
www.thetycoonmedia.com

In today's digital age, where every byte of information holds immense value, the importance of cybersecurity cannot be overstated. As our world becomes increasingly interconnected, the threats posed by cyber attacks grow in complexity and frequency. In such a landscape, the role of trustworthy cybersecurity companies becomes paramount, serving as the vanguards in the battle to safeguard our data and privacy.
In our annual edition of "The Most Trusted Companies in Cybersecurity," we meticulously analyze and showcase the enterprises that have consistently demonstrated excellence, innovation, and reliability in the realm of cybersecurity. These are the companies that not only

provide cutting-edge solutions but also prioritize transparency, accountability, and customer trust.
This year, it is our honor to feature Portalz on the cover of our prestigious publication. Portalz has emerged as a beacon of trust and reliability in the cybersecurity industry, setting new standards for excellence and innovation. Their unwavering commitment to protecting digital assets and empowering businesses to navigate the complex cybersecurity landscape has earned them the trust and admiration of clients worldwide.
What sets Portalz apart is not just their technological prowess, but also their holistic approach to cybersecurity. They understand that effective cybersecurity is
not merely about building impenetrable walls, but also about fostering a culture of security, education, and resilience within organizations. Through a combination of advanced technologies, expert guidance, and comprehensive training programs, Portalz equips their clients with the tools and knowledge needed to stay ahead of emerging threats.
Moreover, Portalz has distinguished itself through its unwavering dedication to ethical practices and customer-centricity. In an industry often plagued by opaque policies and hidden agendas, Portalz stands out as a beacon of transparency and integrity. They prioritize open communication, ethical decision-making, and a genuine commitment to the well-being of their clients, earning them the reputation as a trusted partner in cybersecurity.
As we celebrate the achievements of Portalz and other esteemed companies in the cybersecurity sector, let us also reaffirm our commitment to building a safer, more secure digital world.
 Kevin Williams Editor-in-Chief The Tycoon Magazine
Kevin Williams Editor-in-Chief The Tycoon Magazine
KevinWiiams Editor’s Desk


Cybersecurity A Historical Overview and Challenges of New Era Towerwall Fortifying Your Cyber Defenses And Safeguarding Digital Assets C O N T E N T S
The Evolution of
Cover ory
TYCOON Magazine The TEAM CONTACT US www.twitter.com/TheTycoonMag www.linkedin.com/company/the-tycoon-media www.facebook.com/thetycoonmedia www.thetycoonmedia.com admin@thetycoonmedia.com +1 614 467 0981



8

Traditionalcybersecuritysolutionsarestrugglingto keeppacewiththeevolvingtacticsof cybercriminals.Astechnologyadvances,sodothe methodsusedbyhackerstoexploitvulnerabilities. Therefore,thereisanurgentneedfornew-age cybersecuritysolutionsthatcanadaptandrespondtothese ever-changingthreatseffectively
Innovativecybersecuritysolutionsarecrucialto safeguardingsensitiveinformation,protectingdigitalassets, andensuringtheintegrityofonlinesystems.Byinvestingin cutting-edgetechnologies,organizationscanenhancetheir cybersecuritypostureandstayaheadofcyberthreats.
PortalzPtyLtdentersthesceneasaprominentplayer
FoundedbyWolfgangFlatow(CEOandInventor),the companystandsoutasatopproviderofstate-of-the-art cybersecuritysolutionsspecificallydesignedtotackle today'smostcomplexandcriticalsecuritychallenges.With apassionforinnovationandacommitmenttosafeguarding digitalassets,Wolfgangleadshisteamindeveloping advancedsolutionsthatconfidentlyempowerbusinessesto navigatetheever-evolvingcyberthreatlandscape.
MeettheTech-savvyLeader
Throughouthisfour-decadejourneyintheITfield, Wolfganghasbeeninvolvedinvariousfacets.Itallbegan atthedawnofpersonalcomputinginthe80s,crafting


9
programsforXerox,Commodore64andAmiga,AtariST, AppleII,Macintosh,andIBMPCs
Intheearlystagesofhiscareer,hedevelopedspecialist calculators,simulatedplanetaryorbits,andcreatedgames. Notably,hisJokerPokergamewasbundledwith CommodorePCsandthenportedtosixPCbrands. Wolfgangdesignedanddevelopedagroundbreakingclient queuingapplicationforQSystemsPerthin1990, controllingnumerousperipheralsandfeaturinginnovative userinterfaces,thatsoldgloballytogovernments,social securityagencies,andbusinesses.
Between1991and2001Wolfgangworkedforsoftware companieslikeSouthernGroup,RioTinto,andINeedHits inPerth.In2003,hefoundedCertainEdgePtyLtdin
BrisbanethatcommercializedhispatentedUniversal DatabaseSchema(UDS). Subsequently,heandhisteam createdUniDap,arapidapplicationdevelopment(RAD) enterpriseplatformleveraginghisUDSarchitecture. UniDapprovideseffectivesolutionstogovernmentand businessentitiesacrosstheglobe.
WolfganghascontinuedR&DinpursuitofimprovedIT architectureandsolutionstouniversalsystemproblems, including:
l UniversalTaxonomy–aglobalcategorizationID standard
l StandaloneTrustPlatforms–immutabledatasystems withoutdistributedblockchain

l GuaranteedSecurity–impenetrabledataand enterprisesystemssecurity

In2018,hebeganresearchingcomplexnumbersandthe infinitelycomplexMandelbrotSet.Twopatent-pending technologiesemerged:1)FractalAssetManagement –visiblefractalassettokensresidinginand securedbyfractalsand2)FractalTransformation –universalfractaldataencryption.“Fractal Transformation led to the formation of Portalz Pty Ltd in 2022. Fractal security R&D has led to a rich and versatile new art and science, revolutionizing cybersecurity, particularly in the Post Quantum era,”states Wolfgang.
UnparalleledProtectionAgainstQuantum Attacks
Wolfgangproudlystates,“Our Fractal Transform IP delivers 'security certainty' to cybersecurity; a critical breakthrough and paradigm shift from the current 'everything is crackable' baseline.”This revolutionaryadvanceoffersunparalleledprotection againstQuantumAttacksorchestratedbywell fundedcriminalhackers,weaponizedAIand QuantumComputerdecryption.
Portalz'smissionistodeliver guaranteedFractalTransform DataHardeningforpersonal andenterprisecomputer systems.Thecompanyhas ® launchedQuantumBunker forWindows,yourpersonal data,password,andlogin FractalVault,thefirst

10

abletoguaranteeimpenetrabilityofVaultdata.Portalzis ® alsoexpandingtodeliverQuantumBunker toother operatingsystemsandtobringFractalTransformsecurity tofilesanddatabases.
Asakeyplayerincybersecurity,Wolfgangknowsthat governments,military,intelligenceagencies,corporations, andindividualsdependonclassicblockencryption methods,whicharenowvulnerabletoquantumattacks. Portalzoffersaguaranteedsolutiontothemostsignificant cybersecuritythreatinhistory:theimminentdangerposed byQuantumComputerdecryptionofclassicencryption.
QuantumAttackscombinehackerresources,AI,and QuantumComputerstocrackfortressdefensesandbreak classicencryptiontoaccessprotecteddata.Incontrastto classicencryptedciphers,FractalTransformedciphers cannotbecrackedbyanymeans,includingQuantum Computers.
FractalTransformation:ANewErainCybersecurity
FractalTransformationisPortalz'scybersecurity breakthrough;dataissecuredintheMandelbrotFractal. Unliketraditionalblockencryptionmethods,Fractal Transformationoperatesdifferently.Itactsovertheentire payloadwithacontinuousuniquefractalstream,rendering theoriginaldatainaccessible,itnolongerexistsinthe cipher.
Unlikeclassicencryption,FractalTransformationcannotbe compromisedthroughbrute-forceattacks;thereisnofinite algorithmorfinitekeyset.
Thefractaldimensionisinfinitelycomplex,uniqueand unpredictable. FractalTransformationcreatesaportal betweenthephysicalandfractaldimensionsthatonlyyou canopen.
R&D:TheJourneytoImpenetrableCybersecurity
Classicblockencryptionmethodssafeguarding communications,servers,storagedrives,files,and passwordsarepenetrable.Theyhaveprovenvulnerableto conventionalandQuantumComputerbreaches.
SixyearsofR&DhasresultedinthecreationofpatentpendingFractalTransformationIP,markingabreakthrough inachievingimpenetrablesecurity
DataprotectedbyFractalTransformationoffersaguarantee
ofimpenetrability ThecybersecuritystrategyatPortalz revolvesaroundtheconceptofImpenetrableData Hardening,involvingtheeliminatingofplain-textsensitive informationfromstoragedrives,networks,andcomputer memory.
ByincorporatingFractalTransformationweeliminate cybersecurityrisksatthedatalevel.Thisapproachworks handinhandwithclassicFortresssecuritymeasures.Inthe eventofFortresssecuritybreach,sensitiveplain-textdata remainsinaccessible.
EthicalCybersecurityConsiderations
Wolfgangandhisteammeetandsurpassallregulatory securitystandards.Underhisleadership,thePortalzteam prioritizesethicalconsiderations,particularlyconcerning privacy,safeguardingpersonalandprivateinformation,and shieldingagainstQuantumAttacks.
Whilebreachesingovernmentandcorporatesecurity dominatethenews,Portalzisdeeplyconcernedaboutthe devastatingimpactonindividualusers.
Theirgoalistoshowaworldplaguedbycyberthreatsfrom hackers,AI,andQuantumComputersthataguaranteed solutionexists.Theyhaveanewsecurityfoundationto buildanewsecurityfuture.
NewEncryptionStandard
Portalz'svisionisfoundeduponFractalTransformation, aimingtointegrateorreplaceclassicencryptionmethods currentlyinuse.WiththeemergenceofAIandQuantum Computerthreatstoclassicencryptionthereisapressing needforalternatives.Thisechoesahistoricaleventwhen DESwascompromisedin1996,leadingtoitsreplacement withAES.However,replacingAEStodaycomeswith significantlyhighercostsandchallengesduetothe exponentialgrowthofglobalIT
NowtheentireglobalITcommunity,including governments,militaries,intelligenceagencies,corporations, andsoftwaredevelopers,facesthecriticaldecisionof selectingthenextencryptionstandard.WhileNISTis selecting'quantum-resistantalgorithms',Portalzbrings guaranteedimpenetrability.
FractalTransformationisbuiltonentirelynewfoundations, ensuringguaranteedcipherimpenetrabilitybyanymeans, includingQuantumComputers.Itisanewartandscience
11

thatdoesnotcorrelatewithclassicencryptionalgorithms, offeringanewfoundationforcybersecurity.“Whatever the new standard, it will be expensive to implement; choosing the most effective solution is critical. We are very excited to offer a guaranteed solution”saysWolfgang.
UnveilingtheMenaceofQuantumAttackin Cybersecurity
Cybersecurityisclearlyindisarray,includingthenewthreat ofQuantumAttack,acombinationof:
l Government,intelligence,andransom-warefunded Hackers
l Globalhackerrepositoriesandresources
l AI-poweredhackercodegenerationandattack strategies
l AI/QuantumComputerintegrationand'cyberaware systems'
l QuantumComputercrackingofclassicencryption
l SecretDeepStateHackerTechnologies
Theseposesignificantrisksofcriminalinfiltration,privacy breaches,servicedisruptions,reputationdamage,ransom demandsandtheft.ITsystemsfacecontinuousattack resultingintheftofmoney,sensitivedata,tradesecretsand identities.Ransomsaredemanded,privacyisviolated,and confidenceinsystemsisshaken,oftenleadingto bankruptcyforbothcompaniesandindividuals.Wolfgang believesthatifcybersecuritywereeffective,suchbreaches wouldberare.However,suchbreachesare,unfortunately, quitecommon.
EmergingTrendsShapingtheCybersecurityIndustry
AccordingtoWolfgang,primaryconcernforemerging cybersecurityrevolvesaroundweaponisedAIfusionwith QuantumComputers.Thisconcernhasbeenunderscoredby urgentmemosissuedfromtheWhiteHousetoall departments,instructingthemtodevisestrategiestoaddress thisissue,asentimentechoedbygovernmentsworldwide.It appearsthatImpenetrableFractalTransformationhascome intoexistencejustintime.“Our solutions directly target these threats, significantly improving current and future cybersecurity,”saysWolfgang.
QuotingEinstein“You cannot solve a problem with the same mindset that created it”,Wolfgangstates“The solution to classic encryption Quantum Computer vulnerability requires new foundations at the core of encryption technologies”.
ImpenetrableProducts
Seriousaboutyourprivacy,yourpersonalandprofessional datasecurity?
® QuantumBunker providesunequaledsecurityassurance andguarantee.
Thefirstguaranteedimpenetrablestorageofpersonal ® information,QuantumBunker secureskeys,passwords, logins,banking,andprivateinformationinimpenetrable fractalvaults:

12
QuantumFileBunkerbringsthesameimpenetrablesecuritytoyoursensitivefiles–targetedfor2025:

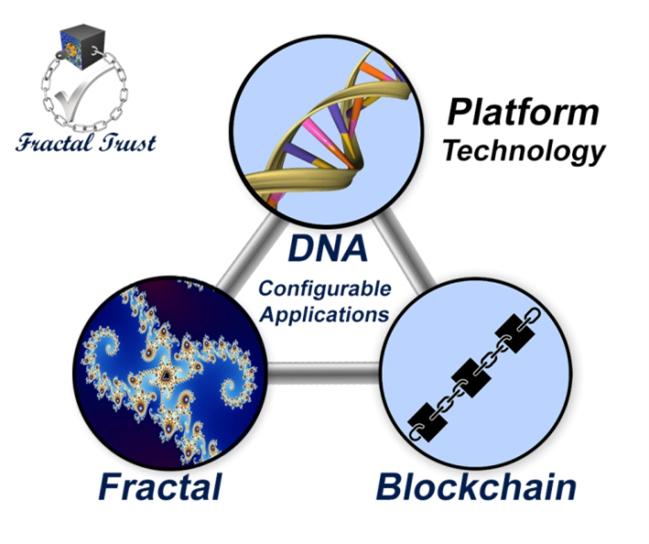
PortalzFractalTrustintegratesFractalTransformation,BlockchainImmutability,andDNAFlexibility–targetedfor 2026:


13

FractalTransformationComponentsfordevelopers-targetedfor2025:

“We foresee greater focus on Data Hardening of information at rest and in transit”saysWolfgang.

14


$130.00 (06 Issues) $70.00 (03 Issues) $25.00 (01 Issue) $250.00 (12 Issues)
Magazine The www.thetycoonmedia.com Renowned Bespoke Tailoring Expert Continues to Shape Fashion Elegance The Most Inuential in Industry 2024 Professor Andrew Ramroop CEO of Maurice Sedwell
TYCOON

16

The Evolution of CYBERSECURITY A
Historical Overview and Challenges of New Era
Cybersecurity,anintegralaspectofourdigital world,hasarichhistoryintertwinedwiththe developmentoftechnology.Fromtheearlydaysof computingtothepresenteraofinterconnectednetworks andcloudcomputing,theevolutionofcybersecurityhas beenmarkedbysignificantmilestonesandchallenges.Let's journeythroughtheannalsoftimetoexplorethehistoryof cybersecurityandtheprominentcompaniesthathave shapeditstrajectory.
Inthenascentstagesofcomputing,duringthe1940sand 1950s,cybersecuritywasanascentconcept.Ascomputers emergedaspowerfultoolsformilitaryandscientific purposes,concernsaboutprotectingsensitiveinformation begantosurface.However,itwasn'tuntiltheadventofthe internetandinterconnectednetworksinthe1970sthat cybersecuritygainedwidespreadrecognition.
The1980sand1990switnessedtheriseofnetworksecurity aspersonalcomputersbecameubiquitous,and organizationsincreasinglyreliedoninterconnected networksforcommunicationanddataexchange.Itwas duringthisperiodthatthefirstcomputervirusesand malwareemerged,highlightingthevulnerabilitiesinherent indigitalsystems.ProminentcompanieslikeSymantecand McAfeesteppeduptoaddresstheseemergingthreatsby developingantivirussoftwareandintrusiondetection systems.
Withthedawnoftheinterneteraintheearly2000s, cybersecuritytookonrenewedimportanceascyberthreats becamemoresophisticatedandwidespread.The proliferationofmobiledevicesandcloudcomputingfurther compoundedthesecuritychallenges,leadingtothe developmentofmobilesecuritysolutionsandcloud securityplatforms.CompaniessuchasPaloAltoNetworks andFortinetemergedasleadersinproviding comprehensivecybersecuritysolutionstailoredtoaddress theevolvingthreatlandscape.
Inthecurrentdecade,thecybersecuritylandscapecontinues toevolverapidly,drivenbyadvancementsintechnology andtheincreasingdigitizationofsociety.Cyberthreats, rangingfromransomwareattackstosupplychain vulnerabilities,havebecomemoreprevalentand sophisticated,posingsignificantriskstoindividuals, businesses,andgovernmentsalike.Leadingcybersecurity companiesareleveragingcutting-edgetechnologiessuchas artificialintelligenceandmachinelearningtodetectand mitigatetheseemergingthreatseffectively
Aswelooktothefuture,theimportanceofcybersecurity cannotbeoverstated.WiththeproliferationofInternetof Things(IoT)devices,theadoptionof5Gtechnology,and theincreasinginterconnectivityofdigitalsystems,the surfaceareaforcyberattackscontinuestoexpand.Itis imperativeforcybersecuritycompaniestostayaheadofthe
17

curvebyembracinginnovation,collaboration,anda proactiveapproachtocybersecurity.
Astechnologypropelsforward,cyberthreatsevolve, presentingunprecedentedhurdlesforcybersecurity companiesin2024.Inthiseraofdigitaltransformation, whererelianceoninterconnectedsystemsanddata-driven technologiesisubiquitous,thetaskofsafeguardingagainst cyberthreatshasgrownincreasinglycomplex.Here,we delveintothekeychallengesconfrontingcybersecurity companiesastheystrivetoprotectindividualsand organizationsfromtheever-changingcyberthreat landscape.
SophisticatedCyberAttacks:Cybercriminalscontinually refinetheirtactics,leveragingadvancedtechniqueslike artificialintelligence,machinelearning,andautomationto orchestratehighlysophisticatedcyber-attacks.From ransomwaretosupplychainvulnerabilities,cybersecurity companiesfacethedauntingchallengeofoutmanoeuvring adversarieswhoexploitvulnerabilitiesindigital infrastructure.
Zero-DayExploitsandVulnerabilities:Zero-dayexploits, targetingpreviouslyunknownvulnerabilities,posea significantthreattocybersecurity.Ascyberattackers capitalizeonthesevulnerabilitiesbeforetheyare discoveredandpatched,cybersecuritycompaniesmust deployproactivemeasurestodetectandmitigatezero-day exploits,oftenrelyingonadvancedthreatintelligenceand vulnerabilitymanagementsolutions.
CybersecuritySkillsShortage:Thedemandforskilled cybersecurityprofessionalsfaroutweighstheavailable talentpool,creatingasignificantskillsshortagewithinthe industry Asorganizationsstruggletorecruitandretain qualifiedcybersecuritypersonnel,companiesfacethe challengeofbuildingandsustainingrobustteamscapable ofeffectivelycombatingcyberthreats.
RegulatoryComplianceandDataPrivacy:Withthe proliferationofdataprivacyregulationssuchastheGDPR, CCPA,andemergingAI-specificregulations,cybersecurity companiesmustnavigateacomplexregulatorylandscape whileensuringcompliancewithevolvingdataprotection requirements.Failuretoadheretoregulatorymandates exposesorganizationstolegalandfinancialrepercussions andunderminestrustincybersecuritysolutionsand services.
SecuringtheCloudandIoTEcosystems:Therapid adoptionofcloudcomputingandtheInternetofThings (IoT)presentsuniquesecuritychallenges,asorganizations grapplewithsecuringdecentralizedandinterconnected ecosystems.Cybersecuritycompaniesmustdevelop innovativesolutionstosafeguardcloudinfrastructure,IoT devices,andassociateddatastreams,whilemaintaining seamlessintegrationandusability.
SupplyChainVulnerabilities:Supplychainattackshave emergedasaprominentthreatvector,targeting organizationsthroughthird-partyvendorsandsuppliers.As interconnectedsupplychainsbecomeincreasinglycomplex andglobalized,cybersecuritycompaniesfacethechallenge ofmitigatingsupplychainrisksandensuringtheintegrity andsecurityoftheentireecosystem.
DisinformationandMisinformationCampaigns:Beyond traditionalcyberattacks,cybersecuritycompaniesalso combatdisinformationandmisinformationcampaigns, whichposesignificantthreatstoindividuals,organizations, andsocietyatlarge.Addressingthesechallengesrequiresa multifacetedapproachencompassingcybersecurity,media literacy,andcollaborationwithgovernmentsandcivil society.
Inthefaceofthesechallenges,cybersecuritycompanies mustembraceinnovation,collaboration,andaproactive approachtocybersecurity.Byleveragingcutting-edge technologieslikeartificialintelligence,machinelearning, andautomation,cybersecuritycompaniescanenhance threatdetectionandresponsecapabilities,fortifying defensesagainstemergingcyberthreats.
Moreover,fosteringcollaborationandknowledgesharing withinthecybersecuritycommunityisessentialfor addressingcommonchallengesandadvancingcollective resilienceagainstcyberthreats.Byworkingtogether, cybersecuritycompaniescannavigatethecomplexitiesof thedigitallandscapeandsafeguardtheintegrity,privacy, andsecurityofindividualsandorganizationsin2024and beyond.
18

Fortifying Your Cyber Defenses And Safeguarding Digital Assets
Thecybersecuritylandscapekeepschangingas cybercriminalscomeupwithnewtricks.Even thoughtheirmethodschange,thebasicrulesfor keepingdigitalspacessafestayconstant.Theseinclude regularlyupdatingsoftwareandsystems,followingstrong securityguidelines,andhavingacomprehensive cybersecurityplantotacklenewdangerseffectively
ThisiswhereTowerwallcomesintothepicture.Asakey leaderwithintheITcybersecurityindustry,thecompany hasbuiltacomprehensivetechnologyandsolutionsetthat rangesfromsettingupformalinformationsecurityprogram planstocompany-widesecuritypolicies.
Foundedin1999,ithasdifferentiateditselfasaleading providerofinformationsecuritysolutions.Butwhattruly setsTowerwallapartisitsuniqueapproach,itscommitment toaclient-centricstrategy,anditsleadershipbya remarkablewoman,MichelleDrolet(ChiefExecutive Officer).
BeyondtheWall:AComprehensiveApproach
Towerwalldoesn'tbelieveinaone-size-fits-allapproachto cybersecurity.Thecompanyrecognizesthatevery organizationhasitsownuniquesetofsecurityneedsand challenges.Itsmotto,“The front line of cybersecurity,” reflectsitscommitmenttoprovidingacomprehensivesuite ofservicesthatsurpassmerelysettingupadigitalbarrier
The4EmethodologyofTowerwall– Evaluate, Establish, Educate, and Enforce –servesasthecornerstoneofits approachtocybersecurity.Thisframeworkisthebasisfor creatingcompletecybersecurityplansforitsclients.The cybersecuritysolutionscompanyassessestheclients' currentsecurity,setsupstrongrules,teachesemployeesthe
bestwaystostaysafe,andmakessureeveryonefollows thesestandards.Thishelpsitsclientstohaveastrong cybersecuritybase.
Furthermore,toadapttotheever-changinglandscapeof protection,Towerwalldevelopedeightdimensionsof cybersecurity Theseeightdimensionsintegrateessential securityelementsandareflexibletocatertovarious industrydemands.Thisinvolvesstudyingand implementingsecuritycontrolframeworkslikeISO,CIS,or NIST800-53,aswellasdevelopingtailoredprogramsand policiesinlinewithitsclients'regulatoryobligations.
“In healthcare, for example, organizations must comply with HIPAA regulations, while financial institutions and higher education institutions must adhere to GLBA requirements. We ensure that our clients are equipped with the knowledge and tools to navigate these complex regulatory landscapes,”statesMichelle.
ProactiveSecurityMeasuresForFortifyingYour Organization
Whenitcomestokeepingyourorganizationsafe, Towerwallunderstandsthatpeoplecanbebothyourbiggest assetandyourweakestlink.That'swhythecompany focusesonmakingsureeveryoneisawareofsecurityrisks andequippedtohandlethem.Itprovidesthoroughtraining andplentyofsupporttohelpemployeesrecognizeandstop potentialthreats.Alongsidethis,Towerwalloffers personalizedtechnologystackrecommendationsto strengthenrobustvulnerabilitymanagement,complemented byroutinepenetrationteststosimulateattacks,andswiftly addressanyvulnerabilitiesthatmayarise.
20
 Michelle Drolet (Chief Executive Officer).
Michelle Drolet (Chief Executive Officer).
InnovationsInCybersecurityServices
Asthecybersecuritylandscapechanges,Michelleandherteamwillkeeponimprovingandenhancingtheservicesof Towerwalltomatchtheirclients'evolvingneeds.ThisincludestheirofferingsandcollaborationsintheAWSmarketplace.
ThisexpansionenablesthemtoprovideacomprehensivepackageofTowerwallcybersecurityandriskmanagementservices toabroaderrangeofcustomers.Moreover,theyhaveavalue-addedresellercomponentthatallowsthemtoresell cybersecuritytechnologytofurthersupporttheirclients'needs.
GuidingClientsThroughCybersecurityComplexity
“A cornerstone of our approach is the integration of risk and compliance management,”saysMichelle.Sheandherteam workcloselywiththeclientstoguidethemthroughtheimportantaspectsofcreatingastrongsecurityandcompliance
21
framework.Thismeansdevelopingpersonalizedcyber programs,conductingin-depthriskevaluations,and providingguidanceonmeetingregulatorystandards.
Theremarkableleaderandherteamarededicatedtomore thanjustgivingadvice—theystandbytheirclientsatevery step,helpingthemconfidentlynavigatethecomplexworld ofcybersecurity.
SimplifyingCybersecurityBestPracticeswith Towerwall
Peopleoftensaythatyoucouldconstructahousewithouta blueprint,butwouldanyoneactuallywanttoliveinsucha building?Likewise,cybersecuritybestpracticesdemanda carefullyplannedstrategy.It'scrucialtograspthedetailsof risktolerance,regulatoryrequirements,andindustry standards.Towerwallaimstosimplifythesebestpractices foritsclients.Thecompanybelievescybersecurity shouldn'tfeellikeanimpossiblechallenge.Instead,itoffers realisticsolutionsandmakessureitsclientsgainuseful insightsandaclearplanforsafeguardingtheirdigital assets.
FosteringIntegrityandInnovation:TheCornerstones ofLastingSuccess
Buildingaculturewhereintegrityandinnovationthriveis thekeytolastingsuccessinanycompany Towerwallaims tonurtureanenvironmentthatsupportsteamwork, creativity,andethicalpractices.Thisbeginswithtaking ownershipofactionsanddecisionsandtreatingall individualswithrespectandfairness.Thecompanybelieves thatbychampioningintegrityandinnovation,itcandrawin andkeeptalentedpeoplewhonotonlyexcelinwhatthey do,butalsoembraceitsvaluesandgoals.
MakingaDifferenceBeyondAccolades
Towerwallhasearnednumerousleadershipandcompany awardsovertheyears,butwhattrulymatterstoMichelle isn'ttheexternalrecognition.It'stheimpacttheyhaveon others'lives.
Oneparticularmomentstandsout—thestoryofitscyber internfromMassBayCommunityCollegeforwhichthe companyorganizedandsponsoredanannualcybersecurity summit,withproceedsgoingtowardstwo(2)cyber scholarships.Thisinternwasoneofthescholarship recipientsand,asaresult,landedaSecurityEngineer
positionatahighereducationinstitute.
Hearingthosewords,“Thank you. It was because of Towerwall,”broughtimmensejoytotheTowerwallteam. Knowingthattheycontributedtoshapinghisfutureand providingopportunitiesforgrowthfilledMichelle'sheart withhappiness.
TransformingSecurityPlansIntoAction
Towerwallgaugessuccessthroughitsclients'readinessand itsabilitytoproactivelymitigatecybersecurityrisks.For nearly25years,thecompanyhasstoodbyitsclientsas theirdedicateddatasecuritypartnerthat“operationalizes” informationsecurityfromplansintoactionablestrategies.It oftencomesacrosswell-meaningsecurityplansthatstall becauseofashortageofexpertiseandresources.
NurturingClientBonds
“One of the most rewarding aspects of our work is the strong and enduring relationships we have formed with our customers,”saysMichelle.Thisbusinessisallabouttrust, andit'sreallysatisfyingtoseehowmanyclientshavestuck withthemsincethebeginning.
Thecompanyisequallythrilledbyhowmanyclients recommendittoothers.Itshowsthatitsdedicationto outstandingserviceandexceedingitsclients'expectations ispayingoff.
LookingBackOnTheJourney:ThankfulnessAnd AnticipationForWhatLiesAhead
Therealmofcybersecurityisever-changing,withnew hurdlesandopportunitiesemergingconstantly The Towerwallteamisdedicatedtostayingaheadofthegame byconstantlylearningandadapting,ensuringthattheir clientsarewell-informedandsafeguarded.
Theirmainaimistocontinueservingtheirclientswith honestyandexcellence,equippingthemwiththenecessary toolsandknowledgetosafeguardtheirdigitalassetsand achievegenuinecybersecuritysuccess.
“As we look to the future, we reflect and feel grateful for the journey that has brought Towerwall to this point. We remain excited about the future as we continue to make a positive impact in the world of cybersecurity,”Michelle.
22








 Kevin Williams Editor-in-Chief The Tycoon Magazine
Kevin Williams Editor-in-Chief The Tycoon Magazine





























 Michelle Drolet (Chief Executive Officer).
Michelle Drolet (Chief Executive Officer).



