USAID CYBERSECURITY FOR CRITICAL INFRASTRUCURE IN UKRAINE ACTIVITY

Cybersecurity Workforce Framework Workshop






Karen Wetzel, National Initiative for Cybersecurity Education
Randy Pestana, Florida International University
1 USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY 2/15/2023
The NICE Workforce Framework for Cybersecurity: A model framework for workforce planning and development


 Karen A.Wetzel Manager of the NICE Framework, NICE karen.wetzel@nist.gov
Karen A.Wetzel Manager of the NICE Framework, NICE karen.wetzel@nist.gov
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY 2
2/15/2023
NIST Mission


• To promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life.



USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY 3
2/15/2023
QUICK FACTS
• Led by the National Institute of Standards and Technology (NIST) in the U.S. Department of Commerce


• A partnership between government, academia, and the private sector
NICE Mission
To energize, promote, and coordinate a robust community working together to advance an integrated ecosystem of cybersecurity education, training, and workforce development.
History
1998: The Comprehensive National Cybersecurity Initiative (CNCI) created. Initiative 8 aims at better preparing the Federal cybersecurity workforce.
2009: Initiative 8 scope expands to include private sector workforce.
2010: Initiative #8,“Expand cyber education,” becomes public.
2014: Cybersecurity Enhancement Act of 2014 Title IV establishes the “National cybersecurity awareness and education program” (NICE).

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY 4
2/15/2023
What NICE Does
Community Coordinating Council
Interagency
Coordinating Council
International Engagement
Communities of Interest
Working Groups
LEADERSHI P & COORDINAT ION COMMUNIT Y ENGAGEME NT NICE FRAMEWOR K
Project Teams
Calls for Comments
RESOURCES
NICE Newsletter

One-Pagers
Framework in Focus
EVENTS
Monthly Webinars
NICE Conference
NICE K12 Conference
Cybersecurity Career
Awareness Week
Federal Cybersecurity

FAQs
Authoring Guides
Playbook
Spreadsheet Data
Success Stories
NF Resource Center
NICE Challenges
CyberSeek

Workforce Summit
FISSEA Forums
Workshops
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
5
Workforce Framework for Cybersecurity (NICE Framework)



- NIST SP 800-181r1





www.nist.gov/nice/framework

✔ A modular, building-blocks approach based on Task, Knowledge, and Skill (TKS) statements
✔ A common, consistent lexicon to clearly share information about what a workforce needs to know
✔ The concepts of work and learner are described in terms that can be applied to any organization
✔ Enables the establishment of regular processes
✔ For use in career awareness, education and training, hiring and career development, workforce planning and assessment
Ukrainian Translation of the 2020 NICE Framework (NIST SP 800-181r1)

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
6
Ukrainian
Official U.S.
translation.
(PDF)Document translated courtesy of the
Academy of Cybersecurity with the support of the U.S. Embassy to Ukraine. Reviewed by Diplomatic Language Services.
Government
Workforce Framework Attributes
Agility
Agility
People, processes, and technology mature and must adapt to change.A defined workforce framework enables organizations to keep pace with constantly evolving ecosystems.
Flexibility
There is no one-size-fits-all solution to common challenges.A workforce framework enables organizations to account for their unique operating context.
Interoperability
Solutions to common challenges may be unique, but they must agree upon consistent use of terms.A framework enables organizations to exchange workforce information using a common language.
Modularity




Using a common workforce framework model enables communication about across workforces (e.g., cybersecurity and privacy) within the enterprise and across sectors.

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
7
Workforce Framework Stakeholders
Employers
Framework




Educators
Identify Assess Define Teach Evidence
Learners
Possess • Acquire
Develop • Demonstrate
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
8
•
COMMON WORKFORCE FRAMEWORK USES
Employers
● Standardizing and aligning job descriptions to Work Roles
● Assessing candidates during hiring process
● Supporting mid-career shifts into the profession
Education & Training Providers

● Developing and aligning training and certifications to the framework
● Aligning curriculum to Work Roles
● Assessing learner capabilities
Learners (students, job-seekers, & employees)
● Introducing careers to interested learners
● Demonstrating workplace capability
● Supporting career paths and development
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
9
✔ Benefits of a Model Workforce Framework

✔ Model Workforce
Framework Components


✔ Background
✔ Supporting Resources
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
A Playbook for Workforce Frameworks
10
https://www.nist.gov/itl/applied-cybersecurity/nice/nice-framewor k-resource-center/playbook-workforce-frameworks
Workforce Framework Components

NICE Framework Building Blocks: Task, Knowledge, and Skill (TKS) Statements


Describes the Work
Describes the Learner
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
11
Using the NICE Framework: Building Block Applications


WORK ROLES
•Groupings of Task statements
•Work an individual or team is responsible for
COMPETENCY AREAS




• Groupings of related Knowledge and Skill statements

• Correlate with capability to perform Tasks in a domain

TEAMS
•Defined by Competency Areas or Work Roles
USAID CYBERSECURITY
CRITICAL INFRASTRUCTURE IN UKRAINE
FOR
ACTIVITY
12
Workforce Framework Work Roles
Work Role: A grouping of work for which someone is responsible or accountable


Work Roles:
• Are not synonymous with job titles or occupations

• May apply to many varying job titles
• Can be combined to create a particular job
Consist of:
• Tasks that constitute the work to be done
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
13
Oversee and Govern (14)
NICE Framework Work Role Categories
Securely Provision (11)
Operate and Maintain (7)

Protect and Defend (4) Investigate (3) Analyze (7) Collect and Operate (6)

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
5 2 W O R K R O L E S 14
Restricted Work Roles
– Title 10: Provides the legal basis for military operations (including cyber)

– Title 50: Legal authority to conduct intelligence operations and covert action (typically CIA)
Collect and Operate (Cyberspace Effects)
• All Source-Collection Manager
• All Source-Collection Requirements Manager
• Cyber Intel Planner
• Cyber Ops Planner
• Partner Integration Planner
• Cyber Operator
Analyze (Intelligence)
• Threat/Warning Analyst
• Exploitation Analyst

• All-Source Analyst
• Mission Assessment Specialist
• Target Developer
• Target Network Analyst
• Multi-Disciplined Language Analyst
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
15
NICE Framework Work Role Examples
Cyber Defense Incident Responder
PR-CIR-001 (OPM Code 531)
Investigates, analyzes, and responds to cyber incidents within the network environment or enclave.
Information Systems Security Manager
OV-MGT-001 (OPM Code 722)

Cyber Defense Forensics Analyst
IN-FOR-002 (OPM Code 212)
Responsible for the cybersecurity of a program, organization, system, or enclave. Analyzes digital evidence and investigates computer security incidents to derive useful information in support of system/network vulnerability mitigation.

Example Tasks (ISSM)
T0157 Oversee the information security training and awareness program.
T0213 Provide technical documents, incident reports, findings from computer examinations, summaries, and other situational awareness information to higher headquarters.
T0215 Recognize a possible security violation and take appropriate action to report the incident, as required.
T0219 Recommend resource allocations required to securely operate and maintain an organization’s cybersecurity requirements.
T0254 Oversee policy standards and implementation strategies to ensure procedures and guidelines comply with cybersecurity policies.
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
• 17 Tasks • 40 Knowledge/Skill/Ability • 53 Tasks • 59 Knowledge/Skill/Ability • 39 Tasks • 70 Knowledge/Skill/Ability
16
NICE Framework Work Roles: Complete List


USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
17
Example Use: Using Work Roles in Hiring
Do we have the right people on our cybersecurity team?
Solution: Conduct a workforce assessment using the NICE Framework
• Determine needed Work Roles



• Assess current cybersecurity staff in needed Competency areas
• Identify gaps and provide requisite training
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
18
Example Use: Using Work Roles in Hiring
How can we be sure to hire the right candidate?
Solution: Use the NICE Framework to…
• Identify Competencies & Work Roles the new hire will be responsible for
• Use language from the NICE Framework in your job description


• Assess candidates for needed knowledge and skills

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
19
Example Use: Using Work Roles in Hiring
I’m looking to shift to a new cybersecurity role in my organization but want to make sure I’m prepared.
Solution: Upskill and reskill with the NICE
Framework


• Use related Work Roles in career pathing
• Clearly communicate organizational needs
• Identify areas of strength and weakness – and then focus on areas that need work

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
20
Getting Ready to Hire
• What NICE Framework cybersecurity Work Roles will the position be responsible for?

• Will this position be responsible for all the Tasks under a Work Role? Are there some missing? Are any shared across a team? Do any need to be adjusted to meet organizational needs?
• Which of the identified tasks will be needed on day one, and which can be learned on the job?
• What academic degrees, industry-recognized certifications, work experience, or other credentials (if any) are required or preferred to evidence sufficient qualifications for the position?

• How will you assess capabilities during the interview process?
• Will you offer support to candidates who meet minimum qualifications but may need additional development?
• Draft the job description using Work Roles and TKS statements, and referencing tools that map Work Roles to common job titles
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
21
Discussion: Example Job Description
• IT Cybersecurity Specialist Typical work assignments include:
• Ensures that the implemented security safeguards are adequate to assure the integrity, availability and confidentiality of the information being processed, transmitted or stored consistent with the level of sensitivity of that information.
• Plans the work to be accomplished by subordinate civilian and contractor; sets and adjust short-term priorities, and prepare schedules for completion of work; assigns work to subordinates based on priorities, selective consideration of the difficulty, requirements of assignments, and the capabilities of employees

• Perform real-time cyber defense incident handling (e.g., forensic collections, intrusion correlation and tracking, threat analysis, and direct system remediation) tasks to support deployable Incident Response Teams.
• Analyzes policy and recommends improvements.
• Serves as an expert consultant evaluation for functional teams, to assist them in anticipating, identifying, evaluating, mitigating and minimizing risks associated with IT systems vulnerabilities.
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
22
Workforce Framework Competency Areas

Competency Area: A cluster of related Knowledge and Skill statements that correlates with one’s capability to perform Tasks in a particular domain.

Competency Areas may:
• Be additive to one or more Work Roles
• Span multiple Work Roles
• Represent emerging domains
Consist of: Title
Description
TKS statements

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
•
•
2nd Draft NISTIR 8355 NICE Framework Competencies: Assessing Learners for Cybersecurity Work https://doi.org/10.6028/NIST.IR.8355draft2 Compete ncies Stakehold ers 23
Using Competency Areas: Examples
• Overlaid on Work Role(s):A position responsible for one or more Work Roles may need the Competency with or across those roles (e.g., Cloud Security)

• Common Ground:When needed to be effective in a specific sector or domain, or for non-cybersecurity staff who need cybersecurity expertise to mitigate risks (e.g.,AI cybersecurity)
• Learning: For students, job-seekers, or employees, serve as a starting place for learning or a way to develop higher-level expertise in an area (e.g., Digital Forensics)
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
24
Example NICE Framework Competency Areas (Subset)
Access Controls
This Competency describes a learner’s capabilities to define, manage, and monitor the roles and secure access privileges of who is authorized to access protected data and resources.
AI Cybersecurity
Asset Management
This Competency describes a learner’s capabilities to utilize artificial intelligence to improve cybersecurity.
This Competency describes a learner’s capabilities to conduct and maintain an accurate inventory of all digital assets, to include identifying, developing, operating, maintaining, upgrading, and disposing of assets.
Cloud Security
This Competency describes a learner's capabilities to protect cloud data, applications, and infrastructure from threats.
Cybersecurity
Fundamentals
This Competency describes a learner’s capabilities to understand and demonstrate the fundamentals of cybersecurity, including risk management; privacy principles; policy, law, and ethics; networking and systems; etc.
Data Security
This Competency describes a learner’s capabilities to protect data and information systems by ensuring their confidentiality, integrity, and availability.
OT Cybersecurity
This Competency describes a learner’s capabilities to improve and maintain the security of Operational Technology (OT) systems while addressing their unique performance, reliability, and safety requirements.

Supply Chain Cybersecurity
This Competency describes a learner’s capabilities related to the process of analyzing and controlling digital and physical risks presented by technology products or services purchased from parties outside your organization.
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
25
Using the Framework to Form Teams


USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
26
Curriculum Development


Using the NICE Framework for Educators, Learners, and Employers
Randy Pestana, Florida International University
rpestana@fiu.edu

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY 27
2/15/2023
Presentation Overview
• Three Primary Users of the NICE Framework
–
Educators
Learners –
–
Employers
• Workforce Pathways
–

Work-Based Learning Approaches
• Apprenticeships
• Internships
• Co-Op Programs
• Fellowships
• Certifications and Badges
• Proficiencies and Competencies
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
28
What Educators Need to Ask Themselves
• What cybersecurity curriculum and faculty currently exist at my institution?

• What are the workforce demands of my government?
• What are the workforce demands of my local industry?
• What are the workforce demands of industry at large?
• Do you have institutional leadership buy-in?
• What is the process for bringing in new/adjunct faculty?
• How long should my pathway be?
• Comprehensive Records vs.Transcripts

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
29
Accessing the NICE Framework


• Visit www.NICCS.CISA.gov and select on “workforce development” where you will find NICE Framework Search Tool
• Click on “categories” that best align to the curriculum you are seeking to develop
Once there, you will see the different “specialty areas” that should be built into your educational pathway
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
•
30
NICE Framework Function for Educators
• Each specialty area will open with a series of “work roles” that have respective “abilities, knowledge, skills, and tasks”
– Each course developed under your larger curriculum should utilize the “knowledge” section
When building hands-on activities and supplemental learning, you want to focus in on the “skills” and “abilities” section –
–

When maintaining an eye on marketplace requirements and advising learning, focus on the “tasks” section

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
31
Lower Division Requirements vs. Upper Division Requirements
Lower Division
• Foundational information you want learners to have:
Upper Division
• Targeted Workforce Pathways
– Work Roles 1, 2, 3 …
• Incorporate Hands-On Experience
–
Foundations course –
Soft-skills development
• Certification Training
– Workforce tracks
–
–
Programming basics
–
–
Mathematics
–

Policy
Interdisciplinary coursework
Electives
• Computer Science
• Electrical Engineering
• Information Technology
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
32
Building Course Syllabus
• Course Content
• Key Learning Objectives

–
What are the framework knowledge units this course is aimed at teaching?
• Tools and Techniques
– Splunk? Python? Kali Linux?
• Work Roles Target
• Competencies Gained
–
What are the framework skills/abilities built into this course?

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
33
What to do with all this information?
College Transcripts
• Transcripts primarily outlines:
– Degrees Earned
–
Accredited Certificates
Earned – Courses Taken [and when]
– Grades Achieved
Comprehensive Records
• Frequently referred to as “Comprehensive Learner Record”
• Expands on transcripts to include key learning objectives of every course
• Can also incorporate digital badges and micro-credentials
–

Prior Institution Information
• More valuable to employers to learners than transcripts
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
34
Questions

• Consider what your institution needs?
• If you are an educator, have you done an internal analysis of your existing programming and resources?
• If you are an employer, what partnerships with institutions of higher education to recruit and retain talent?

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
35
Value for Learners
• Comprehensive Records,Transcripts, and/or digital passports are supplementary to technical resumes.
• Framework serves as resume building support:
Relevant Courses Taken –
–

Knowledge, Skills,Abilities Learned –

Tasks for prior work experience –
Universal language
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
36
Value for Employers

• Alignment to cybersecurity work roles ensures universal language between educators, employers, and learners
• Supports HR personnel [often not aligned with hiring managers] in seeking cybersecurity talent

• Ensures tasks language is accurate to specific role
• Avoids the “unicorn” problem
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
37
Value of Strategic Partnerships
For Educators/Learners
• Alignment of curriculum to industry needs
• Pathway for learners into industry
• Access to industry experts that can teach or present at functions
• Partner in pursuit of research dollars
For Employers
• Access to talent
–
Work-based learning approach
• Shared research and development
– Grant and foundation dollars
– Technology development
–

Academically rigorous reports
• Increased brand awareness
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
38
Work-Based Learning Approaches


Not All Certifications Are Created Equal

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
39
Apprenticeships

• Requires Academic Enrollment: No
• Average length: 12-24 months
• New Hire Conversion Rate: 91%
• Retention Rate after 1 year: 91% • Talent Acquisition Costs: Medium to High • Federal Training and Wage Offsets: Yes
• Require Mentorship: Highly Recommended

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
40
Internships


• Requires Academic Enrollment: Yes
• Average length: 3 months
• New Hire Conversion Rate: 46% •
Retention Rate after 1 year: 70% •
Talent Acquisition Costs: Low to Medium
• Federal Training and Wage Offsets: No
• Require Mentorship: Not Often
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
41
Co-Op Programs


• Requires Academic Enrollment: Yes
• Average length: 6 months
• New Hire Conversion Rate: 28%
• Retention Rate after 1 year: 47%
• Talent Acquisition Costs: Medium to High
• Federal Training and Wage Offsets: No
• Require Mentorship: Sometimes
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
42
Fellowships
• Closed Ecosystem
• Often sponsored by specific organizations, institutions, or governments
• Typically has four components:
–
Academics –
Research/Hands-On Training
Mentorship –

–
Professional Development

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
43
Certifications

• Think about what type of certifications do you want to get
–
Do you want an industry recognized credential?
• i.e., SANS, CompTIA, EC Council
–
Do you want a platform/tool specific certification?
• i.e.,AWS,Azure, Lynix
–
Can this be built into existing curriculum?
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
44
Badges and Micro-credentials
• Badges are made up of “micro-credentials” that verify the achievement of specific skills.
• These are intended to be shorter and more affordable [often free] way of gaining knowledge and skills.
• Value of credentials depends on the key learning objectives and assessment requirements that are built into the microcredentials
• Industry/Government aligned badges more valuable than “in the wild” certifications


USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
45
Verticals vs. Horizontals
Cybersecurity
Academic Degree Programs
• Computer Science

• Information Technology
• Electrical Engineering
• Information Systems Management
• Cybersecurity Policy and Law
• Hospitality Management
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
Analytical Thinking
46
Hygiene Interpersonal Communication Financial Literacy
Effective Writing
Measuring Cybersecurity Workforce Capabilities: Defining a Proficiency Scale for the NICE Framework
Key Characteristics of Workplace Proficiency
Scales
• Demonstrative: How capability is evidenced
• Supervision:Amount and type for the level
Recommendations
1. Establish a workplace-focused NICE Framework
proficiency scale to be applied to Competency Areas and Work Roles

• Professional Skills: Soft skills, employability skills… https://www.nist.gov/system/files/documents/2022/08/03/NIST%20Measuring%20Cybersecurity%20Wo
2. Encourage the NICE Modernize Talent Management
Working Group to establish a Project Team for NICE
Strategic Plan Goal #3:Align qualification requirements according to proficiency levels
3. Engage stakeholders and subject matter experts to develop statements of proficiency to apply to NICE Framework

USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
rkforce%20Capabilities%207-25-22.pdf
47
DEMOONLY








USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY 5 4 3 1 NF Content & Tools Framework DocumentSupplement al MaterialUpdatesTools Users Group LearnShareDiscussInfluence Success Stories ProfileDriversProcessBenefits & Impact Resources by Stakeholde r EmployersEducation & Training ProvidersLearners 2 Framework in Focus Practitioner ProfileCareer PathAdvice NICE Framework Resource Center www.NIST.gov/NICE/Framework 6 About FAQsHistoryAudienceRevision Process 48
Example NICE Framework Tools & Implementations


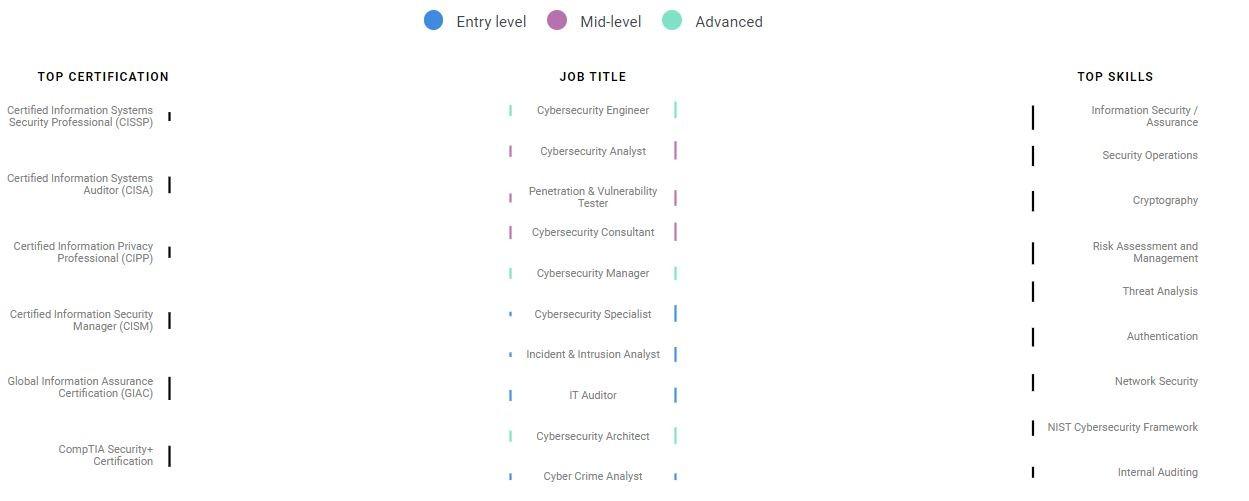
CyberSeek Jobs Map & Pathways



NICE Challenge
NICCS Career Pathways


MilGears







NICE Framework Search
Job Mapping
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
49
NICE Framework
• Updated Knowledge and Skill Statements

• Competency Areas: – NISTIR Report
– List –

Authoring Guide
• OT Cybersecurity Work Role
• Work Role Categories and Work Role names/descriptions
• New Staff
USAID CYBERSECURITY FOR CRITICAL INFRASTRUCTURE IN UKRAINE ACTIVITY
50









 Karen A.Wetzel Manager of the NICE Framework, NICE karen.wetzel@nist.gov
Karen A.Wetzel Manager of the NICE Framework, NICE karen.wetzel@nist.gov






















































































