Version: V4.1
Ratified by: Finance & Risk Committee
Date ratified: 26/10/2022
Job Title of author: Information Governance Manager
Reviewed by Committee or Expert Group Technology Programme Board
Equality Impact Assessed by: Information Governance Manager
Related procedural documents

IGPOL53 Information Security Policy
IGPOL65 Transferring of Confidential Information Policy
Review date: 06/10/2025

It is the responsibility of users to ensure that you are using the most up to date document template – i.e. obtained via the intranet

In developing/reviewing this policy Provide Community has had regard to the principles of the NHS Constitution.

Version Control Sheet
Version Date Author Status Comment
V1 28/08/15 Information Governance Manager and Operational IT Manager. Virtual Review byHub NewPolicy Replaces IGPOL49 –Internet Policy and IGPOL48–Email Policy. Includes Social Media Guidance.
V2 19/01/2018 Information Governance and IT Projects Manager 2YearReview
V3 23/05/2019 Information Governance and IT Projects Manager InterimUpdate Inclusion of whentousethe BCC field to protect confidentiality
V4 27/10/2021 Information Governance and IT Projects Manager 2yearreview
V4.1 18/5/2022 Information Governance and IT Projects Manager Interimreview Update to Use of Public Networks



1. Introduction
Provide Group (hereafter referred to as “the organisation”) wishes to encourage the correct and proper use of the Internet, Email, Instant Messaging Systems and Social Media Sites and expects staff to use these facilities during the normal course of work. The organisation encourages the appropriate use of these systems by staff and to increase their competence and understanding of their potential.
This policy determines how Provide staff can use these services professionally, ethically and lawfully without compromising patient or staff confidentiality and whilst maintaining the security of the IT network.
The use of these systems are intended primarily for Provide business related purposes or professional development and training that supports the goals and objectives of the organisation. Staff should therefore use them primarily for the legitimate business of the organisation and within the bounds of their authority.
2. Scope
This policy applies to all directly and indirectly contracted staff and other persons working for the organisation:
• All Provide employees whilst engaged in work for the organisation at any location, on any computer or internet connection (including mobile phones).
• Any other uses by Provide employees which identify the person as a Provide employee or which could bring the organisation into disrepute on any computer or internet connection.
• Other persons working for the organisation, persons engaged on Provide business or persons using Provide equipment and networks; and
• All usage by anyone granted access to the organisation’s network or to Guest Internet facilities.
Additionally the policy applies to:
• *.nhs.net email accounts for business and personal use on Provide and nonProvide premises including from home, internet cafes and via portable devices (e.g. Mobile phones)
• Any Provide systems whether clinical or otherwise that allows for the sending of electronic messages either indirectly through an NHS Mail account or through integrated messaging capabilities. For example, email and instant messaging functionality in SystmOne or MS Teams, Pando, Webex, or Cisco Jabber.
3. Definitions
Where referenced within this Policy the term ‘data’ may refer to either the organisation’s business data or person identifiable data (PID) – this includes patients, staff, visitors and suppliers.

Any references to ‘Internet’ in this document covers Web browsing, webmail and any other services available from the global Internet or HSCN Network
Offensive material referenced in this policy includes but is not restricted to: hostile text, images, videos or voice relating to gender, ethnicity, race, sex, sexual orientation, religious or political convictions and disabilities.
Instant messaging, often shortened to simply "IM" or "IMing," is the exchange of text messages through a software application in real-time. Instant messaging differs from ordinary e-mail in the immediacy of the message exchange and also makes a continued exchange simpler than sending e-mail back and forth. Approved Instant Messaging systems in the organisation are Cisco Jabber, Cisco WebEx, Pando, Telegram and TPP SystmOne Instant Messaging.
4. Responsibilities
4.1
Responsibilities of the Organisation
The organisation must provide a ‘Duty of Care’ to all its employees by ensuring that, whilst within the workplace, they are protected from information and activities that are classed as ‘socially unacceptable’ or pose a threat to the Confidentiality, Integrity and Availability of the organisation’s data.
4.2
Responsibilities of all Staff
All staff are obliged to adhere to this policy. It is the responsibility of the individual to ensure that they understand this policy. Managers at all levels are responsible for ensuring that their staff have read and understand their obligations in relation to this Policy.
5. Access to Internet and Email
Internet and Email are available to all staff that are registered as users of the computer network. Staff may only use these services while they remain employees of the organisation. An NHS Mail account may be retained by the employee if they move to another NHS provider or NHS healthcare organisation. Internet Access is given to staff by default when a request for a network user account is made by the user’s line manager. Requests for an Email account must be made through the online Provide Technology Selfservice portal: https://servicedesk.provide.org.uk
In order for staff to receive email services, or to change an existing account this must first be approved by an appropriate manager. Any changes to an existing email account must be requested through the Technology self-service portal as above.
Staff can make certain changes to their NHS Mail accounts themselves by logging in through the web portal (www.nhs.net). This includes changes to contact details, address, roles, speciality and work areas.
Access to networks and websites on the HSCN network will only be accessible from Provide issued equipment which includes desktop PCs and mobile devices. Users with

portable devices such as laptops and tablets connect using a virtual private network (VPN) facility called Direct Access which will route onto the HSCN secure gateway and afford the same levels of security.
Use of Public Networks
Wi-Fi that is available in coffee shops, hotels and other public places can often be insecure and should not be used for work purposes.
Whilst Provide laptops benefit from an always-on Virtual Private Network (VPN) and group companies are issued with an alternative VPN solution, this does not make use of public networks completely secure as this only offers protection when communicating with the Provide network or systems within the HSCN environment.
In circumstances where there is a legitimate need to work in such places, the safest way to connect is to tether to a work issued or approved mobile phone. If there is any doubt about the safety of a connection, the user must contact the Provide Service Desk for advice.
5.1 Guest Internet Access
Guest Wireless Internet Access is provided at various sites for non- Provide issued laptops and mobile devices. This is a separate internet service to ensure that there are no security risks to Provide’s internal data and systems and the wider NHS HSCN network. This service is to allow external contractors and guests (and staff using personal devices) to connect to the internet, as well as videoconferencing facilities.
It is prohibited to connect Provide issued equipment to the guest internet without prior authorisation from the Provide Technology Department. Staff are however permitted to connect provide issued mobile phones to the guest wireless internet.
Personal devices connected to the guest internet are not supported by the Provide Technology Department and the guest wireless is supported via best endeavours and should not be relied upon.
It is prohibited to connect personal computing equipment such as laptops, tablets, mobile phones and also Provide issued mobile phones to the internal network in order to receive internet access.
5.2 Blocked Websites
To reduce the risk to individuals, the organisation has implemented software that restricts access to sites based on their categorisation.
The monitoring software maintains a database of website categories to which access is monitored, because they are deemed inappropriate for access at work. The following categories are blocked by the antivirus and firewalls (N.B this list is not exhaustive):
• Pornography / Adult/ mature content;
• Gambling/ betting;
• Alcohol/ Tobacco (see 7.3 below);
• Illegal drugs (see 7.3 below);

• Auction sites;
• Personal dating;
• Spyware/ malware sources;
• Violence/ hate/ racism/ intolerance;
• Weapons; and
• Any site engaging in, encouraging or promoting illegal activity.
Web Mail Services and Messaging Services other than NHS Mail, SystmOne Messaging, Cisco WebEx and Cisco Jabber
The following categories are blocked on the guest internet access (where provided):
• Alcohol
• Adware
• Anime/ Manga/Webcomic
• Dating
• Drugs
• Gambling
• Forums/ Message Boards
• Hate/ discrimination
• Lingerie/ Bikini
• Nudity
• P2P/ File Sharing
• Pornography
• Proxy/ Anonymiser
• Sexuality
• Tasteless
• Tobacco
• Typo Squatting
• Weapons
• Web Spam
It is accepted that legitimate sites may, because of language and or visual images, be incorrectly classified by the screening software but that staff may need to access these sites in order to carry out legitimate Provide business. In these instances it is possible to have such sites entered into an exceptions database and access to the site enabled. In such instances a call should be logged with the Provide Technology Service Desk.
No member of staff is allowed to alter or tamper with their PC internet settings or use additional software for the purpose of bypassing or attempting to bypass the Internet filtering and monitoring software. Doing so is considered a serious breach of IT network security and this policy and may result in disciplinary action which may lead to dismissal.
6. Personal Use
The use of the internet on the organisation’s internal network connection and the NHS Mail Email system is intended primarily for business use so that staff can access the Intranet, approved web hosted applications, undertake research, professional development and training and to access other information relevant to work.
Limited personal use of Internet and Email facilities are permitted provided it is consistent

with the organisation’s code of conduct and does not interfere with the performance of your duties
6.1 Personal use of Email
Employees must regard this facility as a privilege that should normally be exercised in their own time without detriment to the job and not abused. Inappropriate or excessive personal use may result in disciplinary action and/or removal of email facilities. Staff should be aware that both private and legitimate Provide business use of email will be subject to monitoring. There is no absolute right for staff to use the email facilities for personal use.
Use of Webmail systems (e.g. Hotmail, Gmail, etc.) on work equipment, other than NHS Mail (for personal use), are prohibited.
6.2 Personal use of the Internet
The organisation will not be held liable for any financial or material loss to an individual user in accessing the internet for personal use.
Employees wishing to spend significant time outside their own normal working hours using the Internet, for example, for study purposes, should obtain Line Manager approval. It is the Line Manager’s responsibility to file the approval appropriately and to copy the approval to the member of staff.
Social Media, such as Facebook, provide a number of benefits in which Provide staff may wish to participate in their personal life. However, when someone clearly identifies their association with the organisation and/or discusses their work, they are expected to behave appropriately, and in ways that are consistent with both the organisation’s values and policies and their individual responsibility as an employee of the organisation. See Appendix 1 for the organisation’s policy on Social Media.
Please note, the use of WhatsApp messaging application is not permitted for sharing patient identifiable data or for encouraging service users to register/join a WhatsApp group to receive Provide delivered service, support or communication. Please use approved applications for this purpose. Please discuss options with the IG department.
7. Sending and Receiving Emails
The organisation has chosen NHSmail as its primary email system due in part to the security features that this system affords.
Acceptable methods of sending information by Email are listed within the Transferring of Personal Information Policy.
Key messages:
• Use email only when it is the most appropriate means of communication;
• Communicate only with those who are required to read the message to avoid breach of confidentiality;

• Use the Global Address Book with care to ensure email reaches the correct recipient;
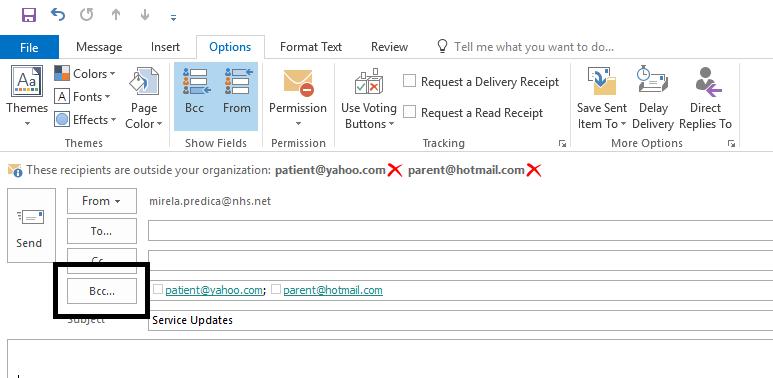
• Use the Blind Carbon Copy (BCC) feature in outlook or NHSmail web portal when sending an email message to a number of people where you need to safeguard security and privacy (See Appendix 5)
• In the event of a mistake,use the ‘recall’ message tool, but be aware that thisfacility is not fail safe;
• File attachments should only be sent via email when absolutely necessary and should be deleted as soon as is practicable. Ideally place large attachments in a shared location (where possible) and include the path to the file in the email. Make use of approved tools to minimise size of attachments, eg Portable Document Format (PDF).
7.1 Large numbers of recipients
Be selective about who you send messages to. Place large attachments in a shared location or in an appropriate shared folder and send only the link to the location.
Use the Blind Carbon Copy (BCC) feature in Outlook or NHS Mail portal where you need to safeguard security and privacy (See Appendix 5)
7.2 Global emails
Global emails are intended only for communicating high-level information relating Provide business within the organisation.
All messages must have a named signatory and be approved by an appropriate Head of Department or Director and/or the Communications Team before they are sent. If you wish to reply to a global email message, only reply to the named contact at the bottom of the email. Do not respond globally as this takes up unnecessary storage space on email servers
Global e-mails from Provide staff must only be sent by the communication team from the Provide Communication email address. Requests for communications approval and sending of global emails should be sent to provide.communications@nhs.net
7.3 Email received in error
Inform the sender if you receive a message sent to you in error. Delete the message from your mailbox.
Emails that contain unintentionally disclosed personal data thus represent a breach in the data subject’s confidentiality and must be reported in line with the organisations incident reporting policy.
7.4 Phishing email

If you receive an email with suspicious or clearly fraudulent content do not open the email and do not respond to the email or provide your credentials via the link on the email. Delete it immediately. Do not respond as this indicates an active mailbox.
If you are not sure if the email is genuine, please report it to the service desk. Open the service desk portal service desk and open the “I need Something” option. In there they will need to open “SPAM Email” request https://provide.freshservice.com/support/catalog/items/74. Then follow the instructions in the request and upload the email as an attachment and submit.
If you open or respond to a phishing email, you must immediately switch off your device and contact the IT Service desk for assistance.
7.5 Email with warnings about criminal activity / frauds/ scams
Where there are genuine security matters that staff need to be aware of these will be notified by the Police to NHS Security Management specialists who in turn will issue warnings or guidance to staff.
If you receive email purporting to give warnings about criminal activity or scams please do not forward these on to colleagues. Many of these are junk chain letters that have been circulating in one form or another for some time. Please check with the organisation’s local security management specialist in the first instance.
Spam emails should be forwarded to the NHS Mail Service desk so that these can be blocked and investigated if necessary (spamreports@nhs.net)
7.6 Managing Emails during staff absence
Emails and attachments created or received by staff in the course of their duties, are the property of the organisation.
Staff should make arrangements for their emails to be managed during planned absences and use the Out-of-Office message facility to advise contacts of their unavailability and who to contact in their absence
There may be some occasions when it is necessary to access email correspondence from an individual’s mailbox when a person is away from the office for an extended period, e.g. sudden illness or failure to make adequate arrangements for planned absences. The reasons for accessing an individual’s mailbox are to action business information i.e:
• Subject Access requests made under the Data Protection Act;
• Freedom of Information request;
• Evidence in legal proceedings;
• Evidence in a criminal investigation; and
• Line of business enquiry or other information relevant to the organisation.
Where it is not possible to ask the permission from the member of staff whose mailbox needs to be accessed, the procedure for gaining access to their mailbox is to:
• Gain authorisation from the Service/ Department lead;
• Submit a request to the Provide Technology Service Desk;

• A record is made of the reasons justifying access to the mailbox together with the name of the authorised person;
• Only one person who is senior to the absent employee should be authorised to gain access;
• Access is kept to a minimum on a strict need-to-know basis;
• An Out-of-Office message is set-up to alert subsequent contacts of the unavailability of the addressee;
• The need to access the in-box is reduced by using the ‘forward email’ function; and
• Inform the person whose mailbox was accessed as soon as it is practical to do so.
Authorised access to another person’s inbox is provided for the continuation of business purposes only. Access must be justified as a business purpose and kept to a minimum to meet that need. Emails that are clearly personal communications must not be accessed under any circumstances
Advice must be sought from the Information Governance Manager where there are grounds to access personal emails.
The Provide Technology team, reserves the right to inspect the content of an email, including personal emails, if there is credible reason to believe that it contains evidence of unlawful activity, including instances where there may be a breach of policy constituting gross misconduct, or where there is reason to believe that it contains harmful material e.g. a file containing a worm or virus, or where the law requires it.
It is less likely that this procedure will need to be followed if email records are managed appropriately or mailbox access has been delegated to a trusted third party.
7.7 Non-delivery report, delivery reports and receipt reports
If a message is not delivered, you will receive a non-delivery report. This will normally identify the cause of non-delivery such as incorrect address, unavailable end system, etc. Look at this information first before raising a request for support, as you may just need to correct the address.
Delivery reports indicate that the email has been successfully sent and will only be returned if the sender has requested it.
Receipt notifications indicate that the recipient has opened the email. Remember that the recipient may not have read or acted upon the email, as a personal assistant or administrator may have read the email on behalf of the recipient.
Delivery reports or read receipt notifications should only be used when you need positive confirmation that a message has been received and read.
7.8 Formation of Contracts
Email is capable of forming or varying a contract in just the same way as a written letter. Such capability gives rise to the danger of employees inadvertently forming contracts on behalf of the organisation or varying contractual terms to which the organisation then becomes bound. For example sending an ambiguous email to a contractor or supplier that could be misread as asking them to undertake some work on behalf of the organisation could be deemed a legal contract. Employees should take due care when drafting the words of an email so that they cannot be construed as forming or varying a contract when

this is not the intention. Please contact the contracts team if in any doubt, at provide.contracts@nhs.net
7.9 General rules for Email
You must not:
• Use other people’s mail accounts to send your emails;
• Give others authority to view or amend your mailbox unless fully justified;
• Engage in any activity, which is illegal, offensive or likely to have negative repercussions for the organisation;
• Allow third parties to read personal or confidential data in emails by leaving your screen in view of such third parties;
• Read other people’s emails sent to someone else, without their express permission;
• Create or send any offensive, obscene or indecent images, data or other material;
• Initiate or propagate any provocative exchanges of email;
• Initiate or propagate electronic chain letters or junk email;
• Engage in unauthorised selling or advertising of goods and services;
• Create or send messages that may constitute racial, sexual harassment or harassment on the grounds of a disability;
• Send any unsolicited commercial or advertising material either to another user or organisation(s);
• Forge, use a false identity or anonymously send emails
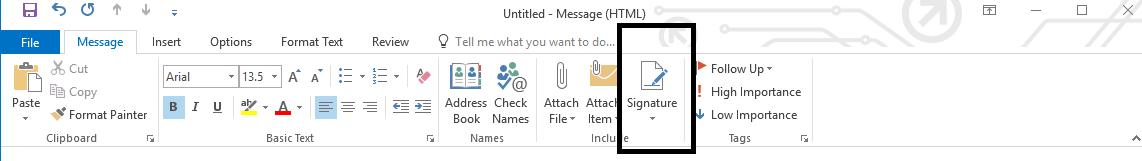
7.10 Email Signatures
All staff should adhere to a consistent email signature. Please see Appendix 4, Email Signature Guidelines.
Directorate/department specific additions/amendments to this format must be approved by the Head of Service initially and then by the Communications Team, to ensure consistency across Provide
Provide Email Signatures must only be used on Provide issued NHS Mail accounts.
8. Use of Instant Messaging for work
The organisation has approved the use of, TPP SystmOne Instant Messaging (IM), Cisco Webex, Pando, Telegram and Cisco Jabber as Instant Messaging services for use to carry out Provide Business. The use of other IM Systems (including Whatsapp) to conduct Provide Business are strictly prohibited and approval must be sought from the Technology Programme Board.
Instant messaging has a place to play in communication with colleagues but it is not always the best way of communication so please consider the following points.
• Some members of staff do not like this way of making contact therefore please respect individual views when deciding methods of contact.

• If your message requires the recipient to do something, consider using email as there is no way to save an instant message so actions can easily be forgotten.
• Remember that you are ‘interrupting’ the recipient so consider if this is the best way to contact them.
• A message can be sent even if the recipient is not in front of their computer so there is no guarantee the person is actually going to get the message.
• Any patient related communication must be attached to the patient record.
Consider using Instant Messaging in the following type of circumstances:
• To tell a clinician their patient will be late
• ‘Can you call me when you have a minute’
• To ask a question when you do not want the patient or other individual to overhear you.
What it is not for:
• It is not to be used as a ‘chat room’ It is not a replacement for email
9. Personal use of Social Media Sites
Social media is the term commonly used for websites which allow people to interact with each other in some way - by sharing information, opinions, knowledge and interests. As the name implies, social media involves the building of online communities or networks, encouraging participation and engagement.
Social networking websites (such as Facebook, Instagram, Snapchat, Twitter and Google +) are perhaps the most well known examples of social media, but the term covers other web-based services. Examples include Blogs, audio and video podcasts, ‘wikis’ (such as Wikipedia), message boards, social bookmarking websites (such as del.icio.us), photo, document and video content sharing websites (such as Flickr and YouTube and Instagram), or micro-blogging services (such as twitter)
These media provide a number of benefits in which Provide staff may wish to participate in their personal life. However, when someone clearly identifies their association with the organisation and/or discusses their work, they are expected to behave appropriately, and in ways that are consistent with both the organisation’s values and policies and their individual responsibility as an employee of the organisation.
The intention of this Policy is not to stop staff from conducting legitimate activities on the Internet, but serves to highlight those areas in which problems can arise for both individual staff members and the organisation. Please note there have been several cases where staff have been dismissed by their employer for inappropriate use of a social networking site or other media.
To this end when identified as a Provide staff member (for example by use of e-mail address, by joining a NHS or health related network on social network sites or by making reference to Provide as your employer), staff:
• Must not reveal confidential information about our patients, staff, or the organisation;

• Must not discuss work-related issues online, including conversations about patients or complaints about colleagues. Even when anonymised, these are likely to be inappropriate.
• Must not engage in activities on the Internet which might bring the organisation into disrepute;
• Must act in a transparent manner when altering online sources of information such as websites like Wikipedia;
• Must not use the Internet in any way to attack or abuse colleagues; and
• Must not post derogatory or offensive comments on the Internet about colleagues, their work or the organisation
• Must not build or pursue relationships with service users, even if they are no longer in your care.
• Must not post pictures of service users on Social networking sites or other websites (even if they ask you to do so).
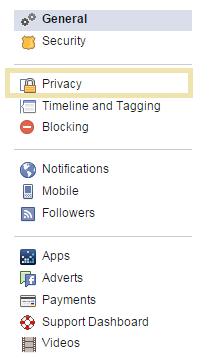
• Must be aware that even applying privacy settings in Facebook (and other social networking sites) does not mean that any postings will be kept out of the public domain. These postings could be copied by people entitled to access them and sent on to others beyond the original posters control.
Any online activities associated with work for the organisation should be discussed and approved in advance by a Line Manager and by the organisation’s Communications team where necessary.
Please refer to Appendix 1 for guidance on using Social Media Responsibly
10.Viruses and Malware
Viruses and Malware can damage computer systems, destroy data, cause disruption and incur considerable expense for the organisation. The Provide Technology department will ensure that computers connected to the network have appropriate virus protection software and that this is updated as appropriate.
Employees must not open email attachments or download documents from external sources unless they are sure of their authenticity. If in doubt seek clarification from the sender or the Provide Technology Service Desk. Areas expecting emails from unknown sources should request a code be inserted in the tile/subject heading eg a job vacancy code.
If any viruses are found or you suspect that your machine may be infected, the Technology Service desk must be informed immediately (0300 303 9955)
It is forbidden to download or send executable computer programme files as attachments, without prior consent from the Provide Technology Service Desk. The downloading and subsequent use of any software without the prior approval of the Service Desk is strictly forbidden (this includes screen savers).
It will be considered a serious breach of this policy if an email user deliberately infects or makes any attempt to infect the organisations or other network system with computer viruses.

11.Harassment
It is strictly forbidden to send messages that contain offensive or harassing statements or language, particularly in respect of race, national origin, sex, sexual orientation, age, disability, religious or political beliefs. Remarks sent by email, instant messaging systems or other internet services that are capable of amounting to harassment may lead to complaints of discrimination under the Sex or Disability Discrimination Acts or the Race Relations Act
12.Defamation
The ease of use of email and Instant Messaging systems can lead to unguarded and impetuous comments being made, which in turn could be classified as defamatory. Defamation arises where there is the publication of an untrue statement tending to lower the subject of the statement (which may be an individual or an organisation) in the estimation of the public generally. Liability for the tort of defamation applies to electronic communication just as it does to more traditional forms of publishing. Any expression of fact, intention and opinion can be held against the author and/or the organisation, therefore do not include anything in a message you are not prepared to account for or defend. Employees are therefore advised to take care when sending messages to ensure that they are not defamatory, incur liability on the part of the organisation or adversely impact on the image of the organisation.
13.Copyright
Email, Internet and Instant Messaging Users must observe all contractual, copyright issues. Under the Copyright, Designs and Patents Act 1988, copyright law can be infringed by making an electronic copy or making a ‘transient’ copy (which occurs when sending an electronic message). Copyright infringement is becoming more commonplace as people forward text, graphics, audio and video clips. Employees must not copy, forward, upload or otherwise disseminate third-party work without the appropriate consent
14.Confidentiality
Employees are reminded that they are bound by the common law duty of confidence and the Data Protection Act 2018 and General Data Protection Regulations (GDPR) which apply to person identifiable information of patients, staff, contractors or third parties. Any disclosures of person identifiable information should be done in accordance with the organisation’s Data Protection Policy.
Confidentiality of other information that is not person identifiable may be protected under legislation associated with the Freedom of Information Act 2000.
15.Breach of Policy
Staff will be liable to disciplinary action if they are in breach of this policy and depending on the severity of the offence staff may be liable to summary dismissal.

The distribution or the accessing of any information via the Internet, Email and Instant messaging Systems is subject to UK law and any illegal use will be dealt with appropriately. Emails and Instant Messages both in hard copy and electronic form, are admissible in a court of law.
If staff conduct and/or actions are unlawful or illegal the individual may be personally liable. In the event of an accidental breach of this policy staff members must advise their line manager immediately so that appropriate steps can be taken to mitigate or remove any possible risk(s) e g the exposure and/ or loss of sensitive or person/ patient identifiable data.
16.Monitoring
The organisation has the ability and legal right to monitor Internet, email and Instant Messaging usage. By using these systems the employee consents to any monitoring the organisation considers to be appropriate. Monitoring will be conducted by the organisation as the most effective way of ensuring compliance with this policy.
Monitoring is required because the use of these systems for business purposes and personal use is subject to UK law, as well as regulations, standards, and guidelines issued by the Department of Health and the NHS. Any employee using these facilities illegally or inappropriately could put the organisation in breach of the law, for which the penalties can be severe.
All monitoring will be undertaken in accordance with the Telecommunications (Lawful Business Practice) (Interception of Communications) Regulations 2000 and the Regulation of Investigatory Powers Act (2000).
The organisation will always consider if any monitoring intrudes unnecessarily on an employee’s privacy and all monitoring will be carried out in accordance with current relevant legislation.
When monitoring takes place staff will be made aware of the purpose and extent of the monitoring to be carried out except for the purposes defined under ‘Monitoring without consent’.
Employees will be allowed to make representations about the information gathered through monitoring where it may have an adverse impact on them.
All staff have a right of access to information held on them, including information obtained through monitoring; such information may be withheld if by doing so it would prejudice the detection of a crime.
16.1 Monitoring of Internet Access
The organisation monitors all internet activity by staff. This is an automatic process, carried out by computer software, which records the volume of Internet traffic, the Internet sites visited, type of site and length of time of any visit to the site. This recorded information will be retained for analysis, and will be processed according to the principles of the Data Protection Act.

Reports will be monitored and action taken where necessary in line with this policy. Where required, reports can be requested by the Human Resources department, Senior Management and line managers.
Evidence of excessive personal use, inappropriate or attempted inappropriate use will be presented to the staff member’s Line Manager for appropriate action to be taken in accordance with the organisation’s disciplinary and dismissal policy and procedures.
No member of staff is permitted to access, display or download from Internet sites that hold offensive material. Doing so is considered a serious breach of security and may result in dismissal or prosecution.
16.2 Monitoring of Email
The organisation retains the right of access to and ownership of all email sent from and received by its systems.
When the monitoring of personal emails is necessary monitoring will be confined to the message address or heading wherever possible.
17.Review
This Policy will be reviewed every 2 years by the Information Governance and IT Projects Manager and the Technology Operations Manager. Earlier review may be required in response to exceptional circumstances, organisational change or relevant changes in legislation.