







Standing at the forefront of the digital and AI revolution, the importance of coding and computational skills has reached unprecedented heights. In today’s professional landscape, whether it’s in the fields of medicine, space exploration, education, science, or business, no sector remains untouched by this transformative wave. To not just survive but thrive in the 21st century, basic computer literacy is no longer sufficient. Learners must evolve into “digital natives” who can fluently read, write, and communicate in the languages that machines and AI comprehend.
Recognizing this imperative, the National Education Policy of 2020 (NEP 2020) has strongly recommended the integration of coding skills, computational thinking, critical analysis, and problem-solving abilities into the curriculum. Moreover, forward-looking subjects like AI, Data Sciences, Computer Applications, and IT have been introduced as elective subjects from grade 9 onwards. It wouldn’t be surprising if further transformative measures are taken even at the elementary education level.
Uolo has introduced an innovative 360-degree program for a coding-focused computer science curriculum, known as Tekie, spanning grades 1 to 8. Tekie is a significant stride towards STEM education that aims at making learners future ready—enabling them with skills needed in the ever-changing, technology-driven, and dynamic 21st-century world.
Tekie adopts a captivating and engaging approach to learning, in line with the recommendations of the NEP 2020. The curriculum is ingeniously woven into the thrilling adventures of Mel and Conji, fictional characters from the enchanting land of Avora. The Mel and Conji series epitomizes a modern method of acquiring Computer Science knowledge and honing coding skills and computational thinking.
Tekie is a technology-empowered curriculum that encompasses a few key components:
• Main Content Books: These introduce learners to the theory of computer science and the tools used in the field. Topics in AI are also covered, along with experiential and curiosity-based learning resources.
• Coding Book: Specifically designed to nurture coding skills, this booklet aligns with the experiential and contextual learning approach of the curriculum, fostering critical thinking and problem-solving abilities.
• Animated Learning Videos: The program is powered by high-quality animation-based learning videos that deliver learning in an engaging manner.
• Teacher Manual: This valuable resource supports classroom instruction, ensuring that educators can effectively deliver the curriculum.
Welcome to the captivating realm of Tekie! We hope you relish this educational journey as it equips you with the tools you need to thrive in the exciting and ever-changing world of the 21st century.
Each chapter has been divided into two key sections.
In every grade, students embark on an immersive experience in the “Adventures of Mel and Conji”. Within each chapter, in the initial section (Section A), the story unfolds, enveloping learners in an exciting journey. Through the story, students actively connect with fundamental concepts in the realm of Computer Science.
This section of the chapter focuses on the essential academic content. It provides the learning goals and assists teachers in their classroom instruction.
This section also includes the following academic assets:
HOTS questions to trigger engaging group discussions in the classroom.

Interesting facts related to the application of a concept.
What are some other things we can do with spreadsheets?
The first spreadsheet program was VisiCalc, which was released in 1979.

Probing questions to stimulate HOTS at individual level.
Think and Tell
Identify rows and columns for cell B26 and C71.

Milestone exercises to practice specific concepts.

QR codes to explore an exciting application of the concept. This element builds curiosity in children and helps them grasp concepts through digital visual aids.


Scan the QR code to learn how to add images in Google Sheets.
This is the chapter summary. It enables learners to glance through all key concepts covered in the chapter.

A pool of questions catering to all topics and skills covered in the chapter.









We all use computers in our everyday lives—to play games, do homework, watch movies, and much more. But have you ever wondered what makes a computer work?
A computer comprises two components: software and hardware. Software and hardware work together to make the computer function properly.
Software is a set of instructions that tells a computer what to do. Software is intangible, which means you cannot touch it. Operating systems (Microsoft Windows, Linux, macOS, etc.), word processing applications (Microsoft Word, Google Docs, OpenOffice Writer, etc.), and web browsers (Google Chrome, Microsoft Edge, etc.) are all examples of software.



Hardware refers to the physical components and electronic devices that make up a computer system or any technological device. Hardware is tangible, which means you can touch and physically interact with it. For software and hardware to work together in a computer system, software first identifies if they are compatible, that is, if software can function appropriately using the available hardware else either of the two needs to be replaced. Next, software tells the hardware which tasks to perform and hardware performs these tasks.
The hardware components can be classified into two categories: internal and external hardware.
Just like we have some internal and some external organs in our body that work together to help us perform various activities, a computer also has internal and external parts that team up to make it work. In this chapter, we are going to explore these hardware components and discover how they work together to turn the computer into a powerful machine.
Let us learn more about various hardware in detail:
The external hardware components, also known as peripherals, are attached to a computer outside the central processing unit (CPU) box. External hardware components can be categorised into three kinds:
Input devices: Input devices are used to give instructions to the computer. They convert data from the real world into a form that the computer can understand. Keyboards, mouse, and scanners are examples of input devices.
Output devices: Output devices are used to show the results of the information processed by a computer. They convert data from input and other devices into a form that can be understood by humans. Some common output devices include monitors, printers, speakers, headphones, and projectors.
Storage devices: Storage devices are used to store data and programs so that they can be accessed later. They are used to keep data even when the computer is turned off. Some common storage devices include hard drives, compact discs (CDs), and digital versatile discs (DVDs).
Let us learn more about these external hardware devices in detail:
The mouse is an input device that controls a pointer or a cursor on the computer screen. A mouse has three parts:
1. Left button: This button is used to click, select, drag, or double-click.
2. Right button: The right button is used to display additional information or properties of an item.
3. Scroll wheel: It helps to move a page up or down.
There are two main types of mouses: mechanical mouse and optical mouse. Mechanical mouse has a metal or rubber ball beneath it that rolls on the surface below when we move the mouse. The movement of the ball is detected by the sensors inside the mouse. This information is used to move the cursor on the screen. A smooth and clean surface, similar to a mat, is critical for smooth functioning of this type of mouse. Nowadays, the mechanical mouse is majorly replaced by optical mouse.
Optical mouse uses a light source, typically a Light-Emitting Diode (LED), and a light detector to detect the movement of the mouse. The light detector measures the amount of light that is reflected from a surface, and this information is used to move the cursor on the screen.
A keyboard is one of the main input devices for computers. A keyboard is made up of buttons which are called keys. These keys can be classified into various groups of keys based on their uses, such as alphabet keys, numeric keys, control key, function keys, and navigation keys.



We can also use a combination of multiple keys to perform an action. These combinations of keys are called shortcut keys.
A printer is an output device that is used to copy digital information (like words or pictures) on a piece of paper or software (as a PDF or .XPS file). A printer is an external hardware device of a computer.
The digital version of the information is called the soft copy, and the printed version of the information on paper is called the hard copy. A computer can work with or without a printer, but a printer can be useful.





There are two main types of printers: impact printers and non-impact printers.
Impact printers: Impact printers create images through a direct contact by striking an ink-soaked strip against paper. They are relatively inexpensive, but they can be noisy and slow. Dot matrix and daisy wheel printers are the most common types of impact printers.
Non-impact printers: Non-impact printers create images without making a direct contact with the paper. They are quieter and faster than impact printers but are more expensive due to their high-quality output. Inkjet and laser printers are examples of non-impact printers.
Did You Know?
Some printers, along with paper, can print on cloth, plastic, and leather as well!

A scanner is a device that is used to scan images and documents into a computer. The scanned data is then converted into a digital format and displayed on the screen.
There are various types of scanners available, each with its own advantages and disadvantages. Some of the most common types of scanners include:
Flatbed scanners: Flatbed scanners are the most common type of scanner. They use flat glass surfaces to scan objects, such as documents, photographs, and artwork.
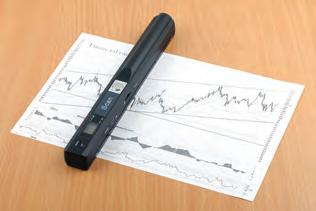

Handheld scanners: Handheld scanners are small, portable scanners that can be held in the hand. They are used to scan objects such as books and magazines that are difficult to scan using a flatbed scanner.
Sheetfed scanners: Sheetfed scanners are used to scan individual sheets of paper. They are typically faster than flatbed scanners, but they can only scan one sheet at a time. The stack of papers is kept on top, and the scanner automatically scans them one by one.


Drum scanners: Drum scanners are the highest-quality type of scanners. They are expensive and are used to scan high-resolution images such as photographs and artwork for magazines and books.
A microphone is an input device that is used to record voice, music, and sound. This device converts sound waves into a digital form that can be stored on a computer. A microphone is used in video conferencing, speech recognition, recordings, and music concerts.

A light pen is a pointing device that is used to interact with a computer screen. This device has a light sensor that detects the position of the pen on the screen. The light pen can be used to select items on the screen, draw lines, or write text. This device has better positional accuracy than a touch screen system.
A webcam is a digital video camera that is connected to a computer. This camera can be used to capture images and videos, and to conduct video calls. Nowadays, web cameras are often used for online chatting and live streaming.


A monitor is the primary output device of a computer which displays images and text on a screen. A monitor is also known as a visual display unit (VDU). The images we see on a monitor are made up of tiny dots called pixels (picture elements). The image clarity depends on the number of pixels on the screen. The display is clearer if the number of pixels is high.
A plotter is a type of a printer that is used to draw graphs and charts. Plotters use pens or pencils to draw images on paper. They are like printers, but are much bigger in size. They are typically used by engineers, architects, and other professionals who need to create high-quality and detailed drawings.


A projector is an output device that projects images on a large screen. This device takes an image as an input from the computer and displays it on a big wide screen. They are often used for presentations, meetings, and in smart classes.
We know that smartphones are also computers. Which input and output devices can you identify in them?
CD stands for a compact disc. These are circular optical discs that are inserted into a CD player (a device designed to play CDs) to read the information that they store. Although these discs are cheap, they offer limited storage capacity (of up to 700 MBs) and can break easily.



DVD stands for a digital versatile disc. It is similar to a CD, but it can store from 4.7 GB to 17 GB of data. However, it is fragile like a CD and comes with limited storage capacity, which may not be enough for large files like 3D computer games and high-resolution movies.
Blu-ray discs are similar to CDs and DVDs, but they offer huge storage capacity. Blu-rays come in various storage capacities, depending on the number of layers of data storage they have. A single-layer Blu-ray disc can hold up to 25 GB, a double-layer disc can hold 50 GB, whereas a triple-layer disc can hold up to 100 GB of data.



A pen drive, also called a USB flash drive, is a small and sturdy portable storage device. It comes in various shapes and sizes. Pen drives can store up to 1 TB of data. They are easy to use and are typically rewritable, meaning that you can use them multiple times for storing new files after deleting old files. However, they can be much more expensive than CDs, DVDs, and Blu-ray discs.
Why is it important to get rid of old computers and devices in a way that does not harm the environment?
Choose the correct answer.
1 What does CD stand for in the context of storage devices?
a Compact disc
b Computer display
2 What is the primary function of a printer in a computer system?
a To cool down the CPU when it generates heat.
b To convert digital information into physical copies on paper.
c To scan images and documents in a digital format.
d To connect to the internet.
3 Give one use of each of type of scanner:
a Flatbed scanner:
b Sheetfed scanner:
c Central device
d Circular disc
Internal hardware components are the parts of a computer located inside the CPU box. They include the motherboard, CPU, RAM, ROM, disk drives, and hard disk.
A motherboard is the central component inside a computer that connects all the other components, such as the CPU, RAM, and disk drives. The base of the motherboard consists of a board, which has several copper traces that connect all the other components and allow communication between them.
A motherboard contains:
1. A processor chip (CPU).
2. A basic input/output system (BIOS).
3. Memory chips (RAM and ROM).




The central processing unit (CPU) is like the brain of a computer. It is a small but powerful chip that helps a computer think and process information received from the hardware and software running on the computer. It has three components:
1. Memory Unit (MU): The memory unit of a computer is like its storage space. It is where the computer keeps all the information, like programs, files, and data.
2. Arithmetic and Logical Unit (ALU): This unit performs arithmetic operations like addition and subtraction, and helps with logical operations like figuring out if something is true or false.
3. Control Unit (CU): It tells a computer what to do and in what order. It also helps move information smoothly among the various components of the computer.
Random access memory (RAM) stores information temporarily. This memory is a computer’s short-term memory that holds the data and programs that the computer is currently using. When you open a program, it goes into RAM so that the computer can work on it quickly. But when you turn off the computer, everything in RAM gets lost.


Read-only Memory (ROM) is a computer’s long-term memory, as it retains information even when the power is off. This memory consists of instructions needed initially when the computer starts. The information stored in this memory cannot be changed, but can only be read.

A disk drive enables users to read, write, delete, and modify data on a storage disk. The disk input/output (I/O) activities are managed by either an internal or external component. There are various kinds of disk drives, including a hard disk drive, and CD and DVD players. A hard disk drive is the most frequently used disk drive.
A hard disk is a high-capacity disk drive that stores data permanently. At present, hard disks are available in various capacities, 512 GB, 1 TB, 5 TB, and so on. This type of disk has a

collection of disks known as platters. Hard disks are made up of one or more platters that are coated with magnetic material. The platters are rotated at high speed, and the data is stored as a series of magnetic charges.
In 1956, the first hard disk was as big as two fridges and as tall as a person, but it could only store 5 megabytes of data!

Switched-mode power supply (SMPS) is the hardware component used to control the power supply. SMPS takes electric power from a source (AC mains) and converts it into low voltage direct current (DC). Its primary function is to always supply well-regulated power to the motherboard and the other parts of the computer. It also has an in-built fan to reduce the heat produced by the computer.
What would happen if SMPSs are not used in a computer?

Modem stands for modulator-demodulator. It is a device that allows a computer to connect to the internet with the help of telephone lines or a wireless medium. Modems convert digital data from a computer to analog signals for transmission over communication channels and analog signals into digital data that the computer can understand.
The process of converting analog data to digital data is called modulation. The process of converting digital data to analog data is called demodulation. Modems are of two types: internal and external. Internal modems are placed inside a CPU box, and external modems are devices that can be connected to a computer via a USB port.
It is an electronic device designed to spread the heat generated by the CPU. The heat sink is generally made of aluminium or copper and uses a fan to keep the processor cool. This device helps prevent the CPU and other components from overheating.
A port is a slot on the motherboard that is used to connect hardware devices like keyboard, mouse, monitor, and speaker to the motherboard. The cables of these hardware devices are plugged into these ports so that they are attached to the computer and start functioning.

There are various types of ports on the motherboard.




Let us learn about a few of them:









USB
A serial port is a port that is used to connect devices such as mouse, keyboards, and printers to computers. This port transfers data 1 bit at a time, which makes it slower than other ports like USB.
Similar to a serial port, a parallel port is used to connect devices such as printers and scanners to computers. This port transfers data 8 bits at a time, which makes it faster than a serial port.
A universal serial bus (USB) is a modern port that is used to connect multiple devices to computers, including keyboards, mouse, printers, storage devices, and cameras. This is the most common port on current computers.
Personal System/2 or PS/2 is used to connect keyboards and mouse to computers. Now, USB ports are used in place of PS/2 ports.
VGA
FireWire is a high-speed port that is used to connect devices such as external hard drives and digital cameras to computers. This port is being replaced by USB 3.0 and Thunderbolt.
A Video Graphics Array (VGA) port is like a serial port. A VGA port has holes instead of pins. Nowadays, VGA is being replaced by HDMI and display ports. They are used to connect projectors to a computer.
High-Definition Multimedia Interface, or HDMI is a port that is used to connect a high-definition monitor or TV to a computer. This port can also be used to connect other devices, such as game consoles and HD cameras.
Audio ports are used to connect speakers, headphones, and microphones to computers.
An Ethernet is a port that is used to connect a computer to a network. It is the most common way to connect computers to the internet.
1 Write T for true and F for false.
a A CPU processes information from both hardware and software.
b ROM retains data even when the computer is turned off.
c A hard disk drive is a type of external hardware component.
d RAM stores data permanently and does not lose data when the computer is turned off.
e A motherboard is responsible for performing arithmetic operations in a computer.
2 Match the type of port with its description.
Port
VGA
USB
Ethernet
HDMI
Description
Used to connect a computer to a network.
Used to connect projectors to a computer.
Connects a high-definition monitor or TV to a computer.
A modern port used to connect a wide variety of devices to computers.
Hardware refers to the physical components and electronic devices that make up a computer system or any technological device.
The computer hardware components can be classified into internal and external hardware.
A mouse is a pointing device that is used to select and move objects on the screen.
A keyboard is an input device that is used to enter text and data into the computer.
A monitor is an output device that is used to display the output of the computer.
A printer is an output device that is used to print documents.
CDs can store up to 700 MB of data, DVDs can store from 4.7 GB to 17 GB of data, and Blu-ray discs can store from 25 GB to 100 GB of data.
Internal hardware components are located inside a CPU box, whereas the external hardware components are attached to the computer outside the CPU box.
A motherboard is the central component inside a computer that connects all the other components, such as the CPU, RAM, and disk drives.
The CPU is the brain of the computer which has three components: ALU, CU, and MU.
RAM is the short-term memory of the computer, and it stores the data that is currently being used.
ROM is the long-term memory of the computer, and it stores the data that is needed to start the computer.
The hard disk is the main storage device of the computer; and it stores all the data, including programs, files, and documents.
The SMPS is the power supply unit of the computer, and it converts the AC power into DC power.
The modem is a device that allows a computer to connect to the internet.
The heat sink is a device that helps keep the CPU cool.
The ports are the slots on the motherboard that are used to connect hardware devices.
A. Fill in the Blanks.
Hints temporarily brain hardware long-term CPU
1 The physical parts of a computer system, such as the CPU, monitor, and keyboard, are called
2 consists of the ALU, CU, and MU.
3 The CPU, or the central processing unit, is often referred to as the computer’s
4 Random access memory (RAM) stores data
5 Read-only memory (ROM) is the computer’s memory that retains information even when the power is off.
1 Which hardware component connects all the other components of a computer?
a CPU
c Motherboard
b Monitor
d RAM
2 Which type of scanner is commonly used for scanning books and magazines?
a Flatbed scanner
c Sheetfed scanner
b Handheld scanner
d Drum scanner
3 Which type of printer creates images through a direct contact by striking an ink-soaked strip against paper?
a Inkjet printer
c Dot matrix printer
b Laser printer
d Non-impact printer
4 What is the purpose of a projector?
a To store data
c To project images on a screen
b To draw high-quality images
d To scan documents
5 Which optical disc format offers the highest storage capacity?
a CD
c Blu-ray disc
b DVD
d Pen drive
1 I am a hardware component responsible for converting sound waves into a digital format.
2 I am a part of the CPU that performs arithmetic operations like addition and subtraction, and helps with logical operations.
3 I am a high-capacity disk drive used for permanent data storage.
4 I am a pointing device used to select and move objects on a computer screen.
5 I am an output device commonly used for displaying images and text.
1 An optical mouse uses a light source and a light detector to detect movement.
2 A USB is currently the most common port used to connect various devices to computers.
3 A microphone is an output device used for displaying images on a computer screen.
4 Blu-ray discs have a storage capacity of up to 100 GB.
5 A plotter is typically used by architects and engineers to create high-quality drawings.
1 Explain the difference between RAM and ROM.
2 Name two types of impact printers and two types of non-impact printers.
3 What are the advantages of an optical mouse over a mechanical mouse?
4 What are the primary differences between USB, HDMI, and VGA ports?
5 Why can a plotter be preferred over a regular printer for printing a wall-sized world map for a school?
1 Vivek wants to video call his friend who lives abroad. Which device must he connect to the computer to do this?
2 Suppose Veera is working on a project that requires high-quality images for a digital school magazine. What do you think she should choose: a flatbed scanner or a drum scanner? Justify your choice.
3 Aarav is preparing a presentation for his class. Name the device that he must use to effectively display his slides to the whole class on a large screen.
4 You are in charge of a computer lab and you need to connect various hardware devices such as keyboards, mouses, and monitors to computers. Explain which types of ports you would use and why.
5 Anika wants to store important data from her computer in a storage device that is portable, rewritable, and can store a large amount of data. Name the device she must use.





We have learnt about measuring quantities in Science and Maths. We measure length in centimetres, metres, and kilometres. Similarly, we use grams and kilograms to measure weight. But what do we use to measure and express these quantities? We use numbers.
But what are numbers made of? They are made of digits—0, 1, 2, 3, 4, 5, 6, 7, 8, and 9. These ten digits together form our Number System
A Number System is a way of representing and expressing numbers using a set of symbols or digits.
Different number systems can use different symbols and rules to represent a number in that number system.
The base of a number system is the total number of digits the system uses. The number system that we use is the decimal system, also known as the base-10 system. The numbers are expressed using ten different digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.

A question arises here: why do we need to learn about different number systems?
The answer is that the different number systems help us understand computers better as computers do not work on the decimal number system. We will later see which other number systems they work on.
Furthermore, learning about different number systems helps us to represent data in different number systems. They also help us to convert data represented in number system to another number system.
There are four types of number systems that computers understand. Let us learn more about each one.
The Decimal Number System is the number system that we use every day.
The Decimal Number System is a base-10 number system that has combinations of the following 10 digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
Base is 10.
When we deal with a decimal number system, we write the base of the number system as the subscript of the number.
For example, if we want to write 70, 128, and 349 in a number system notation, we will write: (70)10, (128)10, and (349)10.
Decimal Number System
Digits used: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
Base is 2.
The Binary Number System is a base 2 number system that uses only two digits—0 and 1. A binary number is called a Binary digit or a bit. We express binary numbers as (101)2, (1001)2, (101011)2, and so on. The Binary System forms the basis of data storage in computers. In fact, a bit is the fundamental unit of data storage. Different digital devices like calculators, TVs, cell phones, burglar alarms, and watches use this system. But how do these devices understand a bit?
Imagine you have a flashlight. It only has two buttons: one to switch it on and the other to switch it off. The state of an “on” flashlight is 1 and the state of an “off” flashlight is 0.
If we want to store this information:
The first flashlight is on and second one is off. It can be depicted as “10”. This is how these digital devices store information using the Binary Number


Computers store data in binary form using electronic switches that can either be on (representing 1) or off (representing 0). This binary storage is the basis of all digital memory. To know more about binary storage, scan this QR code.
Binary Number System
Digits used: 0 and 1.
Did You Know?
Acharya Pingala, a Vedic Scholar, was the inventor of the Binary Number System.

Each number in the decimal number system can be represented in the binary number system as well. This table shows the decimal numbers 0 through 15 in their binary forms:
The Octal Number System has a base of 8 and has eight digits: 0, 1, 2, 3, 4, 5, 6, and 7. We express numbers in the octal number system as (40)8, (214)8, (376)8, etc.
The Octal Number System is widely used in computer applications in the aircraft sector. The octal numbers are used in the form of codes.
Base is 8.
Digits used: 0, 1, 2, 3, 4, 5, 6, and 7.
Just like in the binary number system, all decimal numbers can be represented in the octal number system as well. This table shows the decimal numbers 0 through 15 and their octal forms:
The Hexadecimal Number System has a base of 16 and has digits from 0 to 9 and letters of the alphabet A to F, where A is 10, B is 11, and so on up to F as 15. We express numbers in this system as (CD)16, (129A)16, (A56)16, etc.
Base is 16.
Digits used: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9.
Letters used: A, B, C, D, E, and F.
Imagine that you have a special way of counting on your fingers. Instead of just using your regular 10 fingers, you have 16 different symbols to count with. The first 10 symbols are just like your regular fingers, and they are represented by the numbers 0 to 9. But this is where it gets interesting: after you’ve counted up to 9 on your regular fingers, you don’t stop. Instead, you start using your special symbols, represented by the letters A, B, C, D, E, and F. These symbols represent the numbers 10, 11, 12, 13, 14, and 15, respectively.
So, when you count with your fingers in hexadecimal, it goes like this:
0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A (which represents 10), B (which represents 11), C (which represents 12), D (which represents 13), E (which represents 14), F (which represents 15).
The Hexadecimal Number System is commonly used in computer programming and in microprocessors. It is used to describe locations in the computer memory.
This table shows the decimal numbers 0 through 15 and their hexadecimal forms.
Is the value of 0 and 1 the same in different number systems?

A number in one particular number system can be converted into another with some specific rules. Let us learn how to do it.
Let us first learn to convert a decimal number into binary with an example. We will convert (35)10 to its binary form.
Step 1: Divide the number repeatedly by two and note down the remainders. See below:
Step 2: Write the remainders in reverse order.
The final number with only the 0 and 1 digits is the required number. So, (35)10 (100011)2.
We can also represent the above method in a different way.
Step 1: Create a table and place the number to be converted in the first row.
Remainders 110001
Reverse of Remainders 100011
Step 2: Write the base of the target number system, as shown. Here, we want to convert 35 into binary. So, we write 2.
Step 3: Now, divide the number by the base of the target number system and write the quotient in the next row. Write the remainder in the cell next to it.
Step 4: Repeat the process till you get a 0 as quotient.
Step 5: Take the remainder from bottom to top. That is the desired binary number. So, we again get (100011)2
Now, what if we want to convert a decimal number to an octal?
We will take the same step-by-step approach. This time, we will use 8 as divisor instead of 2. Let us write (435)10 in its octal form. We follow the same approach. So, (435)10 in octal is (663)8
Now, what if we want to convert a decimal number to a hexadecimal?
We will repeat the same process. This time the divisor will be 16, because the base for hexadecimal is 16. We will try to write (846)10 in the hexadecimal form. So, (846)10 in hexadecimal is (34E)16
Convert (442)10 into binary, octal and hexadecimal.
To convert a number in a given base to a decimal, let us use (101011)2 to understand the step-by-step approach.
Step 1: Write the number in a row and note the position of the digits from right to left, as shown:
make a third row and write the values of base to the power of the position. Notice the new
a fourth row and write the products of the digits in each place with the base power number. Notice the new row below.
Step 4: Find the sum of the numbers found in each place. In this case we get:
So, we get (43)10.
Now, let us try to convert an Octal into a Decimal. What is the decimal equivalent of (1705)8? We repeat the
We get, 512 + 448 + 0 +
So, (1705)8 is (965)10 in decimal.
Now, let us try to convert a Hexadecimal into a Decimal. What is the decimal equivalent of (1AC7)16?
We repeat the same process:
We get, 4096 + 2560 + 192 + 7 = 6855.
So, (1AC7)16 is (6855)10 in decimal.
Convert the following numbers into the decimal form.
There is a standard method to convert a binary number into its octal or hexadecimal form.
Let us see this using an example. We will convert (1110101)2 into its octal form.
Step 1: We will group the digits of the binary number. We will form groups of 3, because:
Base of octal = 8
Base of binary = 2
23 = 8
So, we form groups of 3 starting from the right. If 1 or 2 digits are left, we put them in a new group. See below:
Step 2: Now, treat each group as a separate binary number and convert into the decimal form. So, we get:
Step 3: We join the decimal numbers formed from the grouped digits. The number formed is the desired number.
So, (1110101)2 = (165)8.
Now, let us convert (110101011)2 into its hexadecimal form.
This time, we form groups of 4 starting from the right.
We get (1AB)16.
So, (110101011)2 = (1AB)16
Convert (1001001001)2 into its octal and hexadecimal form.

The method to convert hexadecimal and octal numbers into their binary form is also very similar. We will also use the concept of groups of digits that we learnt in the previous section.
Let us use the hexadecimal number (1A7)16 to go through the process.
Step 1: We take each digit of the number separately.
Step 3: Write each derived binary number in groups of 4.
Again, we are writing digits in groups of 4 because:
= 16 Base
= 2
= 16
Step 4: We now join the different 4-digit binary numbers derived. These final numbers are the desired binary number.
We get 000110100111.
So, (1A7)16 in the binary form is (000110100111)2 or simply (110100111)2.
Similarly, we can convert an octal number into binary by making the groups of 3 digits from the right.
Convert the following numbers into binary form.
1 (174)8
2 (B12)16
Converting hexadecimal numbers into octal numbers, and vice versa, has to be done via other number systems.
Let us say we want to convert (721)8 into its hexadecimal form.
We first find its decimal form. The decimal form of (721)8 is (465)10
Now, convert this decimal form into the hexadecimal form. The hexadecimal form of (465)10 is (1D1)16
So, the hexadecimal form of (721)8 is (1D1)16.
We follow the same steps while converting a hexadecimal number into its octal form.
Convert the following:
1 (764)8 into its hexadecimal form.
2 (2B1)16 into its octal form.
Binary addition is similar to the addition of decimal numbers.
When we add (0)2 and (0)2, we get 0. So, (0)2 + (0)2 = (0)2.
When we add (0)2 and (1)2, we get (1)2. So, (0)2 + (1)2 = (1)2.
But what happens when we add (1)2 and (1)2?
(1)2 is basically 1 in decimal as well. So, (1)2 + (1)2 = (2)10 = (10)2
So, a new place is created and 1 is carried over.
We can summarise the rules of binary addition as follows:
If we are adding x and y:
Think and Tell
In a binary system, only 1 can be carried over. In the decimal system, what numbers can be carried over?

So now, we can add bigger binary numbers by this method. For example, let us add (101101)2 and (10110)2. So, the sum of (101101)2 and (10110)2 is (1000011)2.
Following from the previous section, the rules of binary subtraction are as follows:
For example, let us subtract (11010)2 and (1100)2.
So, the subtraction of (11010)2 and (1100)2 is 01110.
A Number System is a way of representing and expressing numbers using a set of symbols or digits. Every number can be expressed in different number systems. But the value remains the same.
Base is the number of digits the number system uses. The base of binary is 2, octal is 8, decimal is 10, and hexadecimal is 16.
We use the Decimal Number System in our daily lives.
Binary Number System uses two digits: 0 and 1. Each binary digit is also called a bit.
The Octal Number System is a base-8 number system that uses digits from 0 to 7.
The Hexadecimal Number System has a base of 16. It uses digits from 0 to 9 and letters of the alphabet A to F where A is 10, B is 11, and so on.
We have different rules to convert the number expressed in one number system to another.
Hints
1 The Binary Number System uses two digits: and
2 The Binary digit is also known as a
3 The Decimal Number System is a base number system.
4 In Octal and Hexadecimal Number Systems, we have and digits, respectively.
5 When converting binary numbers to their octal form, we put digits together in groups of .
1 Which of the following digits cannot be used in the octal number system?
a 8
c 0
b 7
d 1
2 Another name for the base-10 number system is number system.
a Octal
c Binary
b Decimal
d Hexadecimal
3 What does “A” represent in the Hexadecimal Number System?
a 7
c 10
b 9
d 12
4 Which number system is used by digital devices like computers and calculators?
a Binary
c Octal
b Decimal
d Hexadecimal
5 When converting a binary number into a hexadecimal number, we will form groups of how many digits?
a 1 b 2
c 3 d 4
1 I use only two digits, 0 and 1. Computers use me to store and process information.
2 I am used in counting and doing calculations every day. I have 10 digits, starting from 0 to 9.
3 I am a number system with base 8.
4 I am unique as I let you use letters of the alphabet as my digits too.
5 I am common to all number systems. My value is also the same in all the number systems.
D.
1 The Decimal Number System is based on the digits 0 to 10.
2 In the Hexadecimal Number System, the letter “D” represents the digit 10.
3 The Binary Number System is the foundation of how computers understand and process information.
4 Computers can only perform addition, not subtraction.
5 (D716240234)16 is an octal number.
1 What is a number system?
2 What is the base of a number system? Why is it important?
3 What does the term “hexadecimal” mean in the context of number systems?
4 Convert the hexadecimal number (6475)16 into binary.
1
the following decimal numbers into their octal, hexadecimal, and binary forms.
2
the following binary numbers into their decimal, octal, and
3 Convert the following numbers into their decimal and binary forms.
4 Add the following binary numbers.
5 Subtract the first binary number from the second binary number.





Imagine exploring new places, paying bills, shopping for groceries, transferring money, ordering food, or chatting with friends from anywhere without having to leave home—all made possible because of the internet. The internet is a worldwide network of connected devices for sharing information and communication.
Nowadays, the internet has become an essential part of our everyday lives. With its widespread availability, our dependency on the internet has grown significantly. The internet has its advantages, however, it also hosts various dangerous unethical practices if one is not aware of them.
The internet has several advantages:
The internet is a huge library of information on every subject. You can use it to learn about different subjects and also learn different skills, such as using graphic design software, learning coding, improving communication skills, etc.
The internet provides access to news and current events from around the globe, helping us stay informed about what is happening in the world.
We can shop for clothes, books, gadgets, and almost anything online, saving time and letting us choose from a wide range of options.
Through the internet, we can talk to friends and family and even make new friends from around the world, breaking down geographical barriers. Email, messaging apps, and social media platforms enable instant communication, helping us stay in touch with loved ones.
Internet-based services allow us to pay bills, book flights, transfer money, and schedule appointments, all from the comfort of our homes.
The rise of the internet has led to massive growth in businesses. Individuals and companies have embraced online platforms to reach wider audiences, resulting in increased sales, global expansion, and innovative ways of conducting commerce.
The internet enhances media and entertainment experiences. People are drawn to the internet for activities like downloading songs, listening to music, watching movies, playing games, and reading newspapers, comics, and books online.

Lavanya has recently started a handmade jewellery business, but she is not attracting enough customers. How can the use of the internet help her?
The internet offers numerous benefits, but it is important to use it carefully because misusing it can create risks. Here are some of the internet’s threats:
Hacking is the process of breaking into a computer system, a website, or an online account without permission. Think of having a box with a lock that only you can open. It is similar to hacking if someone tries to unlock it without your permission. Hackers have advanced knowledge of computers and technology and use their skills to steal important data. Hacking is against the law and can harm people’s privacy and safety.
Hacking can be done for various reasons:
Black hat hackers want to steal information by spreading viruses or creating other problems.
Ethical hackers or White hat hackers work for companies, governments, or cybersecurity firms, engaging in cyber spying to identify vulnerabilities in computer systems, networks, or applications to prevent malicious hackers from stealing sensitive information from their countries or organisations. This is known as ethical hacking.
Malicious refers to actions done on purpose to cause harm or damage, often intending to create problems, distress, or negative outcomes for others.
When a hacker gets access to digital personal data without your permission, it is called a Cyber Attack.
Spams are unsolicited and often repetitive messages sent to a large number of people over the internet. These messages can be in the form of emails, texts, or comments on websites. Spam messages can have harmful links or files that might put viruses on your device, leading to unauthorised collection of your personal information.
Spamming is getting a bunch of unwanted advertisements in your emails.
Here are some ways you can recognise spam using the following tips:
• Notice errors in grammar and spelling, as legitimate sources usually have proper writing.
• Messages that do not include your email address in the To: or Cc: fields are common forms of spam.
• Attachments or hyperlinks from unknown sources might contain harmful software or inappropriate content.
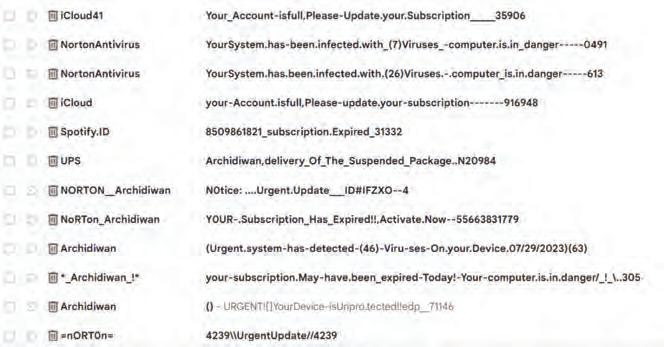
• Be cautious of messages with generic greetings like Dear Customer instead of your name.
Did You Know?
The very first internet message in 1969 was simply “LO”. Although the intention was to type “LOGIN”, the system crashed after just two letters, which ultimately marked the beginning of the internet.

Plagiarism means taking words, ideas, or images from someone else and presenting them as one’s own work. It is considered an ethical violation and a form of academic or intellectual fraud.
If someone is caught committing plagiarism, there can be various consequences, depending on the situation and the context in which the plagiarism occurred. Some schools and universities use special software to detect plagiarism. This tool checks the work against online sources and databases to find any copied parts. If caught, one could fail the assignment, the course, or even be expelled.
If copyrighted material is used without permission, legal action could be taken by the original creators or copyright holders. This may result in fines or other legal consequences.
Copyright allows creators to own and control their creative stuff, like books, music, videos, or art. It means others can’t use, copy, or share the original work without the permission of the copyright holders.
To avoid plagiarism:
• One can rephrase the material.
• Quote the words of another person by using quotation marks and giving credit to avoid plagiarism.
Cyberbullying is when someone uses the internet to hurt, target, threaten, or harass others. Cyberbullying can happen through various platforms, such as social media, text messages, emails, and online forums.
One must be vigilant while using the internet since cyberbullying exists in various forms. It could be in any of the following forms:
Harassment: Sending mean or hurtful messages, repeatedly posting offensive comments, or sharing embarrassing photos or secrets of someone publicly online.
Impersonation: Pretending to be someone else and sending harmful messages or spreading false information using their name.
Cyberstalking: Constantly tracking someone online or sending threatening or intimidating messages to someone, often causing fear and distress.
Imagine you wrote a story for class and someone copied your story and said they wrote it. What kind of crime is that?
Phishing is an act in which someone tricks you into revealing personal information like passwords, credit card numbers, or other sensitive data by pretending to be a trustworthy person or organisation. This usually comes in the form of messages or emails that seem authentic or from reliable sources like banks or government organisations.
Phishing messages often use attachments and urgent language, claiming your account is at risk or you’ll miss something important, pushing you to act quickly.

Phishing focuses on deceiving individuals into revealing sensitive information, often for malicious goals like identity theft or unauthorised access.
Online scams are dishonest schemes occurring on the internet where people try to trick others into giving away money, personal information, or valuable things. Online scams cover a wide range of misleading activities, like fake offers, lottery wins, and investment fraud, where victims are promised something valuable in return to manipulate them into sending money or valuable assets.
Piracy involves the unauthorised copying, distributing, or using of copyrighted materials like software, music, movies, or media without permission from the copyright owners. This causes financial losses for creators. Legal consequences, such as fines or criminal charges, can occur based on copyright laws.






Additionally, pirated content lacks the quality, security, and support of legitimate copies. Pirated software can even carry malware, risking harm to devices and personal data.
Softlifting means unauthorised installing, copying, or sharing software, especially among friends and family. Softlifting is considered to be the most common form of software piracy. This breaks copyright rules and software agreements.
Identity theft is a crime where someone steals personal information like names and credit card details to pretend to be another person. They do this for illegal purposes or to gain money. This stolen information is used to imitate the victim, enabling the thief to secure loans in the victim’s name or acquire prescription drugs, potentially affecting the victim’s medical history.

Identity theft can lead to financial troubles, damaged credit records, and emotional distress. It is a serious crime with significant consequences.
Identity theft can occur in any of the following ways:
Phishing: Sending misleading emails or messages that seem to be from legitimate sources, asking recipients to share sensitive information.
Data Breaches: Hacking into the databases of companies or organisations to steal large amounts of personal data.
Skimming: Illegally capturing credit card information by attaching devices to ATMs, petrol pumps, or other payment terminals.



Safe computing practices are all about protecting ourselves and our devices while using the internet and technology.
Some online safety practices are:
1. Children should always use the internet under the supervision of their parents.
2. Use passwords that are hard to guess and different for each account.
3. Keep your passwords secret and change them periodically.
4. Do not share or disclose your identity with strangers online.
5. Restrict your online profile to being checked by some trusted people only.
6. Keep your computer and phone up-to-date. Updates often fix security holes.
7. Do not click on links in emails or attachments from unknown sources.
8. When shopping or working online, stick to well-known and secure websites.
9. Set a strong password for your home Wi-Fi network to keep outsiders from sneaking in and causing trouble.
10. Do not use public Wi-Fi for online transactions, as it can increase the risk of hacking.
11. Download files from trusted sources only. Unclear downloads can bring unwanted risks to your device.
12. Be cautious when sharing pictures or your location online.
When engaging in online shopping, you may notice that the system remembers information about your prior searches. On platforms like YouTube, Instagram, Facebook, etc., you get suggestions similar to the items you recently searched for or purchased. Your online actions create digital footprints, leaving traces of your online activities.
Digital footprint is the trail of information that you leave behind when you do something online. This data is being saved and can be used for different purposes.
Digital Footprint is created every time you:
• Search for something on the internet
• Shop online
• Post a message
• Click on a link
• Watch a video


There are two types of digital footprints:
1. Active digital footprints: Active digital footprints are the data that are left behind when you knowingly share information online. For example, if you knowingly choose to post something on Instagram, you are aware that other users of the internet can view that information.
2. Passive digital footprints: Passive digital footprints are used when information about a user is gathered from him or her without their knowledge. For instance, when you “like” or “dislike” anything online, your preferences are used to customise various advertisements for goods you might find appealing.

What type of digital footprint is created when you search for a recipe online and the website tracks your search history to suggest more recipes?
Let’s learn what creates the traces of our online activities.
1. Browsing history: Every website you visit is recorded in your browser’s history.
2. Social media posts: Anything you post on social media platforms becomes a part of your digital footprint.
3. Searches: Search engines remember your searches and use them to show relevant advertisements.
4. Online purchases: Your online shopping history is stored on e-commerce websites.
5. Emails: Email communication leaves behind a record of your interactions.
It is important to prevent unwanted digital footprints to maintain our privacy online. Here’s how this can be achieved:
1. Privacy settings: Adjust privacy settings on social media platforms to control who can see your posts and personal information.
2. Private browsing: Use private or incognito mode in web browsers to prevent saving your browsing history.
Incognito mode, also known as private browsing or privacy mode, lets you browse the internet without leaving behind a trace of your activity.
3. Limited sharing: Be cautious about sharing personal details online. Think before you reveal too much.
4. Regular logout: Log out of your accounts after using them, especially on shared devices.
5. Clearing cache: Periodically clear your browser’s cache, cookies, and browsing history.
6. Avoid Over-sharing: Think twice before posting personal information, location, or sensitive data online.
Computing ethics should be followed to ensure that people use technology and computers in a responsible, respectful manner. Computing ethics keep us safe online, make sure we don’t harm others, and help us make good choices on the internet.
Computing ethics, also known as computer ethics, is a branch of ethics that deals with the moral principles and guidelines governing the responsible and fair use of technology, computers, and digital information. Here are some computing ethics principles that one can follow:
1. Respect the privacy of others and your own by not sharing sensitive information.
2. Always share correct information and do not spread fake stories.
3. Use strong passwords, update your software, and do not do harmful things like hacking.
4. Show respect for copyright by not using or sharing digital content without permission.
5. Make sure that everyone, irrespective of their limited abilities, resources, or location, can use technology easily.
6. Be clear about what you do online, especially when dealing with important tasks or choices that impact on others.
7. Keep learning about the latest in computer ethics and cybersecurity to make smart and ethical choices online.
8. Update your operating systems and other software, like antivirus, frequently.
9. Backup your important data regularly.
10. Be careful while sharing your electronic devices.
11. Buy a licensed copy of the software.
12. Make use of firewalls.
A firewall is a digital security guard for your computer or network. It helps keep out unwanted and potentially harmful data while allowing safe information to pass through.
1
Match the practice with its description.
Practice
Supervising children’s internet usage
Paying online using public Wi-Fi
Data breach consequences
Keeping antivirus updated
Description
The exposure of user data, such as emails and phone numbers
Computing ethics principles that one must follow
Ensuring that the use of the internet is under parental supervision
It can increase the risk of hacking, resulting in losing all the money in the account
Tick () the correct option.
a What is the potential consequence of sharing personal information, location, or sensitive data online?
i Your online presence will become more interesting
ii It will lead to decreased digital footprints
iii Your online security will improve
iv It will threaten your privacy and security
b Which type of digital footprint is created when information is gathered about you without your knowledge?
i Active digital footprint
iii Public digital footprint
c What is one of the goals of computing ethics?
i Spreading fake stories
iii Hacking
ii Passive digital footprint
iv Private digital footprint
ii Preventing harm
iv Ignoring privacy
1 The internet lets us book tickets online, shop, talk to friends, and pay bills, no matter where we are.
2 The internet helps businesses grow by reaching more people, doing worldwide transactions, and communicating easily.
3 Hacking is the process of breaking into a computer system, a website, or an online account without permission.
4 Spams are unsolicited and often repetitive messages sent to a large number of people over the internet.
5 Plagiarism means taking words, ideas, or images from someone else and presenting them as one’s own work. It is considered a crime or an act of fraud.
6 Cyberbullying is when someone uses the internet to hurt, target, threaten, or harass others.
7 Phishing is when someone tricks you into sharing private information, like passwords or credit card numbers by pretending to be someone you trust.
8 Online scams are tricky schemes on the internet where people try to trick others into giving away money, personal information, or valuable items.
9 Piracy is when people copy or use copyrighted things, like software, music, or movies, without permission from the owners.
10 Identity theft is a crime where someone steals personal information, like names and credit card details, to pretend to be another person.
11 To be safe online, create strong passwords and update them regularly.
12 Avoid clicking on links from unknown sources to stay safe.
13 Digital footprint is the trail of information that you leave behind when you do something online.
14 Incognito mode lets you browse the internet without leaving behind a trace of your activity.
15 Computing ethics deals with the moral principles and guidelines governing the responsible and fair use of technology, computers, and digital information.
Hints cyberstalking ethical private browsing firewall spams
1 are unsolicited and often repetitive messages, sent to a large number of people over the internet.
2 An hacker works for governments or cybersecurity firms.
3 Constantly tracking someone online is called .
4 lets you browse the internet without leaving behind a trace of your activity.
5 A is a digital security guard for your computer or network.
1 What is the primary purpose of white hat hackers?
a To spread viruses and malware
c To explore computer systems for fun and learning
2 What is the purpose of online scams?
a To provide free services to users
c To enhance online security measures
b To steal sensitive information
d To keep organisations safe from security risks
b To trick individuals into sharing personal information or money
d To educate people about ethical hacking
3 Which of the following is a good practice to prevent unwanted digital footprints?
a Sharing personal details openly
c Clearing cache and cookies regularly
b Logging into accounts on public computers
d Using the same password for all accounts
4 Which of the following is an example of an ethical computing practice?
a Sharing someone else’s work without permission
c Spreading rumours online
b Creating strong and unique passwords
d Ignoring software updates for security reasons
5 Which of the following is NOT a recommended online safety practice?
a Using strong and unique passwords
c Keeping operating system and antivirus updated
b Sharing personal information with strangers
d Using private browsing mode
1 I let you book tickets or pay electricity bills from the comfort of your home.
2 I am a bunch of unwanted and repetitive advertisements in the emails of the users.
3 I am the act of unauthorised installing, copying, or sharing software without permission, usually among friends and family.
4 I am a law that grants creators ownership and control over their creative works.
5 I am the type of digital footprint that remains when you knowingly share information online.
1 The internet restricts us from booking tickets online.
2 The internet enables us to learn about different subjects and acquire new skills.
3 Piracy is the unauthorised copying or distributing of copyrighted materials.
4 Digital footprints do not leave any hints of we do online.
5 Keeping software updated is not necessary for cybersecurity.
1 What is the internet?
2 What is softlifting?
3 What are some computing ethics principles?
4 What are digital footprints? Write their types.
5 What are some ways you can recognise spam?
1 Pranjal visits random and unsafe websites and enters his details on them, and as a consequence, he receives plenty of unwanted emails. What are these unwanted emails called?
2 Priya and Moni created an art project about “Save Wildlife” that won a competition. Unfortunately, someone stole their work and shared it online without permission. What crime did they become victims of?
3 During COVID-19, the avoidance of exchanging physical cash was supported by the internet. How did the internet help in this situation?
4 Ramya was searching for shoes. Later, she received suggestions from various shoe brands in the form of advertisements. Why did these advertisements appear?
5 Arnav sees a funny photo of one of his friends on social media, and he wants to share it on his own social media account. What do you think he should do to ensure he does not violate anyone’s rights and share the content properly?




Imagine that your mother plans to start giving you pocket money of ₹500 to help you learn the value of money. At the end of the month, your mother asks you how you spent the money and how much you have saved. You tell her roughly but do not have an exact record of your expenses and savings.
You can have an exact record of your expenses and savings using a tool called a spreadsheet.
A spreadsheet is a tool for storing data, performing computations, organising information, and analysing data in a tabular format.
There are various spreadsheet tools such as Microsoft Excel, Google Sheets, and LibreOffice Calc. Microsoft Excel requires a license to use, whereas Google Sheets and LibreOffice Calc are web-based applications that are free to use and allow multiple users to work on the same spreadsheet simultaneously.
We will be learning Google Sheets to prepare a spreadsheet for your expenses.
Before we start, let us learn about the uses of spreadsheets.
1. Tracking expense and savings: Spreadsheets can be used to track income and expenses, create budgets, and set financial goals.
The first spreadsheet program was VisiCalc, which was released in 1979.

2. Organising data: Spreadsheets can be used to organise data in many ways, such as creating lists, tables, and charts.
3. Performing calculations: Spreadsheets can be used to perform a variety of calculations, such as adding, subtracting, multiplying, and dividing numbers. We can even perform complex calculations such as those related to trigonometric functions and statistical analysis.
4. Creating charts and graphs: Spreadsheets can be used to create charts and graphs to visualise data.
Let us create a Google spreadsheet for tracking our monthly expenses.
Steps to create and name a spreadsheet:
1. Open the Chrome browser and then go to https://docs.google.com/spreadsheets/.
2. Click the plus sign to open a blank spreadsheet.

3. Rename the spreadsheet at the top-left corner by replacing ‘Untitled spreadsheet’ with your project name.

What are some other things we can do with spreadsheets?

A spreadsheet is made up of rows and columns. These rows and columns form a grid or a table.
A Google Sheets window has the following components:
• Cells: Cells are the small boxes in a spreadsheet where you can enter data.
• Rows: Rows are the horizontal lines of cells in a spreadsheet. Rows are numbered 1, 2, 3, and so on.
• Columns: Columns are the vertical lines of cells in a spreadsheet. Columns are labelled with the letters A, B, C, and so on.
• Active cell: An active cell is the cell that is currently selected. During selection, it is highlighted with a blue border.
• Cell address: A cell address is the name of a cell in a spreadsheet. This address is made up of a column letter and a row number, such as A1 or B3.
• Formula bar: The formula bar is located above the spreadsheet. In this bar, you can enter and edit formulas, which are used to calculate values in cells.
• Sheet tab: A sheet tab is a labelled tab located at the bottom of the spreadsheet window. You can have multiple sheets in Google Sheets by adding more sheet tabs.
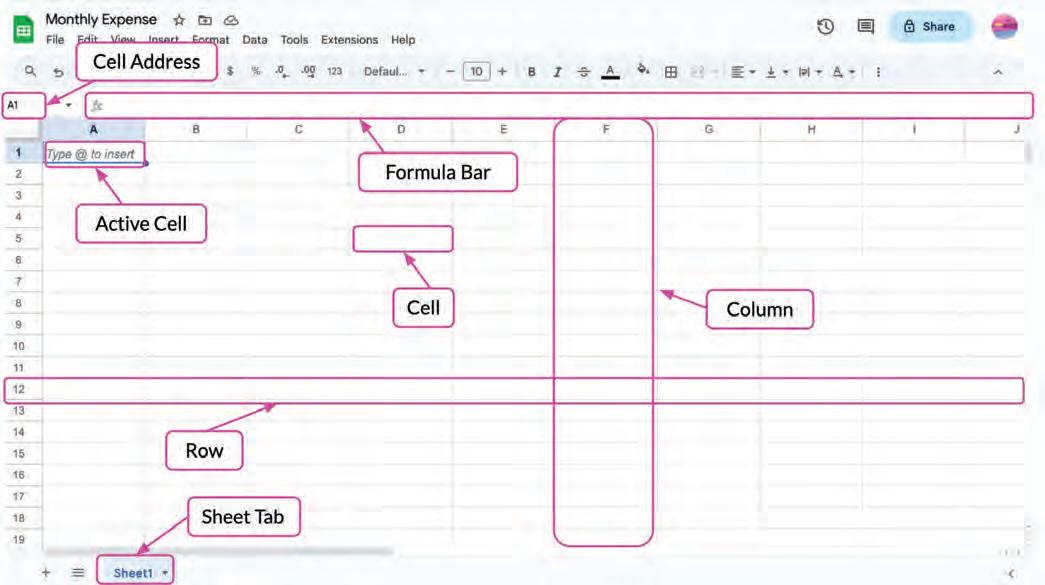

We can move around in a spreadsheet, using the arrow keys to change an active cell and look at different information. To move left, press the left arrow key. To move right, press the right arrow key. To move up, press the up arrow key; and to move down, press the down arrow key.

1
Match the columns.
Column A
Active cell
Formula bar
Cell address
Column B
Enter and edit formulas
Name of a cell in a spreadsheet that contains a column letter and a row number
A tool for storing data, performing computations, organising information, and analysing data
Spreadsheet The currently selected cell
2
Answer the following.
a What are cells?
b What is the blue highlighted box known as?
c What is a cell address?
d With what component can we access multiple sheets within Google Sheets?
e How can we change an active cell?
To enter data in a cell, first click the cell to select where you want to type and then start typing.
Now, let us start our project to track our monthly expenses.
Type the given data in a spreadsheet:
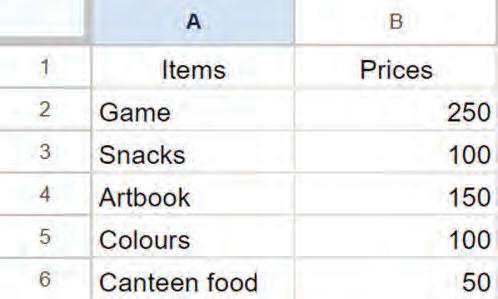
We entered the names of the items we bought and their prices. As you can see, the values in a data cell can be of various types. Let us learn about the data types Google Sheets can have.
There are two main data types a cell can have in Google Sheets:
1. Numbers: Numbers can be integers or decimals. They can also be positive or negative.

2. Text: Text is a sequence of characters. These characters can be letters, numbers, or operators. Text can also include date and time.
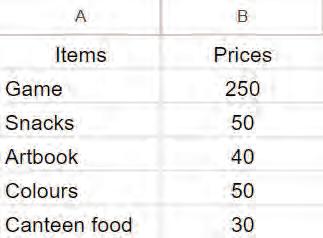

Now, we have a record of our monthly expenses on the spreadsheet. To find out how much money we spent in a month, we need to use a formula.
A formula is a logical expression of numeral values and operators (+, –, /, ×, %) to do the calculations.
For example, you can add a formula in a cell to add up the numbers in the entire column or to find the average of a group of numbers.
In a spreadsheet, formulas are made up of numbers, operators, and cell addresses.
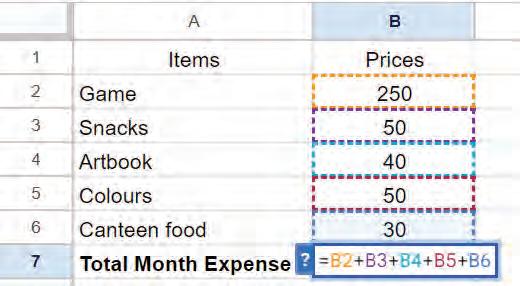
Let us find out the total amount of money spent in a month by adding a formula in the prices column (B column).
To calculate the total monthly expense:
1. Select the cell where you want the total monthly expense to appear.
2. Type the ‘=’ sign, followed by the cell address you want to add, separated by the ‘+’ operator.
For example: =B2+B3+B4+B5+B6.
Now, let us find the average price of the items bought in the month. To do this, we will add up the prices of all the items and then divide the sum by the number of items.
To calculate the average price of the items:
1. Select the cell where you want the average price to appear.
2. Type the formula to find the average price.
For example: =(B2+B3+B4+B5+B6)/5.

We learnt how to add a formula in a cell to perform calculations in a spreadsheet. However, there is a quicker method for calculations, which is known as a function.
In Google Sheets, we have several built-in functions for various operations.
Functions in Google Sheets are the formulas that are already available. They can analyse data and perform calculations on it.
A function can be applied to a cell range, which is a group of adjacent cells (cells located next to each other).
A cell range is defined by specifying the starting cell and the ending cell. This range includes all the cells that fall between these two cells in a continuous sequence.
Cell ranges are represented using a colon (:) that separates the starting and ending cells.
Refer to the given table to learn about the built-in functions available in Google Sheets. Cell ranges and cell addresses given in the table can be referred to from the monthly expenses project that we have created in Google Sheets.
Function Name Purpose Example
SUM Calculates the sum of the values in a cell range.
AVERAGE Calculates the average of the values in a range of cells.
PRODUCT Multiplies the values in the specified range of cells.
MOD Returns the remainder of the division of a number by a divisor.
Input =SUM(B2:B6)
Output 420
Input =AVERAGE(B2:B6)
Output 84
Input =PRODUCT(B2:B6)
Output 750000000
Input =MOD(B3,7)
Output 1
SQRT Returns the square root of a number. Input =SQRT(36)
Output 6
INT Rounds the number to an integer value. Input =INT(–25.6)
Output –26
POWER Returns the result of raising a number to a specified power.
Input =POWER(B6,3)
Output 27000
ABS Returns the absolute value of a given number. Input =ABS(–23)
Output 23
COUNT Counts the number of cells in a range that contain numbers.
Input =COUNT(B2:B6)
Output 5
MIN Returns the lowest value in a range of cells. Input =MIN(B2:B6)
Output 30
Function Name Purpose
Example
MAX Returns the highest value in a range of cells. Input =MAX(B2:B6)
Output 250
IF Verifies if the provided condition is met. This function returns value1 when the condition is true and value2 when the condition is false.
=IF(condition, value_if_true, value_if_ false)
Input =IF(B2<50,’Affordable item’,’Costly item’)
Output Costly item
CONCATENATE Combines multiple text strings into one. Input =CONCATENATE (A5,A3)
Output ColoursSnacks
LEN Returns the length of the text string. Input =LEN(A1)
Output 5
UPPER Converts the text into capital letters. Input =UPPER(A5)
Output COLOURS
LOWER Converts the text into small letters. Input =LOWER(A6)
Output canteen food
TODAY Returns the current date.
Input =TODAY ()
Output 10/26/2023
NOW Returns the current date and time. Input =NOW()
Output 10/26/2023 9:41:52
Let us try to calculate the total expenses and the average price using the built-in functions.
The SUM() function is used to calculate the sum of the values in a cell range. To calculate the total monthly expense using the SUM() function:
1. Click the cell where you want the sum to appear.
2. Type the ‘=’ sign, followed by the function name with round brackets = SUM().
3. Inside the round brackets, add the cell range you want to calculate, i.e., =SUM(B2:B6)
4. To get the total monthly expense, press Enter.

420
The AVERAGE() function is used to calculate the average of the values in a range of cells.
To calculate the average price of the items using the AVERAGE() function:
1. Click the cell where you want the average to appear.
2. Type the ‘=’ sign, followed by the function name with round brackets =AVERAGE()
3. Inside the round brackets, add the cell range you want to calculate, i.e., =AVERAGE(B2:B6)
4. To get the average price, press Enter




Now, we have a complete and accurate record of what and how much we spent in a month. Whenever we create something on a computer, we need to save it so that we can come back to it later to check or update it, as needed.
However, Google Sheets makes this even easier with its autosave feature that automatically saves your data every time you make a change.
When done, you can close the spreadsheet by clicking Close.
1
Observe the given table.
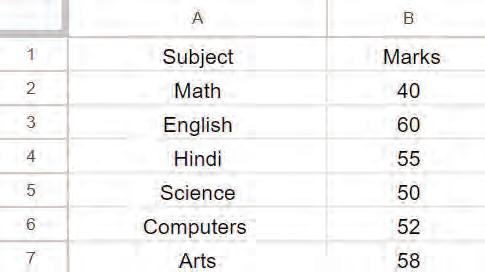
Identify and write down the values that the given functions will return.
a =COUNT(B2:B7)
b =AVERAGE(B5:B7)
c =LEN(A6)
d =UPPER(A5)
2
Which function returns the remainder of the division of a number by a divisor?
a SUM()
c PRODUCT()
b AVERAGE()
d MOD()
1 A spreadsheet is a tool for storing data, performing computations, organising information, and analysing data in a tabular format.
2 An active cell is a cell that is currently selected. When selected, it is highlighted with a blue border.
3 A cell address is the name of a cell in a spreadsheet. It is made up of a column letter and a row number, such as A1 or B3.
4 A sheet tab is a labelled tab located at the bottom of the spreadsheet window. You can have multiple sheets in a Google Sheets by adding more sheet tabs.
5 You can move around in a spreadsheet using the arrow keys to change the active cell and look at various types of information.
6 A cell can have two main data types in a Google Sheets: numbers and text.
7 A formula is a logical expression of numeral values and operators (+, –, /, ×, %) to do the calculations.
8 Functions in Google Sheets are formulas that are already available. These functions can analyse data and perform calculations.
9 A cell range is defined by specifying the starting cell and the ending cell. This range includes all the cells that fall between these two cells in a continuous sequence.
A. Fill in the Blanks.
Hints functions spreadsheet autosave formula bar cell range
1 A is a tool for storing data, performing computations, organising information, and analysing data in a tabular format.
2 The is located above the spreadsheet.
3 The SUM() function is used to calculate the sum of the values in a .
4 are the built-in formulas that analyse data and perform calculations on it.
5 Google Sheets has feature that automatically saves data every time you make a change.
B. Tick () the Correct Option.
1 Which of the following is the correct way to write the SUM() function?
a =SUM(B2-B6)
c =SUM(B2:B6)
b =SUM(B2+B6)
d =SUM(B2 * B6)
2 What is the cell address for the cell in the fifth column and third row?
a C3
c E3
b C5
d F3
3 What is the output of the formula =SQRT(16) in Google Sheets?
a 2
c 8
4 Which symbol is used to begin a formula in Google Sheets?
a = (equals sign)
c – (minus sign)
b 4
d 16
b + (plus sign)
d * (asterisk)
5 Which function is used to combine multiple text strings into one?
a CONCATENATE
c UPPER
C. Who Am I?
b LEN
d LOWER
1 I am a function used to multiply the values in the specified range of cells.
2 I am a function used to return the absolute value of a given number.
3 I am a function used to verify whether a provided condition is met.
4 I am a function that converts text into lowercase.
5 I am a function that returns the length of a text string.
D. Write T for True and F for False.
1 An active cell is a cell that is currently selected.
2 Rows are the vertical lines of cells in a spreadsheet.
3 MAX returns the lowest value in a range of cells.
4 COUNT returns the number of cells in a range that contain numbers.
5 MOD returns the square root of a number.
E. Answer the Following.
1 List the common uses of spreadsheets.
2 Which function is used to find the minimum value in a range of cells? Give an example.
3 What are the basic components of the Google Sheets window? Name any three.
4 What is the output of the following formula?
=UPPER(‘hello’)
5 What is the output of the following formula?
=CONCATENATE(‘Hello’, ‘world!’)
F. Apply Your Learning.
1 What is the output of the following formula, given that the value of the cell C1 is 50?
=IF(C1>10, ‘Greater than 10’, ‘Less than or equal to 10’)
2 Explain the purpose of the IF function in Google Sheets. Use this function to check if the value in cell H1 is greater than 50. If it is, display ‘Yes’; otherwise, display ‘No’. Provide the formula and the result.
3 Create a formula that multiplies the values in cells J1 and J2 and then adds the result to the value in cell J3. Display both the formula and the final result.
4 Observe the given table.
Now, write the formula and the result for the following questions.
a What is the total cost of all the stationery items in the table?
b Which stationery item is the most expensive?
c Which stationery item is the least expensive?
d What is the average price of a stationery item in the table?


Web development is the process of designing, building, and maintaining web applications that work on the internet.
Imagine you need to make a cardboard house for your school competition project. Before you begin making the project, you need to plan for it.
You need to decide how many rooms your cardboard house will have and how they will be arranged. You also need to find out what materials you will need to build it.
Once you have your plan ready, you can start building the house by putting together the various parts like walls, roof, and windows.
Web development is similar to building a cardboard house; but instead of using cardboard and tapes, you would be using code. When you build a website, you use code to tell the computer how to display the various parts of the website, such as the text, images, and videos.
Web development involves multiple tasks, such as:
• Designing the layout and appearance of the website
• Writing the code that makes the website work
• Adding content to the website, such as text, images, and videos

The first website, CERN, was created in 1989 and is still alive today.
There are three main types of programming languages used in web development:
HTML (HyperText Markup Language): HTML is the markup language used for creating websites. It is also used to structure the content of a website. For example, HTML tags can be used to tell the computer whether a piece of text is a heading, a paragraph, or a list.
CSS (Cascading Style Sheets): CSS is used to style the content of a website. For example, CSS can be used to change the font size, colour, and alignment of text.
JavaScript: JavaScript is a programming language that can be used to add interactivity to a website. For example, JavaScript can be used to create menus, animations, and games.
HTML
HTML stands for ‘HyperText Markup Language’. It is used to develop web applications. It tells a web browser how to display content on a website.
In HTML, ‘Hypertext’ means the text that is more than static text. It can be interactive and linked to other pages or resources.
Markup are the tags we use in HTML to structure and format the text on a web page. These tags are the instructions that tell the browser how and where to display the content on a page.
1 Easy to Learn: HTML is an easy language to learn, even for beginners. It is made up of tags that tell the browser what to do.
HTML is not a programming language because it does not include any logic or algorithms.
2 Platform Independent: HTML is platform independent, which means that it can be used to create web pages that can be viewed on any device, regardless of the operating system or web browser.
3 Media Support: HTML can be used to display images, videos, and audio on web pages.
4 Hypertext: HTML supports hypertext, which means that text on a web page can be linked to other web pages or resources.
5 Semantic Structure: HTML introduced many new semantic elements, which can be used to improve the accessibility of web pages.
6 Case Insensitive: HTML is a case-insensitive language.
An HTML document is structured into two main parts: the head and the body.
The head contains information about the document, such as the title.
The body contains the content of the web page, such as text, images, and videos. The body is displayed in the browser window.
The basic structure of an HTML document looks like this:
1 The <html> and </html> tags enclose the entire document.
2 The <head> and </head> tags enclose the head section of the document.
3 The <title> and </title> tags enclose the title of the document.
4 The <body> and </body> tags enclose the body section of the document.
A web browser is a software application that allows you to access and view web pages.
There are many web browsers available, such as Google Chrome, Mozilla Firefox, Microsoft Edge, and Apple Safari. All web browsers work in a similar way, but they may have different features and user interfaces.
HTML Document Basic Structure <html> <head> <title> Document Title</title> </head> <body> <!-- Content goes here --> </body> </html>
They allow us to browse websites, watch videos, listen to music, and play games.
Some of the basic components of a web browser are as follows:
• Address bar: The address bar is where you type the URL of the website you want to visit.
• Navigation buttons: The navigation buttons allow you to move forward, back, and refresh the current web page.
• Tabs: Tabs allow you to have multiple web pages open at the same time.
• Bookmarks: Bookmarks allow you to save the URLs of your favourite websites so that you can easily access them later.
• History: The history feature allows you to view a list of the websites you have recently visited.
Tags
A tag tells the browser how to display the content that follows it. Tags are enclosed in angle brackets (< and >). For example, <h1> is the opening tag for heading and </h1> is the closing tag for heading. To create an HTML document, we have the following tags:
Tag Purpose Syntax
<!----> Used to insert comments in the HTML code. <!--comment–->
<p> It is used as the paragraph tag that is used to add a paragraph.
Heading tags
HTML heading tags are used to add headings and sub-headings to the content you want to display on a web page. HTML has six levels of heading from <h1> to <h6>.
<p>content</p>
<h1>Most important heading</h1>
<h2>content</h2>
<h3>content</h3>
<h4>content</h4>
<h5>content</h5>
<h6>Least important heading</h6>
<div> This tag is used in HTML to make divisions of content in the web page such as text, images, and header.
<br> Inserts a single line break
<div>content</div>
Should be added where the line break is needed. <b> Converts the text into bold <b>text</b>
<i> Converts the text into italics <i>text</i>
<img> Displays an image <img src=”https://example.com/image.png” alt=”This is an image of a cat.” />
<a> Creates a link. Links can be used to link to other web pages, images, or other resources.
<a href=”https://example.com”>This is a link to the example website.</a>
An element is a combination of a tag and its content. For example, the <h1> element is a heading element. There are mainly two types of HTML elements:
1 Container Elements: Container elements are HTML elements that can contain other elements or text within them. They have both an opening tag and a closing tag to enclose their content.
Examples: <html></html>, <head></head>, <body></body>.
<h1> This is my first HTML document. </h1>
2 Empty Elements: Empty elements, also known as void elements or self-closing elements, do not contain any content between opening and closing tags. They are self-contained and do not require a closing tag.
Examples: <br>, <hr>, <img>.
It is used to define the characteristic of an HTML element. An attribute is always placed in the opening tag of an element and generally provides additional styling (an attribute) to the element.
<h1> <font color= ''red''> This is my first HTML document. </font> </h1>
Let us build a simple Space Exploration web page project while learning the concepts in the chapter. We will be building this project by dividing it into tasks.
Task 1: Create a web page and name it Space Exploration. Add the heading ‘Space Exploration’ and then add an introduction for it.
Code
<html>
<head>
<title>Space Exploration</title> </head> <body>
<h1>Space Exploration</h1> <div>
<p><b>Space exploration</b> is the study of space and everything beyond Earth’s atmosphere. We use robots and spacecrafts to explore space and learn new things about it. <br><br> Space exploration has led to many <i><b>amazing discoveries</b></i>, such as exoplanets (planets that orbit other stars), water on Mars, and black holes. <br><br> Space exploration is also important for inspiring people and showing us what is possible. </p> </div> </body>
</html>
Space exploration is the study of space and everything beyond Earth's atmosphere. We use robots and spacecrafts to explore space and learn new things about it.
Space exploration has led to many amazing discoveries, such as exoplanets (planets that orbit other stars), water on Mars, and black holes.
Space exploration is also important for inspiring people and showing us what is possible.
1 Match the following terms with their descriptions.
Column A
Column B
<h1> Is a language for structuring web content.
<!-- --> Converts the text into bold.
<div> Is used for inserting comments in HTML code.
HTML Is used to create a division within a web page.
<b> Defines the main heading of a web page.
2 Identify the error in the following element examples:
a <titl>My Web Page</title>
b <h1>Welcome to My Page<h1>
c <p>This is a paragraph</h>
d <a href=”https://www.example.com” Example Website</a>
CSS stands for Cascading Style Sheets. It is a language used to style HTML elements. CSS can be used to change the appearance of HTML elements, such as their font, colour, and size.
Some key features of CSS include:
1 Selectivity: CSS can be used to select specific HTML elements to style such as changing colours, styling fonts, spacing elements, and resizing them.
2 Consistency: You can use the same styles for many pages on a website to make them look similar.
3 Cascading: CSS styles are applied in cascading order. This means that the most specific style will be applied to an element, even if there are other styles that are more general.
4 Responsive design: CSS can be used to create responsive web pages that work on all devices, from desktop computers to smartphones.
5 Animations and transitions: CSS can be used to add animations and transitions to web pages, which can make them more visually appealing and engaging.
There are three ways to add style to an HTML document:
1 Inline CSS: Inline CSS is used to style a single HTML element. To add inline CSS, you use the style attribute.
For example, the following code will make the <h1> element red and 20 pixels in size: <h1 style=”color: red; font-size: 20px;”>This is a heading</h1>
2 Internal CSS: Internal CSS is used to style all the elements on a single HTML page. To add internal CSS, you use the <style> tag. The <style> tag should be placed in the <head> section of your HTML document.
For example, the following code will make all <h1> elements on the page red and 20 pixels in size:
Code
<html>
<head>
<style> h1 { color: red; font-size: 20px; }
</style>
</head>
<body>
<h1>This is a heading</h1>
<h1>This is another heading</h1>
</body>
</html>
3 External CSS: External CSS is used to style all the elements on all of the pages of a website. To add external CSS, you use the <link> tag. The <link> tag should be placed in the <head> section of your HTML document.
For example, the following code will link to an external CSS file called style.css:
Code
<html>
<head>
<link rel=”stylesheet” href=”style.css”>
</head>
<body>
<h1>This is a heading</h1>
</body>
</html>
The style.css file would contain the following CSS:
Code
h1 { color: red; font-size: 20px; }
If you only need to style a single element, then use inline CSS.
Think and Tell
What CSS will you use to style a web page?
If you need to style all the elements on a single page, then use internal CSS. If you need to style all the elements on all the pages in a website, then use external CSS.
CSS classes are a way to group similar HTML elements together so that you can style them all at once. This can save you a lot of time and effort, especially if you have a lot of similar elements on your page.
To create a CSS class, you add the class attribute to an HTML element and assign it a unique name. For example, the following code would create a CSS class called my-class:
<p class=”my-class”>This is a paragraph</p>
Once you have created a CSS class, you can style it using the . (dot) character and the class name. For example, the following CSS code will make all paragraphs with the my-class class red and 20 pixels in size:
.my-class {
color: red; font-size: 20px;
Selectors are used to select the HTML elements that you want to style, and properties are used to define the styles that you want to apply to those elements.
Some of the most common selectors in HTML include:
1 Element Selectors: Select elements by their tag name, such as h1, p, or img.
2 Class Selectors: Select elements by their CSS class.
3 ID Selectors: Select elements by their ID.
4 Combination Selectors: Combine multiple selectors to target specific elements.
There are many CSS properties, including:
CSS Property Purpose Syntax
color Sets the colour of the text. color:blue
font-family Sets the font family of the text. Font-family:cambria font-size Sets the size of the text. Font-size:x-small
Note: x-small, small, medium, large, x-large, xx-large can also be used as values.
font-weight Sets the weight or thickness of the text. Font-weight: bold
Note: lighter, or any number can also be used
text-decoration Formats the text.
Text-decoration: underline
Note: line-through, overline can be used. Text-align Aligns the text.
Text-align: left
Note: right, center, justify can be used. background-color Sets the background colour of the element. Background-color:red background-image Sets background images for an element, you can set one or more images.
Background-image:url(”https://example. com/image.png”)
border To set the border around the element. Border: solid border-color Sets the colour of the border of an element. border-color:blue border-radius Round the corners of the outer border edges of an element. border-radius:30px
padding To set the space around the content of the element.
padding:40px
Note: Any number can be added according to the use.
margin To set the space around the element itself. margin:20px
Note: Any number can be added according to the use.
You can also use a shortcut called the background property to set multiple background-related properties in one declaration. For example, you can use the background property to set the background colour, image, size, and position of a div element all at once.
Here is an example:
div { background: blue url(‘image.jpg’) no-repeat center/cover; }
In this example:
• blue sets the background colour to blue.
How are Selectors and Properties different?
What are the benefits of having classes in an HTML document?
• url(‘image.jpg’) sets the background image to the image named image.jpg.
• no-repeat prevents the image from repeating.
• center/cover positions and sizes the image so that it covers the entire div element.
You can apply the background property to any HTML element, not just to div elements. For example, you can apply it to the <body> element to set the background of your entire web page.
Project: Space Exploration
Task 2: Use internal CSS to make the project colourful and attractive.
1 Inside the head element, create a style element and:
a Add a style for body element.
b Create a content class for styling internal content.
Code
<html>
<head>
<title>Space Exploration</title>
<style> body { background-color: powderblue; color: black; text-align: center; }
.content{ color: darkred; text-align: left;
</style>
</head>
2 Update the body element by applying the content style in content div.
Code
<body>
<h1>Space Exploration</h1>
<div class=content>
<p><b>Space exploration</ b> is the study of space and everything beyond Earth’s atmosphere. We use robots and spacecrafts to explore space and learn new things about it. <br><br> Space exploration has led to many <i><b>amazing discoveries</b></i>, such as exoplanets (planets that orbit other stars), water on Mars, and black holes. <br><br> Space exploration is also important for inspiring people and showing us what is possible.
</p>
</div>
</body>
</html>
Output

1 Fill in the Blanks.
Hints background-color background internal similar <link>
a If you want to style all elements on a single HTML page, you can use CSS.
b CSS classes are used to group HTML elements together.
c The shorthand for setting multiple background-related properties in one declaration is the property.
d To set the background colour of an element, you can use the property.
e External stylesheets are linked to HTML documents using the element.
2 Write T for True and F for False.
a Internal CSS is added to the <body> section of an HTML document.
b You can create a CSS class by adding the class attribute to an HTML element.
c The no-repeat property of CSS prevents the image from repeating.
d External stylesheets are included directly within an HTML document, using the <style> element.
e CSS can be used to change the colour and size of HTML elements.
1. Create a web page with the following content:
a. A title: My Dream Vacation
b. A paragraph describing my dream vacation
c. Set the font and background colour.
2. Create a web page with the following content:
a. A title: My Favourite Game
b. A CSS class called ‘my-favourite-game’ that sets the background colour of the page to cyan.
c. A paragraph describing my favourite game and why I like it.
A Fill in the Blanks.
Hints head web applications angle body external
1 Web development involves designing, building, and maintaining
2 The basic structure of an HTML document consists of the and the .
3 HTML tags are enclosed in brackets.
4 You can apply CSS using three main methods: inline styles, internal stylesheets, and stylesheets.
B Tick () the Correct Option.
1 Which type of CSS would you suggest to style a single HTML element?
a Internal CSS
c Inline CSS
2 Which HTML tag is used to create a single line break?
a <newline>
c <b>
3 Which of the following is an example of a CSS class?
a .my-class
c <class=”my-class”>
b External CSS
d Outline CSS
b <line-break>
d <br>
b my-class
d my.class
4 Which of the following HTML elements is used to create a link?
a <p>
c <h1>
b <img>
d <a>
5 Which of the following CSS properties is used to set the colour of the border of an element?
a border-color
c bordercolor
C Who Am I?
b color
d border
1 I define the characteristics of an HTML element and am placed in the opening tag.
2 I make divisions of content on a web page, like sections of text, images, headers, and more.
3 I am a CSS property to set the space around the element itself.
4 I convert text into an italic format in HTML.
5 I display images on a web page. You can specify the image source and alternative text using attributes with me.
D Write T for True or F for False.
1 A web browser is a software application that allows you to access and view web pages.
2 CSS-created web pages don’t work on all devices.
3 You can use the . (dot) character and the class name to style a CSS class.
4 Element selectors select elements by their tag name, such as h1, p, or img.
5 Class Selectors select elements using their ID.
E Answer the Following.
1 What is web development, and what are its two main categories?
2 What is the basic structure of an HTML document?
3 What does the HTML tag <img> do, and how can you specify the source of an image?
4 What is CSS, and what are some of its features?
5 What are selectors and properties in CSS? Provide examples of each.
F Apply Your Learning.
1 In CSS, how would you make all paragraphs with the class “my-class” blue in colour and 30 pixels in size?
2 When you use the HTML tag <div>, what purpose does it serve?
3 You have a paragraph of text that you want to make bold. How would you do this using HTML tags?
4 Create a CSS class named “highlight” that changes the text colour to yellow and applies the ‘back.png’ images as background of the web page.
This book embodies the principles outlined in the National Education Policy (NEP) 2020. It unveils the world of computer science through a unique and captivating pedagogical approach—seamlessly integrating curriculum content into the mesmerizing adventures of Mel and Conji, fictional figures hailing from the enchanting world of Avora. Our aim is to prepare learners for the dynamic and technology-driven landscape of the 21st century, equipping them with the essential skills they need to thrive in an ever-evolving world.

• Explore More: QR codes to explore an exciting application of the concept. This element builds curiosity in children and helps them grasp concepts through digital visual aids.
• Discuss: Questions to trigger engaging group discussions in the classroom.
• Think and Tell: Probing questions to stimulate thinking at an individual level.
• Did You Know? Interesting facts related to the application of a concept.
• Points to Remember: Chapter end summary.
• Do It Yourself: Milestone exercises to practice specific concepts.
• Chapter Checkup: A pool of questions catering to all topics and skills covered in the chapter.
Uolo partners with K-12 schools to bring technology-based learning programs. We believe pedagogy and technology must come together to deliver scalable learning experiences that generate measurable outcomes. Uolo is trusted by over 10,000 schools across India, South East Asia, and the Middle East.
hello@uolo.com
�275