





Academic Authors: Jatinder Kaur, Ayushi Jain, Chandani Goyal, Kashika Parnami, Anuj Gupta, Simran Singh
Creative Directors: Bhavna Tripathi, Mangal Singh Rana, Satish
Book Production: Rakesh Kumar Singh, Sakshi Gupta
Project Lead: Jatinder Kaur
VP, Learning: Abhishek Bhatnagar
All products and brand names used in this book are trademarks, registered trademarks or trade names of their respective owners.
© Uolo EdTech Private Limited
First published 2023
Second published 2024
Third published 2025
This book is sold subject to the condition that it shall not by way of trade or otherwise, be lent, resold, hired out, or otherwise circulated without the publisher’s prior written consent in any form of binding or cover other than that in which it is published and without a similar condition including this condition being imposed on the subsequent purchaser and without limiting the rights under copyright reserved above, no part of this publication may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior written permission of both the copyright owner and the above-mentioned publisher of this book.
Book Title: Tekie Computer Science 8
ISBN: 978-81-978912-8-1
Published by Uolo EdTech Private Limited
Corporate Office Address:
85, Sector 44, Gurugram, Haryana 122003
CIN: U74999DL2017PTC322986
Illustrations and images: www.shutterstock.com, www.stock.adobe.com and www.freepik.com
All suggested use of the internet should be under adult supervision.
Standing at the forefront of the digital and AI revolution, the importance of coding and computational skills has reached unprecedented heights. In today’s professional landscape, whether it is in the fields of medicine, space exploration, education, science, or business, no sector remains untouched by this transformative wave. To thrive in the 21st century, basic computer literacy is no longer sufficient. Learners must evolve into ‘digital natives’ who can fluently read, write, and communicate in the languages that machines and AI comprehend.
Recognising this imperative, the National Education Policy (NEP) 2020 has strongly recommended the integration of coding skills, computational thinking, critical analysis, and problem-solving abilities into the curriculum. Moreover, forward-looking subjects like AI, Data Science, Computer Applications, and IT have been introduced as elective subjects from grade 9 onwards. It wouldn’t be surprising if further transformative measures are taken even at the elementary education level.
Uolo has introduced an innovative 360-degree program for a coding-focused computer science curriculum, known as Tekie, spanning grades 1 to 8. Tekie is a significant stride towards STEM education that aims at making learners future-ready—enabling them with skills needed in the ever-changing, technology-driven, and dynamic 21st-century world.
Tekie adopts a captivating and engaging approach to learning, in line with the recommendations of the National Curriculum Framework (NCF) 2023 and NEP 2020. The curriculum is ingeniously woven into the thrilling adventures of Mel and Conji, fictional characters from the enchanting land of Avora. The Mel and Conji series epitomises a modern method of acquiring computer science knowledge and honing computational thinking skills. The program includes chapters that provide a deeper immersion in computer science that both learners and teachers may find interesting.
Tekie is a technology-empowered curriculum that encompasses the following components:
• Main Content Books: These introduce learners to the theory of computer science and computer tools. Topics in AI are also covered, along with experiential and project-based learning resources.
• Coding Books: Specifically designed to nurture coding skills, this booklet aligns with the experiential and contextual learning approach of the coding curriculum, fostering critical thinking and problemsolving abilities.
• Animated Learning Videos: The program is powered by high-quality animation-based learning videos that deliver learning in an engaging manner.
• Teacher Manual: This valuable resource supports classroom instruction, ensuring that educators effectively deliver the curriculum.
Welcome to the captivating realm of Tekie! We hope you relish this educational journey as it equips you with the tools you need to thrive in the exciting and ever-changing world of the 21st century.
Tekie is an interactive, engaging, and experiential computer science program. It enables learners to attain mastery in computer science theory, new-age computer tools and coding. These are delivered through a storytelling-based coursebook and an experiential learningoriented coding book.
The learning experience is augmented by a digital platform that gives learners access to learning videos and experiential activities and projects that are rooted in the curriculum.
Engaging Textbooks
Comic Stories
Teacher Manual
Test Papers
Additional Projects
Test-paper Generator

Student and Teacher Platform
Learning Videos
Interactive Classroom and Homework Assignments
Byte-size Lesson Modules

The National Education Policy (NEP) 2020, introduced by the Government of India, represents a transformative shift in the country’s education system. It aims to create a more holistic, dynamic and multidisciplinary approach to education. The NEP highlights the need for early development of computational thinking, coding, and digital literacy as vital skills for students’ holistic growth. UOLO is fully committed to actualising the vision of NEP 2020 by meticulously adhering to its outlined recommendations.











1. Focus on conceptual understanding
2. 21st century skills, values, and dispositions
3. Computational and critical thinking
4. Application in real life
5. Holistic and integrated learning
6. Experiential learning
7. Enjoyable and engaging
8. Artificial intelligence and coding concepts
9. Digital literacy and emerging technologies
10. Factoids on India
Competency-based Education
NEP Pages 12, 17 and 22
Teaching and Learning Pedagogy
NEP Pages 3, 5, 11, 12 and 56
National Pride
NEP Pages 15, 16 and 43
11. Assessment of core concepts and application skills Assessments
NEP Pages 12, 18 and 22
Project-based Learning
Engaging hands-on projects encouraging practical application of computer science and coding
Story-based Approach
Enchanting tales that bring learning themes to life, making education a captivating adventure 5 7
Equipping the students with future-ready skills through exposure to the latest tools and technologies
2 3 4 6 8 9
Engaging activities to deepen students’ understanding and engagement with AI concepts
Test papers designed to evaluate understanding of core concepts and application of skills 3 4 11
Projects on the digital platform to deepen understanding and develop essential practical skills

Invites learners to discuss in small groups and present different perspectives
Story-style learning videos that deliver concepts to students.
Intellectually stimulating questions designed to encourage deep, analytical, critical, and evaluative thought process
Interactive quizzes that reinforce learning and assess students’ understanding
3 7 9 11
Think It Through
Probing question related to the concept that arouses curiosity
Tool to create customised assessments that align with the curriculum and help evaluate students’ progress effectively.
Enjoyable and engaging
Artificial intelligence and coding concepts 9 Digital literacy and emerging technologies
Factoids on India 11 Assessment of core concepts and application skills
The National Education Policy (NEP) 2020 outlines essential skills, values, dispositions, and learning approaches necessary for students to thrive in the 21st century. This textbook identifies and incorporates these elements throughout its content, activities, and exercises. Referred to as “NEP Tags”, they are defined as follows:



INTEGRATED



Art Integration
Bringing creativity and fun into learning by combining music, drama, and art with other subjects CRITICAL

Sports Integration
Using games and sports in daily life to enrich computer-related activities
Holistic & Integrated Learning
Cross-curricular linkages to make the learning experience more holistic, joyful and meaningful
Critical Thinking
Coding opportunities to apply higher-order skills like algorithmic and computational thinking, and problem-solving

SDG
Hands-on Activity
Step-by-step activities to enable learners put theoretical knowledge into practice
Sustainable Development Goals
Applied computer science activities related to real-world issues and sustainable development

SEL Social Emotional Learning
Developing the skills to understand and manage emotions, build positive relationships with others and make responsible choices

The curriculum is thoughtfully mapped to introduce tools and technologies at each grade level, ensuring a smooth and progressive learning experience for students. Beginning with basic concepts in junior grades, the curriculum gradually incorporates more advanced tools and concepts in higher grades. This structured approach enables students to build on their knowledge each year, equipping them with essential skills in computer science and technology as they progress from grade 1 through grade 8. By the time they reach the higher grades, students are well-equipped to tackle complex projects, think critically, and apply their skills in real-world scenarios. The curriculum not only fosters technical proficiency but also encourages creativity, problem-solving, and a deeper understanding of the digital world.









































1

We
Theme Page: Lists the chapters covered under a unit



2
We see many things around us. Some things are present in
Comic Story: To introduce key concepts in a fun way
Did You Know: Interesting facts related to the topic
Discuss: A multi-faceted probing question related to the concept that arouses curiosity

3
4




Explore More: Short videos to find out more about the topic
Do It Yourself: Short exercises between the chapter to pause and assess comprehension













































































































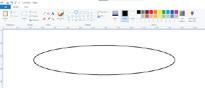
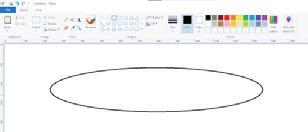
Drawing in Paint
Let us now learn to draw shapes in Paint.
Drawing an Oval
Follow these steps to draw an oval:
1. Open Paint and click on the Shapes group.
2. Click on the Oval shape.

3. After selecting the shape, go to the drawing area.
4. Hold the left mouse button, drag the mouse, and then release the mouse button. You will see that an oval has been drawn. Oval
Points to Remember

Project-based Learning: A project-based learning approach employed to foster an engaging and interactive learning experience Points to Remember: Summary of the chapter
and smartphones.
Chapter Checkup: Chapter-end practice exercises aligned to different levels of Bloom’s Taxonomy

Apply your learning: Intellectually stimulating questions designed for higher-order thinking and analysis
Have you ever given a command to the speaker at your home to play a song, and it plays it?
Do you know what these speakers are known as?


These special speakers, which follow your voice commands, are smart speakers Smart speakers can do this because of AI.
What is AI?





Artificial Intelligence: Chapters on Artificial Intelligence to explore the fundamentals of AI, including its principles and applications in various fields
AI stands for Artificial Intelligence It gives machines the ability to learn and do things on their own, just like humans do
AI Around Us
• Talking Toys: Some toys use AI to understand your voice and respond with sounds, songs, or even short sentences.

A. Fill in the blanks.
• Robot Helpers: These machines help us with daily tasks at home. They can clean floors, cook food, etc. They do work in the same way as a human does.
Fun with AI: Engaging AI activities designed to help students explore and apply AI concepts in practical ways




AI devices are all around us. There are many types of machines that use Artificial Intelligence (AI) to perform tasks or respond to us. Some examples of such AI devices are:

• Smart Speakers: These speakers respond to your voice commands. They use AI to understand your voice commands, like when you ask them to play music or tell you a story.
• Selfie Magic: Some phones use AI to edit your selfies. The AI can adjust lighting, smooth out backgrounds, or add fun filters.



Test Paper 1 (Based on Chapters 1 to 3)
Test Papers: Designed to evaluate understanding of core concepts and application of skills
1 Things that are present in nature are called
2 Some machines need to work.
3 Computers are used in to keep information of patients.
4 At restaurants, computers are used to order and pay for
B. Tick () the correct answer.
1 Which of the following is a human-made thing?
a Mountains b Trees
c Cars d Animals
2 Which machine helps us keep our food fresh?
a Refrigerator b Washing






•
• Network Terminologies and Devices
• Types of Computer Networks
• Network Architecture and Protocols
• Accessing a File From a Shared Drive
•
•
• Digital Footprints
•
• Cryptocurrency:
•
• Accessing
• Classification of Mobile
• Developing an App
•
• Augmented
• Metaverse
•
• Biotechnology
• Brain-computer Interfaces
• Generative AI
• Understanding Databases
• Database Management System
• Structured Query Language
• More SQL Queries
• Creating a Video in Canva
• Components of Video Editor in Canva
• Adding Videos in Canva
• Basic Video Editing Tools
• Applying Effects on Videos
• Downloading and Sharing a Video
• What is Artificial Intelligence?
• Data and AI
• Applications of Data Science
• Fun with AI: Rock, Paper, Scissors
•
• Fun with AI: Using AI Story Generator






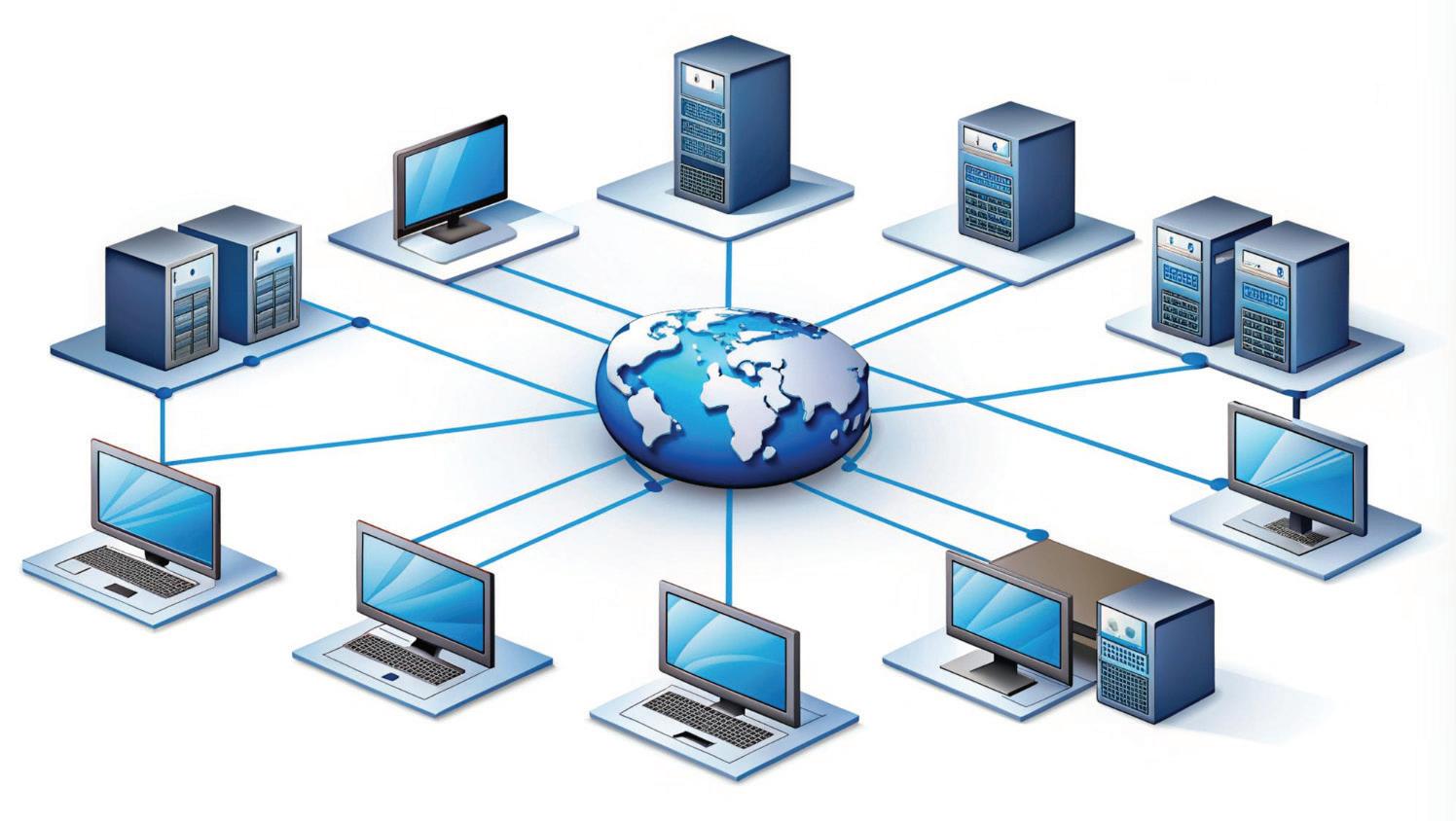
Suppose you are going on a family road trip and observe how roads connect different places, such as villages, cities, and towns.
In a similar way, our world is connected through computer networks. Just as roads link various locations, computer networks link devices, allowing them to share information. These digital roads help messages and data travel between computers, regardless of their location.
A computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other.
When several people are working on the same project under one roof or at remote places, they need to communicate with each other, and this is possible only with the help of a network. If different people are living in different places, they share messages with each other. If they are all located in one building, they can easily share hardware resources with each other, such as one printer, which can be shared among
many team members. Therefore, there is a great need for computer networks in our lives, even for sending a small message to another person to communicate with people across the globe, for storing huge amounts of information, making video calls, sending audio messages, sharing software among many people, etc.
Computer networks are used for different purposes in our daily lives.
File Sharing: With the use of networks, you can share the data and documents with each other. For example, you can share any file with your friend who is located remotely in a different country.
Resource Sharing: Suppose all the students in your class are in the Computer Lab, each using an individual computer. The teacher has asked all the students to print an article on the topic “Importance of Communication in Our Lives”. Will you want a separate printer for every computer? The answer is No.
You can observe that only one printer in the lab will be shared with all the students, and this is possible only because of the computer network. This is called resource sharing.

Communication: Suppose your teacher has assigned a project to you with two other team members. One of your team members has gone to some other city for a week. You can then connect to your team members using a computer network and complete the project on time. This is only possible with the help of computer networks.
Database Access: Computer networks help to access the same database from multiple computers. This further enhances the storage capacity of data and access to the stored data.

Security: Suppose you have stored your class assignments on the network. Your data is secured on the network because in the network, a key (password) is provided to the user to access that data.
Backup: What will happen if you accidentally delete your project files from your individual computer on the network? Do not worry about that. In computer networks, the data is stored on a central computer, known as a server. This server has a backup utility enabled on it. So, taking the backup of data is also a benefit of computer networks. In case of data loss, you will have the backup copy of your data.
Computer networks are beneficial to us in many ways. Some of the advantages of computer networks are discussed:
Cost Reduction: Because the hardware resources (printers and scanners) are shared among all the computers on the network, the cost of additional equipment is saved.
Less Data Redundancy: Data redundancy occurs when the same piece of data exists in multiple places. All the data on the computer network is stored on the server. Therefore, there is less redundancy in the network.
Less Data Inconsistency: Data inconsistency means when the same data exists in different formats at different places. Since data redundancy is reduced, it also reduces data inconsistency.
Data Centralisation: In a computer network, the server provides services to all the other computers. All the data in a computer network is stored on a server at a centralised location. This centralised storage of data provides easy accessibility to all users.
Data Recovery: The server’s capability of taking regular data backup helps with easy data recovery in case of data loss or network failure.
Apart from many advantages, there are also some disadvantages of computer networks. Let us learn about them.
Security Concerns: Network security is a major concern as the data is being shared in a wired and wireless medium which can be stolen by some tricky people, leading to data loss or change of data.
High Maintenance Cost: A computer network needs timely maintenance by a special team of experts. The maintenance cost of a computer network is higher than that of an individual computer.























































Complex Architecture: Computer networks have a complex architecture, for which a specific type of setup is required. Purchasing the necessary equipment (such as cables and other devices) for network architecture can be expensive.
Compatibility Issues (Hardware and Software): To be a part of the network, you should have the same version of hardware and software as all the other computers that are supposed to be part of the network.


Data Loss (In Case of Network Failure): If the server computer that stores all the data of individual computers fails, all the data will be lost. This is a major disadvantage of a computer network.
Need for Skilled Personnel: Managing a large network is complicated, requires training, and a network manager usually needs to be employed. To maintain a large network, a special team of skilled technical persons is required. Hence, it bears an extra maintenance cost.
Answer the following questions.
1 What do you mean by resource sharing?




























2 The computer teacher has assigned a project to Sneha and Priyanka. Due to some emergency, Priyanka has to go to New Zealand. How will Priyanka and Sneha complete their project together on time?
3 Suppose there is only one scanner in your computer lab at school. All the subject teachers want to scan their documents while sitting at their computers in the computer lab. Is this one scanner sufficient, or is there a need for a separate scanner for every computer?

Some important network terms are discussed as follows:
Node
A device in a computer network which is used to send or receive data. A computer, mobile, tablet, laptop, etc., are called nodes.
Link It is a connection between two computers or devices, such as cable, Wi-Fi, fibre optic, etc.
Packet
A unit of data or information that is transferred over the internet. For example, you send an email or message to a friend.
Protocol Protocols refer to a set of rules which are to be followed for sending data on a network.
Topology The physical arrangement of computers or devices to link with each other. For example, star topology, bus topology, etc.
Bandwidth The amount of data or information that can be transmitted over the internet or network. For example, 1 Gbps or 1 Mbps (bps-bits per second, G stands for Giga and M for Mega).
Latency The time taken for a message to travel from one end of the network to the other end.

Data units start from one bit and can go up to yottabytes. Scan this QR code to know more about data units.

Computer network devices are hardware components that are required for computers to communicate with one another over the network. Some of these are discussed as follows:
Network interface card (NIC): It is a hardware component installed on a computer to connect a computer to a network. It is a circuit board or a chip without which a computer cannot connect with another computer on a network.

Ethernet networking cable: It is a hardware cable which is required to connect one computer with another computer to share information and devices like printers or scanners. This cable connects wired devices in a Local Area Network.











Modem: Modem stands for Modulator-Demodulator. It is a hardware device which sends and receives data over a telephone line, cable, or fibre optic. A modem converts digital signals from a computer into analog signals which can travel over telephone lines. It also re-converts analog signals back into digital signals.
Hub: It is a networking device that transmits the received information to all the devices on the network. A hub has many ports in it. A computer that intends to be connected to the network is plugged into one of these ports.

Switch: A switch is a device that connects different computers on a network. It transfers data from one computer to another. A switch receives data from one computer, processes that data, and forwards that data to the destination device.
Router: It is a device which routes the data or information over a network. Routers may also be used to connect two or more logical groups of computer devices known as subnets or subnetworks.

A router needs the IP address of a computer to which the data is to be sent. The IP address of every computer is unique (does not match with any other computer).
1 Fill in the blanks.
a is a device that converts one type of signal to another.

b is used to connect multiple computers and devices directly to the network using cables.
2 Name different computer network devices.

There are different types of networks, which are categorised according to the geographical area they cover. Let us discuss the types one by one.
Personal Area Network (PAN): A PAN, which is the most fundamental kind of network, consists of a wireless modem, one or two PCs, smartphones, tablets, printers, etc., working within a range of 10 metres. These networks are usually controlled by a single person or business from a single device and they are generally found in small scale workplaces or houses. They can be categorised into wired and wireless, based on the type of connectivity among the networking devices.
Local Area Network (LAN): It is a computer network that only extends up to a few metres across a relatively limited region, such as a school or a college building. LANs are commonly used to link desktop computers and workstations in corporate settings, to share resources. LAN ranges between 100 and 1000 metres.
Metropolitan Area Network (MAN): It is a computer network that connects devices within a metropolitan city or a small town. Two or more connecting LANs form a MAN. A MAN ranges up to an area of 100 km. MAN is costlier than LAN. A cable TV network is an example of a MAN.
Wide Area Network (WAN): Wide Area Network connects computers from various countries and continents. WAN connects different LANs and MANs from across the globe. The internet is an example of WAN.













Wireless Network: A wireless network can be created in a small area such as a room or a house. The technology used to create a wireless network is known as Wi-Fi. Wi-Fi stands for Wireless Fidelity. It is a type of Local Area Network (LAN) that uses wireless communication technology to connect various devices like computers, smartphones, tablets, and other gadgets to the internet using a Wi-Fi router. These devices can be connected without the need for physical cables.

Topology is a physical and logical layout of different devices (nodes) and connections in a network. The configuration of how computer systems or network devices are connected to one another is known as a topology. Different types of network topologies are discussed as follows:
Bus Topology: In a bus topology, all the nodes are connected to a single common cable. A node puts a message on the cable, that is sent to all other nodes in a network. The disadvantage of it is that the messages clash when multiple nodes try to send data at the same time. Terminator removes data from the line.
Star Topology: In star topology, the nodes are connected to a centralised hub, switch, or a computer forming a star. The central computer is called the server, while other computers are called the clients. The disadvantage of the star topology is that if the central computer fails, the whole network will be disabled.
Ring Topology: In ring topology, the nodes are connected to each other forming a ring. A node forwards the message received from the previous node to the following node. Data flows unidirectionally, in a clockwise direction. The disadvantage of it is that if any one node fails, the entire network will fail.


















Tree Topology: In tree topology, nodes are connected in a parentchild hierarchal manner. Tree topology is a combination of star and bus topology. The disadvantage of this topology is that the entire communication depends upon the bus and if the bus fails, the entire network will fail. Which

Mesh Topology: In the mesh topology, every node is directly connected to every other node forming a mesh. The disadvantage of mesh topology is that the network is costly, due to the large number of cables used and it is difficult to find a faulty node. An example of mesh topology is the internet.


The following architectures are used to design networks:
Network Architecture
Peer-to-Peer Architecture
Peer-to-Peer (P2P) Architecture: It is a type of networking architecture in which all the connected computers have equal abilities. All computers in this network are of the same level. Bitcoin () is an example of P2P architecture.

Client-Server Architecture
Client-Server Architecture: It is a type of network in which a central computer manages most of the resources. This computer, which has all the resources and provides services to others, is called a server and the computers which use services provided by the server are known as clients. That is why the name of this architecture is clientserver architecture.
The following table summarises the differences between peer-to-peer and client-server architecture:
Peer-to-Peer
In this architecture, every node serves as a client and server.
Peer-to-Peer network is less secure because as the number of nodes increases in this network, the chances of vulnerability also increase.
Every node participates in equal management of the network. Therefore, client growth may affect the performance.
The server is not bottlenecked, because the service requests are distributed among all clients.
In this architecture, one or more nodes serve as a server and all other nodes behave as clients.
Client-server network is more secure because the server can validate the client’s access.
Most of the work is managed by the server. Therefore, client growth does not affect the performance.
The server may become overloaded with an increase in the number of service requests by the clients.
A network protocol is a set of rules which governs the communication between computers over a network, i.e., it describes how the information will be transmitted over the network.
Let us learn about some of the main network protocols.
The TCP/IP stands for Transmission Control Protocol/Internet Protocol. TCP/IP is a combination of two separate protocols: Transmission Control Protocol (TCP) and Internet Protocol (IP).
TCP provides end-to-end communication between computers and specifies how the data will be divided into small packets. Then, those packets will be transferred to the destination, where all packets will be assembled again to recreate the original message.
IP assigns a sequence number to every packet so that packets can be assembled in the correct order at the destination.

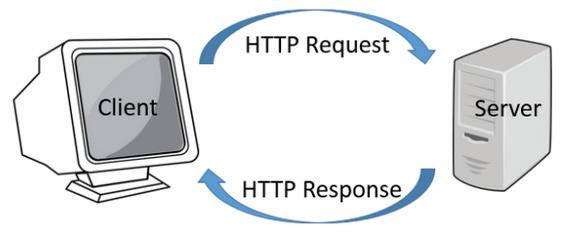

Hypertext Transfer Protocol (HTTP): HTTP is used to transfer data such as texts, images, videos, and other multimedia files over WWW (World Wide Web). When you want to open any website such as www.flipkart.com, HTTP protocol sends a request to the web server to open that website. The message sent by the client (Web Browser) is called the request and the message responded by the server is called the response.

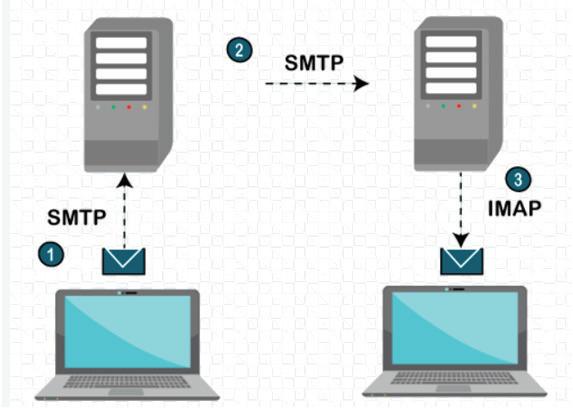
Simple Mail Transfer Protocol (SMTP): This is the simplest protocol used to send emails between computers. SMTP is used to send messages from mail client to mail server. The email at the receiver’s end is received using IMAP.
Internet Message Access Protocol (IMAP): It is a popular internet protocol for retrieving emails. Its usage varies according to the environment. While using an email application, it is essential to specify the sending protocol (SMTP) and the email receiving protocol (IMAP).
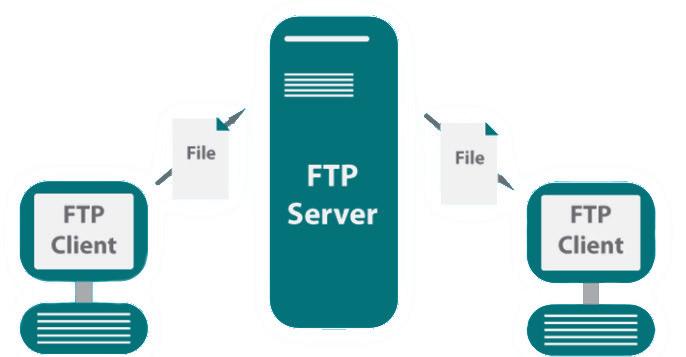
File Transfer Protocol (FTP): FTP is the simplest method to transfer files from one computer to another over a network, using FTP client and FTP server software. This protocol is used for uploading and downloading files from a computer to the internet. It makes use of TCP/IP connections for transmitting files.
TCP/IP was developed in the year 1970.
Nowadays, you can share your data with other users even if they live in a remote area or faraway place. This sharing or transferring of data is possible only through a shared drive or Google Drive.
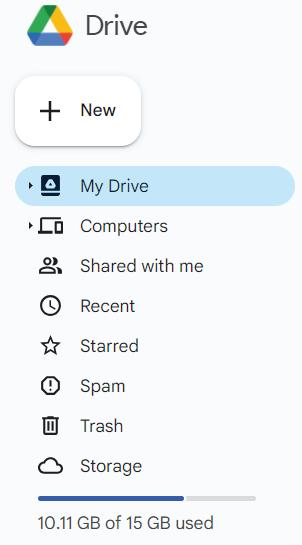
It allows you to share your data on Google Cloud Servers. Google Drive offers 15 GB of free storage capacity.
Follow the steps mentioned below to store a file on Google Drive:
1. Sign in with your Google Account. If you do not have a user ID and password, first register yourself on Google.

2. Click on the Google apps icon button located on the top right-hand corner of the Gmail account.

3. Click on the Google Drive icon. The Google Drive window will open.
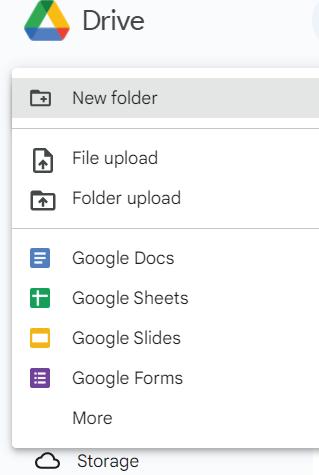
4. Click on the New button. For uploading a single file, click on the File upload option. For uploading a folder, click on the Folder upload option.

Google Drive was launched on 24 April, 2012.

5. The Open dialog box will appear. Select the file you want to upload.
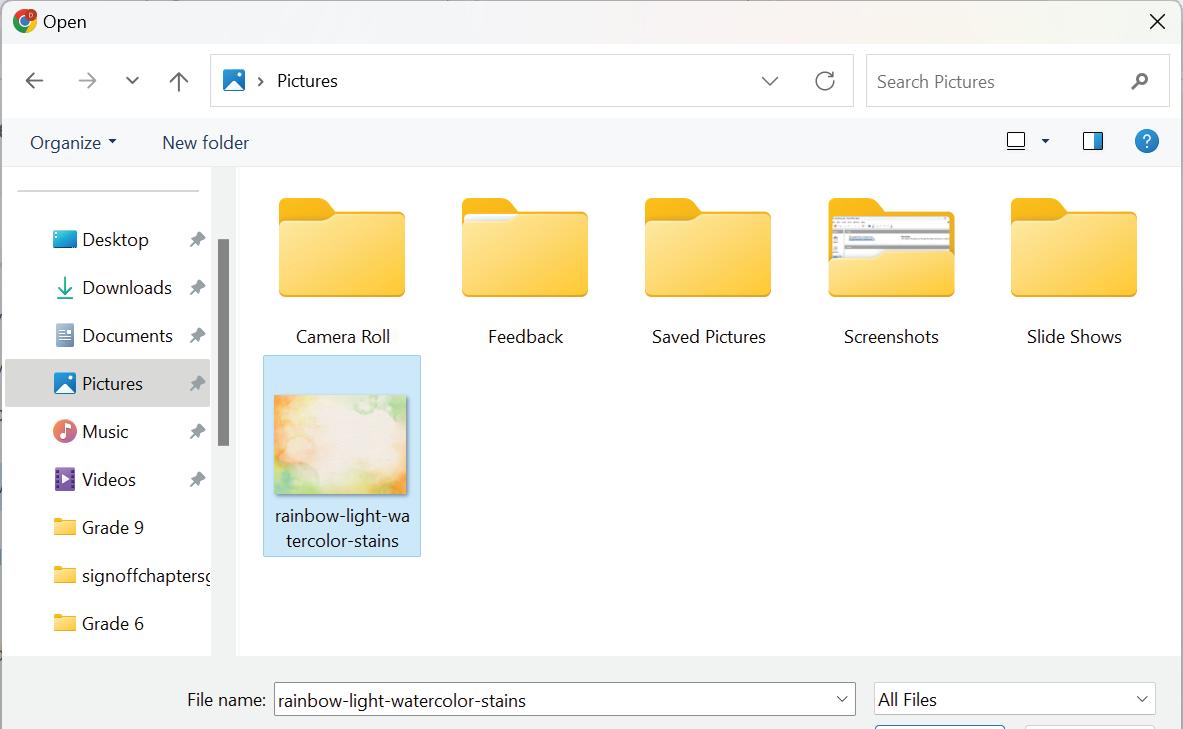
6. Click on the Open button. The selected file will be uploaded on Google Drive.
Follow the steps to share a file on Google Drive:
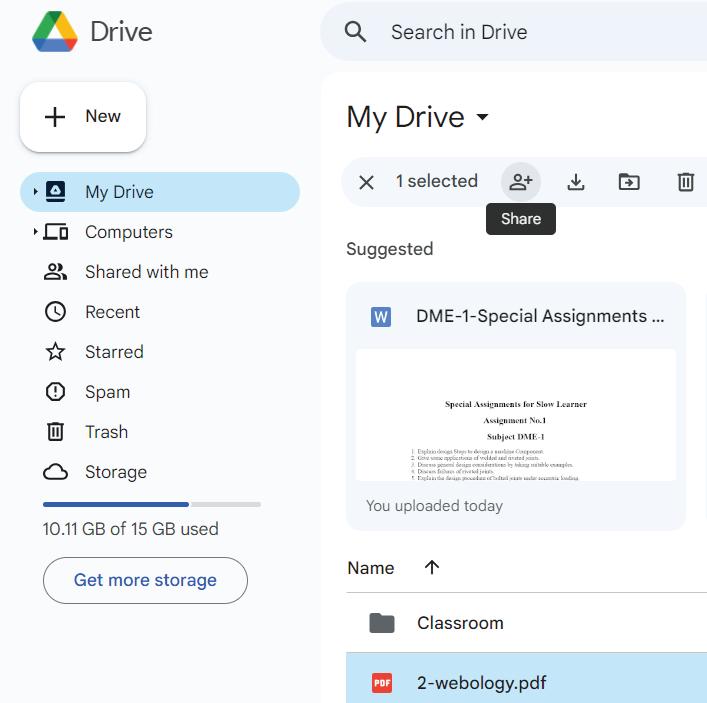
1. Select My Drive, and select the file you want to share with another user.


2. After selecting a file, click on the Share icon. Type the email addresses of recipients in the Add people and groups box. If you want, you can also add a message that will be emailed to the recipients.

3. You can select whether the other user can edit, comment, or simply view the shared file or folder.
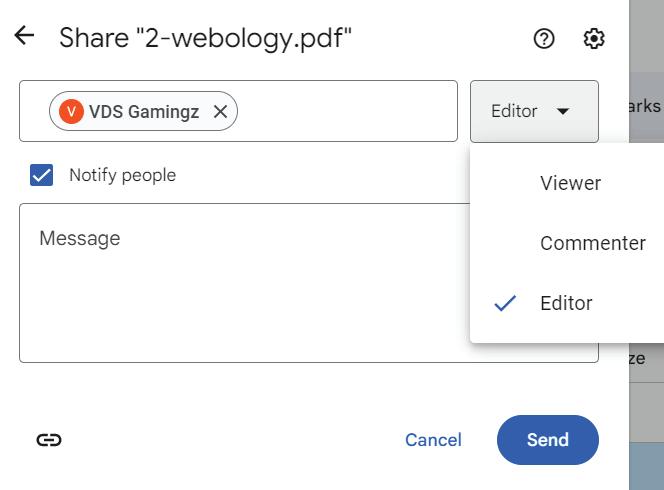
Viewer: Allows the recipient to only view the file.
Commenter: Allows the recipients to add their comments only on the shared file.
Editor: Allows the recipients to edit the shared file.
By clicking on the Send button, the file will be shared. You can also click on Copy Link option to get the link of the shared file and then you can share it with the recipient through email or message.
Select your profile icon and click on the Sign Out button to get signed out of Google Drive.
Because of security breaches on the network, it is necessary to use some network security measures. Some common network security measures are discussed below:
Firewall: A firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organisation’s previously established security policies. It protects unauthorised access to a computer by blocking unsolicited communication. Firewalls come in both hardware and software forms. Some examples of the latest firewalls are Sophos Firewall, Check Point Firewall, pfSense Plus, WatchGuard, etc.
Antivirus: Computers are vulnerable to attacks or viruses when they are connected to a network. Therefore, it is necessary to install antivirus software on the computer system. A number of antivirus software programs are available in the market. For example, AVG, Quick Heal, Norton, McAfee, Avast, Kingsoft, etc. These antivirus software programs scan all the drives of a computer to detect any malicious virus in any file or folder. They get rid of that virus, either by deleting it or making it inactive.
When you access the internet to perform some online activities such as shopping or transferring of money, etc., your computer is at high risk. Therefore, some online protective measures must be followed, some of which are as follows:
Clear browser cookies.
Remove unknown or unwanted applications.
Regularly update all applications and software.
Perform secure transactions on the portals with a padlock sign.

Keep passwords safe and strong.
1 Match the protocols with their functions.
HTTP (Hypertext Transfer Protocol) Used to send emails between computers.
SMTP (Simple Mail Transfer Protocol) Transfers data such as text, images, and videos over the World Wide Web.
IMAP (Internet Message Access Protocol) Transfers files from one computer to another over a network.
FTP (File Transfer Protocol) Retrieves emails and is essential for email applications.
2 Select the correct network type for each description.
a connects devices like PCs and smartphones within a 10-meter range in a small area.
b links devices within a school or office, covering between 100 and 1000 meters.

c connects networks within a city or town, spanning up to 100 kilometers.
d connects devices across countries and continents, like the internet.
A computer network is a way to connect computers using communication devices so that they can exchange data and resources with each other.
Computer networks have many uses such as file sharing, communication, database access, data backup, etc.
There are many advantages of computer networks like security, reducing data inconsistency, less data redundancy, and communication.
There are many disadvantages of computer networks like network failure, stealing of data, maintenance cost and complex architecture.
Computer networks are of many types: PAN, LAN, MAN, WAN and wireless.
There are different network devices such as hubs, switches, routers, NICs, and Ethernet networking cables.
Different topologies of computer networks are: bus, star, ring, tree, and mesh topology.
Different internet protocols are: TCP/IP, HTTP, FTP, SMTP, and IMAP.
A firewall is a network security device that monitors and filters incoming and outgoing network traffic.
To keep your system safe while doing online activities, always browse the sites with a padlock sign, clear browser cookies and history, keep strong passwords, etc.
Checkup A. Fill in the blanks.
is a group of two or more computers connected to exchange information/data and to share resources. In a topology, all the nodes are connected to a single common cable.
connects devices within a city or a small town.
Data means when the same data exists in different formats at different places.
software scans all the drives of a computer to detect any malicious virus in the computer.
B. Tick () the correct option.
Which of the following is not an advantage of a computer network? a Cost reduction
data redundancy c
maintenance cost
data inconsistency
A computer network is a group of two or more computers connected together to exchange and to share .
a Data, Resources
c Software, Connections
b Devices, Secrets
d Hardware, Communication lines
Data occurs when the same piece of data exists at multiple places.
a Inconsistency
c Consistency
Which of the following is not a network topology?
a LAN
b Differentiation
d Redundancy
b Star
c Mesh d Bus
A routes the data on a network. a Hub b Switch c Router
C. Write T for True and F for False.
MAN is costlier than LAN.
PAN connects people across the globe.
Hub uses only a single port.
No data recovery is possible in the case of communication over computer networks.
There is no single point of failure in the case of mesh topology.
D. Answer the following questions.
Define WAN.
Write the advantages of computer networks.
Explain the terms hub and router.

E. Apply your learning.
Ms Anju wants to open her new office branch in Pune and wants to connect with previously opened branches in Haryana and Mumbai. Which network type will she prefer?
Ram wants to create a computer network in a circular way. Which type of topology will you suggest to him?
In a household, wireless networks (Wi-Fi) are commonly used. Describe the advantages of having a wireless network at home as compared to a wired network.
Arun is the technology officer in an organisation. What are three potential disadvantages or challenges that he might face when managing a computer network?
Imagine you are a businessperson. Why do you think it is a good idea for you to connect all the computers in your company to a network?








Imagine you have the habit of diary writing. You write all your secrets in the diary and keep it hidden in your room. What if someone steals it or reads it? This is a violation of your privacy.
Similarly, while using the internet, you have to be very careful and respect others’ privacy. Let us learn more about moral principles in this chapter.
The uses of the internet and other technical breakthroughs have made the world more interconnected in the current digital era. Even though this connectivity has many advantages, it has also raised some ethical questions about how people behave and interact online.
The study of appropriate behaviour and moral principles in the digital sphere is known as cyber ethics, also referred to as internet ethics or online ethics.








Privacy Safeguards: Cyber ethics places a strong emphasis on the value of protecting people’s privacy online. Every individual’s private data and personal details should remain safe. This therefore includes respecting user consent, handling sensitive data securely, and preventing unauthorised access or data breaches.

































Cyber ethics outline moral principles for good human behaviour and interaction in the digital world. These ethical principles are essential to ensure responsible and ethical conduct in the use of technology and the online environment. Cyber ethics include:























Online Behaviour: Ethical behaviour in cyberspace includes promoting respectful and responsible online communication. This involves refraining from cyberbullying, hate speech, harassment, and other harmful types of behaviour that can negatively impact individuals or communities.


















































































































Digital Security: The digital devices as well as the data need to be protected against any theft or damage. This means that intellectual property should remain secured. Intellectual property refers to the ownership and protection of creative and unique ideas, inventions, and digital works over the internet. As you would not take someone’s artwork or story without permission, it is very important to respect and not use people’s digital work online, such as videos, music, and software, without permission. Respecting the rights to one’s intellectual property is a fundamental value.
Bridging the Digital Divide: Not all sections of society have the same access to technology. The poor, for example, have no access at all. Ethical use of technology promotes equitable access to technology for all members of society.
Accountability: People and organisations need to be accountable for their online behaviour in the digital age. This includes taking responsibility for errors, making changes for harm done, and upholding moral principles in all online activities.
We now know that bad practices exist in the cyber world. We also understand that cyber ethics tell us how the world should be. There are some issues in achieving cyber ethics:
1. Restriction: Following cyber ethics online is always good. However, if restrictions are too srict, then they can limit the freedom of expression and innovation.
2. Interpretation: One cannot determine that following what type of behaviour online is acceptable or not. People may agree on some points and disagree on others.
3. Enforcement: Due to the international nature of the internet and the fact that several nations have their laws and regulations, it can be difficult to implement cyber ethics on a global scale.
4. Anonymity: Cyber ethics may conflict with people’s desire for online anonymity. It may be required for the people to expose their identity to be held accountable.
5. Evolving technology: As technology evolves rapidly, cyber ethics must adapt, which can be challenging to keep up with.


Many unethical practices are prevalent in society these days. Let us learn about them.
Using the internet to harass, scare, or hurt people is referred to as cyberbullying Cyberbullying can happen if you send or receive messages to humiliate or threaten someone, spread untrue rumours, post embarrassing images, or create fake profiles. The victims of cyberbullying may suffer severe emotional and psychological effects.







Cyberstalking is the practice of constantly following someone’s online activity, mostly with the intention of frightening or upsetting them. Keeping an eye on someone’s social media pages, sending unwelcome messages, and issuing threats are some examples of cyberstalking. In many places, cyberstalking is prohibited and can lead to serious legal action.


When someone copies another person’s ideas, work, or content without giving proper credit or getting permission, it is called plagiarism. This immoral behaviour can be seen in a variety of circumstances, including online content creation and academic content. It damages the worth of original work and may have negative effects on one’s academic or professional career.
Phishing is a dishonest internet practice in which attackers pretend to be reliable organisations and trick people into disclosing personal information, such as passwords or financial information. The attackers can then use your personal information to do malicious things, like steal your money or identity. The most common form of phishing is email phishing.
Hacking involves unauthorised access to computer systems, networks, or devices. Hackers generally have bad intentions to engage in malicious activities such as data theft, spreading viruses, or disturbing digital infrastructure. Another form of hacking called ethical hacking, or “white hat” hacking, is performed by professionals to fix the problems in a computer system or network to keep them safe from hackers.
Spamming refers to sending lots of unwanted and annoying messages to many people, often to make money or promote something. Spamming is considered unethical because it interferes with digital communication.
Identity theft happens when someone pretends to be someone else. He/she does this often to steal money, data, or other important information, like credit card details, bank details, etc. This can really hurt people, causing them emotional and financial problems.
Match the following.
Spamming
Phishing
Identity theft
Hacking
Pretending to be a reliable source in order to trick others into disclosing their passwords or personal information.
Sending emails or messages that are meaningless and unnecessary.
When an unauthorised person tries to access a computer system, a network, or data.
Stealing someone’s personal information to commit fraud.

Online safety measures are safeguards and behaviour designed to keep your security, privacy, and personal information safe when using the internet. Here are some important tips for online safety:
Use Secure Passwords: Create strong, challenging passwords for each of your accounts and change them frequently. Use a combination of symbols, numbers, and letters.

Phishing Alert: Be wary of emails, messages, or websites that request private data, such as passwords or credit card numbers. Before sharing any personal information, make sure the sender or website is genuine.
Regularly Update Software: Update your operating system, antivirus program, and other programs regularly. Security fixes are frequently included in software updates.

Use Secure Wi-Fi: Avoid accessing sensitive accounts or disclosing personal information when using public Wi-Fi networks.
Protect Personal Information: Exercise caution while disclosing personal information on websites and social media. Do not disclose too much personal information to the public.
Privacy Settings: To limit who can view your information, review and modify the privacy settings on social media sites and online accounts.

Educate Yourself: Keep yourself updated about frequent internet hazards and frauds. The best defence against cyberattacks is awareness.
Secure Your Devices: Use screen locks, PINs, or biometric authentication to secure your PCs, cell phones, and tablets to avoid illegal access.
Data Backup: To prevent data loss due to hacker attacks or hardware failures, regularly backup vital data to an external source or a cloud service.
What measures should you follow while shopping online?

An online activity trail is what a digital footprint looks like. It includes everything you do online, including sending emails, publishing on social media, and even just surfing websites. Your digital footprint reveals where you have been online, just like your footprints in the sand do. Because your digital footprint can impact your reputation and privacy, it is crucial to be cautious online. Think before you click, always!
Some examples of a digital footprint are as follows:
1. Social media posts
2. Online shopping
3. Emails
4. Search history
5. Online comments and review

Digital citizenship is the term used to describe the ethical and responsible use of technology. By engaging in good digital citizenship, we help create a more secure and civilised online community for everyone. Here are a few examples:
1. Respecting others: A good digital citizen should avoid cyberbullying when making comments on social media or participating in online forums.
2. Privacy protection: Digital citizens should keep their information private, including passwords and communications.
3. Using reliable sources: Always verify the reliability of information before sharing it to stop the spread of false information.




















































4. Responsible posting: Avoid posting any kind of offensive or dangerous material on social media.
5. Online etiquette: Always use appropriate language and avoid the use of uppercase letters while communicating online.
6. Copyright awareness: Be aware of copyright and refrain from using other people’s work frequently. Do not use anybody else’s work without their consent or due attribution.
7. Cybersecurity: Follow practices such as using secure passwords and keeping software up-to-date to attain a secure working environment.

In India, when someone writes a book, creates music, or makes art, their work is protected by copyright. This protection lasts for their whole life, and then an additional 60 years. If there are many authors, it lasts for 60 years after the last author passes away.
Tick () the activity that will contribute to the digital footprint:
Shopping online for a school bag
Posting a comment on a friend's picture on social media
The study of appropriate behaviour and moral principles in the digital sphere is known as cyber ethics, also referred to as internet ethics or online ethics.
While using the internet, you have to be very careful and respect others’ privacy.
Using the internet to harass, scare, or hurt people is referred to as cyberbullying.
Cyberstalking is the practice of constantly following someone’s online activity, mostly with the intention of frightening or upsetting them.
When someone copies another person’s ideas, work, or content without giving proper credit or getting permission, it is called plagiarism.
Phishing is a dishonest internet practice in which attackers pretend to be reliable organisations and trick people into disclosing personal information, such as passwords or financial information.
Hacking involves unauthorised access to computer systems, networks, or devices.
Spamming refers to sending lots of unwanted and annoying messages to many people, often to make money or promote something.
Identity theft happens when someone pretends to be someone else.
A digital footprint includes everything you do online, including sending emails, publishing on social media, and even just surfing websites.
Digital citizenship is the term used to describe the ethical and responsible use of technology.
Observe the online safety measures to keep your security, privacy, and personal information safe when using the internet.

A. Fill in the blanks.
Hints
is the act of using digital platforms to harass, scare, or harm others.
Plagiarism involves using someone else's work or ideas without proper
Phishing is a deceptive online practice that aims to trick individuals into revealing information.
Cyberstalking is an illegal and internet activity.
theft happens when someone pretends to be someone else.
B. Tick () the correct option.
What is the primary goal of phishing attacks?
a To promote online safety
c To spread awareness about cybersecurity
Which of the following is an ethical practice?
a Identity theft
c Plagiarism
What is the purpose of digital footprints?
a To track your online actions
c To protect your identiy
What is the main reason behind identity theft?
a Drive for fame
c Financial gain and dishonest behaviour
What is the meaning of the term "digital citizenship"?
a Being a citizen of a digital nation
c Acting ethically and responsibly online
C. Who am I?
b To imitate trusted entities
d To encourage ethical hacking
b Ethical hacking
d Cyberbullying
b To hide your online activities
d To stop online communication
b Requirement for social interaction
d Individual curiosity
b Owning a digital device
d Having a digital footprint
D. Write T for True and F for False.
Cyberstalking involves constantly monitoring someone’s online activities.
Spamming refers to sending unwanted emails for promotional purposes.
Digital footprints cannot be traced to a specific person.
Digital citizenship is the term used to describe the ethical and responsible use of technology.
Plagiarism is defined as the act of copying another person’s idea, work, or content giving proper credit or taking permission.
E. Answer the following questions.
What do you mean by cyberbullying?
Explain the concept of digital citizenship and why it is important for young internet users.
List three online safety measures that can help protect your personal information and privacy. Define the term ‘intellactual property’.
F. Apply your learning.
Sneha has received some messages from her classmates that are not appropriate. What type of behaviour are her classmates showing? Is it ethical or unethical?

Arvind is very upset as he receives many unwanted emails daily. What is the name of this activity?
Prabha has received an email asking for her bank account details. Should she respond to that email or not?
Ravi uses the internet daily to search for information for his studies. What ethical practices should he be aware of and follow while being online?
You have received an email stating that you have won an iPhone. Should you believe such emails and respond to them or not?









Imagine you went on a school trip. You and your friends decided to create a digital diary. You wanted to store and save the memories of this trip in the drive.

In this diary, you all wrote down all the things that you did together, and everyone in the group has a copy. Whenever you or your friends added anything new to the diary, like a special memory or an important event, everyone of you had to agree if it was true and accurate.
The digital technology named Blockchain works in a similar way. Blockchain is a shared, unchangeable record that helps track transactions and assets in a business network.
To understand Blockchain in a better way imagine that you and your friends were using computers to note down your memories. Each time a new memory was entered, it was like adding a new page to this digital diary.

But here is the interesting part: every new page is linked to the one before it, just like a series of dots that are connected. Each page can be considered a block. Thus, a chain of connected pages is a blockchain.
Since everyone of you can see the whole chain, it’s really hard for anyone else to sneak in and change something without everyone noticing it.



The blockchain helps computers keep important information safe by connecting the pieces together in a way that’s really hard to cheat.






Blockchains have the following features:
Decentralisation
Decentralisation means that there is not just one single person, organisation, or central authority in control of it. Instead, control or decision-making is spread out among many different individuals or entities.
A blockchain is a digital chain that may be made up of many blocks from many parties involved. It allows people to store and share information in a decentralised and distributed system.

Transparency
A block is a specific unit of data that is part of a blockchain that holds specific verified information. The whole process is designed to be immutable, which means that while the information in it can be seen by all the users, no one will be able to change or delete the information.
Transparency means that everyone who is a part of that blockchain can see all the information, and nothing is kept hidden from them. This helps to build trust among the users.

Blockchain also keeps the personal details of the users safe. This means that while everyone gets to see the information in that blockchain, no user can see each other’s personal information.
You Know?
Blockchain technology came into existence in 2008. However, the identity of the person or group behind the creation remains a mystery. The pseudonym “Satoshi Nakamoto” is used as the inventor, but the real identity of this individual or group has never been found.
Let us understand how Blockchains actually work.

Imagine that you want to buy a piece of artwork from an online seller. What would the entire process look like if it were operating through Blockchains? Let us see!































All before, during and after details of the purchase available on the blockchain






Artwork physically transported to buyer, information confirmed and updated on blockchain
Blockchain records transfer of money from buyer. Information confirmed by bank.
1. You, as the buyer, get accurate information on the blockchain on whether the artwork you are interested in is actually available with the seller or not. The security and transparency in blockchains allow us to trust the information and the seller.
2. You contact the seller to buy the artwork.
3. You then send a request to the seller that you want to buy the artwork. This request ‘transaction’ is recorded in the form of a block on the blockchain. Remember that each piece of new information is stored as a block in the blockchain. So, both you and the seller will be able to ‘see’ the updated information.
4. The seller reviews your offer, and you mutually agree on the terms of the transaction. Once both parties have agreed, this information will be recorded as a block on the blockchain. Both of you will be able to access this information anytime you want, but neither of you will be able to change it.
5. After that you make the payment. Once the bank confirms that the money has been deposited into the bank account, this information of making the payment is also safely recorded on the blockchain. Since this information cannot be changed, your money is secured.

6. The seller sends the artwork to you, and you receive it after some time. This information is also updated into the blockchain.
7. Once you receive the artwork, you update the information that the transaction is now complete. What information is so important on the agreement that the blockchain should not allow any party to change it?
8. In case the seller refuses to send the goods even after receiving the money, the entire transaction details are available as proof that the artwork was not sent to you even after you had paid for it. Once again, the blockchain system can save you from losing your money.
9. At the end of the entire transaction, the blockchain now holds all details. It also knows that the seller no longer has that particular artwork, and that you now possess it.
It is important to note that the above example is a visualisation of how the purchase of artwork could work through blockchain. All digital transactions around us do not work on blockchains today.


Blockchain is a technology that can be applied in many fields! See some surprising uses!
Like all other technologies, blockchain has some challenges too. Let us look at some of them.
Long Validation Process
One of the biggest strengths of blockchain is that it can provide accurate information. But the process of validation itself is sometimes very cumbersome!
Slow Speed in Working with Large Amounts of Information
The blockchain records all developments as information. But what if there are too many transactions that involve several people? Maintaining verified information at each step would become very difficult. So, while working on a larger scale, maintaining speed with security is difficult.
Interoperability
We learnt that blockchains are decentralised. It is possible that different blockchains are fundamentally different in the way they have been designed and created. This sometimes makes it difficult for different blockchains to communicate with one another.
Legal Challenges
Technology brings users from across the world together! But citizens of different countries are bound by the laws of their respective countries. Laws related to IT and technology tend to vary from country to country. So legal situations while dealing with blockchains might be complicated.
Do It Yourself 3A
Tick () the correct answer.
What is a blockchain?
a A type of physical network b A digital puzzle c A decentralised digital book of records d A type of computer

Write T for True and F for False.
a A blockchain is controlled by a single central authority.
b Different blockchains may be different.
c Different countries have the same laws related to blockchain.
d The information stored in blocks can easily be accessed by anyone who has access to the blockchain.
Imagine your school starts using blockchain for the entire exam process. Thus, there will be different blocks for creating question papers, conducting exams, and announcing results. Will you be able to change your marks in the system without the teacher knowing? Why/Why not?
We use the Indian Rupee, or INR, to buy things in India. The INR is the national currency of our country. Similarly, other countries have other currencies. We use Dollars, Euros and Pounds in the US, Europe and the UK, respectively.
When we withdraw money from the bank to buy something, the bank stores the records of our account. It can, at any time, tell us how much money is left in our account.
What if we use a debit card or UPI to pay? The bank digitally certifies that we have the money and lets us make the purchase. Once the purchase is made, the money immediately gets debited from our bank account.
Cryptocurrencies are very different from our usual currencies. Cryptocurrency is a purely digital or virtual currency that can also work as a medium of exchange. But, it exists only in digital form and doesn’t have physical coins or banknotes.
Bitcoin is the name of a famous Cryptocurrency.
Unlike traditional currencies, Cryptocurrencies do not have a banking system that records transactions. So how do they work? Cryptocurrencies work on blockchain. Let us learn how.

























































































































































































































































In usual currencies, the bank is the figure of authority that allows or disallows a transaction. The given infographic shows how the system works for usual currencies.
Buyer requests a purchase
Seller asks the bank if the Buyer has money in the bank
Bank updates the bank account against the purchase
Bank confirms that there is money in the bank
In the case of Cryptocurrencies, there is no centralised banking system. The entire system works on blockchain.
A blockchain replaces the role of the bank in this case. This process is modified in the following way:
Buyer requests a purchase
Seller seeks a confirmation from the blockchain if the buyer has sufficient Cryptocurrency


has the















































A block containing information on the purchase is added to the blockchain and the buyer’s balance is updated
For normal currencies, the bank, as a financial institution, knows all about every transaction and the account details of every person involved in the transaction. How does it work in case of cryptocurrencies?

Let us look at these points to find out how the blockchain system works for Cryptocurrency.
Confirming the cryptocurrency with the buyer: Since blockchain is a decentralised and transparent system, every piece of information is available for confirmation. Hence, the amount of cryptocurrency that the buyer holds can be double-checked.
Making the purchase safely: A new block is added to the blockchain that contains information about this transaction. The entire blockchain now knows how much currency was spent on this purchase.
Account updation after purchase: Once the buyer has bought an item, this information is added to the blockchain as a new block. This amount is deducted from the buyer’s initial sum of cryptocurrency. This new amount is now available for buying things in the future.
Trusting the information: Since Cryptocurrency is purely digital, it is always possible for the buyer to say that they have more money than what they actually have. How can we make sure, then, that the information is true?
We do not have a bank in the case of Cryptocurrencies, but the information regarding the amount is held within the blockchain. This information has been verified by multiple users and records can be doublechecked at any time and from any place.
Match the Following:
Cryptocurrency
Traditional Currency
Physical coins and banknotes used for buying
Digital currency that works on blockchain
A famous example of a cryptocurrency
Compare traditional currencies (like INR, USD) with cryptocurrencies (like Bitcoin). List at least two similarities and two differences between them.
Blockchain is a digital technology for storing and securing information.
Blockchain is decentralised, meaning no single person or authority controls it.
A blockchain is a digital network composed of blocks.
Blocks hold verified information and cannot be changed or deleted.
Information within a blockchain is transparent but safeguarded against unauthorised changes.
Interoperability is a limitation of blockchain, as different blockchains might struggle to communicate due to design differences.
Cryptocurrency is a type of digital or virtual currency that serves as a medium of exchange.
A. Fill in the blanks.
Hints block individuals blockchain bank privacy
The specific unit of data that is part of a blockchain and holds verified information is called a .
The information stored in a is divided into blocks.
Blockchain ensures so that the individual and personal details of participants are secured.
Decentralised means that the control or decision-making is spread out among many different
Cryptocurrency is based on blockchain technology. It is not controlled by any or any government.
B. Tick () the correct options.
Which of the following statements about blockchain is incorrect?
a Anyone can easily change information in a blockchain.
b Blockchain uses blocks to store information.
c The information stored in a blockchain is secure.
d Blockchain utilises decentralisation and security features to store information.
Which feature of blockchain allows everyone in the network to see the entire history of the data?
a Security b Transparency
c Privacy d Immutability
In a blockchain, each new block needs to be verified by:
a the buyer b every individual on the blockchain
c the seller d a portion of blocks
What challenge can arise due to the decentralised nature of blockchains and their potential differences in design?
a Enhanced communication between blockchains.
b Simplified data sharing among different blockchains.
c Improved interoperability between various blockchain networks.
d Difficulty in communication between different blockchains.

C. Who am I?
I am a digital technology that connects pieces of information in a secure way.
I am a type of currency that exists only in digital form and works on blockchain technology.
While withdrawing regular currency notes, I maintain a record of the transaction.
I am a national currency used to buy things in India.
I am a unit of data in a blockchain that holds specific verified information.
D. Write T for True and F for False.
Decentralised means there is one central authority controlling everything.
Blockchain can be used to create transparent voting systems where every vote is recorded and cannot be altered.
If your school uses a blockchain-based digital identity system for students, you cannot view other students’ personal information.
Cryptocurrencies have a banking system that records transactions, similar to traditional currencies.
In a blockchain network, any user can easily access, change or delete the information stored in a block.
E. Answer the following questions.
What are blockchains? Give an example that can work on a blockchain.
What is a cryptocurrency. Write the name of a famous cryptocurrency.
How does blockchain ensure the security and immutability of information?
How does the transparency of a blockchain system help build trust among users?
state the challenges of blockchains.
Imagine a school club where everyone gets to make decisions. Name the system which allow everyone to make decision?
Suppose your school library considers using blockchain technology for the process of issuing and returning library books. As a student, what benefits do you think this will have?
Imagine if anyone could change their Cryptocurrency balance to show that they have more money than they actually do. What could go wrong in such a case? How does the blockchain prevent this from happening?
We saw in the chapter how the purchase of artwork could potentially work on a blockchain. How is this different from the usual digital purchases?







Suppose you are ordering food for dinner tonight. You will fetch your phone, use a food ordering app, and place the order. It is that simple!
Your smartphone must have a variety of apps. Do you ever realise how these apps are created and how they work? Well, you will learn about apps in this chapter.
Apps or Applications are software programs or mobile applications that can be downloaded and installed on electronic devices like smartphones, tablets, and computers. These apps serve various purposes and can be used for playing games, accessing social media, learning, productivity, communication, and many other activities. You are likely to be familiar with popular apps and may use them regularly for entertainment, education, or communication.


In short, an app refers to a program or software application designed to perform specific tasks or functions on a computer, smartphone, tablet, or other kinds of digital devices.
The first mobile app store was launched by Apple in July 2008, alongside the release of the iPhone 3G. It was called the “App Store,” and it initially featured 500 apps.
1. Social networking apps: Social networking apps are apps that help people connect and share with others online. They let you make friends, post updates, and chat. Facebook, Instagram, LinkedIn, Snapchat, and X (formerly known as Twitter) are some of the commonly used Social Networking Apps.


2. Productivity apps: Productivity apps are apps that help you get things done and be more organised. Microsoft Word, Google Drive, Snapseed, Analytics, and YT Studio are a few examples of productivity apps.

3. Educational apps: Educational apps are digital apps designed to support learning and education across various subjects and skill levels. They include interactive learning platforms which offer engaging lessons; quiz apps, language learning tools, and educational games for younger learners. These apps enhance learning by providing interactive, accessible, and flexible educational experiences.

4. Gaming apps: Gaming apps are apps where you can play fun games. These apps provide entertainment and challenges, allowing you to explore virtual worlds, solve puzzles, or compete with others. Temple Run, Angry Bird, Sportify, MineCraft, and Fruit Ninja are a few examples of gaming apps.

5. Food delivery and cooking apps: Food and cooking apps are apps that help you discover recipes, cook delicious meals, learn about food, and order food. Zomato, Swiggy, DoorDash, Insta Mart, and Zepto are few examples of food delivery and cooking apps.














You can access apps from your mobile phone, desktop, or directly from the web. Let us learn all these methods to access the apps.





Think and Tell
What are the most popular apps according to you?

Desktop apps are like the computer version of the apps you use on your phone, but they are designed to work on your computer and do all sorts of different things, from writing documents to playing games or editing pictures.
Desktop apps are software applications that you can use on your computer or a laptop where they are installed and run locally. Desktop applications do not require an internet connection to run. For example, Microsoft Word is a desktop app that helps you write essays and stories on your computer. There are also games like Minecraft that you can play on your computer. Skype, Microsoft Power Point, Paint, Microsoft Excel, and iTunes are a few examples of desktop apps.

A web app is a software application that operates on web servers and is accessed by users through web browsers over the internet.
Web apps, short for web applications, are software applications that run on web servers and are accessed through web browsers over the internet. These applications provide a user interface and functionality similar to traditional desktop applications but are designed to be used within a web browser. Since web apps are hosted on web servers, users can access them from anywhere, using various devices, without the need for installation. This ease of accessibility is a significant advantage for both users and developers. Web apps can be accessed from any device with a web browser and an internet connection. They are not tied to a specific operating system, making them platform-independent. Padlet, YouTube, Gmail, and Google Drive are a few examples of web apps.




Mobile apps are programs you install on your phone to make it more fun or helpful for whatever you want to do.





















A mobile app is a tiny computer program that you can download and used on your smartphone or tablet. It makes your phone do fun or useful things beyond making calls or sending texts. Mobile apps can be games you play, tools that help with homework, maps that show you where to go, or even things like filters that make your photos look improved. Mobile apps can be downloaded from the app stores available on your mobile. An app store can host large numbers of mobile apps. You can check the various features of the app you want to download and compare it with other related mobile apps available on the app store. Instagram, Camera, Telegram, iMusic, and Google Maps are a few examples of mobile apps.












































































































To know more about web apps, scan this code.
1 Match the different types of apps with their suitable examples:
Types of App










































2 Fill in
a and are social media apps.
b Apps can be and installed on electronic devices.
c run on web servers and are accessed through web browsers over the internet.
d You can download a mobile app from available on your phone.
Apps can be classified based on the technology used to create them, and their usage.
There are two types of apps based on how they are made. They are:
Native apps are specifically designed for a particular type of phone, such as iPhones or Android phones. They are known for their high speed and excellent performance because they are designed exclusively for your phone. Examples of native apps include Camera, Gallery, Clock, Maps, and Settings.

Native apps can sometimes be used even without an internet connection! That is because they are installed directly on your device, and many of them store information on your phone. It is like having a little piece of the internet right on your device! Did You Know?
Hybrid apps can work on different types of phones and use web technologies, allowing them to work on multiple platforms and access device features. They are compatible with both iPhones and Android phones and can be downloaded and installed from their respective app stores, such as the Google Play Store for Android phones and iTunes for iPhones. Although they may not match the speed and smoothness of native apps, they offer versatility by running on a wide range of smartphones. Examples of hybrid apps include Uber, Zomato, Instagram, Telegram, and X (formerly known as Twitter).

Native apps are built specifically for one type of mobile operating system, such as iOS (for Apple devices) or Android (for Android devices).
Hybrid apps are developed using web technologies like HTML, CSS, and JavaScript and can run on multiple platforms (iOS, Android, etc.) with some modifications. They typically offer the best performance and responsiveness because they are optimised for the particular device and its features.
Native apps have complete access to device features, like the camera, GPS, and sensors, allowing them to take full advantage of these capabilities.
They are distributed through platform-specific app stores like the Apple App Store and Google Play Store.
There are many apps based on their usage. They are:


Hybrid apps might not feel as fast or quick as regular apps because they use a part that is like a web browser to show things, and that can be a bit slow.
Hybrid apps can access device features to some extent using plugins, but not as exclusively as native apps.
Hybrid apps can be distributed through web browsers as web applications. They can also be distributed through app stores.

Educational apps are software applications designed to facilitate learning and provide educational content on various subjects and skills. These apps are developed to make learning more engaging, interactive, and accessible for users of all ages, from children to adults.








How can we get hybrid apps onto our phones? Is it similar to how we get native apps?


Social networking apps are like virtual platforms where you can meet and talk to your friends and even make new ones. They are special apps on your phone or computer that help you connect with people, share things about your life, and see what your friends are up to.


Did you know that the "Like" button on Facebook was originally going to be called the "Awesome" button? Facebook's founder, Mark Zuckerberg, considered different names for it before settling on "Like". So, every time you click "Like" on a post, you are giving it a little touch of awesomeness!
Entertainment apps are online portals for having fun and enjoyment on your phone or tablet. They are special apps that offer all sorts of things to make you happy and have a great time.























Banking apps are like a virtual bank branch on your phone or tablet. They are the special apps provided by your bank to help you do immediate money transactions without going to the bank in person.








Name four native apps and four hybrid apps. Which one between the two categories do you use the most?
a These apps can help users develop a wide range of skills, including reading, writing, maths, and problem-solving.
b These apps are like virtual platforms where you can meet and talk to your friends.
c These apps provide you with help when you do important financial transactions.
d These apps let you shop for all sorts of things without having to go to a physical store.
e These apps are the portals for fun and enjoyment on your phone or tablet.
MIT App Inventor is a visual development platform that allows users to create mobile applications for Android devices without the need to write traditional codes. It is designed to make app development more accessible to a wide range of people, including those who do not have extensive programming experience. MIT App Inventor provides a visual, drag-and-drop interface for designing the user interface and functionality. Users can assemble components and connect blocks to create the app’s logic.
Let us create a simple app using MIT App Inventor.
The name of this app will be Magic_Button.
The app will have the following components:
1. A button
2. An image (Download any image from the internet and save it on your computer for later use.)
These two components will be added to the app design. Initially, the image will not be visible. The idea is to display the image only after the user clicks on the button. Let us design the app now.
Visit the following link to open MIT App Inventor: https://appinventor.mit.edu/
The given screen appears:

Click on the Create Apps! Button.
A sign-in screen appears. You can use your Gmail ID to login, or you can create a new one as well.
After signing in, the Welcome to MIT App Inventor pop-up box appears. Click on the Continue button at the bottom of the screen.
Another screen appears, from which you can choose to view the tutorials or start a new blank project.
Click on START A BLANK PROJECT
Continue Button
The Project View window appears.
Click here to start a blank project
A dialog box appears, asking you to give a project name to your project.
Give an appropriate name to your project, for example, Magic_Button and click on OK.
A new project with the same name will be created.
The Project View window will open.
The Project View window is divided into four sections:
Palette: Various components are presented under different categories in the palette.
Viewer: You can select any component from the palette and drag and drop it onto the screen in the Viewer section.
Components: The Components section shows the various components that are placed in the Viewer.
Properties: The Properties section shows the properties of the selected components.
Let us now create the interface of the app.
From the Palette section, click on the Layout tab.
Drag the VerticalArrangement component and place it on the screen in the Viewer section.
Now, click on the VericleArrangement1 component in the Components section and go to the Properties section.

Scroll down to the Height property and click on it.
Select the Fill parent option and click on OK
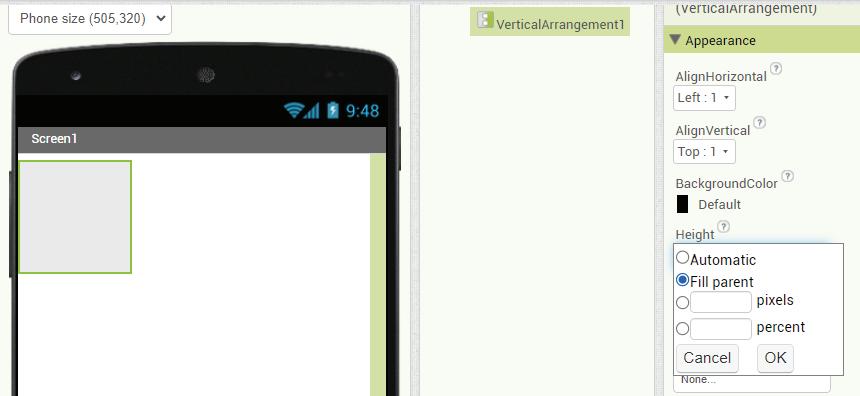
Similarly, select the same option for the Width property. The VerticalArrangement component will fill the whole screen.
Now, from the User Interface tab, drag the Button component and drop it on the screen.
You can also observe that the Button1 component is added under the Components section.
Now in the Properties section, scroll down to the Text property of the button. Replace the text “Text for Button1” with “Magic_Button”.
From the Palette section, drag the Button component and place it in the Viewer section on Screen1
Now, change some more properties of the button in a similar way from the Properties section:
o Font Size: 20
o Background Colour: Cyan
o Text Colour: Blue
o Shape: Rounded
o Height: 10 percent
o Width: Fill parent
Now, drag an Image component from the User Interface section and place it on the screen.
From the Components section, select Image1 and click on the Picture option in the Properties section. A drop-down will appear. Click on the Upload File option.
The Upload File dialog box will open. Click on the Choose File button.
An Open dialog box appears. Select the picture that you have downloaded from the internet and click on Open.
The image will appear on the screen.
You can now set the properties of the image.
o Height: Fit to parent
o Width: Fit to parent
o Visible: Uncheck (to hide the image initially)
After setting all the properties of both objects, the screen will look as shown here:

After that, you have arranged your components on the screen. Let us now create the code for the app.
Coding in MIT App Inventor is very easy and user-friendly. You can create code for your app by using various blocks present in the Blocks Editor
To create code for your app, follow the given steps:
Click on the Blocks Editor button on the right-hand upper corner of the Project View window.
The Blocks Editor will open with the Blocks section on the left and the Viewer section on the right.

Click on Screen1 > Button1 from the Blocks pane.
The blocks related to Button1 will appear.
Drag when Button1.Click block from the Blocks drawer and drop it in the Viewer pane.
Now, click on the Image1 component in the Blocks panel. The blocks related to the image are displayed.
Drag set Image1.Visible to block and drop it inside the when Button1.click block.
Now, from the Built-in > Logic drawer, drag the true block and snap it together with the set Image1. Visible to block.
The code for your app is complete.
Now, when you click on the Magic_Button on your mobile app, you will see a picture of a flower.
To test your app, you will need a mobile phone.
Go to the Google Play Store of your android phone and search MIT AI2 Companion App
Install the app by clicking on “Install”.
After installation, open the app. You have to provide a six-character code to connect.
Now, to get the code, go to your computer where you have created your app.
Go to the Connect menu and select the AI Companion option.



A Connect to Companion window will open with a six-character code.
You can now fill in this six-character code on the mobile phone app.
The app will now open on your mobile.
Click on the button that you have created, which is the Magic_Button.
You will be able to see an image of the flower.
Do It Yourself 4C
Create an app on MIT App Inventor to show your name when you click on a button.

1 Apps or applications are software programs or mobile applications that can be downloaded and installed on electronic devices like smartphones, tablets, and computers.
2 Social networking apps, productivity apps, gaming apps, food delivery and cooking apps are different types of apps.
3 You can access apps from your mobile phone, desktop, or directly from the web.
4 Desktop apps are software applications that you can use on your computer, just like you use games or apps on your smartphone.
5 Web apps, short for web applications, are software applications that run on web servers and are accessed through web browsers over the internet.
6 A mobile app is a tiny computer program that you can download and use on your smartphone or tablet.
7 Native apps are specifically designed for a particular type of phone, such as iPhones or Android phones.
8 Hybrid apps can work on different types of phones and use web technologies, allowing them to work on multiple platforms and access device features.
9 MIT App Inventor is a visual development platform that allows users to create mobile applications for Android devices without the need to write traditional codes.
Fill in the blanks.
An is a computer program that you can download and use on your smartphone or tablet. are special apps that let you shop for all sorts of things without having to go to a physical store. apps are developed using web technologies like HTML, CSS, and JavaScript and can run on multiple platforms.
In MIT App Inventor, various components are present under different categories in apps are apps that help people connect and share with others online.
B. Who am I?
I am like a virtual bank branch on your phone or tablet.
I can assist you to design and make the app of your dreams.
I am a computer program that you can download and use on your smartphone.
I can show the properties of the selected components.
I am a type of app that can work on different types of phones, like both iPhones and Android phones.
C. Write T for True and F for False.
Apps are software programs that can be installed on your desktop.
There are two types of apps: hybrid and native.
Web apps do not operate on web servers and are not accessed by users through web browsers.
Native Apps provide the best performance as they are optimised for the particular device.
The Components section shows the various components that are placed in the Viewer.
D. Answer the following questions. What

E. Apply your learning.
Ramesh wants to learn how to design an app on MIT App Inventor. Which website should he visit?
Tia wants to understand the e-commerce apps and know a few examples. Can you explain it to her?
Umang wants to download a specific app for his iPhone. Where can he get the app?
Geet is using her computer and wants to learn about web apps. Can you help her understand about them?
Meher has installed an app on her phone that was not a pre-loaded app. What type of app has she downloaded?








Have you ever experienced putting on a special pair of glasses and suddenly started exploring a totally different world? It can be a forest, an ocean, or even a gaming environment.
Also, imagine having a robot friend. How would you interact with it? What type of tasks would you like it to do?
In recent years, innovative advancements like Augmented Reality (AR), Virtual Reality (VR), Metaverse, 3D Printing, and Robots have taken place, changing the way we play, learn, and work. Let us discuss each of them one by one.

Augmented Reality (AR) is a technology that overlays digital content—like images, text, or animations—onto the real world
This is done using devices such as smartphones, tablets, or AR glasses.
AR enhances the user's perception and interaction with their surroundings by providing additional information or creating immersive experiences that blend the physical and digital worlds.



In 2016, the popular game Pokémon GO introduced millions of people to augmented reality. It got players out and about, hunting for digital Pokémon creatures in the real world using their smartphones. It's like a global treasure hunt that brought AR to the masses and became a huge craze!
Here are some practical uses of AR: Gaming: With AR games, you can see and interact with virtual objects in your real surroundings.


Shopping: You can try on clothes, makeup, or spectacles, etc., virtually without going to a store. You can check how furniture looks in your room before buying it. Also, you can search for products by pointing your smartphone at them.
Navigation: Using AR, you can find an easy way in a new city, discover nearby places of interest, or get real-time information while driving.


Science and Experiments: AR helps you understand complex ideas by showing them visually. You can explore the human body in 3D, see how planets move in the sky, or watch chemical reactions happen right before your eyes.
What is one experience that you would like to have throughout augmented reality?
Here are some advantages and disadvantages of Augmented Reality:
Advantages
Fun and Engaging: AR makes learning and playing more fun by adding exciting digital elements to the real world.
Enhanced Learning: It helps students understand complex topics better with interactive 3D models and visual aids.
Exploration: AR can take you on adventures without leaving your room, like exploring the depths of the ocean or the surface of Mars.

Disadvantages
Screen Time: Using AR often involves staring at screens for a long time, which can be tiring and not good for your eyes.
Cost: Some AR devices and apps can be expensive, and not everyone can afford them.
Privacy: AR can sometimes track your location and what you’re doing, which might make you worry about your privacy.

Creativity: You can create your own AR experiences, like drawing in 3D space or making your own virtual world.
Practical Uses: It can be used for practical things like trying on clothes before buying them or finding your way with helpful directions.

Answer the following questions.
Distraction: While AR is fun, it can also be distracting. It’s important to use it responsibly, especially in school or while walking outside.
Technical Issues: AR might not work well if your device has a low battery or if there are problems with the app.

To watch how augmented reality works, scan this QR code.
1 Write any two uses of Augmented reality.
2 Mention any two disadvantages of Augmented reality.
Virtual Reality (VR) is a technology that creates a fully immersive, computer-generated environment that users can interact with.
Users wear VR headsets that block out the real world and replace it with a digital environment, giving the sensation of being in a different place or world. They can interact with the virtual environment using controllers or body movements, enhancing the feeling of presence within the digital world. This technology is often used in gaming, simulations, and training applications.


Did You Know?
Some people may experience motion sickness when using VR, which is often referred to as “cybersickness.” It is similar to motion sickness experienced in vehicles.

Can you think of any industries or fields where the use of VR will really help flourish or where it will be particularly useful?


Gaming: VR is used for bewitching gaming experiences. You can put on a VR headset and feel as if you’re inside the game, whether it’s exploring magical worlds, solving puzzles, or battling virtual monsters.

Education: VR can be used in classrooms to make learning more engaging. Students can take virtual field trips to historical sites, explore the human body in 3D, or even travel to space to learn about planets and stars.

Training: VR is used to train people for different jobs. Pilots can practise flying in a virtual cockpit, medical students can simulate surgery, and firefighters can learn how to handle emergencies in a safe virtual environment.

Virtual Tours:
You can use VR to take virtual tours of famous landmarks, museums, and cities around the world. It’s like travelling without leaving your home.

Architecture and Design: Architects and designers use VR to create virtual models of buildings and spaces, allowing them to walk through and make changes before construction begins.
1 Fill in the blanks.
a Students can take virtual field trips to , explore the human body in 3D, or even travel to space to learn about and
b You can use VR to take virtual tours of famous , , and around the world.
2 Choose the picture that is showcasing VR and explain why.



The Metaverse is a virtual space where people interact in real time using augmented and virtual reality technologies. It combines aspects of social media, online gaming, and virtual worlds, allowing users to work, play, shop, and socialise in an immersive, 3D digital environment.






Following are the uses of metaverse:
1. Social Interaction: People can connect, socialize, and attend virtual events in immersive 3D environments.

2. Gaming: It offers an enhanced gaming experience with fully immersive virtual worlds.
















































































































Robotics is a field that involves creating and working with robots. Robots are like machines with the ability to move and perform tasks on their own, often controlled by computer programs. They can come in all shapes and sizes, from small robotic toys to large industrial machines.
Robotics is a field of engineering and science that involves the design, construction, operation, and use of robots. It is not just about building something that moves; it is about making robots that can think and make decisions. We use various sensors and programming languages to make robots smart.



Robotics is used in many different areas, such as manufacturing, medicine, space exploration, and even in our everyday lives. For example, some robots help assemble cars in factories, while others can assist surgeons in delicate surgeries.
Did You Know?
Robots like Sophia and Atlas are designed to look like humans and can also move just like humans. These robots can express themselves with proper emotions.

Vacuum Cleaners: These are autonomous vacuum-cleaning robots that navigate your home and clean the floors without human intervention.

Medical Devices: In some healthcare settings, robots assist in surgeries, deliver medications, or help with rehabilitation exercises.

Drones: Unmanned aerial vehicles (UAVs) or drones are used for tasks such as aerial photography, surveillance, and even package delivery.



Traffic Lights and Road Signs: Some traffic management systems use sensors and automation to optimise traffic flow and improve safety. Automated Coffee Machines: Coffee shops and vending machines often use robotic systems to grind beans, brew coffee, and serve drinks.





3D printing is a process that creates three-dimensional objects by layering materials based on digital models.
3D printing builds objects layer by layer, which allows for the creation of complex designs.


Follow the given steps to know about how 3D printers work:
1. Design Creation: A digital 3D model is created using computer-aided design (CAD) software.
2. File Preparation: The 3D model file is converted into a format that the printer can understand, typically a .STL file. The model is then sliced into thin horizontal layers by slicing software.
3. Printing Process: The 3D printer reads the sliced file and begins printing the object layer by layer. It does this by depositing material, such as plastic, resin, or metal, through a nozzle or laser.
4. Layer Formation: Each layer is printed on top of the previous one, and the material solidifies or cures to form a solid object. The printer repeats this process until the entire object is complete.
5. Post-Processing: After printing, the object may require additional processing, such as removing support structures, sanding, or painting, than You have a real, physical object that you can touch and use. It is an exact copy of what you designed on the computer.


Astronauts on the International Space Station can use 3D printers to make tools and parts they need. It provides a space toolbox that can create new tools whenever they want!
Arrange the steps in the correct order to explain how a 3D printer works:
1 The 3D printer reads the sliced file and begins printing the object layer by layer.
2 A digital 3D model is created using CAD software.
3 Each layer is printed on top of the previous one, and the material solidifies to form a solid object.
4 The 3D model file is converted into a .STL format and sliced into thin horizontal layers by slicing software.
Biotechnology is a stream of science that uses living things, like cells and bacteria, to make useful things. It is like using tiny living factories to create medicines, food, and other things that can help people and the environment.

Computer scientists create software and algorithms to process and analyse biological data. This includes studying genetic information, identifying patterns in biological processes, and predicting how organisms might respond to different conditions.

Computers play a crucial role in biotechnology, enabling advancements in research, development, and application. The following illustrates their contributions:
1. Machine learning and artificial intelligence are increasingly used in biotechnology. They can help in drug discovery, predicting disease outbreaks, and even analysing medical images like X-rays and MRIs.
2. DNA sequencing, which is crucial for understanding genetics, relies heavily on computer algorithms. High-performance computing is used to process the enormous amount of data generated during DNA sequencing.

3. Biotechnology labs often use automated equipment controlled by computers. Robots can perform repetitive tasks like mixing chemicals, running experiments, and even handling samples, making research more efficient and accurate.

Did You Know?
Scientists have used biotechnology to create a type of bioluminescent plant. That means they made a plant that can glow in the dark, just like fireflies! It is not only fascinating to look at, but it could also help reduce the need for electric lighting in the future.
1 Computer scientists create and to process and analyse biological data.
2 Robots can perform repetitive tasks like , , and even handling , making research more efficient and accurate.
3 High-performance computing is used to process the enormous amount of generated during sequencing.
Brain-computer interfaces (BCIs) are a fascinating area of technology that allow direct communication between the brain and a computer. They work by translating brain signals into commands that can control devices or software.
The primary purpose of BCIs is to enable individuals to control and interact with computers, robotic systems, or other devices directly using their brain activity without the need for traditional input methods like keyboards or mouse. They can help people control robotic arms with their thoughts.
Here is a simple breakdown of how they work:

Signal Acquisition: Sensors, often placed on the scalp (like in EEG headsets), pick up electrical activity from the brain. These sensors detect the brain's electrical signals, known as brainwaves.
Signal Processing: The raw signals from the sensors are processed to filter out noise and enhance the meaningful data. This often involves complex algorithms to interpret the brain activity patterns. Explore More!


To know more about how BCI works, scan this QR code.
Translation to Commands: The processed signals are then translated into commands that a computer or device can understand. For example, if the BCI detects a specific brainwave pattern associated with the intention to move a cursor, it can translate this into moving the cursor on the screen.
Feedback and Control: The computer or device responds to these commands, and sometimes the system provides feedback to the user, which can help in refining the control and interaction.
In case you get an opportunity to use a BCI what game would you like to play and what commands would you give the computer through this technology?
Generative AI refers to algorithms and models, particularly those based on deep learning techniques, that can create new content such as text, images, music, or even videos. Examples of generative AI include large language models like OpenAI’s GPT-4, image generators like DALL-E, and audio generation models like WaveNet.


The use of generative AI is not only limited to scientific tasks but various daily routine tasks as well. Some of these are:
Content Creation: Generative AI can automate and enhance content creation across various industries. It is used to write articles, generate graphics, compose music, and create video content, leading to faster production times and cost savings.
Design and Art: In design and art, generative AI allows artists and designers to explore new creative possibilities. It can generate unique visual art, assist in architectural designs, and inspire new fashion trends.
Education and Training: Generative AI can create personalised educational content, such as tailored exercises or simulations, to improve learning outcomes. It can also generate realistic training scenarios for professionals in fields like healthcare, aviation, and military training.
Healthcare and Medicine: In healthcare, generative AI is used to synthesise medical images, simulate biological processes, and generate potential drugs. It aids in developing new treatments and understanding complex biological systems.
Gaming and Virtual Worlds: Generative AI is transforming the gaming industry by creating dynamic and immersive game environments, non-player characters (NPCs), and storylines. It enhances player experiences by providing unique and interactive gameplay.

1 Match the following steps in the Brain-Computer Interface (BCI) process with their correct descriptions:
Signal Acquisition
Signal Processing
Translation to Commands
Feedback and Control
The system responds to commands, often providing feedback to the user.
Processed signals are converted into commands that control devices.
Sensors pick up electrical activity from the brain.
Raw signals are filtered and processed to extract meaningful data.
2 Generative AI has diverse applications across many fields. Which of the following is an example of generative AI in action?
a Creating unique and dynamic game environments
b Storing large amounts of data in cloud servers
c Managing email communications
d Browsing the internet faster
Augmented Reality (AR) is a technology that overlays digital content, like images, text, or animations, onto the real world.
Virtual reality is a technology that uses special goggles or headsets and sometimes even gloves or controllers to make you feel as if you are inside a computer-generated environment.
Virtual Reality is being used for:
The Metaverse is a virtual space where people interact in real time using augmented and virtual reality technologies.
Robotics is used in many different areas, such as manufacturing, medicine, space exploration, and even in our everyday lives.
3D printing is a process that creates three-dimensional objects by layering materials based on digital models.
Biotechnology is a stream of science that uses living things, like cells and bacteria, to make useful things.
Brain-computer Interfaces let our thoughts and brains talk to computers and machines.
Generative AI refers to algorithms and models, particularly those based on deep learning techniques, that can create new content such as text, images, music, or even videos.
A. Fill in the blanks.
Hints automated Augmented Reality headset control, interact tangible
BCIs enable individuals to and with computers directly using their brain activity.
Biotechnology labs often use equipment controlled by computers.
A 3D printer is a machine that can create real, objects from a computer design. makes your world more fun and interactive with the help of gadgets.
When you put on a VR , it covers your eyes, and you can’t see the real world anymore.
B. Who am I?
I am a form of AI that can create new content such as text, images, music, or even videos.
I let your thoughts talk to the computer and give commands.
I show you a mix of the real world and computer.
I can make a tangible product from a design.
I am used to making training and virtual tours more fun and real.
C. Write T for True and F for False.
The first step in 3D printing is to load the design into the 3D printer.
BCIs do not need inputs from a keyboard or mouse.
Robots are used in space exploration.
Biotechnology is the science of non-living things.
VR technology uses special headsets to see the virtual world.
D. Answer the following questions.
What are the uses of Augmented Reality? Where do we see robots in our lives every day?

E. Apply your learning.
Meenal wants to know where we all see robots in our daily life and how they make our lives easier. Help her to understand this.
Kriti does not understand the difference between AR and VR. Can you help her to understand?
Soumya has to make a presentation about Brain Computer Interfaces. What points do you thinks he should include in the presentation?
Manish wants to operate a 3D printer in the lab. What are the steps he must take to ensure that he is successful in making his design physically?
How will Misha tell her friends how








When you visit your school library, you can observe that the books are organised in a very systematic manner. You go to the particular bookshelf and fetch the book that you need. Then you ask the librarian to issue it to you. How do you think these books are organised in such a manner?
Yes, they have been given a unique number, and then they are arranged according to their genre, author, date of publication, etc.
Now, think of the same data being organised on a computer. This data can be maintained on a computer, also known as a database.
When we maintain data in an organised and structured manner in digital form on a computer, it is called a database.
It is a group of related facts organised together so that they can be accessed, controlled, and modified. It is an organised method of saving and finding information.
Where have you seen the use of a database in your daily life?
A database is a collection of tables, where each table consists of rows and columns. Each row represents a single record, and each column denotes a single piece of information surrounding that record.

A table is a grid-like structure consisting of rows and columns. In a database, the columns are referred to as fields and the rows are referred to as records.
Field: It is the title at the top of each column, describing what kind of data is in the column. It is also referred to as an attribute.
Record: It is a row in the table, containing all the information for one entry.
Student_Name
Shreya Delhi 9988776655 12-03-2010
Asmi Noida 3344556677 23-09-2011 Aarna Gurgaon 7867564534 04-04-2011 Fields Records
In the above table, Student_Name, Location, Phone Number, and Date of Birth are the fields in the table and [Shreya, Delhi, 9988776655, 12-03-2010], [Asmi, Noida, 3344556677, 23-09-2011], [Aarna, Gurgaon, 7867564534, 04-04-2011] are the three records in the table.
Databases are used to store several types of information, such as customer records, product data, and medical records. They are used by almost all organisations, governments, and businesses to keep their records in a systematic manner.

In the 1960s, the first databases emerged with hierarchical models. Relational databases, introduced in the 1970s by E.F. Codd, revolutionised data management, leading to modern database systems.
Here are some of the advantages of using a database:
It can carry vast quantities of data.
It can organise data in a manner that makes it easier to retrieve.
It can be used to modify and erase data rapidly.
It can be used to share data with others. Is it important for data to be


A database management system (DBMS) is a software application that enables you to construct, operate, and interact with databases. Some common examples of DBMS are MySQL, Microsoft SQL Server, and Oracle.
Here are some of the key roles or functions of a DBMS:
Storing Data: A DBMS can retain a huge amount of data in an organised form. This makes it easy and simple to access and recover the data when necessary.
Managing Data: A DBMS can manage the data in a database, such as adding, removing, modifying, and restoring data. It may also help to ensure that the data is genuine and consistent.
Protecting Data: A DBMS can protect the data in a database from unauthorised entry, change, or loss. It can do this by applying security measures such as user login and encryption.
Querying Data: You can access a specified piece of information from the database by making use of queries. This means that users may ask questions about the data, and the DBMS will deliver the results of the query.

A database is a structured data storage system used to store, organise, and retrieve information. It has evolved from manual systems to digital databases, playing a crucial role in modern data management.

Here are the various types of DBMS systems:
Hierarchical Database Management System (HDBMS) keeps data in a tree-like structure. Each record may have one or more child records, and each child record might have one or more grandchild records. HDBMS are well-suited for maintaining data that has a natural order, such as the structure of a corporation or the arrangement of plants and animals. Some examples of HDBMSs include IBM’s Information Management System (IMS) and the Integrated Data Store (IDS).
Relational Database Management System (RDBMS) are the most commonly used type of DBMS. They hold data in the form of tables, which are made up of rows and columns. Each row represents a record, and each column indicates a field. RDBMS are highly efficient in preserving and locating data, and they are also quite adaptable. Some notable RDBMSs include MySQL, Oracle, and Microsoft SQL Server.
Object-Oriented Database Management System (OODBMS) stores data in the form of objects. Objects are like records, but they may also have methods, which are like functions. OODBMS is well-suited for keeping complicated data, such as data that is tied to things in the real world.
Network Database Management System (NDBMS) stores data in a network-like structure. Each record may have one or more parent records, and each parent record might have one or more child records. NDBMS are well-suited for maintaining data that involves a complicated connection between records, such as airline routes between cities.
Do you think that a person with special knowledge of databases is required to handle it?
Database Management System consists of six main components.
These are:
• Data
• Hardware
• Software
• Users
• Procedures
• Database Access Language

Access Language
Data: This is the most significant component of a database. It is a collection of fundamental facts and figures that are recorded in the database.
Hardware: The hardware consists of the real computers that store and manage data in the database. This includes the computer, the hard disk drive, and the RAM.
Software: The software is the tool that operates the information. It is responsible for storing, obtaining, and managing data. The most common database application is termed a database management system (DBMS).
Users: The users are the individuals who connect with the database. They might be end-users who use the database to see data or database managers who operate the database.
Procedures: A procedure is a form of general instructions or guidelines for using a DBMS. These instructions include how to set up the database, install it, log in and out, manage it, create a backup, and generate reports from the database.
Database Access Language: Database Access Language is a language that allows users to give commands to a database to operate the data stored. You can use this language to ask the database to do many things, such as getting data, modifying it, or removing it.

Your favourite streaming service, like Netflix, uses big data and databases to recommend movies and shows to you.
Answer the following questions. Do It Yourself 6A
Name the components of a DBMS.
Name the different types of DBMS. 1 2
SQL, or Structured Query Language, is a powerful tool used for managing and manipulating data in databases. SQL provides a way to communicate with and manipulate databases through the following main operations:
• Data Querying: Allows users to retrieve specific data from databases.
• Data Manipulation: Includes commands to insert, update, and delete data.
• Data Definition: Enables users to define and modify the structure of the database objects, such as creating, altering, and dropping tables.

SQL statements are classified into the following two categories:
Data Definition Language (DDL): The SQL statements or commands that are used to create or delete tables are called DDL commands. These are necessary for creating, altering, and deleting the table. For example, create database, create table, add, modify, drop, etc.
Data Manipulation Language (DML): The SQL statements or commands that are used to insert, delete, or update data in the table of the database are called DML commands. For example, insert, delete, update, etc.
In the previous class, you learnt about creating tables, inserting data, and using the SELECT command with the WHERE clause. In this chapter, you will be introduced to more advanced SQL commands and concepts.
Before learning about SQL queries, let us first quickly learn about the various data types and keys used in SQL.
There are the following main data types used in SQL:
Data Type Description
Number Numeric data types are used to store a numeric value in a field column. It may be decimal, integer or real value.
Character (Fixed Length) This data type is used to store fixed-length character strings. If the string is shorter than the specified length, it is padded with spaces.
Varchar (Variable Length) It is used to store variable length alphanumeric data.
NUMBER(n, d) where n specifies the number of digits and d specifies the number of digits to right of the decimal point.
CHAR(size) where size represents the maximum (255 Characters) number of characters in a column.
VARCHAR(size) / VARCHAR2(size) where size represents the maximum (2000 characters) number of characters in a column.
Roll_number int (2)
Salary int (6, 2)
Name char(20)
Address Varchar(50)
Date It is used to store date in columns. The standard date format is YYYY-MM-DD.
Date
dob Date
Time It is used to store time in columns. The standard time format is hh:mm:ss. Time joining_time Time
Keys in a database are used to define any constraints on the table. We know a database can have multiple tables. Keys are also used to establish and identify relationships between tables. There are many keys that can be defined for a table. A table can have multiple keys also.
Primary Key The primary key is the attribute or set of attributes in a table that uniquely identifies a row in that table. There should be only one primary key in a table.
Candidate Key There might be multiple attributes that can uniquely identify a row in a table. Candidate key is the attribute that uniquely identifies a row in the table, but is not considered as the primary key.
Composite Key When a primary key consists of more than one attribute, it is called a composite key.
Foreign key Foreign keys help us to establish a relationship between multiple tables in a database.
Let us now revise some of the basic SQL commands that you have learnt in the previous grade.
The Create Table command is used for creating tables.
Create Table table_name (
column_name_1 data_type_1, column_name_2 data_type_2,
column_name_n data_type_n );
CREATE TABLE Students (
Student_ID VARCHAR(6), Student_Name VARCHAR(50), Grade INT, Section CHAR(1), Roll_Number INT, Library_ID VARCHAR(7), House_ID VARCHAR(4), Enrollment_Date DATE );
The Create Table command is used to create a new table in a database. When defining a table, you can set a primary key to ensure each record is unique.

Create Table table_name (
column_name_1 data_type_1 PRIMARY KEY, column_name_2 data_type_2, ………
column_name_n data_type_n );
CREATE TABLE Students ( Student_ID VARCHAR(6) PRIMARY KEY, Student_Name VARCHAR(50), Grade INT, Section CHAR(1), Roll_Number INT, Library_ID VARCHAR(7), House_ID VARCHAR(4), Enrollment_Date DATE );
Insert table command is used to insert values in the created table.
INSERT INTO table_name (column1, column2, ...) VALUES (value1, value2, ...);
INSERT INTO Students (Student_ID, Student_Name, Grade, Section, Roll_Number, Library_ID, House_ID) VALUES (‘STU001’, ‘Riya Das’, 7, ‘A’, 23, ‘LIB007’, ‘H001’, ‘24-07-2024’);
The SELECT statement is used to query the database and retrieve specific data.
SELECT column1, column2, ... FROM table_name WHERE condition;
Output
SELECT * FROM Students; Gives all the records entered in the table
SELECT Student_Name, Grade FROM Students; Gives only two columns Student_ Name and Grade
SELECT * FROM Students WHERE Grade = 7; Gives all the records of the students who study in grade 7.
Let us now learn about some more SQL queries.
You have seen that we can use the SELECT statement with WHERE clause. There are some more clauses which can be used with the SELECT statement. Let us learn about them.
The Order By clause allows us to sort the results in ascending or descending order. For example, To list students by age in ascending order:
SELECT * FROM Students ORDER BY Age;
To sort by age in descending order, use DESC:
SELECT * FROM Students ORDER BY Age DESC;
The Distinct keyword helps eliminate duplicate values. For example, to list unique cities where students live:
SELECT DISTINCT City FROM Students;
The Update command modifies existing records. To update the address of a student: UPDATE Students
SET Address = ‘1010 Elm Street’ WHERE StudentID = 1;
The Delete command removes records from a table. To delete a student from the database:
DELETE FROM Students WHERE StudentID = 3;
Aggregate functions perform calculations on a set of values and return a single value. Common aggregate functions include:
• COUNT(): Returns the number of rows.
Example: Count the number of students in each grade level:
SELECT Grade, COUNT(*) FROM Students
GROUP BY Grade;
• SUM(): Returns the sum of a numeric column.
Example:
SELECT SUM(salary) FROM Employees;

• AVG(): Returns the average value of a numeric column.
Example:
SELECT AVG(price) FROM Products;
• MAX(): Returns the maximum value.
Example:
SELECT MAX(age) FROM Employees;
• MIN(): Returns the minimum value.
Example:
SELECT MIN(quantity) FROM Orders;
To search for specific data in a MySQL database, you can use SQL queries by specifying some conditions.
The where clause is used to filter the rows returned by a query based on specified conditions.
Syntax:
select * from table_name where condition;
Example:
select Student_Name from Student where Gender = ’F’;
This SQL statement retrieves the Student_Name of the girl students.
Output
Wildcard operators in SQL are special characters for pattern matching in text data. They help in finding data that matches a pattern, not just an exact value. They are used with the 'like' clause in an SQL query. Two main wildcard characters used in SQL are '%' (matches multiple characters) and '_' (matches a single character). Let us look at their usage.
Using '%' Character: The percent sign (%) represents zero, one, or multiple characters.
Syntax:
select column_name from table_name where column_name like '%pattern';
Example:
select Student_Name from Student where Student_Name like '%s%';
Using '_' Character: The underscore (_) represents a single character.
Syntax:
select column_name from table_name where column_name like 'pattern_pattern';
Example:
select Student_Name from Student where Student_Name like 'P_yal';
Match the following.
Create Descending order
Distinct Filter rows
Where
Create a new table
Desc Eliminates duplicate values
A database is a structured collection of related data that can be easily accessed and managed.
Databases use tables to organise data, with rows for individual records and columns for specific information.
Components of a DBMS include data, hardware, software, users, procedures, and database access language.
Advantages of databases include handling large data volumes, efficient data organisation, quick data changes, and data sharing.
A Database Management System (DBMS) is software that helps create, operate, and interact with databases.
SQL is the language used to interact with the database.
Two types of SQL statements are Data Definition Language (DDL) and Data Manipulation Language (DML).
Keys in a database are used to define any constraints on the table.
The primary key is the attribute or set of attributes in a table that uniquely identifies a row in that table.
Wildcard operators in SQL are special characters for pattern matching in text data.

A. Fill in the blanks.
percent data column SQL DBMS
A database is a structured collection of
In a database, each piece of information is stored in a
The software used to manage and organise databases is called a .
The sign represents zero, one, or multiple characters in a value.
To retrieve specific information from a database, you can use a special language called .
B. Tick () the correct option.
What is a database?
a A place to store variables
c A storehouse for variables
Which of the following is an example of RDBMS?
a IDS
c Oracle
Which of the following is NOT a component of DBMS?
a Users
c Hardware
What is a record in a database?
a A collection of data
c A row in a database table
b A collection of organised information
d A kind of tree structure
b IMS
d None of these
b Data
d Network
b A collection of books
d A column of information
What is a primary key called when it consists of more than one attribute?
a Primary key
c Foreign key
b Composite key
d Candidate key
A column in a database table 2 DBMS
3 Different types of DBMS
4 Components of a DBMS
5 Attribute
D. Write T for True or F for False.
Relational, hierarchical, and network
A software application that helps users create, manage, and access databases
A special character for pattern matching in text data
Data, hardware, software, users, procedures, and database access language
A database is a collection of data organised in a way that makes it easy to retrieve, manage, and update.
In a database, information is stored in tables, which are made up of rows and columns.
The where clause is used to filter the rows returned by a query based on specified conditions.
Databases are only used by businesses and organisations; they have no relevance in our everyday lives.
Two main wildcard characters are % and &.
E. Answer the following questions.
How is data stored in RDBMS?
What do you mean by DML commands?
What are the advantages of using a database?
What is a database management system (DBMS)?
What are the wildcard operators used in SQL? Explain them.

F. Apply your learning.
Consider the following Employee table and answer the queries given below:
Display the IDs and names of all the employees.
Display the names of the employees whose salary is less than ₹23000.
Display the names and IDs of the employees whose salaries are more than ₹23000.
Display the minimum and maximum salaries from the table.








Video editing is the process of arranging and modifying video clips to create a video project. It involves cutting, adding, and enhancing clips to make the video more interesting and effective. Video editing is used to create presentations and reports in schools and offices, producing stories for series and movies and to create content for social media platforms.
Let us start a video project from scratch.
Follow the given steps to create a blank video in Canva:
1. Log in to www.canva.com and create an account if you do not have one.
2. Click on the Create a design button on the home page.
3. A drop-down list of options will appear.
4. Click on the Video option.


You can also click on the Video icon on the home page and select from the various options.

Let us discuss the various components of Canva window as marked in the above image.
1. Canvas: The canvas is your workspace, where you build and design your video. Here you can add and arrange all the elements of your video project, including text, images, videos, and audio.
2. Timeline: The timeline is a critical component that allows you to control the timing of your video. You can arrange elements on the timeline to determine when they appear and for how long. It helps you arrange objects like text, images, and videos in the desired sequence.
3. Zoom controls: Canva offers zoom controls that allow you to zoom in and out of your canvas. This feature helps you focus on specific details while working on your video.
4. Grid view: Grid view provides an overview of all the pages in your video project, helping you visualise the structure and flow of your video. It is a useful tool for organising your content effectively.
5. Preview: The Preview option allows you to see how your video will appear to your audience. It is a valuable tool for reviewing your video before finalising it, ensuring everything looks and sounds right.
6. Elements: The Elements option offers a wide range of design elements, including photos, videos, stickers, shapes, and icons. You can search and browse for elements to enhance the visual appeal of your video project.
7. Text tool: Text tool enables you to add text to your video. You can choose from various fonts, colours, sizes, and styles to customise your text elements. This is essential for creating titles, captions, and onscreen messages.
8. Uploads: This feature allows you to upload your own media files, such as images, videos, and audio clips, to incorporate them into your video project. It is a way to personalise your content and add unique elements.
9. Draw: You can draw any shape in your video by using the tools present under this drawer.
10. Projects: You can view all your projects that you have created up to now under this option. You can select any one of them to work upon.
11. Notes: You can add notes to your project to keep track of ideas, reminders, or specific instructions. Notes are useful for collaborating with others on your video project.
12. Canva assistant: This is a artificial intelligence tool that helps you with your queries during the project. You can ask any query by clicking on the Canva Assistant button.

You can use Canva’s Timeline feature to precisely control when each video element appears and disappears.
Match the features with its correct descriptions.
Canvas Lets you zoom in and out of your canvas to focus on details.
Timeline Enables you to add and customize text in your video.
Zoom Controls Your workspace where you build and design your video.
Preview Helps you control the timing of your video by arranging when elements appear.
Text Tool Lets you see how your video will appear to your audience before finalizing it.
You can add videos to your project using various options. Let us discuss them one by one.
You can upload your videos to Canva and add them to your project. Follow the given steps to add video from your device.
1. Click on the Uploads option in the side bar.
2. Click on Upload files and select the video files from your device. Wait for the upload to complete.
3. Drag and drop the uploaded video onto the timeline.

Follow the given steps to add videos to your video project in Canva:
1. Click on the Elements option in the side bar.
2. Type keywords related to the type of video you need in the Search bar (e.g., ‘nature,’ ‘city,’ ‘people’).
3. Go to Videos section, click on the video you want and drag it to the timeline.
4. You can resize it from the ends of the video to fit it according to the dimensions.
5. You can also add a new page and then add the video to that page.
Let us discuss some basic video editing tools.
To trim and split your videos, follow these steps:
1. Click on the video in the timeline to select it.
2. Hover over the beginning or end of the video clip and drag the edge to trim the video to the desired length.
3. Move the playhead (the vertical line) to the point where you want to split the video. Click on the Split button that appears above the timeline.

To resize or crop your video, follow the given steps:
1. Click on the video in the timeline.
2. Drag the corners of the video to resize it.

3. Crop the video by clicking on the Crop button above the canvas. Drag the edges of the video to crop it to the desired size. Click Done when finished.
You can add music or sound effects to your video:
1. Click on the Element option in the side bar and go to Audio section.
2. Type keywords in the Search bar to find the type of music or sound effect you want.
3. Click on the audio track and drag it to the audio timeline.

4. Click on the audio track in the timeline to adjust the volume or trim the audio.
You can enhance your video in Canva using the following effects.
Follow the given steps to apply filters and effects in your video:
1. Click on the video in the timeline.
2. Click on the Edit video button above the canvas.
3. In the tools tab, go to the Filters section. Select the filter of your choice.
4. Use the slider to adjust the intensity of the filter.
You can add text and graphics to your video by following the given steps:
1. Click on the Text option in the side bar.
2. Select a text style and click on it to add it to the canvas.
3. Double-click on the text box to edit the text. Change the font, size, colour, and position as needed.

4. Click on the Elements option in the side bar. Search for graphics or stickers and drag them onto the canvas.

You can make your video more dynamic by adding animations to it. Follow the given steps:
1. Click on the text or graphic you want to animate.
2. Click on the Animate button present above the canvas.
3. Select an animation style from the options.
4. Customise the animation duration and delay if needed.
5. Your video is ready. Click on the Play button to watch your video.

Downloading lets you save your video, while sharing helps you show it to others or collaborate on it.
Follow these steps to export your finished video:
1. In the top right corner, click on the Share button.
2. Select Download from the dropdown menu.
3. Choose the video format (MP4 is recommended).
4. Wait for the video to process and download to your device.
Now that your video is ready, you can share it with others by following the given steps:
1. In the top right corner, click on the Share button.
2. Set the sharing options, like who can see your video and if they can edit it.
3. Click on Copy link to get a shareable link or choose how you want to share it, like through email or social media.
Have you ever used the Preview option in any application before finalizing your video?

1 Fill in the Blanks.
a To upload a video, click on tab in the side bar.
b Drag the video to the after uploading.
c Find videos by clicking on and using the Search bar.
d Trim a video by dragging the or
e To share your video, click on the button in the top right corner.
2 Solve the following crossword using the given hints.
Across
1. The button you click to adjust the visual appearance of your video with different styles.
4. A tool used to cut a video into segments.
6. The button you click to start watching your edited video.
Down
2. To change the size of a video.
3. The section where you upload your own video files
5. The format recommended for downloading videos.
1 Video editing involves arranging, modifying, and enhancing video clips to create a project.
2 Key components of Canva’s video editor include the canvas, timeline, text, elements, uploads, and audio controls.
3 You can add text in your video to express your thoughts along with the video.
4 You can add pictures to your video in Canva to enhance the presentation of the video.
5 Adding videos in Canva brings motion to your project, with options to resize and preview.
6 You can insert audio in Canva for background music with volume control.
7 Applying filters and effects can enhance the visual appeal of your video.
8 Animations make your video more dynamic by adding movement to text and graphics.
9 After finishing, you can download or share your video using the Share button.

A. Fill in the blanks.
Hints Create a design Preview Canvas Uploads trim split
1 The option in Canva lets you upload your own videos, images, and audio files.
2 To start a video project in Canva, you first click on the button on the home page.
3 The feature helps you see how your video will look before finalizing it.
4 You can and your videos using basic editing tools in Canva.
5 The is your workspace where you build and design your video in Canva.
B. Tick () the correct option.
1 What does the Timeline in Canva allow you to control?
a The colour of the text b The timing of video elements
c The size of the canvas d The type of filters used
2 Which option in Canva helps you add animations to your video?
a Uploads b Elements
c Animate d Text
3 What file format is recommended when downloading your video from Canva?
a JPG b MP4
c PNG d GIF
4 To add your own video file to a project in Canva, which option should you use?
a Elements b Uploads
c Video Library d Timeline
5 What feature helps you focus on specific details of your video while editing?
a Zoom controls b Filter options
c Canvas d Grid view
C. Who am I?
1 I help you organize the timing of your video elements in Canva.
2 I am the workspace where you build and design your video.
3 I help you add motion to text and graphics in your video.
4 I let you see an overview of all the pages in your video project.
5 I offer a variety of design elements like stickers, shapes, and icons to enhance your video project.
D. Write T for True and F for False.
1 The Timeline in Canva allows you to control when elements appear in your video.
2 The Elements option in Canva is used to add text to your video.
3 You cannot resize or crop videos in Canva.
4 Canva’s Video Library offers a wide range of pre-existing video clips.
5 You can download your finished video directly from Canva. E. Answer the following questions.
1 What do you mean by video editing?
2 How does the timeline help you control the timing of your video?
3 Write the names of basic video editing tools.
4 Why is the Preview option important in Canva?
5 How can you add text to your video? F. Apply your learning.
1 Neha is enhancing her Canva video by adding photos. What are the steps she should follow to resize the video clips effectively?
2 Kavita wants to add background music to her Canva video. Where can she find the audio option to do so?

3 Rahul wants to add captions to his Canva video. Which option should he use to add text?
4 Ravi needs to ensure that his video elements appear at the right times. What tool in Canva will help him manage the timing of these elements?
5 Arjun is an artist. He wants to create a drawing using his imagination. Which option can he use to do so?








You may have noticed that while texting a friend using your smartphone, the predictive text fills in the rest of the phrase even before you get to the end of the sentence. Similarly, while shopping online, you get product recommendations based on your shopping history. Or when you are out for a jog, your smartwatch helps you track your fitness goal by giving useful information like the number of steps. All of this is possible because of Artificial Intelligence (AI), a technology that has transformed how we live, work, and interact with machines around us.
AI can be defined as a branch of computer science concerned with creating intelligent machines that can learn from data, solve problems, and make decisions. It involves the study of principles, concepts, and technologies that enable machines to exhibit human-like intelligent behaviour.

Be it in your classroom, in the marketplace, or at home, you can find applications of AI everywhere. Some prominent fields where AI has made a significant impact are given as follows:
Healthcare Detecting diseases, discovering new drugs, doing remote surgery
Business Preventing fraud, helping us shop by giving recommendations
Education Smart content that helps us learn
Banking Managing money and bank accounts, preventing fraud
Transport Autonomous vehicles, ride-hailing apps, navigation system
Social media Face recognition, content filtration
Security Data security, identification of fraud, threats, etc.
Robotics Heavy industry, robotic surgeries, home assistants
Smart homes Smart devices and connectivity to mobile applications
Artificial Intelligence depends on data for its effectiveness. The quality and type of data fed into AI systems determine how smart they become. AI has three main domains based on the type of data they use:
Data: Data is the foundation of data science. It works with numeric and alpha-numeric data.
Computer Vision: Computer vision works with image and visual data.
Natural Language Processing: NLP works with textual and audio/speech-based data.
Every domain of AI uses a specific type of data that acts as input to the machine and requires a specific method to handle and utilise it.
What is the difference between data science and data analytics?
Data science is an important field in today’s world because we create a lot of data every day—way more than ever before. Whether it is from our phones, computers, or other devices, there is a massive amount of information coming in constantly. To make sense of all this data, we need special methods and tools to process, analyse, and understand it.
Data science is a domain of computer science that helps us learn things from data by using scientific methods, algorithms, and statistics.


Data science combines ideas and methods from statistics, maths, data analysis, and computer science to dig out useful information from huge piles of data collected over time. This makes it easier for us to study all kinds of data—both organised and messy—and turn it into something that we can understand and use in the real world.

In data science, various data formats, such as CSV (Comma-Separated Values), JSON (JavaScript Object Notation), Excel (XLSX), XML (Extensible Markup Language), SQL (Structured Query Language) are used to represent and store different types of data. Did You Know?
Data science can be considered the study of data. It involves the following processes:
• Collecting the data
• Analysing the data
• Using data to solve problems or make data-driven decisions
The problem can be anything from predicting the weather, recommending films on Netflix, finding the fastest route, or even understanding trends on social media. So, data science encompasses various disciplines that focus on data analysis and finding the best possible solution.

Let us take a simple example: Suppose your school wants to find out which sports or games students like the most. Here are the steps they could follow.
Collecting data: The school distributes a survey to every student, asking about their favourite sport.
Analysing data: After collecting responses, they examine the survey results to identify the most popular sport.
Making data-driven decisions: With this information, the school can decide which sport or game to organise more frequently.
Collecting Data
Analysing Data
Making Decisions
This process ensures that decisions are based on data, leading to better outcomes that align with students’ preferences.

Considering the fact that Google processes more than 20 petabytes of data every day, had there been no data science, Google wouldn’t have been the ‘Google’ we know today.
There are different components of data science, which include:
The science of collecting and analysing numerical data in large quantities in order to gain helpful insights.
A tool used to interpret large amounts of data easily through visual representations.
Components of Data Science
MACHINE LEARNING
The study and development of algorithms that enable machines to make predictions or decisions based on data.
DEEP LEARNINNG
A subset of machine learning focused on algorithms that automatically learn and determine the best models for data analysis and prediction.
Data science is everywhere in our daily lives. Here are a few reasons why it is important:
1. Making Informed Decisions: Whether it is a business deciding which products to sell, a doctor determining the best treatment for a patient, or a school planning a new curriculum, data plays a crucial role. It helps people make smart, evidence-based decisions.
2. Solving Problems: Data science helps us find solutions to complex problems. For example, by analysing weather data, scientists can predict hurricanes and help people prepare for them.
3. Creating New Opportunities: Companies like Google, Amazon, and Facebook use data science to develop new technologies and services that enhance our lives, making things easier and more enjoyable.
Collect and analyse data from your classmates about their favourite snacks and drinks. Then, use the data to recommend healthy and popular options for a school event. Identify and write the three processes of data science as per the given scenario:
Collecting data:
Analysing data:
Making data-driven decisions:
Data science is used in many fields and impacts our daily lives in many ways. Let us learn about the applications of data science.
Data science plays an important role in education. It enables personalised learning for students, which improves student outcomes. Additionally, data science algorithms use feedback from students and teachers to enhance personalised learning experiences.
Data science is also used in other aspects of education, such as designing curriculum based on student performance and optimising administrative tasks. For example, identifying students struggling in certain subjects can inform school administration to hire additional tutors and get more learning resources, etc.


Data science plays an important role in the healthcare sector. Data science algorithms analyse medical images to detect symptoms of diseases with high accuracy, helping doctors diagnose their patients in the early stages of a disease. It uses patient data, such as their medical history, to predict which patients are at risk of developing chronic diseases and recommends preventive measures for these diseases. It also helps analyse real-time health data collected through wearable devices to monitor conditions like heart disease. Data science also optimises hospital operations by predicting patient admissions, managing resources better, and reducing wait times. This helps improve overall healthcare services for patients.



Data science makes the entertainment sector more personalised by analysing data to understand what people like or dislike. For example, streaming services like Netflix use data on what films or shows you watch to recommend new films and shows you might enjoy. Music apps like Spotify create personalised playlists by analysing what you listen to more frequently. Video games also use data science to tailor game experiences to your preferences.
Data science has transformed the sports industry by enhancing performance analysis, strategy development, and fan engagement. It helps study players’ performances in terms of various parameters, like speed and technique, to optimise training and game strategies. For example, data on batting patterns and defensive moves in cricket helps coaches develop better game plans. Smart wearable devices help to track athletes’ health and fitness data in real time to personalise training needs and prevent injuries.


Data science helps analyse extensive environmental data to understand patterns, make predictions, and inform policy decisions. For example, data scientists use satellite images and sensor data to monitor deforestation, detect illegal fishing activities, and track wildlife populations. Climate scientists analyse historical weather data to predict climate change impacts and help policymakers plan to decrease its effects. Air quality data collected from sensors helps identify pollution sources and develop strategies to improve air quality. Data science also optimises resource management by predicting water demand and managing renewable energy sources like wind and solar power, contributing to more sustainable environmental practices.
Data science plays an important role in helping stores understand customer preferences and how to improve the shopping experience. For example, when you shop online, have you noticed how websites suggest other items you might like? It is possible through data science. The website uses data science to analyse your previous purchases and suggest similar things. Data science also helps stores maintain stock so they do not run out of items. It also helps to fix prices based on data on what people are willing to pay.







Data science helps make travel safer, more efficient, and more convenient. For example, when we use a navigation app, like Google Maps, data science helps us calculate the fastest route by analysing traffic data from many drivers. Data science also predicts jams and suggests alternate routes to avoid delays in reaching the destination.
Data science helps transport companies optimise their routes and schedules by analysing passenger demand and vehicle availability data. For example, airlines use data science to forecast flight demand and adjust ticket prices accordingly. Data science improves safety by analysing data from vehicle sensors to prevent accidents.




















































































































































































































Data science is used in banks and financial institutions to detect fraud and make smarter money decisions. Banks use data science to analyse transaction patterns or financial data to detect fraud. For example, when using a credit card, data science looks for unusual spending patterns that could indicate fraud. Data science helps predict how much money a company might make in the future based on its past sales data, which helps investors decide whether to invest or not.
Data science also helps banks decide whether to lend money or not by analysing a person’s credit history and money-spending habits. This ensures that the bank is lending money to someone who is likely to pay it back.

Data science helps to make our experiences more personalised and engaging on social media platforms like Facebook, Instagram, YouTube, etc. For example, when you use Facebook or Instagram, data science analyses your previous likes, comments, and shares to show you posts from friends and pages you are interested in. Data science helps detect fake social media accounts and harmful content to make social media safer. Data science helps social media platforms target advertisements to specific groups of people based on their online activities.

Let us perform the following activity to understand how the domain of AI, data, acts as an input to the machine and how the machine interprets and learns from this data. Rock, Paper, Scissors is an interactive game based on data for AI where the machine tries to predict the next move of the participant. It is a digital translation of the basic rock, paper, and scissors game where the machine tries to win by learning from the participant’s previous moves.
Objective: The objective of this interactive AI-based game is for students to build their understanding of the AI domain, particularly focusing on how AI can analyse data to make predictions.
Follow the given steps to explore how this application works.
1. Visit the given link: https://next.rockpaperscissors.ai/
2. The following window appears.

3. Make a paper (palm), scissors (index and big fingers), and rock (fist) in front of the camera, as shown.

4. Now, start playing the AI game. Make your moves (rock, paper, or scissors) and see how the machine reacts if you make moves in a specific order or randomly.
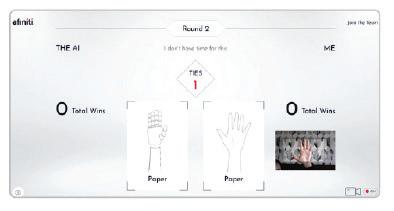
Match the applications of data science with its correct description.
Application Description
Education
Environment Protection
Sports
Finance
Healthcare
Optimising player training and injury prevention through data analysis.
Improving diagnoses and treatments by analysing medical images and patient data.
Personalising learning experiences and improving administrative tasks using student data.
Monitoring pollution, managing resources, and predicting climate impacts.
Detecting fraud and analysing spending habits for better investment decisions.
1 Artificial Intelligence (AI) refers to creating intelligent machines capable of learning, problem-solving, and decision-making like humans.
2 AI applications are prevalent in various fields, including healthcare, business, education, banking, and social media.
3 Data science involves processing and analysing data to extract meaningful insights and support decision-making.
4 The main processes in data science include collecting data, analysing data, and using data to make informed decisions.
5 Data science helps solve complex problems and create new opportunities across industries such as education, healthcare, and entertainment.

6 Data science applications are essential in modern technologies like autonomous vehicles, smart homes, and fraud detection systems.
7 Understanding and leveraging data science is crucial for optimising operations and enhancing the user experience in multiple sectors.
A. Fill in the blanks.
Hints medical images social media transport math intelligent
1 Artificial Intelligence (AI) is a branch of computer science concerned with creating machines.
2 In healthcare, data science algorithms analyse to detect symptoms of diseases.
3 Data science helps companies optimise their routes and schedules.
4 AI applications in include content filtration and detection of fake accounts.
5 Data science combines ideas and methods from statistics, , and computer science.
B. Tick () the correct option.
1 Which of the following is a component of data science?
a Healthcare b Computer vision c Visualisation d NLP
2 Which of the following is NOT an application of data science in education?
a Designing curriculum based on student performance
b Predicting weather patterns
c Personalising learning experiences
d Optimising administrative tasks
3 Data science in sports helps analyse players’ to optimise training.
a Salaries b Performances
c Diets d Social media profiles
4 Data science in transport improves safety by analysing data from a Vehicle sensors b Social media posts
c TV advertisements d Roadside advertisements
5 Data science in retail helps stores understand customer preferences and maintain .
a Inventory b Customer relationships
c Security cameras d Loyalty programs
C. Who am I?
1 I help businesses prevent fraud and provide shopping recommendations.
2 I use data science to create personalised playlists and recommend new songs.
3 I am a data science application that helps predict flight demand and adjust ticket prices.
4 I analyse traffic data from drivers to calculate the fastest route and avoid jams.
5 I use data science to monitor deforestation and illegal fishing activities.
D. Write T for True and F for False.
1 Data science algorithms can help identify pollution sources to improve air quality.
2 AI is limited to use in social media and does not apply to healthcare.
3 Data science in education helps in optimising administrative tasks.
4 AI and data science cannot be used in banking due to security concerns.
5 Data science can help in developing new technologies and services by analysing data.
E. Answer the following questions.
1 What is artificial intelligence (AI)?
2 How does data science contribute to the healthcare sector?
3 Explain the processes of data science.
4 What role does data science play in the sports industry?

5 Describe how data science is used in the entertainment industry.
F. Apply your learning.
1 Your school wants to reduce electricity usage. How could data science help achieve this goal?
2 A hospital wants to improve patient wait times. How can data science contribute to this improvement?
3 A sports team wants to improve their training regimen. How can data science assist them?
4 An e-commerce platform wants to increase customer satisfaction. How can data science be utilised?
5 A city wants to implement a smart traffic management system. How can data science aid in this implementation?








Have you ever wondered how AI assistants like Alexa or Siri listen to your commands and respond? It is possible with the help of a domain of AI, that is called Natural Language Processing
Imagine a situation where you are talking to a computer or a robot. As it is a machine, it will not be able to understand your language. Here, NLP plays its role. NLP makes the machine understand your language and respond to you in a way that makes sense.
NLP helps computers understand us and talk to us like people.
Imagine you have a computer that has NLP. How would you use it to make your daily life easier?

With its wide range of useful applications, NLP transforms our day-to-day interaction with technology. Some of these are given as follows.

Virtual Assistants: This is one of the most common applications of NLP. A virtual assistant is an AI tool that understands and responds to voice commands or text inputs, such as questions and requests, or performs tasks for you. Virtual assistants come in the form of applications or combinations of devices loaded with applications. Siri on the iPhone, Alexa on the Amazon Echo device, and Google Assistant on the Android phone are some of the popular virtual assistants. You can ask a virtual assistant to set alarms, check the weather, play your favourite songs, or even tell you jokes.
Search Engines: Search engines are websites and applications that help you find information on the internet. Google, Bing, Yahoo, etc., are some of the popular search engines. These search engines use NLP to understand the words you type into the search bar and then direct you to relevant web pages. NLP helps search engines comprehend the meaning and context of your search and help you find what you are looking for.



Sentiment Analysis: NLP can be used to analyse the sentiment or emotion expressed in the text. For example, businesses might use sentiment analysis to analyse customer feedback and preferences for their products and services across reviews on social media platforms and product remarks on online stores. This insightful data can help companies enhance their products, services, or customer experiences.
Spam Detection: NLP helps keep your email inbox free from unwanted mails, also known as spam. Spam-detecting algorithms employ NLP to identify patterns or characteristics common to spam emails, such as certain keywords or phrases, and then filter spam from reaching your inbox.


Autocorrect: Autocorrect is a handy tool featured on devices, such as smartphones, laptops, tablets, etc., that allow users to automatically correct misspelt words as they type them. Autocorrect algorithms employ NLP to analyse the context of the text being typed and suggest corrections based on frequently used words and phrases. This is particularly useful when typing on small touchscreen devices.
Speech Recognition: NLP algorithms analyse audio input from speech and transcribe it into text, enabling hands-free interaction with devices, such as smartphones or voice-controlled appliances. Speech recognition technology is used in applications like voice search, home automation, voice dictation, voice biometric, etc. The ‘Read Aloud’ feature in Microsoft Word makes use of NLP algorithms to read all or part of your document, highlighting each word as it is read. You may also dictate your documents in Word. Dictating within Microsoft Word automatically translates your spoken words into text.


Education: Chatbots and virtual assistants that are powered by NLP engage with students in natural conversations, providing guidance and support. NLP enables automated assessment of students’ work and provides them with instant feedback and assistance in identifying areas for improvement, saving educators’ time. ChatGPT, for example, offers personalised learning experiences by adapting to individual learning styles. NLP-powered tools like Grammarly analyse written text for grammatical errors or inappropriate word usage.
Language Translation: NLP facilitates the translation of text from one language to another. A popular example is Google Translate, which uses artificial intelligence to provide instant translations. NLP algorithms analyse the structure and meaning of text and capture the patterns and probabilities of word sequences. This allows them to provide suggestions for improving translations, detecting errors, or offering alternative translations.

1. Visit this link with the help of your teacher: https://www.squibler.io/ai-story-generator
2. You will arrive at this page.
3. Write the idea of your story in the Story Plot section. For example, ‘A librarian finds a book that brings stories to life.’
4. Pick the Creativity Level: Choose between “Realistic” for grounded stories or “Inventive” for imaginative tales. You can also balance the two by placing the slider in the centre.
5. Pick the Length: Select your story’s length from the dropdown menu: Short or Medium.
6. Advanced Settings: Fine-tune your story by adjusting ‘Narrative perspective,’ ‘Genre,’ ‘Character names,’ ‘Setting description,’ and ‘Character description.’
7. Click Generate Story: Click ‘Generate Story’ and enjoy.
Let us look at the example given below;
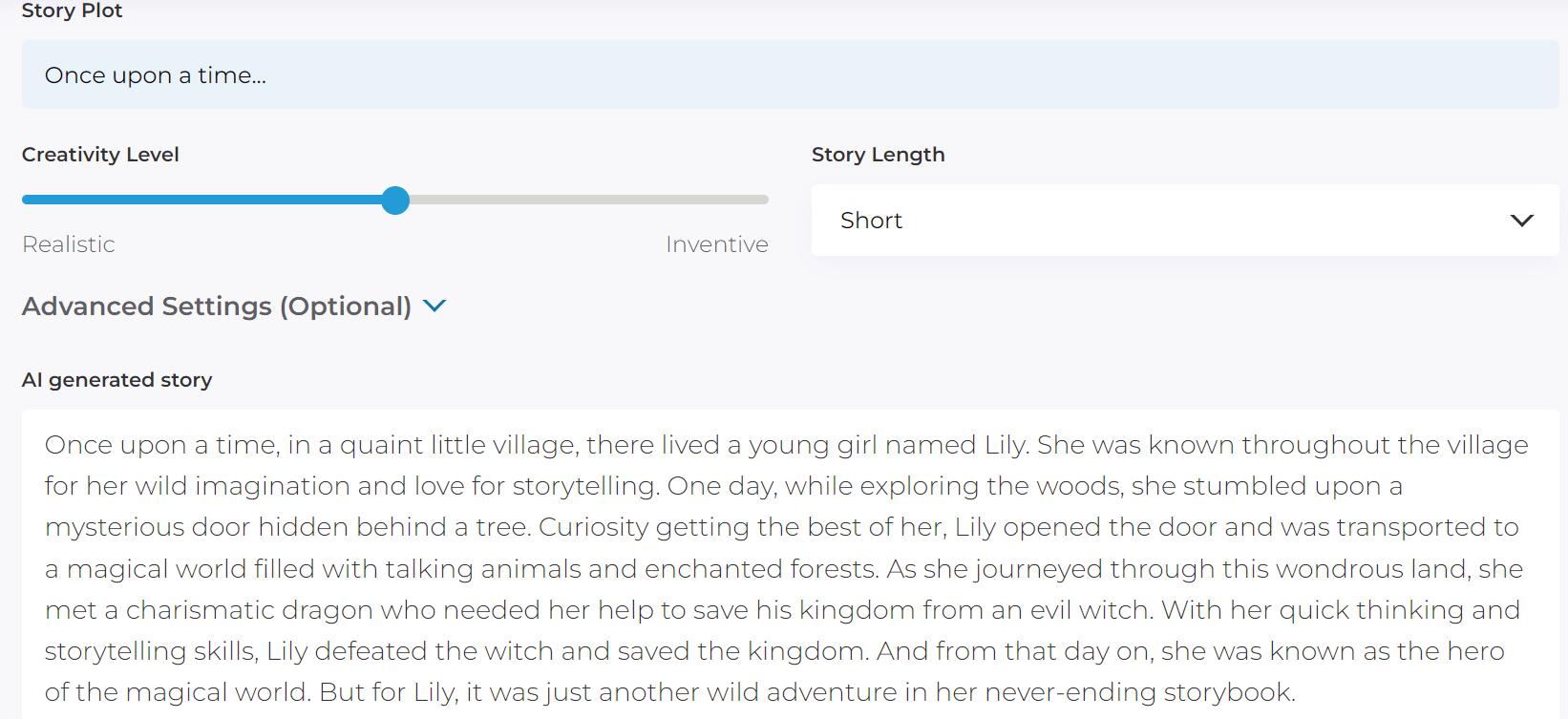

To understand the concept of NLP practically, let us create an app which will convert the input text to speech. For this, we will use the MIT App Inventor. This app will process the input text and convert it to speech.
The MIT App Inventor is an online platform for creating apps for mobile phones and tablets. It is a very easy and simple platform to learn app creation and coding. This platform focuses on teaching everyone, especially young children, to create their own apps.
Follow the given steps to create an app:
1. Visit the following link to open MIT App Inventor: https://appinventor.mit.edu/
2. The following screen appears:
3. Click on the Create Apps! button.
4. A sign-in screen appears. You can use your Gmail ID to login, or you can create a new one.
5. After signing in, the Welcome to App Inventor pop-up box appears. Click on the Continue button at the bottom of the screen.
6. Another screen appears, from where you can choose to view the tutorials or you can start a new blank project.


Continue button
1. Click on START A BLANK PROJECT
2. The Project View window appears.
3. A dialog box appears asking to give a project name to your project.
4. Give an appropriate name to your project, for example, text_to_speech and click on OK.
5. A new project with the same name will be created.

Click here to start a blank project

6. Click on it. The Project View window will open.
The Project View window is divided into four sections:
Palette: Various components are present under different categories in the palette.
Viewer: You can select any component from the palette and drag and drop it on the screen in the Viewer section.
Components: The Components section shows the various components that are placed in the Viewer.
Properties: The Properties section shows the properties of the selected component.


Let us now create the interface of the app.
1. From the Palette section, drag the Button component and place it in the Viewer section on Screen1.

Button 1 added in Components section
2. You can see that the Button1 component has also been added under the Components section.
3. Now in the Properties section, scroll down to the Text property of the button. Replace the text “Text for Button1” with “Text to Speech”.
4. Now, in the Palette section, click on the Media drawer.
5. Select the Text to Speech component and drop it on Screen1.
6. It will not be visible on the screen. However, you can see it below Screen1 as a non-visible component.
The interface of the app is created. Now, let us create the code for it.
The next step is to create a code for the app. To code in MIT App Inventor is very easy and user-friendly. You can create code for your app by using various blocks present in the Blocks Editor

To create the code for your app, follow the given steps:
1. Click on the Blocks Editor button in the right-hand upper corner of the Project View window.
2. The Blocks Editor will open with the Blocks section on the left and the Viewer section on the right.

3. Click on Screen1 > Button1 from the Blocks pane.
4. The blocks related to Button1 will appear.
5. Drag the when Button1.Click block from the Blocks drawer and drop it in the Viewer pane.
6. Similarly, click on Screen1 > TextToSpeech1
7. The blocks related to the Text to Speech component will appear.
8. From the Blocks drawer, drag the call Text to Speech1.Speak block and drop it inside the when Button1.Click block.
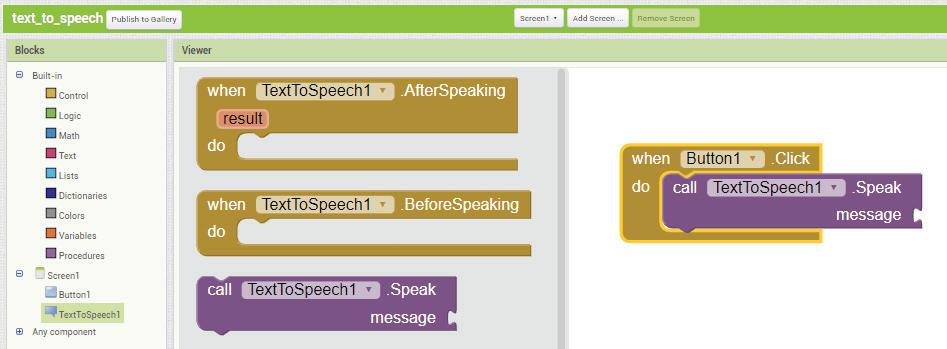
9. Now, from Built-in > Text drawer, drag the “A text string” block and plug it into the socket labelled message
10. Click inside the text string block and type your desired message. For example, “Welcome to the world of coding!”
11. Your app and its code are ready to use.
1. To test your app, you will need a mobile phone.
2. Go to the Google Play Store of your Android phone and download the MIT AI2 Companion App.

3. Install the app by clicking on Install
4. After installation, open the app. You will need to provide a six-character code to connect.
5. To get the code, go to your computer where you have created your app.
6. Go to the Connect menu and select the AI Companion option.


You can scan this QR Code to get the MIT AI2 Companion App on your mobile phone.
7. A Connect to Companion window will open with a six-character code.


You can now fill in this six-character code on the mobile phone app.
1. The app will now open on your mobile phone.
2. Click on the button that you have created.
3. You will be able to hear the message that you have provided in the app code, that is “Welcome to the world of coding!” Welcome to the world of coding!

Answer the following questions.
1 How do search engines use NLP?
2 What is sentiment analysis and how is it used?
3 How does NLP assist in spam detection?
1 Natural Language Processing, or NLP, makes the computers understand the human language in text and spoken form.
2 A virtual assistant is an AI tool that understands and responds to voice commands or text inputs, such as questions and requests, or performs tasks for you.
3 Search engines are websites and applications that help you find information on the internet.
4 Google Translate is an AI-powered translation app that allows users to translate text into different languages.
5 NLP can be used to analyse the sentiment or emotion expressed in a text.
6 Autocorrect is a handy tool featured on devices, such as smartphones, laptops, tablets, etc., that allows users to automatically correct misspelt words as they are being typed.
7 MIT App Inventor is an online platform for creating apps for mobile phones and tablets.
8 The Project View window of MIT App Inventor is divided into four sections, Palette, Viewer, Components, and Properties.
Fill in the blanks.
1 is a handy tool featured on smartphones that allows users to automatically correct misspelt words as they are being typed.
2 on iPhones is a popular virtual assistant.

3 NLP helps keep your email inbox clean and clear from unwanted mails called 4 is an AI-powered language translation tool.
5 is the domain of AI that deals with the language-based interactions between a machine and a human as well as between two machines.
B. Tick () the correct option.
1 NLP helps comprehend the meaning and context of your search and find what you are looking for.
a Search Engines b Home Automation
c Spams d Sentiment Analysis
2 Which of the following application uses speech recognition?
a ChatGPT b Grammarly
c Spam Detection d Dictating to Microsoft Word
3 What is the full form of NLP?
a Natural Language Processor
b Natural Language Processing
c Natural Language Program d Neuro Language Processing
4 Which of the following is a potential application of sentiment analysis using NLP?
a Chatbots tutoring students
b Autocorrecting misspelt words
c Assessing customer feedback on products
d Asking a virtual assistant to check the weather
5 You can ask to play your favourite song.
a Siri b Alexa
c Google Assistant d All of these
C. Write T for True and F for False.
1 ChatGPT is an NLP-powered tool.
2 NLP algorithms are trained on vast amounts of text data.
3 Virtual assistants come in the form of applications only.
4 E-commerce sites make use of sentiment analysis to know customer’s preferences.
5 NLP can be used to analyse written text for grammatical errors.
D. Answer the following questions.
1 Define NLP.
2 What are virtual assistants?
3 How does NLP contribute to providing a personalised learning experience?
4 How can NLP help businesses know their customer preferences?
5 What is the purpose of the MIT App Inventor?
F. Apply your learning.
1 Sita’s friend Anita is visually impaired. Sita sees Anita working on MS Word and notices that the text in the file is being read aloud to Anita. What will Anita’s answer be when Sita asks her about this interesting feature in MS Word?
2 Sneha notices that whenever she makes a spelling mistake while texting, the messaging app automatically corrects the word. Which application of NLP do you think is being used here?
3 Rohan is amazed to see how his friend uses Alexa to play his favourite songs with voice command. He asks what else this virtual assistant can do besides playing his friend’s favourite songs. What do you think Rohan’s friend will tell him?




Test Paper 1 (Based on Chapters 1 to 4)
A. Fill in the blanks.
1 A is a way to connect computers using communication devices so that they can exchange data and resources with each other.
2 is the term used to describe the ethical and responsible use of technology.
3 is the name of a famous cryptocurrency.
4 apps are virtual platforms where you can meet and talk to your friends, and even make new ones.
B. Tick () the correct option.
1 occurs when the same piece of data exists in multiple places.
a Data redundancy
c Data centralisation
b Data inconsistency
d Data recovery
2 is the practice of constantly following someone’s online activity, mostly with the intention of frightening or upsetting them.
a Cyberbullying
c Plagiarism
b Cyberstalking
d Phishing
3 apps are programs you install on your phone to make whatever you want to do more fun.
a Web
c Mobile
C. Write T for True and F for False.
b Desktop
d None of these
1 Protocols refer to a set of rules which are to be followed to send data through a network.
2 Cyber ethics may conflict with people’s desire for being anonymous online.
3 A blockchain is controlled by a single central authority.
4 Google Drive is an example of a gaming app.
D. Answer the following questions.
1 What does NIC mean?
2 What is a blockchain?
3 What are hybrid apps?
4 Mention some apps based on their usage.
E. Apply your learning.
1 Richa is confused between a hub and a switch. Help her by explaining each concept.
2 You receive a message that says that you have won a free vacation that can be accessed through a given link. Should you trust that message and click the link?
3 Rashi wants to know about the transparency feature of blockchain. Explain the concept to her.
4 Kashika has installed an app on her phone that was not loaded in the phone already when she bought it. What type of app has she downloaded?

A. Fill in the blanks.
1 is a technology that overlays digital content—like images, text, or animations—onto the real world.
2 The SQL commands that are used to insert, delete, or update data in the table of a database are called commands.
3 The option offers a wide range of design elements, including photos, videos, stickers, shapes, and icons.
4 NLP, also known as , helps keep your email inbox free from unwanted mails.
B. Tick () the correct option.
1 The is a virtual space where people interact in real-time using augmented and virtual reality technologies.
a 3D Printing
c Metaverse
b Biotechnology
d BCI
2 data types are used to store a numeric value in a field column.
a Number
c Date
b Character
d Time
3 A is an AI tool that understands and responds to voice commands or text inputs, such as questions and requests, and also performs tasks for you.
a Language translation
c Sentiment analysis
C. Write T for True and F for False.
b Spam detection
d Virtual assistant
1 Drones are used for tasks such as aerial photography, surveillance, and package delivery.
2 HDBMS stores data in a network-like structure.
3 Video editing involves arranging, modifying, and enhancing video clips to create a project.
4 The MIT App Inventor is an online platform for creating apps for mobile phones and tablets.
D. Answer the following questions.
1 What is the primary purpose of BCI?
2 Describe the key role of a DBMS.
3 What is data science?
4 What is speech recognition?
E. Apply your learning.
1 Simran wants to know the role of robots in the medical field and how they make our lives easier. Help her understand this.
2 Anuj wants to know the difference between RDBMS and OODBMS. Explain them to him.
3 Bhavna is unaware of the role of data science in the field of sports. Write any two roles to inform her.
4 Raghav wants to translate a paragraph from English to French. Which application can he use to do this?

This book embodies the principles outlined in the National Curriculum Framework (NCF) and the National Education Policy (NEP) 2020. It unveils the world of computer science through a unique and captivating pedagogical approach— seamlessly integrating curriculum content into the mesmerising adventures of Mel and Conji, fictional figures hailing from the enchanting world of Avora. Our aim is to prepare learners for the dynamic and technology-driven landscape of the 21st century, equipping them with the essential skills they need to thrive in an ever-evolving world.
• NEP Tags: To showcase alignment with NEP skills and values.

• Explore More: QR codes to explore an exciting application of the concept.
• Discuss: Questions to trigger engaging group discussions in the classroom.
• Think and Tell: Probing questions to stimulate thinking at an individual level.
• Did You Know? Interesting facts related to the application of a concept.
• Fun with AI: Engaging AI activities to explore and apply AI concepts in practical ways.
• Do It Yourself: Milestone exercises to practice specific concepts.
• Chapter Checkup: A pool of questions catering to all topics and skills covered in the chapter.
• Test Papers: Designed to evaluate understanding of core concepts and application of skills.
Uolo partners with K-12 schools to provide technology-enabled learning programs. We believe that pedagogy and technology must come together to deliver scalable learning experiences that generate measurable outcomes. Uolo is trusted by over 15,000+ schools across India, Southeast Asia, and the Middle East.
ISBN 978-81-978912-8-1

hello@uolo.com
Not to be sold separately