Most Trusted Cyber Security Companies
Venkatesh Sundar Founder & CMO









Every innovative invention conceived by humankind has an array of pros and cons associated to it. Considering the benefits or convenience a particular invention offers, solutions are developed that address the disadvantages or repercussions of using that invention.
Take the motor vehicle for instance. Along with the advantage of convenient and speedy travel that it provides, there is always the risk of accidents. The solutions developed in addressal of this risk include the likes of seatbelts, air bags and most recently, technology that assesses driver behavior and the threats in the vehicle’s vicinity.
The same is applicable when the invention under consideration is the internet. Although it provides every individual with global connectivity and mildly ominous convenience, every packet of information sent across the internet is prone to a cyberthreat.

In a time and age where almost all our personal information is being stored digitally, cybersecurity cannot be disregarded – especially when it comes reinforcing cybersecurity measures for those companies which are working remotely.

Based on considerable research, companies that have failed to implement stringent cybersecurity measures have suffered substantial losses in terms of data as well as financial losses.
A few experts shed light on the importance of implementing stringent cybersecurity measures: “As large sections of the workforce have moved to working outside traditional organizational boundaries, the threat surface for sensitive information has expanded dramatically presenting a range of novel cybersecurity challenges,” says the Founder and CEO of QuintessenceLabs, Dr Vikram Sharma.
“The COVID 19 pandemic has caused enormous pressure, throwing the global economy into a recession. Some organisations might consider downsizing by cutting down on business lines considered as ‘non-critical’ which may include cybersecurity services. This short term plan might however prove to be ‘penny wise and pound foolish’ in the long haul, as this will further increase the impact of attacks on the organizations,” says Flavius Plesu, the Founder and CEO of OutThink.
“More traffic equals more vulnerabilities and opportunities. That’s how hackers think. I believe 2020 was the most important year in cybersecurity and the beginning of a new era in
the digital world. It is not a coincidence that companies and even governments started to spend much more money on cybersecurity” Says George Egri, the Co-Founder and CEO of BitNinja.
These statements most certainly act as admonitions to those who seek the ‘why’ when the term cybersecurity is brought up in board meetings and other scenarios pertaining to organizational security

This edition, the Most Trusted Cyber Security Companies, brings into spotlight those organizations that are striving to deliver innovative cybersecurity solutions and are making their mark in the process.
Abhishaj Sajeev abhishaj@insightssuccess.com






Indusface www.indusface.com
VenkateshSundar
FounderandCMO
IndusfaceisaSaaScompanywhichsecurescriticalWeb applicationsof2000+globalcustomersusingits award-winningplatform.
QuintessenceLabs www.quintessencelabs.com
Bitninja bitninja.io
Wings2i www.wings2i.com
Dr.VikramSharma
FounderandCEO
GeorgeEgri Co-founderandCEO
QuintessenceLabsdeliverspowerfuldataprotection,enhanced bythequantumpowerofnature.
BitNinjaisthefirstintegratedserverdefensenetworkinthe world.
OutThink www.outthink.com
VinodKumarAgrasala CEO
FlaviusPlesu Founder&CEO
Wings2iisaProfessionalServicesOrganizationfocusingon KnowledgeServicesindomainsrelatedtoInformation Technology
TheOutThinkplatform(cloud-SaaS)hasbeendeveloped specificallytoidentify,measurehumanriskandaffect behaviourchange.

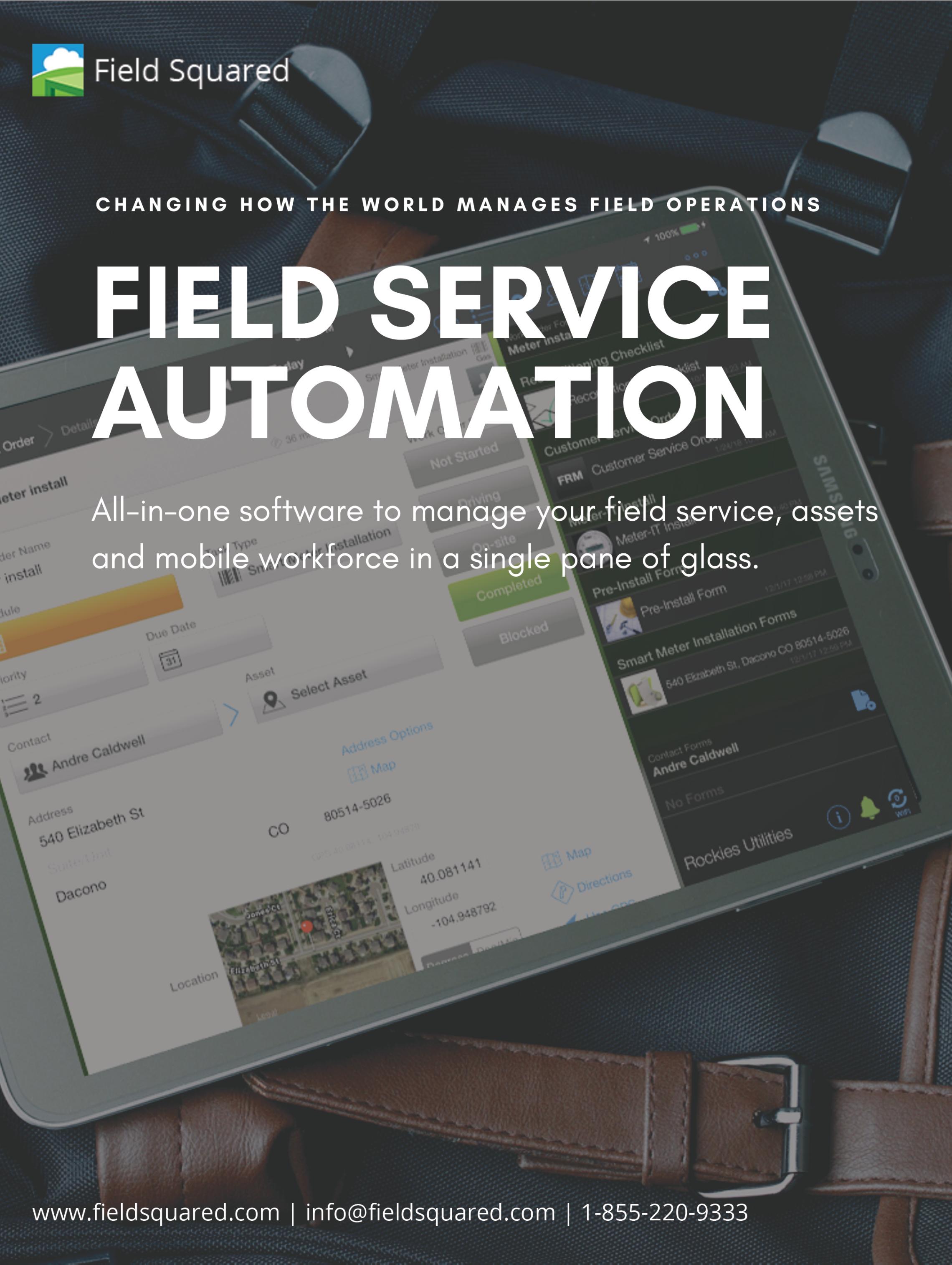
AIDING BUSINESSES SEAMLESSLY IN SECURING THEIR WEB APPLICATIONS
Venkatesh Sundar Founder & Chief Marketing Officer

thastrulybecomeimportantforbusinessestofirst
Iacknowledgetheriskofthreatsbeforeembarkingon anytechnologicaldevelopment.Thisistrueevenmore forsmallerbusinessthanlargerestablishedenterprisethat willdoitforcomplianceandregulatoryrequirements withoutachoice.Itisnotonlyaboutrisk,butalsobuilding trustwiththeircustomerstoshowthattheyaretaking securityandsecuritymeasuresseriouslyandtakingstepsto addressthemproactively
Theunderlyingdifferentiatorbetweennewbusinessand technologicaldevelopmentstodayisthespeedwithwhich businesscantakethemtomarketandtheymustdothis withoutcompromisingsecurity.Toaligntheirinitiatives andtechdevelopment,itisimperativenowmorethanever tomakesecurityacostofdoingbusinessandforany initiative,andpartnerwithexpertstoprovidethoseservices insteadofdoingitallthemselves.
Forthose,whohavekeptsecurityaspriorityarefinding applicationsecurityacomplexproblemandarestruggling tocomprehendit.Itisgivingrisetomanyquestionsintheir mindsuchaswheretostart,whichproductstopick,howto buildtheexpertiseandensuretostayprotected.Withthe visionofenablingbusinesstogodigitalfearlesslywith theirapplications,Indusfacewasincepted.
Thecurrentpandemichascausedahugechangeinbehavior onhowweapproachworkanddigitizationinitiativeshave beengivenarocketfuel.Itisneededforsurvivalandbeing relevantevenmorenow.Thismeansmoreapplication,need formoreonlineservicesandthesecuritythreatsandneed willincrease.
Noteverybodyhastheexpertisetoaddresssecurityand hencepartneringwithvendorswhonotonlyprovidethe technologybutalsotheexpertisetomanageitforthe customersisgoingtobeapressingneedasnewSMB businessstartadoptingdigitizationinitiativesandwillhave aneedforManagedServiceevenmorethanlarge enterprises.Indusfaceisservingwelltothisdireneed.
Thoughintheshortruntherewillbesomepausein spendingasthebusinessthemselvesaregoingthrough toughtimes,inthelongrun,theCOVID-19pandemicled tomoredigitizationinitiativesanditwillcontinuetostay evenafternormalcyisrestored.Thismeanstheneedfor securitywillalsoincreaseinparallel.Accordingtothecore teamofIndusface,cybersecuritymarketitselfisgoingto expandalotmorethanitwasprojectedtobepostthis pandemicera.
ThecompanyhasbeenmentionedintheGartnerMagic QuadrantandForresterTechNowreports,isCERT-In empanelledasatrustedscanningvendor,andhasbeenthe recipientofmanyawardssuchastheEconomicTimesTop 25,NasscomDSCITopSecurityCompanyoftheyear AwardandisfundedbyTataCapitalGrowthFund.
ASaaScompany,Indusfacesecurescriticalweb applicationsof2000plusglobalcustomersusingitsawardwinningplatformthatintegrateswebapplicationscanner, webapplicationfirewall, DDOS/BotAttackmitigation, CDNandthreatinformationenginealongwitha24x7fully managedwebapplicationsecurityservice includedinthe offering.
Indusface’sWASsolutionisafullymanagedriskdetection servicethatenablesbusinessestodoon-demandunlimited automatedsecurityscanningoftheirwebapplications.It providestheminstantvisibilityoftheirsecurityriskand takesaction.
Our promise, though, is very simple – Make it extremely easy for you to secure your Web and Mobile Applications.




Aspartofthesameserviceinapremiumbusiness,canalso requestondemandmanualpenetrationtestingandbusiness logicsecuritycheckstododeeperriskassessment.Thisis backedwitha24x7supportteamtoprovideguidance,proof ofconceptsandevidenceoftheexploitableriskssothat businesscantakequickaction.
Secondly,itsrecentlylaunchedAppTranasolutionisafully managedriskbasedprotectionandwebapplicationfirewall thatincludestheriskdetectioncomponentandalso managedwebapplicationfirewalltoinstantlyfixthose vulnerabilitiesandmitigateriskbackedwitha24x7support teamtoprovideunlimitedupdatestopolicies,customrules. ItisbackedwithazerofalsepositiveguaranteedwithSLA.
Uptosomeextent,changehasoccurredasbusinessesare startingtorealizetheimportanceofsecurity.Venkatesh Sundar,theFounderandChiefMarketingOfficerof Indusface,wishestobringmorechangesinthecyber securityarena.
Whiletalkingaboutmorechangesthatareyettobe witnessed,Venkateshasserts, “Security has become a concern and a boardroom discussion. There is no need to sell the need for security. However, the purchase behaviour is still based on risk mitigation and not productivity enhancement. Now that business has accepted the risk is real and will not go away, for any digitization initiatives the
overall ecosystem can get better, and more secure if the business approach it as efficiency building.”
“By keeping away the attackers, breach attempts, the efficiency of the business improves as the application has to deal only with relevant payloads, logs, metrics and data. It is a shift in thinking and with this thinking, a business can focus more on the positive emotions and benefits and ROI metrics of efficiencies, productivity enhancements by embracing security initiatives as opposed to only the negative emotions of what could go wrong. Another thing I would change is in the ecosystem is more broad and at grassroot levels to make cybersecurity a more integral part of the education system to help develop better future leaders, and professionals and engineers with this skill set.”
Withrespecttosustainingthedifferentiator,Indusfaceaims atapplyingtheKISPrinciple-KeepingitSimple.Its missionistomakeitextremelyeasytosecureweb applicationsforcustomers.Everythingthatitdoeswithin thecompanyhastoconnecttothispromiseofhelping customersstaysecuredwithoutanyeffortorveryminimal effortfromcustomers’sideaftertheypartnerwiththe company
Thus,itsproductdevelopmentandprioritiesarealways mappedtoansweringquestionssuchas-Canithelpdetect risksbetterforcustomerwiththisinitiative?Canithelp protectagainstthoserisksbetterforcustomerwiththis initiative?Andcanitmakesimpleforthecustomer(so simplethatitjustworks,nomatterhowmuchbackend complexitiesonproductandprocessarebuiltaroundit)?
Indusfacebelievesthataslongasitdoesthesethreethings consistently,persistentlyandbuildstherighttalentto deliveronthis,itwillstayaheadofthemarket.
Inupcomingyears,thecompanyseesitselfsecuringa
We want to enable you to go digital fearlessly and help you expand your business without worrying about the security of your applications.
If you are experiencing a security problem with your application, we will be your confidant who will stand beside you till we resolve and secure the application.
millionpluswebandapplicationsandKISforthecustomer andborrowinganotefromAmazonwayofworking.The companywillstillconsideritselftobeindayzeroevenat thatpointoftimeastherewouldstillbeafewmillionmore applicationstosecureusingKISprinciple.
Asthewindofchangeincybersecurityhasarrived,many entrepreneursareaspiringtoventureintothecybersecurity industry Aswithanybusiness,commitmentandchallenges involvedareveryhigh,onemusthavethedrivetoseeit through,believesVenkatesh.Headvisesthosebudding entrepreneurstomakesuretheproblemandneedis identifiedandvettedwithfewbusinesses,andthemarketfit productischeckedbeforebuildingit.
Hesays, “The possibility of virality and new need being created (like tweeting and social networking) is unlikely for a b2b Cyber Security business. Like any business venture it starts with an idea and what you feel is an identification of a need by solving a problem but try to vet the product market fit before building the product is my key advise. Once the need is established also think what is unique about your offering besides just the idea to sustain the uniqueness and be better on a sustainable basis. It most likely will come down to do you have the unique talent with respect to product building, sales relationship and ability to sustain it on a ongoing basis as you embark on this journey.”
“The Risk Based Fully Managed Application Security technology offering from Indusface provided us the best value for money. We signed up with Indusface as not just a technology supplier, but as an application security partner for enabling us to drive more digitization initiatives.”Kiran Belsekar, VP-Info security, Aegon Life
“Indusface has proved to be a valuable security partner with its Total Application Security solution. Their ‘detect-protectmonitor’ package handles security worries so we can focus on improving services for our customers. Vulnerability detection, attack blocking and near real-time reports are some of the key differentiators that we enjoy with them. The web application scanning and web protection combination has ensured that we are protected from highly increasing threat vectors.”Sharad Sadadekar, CISO, HDFC Life
“As one of the leading banks in India, securing application infrastructure is critical for us. Indusface’s Total Application Security package allows us to scan vulnerabilities continuously and prevent attacks. Indusface also provides the unique benefits of expert handling and tuning on custom rules with round-theclock traffic monitoring and protection through on-premise appliances.” - Deval Mazmudar, CISO, IndusInd Bank



CyberSecurityisincreasinglybecomingaparamount aspectpertainingtotheinternet,withtheworld movingtowardsbecomingmoredigital.
Cyberattacksareathreattocriticaldataandpersonal informationandprotectingcompaniesandindividualsfrom suchattacksisthemostessential.
BitNinja,beingthefirstintegratedserverdefensenetwork intheworld,itcombinesthemostpowerfuldefense mechanismandprovidesabroadlevelofprotection.Each protectedservercandetectanddefendagainstawiderange ofserverattacks.“Theserversshareattackinformation witheachother,andthiscollectiveknowledgeofthe defensenetworkmakesBitNinjaaveryefficientandunique solutionagainstCyberattacks,”saysGeorgeEgri,theCoFounderandCEOofBitNinja.
SinceGeorgejoinedBitNinja,hehashadthechanceto provideasolutiontothesecurityproblemsofhundredsof companies,helpthemtoprotectmorethan5million websitesworldwide.
Inthefollowinginterview,Georgesharesvaluableinsights intothecompany’sstrongholdwithintheindustryandhow heplanstosustainitssuccessforthecomingyears.
BelowarethehighlightsoftheinterviewbetweenGeorge EgriandInsightsSuccess:
Giveusabriefoverviewofyourcompany,itsvision,and itsjourneysinceinception.
Alsolistthepopularproducts/solutionsthatmakeyour companystandoutfromthecompetition.
BitNinjagivesultimateprotectionagainstcyberattacksfor webhostingcompanies.OurmissionistomaketheInternet
asaferplace!Wecreatedaneasy-to-use,security-as-aservicedefensetool-namedServerProtection-tosupport thisgoal.Themainpurposeistoprotectserverswithless effortandmaintenancefromtheclients.BitNinjadoesits jobsilentlyinthedark,justlikeaninja.
Westartedasasharedhostingcompany.Wehadmany customercomplaintsbecauseofthelackofcybersecurity, sowebegantosearchforatoolthatpreventseverytypeof cyberattacks.Wefoundtoolsthatofferasolutionfora certainkindofattack,andwealsoshouldhavesync betweenthedifferentsoftware,whichprovedtoo complicated.Therefore,wedecidedtodevelopourown cybersecuritytool.
Whenwehadtheproduct,thencametheideathatwe shouldtrytosellitonthemarket.Thedemandwassohigh thatwedecidedtofocusmostofourresourcingon BitNinja.Thatishowitallstartedandtilltoday,weprotect serversfrom80countries,defendmorethan4million websitesworldwideandwehavealreadyblocked40+ millionHTTPattacks.
Thankstoourcrowdsourcingmethod,wehave10+million IPaddressesonourreputationlist.Our(patentpending) SourceCodeStructureAnalysistechniqueisuniqueonthe market.Itsmalwaresignaturedatabasealsousesthesame crowdsourcingmethodasourIPreputationsystem.
WefocusonbotnetsformedbyinfectedLinuxservers. Server-basedbotnetsareespeciallyvaluableforthebad guysasservershavetypicallyhighamountsofvarious resourceslikeCPU,memory,andthemostimportant, internetbandwidthwithtrustedand,inmanycases unrestricteduploadtrafficcapacity.Serverstypically operate24/7andhaveatleastonefixedIPaddress.Inmany cases,serversalreadyhaveeverycomponentforhackersto operate.
Thereisahugedemandforhigh-capacitybotnetsinthe darkmarketsfordifferentpurposeslikesendingspam, differentDoSattacks,andsimilarcybercrimes.Thereare moreandmorebotnetinfectionsthatservershavetoface.
BitNinja users can protect their server like a pro sysadmin without the need of supervising the service.
“ “
Thisisthereasonwhywedecidedtospecializeinbotnets.
Astheco-founderandCEO,whatisyouropiniononthe impactofthecurrentpandemicontheCyberSecurity industryingeneral?
Cybersecuritybecamemoreimportantyearbyyear A milestonewasin2016whenthestricterGDPRruleswere introducedintheEU.In2017criticalransomwares,suchas theNotPetyawerediscoveredandinthatyearalso appearedthefirstransomworm.Theseareunimportant happeningscomparedtotheCovid-19.
Morepeoplestartedtobuyonlinewhichcanbeagreat opportunityforhackerstostealcreditcardcredentials.
Morepeopleworkremotelywhichisagoodoccasionfor thebadguystofindavulnerabilityandbreakintoa company’sdatabase.Anddon’tthinkthatthetargetsare onlybigcompanies.Morethanhalfofthetargetedattacks happentoSMBbusinesses.Theinternettrafficgrewrapidly thisyear
Moretrafficequalsmorevulnerabilitiesandopportunities. That’showhackersthink.Ibelieve2020isthemost importantyearinCybersecurityandalsothebeginningofa newerainthedigitalworld.Itisnotacoincidencethat companiesandevengovernmentsstartedtospendmuch moremoneyonCybersecurity.
Asanestablishedbusinessleader,whatwouldbeyour advicetothebuddingentrepreneursaspiringtoventure intotheCyberSecurityindustry? Itisthelastchancetostartit,sodoitnow!
Howdoyouenvisiononsustainingyourcompany’s competencyinthisevercutthroatandvolatileworldof business?Wheredoyouseeyourcompanyinthenext fiveyears?
Inthisregion,therearealotofwell-qualifiedprofessionals. HungarianprogrammersareintheTop5intheworld!So,I predicttheprogrammingpartofthejobwillgosmoothly Andifyourproductisbetterthantheotherdepartments, suchasthesalesorthemarketingteam,haveaneasierjob.
Furthermore,wehirepeoplewhosecharacteristics matchingourcorevalues.Webelievethatthecombination ofthesecharacteristicswithagreatproductdoesnotjust leadtoasustainablecompanybuttoasuccessfulone.Inthe future,wewillopenanofficeintheUSA,andweare planningtoraisetheSeriesBroundinthenexttwoyears. AndasImentionedbefore,wewilllaunchsomenew productstoo.
“Before we started using BitNinja, we had major problems, like overall load went up during the attacks, we faced password hacks and PHP code injections. But with BitNinja, we experienced major positive changes: less hacks and reduced overall load on the servers ” — Ganesh Hosting
“Bitninja provided us with a complex solution that wasn’t provided by others and changes after applying a solution, reduced the load on systems and engineers significantly”
“The Dashboard and its GUI is great. Its practical style helps decision-makers in order to understand each aspect of the software and the volume and diversity of threats posed to their servers.” — Insomnia
 George Egri Co-founder, and CEO
George Egri Co-founder, and CEO
There was a time in the world of jet fighter avionics when even the most advanced of countries had aircrafts with radars that were to be operated manually. What it meant was that a pilot besides doing keeping the aircraft flying and chasing enemies while under pressure, was also responsible for operating the radar and trying to detect enemy aircrafts and missiles.
Besides making the job cumbersome and tedious, it left a lot many gaps through which enemies could take down the best jet fighters. That was till the Russians designed a radar that took care of the scanning electronically. Security and gaps were reduced drastically, and the pilot and co-pilots could do much, much more!
Speaking of gaps in security, things on the ground too seem to be taking the same line in the cyberworld. In the present what we come across as
security is essentially the yester-years’ anti-virus packages stuffed with humongous details of every type of cyber threat. With precious little ability to detect anomalies beyond a certain band, what the world awaits fervently are AI & ML-backed cyber security systems. We tell you how the latter matches up to all the threats in the cyberworld!

1. It can identify and neutralize existing threats with inputs from previous cases & using its neural networks, bring forth the right solutions from any number of options.
2. If the threat is new, it can, given its ability to read thru and analyse vast amounts of data, pick up each characteristics of the threat as also how best to handle them with existing resources within the organization that could be part machine, part human endeavour.

3. Pitting machines against machines. Bots can do lots, harm included. And the best way to handle them is to get a super-bot, an AI & ML-assisted bot which can match the bot, act for act and help either avoid it completely or help take it apart with the right resources. Number-crunching being a machine-forte, AI-assisted bots can scan the horizon practically on a daily basis to discover and neutralize bots.
4. Pitting machines against the worst that human can do! Bots as a threat are entirely different from those launched by malicious human intent. Nevertheless, both are designed to harm human interests. Like a game of chess where outwitting the adversary is a necessity to survive with every move, even in the game of survival in the cyberworld, the AI’s legendary ability (including defeating Grand-Masters of Chess!) to outwit both bots and humans can come in handy.
5. Signature-protection employed by antiviruses not a patch over end-point protection employed by AI! The former works on a finite set of tell-tale signatures of viruses and other cyber-threat including ransomware. A slight delay in updating by means of a virus patch is all that is needed to bring down a system that is protected by an antivirus package. And delays in patches or dated packages themselves aren’t anything new in the world of antivirus packages! Compare this with a system mimicking nature-based neural networks that continually update themselves and you see the obvious advantage that a AI-backed and ML-assisted system has.
6. Do you bolt the stable door before or after the horse has bolted? Continuing from the above, despite the likely higher initial costs in the case of AI, the protection it provides could offset the likely costs a system may have to incur where a threat manifests itself and besides decapitating it, needs sever cleaning up. Summing up, the cyber world today has threats, to which the only answer is a system that self-adjusts and proactively takes steps instead of restricting its actions along known and predictable lines.
7. Securing data where users work from remote locations. Phishing in the times of work-from-home is a form of cyber-security threat that is increasingly gaining foot-hold, given the physical distance and the likelihood of employees not knowing the difference between the authentic and the fraud. Be it emails, SMSs or through other forms, Phishing is increasingly getting sophisticated and difficult to identify. This leaves the
gates wide open for a system that has the ability to read a threat in its entirety from head to toe against vast amounts of information that it captures on its own in the process of scanning for threat. Neural networks, central to any AI-assisted security system can adjust its sights to catch the best and most pernicious of phishing threats and do so continually without the need for constant updates. Zero-day threats thus aren’t so with AI given its constantly evolving learning methodologies and data-base!
8. With cybercrimes becoming increasingly sophisticated, their response can quite often slowdown the best of IT infrastructure given the size of the response, and the resources they consume. AI-assisted cyber-security system with its human-like ability to read the level of resources available, can adjust itself while still keeping its sights trained on the threat despite having to go through humongous quantities of data and scenarios.
With some much in favour of them, can ML and its most known outcome, AI be called THE panacea for all cybersecurity issues? If experts and recent experiences are anything to go by, they could be a far cry at the moment, and primarily for two reasons:

- It’s used these days to mean a very rudimentary form of machine-learning with algorithms that make it narrow and weak. Narrow as they tread a single narrow path which sees them crunching data for a single domain, even though the data itself may be vast in volumes. This is far, far from what a strong AI can be expected to do including treading, surveying, and investigating across multiple domains, and answering questions authoritatively besides fielding solid security systems.
- AI works on data, and like everything where there’s a direct correlation between input and output, it’s the quality of data which finally determines the ability of the system to pinpoint trends, patterns and tell-tale signs. Most information either may not have the right information in the right quantities or could have them in formats that make them anything but useful for machine learning. In the absence of these, it could only be hype and precious little beyond.
OutThink is a revolutionary Human Risk Management Platform (SaaS) empowering CISOs by targeting the source of 90% of all data breaches: human behaviour.
bringstheworld'sfirsthumanriskmanagementplatform. Aninnovative,disruptivesolution,OutThinkisthe revolutionoftraditionalsecurityawarenesstraining.Used byFTSE100organisations,theOutThinkplatform(cloudSaaS)hasbeendevelopedspecificallytoidentify,measure humanriskandaffectbehaviourchange.
Withtheorganizationsadoptingmoreofdigital technology,cyber-securityattacksare constantlyontherise.Manyorganizationsand cybersecurityanalystsareoverwhelmedtodayduetodata breachattacks,analysingsecuritylogs,investigating potentialfraudattemptsandmore.Therefore,all organizationshavetheessentialneedtoimproveendpoint securityandresilience,reducefraudulenttransactions, protectprivilegedaccesscredentials,andsecuremost importantinformationetc.Utilizationofappropriate technologiesandinnovationsincybersecurityare necessarytorespondtocyberthreats.
OutThinkisaLondon-basedcompany,recognisedglobally forinnovationincybersecurity.OutThinkwassetupin 2015byateamoffourCISOs,human-centredsecurity professors,andresearchersfromRuhr-UniversityBochum, UCL,andRoyalHolloway,UniversityofLondon.
OutThinkFounderandCEO,FlaviusPlesubringstwo decadesofexperienceinseniorsecurityroleswhich inspiredtheorganizationtodeveloptheworld'sfirsthuman riskmanagementplatform(SaaS),acybersecuritysolution ‘byCISOs,forCISOs’.
AsaformerCISO,Flaviushasledcomplexcybersecurity transformationprogrammesacrosslarge,global organisations.Itishispassionforsecuritythatmotivated FlaviustochallengethestatusquoandstartOutThink,to solvethepeoplechallenge.OutThinkleveragesML (MachineLearning)andNLP(NaturalLanguage Processing)approachestogaindeepinsightaboutspecific individuals'/groups’attitudesandbehaviours.OutThink
InaninterviewwithInsightsSuccess,FlaviusPlesushares thejourneyofOutThinkanditscontributioninensuring cybersecurity
Giveusabriefoverviewofyourcompanyandpleaselist thepopularproducts/solutionsthatmakeyourcompany standoutfromthecompetition.
TheOutThinkteamincludesexpertsincybersecurity, cognitivepsychology,datascience,engineering,and softwaredevelopment.
OutThinkProducts:
AdaptiveSecurityAwarenessTraining
PhishingSimulations

HumanRiskIntelligence
PredictiveHumanRiskModels
AstheFounderandCEO,whatisyouropiniononthe impactofthecurrentpandemicontheCyberSecurity industryingeneral?
TheCOVID-19pandemichasforcedorganisationsand individualstoembracenewpracticessuchassocial distancingandremoteworking.Whiletheworldisfocused ontheeconomicthreatsposedbyCOVID-19, cybercriminalsaroundtheworldunquestionablyare capitalizingonthiscrisis.Therehasbeenaspikein phishingandransomwareattacksashackersareusing
COVID-19asbaittoimpersonatepublicorganisations, therebymisleadingpeople.Notonlyarebusinessesbeing targeted,butend-usersarebeingtrickedintodownloading illegitimateCOVID-19relatedapplicationsandgranting themexcessiveprivileges.
Inyouropinion,whatcouldbethefutureoftheCyber SecurityindustryposttheCOVID-19pandemic?And howareyoualigningyourcompanywiththat prospectivefuture.
TheCOVID-19pandemichascausedenormouspressure, throwingtheglobaleconomyintoarecession.Some organisationsmightconsiderdownsizingbycuttingdown onbusinesslinesconsideredas"non-critical"whichmay includecybersecurityservices.Thisshort-termplanmight howeverprovetobe“pennywiseandpoundfoolish”inthe longhaul,asthiswillfurtherincreasetheimpactofattacks ontheorganizations.
Asanestablishedbusinesleader,whatwouldbeyour advicetothebuddingentrepreneursaspiringtoventure intotheCyberSecurityindustry?
Buildyourproductwiththecustomerinmind,youmust knowyourcustomerandwhattheytrulywant.Itsounds obvious,butitisfarfromtrivial.MycustomeristheCISO. IdevelopedtheinitialOutThinkproductwiththreeother CISOs,whichmeansthatoursolutionisbuiltforCISOs,by CISOs.Whenspeakingtocustomers,theyreallylikeit, becauseitissomethingtheyreallyneed,itissolvingabig problemforthem,inaninnovativeway.Ifcustomersdonot absolutelyloveit,youwillstruggleandhavelimited opportunityforgrowth.
ThesecondpieceofadviceIwouldgiveistobuildanew category.Youwillmostlikelybeenteringintoamarketthat isalreadydominatedbybigplayers–atfirst,youwillbea smallfishinabigpond,butwhenyoustartyourown categoryyoucanbethesharkinanentirelyfreshpond.
Read“PlayBigger:HowPirates,Dreamers,andInnovators CreateandDominateMarkets.”
Finally,trytohavesomefunalongtheway.Beingthe FounderandCEOisreallycool!
Howdoyouenvisiononsustainingyourcompany’s competencyinthisevercutthroatandvolatileworldof business?Wheredoyouseeyourcompanyinthenext fiveyears?
OutThinkasacompanyisentirelyfocusedonitshuman riskmanagementplatform;itsfurtherdevelopmentand continuousinnovationisourprimarymissionforthenext twoyears.Ourstrategyistorevolutionisecybersecurity trainingandthebroadercybersecuritysector,bypursuing trulyindividualisedtraining.Wewillfocusondeveloping anddeliveringatop-qualityproductwhichinreturnwill makethecompanysustainable.
“OutThink is helping me understand human risk factors across the business, empowering my team to design targeted responses” - Head of Security Awareness, Global Telco
“I love OutThink; it gives me new insight into the Human Factor, allowing my team to engineer the right processes and equip people to follow them” - Global CISO, FTSE100 Organisation
 Flavius Plesu Founder and CEO
Flavius Plesu Founder and CEO



Usheringintoanerapredominatedbyremote workingandtheincreasinglyredundantuseof commercialsecurityinfrastructure,companies acrosstheworldfaceimminentthreatspertainingto cybersecurity.
Tacklingthesethreatshastakenprimeimportanceonthe dailytasklistsofCSOsandcybersecurityprofessionals. Derivingcomprehensivesolutionsandintelligentdefence systemsagainstthesethreatsiswhatcompaniesworkingin thecybersecurityspacearestrivingtoachieve.
Oneprominentnameamongsuchcompaniesis QuintessenceLabs,headquarteredinCanberra,Australia. QuintessenceLabshasaneclecticfoundingstory.Having runinformationtechnologybusinessesinCanberrafor manyyears,FounderandCEODrVikramSharmatook theopportunityintheearly2000’stojointheSloan ProgramatStanfordUniversityintheUS.Duringhistime there,hewasableattendafewphysicsclasseswherehe wasabletolearnofthehugeprogressbeingmadeinthe realmofquantumtechnology.
Buildingonthatknowledge,theapplicationofquantum sciencethatreallycapturedVikram’sattentionwasquantum cybersecurity,forwhichhesawmajorsocietalbenefitsand abusinessopportunity
Hesawthatquantumcybersecurityhadthepotentialto protectdatafromthisnewthreatofquantumcomputing, somethingthatwassoongoingtobeneededonaglobal scale.DrVikramlaterreturnedtoAustraliatoworkon ground-breakingresearchwiththeQuantumOpticsGroup intheDepartmentofPhysicsandgainhisPh.D.inquantum physicsintheprocess.
QuintessenceLabsemergedin2008fromthisworld-leading research,withamissionto Secure the world using Quantum Innovation.Thecompanyisnowagloballeaderin commercialquantumcybersecuritysolutions.Itsproduct suiteleveragesadvancedquantumsciencecoupledwith leading-edgecybersecuritydataprotectionsoftwareto deliverhigh-value,highlysecurequantumcybersecurity solutions.Thesesolutionsalloworganizationstoprotect theirinformationagainstthemostadvancedthreats, includingthosefromquantumcomputers.
Keyelementsofthecompany’stechnologyinclude:
qStream–theworld’sfastesttruerandomnumber generator
TrustedSecurityFoundation(TSF) deliveringa highlycapableandcrypto-agilekeyandpolicy managementoffering.
qOptica–advancedkeydistributionleveraging quantumeffectstoultra-securelyexchangeencryption keys.
qClient–interoperablesoftwaredevelopmentkits (SDK)tosupportswiftandseamlesswithexisting infrastructureandapplications.
OtherproductsincludeqSecure,asecurework-from-home solution,andqProtectvirtualzeroizationcapabilityto securedatainvulnerablelocations.
CustomersusingQuintessenceLabs’solutionsinclude financial,cloudstorage,aerospace,governmentanddefense organizationsseekingtoenhanceprotectionofvaluable informationassets,todayandinthefuture. Thecompany’scapabilitieshavebeenrecognizedthrough severalawards,includingtheonebytheWorldEconomic Forum,thatnamedthecompanyaTechnologyPioneerin 2018andaGlobalInnovatorin2020.
WeaskedDrVikramonhisopinionregardingtheimpactof thecurrentpandemicontheCyberSecurityindustry,to whichhesaid,“Aclearconsequenceofthepandemicisthat manymorepeoplehavebeenworkinginremotelocations thanonecouldhaveimaginedjustashortyearago.Aslarge sectionsoftheworkforcehavemovedtoworkingoutside traditionalorganizationalboundaries,thethreatsurfacefor sensitiveinformationhasexpandeddramaticallypresenting arangeofnovelcybersecuritychallenges.”
“Manyorganizationshavebeenstrugglingtoimplement solutionsandsystemstosupportsecureinformation exchangewithoutimpactingproductivity.Inresponseto thisurgentneed,QuintessenceLabsisrollingoutthe qSecureWork-from-Homecapabilitywhichdeliversrobust dataprotectionthatseamlesslyintegrateswithexisting infrastructureandapplicationswhilehavingaminimal impactonuserexperience,”headds.

Inhisadvicetothebuddingentrepreneursaspiringto ventureintotheCyberSecurityindustry,DrVikramsays, “Cybersecuritysectoriscertainlyadynamiconewith significantyear-on-yeargrowthforecastoveratleastthe nextdecade.Thatbeingsaid,itisalsoahighlycompetitive market,andthereforeyoumustbeabletoclearlyarticulate yourcustomervaluepropositionandidentifydifferentiators andcompetitiveadvantages.”
Aswithanystart-upventure,asanentrepreneuryoumust havestrongbeliefinyourvisionandbecommittedto seeingyourideamaturethroughtoasuccessfuloutcome (howeveryouchoosetodefinesuccess)–thiswillsustain andmotivateyouthroughtherollercoasterjourneythat mostnewventuresexperience,”heconcludes.
InnovationisintheDNAofQuintessenceLabs’cultureand embracedbyeverymemberoftheteam.Thecompany investsheavilyincontinuousR&Dandpartnerswith severaloftheleadingresearchinstitutionsinthefieldof quantumsciencetoensurethatitstechnologyandsolutions benefitcustomersthroughthetranslationoffrontier-ofscienceresearch.
Infiveyears,itisexpectedthatquantumcybersecuritywill becomemainstreamandwillbeoneofthecriticalpillarsof arobustcybersecuritystrategyformostorganizations.In thiscontext,QuintessenceLabsisprimedtodeliverglobal leadershipinsupportingcustomersachievearesilient quantum-safecybersecuritypostureinacomplexcyber threatenvironment.
“With QLabs, we have been able to strengthen our security services, integrating their quantum random number generator and key manager into our cloud storage architecture.”
– Josh Baxter, President of NetDocuments. “The ability of QLabs’ qCrypt to deliver high-speed, true random numbers, combined with PKWARE’s Smartcrypt data security platform, provides stronger-thanindustry-standard data protection and allows customers to stay ahead of increasingly sophisticated cyber-attacks.”
– Matt Little, Chief Product Ofcer, PKWARE
“QuintessenceLabs and its fellow pioneers are front and center in shaping the ongoing Fourth Industrial Revolution and we believe they will be transforming society and industry in a positive way in the years to come.”
Fulvia Montresor, Head of Technology
are pleased that QLabs’ qCrypt qualifies for the VMware Ready™ logo. This signifies to customers that qCrypt can be deployed in production environments with confidence and can speed time to value within customer environments.”
Kristen Edwards, Director Technology
Partner Program, VMware


ybersecuritywasalwaysanissue,evenbeforethe
CpresentCovid-19pandemicandtheresultantworkfrom-homeenvironment.Ifearlieritwasabout securingdata&informationatspecificlocationscalled offices(besidesaselectfewwhoworkedfromhome)from clearexternalthreats,thewholesalework-fromenvironmenthaschancedthedynamicsbystretchingthe securityaspecttoincludeunmarkedremoteplaceswhere employeesandassociateslive,andthesedaysworkfrom.
Onthetopicofwhobenefitsbypilferingdatatootherehas beenamarkedshift.Ifearliertheyconstitutedunseen externals,thesedaystheycouldbeanorganization’sown employeesandassociatessecuringtheirinterestsby copyingandstoringcrucialproprietaryinformationintime whenjobsarehardtocomeby.
Followinghavebeensomeoftherecenttrendsintheworld ofcybersecuritywhenseenfromtheprismoftheCovid-19 pandemic.
Ÿ
Theissueofdatasecurityhasmovedfromthe confinesofofficestowhere-everjob-relateddatatravels, beithomesorotherremotelocations.Withalmostall organizationsnowfunctioningwithemployeesworking fromhome,thecyberworldpresentsthenewfrontierin thefighttosecuredata,beitrelatedtoproprietary technology,finance,employeeinformationorcustomer relateddetails.Unsurprisingly,physicalviolence, pilfering,theft,robbery,streetmuggingetchavegone downdrasticallywiththeadventofstrictsocial distancingnormsinpracticallyeverycountrywhich seeslesspeopleoutintheopen.
 The Achilles’ Heel
The Achilles’ Heel
Theconceptofwork-from-homeandincreasinguse ofAIandroboticsinindustryworldwideisamixed outcomeofCovid-19whichputsfurtherpressureon datasecurityandstorage.Thecloudisanoptionthought theissueofdatasecurityremains.
Ÿ Movingoutofdefinedofficespacesandusingthe internettodoone’sofficeworkpresentsanewleveland kindofdata-securitythreat.Itisheightenedbythefact thatproprietarydatacannotalwaysbesecuredonthe internet,despitethebestsystems.
Ÿ Withmosthomesoperatingwithbroadband connectionwhoseconfigurationdoesnotcomparewith corporateones,worksometimesdrawstoacrawl. Besides,theabsenceofdedicatedcorporatefirewalls wouldmeansemployeesareperenniallyopentocyber snooping,phishingandhijacking.Theirnumbersinfact haveshownamarkedspikesincetheCovid-19crisis.
Ÿ Withwork-from-homebeinganormtodayratherthan anexception,mostorganizationsruntheriskofinsiders ieemployeesandassociatesthemselvescopying, pilfering,storingandsharingproprietaryandhigh-value informationtothedetrimentoftheformer.
Theeventthatcausedthebiggestchangeintheoffice-work thscenariosincethe19 centuryIndustrialRevolution,the Covid-19pandemicbroughtchangewithsuchspeedand alacritythathumanitydidn’thaveachancetoexpressits likes,dislikesandreservations.Whatseemedanextended, andinsomecases,paidholidayquicklyturnedintoan overburdened,boringeventwithmostemployeesrealizing thatofficecommute,banter,meetingandinteractionswere partofanexcitingandinterestingphenomenonthatmade workproductive,funandfulsome.
WithrealizationdawningthattheCovid-19pandemic wasn’tdesigned(byintentorotherwise)toendsoon,and thelikelihoodofavaccinebeingsomedistance, GovernmentsandEmployees,andtheirrepresentativeaided byhumongousdatanowavailableonlineoneveryaspectof thepandemicseemtocometosomeconclusionsonhowto tacklethemenacewhilekeepingthewheelsofeconomies moving,andmostimportantlykeepinghomeandhearth functionalforthelargestproportionofhumanity worldwide.Someofthemeasuresbeingdiscussedinclude:
1 Useofsecuresystemsonthecloud.Thecloudasan institutionisonethathasgiventoindustry,commerce andgenerallyallmannerofhumanendeavourthe freedomtooperatefromanywhereontheplanetwhile stillhavingdatasafeandsecureatacentrallocation. That,andthepresenceofthebestITinfrastructureinthe formofcomputers,smartphone,printer-cum-scanner, video-conferencingplatforms,CRMs,andlastandnot certainlytheleastsupersafeandreliableinternet
connection(ifpossible,aVPN)couldpossibleevendo awaywiththeneedforanofficeinthefuture-provided itdoesnotcomewithhidden,unforeseencostslikelow employeemorale,burnout,compromisewithdata securityetc.
2 Trainingemployeesonthehardstuff.Movingthings tothecloudmeansonething:trainingemployeeson mattersrelatingtoinput,retrievalandusedatawhile keepingthingsalwayssecure.Thatbesides,employees wouldhavetobetrainedtousevariedmeansof connectivitygiventhatcyberconnectivityisessential forworking,andoneofeasiesttolose.CodeofConduct andPolicieswouldhavetobedrilledinhardsotoothe meritsanddemeritsofnotfollowingestablishedand approvedpractices.
3 Upgradeandupdatecyber-securitysystems.Itisthe essentialdifferencebetweenprovidingsecuritytoa buildingandallitsresidentsvsprovidingsecuritytoall theresidents-betheywithinoroutsidethebuilding. Work-from-homestretchesanycyber-securitysystemto itswidestgiventhattheusers(employeesinthiscase) mustsomewhereintheirworking,accessestheopen internettoaccesstheirworkincludingthoseonthe cloud.Whilemostcompaniesgivingemployees accessestothecloudarenotataloss,thoseaccessing legacysystemscouldbe.
4 Checkatregularintervalssecuritymeasuresof outsourcedITservicesandinfrastructureincluding thoseonthecloudforeffectiveness,bugsandthelatter’s owncyber-securityarrangements,especiallywith respecttothelatestthreats.

5 Check(andrecheck)theorganization’ssystemsand capabilitiestorecoverfromadebilitatingcyber attackbyplayingoutreal-lifescenariosandmapping theoutcomesforcorrectionsandpluggingofloopholes.
Itisonlybytakingprecautionsincludingthosestatedabove thatorganizationscanbeexpectedwithadegreeof assurancetosecuredataandinformationalwaysremains safeandplacewhileemployeesworkfromanywhereonthe planet.
Intheend,thereremainsonlyoneparadigminthecaseof cybersecurity.Continuousandrelentlesssurveillance.
- M Purushoutham

organizations.Theideawastoenablebusinessesthrough providingwingsofknowledgeandexpertise.
Consultingbusinesshasgrownmulti-foldinthepast fewyears.Itsgrowthprospectushasshotupdueto theincreasingneedofbusinessestoavailright guidancewhenitcomestooptimumutilizationoftheir resources.Financialandtechnologicalresourceallocation hasturnedouttobetheprimeconcernsfororganizations. Hence,consultancyintheseverticalshasbecometheneed ofthehour.
Evenmoreso,varioustechnologicalinnovationshave pushedmanybusinessestoadaptdigitizationandits ancillaryservicestoyieldmaximumbenefitfortheir organization.TechnologysegmentslikeAI,Machinelearning,IoT,Cloud,Automation,andmanyothershave givenbirthtothedemandforappropriateguidancein adoptingthesewithapttechnologicalsolutionfor generatingmaximumROIforcompanies.
Oneoftheleadingcompanies,leveragingthisgrowth opportunityinthemarketisWings2iITSolutionsPvt. Ltd.Thecompany’sManagingDirectorandPrincipal Consultant–VinodKumarAgrasala,intheexclusive Interview with Insights Success, shedssomelightonthe dynamicoperationsofWings2i.Let’sdive-intoseewhathe hastosay:
Giveusabriefoverviewofyourcompany,itsvision,and itsjourneysinceinception.Pleaselistthepopular products/solutionsthatmakeyourcompanystandout fromthecompetition.
Vinod: Wings2iwasfoundedwithakeyaimofbeing amongthemosttrustedknowledgepartnersforglobal
Making‘PremiumKnowledgeServicesavailablefor non-premiumprices’toourglobalcustomers,especiallythe SMEsegmentshasbeenourprimaryobjective.Our flexible,andcustomizableserviceofferings,andour willingnesstogothatextramiletosatisfythebusiness prioritiesofourclients,havegainedusthepositionthatwe areenjoyinginthemarket.
Asthefounder/CEO/Director,whatisyouropinionon theimpactofthecurrentpandemicontheCyber Securityindustryingeneral?
Vinod: Thecurrentpandemichasbroughtinandcontinue tobringinparadigmshiftinthinkingofbusinessleaders,in termsofbusinessdeliveryandoperation.Thiscouldleadto far-fetchingchanginginstrategyandtacticsofbusiness organizations.
Remoteworking,whichstartedmorelikeaforcemajeure conditionhasalreadyturnedintoanewnormalcyformany organizations,thoughmostofthemstillconsiderthatasa ‘medium-term’workaround.Iwillnotbesurprisedifmany organizations,especiallytheSMEsandnewage organizationsfindthistobeamuchmoreefficientandlean wayofrunningthebusiness.
Whiletheexponentialadvancementincybertechnologies includingcloudhasenabledorganizationstomakethis transitionmuchmoreseam-lessthanwhatitcouldhave beenotherwise.
However,italsobringsinnewerkindofrisksand associatedimpacts.Itbringsinshiftinthewayrisks, includingtherisksrelatedtodatasecurityoforganizations arepanningouttobe. Itisforcingtheriskmanagersand riskconsultantstorethinkandre-structurethewayone looksatinformationsecurityandotherrelatedrisks
We have grown organically, and we are targeting the same in the near future too.
“ “
Oneexampleisthesignificantshiftofrisk-focusfrom corporateinfrastructure,physicalandnetworksecurityetc, toriskrelatedtoprotectionofend-usersystems,remote access,cloudsecurityandsoon.
ButasImentioned,whatseemedtobeaquitspeedy advancementintechnologyearlier,hasturnedouttobea hugereliefandblessingfororganizations–andofcourse, theriskmanagementdomainsarealsomoreorlessbetter preparedforsuchscenarios.
Inyouropinion,whatcouldbethefutureoftheCyber SecurityindustryposttheCOVID-19pandemic?And howareyoualigningyourcompanywiththat prospectivefuture.Asanestablishedbusinesleader, whatwouldbeyouradvicetothebudding entrepreneursaspiringtoventureintotheCyber Securityindustry?
Vinod: Onthelargerpicture,thedomainisgoingtobethe same:identifyingandmanagingtherisksrelatedtothe informationassetsofthebusinessesinaproactiveandcosteffectivemanner

Thatisnotgoingtochangeatall.Whatchangesistheway thecriticalityoftheassetsis,whattherisksaffectingthem are,andwhataretheprotectionmeasuresare.
Tobeclear,thiswouldhavebeenawayofworkingina littlefartherfuture,withoutthepandemicalso,inmyview. Whatthepandemicsituationdid,istofastentheprocess, andthatmadeitlooklikeforcedresponse.Ofcourse,many organizationswerecaughtoff-guardandtheyhavebeen impacted.Iamnotunderminingthatfact.
Thekeydifferenceisthesuddenshiftinfocusthatis requiredintermsofassetsandtechnologiesinfocus.And theprofessionalsintheriskmanagementareaareexpected togearupintermsofskillsandknowledgequickly,ifnot alreadydone.
We,asanorganizationarealsointhesameboat.Wehave beengearingupforthoseareasoftechnologyframeworks otherwisealso,andthatishelpingalot.
Remotedeliveryofserviceshasbeenapartandparcelof ourdeliverymodel,andhenceithasnotimpactedusmuch.
Myadvicetoanybusinessleaderinthisspace,including myself,istobehorizontalasmuchaspossible,andfocus ontheprocessandframeworkofRiskmanagementmuch
more,thanthespecializationonspecificdomainand informationtechnology Weneedthoseexpertise,definitely –buttherateofchangeinthosearemuchhigherthanever before,andanylargeinvestmentonspecifictechnologyor domainbeyondwhatisnecessarycankeepyoutiedonto thatandmakeyourorganization’sinertiatowardschanging businessconditionslarger!
Howdoyouenvisiononsustainingyourcompany’s competencyinthisevercutthroatandvolatileworldof business?Wheredoyouseeyourcompanyinthenext fiveyears?
Vinod: Quitefrankly,Idon’tthinkwedidanything significantlyradicalintermsofbusinessstrategyortactics thanstickingtothebasicsofourvisionandvalues.We focusedonthekeyaspectofbeing‘thetrustedknowledge Partner’muchmorethananyotheraspectssuchasrevenue orgrowth.Growthandfinancialnumbershaveneverbeena drivingfactorforus.Especially,consideringtheeconomic andbusinessscenariosaroundthecurrentsituation,our focusisverymuchonsustainingthebusinessandour naturalprogressasmuchasimpact.
Vinod Kumar Agrasala Managing Director & Principal Consultant

