

Comprehensive Digital Risk Protection with Cyble Vision
Capabilities
Darkweb and Open Internet Monitoring
Compromised credentials
Sensitive data leakage
Executive brand protection monitoring
Open-Source Intelligence
Cybercrime Intelligence
Advisories on 400+ threat actors and 700+ malware operators
Monitor 80% of Cybercrime markets

Cybercrime conversations/mentions in forums and markets
Attack Surface Detection & Hunting (DRPS)
Public facing assets
Vulnerable assets
Code Leakage (e g GitHub/bitbucket)
Cloud buckets S3, Azure
Malware campaigns
Third Party Cyber Scoring
Vendor risk score
Derived from Darkweb, deep web, attack surface, public breaches, disclosures, etc
Brand Reputation Monitoring (DRPS)
Fake/Typo Squatted Domains and Fake Content

Fake Domains and Fake Content
Fake app detection
Phishing URLs
Take downs
Social media monitoring
Threat Intelligence
IoCs
Security Advisories
Compromised Cards
BINs
ATM PINs









28

Threat Intelligence: What it is, And Why it Matters


HOT SEAT
36 New in Open Source Intelligence? Here Are Ten Wildly Effective OSINT Tools
46
The Dark Side Of Anonymity: A Closer Look Into 4chan Communities
56 64
AI’s Sinister Grip: AiGenerated Models, Deepfake Scams, Voice Cloning….. What Lurks Beyond?

BOTTOM LINE
Exploiting Digital Playground: Why Are More Kids Becoming Hackers, Turning To Cybercrime?

Editorial Management
Augustin Kurian Editor-in-Chief editor@thecyberexpress.com
Chandu Gopalakrishnan Executive Editor chandu@thecyberexpress.com
Avantika Chopra Associate Editor avantika@thecyberexpress.com
Vishwa Pandagle Journalist vishwa@thecyberexpress.com
Ashish Khaitan Journalist ashish@thecyberexpress.com
Rajashakher Intha Director - Marketing & Technology raj@thecyberexpress.com

Ashish Jaiswal Conference Manager ashish.j@thecyberexpress.com
Priti Chaubey Content Strategist priti.c@thecyberexpress.com
Ravi Gupta SEO Analyst ravi@thecyberexpress.com
Vittal Chowdry Design Lead vittal@thecyberexpress.com
From The Editor’s DESK
Welcome to the June issue of The Cyber Express, where we embark on an immersive journey through the everevolving world of cybersecurity, delving deep into the multifaceted realm of Threat Intelligence. In this edition, we explore the intricacies of this crucial field, shedding light on its true essence and illuminating the distinctiveness that sets it apart from the malevolent practice of doxxing.
As we commence our odyssey, we take a momentous pause to reflect upon the five-year anniversary of the General Data Protection Regulation (GDPR). This ground-breaking regulation has revolutionized how we perceive and safeguard our personal data, reshaping the digital landscape and instilling a sense of empowerment in individuals and organizations alike. Join us in celebrating this momentous milestone as we pay homage to the transformative power of the GDPR.
In our relentless pursuit of knowledge, we turn to the sagacious words of renowned cybersecurity researcher Andrew Patel. With his vast expertise, Patel unravels the intricate web of Social

Engineering in the age of Artificial Intelligence.
Prepare yourselves for an extraordinary revelation as we present the definitive list of the top ten exceptional ONIST tools. These remarkable instruments serve as indispensable companions, arming cybersecurity enthusiasts and professionals with an array of advanced capabilities to fortify their digital defenses.

Venturing into the shadows of the cyber world, we embark upon an exploration of the enigmatic 4Chan communities. In this captivating article, we unveil the dark side of anonymity and its potential for cultivating malevolence. The veil of secrecy that shrouds these online spaces is not without consequence, and we must shed light upon the complexities and risks associated with these hidden corners of the internet.
Prepare to be captivated by an extraordinary exposé on the emergence of AI-generated love scams. This thoughtprovoking article delves into the sinister techniques of deepfake and voice cloning, revealing the disturbing implications of
their application in the realm of cyber deception. As technology advances, so does the potential for deceit, and it is imperative that we remain vigilant against the insidious manipulation of our emotions in this digital age.
Lastly, our gaze turns to a disquieting reality as we address the alarming rise of young individuals in the realm of cybercrime and hacking. Through an insightful lens, we delve into the root causes behind this burgeoning trend, seeking to understand the motivations that drive our youth toward these illicit pursuits. As society grapples with this complex issue, it is essential that we foster education, awareness, and mentorship to guide our youth toward more positive and ethical endeavors in the realm of cybersecurity.
In this remarkable edition of The Cyber Express, we invite you to immerse yourselves in a captivating tapestry of knowledge and discovery.
Most importantly,
We welcome your feedback at editorial@thecyberexpress. com Stay
IMPORTANCE OF DATA SECURITY AND GDPR INCEPTION
 - By Mike Gunion
- By Mike Gunion
VP, Sales & Marketing at Infinit-O Global, Limited

As our reliance on digital data increases, so does the need for robust data security measures. As stated in the 2022 Official Cybercrime Report , the expense of cybercrime is expected to reach $8 trillion in 2023 and $10.5 trillion by 2025. With customer information stored in vulnerable databases all over the world, data security has never been more critical.
According to a study titled “ The Virtual Battleground,” identity fraud losses totaled $52 billion and affected 42 million US adults.
In this article, we will explore the importance of data security and the inception of the General Data Protection Regulation (GDPR) in addressing these issues.





DIGEST
The Implications of Effective Data Security
As businesses increasingly rely on data for decision-making and providing personalized services, the importance of data security in the enterprise cannot be overstated.

Data breaches can lead to significant financial losses, reputational damage, and legal ramifications.
Furthermore, the loss of customer trust can be just as damaging, particularly for small businesses that rely on long-term relationships with clients. As such, securing data is crucial for maintaining client trust and preventing potential breaches.
A key aspect of data security is understanding the different types of threats that can compromise information. These threats can be categorized into the following three main areas:
• Confidentiality: It involves ensuring that only authorized individuals can access sensitive data
• Integrity: It focuses on preventing unauthorized changes to the data.
• Availability: It ensures that authorized users have access to data when needed.
By addressing these three aspects of data security, businesses can develop a comprehensive strategy to protect their valuable information assets
Data Security’s Role in Protecting Information and Impacts of Data Breaches
When a breach occurs, clients may face loss of trust, financial loss, and
even identity theft, among other consequences. The potential impacts of a data breach highlight the need for businesses to prioritize data security and protect their clients’ sensitive information.
In addition to the immediate financial losses resulting from a breach, companies may also suffer long-term reputational damage.
Relationships with vendors and partners may also be adversely affected, leading to a decline in business and potential litigation. Moreover, a data breach can expose sensitive intellectual property, potentially undermining a company’s competitive advantage in the market.
To better understand and manage the risk of data breaches, businesses should consider conducting regular risk assessments and audits.
These assessments can help identify vulnerabilities in the organization’s data management practices, allowing for the implementation of targeted security measures to address these weaknesses.
Additionally, businesses should develop a robust incident response plan to ensure a swift and effective response to any data breach events.
Data Security Measures and Strategies
To safeguard client data, robust data security measures may include:
• Encryption
• Multi-factor authentication
• Regular data backups
• Intrusion detection systems
By employing such measures, businesses can minimize the risk of unauthorized access, protect sensitive information, and ensure the confidentiality, integrity, and availability of client data.
Encryption is a crucial element of data security, as it renders data unreadable to unauthorized individuals. By encrypting data both at rest (e.g., on storage devices) and in transit (e.g., during transmission over networks), businesses can significantly reduce the risk of data breaches.
Multi-factor authentication, on the other hand, requires users to provide multiple forms of identification before accessing sensitive data, adding an extra layer of security to prevent unauthorized access. Regular data backups help ensure the availability of data in case of system failures, while intrusion detection systems monitor networks for signs of malicious activity.
In addition to these measures, the implementation of the General Data Protection Regulation (GDPR) framework has significantly impacted data security practices.
The GDPR is a comprehensive set of data protection rules that apply to businesses operating within the European Union and those dealing with EU citizens’ data. The regulation aims to give clients more control over their personal data and enforce greater transparency and accountability among businesses that handle such data.


Increased Data Breach Transparency
One of the key aspects of the GDPR is the requirement for businesses to report data breaches to the relevant supervisory authority within 72 hours of becoming aware of the breach.

This increased transparency helps ensure that organizations take the necessary steps to mitigate the effects of a breach and prevent future incidents. Additionally, the GDPR mandates that organizations inform affected individuals without undue delay if the breach poses a high risk to their rights and freedoms.
Improved External Security
The GDPR has also led to improved external security measures. Businesses are now required to conduct regular risk assessments and implement appropriate security measures to protect personal data. Furthermore, the regulation encourages organizations to adopt a “privacy by design” approach, meaning that privacy considerations should be integrated into the development process of new products, services, and processes.
How Can You Protect Your Data and Stay Secure?
With the growing threat of cybercrime and the potential consequences of data breaches, businesses must prioritize the protection of their clients’ sensitive information. Implementing robust data security measures, such as encryption, multi-factor authentication, and intrusion detection systems, can help safeguard client data and maintain trust.
The inception of the GDPR has significantly impacted data security practices, fostering increased transparency and accountability among businesses that handle personal data.
By giving clients more control over their data and enforcing stringent security requirements, the GDPR has not only strengthened data protection but also increased trust between clients and businesses. As a result, businesses that prioritize data security and embrace GDPR compliance are better positioned to thrive in today’s digital landscape.
SOCIAL ENGINEERING IN THE AGE OF AI
 - By Andy Patel Senior Researcher, WithSecure
- By Andy Patel Senior Researcher, WithSecure




INSIDER
Generative models will soon be integrated into the productivity tools we use daily. AI features will be included in word processors, email clients, artistic software, presentation software, search engines, and more.

Extrapolate forward a little, and those models will be built into operating systems, available for use with just a few API calls, precipitating a new generation of apps we haven’t even thought of yet.
Generative AI’s integration into the tools we use every day means that it’ll be used to create both benign and malicious content. Thus, detecting whether a piece of content was created by an AI won’t be enough to determine whether it’s malicious. Adversaries will use these technologies as much as we do. And they will become more productive just as we will.
One way they might use generative AI is to create content designed to socially engineer us. It’s not like AI will refuse to generate social engineering content. Most of it is designed to look like regular business and interpersonal communication anyway. Social engineering content is, almost by definition, designed to look benign.
Ask ChatGPT to write an email from you to a colleague, telling them that you are in a hurry to get their feedback on a presentation that you are working on, and it’ll happily comply. There’s nothing malicious about that request. The same goes for an email informing someone that you just bumped into their car in the company parking lot. And the same from a partner or authority requesting someone to re-upload some confidential documents to a new repository that was created in response to GDPR rules.
In a study I published earlier this year, I used a large language model to generate various types of undesirable content ranging from phishing, to fake news, to online harassment. It complied with my every request and did a great job writing the content I asked of it.
While I was conducting that research, access to GPT-3 wasn’t cheap. So I speculated that criminals would adopt it based upon a return of investment calculation – whether paying to generate content would be cheaper than writing it themselves or sticking to the copy-paste methodology they were already using.
And then it got cheaper. Ten times cheaper, for instance, when gpt3-turbo was released. And then stuff like alpaca ¬– a model you can run on a laptop – came out. At this point, I had imagined that using a language model to create content is practically a no-brainer.
So why would an adversary use a language model to create phishing and spear phishing content?
For phishing, the case is fairly obvious. You write one prompt. You supply it to the model many times. And each time, a slightly different piece of content is produced. This allows you to send dozens or hundreds of different spam emails out instead of copy-pasting the same one as you might be doing right now.
Also, these models write good English. Phishing messages are known for their spelling mistakes, grammatical errors, and bad English.
People can almost spot a phishing email because of how badly written it is. But GPT-3 doesn’t make those kinds of errors.
Oh, and it can write in other languages, too. A criminal operation utilizing GPT-3 doesn’t need someone capable of writing good English anymore. They also don’t need people who can write in other languages. And they don’t need to worry about whether Google Translate will do a good enough job.
For spear phishing, the reason to use a language model might seem a little less clear. Why write a prompt to generate a piece of content you may only use once or a few times? I already mentioned one reason – to produce high-quality writing in a language you may not be fluent in.
The other, which is less obvious, is to do style transfer.
It is possible to present a language model with a written style and then ask it to write in that style. This is something that even a trained writer may find difficult. The ability to have a model generate content in a specific written style enables an attacker to better impersonate someone. And that gives the attack a better chance of succeeding.
And there are other nefarious things you might do with style transfer. Inject a fake document into the trove of documents you are about to release to the public after a hack-and-leak operation. How would the owners of the faked document possibly refute its authenticity?
Spear phishers could also use a large language model as a sort of chatbot.
Some highly targeted spear phishing tactics involve a process whereby the attacker builds trust with their victims over time. This connection is built over multiple back-and-forth messages. A large language model could be used to automate this trust-building process, thus allowing attackers to scale their operations.
Another option that hasn’t been explored yet is to use a language model to suggest tactics that might be used to socially engineer an individual. Present such a model with some of their social media posts, or perhaps a curated list of facts harvested from scraping their presence from the Internet and ask it the right questions. One might even envision a taskbased architecture that can select one of the victim’s contacts and gather the content required to mimic their writing style.

INSIDER
There are no obvious technological solutions that can definitively tell us whether we’re being socially engineered, whether it be by humans or their AI buddies. So, for now, we’re going to have to rely on vigilance. And that is built by things like media literacy and phishing awareness training.
One approach to phishing awareness that I’ve not seen a lot of mention of is to teach users about the psychology used in social engineering attacks. We could be teaching employees about concepts such as confirmation bias, authority bias, and scarcity.
The principle of social proof can further help in such training – by encouraging employees who’ve identified and reported threats, or even fallen for them, to share their stories, so that others will learn how to be more vigilant in the future.
Creating an environment where employees help one another to identify threats might be useful if they do it without forwarding potentially malicious content to each other. And finally, a company might consider rewarding employees for following safety protocols and reporting threats.
There’s no silver bullet against social engineering attacks. But vigilance and awareness are going to beat overconfidence in technological solutions. At least for now.


The Thin Line Between Threat Intelligence and Doxxing

While cybersecurity companies are unanimous in their stand that doxxing is harmful, two crucial factors decide whether threat intelligence gathering falls under doxxing: purpose and tools
- By Chandu GopalakrishnanDoxxing. Although the term has been in the cybersecurity news for over a decade, Elon Musk gave it Universal recognition in December 2022 when he, as the owner and CEO of Twitter, suspended the handle @Elonjet
Reason? Doxxing.
Jack Sweeney, a 19-year-old freshman from the University of Central Florida, started monitoring and sharing information about Elon Musk’s flight paths in June 2020.- The updates were published live on @Elonjet.
Elon Musk reportedly offered Sweeney $5,000 to shut down the Twitter account where he was publishing the information, but Sweeney turned down the offer and requested $50,000 instead
Despite Musk’s refusal to pay, the account (@Elonjet) gained over 300,000 followers and was later blocked by Twitter in December 2022 due to Musk’s concerns about his personal security.
The fact that Musk’s flight details were publicly available triggered the debate on whether Sweeney’s act constitutes as doxxing, and a larger concern about whether opensource intelligence (OSINT) methods and processes can be considered doxxing.
Collecting and sharing cyber threat intelligence is never doxxing, cybersecurity practitioners told The Cyber Express. However, the thin line of classification between threat intelligence and doxxing remains highly susceptible to interpretation.

FORESIGHT
Doxxing, Musk, and open source information
Doxxing – short for dropping documents – is the act of curating and publicly announcing Personal Identifying Information (PII) about a person, group of people, or a firm on the internet.

Sweeney’s initial motivation for tracking flights was his hobby, which began with monitoring influential personalities’ jets but expanded as he gained popularity.
At a very young age, his work has brought him unexpected fame and recognition, with a large following on his social media accounts and numerous media articles covering his work.
Reports indicate that Sweeney tracks more than 127 other flights, including those owned by influential individuals such as Bill Gates, Jeff Bezos, Donald Trump, and several Russian oligarchs, including Vladimir Putin.
He also recognized the potential of transforming his hobby into a business due to the significance of the information he had access to. As part of a deal, he agreed to stop tracking Mark Cuban’s jet in exchange for business advice.
After failed negotiations between Musk and Sweeney, tables turned when Musk acquired Twitter
The @Elonjet account was restricted in December 2022 and subsequently blocked, along with the personal Twitter handle and other flight tracking accounts operated by Sweeney.
The move was part of the larger Twitter account suspensions in
December 2022, triggering conspiracy conversations that Musk’s hurried and heated Twitter purchase was for taking these accounts down and silence any conversation that these accounts caused.
Ten journalists, including Keith Olbermann, Steven L. Herman, and Donie O’Sullivan from The New York Times, The Washington Post, CNN, and The Intercept, had their Twitter accounts suspended by the platform on December 15, 2022.
According to Musk, they were in violation of the doxxing policy, announced a day before the ban. At first, it was believed that the suspensions were permanent, but Musk later clarified that access to the accounts would only be restricted for seven days. Some of the accounts were restored earlier.
Twitter did not offer any explanation for the decision initially, but later said that the ban was due to a new rule that prohibited the sharing of realtime flight information of private jets.
All the suspended accounts had one thing in common: they had posts with information attributed to the @ElonJet account or links to it. @ ElonJet and other similar accounts were suspended from Twitter on December 14, 2022, but continued to operate on Facebook, Mastodon, and other social media platforms.
“Any account doxxing real-time location info of anyone will be suspended, as it is a physical safety violation,” Musk tweeted then.

Many of the suspended journalists said they had not violated the rule, and while some had included links to @ElonJet in their articles or reported about the account, it was already suspended at the time of media reports.
Mastodon’s Twitter account was also suspended after linking to @ElonJet. Musk ran two Twitter polls asking followers when the accounts should be restored, and in both cases, a majority of users said it should happen immediately.
Following those polls, Musk reinstated several of the accounts, but others remained suspended, and some journalists were told that their accounts would not be restored unless they deleted certain posts, as outlined in the Twitter enforcement policy.
The suspensions received criticism from various organizations and individuals, who claimed that they undermined Musk’s repeated claims of supporting free speech on Twitter. The suspensions were condemned by representatives of several countries and organizations, including the United Nations and the European Union.
EU officials said the actions may have violated the Digital Services Act, which could result in sanctions or even a ban of Twitter in Europe. The Government Accountability Project filed a complaint with the United States Congress regarding the suspensions.
All the while, Musk had been adamantly citing doxxing as the major reason for suspending all these accounts. Where does open source intelligence turn into doxxing? Can threat intelligence be considered doxxing?
OSINT, threat intelligence, and doxxing
Cyberattacks are a significant threat to organizations, and Cyber Threat Intelligence (CTI) is a crucial tool for preventing, detecting, and responding to these attacks.
Details of vulnerabilities and alerts on data breaches and ransomware attacks also fall under threat intelligence. However, threat intelligence is not the same as doxxing although there are similarities in the methods used to collect the information, cybersecurity practitioners told The Cyber Express.
“The main difference between threat intelligence and doxxing is the intention and purpose behind the collection of information,” Amit Spitzer, Chief Security Officer at Cato Networks, told The Cyber Express.


“Threat intelligence is focused on identifying potential security risks and protecting against them, while doxxing is often done with malicious intent and can be used to harm.”
CTI can be classified into three types: strategic, tactical, and operational. Each type serves a unique purpose, and integrating them provides a comprehensive understanding of the threats an organization faces.
Strategic CTI is long-term planning that identifies broad trends. It assesses an organization’s overall risk posture and helps formulate strategies to mitigate potential risks.
I don’t think threat intelligence can be considered doxxing. Threat intelligence focuses on attacks more than attackers. And although threat intelligence might reveal personal information about attackers, doxxing is done with the intent to publicize private information.
Paul Bischoff
Consumer Privacy Advocate at Comparitech
Tactical CTI gathers and analyzes information about potential threats to an organization, with the aim of identifying and mitigating those threats.
Operational CTI provides realtime information that is useful for responding to active threats. It can track adversary movements and take immediate action to thwart an attack. It aids organizations in understanding the motives and capabilities of their adversaries, as well as their likely next steps.
“Threat intelligence is the collection and analysis of information about potential threats to an organisation or individual. This information is typically limited to Tactics, Techniques, Procedures (TTPs) and Indicators of Compromise (IOCs) from threat groups,” explained Brad Freeman, Director of Technology at SenseOn.
“It does not normally extend to personal information about the actors involved in the activity.” All these steps involve data collection about the organization concerned as well as the competitors. Independent cybersecurity companies collect this data from clear, deep, and dark web.
“Threat intelligence focuses on attacks more than attackers. And although threat intelligence might reveal personal information about attackers, doxxing is done with the intent to publicize private information,” Paul Bischoff, consumer privacy advocate at Comparitech, told The Cyber Express.

“Part of an organization’s threat intelligence might involve internally digging up information about employees to see who on staff might be vulnerable to doxxing or other attacks, but that info is not publicized.”
While cybersecurity companies are unanimous in their stand that doxxing is harmful, a crucial factor turns detrimental in determining whether threat intelligence gathering falls under doxxing: the source of the information.

“While the concept of doxxing is decades old, doxxing is still alive and well today — and it can be very dangerous. Once someone’s physical address, job location, phone number, email, or other information is out there, they become an easy target,” read an advisory by cybersecurity company Avast
Chief Security Officer at Cato NetworksThreat intelligence is not the same as doxxing, although there may be some similarities in terms of the collection of information. The main difference between threat intelligence and doxxing is the intention and purpose behind the collection of information.
Amit Spitzer
The act of doxxing has become simpler than ever in the era of technology. A person can easily search for and find personal information about someone else with just a few clicks.
Typically, this information can be located on various social media platforms, forums, and websites where people voluntarily disclose their personal details.

Doxxing can have serious consequences, including causing victims to go into hiding and face harassment, physical threats, embarrassment, fear, anxiety, and depression. However, the legality of doxxing depends on the laws of the jurisdiction in question.
“It’s usually not a crime to publish already publicly available information about a person. For example, it’s usually not illegal for you to tweet someone’s office phone number that you copied from their website,” said an analysis report by Malwarebytes
Labs.
“But it is illegal if you tweet a personal phone number that you stole from a device. In other words, doxxing is generally illegal if the doxer takes the data through illegal activity.”
Take the case of Reddit user Michael Brutsch, who used his online identity violentacrez for trolling. He became known as a troll due to his controversial posts, including subreddits featuring misogyny and sexualized images of underage women.
For a long time, Brutsch successfully kept his real identity secret, but Gawker journalist Adrian Chen was able to dox him by connecting him to violentacrez.
Brutsch’s risky behavior, such as attending Reddit meetups and hosting a podcast with his voice, helped Chen uncover his true identity.
After being doxxed, Brutsch lost
his job and faced public shame, exacerbated by a CNN interview he did. There is little information available about what happened to him after this incident, but his notorious history as a Reddit troll remains easily accessible online. Like the ethics of doxxing, the legal view on it is also highly debated, and is subject to the geography of action.
Doxxing and threat intelligence: What does the law say?
The legal landscape surrounding doxxing is still developing, and while not every case may be unlawful, it can be considered unethical. Even if individuals are not prosecuted for doxxing, they may still face consequences such as being banned from social media platforms and websites.
FORESIGHT

“In the United States, the legality of a doxxing attack depends on how the information was obtained and whether the information was public before it was released. It may also depend on the specific circumstances and wider patterns of behavior surrounding the attack,” read an advisory by cybersecurity business ZeroFox
“If a digital threat actor gains access to the target’s PII through legal means (e.g. using open source intelligence) then it may be legal to publish that information. However, if the threat actor unlawfully gains access to the target’s information, they could be charged under federal antihacking laws.”
The source of the information is detrimental in deciding the legality of the doxxing attempt, US-based law firm Salar Atrizadeh corroborated
“Doxxing is illegal especially if the published information could not be found in the public domain and was illegally obtained by the culprit. It can constitute a violation of state or federal laws if it was intended to threaten, annoy, harass, or intimidate the victim,” explained a blog post by the law firm.
“For example, doxxing a federal government employee (e.g., senator) can be in violation of federal laws. Doxxing can be illegal in some jurisdictions when the victim’s residential address and mobile number are posted on the internet to invite others to blackmail the victim.”
Doxxing is not considered illegal mainly because much of the information that is disclosed is already accessible on the internet. What distinguishes doxxers from others is that they go to greater lengths to unearth personal data than the average person would.
The general consensus in the US is that exposing personal information of a famous person is not necessarily a criminal offense, unless it is used to make threats or to commit identity theft or unauthorized access to private email accounts, according to American lawyer David Lindsey
“According to cyber crimes experts, the line between legal doxxing and criminal doxxing is actually quite clear: any information obtained cannot be used for financial gain, nor can you use the information to impersonate someone,” Lindsey wrote in an explainer
“And if you accessed the information through illegal means, you’ve committed a crime and all actions that follow are also crimes. Posting personal information, obtained legally, in and of itself is perfectly legal.”
“Doxxing is the act of publicly releasing private or identifying information about someone without their consent. It is often done to harass, intimidate, or harm someone. The information released is likely to include home and work addresses, financial details, and other private information,” noted SenseOn’s Brad Freeman.
“To put it another way, doxxing is the work of an amateur likely against an individual. Threat Intelligence is the work of professionals against a threat group.”
Brad Freeman Director of Technology at
Threat intelligence and doxxing are different concepts. Threat intelligence is the collection and analysis of information about potential threats to an organisation or individual. This information is typically limited to Tactics, Techniques, Procedures (TTPs) and Indicators of Compromise (IOCs) from threat groups. It does not normally extend to personal information about the actors involved in the activity.
SenseOn

Threat Intelligence: What it is, And Why it Matters

 - By Vishwa Pandagle
- By Vishwa Pandagle


What is the importance of threat intelligence?
Ridiculous question.
The fact that you are reading this, and that at least one entity is aware of it and is storing the information that you read it, and the extremely high possibility of at least one person being aware of it without your consent, increase the relevance of threat intelligence in 2023.
From right defense against ransomware gangs to getting your incident disclosure right, cyber threat intelligence plays a major role in organizational operations.
“Threat intelligence is data that is collected, processed, and analyzed to understand a threat actor’s motives, targets, and attack behaviors,” according to cybersecurity firm Crowdstrike.
Threat intelligence enables us to make faster, more informed, databacked security decisions and change their behavior from reactive to proactive in the fight against threat actors.
Simply put, cyber threat Intelligence is nothing but information about
threats that may leave information exposed, and depending upon specific cyberattacks, financial loss.
Cyber threat intelligence or online threat information helps companies, enterprises, and individuals take better precautions so incoming attacks are prevented.
Cyber threat intelligence is secured by analysts and researchers besides legal authorities who employ digital tools and human resources to keep a tab on online crime. There are several mediums where cybercriminals join to sell malware, develop malicious software, leak data, and hire hackers
A cyber threat team belonging to the government, organizations, or independent researchers keeps a close eye on underground forums, Telegram channels of notorious gangs, leak sites, breach forums, and more.
Each is used for several general and specific information sharing by cybercriminal groups.
How do we gather cyber threat intelligence?
Cyber threat intelligence has grown much bigger from the simplistic explanation. The possibility of a cyber attack comes in-built with any connected device. Entire businesses have cropped up to address the growing demand for threat intelligence.

The implementation of artificial intelligence for cybersecurity is driving the expansion of the global Threat Intelligence Market. It is projected to grow from USD 4.93 billion in 2023 to USD 18.11 billion by 2030, according to a research report by Fortune Business Insights.
Cyber threat intelligence gathers information about risks to online security posed by any individual. These individuals or groups may plot, create specialized software, launch phishing emails, attack vulnerability, or leak exfiltrated data.
Information about online threats to individuals, organizations, governments, etc., is collected and defenses are put in place to stop them before it strikes. Or, appropriate measures are taken to prevent a further attack if the incident has already occurred.
Cyber threat intelligence reports also help in nabbing cybercriminals and closing their websites, as seen in the seizure of the Hive ransomware group network, and nabbing of Conor Fitzpatrick.
Fitzpatrick, aka Pompompurin ran the infamous BreachForums where several illegal data leaks and breaches were publicized and sold by threat actors.
The information gathered has to go through a five-step process of conversion, from threat intelligence to actionable intelligence, according to cybersecurity company Flashpoint.

The five phases of cyber threat intelligence
PHASE 1: Planning and Direction
“The first step in this process is to set the direction of your program, meaning you need to outline what you’re looking for and what questions you want to ask and answer,” said an analysis by cybersecurity business Rapid7.
In phase one of the threat intelligence lifecycle, the main goals and tasks for your threat intelligence program are laid out, which are often referred to as intelligence requirements (IRs). The IRs should reflect the core objectives of the team and the value that finished intelligence will ultimately deliver.

Senior leadership, such as the Chief Information Security Officer (i.e., the CISO or CSO), will guide planning and direction at this stage and establish the core program goals and challenges, along with all potent external threats.
Key considerations in phase one include determining which types of assets, processes, and personnel are at risk, how threat intelligence can improve operational efficiency for the team, and what other systems and applications could benefit.
PHASE 2: Collection and Processing
In phase two, data quantity and quality are both crucial aspects of the threat intelligence collection stage.
“Your goal is collect as much information as possible about potential threat vectors, existing vulnerabilities, and publicly available information a threat actor could use to gain unauthorized access to your systems,” noted cybersecurity company Synk
Intelligence collection establishes the scope of your sources, both in terms of the data volume and type. The processing component then seeks to normalize, structure, and deduplicate all of the amassed data.
CYBERVILLE
Specific processing procedures often include reducing the volume of raw data, translating conversations obtained from foreign-language dark web marketplaces and illicit forums, and metadata extraction from malware samples.
Key considerations in phase two include identifying current internal and external blindspots, determining what technical and automated collection techniques can be employed, and assessing how well your team can infiltrate cybercriminal forums and closed sources on the dark web.
PHASE 3: Analysis
“Threat intel analysis is an integral phase of the threat intelligence lifecycle where security analysts make sense of collected threat data by adding context,” said a report by cybersecurity business Cyware
“It is in this stage that threat information is correlated and
contextualized to identify potential security issues and develop actionable insights that are needed to create appropriate countermeasures to respond to the identified threats.”
During the analysis phase, the enriched and contextualized threat intelligence is derived through the application of known structural data or advanced correlation and data modeling techniques.
As artificial intelligence and machine learning technologies continue to advance, certain human-oriented tasks will become increasingly automated, allowing operational resources and staff to focus on more strategic tasks and investigations.
Phase three involves identifying which assets, processes, and personnel are at risk, assessing how threat intelligence can improve operational efficiency for the team, and identifying other systems and applications that could benefit from the same.

PHASE 4: Production
After completing the threat intelligence analysis, the focus of phase four shifts towards developing easy-to-understand graphical charts, dashboards, and reports based on the finished intelligence.
“During production, it’s essential to identify the most meaningful information and derive logical conclusions from the data and analysis completed in the prior phase,” said the Flashpoint report
Specific processing procedures often include reducing the volume of raw data, translating conversations obtained from foreign-language dark web marketplaces and illicit forums, and metadata extraction from malware samples.
“Recommendations that outline appropriate courses of action will often include prepared decision trees and procedures to initiate incident and ransomware response, threat remediation, and patch management, among many others.”
Phase four involves identifying the most critical findings of the analysis, determining the best way to present them visually, evaluating the reliability, relevance, and accuracy of the analysis, and determining any clear and concrete recommendations or next steps for the final analysis.
PHASE 5: Dissemination and Feedback
Dissemination involves getting the finished intelligence output to the places it needs to go,” noted a cybersecurity company.
Finished intelligence reports are distributed to the appropriate stakeholders, including dedicated fraud teams, cyber threat intelligence (CTI) teams, security operations (SecOps) teams, vulnerability management teams, third-party risk teams, and senior leadership teams responsible for resource allocation and strategic planning.
Upon receiving the finished intelligence, stakeholders evaluate the findings, make key decisions, and provide feedback to continually refine intelligence operations. Data collection can be automated, but detecting patterns and threats from them require the seasoned eyes of an analyst.
Cyber Threat Intelligence: What is the role of analysts?

“Cyber threat intelligence analysts are specialists in cyber threat, who use their analytical and technological skills to address complex cyber threat challenge issues, generate detailed reports, and brief the company on short and long-term security concerns,” explained SOCRadar
“This work involves effort, creativity, research, and technical skills.”
CTI analysts don’t just work with present cyber intelligence threats but also create future plans to create better defenses. Their insights offer regular guidance to engineers in developing tools to have better detection, prevention, and reporting of online threats.
CYBERVILLE
They have expertise in gathering raw data, filtering what is relevant and critical, investigating, and deciding on the best course of action to assure digital security.
CTI analysts working for cyber threat intelligence firms make sure they have the best tools in place while making way for adapting to future trends that might prevail.

Cyber threat intelligence teams also keep key focus on raw data which is analyzed to further understand what the cybercriminals might have intended to do with the software and how they were able to perform security breaches.
Several cyber threat intelligence companies follow models and patterns that help them detect threats and gain greater knowledge.
Some of the prominent threat intelligence companies are
Mimecast threat intelligence, Palo Alto Networks, VirusTotal Intelligence, and Y Combinatorbacked Cyble
1. The dynamic intelligence feed offers the data they use to investigate threats.
2. Using cognitive technologies to foretell if threat actors placed specific automation processes helps in swiftly completing investigations.
3. Employing a bidirectional integration platform by the cyber threat intelligence team elevates functionality across the IT ecosystems and eases better communications.

4. Smart data visualization is nothing but the presentation of complex or any found data about threats in an easy manner. The complexity of attacks is unfolded with simpler maps, graphs, charts, and diagrams.
5. Analysis tools make several detection and representation work easier with reports that explain what it is fed to understand. It may also help efforts in having better collaboration between intelligence agencies in different countries to take better cohesive actions.
The kind of data and its analysis used by cyber threat intelligence officials
Different pieces of information, tech, and previous reports are investigated to perform analysis and functions leading to creating guards against cyber threats. There are several ways different teams approach this work.
However, a few techniques are commonly observed in cyber threat intelligence work.
• Tactical Threat Intelligence
Suspicious IP addresses, file hashes, unexpected network traffic, and malicious domain names are investigated to stop them from reaching their targets. This is often done in tactical threat intelligence.
• Operational Threat Intelligence
Cybercriminals are investigated to further investigate their attacks and attack vector. A large portion of this analysis relies on human intelligence besides artificial intelligence feed.
Information and experiential data are correlated to draw conclusions and come closer to the threat in operational threat intelligence.
• Strategic Threat Intelligence
The motivations of cybercriminals combined with their connection with other criminal networks are closely analyzed in this method.
Geographical targets that are outside the jurisdiction of specific threat intelligence groups are investigated by collaborating with officials across the globe. War crimes and cyber espionage are closely monitored in this threat intelligence with attention to concrete actions to prevent them.
Cyber Threat Intelligence: In a nutshell

An active, diligent, and proactive team of cyber threat intelligence can help create one of the best defensive infrastructures to combat or thwart any online threat. Artificial Intelligence lends a helpful hand in minute data analysis and creating reports to facilitate research and results.
The best practices are updated based on cyber threat intelligence reports that identify common factors and unique activities in malicious software and online platforms. It helps to create defenses while proactively anticipating the Tactics, Techniques, and procedures (TTPs) used by cybercriminals.
Cyber threat intelligence is nothing but foreseeing threats, understanding the likelihood of tricks to be used by hackers and developers, and analyzing risk to cover it before it hits the infrastructure. Cybercriminals, no matter how far ahead they plan to reach, their footprints and traces of crime lead cyber threat intelligence teams to them.
New in Open Source Intelligence? Here Are Ten Wildly Effective OSINT Tools
US $58.21 billion. That is the projected market value for open source intelligence (OSINT) products and services by 2033, according to Future Market Insights.
The market is being driven by various organizations that are investing in developing open source intelligence tools and technologies, offering OSINT services, training and educating OSINT professionals, and creating partnerships and collaborations.
Key players in the market are adding value by developing innovative tools such as data mining software and social
media analytics platforms, all of which have extensive application in threat intelligence
They also provide expert analysis and interpretation of the data they collect and offer customized services to clients by monitoring analysis on specific topics.
These players are advancing the market through mergers, collaborations, partnerships, acquisitions, and product launches.
What is open source intelligence? Why is that sector getting big bucks?


Understanding OSINT
The practice of gathering and analyzing information from publicly available sources, such as news articles, social media, government reports, and online resources, is known as open source intelligence (OSINT).
In recent years, OSINT has become increasingly important for law enforcement agencies, intelligence agencies, and private investigators as a means to gather information and stay ahead of potential threats.

Social media platforms like Twitter, Facebook, and Instagram are among the primary sources of OSINT.
These platforms offer a wealth of information that can be used to track individuals, monitor trends, and gather intelligence on specific topics.
OSINT analysts use tools like social media scraping software to collect large amounts of data and extract useful insights from them.
Online forums and discussion boards are another valuable source of OSINT. They can provide useful information on specific topics or industries and can be used to monitor trends and identify potential threats.
OSINT analysts use specialized search engines and software to monitor these forums and identify relevant discussions.
Government websites and databases are also significant sources of OSINT. Public records, government reports, and other publicly available data can be used to gather intelligence on individuals, companies, and other entities.
News websites and blogs can also offer valuable insights into current events and trends.
The effectivity of the data collected heavily depend on two things: the tools of collection and the methods of analysis.
Here ten wildly effective tools for collecting and analysing open source intelligence

Google (Yes, that counts!)

If you know how to use advanced filters to refine your search, search engines such as Google, Bing, and DuckDuckGo can serve as effective and free open-source intelligence (OSINT) tools.
Investigators have been able to increase the capacity of these tools by reverse-engineering search engines using a process called Google dorking or Google hacking, which includes using search operators or functions beyond Google.
However, the method of using search operators can be controversial as it may cross the line regarding how “public” the information is. For example, finding a link to a PDF file containing a list of passwords can be considered a prosecutable offense if downloaded.
One example of Google dorking is searching for PDF files on a company’s website domain. By typing “site:company. website.domain filetype:pdf” into the search bar, you can be surprised by the number of openly available documents that can be found using this method.
Although Google can be used as an OSINT tool and has powerful algorithms and a free price, it has limitations such as providing limited results and requiring a lot of trial-anderror. Additionally, the method can pose privacy issues and raise questions about the legality of obtaining certain documents.
AmIBreached
AmIBreached is an application designed to assist users in determining their exposure in the dark and deep web. The app provides a comprehensive approach to cybersecurity by allowing individuals to check if their personal information has been compromised or leaked in cyber breaches.
With the increasing number of data breaches and cyber threats, it has become crucial for individuals to take proactive measures to protect their personal information. AmIBreached addresses this concern by offering a user-friendly platform where users can easily assess their online security.
The app works by scanning various sources in the dark and deep web to identify any instances where a user’s personal information, such as email addresses, passwords, or financial details, may have been exposed. It also notifies users if their information appears in publicly available databases or has been shared on underground forums.
The app does not collect or store any personal data from users, ensuring that their information remains confidential. Instead, it employs advanced algorithms and techniques to match user inputs with the available breach data without compromising privacy.


Upon completing the scan, AmIBreached provides users with a detailed report indicating whether their information has been compromised and the specific breaches associated with it.

Intelligence X
Intelligence X is an exceptional archival service and search engine that not only preserves past versions of web pages but also completes leaked data sets that could be removed from the web due to illegal content or legal concerns. Although similar to the Wayback Machine, Intelligence X differentiates itself by focusing on preserving data sets, no matter how controversial, without any bias.

In the past, Intelligence X has safeguarded a list of more than 49,000 Fortinet VPNs that were exposed to a Path Traversal vulnerability, as well as plaintext passwords that were revealed on hacker forums.

The service has also indexed data obtained from the email servers of influential political figures such as Hillary Clinton and Donald Trump, as well as media footage of the 2021 Capitol Hill riots and Facebook’s data leak of 533 million profiles.
For intelligence collectors, political analysts, news journalists, and security researchers, this information can be very valuable in various ways.
SEON
SEON is a top choice for verifying identities through social media and digital platforms. This method has become increasingly popular due to its high barrier of entry for fraudsters, ability to gather a user’s digital footprint, and potential to reveal information about someone’s socioeconomic background.

Although manual searches on LinkedIn, Facebook, or Twitter are possible, SEON is a specialist solution that checks more than 50 social and online signals based on an email address, IP address, or phone number.

SEON’s fraud prevention tool offers real-time results and additional checks such as velocity, behavior, and device fingerprinting. It also provides data enrichment modules that give users a risk score and more information. The service is flexible and can be queried manually, via API, or through a Google Chrome extension.
While SEON lacks some of the more forensic elements of other entries on the list, it is customer-focused and provides valuable information for those who need to verify identities.
3 4
Lampyre
Lampyre is a paid application specifically designed for OSINT purposes, particularly for tasks like due diligence, cyber threat intelligence, crime analysis, and financial analytics. Users have the option to install it on their PC or run it online.
The standout feature of Lampyre is its one-click functionality. By inputting single data points such as a company registration number, full name, or phone number, Lampyre efficiently scans vast amounts of data to extract relevant and interesting information.
The company automatically processes data from over 100 regularly updated sources, which can be accessed through PC software or API calls if required. The SaaS (Software-as-a-

Maltego
Maltego is an advanced Java application that aims to streamline and accelerate investigations through its exceptional database access and visualization tools.
Whether you work in trust and safety, law enforcement, or cybersecurity, Maltego offers oneclick investigations that provide easily understandable results.

Currently, Maltego allows users to visualize up to 1 million entities on a graph, with access to 58 data sources. You can even integrate your own public databases and manually upload additional data sources.
Once all the relevant information is loaded into the program, you have the flexibility to choose from various
Service) version is called Lighthouse, and users pay per API call.
However, it’s important to note that like other OSINT tools, users need to exercise due diligence and verify the openness of the databases utilized. While Lampyre automates searches, it is advisable to double-check the source of the information and the reliability of the provider, as one researcher discovered.
Lampyre offers several benefits, including its effectiveness in cybersecurity and due diligence tasks, the ability to gather data from 100+ sources, and an affordable subscription or yearly purchase option. However, users may face a slight learning curve due to the less intuitive nature of Lampyre and its Lighthouse SaaS software.

visualization layouts, such as blocks, hierarchical, or circular, and utilize weights and notes to customize the graphs according to your preferences.
HOT SEAT 5 6
In addition to being a powerful tool, Maltego provides a curated collection of valuable resources on OSINT tools and techniques, enabling users to maximize their productivity. They also offer the option to purchase the Maltego Foundation course online.
Maltego offers several advantages, including excellent graph visualization tools and multiple options for data visualization. However, it should be noted that Maltego is a Java application only and has a slightly dated user interface.

GHunt
GHunt is a specialized tool designed to assist users in extracting valuable information from Google accounts. It is primarily focused on gathering OSINT (Open Source Intelligence) from Google services such as Gmail, Google Photos, and Google Drive. GHunt offers a user-friendly interface and provides a range of features for conducting efficient investigations.

Similar to Recon-ng, GHunt is a free and open-source tool. It enables users to perform various tasks, including checking if a target email address is registered with a Google account, detecting whether 2-step verification is enabled, and retrieving information about the target’s Google contacts.
Recon-ng
Recon-ng, originally developed as a free and open-source script for gathering technical information on website domains, has evolved into a comprehensive framework accessible through a commandline interface on Kali Linux or as a web application.
Its interface bears similarities to Metasploitable, another computer security project focused on penetration testing, sharing the common objective of assessing and identifying web vulnerabilities. Among its notable features are GeoIP lookup, DNS lookup, and port scanning.
Although Recon-ng is a more technically advanced tool on
this list, there are ample online resources available to help users learn how to leverage its capabilities. With Reconng, investigators can locate sensitive files like robots.txt, uncover hidden subdomains, identify SQL errors, and gather information about a company’s CMS or WHOIS data.

Recon-ng offers the advantages of being free and open-source while serving as a valuable tool in the field of cybersecurity.

However, it is important to note that Recon-ng operates solely through a command-line interface, making it less suitable for investigators with limited technical expertise.
One of the standout features of GHunt is its ability to scan Google Drive for shared files. This feature allows users to search for files that have been shared with the target account, providing potential insights into the individual’s activities and connections.
Additionally, GHunt can extract metadata from Google Photos, giving investigators access to valuable information associated with images uploaded to the account.
GHunt is a valuable asset for cybersecurity professionals, investigators, and researchers. It offers a straightforward approach to gathering OSINT from Google accounts, making it a useful tool in various scenarios. However, it’s important to note that GHunt is a command-line tool, meaning it requires some technical proficiency to utilize effectively.

HOT SEAT 9
Shodan
Shodan serves as a robust search engine designed specifically to explore and discover internetconnected devices. Unlike traditional search engines that focus on indexing web pages, Shodan scans and catalogs information about a wide range of devices, including servers, routers, webcams, and more. This unique specialization makes Shodan an invaluable tool for various purposes, such as cybersecurity, network monitoring, and research.
The extensive capabilities of Shodan empower users to conduct targeted searches for specific devices or vulnerabilities using a variety of filters and operators.
Users can narrow down their search
by factors like geographical location, IP address, organization, operating system, open ports, and even specific banners or keywords.
By providing comprehensive details about these devices, Shodan enables users to identify potential security weaknesses and evaluate the overall security status of networks.
One of Shodan’s standout features is its ability to uncover unprotected or inadequately secured devices that are accessible to the public. This includes devices with default or weak credentials, exposed administrative interfaces, or outdated software versions. By pinpointing these vulnerable devices, users can proactively take measures to secure them or report the issues to the appropriate authorities.

Shodan goes beyond search capabilities by offering additional functionalities. Users can monitor specific devices or networks for changes, access historical data related to devices, and leverage APIs to integrate Shodan’s features into other applications or tools.
While Shodan provides valuable insights and is widely utilized by cybersecurity professionals, researchers, and enthusiasts, it is essential to exercise responsible and ethical use. As Shodan exposes information about potentially sensitive devices and systems, it is crucial to prioritize privacy and adhere to legal and ethical boundaries in its usage.


Social Mapper

Social Mapper is an open-source intelligence tool built in Python that utilizes facial recognition technology to correlate social media profiles. It is freely available on GitHub, allowing users to access and utilize it without any cost. The tool gathers data from various popular social media platforms, including Facebook, Instagram, LinkedIn, Google Plus, Twitter, and Vkontakte.
Social Mapper is particularly useful during the reconnaissance phase and can assist in conducting social engineering attacks targeting organizations or individuals.

Please ensure that Python is installed on your system as Social Mapper relies on this programming language. You can refer to the Python Installation Steps on Linux for guidance on installing Python.
It is worth noting that while OSINT can be a useful tool for gathering information, it has limitations. Information obtained through OSINT should always be verified through other sources before being used to make decisions or take action.

THE DARK SIDE OF ANONYMITY: A CLOSER LOOK INTO 4CHAN COMMUNITIES
 - By Ashish Khaitan
- By Ashish Khaitan
In the vast realm of the internet, where pop culture collides with hacktivism, crime, and terrorism, there exists a notorious online community that thrives on offensive content and serves as a breeding ground for criminal activities. This is the enigmatic story of 4Chan and its intriguing evolution into a hotbed for hackers.
Originally created as a response to Japan’s 2chan, 4Chan, which is also known as the “website with no rules”, started as a place for anime enthusiasts to discuss manga, comics,
and their favorite TV shows. However, as time passed, the website users began witnessing extremities and lawlessness on the platform, which caught the attention of the hacker community.
From leaked nude photos of celebrities to encouraging iPhone users to microwave their devices, 4Chan became a popular spot for everything wrong, including hacking.
4CHAN

Since its inception in 2003, the popular image board website has been involved in several controversies. However, things took a darker turn as users began witnessing anonymous confessions to murders, hacking sensitive data, and more on the website. Hacking remained a major concern because sensitive data was being leaked on the site, costing millions of dollars in damage, and reputation as well as gravely impacting the lives of people.
This route largely differs from the standard social media platforms where users are required to sign up with a name and email. This unique feature was something that no other social media website was able to offer to its users — complete anonymity! The website’s founder was also baffled at the sheer number of visitors they were getting every month.

Christopher Poole or also known by his online alias Moot, started 4Chan after being inspired by 2Chan, a Japanese imageboard that later inspired 4Chan — almost mimicking the original image board but catering to English-speaking communities.
One of the major successful traits of 4Chan was its ability to post anonymously and the inner engineer of the website allowing posts to disappear under a thread —- leaving no chance of evidence against criminals confessing their crimes online.



In a TED Talks show titled “The case for anonymity online,” Poole explained how 4Chan became one of the most visited websites in a couple of years. With over 7 million monthly visitors, 700,000 posts per day, and 48 individual boards to use, the website was thriving in the early days of the internet and destroying every other social media platform in terms of daily traffic.
However, behind these jokes, memes, and funny cat videos, many popular threat actors and hacktivist groups began formulating on the platform.
Among those hacker groups, Anonymous, which was also a part of the 4Chan community back in the day, began experimenting with the 4Chan community with their channel “Marble Cake.”
The group, which was yet to establish a name in the hacking community, gained international support from people demanding free speech with its campaign, “The Project Chanology.”


During the TED Talk, Poole also spoke about the Tom Cruise controversy that triggered an extreme reaction on the platform, which eventually led to protests where several were hurt.
What was the Tom Cruise Church of Scientology controversy?
On January 14, 2008, a video by the Church of Scientology featuring an exclusive interview with Tom Cruise, was leaked on YouTube.
The video featured the Hollywood actor discussing his devotion to the “Church of Scientology” drew flak online as many termed Cruise’s behavior “strange”.
In response to the ongoing trolls and memes, the Church of Scientology took down the video from YouTube with a copyright claim. This angered the internet community and soon protests broke out.
“Scientology had this embarrassing video of Tom Cruise. It went online. They got it taken offline and managed to ‘piss off the internet’. So, over 7,000 people, in less than one month, organized in hundreds of cities around the globe and protested the Church of Scientology,” Poole explained during his TED Talk.
The protest went on for a couple of months, and many people got hurt. Poole also explained in the Ted Talks show that some individuals continued to protest against the Church of Scientology after two years of the incident.
Source: Wikimedia Commons/Author failquail
The /b/ random board: Hacking for fun, nothing to lose!
The /b/ random board gave users the freedom to post literally anything on the platform. It was unlike any other boards on that platform, which were dedicated to users sharing information about their favorite games, anime, memes and more.
The /b/ random board was filled with posts threatening people for murders, asking users how to bury bodies, suicide-encouraging posts, and extremities that could get anyone arrested.

Moreover, it has been rumored that the world-renowned hacker group Anonymous also began their journey on the /b/ random board.
Anonymous started by doing silly pranks, such as prank calling companies, hacking small sites for fun, and sharing their data with the 4Chan community, but soon, these minor pranks turned into something big, and this hacker group soon became one of the most feared groups of individuals to ever exists on the internet.
On January 21, 2008, Anonymous shared its first official video titled “Message to Scientology,” claiming to “destroy” the Church of Scientology for brainwashing its members.

A couple of months after their warning, Anonymous hacked the website of the Church of Scientology and leaked their internal documents on the website. The hacker collective paved the way for hacktivists to be thought as more than just prank-calling teens.
However, hacking activities by 4Chan users continued to take an extreme form and went beyond free speech, activism, and protests. In another incident, the 4Chan community hacked the third annual TIME 100 poll for World’s Most Influential Person.

Source: music machinery

To achieve this feat, 4Chan members decided to make its founder Christopher Poole, the number 1 on the TIME 100 list, beating the likes of globally recognized figures such as Barack Obama, Vladimir Putin, and Oprah Winfrey.
Source: Semantic Scholar
The hackers on the imageboard forum created programs that were submitting millions of votes in favor of Poole. They even went as far as spamming multiple platforms with links dedicated to pushing the founder to the number one position.
However, that was just the beginning. In 2012, the same board members restarted the campaign, and this time, they made Kim Jong Un, the monarch of North Korea, the person of the year.
These incidents confirmed that /b/ random board members were not ordinary people but highly skilled individuals familiar with hacking and digital manipulations.
Bald For Bieber. Cutting For Bieber
By this point, it was evident that the /b/ random board was not afraid of anything as long as they got the last laugh. In this sense, they launched campaigns, hacking attempts, and defamatory polls.

But things turned dark when /b/ random board members began the “#baldforbieber” program, a one-of-a-kind prank that made people do unthinkable things to themselves.
In October 2012, the 4Chan community pushed a prank post about Justin Bieber having cancer, and their prank encouraged young girls to shave their heads in support of the pop singer.

They also posted a fraudulent response from Justin Bieber for the campaign. The hashtag soon went viral prompting young girls into shaving their heads.

While Justin Bieber was nowhere associated with the campaign, in 2013, 4Chan’s/b/ random board pushed another campaign called “#cuttingforbieber.”
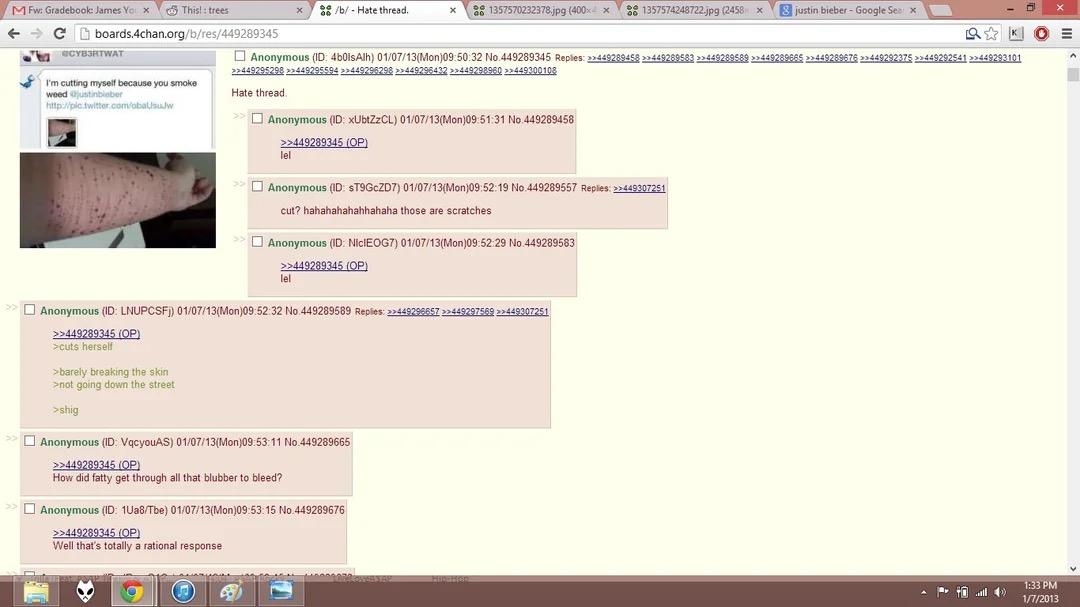
This campaign was targeting young girls and boys, encouraging them to cut themselves to make Justin Bieber stop smoking after TMZ leaked an image of the young pop star holding a blunt.
Source: Reddit

The /b/ random board continued running the fake campaign that was directly brainwashing young Justin Bieber fans to cut their wrists with razor blades, which prompted many to question on the authenticity of the internet.
The prank was initially started by a 4Chan user who posted this message on the /b/ random board, “Let’s start a cut yourself for Bieber campaign. Tweet a bunch of pics of people cutting themselves and claim we did it because Bieber was smoking weed. See if we can get some little girls to cut themselves.”
4Chan cyberbullying: Destroying families and peace for a few giggles

For an outsider who has not invested much time on 4Chan, the community may seem like an innocent gathering platform for otakus, gamers, and pop culture enthusiasts, sharing their everyday life.
However, several stories suggest that the platform was a breeding ground for hacking and cyberbullying, targeting innocent users.
The infamous ‘Jessi Slaughter’ cyber horror was one among many such incidents, where the then 11-year-old girl became a target of 4chan trolls, leading to extreme cyberbullying and harassment. Reports suggest that it all began when rumors of the YouTuber being sexually involved with Dahvie Vanity, the lead singer of the Blood on the Dance Floor band began circulating on social media platforms.

Jessi Slaughter responded to the rumor by posting a profanity-laden video on YouTube video mocking the “haters” stating that she did not care.
“If you can’t, like, realize that and stop hating, you know what? I’ll pop a Glock in your mouth and make a brain slushy”, she can be heard saying in the video, which soon went viral.
Source: Reddit
Soon, the video began circulating with 4Chan users targeting Jessi Slaughter’ by leaking her real name, her father’s name, and even her address.
Things intensified after Jessi’s father appeared in one such video and threatened the online community with dire consequences for targeting his daughter.

Source: news.com.au
The /b/ random board members began sending spam emails, fake police case calls, absurd items to her house. They also started flooding the email accounts of her parents.
Later, when Jessi appeared on Good Morning America (GMA), to discuss the cyberbullying incident, informing how the incident impacted her.
However, hackers on the platform continued to target individuals and even manipulated the 4Chan website to look like a family-friendly place for people. They exploited Google to show that the website was a cool place to hang out and that no profanity, bullying, or hacking occurred on its boards.

This operation was called the /b/ipolar, where the hackers were basically fooling the entirety of the internet into thinking that 4Chan was a family-friendly website.
Around the same time, Jessi went through different mental institutions, was denied internet access, and was put in foster care. Later, Jessi’s friend had also shared a video of Jessi apologizing to the public.

Source: Reddit
Jessi’s father died of a heart attack at the age of 53 and Jessi was reportedly diagnosed with fibromyalgia and was left wheelchair-bound.
It is evident that 4Chan is a problematic online community that poses significant risks to teenagers and young people. Throughout this report, we have explored why 4Chan is considered a bad place and why individuals must think rationally when engaging with such online communities.
The anonymous nature of 4Chan allows for the propagation of harmful and offensive content. Without accountability, users feel empowered to express extreme views, engage in cyberbullying, and spread hate speech. This toxic environment can harm the mental health and wellbeing of teenagers and young people, who are particularly vulnerable to online influences.

4Chan is also known for its involvement in illegal activities. The platform has been associated with the sharing and distribution of explicit and illicit content, including child pornography. Engaging with such content exposes young individuals to criminal behavior and perpetuates a cycle of exploitation and harm.
Given these factors, teenagers and young individuals must approach online communities like 4Chan cautiously and rationally. They should know the potential dangers and understand the implications of engaging in such platforms.
By critically evaluating the content they encounter and seeking reliable sources of information, young
individuals can protect themselves from the negative influences on 4Chan.
In conclusion, 4Chan represents a toxic online community that poses numerous risks to the well-being and safety of teenagers and young people. Individuals must reason, exercise caution, and prioritize their mental health when navigating the internet and engaging with online communities. By promoting digital literacy, critical thinking, and responsible online behavior, we can mitigate the detrimental effects of platforms like 4Chan and foster a safer online environment for all.
AI’S SINISTER GRIP: AI-GENERATED MODELS, DEEPFAKE SCAMS, VOICE CLONING….. WHAT LURKS BEYOND?
 - By Ashish Khaitan
- By Ashish Khaitan
AI is not something new, and nor does it belong to the future. What we are witnessing right now is the first initial adoption of AI in our everyday life. Tools like ChatGPT, Bard AI, Perplexity AI, and Forefront AI are already changing how people work and have proven effective in increasing productivity.
However, AI has the potential to create illusions to such an extent that it diminishes the line between what is real and what is fake! And that is the scary part.
Ray Kurzweil, a renowned futurist, introduced the “Law
of Accelerating Returns.” He claimed that technology and other evolutionary systems change exponentially. Based on this idea, Kurzweil predicted the nearness of the Singularity, a significant event that will disrupt human history and is expected to occur before the end of the 21st century.
“Within a few decades, machine intelligence will surpass human intelligence, leading to The Singularity — technological change so rapid and profound it represents a rupture in the fabric of human history,” says Ray Kurzweil

However, is that time already here?
Recent incidents indicated how AI is impacting jobs around the world. However, the technology has also found its way into the adult entertainment industry.


OnlyFans, a content subscription service used by the adult entertainment industry, is facing its biggest enemy yet.
With tools like ChatGPT, and Stable-diffusion AI, people can generate real-like images and videos of women who don’t actually exist. These AI generated models can work around the clock and produce content much faster than human models.
AI-generated
Michihito marveled at the position of mayor and managed to come in third place with 4,013 votes, defying conventional norms of the standard political setup.
“We believe AI is the future of corporate governance, and our appointment of Miss Tang Yu represents our commitment to truly embrace the use of artificial intelligence to transform the way we operate our business and ultimately drive our future strategic growth,” explained NetDragon president Dejian Liu.
These cases don’t stop here either. Several studies suggest that AI models can work around the clock and never get tired, which means that content can be produced at a much faster rate than actual humans.
Another concern is that AI models could lead to more unrealistic expectations and put pressure on human models to conform to a certain standard. This could lead to a decrease in diversity and individuality in varied industries.

AI model generated using Stable Diffusion. (Source: AI Assistant/@OnlyFansAI/Twitter)

OnlyFans, a content subscription service used by the adult entertainment industry, is facing its biggest enemy yet.
With tools like ChatGPT, and Stable-diffusion AI, people can generate real-like images and videos of women who don’t actually exist. These AI generated models can work around the clock and produce content much faster than human models.
AI-based OnlyFans models: No longer human!
Since its launch, OnlyFans has filled a big void in the adult entertainment market that other companies were overlooking — a subscription business model for individuals, especially sex workers who produce pornography.
In 2022, just a few years after its launch, the company was valued at approximately $18 billion, eight times more than its value in 2020.
With such a lucrative market where the source of revenue comes directly from user-generated content (also known as UGC or consumer-generated content),
AI has found a place in this industry through humanoid models. And they sometimes look more real than human models themselves.
With the help of modern technology and artificial intelligence, individuals have managed to generate an image of fake cam girls, proving how sophisticated its capabilities are.

In one such incident, a particular AI-generated image went viral on Twitter wherein the image featured four women with identical faces posing in lingerie on a bed.

AI models by The Realist/@TheRRRealist. (Source: The Realist/Twitter)
While some users were baffled by the realism of the image, others were not sure how to react as they stated that these women were not real.
However, one of the users on social media, who was aware of the technology and how to use it to create life-like humans, said that “I am totally starting a fake AI generated OnlyFans for gullible idiots if I fail this trading thing,” the Twitter user wrote.
THE COVER
Moreover, upon investigation, it was found that there were various social media accounts, businesses, companies, female models, and even governments that are already using AI-generated humans to work alongside them.
Some of these private companies offer image packs of AIgenerated female models, while real-like models are also offering companies to make models after them.
According to an article in Rolling Stone, the emergence of Claudia, a young AI model who fooled the internet with her life-like pictures, was attributed to the ingenuity of two computer science students.

The creators behind Claudia allegedly stated that the entire account was merely an experimental venture to assess the effectiveness of AI-generated images in deceiving people.

Consequently, the Reddit account where Claudia’s image initially surfaced has implemented a verification process for its members.
Interestingly, the student duo behind the Claudia revealed that they had successfully generated a sum of $100 by circulating the images the AI model .
Using Artificial Intelligence For Scams
Apart from lust traps, AI has also been successfully integrated into online scams.
As with any online tool, AI can also be exploited for malicious purposes. In cybersecurity, AI is slowly turning into a double-edged sword, empowering cybercriminals to launch sophisticated scams that can evade traditional security measures.
As AI is enabling scammers to personalize attacks and improve social engineering techniques, these criminals are adopting the technology faster than ever.
These scams have already infiltrated world politics, business policies, and national security and paved roads for communist riots. Elon Musk’s recent deep fake scam is just one such incident among the many to follow.
https://twitter.com/cb_doge/ status/1657415913430286336
This dark side of AI is evident not only in the realms of online romance and dating scams but also in broader domains such as world politics, business policies, and national security.
Impersonation scams and voice manipulation
Diffusion. (Source: /Twitter)
Drawing a parallel to tubers, who craft fictional personas distinct from their true selves, the creators expressed surprise at the unexpected level of attention their creation garnered.
Today’s cybercriminals are taking advantage of AI software to perpetrate terrifying scams that prey on human emotions. By utilizing AI-generated voice samples, scammers can convincingly impersonate family members, friends, or colleagues, going beyond conventional hacking methods.
This unsettling trend poses significant risks, as unsuspecting victims may fall victim to fraudulent requests or divulge sensitive information under the guise of trusted individuals.


AI investment scams
The California Department of Financial Protection and Innovation has warned about AI investment scams.
These fraudulent schemes exploit “buzzworthy terms” to persuade individuals to invest in cryptocurrencies. Scammers employ AI to present a facade of artificial intelligence-powered trading platforms that promise exorbitant profits.
Unfortunately, unsuspecting investors may find themselves losing their hard-earned money to these deceptive schemes.
Malicious manipulation of video and textto-speech tools

Video and text-to-speech software, initially developed for legitimate purposes, is among the prime tools used by scammers.
By crafting seemingly authentic videos or employing advanced chatbot technology, scammers create persuasive personas and forge connections with their victims.
This manipulation extends beyond text-based communication, allowing scammers to manipulate emotions and establish deeper connections that facilitate fraudulent activities.
LinkedIn job scams
The popularity of LinkedIn as a professional networking platform has provided scammers with an opportunity to exploit unsuspecting job seekers.
Using AI, scammers fabricate fictitious profiles and reach out to users with enticing “get rich quick” ventures.
These fraudulent promises often involve crypto scams and work-from-home schemes that can result in financial loss and the exposure of personal information to significant risks.
The following is a list of prevalent online scams that leverage AI for fraudulent activities:
Summing up
In the ever-advancing realm of AI, an intriguing paradox emerges—where progress brings astonishing possibilities, it also unfurls an expanding tapestry of threats.
Cybercriminals, akin to cunning maestros, deftly manipulate the symphony of AI, orchestrating scams of unprecedented complexity.
Their craft extends beyond mere individuals and businesses, penetrating the very fabric of national security. Now, more than ever, we find ourselves standing at the precipice, beckoned by the call for heightened vigilance and unwavering awareness.
As we navigate the labyrinth of evolving threats, our digital security and financial well-being lie precariously in the balance, awaiting the shield of our resilience in the face of the ever-cunning dance of AI-powered fraud.
EXPLOITING DIGITAL PLAYGROUND: WHY ARE MORE KIDS BECOMING HACKERS, TURNING TO CYBERCRIME?
 - By Avantika Chopra
- By Avantika Chopra
While it is evident that teenagers hack, the question is why? Why are so many hackers’ kids? What urges them to step
into the dark side and indulge in criminal activities? And, is there a way out?

BOTTOM LINE
At the age of 5, an American boy Kristoffer von Hassel became the youngest hacker after he found a vulnerability in the Microsoft Live Xbox system that allowed him to bypass the parental blocks put in his dad’s gaming console to prevent him from playing.
By repeatedly trying multiple password combinations, Hassel found a glitch that let him enter the wrong password and then allowed access when he entered a series of spaces.
Hassel was soon discovered by his parents playing the video game, which led to the reveal of the security glitch and the massive media coverage that followed.
However, not all hacking stories have a happy ending. Many lead to arrests.
A simple Google search will list multiple hacking incidents involving teenagers and young adults. A recent report highlighted how some of the biggest cybercrimes were being orchestrated by individuals who were not old enough to graduate high school.
In 2022, a 16-year-old was accused of being one of the leaders of the infamous extortion hacker group Lapsus$. The teen allegedly amassed $14m through his hacking activities and managed to infiltrate tech giants and corporations such as Microsoft. The police arrested seven individuals between the age of 16-21 in connection with the hacking group investigation.
17-year-old Graham Ivan Clark was the mastermind behind the massive 2020 Twitter hacking that impacted over 130 Twitter accounts, including those of Elon Musk, Bill Gates, Barack Obama, and Joe Biden. Clark was sentenced to 3 years of jail.
While it is evident that teenagers hack, the question is why? Why are so many hackers’ kids? What urges them to step into the dark side and indulge in criminal activities?

Children, by nature, are curious beings, and while “hacking” may have a negative connotation, especially with regard to children, it often is not the motivation. Many teens are drawn to technology and explore hacking out of curiosity.
A recent study shows that 70% of children spend at least three hours on devices daily. At the same time, only about half of parents use parent-controlling apps or supervise children as they use digital devices, while the rest pay less attention to their children’s digital behavior.
The freedom to explore often gives children a chance to stumble into activities which they may not entirely understand.
Many, especially those with technical aptitude and an inclination towards critical thinking and problem-solving, explore hacking to understand how systems work and satisfy their inquisitive nature.
In a study conducted by the National Crime Agency, it was found that teenage hackers were motivated by “idealism and impressing their mates rather than money,” The Guardian reported.

The study, which interviewed teens as young as 12 arrested for computer-related crimes, found that the children were inspired by their desire to solve technical problems, seek attention and prove themselves to their friends.
“Conquering the challenge, proving oneself to the group and intellectual satisfaction are more important motivations than financial gain,” the report stated.
Jake Davis, aka Topiary, was a former member of the infamous hacker collective Anonymous. At the age of 18, Davis was arrested in July 2011 for criminal activities, including cyber raids and hacking of government websites.
In an interview, Davis shared how his purpose was to challenge secrecy. “It was not financially motivated at all, as the NCA report says, it was mostly politically motivated. I was motivated as a teenager by the idea that this internet was this utopian space that shouldn’t be controlled or filtered or segmented or chopped up into little blocks and distributed out, and that it should be open and free, and anyone in the world should be able to use it.”
Davis was only 13 when he began exploring the internet. While curiosity, peer pressure, and the need to challenge technology plays a crucial role in stimulating children towards hacking, unsupervised exposure to the digital landscape also leaves them vulnerable to exploitation, especially by the perpetrator who are always on the lookout for the innocent.
Hacker:HUNTER, a four-part series, explores the different phases of teen hacking and tells the stories of children for whom hacking turned into their favorite game.
Directed by Hugo Berkeley, Didi Mae Hand, and Lara Maysa Ingram, the cybercrime series provides an overview of children hackers, how they get acquainted with the hacking world, what stance the penal system takes with regard to minor offenders and, finally, raises the question of whether there is a way out from the cybercrime.
Hackers Recruit Children Through Online Gaming
In recent years, gaming has captured the attention of children worldwide, exposing them to a world of unlimited virtual possibilities. However, with this, they have also become easy targets for hackers, who often lurk on gaming platforms to identify skilled children and groom them into carrying out hacking tasks.

“Kids are curious. Kids want to play. And that’s just amazing! For this season, we asked ourselves what happens if that curiosity turns into criminal behavior? Is it even possible for a 14-year-old to figure out that they are doing something illegal while sitting on their computer in their kid’s room?” asks Rainer Bock, hacker:HUNTER’s Executive Producer.
Rehabilitating teen hackers
Over the years, the number of teen hacking incidents has continued to rise, urging law enforcement agencies to take a harder look at the issue impacting young minds. However, it is often wondered whether hackers can be rehabilitated and if they can eventually be trusted.
There have been several incidents where teen hackers have confessed to being in a “dark place” while indulging in hacking-related activities and regretted their actions.
In an interview, former hacker Cal Leeming, who was convicted of using over 10,000 stolen identities to buy £750,000 worth of goods, shared how he got into the illegal at the age of 11.
“I was convicted of ‘causing a computer to perform a function with intent to secure unauthorised access’, under The Computer Misuse Act (1990), at the age of 12. I’m still the UK’s youngest convicted hacker,” he told Metro News.
In his interview, Leeming shared how things quickly escalated into crime and he was “breaking into various ISPs [internet service providers] and companies to steal data.” However, things got to a point where Leeming said that he “wanted to get caught”.
Charlton George, who brought down the websites of the FBI and Home Office at the age of 16, regretted his actions
“I honestly regret doing that type of thing now. I got caught up in a world that is rather dark, but it gives you a home when you’re not quite happy with real life,” he said, Coventry Telegraph reported.
While many know Marcus Hutchins as the hacker “who saved the internet” as he stopped the WannaCry ransomware attack, not many know that he was arrested for the hacking he had done during his teen. Hutchins was accused of being part of a conspiracy where he created and distributed malware ‘Kronos’, which targeted banking websites. He was sentenced to “time served” and one year of supervised release.
Talking about teen hacking becoming an issue in the future, Hutchins told the online magazine Slate that it was a “very hard problem to solve.”
“It is very hard to put an end to teen mischief without putting them in jail, and no one wants to see teens in jail, especially not myself. It’s very hard to think of any way that’s enough deterrence to stop them from doing it without just being completely overboard. I personally can’t think of any punishment that would have stopped me at that age that wasn’t way over the top,” he said.
While clearly, there is no one solution to the prevalent problem of teen hackers, it is essential to look at all aspects of individuals, especially teens indulging in criminal activities.
In a bid to deter cybercrimes committed by teens, law enforcement agencies need to look beyond the crime and take initiatives such as rehabilitation programs to help them move towards the right path.

UPCOMING EVENT
World CyberCon
Middle East Edition 2023
30 August 2023
Riyadh, Saudi Arabia







