








owadaysmostoftheworldreliescompletelyonthe
Ncommunicationsystems.However,amongstalltheseusers, onecaneasilyassumethatonlyaround50percentiswell preparedtohandleanythreatfromcybercriminals.Thankstothe risingadoptionofcloudtechnology,itcanbeeasilyconsideredthat futurebusinesseswouldbecompletelydata-driven.So,asociety whichisseverelydependentonnetworking,mustprotectthe networksinordertofunctionproperly.However,manyofthepeople stillgetsconfusedwhenitcomestocybersecurityandnetwork security.Butthere’sabasicdifferencebetweenthesetwo.Foran exampleifoneassumesacompanyasacastle,thencyberhelpsto protectthecastlefromanyoutsidethreats,whereasthenetwork securityworkstomaintainmuchneededpeaceandharmonyinside thecastle.
Networksecurityisnothingbutasubsetofcybersecurity,thataims toprotectanydatathatisbeingsentthroughdevicesinanetworkto makesurethattheinformationisnotchangedorintercepted.The mainroleofnetworksecurityistosafeguardanorganizations’IT infrastructurefromanykindofcyberthreatsthatinclude:viruses, Denialofserviceattacks,Zerodayattacks,hackerattacks,Spyware andadware,wormsandTrojanhorses.
Normally,anetworksecurityteamimplementsthenecessary hardwareandsoftwaretoguardasecurityinfrastructure.Byplacing propernetworksecurity,asystemcandetectpotentialthreatseven beforetheyinfiltrateandcompromisevaluabledata.Ifstilla networksecuritygetscompromised,thenthefirstprioritymustbeto gettheattackersoutofthenetworkakacastle.Themoretimean attackerspendstimeinthenetwork,themoretimeitgetstosteal valuabledata.Asperarecentstudy,excludinganymegadata breaches,anyaveragedatabreachcostsaround$188per compromiseddata,duetowhichtheaveragetotalcosttoan organizationinU.Sshootsupto$5.4million.

























Theimportanceofsecurityisvitalforanybusiness,especiallywhenwetalkaboutnetworksystems.
Organizations,irrespectiveoftheirindustryofoperation,needanefficientsecuritysystemtomeettheir
goalsandobjectives.Thishasproliferatedtheimportanceanddemandofnetworkingsolutions
servicestenfold.Itisimmenselyessentialfororganizationstoboastaqualitynetworkthatbrings-forward minimalissuestoensuresmoothfunctioningofbusinessoperationsandoptimalefficiency
Keepinginmindtheneedtosafeguardanorganizations’
infrastructurefromanykindofcyberthreatsor laggingissues,InsightsSuccessMagazinehasshortlisted,“The10MostTrustedNetworkingSolutionProvider
thatareensuringoptimalnetworkefficiencyandsecurity.
Ourshortlistofcompaniesincludes,PeerApp,whichcutsnetworkcostsandboostscustomersatisfactionfor
(CSPs)andenterprisenetworks;Ennetix,whichisaproviderofCloud-based NetworkPerformanceAnalytics,singularlyfocusedonaccuratelyfindingperformanceissuesincomplex networks,andprovidingtoolstoNetworkOperationteamsforproactivelymanagingsuchissues;AvaLAN,a companywhichcontinuestoinnovatewithwiredandwirelesssolutionsforcommercialandretailfuelingstations, digitalsignage,retailpoint-of-saleandotherindustrialautomationapplications;Netranom,whichprovides professionalITSupportandNetworkServicesforBusinesses;Turn-keyTechnologies,Inc.,whichisoneofthe leadingnetworkingintegratorandwirelesscommunicationsprovider;andAVSystem,whichprovidesits customerswithsolutionsthatenableahighlyeffective,secureandflexibleprovisioningandmanagementoftheir connecteddevices.
Inadditiontothese,don’tforgettoflipthroughthepagesofourEditorialArticles; Redesigning Network in the New Era of Security — InfoNetwork; Network Security Threats & Solutions — Editor’sPerspectives; and Growing Dilemma over Enterprise Security —Editor’sPick.
Also,expandyourknowledgebaseabouttheindustrywithourCXOarticles; Technology and Network Convergence: Forging a Path to Smart Grid, Smart Cities and Internet of Things; IT and Communication Trends for Critical Infrastructure; Connecting Dark Data with IoT; and Are You Staying in Network Secure Zone?
Let’sstart


Slawomir
AccurisNetworkshelpsserviceprovidersmonetisethe connectivitybetweennetworks.Accurissolutionsenable subscriberstomoveseamlesslyandsecurelybetweenLTE,GSM, Wi-Fi,IPXandfixednetworkswhileensuringasuperiorqualityof experience.
AvaLANcontinuestoinnovatewithwiredandwirelesssolutionsfor commercialandretailfuelingstations,digitalsignage,retailpoint-ofsaleandotherindustrialautomationapplications.WhileWireless technologyinnovationandmanufacturingisatAvaLAN’score, AvaLANcontinuestofocusonsolvingcustomer’sproblemswith completesolutions.
AVSystemprovidesitscustomerswithsolutionsthatenablea highlyeffective,secureandflexibleprovisioningand managementoftheirconnecteddevices.
BigSwitchenablesdatacentertransformationandaccelerate
Douglas
Biswanath
bydeliveringaresponsive,automated,and
software-definednetworking(SDN)fabric-based networkingsolution.
Ennetix,isaproviderofCloud-basedNetworkPerformance
singularlyfocusedonaccuratelyfindingperformance
incomplexnetworks,andprovidingtoolstoNetwork Operationteamsforproactivelymanagingsuchissues.
Ourmissionistohelpleadingglobalbrandsdeliverafaster,
andmoreprofitabledigitalexperience
Marisa
Onewordcansumupthemostcommonstrategyfor networkdefense-“boxy.”Buildingand maintainingastrongperimeterhasalongand storiedhistory.Consideracastlewithitsmoat,highwalls anddrawbridge.Thatishowmostnetworksaredefended.In abox.Currently,thementalityis:“Doyouwanttoprotecta newsystem?”Putitinsidethebox.“Processingpersonal information?”Putitinsidethebox.
Whilethe“box”approachwassuccessfulinthepast,it’san antiquatedmodel.And,whiletheconventionalapproachhas beenoccupiedwithdefendingthecastlefromaground attack,adversarieshavedeployedanairassaultwiththe latestmodernweapons.
Overthepastdecade,therehasbeenaquietrevolutionwith howITsystemsandservicesareusedwithinorganizations. Fedupwithalackofoptions,viablesolutionsandageneral disconnectwiththebusiness,usershavetakenmattersinto theirownhands.
Thisevolutionstartedwiththeriseinmobileusage.Early on,traditionalsecurityteamsfocusedeffortsonstopping mobileusage.Eventually,theyacquiescedandaccepted mobiledevices,butonlythosethatwere“approved.”
Ultimately,reasontriumphedandmobileisnowtreatedina morelogicalfashion.Whilestillfourletters,“BYOD”isno longerabadword.Unfortunately,wearenowseeingthe samecyclewithcloudservices.
Consumer-focusedservicesaremakingsignificantinroads intoenterprisesaroundtheworld.Itisfairlycommontosee largevolumesofoutboundnetworktrafficutilizingservices suchasDropbox,GoogleApps,Githuboranynumberof othercloud-basedapplications.Infact,theseserviceshave beguntoincorporatefeaturesandfunctionalityspecifically targetedtothesizeandscopeofvariousbusinessoperations.
Thinkofthisasa“bottom-up”approach.Itisasignthat usersinorganizationsarepushingtechnologyadoptionjust asmuch-ifnotmore-thanatraditional“top-down” approach.Overall,thisshouldbeseenasapositive.The shiftisnowaligningITwiththeactualfocusofthe organization.Itisamovetowardtechnologythatworksin the“realworld,”insteadofsimplylookinggood“onpaper.” However,it’snotallunicornsandrainbows.
Whileproductivitymightbeup,itisextremelydifficultto maintainastrongperimeteraroundthisnewblendof traditional,mobileandcloudinfrastructure.Thereactionto thisis:“Thenwhytry?Isn’tthereabetterapproach?”This responseisrational,butnotthesentimentofavastmajority ofthesecurityindustry.
Justaswithmobileadoption,thecommonsecurityresponse tocloudservicesistoattempttoblockuser’saccessand, instead,guidethemtowardan“approved”(andtypically lessusable)server.Thatisn’tembracingrealityand,quite simply,isnolongerfeasible.
Mark NunnikhovenThearchitecturediagramforcurrentnetworksnolongerfits cleanlyintoasimplebox.Tryingtowedgeitintooneis counterproductiveandcanleadtofrustrationamong employees.Itisimperativetoacceptthefactthatthe perimeterasithasbeenknownisnowgone.Whichleadsto thecoreoftheissue-whatstrategiescanbeadoptedto defendtoday’snetworks?

First,itisimportanttounderstandthattraditionalcontrols stillhaveaplaceinmoderndefense.Thereisaneedfor firewalls,intrusionprevention,anti-malware,filtering,etc. Thesetraditionalelementsserveasastrongcomponent,but theyplayasmallerroleandcannotbeconsideredtheendall,be-allofsecurity.Insteadoffocusingonindividual componentsofthenetwork,itshouldbeviewedaccording tothewayspecificdataflows.
Takeatypicale-commercetransaction,forexample: Inatraditionalapproach,eachofthesesystemswouldreside inrelativeisolation.First,theremustbeafirewallonthesite andanti-malwaresoitis“secure.”Second,theshoppingcart isdeliveredtotheuserviaHTTPSsoitis“secure.”Third, thepaymentinformationisencrypted,thusitis“secure.” Finally,theshippingsystemisonlyinternalsoitis“secure” throughaccesscontrol.
Whilenoneofthesecontrolsarebad,theydonottakeinto accounttherealitiesoftoday’snetworks.Now,shopping cartsareprovidedviaPaaS,paymentsareprovidedviaSaaS ansallshippingisdonethrough a third-party API.These providersinherentlychangeovertimecteatingmore variables and avenues forbreaches.
In addition toadding basicsecurity to eachsystemor service,itiscriticaltoexaminehowdataflows.Whena high-levelviewofdataflowisincorporatedintothetypical e-commercetransaction,thefollowingoccurs:

Itisimmediatelyapparentthatthereisavarietyof informationsharedacrossmultiplesystems.Someofthe
systemsarecontrolledbytheenterprise,somearenot.With thisview,therealchallengecomestotheforefront-how canthesafetyoforders(itemspurchased,quantities, shippinginfo,etc.)andprocessingdatabeensuredbyat leastthreedifferententities?Inaddition,payment informationresidesonatleasttwosystems.Howdoesthat affectPaymentCardIndustrycompliance?Thisisthelevel wheresecurityshouldbeapplied-anditmustbeactedupon holistically
Thetoppriorityforsecuritymustbemonitoring.Itisclear thatcontrollingeveryelementofthenetworkcanbe overwhelming.Withthevarietyofservices,endpointsand connections,theaforementioned“box”modelhasbeen demolished.Thus,thetraditionalperimeterisgone.What takesplaceinnetworksrequiresmoretransparencytoread andreactaccordingly
Amodernmonitoringpracticenotonlypullsinlogdata fromnetworkdevicesandapplicationservers(ashas traditionallyoccurred),butalsologsandreportsfromIaaS, PaaS,SaaSandmobilesystems.Thisinitselfcteatesanew challengewithanimmenseamountofdiversedataneeding tobeprocessed.Fortunately,“bigdata”analyticscanbe appliedtoresolvethisissue.
Thereisverylittlevalueindenyingwherenetwork infrastructuredesign,andaccess,isheaded.Thesoundest strategyistowelcomethisrealityandworktoincrease securityofthecurrentnetworktofocusonmonitoring. Itis essential to becognizant of dataworkflows withinthe overallenterprise.Oncethatisestablished,takingstepsto protectdata,regardlessofwhereitisstoredandprocessed, isfarlessdaunting.

Withthenumberofconnecteddevicesin theworldsurgingaheadofthehuman population,survivalinthecoming decadefororganizationswilldependupontheir abilitytoadapttothechangingtechnological landscape.Asconnecteddevices,connected phones,andconnectedlogisticsbecome ubiquitous,theybring-forwardvalueaswellas complexityfororganizations.
Tosteeraheadofthiscomplexmanagementof connecteddevicesandfocusonthecorebusiness, organizationsneedanexpertsolutionproviderfor thesame.Standingtallamongstitscrowdof competitors,AVSystemisonesuchcompanywith aresolutevisionofcreatingtechnologyand productswhichhelpcompanieshandletheir connecteddevices.Thecompanyseeksto automatewhatcanandshouldbeeffortlesstosave costsandlabor,andallowscompaniestofully focusontheirbusinessdevelopment.
Beinganexpertinlarge-scalesolutionsforTelco operatorsandEnterpriseMarkets,AVSystem’s productportfolioisprimarilyfocusedondevice managementandmonitoringsolutions(TR-069, LwM2M).Theconstantlyevolvingcompany currentlyboastsM2MandIoTservicedelivery platforms,WiFivalue-addedserviceplatform, WiFIlocationengineandothersystemsforSDN andNFV.Bydeliveringpredictivemaintenance, AVSystemaimstoeliminatemostofthenetwork problemsinadvance;therebyincreasingtheendcustomersatisfaction.
ItisalsoworthnotingthatAVSystemisanactive memberoftheleadingindustryorganizations, suchasOpenMobileAllianceandBroadband WorldForum.
SlawomirWolf,FounderandCEOof AVSystem,istheleaderwhosowedtheseedsof successandledthecompanytowhatitisknown astoday.Heisthemainindividualresponsiblefor thecompany'sconstantevolvement–frombeinga
AVSystembelievesintechnology;its strongscientificandtechnical backgroundallowsittoconstantlylook forimprovementstocreatesolutions thatanswereventhemostcomplex needsofitsclients.
management,SIMcardmanagement, andfinally,serviceenablement includingserviceactivation.The distinctivefeaturesoftheplatformare usefulforvariousverticalsaswellas CPS,inordertoenableB2BandB2C services.
smallbusinesstobecomingan innovativeandrapidlygrowingmidsizecompany.Presently,Mr Wolf shoulderstheresponsibilitytolook afterthecompany’sstrategic developmentandmanagementofeach andeveryoneofitsbranchworldwide.
DeliveringExcellencewithUnified DeviceManagementPlatform (UMP)
AVSystemhasbeenapartofthe networkingindustryforoveradecade. Initially,thecompany’sfocuswasto helpitsclientsefficientlymanage, provision,andmonitortheirnetworks ofend-userdevicesofanysizeviathe TR-069protocol.Thispromptedthe developmentofits Unified Device Management Platform (UMP), which iscapableofmanagingallkindsof CPEsviaallkindsofprotocols. Today,UMPhelpsover100companies worldwide,includingglobaloperators andlocalserviceproviders,toimprove theirprocessesandreduceoperational costsbyprovidingunrivaledfeatures suchasauto-configuration,mass operations,remotediagnostics& troubleshootingandadvanced monitoring.
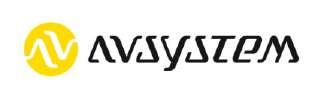
“During the last 10 years, we’ve managed to build a team of highlyqualified engineers from around the world and that provides us with experience and knowledge of how to design products that are secure, reliable and deep-rooted in technology,” mentionsSlawomir.
AVSystemworksattheedgeof technology,constantlyimprovingwhat ithastoday,whileconcurrently anticipatingtheneedsofitscustomers.
Takingintoconsiderationthevast experienceindevicemanagementand cooperationwithvarioustypesof customers—whentheideaofInternet ofThingsbegantoevolve—beingpart oftheevolutionanddevelopingadept IoTsolutionswasthemostnaturalstep forAVSystemtopartake.Thecompany stronglybelievesthatmostofthe problemsfacedbyIoTenvironments canbesolvedbyaneffective introductionofdevicemanagementrelatedsolutions.Hence,leading towardsthedevelopmentofCoiote,a comprehensiveIoTplatformwhich coverseverythingfromdevice managementandmonitoringto connectivitymanagement,application
Presently,AVSystem’sareaoffocus goesfarbeyondthestandardsolutions fordevicemanagement. “Considering the pace of the IoT industry development, we foresee that in the upcoming years, our Coiote IoT Platform will continuously be used by companies worldwide to create a vast ecosystem of connected assets,” asserts Slawomir.
“We expect that the biggest challenge in building truly smart and secure environments will be maintaining and managing millions or even billions of connected devices,” addsSlawomir.
Meetingandexceedingtheneedsof end-customers,AVSystemalso providestop-classsolutionsinthearea ofWiFIValueAddedServices.Its LinkyfiPlatformiscurrentlyusedby manyTelcoandenterprisecustomers, tomanagetheirWiFiaccessand provideinsightintotheircustomers’ behavior.Inthenearfuture,AVSystem expectstogrowrapidly,especiallyin theareaofWiFi-basedindoorlocation services.

 Matt Nelson CEO & President
Matt Nelson CEO & President

Theburgeoninggrowthofcompanies,in everyvertical,aswellaswidespread geographicaloperationsandcontinual additionofcomplexnewtechnologieshas escalatedtheimportanceofnetworkefficiencyand availability AvaLANWireless,anindustry leadingdeveloperandmanufacturerofsecure industrialnetworkingdevices,understandsthis prevalentneedamongorganizations.AvaLAN doesn’tmerelyconnectcellphonesorlaptops, ratheritconnectseverythingelse.
Originatingfromtheheartoftheworld’sleading start-uphub, Silicon Valley in2004,AvaLAN's innovativetechnologyrootsstemmedrightfrom itsearlyfunctioningdays.Itsapproachtoany customerhasalwaysbeentolistenandunderstand whatdevicenetworkingchallengesitscustomers arefacingandrespondwithinnovativenetworking solutionsthataddresses– Security, Reliability, and Complexity.ItistheunmatchedabilityofAvaLAN tolisten,respond,executeandprovideasecure industrialnetworkingsolutionthathaspropelled themtothetopofthisindustry
DeliveringContinuedInnovation AvaLANpossessesacreativeandenergeticteam thatworkstogetherinaquickandefficientmanner totakeoptimalcareoftheircustomers. AvaLAN considers‘listeningtoitscustomers’tobeoneof itscorecompetencies.ThanksinparttoAvaLAN’s continuedinnovationinnetworksecurity,creative networksegmentation,dataencryption,and proprietaryprotocols,AvaLANcansuccessfully respondtoitscustomers,andtheindustry The competentteamatAvaLANgetsneededenergyby solvingitscustomer’svariousproblemsrelatedto networking.Asperthecompany,theproofofa successfulindustrialdevicenetworkiswhenthe userneverlosestheconnectivityandneverfaces anydataintegrityissues.Withground-breaking productsandsolutions,AvaLANworksround-theclocktomakeitsclients’productssuccessfulby notlettingthemdownandbymakingsurethat theirdevicesneverfaceanyissuewithnetwork connectivityornetworksecurity
ACEOServingtheHighTechnologyIndustry MattNelson,CEO,andPresidentofAvaLAN Wirelesshasbeenservinginthishighlydemandingtechnologyindustrysinceitsheydays. Hestartedprogrammingataveryyoungageand beganattendingtechnologytradeshowsduringhis teenyears.Sincethen,healwayswantedtoforma company,onewhichcanlatergoaheadandlead theindustry.Duringhisearlydays,hegotallthe
necessaryexposure,byhelpingand supportingcustomers,whichresulted inbrilliantcustomerfocusthathas neverlefthimtilldate.Throughouthis entirecareer,Mattoscillatedbackand forthbetweenengineering,product management,marketing,sales,finance, andoperations.Mattleadsthrough servantleadershipwhichmeansthat onecannevertakeanyoneforgranted, andasaleaderoneshouldalwaysput hisownpeoplefirstandcannotsay ‘thankyou’enough.Additionally,after takingmoreandmoreresponsibilities throughouthiscareer,Matthasfound hisgreatestjoyinlifebyserving others.ForMatt,theteamofAvaLAN isthebestgroupofpeoplehehasever workedwith,andtheteamnever ceasestoamazehimwiththeir accomplishments.Hebelieveshe cannotthanktheteamenoughfor makingAvaLAN,suchanamazingand greatorganization.
Datanetworkinghasbeenakeyareaof interestforMattsincethelate80’s. Communicatingwithothersthrougha computer,PDA,oramobilephonehas alwaysbeenlikemagictohim,andhe hasworkinginboththewirelessand wiredtechnologyindustryformore thantwenty-fiveyearsyetitnevergets oldthankstotheever-growingneedof goingfasterandfurther Accordingto AvaLAN,thenewfrontierofdata networkingisslowlyimprovingthe
effectivenessandefficiencyofa multitudeofdevices,thenoncomputingindustrialdevice connectivitymarketisvastand excitingnewworld.AvaLAN’s productshaveconnecteddigitalsigns, gaspumps,smartgridsensors, surveillancecameras,POSsystems, andHVACsystemstonameafew areaswheretheorganizationhas deliveredsecureandreliablewireless networkingtechnology
Tilldate,AvaLANhasshippedmore than100,000industrialwireless networkdevices;manyofthe consumersofthedevicesarerepeat purchasersoftheproductsand technologyduetothereliabilityand performanceoftheproducts.Mostof theclientseitherembedAvaLAN’s technologyintotheirdevicesoruse AvaLAN’sfullyassembledproductsin ordertomakebetterproductsor solutionsandtoextractbetter productivity.Overtheyears,the organizationhasbuiltareputationfor reliableandsecureconnectivity StartingfromAvaLAN’shardware clearthroughtotheinterfaceitcreates, alltheproductsareeasytoinstalland use.Theorganizationtakesallthe worriesandcomplexitiesoutofthe industrialwirelessnetworkingand providessoftwareandhardwarethat justplainworks.
AvaLANbelievestheindustrialwired andwirelessdatanetworkingmarket hasnumerousgrowthopportunities. Typically,thecompanysolvesdifficult networkingneedsoraddsadditional valuethroughcustomengineering solutions.Theabilitytoprovidefully customizedsolutionstypicallygives theAvaLANanadvantageoverthe othernetworkingequipment manufacturers.
Recently,thecompanyhascombined twoareasofexpertisetosolveamajor industryneedintheretailfueling
industry.CombiningAvaLAN’s successwiththesecurepointofsale connectivityandfuelpump connectivity,AvaLANisactively deployingvariousproductsinretail fuelingmarket.Thisnewgenerationof productsfromAvaLANhasthemuchneededcapabilitytobemonitoredand managedremotelythroughacustom developedcloudbasedsystem.The organizationisexcitedabout continuingtobuildoutitscloud softwareinadditiontoAvaLAN’snew wiredandwirelessnetworking products.AvaLANhasacompletely uniquetechnologythathasthe capabilitiestosegmentandtrackdata traffic,ensuringsecurePCI compliance.Securingcreditcard informationthroughencryption, proprietaryprotocols,andsecuredata segmentationischangingtheway creditcarddataisbeinghandledand AvaLANisleadingthechangeinthe market. Moreover,AvaLANislooking forwardtoinnovatingonhardware, software,andcloudbasedtechnology whilecontinuingtosolveindustry devicenetworkingchallenges.
MakingtheNetworkingIndustrya BetterPlace AccordingtoAvaLAN,nooneshould havetoworryabouttheircreditcard informationbeingstolen.Currently wiredandwirelessnetworking solutionsfromAvaLANarechanging thewaygaspumpsareconnected.
EMVupgradesongaspumpsare neededtosupportthenewsecurechips ineveryone’screditcardsandAvaLAN isworkingwithamultitudeofvendors tokeepdatasafeandmakingelectronic transactionmoresecureandreliable. Fromdigitalsignstodelivering electricitytohomestoprotectinguser’s creditcards,AvaLANisthe connectivitybehindthescenesmaking itallwork.
I R E L E S S‘‘
‘‘
AvaLAN continues to be inspired everyday by the improvements we can make in people’s lives through the network connectivity of devices

Cloudproviderstypicallyofferdifferent servicelevels,andassociatedprices,for differentsizesofvirtualmachine, memory,anddiskstorage.However,whileall cloudprovidersprovidenetworkconnectivityto tenantVMs,theyoccasionallymakepromises aboutnetworkperformance,butcloudtenantscan alsoseverelysufferfromhighly-variable,erratic networkperformance.
Ennetix,aleadingproviderofCloud-based NetworkPerformanceAnalytics,issingularly focusedonaccuratelyfindingperformanceissues incomplexnetworks,andprovidingsolutionsto NetworkOperationteamsforproactively managingsuchissues.Basedonitsinteraction withclients,Ennetixfoundersobservedthatthere isnolackofnetworkdataormethodstoextract thatdatafromanetwork’sinfrastructure.Thereis, however,ashortageofscalableprocessesthatcan effectivelyextractactionableinsightsfromallthat data.Yet,thisprocessismanual,mundane,and timeconsuming.Inmanyorganizations,network dataisreadilyavailableforonlyashortperiodof time,leadingtoguessworkandfingerpointing.In allcases,effectivemanagementreliestooheavily onhumanfactors,suchasthenetwork administrator’sdepthandbreadthoftechnical expertise,experience,andfamiliaritywiththe networkinfrastructure.
BiswanathMukherjeeakaBis,isaworldleader andvisionaryintheareaofnetworking,andthe Founder&PresidentofEnnetix.Overthepast threedecades,hehaspioneeredseveralgroundbreakingsolutionsforworldwidetelecom networks,whichunderpintoday’sInternet. Additionally,Biswastheco-founderofatelecom startupandhasservedonboardsofnumerous startups.Heisalsoadistinguishedprofessorof ComputerScienceatUniversityofCalifornia, DavisandholdsaPh.D.degreefromthe UniversityofWashington,Seattle,andB.Tech degreefromIndianInstituteofTechnology, Kharagpur,India.Hehasalsoservedoneight journaleditorialboards,mostnotablyIEEE/ACM TransactionsonNetworkingandIEEENetwork. Mukherjeeisanenergeticentrepreneurandis excitedaboutsolvingthenetworkingchallengesof thenextdecade.

TheEnnetixsolutionisanoff-shootof theresearchconductedbyitsfounder BisatUCDavis,whichwasvery interestingacademically,Bissaid,but didnotaddressreal-worldproblems peoplewouldbewillingtopayto solve.Asaresult,headoptedhiswork todevelopEnnetix.Infact,Ennetix wasthefirstentitythatwasnurtured throughanewUCDavisincubator,the


EngineeringTranslationalTechnology Center,andhasreceived$2.3Min grantsfromtheUSDepartmentof Energy’sSmallBusinessInnovation Program(SBIR).

Asbusinessesmigratedatacentersand applicationstothecloud,managingthe underlyingnetworkinfrastructurehas becomeincreasinglycomplex.Witha distributednetworkinfrastructure,a significantpartofthenetworkisnow undertheadministrativecontrolof third-partyserviceproviders. Monitoringnetworkperformanceand identifyingtherootcauseof performance-relatedissueshavegrown evenmorechallenging.Businesses implementnewwaystodeliverservice totheircustomers;andthegrowthin applicationtrafficandthe unpredictabilityofthedemandfor networkresourcesfurthercompound thisissue.

Consequently,networkinfrastructure planningprovestobeahuge challenge.Today,networkperformance managementinvolveswadingthrough largeamountsofnetworkdata, assumingsuchhistoricaldataisreadily available.Inmostorganizationstoday, networkadministratorsareconstantly “fire-fighting,”jumpingfromissueto issue,triagingthemasquicklyas
possible,andapplying“band-aid” solutionswithoutproperroot-cause identification.
TheinformationthatEnnetixprovides enablenetworkoperationsteamsto meetthechallengesinherentin managingtheperformanceoftoday’s networks,bothon-premiseandinthe cloud.TheEnnetixsolutioncombines continuousmonitoring,advanced analyticsbasedonproprietarymachine learningalgorithms,andinteractive visualizationstoprovidecustomersa holisticsetofanalytics.Ennetixhelps itsclientstogetabetterhandleon managingahybridinfrastructureand determineexactlywhathappened (hindsight),predictwhatisgoingto happen(insight),andassesshowit wouldneedtoaddresssevere problems,aftertheoccurrence (foresight).
Currently,Ennetixsolutionisdeployed atseveralorganizations,includingmid tolargesizecompanies,verylargesizeduniversities,andtalkswith severalotherorganizationsarein progress.Lookingahead,Ennetixis pursuingaglobalexpansionstrategy andhascontractssignedupin internationalmarkets.
‘‘ ‘‘
The information that Ennetix provides enables Network Operation teams to meet the challenges inherent in managing the performance of today’s networks, both on premise and in the Cloud







ovember3,1988,isconsideredasaturningpoint
NintheworldofInternet.25YearsagoaCornell Universitygraduatestudentcreatedfirstcomputer wormontheInternet,“MorrisWorm.”TheMorrisworm wasnotadestructiveworm,butitpermanentlychangedthe cultureoftheInternet.BeforeMorrisunleashedhisworm, theInternetwaslikeasmalltownwherepeoplethought littleofleavingtheirdoorsunlocked.Internetsecuritywas seenasamostlytheoreticalproblem,andsoftwarevendors treatedsecurityflawsasalowpriority
Today,thereisaparadigmshift,Morriswormwas motivatedmorebyintellectualcuriositythanmalice,butit isnotthecasetoday.Accordingtoa2015Report,71%of representedorganizationsexperienced,atleast,one successfulcyberattackinthepreceding12months(up from62%theyearprior).
Accordingtosurveyreport,disclosesthat,among5500 companiesin26countriesaroundtheworld,90%of businessesadmittedasecurityincident.Additionally,46% ofthefirmslostsensitivedataduetoaninternalorexternal securitythreat.OnaverageenterprisespayUS$551,000to recoverfromasecuritybreach.SmallandMediumbusiness spend38K.
Incidentsinvolvingthesecurityfailureofathird-party contractor,fraudbyemployees,cyberespionage,and networkintrusionappeartobethemostdamagingforlarge enterprises,withaveragetotallossessignificantlyabove othertypesofthesecurityincident.
Adenialofservice(DoS)attackisanincidentinwhicha userororganizationisdeprivedoftheservicesofaresource theywouldnormallyexpecttohave.Theseattacksarevery common,accountingformorethanone-thirdofallnetwork attacksreviewedinthereport.Astandardapproachisto overloadtheresourcewithillegitimaterequestsforservice.
Bruteforceattacktriestokickdownthefrontdoor.It’sa trial-and-errorattempttoguessasystem’spassword.The BruteForceAttackpasswordcrackersoftwaresimplyuses allpossiblecombinationstofigureoutpasswordsfora computeroranetworkserver.Itissimpleanddoesnot employanyinventivetechniques.
IPspoofing,alsoknownasIPaddressforgery Thehijacker obtainstheIPaddressofalegitimatehostandalterspacket headerssothattheregularhostappearstobethesource.An attackermightalsousespecialprogramstoconstructIP packetsthatseemtooriginatefromvalidaddressesinside thecorporateintranet.
theinternetwhichinturncanspreadinthewholeenterprise network.Theattacksmayencouragethemtounwittingly downloadmalwaredisguisedasafakesoftwareupdateor application.Maliciousandcompromisedwebsitescanalso forcemalwareontovisitors’systems.
Transportlayersecurity(TLS)ensurestheintegrityofdata transmittedbetweentwoparties(serverandclient)andalso providesstrongauthenticationforbothsides.SSL/TLS attacksaimtointerceptdatathatissentoveranencrypted connection.Asuccessfulattackenablesaccesstothe unencryptedinformation.SecureSocketsLayer(SSL) attacksweremorewidespreadinlate2014,buttheyremain prominenttoday,accountingfor6%ofallnetworkattacks analyzed.
NetworkSecurityisanessentialelementinany organization’snetworkinfrastructure.Companiesare boostingtheirinvestmentsinproactivecontrolandthreat intelligenceservices,alongwithbetterwirelesssecurity, next-generationfirewallsandincreasinglyadvanced malwaredetection. The U.S. Federal Government has spent $100 billion on cyber security over the past decade, $14 billion budgeted for 2016.
Increaseduseoftechnologyhelpsenterprisestomaintain thecompetitiveedge,mostbusinessesarerequiredto employITsecuritypersonnelfull-timetoensurenetworks areshieldedfromtherapidlygrowingindustryofcyber


crime.Followingarethemethodsusedbysecurity specialiststofullproofenterprisenetworksystem-
Penetrationtestingisaformofhackingwhichnetwork securityprofessionalsuseasatooltotestanetworkforany vulnerabilities.DuringpenetrationtestingITprofessionals usethesamemethodsthathackersusetoexploitanetwork toidentifynetworksecuritybreaches.
Intrusiondetectionsystemsarecapableofidentifying suspiciousactivitiesoractsofunauthorizedaccessoveran enterprisenetwork.Theexaminationincludesamalware scan,reviewofgeneralnetworkactivity,system vulnerabilitycheck,illegalprogramcheck,filesettings monitoring,andanyotheractivitiesthatareoutofthe ordinary
NetworkAccessControlsaredeliveredusingdifferent methodstocontrolnetworkaccessbytheenduser. NACs offeradefinedsecuritypolicywhichissupportedbya networkaccessserverthatprovidesthenecessaryaccess authenticationandauthorization.
NetworkSecurityisaraceagainstthreats,andmany organizationsareapartofthisracetohelpenterprisesto
securetheirnetworksystems.OrganizationslikeIBM,Symantec,Microsofthavecreatedsolutionstocountertheglobal problemofnetworksecuritythreat.Thesecutting-edgeproductsshowgenuinepromiseandarealreadybeingusedby enlightenedcompanies.

Arealsecuritysolutionshouldhavefourmajorcharacteristics; Detect Threats
Targetedattacksaremulti-facetedandspeciallydesignedtoevademanypointtechnologiesattemptingtoidentifyand blockthem.Oncetheyareinside,theonlywaytofindthesecyberthreatsistounderstandthebehavioroftheindividual attackcomponentsanduseanalyticstounderstandtheirrelationships.
Todayitisnotimportantthatanorganizationwillbeattacked,butimportantandmorecrucialistoidentifywhenand howmuchtheycanlimittheimpactandcontaintheirexposure.Thismeanshavingthecapabilitytorespondquickly oncetheinitialincidenthasbeendiscovered.
Malwareisgettingsquick-witteddaybyday Theyutilizeheuristicstochangetheircodedynamically Acapable solutionshouldhaveanadaptivearchitecturethatevolveswiththechangingenvironment,andthreatstoday’sbusiness faces.
Today’sthreatshavemultiplefacets,andasinglesoftwareorsolutionisnotsufficient.Protectionsystemshouldhave thecapabilitytointegratewithothersecuritytoolsfromdifferentvendorstoworktogetherasasingleprotectionsystem, actingasconnectivetissuefortoday’sdisjointedcybersecurityinfrastructure.
Likeinfectiousdiseases,cyberthreatswillneverbeeradicatedentirely,buttheycanbebettercontainedandunderstood, andtheireffectsminimized.Howcanthisbeachieved?IBMhasbuiltanenterprise-level“immunesystem,”anadaptive securityarchitecturetobattletoday’scyberpathogens.IBMhasdevelopedavastfleetofproducts,QRadar,X-Force ThreatIntelligence,TrusteerPinpointMalwareDetection,IBMThreatProtectionSystemadynamic,integratedsystem tomeddlethelifecycleofadvancedattacksandpreventloss.
TheIBMThreatProtectionSystemintegrateswith450securitytoolsfromover100vendorsactingasconnectivetissue fortoday’sdisjointedcybersecurityinfrastructure.
SymantecisanothermajorplayerincateringenterprisenetworksecuritysystemswithSymantecAdvancedThreat Protection.SymantecATPoperatesviaasingleconsoleandworksacrossendpoints,networks,andemails,integrating withSymantecEndpointProtection(SEP),andSymantecEmailSecuritycloud,whichmeansorganizationsdonotneed todeployanynewendpointagents.Symantecsays,ATPistheonlythreatprotectionappliancethatcanworkwithall threesensorswithoutrequiringadditionalendpointagents.WithATP,Symantec’sgoalistodeliverend-to-endthreat protection,prevention,detection,andresponseinasinglepaneofglass,offeringmorevaluetobusinessesthan individualpointproductscanprovide.SymantecAdvancedThreatProtectioncombinesmultiplelayersofprevention, detection,andresponse.
 Scott Edwards CEO & President
Scott Edwards CEO & President
Justlikeanyothercomplextechnologies, there’snotonesizethatfitsallsolutions whenitcomestonetworking.Theneedsand resourcesofeveryorganizationdiffercompletely fromeachother.Enters,Hurricane,WVbased ManagedServicesITCompany,Netranomthat hasbeenservingtheWV/KY/OHareasince1999. IthasbeenprovidingITSupportsuchasManaged ITServices,ManagedTelephoneSystemsaswell asSecurityandSurveillanceservicestosmalland medium-sizedbusinesses.
IthasalwaysbeenNetranom’sgoaltoprovide enterprise-levelITpracticesandsolutionstothe smallandmediumbusinesssector,withsmall businessprices.Itsrichexperiencehasallowed Netranomtobuildanddeveloptheinfrastructure neededtokeepitspricesaffordableandclientsup andrunning.Netranompartnerswithmanytypes ofbusinessesinthearea,andstrivetoeliminateIT issuesbeforetheycauseexpensivedowntime,so clientscancontinuetodrivetheirbusiness forward.

ScottEdwardsistheCEOandPresidentof Netranom.HeisalsotheMayorofCityof Hurricaneformorethantenyears.Hewaselected stbackon1 July2007.Additionally,heistheowner andmanagingmemberofTeaysProperties,which isarentalcompanywithresidentialpropertiesin PutnamandWesternKanawhaCountyinWV TeaysPropertiescontinuestopurchasehomes, whichisthemainsourceofitsgrowth.
ScottwasbornandraisedinHurricane,WVwhere hestillliveswithhiswifeDanielleandfour children;Justin,Karlee,Chayce,andPeyton.
NetranomhasastateofartNetworkOperations Centerwithabrilliantticketingandremote monitoringsystemthathelpsittobeconnected withitsclientsallthetime.Thishelpsthe companyworkremotelyandprovidequick responsesthatalltheclientslove.Anothergreat pointaboutNetranomisthatalltheurgenttickets arerespondedinthesamedayitself.Notonlydoes
Round the Clock Maintenance: 24/7 accesstoremote&on-siteserver remediationservicesataflatmonthly rate.
Live Help Desk Support: Fastand reliableITsolutionsprovidedforyour businessusers.
“It is always a pleasant experience to do business with Netranom. If you ever need an IT company that delivers on all of their promises, this company is it!” –SandyUnderwood(Ownerof ThePrintingPress).
time and they get it fixed correctly the first time around. I do not have repeat issues of the same problem. Their pricing was also amazing – they reduced my IT cost by half,” –Tanya Thomas(FirmAdministratorBucci Bailey&Javins).
hesystemallowtheorganization
tremoteaccesstoitsclients,italso givesNetranomtheabilitytotakea proactiveapproachtotheirnetworkby keepingtheirserversandworkstations up-to-dateontheircriticalupdatesand patches.
Netranom’sManagedServicePlan ensures:
Proactive Care: Dedicationtothe preventionofdatalossandother businesstechnologydisastersbefore theyhappen.

“We subcontract over 25 phone system installations per month throughout the U.S. and Netranom is by far the best company we have worked with in over 16 years of selling phone systems. They are courteous, professional and on top of everything they do. I look forward to working with them again in all of our future projects,” –BrianHelmke (PresidentofInterfaceTechnologies, Inc.).
“Netranom has been great to work with. They are quick in their response
MostofthepeopletrytocompareIT companiesbyan“appletoapple” comparison,butNetranomalways worksdifferently.Startingfromthe salesprocess,throughonboardingand beyond,thecompanyalways establisheslastingrelationshipwithits clients.Netranomwantsthemtothink ofthecompanyasits “fulltime IT guy”.Also,thecompany'sknowledge isnotlimitedtojustcomputer networkingorcameras.And,insteadof an“appletoapple”comparison, Netranomadditionallylikestothinkof itselfasthewholefruitbasket!
Whenitcomestofuture,Netranomis anticipatingasteadygrowthoverthe nextfewyears,allowingthecompany toopenmultiplesatelliteoffices throughoutWestVirginia,Kentucky andOhio.
‘‘
Your success is our success, and as you grow, we grow




Withtheincreasingrateofrealtimecyber-attacksinrecentdaysontherise,involvementinNetworkSecurityis becomingamoresignificantfactortosecurecomputernetworksandbusinessdatasafe. Thenewandextremely virulentstrainofmaliciousransomsoftwaresthatiscripplingthecomputersgloballyappearstobebadlyhobbled muchofthegovernmentandtheprivatesector
Nowadays,thereseemtobeconstantremindersinthenewsaboutthelatesthackornewesttypeofcyber-attack.Asaresult, thesecuritymarketexperiencedasignificantamountofgrowth.Recentreportsexpectthenetworksecuritymarkettocross $100billionin2019from$76billionin2015.Totakeadvantageofthis,numerouspointproductsandsolutionsfloodedthe marketandeveryoneseemedtotalkaboutthenetworkandhowitneedstobesecure.However,evenwithallthetalk, securitywasstillgettinginthewayofnetworking,addingtoomanycontrols,orslowingthenetworkdown.
NetworkSecurityistheimportantprerequisiteofsecuringinformation Dataisthemostpreciousaspectoftoday’sbusinesses.Topbusinessorganizationsspendbillionsofdollarseveryyearto securetheircomputernetworksandkeeptheirbusinessdatasafe.Eventhecommonpeoplearedependentoncomputers todayforcontrollinglargemoneytransfersbetweenbanks,insurance,markets,telecommunication,electricalpower distribution,healthandmedicalfields.Securityisnotnegotiableinthesecriticalandcrucialareas,whereintheworldis lookingforwardtoincreasetheusageofsystemsandthenetworks.Vulnerabilitiesinthesesystemsareincreasingandthe taskofsecuringthenetworksisbecomingmorecomplex,makingNetworkSecurityanessentialpartoftoday'sbusinesses. NetworkSecurityiseffectiveinpreventingDoS(DenialofService)attacksandassuringcontinuousserviceforlegitimate networkusers.NetworkSecurityinvolvesproactivedefensemethodsandmechanismstoprotectdata,networkandnetwork devicesfromexternalandinternalthreats.

Bygainingphysicalaccesstonetworkdevices,ausercanextractimportantinformationfromthecompany'sserversoreven thestoragedevices.Externalattackersgainaccesstothesenetworkresourcesthroughtheinternetandareabletofetchthe datasuccessfully.Here,theinformationsecuritymanagementcomesintoplaytoensurebusinesscontinuityandreduce businessdamagebypreventingandminimizingtheimpactofsecurityincidents.AnInformationSecurityManagement System(ISMS)enablesinformationtobeshared,whilstensuringtheprotectionofinformationandcomputingassets.
Networksecurityisnotonlyprovidingsecurityinasinglenetworkratherinanynetworkornetworkofnetworks.Network Securityincludestwobasicsecurities.Thefirstisthesecurityofdatainformationi.e.,toprotecttheinformationfrom unauthorizedaccessandloss.Andsecondiscomputersecurityi.e.,toprotectdataandtothwarthackers.Theneedfor informationsecurityisimportanttoprotectthesesecretinformationusersonthenetonly.Here,oninternet,oranynetwork ofanorganization,thousandsofimportantinformationisexchangeddailywhichcanbemisusedbytheattackers.Theneeds ofcomputersecurityfromhackersarethatitshouldbeprotectedfromreplicatingandcapturingvirusesfrominfectedfiles.It needsproperprotectionfromwormsandbombssuchasTrojanHorses,whichareimmenselydangerous.
Theinnovativedaysofnetworksecurity Lookingforwardtothefuture,thenumberofopportunitiesandchallengeswill increasewhenitcomestosecuringtheenterprise.Withtheimportanceofnetwork security,whatorganizationscanlookfortomakesurethatsecurityisintheir

DNAthatareasfollows:
Ÿ Integrated security:Withtheexponentialincreaseindevicesandapplications, thesurfaceareaforanorganizationhasexpandedbeyondtraditionalmeans.To reduceriskandcomplexity,securitywillneedtobeembeddedwithinhardware andsoftwaresolutions.Itshouldalsohaveflexibledeploymentoptionsand workwitheachothertoprovideintegratedmultilayeredprotection. Expectationsfromsecurityarchitecturesismeanttobesimple,open,and automatedsothatthenetworkhasbetterperformance,workswithother solutions,andiseasiertomanage.
Ÿ Need for improved visibility: NetworkSecurityTrendsInfographicplan forgettingthefactsonendpointsecurityandstaycurrentonthe trends.ThisInfographiccompilesrelevantdatafromGartner,IDC, ThePonemonInstitute,Symantecandothers,onthecurrent stateofnetworksecuritythreatsfrommobile,IoTandother endpoints.Asaresultoftheamountofgrowthexperienced bydigitalorganizations,76%ofITprofessionalssayalack ofvisibilityistheirbiggestchallengeinaddressing networkthreats.Itisbecomingmoreandmoreimportant toknowwhatisgoingonwithinthenetworkatalltimes–acrossallapplications,users,anddevices.Expect networkingandsecurityteamstoworkmorecloselyand leveragenetworkinfrastructuretoextendvisibilityeverywhere.
Ÿ Emphasis on analytics: Basedonrecentreports,organizations areusinganalyticsmoreacrosstheboardaspartoftheir securitystrategy Thetypeofinformationandtheamountof informationiscriticallyloweringthetimetodetection.Samplingdata mayhavehelpedidentifyandreacttothreatsinthepast,butwhenlookedfor contextualawarenessandotherproactiveandmoreintelligentwaysof gatheringdeeperinsightsanddata,leadingtomoreaccuratedetectionof anomalousnetworkanduserbehaviorsacrossthenetwork.
Ÿ Move towards cloud: Cloudsecurityoftenreferstouserauthenticationand dataprotection,typicallythroughencryption.Amongthemanyissuesisthe abilitytoauthenticateemployees,tocontrolthecloudservicesanddatathey haveaccessto.Inaddition,managingcloudsecuritysothatpoliciesand compliancestandardsenforcedwithinaninternalnetworkareextendedtothe cloudremainsachallengeformanyorganizations.Asorganizationslooktothe cloudtoenabletheirbusinesswithbenefitslikeflexibility,simplicity,and scale,cloudsecurityadoptionwillfollowcloselybehind.Thisyear,expectto seeincreasinginterestinprotectingdataandapplicationsinthecloud.Clouddeliveredandcloud-administeredsecuritysolutionsaregaininginpopularity also.Thesesolutionsoffereaseandspeedofdeploymentandconsistency, simpleadministrationtoprovideaninitiallayerofdefense.

Withtheadventofvideostreaming serviceslikeYoutube,Netflix, AmazonPrimeVideo,etc.,therateof videoconsumptionisexplodingdaily,whichis severelystrainingoperators’networks.College, universityandK-12networksfacethesame qualityandcostissuesasstudents,facultyand staffusetheInternettoconsumevideoandmedia contentoflongerlengthandatverylargevolumes –forbothacademicandentertainmentpurposes. So,withsolutionsthatcanbedeployedatthecore ortheedgeofthenetwork,entersPeerApp.Itcuts costsandboostscustomersatisfactionfor communicationserviceproviders(CSPs)and enterprisenetworks.Theuniquecontentdelivery platformofPeerAppoffersarangeofnetwork optimizationsolutions–contentlocalizationand caching,livestreamingdelivery,applicationand dataacceleration,smarttrafficmanagementand QoEenhancementforallnetworks.Theawardwinningcontentdeliveryplatformisdeployedto morethan550clientsinover100countries. Additionally,ithelpstoimprovethequalityof experiencewithtrafficacceleration,achieveupto 20percentcostcutting,capacityandcongestion management,andhandleallcontent,including encryption.
PeerAppisledbyMarisaE.Goldenberg,CEO. Herexperienceincludesmorethan20yearsinthe technologyindustry,includingpositionsatESW Capital,Trilogy,andDell.Goldenbergisa respectedstrategicleaderandversatileexecutive, whohasanexceptionalabilitytodrivebothlongtermstrategicbusinesstransformationsand immediateorganizationalimprovements.
Withatrackrecordofintegrityanddedicationto excellenceandcustomersuccess,Goldenbergis adeptatexpandingandstrengtheningenterprise softwareproductsandcompanies.Additionally, shehasdeliveredvalueandresultsto organizationsfromstart-upstoFortune100 companies.
AtRideAustin,anon-profitridesharecompany, Goldenberglaunchedcompanyoperationsand scaledthebusinessforfastgrowthandlong-term sustainability Withinthefirstyearofoperations, theplatformgrossedover$30millioninrevenue
andraisedover$250,000forlocal charities.
Hergeneralmanagementcapabilities werehonedinavarietyoffunctionsat Dell.AsastrategyanalystintheOffice oftheChairman’sCorporateStrategy Group,sherecommendedproduct opportunitiestotheCEOandassisted theBoardofDirectorsinsetting3-year financialtargets.Goldenberg subsequentlymanagedstrategic planningforDell'sEnterpriseProduct GroupandservedasChiefofStafffor theVicePresidentofMarketing.She alsoheldrolesatDellasaFinancial Controllerfora$10billion organizationandDirectorofGlobal Operations.
Goldenbergearnedabachelor’sdegree incomputerscience,cumlaude,from PrincetonUniversityandanMBA fromHarvardBusinessSchool.
Thecontentdeliveryplatformof PeerAppoffersarangeofnetwork optimizationsolutionsthat dramaticallyreducenetworkcostsand improvessubscriber’sInternetquality ofexperience.Productslike PARapid helpstoimprovesubscriberexperience whileloweringcostsandaccelerating
downloadspeedX20. PAQoE
Controller isasmartQoEmanagement foroptimalbandwidthusageand slashesbandwidthcostsby20percent PACache helpstospeedupcontent deliveryuptoX18.And PALive helps tostreamliveeventsandachieves offloadsupto20percent
PeerApp'ssolutionisdeployedatthe coreortheedgeofnetworktodeliver extradimensionofcustomerdelight.

Inadditiontoprovidingmajorsavings onthenetwork,showing50%offloads ofnetworktraffic,reducingIPtransit costsandinfrastructureupgradesare thestandoutfromPeerApp.Manyof PeerApp’scustomersarenow upgradingtheirsystemssincethe HTTPtrafficiscontinuouslygrowing andthereisatrueneedforthecaching solution.Thankstoitsrapidgrowth, drivenbyincreasedcontent availability,userappetite,broadband accessspeedsandconnecteddevices, athomeandon-the-gointernetcontent consumption,especiallylong-form video,hasgrownbyafewfoldsin recentdays.Nowadays,usersexpect internetcontentandapplicationstobe availableallthetimeandonany device,andtheywon'ttolerateany buffering.So,toimprovethequality, mostoftheoperatorsareinvestingin networkupgrades.
Thecontentdeliveryplatformfrom PeerApphelpsoperatorstodeliver globallyoriginatedcontentfroma localsourceclosetothesubscriber, improvingQoEandreducing bandwidthconsumptionthroughoutthe network.ThecompanyredefinesQoE andacceleratesthedeliveryofcontent andencryptedcontentbyupto20 times.Thebestpartisthatthe impressivedeliveryrateisachieved overexistinginfrastructures,and
operatorscanpromoteOTTbundlesas newserviceofferingsbyusingthe platformtosatisfyacustomer’s appetitefordata.Theorganization’s newcontentdeliveryplatformoffersas muchasfourdifferentsolutionsto handlecontentdeliveryfromdifferent aspects,includingencryptedtraffic.
Thisnewenhancementprovides PeerAppwithuniqueleverageinthe marketbyhandlingalltypesofcontent inthenetwork,creatingmajorsavings, improvingthequalityofexperience andoffloadingthenetworkcongestion.
PeerAppprovidesabest-of-breedlocal contentdeliverysolution,550 deploymentsworldwide,track-proven acceleration,networksavingswith assuredQoE,whilemanagingALL trafficandvideo,includingencryption, dynamiccongestionmanagement, capacitycontrol,andCOTS-based virtualizedsolutions.Eventually,these solutionshelpthecompanytocutcosts andtoboostcustomersatisfactionfor communicationserviceproviders (CSPs)andenterprisenetworks. Additionally,thecontentdelivery platformofPeerAppspanscontent localizationandcaching,live streamingdelivery,applicationand dataacceleration,smarttraffic managementforallnetworks,which canbedeployedatthecoreofthe networkandimprovecustomer satisfaction.Thesedifferentiatorshelp thecompanystayaheadofthe competition.
PeerAppcontinuestoleadthemarket withvariousnewandinnovative solutions,expandingitscontent deliveryplatformtohandlealltraffic, includingencryption,andhelping customerstogrowtheirbusiness.





Nowadays,ourbelovedplanetis completelytiedupbytheworld-wideweb,andwecannotevenexecuteour dailytaskswithouttheusageofinternet.Withthis increaseinusageofinternet,wirelessnetworks havebecomeanecessityforeveryorganization acrosstheglobe,andsolutionprovidersare challengedtomeettheever-increasingneedsof professionalsandenterprises.Likeallother industries;knowledge,expertise,andinnovation aresomeofthemostcriticalcomponentsinthe networkingindustry,andsomeoftheprovidersare standingoutamongthecrowd,bydelivering solutionstotransformbusinesses,healthcare, educationandotherfieldsinahighlyvaluable way Turn-keyTechnologies,Inc.isn’tany exception,itisoneoftheleadingnetworking integratorandwirelesscommunicationproviders establishedin1991.TTIhelpsinproviding networkdesign,configuration,installation,and supportservicestoclientsinall50statesand aroundtheglobe.Additionally,thecompanyhas alreadyinvestedheavilyinitsengineers.The engineersholdcertificationsfromthe manufacturerswhomTTIrepresents,andtheyall holdindustryagnosticcertificationsthathelpthem understandandtroubleshootbeyondmanufacturer bestpractices.Sinceinception,TTIhasalways beena“customerfirstandcustomerlast” organization,thecompanyevenprovidesits clientswithoneyearofunlimitedaccesstotheir 24x7x365TechnicalAssistanceCenterupon completionofaninstallation.
CraigBadrickistheCEOandPresidentof Turn-keyTechnologies,Inc.Hejoinedthe companybackin1992androsetothepositionof PresidentandCEOin1999.Withabackgroundin businessandsales,hetookoverasalesrollin PennsylvaniaandNewJerseyandquickly establishedhimselfasanassettoTurn-key Technologies.Craigquicklyexpandeduponthe corebusinessofwirelesscommunicationsby addingWi-FitothesolutionsthatTTIprovides. Thankstotheexpertiseinwirelesstechnologies thatengineersalreadypossessed,Turn-key Technologiesquicklybecameago-topartnerfor themanufacturersthatwerestrugglingtofind competentpartnerstodesign,install,andsupport theirproducts.FromtheearlysuccessesinWi-Fi,

TTIquicklyexpandedtheircapabilities toincludeallaspectsofnetworking fromcore,toedge,tosecurityand peripherals.Craighasbeen instrumentalingrowingthebusinessof TTIover1400percentunderhis leadershipandthecompanywasalso recognizedasoneofInc.Magazine’s 5000FastestGrowingPrivatelyHeld BusinessesinAmerica.Craig continuestolookintoemerging technologiesandbusinessstrategiesto
ensureTurn-keyTechnologiesstaysat theforefrontoftheInformation Technologyandcontinuestoprovide itscustomerswithbestbreedof solutions,alongwithitsbest-in-class services

BeingNimbleistheKey Beingnimbleisoneofthekey requirementsthatMr.Badrickimplants throughouthisbusiness.Themaingoal ofTTIistoconsultwithacustomer, designthenetwork,tweakthedesign basedonconsultationwiththe customerandthenprovideafinal designandbillofmaterialswithintwo weeks.Experiencedprojectmanagers overseeeachinstallationwiththegoal ofeliminatinganyunforeseendelays andminimizinganynetwork disruptionsordowntime.By eliminatingtheunknown,andby properlyplanning,stagingandpreconfiguringtheequipment,the customerfacesverylittledisruptionto theiroperations,evenwhentheyare providingacompletenetwork replacement.
TacklingtheCompetition Turn-keyTechnologiesissocustomer focusedthatithasgarneredextreme loyaltyfromitscustomers,aswellas providingagreatsourceof recommendationsandreferrals.All thankstothecompany’shyperfocus oncustomersatisfactionandthefact
thatitguaranteesallitswork contributestoitsclient’ssuccess. Additionally,thecompanyisalsovery awareofbudgetsandtheneedto providethebestbangforthebuckfor theircustomers.Lastly,thecompany maintainsaverysmalllinecardwitha handfulofmanufacturers,sothatthe clientscanbeassuredthattheyare trulygettingexpertsinthesolutions Turn-keyprovides.
Whenitcomestothefuture,Turn-key Technologieswillcontinuetoinvest heavilyinitsengineers.Accordingto thecompany,ongoingtrainingisa necessityinordertostayontopofthe latesttechnologiesandhowthey impactthenetwork.Emergingtrends liketheIoT,SoftwareDefined Networks,Hyperconvergence, 802.11ax,AugmentedReality,and VirtualReality,networkanalyticsand moreareallbecomingmoreprominent inthecompany’sconversations,so providinganswersonhowtechnology canassistintheadoptionofthese trendsisveryimportant.
Additionally,Turn-keyisalsoworking endlesslytomaketheindustryabetter place,andaccordingtothecompany thekeyistobeatrustedadvisortoits customers.Providinghonestanswers, designingright-sizedsolutions, listeningtothecustomer’schallenges andprovidingcost-effectivesolutions inatimelymannerareallvitally important.Turn-keyisalsoseeinga hugetrendforallaspectsofITbeing offeredasaservice.Lastly,beingable toprovidemeaningfulmanaged servicestoaugmentthecustomersinhouseexpertiseisanareawhereTurnkey’sexperience,businessethics,and customerfocusissuretogrowand maketheITservicesanotherpartof thebusinessthatdoesnotrequire constantworryandconcern.
‘‘
‘‘
Uncover the performance and security issues hiding in your network, and learn the most effective ways to overcome them




