
Award Winning World’s Fastest Growing Cybersecurity Company















The Best Ai-Powered Threat INtel PLATFORM
• Uncover hidden threats.
• Predict and prevent attacks.
• Empower informed decision-making.
• Stay ahead of evolving risks.
• Secure your digital ecosystem.
See Cyble Vision in Action






36 Transfer Mayhem: Why Do We Fail in Vulnerability Management?
46
The Moveit Cybersecurity Regulations: The Half-Yearly Report Card
52
Will We See An Increase In AI-Generated Cyberattacks?



58
Does Scambaiting Actually Deter Scammers?

64
Devastating Cyber Attacks and Data Breaches Unleashed Chaos in the First Half of 2023


82
Anonymous Sudan’s Hacktivism: A Genuine Cause or Just a Facade?
90 Cybercrime Legislation and International Cooperation: Closing the Enforcement Gap
DIGEST

Augustin Kurian Editor-in-Chief editor@thecyberexpress.com
Chandu Gopalakrishnan Executive Editor chandu@thecyberexpress.com
Avantika Chopra Associate Editor avantika@thecyberexpress.com
Vishwa Pandagle Journalist vishwa@thecyberexpress.com
Ashish Khaitan Journalist ashish@thecyberexpress.com
Rajashakher Intha Director - Marketing & Technology raj@thecyberexpress.com

Ashish Jaiswal Conference Manager ashish.j@thecyberexpress.com
Priti Chaubey Content Strategist priti.c@thecyberexpress.com
Ravi Gupta SEO Analyst ravi@thecyberexpress.com
Vittal Chowdry Design Lead vittal@thecyberexpress.com
As we reach the midpoint of 2023, we find ourselves caught in the maelstrom of rapid technological advancements and an equally accelerating pace of cybersecurity threats. The Cyber Express has always been at the forefront of sharing the latest, most critical developments in the cyber world, and this issue is no exception.

To kick off our half-yearly round-up, we present a profound conversation with Ian Beacraft, founder and Chief Futurist at Signal and Cipher. Beacraft offers unique insights into the impending transformation of our workplaces and lives as AI evolves. With the promise of advancements comes the question: What does this AI revolution mean for our security infrastructure?
Complementing Beacraft’s futurist perspective, we delve into the here and now with Tom Van de Wiele, Principal Technology & Threats Researcher at WithSecure. From penetrating AI systems to dealing with zero-day vulnerabilities and simulating advanced persistent threats (APTs), Tom emphasizes the importance of aligning attack strategies with the threat actor being emulated while
maintaining ethical testing practices.
In our quest for cybersecurity awareness, we spotlight a recurrent yet ever-evolving threat - Drone hacking. In the wrong hands, unmanned aerial vehicles have become tools for privacy invasion and illicit data gathering. Our piece lays bare the present concerns and explores potential countermeasures.
However, the crown jewel of this issue is our indepth coverage of the Cl0p Ransomware Gang. Our cover story delves into their recent global rampage exploiting MOVEit. Detailed discussion on specific vulnerabilities like CVE2023-34362 and CVE-202335036, as well as a dissection of flawed vulnerability management, offer an alarming picture of the escalating cyber threats.
To comprehensively understand the current cybersecurity landscape, we examine the devastating cyber-attacks and data breaches that have unleashed chaos in the first half of this year. From dissecting attack strategies to understanding their far-reaching impacts, our retrospective presents a holistic view of the cyber threat landscape of 2023 so far.
Regulation, a critical aspect of cybersecurity, also receives due attention in this issue. We explore ongoing and upcoming privacy and data usage regulations of 2023. These discussions offer invaluable insights into the legislative attempts to counter growing cyber threats and ensure data privacy.

Lastly, we turn our gaze toward the controversial figure of Anonymous Sudan. Known for their hacktivist endeavors, their activities spark debates on the legitimacy of their cause. Is it a genuine pursuit of justice or just a facade? We delve into this complex narrative, leaving our readers to ponder the gray areas of hacktivism.
This issue of The Cyber Express is both a mirror and a telescope, reflecting the state of cybersecurity today and offering a glimpse of what the future holds. We hope the insights, analysis, and thoughtprovoking discussions will help you navigate the choppy waters of cybersecurity.
Most importantly, We welcome your feedback at editorial@thecyberexpress. com
In an enlightening conversation with The Cyber Express, Ian Beacraft, the founder and Chief Futurist at Signal and Cipher, discussed the impending transformation of our workplaces and lives in the face of advancing artificial intelligence (AI).
With a keen eye towards the future, Beacraft is helping businesses navigate through the fast-paced tech landscape, ensuring they stay at the forefront of innovation. His discourse reveals that the imminent shift will likely rewrite job descriptions rather than render them obsolete.
Ian embarked on an enlightening conversation about the transformative impacts of AI in our lives, its potential risks, and the broader implications of artificial general intelligence (AGI).
Beacraft’s insights, drawn from his rich experience in the AI landscape, traversed a wide range of topics - from the phenomenon of ‘technophilia’ and the advent of deepfake technology to the looming challenges in cybersecurity and the future of AGI.
The discourse was an intriguing exploration of AI’s complexity, evoking thoughtful consideration of our evolving relationship with this technology, the inherent risks and possibilities it presents, and the role we play in shaping its future.
The conversation served as a powerful reminder of the dynamic, participatory nature of our interaction with AI, nudging us towards more informed and proactive engagement with this transformative force.

The fear of job displacement due to AI has been pervasive. Beacraft counters this fear by referencing historical episodes where technology has been initially perceived as a threat to employment. He uses the advent of the internet as an example. There were fears that this new technological advancement would result in the loss of traditional jobs. While it did reshape the job market, it also opened up a vast array of new opportunities that weren’t conceivable before.
Similarly, he draws a parallel with the emergence of automobiles. While automobiles rendered the jobs of horse caretakers obsolete, they also opened up new industries, such as suburban housing and recreational skiing.
The main point Beacraft underscores here is our limited vision. We can clearly identify jobs that AI might render obsolete, but it’s harder to envision the new markets, roles, and opportunities that AI might spawn.
The conversation about AI, according to Beacraft, should be centered more on augmentation than on automation. The perspective we need to adopt is one of seeing machines as tools that empower us to create more efficiently and effectively.
AI has been automating tasks, many of which were once considered solely within the domain of human capability, including creative outputs such as art and music.
However, Beacraft emphasizes that the value of human input goes far beyond mere efficiency. He cites examples of work that thrives on human inefficiencies, such as scientific inquiry and experiential creativity. These fields continue to require and value human input, allowing for the potential of more profound and innovative contributions.
Beacraft strongly believes that AI is more likely to redefine jobs than to eliminate them. This shift will inevitably influence how we perceive and define our professional identities. We often tie our self-worth to our work roles. If that role suddenly changes due to AI, the psychological impact could be considerable. However, if we view these changes as an expansion of our abilities and potential, we can adapt to and even thrive amidst the transformation.
In Beacraft’s envisioned future, AI could enable individuals to perform multiple roles within an organization, breaking the boundaries of one specific job description. This shift could be disruptive initially, as we navigate uncharted waters. Yet, in the long run, it could lead to a workforce that is more dynamic, innovative, and flexible.
AI has brought the potential for technological leaps, but its rapid evolution also harbors risks, notably in the form of deepfakes and social engineering.

Technophilia – our increasing fascination with technology – is paving the way for new types of interactions and relationships with AI. This has manifested in various forms, from the romanticized AI relationships depicted in films like “Her” to deepfake representations of people, which are becoming increasingly convincing.
As explained by Ian Beacraft, these emerging dynamics bring with them significant potential risks, particularly in cybersecurity. The attack surface, or potential vulnerabilities within a system that can be exploited by malicious entities, is growing at an alarming rate. Social engineering –the psychological manipulation of people into divulging confidential information – has also become a far more prominent threat with the advent of AI.
For instance, Beacraft mentions the potential danger of AI-enabled automated agents that can deploy malicious code without human intervention. However, an even more frightening prospect might be the ability of AI to mimic voices or personify important figures in one’s life, thereby tricking individuals into revealing sensitive information or performing harmful actions. This nefarious use of deepfake technology is no longer a hypothetical concern; incidents have already been recorded, highlighting the urgent need for countermeasures and public awareness.
Amid this surge in AI technology, the conversation about the development of Artificial General Intelligence (AGI) – machines capable of performing any intellectual task that a human can do – is heating up. This prompts society to ponder the implications of such an advancement.
The discourse surrounding AGI often oscillates between utopian visions of a bright AI-enhanced future and dystopian nightmares filled with rogue superintelligent machines.
Beacraft challenges this binary view, arguing that both ends are flawed; the utopian view tends to blind us with over-optimism, while the dystopian perspective paralyzes us with fear.
Instead, Beacraft advocates for a practical approach, encouraging us to engage with the technology on a dayto-day basis and participate in shaping its evolution.
The future, he argues, isn’t an inevitable fate that happens to us, but something that we actively create. We can’t simply be spectators; we must step into the game, don the metaphorical “kit,” and play our part.
By interacting with AI technologies like OpenAI’s GPT-3, we gain firsthand insights into the reality of AI and are better equipped to have productive conversations about what the future should look like.
As society continues to grapple with the benefits and threats of AI, it’s essential to remember that the path won’t be a straight line to a utopian future; there will be wins and losses, but active participation can steer the trajectory toward a desirable outcome.

The path towards complete AI integration might resemble a rollercoaster ride with its share of rises and falls. Periods of job losses might occur, followed by phases of robust growth, as we grapple with and adapt to the new reality. But, as we have always done throughout history, we will adapt, evolve, and eventually find ways to leverage the new technology to our advantage.
Beacraft’s forecast of the future serves as a reminder that the impending AI revolution isn’t just about survival – it’s about harnessing AI’s potential power to redefine our relationship with work. Rather than cowering in fear of job loss, we should see AI as a tool that can unlock new levels of human potential.
This understanding of our evolving relationship with work will require a shift in societal thinking.
This shift in thinking is about more than just our own individual adaptation or the survival of
businesses. It also invites a broader societal discussion about our relationship with work and the value we attribute to it. Currently, in many societies, including the U.S., jobs have come to define who we are. We usually introduce ourselves to others by mentioning our professional role. But what happens when that role becomes fluid, adaptable, and multifaceted due to AI?
As AI redefines job descriptions, our cultural values around work will need to shift accordingly. The monolithic concept of a lifelong, single-track career might give way to a more flexible understanding of professional life. It may also challenge us to explore our worth beyond our professional roles, focusing more on our contributions to society, our learning capabilities, and our adaptability.

What Beacraft elucidates is that the true value of AI lies not in its capacity to replace human labor but in its ability to empower and augment human potential.
He says, “When you take a look at what augmentation can happen with jobs, that’s where exponential growth happens. You don’t cut your way to growth, you cut your way to efficiency. But growth comes by giving people new potential powers and saying, let’s create together.”
By harnessing the capabilities offered by AI, we may be able to do far more than we previously thought possible. Imagine being your own accountant, project manager, and artist, all in one. This is the vision that Beacraft presents: an evolving workforce that utilizes AI to amplify and diversify its skills, not a bleak landscape of automation and job loss.
The path to this future is not likely to be smooth. As Beacraft warns, “We are in for a very up and down ride.” The back-and-forth fluctuations between job loss and new job creation may cause unrest and uncertainty. But we must remember that these are the growing pains of an emerging new world, a world where AI enhances rather than threatens human potential.
In conclusion, the revolution in artificial intelligence (AI) is reshaping our world in both visible and invisible ways, creating a profound ripple effect across a broad spectrum of disciplines. The concept of ‘technophilia,’ our love and acceptance of technology, has become a significant factor in this transformation, as we’ve started to integrate AI into the most intimate aspects of our lives.
From forming the basis of synthetic relationships to becoming an integral part of our daily interactions, AI has established a presence that is increasingly hard to ignore. However, this transformative evolution is not without its perils. As we grow more reliant on AI, the technology itself becomes a double-edged sword with the potential to cause as much harm as it can bring benefit.
For instance, the emergence of deepfake technology and advanced social engineering techniques presents a sobering example of how AI can be exploited. These cybersecurity threats have already demonstrated their potential to wreak havoc, exemplified by cases

of AI-fueled scams and identity thefts. They underline the urgency for robust, adaptive defenses, improved regulatory measures, and comprehensive public education campaigns.
In the midst of these challenges and opportunities, the dialogue surrounding Artificial General Intelligence (AGI) has gained considerable momentum. Too often, this conversation is bifurcated into utopian and dystopian narratives, neither of which is particularly helpful or constructive. These extreme views can distort our understanding of the implications of AGI and impair our ability to prepare for its rise effectively.
As Ian Beacraft suggests, a more pragmatic approach would involve active engagement with these transformative technologies. By involving ourselves in their evolution, we have the chance to gain firsthand experience and knowledge of AI’s capabilities and limitations. More importantly, we can exert our influence over its trajectory, ensuring that its development aligns with the broader interests of society.
Our interaction with AI isn’t a mere passive relationship. We’re not mere spectators of the technological changes unfolding before us. Instead, we’re participants in this grand experiment, shaping and being shaped by the technological advances of our time. The future, as it stands, is not a fait accompli that merely happens to us; it is a fluid and mutable reality that we have a hand in creating.
Thus, as we stand at the cusp of an AI-driven era, it’s crucial that we take an active role in shaping its landscape. The road ahead is not a straight, preordained path to a utopian or dystopian future but a winding journey full of uncertainties, opportunities, challenges, victories, and setbacks. By accepting this reality and remaining actively engaged, we can better harness the potential of AI while adequately addressing the risks associated with its rise. The future of AI is, indeed, a collective responsibility, and navigating it successfully requires informed participation from all of us.
In a recent interview with Tom Van de Wiele, Principal Technology & Threats Researcher at WithSecure, The Cyber Express gained valuable insights into the world of cyber security and penetration testing.
With over 20 years of experience in the field, Tom has become an expert in offensive security, red team operations, and targeted attack simulations. His extensive knowledge and expertise allow him to uncover vulnerabilities and devise innovative methodologies to breach systems during cyber attack simulations.
Tom emphasizes the importance of aligning attack strategies with the threat actor being emulated and maintaining ethical practices throughout the testing process. His expertise extends to testing applications with advanced AI components, dealing with zero-day
vulnerabilities, and simulating advanced persistent threats (APTs).
By conducting red team operations against well-defended targets, Tom reveals how understanding human behavior and exploiting potential weaknesses can lead to successful attacks.
His experiences shed light on ransomware gangs’ evolving behaviors and strategies, and he shares how his team adapts to their techniques during penetration testing exercises.
Overall, Tom’s expertise and practical insights demonstrate the crucial role of penetration testing in improving organizations’ cybersecurity readiness against real-world threats.

Can you share an instance where you had to leverage a relatively unknown or underutilized methodology to penetrate a system during a cyber attack simulation?

Just like any real coordinated cyber attack that is serious about getting in, so we split up our attacks using different techniques in order to either establish a false narrative or trust relationship that can later be abused, or to avoid detection altogether.
Some of those components can involve less traditional approaches, but always within the expectation levels of the customer and the intended level of sophistication of the threat actor level we need to emulate.
For example, it happens that once we have breached the network, we need to elevate our privileges, but the technical attack surface might be very small. In this case, we have to create our own miniature version of a supply chain attack where, e.g. software utilities that we came across on a company’s network could be altered by anyone. Once the software utilities received my specific and controlled backdoor, I started creating fake but realistic support case situations that would involve using those software utilities for support staff/ administrators/the target individuals to run, and thus have their systems backdoored so we can re-use their access to accomplish our goal.
In other cases, it might involve more obscure ways of hiding the data you have stolen and exfiltrating it over a longer period of time in order to avoid detection using a mix of covert channels e.g. sending out a few hundred meeting requests to an external e-mail account that all
contain small parts of the encrypted target data inside. It could be converting the data into a series of QR codes and making a movie out of it that is then shared over an outbound Zoom call.
Keep in mind that this is not a “carte blanche” or free for all. The methods of attack need to be aligned with the threat actor we are trying to emulate, and need to be in accordance with the attack scenarios we are carrying out to see if they can lead to a successful compromise and whether or not the customer and their security partners are able to detect and respond to the attack.
For most detection methods, including AI powered ones (although these are rare), the same trade-offs need to be made: what is considered normal behaviour versus what is considered malicious?
If enough baseline behaviour and data is generated to fool the detection into thinking the actions were non-malicious, then the attacker wins. It’s all about skewing and poisoning the model to the point where you can start moving the needle of what is acceptable behaviour.
Examples could be flooding the sensors with fake data or creating overt false positives to the point where you get detection fatigue, allowing attackers to slip under the radar of a “new normal”.
Could you talk about a time when you had to exploit a zero-day vulnerability? When conducting penetration tests, how do you ensure that you achieve a balance between thorough testing and avoiding unnecessary disruptions or damage to the client’s operational capability?
Exploiting zero-day vulnerabilities is usually not part of a red team or penetration assignment. By definition, using zero-day vulnerabilities will involve a degree of uncertainty and, thus, risk where the application’s behaviour will be unknown.
In the case of a networked service, it might cause the application to malfunction, corrupt or destroy data, or might render the application itself unusable. As red teaming involves real-life production systems, the risk has to be kept low and in accordance with what was agreed with the customer.
In addition, finding and developing a stable exploit for a zero-day vulnerability takes time that could be spent on testing efforts that offer more value to the company that is being tested, as far as testing their resilience and validating their investments in the form of training, technology and process flows.

In some specific cases an exploit can be tested on a test environment as part of a separate spin-off project to
assess whether or not the detection strategy and tooling would be able to pick it up. In other cases, the cyber attack kill-chain is “de-chained” by assuming that a zero-day exploit was used and supplying the testers with access that would have been obtained if an exploit was triggered, and using that as the starting point unbeknownst to the blue team.
In this way, the detection and response process, along with the people and technology, can be evaluated without causing unnecessary risk. Sometimes, we have received clearance to be able to exploit a number of zero-day vulnerabilities under very specific circumstances, but it should be regarded more as an exception than a rule.
What was the process, and how did you ensure it was reported and handled ethically?
During testing, we come across vulnerabilities all the time that are new or unknown. There we work together with the customer and the vendor or integrator to ensure that the disclosure process is performed ethically while we provide the customer mitigation paths to lower the risk during the waiting period for receiving a vendor update or patch.
Could you explain how you would go about conducting a red team operation against a well-defended target with an established security program, including blue team operations and state-of-the-art intrusion detection systems?
I have performed red teams that have had the head of the incident management team, executive management or an actual technical third party responsible for security operations as my targets.
They all depend on human beings that want to do the right thing, and on internal communication, company-to-company communication, computers and software.
If you are able to think like your target as far as what they need to function and what makes them successful, then you can find and invent scenarios that will be able to undermine and attack whatever it or whom you are trying to target.
This is where the intersection between technical hacking and behavioural psychology becomes more an art than a practice. The more you know how companies function and how they are built up, the more insight you will have in where the cracks might exist that can be exploited or might lead to compromise.
How do you simulate advanced persistent threats (APTs) in your penetration testing exercises?

Adversary simulation always needs to be aligned with the threat actors you are trying to mimic and thus, you need to be able to know about and offer techniques that are at least at the same level as the real cyber criminals e.g. organized crime groups or nation states.
That means for every part of the “cyber kill-chain”, you need to be able to know and document how real criminals operate and how they try to avoid detection while still keeping the scenarios realistic.
That implies being able to have cutting-edge attack techniques that are constantly being developed, being able to set up public but controlled Internet-facing attack infrastructure, actively developing new command and control channels and staying on top of detection strategies that you might be running into.
For some good examples of this, I recommend this 3-part series I wrote about how this actually works in practice from beginning to end while combining physical and Internet based attacks just like a real APT: Red Team Diaries: SE01 E01 – Physical | WithSecure™
How do these simulations help improve an organization’s readiness against realworld APTs?
These simulations help organizations exercise their capabilities and allow them to spot weaknesses or misalignments in their processes, tooling or training.
It means being able to validate your security investments and test them out in real-life scenarios but without the real impact and risk of a real APT-level attack. Not only will it help build resilience to be able to respond to real incidents, but it also strengthens and specializes the team in developing a nose for existing and newer indicators of compromise so that incidents can be handled before they can play out.
Could you describe a time when a penetration testing or red teaming exercise led to an unexpected discovery or an unusual vulnerability in a system? How did you proceed in such a scenario?

Every red team will uncover IT assets without an owner, processes that were languished, as well as areas of shared responsibility where multiple parties all thought the other parties would step in. But not only that, sometimes you come across highly sensitive data that was accidentally leaked outside its intended environment, test or demo environments, with all production data available but with little to no security controls or third parties having access to critical data that was hidden from sight as part of fraudulent or criminal behaviour.
The most important factors here are to be able to establish what it is you are looking at, being able to document how it was uncovered and keeping your customer contacts close in a way that the situation can be handled with the proper discretion and urgency.

When it comes to interaction with the Internet and the outside world, it is beneficial for an adversary to make the target employee or defenders believe that they are, in fact, communicating with a legitimate entity or company. Especially when it comes to the initial breach in making someone go to a website or open a document, but also afterwards once control has been established, and a command and control communication channel has to be kept open.
The latter can be done covertly but will involve a higher cost for the attacker in trying to evade detection. So, in order to bring down the cost, many cyber attackers try to hide in the open by using overt communication channels and endpoints, trying to fool detection and response teams. This is particularly true when it comes to ransomware gangs that are leveraging supply chain attack methods like we saw with the 3CX and SolarWinds breaches.
We utilize overt and covert command and control channels and try to adapt our attacker infrastructure, e.g. “watering hole” servers, to what the target organization might be using.
If the company is heavily dependent on a range of cloud services, then we try to mimic those in the way they look and communicate in order to try and muddy the waters and stay hidden.
That means doing a lot of reconnaissance on the target organization as well as the third parties they use in order to try and blend in. This is also the reason why in the majority of cases, we have to inform the customer that we have breached their network because we are able to walk within the shadows or hide in plain sight unbeknownst to the defenders.

 - By Avantika Chopra
- By Avantika Chopra
How easy is it to buy a drone? As simple as swiping your card or putting in your details to make that purchase. Ta-da, you are now a proud owner of a drone.
However, drones pose several risks that the makers may not have anticipated. Or maybe they had!
In recent years, drones have been considered an alternative for various purposes across industries, including using unmanned aircraft in disaster relief, rescue operations, media, military, and logistics.

So, yes… in the near future, you may have a flying vehicle delivering your Amazon package. So, what’s the downside, you may ask… That’s where things get dark.
Anyone can buy a drone. This means anyone, including criminals, can exploit the very technology created for the benefit of humankind.
But that isn’t something new, right? For years, technology has been abused by law-breakers and wrongdoers who know how to manipulate it for their own benefit. Just like a sly malware, unmanned
aerial vehicles (UAVs), in the hands of a miscreant, have the ability to breach privacy without detection. Drones can discreetly gather data and capture images without attracting undue attention.
You may not even be aware of a drone flying over your backyard, mapping and scanning the very area you feel secure in. However, privacy is not the only concern.
In October 2022, hackers were able to target and compromise the systems of a US financial services company using DJI drones.
By safely landing the drones on the company’s roof, the cybercriminals deployed the modified Wi-Fi Pineapple devices to capture network credentials. By using stolen credentials, the hackers could access the internal networks and steal sensitive data. The attack reportedly significantly impacted the company’s operations.
While the company’s name was never disclosed, security researcher Greg Linares detailed how the hackers could conduct the security breach using drones in a series of tweets.
“An east coast company specializing in private investments detected unusual activity on their internal confluence page originating on their own network. During the incident response, they discovered that the user whose MAC address was used to gain partial access to their WIFI was also logged in from their home several miles away. The team deployed embedded WIFI signal tracing and a Fluke system to identify the WIFI device,” the post began.
“This led the team to the roof, where a ‘modified DJI Matrice 600’ and a ‘modified DJI Phantom’ series were discovered. The Phantom was carrying a ‘modified Wifi Pineapple Device’,” the tweet continued.
Linares further explained that the Matrice was found to be carrying a case containing Raspberry Pi, several batteries, a GPD mini laptop, a 4G modem, and another Wi-Fi device.
Moreover, the DJI Phantom drone had originally been used a few days prior to intercept a worker’s credentials and WIFI. This data was then hard-coded into the tools that were deployed with the Matrice.
“These tools were used to directly target the internal confluence page in order to target other internal devices from credentials stored there,” Linares stated.
In an interview with The Register, Linares noted that drone technology had come a long way. “This paired with drone payload options getting smaller and more capable – e.g., Flipper Zero kit – ... make viable attack packages that are reasonable to deploy,” Linares said.
In his post, Linares called this incident to be the third “real-world dronebased attack” he encountered in the past two years.
And there are more to come.
If cybercrime were to be measured as a country, then it would be the world’s third-largest economy after the U.S. and China, noted a report by Cybersecurity Ventures published in October 2022.
The global cybercrime damage cost is predicted to grow by 15% per year over the next three years, reaching $10.5 trillion USD annually by 2025, up from $3 trillion USD in 2015, the report stated.
Simultaneously, the drone industry has experienced a significant surge in growth.
According to the latest report by Fortune Business Insights, the global commercial drone market growth was valued at $8.77 billion in 2022 and is projected to grow from $10.98 billion in 2023 to $54.81 billion by 2030.

The report highlights how drone services are displacing traditional legacy services in the commercial sector.
Many renowned organizations are investing in designing and developing lightweight commercial drones tailored for a wide range of applications. These include medical emergency transportation, inspection and maintenance, filming and photography, mapping, surveying, and surveillance, among others.
Moreover, with the integration of AI-powered technology, drones now possess advanced computer vision systems, including cameras and sensors, that can accurately understand and interpret the environment.
Interestingly, a surge has also been noted in the number of registered drones with the Federal Aviation Authority (FAA) for commercial use.
According to a Cybernews report, FAA-registered drones exceeded nearly 1 million compared to the United States, which issued approximately 300,000 commercial pilot licenses in 2022.
It is essential to note that these figures exclude drones operated by amateur pilots or hobbyists who don’t require professional licenses, highlighting how vast the current drone landscape is.
Additionally, drones operating below weight limitations (typically under 250 grams) may not require licensing or registration, although registration with local or federal authorities may still be necessary.
As drones continue to increase in accessibility, affordability, and popularity, it is crucial to recognize that regulations and privacy concerns persist as significant challenges for the drone industry.
There is no denying the fact that drones, like all electronic devices, can be hacked. However, the question is… How easily can a drone be compromised? As the scope of dronerelated security issues extends far beyond privacy.
A recent report by Kaspersky revealed that gaining unauthorized access to a drone through hacking is not necessarily a technically challenging task, as numerous drone operators inadvertently leave their drones vulnerable to attacks.
Another report stated that drones can be “hacked easily” due to their reliance on wireless communication between the remote control and the aircraft.

Moreover, threat actors employ multiple approaches when attempting to hack drones. These approaches encompass various techniques, strategies, and methodologies that are specifically designed to exploit vulnerabilities and weaknesses in drone systems.
What’s concerning is that these hackers may not even need to possess their own drones. Instead, they can leverage various exploitative methods to compromise and gain control over drones, manipulating them for their own malicious intentions.

Drones can be divided into four broad categories: commercial drones, military drones, Fixed Wing Drones, and Quadcopters.
1. Commercial Drones: Designed for commercial use, these are utilized in various industries such as aerial photography and videography, delivery services, agriculture, inspection and surveying, and more.
2. Military Drones: Also known as unmanned combat aerial vehicles (UCAVs) or unmanned aerial systems (UAS), armed forces use these for reconnaissance, surveillance, target acquisition, and even offensive operations. These drones vary in size and capabilities and can carry out airstrikes
3. Fixed Wing Drones: Similar to traditional airplanes, fixed Wing Drones achieve flight through forward motion and rely on the lift generated by their wings. They can fly for long durations and at higher speeds compared to other drone types. They are often used for mapping, aerial surveying.
4. Quadcopters: These multirotor drones are characterized by having four rotors. Widely popular due to their manoeuvrability, these achieve flight and stability by adjusting the rotational speeds of these four rotors. They are commonly used in aerial photography, recreational flying, and racing events.
How can a drone be hacked?

Threat actors exploit various methods to gain access to drones. However, these may vary based on the drone
model, its security features, and vulnerabilities in its system.
1. GPS Spoofing: It is a way to confuse the drone into following false navigation instructions. This is done by either sending a strong signal (Overt spoofing) to overwhelm the legitimate GPS signal or by sending a weaker signal (covert spoofing) similar to the legitimate GPS signal.
2. Signal Interference: In this type of attack, hackers may try to disrupt the communication link between the drone and its controller by jamming or interfering with the radio frequency signals.
3. Malware and Firmware Exploitation: Through this, hackers can exploit vulnerabilities in the drone’s software or firmware by injecting malicious code or exploiting software weaknesses. If successful, the hacker can gain unauthorized access to the drone’s functions and control.
4. Wi-Fi Hacking: Often, commercial drones rely on open Wi-Fi connections, leaving them vulnerable to attacks. In this, hackers may attempt to exploit weaknesses in the Wi-Fi network to gain unauthorized access to the drone’s controls or intercept the transmitted data.
5. Physical Access: In some cases, hackers may target the physical components of the drone. By gaining physical access to the drone, they can modify its hardware, firmware or even implant malicious devices to gain control or extract sensitive information.
While flying a drone may be on your checklist, it is essential to understand how these systems can be exploited if left vulnerable. The dual classification of drones as both aircraft and networked computing devices gives them a distinctive legal position, which can be easily exploited by threat actors.
The US laws and regulations surrounding drone access and usage strive to safeguard the public, yet hackers persistently seek opportunities to exploit any loopholes. This highlights the need to understand the factors that contribute to the threat of dronerelated cyberattacks and take proactive measures to mitigate them.

The world is currently reeling under an ongoing wave of cyber attacks, leveraging a critical vulnerability in the popular file transfer software, MOVEit Transfer
Same threat actor, same kind of vulnerability, same scale of attack!
When The Cyber Express reported about Cl0p ransomware’s global rampage using a vulnerability in Fortra’ managed file transfer (MFT) software GoAnywhere, we thought it was the one-off incident of the year.
The world is currently reeling under an ongoing wave of cyber attacks, leveraging a critical vulnerability in the popular file transfer software MOVEit Transfer.
The attacks, orchestrated by the Cl0p ransomware gang, have targeted various sectors, including healthcare, education, government agencies, and financial institutions.
With the potential to inflict severe damage, these attacks have raised concerns about cybersecurity preparedness and the need for swift action to mitigate further harm.
On June 1, 2023, the discovery of a vulnerability in MOVEit Transfer sent shockwaves through the cybersecurity community.
Designated as CVE-2023-34362, the vulnerability allowed unauthenticated attackers to exploit a SQL injection flaw in the MOVEit Transfer web application. This could grant unauthorized access to the software’s database, potentially compromising sensitive information.
The Cl0p ransomware gang, known for its extortion activities, swiftly capitalized on this vulnerability, initiating attacks on various organizations starting from May 27, 2023.


Following the initial disclosure of the MOVEit Transfer vulnerability, Progress Software, the owner of MOVEit, collaborated with cybersecurity experts to conduct an extensive code review.
This effort led to the discovery of multiple SQL injection vulnerabilities in the software, posing further risks to organizations. Progress promptly released patches to address the newly identified vulnerabilities, urging users to update their systems accordingly.
As the Cl0p ransomware gang continued its exploits, organizations across the globe fell victim to their attacks.
Notable victims included Zellis, a payroll provider serving prominent entities like British Airways and the BBC, as well as Boots, a pharmacy chain with a substantial workforce in the UK and Ireland.
The breadth of the attacks extended to various sectors, including healthcare, government, and financial services, with countless organizations facing the grim reality of a potential data breach.
As the situation unfolded, MOVEit Transfer faced yet another blow with the disclosure of a third critical vulnerability (CVE-2023-35708).
This vulnerability introduced the possibility of escalated privileges and unauthorized access, further exacerbating the risks faced by organizations relying on the software for secure file transfers.
The urgency to address these vulnerabilities prompted experts to advise organizations to disable HTTP and HTTPS traffic to MOVEit Transfer on ports 80 and 443 until comprehensive patches became available.
Cl0p continues to release lists of victims, including prominent organizations such as financial institutions, universities, and energy giants.
The victims include U.S.-based financial services organizations 1st Source and First National Bankers Bank, Boston-based investment management firm Putnam Investments, Netherlands-based Landal Greenparks, and U.K.-based energy giant Shell.
Other victims listed are Datasite, National Student Clearinghouse, United Healthcare Student Resources, Leggett & Platt, ÖKK, and the University System of Georgia (USG). The USG is currently evaluating the scope and severity of the potential data exposure.
German mechanical engineering company Heidelberg was also mentioned as a victim, but it stated that the incident occurred weeks ago, was promptly addressed, and did not result in a data breach. Other organizations listed have yet to respond to inquiries.
Recognizing the severity and impact of the Cl0p ransomware gang’s activities, the US Department of State’s national security rewards program, Rewards for Justice (RFJ), offered a reward of up to $10 million for information linking the
group or other malicious cyber actors targeting US critical infrastructure to foreign governments.
Unlike typical ransomware gangs, Cl0p did not directly contact the organizations it hacked. Instead, a blackmail message posted on their dark web leak site instructed victims to reach out before the June 14 deadline

While no stolen data has been published at the time of writing, Cl0p claims to have downloaded a significant amount of the victims’ data.
Various organizations have recently come forward as victims of the MOVEit attacks.
The BBC, Aer Lingus, and British Airways were compromised due to their reliance on HR and payroll software supplier Zellis, whose MOVEit system was breached.
The Government of Nova Scotia and the U.K.’s communications regulator, Ofcom, have also confirmed being affected. Nova Scotia stated that some citizens’ personal information may have been compromised, while Ofcom confirmed that some confidential information and personal data of its employees were accessed.
Johns Hopkins University, Transport for London (TfL), and global consultancy firm Ernst and Young are also believed to be impacted. TfL and Ernst and Young have not yet provided official statements regarding the situation.
The full extent of the attacks is still unknown, and it is expected that more victims will come forward in the coming days and weeks.
Researchers have revealed that Cl0p may have been exploiting the MOVEit vulnerability as early as 2021, indicating advanced planning and knowledge.
The mass exploitation event involving MOVEit Transfer underscores the sophistication and strategic approach employed by ransomware gangs like Clop.
The exploitation of the MOVEit Transfer vulnerability by the Cl0p ransomware gang has had significant repercussions, affecting organizations globally.
The incident highlights the critical importance of promptly addressing
software vulnerabilities and implementing robust cybersecurity measures. Organizations must remain vigilant, regularly update their security systems, and prioritize proactive threat detection and response.
Additionally, collaborative efforts between software vendors, cybersecurity experts, and affected organizations are crucial to mitigate risks and defend against evolving cyber threats.

May 31: Progress Software released a security bulletin about a critical vulnerability in MOVEit Transfer. Patch issued.
June 5: Payroll provider Zellis announces that it was impacted by the MOVEit cyber attack. Companies including the BBC, Boots and British Airways suffer data breaches as a result.

June 1: Cyber security researchers and the US government flag the vulnerability. Progress Software issues advisory with enhanced remediation steps and Indicators of Compromise.
June 7: Ransomware gang Cl0p issues a threat to victims to contact them by June 14, or their data will be posted online.
June 2: CVE-2023-34362 assigned to Progress MOVEit Transfer SQL injection vulnerability. Indicators of Compromise.
June 7: CISA and the FBI announces a US$10 million reward for “information linking the Cl0p gang or any other malicious cyber actors targeting US critical infrastructure to a foreign government”.
June 8: Professional services network and accounting firm, Ernst & Young (EY) announces that it was impacted by the MOVEit cyber attack. As a result, Health Service Ireland (HSE) suffered a data breach.infrastructure to a foreign government”.

June 12: British communications watchdog Ofcom announces that it was a victim of the MOVEit cyber attack, causing a data breach that affected 412 employees.
June 14: Cl0p begins to post the profiles of companies allegedly breached during the cyber attack launched against MOVEit on its data leak website. Cl0p does not leak any of the stolen data.
June 15: Progress Software releases a security advisory for a privilege escalation vulnerability (CVE-2023-35708) in MOVEit Transfer
June 19: Accounting firm PriceWaterhouseCoopers (PwC) announces it was impacted by the MOVEit cyber attack
June 21: Cl0p claims to not have access to data from the BBC, Boots and BA that was thought to be stolen in the MOVEit cyber attack
June 23: PBI Research Services announces that the data of 4.75 million people was stolen from three of its clients (Genworth Financial, Wilton Reassurance and California Public Employees’ Retirement System (CalPERS)) because of the MOVEit cyber attack. Data stolen during the breach includes social security numbers, names, dates of birth and zip codes.

13. Prudential Assurance Malaysia Berhad (PAMB), Malaysian insurance company
14. Transport for London (TfL), UK government body
15. State of Missouri, USA
BSN Takaful Berhad (PruBSN), Malaysian takaful company
US based SaaS


Vulnerability management has become as crucial as any core business decision. This is how to get it right
- By Chandu GopalakrishnanCVE-2023-34362, CVE-2023-35036, and failed vulnerability management. That is what hundreds of organizations across the world currently have in common. And the impending probability of the Cl0p ransomware group listing them as victims.
The Cl0p ransomware group has been targeting unsuspecting victims by exploiting the latest vulnerability in enterprise managed file transfer (MFT) software, MOVEit Transfer. They used a SQL injection vulnerability to carry out their attacks.
This is not the first time the group has used such tactics. In February 2023, it took responsibility for over 130 attacks
by exploiting a zero-day vulnerability in Fortra GoAnywhere MFT (CVE-2023-0669).
Additionally, in December 2020, they exploited zeroday vulnerabilities in Accellion’s outdated file-transfer application software, resulting in data theft from more than 100 companies. It’s worth noting that in all three campaigns, the Clop ransomware group chose not to deploy their own malicious software.
Vulnerability management has become as crucial as any core business decision. The latest numbers attest to it.

Approximately 34 percent of vulnerabilities reported in May pose a significant security risk, with over 56 percent being remotely exploitable, according to the Flashpoint Cyber Threat Intelligence Index.
A comprehensive analysis of vulnerability intelligence for the month of May has unveiled concerning trends regarding the severity and exploitability of reported vulnerabilities
A total of 1,983 new vulnerabilities were reported, and alarmingly, 323 of them went unnoticed by the Common Vulnerabilities and Exposures (CVE) and National Vulnerability Database (NVD) systems.
Of the vulnerabilities disclosed in May, approximately 34% were rated as high-to-critical in severity. This indicates that if these vulnerabilities were to be exploited, they could potentially lead to significant security breaches and pose a considerable risk to organizations and individuals alike.
Furthermore, over 56% of the reported vulnerabilities were found to be remotely exploitable. This means that threat actors could execute malicious code regardless of the device’s physical location.
The ability to exploit vulnerabilities remotely significantly increases the potential impact and scope of cyberattacks, underscoring the need for proactive security measures.
Any business that understands the gravity of the situation would streamline the efforts of their vulnerability management teams by focusing on actionable vulnerabilities classified as high severity.
“Vulnerability management teams can potentially lessen workloads by nearly 88 percent by focusing on actionable, high severity vulnerabilities. This classification is given to vulnerabilities that are remotely exploitable, that have a public exploit, and a viable solution,” said the report.
This strategic approach ensures that the most critical vulnerabilities receive immediate attention and resources, enhancing overall cybersecurity posture.
While it is difficult to assess the impact of a risk averted, there are several instances where companies suffered because of faulty vulnerability management.
There have been significant cyber attacks where organizations suffered the consequences of inadequate management of IT or OT vulnerabilities. Here are a few examples:

NotPetya was a destructive cyber attack that targeted organizations worldwide. It spread through a compromised software update of an accounting program called M.E.Doc, which originated from Ukraine.
The attack took advantage of vulnerabilities in the IT systems of affected organizations, particularly their use of unpatched or outdated software.
NotPetya caused widespread disruption, impacting companies like Maersk, Merck, and FedEx. It resulted in substantial financial losses, system outages, and affected global supply chains.
At the root of it was EternalBlue, an exploit that capitalizes on a vulnerability present in the Server Message Block (SMB) protocol of Windows.
EternalBlue is widely believed to have originated from the U.S. National Security Agency (NSA). It was inadvertently disclosed in April 2017 and was subsequently utilized by the WannaCry ransomware as well.
“We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and
now this vulnerability stolen from the NSA has affected customers around the world,” said the Microsoft report on the situation
“Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen.”
The Triton attack focused on a petrochemical plant in Saudi Arabia and aimed to manipulate the safety systems, specifically the Triconex Safety Instrumented System (SIS).
The attackers exploited vulnerabilities in the plant’s OT environment, gaining unauthorized access to the SIS and attempting to cause physical damage.
Although the attack did not succeed in causing harm, it highlighted the potential consequences of inadequate management of OT vulnerabilities, including safety risks and the possibility of industrial accidents.
In this case, a zero-day privilegeescalation vulnerability in the Triconex Tricon safety-controller firmware helped allow sophisticated hackers to wrest control of the emergency shutdown system in a targeted attack on one of its customers.

“To deploy the malware, the attackers compromised an SIS engineering workstation. Actions taken by the attackers from the compromised system resulted in the controllers entering a failed safe state, automatically shutting down the industrial process,” said an NCSC advisory.
The Colonial Pipeline, a major fuel pipeline operator in the United States, fell victim to a cyber attack that exploited vulnerabilities in its IT systems.
The attack utilized a compromised password to gain unauthorized access to the company’s network, resulting in a temporary shutdown of the pipeline system.
This led to fuel shortages, price increases, and disruptions in the supply chain along the U.S. East Coast.
In this case, the vulnerability was in the policy and process.
During a hearing on June 8 before a House Committee on Homeland Security, Charles Carmakal, the Senior Vice President and CTO of cybersecurity firm Mandiant, revealed that attackers gained entry to the Colonial Pipeline network by exploiting an exposed password associated with a VPN account.
To establish secure and encrypted remote access to a corporate network, many organizations utilize a Virtual Private Network (VPN).
As per Carmakal’s testimony, an employee of Colonial Pipeline, whose identity was not disclosed during the hearing, apparently employed the same password for the VPN in another context. This password was somehow compromised as a result of a separate data breach.
Vulnerability management starts with understanding the broader types and nature of them. They can be broadly classified as process vulnerabilities and policy vulnerabilities.
While policy vulnerabilities very according to region and business, process vulnerabilities – bugs in IT and OT systems – are largely of the same nature.
IT and OT (Information Technology and Operational Technology) vulnerabilities refer to the weaknesses or flaws that can be exploited in computer systems, networks, and devices used in both IT and OT environments. Here’s some information about IT and OT vulnerabilities.

Software vulnerabilities: These are weaknesses in software programs, operating systems, or applications that can be exploited to gain unauthorized access, execute malicious code, or disrupt system functionality.
The ten most common software vulnerabilities are broken access control, cryptographic failures, injection flaws, insecure design, security misconfigurations, vulnerable and outdated components, identification and authentication failures, software and data integrity failures, security logging and monitoring failures, and server-side request forgery, according to cybersecurity company Preforce.
Network vulnerabilities: These vulnerabilities exist in network infrastructure and protocols, making it possible for attackers to intercept, manipulate, or eavesdrop on network communications.
Non-physical network vulnerabilities typically pertain to software or data. For instance, if an operating system (OS) is not regularly updated with the latest security patches, it may become susceptible to network attacks.
In such cases, if the OS remains unpatched, it could be infected by a virus, potentially compromising the host it resides on and even the entire network. Physical network vulnerabilities, on the other hand, relate to the physical protection of assets.
“For example, an operating system (OS) might be vulnerable to network attacks if it’s not updated with the latest security patches. If left unpatched a virus could infect the OS, the host that it’s located on, and potentially the entire network.,” said an explainer by cybersecurity company Purplesec
Human vulnerabilities: Humans can be exploited as a weak link in IT security. Social engineering techniques such as phishing, pretexting, and baiting are used to trick individuals into revealing sensitive information or performing actions that compromise security.

According to The Global Risks Report 2022 by the World Economic Forum, about 95% of cybersecurity incidents occur due to human error.
OT Vulnerabilities:
Legacy systems: Many OT systems were designed and implemented before robust cybersecurity practices were established. These systems often lack built-in security measures and are susceptible to vulnerabilities that can be exploited by attackers.
WannaCry attack stands as the biggest proof of what legacy systems can do to your cybersecurity posture.
“Even though Microsoft was able to patch the vulnerability for the Windows systems, many organizations failed to update their existing systems or delayed the patch installations as the new patch installations would negatively impact the legacy systems,” said an Intellipaat report
Convergence vulnerabilities: As IT and OT systems increasingly converge, the vulnerabilities of one system can impact the other. Attacks targeting IT infrastructure can potentially propagate to OT systems, disrupting critical operations.
“Over the past year, Microsoft has observed threats exploiting devices in almost every monitored and visible part of an organization. We have observed these threats across traditional IT equipment, OT controllers and IoT devices like routers and cameras,” said a Microsoft report on convergence risks
“The spike in attackers’ presence in these environments and networks is fueled by the convergence and interconnectivity many organizations have adopted over the past few years.”
Weak authentication and authorization: OT systems may rely on weak or outdated authentication methods, such as default passwords or shared credentials, making it easier for attackers to gain unauthorized access and manipulate operational processes.
“Poor or missing authentication schemes allow an adversary to anonymously execute functionality within the mobile app or backend server used by the mobile app,” said an OWASP report
“Weaker authentication for mobile apps is fairly prevalent due to a mobile device’s input form factor. The form factor highly encourages short passwords that are often purely based on 4-digit PINs.”
Speaking of mobile apps takes us to the next category.
Remote access vulnerabilities: With the rise of remote connectivity, remote access to OT systems can introduce vulnerabilities if not properly secured. Unauthorized access to OT systems can lead to operational disruptions, safety incidents, or damage to physical assets.
According to cybersecurity company Bitsight, the most common remote access vulnerabilities are lack of established protocols, unsecured networks, unauthorized apps, and unauthorized access to devices.
Supply chain vulnerabilities: OT systems often rely on components and software from third-party vendors. If these components contain vulnerabilities or are compromised during the supply chain, it can expose OT systems to potential attacks.

“A supply chain incident happens when the components that make up the OT system are compromised. This was demonstrated in the recent SolarWinds attack,” said a report by ARC Advisory Group.
“In this case, a software company that sells network management tools had their servers compromised, causing them to update customer’s computer
systems with software that had malicious software, which in turn infiltrated their customer’s systems.”
It’s important to note that the specific vulnerabilities and best practices can vary depending on the industry, organization, and specific IT and OT systems in use. Regular security assessments and engaging with cybersecurity experts can help identify and address vulnerabilities effectively.
Effective Vulnerability management is a proactive approach to identify, assess, prioritize, and mitigate vulnerabilities in computer systems, software applications, networks, and other digital assets.
It involves a systematic and ongoing process of discovering, analyzing, and addressing vulnerabilities to minimize the risk of exploitation by potential attackers.
The goal of vulnerability management is to ensure that organizations have a clear understanding of their vulnerabilities and can effectively prioritize and remediate them based on the level of risk they pose. This helps organizations maintain a strong security posture, reduce the likelihood of successful attacks, and protect sensitive data and resources.
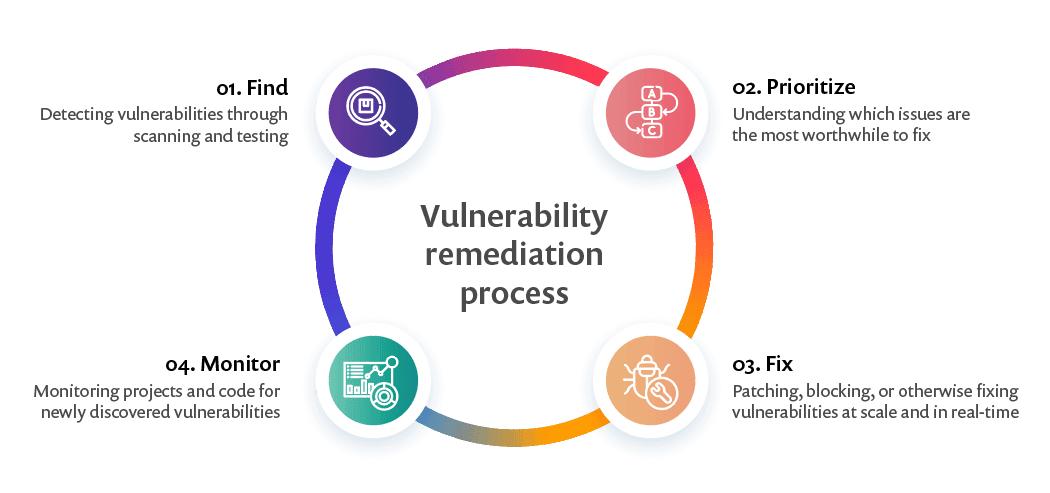
The vulnerability management process typically involves these key steps:

Vulnerability Assessment: This step involves scanning systems, networks, and applications using automated tools to identify known vulnerabilities. These tools search for weaknesses in configurations, software versions, and potential security flaws.
“A vulnerability assessment is
the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe. This process may involve automated and manual techniques with varying degrees of rigor and an emphasis on comprehensive coverage,” said a Synopsys definition of the term
“Using a risk-based approach, vulnerability assessments may target different layers of technology, the most common being host-, network-, and application-layer assessments.”
Vulnerability Prioritization: Once vulnerabilities are identified, they are evaluated based on their severity, potential impact, and exploitability, said a Purplesec explainer
This helps prioritize which vulnerabilities should be addressed first, considering the level of risk they pose to the organization.
“Then, develop a risk-based remediation plan focusing on high-risk vulnerabilities while continuously monitoring and retesting to ensure effective vulnerability management,” the explainer said.
Remediation Planning: After prioritization, organizations develop a plan to address the identified vulnerabilities. This may involve applying security patches, implementing configuration changes, updating software versions, or applying other security measures to mitigate the risks.
“Remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. Effective remediation entails continuous processes that together are called Vulnerability Management,” said the Guide to Effective Remediation of Network Vulnerabilities by Qualys.
Patch Management: Organizations ensure that all systems and software are regularly updated with the latest security patches and updates. Patch management involves monitoring vendor releases, testing patches, and deploying them in a timely manner to close security vulnerabilities.

The process is different from the broader process of vulnerability management, noted a Purplesec report
“The main difference between patch management and vulnerability management is that patch management is the operational process of applying remediations (patches) to vulnerable systems,” it said.
“Vulnerability management is the process of identifying, scanning and prioritizing vulnerabilities for remediation.”
Ongoing Monitoring: Continuous monitoring of systems
and networks is crucial to identify new vulnerabilities that may arise due to changes in software, configurations, or emerging threats. Regular vulnerability scanning and monitoring help maintain a proactive approach to security.
“For continuous monitoring, scheduling daily or weekly scans of systems and subnets will produce enough data for a sound baseline of what is running in the environment and at a system level, which can then be assessed against newer scans to determine what has changed and what the risks are,” said a BeyondTrust report
“Most enterprise vulnerability scanners can cover web and database technologies adequately as a starting point, too, and you can add more specialized tools later if you need more in-depth information.”

Incident Response: In case a vulnerability is exploited or an attack occurs, incident response protocols should be in place to detect, contain, and remediate the incident effectively.
This involves investigating the root cause, recovering systems, and implementing additional security measures to prevent future incidents.
“The incident response process starts with the declaration of the incident,” said a CISA Playbook on cybersecurity incident and vulnerability response.
“In this context, “declaration” refers to the identification of an incident and communication to CISA and agency network defenders rather than formal declaration of a major incident as defined in applicable law and policy.”
Overall, vulnerability management is an essential part of an organization’s cybersecurity strategy. It helps protect against potential security breaches, reduces the attack surface, and ensures the timely and effective mitigation of vulnerabilities to maintain a secure environment.
The Cyber Express takes stock of some of the ongoing and upcoming cybersecurity, privacy and data usage regulations of the year 2023 till date
- By Chandu Gopalakrishnan20,000. That was the approximate number of public suggestions the Indian government received in May over its crucial data privacy regulation.
What is appalling is that the suggestions come from a country where the traditional PC market reached a total of 14.9 million units in 2022, including desktops, notebooks, and workstations.
The draft of the digital data protection bill was shared in November 2022, and since then, it has become a subject

of controversy due to certain provisions that granted the government exemptions from privacy protections.
This move raised eyebrows and clashed with the 2017 Supreme Court judgment that recognized privacy as a fundamental right for individuals.
Even with that kind of debate and bad press, 20,000 comes across as an abysmally low number of responses. And it’s a global phenomenon.

While people express concerns about their online privacy, they often fail to take action to safeguard it, said a report by researchers Ivano Bongiovanni,
Karen Renaud, and Noura AleisaThis paradox is particularly evident in the context of Internet of Things (IoT) devices, which are projected to reach 75.44 billion globally by 2025, said the report.
In an experiment involving IoT devices, participants showed initial privacy concerns but did not align their behavior with those concerns. Even after evidence of privacy violations, many participants continued using the devices, the researchers reported.
Raising awareness goes a long way in helping people understand the need for privacy laws.
Firstly, education and information dissemination are key. By providing clear and accessible resources about privacy laws, their purpose, and the risks associated with privacy violations, individuals can better
grasp why such laws are crucial. Reallife examples of privacy breaches can also be shared to make the importance of privacy laws more tangible.
Secondly, empowering individuals and highlighting the benefits of privacy laws are important aspects of awareness campaigns. By understanding their rights and the protections offered by privacy laws, people can make informed decisions about their personal information.
Collaboration among government bodies, industry leaders, and privacy advocates is vital in raising awareness and promoting responsible data practices. Public discussions and debates provide platforms for individuals to voice concerns and learn from experts.

Here are some of the ongoing and upcoming regulations of the year 2023, aggregated by The Cyber Express:
In August 2022, the Indian government withdrew the Personal Data Protection Bill, 2019, due to public consultation recommendations. It was replaced by the Digital Personal Data Protection Bill, released on November 18, 2022.
This Bill is part of a series of legislations that includes IT rules, the National Data Governance Framework Policy, and a new Digital India Act. In all likelihood, the Bill will become an Act this year.
The bill covers digitized data, provides itemized notice in English or other languages specified in the Indian constitution, and imposes penalties of up to INR 500 crores (more than $60 million) for non-compliance.
It introduces provisions such as deemed consent and the right to nominate as a data subject, while obligations like data localization and privacy by design are currently omitted. The bill sets the stage for India’s data protection regime, promoting digital data usage by organizations.
“Overall, this bill provides greater emphasis and encourages organisations to digitize personal data. Additionally, it is an important and significant start for data protection regime in India,” said a KPMG assessment report

The year 2023 saw the United States witnessing a wave of comprehensive data privacy regulations, as evidenced by the recent enactments in various states.
While the official line is that these laws aim to strengthen consumer privacy rights, establish business obligations, and enhance data protection measures, the Big Tech has criticised them for being too stifling, while privacy activists lament that they are too lenient.
Here are the details of data privacy regulations enacted this year in various states.
Montana recently became the ninth US state to enact a comprehensive data privacy law. The Montana Consumer Data Privacy Act, signed into law by Governor Greg Gianforte, will come into effect on October 1, 2024.
This law aims to safeguard consumer data by granting individuals certain rights, such as the right to know what personal information is being collected and shared, the right to opt-out of data sales, and the right to request the deletion of personal information.
Coincidentally, Montana was the first state to pass a Bill banning TikTok on privacy concerns.
“According to the bill, TikTok also gathers essential user information and could share it with foreign states. The state of Montana also believes that TikTok fails to remove content that promotes dangerous behavior,”
said a Panda Security assessment of the Bill.
“The bill also expresses fears that the app could let China conduct corporate and international espionage that includes tracking adversaries of the Chinese Communist Party, including political figures, journalists, dissidents, etc.”
On May 11, 2023, Governor Bill Lee signed the Tennessee Information Protection Act (TIPA) into law following its unanimous passage in both houses of the Tennessee legislature.
The law aligns with similar regulations in other states, providing individuals with greater control over their personal information. Under the TIPA, businesses must implement reasonable security measures to protect sensitive data and notify individuals in the event of a data breach.
Alternatively, it applies to businesses that control or process personal information of at least 175,000 consumers during a calendar year. The term “consumer” refers to a natural person residing in Tennessee who is acting in a personal context, excluding commercial or employment-related activities.
The application thresholds described above are significantly narrower than those in most other state privacy laws, noted US law firm DavisWright Treamine
“The Virginia law, for example, applies to businesses that control or process personal data of 25,000 Virginia residents and derive over 50 percent of gross annual revenue from the sale of personal data, or that control or process the personal data of 100,000 Virginia residents in a calendar year,” it said.
“TIPA increases the second threshold to 175,000 residents and, following the Utah privacy law, adds that a business must have at least $25 million in annual revenue to be covered.”
The California Privacy Rights Act (CPRA), which took effect on 1 January 2023, has gained attention for its comprehensive approach to privacy protection.
The recently issued CPRA Regulations provide further guidance on implementing the California Consumer Privacy Act (CCPA). These regulations offer clarity on various aspects, including the definitions of key terms, consumer rights, and business obligations related to data privacy practices.
“Under the CCPA, unless an exception applies, a transfer of personal information to a third party for monetary or other valuable consideration constitutes a “sale” and requires the business to provide the consumer with notice of that sale and provide the consumer with the right to opt out,” observed Californiabased law firm Atkinson, Andelson, Loya, Ruud & Romo
“Transfers to “service providers” do not trigger the right to opt out,” the report said.
Following the examples set by privacy laws in Colorado, Connecticut, and Virginia, the Indiana Consumer Data Protection Act was signed into law on May 1, 2023. This new legislation establishes rights and obligations for data protection in Indiana.

Scheduled to take effect on January 1, 2026, this law grants consumers the right to access, correct, and delete their personal information held by businesses. It also establishes requirements for businesses to secure consumer data and notify individuals in case of data breaches.
Unlike states such as Virginia, the Indiana Data Privacy Law does not have a revenue threshold for entities to be subject to privacy obligations, noted global legal service firm White & Case
“In addition, the Indiana Data Privacy Law does not apply to government entities, nonprofits, HIPAA-covered entities and business associates, higher educational institutions (public or private), and Gramm-Leach-Bliley Act-regulated entities and data,” the White & Case report said.
“The Indiana Data Privacy Law also does not apply to certain classes of data including health records, scientific research data, consumer credit-reporting data, data regulated by the Family Educational Rights and Privacy Act or federal Farm Credit Act, and employment-related information.”
Iowa enacted the Iowa Data Privacy Law, which will become effective on January 1, 2025.
This law brings Iowa in line with other states in establishing consumer privacy rights and imposing obligations on businesses.
Similar to other state laws, it emphasizes transparency, individual control over personal data, and the need for businesses to adopt reasonable security measures.
“A business falls within the scope of the Iowa law if it controls or processes personal data of at least 100,000 Iowa consumers, about 3% of the state’s population, during a calendar year,” reported the International Association of Privacy Professionals.
“Alternatively, businesses that derive more than 50% of gross revenue from the sale of personal data fall within scope of the law if they control or process personal data of at least 25,000 Iowa consumers.”
The Colorado Privacy Act (CPA) finalized its rules, set to take effect on July 1, 2023.

This act, similar to the California and Virginia privacy laws, grants consumers certain rights and requires businesses to implement measures to protect personal data.
It introduces obligations such as data minimization, purpose limitation, and data protection assessments to ensure responsible data handling practices.
The Colorado Privacy Act (CPA) will be applicable to businesses operating in Colorado or providing products or services to Colorado residents.
It will apply to entities that meet either of the following criteria: (1) control or process personal data of 100,000 or more consumers in a year, or (2) control or process personal data of 25,000 or more consumers and receive revenue or obtain a discount on goods or services through the sale of personal data.

Like Indiana, there is no specific revenue threshold for the CPA’s applicability.
“The CPA puts in place broad requirements regarding data protection assessments,” said an assessment report by US based law firm Crowell & Moring
“In particular, it states that controllers may not engage in data processing ‘that presents a heightened risk of harm to a consumer without conducting and documenting a data protection assessment of each of its processing activities’.”
The European Union (EU) is taking a significant step in regulating artificial intelligence (AI) with the introduction of the EU AI Act. This proposed law, the first of its kind by a major regulator, aims to categorize AI applications based on their risk levels and establish specific legal requirements for high-risk applications.
Under the EU AI Act, applications and systems that pose unacceptable risks, such as government-run social scoring, will be banned.
High-risk applications, such as CV-scanning tools for job
ranking, will be subject to stringent regulations. However, applications that are not explicitly banned or classified as high-risk will remain largely unregulated.
The impact of AI applications on various aspects of people’s lives, including online content, law enforcement, and healthcare, has driven the need for comprehensive regulations.
The EU AI Act has the potential to become a global standard, similar to the influential General Data Protection Regulation (GDPR) implemented in 2018.
While the proposed law is a significant step forward, there are concerns about certain loopholes and exceptions. The Act may require improvements to address unforeseen risks and provide more flexibility to adapt to emerging AI applications.
Similar to what GDPR did to privacy regulations across the world, the EU’s AI regulation is already making waves internationally, with Brazil’s Congress recently passing a bill inspired by the EU AI Act to create a legal framework for AI.
AI’s popularity has skyrocketed in recent years. Generative tools like ChatGPT have captivated individuals and businesses alike, but as the initial hype has faded, darker implications have emerged. Now that AI is more versatile and accessible than ever, will it create a wave of AIgenerated cybercrime?

AI is a powerful tool for anyone who uses it, including cybercriminals. As this technology advances, security professionals may need to consider how to defend against


Quantifying the threat of AI-generated cyberattacks starts with understanding how cybercriminals may use this technology. Like legitimate uses for intelligent systems, AI cybercrime comes in many forms.
Phishing is one of the most prominent use cases for AI in cybercrime, partly because phishing remains the most common form of cybercrime today. These attacks can be remarkably effective without any help from AI, but generative models can unlock their full destructive potential.
Generative AI can craft convincing, personalized phishing messages the same way it writes blog posts and marketing messages. As a result, social engineering attempts may lack their traditional telltale signs, like misspellings and poor grammar. AI’s speed will also let criminals produce much higher volumes of these messages in less time.
Research has already verified the efficacy of AI-generated phishing. A test at a security conference found that users were far more likely to fall for AI-produced phishing attempts than human-generated ones.
Generative tools like ChatGPT can write more than just natural language. They can also produce code, opening the door to AI-generated malware strains.
Writing new code is a time-consuming, error-prone process, but AI can streamline it significantly. That’s great news for developers, but these benefits extend to malicious code, too. Cybercriminals can use generative AI to automate the writing or checking process when developing new malware strains.
Since AI works so quickly and effectively, the malware it creates may be more threatening than its humanprogrammed counterparts. Cybercriminals could use it to develop and implement new, detection-resistant strains before security researchers have time to adapt. Zero-day exploits are already a widely recognized security concern, but AI could accelerate their emergence as it streamlines malware generation.
Similarly, cybercriminals can also use AI to find new attack vectors. As cybersecurity has become a more prevalent issue, more businesses have implemented extensive protections. Over half of all organizations have a zero-trust framework in place, but no defense is perfect, and AI helps criminals overcome these barriers.
AI can scan business networks and IT infrastructure to find potential vulnerabilities. Today’s complex cyber defenses leave fewer of these opportunities and make them harder to find, but AI can identify them faster and more accurately than people.
Thanks to AI’s speed and accuracy, these vulnerability scans can shorten attack timelines, even against a well-protected business. As more of these models come as off-the-shelf solutions on the dark web, they will also lower the barrier of entry for advanced attacks.
While many of these risks involve using AI to exacerbate existing threats, AI can create entirely new ones, too. Deepfakes — AI-generated media resembling real-world video, audio or image content — could pose security challenges if businesses are not prepared.

Criminals could use deepfakes to make videos or audio messages that look and sound exactly like real, trusted parties. They might impersonate a company’s CEO to direct employees to send sensitive information to a cybercriminal’s email or sow distrust throughout an organization.
Business email compromise is already one of the costliest cybercrimes, and deepfakes could make this type of fraud easier than ever.
Deepfakes could also bypass biometric security or protect cybercriminals’ identities. Since these threats are so new, protections against them are fairly sparse.

These cases are more than theoretical threats. Cybercriminals are already starting to use AI to form more sophisticated or effective
attacks against businesses and individuals alike. Security firm Zscaler has already witnessed deepfake attacks and says AI drove the 47% rise in phishing attacks the company discovered in 2022.
As AI becomes more versatile and accessible, its role in cybercrime will undoubtedly grow. Cybercriminals started using generative models like ChatGPT almost as soon as the technology became available, and AI is only becoming more powerful. The potential returns for cybercriminals are too great for them to pass up.
AI-generated cybercrime could become the norm in a matter of months as current trends grow. Even if it doesn’t happen that quickly, AI will redefine cybercrime over the next few years. The shift is already taking place.
As AI-generated cyberattacks grow, the cybersecurity industry must
adapt. Specific approaches and protections may vary between organizations, but here are some general steps that shift should include.
The best protection against AI attacks is AI itself. Thankfully, cybersecurity is already a leading use case for AI, as 51% of AI adopters use it in security. That trend must grow as businesses try to keep pace with AI-driven advancements in cybercrime.
Security teams can use AI vulnerability detection to find holes in their defenses before criminals do. Similarly, some models can detect deepfakes and other AI-generated content to help protect employees from AI-powered fraud and social engineering. This technology’s speed and accuracy make cybercrime more dangerous, but security professionals can reap the same benefits.
As AI heightens the risks of phishing and other forms of social engineering, employees should become increasingly skeptical about unusual communications. Stricter policies around acceptable actions — even if an authority figure seemingly asks for them — may be necessary.
Zero-trust is essential as part of this increased scrutiny. All employees should also receive training on how to check messages for AI-generated content and why it’s important to verify before trusting anything.
Finally, businesses must recognize that AI’s growth will accelerate the rate of change in cybercrime. Adapting to new criminal trends is already a critical part of thorough security, but these trends will change faster with AI.
According to a 2022 report, 42% of organizations today penetration test once every one to two years, but that may have to change. More frequent testing may be necessary to stay on top of rapidly evolving, AI-driven threats.

Outside of these tests, security professionals should monitor the overall cybercrime landscape closely to identify threats similar businesses are facing they may have to account for.
AI is a revolutionary technology, but that power applies to both good and bad parties. Just as this technology is changing the way businesses operate, it’s opening new opportunities for criminals.
AI has already become a common part of cybercrime. Security teams must adapt to this trend and likewise implement AI to stay safe.
Emily Newton is a seasoned tech and industrial writer who explores the impact of technology in different industries. She has over six years of experience providing insights on innovative technologies.


 - By Zac Amos
- By Zac Amos
Cybercrime has drastically increased in recent years, heavily impacting vulnerable people and organizations. In response, digital vigilantes took up scambaiting to
get revenge on scammers. While it may be a solution to an inadequate system, some argue it has little genuine effect. Does it actually deter anyone?

Some experts project global annual cybercrime costs to reach $10.5 trillion by 2025, up from $3 trillion in 2015. It’s an ever-growing issue that needs attention. Since individuals are most often a target, many responded by scambaiting. It originated as a response to excessive scam emails and calls but has grown in popularity as fraud becomes more rampant.

Basically, scambaiting is a tactic to keep scammers engaged as long as possible to prevent them from targeting others. It usually involves deception or social engineering methods on the scambaiter’s part. They intentionally waste time and typically stall as much as possible. Many upload their interactions to the internet afterwards.
Essentially, scambaiters are digital vigilantes that seek revenge on scammers. Some seek out fraud, while others only react after contact. Since fraud affects almost 4.6 million people annually, they typically don’t have to wait long.
Once they are speaking with a scammer, the scambaiters typically disguise themselves as naive and vulnerable. They pretend to genuinely believe whatever claims they are fed to prolong engagement. Since they are not actually interested, the interactions end up wasting the fraudster’s time and frustrating them.
For example, a scambaiter who receives an illegitimate email will respond and pretend to be oblivious to the fraud. They follow all of the scammer’s orders up to the point where they’d send money. Then, they either pretend to be incompetent to further stall or reveal their deception.
It encompasses all types of scams, so scambaiters are sometimes in contact for days or weeks before revealing themselves.
Many trick scammers into performing humiliating actions or revealing personal information. Some take it further and attempt to disrupt the fraud operation, whether through damaging their computers or publicizing their location.
According to the United Kingdom National Fraud Intelligence Bureau, COVID-related cybercrime reached $34.5 million in losses as of 2021. As long as digital fraud continues to increase, some form of scam prevention will be necessary.
While individuals using scambaiting may not be the best suited for the position, they are often the only ones who take action. Many legal and regulatory bodies don’t take scams seriously because they can be challenging to investigate.
As technology advances, so do scammer tactics.
For instance, they can create fake content with generative artificial intelligence in a few short minutes — and it’s more realistic than ever. Finding their true identity is much more challenging when they essentially produce faulty evidence of their existence — doing a reverse image search with original, unpublished content isn’t possible.
Police have struggled to pursue cybercrime because of the continuously increasing demand. They don’t have enough resources to cover all the new cases they receive, so many go unsolved.
Digital vigilantes potentially prevent more people from becoming victims of fraud. Their efforts may not have an incredibly significant impact, but collective action can help.
In addition, scambaiters often make up for the state’s insufficiencies. For example, Birmingham City University labeled the U.K.’s national fraud hotline as unfit for purpose in 2020 after investigations uncovered consistent inaction.
One discovered that it successfully pursued only one in 50 fraud cases and simply abandoned the others. Scambaiting may not be an ideal response, but it’s often the only solution available to most.

Most internet vigilantes engage in scambaiting because they want retribution or feel a sense of justice. Most often, they seek to cause frustration and disorder — whatever will cause a significant impact.
Scambaiters have four primary motivators:
• Raise awareness: People exposed to videos or descriptions of scambaiting are more likely to recognize fraud.
• Deter scammers: Some take steps to damage a scammer’s resources or reputation, deterring them from future fraud attempts.
• Prevent scams: Keeping a scammer occupied with a call that will go nowhere can protect others from being scammed. As long as they’re busy, they can’t cause actual harm.
• Disrupt operations: Many attempt to cause significant damage or distress to have more longterm disruptions in the fraud operation.
Most scambaiters share these motivators. While they generally have good intentions and get positive results, some are more malicious. It’s an unregulated practice, so they have no set standards.
While scambaiting can be a much faster alternative to regulated activities, it does come with potential disadvantages. The 419eaters forum is a good example. It’s the self-described biggest scambaiting group in the world, with more than 1.7 million threads as of 2021. Although its members put consistent effort into fraud disruption and prevention, their intent is sometimes misaligned.
Their system rewards certain activities. For example, the pith helmet award goes to people who can get their target to travel more than 200 miles in one trip. They also often convince scammers to send nude graphic images because they can then post them online. Their goal is public humiliation.
The reward system incentivizes users to cause disproportional mental or physical strain. Many assume the fraudster’s malicious intentions justify this behavior, but does one immoral action justify another? A large, unregulated collective acting in such a capacity can potentially be dangerous.
Scambaiting can pose risks to the scambaiter as well as the fraudster. The people behind the deception are already willing to steal the life savings of vulnerable people, so there’s potential for more significant adverse reactions.
There are a few potential scambaiting dangers:
• Disproportionate responses: Many people are driven by anger when scambaiting, which increases the likelihood of taking things too far. While some may feel their actions are just, they may only be seeking harm to get revenge on scammers.
• Legal consequences: Many people want to give scammers a taste of their own medicine, but the law doesn’t protect their actions. Doing something illegal in pursuit of catching a scammer is still illegal.
• Increased scam attempts: Scammers will continue to contact someone if they initially answer. Also, they will often bombard scambaiters with messages and calls in retribution.
• Accidental information disclosure: Scambaiters can accidentally expose their personal information — like their IP address — while interacting with a scammer, which can open them up to a potentially dangerous response from the scammer.
People who seek revenge on scammers should be aware of potential scambaiting dangers to protect themselves. While retribution may be as minor as constant phone calls, it can quickly escalate.

Although scambaiting has disadvantages and possible dangers, it’s a relatively common response to increased fraud levels. Scammers are targeting individuals at an unprecedented rate. Regulatory and legal bodies can’t handle their workloads and are resorting to case abandonment. Digital vigilantes may possess questionable motives and methods at times, but they offer many more options than the current system.
Applying standards to scambaiting could help ensure more legitimate and ethical practices. A cybercrime professor from the University of New South Wales believes more regulation and stricter payment barriers could reduce half of all scams at minimum.

However, given the scale that scammers operate at, scambaiters may not have the impact they hope for. Even if they succeed in deterring one scammer, that will likely not translate to deterring the scammer’s entire network. But while scambaiters may not make much of a dent in overall scamming activities, they are improving awareness. Scambaiter content creators have risen in popularity in recent years, providing viewers with inside details on how scams work and bringing scam awareness into the public consciousness.
Scambaiting may not be the perfect solution, but it can still be a valid tactic in a system of inaction. More collective action in the future may genuinely deter scammers from defrauding vulnerable people, and the rise of scambaiters as content creators should help more people avoid being scammed themselves.
Graduated with degrees in English and Digital Media, Zac Amos is a seasoned tech writer. He loves geeking out over tech and can often be found writing about artificial intelligence, cybersecurity or many other tech topics.
As the world becomes increasingly interconnected, cyber-attacks and data breaches loom over individuals, organizations, and even entire industries.

In this cybersecurity world, where remote work and the COVID-19 pandemic have added new dimensions to the challenges, maintaining a strong hold on security has become a cumbersome task.
The statistics paint a very dark picture of the cyber world and the frequency of these attacks.
With a staggering 2,200 attacks occurring daily, it takes a mere 39 seconds for another target to fall victim to a hacker. The financial repercussions are equally distressing,
with data breaches costing an average of $9.44 million in the United States alone.
To explain how this cybersecurity landscape is changing, The Cyber Express has compiled a list of the most influential cyber attacks and data breaches that have transpired over the past six months.
Luxottica, one of the world’s leading eyewear companies, was tangled in a dire situation in late 2022. MCNA Insurance, PharMerica, Shields Health Care Group, NCB Management, Kodi, Latitude Financial, and GoAnywhere are among the organizations that have experienced the impact of cyber-attacks and data breaches in these last two years.

On June 22, 2023, a DDoS (Distributed Denial of Service) attack targeted the websites of the Czech Republic’s public broadcaster, Český rozhlas (ČRo). The attack resulted in the domestic broadcast websites’ shutdown and the iRozhlas’s unavailability.cz radio online portal. This incident occurred just before a panel discussion on the media, and Ukraine was scheduled for broadcast by ČRo Plus. Czech President Petr Pavel, a guest at the discussion, denounced the attack and highlighted its implications for objective reporting on conflicts.
The European Investment Bank (EIB) in Luxembourg fell victim to a cyberattack following recent warnings from Russian hackers regarding destabilizing the Western financial system. Pro-Russian hacktivists, known as the Killnet group, targeted the EIB’s inter-network infrastructure. The group claimed responsibility for the attack on their Telegram channel, and the EIB subsequently confirmed the incident. As of the time of writing, the bank’s website remained inaccessible. The EIB assured that they were actively responding to the attack.
The municipality of Bouchemaine, located near Angers in France, experienced a cyberattack over the weekend of June 17 and 18, 2023.

The town hall issued a statement on June 20, confirming the intrusion into their information system and stating that it affected municipal services’ functioning.
The technical diagnosis was underway to determine the origin and severity of the attack. Further details about the nature of the cyberattack and its potential implications were yet to be revealed as investigations continued.
The Rheinische Post Mediengruppe, a German media company based in Düsseldorf, was targeted by a cyber attack that affected multiple news websites under its umbrella. The attack was directed at the company’s IT service provider, Circ IT, causing technical issues and disruptions across platforms such as Rheinische Post, Saarbrücker Zeitung, and Aachener Zeitung.
While the websites displayed notifications about the disruption, access to e-paper editions and limited news overviews were still available. The attackers reportedly exploited a supply chain vulnerability within Circ IT to carry out the attack.

Helmholtz-Zentrum Berlin, a research center in Germany, was targeted in a cyber attack. This incident followed other cyber attacks in Munich and Bern, where attackers planned to disclose data obtained from the IT service provider Xplain AG.
The San Luis Obispo County Office of Education in California, USA, faced a cyber attack that may have exposed employees’ personal financial information.
The breach was discovered on June 12, prompting the shutdown of the entire system. Law enforcement and the Center for Internet Security were notified to investigate the breach and determine the extent of the compromised data.
Superintendent Dr James Brescia informed school district employees about the breach, offering free credit monitoring services and urging vigilance against data theft. The attack was part of a cyber attack from Russia targeting state and federal agencies with ransomware demands.
Stephen F. Austin State University (SFA) located in Texas, USA, experienced a cyber attack that led to the disruption of their computer networks. The attack is suspected to have taken place from Saturday evening until Monday morning. In order to prevent additional incidents, the university made the decision to temporarily disable access to their networks.
The specific nature of the attack was not disclosed, and the responsible party remained unknown. Criminal organizations have increasingly utilized ransomware attacks to extort payments.

SFA’s information technology staff, external entities, and the University of Texas System worked to identify the compromised files and vulnerabilities. Authorities investigated the attack, and SFA’s network outage impacted the availability of daily law enforcement and fire reports.
A cyber attack targeted the city government of Fayetteville, Arkansas, causing internet and web services disruptions. However, essential services such as police, fire, and emergency response remained unaffected.
The city’s IT department actively worked to restore systems and data, enlisting the help of cybersecurity experts in the investigation and response. Online services were expected to be unavailable for several days, with efforts focused on resolving the issue and bringing services back online.
Meanwhile, concerns were raised about the security of the neighboring city Fort Smith, as reliance on social media and online transactions increased cybersecurity risks for government entities.
The website of the Swiss parliament, “parlament.ch,” was targeted by a DDoS attack, rendering it temporarily unavailable or slow in responding.
The parliamentary services reported that they could mitigate the attack and restore the website’s functionality through appropriate measures. Internal systems and data remained unaffected.
Specialists worked to fend off the attack completely, as announced by the Presidents of the Council of States and the National Council.
Luxury watch retailer Cortina Holdings in Singapore faced a cyber attack, resulting in unauthorized access to one of its servers and data encryption. The company initiated investigations into the incident and immediately isolated the affected server.
External IT consultants were engaged to assist with containment and remedial efforts, while authorities, including the police and the Personal Data Protection Commission, were notified. Although specific details about the leaked data were not disclosed, the company planned to notify affected parties.
The All India Institute of Medical Sciences (AIIMS) in New Delhi successfully thwarted a malware attack that had been neutralized by its deployed cyber-security systems.
The attack occurred six months after a prior incident that had caused disruptions to the institute’s servers. In response to the earlier attack, significant structural changes were implemented by the medical organization to enhance the detection and prevention of security incidents.
These measures were credited with preventing the malware attack that was thwarted in June.
Barmer, a health insurance company in Germany, was affected by a cyber attack targeting one of its external service providers responsible for implementing its bonus program. The attack occurred on May 31, 2023, and investigations were underway to assess the potential extent of the damage and determine if Barmer’s data was compromised.
The service provider addressed the security vulnerability, and it was clarified that the attack was limited to the provider’s infrastructure and not connected to Barmer’s IT environment.
Showmax, a streaming provider in South Africa, confirmed a cyber attack that compromised subscribers’ details. Hackers accessed the platform and published subscribers’ login credentials on a fake website.
Approximately 27,000 subscribers were affected by the breach. Showmax stated that customer emails and passwords were exposed, but no financial information was compromised.
The company asserted that the data was not stolen from Showmax but may have been obtained from other sources. Affected customers were notified and advised to reset their passwords.
South African pharmacy chain Clicks faced a cyber incident on May 31, 2023, where a small number of customers’ data was accessed.

Clicks promptly invoked its cybersecurity protocols, deployed a security patch to limit further access, and reported the incident to the Information Regulator.
The incident affected approximately 0.05% of Clicks’ pharmacy customers, and the accessed data included names, ID numbers, contact details, and selected dispensary information from transactions in May.
Healthcare information primarily related to purchases of over-the-counter medication. No customer passwords or banking information were compromised.
The Metro Vancouver Transit Police in British Columbia, Canada, fell victim to a cyberattack exploiting a security vulnerability in third-party file transfer software MOVEit.
The hackers accessed nearly 200 files, prompting a thorough review to determine the nature of the compromised information. Although the Transit Police network remained secure, the agency confirmed that the cyberattack had not impacted ongoing police investigations or prosecutions.
The MOVEit software vulnerability has been patched and repaired since the incident. The hacking campaign targeting MOVEit affected multiple organizations globally, including several US federal departments, with Russian hackers identified as the initial perpetrators.
ÖKK Kranken- und Unfallversicherungen AG (ÖKK),
a health insurance company in Switzerland, confirmed being targeted by a cyber attack orchestrated by the Clop gang, a Russian hacking group. The breach resulted in data theft.
The leak site of the cybercriminals displayed the names of several notable companies, including Shell, ÖKK, and holiday park operator Landal, which also operates in Switzerland. The extent of the data leak has been limited so far, but additional victims are anticipated to be identified in due course.
A cyber attack impacted Ireland’s Health Service Executive (HSE) on the technology product MoveIT, which was being used by their external partner EY for a recruitment automation project. The attack, identified as criminal and international in scale, resulted in the potential compromise of data related to approximately 20 individuals involved in recruitment processes.
The accessed data included names, addresses, mobile numbers, panel positions, and general information about the recruitment posts. However, no other personal identification or financial data was compromised.
Shell, the global oil and gas company headquartered in The Hague, confirmed being affected by a cyber attack carried out by the Clop ransomware gang.
The incident involved a breach of the MOVEit file transfer tool, marking the second time Shell had been targeted by the Clop gang in relation to the file transfer service. Shell’s investigation revealed that the attack impacted the third-party tool, MOVEit Transfer, which was utilized by a limited number of employees and customers. However, the core IT systems of the company remained unaffected, and Shell did not engage with the hackers.

Boots UK, a prominent health and beauty products chain, was among the organizations impacted by a large-scale cyber attack that also affected the BBC, British Airways, and Aer Lingus. The attack exploited widely used software, granting cybercriminals simultaneous access to multiple companies.
Personal data, including national insurance numbers and, in some cases, bank details, may have been compromised. No ransom demands or financial losses were reported.
Zellis, a provider of HR and payroll systems in the United Kingdom, fell victim to a cyber attack resulting in the theft of sensitive payroll data from organizations such as the BBC, British Airways, and Boots.
Although the Clop group, responsible for the breach, claimed that they did not possess the data belonging to these large UK organizations, it raised the possibility of another unknown hacking group being involved or Clop providing false information.
Clop had been pressuring victims to pay a ransom by exposing company profiles on their darknet website, but
the major UK victims had not been specifically named yet.
The website of the Ministry of Enterprise and Made in Italy (Ministero delle imprese e del Made in Italy) in Rome was targeted by a Distributed Denial of Service (DDoS) attack. The ministry confirmed that its institutional portal and related applications had been unavailable since the morning.
Initial checks indicated that there were no compromises or data theft. Technicians mitigated the attack’s consequences, but the service restoration timeframe remained uncertain. The ministry was in contact with the National Cybersecurity Agency to minimize inconvenience for citizens and businesses.
DDoS attacks targeted multiple government websites in Senegal by a group of hackers known as

Mysterious Team. The attacks caused the websites to go offline temporarily. The group claimed responsibility for the cyber attacks on Twitter, using the hashtag #FreeSenegal associated with campaigners alleging political repression in Senegal.
The attacks occurred during a period of heightened political tensions in the country. Efforts were made to restore the affected websites, but as of Saturday evening, some official websites were still offline.
In a retaliatory move, an Indian hacktivist group called Kerala Cyber Xtractors claimed responsibility for launching DDoS attacks on 10 Pakistani Embassy websites worldwide.
This came after Pakistani hacker collective Team Insane PK had claimed to have attacked 23 Indian government and private organization websites. Kerala Cyber Xtractors stated that the attacks on Pakistani Embassy websites were payback for the alleged attacks on Indian police station websites. The targeted Pakistani Embassy sites included those in France, Germany, and Kazakhstan.
Group DIS, a hosting provider in France, was targeted in a cyber attack by the Alphv/BlackCat mafia franchise. The attackers claimed that Group DIS refused to pay for the security and protection of its client, Lacroix Electronics, and as a result, they threatened to disclose the data. The attackers alleged that over 1 TB of data, including critical customer data and data belonging to Lacroix Electronics, was stolen during the attack. There was uncertainty regarding the specifics of the attack and whether Lacroix Electronics was the primary target or a collateral victim.
The Association of the Pharmaceutical Industry in Germany, the Ludwigsburg district, and the food company Sysco were targeted in cyber attacks.

The Ludwigsburg district experienced a complete IT shutdown, leading to the closure of various administrative services, including vehicle registration, driver’s license office, and job center.
Although employees could still be reached by phone, the exact timeline for restoring the systems remained uncertain. Security experts from various agencies analyzed the IT infrastructure.
The Federal Association of the Pharmaceutical Industry (BPI eV) faced a phishing incident, which led to unauthorized access to one of their email inboxes.
The association informed its members about the data protection incident in accordance with the European General Data Protection Regulation (GDPR). The exact number of affected individuals was not revealed.
Potentially compromised information included email addresses, data from signatures, names, telephone numbers, postal addresses, and message content. The BPI cautioned
about the potential receipt of spam emails or unsolicited calls.
The Uttar Pradesh State Road Transport Corporation (UPSRTC) website in India was hacked, temporarily suspending online bookings for approximately ten days. The hack believed to be carried out by foreign hackers.
Despite the incident, UPSRTC buses continued using manual ticketing methods to ensure uninterrupted service.
The website management company, M/s Orion Pro, set up new servers to restore online bookings. Police cases have been filed, and the Uttar Pradesh government has ordered a security audit of all applications and web portals managed by M/s Orion Pro.
KuCoin, a cryptocurrency exchange, faced a hacking incident in which its official Twitter account was compromised for nearly an hour. During that period, the account was used to promote a fake promotion that led to users losing money. Following the incident, KuCoin announced its intention to compensate all affected victims. The exchange acknowledged that 22 transactions were impacted by the incident and urged the affected individuals to come forward for compensation.
Eurocontrol, the European air traffic control authority, was targeted by a cyber attack by pro-Russian hackers known as Killnet.
The attack disrupted Eurocontrol’s website and web availability, although air traffic was not endangered. While the systems responsible for flight safety remained secure and unaffected, the attack significantly impacted the organization’s communication channels.
Eurocontrol promptly responded by isolating operational systems and implementing preventive measures to mitigate the effects of the attack.
According to sources, the Insurance Information Bureau of India (IIB) fell victim to a cyberattack, potentially compromising some of its data.
As the IIB collected transaction data from insurers in various lines of business, the breach raised concerns about the compromised information.
The incident prompted a high-level response to address the breach and mitigate its impact. While some data was compromised, the situation remained ongoing. Attempts to reach the CEO of IIB for comment were unsuccessful, adding to the uncertainty surrounding the incident.
Israeli websites, including banks, the post office, the electricity company, and the red alert warning app, were targeted in a cyberattack on Quds Day.
The hacker group “Anonymous Sudan” claimed responsibility for the attacks. As a result, some sites experienced temporary outages. The Israel Post confirmed that its website was subjected to a Denial of Service (DoS) attack. Additionally, the hacker group threatened to target Israeli phone providers.
The websites for Prime Minister Justin Trudeau and Parliament were targeted in a cyberattack on the eve of the Ukrainian Prime Minister’s visit.
The attack, claimed by the Russian hacker group NoName on Telegram, responded to what they perceive as Canada’s “Russophobic initiatives” and its attitude towards Russia and China. The attack utilized a distributed denial of service (DDoS) technique to overwhelm servers and slow down or prevent website access.
The discussion forum of Kodi, a media player software, witnessed a data breach. The breach came to light when a dump of the forum software was advertised for sale on internet forums. It was discovered that an inactive but trusted member of the forum admin team had their account compromised, allowing unauthorized access to the admin console and creating database backups.
These backups were subsequently downloaded and deleted. As a result of the breach, forum posts, team
forum posts, user-to-user messages, and user data, including usernames, email addresses, and encrypted passwords, were exposed.

The official website of the Immigration Department of Malaysia was defaced by a hacker, resulting in the site’s temporary maintenance closure. The department acknowledged the cyber attack and assured the public that measures were being taken to address the issue in cooperation with CyberSecurity Malaysia. While the display page of the website was compromised, other online links remained unaffected.
The department confirmed no information was leaked during the attack and cautioned against spreading unfounded speculation.
The European Commission’s school education platform was targeted by cybercriminals who aimed to spread malware and malicious links. The criminals utilized fake profiles impersonating educational institutions, rapidly gaining prominence in Google search results.
These profiles contained links to purported money and premium account generators for popular services such as OnlyFans, Fortnite, and PlayStation Network. However, these links led to malware. The platform’s inadequate checking mechanisms allowed for the creation of fake profiles by anyone.
A bug in the SafeMoon liquidity pair was exploited by a hacker, resulting in a loss of approximately $8.9 million. The hacker utilized the bug to burn a significant portion of SFM tokens in the liquidity pool, artificially inflating the token’s price.
This allowed them to drain the WBNB from the contract in a single transaction. The BNB-based exchange promptly acknowledged the breach and took measures to address the issue. Security firm Peckshield suggested a recent update might have introduced a “public burn bug” that facilitated the hack.
By manipulating the SFM token price using code, the hacker successfully collected over $8.9 million from the exploit.
Russian hackers conducted a series of DDoS attacks on the websites of humanitarian organizations in Germany, including the Red Cross, in response to Germany’s plan to send tanks to Ukraine.
The attacks proved largely ineffective, resulting in temporary inaccessibility of the websites but no significant impact on their services.
Hacker groups such as Killnet, Anonymous Russia, and Anonymous Sudan claimed responsibility for targeting various German institutions, including airports, intelligence services, the cabinet, financial institutions, customs services, and law enforcement agencies.
The Compagnie d’aménagement du Bas-Rhône et du Languedoc (BRL), a water management company in France, experienced a cyber attack of the ransomware type on March 24, 2023.

The attack targeted the company’s information systems to encrypt and extract data. The company’s Information Systems Department (DSI) swiftly mitigated the impact in response to the incident.
Fortunately, the attack did not disrupt the company’s water service or operational functions, ensuring its services’ continuity.
On March 28, 2023, the pension fund PME in the Netherlands was notified about a data breach at one of its software suppliers, which also impacted several other organizations. PME immediately initiated collaborative efforts with specialized research agencies to assess the extent of the unauthorized access and determine whether any data was accessed or stolen.
Additionally, they launched an investigation to ascertain if the breached data was published online, although there are no concrete indications of such activity. PME promptly reported the cybercrime incident to the police and communicated closely with relevant authorities.
The Neue Zürcher Zeitung (NZZ) newspaper in Switzerland was targeted in a ransomware cyber attack, resulting in the unavailability of certain NZZ systems and services.
The attack was detected early on and promptly contained, with NZZ IT collaborating with external specialists and experts to assess the situation.
Consequently, CH Media, which relies on various IT services from NZZ, also experienced disruptions. Both organizations joined forces to investigate the incident and swiftly restore regular operations.
The ACRO Criminal Records Office in the UK investigated a cyber security incident that led to the temporary closure of its customer portal.
ACRO is responsible for managing criminal record information and facilitating data exchanges with other countries for background checks and visa processing.
Although there was no definitive proof of personal data compromise, ACRO notified users about the potential impact on their data. The agency promptly initiated an investigation and reassured users that their payment information and dispatched certificates remained secure.
Luxury retailer Saks Fifth Avenue faced an unauthorized access incident attributed to the Clop ransomware gang on its dark web leak site.
The attack was part of Clop’s ongoing campaign targeting vulnerable GoAnywhere MFT servers. While Saks Fifth Avenue assured that no real customer data was impacted, it did not clarify the potential compromise of corporate or employee data.
As a prominent luxury brand established in 1867 and based in New York City, the retailer serves customers in the United States, Canada, and the Middle East.

Biman Bangladesh Airlines, the national carrier, encountered a cyber attack on its email server, during which hackers issued threats to expose passenger and employee information unless a $5 million ransom was paid.
Despite the State Minister for Civil Aviation and Tourism refuting reports of a ransom demand, internal sources from the Digital Security Agency and Civil Aviation Ministry have presented documents indicating otherwise.
It remains uncertain whether Biman has engaged in negotiations with the hackers.
Hitachi Energy, a global technology company, confirmed a data breach after being targeted by the Clop ransomware group, which exploited a zero-day vulnerability in the Fortra GoAnywhere MFT software.
The breach resulted in the compromise of employee data in specific countries, prompting Hitachi Energy to disconnect the affected system, initiate an internal investigation, and enlist the assistance of forensic IT experts.

While there is a possibility that employee data was accessed, Hitachi Energy maintains that the security of its network operations and customer data remains intact.
The company notified the affected employees, data protection authorities, and law enforcement agencies, and it continues to provide
support while collaborating with relevant stakeholders throughout the investigation.
Sun Pharmaceutical Industries Ltd., a prominent pharmaceutical company in India, confirmed a cyber attack that resulted in a major data breach.
The ALPHV ransomware group claimed responsibility, stating they had accessed over 17TB of data, including sensitive customer and vendor information and comprehensive documents on over 1,500 US employees.
Sun Pharma acknowledged the attack and took immediate measures to contain and address the impact of the incident. The company isolated its network, initiated recovery procedures, and engaged global cybersecurity experts to handle the breach.
A DDoS (Distributed Denial of Service) attack targeted Poland’s online tax filing system, and a Polish government official attributed the attack to Russia.
The incident occurred amidst heightened tensions between Warsaw and Moscow due to the conflict in Ukraine.
Western officials claim Russia is a prominent player in cyber espionage and hacking, while Russia has consistently denied involvement in such activities.
The Polish official stated that the attack did not compromise taxpayers’ data, as it only blocked access to the website without jeopardizing security.
Russian hackers claimed responsibility for a DDoS attack on the Toronto-Dominion Bank (TD Bank) website, marking the first cyberattack by Russian hackers on a Canadian banking institution since the conflict in Ukraine began.
The attack, which occurred on February 26, was announced by a group of pro-Russian hackers on the Telegram network.
TD Bank confirmed the attack, stating that its online and mobile banking channels experienced outages. KeyCorp, another US-based bank, also reported a suspected DDoSrelated online outage.
A cyberattack targeted several Ukrainian state and local authority websites, modifying content on some pages.
A Joint Response Team, consisting of experts from the State Intelligence Service, Security Service of Ukraine, and Cyber Police Department, actively investigated the incident.
The attack did not cause significant disruptions or impact the functioning of government bodies. Most of the affected information resources were restored and operated normally.
Copenhagen Airport and other Danish airports detected website irregularities due to a suspected DDoS attack.
The airport’s press officer, Julie Boll, acknowledged the issue and stated that the cause was under investigation. Users encountered difficulties accessing the websites, but alternative travel information was available through the airport’s app.
Hacker group ‘Anonymous Sudan’ claimed responsibility for the attack.
The Fotomuseum Winterthur in Switzerland fell victim to a cyberattack, resulting in manipulated search engine results.
The museum’s website displayed Asian characters promoting counterfeit and low-quality goods. The attack affected the website’s title and meta description, but customer data remained unaffected.
Strict network settings prevented some visitors from accessing the site for security reasons. The National Center for Cyber Security (NCSC) believed the attack to be commercially motivated, employing a strategy known as “Japanese Keyword Hack” or “Japanese SEO Spam.”
Porsche South Africa’s headquarters in Johannesburg fell victim to a ransomware attack, causing significant disruptions to the company’s systems and backups.
The attack involved a relatively new strain of ransomware called Faust, which was believed to have been derived from the Phobos ransomware family.
Faust is typically spread through various methods, such as malicious websites, spam emails, and pirated software. Once infected, the ransomware encrypted files, modified their names and displayed a ransom note demanding payment in Bitcoin for decryption tools.

The Federal Bureau of Investigation (FBI) reported a cyber incident on the part of its computer network, which officials believed involved a system used in investigations of child sexual exploitation images.
The FBI stated that the incident had been contained and treated as isolated. The malicious activity was isolated to the FBI’s New York Field Office, one of its largest and most high-profile offices. The origin of the cyberattack was under investigation.
NATO experienced a series of distributed denial of service (DDoS) attacks, which were believed to have been carried out by the Russian hacktivist group Killnet.
The attacks temporarily disrupted some of NATO’s websites, but the organization’s classified networks and command structure remained unaffected.
Jens Stolberg, NATO’s secretary general, confirmed that protective measures were implemented to counter the attack, and technical teams worked to restore full access to the affected websites.
The social news aggregator Reddit disclosed that it fell victim to a successful phishing attack on February 5. While investigations were ongoing, Reddit confirmed that the “limited contact information” of hundreds of employees had been accessed.
However, the company reassured users that no non-public data, passwords, or similar information had been compromised. The phishing attack had tricked an employee into accessing a fake intranet gateway, allowing the attacker to obtain the employee’s credentials and access some internal files, dashboards, and certain “internal business systems.”
Coinbase, a cryptocurrency exchange platform, faced a cyber attack in which an unknown threat actor stole the login credentials of one of its employees.
The attacker had targeted Coinbase engineers with fake SMS alerts, tricking one employee into entering their credentials on a phishing page. However, due to multi-factor authentication, the attacker’s attempt to gain access to Coinbase’s internal systems failed.
The company’s cybersecurity team swiftly detected the attack and promptly contacted the affected employee, thus preventing further compromise. Although some contact information was exposed, customer funds and data remained secure.

AT&T, a telecommunications provider, notified approximately 9 million customers of a data breach after a marketing vendor was hacked in January.
The breach exposed Customer Proprietary Network Information (CPNI) from some wireless accounts, including account numbers, phone numbers, email addresses, and limited billing information.
AT&T clarified that sensitive personal information such as credit card details and Social Security numbers were not compromised. The company stated that its systems were not breached, and the incident primarily affected device upgrade eligibility information.
Michigan Health, part of the University of Michigan, confirmed that its public websites were affected by a cyberattack on a third-party vendor responsible for hosting some sites.
The attack caused intermittent website issues, but patient information remained unaffected and secure.
Michigan Health actively worked with the vendor to resolve the situation and expected the sites to be fully functional soon. Patients were still able to access the patient portal without any disruption.
Over 400 government websites in Nepal were hit by a distributed denial-of-service (DDoS) attack, causing disruption and delays at the Kathmandu airport. The attack targeted the Government Integrated Data Centre (GIDC), impacting various government ministry websites, including the Department of Immigration and Passports.
The attack lasted about four hours, with immigration systems going offline, resulting in the manual
processing of visas and passports. The GIDC, managed by the National Information Technology Centre, pledged to investigate the cyberattack and strengthen the system’s security.
According to a press release by the regional health agency, the Appui Santé Nord-Finistère association, based in Bretagne, France, was targeted in a cyber attack.
The attack occurred on January 26, 2023, and affected the association’s IT infrastructure, including personal health data stored in coordination support systems.
In response, the association shut down its entire IT infrastructure, initiated an analysis of the attack with a specialized IT service provider, and began reconstructing an independent and secure IT system.
Audifarma, a pharmaceutical company based in Pereira, Colombia, confirmed that it had been targeted in a cyber attack on its technological infrastructure.
The attack affected the company’s website, mobile application, virtual
shift services, and requests for medicines at home.
Audifarma activated its computer security protocols and disabled its physical and virtual servers to protect information. The company received support from international cybersecurity experts to analyze its systems and find a solution. Audifarma assured users that it had security mechanisms to safeguard their private information.

Brands lead to the closure of 300 restaurants in the UK
Yum! Brands, the parent company of popular fast-food chains KFC, Pizza Hut, and Taco Bell, had to close around 300 outlets in the UK due to a ransomware attack.
The attack prompted Yum! Brands to implement response protocols, take affected systems offline, and enhance monitoring.
Although data was taken from the company’s network, there is no evidence that customer databases were stolen.
Government websites in the Brazilian state of Tocantins were defaced in a cyber attack, with cybercriminals posting images of former President Luiz Inácio Lula da Silva in prison.
The Information Technology Agency (ATI) confirmed the incident and took the portals offline as a precautionary measure.
The Tocantins Civil Police, specifically the Cybercrime Division, was called to investigate the attack and identify the perpetrators.
The Media Center Ukraine, a national news agency and media center, was targeted in a cyber attack traced back to Russian intelligence.
The attack, which disrupted a press briefing by Ukraine’s information protection agency, was attributed to the Russian Sandworm hackers, also known as UAC-0082, with close ties to the Russian GRU.
The attackers used multiple types
of malware, including CaddyWiper, ZeroWipe, SDelete, AwfulShred, and BidSwipe. Although the cyberattack caused a temporary interruption, the Ukrainian authorities were able to restore connectivity promptly.
Several Danish banks, including Jyske Bank, Sydbank, and Djursland Bank, experienced a cyber attack, resulting in temporary disruptions to their online banking services.
The attack, believed to have been a Distributed Denial of Service (DDoS), overwhelmed the banks’ websites with high requests, causing them to go offline.
Bankdata, an IT solutions provider for these banks, confirmed the incident and stated that the issue had been resolved. While DDoS attacks do not compromise data security, they can render online services temporarily unavailable.

The websites of Czech presidential
candidates Petr Pavel and Tomáš Zima were targeted in a DDoS (Distributed Denial of Service) attack, making them difficult to access.
The attacks were attributed to the Russian hacking group NoName057 by Pavel’s team, with the information provided by the National Cyber and Information Security Agency.
The attacks involved overwhelming the websites with numerous requests from various IP addresses across Europe.
The Court of Justice of Pará (TJ-PA) in Brazil was targeted in a cyber attack, leading to the involvement of criminal experts from the Pará Scientific Police (PCEPA) to analyze the incident.
The Computer Expertise Management (GPI) of the PCEPA was called upon by the State Directorate for Combating Cyber Crimes (DECCC) to conduct a criminal investigation.
The experts began their work by examining the court’s Belém headquarters computer network, and its Santa Izabel do Pará facilities. They
also analyzed the computers to determine how the attacker accessed the TJ-PA system.
Royal Mail, the postal service in the United Kingdom, urged people to halt sending mail overseas due to a “cyber incident” that caused significant disruption.
The company could not send letters and parcels abroad while working to resolve the issue. Incoming mail to the UK faced minor delays, but domestic deliveries remained unaffected.
Royal Mail reported the incident to the UK’s cyber intelligence agency and law enforcement. The company called it a “cyber incident” since the cause was unknown.
On January 11, email marketing provider Mailchimp discovered unauthorized access to one of their tools, resulting in a targeted incident involving 133 Mailchimp accounts.
The breach occurred through a social engineering attack on Mailchimp employees and contractors, enabling the unauthorized actor to gain access using compromised employee credentials.
Mailchimp promptly suspended account access for the affected accounts and notified the primary contacts the next day.
NFT Investments Plc, a UK-based NFT investment firm, experienced a cyber security incident involving a fraudulent phishing attack. The attack occurred on January 9 and resulted in the loss of $250,000 of the company’s assets, representing less than 1% of its net asset value.

NFT Investments immediately implemented its incident response plan and commissioned a third-party report to investigate the incident. The company assured that there was no evidence of impaired financial performance.

 - By Vishwa Pandagle
- By Vishwa Pandagle

In January 2023, a cybercriminal group identifying themselves as “Anonymous Sudan” emerged as hacktivists. Throughout their operations, including OpSweden and OpDenmark, they targeted specific countries with the motive to fight against individuals who showed disrespect towards the religion of Islam.

However, doubts have been raised regarding the authenticity of Anonymous Sudan as a genuine hacktivist group due to the contrasting operational methods of the hacker collective when compared to conventional hacktivist groups.
These speculations have stemmed from concerns about the significant expenses associated with their attacking infrastructure, the timing of their cyber attacks, and their alleged affiliation with Russia.
After launching nearly 24 DDoS attacks on Australian organizations, Anonymous Sudan is expected to launch more cyber attacks on the nation, according to researchers. The 24 DDoS attacks were launched between March and April 2023.
And more attacks are suspected in the following months.
Anonymous Sudan hacktivism or pro-Russian attacks?
Anonymous Sudan launched cyber attacks against universities, airports, and medical institutions in France in March 2023.
The hackers from the group attributed their cyber attacks to the perceived humiliation of Islam’s religious figures through the depiction of cartoons. Their actions included threatening and releasing data obtained from cyber attacks conducted on various nations, including those belonging to NATO.
Moreover, the hacktivist group launched the OpIsrael campaign in support of proPalestinian causes and as a way to show support for the Palestinians oppressed by Israeli troops. They have also claimed Distributed Denial of Service (DDoS) attacks on Microsoft, which the company confirmed affected its product Outlook
One of the reasons behind the targeting of Microsoft was the meeting between the US Secretary of State, Antony Blinken, and Saudi Arabian officials, where discussions took place regarding the imposed sanctions on the Sudanese Armed Forces, among other factors.
Anonymous Sudan launched nearly 24 DDoS attacks between 24 March and 1 April on the aviation, healthcare, and education sectors. They called the campaign opAustralia, which was started on 17 March, targeting Australia.
Researchers suspect that the campaign was likely religiously motivated and has been conducted by a Pakistani hacktivist group.
Anonymous Sudan claimed to launch more attacks on Australia in retaliation to the clothing showcased at the Melbourne Fashion Festival, featuring the text ‘God walks with me’ written in Arabic.

Besides the cyber attacks by Anonymous Sudan, the incident had other hacktivist groups launch cyber attacks on nearly 80 Australian organizations, which may not have had anything to do with the fashion festival.
According to a blog by CyberCX on Anonymous Sudan’s authenticity, the following points were highlighted that questioned its true motives –

The hackers mostly operate between UTC 22:00 and UTC 06:00. And, over 80% of its cyber attack claims were made between UTC 06:00 and 18:00. The timings align with several East African nations and most of Sudan and Eastern Europe including Moscow.



Researchers argued that the motive behind the expensive DDoS attacks for a comparatively smaller impact on portals may not amount to a larger goal of the hacktivist. Moreover, the group targets Western countries, which remains consistent with Russian warfare strategies targeting those aligning with pro-Ukrainian nations, further solidifying the researchers’ claim.
Although the group claims to fight for religious reasons including defending the people of Sudan, the hackers started using the Arabic language only after their motives began raising questions.
Anonymous Sudan primarily utilizes Russian and English languages for their posts across various channels. Interestingly, they made their Arabic language post approximately a month after the establishment of these channels.
Researchers argue that the Anonymous Sudan hacktivism is instead a garb to increase the cost of cyber defense in Western countries and others.
They are a smaller group or just an individual who works for religiously motivated and financially motivated reasons.
They have also publicly shown their allegiance to the pro-Russian hackers of the Killnet group and have crossposted on each other’s channels about their cyber attacks.
What researchers have observed about Anonymous Sudan’s hacktivism

“Anonymous Sudan has no known overlap with the original members of the 2019 Anonymous Sudan operation, which was anti-Russia and pro-Ukraine,” researchers from CyberCX stated
The report further stated that the well-known group Anonymous clarified that they are not aligned with Anonymous Sudan.
“CyberCX assesses that Anonymous Sudan is likely to be an individual or a small, coordinated group rather than a grassroots hacktivist organization,” the report added.
The operational methods of the hacktivist group were questioned as well, as they exhibited a level of coordination not commonly seen among issue-oriented hacktivists.
In contrast to other hacktivist groups, who engage in semi-public discussions online to determine their targets for assault, Anonymous Sudan operates differently. Instead, they publicly declare their next targets while simultaneously launching cyber attacks.
After Anonymous Sudan publicly showed its support to the proRussian Killnet group, there was little confusion left about where its affinities lie. They use each other’s Telegram channels which signifies the closeness of operations and trust between Anonymous Sudan and the Killnet group.
It was observed that with increased attacks on Ukraine in the hands of Russia ever since February 2022 led to the formation of several pro-Russia hacktivist personas. Some of the more active groups targeting Ukraine and its allies were found to be Killnet and Anonymous Russia.
“In June, Killnet-affiliated threat actors including Anonymous Sudan announced plans to launch nonDDoS attacks on Western financial institutions and the SWIFT network in conjunction with REvil,” according to the CyberCX report.
REvil, the Russia-based group, extorted money from its target, including the prominent data breach at Medibank. It is a coincidence that
nearly when REvil’s darknet website went offline in the last few months, Anonymous Sudan gained traction for its activities. However, there has been no evidence to support claims of any connections between the two groups.

The CyberCX report maintained that the Russian intelligence was affiliated with pro-Russian hacktivist groups.
“We assess that it is highly likely that at least some members of the Killnet collective are linked to the Russian state,” the report further added. This brings a chance for Anonymous Sudan’s hackers to connect with Russia.
The cyber attack on a Canadian gas pipeline in April 2023 exposed sensitive US signals intelligence to pro-Russian hackers and a member of the Killnet group, Zarya. It was anticipated that an attack such as this would lead to an explosion.
Zarya was suspected to be on standby for instructions from the Federal Security Service (FSB) of the Russian Federation. The leaked briefing from the US classified data asserted that Zarya had controls to increase valve pressure, disable alarms, and start an emergency shutdown of the facility.
Addressing the authenticity of the claims of involvement of the FSB in the cyber attacks, a report read that the briefing showed signs of the hackers receiving instructions from someone presumed to be from the FSB.
The hackers claimed they had done enough damage to the Canadian, however, their intention was not to cause loss of life, only loss of income for Canadians,” according to a Zetter report.
It was concluded that Anonymous Sudan primarily targets Western organizations, specifically the government, media, and healthcare. Although the hackers from Anonymous Sudan claim that they are fighting for religious and Sudanese causes, they turn to seek monetary gains periodically.
Anonymous Sudan was formed three days before the Stockholm Quran burning incident, which led the group to cause cyber attacks in the region. It is suspected by researchers that Russian threat actors use hacktivists’ activities to strategically target European nations, among others. They cause disinformation to polarize Western societies.
Moreover, it was speculated that the Stockholm incident, which witnessed the burning of the Quran, was linked to a former contributor to the Kremlin-backed media outlet Russia Today.


Phishing and ransomware attacks on businesses and governments are on the rise, and criminals are becoming smarter with their tactics. The message is clear: enhanced international cooperation in strengthening cybercrime

legislation. By enhancing collaboration among countries, we can effectively address the growing challenges posed by cyber threats and close the enforcement gap.



Cybercrime is increasing for individuals, businesses, and nations alike. All countries are becoming increasingly affected by data breaches and phishing.
Looking at 93 different countries, the SEON Global Cybercrime Report discovered that the countries with the highest cybersecurity risk are currently Afghanistan, Myanmar, and Namibia due to a lack of or limited legislation.

Those with the lowest cybersecurity risk are Belgium, Finland, and Spain – protected by a combination of legislation and secure technology. An inability to properly enforce cybersecurity, whether that’s on a governmental or business level, is known as the enforcement gap.
While all countries tackle their own specific cybercrime issues, we can extrapolate from US-based data provided by the FBI-run US Internet Crime Complaint Center (IC3) that phishing and pharming attacks are on the rise generally.
This is because these types of attacks can affect all internet users regardless of nationality. Both practices involve convincing internet users to give away sensitive information such as passwords or credit card details.
Criminals can use tactics like social engineering to convince their victims that they are providing data to a trusted person (such as an IT support worker or boss). Also, thanks to the recent rise of Bitcoin, ransomware criminals are starting to demand cryptocurrencies from their victims. This is because it is difficult to trace the movement of currency from one anonymous account to another.
NPR found that: “if the cyber thieves live in countries like Russia — which many do — there’s virtually no chance of getting caught.” The above data demonstrates the significance of government legislation in protecting countries, businesses, and citizens against cybercrime.
Below, we will look at current efforts to improve international cooperation and where improvements can be made.
Cybercrime is a global issue that requires collective efforts. Therefore, this should take the form of sharing information, resources, and expertise.
The US government has proposed that some of the challenges to international cybercrime prevention include:
• Being able to commit the right personnel and resources, being able to identify criminals successfully;
• The ability to share the information collected on criminals internationally;
• he right laws are in place to prosecute cybercriminals. Intrusion detection systems
Developing a common legislative framework that all countries agree upon has, so far, proven to be a challenge.
The Convention on Cybercrime is considered the first international treaty in place to help address cybercrime globally. While the Convention deals with cases of fraud like phishing and pharming, it also aims to tackle criminal activity on the internet and computer technology generally.
According to the Council of Europe, it has been signed by 68 countries, including the USA, Canada, the United Kingdom, and Japan.
As the CCDCOE says, 80% of countries currently base their own legislation on the Convention. However, some countries have not agreed to sign the Convention: India has refused to sign, perhaps due to a lack of involvement in its original negotiation.
To combat cryptocurrency-related cybercrime (and therefore tacitly ransomware-based cybercrime), the United Nations plans to introduce a new treaty for all countries that aims to strengthen financial surveillance laws.

This would apply to any organization working with digital currency, requiring them to collect information on crypto users, which could remove some of the anonymity associated with cryptocurrency.
As cyber threats rapidly evolve – such as in the case of cybercriminals using AI to improve their phishing and pharming techniques – countries with less sophisticated methods and resources for dealing with cybercrime become at greater risk.
Therefore, the ability to share resources and solutions between countries is a possible solution to this issue.
Citizen knowledge of new techniques and discussion of legislation around cryptocurrency may also prove useful in keeping ahead of cybercriminals.
Education surrounding safe cryptocurrency usage is one weak point: thanks to the rise of new phishing techniques, cryptocurrency users are at risk of account takeover fraud if they provide sensitive information to criminals accidentally.
What’s more, many developing countries do not have the personnel and resources to prevent cybercrime, even if they agree to common frameworks for dealing with it. In response to this, the United Nations has established the Global Programme on Cybercrime, in particular for countries in Central America, Eastern Africa, MENA, South East Asia, and the Pacific.
Some of its aims are to strengthen communication between governments and the private sector on cybercrime, as well as help to build a long-term: “whole-of-government response to cybercrime, including national coordination, data collection, and effective legal frameworks.”
As a response to escalating cybersecurity concerns, we propose measures to improve investigative capabilities, such as investing in technology and training for law enforcement agencies.
While the private sector has worked hard to prevent fraud with the help of device fingerprinting and identity verification tools on the market, businesses and governments must work to combat new forms of cybercrime as they arise.
In their Global Security Outlook 2022, the World Economic Forum expressed that preventing ransomware attacks was a growing concern, emphasizing the importance of more secure networks, regulation of cryptocurrencies, and a more concerted effort on the part of law enforcement to arrest cybercriminals.
Finding common ground when it comes to cybercrime legislation is a complex task, but it is significant in helping to tackle new trends like phishing and crypto-ransomware attacks. Internxt’s article on online safety, staying safe online, is essential for anyone who uses the internet.

In truth, no one can afford to be reckless with their information online. Even today, there is a clear need for more harmonized laws, enhanced enforcement mechanisms, and information sharing to combat cyber threats effectively. We can close the enforcement gap and create a safer digital environment by fostering international collaboration.
Jimmy Fong, CCO at SEON, is a young veteran in the fraud detection space. The last three leading fraud and payments startups he has been involved in have been acquired by Visa, Ingenico, and American Express. He’s a regular speaker on disruptive technology in the fintech space and a massive advocate of flattening the tech barrier for merchants and financial institutions to fight fraud effectively. A graduate of Edinburgh University, he looks to marry his passion for tech with doing a bit of good in the world.






