Halton Regional Innovation Centre in Burlington, Ontario and consults to companies developing their own unique quantum roadmaps. In his advisory capacity, Brian asks "what priority business problems do you need to solve" then follows with an assessment of whether Artificial Intelligence and/or Quantum Computing will address those challenges. In terms most relevant to business leaders and individuals, through his books, speaking engagements, consulting and workshops, Brian makes sense of these advanced technologies.


VERSUS


THE QUANTUM
REVOLUTION
It’s interesting to compare both computing technologies to demystify the quantum world.
The architecture of a classical computer

Here you are close to the rabbit hole. The time has come to jump out of your reality.
Alice discovered a new world down the rabbit hole, just like you in the following pages. We will look at a basic level inside a classical computer to avoid shock and compare the architecture with the quantum computer.
Components of a classical computer
First of all, let’s discuss classical computers. Most of us use a laptop daily, whether for work, surfing the Internet, checking emails, or writing with text editors. How? What are the main components of a classical computer?
The figure above shows the basic architecture for a classical computer, yours and mine.
• The input can be keyboard keys, mouse movements, and actions like copy and paste. It could be an interaction between you and the computer or an internal process.
• The central processor unit (CPU) will receive the input and compute the action. The CPU is only meant to calculate.

• If information is needed, the primary memory called random access memory (RAM) helps to store data with high-speed access. If you shut down the computer, the information in the RAM is destroyed.
• The second memory (disk storage) is when you want to keep the information or when computations involve so much data that you write iteratively on the disk.
A computer is just a way to manipulate and transform information. But the data needs to be in the language of the CPU. What is this language? The computer or CPU only speaks in bits or binary numbers, 0’s and 1’s. 0 means “off” and 1 “on.” Bits correspond to the two states of a transistor. Transistors are electrical switch devices.

201
If the transistor is “on,” the current passes through (value 1 for a bit). If the transistor is “off,” the current is stopped (value 0).
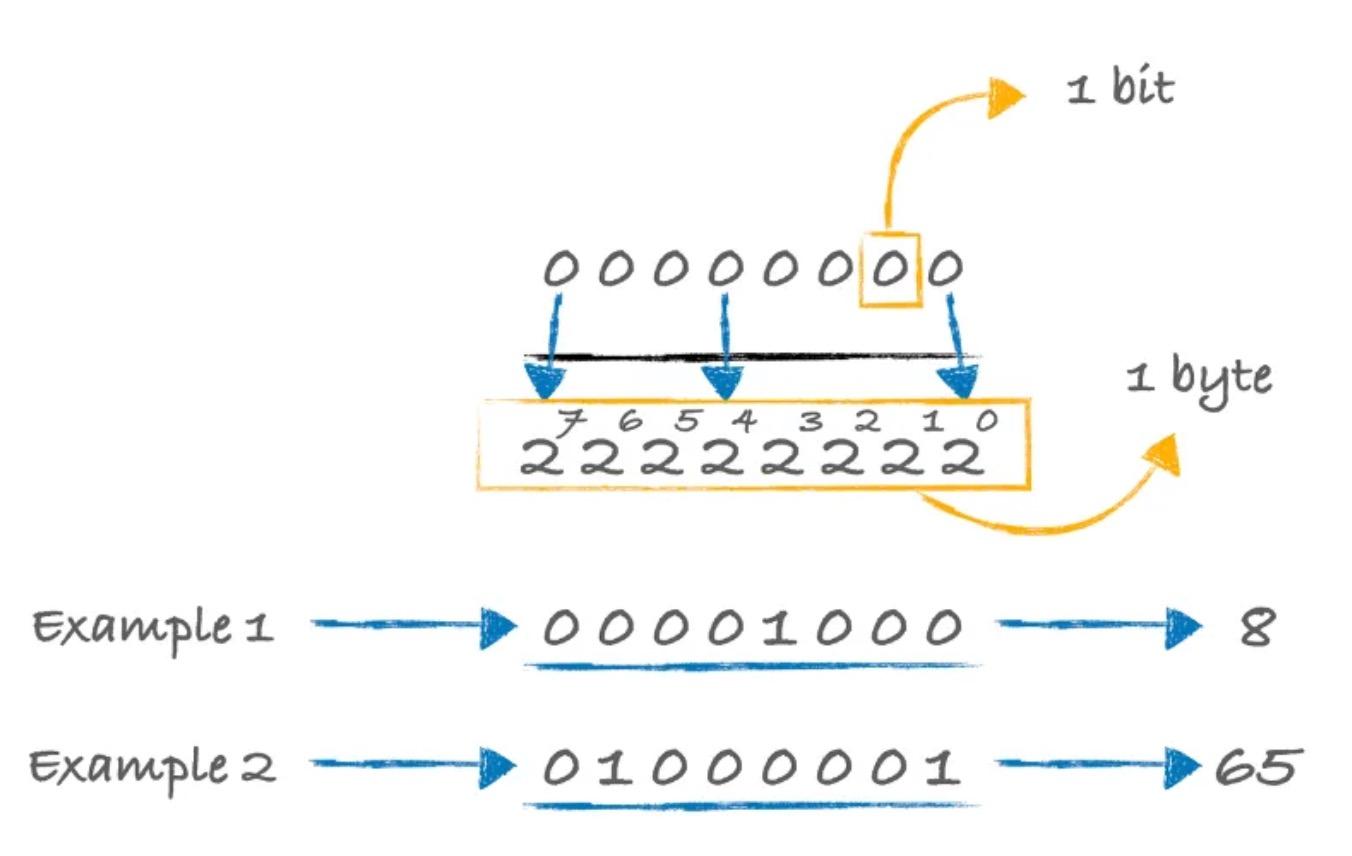
When Bits create Bytes to store more information

Before diving into the quantum world, it’s crucial to have a good survey on how the information is stored in a classical computer. If we just take one bit of information, we are very limited in the
amount of information we can store. 0 or 1 is called a bit, the minimal information unit a classical computer needs. If you group bits in a sequence, for example, eight bits, you form a byte. Then the magic happens. You will have access to 256 possible values, and every quantum of information, document, computation, picture or movie is based on bytes. Imagine long sequences of 0’s and 1’s like in The Matrix.
With eight bits, you can store 2⁷ bits of information.
Imagine that a hard drive has one terabyte, it’s 10¹² bytes, and in each byte, you store 2⁷ bits of information. It’s a lot.
Example: consider a byte like a letter (ASCII convention); a novel contains around 300,000 words. We could use an average of 4 letters per word, leading to 1,200,000 bytes equivalent to 1,2 megabytes or Mb. Your hard drive can contain approximately 833,333 books. Take a coffee and start reading.
The deterministic aspect of classical computation
The beauty of classical computation lives in the deterministic world. Deterministic means that there is no randomness in the evolution of the system. The output will always be the same if you redo the same operation repeatedly.
A processor obeys Boolean algebra’s rules because it uses binary variables and logical operations (logical gates). All of this is deterministic by nature.
It’s why we see thematics like explainability or interpretability in computer science. Explainability is used as the knowledge we have of a model. We could extract the way the model use information and how. Explainability teaches us the mechanics inside the model and answers to the “how.”

Interpretability is the other way to understand the decision of an algorithm. Interpretability means that the cause and the effect in the decision-making are known.
Classical operations are made in sequential order
The CPU has the power of operations.
203
When you buy a laptop, the packaging says “3.4GHz,” you may know that the processor can do 3.4 billion operations per second. These instructions are executed
sequentially by the processor. It passes to the next instruction only if the previous one is done, like this:
You can visualize it as reading a text or a book. You don’t read all pages in a block. You follow one line after another to follow the story thread.

Classical operators: the logic gates

Congrats, you reach the point
where you know how to store information on a computer.
You understand that a computer uses sequential operations, but how do you use or process the bits? You will need operators to manipulate and transform the bits.
Sequential operations in a classical computer Draw by the author.
These operators are at the level of the hardware. They are called logic gates and allow the processor to execute the instruction with fidelity.

Operation through the gate Draw by the author.
A logic gate is usually a simple operation acting on two bits in input and output one bit. Seven basic logic gates exist OR, XOR, NOR, XNOR, AND, NAND, and NOT. I will not go through all of the logic gates but look, take the NOT and the AND gates. We will generate what we call a truth table:

As you see in the picture (Operation through the gate) the logic gate NOT will flip the value of the bit, and the AND gate will output “1” only if the two inputs are 1. You can see it as a multiplication 0x1, and 0x0 will output 0, but 1x1 will equal 1.
Operation through the gate Draw by the author.

205
One interesting thing is that logic gates could perform non-reversible operations, corresponding to loss of information. In the case of the AND gate, we can’t reverse the computation when we have the output because we don’t have the information about each separable bit or state of the bit. The maturity of classical technology will enable you to think in terms of logic gates. The current abstraction of all languages passes above this layer and helps developers to have a better and less complicated life.
The architecture of a quantum computer

A quantum computer is more complicated than a classical one because you need more layers to process the information. The figure below provides you with an overview of the building blocks of a quantum computer. You could see four layers behind the application (compiled quantum algorithm).
 The architecture of a quantum computer Draw by the author.
The architecture of a quantum computer Draw by the author.
The process can be cut into ten steps dispatched in five layers. It’s a control loop where the information will pass two times in each layer. I will use terms like quantum circuit, quantum bits (qubits) and quantum gates to explain the concept of a quantum computer, but I will teach you what they are later in the chapter. So don’t be afraid; the quantum architecture is just here to see the differences from the classical approach.
1 - When we code the quantum algorithm, the application layer is the first and closer to us. This layer compiles the quantum circuit into the language of the computer (like binary assembly in a classical computer).

2 - The logical layer is an interesting part of the quantum computer. This step will deconstruct your quantum circuit into fundamental gates.
You can create high-level quantum gates in your circuit, but the logical controller will deconstruct your gate into fundamental gates to replace your highlevel gate. This is due to the operations done on qubits; inside the quantum computer, just a few quantum gates are implemented.
3 - Quantum error correction: a big name for this step. The actual quantum computers are noisy, meaning that they have lots of destructive decoherence where the qubit loses the information. This loss changes the result of the algorithm. The typical architecture introduces a layer that modifies the quantum circuit and makes it robust to error, called faulttolerant. Controllers introduce a specific waveform to correct the error.
207
4 - The virtual layer is a controller between the virtual and physical environments (steps 5, 6, 7). It keeps the structure of the quantum gates and quantum bits.
5 - We enter the quantum region (steps 6 and 7) on a physical device. The qubits are not virtual. They are physical components of the machine. The goal here is to encode the data into qubits. This layer is the storage of quantum information.
6 - Step 6 is where the magic happens. The computer will run the computation with physical components; it’s the processing of quantum information. Your quantum circuit will be executed, and the value of the qubits will change according to the operations you want to generate a result.
which changes the computation. This last step in the physical region observes to measure the result of the calculation. The observation will lead to a collapse of the quantum state of each qubit. They become classical information.
8 - We must pass again by the virtual environment to translate the hardware readout signals into a virtual qubit measurement.
9 - Quantum error correction filters the results and clears statistical errors. This step is called syndrome measurement; the objective is to diagnose which qubit admits an error. Most of the time, they are Pauli errors meaning that the quantum logic gates operate on another operation. Pauli gates will be explained in the following subsections.
7 - No intermediate result of quantum mechanics can be viewed without measurement,
10 - This last step provides the result in a readable format.


Now we know the basics of classical computers, enough to compare them with the quantum computer. Technology evolves so quickly that it is essential to mention the time we reach them.
Quantum computers are based on quantum mechanics. They are fast compared to classical ones, but they also have cons. They are not magical, keep this in mind; it’s not because they are different or based on another physics that makes them magical. Unfortunately, quantum technology is not as mature as classical computing. A QC doesn’t yet possess a quantum computer’s primary memory (QRAM) equivalent to the RAM in classical computing. Much research is done on QRAM; creating this component will allow researchers and industries to access faster and more complex quantum algorithms.


QUANTUM BITS
Previously we have discussed bits, the fundamental information unit for a classical computer. A QC also needs its essential component called quantum bits or qubits. They are more powerful than their classical counterpart. They can take the values 0’s or 1’s and the infinite possibilities between them. Wait, what?

And the quantum journey begins. The figure above shows the difference between a classical bit, two values, 0 and 1, represented in two dimensions (2D) and their quantum twins. A qubit can be visualized in 3D as a sphere; as we will see later, it is called the Bloch Sphere. 0 and 1 are the values at the poles, north and south, respectively.

But the qubit could also take every other position on the sphere. So, we could store lots more information into a qubit rather than a bit.
The significant difference is that bits are discrete values and qubits are infinite and continuous (called states). When a state isn’t 0 or 1, it is in superposition because it is somewhere between.

213
Classical versus quantum bits Draw by the author.
Probabilities lead the world of quantum mechanics. It is due to the nature of the microscopic scale of matter. Unfortunately, computations will follow the same way. The output has a probability of appearance. That means there are multiple possible outputs for the same input. The computation result will be a probability distribution because you must run your algorithm numerous times.
Parallel instances

One of the advantages of quantum computing is that you don’t need sequential operations or loops. Quantum logic allows the machine to process the computations at the same time. A quantum computer will evaluate every possibility at the same time. A QC can theoretically do 2^n operations at a time.
they lie in linear algebra and always have. Classical computing is about Boolean algebra, but the strength of QC lies in vectors, matrices, and tensors operations. Figure 4 shows what those mathematical objects are. When you create a quantum circuit, you will use gates, also called operators. These gates are matrices applied on single qubits or multiple qubits. A quantum circuit can be seen as a series of matrix multiplications. I will teach you how and why all along with this article. The figure below shows you the different structures we can and will use in quantum algorithms. You have the column vector. Basically, a qubit is represented by a column with two values. Matrix and tensor are the representation of the operators and complex operators.
Linear algebra is enough
The rules of quantum computing are simple;
Quantum Gates

In quantum computing, you also need operators to process the information. These are the quantum gates, and the differences with classical logical gates are insignificant. Quantum gates also take binary inputs and outputs. Unlike classical gates, quantum gates must be reversible.
Reversibility is retrieving the inputs using the output and inversing the operation. If A is the input and I multiply by the matrix X to obtain B, I can invert the process starting with B, multiply by X^-1 (the inverse matrix of X) and get the input A. The theory of quantum mechanics teaches us that we can’t lose information.
 Representation of the different forms of an operator Draw by the author.
Representation of the different forms of an operator Draw by the author.
215
Quantum gates are unitary matrices; their conjugate transpose is also their inverse. The notation for this operator is represented with a dagger like this:

Don’t run now. The conjugate transpose operates as follows:
• Transpose the vector or the matrix
• Compute the conjugate
The conjugate of a scalar is itself; the conjugate of a complex number is the opposite of the imaginary part.


Quantum gates leverage superposition and entanglement, two significant components of quantum mechanics. If two qubits are entangled, they are still in the quantum gates process. They don’t collapse. Quantum gates are mainly used on single qubits or two qubits, so they are 2x2 or 4x4 with orthonormal rows.
Quantum speed-up
Companies look for different things when a new technology appears on the market. Quantum computing isn’t an exception. What can quantum computing bring to the market? How can quantum algorithms be of any interest to a company? We could look at several advantages when we want to test or use another technology. We can look at the ease of use of the technology or algorithms. In the case of quantum algorithms, it will depend on the problem.
We can look at the complexity. Are quantum algorithms less complex than their counterparts? We can look at the energy consumption; this is a point where quantum computers could win with a stable consumption in energy compared to a classical architecture where the power scale exponentially with the power of computation.

Or we can look at the speedup with the decreasing complexity (Big O notation). You gain a quantum advantage when the quantum algorithm is faster than the best classical implementation.
Acceleration
The speed-up is the most used metric to determine if a quantum algorithm is better than the best classical implementation. You can see speed-up as the grail researchers and industries are looking for.
There is a bias here because you can only measure two algorithms (classical and quantum) that will do the exact computation. We can’t use speed-up when we try to create quantum algorithms to solve intractable problems for classical computing. We can’t compare.
For example, two protagonists in quantum information science, Alice and Bob, are in a game. Bob places a ball in one of the six drawers of a cabinet. Alice has no idea which drawer contains the ball.
Classical Alice:
• Best case: Alice opens the first drawer, and the ball is in it. End of the game.
• Worst case: Alice opens five drawers to know where the ball is. She doesn’t need to open the sixth drawer to know where the ball is. Either it was in the fifth drawer, or it wasn’t. It must be in the sixth if it wasn’t in the fifth drawer.
217
Quantum Alice: The function evaluation in quantum computing tells Alice where the ball is. She only needs one try to find the ball.
How is it possible? Think of Alice when she opens one drawer after another. She does it in sequential operation. “I open the first drawer and look inside to see if the ball is in it. If not, I open the second….” A quantum computer and a quantum algorithm taking advantage of this property will evaluate all the probabilities in one of the presence of the ball in the drawers. The quantum algorithm will output the drawer number with the best probability. Alice will just open the corresponding drawer to find the ball.
There is a quantum speed-up comparing the worst classical Alice case and the quantum Alice because the quantum case is faster than the classical one.
We can define the quantum speed-up when the computation time is less for the quantum algorithm than its classical counterpart. But do we need just that? A slight difference in computation time? Exponential speed-ups are required to prove that there is a quantum advantage. That implies the necessary use of a quantum computer. There are different types of quantum speed-up, like linear quantum speed-up. A quantum algorithm will be linearly faster than its classical implementation. There are also exponential speed-up and polynomial ones. We will see examples through this article of their advantages.
There will be a real quantum advantage when quantum algorithms run exponentially or in polynomial time on the noisy intermediate-scale quantum (NISQ).

The current quantum computers are not perfect; they have noise and decoherence, so it’s hard to obtain a real advantage with our few qubits at our disposal.
Big O analysis
In the literature, you will find another way of evaluating the quantum speedup of a quantum algorithm. Researchers use the Big O notation to determine an algorithm’s space and time complexity. Big O is a notation of the measure of the upper bound performance of an algorithm (worst runtime). One of the ways to see it is to determine the number of steps or the number of iterations of an algorithm. Comparing the complexity of both classical and quantum versions of an algorithm shows the speed-up of the quantum version theoretically if the complexity is reduced.

Where linear time is O(n), quadratic time is O(n2), logarithmic time O(n log n), exponential time 2polyn, polynomial-time 2O(log n) and factorial time O(n!). O(1) is excellent, O(log n) is good, O(n) is fair, O(n log n) is bad, but O(n2), O(2n) and O(n!) are horrible in terms of complexity.
Quantum advantage
Quantum supremacy is an older term for the next step after the quantum speed-up. “Supremacy” was judged inappropriate, so researchers replaced “supremacy” with “advantage.” A quantum advantage is a programmable quantum computer that could run a quantum algorithm that a classical one can’t in a feasible amount of time.
For example, in 2019, Google claimed that they realized a computation in 200 seconds compared to 10,000 years in a classical computer.
219
Even if this claim was rebuked by IBM, which shows that the calculation can be done in days on a classical machine with the corresponding optimization, this announcement shed light on quantum computing. More recently, in 2021, China claimed a quantum advantage, running one algorithm 10 million times faster on a superconducting quantum computer.
Another achievement was to run another algorithm one septillion times faster.

Quantum advantages can be expected shortly by some communities and industries. These milestones are expected to validate all the efforts and investments in the quantum computing field. It’s why you need to learn how to use a quantum computer and what quantum algorithms exist now to be ready when the hardware is fault-tolerant (robust to the noise).
Take away
• Classical and quantum computing are different in many ways, but each has pros and cons.
• Classical computers use bits and bytes to store information in a binary format.
• Both classical and quantum computing are governed by what we call gates. They are similar but also different because their physics is different.
• Quantum computing is not mature enough to be used like classical computing.
Quantum algorithms need to be coded at a more fundamental level. It’s why quantum gates are significant.
• The classical world is deterministic; measures of the quantum world are probabilistic.
• Deterministic computation implies you can rerun the exact calculation to obtain the same result.
• On the opposite, probabilistic computation is led by probabilities. The result of a calculation can only be approximate (the result will be different with a variation) because of the probabilistic behaviour.
• Information can’t be lost in the quantum world, so every operation must be reversible. This principle has important implications in the computation process.
• Quantum computing is governed by a different sort of mathematics called linear algebra. Those familiar with the machine learning domain will find similarities with quantum computing.
• A quantum algorithm uses the properties of quantum mechanics, such as superposition and entanglement.
• Some classical algorithms can be run on a quantum computer, but they are not quantum algorithms.

• A quantum algorithm will estimate the operations in parallel rather than sequentially for a classical algorithm.
• Quantum advantage is the speed-up gained from quantum computing over the speed of classical computers’ same types of operations.
221

CHRISTOPHE PERE PhD
Senior data scientist and also a researcher in the field of Artificial Intelligence. Google Scholar. An atypical background in Science and a Ph.D. in astrophysics based on the atmosphere of Venus in the case of an exoplanet to help characterize the atmospheres of exoplanets. Utilization of data processing and data mining methods a data scientist and machine and deep learning methods expert.
ASSOCIATE PROFESSOR
UNIVERSITÉ LAVAL - Québec, QC, Canada
Leading research AI mostly in NLP and Reinforcement Learning
MEMBER PARTNER / RESEARCH
SCIENTIST INTRIQ - Montréal, QC, Canada
Leading research on VQA, data encoding, input/output problem, QML
SENIOR DATA SCIENTIST / RESEARCH SCIENTIST
LA CAPITALE (BENEVA) - Montréal, QC, Canada
- Research in the field of NLP (machine learning, deep learning) for document classification, information and knowledge extraction.
- Using GPUs for deep learning models

- Methods for industrializing data science models in a business context.
In charge of the partnership with Laval University (Quebec) in order to develop three research axes: data mining in order to understand customer behaviour, ethics and bias around data and models in order to minimize discrimination and, cybersecurity with the exploration of connection logs in order to detect malicious behaviour.
POC in QML - The goal is to see if quantum machine learning can be effective with insurance data.

 Photos Guillaume Ruoppolo
Photos Guillaume Ruoppolo
TECHNOLOGY: THINKING

RA01 System
 Luis Alberto Flores Hernandez, PhD
Luis Alberto Flores Hernandez, PhD
The terms virtual, augmented and mixed reality (AR, AR, RM) refer to technologies and conceptual proposals of spatial interfaces studied by researchers in engineering, computer science and humancomputer interaction for several decades. Recently, the term "extended reality" (or REX) has been adopted as an umbrella term for VR/MR/AR technologies. Previously, the use of REX remained "in the lab," or only in specialized domains. The recent turn has led to wider acceptance in society, such as in civil defense, aviation, emergency preparedness and evacuation planning, and almost all educational disciplines, as well as in the realm of criminology.
The work to be developed will focus on the use of REX as a tool in forensic analysis from a broader perspective than the current one.
Although the use of the REX in this area has focused on the analysis of investigations, criminalistics and the police
use of resources, little has been investigated about its use in research on Criminal Forensic Psychology. Currently the REX in this field of research can offer different tools that can contribute to the creation of profiles, analysis of the reasons that lead to crime and delimitation of the factors contributing to crime. The presentation that will take place will address the Ra01 tool from KARTHIC LABS.
PROLOGUE:
The advancement of technologies allows the possibilities to expand as new discoveries occur at the level of systems and programming. It is assumed that humanity is complex from a perspective of action and thought, resulting in general problems for states, loss of life, and generalized chaos, so predicting human behaviors, as well as what they may think, includes an important challenge to achieve, since this can allow a safer world for all social groups.
The implementation of technologies that allow access to ways of acting and thinking, thereby trying to avoid problems that can trigger significant evils, is a project that seeks to address, in order to achieve a fairer and safer society.
INTRODUCTION
Technologies and their advances have allowed each individual's life to be more accessible and adapted to their needs. Ra01, or thinking technology, is presented as a programming system, which makes use of different elements that allow it to be configured in such a way, that it has access to a variety of aspects within people's lives. Through studies of psychology or criminology, a profile of each individual can be configured, thus allowing to anticipate events, in which it can be conceived as a danger to others.
The motto is "A system that can think what you are thinking", this is a system that has the ability to think using sophisticated construction engines, or also known as "Technology of tomorrow" by implementing Pandav engines.
The means by which its use can be diversified are as many as there are technological spaces, but they can be grouped into those that can be worn on the user, such as smart glasses or mobile devices, or those that are a little more withdrawn as the cloud and its storage and interconnection possibilities.
(See Image 2)
The system makes the connection from a much deeper perspective between man and machine, thus seeking to identify what man thinks, through the machine and it is through the implementation of Thingk Computin technology, that such unification is sought. The premises that are kept in mind are to ensure security for
229

national sectors, the police or companies, but also focusing the study within social groups, or those who can be considered more helpless such as women or girls, placing at their disposal aid in case of emergencies. In order to configure such a system, multiple technologies or sciences are used, which allow access to the required information. As has been said, biometric processes play a fundamental role due to the importance they have in the collection of data from each individual, such as the face or fingerprints. Likewise, social information, which can be obtained through the interactions or reactions that each individual makes through social networks is a key point. AR. Smart glasses connected to the nuve. (image 3)
All this applies within machines as mentioned, investing in artificial intelligence,
machine learning, and deep learning, thereby trying to offer as much information as possible to the machine, or in other words configure it. Other transversal elements such as numerology, astrology, descriptive analytics, and the different branches of psychology, are combined as contributions for such configuration. (image 3)
Emphasizing the criminalistics processes, it seeks to carry out studies of pre-criminal behavior, with the sole purpose of safeguarding everything that is possible, acting even before the individual manages to execute his action. Thanks to behavioral analysis, threat prediction and criminal analysis, the necessary information can be obtained to fulfill these purposes, and even the defense of those criminals who can access such an element is taken into account. (see image 4)
231


http://ra01 org/ image 22

image 4
http://ra01.org/

The complementary value of the system is cybersecurity, due to the need for institutions or states to protect the information of all participants in each region.
It is understood with all this, that you work in search of the necessary solutions and through it obtain the system that can be summarized with your phrase "A system that can think what you are thinking".
Mental Psychology
Physiological Psychology
http://ra01.org/ image 5




References:
Social Psychology
Criminal Psychology
RA01 -Technology of thought. (n/d) Thinking Technology: A system that can think what you are thinking. http:// www.ra01.org/ra01s/index.html#intro.
http:ra01.org/
http://karthiclabs.org
Hernandez, PhD Luis Alberto Flores


237
The RA01 System is a system that can think what you are thinking . . .
Ra01 is a system having capabilities of thinking using the in build engines with the sophisticated "Technology Tomorrow ” using engines called "pandav engines."
PANDAV engines:
1. Thinking engine
2. Analytical engine with predictive
3. Social engine
4. Personality engine
5. Criminology engine
It functions with:
• Personal Computers
• Glasses
• Wearable’s
• Mobiles
• Televisions
CLOUD CONNECTED & MANAGED BY RA01
FACE RECOGNITION

Face recognition is a technology capable of identifying or verifying a subject through an image, video or any audiovisual element of his face.
FINGERPRINT IDENTIFICATION
Fingerprint identification is one of the most well-known and publicized biometrics. Because of their uniqueness and consistency over time.
IDENTITY
CONFIRMATION
Identity verification is a necessary process that ensures a person's identity matches the one that is supposed to be.
MOBILE & MOBILITY
Mobile technology is the technology used for cellular communication.
Mobile technology has evolved rapidly over the past few years.
HEALTH INFORMATION
Health information technology is the area of healthcare that oversees the technology systems healthcare providers use to manage patient data.
SOCIAL INFORMATION
SOCIAL INFORMATION INSTAGRAM
SOCIAL INFORMATION
GOOGLE
SOCIAL INFORMATION WHATSAPP
SOCIAL INFORMATION
FACEBOOK
Users create social networks for a variety of reasons, to track lives of friends or work or opinions of the users they respect.
NLP – NATURAL LANGUAGE PROCESSING
Natural language processing (NLP) is a subfield of linguistics, computer science, and artificial intelligence concerned with the interactions between computers and human language.
ML – MACHINE LEARNING
Machine learning is an application of artificial intelligence (AI) that provides systems the ability to automatically learn and improve from experience without being explicitly programmed.

239
SOCIAL MEDIA & PERSONAL ANALYTICS
Social media marketing plays such a critical role in overall marketing success in 2021, and social media analytics tools are a critical source of strategic marketing information.
SOCIAL PSYCHOLOGY
According to psychologist Gordon Allport, social psychology uses scientific methods "to understand and explain how the thoughts, feelings, and behavior of individuals are influenced by the actual, imagined, or implied the presence of other human beings."
ASTROLOGY
Astrology in the United States is a broad term that centers around Zodiac signs. The level of commitment and understanding of the Zodiac sign varies.
TECHNOLOGY OF NUMBERS
Numerology is any belief in the divine or mystical relationship between a number and one or more coinciding events. It is also the study of the numerical value of the letters in words, names, and ideas.

PREDICTIVE ANALYTICS
Predictive analytics encompasses a variety of statistical techniques from data mining, predictive modeling, and machine learning that analyze current and historical facts to make predictions about future or otherwise unknown events.
PREDICTIVE CRIMINOLOGY / POLICING
Predictive policing refers to the usage of mathematical, predictive analytics, and other analytical techniques in law.

PHYSIOLOGICAL PSYCHOLOGY
Physiological psychology is a subdivision of behavioral neuroscience (biological psychology) that studies the neural mechanisms of perception and behavior through direct manipulation of the brains of nonhuman animal subjects in controlled experiments.
MENTAL PSYCHOLOGY
Mental health, defined by the World Health Organization (WHO), is "a state of well-being in which the individual realizes his or her own abilities”.
CRIMINAL PSYCHOLOGY
Criminal psychology, also referred to as criminological psychology, is the study of the views, thoughts, intentions, actions and reactions of criminals and all who participate in criminal behavior.
241
PRE-CRIMINAL BEHAVIOR
Crime (or precrime or precriminal behavior) term coined by science fiction author Philip K. Dick. It is increasingly used in academic literature to describe and criticized the tendency in the criminal justice systems to focus on crimes not yet committed.
BEHAVIORAL ACTIVITIES
What Influences Criminal Behavior? Criminology Has Uncovered A Number Of Factors That Can Lead Someone Toward Crime.
CRIMINAL ANALYTICS
Crime analysis is a law enforcement function that involves systematic analysis for identifying and analyzing patterns and trends in crime and disorder.
THREAT PREDICTIONIDENTIFICATION - SECURE
Real Time Threat Prediction, Identification and Mitigation for Critical Infrastructure Protection Using Semantics, Event Processing and Sequential Analysis.
CYBER SECURITY
Cyber security refers to the body of technologies, processes, and practices designed to protect networks.
DEFENSE FROM CRIMINALS
The criminal law covers various punishments for offences which vary from case to case.
DL-DEEP LEARNING

DATA SCIENCE
AUGMENTED REALITY

243

LUIS ALBERTO FLORES HERNANDEZ
PhD
Ambassador of Peace, International Organization for Peace & Development. The Royal House of Baloi, Royal Member/Patron
Dren Doctor of Philosophy in Criminology. PhD from Cambridge International University.
Doctor Degree of Philosophy Political Sciences and International Relations.

Ph.D. Specialized in Foreign Policy, Social Policy, Public Policy, Government, and Bureaucracy, Harvard University.

Degree in International Law from the Military University of El Salvador, Diploma in Cyberlaw, Cyberspace.

Master's Degree in Criminology: Crime and Victimology. By the International University of Valencia.
Member of: EPALE Electronic Platform dedicated to adult education in Europe, European Commission. Specialized training in Gender
Violence, Cybercrime, Cyberspace, Organized Crime and Criminal Profiling. Non-Verbal Communication.
Diploma in Cybersecurity and Fight against Cybercrime. By C1B3R
WALL ACADEMY.
Bachelor of Science in Criminology.
B.Sc. at Cambridge International University.
Current Positions: 2020 Leadership at Karthic Labs.
2021 International External

 By: Alfredo Lacayo Evertsz
By: Alfredo Lacayo Evertsz

QML Algorithm 'FINANCIAL QBITS.' Upgrades 500-year Financial Paradigm And
Promises To Help Boost The Economy
Introduction
Exploiting the exotic properties of quantum theory, we can build ultrafast information processing systems (AKA: computer algorithms). This quantum advantage is expected to optimize both, classical and quantum information processing (IBM Research, 2016).
We can prove that this works with an algorithm that processes financial statements and thus, classical information.
What problem does this algorithm solve?

The global economy depends on the success of businesses. And yet, countless business teams lack an essential element that hinders their growth and success: financial literacy.
This problem can be solved with training but the traditional paradigm to become financially literate in the business world is extremely complex. This makes it intellectually taxing and intimidating because it is made up by countless concepts that take one textbook and at least one year to learn. The traditional scheme was observed in the work of Luca Pacioli in 1494 and it is one of the few things that have not been upgraded since the Renaissance. In fact, it is still used even by the top 10 US business schools as ranked by US News & World Report, 2022.
The complexity of Pacioli’s scheme keeps many people in business from having a clear and solid understanding of financial statements. This affects their ability to interpret them and make savvy business



249
decisions, affecting the performance of entrepreneurs, executives, business owners, portfolio managers, credit analysts, business consultants and bankers, to name a few. Given its implicit harm to the economy and the looming financial uncertainty, a radical renovation to this paradigm is much needed ASAP.
This is why Qbit Solutions Research Team (QSRT) created Financial Qbits, a QML algorithm that provides a long overdue educational upgrade to Pacioli’s scheme. With Financial Qbits, people can learn in 10 hours what would normally take at least one year with the traditional scheme from 1494. This is because Financial Qbits exploits the exotic properties of quantum computing and deep learning to condense the infinite complexity of the traditional paradigm into one visual information processing unit that makes financial statement information much easier to learn and apply.
Successful Financial Qbitsbased training programs have been hosted by the University of Rhode Island (URI), by Florida International University (FIU) and by Florida Atlantic University (FAU). Hacia Ganancia, an online financial training program funded by JPMorgan Chase, was entirely based on Financial Qbits’ visual algorithm. Hacia Ganancia surpassed all key performance standards.
How does Financial Qbits work?

Nutshell explanation:
Through quantization, the infinity of Pacioli’s traditional concepts was condensed down to a minimal-complexity wave function that encodes the answer to all conceivable problems in just 12 multistate qubits. The qubits span from an abstract/unobserved level to a concrete/observed level. They represent doubleentries: binary interactions, in which Alice sends an amount of wealth to Bob.
These basic financial transactions are the indivisible building blocks, or pixels that can be used to reconstruct all financial statements and thus, all financial stories from scratch. Therefore, doubleentries are the quanta of this field (Lacayo & Bravo, 2020).


Notice that quantization reveals a highly entangled architecture (Levine, et al., 2019), where complexity scales linearly, not
exponentially (Huggins, et al., 2018) and it enables quantum states across a phase transition to require only a very small training data set (Caro, M., et al., 2022). This simple structure literally contains at least one textbook worth of information because it encapsulates all of Luca Pacioli’s Double-Entry System in a state of potentiality at its minimal complexity level. How is this useful?
251






Using this minimalcomplexity wave function as a computational resource (Biamonte, 2016) by following eight (8) computable steps, we obtain ultra-fast processing of financial statements, one qubit at a time. This translates to hyperfast financial literacy as it provides a shortcut to understand and analyze the story of a business at any given period of time.

What’s the quantum advantage?
With Financial Qbits, people can learn in 10 hours what would normally take at least one year with the traditional paradigm from 1494. Results are based on solid empirical evidence. Please see Empirical data – Proof of Quantum Advantage.
Has Financial Qbits encountered resistance in the quantum community?
Some scientists, especially those with a strong background in theoretical physics, consider that Financial Qbits is good progress in applying quantum theory to solve real world problems. Others, who normally have more of an experimental background and not as strong theoretical background, claim that the qubits on FQ refer to classical entities and that therefore, it cannot be considered quantum. QSRT’s response is that FQ’s qubits represent classical entities because it processes financial statements, which, yes, they are part of the classical world. However, as Dr. Charles H. Bennet from IBM Research points out, the advantage of applying quantum principles to compute information, works for processing both, classical and quantum information (IBM Research, 2016). Therefore, the fact that Financial Qbits processes classical information, does not take away from its quantumness.
Financial Qbits should come as no surprise. After all, quantum effects are expected to be found at the base of all reality and there is no reason why financial accounting, a field of discrete information units, should be the exception. In fact, this is great news for the quantum community because FQ’s simplicity should prove, even to “anti-hypes,” that quantum computing is indeed a practical science that can produce useful tools.
Quantum/Tensor network theory postulates:
Atomicity/discreteness – A system is discrete, or pixelated when it is made up by a fundamental building block from which the entire system can be reconstructed from scratch. In this case, the double-entry.
us to “zoom out” and understand the system as a whole.

Superposition of states – All probable outcomes are in a state of simultaneous existence until a measurement, or observation is made, which collapses the wave function into just one outcome.
Time-reversibility - The effects of an event can be reversed by another event with opposite orientation. This implies that the system is consistent with the Wheeler-DeWitt equation and its notion of timelessness (DeWitt, 1967).
Entanglement – Immediate connection between different elements without necessarily having direct contact.
Emergence – Holistic, or macroscopic structure that results from the collective interactions at the microscopic level that allows
Financial Qbits’ wave function is a multi-layered network of interconnected qubits, in which Entanglement would be the glue that holds the qubits together (Orús, 2014) across
257


259
different states, or phases; forming multi-state qubits.

Operators - For each measurable parameter, there is a physical characteristic that describes it (Hyperphysics, 2016).
Deep learning postulates:
Meta-learning - Ansatz, or pre-existing assumption that serves as the “optimal initial state” (Pranay, et al., 2022).
Concept encoding at different layers of abstractionConcepts can be expressed as a hierarchical encoding of nodes and connecting dynamics at many layers of abstraction (Serb & Prodromakis, 2019).
Information reuse (AKA: Information recycling)Information gained from one layer can be used as an input for the next layer up (Levine, et al. 2019).
Empirical data – Proof of Quantum Advantage
Empirical evidence shows that Financial Qbits helps people learn in 10 hours what would normally take at least one year with the traditional paradigm from 1494. We measured the new paradigm’s effectiveness using a pretest/posttest performance study. Test takers were 400 business professionals trained with the traditional model, 40 of them accountants. The pretest asked how to solve two hypothetical business transactions. None of the test takers was able to answer both questions correctly; five were able to answer one of the two questions; 395 were not able to answer either, which means that the success rate was less than 1.25%. After training with the new QML-based training program, 77.5% of the group was able to pass a test of equal difficulty as the pretest; an improvement greater than 75%.
Today, with Financial Qbits’ new web app version, even people with no background in finance or accounting, are consistently learning on an average of 10 hours what would normally take one year with the traditional paradigm.

QML literacy objectives: Speak the language of the quantum, understand a ground-state quantum wave function and the six postulates that make it work, learn how a wave function/tensor network can be used as a computational resource for hyperfast computation, grasp the Deep Learning postulates of Metalearning, information encoding at different layers of abstraction and information reuse.
Financial literacy objectives: Speak the language of accountants in record time, build financial statements from scratch to have a true understanding of the
numbers and perform basic financial analysis to evaluate the condition of a business. All in 10 hours.
Financial Qbits provides a unique opportunity for business people and QML enthusiasts to obtain a shortcut to understand financial statements and a ground-state wave function once and for all. Given its radical improvement over the traditional paradigm from 1494 for its clear quantum advantage, Financial Qbits is poised to help boost the economy and it is an important victory for the ongoing second quantum revolution.
“Welcome to the new financial paradigm!”
Alfredo
Lacayo Evertsz

ALFREDO LACAYO
EVERTSZ is head researcher and cofounder of Qbit Solutions Research Team (QSRT), the creator of Financial Qbits, the first useful and usable by all commercial application of quantum computing technology, which was completed after more than 10 years of R&D in Quantum Information Science, Tensor Network Theory & Deep Learning. Financial Qbits has taught financial accounting to more than 1,000 people, including 500+ SBDC clients and it has been hosted by the University of Rhode Island (URI), by Florida International University (FIU) and by Florida Atlantic University (FAU).
Hacia Ganancia surpassed all key performance standards. Alfredo was named Super Star Champion of Change in 2018 by the SBDC@FIU for his educational creation’s impact on the business community. He has been general manager in the securities industry and a certified stock broker for international stock exchange markets. Alfredo is a finance graduate from the University of Florida and has written four (4) papers with his team, the most recent one being: “Deep Learning by a Unitary Tensor Network Algorithm Provides Hyperfast Financial Literacy.” Evertsz has a Bachelor’s of Science in Finance, Business Administration from the University of Florida.

TECHNOLOGY IN THE MAKING

Linda Restrepo | Publisher
Editor
VECTOR N360 ™ © INNER SANCTUM
-
TECHNOLOGY IN THE MAKING
DISCLAIMER: This Magazine is designed to provide information, entertainment and motivation to our readers. It does not render any type of political, cybersecurity, computer programming, defense strategy, ethical, legal or any other type of professional advice. It is not intended to, neither should it be construed as a comprehensive evaluation of any topic. The content of this Presentation is the sole expression and opinion of the authors. No warranties or guarantees are expressed or implied by the authors or the Editor. Neither the authors nor the Editor are liable for any physical, psychological, emotional, financial, or commercial damages, including, but not limited to, special, incidental, consequential or other damages. You are responsible for your own choices, actions, and results

Linda Restrepo |
Publisher - Editor







 By Patrick Pascal
By Patrick Pascal

































 Linda Restrepo Editor | Publisher
Linda Restrepo Editor | Publisher

















































 Edificio Valori at Peking University
Edificio Valori at Peking University


 hi resolution capture of the wheather balloon sure... Check the dome camera's and computers.
hi resolution capture of the wheather balloon sure... Check the dome camera's and computers.



















































 The architecture of a quantum computer Draw by the author.
The architecture of a quantum computer Draw by the author.




 Representation of the different forms of an operator Draw by the author.
Representation of the different forms of an operator Draw by the author.


















 By: Alfredo Lacayo Evertsz
By: Alfredo Lacayo Evertsz









