
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 12 | Dec 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 12 | Dec 2024 www.irjet.net p-ISSN: 2395-0072
Bindushree A N1,Lavanya N G2, Basava H K3, Harsha S Kulambi4
1Bachelor of Engineering, Information Science and Engineering, Bapuji Institute of Engineering and Technology, Davangere, affiliated to VTU Belagavi, Karnataka, India.
2Bachelor of Engineering, Information Science and Engineering, Bapuji Institute of Engineering and Technology, Davangere, affiliated to VTU Belagavi, Karnataka, India.
3Bachelor of Engineering, Information Science and Engineering, Bapuji Institute of Engineering and Technology, Davangere, affiliated to VTU Belagavi, Karnataka, India.
4Bachelor of Engineering, Information Science and Engineering, Bapuji Institute of Engineering and Technology, Davangere, affiliated to VTU Belagavi, Karnataka, India.
Abstract - Inadditiontorequiringsignificantsocialand humanresources,thevotingprocessinatraditionalvoting environmentcanoccasionallybecomehighlyinconvenient since some voters are reluctant to go to a polling place to cast their ballots. Internet voting is made easier by the advancementofcomputernetworksandthedevelopmentof cryptographymechanisms.Wepresentasecureinternetin this paper. voting procedure that can be used for online voting.Thesuggestedvotingmechanismwill work forbig companieswithofficesspreadacrossmultiplelocationsand is based on digital signatures and cryptography. Three separate phases make up the suggested system: the registration phase, the authentication phase, the voting phase, and the counting phase, which involves the voter, votingserver,andvotingauthority
Key Words: Internet voting, digital signatures, and web servers
Intoday'sdemocraticworld,thephraseselectionandvoting arenowwidelyused.Internet-basedelectronicvotingwould befarmorelucrative.Manyvoterswouldvaluetheabilityto castaballotfromanylocation.Employeesfromeveryoffice canparticipateintheelectionfromtheirownofficesifthe companyhasofficesspreadacrossmultipleregionsanduses online voting. As the name suggests, electronic voting is a voting procedure conducted by computers or other electronic media. Generally speaking, an online voting systemshouldmeetthefollowingcriteria:
1.Accuracy
2.Simplicity
3.Democracy
4.Verifiability
5.Privacy
6.Security
Securityandprivacyaretheprimaryconcernsforsuchan online voting system, and from that perspective, implementingasecureInternetvotingsystemseemstobe anotherapplicationofcryptographyandnetworksecurity. Electronicvotinghasbeenextensivelyresearchedoverthe past 20 years, and numerous e-voting systems have been proposedinthelastfewdecades,increasingbothsecurity andeffectiveness.However,tothebestofourknowledge,no comprehensive and workable solution has been found for large-scaleelectionsconductedoveranetwork,suchasthe Internet.
Our method proposes a useful implementation of current cryptographic techniques and digital signatures that guaranteevoterauthenticationandtheintegrityofthevote cast.onbothlevels.Sinceeveryvotingsystemcriterionmust besatisfied,designingasecureelectronicvotingsystemover anetworkisinfactanextremelychallengingprocess.Ifeven oneofthestandardsisnotfollowed,theremaybeflawsand kinks that a third party could use to alter or fabricate the finerpoints.Theelection'soutcomeisthendetermined by adding up all of the votes, which the authorities jointly decipher. Voters must be able to keep their votes secret underavotingsystem
Thisstudy[1]reviewsthevoteverificationtechniquesthat arecurrentlyinuse.Bytalkingabouttheirshortcomings,we can suggest a stronger and more dependable vote verification system. approach. The authors of this study aimedtosuggestavoteverificationmethodthatwouldallow allelectionparticipantstoverifyvotesandbeabletoverify votesagainstsignificantpotentialthreats.Theymustlookat a mix of procedural and technical options to achieve this goal.Theymustlookintoacombinationoftechnologicaland proceduralsolutionsforthisreason.
The design for electronic voting systems based on trustworthywebserviceswassuggestedbytheauthor[2].

Volume: 11 Issue: 12 | Dec 2024 www.irjet.net p-ISSN: 2395-0072
Thefindingsfromtheexaminationofthesuggesteddesign's evaluationshowedthatsolution,significantlyimprovethe dependability. outlined how this architecture can address the primary needs of electronic voting. One of the most crucialcharacteristicsandthemostcrucialprerequisitefor electronicvoting,alongwithsecurity,isavailability,whichis met. Since security is a crucial component of electronic voting systems, the author has employed pre-existing techniquestoaccomplishwebservicesecurity.Theauthorof thestudy[3]suggestedanarchitectureforanonlinevoting systemthatreliesontrustworthywebservices.Hethenused RewardPetriNetsandRBDtomodelthissystem.Lastly,he conductedaquantitativeevaluationofthesemodels.Hecan choose whether or not to apply this system by also consideringtheevaluation's findings.Itis evidentthathis architecturesignificantlyimprovedreliability.Healsotook into account the primary criteria for voting, such as confidentiality, portability, precision, originality, and so forth. He employed a few strategies to develop a secure systemwhilekeepinginmindthesecurityrequirementsof voting. He demonstrated that even if some parts fail, this systemwillstillfunction,andthatavailabilityandsecurity aretheThemostcrucialvotingsystemspecificationswillbe covered. Voters can vote online with ease and without spendinganytimeormoney.Thus,systemshavetheability tomotivatepeopletovote.
Theauthor[4]suggestedanelectronicvotingprocessthat guarantees the accuracy and anonymity of voters and candidates.Therearestillalotofproblems,aswhenalotof votersWilltherebeadenialofservice(DOS)ontheInternet iftheycasttheirvotessimultaneously?Howcanasafeand effective online voting system be created? However, the several measurement levels included in our plan have reducedthepossibilityofinjusticeinrealelections,atleast forthecountingprocess
Accordingtothesuggesteddesigninpaper[5],votingisonly permittedatthelocationswherevotingstationsaresetup. Despitethefactthatmobileterminalscanbeusedforvoting Depending on the wireless conditions, extra security standardswillbeneededeverywhereifthewirelessnetwork continues to grow in the days ahead. Additionally, the authenticationprocessneedstobestrengthened,andthere shouldn't be any forced voting or data disclosure on the wireless network. One important method that democracy reflectsthewillofthecountryisbyvoting.Forthisreason, further research on security technologies used with electronicvotingsystemsshouldbeongoing
Anonlinevotingprocedurewaspresentedbytheauthor[6]. Blind signatures are used in the proposed internet voting protocoltosafeguardballotcontentwhileitisbeingcast.As wefeelthatasecureelectronicvotingsystempreventsballot buyingandenablesallvoterstoconfirmtheoutcomeofthe vote. The suggested internet voting protocol is both verifiableanddetersballotpurchasing.Duringtheelection,
any unapproved party or candidate may still attempt to purchase ballots. However, once the election results are announced,novotercandemonstratewhoseballottheycast. Toputitanotherway,ballotpurchasingmaystilloccur,but the buyer cannot be certain that the voter will mark the ballotinthewaythattheydesire.
Voters,votingclients,votingservers,andvotingauthorities aretheparticipants.Thefollowingphaseswillmakeupthe system:
1.Enrollment
2.Verification
3.Castingaballot
4.Counting
Phase of registration: Anauthorizedrepresentativeofthe corporation will visit each office and, after confirming an employee'sidentity,registerthemtovoteandGivehimor hertheusernameandpassword.Forsecurityreasons,the votercansubsequentlychangetheirpasswordonline,just liketheycanwhentheyfirstreceivetheirATMcardandPIN fromthebank
Phase of voting: Duringthisstage,thefirstballetrequestis made.Thepublicencryptionkeyandballetwillbesentto the voter. This key will be used to encrypt the vote. That encryptedvoteisoncemoreutilizethevoterprivatekeyto digitallysign.Thevotingserverreceivesthedigitalsignature andencryptedvote.Thevotingserverstorestheencrypted voteafterfirstverifyingthedigitalsignature.
Phase of counting: All encrypted votes are first decoded beforebeingcounted.Todecrypt,theauthorizedindividual willinputtheprivatedecryptionkey.TheAftercountingis complete,theoutcomewillbeannounced.
This system is being designed for a company with offices spread throughout several cities. Our top priority is to ensure the security of the cast ballot while it is being transportedfromWeareconcentratingonofferingsecurity againstbothpassiveandactiveintruderswhenitcomesto votertovotingserverstorage.Avoter'scastballotcanbe accessedbyapassiveinvader,posingathreattothevoting system's privacy and confidentiality features. The active invadermayinterferewiththeintegrityofthecastvoteand tamper with it. Therefore, we are utilizing the idea of cryptographyandutilizingdigitalsignaturestoaddressthis securityissue.Inordertoprotectagainstpassiveintruders, we are encrypting the client system's cast vote before sendingittovotingserverviatheinternet,wherethevoteis decryptedontheserversidepriortocounting.Forthis,we needtwokeys:oneforthevotersystem'sencryption,which

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 12 | Dec 2024 www.irjet.net p-ISSN: 2395-0072
should be known to the public, and another for the decryptionoftheencryptedvotepriortoitscountingonthe voting server, which needs to be private. Therefore, two asymmetrickeysarerequiredforthispurpose.
Weareutilizingdigitalsignaturestoprotectagainstactive intruders who could change or tamper with the cast vote whileitismovingfromvotertovotingserver.Whenavoter Aftercastinghisorherballot,thevoterwilldigitallysignit usingtheirownprivatedigitalsignatureandsendittothe voting server, where the voter's publicly known digital signatureverifier will verify thesignature. Weareusing a pairofasymmetrickeysforeveryregisteredvoterinorder to achieve this goal, which calls for each voter to have a private digital signature and a public digital signature verification.Asshowninpicture1
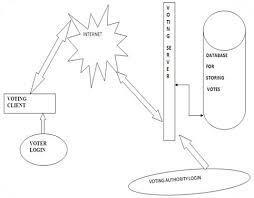
Figure1: Web-basedonlinevotingsystemdesigncomprise thevotingauthority,votingclient,votingserver,andvoter.A voterwhohasregisteredconnectstothevotingserver by utilizinghispasswordandaccesscredentials.Throughthe internet, the voting client and voting server exchange information.
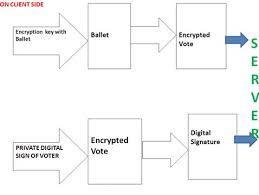
Whenavoterwantstocastaballot,hefirstrequestsaballet fromtheserver,whichthensendstheballettogetherwith thepublicencryptionkey,asshown infigure2.Thevoter encryptscastaballotwiththiskey,andthenusedhisprivate
keytodigitallysigntheencryptedballot.andforwardthem both to the server. Using a public signature verifier, the votingserverusesdecryptiontovalidatethevoter'sdigital signatureontheserverside.Votingisstoredifthesignature islegitimate.forcounting;ifnot,thevoteiseliminated.
Inordertoregistervoters,theauthorizedvotingauthority willvisiteachcompany'sofficeandmanuallyconfirmeach employee'sidentity.Whenregisteringtovotecreateapairof asymmetric keys, one private and one public. The voter keepshisprivatekeyprivate,andthepublickeyissentto the server along with his other voter registration information.
Voters can modify their password for security reasons by loggingintothewebsite.
Voters log in with their own username and password on electionday.Theserversendstheballettogetherwiththe publicencryptionkeywhenthevoterrequestsit.Thevoter votedandusesapublicencryptionkeytoencryptit.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 12 | Dec 2024 www.irjet.net p-ISSN: 2395-0072
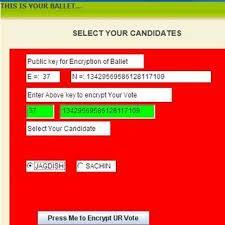
Everycandidate runningfor office hasanIDthat wehave internallyallocated,andwhenavotercastshisorherballot, theIDisencryptedusingapublicencryptionkeythatBallet provides. The voter then uses their own private digital signaturetodigitallysignthatvote.Andforwardthesetwo totheserver.
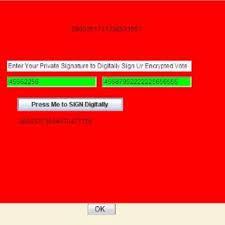
Figure 6: showsapictureofBalletfollowingdigital signatureandencryption.
Thevoteis encrypted,so if a passiveintruder manages to accessthecastvote,hecannotdeterminewhothevoteris.If an active hacker changed the vote and sent it to the polls Because the vote is digitally signed, the server can easily detectwhenavotehasbeenedited.Whentheserververifies thesignature,itdiscoversthatthevotehasbeenalteredand notifiesthevoterofthis.
6. Conclusion
Afterconductingtestsonoursystem,wehavedetermined thatitoffersprotectionagainstallkindsofattackswhenthe vote is moving from the voting client to server for voting. Security risks from both active and passive intruders are
includedintheseattacks.Thistechniquecanalsobeusedto getstaffopinionsonparticularmatters.Inthefuture,voter authentication will be more secure if we can utilize the voter'sthumbimpressionortakeapictureoftheirfaceand compareitwithaphotoinourdatabaseratherthanusing theirusername.Comparedtoaregularvotingsystem,this onesavesmoneyandtime.Italsopreventspaperwasteand isenvironmentallybeneficial.
[1]"VoteVerificationthroughOpenStandard:ARoadmap," by Ali Fawzi Najm Al-Shammari and Sergio Tessaris, 9781,4577-0953-1/11IEEE2011.
[2] "An Architecture for E-Voting Systems Based on DependableWebServices,"byAmirOmidiandMohammad AbdollahiAzgomiIEEE©2009978-1-4244-5700-7/10
[3]SaeedMoradiandAmirOmidi,"QuantitativeAssessment and Modeling of an Internet Voting System Using Dependable978-1-4673-0479-5/12/©2012IEEE
[4]WebServices
[5]HaijunPan,EdwinHou,andNirwanAnsari,"Protecting the Privacy of Voters and Candidates in Electronic Voting Systems"IEEE©2011978-1-61284-680-4/11/$26.00
[6] An analysis of the electronic voting system employing blindsignaturesforanonymitywaspresentedbySeo-IlKang and Im Yeong Lee at the IEEE 2006 International ConferenceonHybridInformationTechnology(ICHIT'06)07695-2674-8/06.
[7]"AVerifiableElectronicVotingScheme,"Chun-TaLi,MinShiang Hwang, and Yan-Chi Lai, 2009 Sixth International ConferenceonInformationTechnology:NewGenerations
[8]“DistributedeVotingusingtheSmartCardWebServer” by Lazaros Kyrillidis, Sheila Cobourne, Keith Mayes, Song Dongy,andKonstantinosMarkantonakis3/12/2012978-14673-3089IEEE
[9]"Watermarkingine-votingforlargescaleelections,"by Yousfi Souheib and Derrode Stephane, 978-1-4673-15203/12/$31.00©2012IEEE