









Internethascreatedavirtualparadisewecannotlivewithout.Thestatementmaysoundlittleglorified
butitisanunwaveringfact.WethepeopleuseplatformslikeFacebooktofindandmakeafriend, LinkedIntofindajob,Emailserviceprovidersforbusinessandothersocialmediaforevenbasic communicationpurposes.Wehavecomesofarthatwekeepanonlineassistanttoperformourregular dutiesoreventodecideourdailyroutine.Anyonecanwitnessthestridethatinternethasbrought.Hence, inthesocialtimeswherepeopleareidentifiedbytheironlinepresence,thesecurityofthepersonal informationisthemostimportantconcern.
Everyoneisawareoftheconceptofidentitytheft,butnotwiththepossibleconsequencesandtheirgrieve nature.Thethreathasknockedourdoorsalready.Takealookatthesituationofaninnocentteenagerusing Facebook,whofellinlovewithagirl,hedoesn’tevenrecognize.Hewasblackmailedtopay10,000 dollars.Even,theIndiangirlwenttomeetherTinderboyfriendandlostherlife.Ifanidentityofa teenagerisatthestakewhatisyou’rethoughtontheconditionofchiefpersonnellikeaPresidentof countryoraCEOofafortune500organization?Thethreatsaregettingbiggerandbitter.Risingconcerns regardingdarkwebincludingonlineterrorismactivities,cyberbullyingandchildpornographyaremaking thewayofonlinesecuritytougherthanever.
However,onlineplatformsarefightinghardwiththeissuesbutevidentlyeverythingisnotundertheir control.Withbillionsofvolatileandunassumingusersonline,adesiretocontroleveryactivityorassuring itssecuritylookslikeadreaminbed.Keepingasimplepasswordoroptionslikesignintoidentifythe userarenotgoingtohelpifthereisnoorganizedsystemofskilledprofessionalstoeattherock.
Ifthelastthreehundredwordshavemadeyouconscious,andhasleftyouinadilemma,hereiswhat InsightsSuccesshasinstoreforyou.Adistinctivelist,The10MostTrustedIdentityandAccess ManagementSolutionProviders,2018comprisingoneofthemostrecommendedidentityand accessmanagementsolutionprovidersintheworld,whoareensuringthemanagementandsecurity ofyouridentity.Theyareprovenleaderswiththeteamofexpertswhocancreateaguardingfence aroundtheidentityofitsassociatesthatcannotbecrossedeasily.Soundslittleclichédorpoetic, right?Ifyoudon’tbelievemethenstartflippingthepagesandallowusunleashtheircapabilitiesof theenlistedcompanies.Iamsuretheyarewortharead.
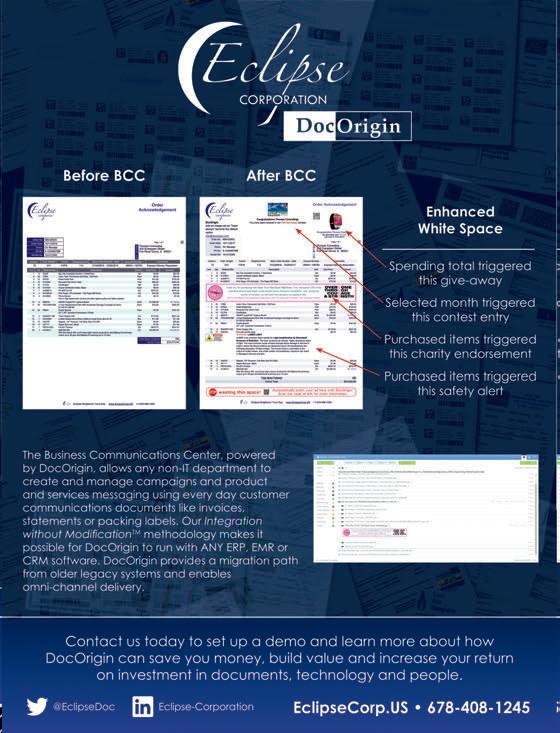
FeaturingasourcoverstorywehaveAvatier.Itsidentitymanagementsolutionsrequirefewerlogin credentialsandprovidetheabilitytocollaborateacrossandbeyondbusinessboundaries.
ThiseditionalsohighlightsthecontributionfewothercompaniesincludingTheIPGGroup,a specializedintheconception,integrationandoperationofIAM-Solutions.Itofferssolutionsforthe comprehensiveprotectionofuserdataandaccesspermissions,andJanrainapioneeredCustomer IdentityandAccessManagement(CIAM).
Tothedelightofitsreadersthemagazinealsofeaturesarticleswrittenbysomeestablishedindustry leadersandourveryownin-houseeditorialteam.Don’tforgettoflipthroughitaswell.
Let’sexplorethepotentialofidentityandaccessmanagementindustry,shallwe?
Kedar Kulkarni












 Chairman, CEO & President
Nelson Cicchitto Avatier
Chairman, CEO & President
Nelson Cicchitto Avatier

In this industry, you have to work very closely with your clients' CIOs and CSOs. You also have to strive to involve decision makers and stakeholders from as wide a range of departments as possible.
 MOST TRUSTED
MOST TRUSTED
Thereareveryfewlessons thatcanbeappliedacross everyindustryandvirtually everyaspectoflife.Oneofthese timelessadagesisthatitiseasierto reachthetopthantostaythere.Only theverybestcompanies,thosewith clear,drivenfocusandan unwaveringcommitmentto excellence,achievethatfeat.
In1997,anidentitymanagement softwarecompanywasfoundedin Pleasanton,CAandquickly establisheditselfasoneofthe foremostplayersinthearena.Today, itoperatesofficesin10major internationalcitiesandpartnerswith top-tierclients.Forovertwenty years,ithasbeentheleaderinits field.
MeetAvatierAvatierisoneoftheworld’sleading providersofidentitymanagement software.Itsproductshelp organizationscomplywith governmentandindustryregulations, improveefficiency,andstrengthen security,allwhilereducingcosts.
TheU.S.federalgovernment, regionalgovernments,themilitary,
andgovernmentalinstitutionsfrom aroundtheworldemployAvatier’s software.Thecompanycounts amongitsclientsseveralofthe world’smostprestigioushotel chains,premiermedicalandhigher educationinstitutions,andleading brandsfromarangeofindustries.
ThekeyprongsofAvatier’ssolution includesinglesign-on,helpservice passwordreset,automateduser provisioning,andaccessrequest management.Itsdynamicpatented workflowwithmulti-factor authenticationisaunifiedsystemthat facilitatesseamlessreportingacross everynexus.
InsightsSuccessspokewithNelson Cicchitto,theChairman,CEO,and PresidentofAvatierCorporation
NelsonisaveteranoftheITindustry andhasbeenwithAvatiersincethe verybeginning.
AfteraBachelorofSciencehonors degreefromtheUniversityofNorth Texas,hejoinedtheChevron InformationTechnologyCompany, wherehedesignedtheirfirstcommon operatingenvironmentandX.500 directory.NelsonthenhelpedPacific BellimplementtheStandardDesktop initiativefor20,000employees.
Overthepasttwodecades,his contributionsandleadershiphave propelledAvatiertoworldwide acclaimandcementedhisreputation asoneoftheindustry’stop visionaries.
WeaskedNelsontosharewithushis visionforAvatier.Theanswerwas veryspecific.
“To simplify.”
Thosetwowordsarethedriving forcebehindacompanythatdelivers sophisticatedsolutionsthatcanbe employedwithoutin-depthexpertise.
“Avatier ease the process of the identity, identity management, and access governance space,”he elaborates,“We make it easier for customers, employees, and contractors to request and receive access when they need it. Avatars and user identities are things of the past.”
Thiseasy-to-useidentity managementtechnologydoesnot compromiseonsecurityatanylevel.
“Data security is paramount, and we emphasize compliance with industry regulations, too. All of this revolves around customer satisfaction, which is our primary focus.”
NelsontouchedonwhyAvatierhas managedtodrawsomanyclientsso quickly.
“No other product can be deployed and operated as easily as ours. Because it is based on Docker containers, Avatier software can run on a client’s premises, on our cloud,

They see value in what we bring to the table and that is the reason they continue to buy from us.
or on any cloud they choose. It delivers seamless flexibility and freedom at any point on the globe.”
“It is also the most affordable in terms of maintenance,”heexplains.
“We have even built an ROI calculator into our technology so clients have complete control over how their investments amplify their success.”
Morepeopleareconnectingtothe webandtoeachothereveryday. Thiswidespreaduseofdigital devicesisgeneratinganincreasingly heterogeneousrangeofplatforms. Avatier’sproductsarecompatible witheverymajorplatformanddevice andcanbescaledupordownasa client’sneedsexpandandevolve.
Anunfortunateby-productoftherise ofdigitalidentityandaccessisa correspondingincreaseinthenumber andthesophisticationof cybersecuritythreats.Avatierisatthe forefrontofthebattleagainstthese risksthroughthedevelopmentofits innovativesolutions.
OneofthekeydriversofAvatier’s successisitsunrelentingfocusonthe futureofidentitymanagement.This philosophyisthefoundationoftheir proactivethreatdefensemechanisms. Itkeepsclientsatarm’slengthfrom theriskofdatacompromisethrough dynamicchange.
Thisconstantinnovationand evolutionplacesAvatier’scustomers inthe’toohard’categoryoftargets formostattackers.Thiscommitment
toimpregnablesecurityhasearned Avatierapprovalfordeploymentby theU.S.military,arguablythemost prestigiousfeatherinanycompany’s cap.
Forendusers,Avatier’sfocusonthe futurealsomanifestsasseamless interactionacrossalltheirdevicesin realtime.Itgivesthem unprecedentedaccesstotheirown dataaswellasshareddata, regardlessoflocation.
Thecompany’sbusiness-driven identitymanagementforegoescoding infavorofconfiguration.Avatierhas developedanintuitiveinterfacethat isdesignedforeaseofusewithout theneedforcomplicatedtraining.
Avatierissuccessfulinlargepart becauseithasbeenabletoovercome challengesquicklyandeffectively. Nelsonrevealsthatwhileunique problemsdoariseonoccasion,two specificconcernsgeneratethebulkof thehurdles.
“Avatier can overcome any software obstacle easily; it is in customer education that we are confronted with our two biggest challenges,”he says.
“One is the customer who has never deployed an identity management solution and does not appreciate the breadth of possible complications. The other is the customer who is upgrading to Avatier and needs to be shown exactly how, where, and why our solution is superior.”
“In the first scenario, we educate them on what we do and help them set the right expectations. In the second, we have to demonstrate how Avatier’s speed, functionality, and ease outclasses anything they might have used before.”
Nelsonenjoysbeingconfrontedby problemsofthisnature.Theygive himtheopportunitytoelaborateon theagile,streamlinedsoftwarethat hehashelpedcreate.Thisinteraction withclientsfromdiverseindustries hasbeenalearningprocessforhim aswell.
“In this industry, you have to work very closely with your clients’CIOs
We make it easier for customers, employees, and contractors to request and receive access when they need it. Avatars and user identities are things of the past.
Avatier
WritingtheFuture
Avatiersoftwarehasalready establisheditselfasafeasible alternativetosimilarsoftware producedbymanufacturersthatare farolderandmuchbigger.Nelsonis confidentthathiscompanyhasboth thevisionandthestrategytosurpass them.
and CSOs. You also have to strive to involve decision makers and stakeholders from as wide a range of departments as possible.”
Heexplains,“If just a part of the organization wants the solution, it is difficult to keep the entire organization happy and invested in its use. By educating all their departments, we can demonstrate what each has to gain and why Avatier is the clear choice.”
“When all of them see the benefits in the proposition, they will see the value in the implemented solution.”
ThereisnodoubtthatNelsonis passionateaboutIT,especially identitymanagement.However,he alsoplacesgreatemphasison nurturingbuddingentrepreneursand softwarespecialists.Weaskedhim whatheconsiderstobethemost importantphilosophytoinculcatein hisprotégés.
“Embrace change,”hereplies, almostinstantly.“Irrespective of the specific field of the industry to which you belong, innovation is the single most important factor for success.
Individuals and companies with the ability to consistently reinvent themselves for the benefit of the customer will always be in demand.”
“Avatier is always pushing the boundaries of what is possible because the culture of change is firmly entrenched here. We are constantly patenting new technology but change goes beyond that; we are also quick to adopt the latest sales, marketing, and development strategies.”
Nelsonreiteratesthatitisnotchange forchange’ssake,butaclearplanto innovateonthefactorsthatmatterto theircustomers.
“They see value in what we bring to the table and that is the reason they continue to buy from us.”
Perhapsthegreatestindicatorthat Avatierdeliversonwhatitpromises isthecompany’sincrediblecustomer renewalrate.
Whengiventheoption,an overwhelming97%ofclientsmake anactivechoicetokeepusing Avatierproducts.Thisvoteof confidencereinforcesthecompany’s resolvetodeliversolutionsthatcover allbasesbeyondexpectations.
“Our technology will be adopted more widely. There is a watershed change approaching in terms of the adoption of enterprise cloud solutions. Currently, just under half of businesses have moved their resources to the cloud. When they realize that the cloud is the future, they will embrace it swiftly to gain an edge.”
Nelson’sconfidenceisbasedon Avatier’sabilitytoprovideits solutionbothinthecloudandona client’spremises.
“Avatier software can establish the greatest market share because of its flexibility. I see people using our range of products as their sole method of logging on to any application, anywhere in the world.”
GivenAvatier’sdrivenleadership, commitmenttoinnovation,and brilliantproductrange,wewouldbe hard-pressedtodisagree.
is always pushing the boundaries of what is possible because the culture of change is rmly entrenched here.


10DukeSoftwareLtd. 10duke.com NeilFenton ExecutiveChairman
AvatierCorporation avatier.com
Axiomatics axiomatics.com
BlackBerryLimited blackberry.com
NelsonCicchitto Chairman, CEO&President
10Dukedesignsandcreatestechnologytomeetthedemandsof 21stcenturyonlineapplications.Itofferitscustomers significantshortcutsindeliveringinnovativeapplicationsthat cancompeteandscale.
Avatier'sidentitymanagementsolutionsrequirefewerlogin credentialsandprovidetheabilitytocollaborateacrossand beyondbusinessboundaries.
NiklasJakobsson CEO
JohnChen ExecutiveChairman& ChiefExecutiveOfficer
Axiomaticsisthepremiervendorofdynamicauthorization deliveredthroughAttributeBasedAccessControl (ABAC)solutions.
Blackberryisleadingthewaywithasingleplatformfor securing,managingandoptimisinghowintelligentendpoints aredeployedintheenterprises,enablingitscustomerstostay aheadwiththetechnology.
IDEX idexbiometrics.com
ILANTUSTechnologies ilantus.com
StanSwearingen CEO
BinodSingh CEO
IPGGroup ipg-group.com
Janrain janrain.com
PistolStarInc. portalguard.com
MarcoRohrer CEO&Managing Director
IDEXBiometricsfingerprintsensorsandbiometricsolutionsare highlysecure,customizableanddeliverastrongbiometric performancewhileensuringanoutstandinguserexperience.Allat amassmarketprice.
ILANTUShaslearnedthroughcustomersforover18yearsand provideroundpegsforroundholes–solutionstailoredtosegments andindustriesthatreallysuitdifferentorganizationalenvironments.
TheIPGGroupisspecializedintheconception,integrationand operationofIAM-Solutions.Itoffersolutionsforthe comprehensiveprotectionofuserdataandaccesspermissions.
JimKaskade CEO
TomHoey Founder&CEO
Safetrust safetrust.com
JasonHart Founder
JanrainpioneeredCustomerIdentityandAccessManagement (CIAM)andleadsthemarketitcreated.
PistolStarhasexperiencedphenomenalgrowth,attributingits successtoanunderstandingofcustomers'pain,havingtheability todemonstrateapositivereturnoninvestment,and differentiatingitselffromthecompetitionbydeliveringflexible solutions.
Safetrustbringsmobilitytothemodernenterpriseasaglobal pioneerinphysicalandlogicalidentitysolutions.
Nearly95percentofallsuccessfulattackson enterprisenetworkstargetedorganization’susers throughemail.Withtheindustryofcybersecurity evolvingsorapidly,hackersareconsistentlychangingtheir tactics,keepingitalmostimpossibletokeepupwith.
Withtoday’sgrowingsecuritylandscape,emailthreatsare oneofthemostcommonstrategiesutilizedbycyber criminals.Whatstartedoffwithspamemailssenttoyour junkfolder,hasevolvedtoamorerobusttactictodeliver destructivecontentstraighttoyourinbox.Herearethetop fiveemailsecuritythreatsthatwe’veseensofarthisyear:
Emotet
Emotetisanadvanced,modularbankingTrojanthat primarilyfocusesasadownloaderordropperofother bankingTrojansandcontinuestobeamongthemostcostly anddestructivemalwareaffectinggovernments,privateand publicsectors.Emotetcanevademostsignature-based detections,andbecauseitisVirtualMachineaware,it generatesfalseindicatorswhenraninasandbox. Additionally,Emotethasseveralmethodsformaintaining persistence,includingauto-startregistrykeysandservices aswellasDynamicLinkLibrariestocontinuouslyupdate andevolveitscapabilities.
Initialinfectionofthismalwareoccurswhenauseropens orclicksamaliciousdownloadlink,PDF,ormacro-enabled MicrosoftWorddocumentincludedinthemalspam.Once downloaded,Emotetestablishespersistenceandattemptsto propagatelocalnetworksthroughoneofitsincorporated
spreadermodules.Thenegativeconsequencesfroman Emotetinfectioncanbetemporaryorpermanentlossof sensitiveproprietaryinformation,disruptionofregular operations,financiallossesincurredtorestoresystemsand files,andpotentialharmtoanorganizationsreputation.
AnewversionoftheinfamousbankingTrojanUrsnifmade itsappearanceagainearlierthisyearinJune.Thismalware iswellknowninthecybersecuritycommunityandwasthe mostactivemalwarecodeinthefinancialsectorfromthe endof2016intoearly2017.Thismalwareiscapableof stealingusers'credentials,credentialsforlocalwebmail, cloudstorage,cryptocurrencyexchangeplatformsandecommercesites.
OnceUrsnifinfectsanewmachineitwillattempttospread tootherusersintheaddressbookofthecompromisedemail accounts.Ittricksthevictimintoopeningthemalicious emailbecausethemessageispresentedasthereplytoan existingconversationconductedbythevictiminthepast. Forexample,ifyoureceiveanemailthatwasareplaytoa previousconversationfromawhileback,youcanlookat the“To:”fieldintheemailandseeifit'srepliedtoalarge numberofunsuspectingusers.
Anotherfeatureaboutthismalwareisitsabilitytokeep trackofcompanynamesandtitlethemaliciousdocument “VICTIM_COMPANY_.doc”inordertolooklegitimate. Oncethevictimclicksenablemacros,thesecondstepof theinfectionprocessbegins,whichlaunchesamalicious
scriptthatdownloadsandexecutesapayloadfromaserver controlledbytheattackers.Onceinstalled,Ursnifcan operatewithoutbeingnoticedbyboththeuserandthe operatingsystem.
Extortioncampaignshavebeenaroundforquitesometime buttherewasonethatwasinfullswingacrosstheglobe thatusedaclevertwisttotrickunsuspectingusersinto payingaransom.Theattackerforthisextortioncampaign claimstohaveinstalledmalwareonyoursystemandhas alsousedyourwebcamtorecordyouwatchingporn.The attackerthengoesontothreatenthereleaseofthisvideoto everyoneinyourcontactsunlessyoupaytheBitcoin ransom.
Thebasicpremiseofthistypeofextortionattempthasbeen aroundforquitesometime,buttheadditionofthe Username/Passwordcombinationinthesubjectlinehas unsuspectingusersworried.Whileresearchingthis campaign,Nuspire’sSecurityAnalyticsTeam(SAT)came acrossmultipledifferentcountsofaffectedusersclaiming theUsername/Passwordcombinationwassomethingthey hadusedeightyearsago.Inthiscase,theattackerhas somewhatautomatedtheattacktocreateascriptthatpulls directlyfromusernamesandpasswordsofagivendata breachthathappenedeightyearsago.Therefore,every victimwhohadtheirpasswordcompromisedaspartofthat breach,isnowgettingthissameemailattheaddressthey usedtosignupforthehackedwebsite.

Hopefully,ifyouwereaffectedbythatdatabreachyou updatedyourusername/passwordcombination.Granted,the peoplewhodidn'tbotherchangingthisinformation,this attackdirectlyaffectsthem,butrestassuredthisattacker doesn’thavearecordingofyouthattheyplantosendoutto yourcontacts.Itismerelyscaretacticstomakesomeeasy money,anduponinvestigationofmultipleBitcoin addressesassociatedwiththiscampaign,theattackerwas indeedmakingeasymoney.
Thisattackcouldevolveinthefutureandusemoreupto datedatabreacheswhichinturncouldscaremoreusersinto payingtheransom,sobeonthelookout.
GandCrabholdsthetopspotinransomware,partlybecause it’susedbytheMagnitudebotnet.AlthoughGandCrabis usuallyspreadviaspamemail,ithasrecentlybeen distributedviacompromisedwebsitesandisnow
Shawn Pope Cyber Security Engineer
Shawn Pope is the Cyber Security Engineer of Nuspire Networks, a state-of-the-science managed network security provider for some of the largest and most distinctive companies around the world.
appendingthe.KRABextensiontotheencryptedfiles. TowardstheendofApril2018acampaignwiththesubject line“YourOrder#{RandomDigits}”wascirculating.There islimitedcontentinthebodyoftheemailandhasan attachedZIPfilewhichincludesaWorddocumentthat containsmaliciousmacrosthatdownloadandexecute GandCrabransomware.
GandCrabisunderconstantdevelopmentwherenew versionsareconsistentlybeingreleasedatanaggressive pace.Itsbasicfunctionalityiswelldocumentanddoesthe sametypicalthingsransomwaredoes,includingencrypting fileswiththe.KRABextension,changingtheuser’s background,andleveragingTorforcommunications.One oftheinterestingelementsofGandcrabisitsuseof namecoindomainsforCommandandControl(C2) communication.Theseareeasilyidentifiedbythe.bittop leveldomain(TLD).SinceattackersrelyheavilyonTor andnamecoindomainstohelpevadeidentification,itisa nobrainerforthemtouseadecentralizedDNSservicethat doesnotrelyoncentralauthority.Thisalsoincreasesthe difficultyofhavingdomainsshutdownandidentifying thosethatarepotentiallybehindthem.
BytheendofQ22018Microsofthadtakenoverthetop spotfromFacebookforthenumberonetargetofcorporate phishingattacks.Reasonbeing,it’shighlyprofitablefor hackerstocompromiseanOffice365account.Hackerssee email-basedattacksasaneasyentrypointintodata,files, andcontactsfromotherOffice365apps,including SharePoint,OneDrive,Skype,Excel,andCRM.
WeseealldifferenttypesofPhishingattemptsfromquite possiblytheworstattemptstoexactreplicasofalegitimate Office365loginpage.Unfortunately,Phishingwillalways existandcanslipthroughthegapsinemailfilteringdueto thefactthatnewdomains/URLsarepoppingupeveryday
tohostfakeloginpages.Thisiswhereuserawareness trainingisextremelyimportant.Educateyourusers,rollout trainingexerciseswhereemployeeswithfakePhishing emailsandseewhoclicksonthemandwhodoesn’t. BecausePhishinghasbecomesopopular,educationwill payoffinthelongrun.
Asidefromtrainingandeducatingemployeesonmalware, andransomwarethatmightcomeinthroughauser’semail, thereareafewothersolutionstotakeintoconsideration thatcanpreventtheseattacksfromenteringyournetwork.
1. Useantivirusprogramswithbehaviorandheuristic detectioncapabilities,withautomaticupdatesof signaturesandsoftwareonclientsandservers.
2. Implementaspamfiltertofilteroutknownmalspam indicatorssuchasmalicioussubjectlines,andblock suspiciousandblacklistedIps.
3. Markexternalemailswithabannerdenotingitisfrom anexternalsource,thiswillassistusersindetecting spoofedemails.
4. Implementablockpolicyforfileattachmentsthatare commonlyassociatedwithmalwaresuchas.dll,and .exe,andattachmentsthatcannotbescannedby antivirussucha.zipfiles.
5. ImplementDomain-BasedMessageAuthentication, Reporting&Conformance(DMARC),avalidation systemthatminimizesspamemailbydetectingemail spoofingusingDomainNameSystem(DNS)records anddigitalsignatures.
6. Implementasolutionthatcansendthe unknown/suspiciousfilestothesandboxforfurther investigationandanalysis.
7. Andmostimportantlyemployeetrainingonsocial engineeringandphishing.Urgeemployeesnottoopen suspiciousemails,clicklinkscontainedinsuchemails, orpostsensitiveinformationonline.

Theriseincyber-crimesisoneofthemaincausesof Datacenteroutages.Aspertherecentsurvey conductedbyindustryinsiders,cyber-crimecaused 22percentdatacenteroutagesin2015opposedto2percent outagesin2010.Addingtoallthese,nowmostofthedata centersarere-evaluatingtheirsecuritypoliciesafterthe recentWannaCryransomwareattack.
Datacenteroutagescausecompaniestolossrevenuein manyways.However,thecostliestlossisservice interruptionandlossofITproductivity.So,the organizationsarenowrealizingthattraditionalsecurityis nolongersecureenoughtosecureanydatacenter.Arecent studyhasfoundthat83percentoftraffictravelseast/west withinthedatacenter,whichstaysundetectedbythe perimetersecurity.Inthisenvironment,whenanattacker infiltratestheperimeterfirewall,thencanjumpacrossthe systemwithease,extractinformationandcompromise valuabledata.Additionally,datacenterscanfaildueto trespassersoraterroristattackorbynaturalcalamities.
So,howcanonesecureadatacenterinthebestway possiblefromanykindofcyberthreat?Don’tworrywe’ve gotyoucovered,withthepointsbelow.
Asthefirststep,oneshouldMaptheDataCenterandflag thehackerswithinthevirtualandphysicalinfrastructure. TheCSOsandCIOswithasystemmapoftheirsystems canreacttoanysuspiciousactivityandtakestepstostop databreaches.Beingabletovisualizedifferenttraffic patternswithinanetworkhelpstounderstandthreats,that eventuallyelevatesthelevelofsecurity.
Understandingandmeasurementoftrafficflowwithin thedatacenterboundaryareveryimportant.Inthecaseof
anyinterruptionintrafficacrosseast/westvsnorth/south, protectedvsunprotectedonecangettoknowaboutathreat. Additionally,vulnerablezonesandunprotectedtrafficneed tobemonitoredforabetterresult.
Firewallrulesneedtobedefinedandimplementedasper requirements.Additionally,oneshouldallowtrafficonly afterthoroughverificationandselectivelyallow communicationtoensuremaximumprotection.Thekeyis toidentify,what;slegalandsecuredandwhatcanbe blockedtoenhancesecurity.
OneneedstoBuildaTeamwithexecutiveswho understandhowtrafficflowswithinthepremisesandcan access&secureinformation,takenecessarymeasuresto secureimportantassetsalongwiththeimplementationof roadblocksfortheattackers.
Securitymustmoveasfastasadatacenter’stechnology adoption andintegration.SecurityStrategyShouldChange AlongsidetheTechnologyanditshouldnotbetreatedas anadd-onoption.Additionally,businessesalsoshould ensurethattheirvirusprotection,signaturesother protectionfeaturesareuptodateforbetterprotection.
BusinessesshouldIdentifyandPlaceControlsoverhighvalueassets,whichwillhelptoreducerisk.However,older securitysolutionsarecompletelyblindtonewthreats,new securitycompanieshaveproducedlatestsolutionsthat protectdatainthevirtualworld.
AccessRestrictionalsoneedstobeimposed.Every businessshouldthoroughlycheckaperson’sbackground beforegivingtheaccesstoaprizedpossession.Accessto themainsiteandtheloadingbaymustbelimited,
additionally,two-factorauthenticationsandfortifiedinteriorswithsecurityguardsandrovingpatrolswouldhelpto safeguardtheemployeesandthedatacenter.

InstallingSurveillanceCamerasaroundthedatacenter,alongsideremovingsignswhichmayprovidecluestoitsfunction helpstolocateanintruder.Abufferzonebetweenthedatacenterandalltheentrypointswilllimitunlawfultrespassingtoa greatextent.Additionally,thedatacenterneedstobefarawayfromthemainroadanditshouldnothaveanywindowsother thanadministrativepurposesforbettersecurity.
AdatacentershouldCheckTestBack-UpSystemsregularlyasprescribedbythemanufacturer.Itshouldalsoensureto makealistandofDo’sandDon’tsintheeventofanattack.Recoveryplansandsecurityplansalsoneedtobechecked thoroughly.
DatacentersarealwaysaSoftTargetforTheTerrorists,asanattackonthemcandisruptanddamagemajorbusinessand communicationinfrastructure.So,securityneedstobetakenseriouslyandtodothatproactivestepsshouldbetakentolimit theimpactofaterroristattack.
TrainedSecurityGuardsneedstobepostedinsideadatacenterandtheyshouldbewelltrained.Securityofficersmust undergostrictsite-specifictrainingtomonitorsurveillancefootage.Dependingonthesizeofdatacenterandthenumberof securitycamerasmultiplesecurityofficersmayberequiredonduty. Securityofficersdedicatedtoinspectingsurveillance footagehelpswhenitcomestosecuringadatacenter.
DisasterRecoveryisverymuchimportant,thatmustbeinplace.Ifthedatacenterstopsfunctioningafteranattackor naturalcalamity,itmusthaveawaytorestoreoperationsassoonaspossible.Tobereadyforadisasterandtoevaluatethe disasterrecoveryplan,it’snecessarytotrainstaffswellandexperiencesimulateddisasters.
Toavoidtheseobstacles,oneneedsafairbitofknowledgeofnewsecuritysystems,solidplans,andcomprehensive visibility.Themoreworkadatacentercandoupfrontintheabove-mentionedareasthebetterthechancesofsuccesswith lesseroutages.
HeadquarteredatStockholm,Sweden, Axiomaticsprovidesaccesscontrolsoftware thatprotectsthemostcriticalassetsoftoday’s modernenterprises.Thisincludesapplicationsanddata sourcesandmicroserviceswhichareutilizedbythe Fortune500andfederalgovernmentagenciesaroundthe worldtosharesensitivedatasecurely,meetcompliance andminimizedatafraud.Throughapolicy-based approachtodynamicauthorizationthatutilizesthe AttributeBasedAccessControl(ABAC)model, Axiomaticshelpsenterprisesacrossindustriestolock downconfidentialdataandIPwhilesecurelysharingand collaboratingwithauthorizedusers.
NiklasJakobssonistheCEOofAxiomatics.Hehas over25yearsofexperienceinthetechnologysector, amongwhichfifteenofthoseyearshavebeeninasenior managementposition.Niklashasalsoworkedand operatedinmostoftheITbusinessmodelsrangingfrom opensourcetoSaaS,softwarelicensesalesto outsourcingininternationalenvironments.Hefully comprehendsthecomplexityandopportunitypresentin themarketwhichhasledAxiomaticstoensureflexibility andfocusonitsproductoffering.
PriortoAxiomatics,Niklaswasthecountrymanagerat CATechnologies,acomputersoftwarecompany,where hewasresponsibleformanagingITservices.Hisrole withCATechnologieshasbeeninstrumentalinshaping thevisionofhowAxiomaticsworkswithlarge enterprisesandgrowingsoftwarefirms.
Asapeople-personcombinedwithhisinternational businessacumen,Niklashasbeenabletobetterlink operationsacrossEuropeandtheAmericaswitha cohesivevision.
Atitscore,dynamicauthorizationisapolicy-based approachwhichensuresrightuserstohaveaccesstothe rightassetsattherighttime.Asthepremiervendorin authorization,Axiomaticssolutionsareidealfor enterprisesandgovernmentagenciesthatneedto securelyshareinformation,whilecomplyingwith complexandever-evolvingregulations.Thesuitecovers thelifecycleofpolicy-basedaccesscontrol,helping customerstocreatetheframework,implementand maintaintheirpolicies,aswellasenforceandaudit accesscontrol.
Sofar,theexpertshaveledthefieldandprovenits flexibilitybyhelpingcompaniesinupgradingtheir legacyaccesscontrolapproachesandtacklingnew initiativessuchasmigratingtothecloud,digitalbusiness transformation,newcustomerportaldevelopmentand adoptionofAPIsandmicroservices.
WithAxiomatics'dynamicauthorization,theycanset fine-grainedpoliciesbuiltonattributesofdatathat dictateaccesscontrolpermissions.Thisincludes informationsuchastheuser'srole,thetimeofday, currentlocation,anddesignationofaspecificteamor project.Thiscansolvemorecomplexaccesscontrol scenarios,suchascontextualdynamicdatamaskingof specificdatatypestomeetprivacyrequirements.In additiontosafeguardingsensitiveinformationcritical applicationsanddata,Axiomaticsdynamicauthorization productsallowtherightinformationtobeshared,under therightconditions.
Beingaprovenleaderintheindustry,Axiomatics'bestin-classsolutionsanditsstrategicbusinessprocessesare builttosetthecompanyapartfromothercompetitors. Ontheotherhand,itcontinuestobemorefocusedonthe

rightproductinnovationstohelpeasethepainsoflegacy accesscontrolandfacilitatetheadoptionofdynamic authorization.Atpresent,Axiomaticsisadvancingtowards itsmilestonealongwithitscustomer'sgrowthby innovatingnewapplicationsofdynamicauthorizationthat supportandenablingthebusinesstobecomemoreagile, secureandcustomer-focused.
ServingcustomersdrivestheexpertsofAxiomaticsand enablethemtoworkhardeachday.Theyfeelpridein helpingtheclienteletosolvetheiraccesscontrolissues.

ForoneoftheirEuropeanbankingcustomers,theAttribute BasedAccessControl(ABAC)solutionprovideda centralizedandexternalizedapproachtoachieve compliancewithprivacyregulations,fortheData ProtectionLawandGDPR(transparencytoaccess).The benefitsfromthisimplementationarequantifiable, includingreal-timereportingandcostreductionfor developmentefforts.Thecustomeralsoexperiencednearly 20percentcostreductionformaintenance,easeinonboardingapplicationsandservices,andtheabilityto changepolicylanguageenterprise-widewhenneeded.
Theclientsaid,“Wenowhavetheabilitytobeproactive. Wearewellpositionedtohandleall futureregulatoryrequirementsquicklyandcosteffectively.”
Fromthebeginning,Axiomaticshasbeenapioneerin openingupanewapproachtowardaccesscontrol.Asthe adoptionofdynamicauthorizationisbecomingmore mainstream,thecompanywillcontinuetobeonthe frontlinesasathoughtleaderandshareleading-edgeuse casesontheapplicationofaccesscontrolfor applications,APIs,microservicesanddatastores. Axiomaticswillcontinuetoserveastheleaderinaccess control,andwillcontinuetoimproveitsproduct offeringsbyintegratingwithinamultitudeofecosystems bothinIAMandinindustriessuchasmanufacturing, healthcare,thefederalgovernmentandbanking.
About the Author
With a massive experience of more than 15 years Elena Briola, currently serves as VP Marketing at Cloud4Wi and she is responsible for all areas of marketing and communications, including product marketing, marketing communications, corporate communications and internal communications.
Thanks to her competences, Elena has managed complex projects, supporting various national and international customers in strategic activities, from the business planning to the product planning and marketing. Moreover, she has written several articles and reports on new generation wireless technologies.

Flexibility,definedastheabilityto changebusinessplanstoaccountfor changingconditionsandnew information,isessential.Beingaflexible managerrequirestalent,smarts,andtheability tocreateafuturefewothersmaysee.
Beingflexibleallowstechcompanies,like Cloud4Wi,tosteparoundhugeroadblocksand betterfocuson“rightnow”business opportunities.Misusedandmisunderstood, flexibilitycanalsobearefugeformanagers andwholecompaniesthatareunabletomake decisionsandstickwiththem.
Whilewemustalwaysbeflexible,deciding wheretheflexmustendcanbearealchallenge. Beingtooflexible–wishy-washyeven–isjust atleastasdeadlyasnotbeingflexibleatall.
FlexibilityasIntuition
Flexibilitycanundoubtedlybelearned.Over time,bytrialanderror,andwithdeep introspection,mostmanagerscanbecome betterflexiblemanagers.Itseemsevidentthat somemanagersnaturallyseemtoseeand understandflexibledecisionmakingandits consequencesmuchbetterthanothers.Tech companiesshouldseektoidentifythese “natural-born”flexiblemanagersandusetheir wisdomwhenpossible.
Developingaflexiblecultureisalsoessential. Thisstartswithanunderstandingthatoncea decisionhasgainedthesupportofkey stakeholders,itisnolonger“owned”by whoeversuggestedit.Thatmeansifthe decisiongoeswrong,theconsequencesfallon everyone.Asharedresultistheonlyway flexiblethinkerscanbeencouragedtooffer theirbestideas,withoutfearofdisruptingtheir careers.
Howtechcompaniesrespondtothechanging customerenvironmentandotherexternal
|December 2018| 24
challengescandefinesuccessandfailure.Bothinflexibility inexecutionandchangejustforchange’ssakecanturna techcompanyintoafurnitureliquidationsale.
Flexibilitymaybethetechmanager’smostimportant personalquality.Theabilitytomakeaquickdecisionthat doesn’tforegoongoingcoursecorrectionsiswhatmakes onemanagerasuccessandanother“doyouremember what’s-her-name?”
Gonearethedaysofstrategicplanscreatedmonths,even years,inadvanceandetchedinstone.Still,wesometimes seeweeksormonthsofimmobilitybycompanies confrontedwithbadnewsornewchallenges.Decisions–good,bad,indifferent–arewhatdriveabusinessforward. Remainingstillrarelyhelps.Moreover,nochoiceis generallyworsethanaso-socall.
Whenindoubt:DoSomething(ButNotAnything) Planningisanecessitybutbeinginlovewithafailingplan isdeadly.Techcompaniesthriveonshort-termactivityand flexibilitythatsupportschangewhenchangeisnecessary. Timingcanbeeverything.
Whenthingsaregoingwrong,theabilitytounderstandthe consequencesofpossibledecisionsisessential.Awellcalibratedcrystalballviewintothefuturewouldbehelpful butisseldomavailable.Usually,adecisionwillbemade basedonthebestavailable–ifincomplete–information. Notmakingadangeroussituationworseshouldbeagoalof theprocess,buttherealpurposeisdoingsomethingthat getstheteamandthebusinessworkingtosolvethe problem.Eveniflaterchangesarerequired.
Iftoolittleflexibilityisaproblem,toomuchcanbedeadly. Flexibilitycanbetherefugeofthesoft-mindedmanager, swayinginthewindsofindecisionandtryingtomakea popularchoice.Flexiblemanagershaveacalibratedsense ofwhenchangeistoomuchandrisksthegoal.
Sometimes,however,onlybigchanges–the“HailMary pass”ofbusinessdecisionmaking–hasachanceofsaving theday.Atthosetimes,itIsimportanttechcompaniesdon’t tossprocesstothewinds.Ifyoursisa“consensusdecision” company,thinktwicebeforeallowingasinglemanageror smallgrouptodecide.Likewise,ifasinglemanageris usuallythefinaldecisionmaker,don’tallowthewashof conflictingdecisionstoruintheday.
1. Choose your core offering wisely. Be flexible in how you bring it to market.
Everytechcompanyneedsamotivating“bigidea”or technologythatstaff,engineers,investors,andcustomers
This article is a collection of what I and our Cloud4Wi team have learned – sometimes the hard way – from our combined many decades of experience. We’ve found that flexibility not only works, it may be the only path to success in many cases. We’ve also found that self-conscious flexibility, nervous flexibility, can be almost as bad as not flexing at all.
Please share the lessons of flexibility with those around you, especially your reports, and create an environment where people feel free to take chances for the good of the enterprise. Used wisely, flexibility always repays.
canrallyaround.Thereneedstobeenoughflexibilityin howthebigideabecomesaproductorservicethatasthe marketplacechangesorroadblocksareencounteredthebig ideacanberefocusedonthenewopportunity.
2. Take advantage of hot trends, but don’t look like you are stretching the truth to appear “cool.”
ArtificialIntelligencehasmadeheadlinesrecently.Tech companiesshouldembraceAItobuildcutting-edge products,aswellasimprovingbusinessprocesses.AIdrivendigitalmarketingframework,forexample,canhelp techcompaniesbetteridentifypotentialcustomersand targetthemwithtailoredmessages.
3. Where not to be flexible: Company values
Manypeoplegotintothetechbusinesswiththehopeof makingtheworldabetterplace.Companiesbenefitfrom havingsolidvaluesthatremainconstantwhenputtothe test.Worktoidentifytheseandmakethemanon-flexible partofcompanyculture.Standupformanagerswhomake toughdecisionsthatgivelifetothesevalues.Thevalues canhelpguideyourdecisionsand,whennecessary,put edgesaroundtherangeofflexibleoptionsbeingconsidered.
Nowadaysincomplexcomputingenvironments, alongwithheightenedsecuritythreats,astrong usernameandpassworddoesn’tcutitanymore. Therefore,identitymanagementsystemsoftenincorporate elementsofbiometrics,machinelearningandartificial intelligence,andrisk-basedauthentication.Inthis overarchinggoalofidentitymanagement,Information ProcessGroup(IPG)aimstoalignthestrategicorientation oftheIdentity&AccessManagementactivities.The organizationmeasuresthegradualimplementationofthe technicalandtheongoingoperationoftheidentity&access managementsolutionoptimallywhileprovidinguserswith individualtrainingopportunitiesatanytime.
Additionally,asaleadingproviderandoperatorofidentity andaccessmanagementsolutionsinEurope,IPGdeals exclusivelyandspecializesintheanalysis,assessment, planningandimplementationofsolutionsforthe managementofuserdataandaccessrights.
AMarketingSpecialist
IPGisledbyMarcoRohrer,theCEOandManaging Director,whobelievesincontinuityandlong-termidentity &accessmanagementactivities.Marcobeingagraduated BusinessEconomistFHwithspecializationin entrepreneurshipandorganization&marketingadviceson thedesignofuser,authorizationandprocessmanagement roles.Healsoconcentratesoncertainspecificareasinorder todefinerequirementsforthedevelopmentofexisting identitymanagementinfrastructures.Inthelasttwoyears, Marcohasbeenarmoredwithgreatsuccessandleadsa comprehensiveprojectfortheintroductionofanidentity managementinfrastructureinthecomplexenvironmentofa large,all-sectorinsurance.
Likebefore,theexpertsunderhisleadershipareconvinced thatthecompany’scustomersshouldnothavetoworry aboutthedetailsofanIAMsolutionandcanhandover theirdailyoperations.Therefore,theexpertsofIPGare
continuouslyexpandingtheManagedServices(IAM OperationServices)tofurtherstrengthenthecompany’s marketpositioninthefuture.
HeadquarteredatWinterthur,Switzerland,IPGoffersrange ofinnovationandtransformationidentity&access managementsolutionslikecompetentstrategy,processand organizationalconsultingtotechnologyconsulting, industry-specificimplementation,stableoperationand tailor-madetraining.Furtherasafull-serviceprovider,IPG alsooffersoperatingservicesandmanagedservicesaswell asacomprehensivetrainingprograminGermany,Austria andSwitzerland.
BeingoneofthepioneersintheIAMspace,IPGassumes responsibilityasabusinesspartnerandhasproven competenceintherealizationofcomplexIAMsolutionsfor almost20years.Today,theIPGGroupisoneoftheleading consultingandintegrationcompaniesforIAM.FurtherIPG promisessuccessfulprojectsbasedonaholisticapproach withthesophisticatedbestpracticesandcomprehensive industryinvariousfieldsformthebasisforafavorable IAMbusinesspartnership.
TheoptimalexploitationofIAMspotentialbenefitsatthe levelofbusinessprocessescanonlybeachievedbasedon comprehensiveconsiderationandproactivecontrolat variouslevels.Inordertorealizethesepotentialbenefitsfor itscustomers,IPGhasestablishedastrongadvisory competence,whichensuresthatthenecessarytaskswithin theframeworkoftheIAMprojectsareimplemented efficiently.
Nevertheless,itiscurrentlynoticeablethatservice companiesaretryingtoenterthemarketbyaddressing newertopicssuchascustomerorconsumeridentity
management.However,IPGseesitselfwellpreparedto operatesuccessfullyinthemarketinthelongterm.Expertise andexperienceinthissegmentareanessentialprerequisite. Customersexpectconsultingandimplementationexpertise andwanttobenefitbestpractices.
Withqualifiedexperts,IPGstandsforconsistentmethodsin IAMstrategyfromimplementationtooperationandfor orientation&predictabilitywithastep-by-stepapproachwith clearactionfieldsandguides,scalableandprioritized adaptationtocustomerneeds.
SincetheIAMmarkethaschangedgreatly,especially concerningsoftwarevendors.IPGisconstantlyreviewing technologieswhichareindemand,inordertooffer significantnewopportunities,butisalsocommittedto proven,long-termpartnerships.Thisalsoformsabasisfor differentiatinginthemarketfromnewcompetitors.Through acomprehensiveproductandtechnologyexpertiseIPGis abletocombinethiswithproceduralandorganizational expertise.
Additionally,IPGcontinuestofocusongrowthand expandingitsleadingpositioninGermany,Austriaand Switzerlandandfocusingintheexpansionofmanaged services.Ontheotherhand,itisalsoactivelyengagingwith topicssuchasIAM,BlockchainandInternetofThings(IoT)

inordertocontinuetobeacompetentpartnerforIAMina timeofincreasingdigitalization.
“Theprofessionaloperationalsupportallowsustoflexibly leadtheIAMoperationwithfullcosttransparencyand ensuresthatourIAMsystemisuptodate”-YvesOggier, HeadofITOperationSupportProcessesatSanitasHealth Insurance,Switzerland
“BeingabletoaccesscurrentIAMKnowledgewithout havingtocreateourowndepartmentandcompletecost transparencyisimportanttous”-SimoneBonanni,Head EngineeringandOperations,AMAG
MarcoManaging Director
We specialize in design, integration, operation and
relating to IAM solutions.


Thecloudhasnowbecomeawell-established deploymentoptionforbusinessapplications.It providesanexceptionalgroundforgroundingthe businessintelligencesystems,asitprovidesbusiness agility,scalability,andlowersthetotalcostofownership. So,itisalittleuncharacteristicthatalthoughmost applicationshavemigratedtothecloud,datawarehousesthefundamentalofanybusinessintelligencestructures-are stillmostlyonproposition.
Ofcourse,that'snotentirelysurprisinggiventhat businesseshaveinvestedheavilyinanon-premisedata warehousetechnology,withstrongconcernsabout protectingsensitivedata.Beingseamless,migrationofthe datawarehousetothecloudmustensurethatadditional cloudsecuritymeasuresareaddressed.
Stepsrequiredtobesupervisedwhilemigrationofthe DataWarehouses
Characterizethecurrentdatawarehousealongmultiple dimensions
Detailedanalysisshouldbecarriedouttocoverthe sensitivedataaspectsverycarefully.Itshouldbetaken underconsiderationonwhatoptionsareprovidedbythe cloudvendor,andwhataretheorganizationalneedsforthe confidentiality.Thoroughanalysisoftheregulatory standardsmustbecarriedout.
Therecouldbemultiplebusinessusersandbusinessunits whoareusingthedata.Wecanalsoeaseoutthemigration processbyprioritizingandbreakingdownthewholedata warehouseintosignificantbusinessprocesssubjectareas.
Selecttherightcloudvendorforyourwarehouse
Therearenumerouscloudprovidersoutthereinthemarket. Amazon,GoogleCloud,MicrosoftAzurearesomeofthe marketleadersinamongcloudsolutionprovider’sindustry. Basedontheoutcomeoftheclassificationoftheexisting warehouse,wemustcreateamatrixofthefunctionalities requiredvs.existingfeaturesinrespectivecloudprovider’s environmentandthenmakethefinalchoice.Ofcourse,the monetaryexpensesalsoplayavitalroleinmakingthis decision.
Identifytechnologychoicesdependingontheresiliency ofconceptprojects
Choosingtheappropriatedatabasetechnologyforhosting thewarehouseisthemostimportanttechnologydecisionto bemade.Youarerequiredtoidentifythequeries symbolizingthetypicalworkloadbasedonperformance tests.Thefactorsneededtobeconsideredwhilemakingthis decisionare:
Datatypesneededbytheapplication
Ÿ Databasetechnologiesavailablefromthecloudprovider
Ÿ Databasefeaturesrequired

Ÿ

Real-timedataprocessingneeds
Ÿ Numberofconcurrentusers
Ÿ Performanceneedsetc.
Thecomputeandthestoragenecessitieswilldecidethe infrastructureneededforhostingthedatawarehouse. Preparingasurefiremigrationplan
Preparingawellthoughtoutprojectplaniscertainlycrucial forasuccessfulmigration.Youmustprimarilyinvolve businessusersintheentiredecisionmakingandproject plan.Theyshouldbefullyawareofthemigrationstrategy andinfacttheymustcontributeintestingthenewsystem.
Mostdatawarehouseprojectsonthecloudarerequiredto setupaVPC.AVPChousestheentireproduction warehousesetup.Itisveryimportanttocreate correspondingenvironmentsfordevelopment,UATandQA toensuresmoothoperationsofthesystems.Setupaccess controlandsecurityoneachoftheenvironments.Alsolay outthecompletearchitecturebeforehand.
Migrationembroilsinitialmovementoftheolddata followedbytheincrementaltugofthedatafromthevarious sources.Athoroughdescriptionneedstobeinplacethat plotsthesourcedataelementstothetargetdataelements.It isdesirabletorunthemodeleddatamigrationprojectin
parallelwiththelegacysystemsothatitiseasiertotestand determinethesuccessofthemigration.Themigrationand extractionneedstobesetupinarepeatedmannersothatin casetherearesomeconcernswiththemigration,itcanbe re-processed.
Intheprimarystageofthedatamigration,wetypicallytest andcompareoneorseveralsamplequeriesanddatasets.In addition,wewouldliketocommendcomparisonofrow countsofobjects,minandmaxvaluesaswellassample datarowassessments.Outliningthesuccesscriteriaforthe migrationandtestingisofgreatestimportancetoensure longtermsuccessoftheclouddatawarehouse.Youalso needtoreassurethatincrementaldataloadsworkcorrectly throughout.
Nowadays,therehasbeenalotofsupportfordata warehousesinthecloud.Movingdatawarehousestothe cloudisyieldingrealbusinessbenefits,sincemanyvendors areexpandingthebreadthanddepthofservicesfor warehousingandanalysisofthedata.However,migration isnotexemptedofchallenges.Makesureyouthinkthrough allthedifferentaspectsofdatawarehousemigrationand thencomeupwithaninfallibleplantoaddressthose challenges.
Identityandaccessmanagement(IAM)solutionswere originallyusedbycompaniestocontrolemployeesand contractors’accesstoenterpriseresources.As consumershavebecomemoredigitalsavvy,companies haveadoptedidentitymanagementprogramsgearedtoward customerstogatheromnichanneldataforimproved businessinsightsandenhanceuserexperiences.While similar,customer-centricIAMhasaddedfeaturesandisa relativelynewcategoryforIAMthatspecializesin registration,authorization,authenticationandmanagement ofcustomeridentities:CustomerIdentityandAccess Management(CIAM).
Alargeenterpriselookingtosucceedinthedigitalage shouldcraftanidentitymanagementprogramthatincludes considerationsforcustomerIAMseparatefrom traditional/employeeIAM.Thecorefunctionalitiesarethe same,buteachhaveuniquefeaturesetsfortheirdifferent usecases.Inadigitally-transformedenterprise,the employeeIAMarmincludesaccesscontrolsfordifferent internalsystemsandpermissioningforeachdepartment, teamandindividualcontributor.ThecustomerIAMarm shouldgofurthertointegratewiththeCRM,marketing automationstack,contentmanagementsystemsandother applications,accordingtotheKuppingerColeLeadership Compass,tocreateasingle-viewbackendforbetter customerinsights.Italsoneedstoprovideakeycustomerfacingelement:registrationandlogin.WithCIAM,an enterprisecanaggregatedatafromdifferentaccountsand engagementpoints,whichenablesasingleviewofthe customerthroughouttheirjourneyandcreatesaseamless omnichannelregistrationanduserexperienceinstore,on desktop,mobiledevicesandmore.
AsaCIAMindustrypioneer,Janrainrecognizedtheneed foranenhancedIAMsolutiondesignedspecificallyfor customersearlyonandcreatedacloud-basedidentity ® platform,JanrainIdentityCloud,thatworld-renowned brandslikePfizer,Samsung,Philips,McDonald’sandDr Pepperrelyontosecurelymanagebillionsofidentitiesand offerseamless,omnichannelcustomerexperiences.Theyall benefitfromtheJanrainIdentityCloudfeaturesetthatis optimizedforlarge-scaleconsumerusecases.To adequatelydothis,theJanrainIdentityCloudenablesthe followingkeyfeatures--amongothers--ontopofstandard IAMcapabilities:scalability,userexperienceandsecurity.
InaCIAMusecase,thevolumeofidentitiesismuchlarger, asalargeenterprisewillhavehundredsofthousands,ifnot millions,ofcustomersinitsdatabase.Acloud-based identitymanagementsolutioncanscaletoaccommodate tensofmillionsofidentities,performduringtrafficspikes frommarketingcampaignsandothertriggers,andadaptto complexusecaseswherecustomeridentities,device identitiesandidentityrelationshipsaremanaged.
Userexperience(UX)isaconsiderationthatisuniqueto CIAM.ForatraditionalIAMprogramthatisusedfor employeesonly,UXisimportantbutnotcritical. Employeeswillhaveahighertoleranceforlessstreamlined UXbecause,frankly,theydonothaveachoice.Ina customerusecase,enterprisesrisklosingacustomerwho hasabaduserexperience.AccordingtoChatbots Magazine,91percentofunsatisfiedcustomerswillnot returnforarepeatpurchaseorservice.WithJanrain, enterprisescantranslatethebenefitofasingle-view customerdashboardonthebackendtoafrontendUX
How brands should position identity & access management for employees and customers
wherecustomersreceivepersonalizedcommunicationsand streamlinedregistrationandloginacrossdigitalproperties thatcomplementofflineexperiences.
Whilebothemployeeandcustomerdataprivacyare important,enterprisesarecollectingcustomerdatathatis arguablymoresensitivethanemployees(e.g.banking information,medicalhistory,onlinebehavior),andintoday’s privacyclimate,datasecurityissimplynon-negotiable.A sophisticatedCIAMsolutionmustbeheldaccountableforits securitystandardsandbeabletoreduceanenterprise’srisk forbreaches.WithCIAM,informationsecurity,ITand marketingteamsmustalignwiththeirvendortoassure rigoroussafeguardsareinplacetoreducerisk.Janrainleads theCIAMcategoryinaccreditedthirdpartycertificationsand proudlyearnedanumberoftopsecuritycertifications, including:CSASTARLevel2,ISO27018,ISO27001:2013, SOC2TypeII,HIPAAandHITECH.Inaddition,Janrainhas partneredwithAkamai,theworld’slargestandmosttrusted clouddeliveryplatform,toprovideanaddedlevelofsecurity toshieldJanrainclientsandtheircustomersfromdata breaches.
Digitaltransformationisastrategicinvestmentonmostneartermenterprisebusinessplans,promptingbusinessleadersto

workcross-functionallytoputanidentitymanagement strategyinplace.RatherthanretrofittingatraditionalIAM solutiontoaccommodatecustomers,pragmaticbusiness leadersshouldbuildoutalargeridentitymanagement strategy,whereemployeeandcustomerIAMaresubsets withdifferentfeaturestoalignwiththeirvastlydifferent objectives.Identityisbecomingacorepartofbrand strategy,furtheremphasizingtheneedtomakesureidentity managementisdesignedforsuccess.Byimplementinga dedicatedCIAMsolution,anenterprisewillbenefitfrom thescale,userexperience,andsecurityneededto successfullyservecustomersinthedigitalage.
Foundedin2002,JanrainpioneeredCustomerIdentityand AccessManagement(CIAM)andiswidelyrecognizedby industryanalystsasaglobalCIAMleader.TheJanrain IdentityCloudprovidesidentitymanagement,securityand activationsolutionsthatenableseamlessandsafecustomer experiencesacrosstheirdigitallyconnectedworld,while providingenterpriseorganizationswithdeepcustomer insights.Janrain’sidentitycapabilitiesincludesocialand traditionalloginandregistration,singlesign-on,customer profiledatastorageandmanagement,customersegments, customerinsightsandengagementsolutions.Thecompany reachesover1.75billiondigitalidentitieswithover3,400 commercialdeployments.JanrainisbasedinPortland, Oregon,withofficesinLondon,ParisandSiliconValley.
CIAM is all about easier and secure account access, friction-free customer experiences, and allowing companies to gain a better understanding of their customers, their needs, and how offerings resonate with their consumers.
Fromtheinceptionofpackagedapplications, companiesofallsizeshavetakenadvantageofthe economiesofbuilding,maintaining,changingand deployingfunctionalitythroughthirdparty softwareproviders.Whybuildageneralledgeror payroll/humanresourcessystemwhenyoucan licenseitinstead?Whynotleverageoutofthebox functionalityofferedbythirdpartysoftwareand relyonthevendortooffersupportand maintenanceandstaycurrentonregulatory, industryandprocessbestpractices.
Shoeb Javed CTO Worksoft
Thefirstgenerationofmainframesoftware transformedquicklyasthetechnologyevolved, introducingclient-serverasthebetter,morecosteffectivedeploymentplatform.Theapplications themselveswerestillbeingdevelopedand deployedinfunctionalsilos–theirinteractionwith othercriticalfunctionsofthebusinessanafterthought.Althoughlessthanideal,interfaceswere developedtotransportdatafromonesystemtothe next–leadingtotheintroductionofmiddle-ware asaneconomicalmeansof“connecting”thesilos.

Atthattime,SAPemergedastheleaderindelivering comprehensive,end-to-endbusinesssolutionsonthemost advancedplatforms.Theyquicklycapturedthemarketand cross-industryadoptioncontinuedtodeliverbestinclass resultstotheircustomers.PeopleSoftwasalsointroduced tothemarketduringthisera,initiallyfocusingonthe payroll/humanresourcesmarket.Theyultimatelystarted developinganddeliveringERPandCRMsystemsaswell.
Changecontinuedtoaccelerateasweb-basedsystemswere introducedwhichimpactedtheeconomicandtechnological dynamicsof“userrequirements,”development, deployment,andcosts.
Throughoutthisevolution,industries,companiesand individualsnotonlydevelopedanincrediblerelianceonthe performanceoftheir“systems,”butforwardthinking organizationssawthisasaquickpathtocompetitive advantage.
Theproblemthenasnow–howdoyouacceleratethevalue ofthetechnologyinvestmenttothebusiness?The technologywaspurchased,licensed,andimplementedto achieveaspecificsetofbusinessbenefits.Whenitcomesto theselargeenterpriseapplicationinvestments,companies conductin-depthevaluationsandbuildbusinesscasesto mapoutexactlywhatresultstheyexpecttorealize.This typicallyinvolvesalookatwhatfinancialandhuman capitalinvestments–timeandmoney–willbeneededto achievesuccesswithaproductaswellasthefinancial, efficiency,andcompetitivegainsthatcomewiththe ongoinguseofthesoftware.
Ononesideoftheequation,developmentmethodshave evolvedtomeetthisneedforspeed.Waterfall methodologiesarebeingreplacedwithAgile.DevOpshas becomethenewbuzz-word.Butthere’ssomethingelseto consider–thebusinesssideofthings.Thereisaneverincreasingrelianceonpackagedapplicationstoexecuteand delivercriticalbusinessoutcomes.It’simportantthat applicationsaredevelopedanddeployedquicklyand changescanbemaderegularly,buthowdoyouensurethat businessprocessesarerunningflawlessly?
Surprisingly,manycompaniesaremanagingtheirenterprise applicationprocessesmanually.Thismeanshoursofwhiteboardmeetingsspenttryingtounderstandexistingbusiness processes.Weeksduringeveryprojectspentwritingtest scriptsthatbreakwhensomethingchanges.Delaysin deliverybecausemanualtestingcan’tkeeppacewith
businesschange.Theimplementationandongoing managementofenterpriseapplicationsiscomplex,anda crucialcomponentismakingsurethatend-to-endprocesses work—everytime,everyday.Manualorfirstgeneration testingmeanssystemdowntime,errorsinproduction, wastedtimeandenergyandcompaniesleftopento technology
Thebiggerpictureisthatthoseapproaches
Shoeb Javed, chief technology ofcer, Worksoft, is responsible for the technology strategy, software development, quality assurance and customer support for all Worksoft solutions. As CTO, Shoeb also works with quality assurance and business leaders of some of the largest global Fortune 1000 corporations to help automate testing of complex packaged enterprise applications to speed up project timelines and improve operational efciencies.
risk.
are fundamentallystandinginthewayofachievingtheresults companiessetouttoachievewithpackagedapps.Howcan youmakethefinancial,productivity,andcompetitivegains thatyouwerecountingonifyourprocessesaren’t performingflawlessly?
Thankfully,theansweristoday’sfifth generationtestautomationthatis enablingbusinessusersand organizationstoadopt,accept,and utilizenewapplicationsfaster.When processesacrossenterprise applicationsareexecutedseamlessly andasdesigned,companiescan harnessthepotentialoftheirenterprise applicationstoachievestrategicgoals likeenteringnewmarkets,increasing revenue,andmaintainingacompetitive advantage.
Worksoft,thepre-eminentfifth generationautomationplatform, deliversunmatchedspeedin automatingtheidentificationofcurrent businessprocessesandautomatically creatingteststoensurethateach business-criticalprocessworksas required.Anindependentstudyof Worksoftcustomersbyindustry analystIDCidentifiedmanyunique benefitsofWorksoft’sautomation platform,butchiefamongthemwas acceleratingdeliveryofthese applicationsbyanaverageofnearly twomonths.Considerhowmuchmore youcouldaccomplishifyoucouldcut weeksandmonthsfromeveryproject.
Leadersacrosstheglobehaveadopted Worksoftastheirweaponofchoiceto improvetheirfinancialandoperational positionsintheirrespectiveindustries.
Firsttomarketwithautonomouscars? Movingyourbusinessmodelfrom DVDstoonlinesubscriptionservices? Evolvingfromanonlinebookstoreto theworld’slargestinternetretailer? Thesecompaniesdidn’tsimplytryto
keepup.Theyweredeterminedtolead.
Today’sdigitaleconomybrings massiveopportunitytocompanies lookingtodisruptthemarket.There hasbeenafundamentalchangetothe businesslandscapeandcompanieswho arecompetitiveinnovatorswillwin.

AbouttheCompany: Worksoftprovidestheworld'sleading automationplatformforenterprise applications.Companiesworldwide relyonWorksoft'sautomatedbusiness processdiscovery,documentation, compliance,testing,riskanalysis,and RPAtosupportcriticalpackaged applications,includingSAP, Salesforce,Oracle,Workday, SuccessFactors,ServiceNowandmore. Ourfifth-generationautomation platformhelpsenterprisesaccelerate innovationandchange,lower technologyrisk,andincrease efficiency.Ourecosystemincludes partnershipswithAccenture,IBM, Cognizant,SAPandourGlobal5000 customersinclude3M,Intel, Microsoft,Siemensandmore.



SaaSor‘SoftwareasaService’isbeingusedrigorouslyincurrentbusinessventuresasitprovides moreaccuracyandvisiontoanybusinessproject.Interestingly,withthissolution,theimportance ofinstallingthehardwaredevicestorunthedataanddifferentapplicationshaslostits importance.Itisaveryselectivesectionofcloudcomputing,throughwhichthefuturebusinessdata collectionprocesscanbesimplerthanever.SaaSisaveryprofitablegenreinthefieldoffuturistic businessventures,andthusaquestionmayariseabouttheSaaSbusiness,andthatiswhatcouldbethe revenuestreamforsuchbusinessenterprise,oringeneralwords,theearningprocessfortheSaaS business!
UnfortunatelysomepeoplebelievethattherearenosuchgoodwaysofearningrevenueforSaas businessandiftherearesomesources,thoseareveryminorintheirconducts.Interestingly,thereality andthecurrentsituationareotherwise,andthereareanumberofwaysinwhichtheSaaSbusinesscan earnitsrevenue.‘Payment’togetthesoftwareisnottheonlymodeofearning,andtheenterpriserof thisbusinesscanearngreatrevenuewithmultipleoptions,withoutstressingoutonparticularsectionof thebusinessventure.Herearesomeofthesolutions:
ASet-upcostisoneofthecommonwaystoearntherevenueanditgivesclaritytotheprovidersabout theauthenticityoftheusersanddeterminesthecommitmenttoo,thusitisagreatwaytoexplorethe mindsofthecustomersandthepossiblefuturerelationshipwiththeusers.Ontheotherhandthesetup earningcanactuallyleadtotheupsellmarketfortheSaaSproviders.Itisoneoftheeasiestwaysto enhancetherevenuethroughtheexistingcustomers,anditisagreatbusinessopportunity,asthisway ofearninglessensthedependencyofthebrandonthepressureofaddingupnewcustomers.To maintainthecontinuitywiththeexistingcustomerscertainfacilitieslikeofferingadditionalstorage, speed,data,bandwidthorthefrequencyareenlistedas'services'.Though,thisprocessofearningis largelydependentonthebenefitoftheproductortheservice,alongwiththeneedorrequirementofthe client.
ItisanothergreatwaytoboosttheearningfortheSaaSbusinessas,throughthisprocess,itbecomesa two-waysystemtogetbusiness,wheretheusersadvertiseorselltheproduct.Astheprocessis
dependentontheusers,itisnotdependentonany otherexternalwayfromthebusinessproviders' side.TheSaaSprovidersareonlyresponsibleto paythecommissionaftergettingtherevenue.So itisdefinitelyawin-winsituationfortheSaaS providers.

Saasprovidersareonthevergeofaddinganew structureforgreatrevenue,whicharecustomer serviceandinformationcharges.Aswiththis system,thebusinessprovidersoffertosalesome oftheresearchedinformationtotheclients.Itis notverydifficultfortheclientstovaluethemby payingthemoneyastheyaregettingagreathelp, andinterestinglyitcanworkfortheclientsto clingtotheserviceswhichcancreatethepathfor morebusiness.Basically,agreatcustomerservice isthekeytoearngoodmoneyandwiththe satisfactionofthecustomers;theprocesscanbe ontheloopforagreatrevenuesystem.
Advertisementsarethemostcommonsectorof
earningmoney,anditisthebestwayofearningthrough thefreeversionusers,butnotveryaptforthepaid customers.Asthepaidcustomersalreadypayacertain amount,addingadvertisementscancreateanegative impactonthem.Soeveniftheadsarethere,theymust beinawaythatlookslessannoyingfortheusers.
Thisisratheracomplicatedbuteffectivemethodof earninglucrativerevenue.IftheSaaScancoordinateor workwithothersoftwareapplications,theimportance ofitcanrisetoawholenewlevel.Thisworkmodelcan domagicforsomeoftheusersanditcanhaveagreat valueorearninginthefuture.Butthisgreatsystem comeswithcertainrisks,andthereasonis,theamount ofmoneyinvestedtocreateandrunit.Butifthe developerscanbeassuredofitsserviceandthedemand ofthecustomers,itcanturnouttobeagreatmoneymakingoption.
WhensomeoftheSaaSissoaptthatthepotential customerswanttoavailitfortheirbusinesspurpose, thetie-upwiththeprovidersortheresellingofthe productcanbebeneficialformthepointofviewofthe revenue.ThisprocessisknownastheWhiteLabel Licensing.
Attheendofthisdiscussion,theconclusionis,abetter servicecanopenupnewtrailsforRevenueStreamsfor SaaSBusiness.SaaSisnotanewconcept,butthevast implicationisdefinitelynew.Sothereareanumberof scopesyettobeexploredbythedevelopersofthisnew business.Thus,thefutureandthesuccessofSaaS businessisdependentonexploringvariouswaysfor SaaSrevenue,andwithmoreinnovativeideasforthe revenue,themarketofSaaSbusinesswillbemore strengthenedtotouchthezenith.


