Introductionto5GandMobile Telecommunications November 2022





The Railway Industry Association (RIA) is the national trade association representing a large proportion of the UK rail supply chain,withover300membercompaniesfrom Tier-1stostart-ups (over 60% of our membership are SMEs) based across the UK.





RIA represent members’ interests to Government, major clients,regulators,andotherbodies:
Strong working relationships with Government and key clients.
Regular events with Ministers and politicians for members to join, feed into consultations, and a range of campaigns on major issues for the industry.
RIA host client workshops and meetings for members to engage directly with and feed back to clients including Network Rail, HS2, Transport for London (TfL) and East West Rail (EWR).
RIA host visits at member sites with politicians as part of our Rail Fellowship Programme.
RIAOfferaforumfordialoguebetweenmembers:
A substantial events programme every year, holding around 70 events. Our member-only InterestGroups are curated by our specialist technical and policy teams, hearing senior industry figures covering a wide range of subjects, initiatives and major developments.
Members can participate in rail industry committees or groups (e.g. our SME Group or Public Affairs and Communications Network) to network with industry colleagues.
Join our two flagship conferences each year: our Annual Conference, typically in November, Innovation Conference, late March, and our midsummer RISE Awards Dinner.
Wekeepmembersuptodatewithindustrynewsandinformation – with five weekly mailings, as well as a range of other communications which you can tailor to suit your interests.
Weprovideaplatformformemberstoshowcasetheirpositivenewsstoriesorexciting developments: Our Members News section of the website hosts press releases sent by members, which are then shared on our social media channels.
Wepromoteexportsofmembers’productsandservices: RIA hosts trade missions and events through our close relationship with the Department for International Trade (DIT), whom we partner with for our virtual and in-person trade missions.
Introduction to 5G and Mobile Telecommunications
Foreword
Recently, the term 'Industry 4.0’ has entered popular lexicon, heralding some of the biggest socio-economic changes since the widespread adoption of computers and the internet in the 1980s. The intervening decades have seen the ubiquitous automation of office functions throughOperationalTechnology(OT)andInformationTechnology(IT),both ofwhicharenow taken for granted in our everyday lives.
The ‘Fourth Industrial Revolution’ is well underway. We are witnessing the mass adoption of autonomous machines, advanced robotics, big data and analytics, the internet of things, digital ubiquity, cloud computing, smart factories, machine learning & AI, and cyber-physical interaction. Some of these terms may seem like space-age buzzwords, but the truth is that they are here right now, often masked by simple user interfaces which hide the advanced technology behind. For some techniques, current iterations belie potential future functionality - and its implications. Alexa: Filet steak and asparagus please. Rare. Pronto.
Whether functional now or aspirational, all are dependent upon communications: between devices, users, 'the cloud’, data stores, service providers and more. Communications are therefore one of the fundamental underpinnings of the ongoing digital revolution. Networks are a necessity for delivering Industry 4.0 because of the requirement for speed, bandwidth, and reliability. Public mobile will play a major part, and even more so with the roll out of 5G. However mobile communications in general, and 5G in particular, is often misunderstood by those not directly involved with technical implementation.
We hope that this RIA guide will allow our members to understand more about the topic, enabling them to scope, plan and execute projects. It has been created with the assistance of mobile data professionals from within our membership, but the advice provided within is agnostic to supplier. The guide is not prescriptive but instead gives general pointers and examples of good practicewhere possible. The aim was to provide a practical guide to aid the planning, specifying and delivery of rail projects, harnessing the full benefits of public 5G networks in the coming years.
Like all technical guides, it starts thick and fast with technical termsandacronyms!Ratherthandefinethemallas we go,we have instead opted to include a handy glossary up front.
We would like to thank our members for creating this guide. We hope it is of use to other members and, as always, we welcome any feedback – technicalteam@riagb.org.uk
Dr Sam Bemment, Technical and Innovation Manager, Railway Industry Association, October 2022.


3
Introduction to 5G and Mobile Telecommunications 4 Contents Foreword.................................................................................................................................................3 Contents..................................................................................................................................................4 Glossary of Terms....................................................................................................................................5 Network Data Technologies..................................................................................................................10 2G Service .........................................................................................................................................10 3G Service - Support ends 2022........................................................................................................10 4G – Current technology...................................................................................................................10 5G – Future technology ....................................................................................................................11 NB IoT................................................................................................................................................11 LTE-M................................................................................................................................................11 Network and Tariff selection ................................................................................................................12 Voice tariff with associated data bundle..........................................................................................12 Mobile Broadband............................................................................................................................12 M2M/IoT...........................................................................................................................................13 Quality of Service (QoS)....................................................................................................................13 Technical operation, specific events, and faults...................................................................................14 Mobile Cells.......................................................................................................................................14 Cell switching....................................................................................................................................15 ‘Network is down’.............................................................................................................................15 Mobile ‘Black holes’..........................................................................................................................16 Antennae (Aerials)............................................................................................................................16 Routers..............................................................................................................................................18 Dongles vs Routers............................................................................................................................18 Multi IMSI..........................................................................................................................................19 SIM Faults..........................................................................................................................................19 Roaming SIMs ...................................................................................................................................20 Cost of Failure...................................................................................................................................21 Security .................................................................................................................................................22 Data Path Diagrams ..........................................................................................................................22 Tips and questions for potential suppliers............................................................................................26
GlossaryofTerms
Term Definition Description
2G/3G/4G/5G n Generation
APN Access Point Name
Different types of mobile phone data systems offering varying speed and connectivity.
The name of a gateway between a GSM, GPRS, 3G or 4G mobile network and another computer network, frequently the public Internet. A mobile device making a data connection must be configured with an APN to present to the carrier.

Apps Applications
ATA Analogue Telephone Adapter
Backhaul
Cell
Individual mobile transmitter/ receiver
Small software programs that run on phones and tablets and perform specific tasks such as providing a location, playing video or music, editing photos etc.
Aplug-inadapter that converts ananalogue signal to a digital signal.
In hierarchical telecommunications networks, the backhaul portion of the network comprises the intermediate links between the core or backbone network, and small subnetworks atthe edge of the network connecting to the end destination.
Each Cell/Transmitter tower for a mobile network can hold several individual cells. Often cells from multiple operators can be housed onthe same physical towers, by motorways and in Cities, for example.
Circuitswitched
CyberEssentials
The traditional method of connecting a phone call where a physical path between sender and receiver is established.
Cyber Essentials is an online self-assessment questionnaire which relies on you being able to understand the questions and know the answers. A board member from your organisation must sign a declaration to confirm that all the answers are true. There are no checks on your IT systems.
5
Term Definition Description
CyberEssentials Plus
Cyber Essentials Plus includes the self-assessment questionnaire but a technical expert will also conductanauditonyourITsystems.Thismeansthat iftherewereissuesthatyouwerenotawareofwhen you answered the self-assessment questions, these would be picked up during this audit. As this assessment needs time from technical experts, it is more expensive than the Cyber Essentials assessment.
Cyber-physical
Datapackets
System is a computer based system in which a mechanism is controlled or monitored by computerbased algorithms.
Individual elements of digital data.
dB Decibel A measure of signal strength / gain for mobile technology.
eSIM Embedded SIM card. Originally eSIM technology (the ability to reprogram a SIM remotely) was exclusively available on a SIM that was permanently embedded in a device. This is no longer the case and eSIM technology is now available on removable plastic SIMs compatible with any device with a SIM slo. (See Multi IMSI)
eUICC
GGSN Gateway GPRS Support Node
Embedded UICC. Many people use eSIM and eUICC interchangeably. This might not strictly be accurate but works well if people remember that the technology is no longer exclusively an embedded technology.
A major component gateway in the data path of mobile networks.
to 5G and Mobile Telecommunications 6
Introduction
Term Definition Description
GPS Global Positioning System
A network of satellites positioned in earth orbit to determine the location of a GPS enabled device.
GSM Global System for Mobile Mobile phone systems that can transmit data as well as voice.
HighGain Refers to a High Gain Antenna
IMEI International Mobile Equipment Identity
IMSI International Mobile Subscriber Identity
Designed to increase the signal gain in less covered regions, A high-gain antenna (HGA) for example, could be a directional antenna with a focused, narrow radio-wave beam width.
An electronic serial number that identifies a piece of GSM enabled equipment such as a mobilephone
The unique identifying code of a subscriber on the mobile network.

IoT Internet of Things A collection of internet connected devices whichcan connect and communicate with each other and a central management system.
IPnetworks
Internet Protocol is a term used to describe the standard of communication used by internet connected devices.
IPsec Internet Protocol security A set of protocols that provides security for Internet Protocol. It can use cryptography to provide security. IPsec can be used for the settingup of virtual private networks (VPNs) in a secure manner. Also known as IP Security.
Latency
The delay before a transfer of data begins following an instruction for its transfer.
7
Term Definition Description
LPWA Low Power Wide Area Is a wireless technology that provides connection to a network over a wide area. This is used to connect large numbers of devices that transmit low data volumes, such as water meters. The frequencies used are unlicensed and may suffer from congestion and security issues. LoRaWAN and SigFox are proprietary vendors.
LTE Long Term Evolution A term generally used to refer to modern mobile technology from 4Gonwards.
MNO Mobile Network Operator
MTBF MeanTime Between Failures
A mobile providerrunning and managing their own network infrastructure i.e. Vodafone, o2,KPN, Telenor, EE, 3.
MTBF (mean time between failures) is a measureof how reliable a hardware product or component is. For most components, the measure is typically in thousands or even tens of thousands of hours between failures. For example, a harddisk drivemay have ameantimebetweenfailuresof300,000hours.
MVNO Mobile Virtual Network Operator
A specialist mobileproviderusingaphysicalnetwork infrastructure managed by an MNO. Some specialise in Consumer i.e. Tesco Mobile, Giff Gaff, Asda Mobile while others specialise inniche markets such as National Infrastructure i.e. Mobius Networks, CSL Dualcom.
Network slice/ NetworkSlicing
“Not-Spots”
Areas of no coverage
Packet-switched
Is a separated, self-contained, independent, and secured part of the network, targeting different services with different requirements on speed, latency, and reliability.
A phase referring to remote areas of no network coverage from any MobileNetwork Operator.
The braking down of data and voice in to small packets which are sent over an internet connection and reassembled by the receiving System.
5G
Telecommunications 8
Introduction to
and Mobile
Term Definition Description
Ping A ping or ping test is used to establish if a computer or device is connected to a network. It can also be used to determine the latency or speed between two devices.
P2P Peer-to-Peer In a P2P network, the "peers" are computer systems which are connected to each other via the Internet. Files can be shared directly betweensystems on the network without the need of a central server.
RAN Radio Access Network

Roaming
SIM Subscriber Identification Module
TCP Transmission Control Protocol
TDM
Time division Multiplexing
A radio access network (RAN) is a major component of a wireless telecommunications system that connects individual devices to other parts of a network through a radio link.
Usinga networkotherthanyour‘Home’ -i.e.using the ‘signal’ of O2 UK using a VodafoneSIM.
A smart card inside a mobile phone, carrying an identification number unique to the owner, storing personal data, and preventing operation if removed.
A suite of communication protocols used to interconnect network devices on the internet.
Time division multiplexing (TDM) is a method of transmittingandreceivingindependentsignalsover a common signal path by means of synchronized switchesateachendofthetransmissionlineso that each signal appears onthe line only a fraction of time in an alternating pattern.
URLLC
VPN Virtual Private Network
Ultra-Reliable, Low Latency, communications. Typically, <8ms end to end.
A technology that creates a safe and encrypted connection over a less secure network, such as the internet. VPN technology was developed as a way to allow remote users and branch offices to securely access corporate applications and other resources.
9
NetworkDataTechnologies
Data connectivity over mobile communications has evolved over time and will continue to do so. Each evolution, enabled by new technology, is referred to as a Generation, or ‘G’ in shorthand. Figure 1 shows the overlap and lifespan of the various technologies used in mobile networks. It is important to note that 3G will end before 2G, and that 4G is likely to be with us for some time to come.
Figure 1: Launch and termination dates of various generations of mobile data connectivity.
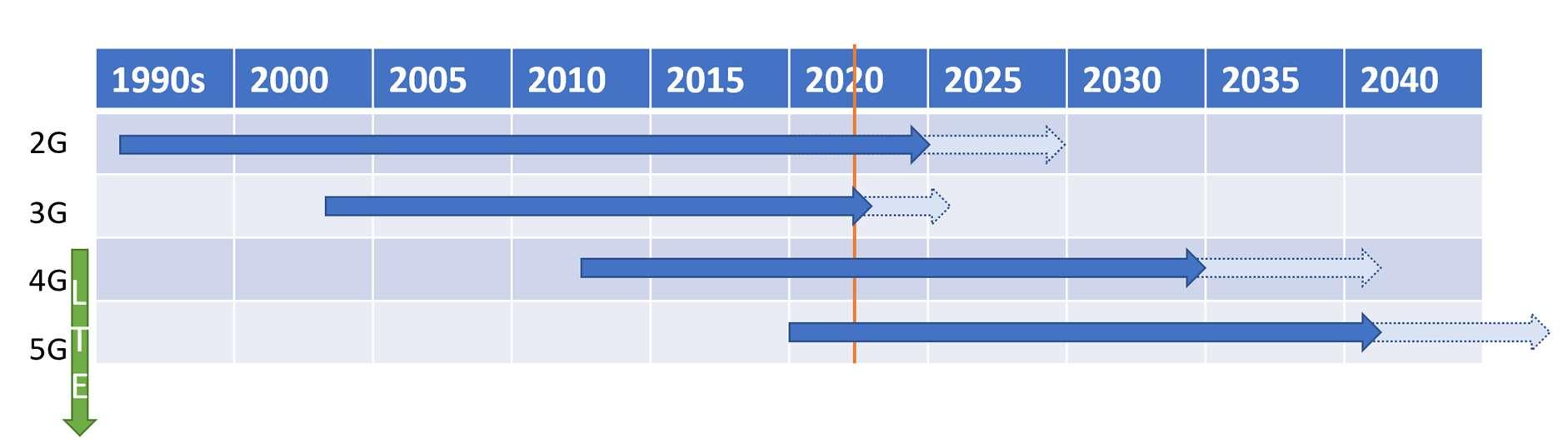
2G Service
2G will continue to be operated in the UK until at least 2027. This may, however, be pushed back to 2030 with the impact of Huawei and Covid19. It will become a ‘thinner service’ as some of its existing capacity will be moved across to 5G applications over the next few years.
3G Service - Support ends 2022
3G Networks have a shorter lifespan ahead of them. Most networks are looking at no longer supporting 3G from 2022. What ‘no longer support’ means is open to interpretation, some will winddown coverage and others will look to switch off completely. Most MNOs have not sold any devices that do not support 4G, in the aim to wash out any 3G only users over the last 3 years. Again, you will likely see coverage reductions in the meantime as the favourable frequencies are moved to 4G to further enhance coverage and throughput.
4G – Current technology
4G is, for now, is still current technology and therefore there are not yet any official notices to withdraw it. As the first iteration of the Long-Term Evolution (LTE) Stack, it is likely to remain until at least 2035.
Introduction to 5G and Mobile Telecommunications 10
5G – Future technology

5G is the next generation of the LTE network, further enhancing speeds and capacity as well as introducing fundamental changes in the way devices connect to the networks, designed with more “always on” capacity. Just like when 4G was released, although 5G has major advantages over 4G, these benefits, generally, won’t precipitate fully to most products in the short term, as speeds of transfer forlarge data isn’t acurrentrequirement formost IoTapplications.Overtime,the subsets of 5G (LTE-M, NB IoT and URLLC) will be rolled out with further releases of the LTE programme.
NB IoT
NarrowBand-InternetofThings(NB-IoT) isastandards-basedlowpowerwidearea(LPWA)technology developed to enable a wide range of new IoT devices and services. NB-IoT significantly improves the power consumption of user devices, as it can go into ambient mode and still retain itscredentials with the nearestmast.Thisalsogivesenhancedsystem capacity andspectrum efficiency, especiallyindeep coverage. Battery life of more than 10 years can be supported for a wide range of use cases.
New physical layer signals and channels are designed to meet the demanding requirement of extended coverage – rural and deep indoors – and ultra-low device complexity. It also benefits from all the security and privacy features of mobile networks, such as support for user identity confidentiality, entity authentication, confidentiality, data integrity, and mobile equipment identification. This level of security and the utilitarian nature of the service gives it an advantage over bespoke public frequency services like LoRaWAN or SigFox that do not have national coverage in the UK.
LTE-M
LTE-M is the simplified industry term for the LTE-MTC low power wide area (LPWA) technology standard, released and implemented as a standard before NB IoT. LTE-M is a low power wide area technology which supports IoT through lower device complexity and provides extended coverage, while allowing the reuse of the LTE installed base. This allows battery lifetime up to 10 years or more for awide range of usecases. The throughput is higherthan NB IoTand is seen as adirect replacement for 2G/3G applications as the 2G & 3G frequencies are re-farmed as part of the 5G up-grade rollout.
As with NB IoT, it is supported by all major mobile equipment, chipset, and module manufacturers. LTE-M networks will co-exist with 2G, 3G, and 4G mobile networks and benefit from all the security and privacy features of mobile networks, such as support for user identity confidentiality, entity authentication, confidentiality, data integrity, and mobile equipment identification. It offers far greater throughput and levels of Security than LoRaWAN and SigFox. (See LPWA).

11
NetworkandTariffselection

Since the introduction of 3G, the networks have universally had three data offerings, with varying levels of service quality leading to suitability for different applications:
Voice tariff with associated data bundle

This tariff is, as it states, a voice tariff that has some data provision added to it. It is designed only for smart phones and occasional tethering of devices such as laptops to send and receive emails, browse the Internet, and then disconnect from the network.This tariffhoweveris generallywhatis procuredthroughcorporatemobile contracts. When a procurement team is required to supply data SIM’s they will contact their mobile network account manager. They oversee the mobile phone account, and will invariably be supplied with a voice SIM, with an amount of data attached.
However, use of this tariff explicitly forbids its use for anything other than within mobile phones and associated periphery's. If it is used in an IoT product, the network - under its fair use policy - will likely limit the amount of data being transmitted, throttle its speed, intermittently disconnect it from the network, or – ultimately -permanently disconnect the service. This gives the impression of unreliability.
If a voice tariff SIM is used in an IoTapplication, then to the end user it may appear as though the sim is suffering from a list of random connectivity issues. This perpetuates the perception that mobile data transmission is unreliable.


Mobile Broadband
This tariffisdesignedto beusedby smartdevices,tablets,andcomputers.Generally, under the T&Cs of the contract, the networks specifically forbid it's use in IoT products. This tariff allows greater volumes of data to be sent and received before triggering alerts within the network (alerts are indicators to that network when the SIM may have been deployed in an inappropriate manor). The same fair use policy is used to police the tariff and the result is – as above - connectivity issues as the network temporarily forces the SIM offline, controls or throttles speeds, and potentially permanently disconnects the SIM.

Introduction to 5G and Mobile Telecommunications 12
M2M/IoT.
This tariff has been designed for IoT applications and the SIM is flagged to show that it is potentially going to be connected continually for days, weeks and even years. However, because it creates a higher load on the network this service does come at an additional cost over and above the previous two tariffs. This price differential often appears to be just profiteering by the network, which is far from the case. At the radio level, an IoT device is connected perpetually, regardless of whether it is sending data. This connection is a fixed resource, and as such the network places a cost on its continual use [See RAN].
Quality of Service (QoS)




There is a stark difference between the Quality of Service [QoS] which MNO’s provide for the three tariff types above.
Typically, the network’s Service Level Agreement offers 85% availability for Voice and Mobile Broadband availability. This is clearly not enough for the majority of IoT devices which, in order to provide the service as intended, require as close to 100% availability as possible.
The Mobile Network Operators (MNO) standard offer for M2M/IoT is typically 96% availability. Although this is a massive improvement on the standard Voice and Mobile Broadband, it still equates to 57 minutes off-line a day.

This is where a Mobile Virtual Network Operator (MVNO) can add value: they will build upon the 96% availability offered by the networks. Many offer 99.5% or better uptime, though noting it is worth scrutinising these claims as some of the numbers published vary widely.
Under 5G, the networks will offer additional tariffs and services to meet growing needs of Industry 4.0. These will include URLLC, narrowband IoT, higher Quality of Service as a premium offering, and lower Quality of Service for lower-cost connections, for general use. There is currently some industry discussionaround network slicing to offer guaranteedbandwidth formission critical applications such as ‘Blue light’ services, critical infrastructure.
13
Technicaloperation,specificevents,and faults Mobile Cells
Figure 2:
Left: Idealised cell lay-out – antennae optimally placed without signal obstructions.

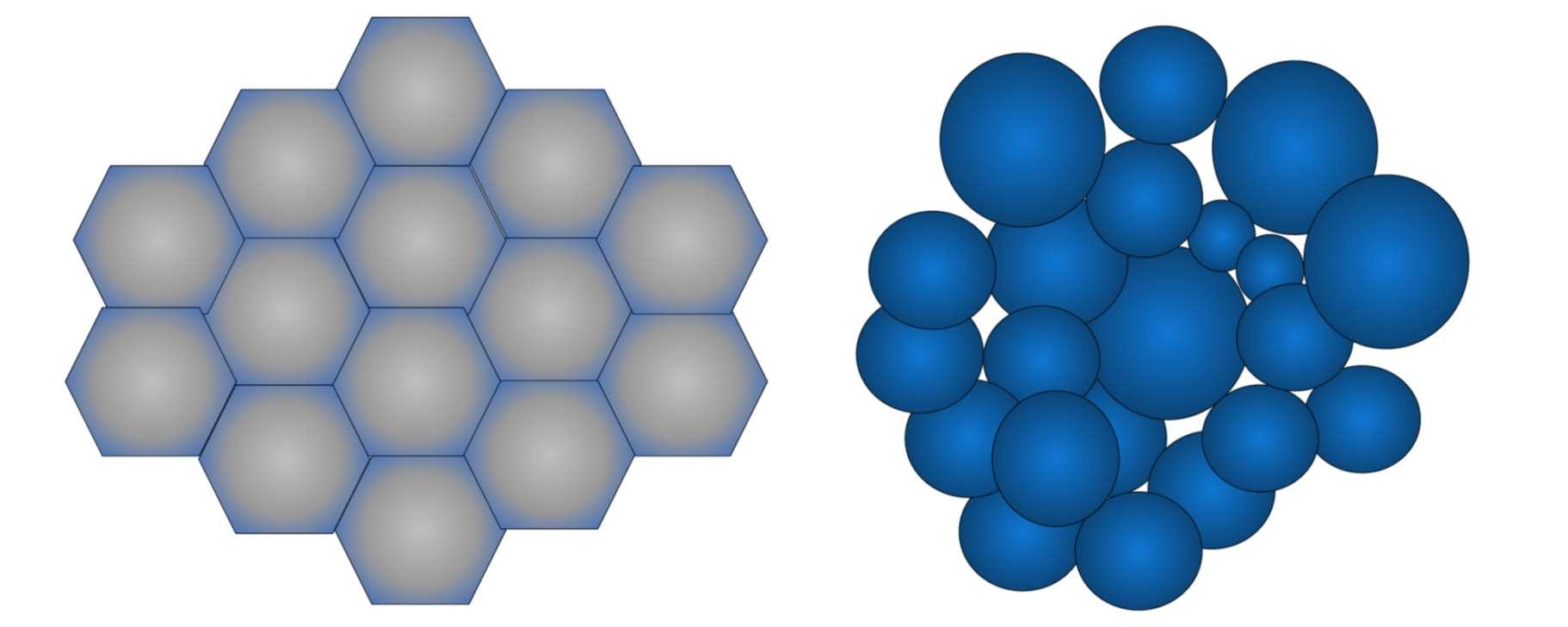
Right: Cell configuration in the real world, with sub-optimal antennae placement and obstructions.
Mobile networks cells are constantly changing. A cell will create a donut shaped signal area and anything in that donut will get a signal, but this signal gets weaker the further away from the cell you go. As a user connects to a cell, the size of the footprint shrinks (so-called Cell Breathing). If you are at the edge of a cell and it shrinks, you will no longer have a connection to that cell and you will connect to another cell that is also serving your location if there is one, or you will drop to another technology, such as 2G/3G.
The weather affects cell performance, as do trees and buildings. Modern buildings are particularly bad for mobilenetworkreceptionasthemixofglass,steelandfoil backed insulation scatters, reflects, and absorbs the mobile signal.

Introduction to 5G and Mobile Telecommunications 14
Cell switching
Cell switching is the action of handing a device from one mobile cell to another. It occurs all the time when your device is moving, as you are passed from cell to cell along your journey. It can also occur when your device is static, although less frequently. For example, if you are static and connected to a cell that is suffering from network congestion, then the cell may ask your device to switch to another cell that is also serving your location in order to balance the load.
Due to organic cell switching and operational changes to networks, it is important to note that the network coverage pattern observed at device installation can change substantially.

‘Network is down’
It is true that mobile networks and cells do go ‘down’ from time to time. However, this is planned and generally takes place overnight, in very specific locations and for specific reasons such as hardware maintenance. When things come back up, it is always the devices that are poorly set-up that prevent these events passing seamlessly. Unfortunately, the poorly configured devices may still regard their last session prior to the disruption as active. Unless the device has been set up to monitor its connection, the device is unable to recover from this state without human intervention – usually a manual reboot.
Mobile Network Operators have invested heavily in their networks, improving cell densities within towns and cities. This has increased further with the rollout of 5G. Within most urban environments itiscommonforamobile devicetoseeupto50cellsitcanconnectto,andeveninquiterurallocations the ability to see a handful of cells is the norm. Therefore, for whatever the reason a cell may be offline, there are usually other cells which can handle the data.
A poorly configured device may fail to reconnect after a disconnection, giving the impression the network is permanently down when there was only a momentary loss of a single cell, and/or when other cells are still available. This is, of course, an issue if the device in question is a remote IoT monitoring station!
Wise data plan selection alongside correct device configuration can help alleviate these occurrences.
15
Mobile ‘Black holes’
‘Black holes’ are when the connection simply disappears. If you have deployed a mobile solution, you will probably have come across these without knowing what they are, or what causes them.
When a device has been connected to amobile network for a period, the network sleeps the radio layer of the RAN if no data has been transmitted. The period this takes varies depending on the usage of the cell you are connected to. This has no impact on the IP layer which stays ‘connected’.


When your device wishes to send data again, the radio layer wakes, and your sessioncarrieson.This isexhibitedas the firstpacketofdatatakinga bit longerthan the packets that follow it. Occasionally, the radio layer does not wake correctly, but because you still have an IP layer the software still believes it is connected, and the packets effectively go ‘into a black hole’. This can cause software hang-ups and glitches.
Tip: Black Holes can be resolved by simply as sending a ‘ping’ now and again - though this increases the data volume used - and rebooting the device if it fails to receive a reply ‘ping’. An alternative is to monitor the Transmission Control Protocol (TCP) session, and restart the session if the TCP connection fails.

Antennae (Aerials)
The placement and design of antennae are some of the most important considerations of any deployment using mobile radio.
It is commonplace for antennae to be mounted on the side of cabinets that house the router. It is thought, by mounting the antenna on the side insteadof the top of the cabinet, there will be reduced chance of water ingress. However, antennae procured from reputable manufacturers will have a series of neoprene washers and membranes that, if the fitting instructions are followed and any nuts not over tightened, will provide a stable watertight seal for the life of the equipment.
By placing the antenna on the side of the cabinet – especially a metal cabinet - the signal reception is effectively shielded by at least 180 degrees. If the antenna is placed on top of the cabinet, it will have full 360 degrees sight of any mast.
Introduction to 5G and Mobile Telecommunications 16
??
Cutting corners with the antenna – whether location or specification - can cause huge dips in the performance of the connected device.


A word of caution about using a directional antenna to get a better signal. Whilst this may help if the location will only ever be served by a single cell site, if the location is served by multiple cells, then using a directional antenna will be counterproductive as the device cannot switch to another cell. It is likely that installation of a directional antenna will limit flexibility in the longer term.

Tip: Even low-loss cabling loses ½ dB per meter.Thismeans if an antenna with 3 dB gain is fitted to 3 metres of cable, half the gain/performance of the antenna is lost.
Keeping the cable length between the antenna on the router/modem as short as possible will therefore enhance the overall performance of the connection.
17
In rural locations or smaller towns, cell towers are a regular sight and can often be visible for miles around. In dense urban environments, the equipment is instead mounted at strategic locations in, around, and upon existing buildings.
Routers
Mobilephonemanufactureshavespenthundredsofmillionsofpoundsonresearchanddevelopment, and on software to optimise the way the modern cell phones connect and participate in an expensive approval process with Mobile Networks, ensuring that connectivity is flawless.
Contrast this to the modem and routers available for industrial use. Although many have a degree of built-in intelligence, they rely heavily on being set up correctly for their location and traffic profile by a skilled engineer. Unfortunately, the skill set neededtodothisiscurrently inshortsupplyandmostfieldengineersandcomputer network specialists leave the default settings ‘as-is’. This in turn degrades the hardware’s potential performance and ultimately the performance of the delivery of the data.
There are suppliers of SIMs and Hardware who can ship preconfigured devices that have been set-up correctly to optimise the performance of the device and the connection to the mobile network. However, it is still important to think of the interaction between the firmware, software, and application layer within the router and how that is expecting to react with the local devices and the network.

Dongles vs Routers
So-called ‘dongles’, which connect via USB, are not designed for permanent installations. Power control is difficult, and there is no connection management, as the user is expected to disconnect the dongle and reconnect it if there is an issue. Also, since the USB port can stay live in a power cycle then the standard ‘turn it off and turn it back on again’ process often has no effect. The radio module versions are also constantlychanging, whichcancauseincompatibilityissueswithdeployedhardware.
Large estates of devices quickly become impossible to manage. USB dongles are not designed to manage black holes, and radio performance can be poor.
In general, dongles are designed for light domestic/office use. When they are used constantly, they have a Mean Time Between Failure (MTBF) of six to eight months. The devices become unreliable rather than fail completely resulting in an increase of expensive site visits.
With routers, the hardware platform is stable and any changes to the radio modules are controlled and tested before they are released. The MTBF is commonly five years. The manufacturers have connection management to prevent mobile ‘black holes’ (if the device is configured correctly). Hours of engineering time out in the field can be saved by bench testing the manufacturer’s default settings against what is configurable and observing the net result. However, a lack of knowledge about the router’s capabilities is often where projects fail to deliver the performance required by the end user.

Introduction to 5G and Mobile Telecommunications 18
Multi IMSI
Multi IMSI is used to switch between the identities of the SIM on a single SIM. For example, the SIM could hold an O2 IMSI and a Vodafone IMSI (or up to 10 IMSIs) and be told which to use by sending an Over the Air (OTA) command. Multi IMSI technology is aimed at providing a cheaper service to the end user - instead of using a roaming SIM with its associated costs generated by their international interconnects needed to provide the roaming service. The multi IMSI uses an IMSI of a national operator and accesses local prices instead of roaming prices. This would seem to be the ideal solution: low-cost multi-network connectivity.
However, Multi IMSI brings additional complexity which is worth understanding before adopting this option. The software and operating system that supplies the OTA command is bespoke to the MVNO that supplied the SIM. At present, no MNO supports the Multi IMSI deployment on their back office. As the solution is bespoke, this leaves the end user with a question mark over the longevity of the Multi IMSI solution. An MVNO could cease trading or change their back-office platform, leaving the SIMs dead and the end user with no choice but to exchange the physical SIMs in their devices.
The SIMs could also be stranded if the process of an OTA command is not received by the SIM or if there is an interruption during application of the changeover applet. The SIM may have been told to change from a Vodafone IMSI to say, a Three IMSI, which for a myriad of reasons does not take effect, and the Bootstrap network is not available in that location. Again, the SIM can become either temporarily or permanently stranded.
Tip: No Network covers 100% of the UK land mass. Ask vendors of Multi IMSI systems to demonstrate how they recover a stranded SIM where there is no Bootstrap network coverage. More importantly, ask for a written guarantee that the SIM platform will be supportedforthe life oftheproject. Thinkabout theexpected lifeofthe projectfromwhen the last SIM is deployed, rather than from the first.

SIM Faults
IoT SIMs rarely go faulty, as they have solid state construction without moving parts. The primary reasontheymay notwork isoftenthewaythatthey aresetuponthenetwork,withthemostcommon problems being:
• Wrong IP addressing
• Duplicate IP addressing
• Wrong APN input into set-up of device
• SIMs being shipped but not activated
• SIMs being enabled for WAP not WEB
• Too large a current applied to contacts
Tip: Use of an MNO or MVNO with a BSI 9001 system in place can eliminate most ‘SIM faults’ from SIM shipment and set-up.
19
Roaming SIMs
Roaming Sims fall into two categories. The first is a true roaming SIM that will connect to any network available to it. The second category is a managed or steered SIM. The steered sim has a list of partner networks that it will choose over any over other network open to it. This can create a problem when the preferred partner network is not available for the transmission of data in any given location.
A roaming SIM is designed to give you the best connection available in the location it is used in. The SIM allows access to the available networks, but it is the router/modem that chooses the network. The roaming SIM allowstherouter/modem to run asite survey when it is first powered uptosee what networks are available to it. Networks that have a poor signal or offer low throughput are blacklisted and the ones that are left are put in a preferred order (based on signal strength and throughput). When the preferred network has low signal or throughput this is also black-listed and then the next network from the preferred list is selected. Once all networksare black-listedthewholeprocess starts again. This process is perfect for a fixed device.
One common issue that can be experienced with a Managed Roaming SIM is where the home network applies a set of rules on how the connection is managed, so called steered roaming. Steered Roaming is where the SIM checks against an onboard Public Land Mobile Network (PLMN) list. It may then, for example, steer the router away from a strong Vodafone signal to a weaker Three signal because the supplier has a better deal with Three than they do with Vodafone.
Within the EU, and in the consumer market, charges for roaming are mandated to be equivalent to those applied on the home market. Since Brexit, there is no longer a requirement for this rule to apply to UK MNO’s. If a device will be crossing borders or deployed overseas, roaming charges could form most of the cost of the subscription. It is wise to check any contracts carefully, including for penalties should allowances be exceeded.



Introduction to 5G and Mobile Telecommunications 20
Another system deployed to save costs is Network Level Steering. Consider that you have a Telefonica (O2) SIM and you are network roaming. The device picks EE to connect to (maybe using managed roaming). When the authentication request hits O2’s network, they reject it because they want you to use O2 where possible, as it costs them less.
A device will usually try this process five times before the O2 network will allow the authentication request through. The duration of thisvaries by device but is typically ten seconds per retry, which equates to a delay of up to 60 seconds before a connection is made.
By this point, most applications will have timed out, and will reinitiate the process, therefore giving the perception that no connection can be made. A true Global Roaming SIM does not have steered roaming applied to it and will connect to the first network it tries on the assumption that the device has already applied your criteria for the best possible connection at that time.
Tip: Use an un-steered roaming SIM from a Global carrier, which will have robust reciprocal agreements worldwide. Some Sims issued by minor carriers do not have robust reciprocalagreementsinplace andtheirperformancereflectsthisoverthe life of a project.

Cost of Failure
The cost of failure is often disregarded when planning or executing a mobile deployment. Often, to keep the costs and ongoing revenue down, the cheapest option for both the hardware and SIM solution are chosen. If the cost of failure is factoredinto thecost ofthe project,thechoiceofhardwareandSIM provideroften changes.
Getting a system that works to specification at the best price means making the right choices on network, software, hardware, application layer and SIM provider and this requires some specialist knowledge. Often customers are reliant on their suppliers for technical advice and that is usually of variable quality.

A marketing team may use the word industrial router to increase the market perception of the hardware, however, when you drill down to the mean time between failures of its component parts, it matches consumer grade devices and not those of true industrial specifications. The cost of engineers being dispatched to reboot and replace hardware more than once during the life of the project means the price differential between two solutions pales into insignificance. It is also important to consider the cost in lost service and the potential of reputation damage.

21
Security
Security will be one of the main areas of focus for the next decade as systems move away from being standalone (isolated) systems to interconnected IP based that will run over public network infrastructure (not leased lines). It is strongly advised that both project design teams and procurement should be aware of Cyber Essentials and Cyber Essentials Plus and ensure as a minimum any supplier hold both certifications. Cyber Essentials is a simple but effective Government backed scheme that will help to protect your organisation against a range of the most common cyber-attacks.
A vast majority of Cyber-attacks are very basic in nature, carried out by relatively unskilled individuals. They’re the digital equivalent of a burglar trying your front door to see if it’s unlocked. However, as many are now finding out to their cost, Cyber-attacks are becoming more and more sophisticated in their execution.
There is a reluctance to acknowledge that the highest level of cyber security should be incorporated into any project (It makes no sense to be a little bit secure – you have locked the doors, but all your windows areopen). Thismay be because ofthe perceived cost of increasing the cyber securityor even the mis held conception that ‘no one would bother hacking the traffic lights in our sleepy backwater’, or, ‘Hackers are only after big corporations and banks as that’s where the money is’. Sadly, unless it is a specifically targeted attack on a bank or corporation, the hackers are unaware of who or what they are trying to hack into when they mount the attack.
At the very least, a hostile attack will cost you the value of the data being transmitted and loss of reputation. The attack may be a planned Distributed Denial of Service {DDoS} where your equipment willhave malware added and at that prearrangedmoment in time, many thousands of devices around the worldwill mount a DDOS attack on a third party. If the hackers succeed in breaching your security, they may indeed leave malware to shut down your system until a ransom is paid.
Security is the silent killer in business today. No company has an incentive to talk about failure and so the opportunity for learning to minimise risk is missed. This also leads to an underestimation of the scale of the problem.


Data Path Diagrams
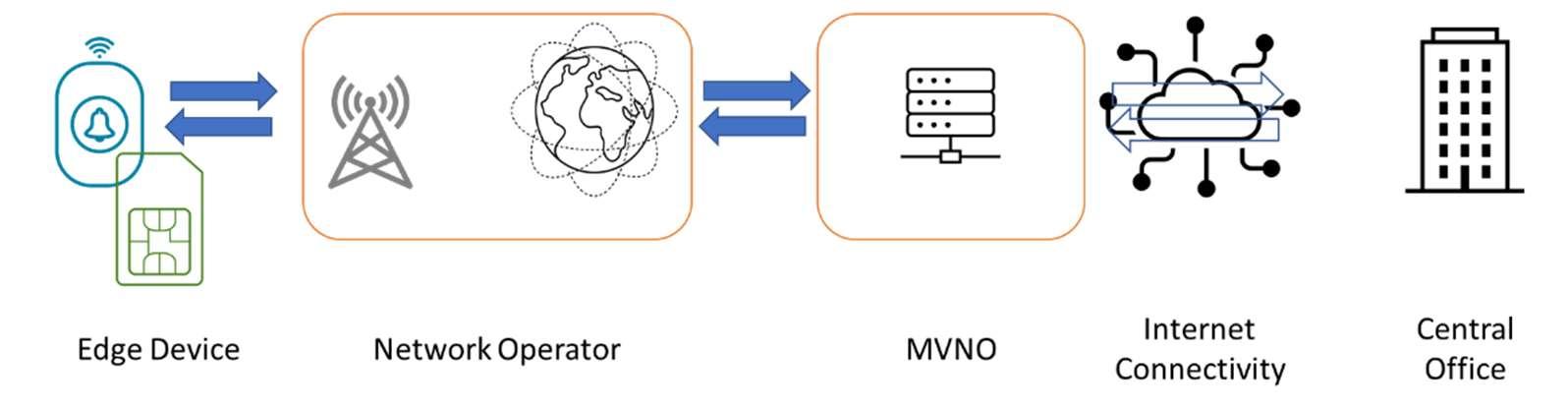
Security of mobile devices is often hampered by the lack of clarity of what systems are involved. The first step to understanding security in a mobile environment should be to build a data path showing every component from the remote end to the centre. An example diagram (Figure 3) helps asaframe ofreferencewhereyouhavearemotedevice– apanic button in this case- connected over mobile through a Mobile Virtual Network Operator (MVNO) providing a private network with fixed IP to the customers central office. This is the model used by the bulk of IoT applications today.
Introduction to 5G and Mobile Telecommunications 22
However, the reality is that these resources are shared with multiple companies. Some of whom have good security and some who have not. The shared resources model is shown in Figure 4.
This shared resources model, shown in Figure 4, creates some internal vectors of attack that are not often recognised. We have added another customer – a security company with CCTV running over the same private network. The first potential breach is at a Mobile Network Operator (MNO) level. They assume that a Peer-to-Peer connection between SIMs is desirable, creating a short-cut through the MNO, bypassing the security put in place by the customers, the network and the MVNO (Figure 5).

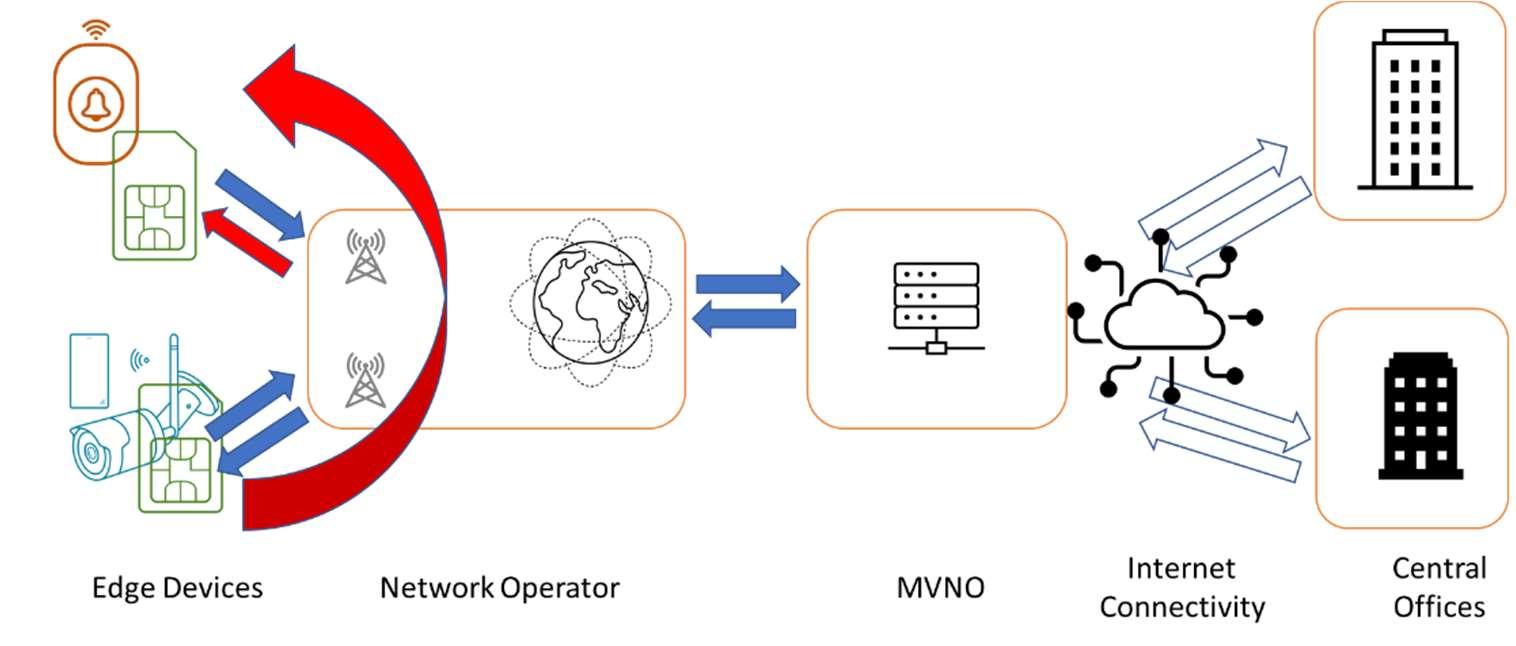
The next most common breach in service is at the MVNO – Figure 6. Ideally, when creating private networks, a distinct subnet should be used for each customer. This minimises the chance of cross infection. Commercialandtechnical pressures oftenmean that asharedsubnet ismore the norm. This shared subnet creates a very real opportunity for viruses, malware, or a Denial-of-Service attack to jump the gap.
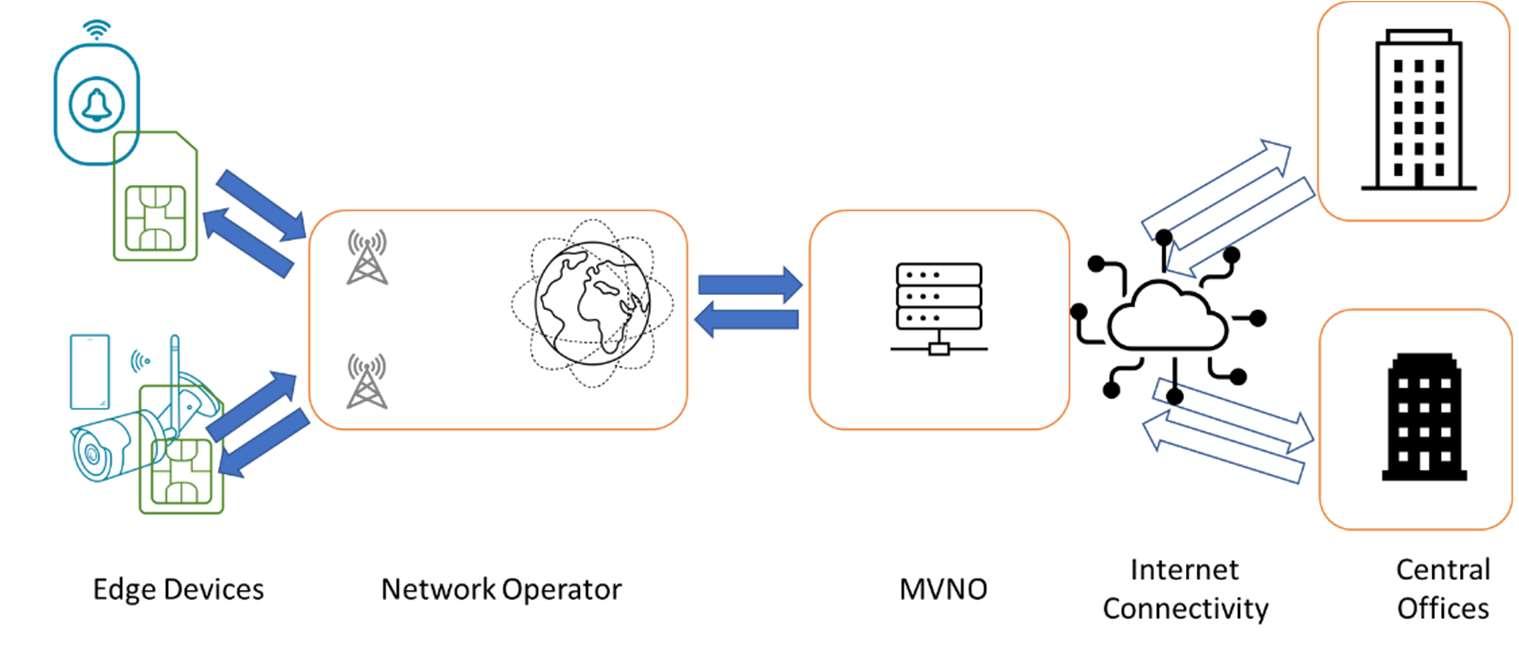
Figure 3 (Above): Simple data path diagram showing a panic button connected to a central office via Network Operator and MVNO.
Figure 4 (Below): Combined data path diagram showing other network users connected to other central office via Network Operator and MVNO.
23
Figure 5 (Top): Unsecured 3rd party edge devices can prove a weak spot via network operators if peer-to-peer communication is enabled.
Figure 6 (Above): A similar breach can be created at the MVNO level if shared subnets are used.
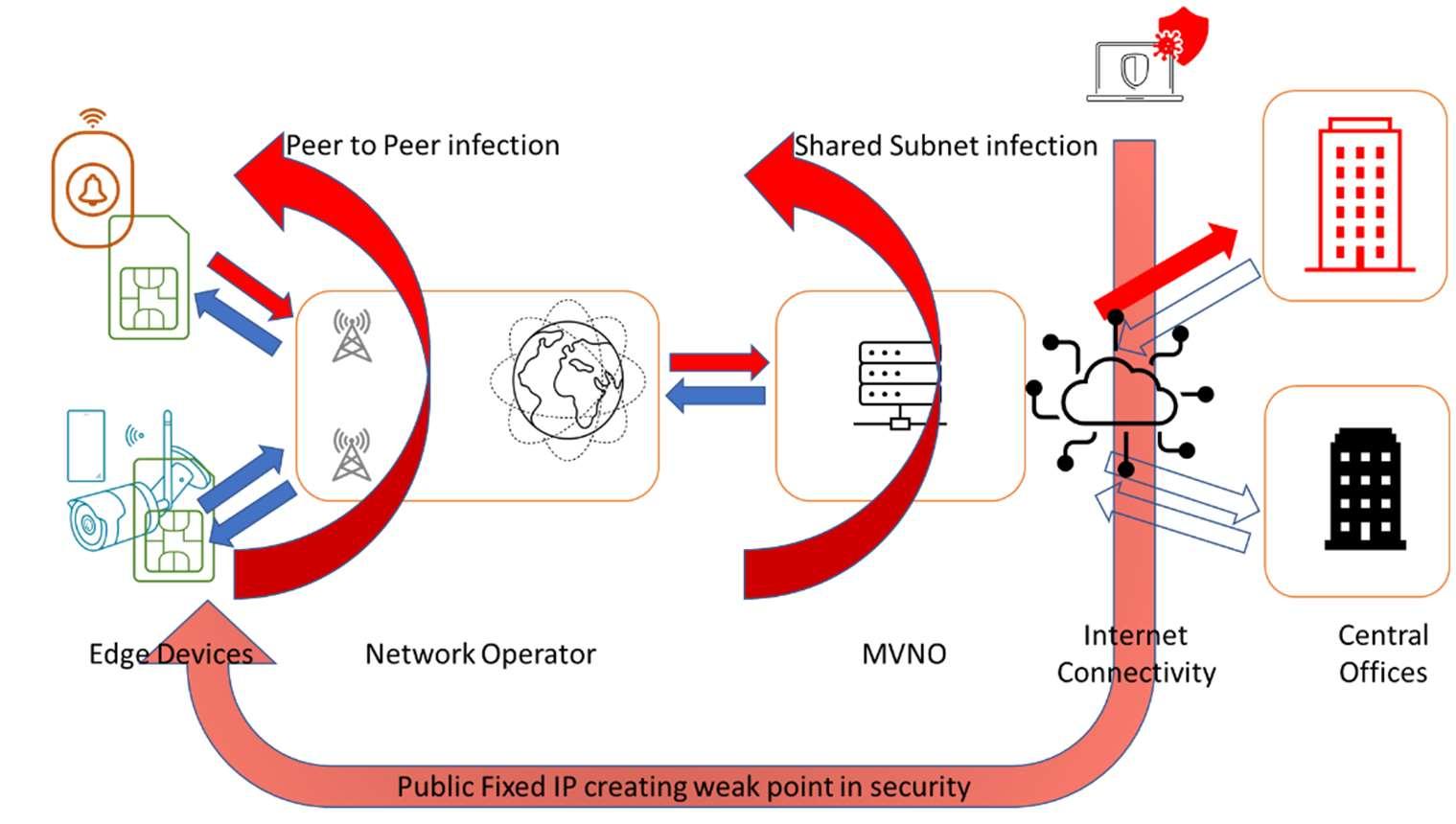
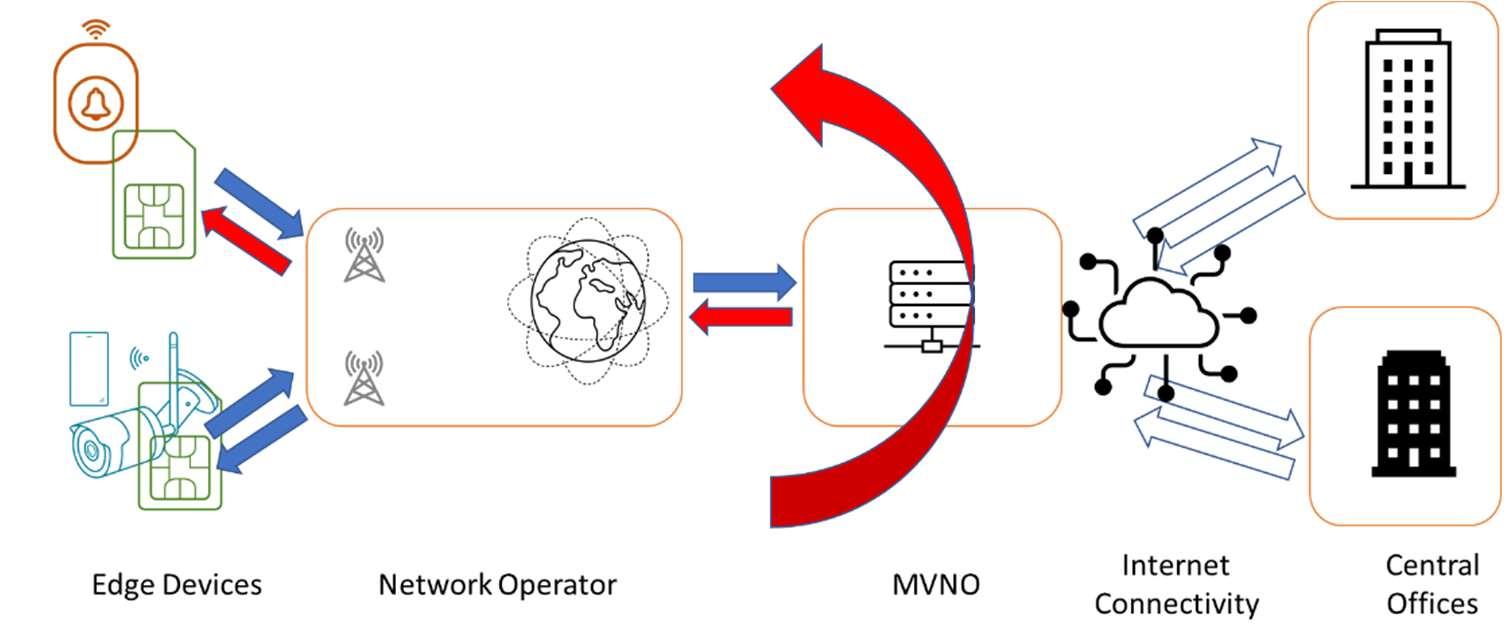
Figure 7 (Below): A fixed public IP address can make the edge device visible on the internet, which, in bypassing all network security, provides the easiest point of entry into a system which will often be the one exploited.
Introduction to 5G and Mobile Telecommunications 24
The last common vector of attack is that of fixed Public IP addressing – Figure 7. It is a very common requirement for remote access so that engineers can access a system from their laptops or that customers can easily access their own CCTV. However, having a fixed Public IP address bypasses all security in the mobile network. It puts that camera directly out on the internet – eventually it will be found and will only have limited levels of protection.

A chain is only as strong as its weakest link, and any public fixed IP equipment will be the easiest point of entry into a mobile system. As we have seen above, once in, a virus ormalwarewillexploit any otherweak points inthe system and compromise not just the original system but all the other users of the network.
Inourexample,acamera withapublic facingfixedIP ishackedand malware is loaded onto the camera. Once on the camera, the malware then uses multiple points of weakness to infect all the devices in the system. The same malware can then use the paths in place to infect upwards to the companies’ central offices. The nature of modern hacking is that none of this is targeted. The malware is an autonomous, opportunistic system that simply exploits any weakness that it sees. It will then lie dormant for some months before deploying itself as Ransomware or Distributed Denial of Service attack.

25
Tips and questions for potential suppliers
Ask for core availability statistics for the last three years, and on-street, if available.
Make sure the supplier bills by the byte.
Invest in a good omni-directional antenna.
Ensure it’s a global non-steered roaming SIM; preferably with a device roaming algorithm.
Minimise antenna cable length.
Ensure the supplier provides Permanent Roaming.
Be aware of typical SIM network fault reasons.
Ensure you are being provided a Machine-to-machine SIM rather than a Consumer SIM.
Avoid use of USB Dongles for critical or commercial applications.
Test the SIM connection in as real conditions as is possible.
Do not use Pay-as-you-go SIMs.
Use a SIM that employs Multi-Path Multi-Network architecture.
Use a private APN to restrict the devices that can access the network.
Ensure hardware has the ability to manage its own connection.
Use suppliers that match or exceed corporate Code of Connectivity standards.
Use IoT tariffs to avoid delays in regular data transmission.
Use data aggregation to ensure overuse of one Sim is compensated in underuse of another.
For larger data usage applications, find a supplier that can provide data reservoirs to allow for flexibility around pricing.
Ensure Firewalls and Servers are correctly specified to allow the solution to operate at peak performance.
Ensure the supplier has suitable contention ratios within their network to provide high bandwidth media if required.
Introduction to 5G and Mobile Telecommunications 26

27
Notes
© 2022 Railway Industry Association Ltd and affiliates.


Kings Buildings, 16 Smith Square, London, SW1P 3HQ +44 (0)20 7201 0777 www.riagb.org.uk

28
Introduction to 5G and Mobile Telecommunications























































