
4 minute read
Easy-To-Use Tool Helps Dental Practices Complete HIPAA-Required Analysis
One of the essential elements to HIPAA compliance is the completion of an enterprisewide risk analysis. A risk analysis generally is comprised of three parts:
■ A compliance assessment — Is a covered entity in compliance with every element of the HIPAA privacy and security rules?
Advertisement
■ A technical assessment — Does a covered entity have the technology necessary to comply with the technical implementation specifications, or safeguards, of the HIPAA security rule? CDA Practice Support
■ A risk assessment — How well is a covered entity prepared to manage the threats and vulnerabilities to the systems that store and communicate protected health information?
The risks of not conducting a risk analysis can be severe for small-sized health care providers. On March 3, 2020, the Office for Civil Rights (OCR) announced it had reached a settlement with a medical practice that provides services to over 3,000 patients. OCR found that the practice never conducted a risk analysis and failed to implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level. The practice agreed to pay $100,000 and to implement a corrective action plan that includes two years of monitoring. 1
Conducting a thorough risk analysis, especially the risk assessment, is a timeconsuming task for a small health care provider. Fortunately, the Office of the National Coordinator for Health Information Technology (ONC) provides a free security risk assessment tool created specifically to assist small businesses. 2 ONC recognizes that smaller health care entities face greater challenges in meeting information security standards because of limited resources. The Security Risk Assessment Tool organizes information entered into it and produces reports. The tool can be as useful as the work put into it, much like the usefulness of a business plan to the development of a dental practice. The process forces the user to consider questions it may not have considered before. However, the tool may not account for newer or previously unrecognized risks and vulnerabilities, for example, social media use, and the user should be careful to include these newer risks while entering information into the tool.
The information a user enters into the tool is saved on the device of the user’s choosing and is not transferred to or collected by ONC or the Department of Health and Human Services. The user can stop entering information at any point, save the information and continue the process another day. The tool allows an individual to include an inventory of assets that hold PHI and a list of vendors that use PHI. With asset tracking, the tool allows an individual to note each asset’s encryption level, type of information held or used, location, assignment (individual or purpose), internal identifier and disposal status. Vendor tracking includes vendor contact information, purpose for the vendor’s use of PHI and whether vendor has provided assurances of performing its own risk analysis.
An individual also may upload to the tool other documents that are relevant to the risk assessment, for example, a plan prepared by an IT consultant to address vulnerabilities in the covered entity’s information systems or a document describing an implemented alternative to an addressable security rule safeguard.
The risk assessment tool has seven sections of multiple-choice questions (FIGURE 1 ). It uses branching logic, which means the questions posed depend on responses to previously asked questions. Vulnerability selection and threat rating is presented after each section (FIGURE 2).
FIGURE 1 Assessment Content
Content within the assessment is broken down into these main categories:
Section 1: Security Risk Assessment (SRA) Basics (security management process)
Section 2: Security Policies, Procedures and Documentation (defining policies and procedures)
Section 3: Security and Your Workforce (defining/managing access to systems and workforce training)
Section 4: Security and Your Data (technical security procedures)
Section 5: Security and Your Practice (physical security procedures)
Section 6: Security and Your Vendors (business associate agreements and vendor access to PHI)
Section 7: Contingency Planning (backups and data recovery plans)

FIGURE 2. One of the assessment screens on the ONC Security Risk Assessment Tool.
A risk report is generated after all sections are completed (FIGURE 3). The report provides a risk score, details the areas that need review and identifies vulnerabilities along with associated threats. A detailed report, which includes all the information entered into the tool except for uploaded files, can be viewed as well as saved as a PDF or Excel document.
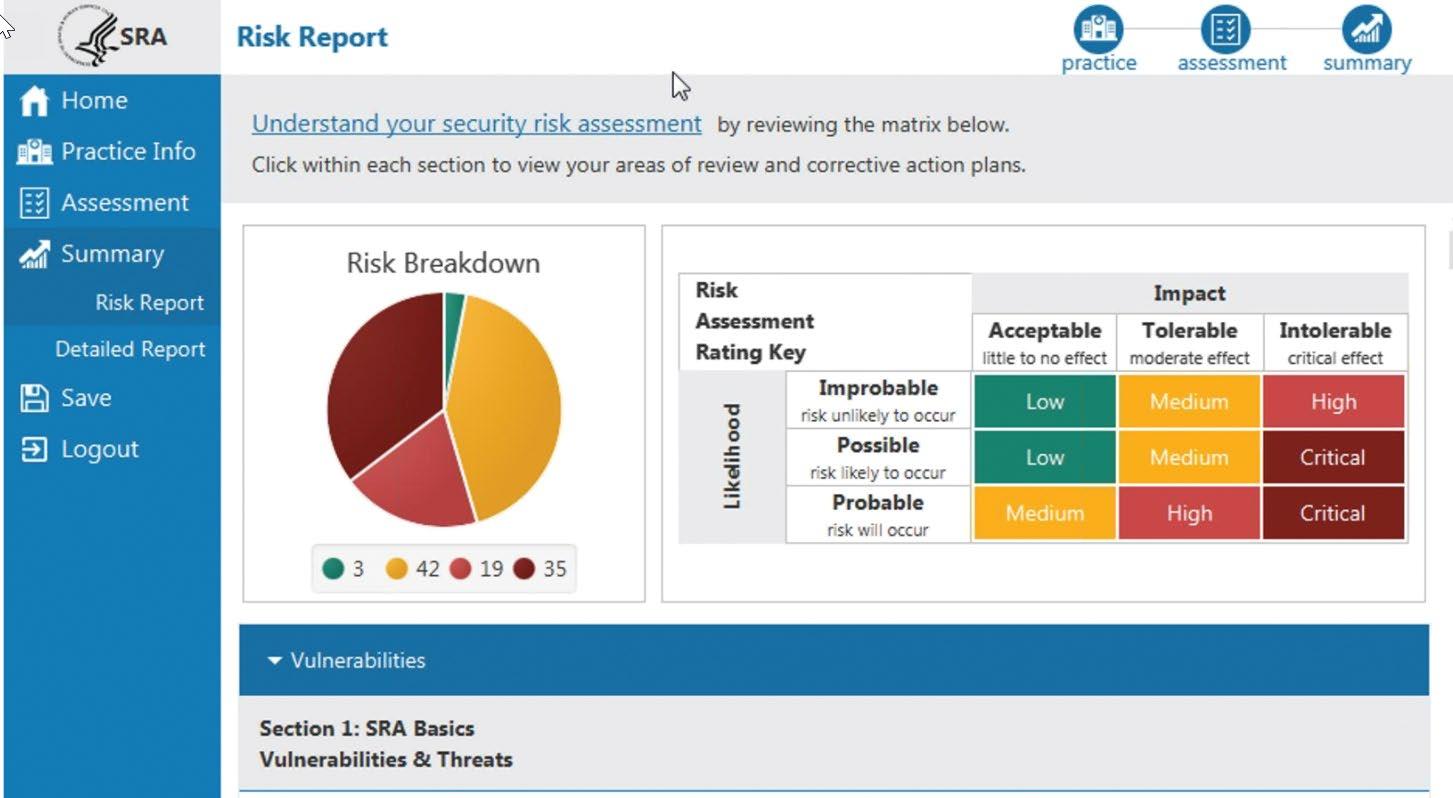
FIGURE 3. Part of a summary risk report produced by the ONC Security Risk Assessment Tool.
The current version of the tool is only available for Windows operating systems. However, any dental practice using iPads may still download the previous version from the Apple App Store or the HealthIT.gov website. A PDF copy of the paper version of the older tool and a video recording of a training session can be found on the HealthIT.gov website.
REFERENCES
1. U.S. Department of Health and Human Services. Health care provider pays $100,000 settlement to OCR for failing to implement HIPAA security rule requirements. www.hhs.gov/ hipaa/for-professionals/compliance-enforcement/agreements/ porter/index.html.
2. HealthIT.gov. Security Risk Assessment Tool. www.healthit.gov/ topic/privacy-security-and-hipaa/security-risk-assessment-tool.
Regulatory Compliance appears monthly and features resources about laws that impact dental practices. Visit cda.org/ practicesupport for more than 600 practice support resources, including practice management, employment practices, dental benefit plans and regulatory compliance.







