Network Modernization





This document is intended to be used as a guide and reference between Managing Information Systems 3 Inc. (MIS3 Inc) and City of Kawartha Lakes (The City). No part of this document or related files may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise stated) without the prior written permission from Managing Information Systems 3 Inc. (MIS3 Inc.)

This document has been revised by:






MIS3 has performed a Network Modernization Assessment for The City. A recent City of Kawartha Lakes (The City) survey and IT Satisfaction Scorecard identified Network Infrastructure as the #2 priority overall for leadership staff and was the #1 priority for many departments including Engineering, Public Works, and Community Services with significant mobile and remote access requirements and non-regular business hour work schedules.
MIS3 understands The City office locations are centrally networked via a hub and spoke architecture providing access to centralized resources, data, applications and communication gateways for over 130 remote sites.

Voice services are centrally provided via a phone system in the City’s data-center using PRI trunks and both analog phone lines and VoIP are in use at City facilities. VDI and thin clients are used by half of The City staff to access applications and services alongside VPN connectivity.
Over 400 mobile devices are in use, managed by a Mobile Device Management (MDM), for Apple iOS and Android devices. Given the distributed work force, access to applications located on premise and Software as a Service (SaaS) applications require flexibility and agility with cyber security visibility, control and governance at the forefront. Moving forward, a fully centralized network and traditional VPN solution may no longer be the best approach in providing secure, reliable, fast network services to employees across all nine lines of business.
The nine City departments expect a positive change and plan to create a network modernization strategy to prepare The City, for future service innovation and evolution. MIS3 has been working with the City IT team to understand the various lines of business, business requirements, feedback from the satisfaction scorecard, technical diagrams for the current state, future state requirements, and workflow processes.
In our understanding of this information, MIS3 have developed a current state to future state network roadmap with recommendations that will help The City, move and adopt towards a modernized network architecture. By continuing to keep the lights on and modernizing how existing and new services will be delivered and consumed securely The City will have a path forward to execute against.
The City of Kawartha Lakes (The City) completed an internal IT satisfaction survey. The purpose of the survey was to better understand IT satisfaction across the various lines of business and the value IT is providing.

The relationship between the business and IT was centered around 4 core areas:
Executes requests
Communication
Understanding of the needs
Training
An IT capacity scorecard was also developed to understand:
Capacity needs
Shadow IT
Project completion
Work orders
The city benchmarked their performance by categorizing capacity and relationship.
Capacity looked at 2 critical areas:
- Shadow IT, procurement of non-sanctioned IT applications
- Satisfaction of service desk Relationship
- Executes requests against business needs
- Understanding of needs
- Communication between IT and business
- Training measured by quality and timing

The survey determined The City was above average compared to the market in shadow IT, executes requests, and below average in capacity constraints and training effectively.
The scope of this project included a review of the IT Satisfaction Scorecard, prepared by Info Tech Research Group. In our engagement, we began gathering information from IT and application stakeholders to understand current state of all infrastructure, applications, databases, mobile devices, remote access and security access with authentication.
A deeper conversation around the business vision, alignment with the various departments and documenting requirements through review of existing surveys, questionnaires, diagrams, interviews, locations, application portfolio were completed.
MIS3 has performed a Network Modernization Assessment to review current state and establish future state recommendations to help improve the IT services. Network architecture, application access, application performance, mobility and the overall communication and relationship between the business and IT have been reviewed. The foundation of this report is based on business requirements, their vision and satisfaction with IT and their performance.
A critical component for this report and assessment is centered around the existing network at The City. MIS3 has established a current state of networking challenges, opportunities, priorities and a firm understanding of the overall architecture.

The City, has developed 3 categories to enhance their approach to aligning business outcomes and objectives with technology.
1. IT Strategy
- Innovation & Transformation
- Business Support

- IT Capability Improvement
2. IT Performance
- Develop meaningful service metrics and ensure business / user satisfaction
- Maximize business value from IT through benefits realization
3. Business Relationship Management
- Transform IT into a value creator
- Build and deliver a business focus and narrative for IT, less technical
- Manage stakeholder relations and priorities
Core departments involved in this survey included:
9. Fire Services
Engineering and Assets scored the lowest with a 50% satisfaction rate and their top 3 priorities to improve the level of IT satisfaction were:
1. Improve the network and communication infrastructure
2. Devices being used
3. Data quality
The city has common areas of improvement across all lines of business focusing:
- Business applications
- Service desk
- Network & Communication Infrastructure
- IT Security

- Data Security
- Devices
MIS3 completed the following deliverables listed below, to accomplish the scope of achieving a network modernization strategy for The City. The six phases below, describe which areas were reviewed to better understand The City’s networking and security environment to help build a recommendation roadmap for a future state and modernized network:
Establishing a current state with an understanding of business requirements, devices, users, locations, age of hardware, software, number of devices, offices and more.
Application and database portfolio and review including criticality of application, internal or external facing applications, line of business owners and more.

Understanding of application access, authorization workflow, review of tools from MFA, SSO, Virtual Private Server (VPS) and more across laptops, workstations, mobile devices.
Phase 4 – Policy Review
Review of cyber policies from remote desktop, cloud security, data and other relevant ones that apply.
Phase 5 – Performance Review
Review of network performance and any latency concerns across applications, lines of business, hub and spoke architecture review.
Phase 6 – Mobility Review
Review of devices, operating systems, access, authentication.

In closing, MIS3 will provide a framework to The City to adopt our Transformational IT practice. We help all organizations including local government, combine business value, achieving their business objectives with an outcome enabled approach with our transformational IT approach executed by new and emerging next generation technology frameworks, technology, and tools.

Our Transformational IT practice consists of 2 specific areas:
IT Modernization framework helping clients modernize how they keep the lights on and deliver new applications and data services utilizing SaaS, Public Cloud (IaaS / PaaS) and om premise private / hybrid cloud. Guiding and leading the way in developing a secure architecture, user access, zero trust and compliance.
Executing against a proven Secure Digital Transformation framework focusing on the 4 core business pillars of Digital Transformation listed below. We combine the business objectives and vision with next generation technology strategies and tools to realize the outcomes for our clients.

MIS3 will help The City achieve its Network Modernization plan by moving towards the new IT service delivery model. Adoption of SaaS, Public Cloud and Hybrid Cloud on premise for new and existing applications. Networking functions will become automated, software defined for ease of management and provisioning, convergence of networking and security brought to the edge rather than traditional model of steering all network traffic back to the local data centre.


Through IT Transformation, The City will have a blueprint in place to begin their network modernization roadmap, plus a secure digital transformation framework to execute against.

A current state is a description of a subject matter in its present form (i.e. the ‘As is’ state).
The description for the City of Kawartha Lakes will be broken down into the following area:

1. Internet perimeter
2. Core routing
3. Servers
4. Wide area network (WAN)
5. Local area network (LAN)
6. Voice (phone) system
7. Internet of Things (IoT); machine networks
8. SCADA network
9. Provincial systems
10. Management systems.
The city currently has 135 sites connected via hub and spoke architecture across 30+ communities. The connections vary between sites and speed consisting of:
- Wireless
- City owned fibre
- Fibre
- Dark fibre
- Cable
- DSL
- Mbps down between 1.5 – 120
- Mbps up between 1-100

CKL has a symmetrical 500Mbps (megabits per second) fibre optic Internet link. This link is used by internal staff and devices (e.g. workstations, laptops, IoT) to access Internet services (browsing, SaaS, etc.). Allow staff remote access from the Internet to CKL applications that are on premises and to allow specific services to be accessed from the Internet.
A single node firewall (purchased in 2019) is connected to the Internet link. The firewall provides security, protection and remote access (VPN clients). In addition to the Internet link, the firewall is connected to the following networks:
1. DMZ; used to allow untrusted users access from the Internet to CKL services.

2. Province; used to provide access to/from Provincial applications to CKL staff.

3. Internal network; link to CKL’s internal network.
The firewall is providing the following services:
1. Access Rules: Standard protection from outside attacks.
2. Network address translations (NAT): Translate internal IP addresses to external IP addresses and vise-versa.
3. Geo blocking: Deny traffic from areas of the world often associated with malicious traffic.
4. Web site blocking: Deny traffic to undesirable websites (e.g. sites that infect devices, unwanted content, no business value, etc.).
5. Limited email scrubbing: Scans electronic mail for harmful payloads that can compromise an internal device (e.g. infect with ransomware, command and control, etc.).
6. Remote access for staff via VPN (virtual private network) connections.
a. No split tunneling: Remote access VPN is configured so that when a VPN connection is established; all traffic, whether it’s for internal servers or external browsing will traverse the corporate 500Mbps Internet link, go through the corporate firewall, and if needed, go back out the corporate 500Mbps link (e.g. a remote user browsing the Internet will go through the firewall and back out again).
In the context of Technology; a demilitarized zone is a network that is created to allow traffic from external untrusted networks/devices to a specific set of internal networks/devices.
CKL’s demilitarized zone is routed through and protected by a single firewall acting as the proxy, load balancer and NGFW.

Servers with shared storage are used to host a high available two node hypervisor cluster. Guest virtual servers are created within the hypervisors. Services provided in the DMZ are as follows:
1. VDI Gateway: A remote access solution for internal staff.
2. Outlook Web Access: Allows secure remote access to email.
3. Secure File Transfer Protocol (STFP): Allows files to be placed or picked up. Uses encryption.
4. Zendto: A solution to transfer large files. Uses encryption.
5. Simple Mail Transfer Protocol (SMTP): Used to send out-bound email.
6. Domain Name Server (DNS): Used to resolve names to IP addresses. In this case, to service name resolution for Internet users.
7. Moodle: An open-source learning platform.
8. Active Directory Federation Service (ADFS Proxy): A means to provide protection to internal Active Directory servers. Used for authentication using Active Directory accounts.
9. Novus Proxy: A means to allow and control traffic from internal users/devices to the Internet.
10. Novus Reverse Proxy: A means to allow and control traffic from external users/devices to internal server services. Can also be used for load balancing services.

A single node router (RO-CH-NOC-CORE) is used for the core routing and switching. The City uses 10Gbps modules to connect the servers and hypervisors.
Additional modules (e.g. 1Gbps) are used to provide connectivity to WAN sites, the Internet perimeter, edge switches, and a WLAN WIFI controller.
The core router provides the following services:
1. Routing
2. Switching
3. VLAN
4. Trunking
5. Gateways for WAN sites connected with fibre

There are eight racks for servers. A Virtual server infrastructure is in place using hypervisors. Virtual machines (aka guests) are created within this environment.
All physical servers have either a 1Gbps or 10Gbps connection directly into the core router.
The WAN consists of; CKL owned fibre, leased dark fibre, service provider links (e.g. cable, fibre, etc.), virtual private network sites, and wireless point to point (P2P). Remote sites connect using routers at the remote end and a WAN router (RO-CH-NOC-WAN) at the main site. Encrypted tunnels are used to create secure links from the remote sites to the head end WAN router.

Sites that use CKL owned fibre or leased dark fibre connect directly to the core router. Fibre connections use a Hub and Spoke topology and a dedicated WAN router (RO-CH-NOC-WAN) is the gateway for each spoke on the WAN. Daisy-chained sites also exist, for example 31 Mary St East connects to 50 Wolfe St, which connects to 33 Mary St East, which then connects to the core router.
Layer 2 broadcast domains extends from the core router all the way down to the last network port on that fibre connection. As an example, 89 St David St, 48 Lagoon Rd and 51 Wilson Rd are all in the same Layer 2 broadcast domain. If a PC connected to switch SW-LANDFILL-SCALE broadcasts an Address Resolution Protocol request (ARP) for the gateway address on the Score router; all switches (8), a firewall, all the network devices, and the core router will get that same broadcast packet request.
A High-speed wireless point-to-point network has been established and connects approximately 15 wireless links and sites. The topology is a combination of hub-and-spoke and daisy chain. The main wireless network from City Hall is to a water tower. From there it connects to the rest of the wireless network (~6 direct connects). There is one point to point wireless link from 33 Mary St E to the Lodge Park switch.
Like the fibre WAN, the Wireless Point to Point network (excluding 33 Mary St E to Logie Park switch) has a broadcast domain that spans multiple links and uses the core router as the network gateway. For example, the gateway for a workstation connected to switch SW-FLEET_SERVICES will be the core router.
The core router is configured with a trunk port that will span the wireless link, and virtual interfaces to handle Layer 3 routing.

The local area network (LAN) switches are a mix of Layer 2 and Layer 3 switches. They provide network ports, switching, Virtual LAN (VLAN) and VLAN trunking functions. A combination of switch stacks and hub-and-spoke connections to edge switches are used. For a hub-and-spoke setup; a switch or switch stack will act as a core switch for that site. 1Gpbs links are used to connect edge switches to the core switch.
Wireless LANs (WLAN) uses a Wireless Controller that is connected to the core router at the main site. WiFi access points (AP) are connected to the LAN switches at various buildings. The WLAN is used by City staff with dedicated accounts and non CKL staff (public user) that have accounts with daily or weekly rotating passwords.

Smaller firewalls are used at many sites to protect the corporate network from untrusted vendor devices and/or to separate devices that are used by the public (e.g. PC at a Library). The number of devices connected to a single firewall is relatively low.
The two main use cases for a local firewall are:
1. Connect untrusted vendor devices, such as Building Automation Systems (BAS), fire suppression equipment, etc.
2. Control traffic of devices used by the Public (e.g. PC at a Library).

CKL has deployed a 2 node high available phone system cluster running in an active/passive mode. Commodity servers are used as the physical servers. Three Telco provided Primary Rate Interface (PRI) lines are used to provide Public Switched Telephone Network (PSTN) services (call in, call out).
Quality of Service (QoS) is configured on the switches such that low latency switching for VoIP traffic is given priority over all other IP traffic. No other QoS policies are configured on the network.

The Internet of Things (IoT) are devices that are connected to a (IP) network, typically act with the physical world (e.g. sensor, controller), exchange data with other devices, and have very little or no interaction with people. They are meant to be configured, run on their own, and send/receive data from a central system. In most cases, these devices are controlled by a central system.
CKL has various IoT devices throughout the network, such as but not limited to; Building Automation Systems (BAS), Fire Suppression, solar panels, security systems, etc. IoT devices that have been deployed are segregated from the corporate network and placed behind a local firewall on isolated networks.
Supervisor Control and Data Acquisition (SCADA) is software and hardware that is used for controlling and gathering data in industrial systems.
CKL has approximately 44 sites using SCADA systems, the primary use is for water and wastewater treatment. Devices on and dedicated to the SCADA network are; SCADA Workstations, PLC’s, hypervisors and SCADA servers. Devices on the SCADA network do not have access to the Internet.
There are three site types for the SCADA network:
1. Hub-Core site (the data centre); collects data from all sites.
2. T1 aggregate site; collects data from T1 and T2 sites, sends data to the Hub-Core site.
3. T2 leaf site; collects data and sends it to a T1 site.
Provincial systems (e.g. ICON) are used by internal CKL staff. A dedicated router, link and server is used. A router provided by and managed by the Province (ENA Router), connects to the corporate firewall. These systems are accessible by internal networks, VPN users and VDI. There is no external access (Internet) to this system.
The city is current using 135 applications that consist of the following makeup:
Software as a Service (SaaS)
- 21 SaaS applications (18 internal facing and 3 that are both internal and external facing)

- 5 SaaS applications are determined to be tier 1 and 16 are considered tier 4
- 7 SaaS applications require VPN connectivity
On premise
- 114 are on premise in the data centre
- 111 applications are internal with 3 being both internal and external facing
- 12 applications are tiered 1 and the remainder 102 are tier 4
- 4 applications DO NOT require VPN access
- 110 applications require VPN access
Using MFA and a captive portal for corporate devices logging in using PW and Username where they are directed and login via token (software). Paramedics use hard tokens but are looking to move towards software tokens.

They use VPN, to connect to a majority of their applications or VDI connection. There is no identity approach for user access or zero trust strategy.
SaaS is becoming more widely adopted and for some of the SaaS applications today the user can go straight to the application or service using public internet. The user experience around performance and access seems to be very positive. That level of speed and experience is one of the areas the city would like to achieve for all applications regardless of location, with a consistent enforcement of cyber security policies, control and visibility but frictionless.
Information management directive establish a policy framework and guideline with the help of council. The City has created a management directive outlining policies across 9 areas outlining responsibilities for management, IT and end users:
1. Information systems

2. Software
These policies apply to all information systems under the jurisdiction of The City, with the exception of, public access computers. The Director of Corporate Services shall be responsible to ensure compliance with this policy.
The network modernization strategy and cyber security will need to incorporate these directives and policies into the overall visibility, control and governance for the future state.
MIS3 reviewed the IT satisfaction scorecard to gain an understanding of challenges and areas of opportunities for improvement within IT.
Top 4 departments that are not satisfied with the network / comm infrastructure today are:
- Engineering & Assets
- Fire Services
- Community Services

- Public Works
Community Services and Public Works having cellular issues with connectivity. Looking to provide laptops to Public Works employees mounted inside vehicles with antennas for improved connectivity and access.
Moving towards mobile apps on their devices to avoid connecting to VDI session for enhanced experience.
Key application in used in the field is Workforce Management for work orders created inside JDE, looking to modernize front end application and making it mobile friendly to complete work in the field rather than coming back to the office to complete at a workstation. All sites access the following applications and services:
Email JDE
Employee website

File services
Zoom, but voice services not at all locations, some have VoIP from analog services.
QoS settings only apply to VoIP traffic, and are not application or user specific. Majority layer 2 switches but being upgraded to layer 3. There is dedicated VLAN’s from several locations to the core.
PBX is centralized for all voice services from call centre to corporate employees built with HA. 3 PRI’s no SIP to telco’s.
Looking to switch to SIP trunking from PRI for the future. Physically splitting the phone system up with dual servers being relocated to different buildings, SIP connections and links.
EOL office phones looking to put in hoteling.
Micro-segmentation is a future goal for their architecture.
Remote workers are always connected via VPN


IoS devices, Apple devices also have EoL devices in the field.
Laptops, workstations, thin clients, chrome books, chrome boxes, android devices. IPAD for long term care.

IPAD in economic development.
Budget for 100 more laptops.
350 thin clients.
150 laptops / workstations (validation required)
No BYOD.
Each employee gets only one device.
507 mobile phones and GPS devices.
Looking to move towards mobile friendly work force management platform (JDE) for work orders and ease of completion in the field.
The City, wishes to consider technology, people and process changes to improve customer service and for the IT Division to better service a workforce that has evolved from on premises to a hybrid of on premise and work from anywhere.
MIS3 review of The City’s network architecture uncovered several findings:
Over 130+ sites across The City, with a variation of connectivity and speeds for both upstream and downstream traffic.
Limitations by the ISP provider due to rural sites forcing either DSL, Wifi or Point to Point connections over dark fibre.
There will be an additional 13 + sites to be added to the total locations before end of 2022.
Majority of applications run in the data centre and all VPN / VDI traffic is routed back to the data centre through layer 2 routing.
Perimeter firewall handles all encryption / decryption (No HA today), load balancing with no proxy in place today.
Single core router connected to servers.
Major rendering applications like AutoCAD for Engineering are having latency challenges Engineering users who have remote access through personal workstations have some capability issues due to VDI environment.
No Quality of Service (QoS) settings on an application, session, users or service level all VoIP traffic gets priority.
The City, uses 135 applications today made up of 21 via SaaS and the remainder 114 on premise in their data centre.
Mixture of tier 1 and 4 internal facing applications vs external facing applications with a majority of them requiring VPN connectivity.
Requirements
City departments would like an improved working relationship with the City’s IT Division. Areas for improvement that are top of mind for all 9 departments include: service levels, network communication, remote access to data, applications and journey towards mobile applications, agility in the day to day operations and overall empowerment of employees.
Key areas of growth that will require a modernized network architecture and cyber security approach include:
Shift to cloud based applications (i.e SaaS)
Wifi services
Video conferencing and streaming
Remote workforce
Open data sharing

Areas of concerns identified by The City
Data leakage
Data loss
Privacy
Communication complexity
Audit, compliance and risk management
Internal skillsets, training and development for IT / Security operations

A future state is where you want a system, infrastructure, network, business process, etc. to be (i.e., the ‘To Be’ state). It typically is something that needs to happen over a period of time (e.g., 3 to 5 years).
Life Cycle Management is the practice of implementing a pre-defined term (in years) to hardware or software in which it will be in use. The end date can come from the vendor; known as end of life, end of support, end of service, etc. Or, an organization can impose their own life cycle management term; for example, a server will be replaced 7 years from the date of installation.
A best practice is to go with an organization’s imposed, term but, it will be trumped in the event a vendor announces end of life date.
Suggested lifespan for devices is:
1. Server hardware 5 to 7 years.
2. Network infrastructure 7 to 10 years.
Lenovo has historically provided service and support for at least five years following a product's withdrawal from marketing. The oldest server is 2019 and should still be in support. However, it is recommended that budgeting for server refresh should be reviewed in the June 2023 budget cycle.
The core router is a special case in that a longer replacement cycle is required. It is recommended that high level planning begin in Q3 2022. High level planning should include costing, estimated timelines and would consist of:
1. A suggested replacement with appropriate I/O modules (10Gbps module, 1Gps modules, etc.) and have redundancy built into it (e.g., multiple power supplies, multiple supervisors, etc.).
2. Professional services to replace the equipment.


3. And estimated timeline to install the new equipment and remove the existing core router.
This high-level plan will be used during the June 2023 budget cycle.
The Wireless Controller will no longer be supported in the second half of 2023. It is recommended that this device is replaced.
For devices not listed in the table above, an exercise should be done in Q4 2022 to determine:
1. List devices that have end of life announced.

2. Determine what the replacement equipment will be.
3. Create a high-level plan to replace the equipment. Like the high-level plan for the Core switch, determine the cost of the equipment, professional services (if needed), and estimated timing (in years and quarters).
All, of the WAN links that are City owned or leased dark fibre should have Layer 3 segmentation between the Wide Area Network and the Local Area Network. Broadcast packets can be both Layer 2 Ethernet packets (ARP, device discovery, etc.) and Layer 3 broadcasts. The intention of a broadcast is for a device to query all devices on the local network for a particular service. A network broadcast will be sent to every active port on the network. Because of this, best practices in a network design is to limit a broadcast domain with Layer 3 IP network segments.
Some reasons to limit broadcast domains are:
1. Make better use of bandwidth, do not flood the WAN link with broadcast traffic.
2. Limitation of broadcast storms; Layer 3 routed ports do not pass broadcast traffic.
3. Broadcasts can be used as a denial of service (ties up network resources on all devices).

4. Trying to determine the source of a broadcast storm is very difficult large broadcast domains (e.g., spanning multiple buildings).
5. etc.
The recommendation is to create IP point to point networks on links between buildings and have traffic routed instead of switched. Implement a routing protocol (EIGRP) so that networks are automatically discovered to the network devices. Routing protocols also enable a network device to take advantage of multiple links. If there are two equal links between two sites; a routing protocol will automatically load balance traffic over the two links. If a link fails, a routing protocol will automatically divert traffic to the active link.
Also, if sites are connected in a ring configuration and a link fails on the ring, traffic will automatically be rerouted to go the other way. For example, Site A connects to Site B which connects to Site C which connects back to Site A. If the link between Site A and Site B fails, the
routing protocol will change its path and route traffic destined for Site B to Site C and then from Site C and to Site B (and back again; Site B > Site C > Site A).
It is recommended that Layer 3 switches are installed, Layer 2 switches do not have routing and routing protocol functionality.

The recommended routing protocol to use is Enhanced Interior Gateway Routing Protocol (EIGRP). When the switches are connected and configured, the routing protocol will take over and automatically learn how to route to all the networks.
The same recommendations apply to all the Wireless point to point links. For each wireless link, have a Layer 3 switch on each end and create a wireless IP network (e.g., a /30 network). For example, replace the switch at the water tower (the link from City Hall to the water tower) with a Layer 3 switch. Replace or install Layer 3 switches downstream the wireless network. Then route the traffic and use routing protocols to discover network networks and effectively use multiple links (load balance and failover).

The wireless Access Points (AP) are currently configured in Local mode, which is the default mode. In this mode, APs are centrally managed and only operate when connected to its wireless controller.
In FlexConnect mode, APs are centrally managed but traffic can either be tunneled back to the wireless controller or sent directly out the switch port the AP is connected to. And the AP can still function even when the wireless controller is lost (e.g., connection or device issue).
It is recommended that the APs are configured to use FlexConnect mode and exit traffic directly to the local switch. Thereby allowing devices on the wireless network communicate with devices on the local wired network.
As an example, an iPad printing to a local printer using Bonjour. In local mode traffic will traverse the WAN link to the wireless controller. Then traverse back over the WAN link to the printer. This is an issue for sites with slow links.
This section is to provide optional recommendations for CKL to review for the future state.

A significant single point of failure is the core router (i.e., only 1 node). Although these devices are extremely reliable, there are times when the device can be taken offline:
1. Firmware upgrades
2. Module replacements
3. Component failures
To overcome this, many organizations implement a multi-core design (e.g., 2 nodes) that are setup in such a way that if one core fails, all traffic will be re-routed through the second active node.


o Inventory all applications residing on virtual on physical hardware.
o Create and validate naming conventions for all workloads.
o Build an application portfolio excel sheet with details on each application.
o Identify tier, users and purpose for each application.

Establish current application portfolio to determine what is on premise, public cloud and SaaS plus roadmap to retire, replace, re-platform and retain applications.

Replace

Replace applications with the adoption of Software as a Service (SaaS) applications such as MS365. This shift in application portfolio would reduce the traffic passing through the data centre, since the end user can go directly from the internet to the SaaS application. This poses new cyber security challenges

for all organizations and a solution to overcome this new approach will be detailed below under the heading SASE.


SaaS has several benefits from centralizing data, empowerment of employees to collaborate, share data, communicate, and access to applications quickly.
A traditional network and security architecture are becoming less relevant, and a modernized architecture based on a Zero Trust Identity based approach are becoming more of a reality for organizations to reimagine their perimeter.
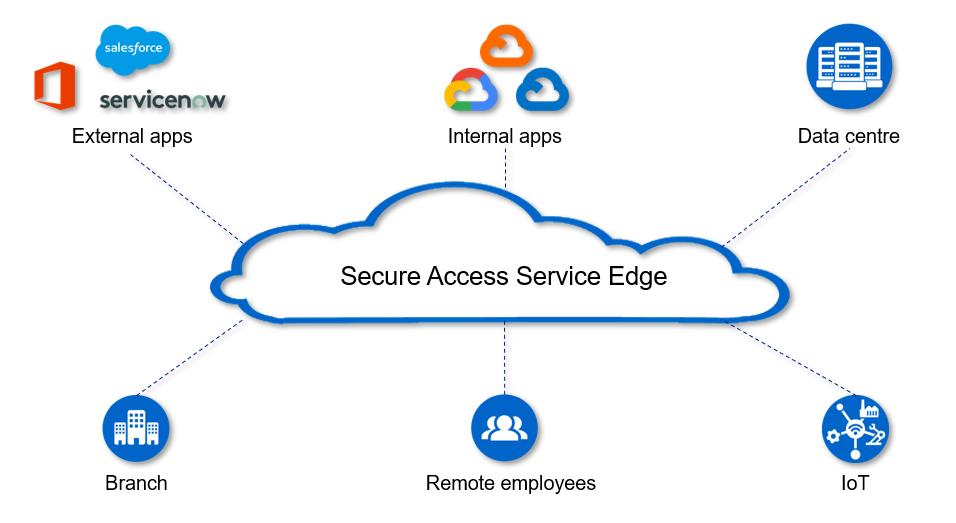
SASE is a cloud-based architecture that delivers network and security services meant to protect users, applications, and data regardless of geography.
SASE promises to deliver the necessary networking and security capabilities in the form of clouddelivered services. A SASE model eliminates perimeter-based appliances and legacy solutions. Instead of delivering the traffic to an appliance for security, users connect to the SASE cloud service to safely access and use web services, applications, and data with the consistent enforcement of security policy.
MIS3 recommends The City adopt SASE to achieve a hybrid and modernized network architecture. This will allow The City to adopt and execute a software-defined wide area networking (SD-WAN) and security into a cloud service that promises simplified WAN deployment, improved efficiency and security, and to provide appropriate bandwidth per application.


This approach in our Transformational IT practice is a cloud service, SASE can be readily scaled up and scaled down and billed based on usage. As a result, it can be an attractive option in a time of rapid change and innovation at The City.
The City, should consider SASE since this combines SD-WAN capabilities with security and delivers them as a service. Security policies enforced on user sessions are tailored to each based on four factors:
the identity of the entity connecting
context (health and behavior of the device, sensitivity of the resources being accessed)
security and compliance policies

an ongoing assessment of risk during each session.
The WAN side of SASE relies on capabilities supplied by entities including SD-WAN providers, carriers, content-delivery networks, network-as-a-service providers, bandwidth aggregators and networking equipment vendors.
SASE reduces complexity and cost.
Enterprises deal with fewer vendors, the amount of hardware required in branch offices and other remote locations declines.
Number agents on end-user devices also decreases.
End users have the same access experience regardless of what resources they need and where they and the resources are located.
SASE also simplifies the authentication process by applying appropriate policies for whatever resources the user seeks based on the initial sign-in.
Security is increased because policies are equally enforced regardless of where users are located.

As new threats arise, the service provider addresses how to protect against them, with no new hardware requirements for the enterprise.
Key Areas to Consider are:
Cloud Access Security Broker.
Secure Web Gateway.
Private Access / Reverse Proxy.
Email DLP
MIS3 would recommend the following be completed before The City continues to adopt more SaaS services to ensure cyber risk is mitigated.

Recommendations before or during adoption of SaaS are as follows:
Creation of a Cyber Security program starting with the selection of a framework and complete an assessment (NIST 800-53, CIS18).





Adaptive Multi-Factor Authentication is a method The City should consider for using contextual information and business rules to determine which authentication factors to apply to a particular user in a particular situation
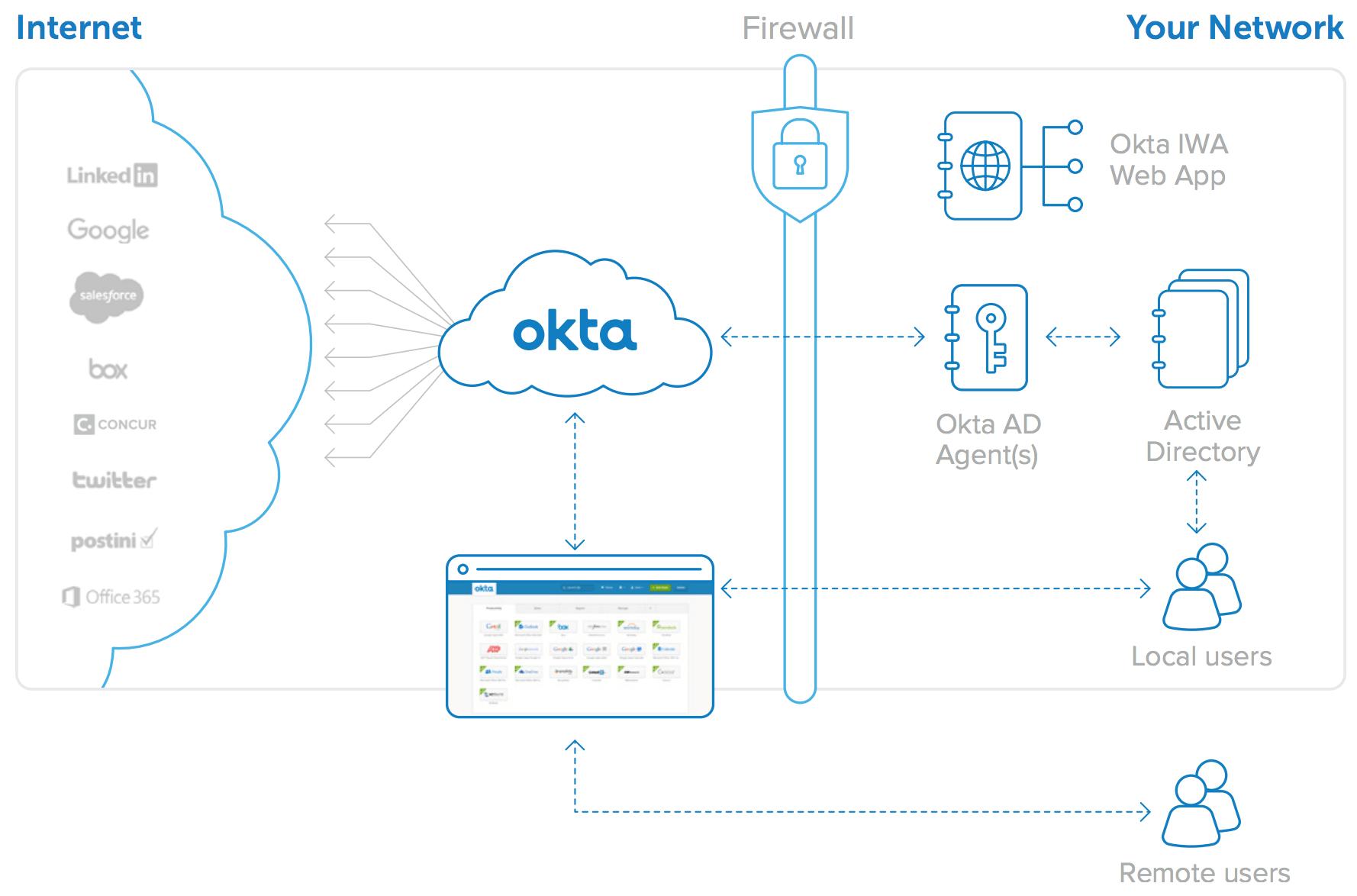
This can be created for employees, contractors, and partners under profiles, establishing an IDP. Currently The City uses Thales for MFA but they may not have the simplicity and ease of use today compared to next generation adaptive MFA technologies for workforce identity, such as Okta. Passwordless, frictionless and push notifications alongside integration with Active Directory, Azure AD, LDAP and other forms of authentication are possible.

Additional capabilities The City can leverage through a single platform for adaptive MFA are:
SSO with SAML integration for SaaS Applications and on-premise legacy applications.
Creating a Data Governance Framework aligned with Management Directive:
Defining an operating model for the data governance steering committee.
Defining a data lifecycle model including retention, use and disposal phases.
Developing and maintaining policies, procedures and tools to align with legal requirements to ensure consistency in how data is used, ensure data quality, integrity to support operations, and evidence-based decision making.
Defining roles and responsibilities to govern the management of all data and data-related assets plus types.
Ensuring responsible and respectful access to The City’s data and data assets by identifying, documenting, and increasing visibility through the creation of policy and processes for the protection and sharing of data and data-related assets.
Assisting in the development, implementation and maintenance of The City Data and Analytics Strategy including data management standards, tools, policies and procedures related to institutional data assets.

Defining requirements for a data catalog and metadata repository that stores information about institutional data assets, systems, domains and stewards that includes automated workflows, and machine learning functionality.
Implementing a communication plan and change management strategy to increase maturity to provide trusted and fit data for the City.

Endpoint Detection and Response (EDR), also referred to as endpoint detection and threat response (EDTR), is an endpoint security solution that continuously monitors end-user devices to detect and respond to cyber threats like ransomware and malware.
MIS3 recommends The City look revaluate their EDR strategy and technologies available in the marketplace.
While an EPP provides security measures to prevent attacks, EDR can proactively address threats after they have penetrated an organization's endpoints, before they cause damage. Antivirus software, also known as legacy AV, is the “lowest common denominator” of endpoint security.
Zero Trust is a strategic approach to cybersecurity that secures an organization like The City, by eliminating implicit trust and continuously validating every stage of a digital interaction.
Three core concepts from "Zero Trust" to implement today:
Assume all traffic is a threat.
Give minimal privileges.
Verify people are doing the right thing.
MIS3 recommends The City move towards a Zero Trust approach to achieve a modernized network. An identity-based approach to Zero Trust will develop a blueprint leading to the strategy, tools and technology to achieve it.

Core areas of identity in Zero Trust:
Application to application trust communication (API Security)
Machine to machine trust communication (Micro-segmentation)
Human to machine trust communication (Privilege Access)
Human to application (MFA, SSO, CASB)





MIS3 recommends The City, leverages all recommendations put forward in this report:

Redundancy, high availability with no single point of failure for the core network, NGFW and layer 2-3 switching for the on premise data centre.
Incorporating a load balancing software technology like f5 to sit in front of NGFW and handle all concurrent connections including any encryption / decryption, SSL certificate, TLS connections and WAF.
Adoption of SASE will be instrumental for The City to achieve network modernization. The City can speak to the firewall vendor who has their own SASE solution and portfoliothat includes access control, advanced threat protection, user behavior monitoring and other services that promise to protect enterprise applications and resources.
MIS3 recommends an alternative to the current firewall based on capabilities, cost, manageability and execution. New and merging next generation technologies are the future and provide reduced complexities, ease of deployment and great automation. To achieve SASE at The City MIS3 does recommend the following software cyber security technologies:

- Netskope for CASB, Private Access (VPN), Secure Web Gateway (SWG), Email DLP, IaaS Security and Posture.


- Versa Networks for SDWAN.
MIS3 recommends The City use Microsoft for MFA and Identity if it meets their workflows, licensing model and cost. If not, then we highly recommend Okta for their adaptive MFA technology specializing in workforce identity access management.

MIS3 recommends for EDR a balance between Microsoft Defender which is available in their licensing agreement plus a next generation EDR platform from SentinelOne or Crowdstrike. Both are great platforms, but SentinelOne has both an on premise and cloud offering vs Crowdstrike cloud only deployment and interface.







Zero Trust requires an identity based, approach and focusing on four core areas. The first area is application to application trust communication with a focus on source and destination with an emphasis on API security. MIS3 recommends Salt Security for API security in combination with complimentary partners such as Palo Alto, Cisco, Microsoft, RedHat and f5.


Application programming interface (API) security refers to the practice of preventing or mitigating attacks on APIs. APIs work as the backend framework for mobile and web applications. Therefore, it is critical to protect the sensitive data they transfer.


The second area of Zero Trust with an identity focus is machine to machine trust communication. This includes IoT, infrastructure connecting to infrastructure and lateral movement across your network inside your data centre.
Micro-segmentation is a network security technique that enables security architects to logically divide the data center into distinct security segments down to the individual workload level, and then define security controls and deliver services for each unique segment.


MIS3 recommends micro-segmentation with the ability to complete this with ease both on premise and inside public cloud. The technology platform to enable this is called Guardicore.
Guardicore, is a cloud and data center security company that protects your organization's core assets using flexible, quickly-deployed, and easy to understand segmentation and micro-segmentation controls.

The third area of focus for Zero Trust is Human to Machine trust communication focusing on privilege access and enforcing least privilege access and controlling excessive permissions. This applies to administrators managing servers and other assets both on premise and inside public cloud.
MIS3 recommends Okta and or Sonrai Security for Privilege Access Management.


Okta works with Privileged Access Management (PAM) partners to provide secure, user-friendly authentication and account provisioning.

Centralize identity through Okta to confidently verify and authenticate users for privilegedaccount access via SSO and MFA.
Customizable and adaptive access policies reduce the verification burden on authorized individuals.
Reduce the attack surface area with automatic privileged account provisioning and deprovisioning.
Real-time access event reporting and API integrations makes suspicious activity easier to spot.


The Sonrai identity graph examines all users, roles, trusts, policies, permissions, non person identities, and groups.
The fourth area of Zero Trust is Human to Application trust communication. This is where humans access applications on premise, inside public cloud and SaaS based on conditional access, identity, authentication against your directory services (LDAP, AD, Azure AD etc..) and profiles are created to publish applications via single sign on (SSO), SAML integration and adaptive MFA.
This includes contractors, partners, part time workers and more. Additional visibility, control and governance inside SaaS applications to enforce policy. The core technologies in this area are:
The skills gap around network modernization will be understanding how the network perimeter is now reimagined. A basic understanding of SASE and the key components that transform the organization in converging network and security together is where The City IT planning and architecture team, security and network operations team will need to spend their time.

Proof of concepts for all relevant concepts and technology tools will allow The City to gain an understanding of transformational IT. This understanding will help IT reimage the perimeter and develop an aptitude for next generation cyber security tools and technologies.
Online training and certifications are available, plus professional services, access to their own interface, trainers and online material for reference alongside certifications.

MIS3 can provide guidance to The City around where to start with this SASE strategy, what are the pre-requisites, which technologies to adopt first, how they integrate and help them administer it for ongoing operations.

The bill of materials is 90% software with a cloud deployment and interface with no hardware on premise. Time to deploy is greatly reduced with no disruptive upgrades, or patching required.
Support terms of 12 months are assumed, and all pricing is list in CAD$ without any discounts applied. MIS3 believes The City can expect anywhere from 35% – 55% off list price stated above.
MIS3 recommends The City review this document and decide which strategy they would like to adopt first.
Determine the business vision and how to align the technology strategy with the business. Select the actions to be undertaken and develop a strategic roadmap to move forward. Prioritize what needs to be done and in which order than develop set of technical requirements to issue the RFP.
Define technical requirements and scoring system where price is 15-20% of the selection and more merit is provided to the quality of the response, references and overall proposal.
Review and shortlist proponents and complete a proof of value with success criteria. Establish bill of materials, review pricing and select.


Proxy
Control network traffic, selecting the right destination based on server performance, security, and availability.
Hardware of software full proxy solution with the ability to:
Inspect, manage all network traffic internally and externally
Report on application traffic entering andexiting your network
Basic load balancing to complex traffic management decisions based on client, server, or application status, giving you granular control over app traffic.
optimize the speed and reliability of your applications via both network and application layers.
Using real-time protocol and traffic management decisions based on application and server conditions, extensive connection management, and TCP and content offloading, dramatically improves page load times.
highly optimized TCP/IP stack, TCP Express, combining TCP/IP techniques and improvements in the latest RFCs with extensions to minimize the effect of congestion and packet loss and recovery.
Independent testing tools and customer experiences show TCP Express delivering up to a 2x performance gain for users and a 4x increase in bandwidth efficiency.
SSL performance allowing cost-effective protection to the end-to-end user experience by encrypting everything from the client to the server.
Scale on-demand and absorbs potentially crippling DDoS attacks.
Inspection levels necessary to block bad traffic and allow good traffic to pass through.
Event-driven scripting language

Cloud based workforce identity and access management tool.
Providing key capabilities (SSO, Universal Directory, Advanced Server Access for PAM, Adaptive MFA, Lifecycle Management for user onboarding and off boarding automation, API Access Management and Access Gateway for legacy applications).

Integration with Active Directory, Azure AD, LDAP, Kerberos if required
SDWAN
Combining full multi-tenancy, multiple deployment options, zero-touch provisioning and a broad set of security functions.
key capabilities such as multi-tenancy, multi-service, elasticity and zero-touch provisioning.
Multi-tenancy, both at the data center, cloud, and branch site, to improve service agility when provisioning as well as significantly lowering capital and operating costs.
Multi-service capabilities and service chaining ensure that organizations can include critical security functions like next-generation firewall and secure web gateway that is easily integrated into their existing network infrastructure.
Help reduce WAN connectivity costs by seamlessly integrating Internet, LTE, and broadband alongside MPLS.
Application-aware routing and the ability to identify thousands of specific applications, SDWAN carefully map different applications across the network based on your custom business policy and application-specific SLAs.
Low-cost appliance, and zero-touch configuration through central management.
Zero-touch provisioning to deploy a fully featured set of SD-WAN and branch security capabilities onto a single appliance.
Capacity increases can be quickly administered centrally from the management platform.
Multiple connections of any type are virtualized through a software overlay that leverages the entire aggregated bandwidth and orchestrated with granular policies that automate the entire process.
EDR
AI-powered prevention, detection, response, and threat hunting across user endpoints, containers, cloud workloads, and IoT devices.
Empowering modern enterprises to defend faster, at greater scale, and with higher accuracy across their entire attack surface.
Multi-site, multi-level architecture tailored to your org structure with no extra charge.
Manage your operations from one intuitive console.
Cloud-native, Cloud-first SaaS, hybrid, and on-premises deployment & management availability.
Automatic correlation of benign and malicious telemetry, events are mapped to MITRE for faster investigation and response.
Real-time reconstruction.
Machine-powered attack reconstruction generates focused, contextualized alerts for faster MTTR.

Fully automated recovery with 1-click remediation & rollback
Single agent
Cloud inline Protection:
Real-time inline cloud security for managed and unmanaged SaaS applications, covering browsers, desktop apps, mobile apps, and sync clients, plus IaaS/PaaS user traffic to monitor and control usage and protect data. Provides risk assessment, granular policy enforcement, DLP, analytics and reporting based on 90-day metadata retention.
Risk Insights
- Inline SaaS app discovery
- Insights into risks including anomalous activities and compromised credentials
- Cloud Confidence Index (CCI) risk ratings, database includes 33,000+ cloud services and apps
Granular Controls
- Client, forward and reverse proxy support for managed and unmanaged cloud services and apps with IdP/SSO/AD integration - Real-time policy enforcement for managed and unmanaged cloud apps and services
- Granular policy controls including app instance and activity awareness
- SSL/TLS traffic inspection including v1.3 native support with cloud performance and scale
Analytics and Reporting
- Analytics and reporting based on 90 days of data retention (longer, up to 1 year, by contract)Open REST API available for integration with third-party applications
Standard Data Protection (DLP)

- Data-in-motion DLP analysis for cloud services and apps, plus web traffic, files and forms
- 40+ regulatory compliance templates including GDPR, PII, PCI, PHI, source code, etc.
- Includes 3,000+ data identifiers for 1,000+ file types, plus custom regex, patterns, and dictionaries - AI/ML standard document classifiers (e.g. resumes)
- Incident management and remediation
Standard Threat Protection
- Anti-malware engines, client traffic exploit protection, and true file type analysis

- 40+ threat intel feeds, plus importing IOCs including malicious URLs and file hashes
- Cloud Threat Exchange (CTE) enables threat intel sharing with EPP, EDR, SIEM, etc.
- Unpacking and de-obfuscation with bare-metal sandboxing for portable executable (PE) files
- UEBA sequential anomaly rules to detect bulk uploads, downloads, deletes, plus proximity, failed logins, rare events, risky countries, and instance aware data exfiltration (between company and personal instances)
- Incident management and remediation
- Hyperscale, carrier grade global private network delivers the Cloud Security Platform from data centers around the world - Fast performance for access to internet and cloud applications with minimal round trip time
- Extensively peered with the major cloud providers
SaaS API protection for Onedrive/Sharepoint
API-based security for sanctioned Microsoft OneDrive and SharePoint application to understand usage and protect data.
API-based protection for Microsoft OneDrive and SharePoint
Policy enforcement
Analytics and reporting based on 90-day data retention
CASB API-enabled Protection
APIs Covered: Onedrive/Sharepoint
API-enabled security for managed SaaS applications to monitor and control usage and protect data. Provides protection using APIs, granular policy enforcement, DLP, analytics and reporting based on 90-day metadata retention.
Includes the following capabilities:
Analytics and Reporting
- Analytics and reporting based on 90 days of data retention (longer, up to 1 year, by contract)Open REST API available for integration with third-party applications
Standard Data Protection (DLP)

- Data-at-rest DLP analysis for managed cloud services and apps
- 40+ regulatory compliance templates including GDPR, PII, PCI, PHI, source code, etc.
- Includes 3,000+ data identifiers for 1,000+ file types, plus custom regex, patterns, and dictionaries - AI/ML standard document classifiers (e.g. resumes)
- Incident management and remediation
- Anti-malware engines and true file type analysis
- 40+ threat intel feeds, plus importing IOCs including malicious URLs and file hashes

- Cloud Threat Exchange (CTE) enables threat intel sharing with EPP, EDR, SIEM, etc.
- Unpacking and de-obfuscation with bare-metal sandboxing for portable executable (PE) files
- UEBA sequential anomaly rules to detect bulk uploads, downloads, deletes, plus proximity, failed logins, rare events, risky countries, and instance aware data exfiltration (between company and personal instances)
Private Access (Next Gen VPN)
Private Access (NPA) is a cloud-based Zero Trust Network Access (ZTNA) solution that is a fully integrated component in the Security Cloud platform. NPA directly connects remote workers to private applications running in public cloud environments or private data centers; reducing risk and simplifying security operations.
NPA includes the following capabilities:

- Secure end-to-end connectivity using TLSv1.3 between remote users’ devices and private applications.
- Inline access policies that ensure that users are directly connected only to the applications they are authorized to use and do not have broad network-level access.
- Support for browser-based access to web applications (e.g. HTTP or HTTPS applications) and for non-web / thick applications (e.g. SSH, RDP, Microsoft Windows Active Directory). Support for both TCP and UDP protocols on almost all associated ports.
- Integration with Microsoft Active Directory and Single Sign-On (SSO) providers to understand users, groups and organizational units, and therefore ensure only authorized users can gain access to applications.
- Device security posture checking to ensure that only corporate devices meeting a specific security posture can access private applications.
- Use of the lightweight Netskope Client (supported on Microsoft Windows or Apple macOS devices) to steer application traffic to the Cloud security platform using either DNS or the IP address.
- Unlimited number of Private Access Publishers (supported on AWS, Azure, VMWare ESX, and any CentOS based virtual machine) to make private applications available to authorized users through the Security Cloud platform.
- Network Events, and Alerts, for Private Application access retained for analytics and reporting for 90 days.
Inline cloud and web proxy for HTTP and HTTPS traffic inspection using a steering client for web, SaaS, and IaaS/PaaS user traffic, and GRE or IPsec tunnels for offices. Includes the following capabilities:
Next Generation Secure Web Gateway - PROFESSIONAL
- Includes cloud native forward cloud and web proxy with SSO, MFA and AD integration
- Reverse proxy for managed cloud services and apps with IdP integration
- TLS traffic inspection including v1.3 natively with cloud performance and scale
- Cloud XD decodes thousands of managed and unmanaged cloud services and apps
- Granular policy controls including app instance and activity awareness
- Cloud Confidence Index (CCI) risk ratings, database includes 33,000+ cloud services and appsAnalytics and reporting based on 90 days of data retention (longer by contract)
- Open REST API
Web Filtering
- URL filtering for 120+ categories, languages for 200+ countries, and 99.9% of the active web
- Filtering includes YouTube categories, translation services, safesearch, and silent ad blocking
- Dynamic web page categorization for 70 categories, plus site lookup tool and reclassification service - Allow, block, or proceed with warning, plus custom alerts to system tray or web browser
- Create custom web filtering categories plus allow and deny lists
- Determine traffic inspection by URL category or domain
Standard Threat Protection
- Anti-malware engines, client traffic exploit protection, and true file type analysis.

- 40+ threat intel feeds, plus importing IOCs including malicious URLs and file hashes.
- Cloud Threat Exchange (CTE) enables threat intel sharing with EPP, EDR, SIEM, etc.
- Unpacking and de-obfuscation with bare-metal sandboxing for portable executable (PE) files.
- UEBA sequential anomaly rules to detect bulk uploads, downloads, deletes, plus proximity, failed logins, rare events, risky countries, and data exfiltration between company and personal instances.
Standard Data Protection (DLP)

- Data-in-motion DLP analysis for cloud services and apps, plus web traffic, files and forms.
- 40+ regulatory compliance templates including GDPR, PII, PCI, PHI, source code, etc.
- Includes 3,000+ data identifiers for 1,000+ file types, plus custom regex, patterns, and dictionaries - AI/ML standard document classifiers (e.g. resumes).
- Incident management and remediation.
- Hyperscale, carrier grade global private network delivers the Cloud Security Platform from data centers around the world - Fast performance for access to internet and cloud applications with minimal round trip time.
In conclusion, The City of Kawartha Lakes will need to move towards a modernized network to meet the needs of the business. Based on the business requirements described throughout this document, and gaining a firm understanding of the current state network, MIS3 have provided a recommendation towards a future state network architecture and capabilities mapped to business requirements for all nine departments at The City.

Below is a visualization of where we believe The City needs to move towards and we have provided the detailed roadmap alongside technology requirements to achieve this.
Key components in achieving a modernized network state will be:

Rationalize applications
Develop high availability in the core network with resiliency and no single point of failure for on premise applications retained.
Adopt proxy solution
SaaS adoption with visibility, control and governance
Adoption of SASE (all components starting with adaptive MFA, CASB and SWG)

EDR solution
SDWAN
Implementing a modern network will allow The City to significantly enhance agility, in turn accelerating revenue, and providing competitive differentiation as applications and services achieve faster time to market both internally and externally.
There are various advantages to digitalization including increased efficiency, increased productivity, lower operational costs, improved resident experience, higher agility, enhanced employee morale, improved communication, increased transparency, improved competitive advantage, and faster decision making.
To make it as is simple as possible, here are three areas The City will benefit from.

To meet today’s availability and networking performance demands from the business, The City will require a network infrastructure that is self-healing, highly automated to minimize human involvement and related errors, and optimized for cloud computing and modern application architectures.

In our experience, this is best delivered by programmable or otherwise self-defining fabrics, which provide high levels of automation and simplified management with the help of collapsed and flattened architecture. Programmable fabrics are really good for fast, easy provisioning of network services and capacity.
Compared to three-tier topologies, fabric-based networks rely on fewer devices, support higher data-transfer speeds and scale faster. As a result, they offer a more cost-effective, less complex, low-latency network solution that’s highly automated
By selecting network fabric solutions, The City can give back time to their IT teams and add further efficiencies by introducing workflow automation that integrates their end-to-end operations processes.
Automation is more important than ever. However, you don’t want to simply automate within the network. Consider how to automate across IT domains, giving the IT teams at The City automated steps for the full operations lifecycle:
end-to-end provisioning
validation
troubleshooting and repair.
Lifecycle automation tools that are cross-domain and deployable out of box, which shortens time to value and minimizes the required skills to get started. Cross-domain means you not only automate the network, but also the operations across compute, storage, cloud, applications and more using workflows.
Lifecycle automation provisioning to include validation, troubleshooting and remediation, activities where operations teams typically spend 80 to 90 percent of their day. While prebuilt workflows allow The City’s IT team deploy quickly with confidence, once they become more experienced, open and customizable automation tools will provide a greater level of flexibility to adapt and tailor to more specific needs.
3. Drive your WANs with software


Software-defined WANs (SD-WANs) will be big enablers of this with practical improvements to how they operate with The City’s existing systems and their availability in a wide variety of packaged solutions and services.
SD-WAN can boost The City’s network performance, improve reliability and potentially reduce costs at the 130+ branch sites by sorting traffic between two connections: your MPLS service if applicable and internet connections.
Service providers also provide direct connections to many cloud providers, such as Amazon Web Services and Microsoft Azure. The correct path selection and prioritization, may provide higher performance than doing it yourself with an over-the-top solution.