Shaping the Future of Digital Safety, 2025



Shaping the Future of Digital Safety, 2025






Intoday’sincreasinglydigitizedworld,
wheredataiskingandinnovationreigns supreme,theroleofcybersecurityleadersis evolvingatbreakneckspeed.Theystandasboth gatekeepersandvisionaries,taskedwith defendingdigitalinfrastructureswhilepioneering strategiestostayaheadofever-evolvingthreats.
CIOBusinessWorldrecognizestheindispensable leadershiptheseprofessionalsbringtomodern enterprises,astheynavigatealandscapefraught withcomplexity,innovation,andrisk.
TheNewCornerstoneofBusinessStrategy
Gonearethedayswhencybersecuritywas relegatedtothebackoffice,anecessarybutlowprofilefunctionofIT.Today,cybersecurity leadersareattheboardroomtable,shaping policiesthatdrivetrustandresilience.Whether it’ssafeguardingcustomerdata,mitigating supplychainvulnerabilities,orprotecting intellectualproperty,theirinputisnowacritical componentofbroaderbusinessstrategies.

Theriseoftechnologiessuchasblockchain, artificialintelligence(AI),andtheInternetof Things(IoT)hasamplifiedthecomplexityof securingdigitalecosystems.Theglobalecommercesurge,forinstance,highlightshow evenseeminglyimpregnablesystemslike NFTs—digitaltokenslaudedfortheir security—arevulnerable,asevidencedbythe piratingofMetaBirkinNFTs.Cybersecurity
leadersmustnotonlycountersuchincidentsbutalsoanticipatenovelattack vectors,oftenoperatingastheorganization’schiefriskofficers.
Cyberthreatsarenolongerconfinedtotraditionalhackingmethods.The spectrumhasexpandedtoincluderansomware,databreaches,andAIdrivenattacksthatexploitautomationandscale.Thisescalationdemands thatcybersecurityleadersbeasadaptiveastheiradversaries.Thefigures speakvolumes:over230millionU.S.consumersengageinonline transactions【8†source】,highlightinghowevenminorbreachescanhave exponentialrepercussions.

Moreover,theintegrationof cybersecurityintodaily operationshasaddedlayersof accountability.Beyond technology,cybersecurity leadersmustaddresshuman factors—trainingemployees, fosteringacultureofvigilance, andmanaginginsiderthreats. Thisbalancebetweentechnical acumenandpeople managementdistinguishes successfulleadersinthis domain.
Inafielddefinedbyitsfluidity,cybersecurity leadersmustembodytheveryessenceof innovation.Theyareincreasinglyrequiredto adoptaproactiveapproach,employing predictiveanalyticsandthreatintelligenceto preemptbreaches.Collaborationisalso pivotal—beitsharingintelligencewithin industryconsortiumsorworkingwithpublicsectoragenciestoensurerobustlegislative frameworks.
Thecallfortransparencyandpublictrust cannotbeoverstated.Justascustomers demandtraceabilityinsupplychains,they nowseekreassurancesabouthowtheirdatais managedandsecured.Leaderswhoprioritize thistransparencyarenotonlyfortifyingtheir defensesbutalsoenhancingtheirbrand’s reputationinahighlycompetitivemarket.
Thedigitaleraisbothanopportunityanda challengeforcybersecurityleaders.They mustleveragetheirexpertisetocraft resilientsystemswhilefostering environmentsoftrustandinnovation.As CIOBusinessWorldobserves,thefuture belongstoleaderswhocanmergetheir technicalprowesswithstrategic foresight—thosewhoseecybersecuritynot merelyasalineofdefensebutasalinchpin oforganizationalsuccess.
InthewordsofaseasonedCIO, “Cybersecurityisn’tjustaboutsecuring assets;it’saboutsecuringfutures.”As threatsbecomemoresophisticated,somust theguardiansatthehelm.Thehorizonmay becomplex,butwithvisionaryleaders steeringthecourse,businessescannavigate itwithconfidenceandresilience.




Intherapidlyevolvingdomainofcybersecurity,the journeyofMaheshKGuptaservesasacompelling narrativeofvision,adaptability,andleadership.An esteemedcybersecurityleader,Mahesh'spathisa testamenttoperseveranceandthepursuitof innovation.Withacareerspanningovertwodecades, hehascarvedanicheforhimselfthroughhis strategicforesight,hands-ontechnicalexpertise,and passionformentoringthenextgenerationof cyberprofessionals.
AJourneyRootedinVersatilityandPerseverance
Mahesh'sacademicjourneybeganatBITSPilani,wherehe pursuedElectronicsandCommunicationEngineering. Duringhisstudies,theburgeoningfieldofITemergedasa promisingcareeravenue.Drivenbycuriosityandambition, MaheshjoinedIBMSoftwareLabs,embarkingona journeythatwouldlaythefoundationforhisfuturein cybersecurity
Intheearlydays,Mahesh'sfocusonprotocolslike KerberosandhiscontributionstotheWindowsbackup moduleforfilesystemswerepivotal,thoughheinitially remainedunawareofthecybersecurityimplicationsofhis work.HistenureatIBMfurtherexpandedhisexpertise,as hedelvedintotheLDAPDirectoryServer,nowa cornerstoneofIBMSecurity.
Post-MBAfromIIMAhmedabadandanexchangeprogram atESSEC,Paris,MaheshtransitionedtoAdobeasaglobal productmanager.HistenureatAdobe,followedbya decadeatSymantec,wastransformative,allowinghimto mergebusinessacumenwithtechnicaldepth.Here,Mahesh
spearheadedmultipleproductlines,honinghisskillsin businessmanagement,globalproductleadership,and cybersecurity.
TheconfluenceofSymantec'sacquisitionbyBroadcomand theonsetoftheCOVID-19pandemicmarkedacritical junctureinMahesh'scareer.Facedwithuncertainty,he seizedtheopportunitytopivot.Embracinganewchallenge, hetransitionedtocybersecuritygovernanceand compliance,addressingtheuniquechallengesposedbyIT andOperationalTechnology(OT)inAustralia'scritical infrastructure.ThisperiodalsosawMaheshcontributeasa part-timeeducatoratRMIT,nurturingfutureprofessionals inproductmanagementandcybersecurity.
Cybersecurity,asMaheshaptlydescribes,isanextensionof humanity'sinnateneedforsecurity,asarticulatedin Maslow'shierarchyofneeds.Intoday'sinterconnected world,safeguardingone'sidentityandassetsdemands robustanswerstothreefundamentalquestions:


• SomethingIknow(passwordsor PINs)
• SomethingIhave(mobile devicesorsecuritytokens)
• SomethingIam(biometrictraits suchasfingerprintsorfacial recognition)
Maheshhighlightstheevolutionof cybersecurityfromsimplepassword authenticationtomulti-factor authentication(MFA),incorporating elementslikeOTPs,securitycodes, andCAPTCHAchallenges.Thisshift isaresponsetothegrowing sophisticationofcyberthreats, includingphishingandransomware. Therisingawarenessofthesethreats hasdrivenindividualsand organizationstoadoptadvanced securitymeasures,underliningthe criticalroleofvigilanceinaneverchangingthreatlandscape.
Asaleader,Maheshemphasizes collaboration,clarityofpurpose,and empowerment.DrawingonhisMBA experience,heunderscoresthe importanceofaligningindividualand organizationalgoalsthrough transparentcommunication.By explainingthe"why"behindevery initiative,Maheshensuresthat stakeholdersremainengagedand alignedwiththebroaderbusiness objectives.
Hisleadershipphilosophycenterson fosteringacultureofinnovationand accountability.Maheshbelievesthat equippingleaderstoviewchallenges frommultipleperspectivesisessential intoday'scomplexwork environment.Thisapproachnotonly preemptivelyaddressespotential obstaclesbutalsoencourages
creativityandcollaborationamong teammembers.
Mahesh'scommitmenttoempowering histeamhascultivatedan environmentwhereindividualsfeel valuedandinvestedinsharedsuccess. Thiscultureoftrustandinclusivity hasledtohighermorale,improved performance,andstrongeralignment withtheorganization'svision.
ForMahesh,innovationisthe cornerstoneofeffectivecybersecurity. Helikensthefieldtoagameofchess, wheredefensivestrategiesmust accountforknownandunknown tacticsemployedbyadversaries.This proactiveapproachisrootedingame theory,emphasizingtheneedfor forward-thinkingsolutionsto counteractemergingvulnerabilities.
Mahesh'sdevelopmentoftheworld's firstcloudstoragesecurityservice underscoreshiscommitmentto pioneeringsolutions.Atatimewhen fewerthan10%ofsurveyed customersrecognizedtheneedfor suchaservice,Maheshpersistedin addressingthisblueocean opportunity.Today,cloudstorage securityisuniversallyacknowledged asacriticalcomponentof cybersecurity,validatinghisvision andperseverance.
LeveragingAIandMLfor AdvancedOfferings
Intheageofartificialintelligence (AI)andmachinelearning(ML), Maheshrecognizesthetransformative potentialofthesetechnologiesin cybersecurity.However,he emphasizestheimportanceof judiciousimplementation.
Inthecompetitivefieldof cybersecurity,differentiationis keytostayingaheadofthe curve.Maheshadvocatesfor innovationthroughtheblue oceanstrategy—venturinginto unexploredmarketsratherthan competinginsaturatedones.
OneofMahesh'smost significantachievementswasthe creationandlaunchofthe world'sfirstcloudstorage securityserviceduringhistime atSymantec.Despiteinitial skepticismfromcustomersanda lackofdirectcompetition, Maheshhadtheforesightto recognizethegrowing intersectionofcloudstorageand securityneeds.Hisabilityto anticipatetrendsandinvestin future-readysolutions exemplifieshisstrategic acumen.
Maheshacknowledgesthat stayingaheadofthecurve requirescalculatedrisksanda proactiveapproachto innovation.Whilechallenging, thismindsetisessentialfor organizationsaimingtoleadin anindustrymarkedbyrapid technologicaladvancementsand evolvingthreats.

• Overthepastdecade,Mahesh hasincorporatedAIandMLinto hisproducts,leveragingthese technologiesfordataanalysis, behavioralanalytics,andthreat detection.Byidentifyingpatterns andissuingalertsforpotential attacks,AIandMLhave enhancedtheeffectivenessof cybersecuritymeasures.
Maheshcautionsagainstover-reliance onAI,notingthatattackersalso leveragethesetechnologiestocreate sophisticatedthreats.Tostayahead, defensemechanismsmustincorporate continuouslearning,explainableAI models,andethicalAIpractices. Collaborationbetweenhuman expertiseandAIwillbepivotalin
navigatingtheevolvinglandscapeof cybersecurity.
Maheshenvisionsafuturewhere cybersecuritybecomesasintegralto societyasphysicalandmentalhealth. Heemphasizestheneedfora proactiveapproachtodigitalhealth, advocatingforwidespreadadoption ofcybersecuritybestpracticesatboth individualandorganizationallevels.
Drawingparallelsbetweendigital resilienceandpublichealth,Mahesh aspirestocontributetoacyber-secure ecosystemthatenhanceseconomic productivityandnationalwell-being.
Hisdiverseexperienceasadeveloper, productmanager,educator,and compliancespecialistequipshimto addressthemultifacetedchallengesof cybersecurity
Maheshisalsopassionateabout inspiringthenextgenerationof cybersecurityprofessionals.By sharinghisknowledgeandmentoring aspiringleaders,hehopestofostera cultureofinnovationandvigilance thatwillshapethefutureofthe industry
Giventheopportunity,Maheshwould advocateforgreateremphasison


" I aspire to guide and inspire the younger generation to consider cybersecurity as a viable career path..”
• digitalhealthasasocietal priority.Hebelievesthat cybersecurityshouldbewoven intothefabricofbusinessesand treatedasasharedresponsibility ratherthananafterthought.
Whileadvancedtoolsarecrucial, Maheshunderscorestheimportance ofuserawarenessasthefirstlineof defense.Educatingindividualsabout recognizingphishingattempts, securingdevices,andupdating softwareisfundamentaltobuildinga resilientdigitalsociety
HarnessingTechnologyfor ResourcefulSolutions
Astechnologycontinuestoevolve,
Maheshremainsattheforefrontof integratinginnovativesolutionsinto cybersecurity.Behavioralanalytics, zero-trustframeworks,andAIpoweredthreatdetectionsystemsare shapingthefutureofthefield, offeringnewopportunitiesto strengthendigitaldefenses.
Maheshviewstechnological advancementsasbothachallengeand anopportunity.Bydiagnosingthreats withprecision,organizationscan harnessthepotentialofdisruptive innovationstodriveprogressand improvelives.
MaheshKGupta'sjourneyin cybersecurityisaremarkableblendof technicalexpertise,strategic
foresight,andunwavering commitmenttoexcellence.Hisability toanticipatetrends,foster collaboration,anddriveinnovation haspositionedhimasatrailblazerin theindustry
Throughhisleadership,Mahesh continuestopushtheboundariesof whatispossibleincybersecurity, inspiringotherstoembracea proactive,inclusive,andforwardthinkingapproach.Asthedigital landscapeevolves,hisvisionfora secureandresilientfutureremainsa guidinglightfortheindustry




Intoday’sinterconnectedworld,cybersecurityis morethanjustatechnicalnecessity—itisacritical pillarofglobalstability.Asthedigitalrealm expandstoincludeeveryaspectofmodernlife,from bankingandhealthcaretocriticalinfrastructureand nationalsecurity,safeguardingithasbecomeanurgent priority Thefutureofdigitalsafetydependson strategicdecisionsmadebythoseattheforefrontof cybersecurity Thesechoicesinfluencehowtheworld respondstoevolvingthreats,developsnew technologies,andestablishesethicalframeworksforthe digitalage.
Thedigitalecosystemhasgrownrapidly,butsohave theassociatedrisks.Maliciousactorsexploit
vulnerabilitiesacrosssystems,leadingtoransomware attacks,databreaches,anddisruptionstoessential services.Inresponse,cybersecurityleadersfacearange ofchoicesthatwilldeterminehoweffectivelythese threatscanbemitigated.Theirdecisionsareshapingthe futureofhowgovernments,industries,andindividuals protectthedigitalrealm.
ChoicesinCybersecurity
Public-PrivatePartnerships:Collaboratingacross sectorsisessentialforsharingthreatintelligence, resources,andbestpractices.Organizationsneedto workwithgovernmentstobuildunifieddefenses againstcyberthreats.


GlobalCooperation:Cyberattacksknownoborders, andinternationalcollaborationisvital.Countriesface thechoiceofworkingtogethertocreateframeworksfor informationsharingoroperatingindependently,risking fragmenteddefenses.
AnticipatingThreats:Organizationsmustdecide whethertoinvestheavilyinpredictiveanalyticsand threatmodellingorcontinuerelyingonreactive measures.Proactivestrategiesofteninvolveleveraging artificialintelligence(AI)andmachinelearning(ML) todetectvulnerabilitiesbeforetheycanbeexploited.
IncidentResponse:Anotherkeychoiceishowmuch emphasistoplaceonbuildingresilientsystemsthatcan
recoverquicklyfromcyberincidents,minimizing downtimeanddataloss.
RegulatoryFrameworks:Governmentsand organizationsfacethetaskofestablishingclearand enforceablecybersecuritypolicies.Thesecouldinclude privacylaws,compliancerequirements,and accountabilitymechanisms.
BalancingPrivacyandSecurity:Strikingtheright balancebetweenprotectingpersonaldataandensuring robustsecuritymeasuresisacomplexdecision. Misstepsineitherdirectioncouldresultinpublic distrustorweakeneddefenses.

Cybersecuritydecisionsincreasingly involveleveragingcutting-edge technologies.TheintegrationofAI andMLintocybersecuritysystems hasproventransformative,enabling automatedthreatdetectionandfaster responses.However,thisshiftalso raisesquestionsaboutreliabilityand ethicaluse.
CloudSecurity:Asorganizations migratetocloud-based infrastructures,securingthese platformsisapriority.Choices aroundencryptionstandards,access controls,andmulti-factor authenticationareshapingthefuture ofcloudsecurity
QuantumComputing:Whilethis technologyoffersimmensepotential, italsopresentsanewthreatto traditionalencryptionmethods. Organizationsmustdecidehowto prepareforquantum-resistant cryptographicsystems.
Anotherpivotalchoiceliesin addressingthecybersecuritytalent gap.Thedemandforskilled professionalsfaroutpacesthecurrent supply,leavingmanyorganizations vulnerable.Tobridgethisgap,there areseveralstrategicdirections:
EducationandTraining:Investingin specializedprogramsand certificationstoequipindividuals withtheskillsneededtomanage emergingthreats.
DiversityinCybersecurity: Encouragingunderrepresentedgroups topursuecareersincybersecurityis critical.Adiverseworkforcebrings variedperspectives,whichare
essentialfortacklingcomplex problems.
MentorshipandKnowledgeSharing: Organizationsmustchoosetofoster mentorshipprogramsthatensurethe transferofexpertisetothenext generationofcybersecurityleaders.
Ascybersecuritypracticesevolve, ethicalconsiderationsarebecoming moreprominent.Decisionsinthis areahavelong-termimplicationsfor trustandaccountabilityinthedigital realm.
Surveillancevs.Privacy:The deploymentofsurveillance technologiestoenhancesecurityoften raisesprivacyconcerns.Balancing thesecompetingprioritiesisacritical choiceforpolicymakersand organizationsalike.
OffensiveCyberCapabilities:Nations andorganizationsfacetheethical dilemmaofwhethertodevelop offensivecybersecuritytools,suchas malware,fordefensivepurposes.The potentialconsequencesofsuch decisionsrequirecarefuldeliberation.
AIinCybersecurity:WhileAIoffers significantadvantages,italsopresents risks.EnsuringthatAI-drivensystems aretransparent,unbiased,andsecure isessentialformaintainingpublic trust.
Resilienceiskeytoenduringand recoveringfromcyberincidents. Leadersmustdecidehowtoprioritize resilience-buildingeffortsacross industriesandgovernments.These choicesincludeinvestinginrobust backupsystems,implementingzero-
trustarchitectures,andconducting regularsecurityaudits.
Thedecisiontoadoptazero-trust securitymodel,forinstance,reflectsa fundamentalshiftinhow organizationsapproachcybersecurity Byassumingthatnouserorsystemis inherentlytrustworthy,zero-trust modelscansignificantlyreducethe riskofinsiderthreatsandlateral movementwithinnetworks.
Thefutureofcybersecurityisnot determinedbytechnologyalonebut bythechoicesmadetoday.Whether fosteringcollaboration,investingin cutting-edgetools,ornavigating ethicalchallenges,thedecisionsof cybersecurityprofessionalsare creatingtheblueprintforasafer digitalworld.
Asthedigitallandscapecontinuesto evolve,organizationsand governmentshavearesponsibilityto actdecisivelyandresponsibly The choicestheymakenowwill determinetheextenttowhichsociety cantrustandthriveinan interconnectedworld.Byprioritizing innovation,cooperation,andethical integrity,theycanlaythefoundation forafuturewheredigitalsafetyisnot aluxurybutaguaranteeforall.



Humanityisonthebrinkofa massiveturning point—drivenbythe convergenceofmultiplebreakthrough technologiesadvancing simultaneously.Innovationsin artificialintelligence(AI),quantum computing,robotics,automation, advancedmaterials,andmoreareno longerprogressinginisolation. Instead,theycombinetocreatea powerful“flywheeleffect”that reshapesentireindustriesandthe fabricofourdailylives.Experts
believethismomentmarksthestartof oneofthemostsignificant transformationsmoderntimeshave everwitnessed,asthesedifferent fieldssynchronizeinwaysnever beforepossible.
Thenumbersbehindthisshiftare staggering.Asdifferentindustries adopttheseadvancedtechnologies, newopportunitiesandchallengesare arising:
HealthcareandBiotech($8.5 trillionby2035)
• AI-powereddrugdiscoveryis slashingdevelopmenttimesby upto90%.
• Quantumsimulationsallow doctorstomodeldiseasesatthe molecularlevel,enabling personalizedtreatments.
• Roboticsurgeryandautomated caresystemsaimtosavean estimated50millionlivesevery yearby2035.
ManufacturingandIndustry($7.2 trillionby2035)
• FactoriesequippedwithAIdrivenroboticscanachievea 99.9%reductionindefects.
• Zero-wasteproductionandAIoptimizedsupplychainsmaycut costsbyupto70%.
• Autonomoussystemscould handleupto85%ofproduction tasks,raisingquestionsabout workerretrainingandjob redefinition.
FinancialServices($6.3trillionby 2030)
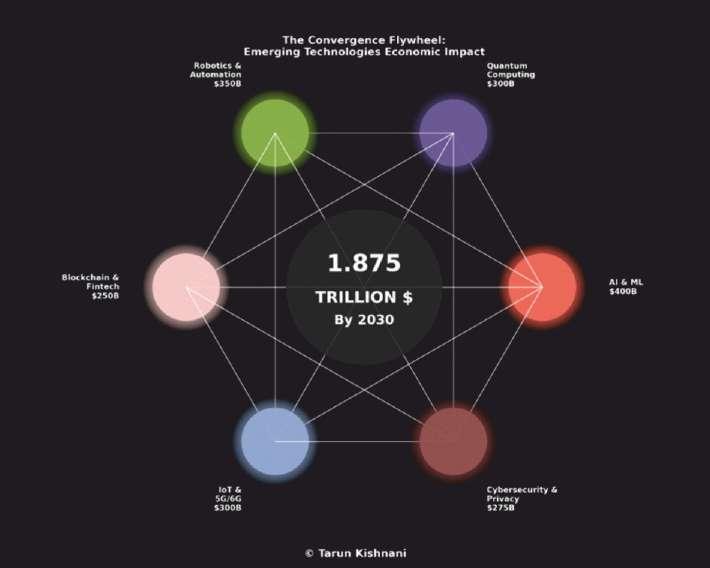
• Quantum-securedblockchainis expectedtoprotectbillionsof globaltransactionsfrom cyberattacks.
• AI-drivenmarket predictions—withhigh accuracy—promiseto revolutionizewealthmanagement.
• Real-timeglobalsettlementscan dramaticallyspeedup internationaltradewhilealso requiringadaptiveregulations.
EnergyandSustainability($5.8 trillionby2030)
• 100%renewableenergygridsare onthehorizon,steeredbyAIthat cancutwastebyupto80%.
• Quantummaterialsforenergy storagemaystabilizesolarand windpower,eveninlocationswith unpredictableweather
• Carboncapturetechnologyaims notjusttoslowclimatechangebut potentiallyreverseitsworst effects.
TransportationandLogistics($4.9 trillionby2030)
• Autonomousvehicles,flying taxis,anddeliverydronesare readytorevolutionizecommutes andshipping.
• Smarttrafficsystemscouldreduce traveltimesby75%,whilezeroemissionoptionslowerpollution.
• Updatingroads,airtraffic guidelines,andlogisticalprotocols willrequireunprecedentedlevels ofcoordination.
“TarunKishnaniisa multidisciplinaryresearcherand strategistpassionateabout connectingsustainability, technology,finance,andbiology tosolvecomplexchallenges. Knownforsynthesizingdiverse insights,headvisesglobalCEOs andcorporateboards,reframing problemsthroughaunifiedlens ofknowledge.”
Hisapproachemphasizesethical leadership,innovation,and capitalstewardship—leveraging researchtoimprovedecisionmaking,negotiations,and governance.Tarun'sfather humorouslycallshima"Jackof all,masterofnone,"alabelhe embracesasastrength,bridging gapsbetweenfieldstodrive impactfuloutcomes. Youcanfindhimon www.tarunkishnani.comand connectwithhimat www.linkedin.com/in/tarunkishn ani
Sources:
1. McKinsey&Company: The Future of AI and Automation in Business
2. WorldEconomicForum: The Future of Jobs Report 2023
3. PwC: The Economic Impact of AI by 2030
4. DeloitteInsights: Quantum Computing and Industry Transformation
5. Gartner: Top Strategic Technology Trends for 2030


Inthedigitalage,cybersecurityleaders playacriticalroleinsafeguardingthe infrastructurethatunderpinsmodern society.Fromprotectingsensitivepersonal datatodefendingcriticalsystemsagainst increasinglysophisticatedthreats,the responsibilityisimmense.Yet,thepathto securingthedigitalrealmisfraughtwith challenges.Therealitiestheseleadersface highlightthecomplexityofthetaskat hand—butwithinthesechallengeslie answersthatcanguidethewayforward.
Thecyberthreatlandscapeisdynamicandunpredictable.Attackers continuouslyrefinetheirmethods,leveragingadvancedtechnologieslike artificialintelligence(AI)andransomware-as-a-servicetotarget vulnerabilities.Theriseofstate-sponsoredcybercampaignsaddsfurther complexity,makingattributionanddefenseevenmorechallenging.
TheAnswerliesinaproactiveapproach.Investinginreal-timethreat intelligencesystems,predictiveanalytics,andinformation-sharing platformsenablesorganizationstodetectandmitigaterisksearly Collaborativeeffortsacrossindustriesandnationshelpbuildaunified frontagainstcyberthreats.
Aglobalshortageofskilledcybersecurityprofessionalsisoneofthe mostpressingissuesfororganizationstoday.Securityteamsoften struggletomanageworkloads,leavingthemvulnerabletoemerging threats.Additionally,existingprofessionalsmustconstantlyupskillto keeppacewithevolvingtechnologies.
TheSolutioninvolvesamultiprongedapproach:
• Investingineducationandtrainingprogramstogrowthetalent pool.
• Leveragingautomationtohandleroutinetasks,freeingup professionalsformorestrategicwork.
• Promotingdiversityincybersecuritytotapintounderrepresented talentandbringfreshperspectivestocomplexproblems.
• Byfosteringarobustpipelineofskilledworkersandintegrating technology,organizationscanaddressthetalentgapeffectively
Despitetherisingcostofcybercrime,manyorganizationsunderfund cybersecurityinitiatives,oftenprioritizingotherareasuntilabreach occurs.Securityleadersfacethedifficulttaskofprotectingtheir organizationswithlimitedresources.
TheAnswerliesinprioritizinginvestmentsbasedonrisk.Arisk-based approachensuresthatresourcesareallocatedtothemostcriticalareas, maximizingtheirimpact.Additionally,usingmetricslikereturnon investment(ROI)andcost-benefitanalysiscanhelpjustifycybersecurity budgets.Forfinancialprotection,cyberinsurancecanserveasavaluable safetynetintheeventofanincident.
Newtechnologies,suchasthe InternetofThings(IoT),5G,and cloudcomputing,expandattack surfacesandintroducenew vulnerabilities.Atthesametime, advanceslikequantumcomputing threatentorendercurrentencryption methodsobsolete.
ThePathForwardistoadopta security-by-designphilosophy.By embeddingsecuritymeasuresearlyin thedevelopmentlifecycle, organizationscanaddress vulnerabilitiesbeforetheybecome threats.RegularassessmentsofIoT devices,robustcloudsecurity protocols,andtheadoptionof quantum-resistantcryptographic systemsarecriticalstepstosecuring emergingtechnologies.
Theincreasingnumberofglobal regulations,suchasGDPRandthe CaliforniaConsumerPrivacyAct (CCPA),addscomplexityto cybersecurityefforts.Organizations mustnavigatetheseframeworks whilemanagingoperationalrisksand maintainingcompliance.
TheSolutioninvolvesstreamlining complianceefforts.Centralized governanceframeworksand automationtoolscanreducethe burdenofmonitoringandreporting. Additionally,fosteringacultureof cybersecurityawarenessensures employeesunderstandtheimportance ofcomplianceandtheirrolein achievingit.
Notallthreatscomefromexternal attackers.Insiderthreats,whether causedbyhumanerrorormalicious intent,posesignificantrisks. Employeesmightfallvictimto phishingattacksormisusetheir accesstosensitivesystems.
TheAnswerliesineducationand technology.Regularemployee trainingonrecognizingphishing attemptsandfollowingsecurity protocolsisessential.Azero-trust architecture,whichassumesnouser ordeviceisinherentlytrustworthy, helpslimittheimpactofinsider threats.Behaviouralanalyticstools canalsodetectunusualactivityand identifypotentialrisksbeforethey escalate.
Cybersecuritydecisionsoften intersectwithethicalconsiderations, suchasbalancingsurveillancewith privacyordisclosingvulnerabilities responsibly.Misstepsintheseareas canerodepublictrustanddamage reputations.
TheSolutionistransparencyand accountability.Clearcommunication aboutdatacollectionandusagebuilds trustwithstakeholders.Ethical oversightofsecuritypracticesensures thatmeasureslikesurveillance technologiesareimplemented responsibly.Establishing accountabilityframeworkshelps organizationsmaintainfairand ethicalpractices.
8.BuildingResilienceAgainst ConstantThreats
Eventhemostrobustdefensescannot
preventeveryattack.Resilience—the abilitytorecoverquicklyand effectivelyfromincidents—isa criticalfocusforcybersecurity leaders.
TheWayForwardinvolvespreparing fortheinevitable.Detailedand regularlytestedincidentresponse plansensureaswiftandcoordinated reactiontobreaches.Investingin redundancy,suchassecurebackups, minimizestheimpactofdisruptions. Additionally,securingsupplychains andthird-partysystemsprevents vulnerabilitiesfromexternalpartners.
Thechallengesfacedbycybersecurity leadersareimmense,buttheyarenot insurmountable.Throughproactive threatintelligence,workforce development,strategicresource allocation,andethicalleadership, theseprofessionalscancreateasafer digitallandscape.
Asthedigitalworldevolves,the choicesmadetodaywillshapethe futureofcybersecurity.Byembracing innovationandfostering collaboration,leaderscantransform theharshrealitiesofdefendingdigital safetyintoopportunitiesforlasting security.













