

Comprehensive Digital Risk Protection with Cyble Vision
Capabilities
Darkweb and Open Internet Monitoring
Compromised credentials
Sensitive data leakage
Executive brand protection monitoring
Open-Source Intelligence
Cybercrime Intelligence
Advisories on 400+ threat actors and 700+ malware operators
Monitor 80% of Cybercrime markets

Cybercrime conversations/mentions in forums and markets
Attack Surface Detection & Hunting (DRPS)
Public facing assets
Vulnerable assets
Code Leakage (e g GitHub/bitbucket)
Cloud buckets S3, Azure
Malware campaigns
Third Party Cyber Scoring
Vendor risk score
Derived from Darkweb, deep web, attack surface, public breaches, disclosures, etc
Brand Reputation Monitoring (DRPS)
Fake/Typo Squatted Domains and Fake Content

Fake Domains and Fake Content
Fake app detection
Phishing URLs
Take downs
Social media monitoring
Threat Intelligence
IoCs
Security Advisories
Compromised Cards
BINs
ATM PINs















STAFF
Editorial Management
Augustin Kurian Editor-in-Chief editor@thecyberexpress.com
Chandu Gopalakrishnan Executive Editor chandu@thecyberexpress.com
Avantika Chopra Senior Sub-Editor avantika@thecyberexpress.com
Vishwa Pandagle Journalist vishwa@thecyberexpress.com
Ashish Khaitan Journalist ashish@thecyberexpress.com
Rajashakher Intha Head - Marketing & Sales raj@thecyberexpress.com
Ashish Jaiswal Conference Manager ashish.j@thecyberexpress.com
Priti Chaubey Content Strategist priti.c@thecyberexpress.com

Ravi Gupta SEO Analyst ravi@thecyberexpress.com
Vittal Chowdry Senior Graphic Designer vittal@thecyberexpress.com
From The Editor’s DESK
Welcome to the May issue of The Cyber Express, where we bring you the latest news and insights on the ever-evolving world of cybersecurity. In this edition, we cover a range of topics, from new cybersecurity concerns surrounding GPT4 to the darker side of AI with a focus on ChatGPT and the worldwide cybersecurity policy discussions it triggered.
This month’s cover story delves into the potential impact of GPT4 on the cybersecurity industry. As AI continues to advance rapidly, it is important to stay informed about the latest developments and how they may affect our digital security. We examine the potential implications of GPT4 and what this means for cybersecurity professionals.
The Cyberville section shines a light on the infamous ransomware gang Lazarus, which has been responsible for a number of high-profile attacks in recent years. We explore their tactics, targets, and the measures organizations can take to protect themselves against this threat.

In addition, we discuss the importance of email authentication for non-profit businesses. With cybercriminals increasingly targeting these organizations, ensuring that email communications are secure and authentic is more important than ever.
We also take a look at the power distribution sector and the critical role that cybersecurity plays in keeping the lights on. With cyber attacks becoming more sophisticated and frequent, it is essential that the industry takes steps to safeguard against these threats.
One of the highlights of this issue is an exclusive interview with Matt Malarkey, Strategic Alliances Manager at Titania, who discusses the new cybersecurity strategy that his company is implementing. Malarkey closely monitors policy, regulatory, and market issues to inform the company’s go-to-market plan and product development.
Finally, we are thrilled to present The Cyber Express’s first-ever Market Trends Report, which takes an in-depth look at AI in
cybersecurity. With AI becoming an increasingly important tool in the fight against cybercrime, this report provides valuable insights into the latest trends and developments in this field.

As always, we hope this issue will help you with valuable insights and practical advice that you can use to strengthen your cybersecurity posture. In a world where cyber threats are constantly evolving, it is essential to stay up-to-date with the latest developments and take proactive steps to protect yourself and your organization.
We would like to thank our contributors for their insightful articles and our readers for their continued support. We look forward to bringing you more news and insights in the coming months.
Most importantly,
We welcome your feedback at editorial@thecyberexpress. com
Stay safe online!
DATING APPS AND SITES: MITIGATING CHARGEBACKS
 - By Monica Eaton Founder of Chargebacks911 and Fi911. Chief Information Officer of Global Risk Technologies.
- By Monica Eaton Founder of Chargebacks911 and Fi911. Chief Information Officer of Global Risk Technologies.
The way many people find love has changed over the last few years, with digital tools and dating channels becoming an increasingly popular way for people to meet their significant other.
More romantics choosing to scour the internet in search of their other half also means big business for dating apps, websites and social platforms.
According to recent data, revenue in the online dating industry is projected to reach over $3 billion in 2023, with 440 million people predicted to use online dating sites and apps by 2027 – 100 million more than the population of the US and double the population of Brazil.
This rise in popularity of dating sites and apps means it’s a fruitful time to be involved in this industry, with strong opportunities for new players to provide a virtual venue for romance and cater for more specific niches and segments of the population.
However, with great opportunity comes new challenges for online businesses vending love this time of year, including a fast-growing problem within the dating space and E-commerce in general: chargebacks.


DIGEST
What are the sources of chargebacks?
Chargebacks are the primary tool issuing banks use to resolve credit card payment disputes for their customers.
When a consumer did not authorize a charge, or is unhappy with a product or service, they can challenge the charge with their financial institution. If the bank feels the consumer’s claim is valid, they will initiate a chargeback to reverse the payment from the merchant back to the consumer.
A simple concept, right? However, when digging a little deeper, chargebacks are very complex and create issues for merchants operating in the dating space and beyond.
For example, there are dozens of potential chargeback triggers that could occur at different stages in a transaction. Many of these triggers have an assigned “reason code,” which are connected to each chargeback case in an attempt to explain what caused the problem.
In many cases, triggers that may not qualify for a legitimate chargeback are filed under a similar but unrelated reason code, initiating a chargeback for an illegitimate reason.
There are three main causes of chargebacks:
• Merchant Error: seemingly minor policy and procedure oversights by the merchant.
Criminal Fraud: criminals (bad actors, scammers, fraudsters) seeking to deliberately steal from consumers.
• First-party fraud or misuse (previously friendly fraud): buyers who appear legitimate, but later file unjustified chargebacks either unknowingly or maliciously.
Regardless of what triggered the chargeback, a dating merchant suffering from illegitimate chargebacks is still liable to lose revenue while also having to pay costly fees for each dispute, increasing overhead costs that may end up being passed on to the consumer. If the situation gets out of control, a merchant may lose the ability to process card transactions entirely.
Why do dating sites experience so many chargebacks?

First-party misuse is a fast-growing threat for many online merchants across practically all industries and verticals. Recent data quantifies it as a $50 billion cost for businesses this year alone. Each product category has unique triggers, but the underlying problem remains the same.
There are a few reasons why a dating site or app might receive a chargeback. Customer might pay for the service, find a match, then file a chargeback to recover the money spent – effectively abusing the chargebacks system and cybershoplifting from the merchant.
However, not every chargeback is a clear-cut case of abuse.
For example, some might sign up for service, then decide the platform isn’t what they’re looking for, and experience “buyer’s remorse.” Others might sign up for a free trial, then forget to cancel before being charged for service. The buyers are still not entitled to chargebacks in either of these scenarios, but there’s more nuance to the situation than outright fraud, resulting in unnecessary chargebacks being filed.
How to mitigate chargebacks
The first step to mitigate chargebacks is to make it easy to cancel the subscription or account. Clearly, no business wants to lose customers, but a cancellation of services is far better than a chargeback.
Companies should make sure they are sending users alerts of upcoming charges, and that their cancellation policies and procedures are fair, straightforward, and easy-to-locate from any point on their site or app.
The cancellation process should be streamlined, and customers should be provided with clear confirmation that they won’t be billed in the future.
Next, billing descriptors should clearly identify the merchant on their customers’ bank statements. If customers can’t recognize a charge based on the descriptor, they may suspect fraud and request a chargeback.
That’s why a merchant’s descriptor should clearly identify the brand by the company name or URL, along with any other relevant descriptive information.
Thirdly, attentive customer service can be one of the best methods of both preventing chargebacks and retaining subscribers. While this may seem obvious, this point cannot be stressed enough.

Many of us have been in a position where we need to speak with a business but cannot get a response by phone, email, etc. By offering responsive customer service across multiple channels, including phone, email, and social media, it will reinforce consumer confidence that they can resolve a transaction dispute or issue with the merchant rather than their bank.
Finally, be aware of the signs of criminal fraud.
Changing account details, such as location, age, or photos right after making a new account is considered suspicious activity. Similarly, criminals also use the tactic of sending a lot of messages to try making fast connections with users.
Merchants should be on the lookout for users who send a high velocity of messages with spam-style content. By staying on top of this, it will prevent fraudulent transactions and thus eliminate the need for customers to file a chargeback.
All love and no loss
Online technology is constantly evolving, and new chargeback threats appear daily for businesses across all verticals. While there are times when it’s impossible to prevent a chargeback, employing an effective chargeback management strategy that is flexible enough to identify new trends and techniques, counteract new technology, and adapt on the fly to a shifting landscape will provide the best opportunity for success.
NEW CHATGPT4.0 CONCERNS: A MARKET FOR STOLEN PREMIUM ACCOUNTS
 - By Marc P. Serber
- By Marc P. Serber

INSIDER
ChatGPT’s implications for cybersecurity has been a hot topic of discussion among security leaders and experts as many worry that the AI software can easily be misused.
Since its inception in November 2022, several organizations such Amazon, JPMorgan Chase & Co., Bank of America, Citigroup, Deutsche Bank, Goldman Sachs, Wells Fargo and Verizon have restricted access or blocked the use of the program citing security concerns.
In April 2023, Italy became the first country in the world to ban ChatGPT after accusing OpenAI of stealing the data of users.
And their concerns are not baseless.
In a report published by Check Point Research (CPR), security researchers highlighted an increase in the trade of stolen ChatGPT Premium accounts, which enables cyber criminals to get around OpenAI’s geofencing restrictions and get unlimited access to ChatGPT.
The market of account takeovers (ATOs), stolen accounts to different online services, is one of the most flourishing markets in the hacking underground and in the dark web. Traditionally this market’s focus was on stolen financial services accounts (banks, online payment systems, etc.), social media, online dating websites, emails, and more.
Since March 2023, CPR sees an increase in discussion and trade of stolen ChatGPT accounts, with a focus on Premium accounts:
1. Leak and free publication of credentials to ChatGPT accounts
2. Trade of premium ChatGPT accounts that were stolen
3. Bruteforcing and Checkers tools for ChatGPT – tools that allow cybercriminals to hack into ChatGPT accounts by running huge lists of email addresses and passwords, trying to guess the right combination to access existing accounts.
4. ChatGPT Accounts as a Service – dedicated service that offers opening ChatGPT premium accounts, most likely using stolen payment cards.
Why is the market of stolen ChatGPT account on rise and what are the main concerns?

ChatGPT imposes geofencing restrictions on accessing its platform from certain countries (including Russia, China and Iran).
Utilizing the ChatGPT API allows cybercriminals to bypass different restrictions, as well as use of ChatGPT’s premium account.
All this leads to an increasing demand for stolen ChatGPT accounts, especially paid premium accounts. In the dark web underground, where there is a demand – there are smart cybercriminals ready to take advantage of the business opportunity.
Meanwhile, during the last few weeks there have been discussions on ChatGPT’s privacy issues, with Italy banning ChatGPT and Germany considering banning it as well.
Moreover, ChatGPT accounts store the recent queries of the account’s owner. So, when cybercriminals steal existing accounts, they gain access to the queries from the account’s original owner. This can include in personal information, details about corporate products and processes, and more.
Trade of Stolen Accounts of ChatGPT
Cybercriminals often exploit the fact that users recycle the same password across multiple platforms. Using this knowledge, malicious actors load sets of combinations of emails and passwords into a dedicated software (also known as an account checker) and execute an attack against a specific online platform to identify the sets of credentials that match the login to the platform.

A final account takeover occurs when a malicious actor takes control of an account without the authorization of the account holder.
During the last month, CPR observed an increase in the chatter in underground forums related to leaking or selling compromised ChatGPT premium accounts:

INSIDER
Mostly those stolen accounts are being sold, but some of the actors also share stolen ChatGPT premium accounts for free, to advertise their own services or tools to steal the accounts.

In the following example, a cybercriminal shared four stolen premium ChatGPT accounts. The way those accounts were shared and the structure of it, led CPR to conclude that those were stolen using a ChatGPT account checker.
against different websites, and thus steal accounts for online platforms.
As SilverBullet is a configurable suite, to do a checking or bruteforcing attack against a certain website requires a “configuration” file that adjusts this process for a specific website and allows cybercriminals to steal account of this website in an automated way.
In the specific case, researchers identified cybercriminals offering a configuration file for SilverBullet that allows checking a set of credentials for OpenAI’s platform in an automated way.

This enables them to steal accounts on scale. The process is fully automated and can initiate between 50 to 200 checks per minute (CPM).
Also, it supports proxy implementation which in many cases allows it to bypass different protections on the websites against such attacks.
accounts
Tools to Hack into ChatGPT Accounts

- Account Checker and Configuration
Files for Bruteforcing tools
SilverBullet is a web testing suite that allows users to perform requests towards a target web application. It offers a lot of tools to work with the results. This software can be used for scraping and parsing data, automated pen testing, unit testing through selenium and much more.
This tool is also frequently used by cybercriminals to conduct credential stuffing and account checking attacks
Another cybercriminal who focuses only on abuse and fraud against ChatGPT products, even named himself “gpt4”. In his threads, he offers for sale not only ChatGPT accounts but also a configuration for another automated tool that checks a credential’s validity.
ChatGPT Plus Lifetime Upgrade Service

On March 20, an English-speaking cybercriminal started advertising a ChatGPT Plus lifetime account service, with 100% satisfaction guaranteed.
The lifetime upgrade of regular ChatGPT Plus account (opened via email provided by the buyer) costs $59.99 (while OpenAI’s original legitimate pricing of this services is $20 per month). However, to reduce the costs, this underground service also offers an option to share access to ChatGPT account with another cybercriminal for $24.99, for a lifetime.



A number of underground users have already left positive feedback for this service, and have vouched for it. Like in other illicit cases, when the threat actor provides some services for a pricing that is significantly lower the original legitimate one, it was noted that the payment for the upgrade is done using previously compromised payment cards.
eyes and ears open to detect deepfakes and to understand their rights against their malicious use.
ChatGPT: The dark side of AI that could put digital security at risk

Cybersecurity, Italian excellence of Cybersecurity, highlights the features of possible new cyber criminal attacks generated by AI
Everyone is talking about Chat GPT, the free chatbot based on artificial intelligence created by OpenAI. The non-profit artificial intelligence research organization promotes the development of friendly AI, i.e. intelligence capable of contributing to the good of humanity.
By accessing their website, you can virtually converse with a “virtual person”, an AI programmed to answer any question, thanks to a sophisticated machine learning model with a high machine learning capability.

But what are the risks that this Chatbot can entail?
ChatGPT has already attracted many cyber criminals, who, in the first place, have made almost identical copies of the site or app.
Downloading those from official stores and installing them on the phone, they can then spread malicious content.
The most serious problem, however, is another one: through specific and artfully built queries, GPT Chat is the perfect tool that, in the hands of an attacker, can help him to create what, in the cyber world, is called spear phishing attack.
They are, in fact, hyper-customized attacks, calibrated on the information that users, without realizing it, share on their social accounts and through daily navigation on PCs and mobile.
In this way, cyber criminals use AI to build deceptive content created specifically for the person they are targeting.
To counter this growing and increasingly insidious phenomenon, Ermes - Cybersecurity (www.ermes. company/it/), Italian excellence of cybersecurity, has developed an effective AI system.

“Companies and employees, as it is accessing today with ChatGPT, will increasingly rely on third-party services or enabling technologies based on AI. For this reason, we are monitoring and developing with Ermes a tool that certainly allows you to use them, but that does so safely through filters and blocks of sharing all that sensitive information such as
email, passwords or economic data, that by mistake we can include in our requests to these services,” Lorenzo Asuni, Chief Marketing Officer di Ermes - cybersecurity.
ChatGBT and Scams, the three main risk factors:
1. The number one scam, therefore, is the birth of phishing sites that exploit the hype on ChatGPT, already hundreds in recent weeks alone.
Recognizing them is not easy: they have similar domains, look almost identical to web pages or apps and often rely on nonexistent integrations, creating duplicates of the service that steal, so, credentials to all those who register;
2. Spear phishing attacks become easier and more scalable with the qualitative and fast production of business email compromise campaigns (BEC), sms (smishing) or ads (malaware), aimed at economic scams, personal data theft or credentials;
3. The sharing of sensitive company information, with the continuous demand for content, answers and analysis.
How does this happen? For example, with a simple “reply to this email” forgetting to exclude the email of the recipient or sender, or giving these new technologies economic data or names of customers or partners.
A practical example: Business Email Compromise, the risk for business emails
ChatGPT responds excellently to any content query, but this becomes particularly risky when used as a business email attack, the so-called BEC.
With BEC, attackers use a template to generate a deceptive email, which prompts a recipient to provide him with sensitive information.
With the help of ChatGPT, in fact, hackers would have the ability to customize any communication, thus potentially having unique content for each email generated thanks to AI, making these attacks more difficult to detect and recognize as such.

Likewise, writing emails or building a copy of a phishing site can become easier without typos or unique formats, which today are often critical to differentiate these attacks from legitimate emails. What scares the most is that it becomes possible to
add as many changes to the prompt as “make the email urgent”, “emails with a high probability of recipients clicking the link” and so on.
Evolution of Lazarus’ DeathNote cluster: from cryptocurrency attacks to the defense sector


cryptocurrency


Recently security researchers investigated DeathNote, one of the clusters that belong to the infamous Lazarus group. DeathNote has transformed drastically over the years, beginning in 2019 with attacks on cryptocurrency-related businesses worldwide.
By the end of 2022, it was responsible for targeted campaigns that affected IT companies and defense companies in Europe, Latin America, South Korea, and Africa. The latest report tracks a shift in DeathNote’s targets as well as
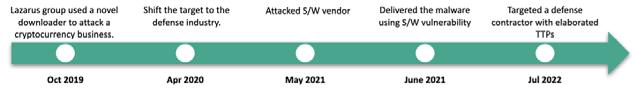

the development and refinement of their tools, techniques, and procedures during the last four years.
The infamous threat actor, Lazarus, has persistently targeted cryptocurrency-related businesses for a long time. While monitoring the actor’s activities, Kaspersky noticed that they employed a significantly changed malware in one case.
In mid-October 2019, security experts came across a suspicious document uploaded to VirusTotal. The malware author used decoy
documents that were related to the cryptocurrency business. These include a questionnaire on specific cryptocurrency purchasing, an introduction to a particular cryptocurrency, and an introduction to a bitcoin mining company.
This was the first time the DeathNote campaign came into play, targeting individuals and companies involved in cryptocurrency in Cyprus, the United States, Taiwan and Hong Kong.
Timeline of the DeathNote cluster
However, in April 2020, researchers saw a significant shift in DeathNote’s infection vectors. The research revealed that the DeathNote cluster was employed in the targeting of the automotive and academic organizations in
Eastern Europe linked to the defense industry.
At this time, the actor switched all decoy documents related to job descriptions from defense contractors and diplomatic-
related ones. Besides that, the actor elaborated its infection chain, using the remote template injection technique in their weaponized documents, and utilized Trojanized open-source PDF viewer software.
Both these methods of infection result in the same malware (DeathNote downloader), which is responsible for uploading the victim’s information.
In May 2021, it was observed that an IT company in Europe, which provides solutions for network device and server monitoring, was compromised by the DeathNote cluster. Moreover, in early June 2021, this Lazarus subgroup began utilizing a new mechanism to infect targets in South Korea. What caught the researchers’ attention was that the initial stage of the malware was executed by legitimate software, which is widely used for security in South Korea.

While monitoring DeathNote during 2022, the researchers discovered that the cluster has been responsible for attacks on a defense contractor in Latin America.
The initial infection vector was similar to what has been the case with other defense industry targets, involving the use of a Trojanized PDF reader with a crafted PDF file. However, in this particular case, the actor adopted a side-loading technique to execute the final payload.
In an ongoing campaign that was first discovered in July 2022, it was revealed that the Lazarus group had successfully breached a defense contractor in Africa.
The initial infection was a suspicious PDF application, which had been sent via Skype messenger. Upon executing the PDF reader, it created both a legitimate file (CameraSettingsUIHost.exe) and malicious file (DUI70.dll) in the same directory.
“The Lazarus group is an infamous and highly skilled threat actor. Our analysis of the DeathNote cluster reveals a rapid evolution in its tactics, techniques, and procedures over the years. In this campaign, Lazarus isn’t confined to cryptorelated business but has gone much further. It deploys both legitimate software and malicious files to compromise defense enterprises. As the Lazarus group continues to refine its approaches, it is crucial for organizations to maintain vigilance and take proactive measures to defend against its malicious activities,” comments Seongsu Park, lead security researcher, GReAT at Kaspersky. To avoid falling victim to targeted attacks by known or unknown threat actors, Kaspersky researchers recommend implementing the following measures:
• Carry out a cybersecurity audit and monitor your networks constantly to rectify any weaknesses or malicious elements discovered in the perimeter or inside the network.
• Provide your staff with basic cybersecurity hygiene training, as many targeted attacks start with phishing or other social engineering techniques.
• Educate your employees to download software and mobile apps only from trusted sources and official app stores.
• Use endpoint detection and response (EDR) product to enable timely incident detection and response to advanced threats. A service such as Kaspersky Managed Detection and Response provides threat hunting capabilities against targeted attacks.
• Adopt an anti-fraud solution that can protect cryptocurrency transactions by detecting and preventing account theft, unverified transactions and money laundering.
How email authentication is crucial to remedying NON-PROFITS’ VULNERABILITY
 - By Gerasim Hovhannisyan CEO and co-founder, EasyDMARC
- By Gerasim Hovhannisyan CEO and co-founder, EasyDMARC

HOT SEAT
Charities are lifelines for the most vulnerable people in society. They have proved essential during Covid-19, the cost-of-living crisis and following natural disasters such as the earthquakes in Turkey and Syria earlier this year. Their domestic and international efforts have been and continue to be crucial during times of hardship.
Like all organizations, charities are digitising. They are offering online services and fundraising opportunities, meaning reliable and trusted digital infrastructure is increasingly important. But as their digital footprint has increased, so has their vulnerability.
For example, following the Turkey-Syria earthquakes prompted cyber actors to disguise themselves as charities to deploy phishing attempts, taking advantage of people’s emotions and those truly trying to help those affected by the earthquakes.
Similarly, charities’ email inboxes are vulnerable to phishing emails, leading to potentially devastating ransomware attacks or data breaches, which could cost them reputationally and financially. But, most importantly, it can stop charities from supporting those who rely on their help.
With dubious emails and phishing attacks being a gateway for many problems, the non-profit sector needs to implement technical tools to deal effectively with unwanted emails.
So, why is technology such as email authentication so valuable? What kind of email authentication technologies exist, and how can non-profit organizations implement email authentication tools?
SPF, DKIM, DMARC, and thorough authentication
To fully protect themselves, charities must implement the email authentication technology trifecta – SPF, DKIM and DMARC. These three technologies have different functions that together provide a defensive barrier for email inboxes.
When an organization uses Domain-based Message Authentication, Reporting, and Conformance (DMARC) on their domains, it means that the sender can identify legitimate emails by verifying those from protected domains. When a DMARC email comes into the receivers’ inbox, it allows the automation of reporting, quarantining or rejecting non-legitimate emails.

For DMARC to operate, Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) must be enabled.
SPF is crucial as it logs all the servers that are permitted to send emails from a domain. At the same time, DKIM signs all legitimate outbound emails with a cryptographic key.
Using SPF, DKIM, and DMARC together provides an almost foolproof solution to the majority of domain impersonation for phishing attempts.
Why email authentication is crucial to stopping phishing
Phishing emails are a common gateway for ransomware attacks, financial scams and data breaches. That means being proactive and stopping potentially destructive phishing emails before they can enter a user’s inbox is key.
In 2022, 97% of companies received at least one phishing attempt via email. With that in mind, email security leaders are increasingly focused on preventing the distribution of phishing emails.
Likewise, to stop malicious emails from landing in inboxes, charities should turn towards guiding phishing emails well before they reach a user’s inbox.
Email authentication allows for a selfservice implementation that creates a transparent email ecosystem, ultimately resulting in a faster rejection process for phishing emails.

The authentication of emails will become even more important to charities with the advent of new tools, such as generative AI, which has sparked concern in the cybersecurity space. AI technology has empowered cyber actors to create targeted and well-composed emails in bulk.
The non-profit sector is falling behind
Non-profit organizations are attractive targets for cyber actors. It’s well-known that charities have limited funding and are more likely to favour spending these funds on frontline charitable work rather than ploughing it into resources, training, and technologies that help protect against cyber threats.
That’s not all. Charitable organizations often rely on volunteers who bring their own devices instead of relying on centrally issued IT equipment. As a result, there is no unified standard of cyber defences across IT equipment, meaning cyber actors can easily compromise access points.
Despite the sector’s vulnerability, recent research has revealed that only 1.2% out of almost 10 million .org domains have implemented DMARC to decrease the risk of phishing attacks out of 9.9 million .org email domains reviewed.
DMARC is designed to prevent phishing by automatically flagging and blocking any incoming emails that are believed to be spoofed.
However, for it to be effective, organizations must configure their systems to a “reject” policy which automatically blocks suspicious emails before they reach a recipient’s inbox.
With a “quarantine” policy, the messages are permitted but directed to the spam folder, while “p=none” allows all suspect emails through.
Unfortunately, the study found that 45.6% (171,486) of the 3.8% of global .org domains with DMARC had been improperly configured, resulting in organizations being unaware of received or blocked emails.
HOT SEAT
By continuing to leave inboxes unprotected from fraudulent emails, cybercriminals won’t stop viewing non-profit organizations as lowhanging fruits with high rewards.
Why email authentication comes out on top
When it comes to cybersecurity, there are three branches - people, process and technology. So it prompts the question, why does email authentication technology come out on top?
Email authentication can be more effective than cyber security training in preventing phishing attacks. Most phishing campaigns involve domain impersonation, where the phishing email sender impersonates a legitimate domain.
Therefore, email authentication ensures emails from domains are verified, and any unverified emails are rejected or directed to the spam folder, avoiding human error or lack of awareness that can occur if people are relied on solely to identify dubious emails.
Human error may be exacerbated at charitable organizations that often have a sizeable proportion of parttime staff, including volunteers, who may need more security training and awareness.
Authentication methods like DMARC, SPF and DKIM are crucial to preventing the risks attached to phishing emails. This makes email authentication an important part of any non-profit’s cybersecurity strategy.

The benefits of email authentication
Implementing email authentication tools is vital to the stable running of
non-profit organizations and, in turn, benefits all people working with or benefitting from charities.
For non-profits, it is important that their reputations remain intact. Emails from a spoofed domain that leads to a hacking incident can severely damage their standing within their community.
An email authentication policy can protect their domain reputation from being negatively affected by malicious actors who use fake domains to impersonate them and launch phishing attacks.
Moreover, deploying DMARC can aid organizations in enhancing email authentication, ensuring that legitimate emails are sent directly to the intended recipient’s inbox. This can be particularly significant for email campaigns developed to support a cause, as it ensures they receive maximum visibility and do not end up in the spam folder.
The benefits of email authentication go beyond supporting non-profits. Donors also benefit from email authentication as non-profits are often entrusted with sensitive personal and financial donor information, which requires adequate security measures to safeguard.
Email authentication adds an extra layer of security, protecting sensitive data from being compromised as a result of phishing, spoofing, or other email-based hacks.
Email authentication is critical for non-profit organizations and should not be viewed as optional but as a necessary layer of security. However, it should be implemented correctly.
Proper implementation of email authentication tools and policies can reduce the risk of costly cyber-attacks and phishing attempts that can lead
to the compromise of both the nonprofit’s and donors’ sensitive personal information and the loss of funds.

IMPORTANCE OF CYBER SECURITY IN THE POWER DISTRIBUTION SECTOR

In the biggest bust of the quarter, the administrator of the infamous data breach forum BreachForums took it offline after the arrest of its US-based owner/ promoter
- By Prashant Diwakar
Securing supervisory control and data acquisition (SCADA) networks in the power distribution sector is crucial to ensure the safe and reliable operation of the power grid. A major cyber attack on a SCADA network in the power distribution sector could result in widespread power outages that last for days or even weeks, causing significant economic damage and disruption to daily life.
A cyber attack could also cause damage to critical infrastructure equipment, such as transformers and circuit breakers, resulting in costly repairs and replacement. In addition, a cyber attack could pose safety risks to workers and the public, such as by causing equipment to malfunction or operate in an unsafe manner.
Nation-state actors are a major threat today. These actors may have advanced capabilities and resources to launch sophisticated cyber attacks, causing significant damage to critical infrastructure and posing a threat to public safety.
Protecting these networks against cyber threats is essential to ensure the continued operation and resilience of the country’s infrastructure, as well as to safeguard national security interests.
India’s power sector has been targeted by cyber attacks multiple times in recent years. With the rapid automation in the power sector, including the power distribution side as well, cyber-attacks are a major concern.
The Indian government has recognized the importance of cybersecurity in the power sector and has taken steps to improve cybersecurity in critical infrastructure, including the establishment of the National Critical Information Infrastructure Protection Centre (NCIIPC) and the development of cybersecurity guidelines for the power sector.
Vulnerabilities of SCADA Network in the Power Distribution Sector
The rollout of Remote Terminal Units (RTUs) across substations linked to a control room via MPLS network poses several security threats that must be mitigated.
These threats include unauthorized access, weak passwords, vulnerable software and firmware, lack of encryption, and the risk of insider threats posed by employees with access to the network.
Unauthorized access is a significant concern as it can be initiated by external hackers or malicious insiders. Strong access control policies, such as two-factor authentication, are necessary to prevent unauthorized access.
Weak passwords can also lead to unauthorized access. Organizations must enforce strong password policies and provide regular training to employees on how to create and maintain secure passwords.
Vulnerable software and firmware pose a risk of exploitation by attackers. Regular patching and updates are necessary to address known vulnerabilities and ensure that the latest security patches are installed.
Encryption is essential to protect sensitive data transmitted across the MPLS network. Organizations must ensure that all data is encrypted, especially data transmitted over the Internet.
Insider threats posed by employees must be considered. Organizations must conduct background checks on employees and implement access control policies to limit access to critical systems.
Regular employee training is also necessary to raise awareness of the risks associated with cybersecurity and the need for all personnel to remain vigilant against potential threats.
Major Cyber Attacks in the Power Sector
SCADA (Supervisory Control and Data Acquisition) networks are critical systems that manage and control industrial processes, including power plants, water treatment facilities, and transportation systems.

These systems are often connected to the internet and other networks, making them vulnerable to cyber attacks. Here are some examples of reported cyber attacks on SCADA networks:
• Stuxnet (2010): One of the most well-known cyber attacks on SCADA networks is the Stuxnet worm, which targeted Iran’s nuclear program. Stuxnet was a sophisticated malware that exploited vulnerabilities in Siemens SCADA software to manipulate industrial processes and cause physical damage to Iran’s uranium enrichment centrifuges.
• Ukraine Power Grid Attack (2015): In December 2015, a cyber attack on Ukraine’s power grid caused a blackout that affected over 200,000 people. The attackers used malware to gain access to the SCADA network and manipulate the system to shut down power.
• Triton (2017): The Triton malware, also known as Trisis, was discovered in 2017 and was specifically designed to target industrial safety systems. The malware targeted a safety instrumented system (SIS) at a petrochemical plant in Saudi Arabia, which could have led to a catastrophic explosion.
• Colonial Pipeline (2021): In May 2021, a ransomware attack on the Colonial Pipeline, which supplies gasoline to the eastern United States, caused the company to shut down its pipeline for several days, leading to fuel shortages and price increases. The attackers used a phishing email to gain access to the company’s SCADA network and install ransomware.
Sourish Dey, Director at Trisim Global Solutions, a company offering cyber security solutions based out of Kolkata, India said “These attacks demonstrate the severity of the cyber security risks associated with SCADA networks. As these networks become increasingly interconnected and accessible, power utilities must remain vigilant and implement robust cybersecurity measures to prevent attacks and protect critical infrastructure. Compromise may result in jeopardizing national security. ”
Major vulnerabilities in SCADA equipment reported in the past
In February 2022, the US Cybersecurity and Infrastructure Security Agency (CISA) reported major vulnerabilities in SCADA equipment manufactured by leading OEMs and said “Successful exploitation of these vulnerabilities may disclose device credentials, cause a denial-of-service condition, device reboot, or allow an attacker to gain full control of the relay. This could result in loss of protection to your electrical network.”
Here are some examples of reported vulnerabilities by OEMs of SCADA equipment:
• Siemens: In 2012, a vulnerability was discovered in Siemens’ WinCC SCADA software, which allowed attackers to gain remote access to the system and execute arbitrary code. This vulnerability was exploited in the Stuxnet attack.
• Schneider Electric: A vulnerability was discovered in Schneider Electric’s Modicon M221 PLCs, which allowed attackers to remotely execute arbitrary code and take control of the system. The vulnerability was caused by a lack of input validation in the firmware. (Source: https:// www.cisa.gov/news-events/ics-advisories/icsa-19-13601)
GE Digital: In 2018, a vulnerability was discovered in GE Digital’s iFIX SCADA software, which allowed attackers to remotely execute arbitrary code and take control of the system. The vulnerability was caused by a lack of
authentication and encryption in the software. (Source: https://www.cisa.gov/news-events/ics-advisories/icsa21-040-01)
• Rockwell Automation: In 2020, a vulnerability was discovered in Rockwell Automation’s Logix controllers, which allowed attackers to remotely execute arbitrary code and take control of the system. The vulnerability was caused by a flaw in the firmware that allowed attackers to bypass the authentication mechanism. (Source: https://www.cisa.gov/news-events/icsadvisories/icsa-22-342-03)
These examples demonstrate that vulnerabilities can exist in SCADA equipment from different OEMs.

To mitigate the risk of exploitation, organizations must stay up-to-date with the latest security patches and updates, conduct regular vulnerability assessments, and implement robust security measures, such as network segmentation, access control policies, and encryption.
It is also essential to work with OEMs that prioritize security and regularly release security updates to address known vulnerabilities.
Guidelines to be considered for Cybersecurity
Indian Computer Emergency Response Team (CERT-In) guidelines: CERT-In provides guidelines and best practices for securing IT systems and networks in India. These guidelines cover various aspects of cybersecurity, including network security, access control, incident response, and security auditing.
Information Technology (IT) Act, 2000: This is the primary law governing cybersecurity and e-commerce in India. The act provides legal recognition for electronic transactions, digital signatures, and other related areas. It also includes provisions for cybersecurity, such as unauthorized access to computer systems, data theft, and hacking.
ISO/IEC 27001: This is the internationally recognized standard for information security management systems (ISMS).
It provides a framework for establishing, implementing, maintaining, and continually improving information security management in an organization. Following this standard can help ensure the confidentiality, integrity, and availability of information assets.
NIST Cybersecurity Framework: The National Institute of Standards and Technology (NIST) Cybersecurity Framework
is a set of guidelines for improving cybersecurity risk management in critical infrastructure sectors, including the energy sector.
It provides a framework for organizations to manage and reduce their cybersecurity risk in a structured and costeffective way.

Infrastructure to build cyber resilience for a SCADA Network in Power Distribution Sector

A bill of materials (BOM) for a cybersecurity project in the power distribution sector involving the rollout of RTUs across substations linked to a control room over an MPLS network would typically include the following components:
• Firewall: A core firewall and perimeter firewall are necessary to secure the network and prevent unauthorized access. A core firewall is installed internally to segment and secure different subnets within the SCADA network, while a perimeter firewall is installed at the network boundary to protect the network from external threats.
Firewalls capable of deep packet inspection, intrusion prevention, and malware detection are essential for protecting against cyber attacks targeting the SCADA network.
• Anti-APT solution: Advanced persistent threats (APTs) are a significant threat to power SCADA networks. An anti-APT solution is necessary to detect and prevent these sophisticated attacks that may evade traditional security measures.
Such a solution may include behavioral analysis, machine learning, and other advanced techniques to identify anomalous behavior and prevent data exfiltration.
• Threat Intelligence: Threat intelligence solutions gather information on emerging threats and vulnerabilities in real-time. Power SCADA networks face a wide range of cyber threats, and timely access to threat intelligence is essential for proactive threat detection and response.
Threat intelligence may also help organizations stay up-to-date with new malware, phishing campaigns, and other threats targeting power systems
• Antivirus and Anti-malware software: Antivirus and anti-malware software should be installed on all endpoints, including servers and workstations, to protect against malware and other cyber threats. Power SCADA networks may be targeted by various types of malware, such as ransomware, trojans, and rootkits. Antivirus and anti-malware software can help prevent these attacks and protect against data loss and downtime.
• Patch management system: A patch management system is necessary to ensure that all software
and firmware are up-to-date and that known vulnerabilities are addressed promptly. Power SCADA networks may use various types of software and firmware, and regular updates are essential to maintain security and prevent the exploitation of known vulnerabilities.

• Security Information and Event Management (SIEM) system: A SIEM system is necessary to collect and analyze security-related data from various sources in real-time. SIEM systems provide advanced log management, threat detection, and incident response capabilities, enabling organizations to quickly detect and respond to security incidents. For power SCADA networks, real-time monitoring and alerts are critical for maintaining operational resilience and preventing downtime.
Deploying Cyber Security equipment and solutions not enough
Identify training needs: Organizations should assess the cybersecurity knowledge and skills of their employees to determine the areas in which training is required. SCADA system operators, network administrators, and other employees with access to critical systems should receive specialized training
to address the unique risks associated with these systems.
• Conduct regular security assessments: Organizations should conduct regular security assessments to identify vulnerabilities and gaps in the network’s security architecture. The assessment should be conducted by an independent third party to ensure objectivity and thoroughness.
• Develop an incident response plan: Organizations should develop an incident response plan that outlines the steps that need to be taken in the event of a cyber attack. The plan should include contact information for key personnel, procedures for notifying stakeholders, and guidelines for containing and remediating the attack.
• Conduct regular drills: Regular drills should be conducted to test the effectiveness of the incident response plan. These drills can help identify areas for improvement and ensure that the organization is prepared to respond to a realworld cyber attack.

CHATGPT: HOW ONE GENERATIVE AI BUSINESS TRIGGERED WORLDWIDE POLICY DISCUSSION
The temporary ban in Italy received widespread attention, raising concerns about the potential impact of such decisions on the development of new AI applications
- By Chandu GopalakrishnanOn April 14, OpenAI CEO Sam Altman confirmed what was being suspected for the past few weeks: there are no plans for ChatGPT-5 as of now!

During a virtual event at the Massachusetts Institute of Technology, Altman stated that there
is currently no GPT-5 in training. His move was quickly tied to the open letter demanding an AI pause.
However, Altman’s statement that there is no GPT-5 in the works may not be comforting to AI’s critics. Altman acknowledged that upgrades
and updates are being developed for GPT-4, which could increase its capacity.
He also admitted that OpenAI is shipping product tweaks that may not be fully optimized for the good of humanity or user safety, such as the
plug-in for GPT-4 that lets its large language model browse the internet, which could lead to data privacy and user manipulation concerns.
Altman attempted to ease concerns by stating that OpenAI spent over

six months training GPT-4 before its public release and emphasized the importance of studying the safety of the model.
However, given OpenAI’s increasing closed-off, for-profit status,
skepticism may be warranted. GPT-4 is a black box, and the company has not released any information about its training data, architecture, construction, or inner workings. And it’s inviting legal trouble too.
OpenAI, ChatGPT data use, and potential legal challenges
Globally, users of ChatGPT have lodged complaints against OpenAI for safety concerns, as the European Union works on passing an Artificial Intelligence Act, the United States defines an AI Bill of Rights, and the United Kingdom recommends that existing agencies regulate AI.
Various countries have expressed their concerns regarding the accountability of AI companies through complaints, investigations, and commentary.

The Center for AI and Digital Policy filed a complaint with the US Federal Trade Commission to halt OpenAI from developing new models of ChatGPT until safety measures are implemented.
“The Federal Trade Commission has declared that the use of AI should be ‘transparent, explainable,
fair, and empirically sound while fostering accountability’. OpenAI’s product GPT-4 satisfies none of these requirements,” said the complaint. “It is time for the FTC to act. There should be independent oversight and evaluation of commercial AI products offered in the United States.”
Additionally, the Italian Garante is investigating OpenAI for a recent data breach and lack of age verification to safeguard younger users during registration from inappropriate generative AI content.
The biggest blow, however, came from Italy.
ChatGPT and the ban in Italy
In March 2023, Italy made history by becoming the first Western nation to block ChatGPT, the advanced chatbot, citing concerns over personal data protection. The decision was made by Garante, the Italian data protection authority, which has given OpenAI
until the end of April to comply with its demands.
Garante stated that ChatGPT’s data collection methods were incompatible with data protection laws, and the platform’s lack of age verification could expose children to harmful content. As a result, Garante used an emergency procedure to temporarily suspend OpenAI’s processing of personal data.
OpenAI blocked access to ChatGPT for Italian residents but the API and Microsoft Bing remained accessible. The GDPD has provided OpenAI with a list of demands it must comply with by April 30 before lifting the temporary ban.
The Italian government wants OpenAI to inform users how their personal data will be used to train the tool and obtain their consent before processing it. OpenAI must also identify accounts used by children and implement an age-gating system for underage users by September 30. The EU’s new proposal aims to
improve how platforms verify users’ age and OpenAI’s approach will be a testbed for new measures.
ChatGPT ban in Italy and its ripple effects
In Europe, OpenAI is walking the path that burnt the heels of many predecessors.

Even before formally centralizing its European legal setup in Ireland, Google was slapped with a €50 million GDPR fine in France. Similarly, TikTok was fined by the Dutch, Italian, and French authorities for privacy violations before it legally established its operations in Ireland in 2021.
OpenAI is yet to establish a local headquarters in any of the European Union’s 27 countries. This leaves the company vulnerable to new investigations and bans by any member country’s data protection authority.
The temporary ban in Italy received widespread attention, raising concerns about the potential impact of such decisions on the development of new AI applications. It did not take much time for liberal democracies of the world to step in with bans, if not regulations.
The Irish Data Protection Commission shortly announced its intention to collaborate with
the Italian Garante and the EU data protection commission to investigate whether ChatGPT had violated privacy laws.
The Swedish and Spanish privacy regulators also said that future probes on ChatGPT might happen if users filed complaints against the service.

Ulrich Kelber, a spokesperson for Germany’s Federal Commissioner for Data Protection, stated that a ban on AI applications could be enforced in Germany if OpenAI violated GDPR or similar policies.
However, Germany’s Minister of Transport and Digital Infrastructure, Volker Wissing, believed that banning AI was not the solution. Instead, he emphasized finding ways to ensure values like democracy and transparency.
Canada’s Office of the Privacy Commissioner investigated a complaint against ChatGPT for collecting personal data without consent.
In France, Jean-Noël Barrot, Minister for Digital Transition and Telecommunications, declared the country’s intention to master AI technology and develop models and technologies that uphold French values, following a wave of AI excitement, followed by AI fear.
As of now, this is where the regulators in the West stand.
THE COVER
North America
An investigation was opened by Canada’s Office of the Privacy Commissioner of Canada on 4 April after a complaint was made, claiming that OpenAI had collected, used, and shared personal information without consent.
Philippe Dufresne, the Privacy Commissioner, stated that the impact of AI on privacy is a significant concern, and his office must keep up with rapidly evolving technology.
Since the investigation is ongoing, no further details have been disclosed by Dufresne’s office.
Meanwhile, in the US, the Center for Artificial Intelligence and Digital Policy (CAIDP) filed a complaint with the US Federal Trade Commission on 30 March, requesting the regulatory body to investigate OpenAI’s practices and prevent the company from releasing new commercial versions of GPT-4.
In its 47-page complaint, CAIDP expressed broad concerns about OpenAI’s practices, arguing that they are unfair, deceptive, and pose various privacy risks.
The company’s lack of evidence of safety checks to protect children from harmful content and violation of emerging legal norms on AI governance were also highlighted.
CAIDP had long planned to file a complaint.
In March, the organization’s president, Marc Rotenberg, and chair and research director, Merve Hickok, called on US policymakers to introduce guardrails for ensuring algorithmic transparency, fairness, accountability, and traceability throughout the AI lifecycle. Two weeks later, they hinted at the possibility of filing a complaint with the FTC.
The European Union and neighbour countries
After Italy banned ChatGPT and Spain raised concerns about privacy, the European Data Protection Board (EDPB) agreed on 13 April to form a task force to coordinate the efforts of European data protection authorities.
At present, there is limited information about the EDPB’s new task force, except for the decision to address ChatGPTrelated action at the upcoming plenary session on 26 April. The minutes from the EDPB’s 13 April plenary session are currently unavailable.
Member countries and their neighbours were charting their individual courses.
On 14 April, ChatGPT came under investigation by France’s data protection regulator (CNIL) following five complaints, three of which were publicly disclosed, according to media reports. The CNIL did not make any official statements.
The first complaint was filed by Zoé Villain, a lawyer and president of Janus International, an association for raising awareness of digital issues. Villain alleged that OpenAI did not obtain her consent for the terms of use or privacy policy when signing up for the service and did not provide access to personal data in violation of her right of access.
The second complaint came from developer David Libeau, who criticized OpenAI’s lack of transparency and fairness in a blog post and accused the company of failing to safeguard people’s right to data protection.
The third complaint was initiated by Éric Bothorel, a member of parliament, on 12 April after noticing ChatGPT provided erroneous information.
Bothorel tested the tool by requesting information about himself and found it to be mostly inaccurate, including his date of birth. Bothorel has organized a seminar on ChatGPT for French members of parliament, to be held at the National Assembly on 9 May.
Montpellier, a French city, has banned its officials from using ChatGPT as a precautionary measure after deputy mayor Manu Reynaud recommended the ban.
Germany was one of the earlier respondents to Italy’s call. However, nothing much was heard after their initial reaction on 10 April.
The body of independent German data protection supervisory authorities of federal and state governments, the Germany’s data protection conference (DSK), launched an investigation into ChatGPT, with a reported launch date of 10 April.
The North Rhine-Westphalia watchdog and the Commissioner for Data Protection and Freedom of Information of Hesse have made similar announcements, but details are scarce as the DSK has not provided any further information.

Ireland, where Google and Facebook faced the regulatory wrath, was comparatively soft on ChatGPT.
The regional media reported Ireland’s data protection commissioner’s decision to communicate with Italy’s regulator regarding ChatGPT’s temporary ban in Italy.
No further information has been disclosed at this time, but the commissioner stated that they will collaborate with all EU data protection authorities on the issue.
On 13 April, the Spanish Data Protection Agency (AEPD) declared that it would conduct an independent investigation to investigate possible violations of OpenAI’s practices.
Additionally, the AEPD reported that the week prior, it had requested that the EU’s data protection regulator add ChatGPT to the agenda of its upcoming plenary meeting The Swiss Federal Data Protection and Information Commissioner (FDPIC) contacted the Italian Garante on 4 April to obtain further details regarding its ban on ChatGPT.
While the FDPIC has not yet initiated a formal investigation, it is currently recommending users to familiarize themselves with how the company handles their data prior to uploading images or making inquiries. This also applies to other AI tools being used by companies, who should ensure that their users are informed about how their data is being processed and for what purposes.
Surprisingly, the UK has not started its policy discussions on ChatGPT, or even generative AI.
On 3 April, the Information Commissioner’s Office issued a reminder to organizations using generative AI software that the regulations governing personal data must be followed without exception.

‘Standards Are No Longer Voluntary’
Titania’s Matt Malarkey shares his experience and insights about the US National Cybersecurity Strategy with The Cyber Express Editor-in-Chief
Augustin Kurian.
As the Strategic Alliances Manager for Titania, Malarkey is responsible for building and managing relationships with key US customers, channel partners, and technology partners, at a time when a huge customer base is gearing up to face cybersecurity policy changes in the US.
Titania is a technology company that specializes in creating cybersecurity software to detect and remediate vulnerabilities. The company has a strong presence in the United States and is constantly expanding its operations, which is where Matt Malarkey comes in.
His job is to create and maintain partnerships that will help the company expand its reach and grow its business.
An experienced professional with a keen understanding of the industry and the market, Matt works cross-functionally with the product management, engineering, marketing, and sales teams to ensure that the company’s alliances align with its overall business goals.
He develops engagement strategies for key customers and partners, ensuring that their needs are met and their concerns are addressed.
Malarkey also keeps a close eye on policy, regulatory, and market issues to inform the company’s go-to-market plan and product development. This helps the company stay ahead of the curve and make the necessary changes to remain competitive in a rapidly evolving market. In addition to building and managing relationships, Malarkey coordinates promotional marketing activity with partners, including the development of joint-propositions. He also represents Titania on panels at in-person and virtual events, where he shares his knowledge and insights with others in the industry.
Titania, along with the entire industry, is currently polishing their strategy to surf along the changing regulatory tides. Malarkey shares his experience and insights about the US National Cybersecurity Strategy with The Cyber Express.

Tell us about Titania, and your role in it
Fundamentally, Titania is a cybersecurity company. We have software tools that are used to assess the security and compliance of networking devices. We help determine whether they are inherently configured, secure, and are in compliance with the security benchmarks.

I’ve been with the company for a little over three years. While the company’s headquartered in the UK, I am based in Washington DC. My role is to establish strategic relationships with both the reseller, community technology partners, and our customers.
Titania has a sizeable number of customers in the US government space. My job is to help manage some of those relationships and try and grow our footprint here in the US.
I think the strategy will bring into focus certain requirement in certain industries where there are no well-defined mandatory standards, or where there’s lack of harmonization across mandatory standards.
We will start seeing greater harmonization of minimum cybersecurity standards across different critical national infrastructure verticals.
The companies that are already within those verticals will have to adhere to some minimum standards, to begin with. The strategy will improve those minimum standards, enhance them, and then ensure that it’s not what we’re seeing this across the board.
The Biden administration is dedicating a lot more attention to this because of some of the very high-profile breaches that have taken place over the past couple of years. I think the strategy will bring into focus certain requirement in certain industries where there are no well-defined mandatory standards, or where there’s lack of harmonization across mandatory standards.
We will start seeing greater harmonization of minimum cybersecurity standards across different critical national infrastructure verticals.
You’re right, it has been a long time coming. The US administration has clearly dedicated a lot of time towards enhancing cybersecurity at a national level. This is just a continuation of the executive orders that we’ve already seen in the last couple of years.
This strategy is significant because it changes commitments to cybersecurity from being voluntary. It stops market forces from dictating how industry adopts cybersecurity and how it employs it.
The requirements and adherence to standards are going to be the norm going forward. We’ve started seeing this already in some areas of the US government. We are going to see increased requirements for mandatory cybersecurity standards across the board.
The companies that are already within those verticals will have to adhere to some minimum standards, to begin with. The strategy will improve those minimum standards, enhance them, and then ensure that it’s not what we’re seeing this across the board.
The Biden administration is dedicating a lot more attention to this because of some of the very high-profile breaches that have taken place over the past couple of years.
Yes, the impact of Colonial Pipeline (breach) was enough to trigger action. Protection for the third-party vendor was all over the cybersecurity news. Do you foresee a lot more collaboration when it comes to third-party companies?
Yeah, I think it’s definitely drawing. The strategy is increasing focus on where liability sits, not just on these large companies or large contractors, but also the third-party companies that they work with.
Speaking of the US, one of the important things currently happening there is the National Cybersecurity Strategy. It was a long time coming. How happy are you with the present plan?
Many times, compliance end up as just ticking off a checklist. The culture of cybersecurity by design is still a crucial area that several industries are yet to attain. How do you think this particular cybersecurity strategy is going to change that?


Moving to a point discussed earlier, you said about harmonization between existing reporting structures and the entry of newer reporting requirements. How exactly will that be done?
That’s all still unclear. However, I expect it to be a process that will look akin to how under the Obama administration developed the National Cybersecurity Framework for critical national infrastructure.
There will be a lot of involvement from trade groups and trade organizations to help sort of inform the development of these minimum standards. The industry may not particularly like the idea of having standards imposed upon them, but the move is definitely important. They have the opportunity to inform or influence the development, and I expect that the government will enable them to be able to do that.
Discussions like that usually come with incentives. What’s your thought on that?
I think you have to have incentives in order to bring people to the table. I would not call it an incentive, but we will for the purpose of this discussion.
The first incentive for industry to be an active participant in the development of these standards and the employment of them is that it is in their own benefit to ensure and enhance their cyber cyber resiliency.
Beyond that obvious point, there are other incentives like better premiums for cyber insurance, which are, as we know, on the rise.
Liability protections for organizations that are adopting these standards and reporting them
correctly and accurately is a key thing. So are penalties for the lack of adherence.
Now that you mentioned cyber insurance, how will the new strategy affect the cyber insurance market? Do you foresee changes in insurance underwriting or do you think there will be better adoption in terms of what you call liability of data?

I’m, afraid I’m not an expert in this specific area, but my thoughts are that if we have an evidencebased approach to assessing and determining and reporting cybersecurity standards, that will give the insurance industry a lot more confidence when it comes to policy underwriting and understanding the risk that their customers are taking.
Going back to the basics, do you find any drawbacks in the screen strategy? Do you find any particular area the government did not pay enough attention to?
I think with all government policy statements, there are holes in it. Or there are things that can be more clearly expressed or more clearly defined. Ultimately, it’s the direction of travel that I am truly supportive of.
If we look at what has been employed in the past, It hasn’t been working to the level that we need. A change is required, and it’s critical to have industry participation in support of this.
There have been some murmurs of discontent from the industry, I think once it starts to recognize the benefits participating, they’ll start to come round to it.



PRELUDE
Artificial intelligence (AI) has transformed many industries over the last few years, and cybersecurity is no exception.
AI-powered tools are now being used to detect, respond, and mitigate cyber threats, making them an invaluable resource for cybersecurity professionals.
As cyber threats continue to evolve and become more sophisticated, the use of AI in cybersecurity is likely to become even more widespread.
In this survey, we have focused on the current use of AI in cybersecurity and examined the benefits and challenges of using AI in cybersecurity. We have also explored the advantages of AI-powered tools, such as their ability to analyze large amounts of data quickly and accurately. We have examined the potential for AI to automate specific cybersecurity tasks and the implications for cybersecurity professionals.
Finally, the survey concludes with a section on the future of AI in cybersecurity, where we have examined the potential for AI-powered tools to evolve and improve and the impact this could have on the cybersecurity industry.
This survey provides valuable insights into AI’s current state and future in cybersecurity. The results will interest cybersecurity professionals, researchers, and policymakers looking to use AI in cybersecurity. We look forward to sharing the results of this survey with the cybersecurity community.

KEY TAKEAWAYS FROM THE SURVEY
55.36% of respondents understand the relationship between AI and cybersecurity, and 24% of respondents claim in-depth knowledge of the topic.
80% of respondents believe that AI will significantly transform cybersecurity and enhance the security of computer systems, networks, and data.
Approximately 70% of respondents believe that the impact of AI on cybersecurity will be positive, while 30% believe it will have a negative impact.
50% of respondents have used AI-based tools for anomaly detection, and 45% have used AI-based tools for behavioral analysis.
73.20% of respondents believe that using AI in their cybersecurity operations will increase efficiency, while 24% believe it will decrease efficiency.
72.41% of respondents believe that using AI in their organization’s cybersecurity will positively impact their security posture, while 23.24% believe it will have a negative impact.

41.95% of respondents have privacy concerns related to using AI in cybersecurity, 41.19% have concerns over bias in decision-making, and 16% have concerns over the need for more transparency.
44.76% of respondents feel that technical challenges are significant in implementing AI in their cybersecurity approach, 36.19% feel that organizational challenges are significant, and 18.41% feel that financial challenges are significant.
25.55% of respondents have used Computer Vision technology in their cybersecurity approach, 39.96% have used Natural Language Processing (NLP) technology, and 32.89% have used Machine Learning technology.
Nearly 5% of respondents have used AI-based tools for other purposes related to threat detection, including identifying malware, conducting vulnerability assessments, and predicting and preventing cyber attacks.
WHAT IS YOUR UNDERSTANDING OF AI IN CYBERSECURITY?




Over half of the respondents (55.36%) in this survey had some understanding of the relationship between AI and cybersecurity, while 24% claimed in-depth knowledge of the topic. However, 19% of the respondents expressed the need for help in understanding the relationship between AI and cybersecurity.






















In-depth knowledge



WHICH AI TECHNOLOGIES HAVE YOU USED IN YOUR CYBERSECURITY APPROACH?







The survey found that respondents had used different types of AI technologies in their cybersecurity approach, with 25.55% having used Computer Vision technology, 39.96% using Natural Language Processing (NLP) technology, and 32.89% having used Machine Learning technology. Only 2.2% of respondents indicated that they had not used AI technology in their cybersecurity approach.


DO YOU BELIEVE AI WILL REVOLUTIONIZE THE CYBERSECURITY LANDSCAPE?





Around 80% of the respondents believed that AI will significantly transform cybersecurity, enhancing the security of computer systems, networks, and data. This suggests that AI has the potential to play a crucial role in the future of cybersecurity.

HOW DO YOU SEE AI IMPACTING THE FUTURE OF CYBERSECURITY?





Approximately 70% of the respondents believed that the impact of AI on cybersecurity will be positive, with AI helping to identify and mitigate cyber threats, detect anomalies in network traffic and system behavior, and enhance the overall security of computer systems and networks. However, nearly 30% of the respondents believe that AI will have a negative impact on cybersecurity, with concerns about potential risks and vulnerabilities associated with using AI in cybersecurity, such as the possibility of AI being hacked or manipulated to carry out cyber attacks. They may also worry about the impact of AI on employment and job loss in the cybersecurity field.
Positively
Negatively No impact




WHICH AI-BASED TOOLS HAVE YOU USED FOR THREAT DETECTION?

Approximately half of the respondents (50%) have used AI-based tools for anomaly detection, while 45% have used AI-based tools for behavioral analysis. Anomaly detection involves identifying unusual or abnormal events or behavior that may indicate a security threat, while behavioral analysis involves analyzing patterns of behavior that may indicate a security threat.
Anomaly detection
Behavioral analysis
Other (Please specify)
None
WHAT ARE THE POTENTIAL RISKS ASSOCIATED WITH USING AI IN CYBERSECURITY?
The survey found that 41.95% of respondents had privacy concerns related to using AI in cybersecurity, while 41.19% had concerns over bias in decision-making. Another 16% had concerns over the need for more transparency. Respondents worry that AI may make decisions that are not consistent with their preferences, or that AI may be biased or discriminatory in decision-making.
ARE THERE ANY CONCERNS OR CHALLENGES ASSOCIATED WITH USING AI IN CYBERSECURITY?


41.95% of the respondents have privacy concerns related to using AI in cybersecurity. They may be concerned about the collection and use of personal data and potential data breaches. 41.19% of the respondents have concerns over bias in decision-making. They may be worried that AI algorithms may be biased and make decisions that unfairly impact certain groups or individuals. 16% of the respondents have concerns over the need for more transparency. They may believe that there should be more transparency in the development and use of AI algorithms in cybersecurity. In addition to concerns, respondents also highlighted some challenges associated with using AI in cybersecurity. 44.76% of the respondents feel that technical challenges are significant in implementing AI in their cybersecurity approach. They may encounter challenges in terms of algorithm development, data processing, and integration with existing systems. 36.19% of the respondents feel that organizational challenges are significant, such as lack of resources or training for AIbased tools. 18.41% of the respondents feel that financial challenges are significant, such as the cost of acquiring and maintaining AI-based tools.
Technical challenges

Organizational challenges
Financial challenges
Other (Please specify)
DO YOU THINK USING AI IN CYBERSECURITY WILL INCREASE OR DECREASE EFFICIENCY?
According to the survey, 73.20% of the respondents believe that using AI in their cybersecurity operations will increase efficiency. AI-powered tools can help automate certain tasks, such as monitoring and analyzing network traffic, which can help cybersecurity professionals focus on more critical tasks. However, 24% of the respondents believe that using AI in their cybersecurity operations will decrease efficiency. They may believe that AI-based tools require more training and maintenance, which can be time-consuming and expensive.
DO YOU THINK USING AI IN YOUR ORGANIZATION’S CYBERSECURITY WILL POSITIVELY OR NEGATIVELY IMPACT YOUR SECURITY POSTURE?

72.41% of the respondents believe that using AI in their organization’s cybersecurity will positively impact their security posture. AI-powered tools can help identify and mitigate security threats more quickly and accurately, which can help enhance overall security. On the other hand, 23.24% of the respondents believe that using AI in their organization’s cybersecurity will have a negative impact. They may believe that AI-based tools are not yet sophisticated enough to deal with advanced threats or that they may introduce new vulnerabilities.
Positively
Negatively
No impact
HAVE YOU USED AI-BASED TOOLS FOR OTHER PURPOSES RELATED TO THREAT DETECTION?
Around 5% of the respondents have used AI-based tools for other purposes related to threat detection, including identifying malware, conducting vulnerability assessments, and predicting and preventing cyber attacks.
RESPONDENT’S PROFILE

AI in Cybersecurity is now a reality and no longer in the realm of possibility. It has the potential to bring about significant disruption to the cybersecurity industry.
Application of AI in the Cyber security domain offers the potential of helping bridge the skill gap and alleviate the shortage of cyber security professionals being experienced by majority of the organizations today. The biggest beneficiaries will be the small and medium sized organizations that struggle to attract and retain cyber security talent. In the next few years, most cyber security products will be forced to have AI capabilities to automate routine tasks, process large volumes of data more efficiently and accurately than a human security analyst or engineer. AI would help augment and assist human security professionals in faster decision making rather than replacing them entirely.
KAUSTUBH MEDHE

HEAD, RESEARCH AND CYBER THREAT INTELLIGENCE SERVICES, CYBLE
On the flip side, AI also threatens to eliminate manually intensive cyber security services such as vulnerability assessments, penetration testing, source code reviews and even risk and compliance consulting services. This will cause short term impacts on cyber security service providers and only those vendors that can effectively leverage AI for performing more complex and value-added services will survive and thrive. Since generative AI platforms can absorb and process user supplied data to provide a response or a solution, users will be tempted to upload sensitive company information or data to such platforms with the expectation of receiving a more customized or relevant answer. Organizations must guard against such misadventures of their staff to preserve the confidentiality and privacy of their data and will have to establish
appropriate security policies and training to prevent such disclosures. Regulators have their work cut out to bring in the necessary guard-rails to prevent the un-intended consequences of adoption of AI in cyber security too. As with all technology, AI can also be classified as dual use – it will be abused by cyber criminals for developing malicious programs, to launch convincing/sophisticated attack campaigns or to bypass “ AI based security mechanisms” with the aim of maintaining an edge over the defenders.
To date, AI has been wellreceived by neuroinclusive community groups as an aid to support learning and working. However, as identified in this report there is a large proportion of individuals who do not know or have a basic understanding of AI – so the learning and working capabilities may not be known, such as summarizing large bodies of text for easier reading. However, accessibility is built in the design, so while on
HOLLY FOXCROFT

HEAD OF NEURODIVERSITY, STOTT AND MAY CONSULTING
the surface we can suggest AI as a ‘unambiguous tool to help us work’ – it needs to be accessible by design. If processing and retrieving new data/information, then that too must be monitored to be free from bias. Essentially, using AI for cybersecurity or supporting those working in cybersecurity, will always require human validation of output produced.
CONCLUSION
In conclusion, the survey results suggest that AI is becoming an increasingly important tool in the cybersecurity industry. Most respondents believe that AI has the potential to enhance the security of computer systems, networks, and data, and many have already used AI-based tools for anomaly detection and behavioral analysis. However, respondents also highlighted concerns and challenges associated with using AI in cybersecurity, such as privacy concerns, bias in decision-making, and technical challenges. Overall, the survey results indicate that AI will continue to transform the cybersecurity landscape in the future, and cybersecurity professionals will need to adapt to take advantage of this technology while mitigating any potential risks.

March 24, USA, Time: 4PM - 5PM (EST)
Boom in Cybersecurity Placement and Education: Trend or Bubble
Graduates from top-ranked cybersecurity programs can expect to make six-figure starting salaries between $100,000 and $200,000, HR news services say. The US, particularly California, has a fine set of institutions that offer undergraduate and higher education programmes in various aspects of cybersecurity, often with significantly higher fees than their global peers. But is the current boom a stable trend or a bubble?
Participants: Vendors, Universities, Cybersecurity Placement consultants
80% C-level Executives and
Region in focus: USA

Key takeaways:
1. Entry-level qualification for cybersecurity has changed drastically
2. Industry and academia are working in tandem to meet the demands of the sector
3. Formal education: High entry barriers and role of industry support
4. Next big thing in technology education
March 31, Switzerland Time: 4PM - 5PM (CET)
Telcos and Privacy in Switzerland

Telcos in Switzerland are subject to stricter rules governing network outages and hacking incidents. ISPs there must detect and counter malicious activity – such as phishing attempts – on websites, blocking them if necessary. This poses questions on stealth browsing and the use of Tor or VPNs. How does Switzerland achieve better cyber monitoring with minimal invasion of privacy?
Participants: Telecom companies, Privacy advocates, Government officials
Region in focus: Europe
Key Takeaways:
1. How does Singapore manage that?
2. How does the cybersecurity industry help the government in achieving it?
3. Are businesses compromising ease for compliance or is it the other way around?
4. What about the geopolitical threats that run the risk of posing cyber threats to businesses?
Heads will join!






