




www.counterterrorbusiness.com | ISSUE 55
it’s important to find a solution that fits your specific circumstances SECURITY THAT ADAPTS TO THE LOCATION PERIMETER SECURITY MARTYN’S LAW SMART CITIES
Why
“What differentiates us is the real quality of our people - apart from having worked on the most prestigious of projects, they have the ability to solve complex security problems using their knowledge bank of products, their innovative approach, design capability and creative dynamism.”
Vaylia offer a full turnkey package of services, from advice and specification to final delivery, installation, testing and sign-off.




We are aligned with some of the most important product suppliers in the fields of Fencing, CCTV, Detection Systems and Hostile Vehicle Mitigation. This means we can offer a larger range of products and services than a single product supplier could.






Using years of industry experience the Vaylia team are able to find solutions to the most complex problems. Fencing, gates, CCTV, PIDS, electronic security measures, HVM, Security Doors, Hatches and Barsets all installed by highly qualified and security cleared installation teams who will complete a project to specification and on-time.




Vaylia Limited, 40 Bank Street, Canary Wharf, London E14 5NR Tel: 0203 059 4560 Email: info@vaylia.com
The UK government has recently been working on and releasing legislation to counter and mitigate the terrorist threat. An updated CONTEST strategy has been released and the National Security Bill has officially become law. Meanwhile, draft legislation for Martyn’s Law has been published and recently scrutinised by the Home Affairs Select Committee. In this issue of CTB, Figen Murray explains why it is important that, contrary to the conclusions of the committee, the legislation should apply to smaller venues such as village halls.

Dr Cath Hill explains some of the findings of the Bee The Difference report and demonstrates why it’s so important for young survivors of terrorism to get the right support.
We take a look at the security threat faced by smart cities and how the public sector can protect itself from cyber threats, as well as previewing some of the shows that are coming up in the second half of the year.




 Polly Jones, editor
Polly Jones, editor

www.psi-media.co.uk






COUNTER TERROR BUSINESS LEGISLATING TO SAVE LIVES To register for your FREE Digital Subscription of Counter Terror Business, go to: www.counterterrorbusiness.com/digital-subscription or contact Public Sector Information, 226 High Road, Loughton, Essex IG10 1ET. Tel: 020 8532 0055 ONLINE // MOBILE // FACE TO FACE www.counterterrorbusiness.com © 2023 Public Sector Information Limited. No part of this publication can be reproduced, stored in a retrieval system or transmitted in any form or by any other means (electronic, mechanical, photocopying, recording or otherwise) without the prior written permission of the publisher. Whilst every care has been taken to ensure the accuracy of the editorial content the publisher cannot be held responsible for errors or omissions. The views expressed are not necessarily those of the publisher. ISSN 2399-4533 PUBLISHED BY PUBLIC SECTOR INFORMATION LIMITED 226 High Rd, Loughton, Essex IG10 1ET. Tel: 020 8532 0055 Web:
EDITOR Polly Jones PRODUCTION MANAGER & DESIGNER Dan Kanolik PRODUCTION DESIGNER Jo Golding PRODUCTION CONTROL Deimante Gecionyte WEB PRODUCTION Freya Courtney PUBLISHER Damian Emmins Follow and interact with us on Twitter: @CTBNews Counter Terror Business would like to thank the following organisations for their support: COMMENT
3 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
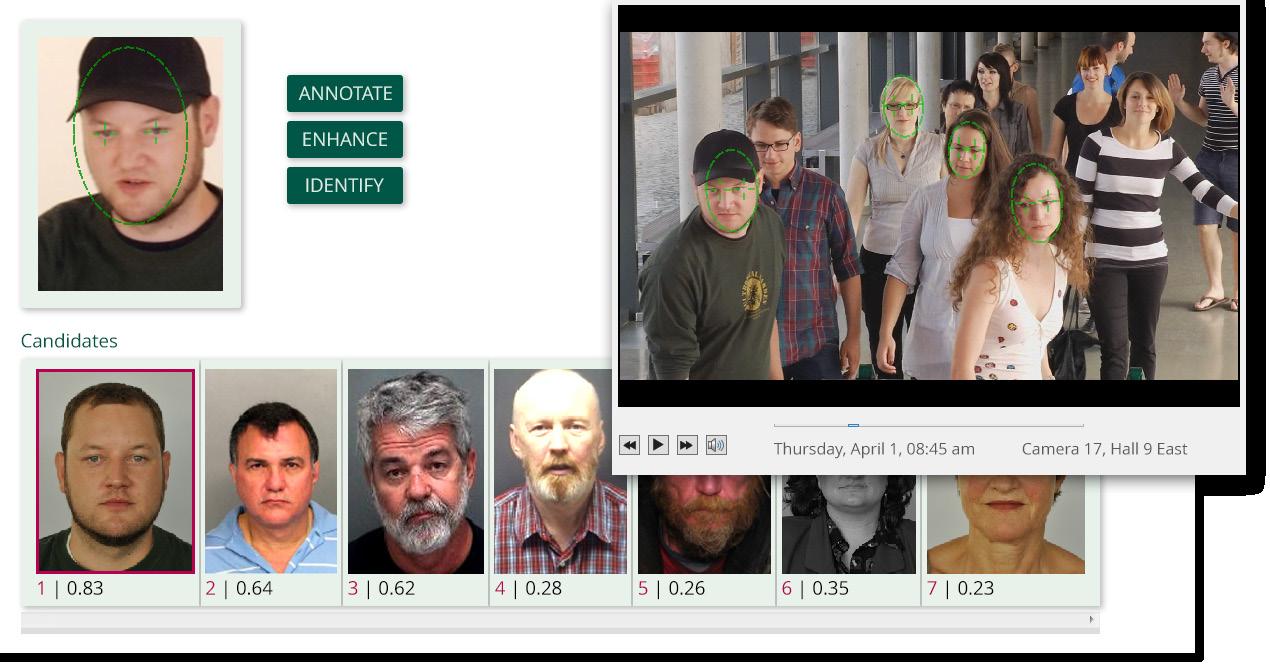
Find suspects in minutes
Reduce search times for suspects in video footage from days, hours . . . to minutes!
Cognitec’s face recognition technology imports still images and video material, finds all faces, and clusters the appearances of the same person, even across multiple media files.
Investigators can search videos to find unknown persons, persons appearing together, frequently seen persons or groups, and known persons.
Talk to us about your face recognition requirements and projects!
Most experienced. Highly trusted. Cognitec is the only company that has worked exclusively on face recognition technology since its inception in 2002.
www.cognitec.com | sales-emea@cognitec.com
4 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
CONTENTS CTB 55
13 SMART CITIES SECURITY
Michael Kolatchev, principal consultant/Rossnova Solutions (Belgium) and Lina Kolesnikova, consultant/Rossnova Solutions (Belgium) discuss the security threats facing the growing number of “smart cities”

17 CYBER SECURITY
Chris Dimitriadis, chief global strategy officer at ISACA (Information Systems Audit and Control Association) on how public sector organisations can protect themselves from cyber threats



19 MARTYN’S LAW
Figen Murray, campaigner and mother of Martyn Hett, after whom the legislation is named, explains why it is important that Martyn’s Law applies to small venues as well
22 SURVIVORS OF TERRORISM
Dr Cath Hill, Manchester Arena attack survivor, lecturer in social work at Lancaster University and member of the National Emergencies Trust’s Survivors Advisory Forum explains some of the findings of the Bee The Difference report

25 PERIMETER SECURITY
Deborah Ainscough, founder and director of event safety and crowd management specialist, Crowdguard, discusses the growing popularity of fan zones in stadium grounds and the need to consider safety and security for these temporary facilities


31 FACIAL RECOGNITION

Facial recognition has been in the news for featuring at high-profile events such as Harry Styles concerts. But these articles in the mainstream press often highlight the privacy concerns surrounding the technology. Without a high-profile success case, it’s hard to convince the public of the technology’s viability
33 AVIATION SECURITY
Shannon Airport presents a rather complex situation when it comes to security. CTB takes a look at the problems the airport was facing and how these have been addressed

35 INTERNATIONAL SECURITY EXPO

The complex, volatile and unpredictable nature of the terrorism threat is a reminder to security professionals around the world to not be complacent when it comes to emerging risks and the sophisticated approaches taken by those looking to cause harm
46 MILIPOL Anti-terror and crisis management is the focus for the 23rd edition

CONTENTS
Counter Terror Business magazine // www.counter terrorbusiness.com 5 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE

Government launches CONTEST 2023
According to the press release, Islamist terrorism makes up around three quarters of MI5’s caseload, with extreme-right wing terrorism making up the majority of the remainder of the caseload.
CONTEST 2023 has been developed by the Home Office, working with a range of government departments, police and the intelligence agencies.


detect. This is why the transformational changes and vital partnerships set out in CONTEST 2023 will modernise our approach and make us all safer.
“The safety and security of our people is the leading duty of government; terrorism will not prevail.
The UK government has launched CONTEST 2023, billed as “a refreshed approach to the evolving and enduring threat from terrorism”.
The UK has experienced nine declared terrorist attacks since 2018 and 39 latestage attacks disrupted since 2017. CONTEST 2023 sets out the UK’s approach to a domestic terrorist risk and addresses a persistent and evolving overseas threat from Islamist groups, and the exploitation of technology by terrorists.
MARTYN’S LAW
The press release points out actions already being taken such as fully operationalising the Counter Terrorism Operations Centre (CTOC), delivering William Shawcross’ Independent Review of Prevent and implementing the recommendations and implementing Martyn’s Law to ensure better protection for people in public places.
Home secretary, Suella Braverman, said: “Any death or injury resulting from terrorism is a tragedy, and the impact on survivors, witnesses and wider society is immeasurable.

“The terrorism risk we face today is rising and becoming harder to
Head of Counter Terrorism Policing, Matt Jukes said: “The Counter Terrorism Operations Centre is a clear marker of the continued collective commitment to tackle the enduring terrorist threat.

“Our mission to keep the public safe cannot be achieved by one organisation alone and we are pleased that CONTEST underlines the importance of collaboration.
“Together with our partners, counter-terrorism policing will always strive to enhance our response, keeping the safety of the public at the very heart of our efforts.”
MPs criticise draft Martyn’s Law bill
Nick Aldworth, former National Coordinator of Protect and Prepare Counter Terrorism policing said: “I know that the committee did its work in a rush, but its conclusions don’t reflect the universal and unpredictable nature of the terrorist threat that was described to them by other witnesses.
MPs on the Home Affairs Select Committee have criticised the draft legislation for Martyn’s Law in a report.
The report claims that the legislation would be ineffective, not prevent attacks and would burden small businesses. It also said that the law would be hard to apply consistently.

The MPs said that it was unclear what the aims of the legislation were, as it had been promoted as terrorism-prevention legislation, but the measures would instead reduce the consequences of an attack that has actually taken place.
It was also claimed that the majority of terrorist attacks in the UK since 2010 would not be covered by the bill. The report stated: “We are concerned to learn that the draft bill would not have made a difference to the vast majority of the terrorist attacks that have happened in the UK in recent years.”
The authors state: “Whilst we welcome the Government’s overall intention behind the Draft Bill, we have some serious concerns about the proportionality of the Bill, especially in relation to the impact on smaller businesses, voluntary and community-run organisations in the standard tier premises, where there is a lack of evidence that the Bill will adequately reduce the threat of terrorism for smaller organisations. We also have some concerns about the unfinished provisions in the Draft Bill, the purpose of the Bill, the regulator and some of the duties required. There are a number of other areas in which we feel that the Draft Bill could be improved upon, including introducing a provision for mandatory lifesaving training and statutory standards for the design of new buildings.”
However the findings of the report have been criticised by Martyn’s Law campaigners and counter terror experts.
“Recommending a single tier and phased implementation will only signpost terrorists to smaller locations and increase the risk to them. At a time when we are seeing terrorists shift their focus to these kinds of venues as soft targets, nowhere is without exposure to terrorism.
“The Government should take their point seriously on including outdoor venues, but their wider arguments are not only wrong but dangerous.”

Figen Murray, mother of Martyn whom the law is named after and who has campaigned for the law said: “Having lost my son to terrorism, along with so many others in the Manchester Arena attack, I find it hard to understand the argument that a few hours of training each year is a disproportionate step for businesses to take.
“Martyn’s law is a proportionate response that will keep millions of us safer and the Government must now press ahead.”
CTB NEWS
CONTEST
READ
CLICK TO
MORE
TO READ MORE 7 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
CLICK
A solution to match your needs
Products made by LISTA have set standards by reaching far beyond standard applications. We are committed to fulfilling customer requirements with bespoke solutions regardless of project size or industry. Our universal system and vast planning expertise will turn your expectations into reality –promptly and reliably.
BEST INDUSTRIAL QUALITY
A system for your success
The LISTA standard unit is the base of a system in which multiple components can be combined and matched. A system has grown out of this in which everything can be combined and matched. and protected with access control. All products are available in almost any colour. In short: LISTA provides a system to organise your business successfully.


For more information contact: info.uk@lista.com
A sound investment
By opting for LISTA you place your trust in durability and continuity. Our unique 10-year product and re-ordering guarantee reflects our corporate philosophy. You can always rely on LISTA quality. Our products are made in Switzerland or Germany and shipped to customers through a broad distribution and service network.
LISTA is the recognised market leader in Europe for workspace and storage solutions
National Security Bill becomes law
Scheme (FIRS), which criminalises those acting covertly for states which pose the greatest threat to national security.
Security minister Tom Tugendhat said: “We are facing growing threats from foreign states. Over the past years we’ve seen attempts to harm our people, damage our economy and undermine our democracy.
“Iran’s recent attempts to kidnap or kill people living in the UK are beyond contempt, and a fundamental violation of our sovereignty.
After being passed by both Houses of Parliament and securing Royal Assent, the National Security Bill became law on 11 July.
The government claims: “This new act brings together vital new measures to protect the British public, modernise counter-espionage laws and address the evolving threat to our national security.
“With this new legislation, the UK is now a harder target for those states who seek to conduct hostile acts against the UK, which include
SURVEILLANCE
espionage, foreign interference (including in our political system), sabotage, and acts that endanger life, such as assassination.
“The new powers will help ensure that the UK remains the hardest operating environment for malign activity undertaken by foreign actors.”
For the first time, the National Security Act includes an offence of foreign interference.
The act also introduces a new Foreign Influence Registration
“The National Security Act provides the tools to expose this type of activity and hold those responsible to account.”
Ken McCallum, director general of MI5, said: “We face state adversaries who operate at scale and who are not squeamish about the tactics they deploy to target people and businesses in the UK.
“The National Security Act is a game changing update to our powers. We now have a modern set of laws to tackle today’s threats.”
Surveillance camera commissioner calls for review

The biometrics and surveillance camera commissioner Professor Fraser Sampson has written to paymaster general and minister for the cabinet office Jeremy Quin outlining identified security and ethical issues in the use of surveillance camera technology, and Artificial Intelligence in the same sphere.
The letter lays out the collective impact on public trust and confidence in the legitimate use of new surveillance technology.

Professor Sampson pointed out there has been a call for a review of public space surveillance. This follows a recent Panorama episode named ‘Is China watching you?’.
The commissioner recently met with the policing minister and separately with the Cabinet Office and Vincent Devine, the government chief security officer and pushed the government to address the presence of these systems on its estate.

Professor Sampson said: “Having recently conducted a survey of the police and local authorities’ use of similar technology, I too am of the


view that a review is needed, if only to answer the question being asked of us on a daily basis: “just how many of these cameras are pointed at us?”. Having had the benefit of a meeting to discuss these issues in the context of their impact on critical national infrastructure and national security with the Security Minister last year,
I now believe the need for a review is supported by the evidenced risks, and the Policing Minister agreed that I would seek an early meeting with you to discuss how such a review might be taken forward.”
CTB NEWS
LEGISLATION
CLICK TO READ MORE CLICK TO READ MORE
9 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE










ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
Six men found guilty of murder in Brussels bombing trial Funding announced for protection for places of worship
Atar is believed to have planned the Paris attack from Syria and is thought to have died in Syria. He was tried in absentia. Krayem was seen with the bomber who attacked the metro station. Krayem also had a backpack full of explosives, but did not detonate them.
Six men have been found guilty of terrorist murder for their part in the 2016 Brussels bombings which killed 32 people and injured more than 300 at the airport and a metro station. Two others have been found guilty of taking part in terrorist activities, while two others have been acquitted of all charges.
Salah Abdeslam was one of those found guilty. Abdeslam is already serving a life sentence in France for his role in the 2015 Paris attacks. After fleeing France, he was arrested in Belgium four days before the Brussels attacks. He has now been found guilty of murder and attempted murder.
Mohamed Abrini was also found guilty for his role in the Brussels attack, he had also already been found guilty of taking part in the Paris attack. Abrini was identified on CCTV fleeing Zaventem airport in Brussels when his explosives did not go off. Abrini admitted to his role in the attacks, confessing that he prepared the explosives for the bombings.
Oussama Atar, Osama Krayem, Ali El Haddad Asufi and Bilal El Makhoukhi were also found guilty of terrorist murder.

HVM
A Tunisian man and a Rwandan man, were cleared of murder but were convicted of taking part in terrorist activities, as were the other six on trial. Brothers Smail and Ibrahim Farisi, were cleared of all charges.
On 22 March 2016, two bombs went off at Zaventem airport just before 8am. 16 people were killed. Around an hour later, another bomb went off at Maelbeek metro station in Brussels’ European quarter, where another 16 people were killed. The court also ruled that three people who died in the years following the attack should be considered victims. These include a 23-year-old who suffered from psychological illness and died by euthanasia, and a man who died by suicide after suffering from post-traumatic stress. Another man died of cancer in 2017 after being forced to halt treatment because of the wounds caused by the metro bombing. The trial took place in a court built especially for the trial in the former NATO headquarters on the outskirts of Brussels.

The defendants are likely to be sentenced in September. Five are already in prison for their roles in the Paris attacks.
UK security minister, Tom Tugendhat, has announced £28 million in funding to protect places of worship. The funding is available through two schemes and is part of the government's commitment to protect faith communities in England and Wales from the threat of hate crime and terror attacks.
The money can be spent on physical protective security, such as CCTV, intruder alarms and secure fencing for mosques, churches, temples, gurdwaras and other places of worship. Mosques will also be able to access a new security guarding scheme later in the year.
Security minister, Tom Tugendhat said: "Freedom of religious belief and the freedom to worship are fundamental. "We will defend against any form of hatred targeting our communities, and are committed to protecting all faiths.
"I encourage any place of worship that feels they would need assistance to apply under the schemes."
Emergency bandage kits to be provided on HVM deployments

Alex Chivers, founder of RAPAID said: “Having emergency bandages available that can be used by anyone without training could mean the difference between life and death for casualties.
reducing the consequences. That’s exactly what’s happening with this partnership between Crowdguard and RAPAID, and I encourage others to follow this lead with collaboration and joined-up thinking.”




Crowdguard, a specialist in counter terrorism risk assessment and hostile vehicle mitigation (HVM), has partnered with RAPAID, the emergency bandages charity and committed to providing emergency bandage kits as part of every temporary HVM deployment. The kits include military-grade emergency bandages, surgical gloves, window stickers and a full set of laminated instructions, and will be available at every Crowdguard temporary HVM deployment at no additional cost to customers.
“We know that people on the scene during the Manchester Arena attack did everything they could to help the injured, but they just didn’t have the kit on hand to stop the bleeding until the emergency services arrived.”
RAPAID emergency bandages kits can already be found in black cabs in five UK cities, along with at prominent visitor attractions, such as the British Museum.
Figen Murray MBE, who has campaigned for Martyn’s Law, following the death of her son Martyn in the Manchester Arena attack comments: “So much of what we want to achieve with Martyn’s Law is an approach to risk mitigation that joins the dots between preventing terror attacks and
Deborah Ainscough, founder and director of Crowdguard said: “Our mission is to protect people and places from vehicle impacts with expert specification and installation of HVM equipment, aligned to a vulnerability, threat and risk assessment. But we cannot protect people from all risks, and we wanted to make sure that, if the worst happens - whether it’s a vehicle attack, a knife attack, an accident or any other type of incident causing heavy bleeding – we have the equipment on site to reduce the consequences and save lives.”
CLICK TO READ MORE
CTB NEWS
TERRORISM TRIALS SECURITY
CLICK TO READ MORE
11 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
CLICK TO READ MORE
BALANCING BUDGET AND RISK WHEN DEVELOPING A HOSTILE VEHICLE MITIGATION STRATEGY

Since 2014 vehicles have been used as weapons in more than 140 attacks around the world. According to the NPSA, 90 per cent of those attacks were in locations with no significant security barriers in place. A quarter of them involved fatalities and two thirds resulted in serious injuries.

It’s impossible to know how many lives or serious injuries could have been avoided had appropriate and proportionate HVM been in place. We need to strike a balance between keeping people and places safer, and enabling people to enjoy doing the things they love, which includes considering the financial implications of deploying HVM. The proposed Martyn’s Law – Terrorism (Protection of Premises) Bill – stipulates a mandatory requirement for events and venues with a capacity of 100+ to undertake a terrorism evaluation, and those with a capacity of 800+ to also implement ‘reasonably practicable’ security measures for proportionate risk mitigation. But one of the biggest questions on everyone’s lips is ‘how do we balance budget and risk?’
PROPORTIONATE, APPROPRIATE, AFFORDABLE
It is essential to assess the risk and threat to each space or event. HVM can work in conjunction with an ATTRO or TTRO, but it is not traffic management or traffic calming; it requires specialist expertise. However, specialist doesn’t have to mean expensive. By working with experts who understand risk mitigation and proportionality, event organisers and those responsible for security can avoid over-specification and unnecessary added costs.
At Crowdguard, our Plan, Provide, Protect model delivers these principles. During the plan phase, our threat, vulnerability, and risk assessment (TVRA) service and vehicle dynamics assessment (VDA), ensure specification is based on a clear understanding of the specific risk, along with any operational and financial constraints. Our collaborative

approach to helping you achieve those goals means we can offer you options to help you balance budget and risk.
To ensure the HVM protects people and assets to its full, rated performance, the Crowdguard service also includes deployment and derigging to strict QA processes and manufacturer’s guidelines, explaining any difference from ‘as tested’ in writing.
COLLABORATION AND CONTINUOUS IMPROVEMENT
Working collaboratively with stakeholders including the police, counter terrorism security advisors (CTSAs) and traffic management companies as well as our clients, we can ensure Martyn’s Law is practicable, proportionate, affordable and effective in protecting people.
CASE STUDY: ADVISING ON COST SAVINGS WITHOUT COMPROMISING SECURITY AT GODIVA FESTIVAL
Over the past few years, Crowdguard has installed HVM equipment at the Godiva Festival in Coventry. This year, our counter terrorism and risk director, Russ Phillips, conducted a full threat, vulnerability and risk assessment and reviewed the existing specification in collaboration with the client and the police.
We found that in some locations the specification can be reduced for future events, while still providing proportionate and appropriate security. This will provide Godiva Festival with a 31 per cent saving on their HVM budget next year!
And we are now talking to Godiva Festival about a longer-term strategy of reducing their annual temporary HVM costs by installing a semi-permanent system in some locations too! L
ADVERTISEMENT FEATURE FEATURE FURTHER INFORMATION www.crowdguard.co.uk
Iain Moran, managing director of Crowdguard, the specialist in HVM risk assessment, specification and deployment, discusses proportionate HVM
12 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
Iain Moran, Managing Director, Crowdguard
SMART CITIES: CHALLENGES & SECURITY THREATS

Cities are the most complex objects created by humans. Modern cities face the challenge of combining competitiveness and sustainable urban development simultaneously.
The notion of a “smart city” came into our lives in 2006. Nowadays there are more than 150 definitions of the term. The International Telecommunications Union defines “smart city” as “ a sustainable city… which uses ICTs to improve people’s quality of life, make urban operations and services more efficient, and boost its competitiveness, while ensuring that it meets the economic, social, environmental, and cultural needs of present and future generations”
The growing number of urban problems pushes city authorities (not only metropolises but also medium and small cities) to look for innovative solutions to make cities resilient, sustainable and livable. In this context, the term “innovative solution” most commonly boils down to a technical solution facing a large number of people,
or a technology in broad sense. That is where a smart city loaded with technical solutions to non-technical problems go to the front. Smart cities make use of known technologies to optimise what often already exists in other forms, but maximises the outcomes to smooth the operation. In essence, the mass of input data is analyzed in (near) real-time to adjust configuration of city control systems to achieve “best currently achievable” outcomes defined using pre-defined criteria and rules. As one can see, a smart city essentially demands the myriad of data collection input points and devices, strong capable networks delivering collected data promptly to appropriate destination(s), and the central brain that makes use of input data to adjust the environment for its users (habitants, transport, etc.). The latter immediately implies that the environment (“the smart city”) is flexibly adjustable and configurable at the most detailed level possible, down to configurability of individual devices and E
SMART CITIES SECURITY
Michael Kolatchev, principal consultant/Rossnova Solutions (Belgium) and Lina Kolesnikova, consultant/Rossnova Solutions (Belgium) discuss the security threats facing the growing number of “smart cities”
13 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
procedures installed at any place in the city. With such an elaborate network of devices, processing capabilities and communications, the trust in data and algorithms, access control to and usage of powerful capabilities comes to be a crucial element on its own. When talking about smart cities, we immediately witnessed the concerns of citizens that smart cities effectively create an environment of total surveillance and control and push towards unwelcomed intrusion into personal life. For convenience, safety and perceived shielding from today’s challenges and pressures, people are readily giving away their independence and privacy. For example, the old artistic idea of TV watching people rather than people watching TV is now absolutely feasible, with subject and object exchanging places. End-user devices are continuously “listening” to their users and feeding this information to central systems to define the next actions or suggestions (even though, this intent is convenience and not spying as such). The notion of smart cities has settled firmly in conspiracy theories.
RISKS AND THREATS
Undoubtfully, smart cities aim to remediate certain risks and downplay
certain threats. For example, extended surveillance, fast processing and quick response units. Meanwhile, security professionals voice concern with challenges and, paradoxically, new vulnerabilities and security threats that come with smart cities, while some old ones still persist. Vulnerability is psychological, sociological, or physical characteristics that can leave the asset unprotected or exploitable for attack. Despite our wishes and effort, there are blind spots and defects, which could be missed during risk planning and vulnerability assessments. We find ourselves in a situation where technologies, which have their own vulnerabilities, as no technology can be 100 per cent secure, are used by players who bring their “old” vulnerabilities to the new and more complex system, and which, in their own way create new vulnerabilities for the whole system. The situation is even more difficult because the new system, smart system, can become very complex and is based on the principle of interdependency.
CYBER SECURITY
Data, information and knowledge are crucial elements of smart cities. A smart city is a hub of transformation of data into information and knowledge,

further transformed to configuration adjustments and actions. We are talking here about BIG data. Such data should be collected, stored and analysed properly. Such data includes a significant amount of sensitive information as well, therefore, its protection is crucial.
Smart city technologies could be disrupted in one or more of the following dimensions: confidentiality attack, such as a privacy breach, data loss or identity theft; integrity attack, such as device hacking for planting malware or viruses, data pollution and manipulation; availability attack, such as Denial of Service, manipulated or provoked full or partial shutdown of a system; or traceability attack, such as data manipulation aiming at hiding or generating false mis-leading traces.
Either due to an intentional (attack) or unintentional (defect or human error) event, system disruptions render part or a whole of a smart system unusable, or, worse, usable for malicious purposes, leading to undesirable outcomes.
Given there are no unlimited budgets available, security of a system, smart city in our context, will likely follow best practices which are fundamentally based on security assessments, identifying and prioritising remediation efforts in function of risks and vulnerabilities.
NEW VULNERABILITIES
Vulnerabilities would be weaknesses of various sorts in systems and technologies, integrations and processes using such systems and technologies,
SMART CITY SECURITY 14 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
A SMART CITY IS A HUB OF TRANSFORMATION OF DATA INTO INFORMATION AND KNOWLEDGE
as well as in procedures executed by humans. Some vulnerabilities are the same as those faced by any organisation today, such as weak security, inadequate data encryption and protection overall, programming bugs or elementary human errors (even though, the latter are not specifically categorised as vulnerabilities and are largely addressed by smart cities via mass automation and digitalisation). However, there are new vulnerabilities as well. CIs in Europe, for example, often use old soft- and hardware. Such a situation creates a “bad heritage” problem, when these old technologies with their large technical debt are integrated into smart city system, a system of systems. Smart city systems are very complex and very much interdependent. No person or organisation can say how all the things work, individually or in combination, what risks they have and how to mitigate them. Given interdependency, there is always a risk of a cascading effect in case of disruption of one of the system’s components. Building and maintaining a knowledge base in the hands of smart city architects, analysts, managers and operators, is a daunting task but shall be addressed. Another concern is the cost of keeping infrastructure, systems
OF THE DIGITAL EXCLUSION AND/OR DIGITAL ILLITERACY OF MANY PEOPLE, WHO COULD BE TARGETED BY ORGANISED CRIMINAL GROUPS
and technologies, operations and personnel up-to-date and maintained. In a complex system of systems, even fully automated testing of a small patch in one of them, might be a long and effort-demanding exercise, as a correctly representative copy of a real system of systems shall be offered for best quality assurance and assessment of undesired impacts on one and all systems. With modern iterative development methods, we all know what this might lead to, provided existing and expected budgetary constraints across multiple countries. Testing might become limited in scope and depth. Building-in redundancy in the smart city system and its components is required but will also impact testing and deployments of changes. Smart cities have many necessary physical objects (sensors, CCTV cameras, lighting systems etc) which are produced outside of a smart city,

often not even in the same region, or in another country. The pandemic has shown that disruption of supply chains could be disastrous. In times of geopolitical instability, the question of having long-term vendor-user agreements is crucial but not always reachable. Therefore, redundancy in suppliers might be needed. In ageing Europe, we risk the problem of the digital exclusion and/ or digital illiteracy of many people, who could be targeted by organised criminal groups. Smart cities are not built and operated by themselves – people and institutions are doing so. The smart city and digital literacy rates are low not only among ordinary users but also among decisionmakers and many stakeholders. Strong governance is needed as to define a sound foundation on which a smart city can be established, architected, constructed and operated in its entirety. L
INTRODUCING THE FUTURE OF SECURITY RATED PALISADE SYSTEMS


LOCHRIN COMBI™ SL1
The next generation of Palisade fencing, this SR1 rated fence is designed to replace standard Palisade with a security tested product for peace of mind.
LOCHRIN COMBI™ SL2
This SR2 rated fence is designed with installers in mind and features simple installation with no specialist tooling, making it a cost effective security solution.


LOCHRIN COMBI™ SL3
An innovative SR3 rated high security Palisade fencing system designed to revolutionise the market, utilising only 10 security fixings for an aesthetic design.

IN AGEING EUROPE, WE RISK THE PROBLEM
SR RATED LPS 1175 : ISSUE 8 FENCING SYSTEMS NOW AVAILABLE +44 (0)1236 457333 | sales@lochrin-bain.co.uk | www.lochrin-bain.co.uk #WESECUREWHATYOUNEEDTOPROTECT SMART CITIES SECURITY 15 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
ALLIED TELESIS FOR NETWORK SECURITY PEACE OF MIND
Chris Dyke, Sales Director, UK&I for Allied Telesis explains how, given the rapid advancement of technology and the increasing reliance on interconnected systems, electronic terrorism poses a significant threat to individuals, organisations, and nations. Effective cybersecurity measures, coupled with securely connected networks, are crucial in countering electronic terrorism and protecting digital infrastructure from malicious actors seeking to exploit vulnerabilities for terrorist purposes
PEDIGREE
Allied Telesis is a leading provider of secure networking solutions with over 35 years of experience in the industry. With a comprehensive portfolio of products including switches, routers, firewalls, and wireless access points, Allied Telesis offers advanced security features, compliance with international standards, and a focus on network resilience. That the company is commitment to customer satisfaction is evident through its ongoing support and maintenance services, ensuring the seamless operation of secure networks. Trusted and experienced, Allied Telesis is the ideal partner for organizations seeking secure, efficient, and scalable networking solutions.
Of all the markets that Allied Telesis works in, high security specifically encompasses many of the areas that it excels in, and it has been able to demonstrate this by means of a number of certifications. These include the coveted JITC, FIPS140-2 and Common Criteria certifications which come from the United States federal government and the Department of Defence which tests and certifies information technology products for military use and are some of the hardest to achieve. Vendors and their associated solutions that hold these are often considered to be the gold standard for security and cyber related technology.
PROCESSES
Allied Telesis designs and builds products using its inhouse facilities ensuring that its supply chain is secure from end to end. With diversity of design and production across the globe, Allied Telesis ensures that interruption to supply is irradicated and processes can be cross-checked to minimise potential problems as early as possible. Allied Telesis builds its networking equipment with a focus on hardware security. This includes secure boot processes, hardwarebased encryption, and tamper-resistant components to prevent unauthorized access or modifications to the device.
Allied Telesis products support robust authentication and onboarding methods including Username/Password, 802.1x,
RADIUS, TACACS+ and certificate-based authentication. Strong authentication mechanisms help ensure that only authorized users can access the network and its resources. As more and more IoT driven devices require network access, having multiple layers of NAC is critical to ensure the strongest method supported by the device can be utilised. Encryption is a critical aspect of network security. Allied Telesis products support various encryption protocols, such as IPsec and SSL/TLS, to secure data transmitted over the network and protect it from eavesdropping and unauthorized access. This is important not only on wide area links between sites but also it is now becoming more commonly used on the local network. Allied Telesis offers switches across multiple ranges with dedicated chipsets supporting MACSEC encryption ensuring end-to-end security for its customers.
PRODUCTS
Allied Telesis offers products with intrusion prevention systems (IPS) that monitor network traffic for suspicious behaviour and take appropriate action to prevent or mitigate potential threats. Used in conjunction with the powerful Allied Telesis AMF-Plus and Vista Manager product suites, once a potential threat is detected on the network, it can be mitigated automatically and either removed or quarantined, so that remedial action can be taken. Of course, the company appreciates that some customers may have their own preferred IPS and/or firewall security so naturally AMF-Plus’s capabilities to neutralise both wired and wireless threats can be used in conjunction with a great number of other providers offerings. Access Control Lists (ACLs) allow administrators to define rules for traffic filtering based on specific criteria, such as source/destination IP addresses, ports, or protocols. This helps restrict network access and mitigate risks associated with unauthorized or malicious traffic. Definition of ACLs that are easily implemented, secure and optimisable has historically been
a challenge. With AMF-Plus, their new security dashboard, makes understanding these rules and propagating them across the network easily achievable.
Allied Telesis managed products use an operating system called AlliedWare Plus and this goes across their entire range of products not just on switches as you might expect; it also covers their firewalls/UTMs, Wi-Fi access-points and industrial and ruggedised products. This means that a customer only needs to learn one command structure and is able to support their entire estate. This minimises potential incompatibilities across vendor borders which might open attack surfaces. This lightweight yet secure operating system uses industry standard syntax so it’s easy to integrate into a customer accustomed to other market leading equipment providers. This operating system receives regular firmware updates from Allied Telesis to ensure that devices remain resilient against newly discovered vulnerabilities. Historically, updating of firmware has been a time-consuming process for customers but this can be automated and scheduled with AMF-Plus ensuring a customer’s network is kept up to date without the hassle of visiting every device.
Allied Telesis is ideally placed in the market to offer best of breed products and support for customers of all markets ensuring peace of mind to CISOs and their IT teams countering security threats that we all face. L


ADVERTISEMENT FEATURE FEATURE FURTHER INFORMATION www.alliedtelesis.com 16 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
Chris Dimitriadis, chief global strategy officer at ISACA (Information Systems Audit and Control Association) on how public sector organisations can protect themselves from cyber threats
BREAKING DOWN DIGITAL TRUST BARRIERS
Public sector organisations in the modern digital economy face an ambitious task in earning – and maintaining – people’s trust. Recent events like high-profile security breaches involving senior government officials, and the ransomware attack on Hackney Council, have fed into a growing distrust in many institutions. And with heightened scepticism about how well-equipped organisations are to protect personal data, building a trusted public relationship is more challenging than ever.
The only path forward is for organisations to make strengthening digital trust – defined by ISACA as “the confidence in the integrity of relations, interactions and transactions among providers and consumers within an associated digital ecosystem” – a central priority, and to strategically work through all obstacles that could impede this pursuit.
What specifically is preventing public bodies from achieving digital trust? According to ISACA’s State of Digital Trust 2022 survey report, the top obstacles are a lack of staff skills or training, lack of alignment of digital trust and strategic goals, lack of leadership buy-in, and lack of budget. Let’s look at each of these areas to see how public bodies can work through these obstacles to achieve digital trust.
LACK OF STAFF SKILLS AND TRAINING
Many of the digital trust fields –areas such as cybersecurity, privacy, IT audit, risk management and IT governance – face critical staffing shortages, as the labour supply in those areas often does not keep pace with public sector demand. But in many cases, organisations can find the right employees by being less rigid about criteria for filling these roles. They can then reduce the skills gaps by providing ongoing training and supporting relevant professional certifications while on the job.
Organisations also need to strongly promote a culture of collaboration among these professionals. Digital trust cannot be achieved with a siloed approach – security and privacy professionals must support each other’s work and ethical considerations related to emerging technology implementations must be considered cross-functionally.
LACK OF ALIGNMENT OF DIGITAL TRUST AND STRATEGIC GOALS
Digital trust is so critical for public sector organisations to succeed that it must be baked into strategic goals from the outset, instead of only being considered once goals already have been established. People rightly expect public bodies to demonstrate urgency in putting plans into action but failing to ensure the necessary security measures are in place can undermine commitments to serve the community. Taking process shortcuts in the name of a near-term goal is likely to lead to a long-term problem that could erode trust with the public and key stakeholders.
LACK OF LEADERSHIP BUY-IN
While public sector leaders may not understand all the intricacies of the threat landscape or data privacy regulations, they should understand how building and sustaining trust with the public is necessary to achieve their goals.

If that is not the case, digital trust champions such as chief information security officers, data privacy officers and risk leaders should engage organisational leaders by communicating in clear, business-focused language what the business risks are of failing to prioritise digital trust.
Too often there is a disconnect between organisation leaders and technology functions in the language that they speak. Framing these conversations around building digital
trust can be an effective way to bridge that divide and gain leadership buy-in.
LACK OF BUDGET
Prioritising digital trust inevitably requires a significant investment in staffing, tools and ongoing training and professional development for employees. While the public sector is often burdened by budget constraints, the risks of failing to make the necessary security investments must be carefully considered.
Public sector organisations are an attractive target for cyber criminals due to the sheer volume of personal identifiable information they hold. And while the tactics employed by bad actors are becoming more sophisticated, many organisations are increasingly at risk due to outdated technology, systems, and processes. As we have seen in the fallout of the ransomware attack on Hackney Council, huge investments in time, money, and resources are required to recover from such an incident, but budgets can be better managed when proactive steps are taken in anticipation of threats.
OVERCOMING THE OBSTACLES
While there is much progress to be made, each of the above obstacles can be addressed through commitment from public sector leaders and a renewed commitment to cross-functional collaboration.
Without earning and preserving trust from the public and other stakeholders, no amount of digital innovation will be enough for modern enterprises to remain competitive. Whatever factors might currently be holding organisations back from driving toward digital trust must be identified and overcome to set a foundation for sustainable success. L
CYBERSECURITY
FURTHER INFORMATION www.isaca.org 17 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
ENVIRONMENTAL STREET FURNITURE (ESF) SECURE, YOUR GLOBAL SECURITY PARTNER


Whether it’s safety, high-security, traffic management or securing your home, ESF Secure have the perfect solution so that you can protect what matters most, and give yourself peace of mind in knowing that your property is protected.


With over 20 years of industry experience, ESF Secure supplies products that protect all aspects of everyday life including transport, event security, private business security, residential properties, public spaces, critical national infrastructure, hospitals, power stations, embassies and data centres.



They are Ireland’s leading provider of hostile vehicle mitigation (HVM) bollards and have been designing, installing, and servicing crash-tested high-security products for over two decades. In that time, their HVM security bollards have helped secure high-profile sites around the world, using their local team of employed, trained and qualified engineers. As their clients can verify, their solutions consider all realistic threat profiles and operational requirements whilst not compromising on site aesthetics. They have experience with working very closely with their wide range


of manufacturing partners, ensuring that they can offer the best possible solution to every security requirement, whilst considering that the overall appearance is not diminished, yet made more presentable to those viewing. With such extensive experience in the security industry, ESF Secure have provided solutions for a wide variety of high-profile organisations and facilities such as: Waterfront Hall – Belfast ESF Secure had the pleasure of supplying this venue with a temporary crash-tested hostile vehicle mitigation (HVM) road blocker and access gate, which ensured safety and security of the venue while it was hosting the annual CyberUK conference for 2023.
Road & Transports Authority (RTA) Stations, Dubai Working with our local UAE partners, Tanseeq, ESF Secure designed and supplied the RTA (Road Traffic Authority) of Dubai with forty bollards for three metro stations. The bollards, tested and certified to UK standard, PAS68 K12 ratings, are designed to withstand a vehicle of 7.5 tonnes travelling at up to 50mph.
Coca Cola Arena, Dubai
In a deal worth over £600k, ESF completed their largest deal to contract to date at the new, state-of-the-art Coca Cola Arena in Dubai. Here, ESF supplied a vast collection of over 700 products including; bollards, benches, tree gates and litter bins to complete the look, and secure the safety, of the ultra-modern arena. ESF Secure pride themselves with being able to provide a sense of comfort and assurance that their client’s resources have been protected to the upmost capability. ESF Secure are always exploring new methods of security to match their clients’ needs no matter the surroundings. L



18 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55 +44 (0) 2890364101 SECURE@WORLDOFESF.COM WORLDOFESF.COM/SECURE
FURTHER INFORMATION worldofesf.com
Figen Murray, campaigner and mother of Martyn Hett, after whom the legislation is named, explains why it is important that Martyn’s Law applies to small venues as well
PROTECTING PEOPLE AT ALL VENUES

Iwas thrilled to see that the prime minister presented the draft bill for Martyn’s Law on 2nd May. Although it was an important step, I appreciated the long journey that still lay ahead. Rishi Sunak explained it at great length during our telephone conversation on 15th December. I knew that the next big step would be the two-month period of scrutiny led by the Home Affairs Select Committee, standard procedure for proposed legislation to undergo. This process started on 6th June, and I was allowed the privilege to give evidence alongside Nick Aldworth as the first two witnesses to appear. Since I started this journey, nerves never came into play, yet I suddenly felt very anxious about this day. What finally hit me after all these months of campaigning and speaking about the legislation was the realisation that what we are working on is so important. At one point I had a “What have I started” moment. The enormity of the responsibility suddenly hit me, the importance of the legislation dawned on me, and I knew how
exceptionally difficult it would be sitting in that room. There was a lot of kindness and care in the room towards me, the grieving mother. But then other witnesses appeared, and a healthy debate ensued. Martyn’s Law clearly was not popular amongst all people present in the room. The final day of evidence led me to go on another trip to London on 20th June. I did not want to miss this significant day, needed to hear what people were asked and what answers would be given. But this day felt very different. Scrutiny was harsh and relentless! Misunderstanding hung in the room and led to confusion, maybe even irritation for some. It was very difficult to sit, yet not being able to speak, object or explain.
WHAT’S NEXT?
The committee has just delivered its report to be presented to the Home Office. I guess thereafter the Home Office will take the comments on board and adapt the legislation before government goes into summer recess. E
MARTYN’S LAW
19 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
SECURITY EXCELLENCE SINCE 1950
ABOUT US
Founded in 1950, Todd Research has a proud history of designing, manufacturing and supplying X-ray scanners, metal detectors and blast suppression equipment across a diverse range of public and private market channels



WHY CHOOSE US ?
Our history, experience and worldrenowned expertise sets us apart from our competitors. With a highly-skilled team focusing on research and development, we provide innovative solutions that suit the specific requirements of every customer we work with,
Global Leaders
Operating in over 80 countries, we focus on being ahead of our competitors and introducing new ideas following the principle of 'innovation, not imitation'
Award Winning Innovation Customer Service

Proud winners of the Queens Award for Innovation 2022, for our cabinet x-ray scanners. From threat assessment and management, to health and safety compliance, we go the extra mile to ensure our customers always have the support they need

WWW.TODDRESEARCH.CO.UK XRAY@TODDRESEARCH.CO.UK +44 1480 832202
WHEN THE CHRISTCHURCH SHOOTER DECIDED ON WHICH TARGET TO ATTACK, THE SLEEPY TOWN OF CHRISTCHURCH WAS NOT HIS FIRST CHOICE, BUT HE DECIDED TO GO FOR IT IN THE END TO SHOW THE WORLD THAT TERRORISTS DO NOT JUST GO FOR THE


My husband and I went to visit families from the two mosques three months after their attack. We arrived late Sunday night and were invited at 9 am Monday to the bigger of the two mosques. We walked during rush hour yet there was very little traffic. As we walked towards the mosque, we realised it was situated right opposite a big park. The mosque was amidst a row of houses in a quiet residential area. It seemed unfathomable that anyone would just walk in and shoot 51 people dead. The picture just did not seem to fit, yet it happened. A few days later we visited the second much smaller mosque. Our journey led us to the outskirts of town, an area where poverty was very evident. We eventually arrived at a dirt track
and saw a tiny house at the end of the drive. It was the size of a small bungalow. Seven people were shot dead and had no chance of escape. It was quite hard to do this trip and see how vulnerable the people at both mosques were. So, when I see comments about village halls hardly likely to become a target I am taken aback at the short-sightedness and the ignorance of such remarks. Whatever the legislation will look like once it has been scrutinised, I can only hope that people are able to consider that terrorism may eventually go the same way as county lines. Terrorists may well start going for softer targets and village halls definitely count as such. L
MARTYN’S LAW 21 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
Dr Cath Hill, Manchester Arena attack survivor, lecturer in social work at Lancaster University and member of the National Emergencies Trust’s Survivors Advisory Forum explains some of the findings of the Bee The Difference report

NOW IS THE TIME TO CREATE CHANGE FOR YOUNG PEOPLE AFFECTED BY TERROR
It’s been six years since the Manchester Arena terror attack, and nearly a third of young people affected by that night have not received any professional support. As a survivor of the attack, along with my son who was ten years old at the time, I know first-hand how crucial it is for young people to receive specialist support. It can help them to recover and rebuild their lives after experiencing trauma.
One of the reasons I co-founded the Manchester Survivors Choir in 2018 was that, as both a social worker and a mum, I could see a need for greater support for those affected, including the many hundreds of young people. Being able to come together with other survivors and share our passion for music, as well as our experiences of the attack, was a lifeline. But it also shone a light on the disparities
SURVIVORS OF TERRORISM 22 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
in support being offered, and the lack of understanding about their needs.
It’s why early last year I approached the National Emergencies Trust about creating new insights into the experiences of young Manchester survivors – and how Bee The Difference was born. The research project is a collaboration between nine incredible young survivors, the team at the National Emergencies Trust and myself and colleagues at Lancaster University. It aims to enhance understanding of the impact of terror on young people; what support is most helpful –and ultimately improve outcomes for future young survivors.
The nine young survivors led the design of a Bee The Difference survey. This launched in August last year and was open to young Manchester survivors who were under 18 at the time of the attack. Having the young people lead it was vital because it meant that the right questions were asked in the most compassionate way possible, and crucially without asking young people to retell their personal stories. The survey also went through a rigorous process with Lancaster University’s Ethics Panel.
More than 200 young survivors filled in the survey in the months that followed, providing both quantitative data and detailed qualitative feedback. Thanks to their contributions we now have a clear picture of how to improve outcomes for young people affected by terror in the future. So, what can we learn from their experiences? The report highlights six actions individuals and institutions can take to improve the support and access available.
BEE VISIBLE
Make sure that support is visible and readily available for young survivors and their loved ones so that the onus is not on them to find it. The research shows that 29 per cent of young Manchester survivors have never received professional support and some of the key reasons for this are that it was never offered to them; they didn’t feel comfortable to ask for it; and they didn’t know where to find it.
In the aftermath of future attacks, local authorities, schools, GPs, charities and others could all play a valuable role by signposting the support available to those affected. Interestingly, the research highlights that offering mental health support early on can help to validate young people’s feelings, so can have a positive benefit straight away, even for those who may not feel ready to take up the offer.
BEE COMPASSIONATE
Listen to, validate and take proactive steps to accommodate young
THANKS
survivors’ new needs. The findings show that the simple act of validating young people’s feelings can make a huge difference to their wellbeing; and is something all adults and organisations in positions of care could be mindful of should the worst happen again. The qualitative feedback in the report suggests young people had their feelings dismissed because of their age.
“... when I asked for help they brushed me off and put it down to just teenage hormones. To then just put me on antidepressants and that was only at 18 - and they didn’t even think of referring me to a therapist.”
BEE EXPERIENCED
Make sure that specialised trauma support is accessible and readily available, wherever survivors are based. While many young people received incredible pastoral care from their schools, many noted that they would have benefitted from more specialised help – and in some cases, this was a long time coming. In fact, while 93 per cent of young survivors felt they needed support in the aftermath of the attack, 70 per cent received no professional help within the first month and 31 per cent received no professional help within the first year.
“I sought help from my school nurse/therapist a few months after the attack when I was experiencing nightmares...She read from a printed stapled booklet and told me to have a bubble bath before going to bed to prevent the nightmares. This wasn’t helpful.”
One form of “experienced” support was peer-to-peer support from other survivors. This proved vital because it gave young people a chance to connect with others who really understood them. Alongside this, specialist traumainformed experts were highly valued. Many were referred to specialists by their GPs or through the Manchester Resilience Hub.
BEE FLEXIBLE
It’s clear that young survivors benefit most when they can choose the kind of therapy that works for them. But this was often not the case, and some felt that adults
made the wrong choices for them. In the future, trusting children and young people to have a say in the support they receive could help to significantly improve outcomes.
“...it was clear the counselling was directed to younger kids as a method of drawing pictures with crayons and being unable to speak freely made the experience feel incredibly condescending and difficult. Therefore it made my mental health worse and I was unwilling to continue.”
BEE PATIENT
Remember that recovery isn’t linear and can take time. Mental health needs evolve over time and sometimes major life events and anniversaries can be retraumatising. Nearly a quarter (23 per cent) of young survivors continue to receive psychological support today. A further one in five have stopped receiving professional support (19 per cent) but feel they would still benefit from it. Anniversaries, in particular, can be triggering for young survivors, making it vital to factor these in when planning for their long-term care.
“I would say that I am affected more now than I was 5 years ago. I receive support from family and friends [...] I struggle to comprehend what even happened that night.”
BEE PROACTIVE
Act on young survivors’ experiences to turn their challenges into future change. There’s more that can be done now to improve support for young people following a major traumatic event and the report suggests ways that individuals, educators, healthcare professionals, government and other public bodies can make a difference. Now that the Bee The Difference report has launched, the hard work needs to really begin. It’s time to create change for young survivors, together. L
FURTHER INFORMATION
To read more about the Bee The Difference research, please visit the National Emergencies Trust’s website: https://nationalemergenciestrust. org.uk/beethedifference/
TO THEIR CONTRIBUTIONS WE NOW HAVE A CLEAR PICTURE OF HOW TO IMPROVE OUTCOMES FOR YOUNG PEOPLE AFFECTED BY TERROR IN THE FUTURE
SURVIVORS OF TERRORISM
23 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE



Get a free quote 0800 408 4766 www.jacksons-security.co.uk SolutionLogisticsProvider Manufac ture Logistics Installation + Ser vice Logistics Logistics Suppor t Made in Britain 25 year guarant e e App roved installation In housedesignteam 70 yearsofexperience Linebacker® PNR Discreet protection against vehicle-borne attacks
Deborah Ainscough, founder and director of event safety and crowd management specialist, Crowdguard, discusses the growing popularity of fan zones in stadium grounds and the need to consider safety and security for these temporary facilities

KEEPING FANS SAFE IN THE ZONE
The FIFA Women’s World Cup has kicked off down under, the eyes of the world are not only on how we secure football matches, but also how we enable fans across the world to enjoy the shared experience of watching the action on a big screen and sharing both the joy of victory and the anguish of defeat.
Fan zones have become an increasingly popular concept for major tournaments, landmark friendlies and league matches alike, providing an opportunity to generate revenue and bring the fan community together.
Whether a fan zone is there to enable fans to enjoy a shared match experience for far away fixtures, as it will be during the FIFA Women’s World Cup, or as a place for fans to congregate before and after a home game, security risks need to be addressed as part of the planning process to provide a welcoming environment for fans before, during and after the match, while addressing the counter terrorism risk.
EXTENDING THE DUTY OF CARE BEYOND THE STADIUM
While most club owners and stadium operators already have robust security measures and risk assessment protocols in place for their actual stadium, managing the crowds outside of the stadium but still within the grounds can be more challenging. Fan zones are often located in these areas within the perimeter of the stadium’s grounds, but outside the protection of the stadium. During fan zone opening hours, pedestrians need to be able to access the area easily, while vehicular access must be prevented and fans – potentially thousands of them – need to be protected from errant vehicles and vehicle-as-a-weapon attacks.
SPECIFICATION & RISK
To create a pedestrian-permeable perimeter that enables fans to flow in and out of the fan zone while protecting them from errant vehicles and vehicle as a weapon attacks, E
PERIMETER
25 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
SECURITY
GROUNDBREAKING WEAPONS DETECTION SYSTEM



THREAT DETECTION THROUGH ELECTROMAGNETICS www.ceia.net GAME DAY AT RECORD SPEED. • QUICKLY AND AUTOMATICALLY SCREEN GUESTS with their backpacks and bags • EXTREMELY HIGH THROUGHPUT with near-zero nuisance alarms
DETECTS HANDGUNS AND MASS CASUALTY THREATS, such as high caliber assault weapons and IEDs
EASY TO RELOCATE AND QUICK TO INSTALL: Less than 1 minute setup time • INDOOR AND OUTDOOR OPERATIONS
more information, contact your CEIA representative at info@ceia.co.uk or call us today at +44 1789 868 840 • +44 7887 421 410 NEW OPENGATE_advert_FC060K0480v1000gUK.indd 1 08/03/2022 08:31:08
•
•
For
PERIMETER SECURITY
an IWA 14-1 certified HVM (hostile vehicle mitigation) system is usually required. The correct specification and configuration of HVM will depend on the level of risk for a specific site, and a threat vulnerability and risk assessment (TVRA) will consider all elements of risk so that the HVM provider can recommend a best-fit solution. This should take into account factors including the layout and topography of the site, the anticipated number of visitors and required flow rates, and vehicle dynamics, such as the likely velocity and mass of a vehicle on approach to the pre-determined location and any stopping distances relevant to the crowded space and fan zone. Specifying the correct HVM system or combination of systems should always be aligned to risk, with any variation from the ‘as tested’ configuration of the HVM system, or additional risk factors due to value engineering, clearly explained in writing by the provider.
EASE AND SPEED OF DEPLOYMENT
For temporary event spaces like fan zones, a surface-mounted HVM system is usually the preferred option because this can be installed and removed quickly and easily with no damage to the road surface and without the disruption of civil engineering works. The time it takes to install a HVM system varies depending on the amount of protection required and the system used, but it can be as fast as five minutes for a single array of a system designed for rapid installation, or a day (or overnight) programme for a more complex and larger HVM installs. Regardless of which system is used, it is essential that the HVM solution is installed in line with the specification by trained technicians to quality assured and clearly documented processes. This includes a photographic record of the project. Installation should always be an integral part of the specification and supply contract because HVM performance relies on correct deployment. It is akin to packing a parachute – you would want an expert to pack it to feel assured it would keep you safe and the same principles apply to keeping fans safe at the stadium.
TEMPORARY VEHICULAR ACCESS
Although the purpose of an HVM system is to prevent vehicles from accessing the location, consideration needs to be given to whether there will need to be authorised vehicular access to the fan zone area at any point. This could include a requirement to allow delivery vehicles, the potential for emergency vehicles to be called to site, or even for normal access to car park areas on nonmatch days. Vehicle access plates can be included in the installation of some HVM systems to enable vehicles to move freely in the area for maintenance and delivery at times when the fan zone is not in use, or to allow rapid access should blue
light services be required. Building this type of flexibility into stadium safety and security enables the installation to remain in place for the entire football season, while adapting to different safety and operational requirements.
CUSTOMISATION & AESTHETICS
Alongside their safety and security function, HVM systems at fan zones also provide an opportunity to enhance the environment with branding, signage, wayfinding or advertising. A key consideration for fan zone security is not just how much the physical measures in place improve safety, but how much they make people feel safer, so there is a balance to be struck between selecting a solution that visibly provides protection and one that maintains a welcoming aesthetic. Fan zones exist to celebrate the power of sport to bring people together, and HVM systems can embrace that principle through customisation. Options include club or tournament branding, information, wayfinding or ads – or a combination of these.
FENCING AND TURNSTILES
If access to the fan zone is ticketed, crowd management for ticket checks
must also be factored into the planning and safety provision. Temporary fencing or hoarding can also be used to segregate the fan zone area from other locations within the stadium’s grounds too. Again, it is important to consider any requirements for vehicular access and controlled pedestrian access so that appropriate vehicle access gates, pedestrian gates or pedestrian turnstiles can be incorporated into the installation. Quality-assured deployment by experienced technicians is equally important when temporary fencing or hoarding is installed for fan zones, ensuring that temporary systems are correctly configured, secured and ballasted to provide the protection of a permanent fixture with a temporary installation.

PROTECTING THE STADIUM’S GREATEST ASSET
Vehicle-as-a-weapon attacks are a low complexity methodology used by terrorists to target crowded spaces with the potential to cause mass casualties and serious injury. HVM protection has an important role to play in protecting the stadium’s most important assets – the fans. L
FOR TEMPORARY EVENT SPACES LIKE FAN ZONES, A SURFACE-MOUNTED HVM SYSTEM IS USUALLY THE PREFERRED OPTION
27 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE 08:31:08
SECURE YOUR PERIMETER WITH AFSS LTD
Vehicle incidents have always been part of our daily lives and with vehicles increasing on our roads year on year incidents increase. Organisations should put in place HVM systems where the public are put in vulnerable lifethreatening situations. PIPS HVM is the only HVM system designed and impacted specifically for these alfresco applications.

STANDARDS
• PAS68
• IWA-14.1
• ASTM

We will be operating the New NPSA ISO 22343 standard, which is affected from late summer 2023 and replaces PAS68 & IWA - 14.1

Whether it’s a perimeter solution incorporating HVM products with integrated access control and detection systems, AFSS Ltd will deliver a calibrated solution which fits each specific organisations operational demands and needs.

• Event physical security measures
• Pedestrian Access control
• Facial Recognition/CCTV

• Stadia security systems
• HVM Measures
www.asset-frontline.co.uk
Tel: +44 (0) 1767 318 620
28 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
Perimeter security is essential to prevent break ins and break outs. A marked, safe and secure perimeter is crucial to protect any property, especially if the building is high-risk or in a high-risk area
CONSIDERING ALL ASPECTS OF PERIMETER SECURITY
Physical barriers are the most obvious sign of perimeter security, i.e. fences, gates and walls, but there are many other aspects, including technology, security systems, alarms and cameras, and good perimeter security encompasses all of these things.
PHYSICAL PERIMETER SECURITY
Physical barriers have been used for thousands of years as an effective way to protect people and property, but nowadays these physical barriers are much more advanced and quicker to install.
Physical security is often the most obvious aspect of perimeter security and often acts as the best deterrent as well. The better your physical perimeter security, the less likely it is that someone will try and break in.
Today, physical perimeter security can range from simple fences and hedges right up to electric gates.
CONSIDER YOUR CIRCUMSTANCES
It is important that whatever physical security you are installing, that it matches your specific circumstances with high-risk or sensitive areas obviously needing more protection. Specialist businesses, contractors
and consultants can help you to pick the protection that is right for your property, as well as install it. On this note, it is important to consider physical barriers that can adapt to the requirements of the location in question. This could be rising bollards to prevent access by unauthorised vehicles or an electric gate to keep out unwanted visitors on foot.
One obvious example of an adaptive physical barrier is to consider extra protection at night or at weekends when the premises may be empty. Many premises have a barrier or gate that is only closed overnight to protect the property when there is not the high footfall or human security option present. However, you need an access control system in order for these to work. This could be in the form of a control panel with a passcode, or for a more secure system, issuing individual access keys or key cards to authorised persons so you know who is entering and when and to prevent something like a passcode being shared across too wide an area. Individual keycards also help to improve fire safety measures and evacuation procedures as you know who is and isn’t in a building at any one time.
For extremely high-risk areas, you can even consider biometricenabled access control.
LAYERS
You should also consider different layers of perimeter security, the most obvious being the property boundary and the building itself, though there are several other factors to consider in between.
Perimeter security can be alarmed to notify those responsible for security in the case of unauthorised entry.

Perimeter CCTV is also an important consideration. CCTV deters any would be criminals from breaking in in the first place, as they know there will be evidence and they could be identified. It also ensures that the physical barriers are monitored for any vulnerabilities and that the perimeter can be remotely monitored, as well.
Perimeter lighting is an integral part of perimeter security. This is often motion-activated to save energy. Again this acts as a deterrent. Good perimeter security will encompass all of the above, thought the most important thing is that it is relevant to and suitable for your premises to provide the best security possible or needed on your budget. L
PERIMETER SECURITY 29 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
MAKING THE UNPREDICTABLE, PREDICTABLE
Security plans are critical with counter terrorism, crime and protest threats continuing to evolve
Events can arise anywhere, at any time. Each incident is different - and many are impossible to predict. As such, the ability to prepare, respond and emerge stronger from threats and crime is key.
It is therefore critically important for organisations to adopt a robust Risk Management Plan that provides assurance, business continuity and organisational resilience. This statement sounds like an obvious one, but all too often these plans are out of date, not proportionate to the risk, and those responsible ‘on-the-ground’ are unarmed – opening organisations up to liability and putting people’s lives at risk.
Given the combination of likeliness and the unpredictable nature of this type of event, coupled with the devastating impacts that can occur, it is no wonder that there is scrutiny around how organisations are managing this type of risk.
The need and urgency for attention in this area is further compounded by the forthcoming Martyn’s Law, with particular focus around counter terrorism threats and the safety of Publicly Accessible Locations, and whilst the legislation is still in draft format, it is clearly recognised that steps need to be taken ‘now’ to address the quality of Security Plans and plug the ‘gaps’ in our armour.
INTELLIGENCE EXCHANGE
In a move to support the sharing of intelligence across multi-stakeholder groups, Zinc Systems, in collaboration with the City Security Council (a collective of City security companies) and the City of London Police have launched an incident and communications platform called “CityINTEL’, that provides a solution for the two-way exchange of intelligence and critical communications, with groups that include Security Organisations; Private Sector Business; Business Improvement Districts; Police Groups; Emergency Services; Travel Networks and Night time economies.
This collaborative initiative not only enables intelligence to be shared but also increases the ‘eyes and ears’ on the ground to drive a more accurate and rapid response to events. The vision
for CityINTELL is a national roll-out, helping to make our country a safer place to live, work and socialise in.
“This platform is an example of the innovative new ways we are seeking to work in partnership with private sector businesses. Not only will it support our ability to react swiftly and efficiently in response to issues taking place in the City of London, crucially, this allows us to collaborate more tightly with the security personnel of Citybased firms, effectively multiplying our eyes and ears on the ground.
Security officers are very often the first responders in times of crisis and as such they provide an important support role to our police officers. We fully anticipate the impact of this new platform to be felt almost immediately in our response to incidents taking place within the City”.
Angela McLaren, City of London Police Commissioner
‘MOVE INTO THE WORLD OF DIGITALISED RISK MANAGEMENT AND KEEP YOUR BUSINESS, DOING BUSINESS’
Alongside the need for proactive horizonscanning and the sharing of intelligence is the need to operate a robust Security Plan, as businesses seek safety and security against a background of natural and man-made threats, and regulation.
This plan covers Proactive ‘preparedness’ measures such as Risk Assessments, Checks and Audits through to Reactive Measures; with the latter requiring standard and emergency operating procedures to be known and trained to those responsible, and for escalation and communication to be accurate, timely and if possible, automated.
It is this need that is now seeing the global incident and emergency management market growing at a compound annual growth rate of 6.7 per cent and is expected to be worth $171.8 billion by 2026 (according to MarketsandMarkets, 2021).
DIGITAL TRANSFORMATIONS
Zinc Systems is supporting organisations in the digital transformation of risk

management through the deployment of its core platform ‘SYNAPSE’ - a product designed to resolve the challenges of incident management, business continuity and organisational resilience.
It operates globally across many sectors including public sector agencies, government, and policing, as well as an enterprise client base. The red thread between them all is that they take the management of incidents and critical activities seriously.
As an integrated risk management platform, SYNAPSE is embedded into the heart of an organisation easily. It is highly configurable, easy-to-use and can scale quickly within a highly secure infrastructure. Core features include: Incident Reporting for any event (HSE, Security, Threat, Crime, Operations); Daily Occurrence Logs; Mass Notification; Case Management; Integrated Mapping and Visualisation; Task Management; Risk Assessments; Assurance - Checks and Audits; Dashboards and Reports; Integration Zone (APIs); Integrated Reporter App and Integrated Verification App. (Patrols, Assets Mg)
Zinc’s mission is to help organisations manage disruption smarter, protect what matters (people, brand, profits) and ensure that risk is minimised. If these are things that keep you awake at night, then it’s time to move into the digital age and implement a risk management platform that helps you prepare and manage for the critical events that can prove catastrophic for you and your organisation. L
ADVERTISEMENT FEATURE FEATURE FURTHER INFORMATION zinc.systems 30 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
Facial recognition has been in the news for featuring at high-profile events such as Harry Styles concerts. But these articles in the mainstream press often highlight the privacy concerns surrounding the technology. Without a high-profile success case, it’s hard to convince the public of the technology’s viability
UTILISING FACIAL RECOGNITION TO KEEP THE PUBLIC SAFE
Ahead of Harry Styles’ concerts in Cardiff on 20 and 21 June, fans were warned that they could be scanned by live facial recognition cameras deployed in the area by South Wales Police. The cameras were to be used to identify people wanted for priority offences.
South Wales Police stated: “it’s being deployed specifically to seek out wanted individuals. Fully appreciate the concert has a young audience, however concert-goers won’t be the only people in the city centre during this time.”
HOW CAN IT BE USED?
Live facial recognition (LFR) works by comparing faces with a watchlist, using artificial intelligence. The police stated that if you are not on a watch list, the biometric data collected won’t be stored and it will immediately be deleted.

At a Beyoncé concert earlier in the year, the force said the technology would be used “to support policing in the identification of persons wanted for priority offences… to support law enforcement… and to ensure the safeguarding of children and vulnerable persons”.
South Wales Police have used the technology at previous events. Using the technology at a rugby match, 108,540 faces were scanned, resulting in the arrests of two people.
South Wales Police has a LFR FAQ page on its website. It states: “The specific purpose for Live Facial Recognition deployment is: To support Policing in the identification of persons wanted for priority offences, to support law enforcement including the administration of justice (through arrest of persons wanted on warrant or unlawfully at large/ recall to prison), and to ensure and promote the safeguarding of children and vulnerable persons at risk.”
The website also lists occasions where the force has used LFR, as well as the
events already listed, the technology was utilised at Pride Cymru in August 2022 and Wales Airshow in July 2023.
The website says: “Live Facial Recognition technology is used as an efficient and effective policing tactic to prevent and detect crime, and protect the most vulnerable in our society.”
EXPECTED INCREASE
Biometrics and surveillance camera commissioner Professor Fraser Sampson recently commissioned an independent gap analysis by Professors Pete Fussey and William Webster. Fussey and Webster highlighted that the use of such technology is likely to increase. They said: “the Policing Minister expressed his desire to embed facial recognition technology in policing and is considering what more the government can do to support the police on this. Such embedding is extremely likely to include exploring integration of this technology with police body worn video”.
PERSUADING THE PUBLIC
So if use of the technology is to increase, how can the public be persuaded to accept it?
In his annual report, published in February, Sampson claims that the extent to which the public will tolerate facial recognition will rely on whether or not they believe that measures are in place to make sure that it is used lawfully and responsibly. There are two main ways to achieve this. The first is to update the legislation. Legislation is currently in the works in the form of the Data Protection and Digital Information (No.2) Bill, which is still at the early stages of its journey through parliament. There needs to be legal oversight over how and when the technology is used and by whom. For example, it may be acceptable to the public for the police to use LFR at concerts, but the public are less
likely to welcome it when used by shops, schools or even private users. There was criticism when Sports Direct announced that the use of LFR had cut crime in its shops. 50 MPs and peers supported a letter opposing the use of LFR by Frasers Group. The legislation also needs to cover how the data collected will be stored and used, who will have access to it and when it should be deleted. The other factor in changing the public’s opinion is to keep the public informed. Forces need to be clear about when they are using the technology and how, so the public can trust them.
Another aspect to consider, is that so far, there have been no highprofile success stories. Perhaps if the public became aware of an occasion or occasions where the technology had been used to identify a threat to the public and potentially prevent a crime, they would be more accepting of its use. One high-profile use case is set to be the Paris Olympics next year. Real-time cameras are set to use AI to detect suspicious activity, such as abandoned luggage and unexpected crowds. However, a new law states that while police can use CCTV algorithms to pick up anomalies such as crowd rushes, fights or unattended bags, it outlaws using LFR to trace “suspicious” individuals. It may be that introducing technology like this could be a stepping stone to getting the public to trust LFR. L
FACIAL RECOGNITION TECHNOLOGY
31 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
The mobile tool revolutionising emergency calls


FlagMii® EML from Regola is an SMS locator and video tool putting operators directly at the scene of an incident, through the mobile phone of the emergency caller. Combining mobile location data with live video feed, the Flagmii software sends an SMS link to the emergency callers mobile, allowing it to send valuable real-time situation video or images back to the control room.
Operators can observe first-hand the severity of an incident and personally guide activities while waiting for emergency services to arrive, enhancing decision-making ahead of rescue operations. FlagMii® EML includes a geolocation and tracking feature, translation services, chat and silent calls for threat/domestic violence situations, as well as support for the deaf or hearing impaired.
Introducing Flagmii® EML – getting resources to the incident, faster.


AIRPORT SECURITY SOLUTIONS
Shannon Airport is the thirdbusiest airport in Ireland and an important destination and transit point for both passenger and military aircraft. As well as an airport and associated buildings, the site also contains engineering works and is therefore both busy and complex.

SPECIAL CASE
The airport has a particular need for perimeter security because its use by the US military has led to it being a target for incursions and protests. It needed a comprehensive, future-proof perimeter surveillance solution that would also provide real-time situational awareness. The solution also had to scale and grow with the airport’s needs and with advances in technology.
The system that Shannon Airport chose uses high-definition scanning radars and intelligent rules-based software to protect both sides of the perimeter. Management and engineers at the airport worked with the supplier to design a long-term perimeter surveillance system with room for growth. The system is based on the supplier’s wide-area surveillance solution that combines high-definition radars and intelligent rules-based software. The solution can handle complex, active sites where legitimate and illegitimate activity may occur together. It can also handle all weather and light conditions – including fog, snow, bright sunlight and darkness, as well as extreme temperatures.
At Shannon Airport, the original installation was set up to surveil the airport grounds and around 10 metres beyond the perimeter. Three radars were used, which provided perimeter protection and a comprehensive overview of site activity. Over the years, the system has been extended to introduce additional capabilities, such as ‘friend or foe’ – which uses a tagging system to tell the technology whether an activity or vehicle is legitimate or not and to trigger an alarm (or not) accordingly.
FALSE ALARMS
The system has also been adapted to avoid the problem of alarms being triggered by wildlife. By specifying the size and source location of objects to be detected in specific areas, the number of nuisance alarms has been reduced – though some alarms do remain to provide ongoing ‘proof of life’ for the system.
The system installed at Shannon Airport is AdvanceGuard, provided by Navtech.
Shannon Airport’s chief security officer John Francis said: “Securing the perimeter is not just about perimeter protection but also about being able to verify whether your perimeter has been breached – and then dealing with it as efficiently and effectively as possible.
“One of our biggest problems has been nuisance alarms – we want to know that if we do have a breach, we can verify it very quickly. The system
is integrated with our CCTV system, so it gives us the ability to resolve alarms remotely very quickly and very efficiently. The nearest camera will respond to that alarm and will highlight the type of alarm – which means that you’re not spending an awful lot of time rushing around dealing with false alarms.”
He added: “Beyond the fence, we want to see or have as much advance notice as possible that we may have a potential breach. Occasionally, for example, animals come up beside the perimeter. The system gives us the ability to see what’s approaching the perimeter so as to give us that much advance notice that we can go out and see what’s going on.
“We use beyond-the-perimeter capability just to give us as much advance warning as possible so if we had a potential breach our patrol can go out and see who or indeed what is approaching the perimeter fence. So the system gives us the ability to, I suppose, put in a response – an early warning system, if you like – and to see if we’ve got a potential issue.”
John said: “We were sufficiently impressed that it works in all weathers, whether it’s fog, heavy rain or even snow – and the product is not affected by the elements of the weather. That is a significant advantage, especially if you’re dealing with other technologies, such as night vision, infrared or other technologies that wouldn’t be as effective or would be affected by atmospherics.” L
AVIATION SECURITY
Shannon Airport presents a rather complex situation when it comes to security. CTB takes a look at the problems the airport was facing and how these have been addressed
33 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
GROUNDBREAKING WEAPONS DETECTION SYSTEM
For more information, contact your CEIA representative at info@ceia.co.uk or call us today at +44 1789 868 840 • +44 7887 421 410
www.ceia.net
GAME


DAY
AT RECORD SPEED.
• QUICKLY AND AUTOMATICALLY SCREEN GUESTS with their backpacks and bags

• EXTREMELY HIGH THROUGHPUT with near-zero nuisance alarms
• DETECTS HANDGUNS AND MASS CASUALTY THREATS, such as high caliber assault weapons and IEDs
• EASY TO RELOCATE AND QUICK TO INSTALL: Less than 1 minute setup time
• INDOOR AND OUTDOOR OPERATIONS
34 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
THREAT DETECTION THROUGH ELECTROMAGNETICS
NEW OPENGATE_advert_FC060K0480v1000gUK.indd 1 08/03/2022 08:31:08
The complex, volatile and unpredictable nature of the terrorism threat is a reminder to security professionals around the world to not be complacent when it comes to emerging risks and the sophisticated approaches taken by those looking to cause harm
EXPLORE THE FUTURE OF SECURITY AT INTERNATIONAL SECURITY EXPO 2023
As the UK Government’s Terrorism (Protection of Premises) Bill, aka Martyn’s Law, progresses through Parliament, this is a crucial time for the security industry to stay as informed as possible.
Returning to Olympia London on 26-27 September, International Security Expo 2023 is set to provide security professionals with all the tools they need to take on current challenges and stay ahead of the curve for the future threats that may arise.

MARTYN’S LAW UPDATES YOU WON’T GET ANYWHERE ELSE
Across the Conferences and Summit there will be essential updates for those looking
to make sure they know how to comply with the Terrorism (Protection of Premises) Bill when it becomes law, including from those who drafted the legislation, those who will be implementing and enforcing it, alongside those who have been campaigning for it.
Shaun Hipgrave, director Protect and Prepare for the Home Office, Office for Homeland Security, will discuss Martyn’s Law from a policy perspective and how it fits into the priorities for the Office for Homeland Security. This is a unique opportunity to understand the Government’s thinking behind the legislation that has been passed to Parliament.
NaCTSO (National Counter Terrorism Security Office) have been charged with E
INTERNATIONAL SECURITY EXPO
08:31:08 35 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
Visual surveillance, scanning & monitoring solutions.


We have led the way in providing the latest and most effective technologies to the security industry, Governments and critical infrastructure for over 35 years.


Whether you are looking for the latest surveillance technology or need the most effective and easily deployed security scanning devices Inspectahire will have a solution to most effectively support your needs or assignment.
UK Distributor for the world leading: Get in touch
inspectahire.com | T: +44 (0)1224 789692 | E: enquiries@inspectahire.com TM
ensuring Martyn’s Law is implemented once it hits the statute books, with preparations already underway to ensure they are ready. A senior NaCTSO official will talk about those preparations and how people can get real practical advice to ensure they are ready. Elsewhere, they will give insight into their future preparations; what they are looking at three to five years ahead.
Looking at the legislation from a different perspective, a panel discussion featuring Tobias Ellwood MP, chair of the Commons Defence Select Committee, Chris Medhurst-Cocksworth, head
COUNTER TERROR POLICE UK WILL PROVIDE AN OPERATIONAL OVERVIEW OF COUNTER TERROR PRIORITIES, WHILST A SENIOR FBI AGENT WILL OFFER THE US PERSPECTIVE

of Pool Re Solutions and a senior member of NaCTSO, will explore the practicalities behind Martyn’s Law from a parliamentary, implementation and insurance perspective.
Figen Murray OBE and Nick Aldworth will return with a panel
delving into some of the areas within the draft legislation that may require amendment or clarifications, asking how the wider security community can help in the delivery of Martyn’s Law.
ESSENTIAL SECURITY INSIGHTS THAT CAN’T BE FOUND ANYWHERE ELSE

International Security Expo has built a reputation for its worldleading content programme, and this year is set to be no different.

The Global Counter Terror & Serious and Organised Crime Summit, in partnership with Counter Terror Business, will deliver high-level policy updates and strategic insights addressing the latest global terror and security trends and priorities.
Counter Terror Police UK will provide an operational overview of counter terror priorities, whilst a senior FBI Agent will offer the US perspective. E
INTERNATIONAL SECURITY EXPO 37 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
PROTECTION FROM EVERY SIDE
Long range detection with REDSCAN PRO






The award-winning OPTEX REDSCAN LiDAR series just went one better, with a new detector featuring its longest range yet. The REDSCAN PRO can accurately detect intruders and moving objects up to 50 x 100m away – making it particularly well suited for those responsible for protecting the highest security sites. And by creating rectangular, high resolution detection patterns, there are no ‘gaps’, so everything from facades to fences, ceilings to roofs can be covered. For the installer, the sensor’s intelligent multiple zones logic means each detection zone can be independently configured, while its camera module brings visual assistance for configuration and post-alarm analysis. The alarms and video stream can all be configured via ONVIF.





www.optex-europe.com














INTRUSION DETECTION | VISUAL VERIFICATION | TAILGATING DETECTION | VEHICLE DETECTION | PEOPLE COUNTING
THE INTERNATIONAL RISK & RESILIENCE CONFERENCE, IN PARTNERSHIP WITH RESILIENCE FIRST, WILL GIVE THE LATEST THINKING AND PRACTICAL INSIGHTS FROM INDIVIDUALS AND ORGANISATIONS WHO LIVE, EAT AND BREATHE RISK AND RESILIENCE

The role of cyber espionage in terrorist activities and how to detect and prevent such activities will be put under the microscope by Joel Aleburu from Microsoft, as Ian Acheson from the Counter Extremism Project discusses how to tackle the proliferation of terror from within the prison system.
The popular realities of terror thread returns this year, with a panel of victims of terror discussing their experiences and the personal impacts it has had on them. Participants include Figen Murray OBE, Ann Travers, Advocacy Officer for the South East Fermanagh Foundation (SEFF) and former Irish Senator Máiría Carhill. This will offer insights from a perspective that is essential to consider.
From a serious and organised crime perspective, the National Crime
Agency will give an overview of their priorities and recent successes. Lina Kolesnikova from ICPEM will explore narco-terrorism in Europe via case studies from the ports of Antwerp and Rotterdam, whilst William Dill from Larne Harbour will talk about enhancing security awareness around human trafficking. Other areas to be explored include OSINT, advanced persistent threats and how evolutions in information communication technologies are a critically important factor in determining global jihadist organisation and their targeting.
The International Security Conference will look at the practical implementation of new policies and how these should be applied within different areas. SCEG (Security in Complex Environments
Group) will run a panel on each day, featuring its members discussing the challenges and opportunities supporting the efforts to keep Ukraine safe and prepare for the future.
Satia Rai, CEO of IPSA and head of diversity, inclusion & belonging for Securitas UK, will host a panel discussion on diversity and how it is essential to stop groupthink, which can be disastrous when developing a security ecosystem. Peter Drissell, director of aviation Security for the UK CAA (Civil Aviation Authority) and Frederick Reitz from SAFEsky Inc. will both give talks exploring aviation security. Elsewhere on the Conference, Thomas Vonier from Chesapeake Strategies Ltd looks at security in public places, with case studies from Paris and Washington DC, whilst Brooke Tapsall from DroneALERT discuss the importance of adversarial testing (red teaming) for increased asset or location protection, using the FIFA World Cup as a case study. The International Risk & Resilience Conference, in partnership with Resilience First, will give the latest thinking and practical insights from E
INTERNATIONAL SECURITY EXPO 39 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE





WWW.F24.COM 01923 437 784 Your trusted partner for Notifications, Critical Event Management and GRC for 360 Operational Resilience Prepare your response to an operational threat with Europe‘s leading Software-asa-Service (SaaS) provider for risk and crisis management, emergency notification and global threat monitoring Scan here to learn more about F24 in a short video Join us on stand E140 to discuss our solutions for all things Resilience +44 (0)1234 826 316 sales@staffordbridge.com www.staffordbridge.com Combining World Class Physical Security with Bespoke Aesthetics Blast Fire Ballistic Security Multi-threat protection Specialising in the design and manufacture of high performance doorsets, walls, windows and louvres Scan Me 40 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
individuals and organisations who live, eat and breathe risk and resilience.
Jamie Shea, former deputy assistant secretary general of emerging security challenges for NATO, will host a panel discussion focusing on global challenges from a security, resilience and economic perspective.
Lianna Roast from the Cabinet Office Emergency Planning College will talk about learning and resilience and turning lessons into action, Verity Davidge, director of policy for Make UK will discuss navigating supply chain resilience through complex and troubling times with Resilience4Ports, whilst Sarah Cumbers from Lloyd’s Register Foundation will talk about their World Risk Poll – the first global study of perceptions and experiences of risk to people’s safety.
THE PLACE TO FIND INNOVATION IN SECURITY
For security buyers, specifiers and decision-makers, the exhibition floor is the ideal place seek out the next
SHOWCASING THE EXCEPTIONAL LEVELS OF SUPPORT RECEIVED FROM UK GOVERNMENT, THE GOVERNMENT ZONE WILL FEATURE THE LEADING AGENCIES AND DEPARTMENTS, PROVIDING A UNIQUE OPPORTUNITY TO INTERACT AND LEARN ABOUT FUTURE PLANS


generation of security solutions. More than 300 international exhibiting brands will spotlight their innovative products and solutions. This includes
the likes of APSTEC Systems, Astrophysics, Audax, Gallagher Security, HS Security Group, Leidos, LINEV Systems UK Ltd, Mitie, E P
INTERNATIONAL SECURITY EXPO 41 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
Pitagone, Rapiscan Systems, Rohde & Schwarz, Smiths Detection, Vaylia and Weytec. With product categories ranging from Screening and Scanning; Perimeter Protection; Hostile Vehicle Mitigation; Intruder Detection and Monitoring; Drone
and Counter UAV; Access Control and Biometrics; and CCTV and Surveillance, attendees are certain to find the solutions to their security challenges, as well as being inspired by a hotbed of product launches revealed at the event.
The Product Innovation Theatre will see leading suppliers come together to showcase their products, services and solutions, with case studies bringing these to life. This allows a first-hand look and an opportunity to understand the capabilities of emerging technologies and solutions.
DELVE INTO SPECIALIST ZONES AND PAVILIONS
Showcasing the exceptional levels of support received from UK Government, the Government Zone will feature the leading agencies and departments, providing a unique opportunity to interact and learn about future plans. Participants include Joint Security and Resilience Centre (JSaRC), Counter Terror Policing, British Transport Police, National Counter Terrorism Security Office (NaCTSO), UK Defence & Security Exports (UKDSE), FCDO Services, Security Industry Authority (SIA), Dstl, and Defence and Security Accelerator (DASA).
The Perimeter Protection Zone, in association with LPCB, supported by PSSA and sponsored by Barker’s Fencing, will feature the latest products from fencing, barriers, bollards, video surveillance and intruder detection, with the popular LPCB Live Testing Lab returning to put LPCB accredited products through vigorous testing live at the event.
FOR SECURITY BUYERS, SPECIFIERS AND DECISIONMAKERS, THE EXHIBITION FLOOR IS THE IDEAL PLACE

The Drone & Counter UAV Zone hosts world-leading suppliers of drone and counter UAV capabilities. Showcasing the very latest technologies and solutions, it is the ideal place to come and meet suppliers who can help mitigate the drone and UAV threat.
The crises we have faced over recent years, and the unbelievable global response we have seen, emphasises the need for the International Risk & Resilience Zone. Highlighting the fundamental aspects of Resilience, Prevention, Response and Recovery, you will find a one-stop-shop to expand your knowledge.
Elsewhere the Counter Threat Pavilion, in partnership with CBRN-UK, Counter-EO-UK and ADS, will showcase companies from within these key industry sectors alongside live demonstrations; whilst the SCEG Pavilion will bring together security and risk companies committed to the development and implementation of
INTERNATIONAL SECURITY EXPO 42 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
international standards for the private security and crisis management sector.
CO-LOCATED WITH INTERNATIONAL CYBER
EXPO – 1 PASS, 2 SHOWS
International Security Expo attendees will also benefit from its colocation with the industry’s hottest cybersecurity event: International Cyber Expo. Expanding into the National Hall at Olympia London this year, it will disrupt the status quo as a dynamic and inclusive annual event where business, innovation and education converge. Drawing a wider audience to International Security Expo, the co-location with International Cyber Expo offers attendees a 360° view of the industry, providing a comprehensive platform to identify products and services from all corners of the industry.
Rachael Shattock, group event director, International Security Expo, added:
“International Security Expo 2023 is going to be an unmissable event for global security professionals. The content on Martyn’s Law will ensure you are in the best position to plan for and understand the legislation, and nowhere else will you get the depth of information from so many of the people behind it, all for free. We are delighted to welcome back hundreds
INTERNATIONAL SECURITY EXPO ATTENDEES WILL ALSO BENEFIT FROM ITS CO-LOCATION WITH THE INDUSTRY’S HOTTEST CYBERSECURITY EVENT: INTERNATIONAL CYBER EXPO. EXPANDING INTO THE NATIONAL HALL AT OLYMPIA LONDON THIS YEAR, IT WILL DISRUPT THE STATUS QUO AS A DYNAMIC AND INCLUSIVE ANNUAL EVENT WHERE BUSINESS, INNOVATION AND EDUCATION CONVERGE
of the industry’s leading brands making it the best place to meet innovative suppliers who can solve all your security needs. Whilst the added value that comes from having full access to co-located International Cyber Expo, allows you to see the full security picture. We really hope to see you at Olympia London this year on 26-27 September.” L
THREAT DETECTION FROM CEIA
CEIA (Company for Electronic Industrial Automation) was founded in 1962 in Italy when it began production of metal detectors for the textile industry, since then our product line has grown covering many sectors from military and security to pharmaceutical and food. Within the security industry, CEIA provide a range of sophisticated technologies designed for the detection of threats including explosives, IEDs, weapons and radioactive materials. CEIA holds more than fifty national and international patents. The manufacturing site is in Italy with offices in the UK, Europe and the US.

CEIA systems are installed in more than 80 per cent of airports worldwide and

over 95 per cent in the UK including Heathrow and Gatwick. Currently around 20 per cent of CEIA S.p.A staff are engaged in research and development, in activities to meet new legislative changes and changing threats. Sectors we cover include: Aviation Transportation; Cargo Screening; Law Enforcement; Court and Prisons; Event Security; Loss Prevention; and Arena Security.
Some of our latest technologies available to see on our stand are: SAMDEX Shoe Scanner, for the screening of passengers’ shoes; OPENGATE for the automatic screening of individuals including their backpacks and bags; and EMA-4 LEDS System, designed to check sealed and unsealed liquid containers carried by passengers. L
FURTHER INFORMATION
For more information and to register to attend this year’s International Security Expo and International Cyber Expo for free, please visit: https://www. internationalsecurityexpo.com/ctb
SURVEILLANCE AND MONITORING SPECIALIST
Inspectahire are the UK’s leading visual surveillance, scanning and monitoring specialists. We have led the way in providing the latest and most effective technologies to the security industry, governments and critical infrastructure for over 35 years. Whether you are looking for the latest surveillance technology or need the most effective and easily deployed security scanning devices, Inspectahire will have a solution to most effectively support your needs or assignment. Our backscatter X-ray devices detect radiation that reflects from the target. They have potential applications where less-destructive examination is required and can operate if only one side of the target is available for examination. These devices scan peoples’ bags by creating a detailed outline similar to a chalk drawing or an extremely detailed X-ray
image. Inspectahire are the UK Distributor for the worldleading Videray Handheld Backscatter X-Ray Imagers and associated technologies. The latest revolutionary technology to hit the market is the Videray PX Ultra. As the industry’s first 160 KeV X-ray source enabling users to see through 10mm of steel, this is the most powerful and user-friendly handheld X-ray imager. The handheld scanners enable a more customised scanning solution that metal detectors and older fixed X-ray machines cannot detect, such as plastic explosives, drugs or non-metallic weapons made of ceramic. L

FURTHER INFORMATION www.ceia.co.uk
FURTHER INFORMATION www.inspectahire.com 43 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
INTERNATIONAL SECURITY EXPO







44 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55 CLICK HERE TO CONTACT US NOW BY EMAIL SAVE TIME AND MONEY WHILST GAINING GREATER EFFICIENCIES AND SECURITY. SUITABLE FOR CRITICAL INFRASTRUCTURE PROTECTION ONE KEY FOR ALL Y OUR L OCKS DOORS | CABINETS | SENSITIVE E QUIPMENT | IT FACILITIES | MOBILE ASSET S www.sellox.co.uk www.cyberlock.com
SECURING CRITICAL ASSETS
The CyberLock solution has been designed to increase security, accountability, and key control within critical infrastructure sites – even when access points are located in remote areas with no possibility of providing power.
WHAT MAKES CYBERLOCK SO SPECIAL?
From its introduction nearly twenty years ago, the fundamental features have been proven in significant installations around the globe, including within governments, embassies, utilities, telecoms, hospitals, defence, offices and schools.
CyberLock provides complete control over who has been issued a CyberKey, when the key can be used and what locks may be opened (with any date or timebased restrictions). It is made possible by powerful but intuitive management software – and the infrastructure to manage controlled access reliably.
What are the main components?
CYBERKEYS

CyberKeys are smart. They are programmed with personalised access permissions for each user, allowing a single key to open multiple locks while still allowing immediate and precise control over who has access to locks and at what time. Each key is unique. The User validates possession when the activity history is collected, and any new permissions to locks may be granted or modified. Some User keys can be remotely updated with the flexibility and reach of a mobile phone. CyberKeys provide all the power to the lock cylinder, removing the need for expensive hardwiring or cables.
CYBERLOCKS
CyberLocks are also smart. Each is designed to retrofit existing lock hardware without wiring or batteries. There are over 400 styles of CyberLock, each designed to match the mechanical lock they need to replace. This may be on doors, cabinets, server racks, switches, elevators, safes and padlocks or mobile assets such as briefcases, toolboxes, transport vehicles, etc. Wherever these locks are located, smart access control may be exercised. Each CyberLock is unique. Unlike mechanical locks, CyberLocks have a
unique, sealed design that resists forced rotation and are made to remain in the locked position if tampered with. These cylinders can even be programmed to deny access in the case of a lost key.
UPDATE FACILITIES
CyberLock offers a unique range of update facilities to meet critical infrastructure needs. This has proven to be essential in some parts of the world where the constancy of infrastructure cannot be taken for granted.
CyberKeys may be updated by authorised PCs, stand-alone stations, mobile phones, keypads, and infrared readers. CyberKeys may also be issued as needed from autovend vaults that can also handle the secure release of mechanical Keys.
THE MANAGEMENT SOFTWARE
The powerful features within CyberKeys, CyberLocks and the Update Facilities are combined in the powerful and intuitive management software, CAW (Cyber Audit Web). This allows the permissions in CyberKeys to be derived from in-house systems (such as Service Now or maybe a Permit to Work system) or be managed using the powerful features within CAW. These include the full mapping of infrastructure and a range of Reports and Notifications to meet the needs of management.
The software goes much further than the management of keys and locks. It can also handle doors fully wired with access by card, fob, or mobile phone –and keyless access to padlocks and key safes. It is designed to meet the needs of global, national, and local businesses.
SOME EXAMPLES OF USE
Airports are under increasing pressure to protect physical assets and electronically control and track anyone that accesses their facilities. The logistics involved in managing multiple points of entry and the thousands of keys in circulation present daunting
challenges for airport administrators. With CyberLock electronic locks and programmable keys, security managers can quickly and affordably increase perimeter security, audit access events, and prevent unauthorised entry without hard wiring.
Power and water companies require a highly efficient and cost-effective method of implementing and maintaining an access control system, regardless of how or where the locks are dispersed. CyberLocks and CyberKeys are programmable and can store critical information about their use and access privileges for employees and contractors. This provides administrators with flexibility while maintaining security. The CyberLock access control solution has been designed to increase security, accountability, and key control in critical infrastructure sites.
Transportation of valuable or sensitive goods from despatch to receipt may require ensuring that no tampering has occurred and that the shipment’s integrity is assured. CyberLock smart keys and cylinders protect against the threat of traditional key duplication because the cylinder and key are electronically bonded through unique access codes. The courier may carry a key that does not work – unless remote authorisation is granted. In some situations, this may require two authorised keys to be present (or three or four). CyberLock has the flexibility to meet these needs.
THE BENEFITS
Virtually every organisation may benefit from improved access control, but the benefits are tangible and immediate for some. If you need to improve the management of access across your organisation, we would like to hear from you. L
ADVERTISEMENT FEATURE FEATURE FURTHER INFORMATION www.sellox.co.uk 45 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE
When critical assets are at stake, controlling and tracking each access is no small task when dozens or even hundreds of keys and locks are dispersed over a vast territory, including different continents
Anti-terror and crisis management is the focus for the 23rd edition
MILIPOL PARIS 2023
Organisers of Milipol Paris, the world’s leading homeland security and safety event, are looking forward to welcoming visitors to the 23rd edition of the bi-annual show, taking place in Paris from 14-17 November at the Paris-Nord Villepinte Exhibition Centre.

This year, 30,000 visitors are expected to attend the trade show, which will feature more than 800 exhibitors from a range of sectors. The four days of the show will be packed with content, including talks and discussions featuring internationallyrenowned experts tackling the key issues facing the security market today.
At 2021’s edition, more than 1,000 exhibitors were in attendance, 65 per cent of which were international, and there were more than 30,000 visitors from more than 150 countries, as well as 150 official delegations. In addition, more than 220 journalists covered the event.
Milipol Paris is a focal point for the latest innovations and the place where the future of the industry is defined. As a platform for business, innovation and discussion, the event will fully meet visitors’ needs, as is evidenced by the fact that 90 per cent of the 2021 attendees declared their intention to go to Milipol Paris 2023.
French minister of the interior, Gérald Darmanin, along with several international ministers of the interior, will be present for the opening ceremony.
The Milipol Innovation Awards will be back again, once again recognising the most innovative companies in the homeland security industry. There will also be exhibitor seminars and live demonstrations as well as pitches delivered on the Innovation & Research Stage. Finally, there will be specific exhibiting areas including First-Time Exhibitor Village, Forensics Zone, Start-up Area, etc.

TOPICS IN FOCUS
The show will cover various topics and issues including law enforcement, urban security, systems integration, antiterrorism - special forces, data protection and communication systems, private security, civil security and cybersecurity and how to tackle modern cyber threats.
LAW ENFORCEMENT
This is one of the most dynamic sectors at Milipol Paris. During the 2021 edition, 304 exhibitors and over 1,700 visitors were involved in this business field, and Milipol organisers hope to make those numbers even better this year. The show will take an international look at the different approaches to policing, delving into the different tactics employed to deal with crowds and violence as well as civil disobedience. It will explore the different tools and innovations available and will explore the question of how the right balance can be struck between civil order and allowing the population their civil liberties and right to protest. Exhibitors from this sector for 2023 will include: Invisio, Kaama, Kermel, Korea CNO Tech, Landguard Systems and more.
URBAN SECURITY
The security of public places and urban security are just as topical as ever, and Milipol Paris 2021 saw 97 exhibitors and over 1,200 visitors from this sector. Again, this issue is nuanced and involves utilising the latest technology to strike the right balance between civic security and energy concerns (regarding street lighting etc.) and people’s civil liberties (the right to not be surveilled). Also, in the current global context of multiple crises, urban, and population safety extends to the prevention of risks like natural disasters (floods, storms, etc.). Here again, platforms play a key role.
MILIPOL 46 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55
They are a real asset for operators in charge of crisis management on the scale of a city, region or country.
Aclima AS, Allwan Security, Atos France, Batisec, Bertin Technologies, Cognyte and many more, will be among the exhibitors in this sector.
SYSTEMS INTEGRATION
At Milipol Paris 2023, visitors will be able to discover the business sector of systems integration, which involves building, connecting and maintaining several disparate systems and tools within a single larger information system. In 2021, 67 exhibitors and over 1,175 visitors were present in this sector. Products in this field include transmission, communication and positioning solutions such as transmitters/receivers, satellite communication systems, connectors, geographic information systems (GIS) and tracking equipment, integrated systems and control rooms for video surveillance, data/image processing and analysis software, information system security, operating systems, rugged computers, onboard communication systems and specific warning systems, weather and seismic monitoring systems and telecommunication networks for deployment in crisis zones.
Exhibitors will include Aerotec & Concept, Cegelec Defense, CP France, Elecdan, Idemia, Thales and more.
DATA PROTECTION - INFORMATION AND COMMUNICATION SYSTEMS
As new regulations related to data privacy will be implemented with the disappearance of third-party cookies, data protection remains one of the major sectors of Milipol Paris.
At the 2021 Milipol show, over 70 exhibitors and 1,000 visitors from this sector were in attendance.
From GDPR and the ePrivacy Directive and Open Data and the DMA (Digital Market Act) through to the DSA (Digital Services Act), the DGA (Data Governance Act) and the DA (Data Act), data protection can be a minefield for companies. But, since 2019, the European Commission has been developing its strategy to create a digital data market that facilitates innovation while strengthening user protection. Once more, it’s all about
balance – this time between personal privacy and useful data sharing.
Advantage Austria, Airbus, Bretagne, Crosscall, Dust Mobile and more key exhibitors have already confirmed their attendance in this segment.
PERSONAL SECURITY
Private security has emerged as a specific business sector of Milipol Paris for the last few editions of the event. With 58 exhibitors and almost 1,000 visitors in 2021, the sector confirmed its growing importance for the show. Large events such as football matches and the Olympic games, as well as large-scale arena concerts, present challenges when it comes to security. Most of these events are manned by private security firms but in some places, the lines between private and state security and policing can be blurred. For example, the U.S., South Africa and Asia have a more highly developed private security sector than a public one. India has 7 million private security guards but only 1.4 million police officers, making it the country with the largest differential in the world. In the U.S., there are 1.1 million private security employees compared to 666,000 police officers. In France, it is the opposite: there are almost 40 per cent more police and gendarmerie officers than private security guards. At the show we will address some of the issues and concerns around private security.
Exhibitors will include AMG Pro, Anorak, Autoclear, DCA France, Icom France – Sorrac and more.
CIVIL DEFENCE
Civil defence encompasses all the means implemented by a state to protect its citizens from natural and man-made risks, or risks related to war. During the 2021 edition, 137 exhibitors and over 800 visitors were involved in this business field.
At Milipol Paris 2021, 20 per cent of the exhibitors selected “civil defence” as a targeted business sector for visitors. The sector was also represented in several categories of the Milipol Innovation Awards, such as individual equipment and crisis management.
Exhibitors for this sector will include ACS, Airbus, Alsetex, Carma MC, Concordia Textiles and more.
CYBERSECURITY
The fight against cyberthreats and cybercrime comes together with two other business sectors covered at Milipol Paris: data protection and systems integration. At Milipol Paris 2021, 35 exhibitors and 300 visitors from this sector were in attendance.

ANTI-TERRORISM –SPECIAL FORCES
Since the attacks of 11 September 2001, which marked the beginning of the “war on terrorism”, the whole planet has been affected by terrorist modes of action. How can we win this asymmetrical war, which has been disrupting the international community for so many years? This is one of the questions that will be addressed at this year’s show. In 2021, 229 exhibitors and 1,100 visitors were involved in this field. At Milipol Paris, visitors will be able to see key innovations designed to help tackle terrorism, including some of the latest UAVs, such as a drone called the “Black Hornet”, which is 10 cm long, weighs 20g, has an autonomy of 25 minutes and can travel at up to 18 kph. France has invested €77 million in this technology.
AP Flyer – Maddos, Area, AT Security, ATS Group and Berghaus will all be in attendance, along with many more.
WHY VISIT MILIPOL?
The established reputation and international media coverage given to the event make Milipol Paris the best place for promoting brands in the homeland security sector and presenting the latest innovative solutions to buyers in the industry as well as official delegations attending the event. 84 per cent of exhibitors were satisfied by the opportunity the event provided to present new products and services (source: visitor survey 2021). It is also the place to discover the latest trends within an evergrowing sector and debate the next developments in order to take up the challenge. L
INFORMATION https://en.milipol.com/ 47 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE MILIPOL
FURTHER
COGNITEC SYSTEMS
+49-351-862-9200
sales-emea@cognitec.com

www.cognitec.com
Reduce search times for suspects in video footage from days, hours . . . to minutes! Cognitec’s face recognition technology imports still images and video material, finds all faces, and clusters the appearances of the same person, even across multiple media files.
SELLOX LIMITED
+44 (0) 1273 741528
sales@sellox.co.uk
sellox.co.uk
The problems of too many keys are well known. Keys get copied, lost, or duplicated. They represent a real threat if controlled access to sensitive assets or equipment is essential. There is a better way to take control – without the complications of wiring or batteries. It is called CyberLock.
SAFELOCKING

0161 627 7947
sales@safelocking.co.uk
www.safelocking.co.uk
No wiring, batteries, or keys. iLOQ is the modern way to monitor, manage and control access on your site. Eliminating the need for physical keys and battery-powered lock cylinders, iLOQ is the answer to sustainable access management with energy-harvesting technology using only a smartphone. Click here to learn more

48 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55 PRODUCT FINDERS FACIAL RECOGNITION INTERNATIONAL SECURITY EXPO INTERNATIONAL SECURITY EXPO

















We are a dynamic SME providing turnkey physical and electronic security solutions. We work extensively in Utility and Infrastructure markets providing an unbiased best in class solution. We have extensive industry experience working on some of the highest profile and time critical projects in the UK. VAYLIA LIMITED 0203 059 4560 chris.plimley@vaylia.com www.vaylia.com VISIT OUR WEBSITE TO SIGN UP FOR YOUR FREE DIGITAL SUBSCRIPTION 020 8532 0055 www.psi-media.co.uk BETT PREVIEW Business Information for Education Decision Makers www.educationbusinessuk.net ISSUE 28.1 PAYROLL TRIPS TECHNOLOGY THAT MAKES A DIFFERENCE IT & COMPUTING How can schools ensure their IT provision is inclusive, effective and tackles digital inequality? PLUS: CYBER SECURITY DESIGN & BUILD FIRE SAFETY WATER MANAGEMENT TRAINING ISSUE 22.6 www.healthbusinessuk.net PLUS: FIRE SAFETY MEDICAL EQUIPMENT VOLUNTEERING CYBERSECURITY DIGITAL TRANSFORMATION RECRUITMENT How to prepare for and deal with the cold weather FACILITIES MANAGEMENT IN WINTER FACILITIES MANAGEMENT CONFERENCE & EVENTS ENERGY DIGITAL TRANSFORMATION PLUS: FACILITIES MANAGEMENT ROAD MAINTENANCE DRAINAGE FIRE SAFETY GREEN SPACES THE BENEFITS OF NATURE How can a green city have a positive impact on its residents? www.governmentbusiness.co.uk ISSUE 29.6 GROUNDSCARE PARKS MAINTENANCE How can parks be maintained in the face of funding pressures? Business Information for Local and Central Government 49 ISSUE 55 | COUNTER TERROR BUSINESS MAGAZINE PRODUCT FINDERS IF YOU LIKE COUNTER TERROR BUSINESS YOU MAY ENJOY SOME OF OUR OTHER TITLES:










50 COUNTER TERROR BUSINESS MAGAZINE | ISSUE 55 The publishers accept no responsibility for errors or omissions in this free service ADVERTISERS INDEX Allied Telesis International B.V. 16 Asset & Frontline Security Services 28 Bailey Street Furniture Group IBC CEIA 26, 34, 43 Cognitec Systems GmbH 4, 48 Crowdguard 12 Durabook 10 Environmental Street Furniture 18 F-24 UK 40 Frequentis 32 Frontier Pitts 6 Inspectahire Instruments Company 36, 43 Jacksons Fencing 24 Lista UK 8 Lochrin Bain 15 Optex (Europe) 38 Sellox 44, 48 Stafford Bridge 40, 48 Streamlight BC Todd Research 20 Vaylia IFC, 49 Zinc Digital Business Solutions 30 PROTECTING PALS : HVM & PERIMETER SECURITY 1ST AUGUST 2023 LIVE ONLINE SPONSORED BY: IN ASSOCIATION WITH: CLICK HERE TO REGISTER GET THE INSIDE TRACK FROM INDUSTRY EXPERTS 365.counterterrorbusiness.com
OPEN UP PUBLIC SPACES
A COMPLETE SUITE OF IMPACT TESTED STREET FURNITURE TO IWA 14-1 STANDARDS
• SEATING, CYCLE PARKING, WASTE DISPOSAL, PLANTING & MORE

• DESIGNED TO STOP 2.5 TONNE VEHICLE TRAVELING AT 30 MPH IN ITS TRACKS
• SHALLOW-MOUNTED TO MAXIMISE VERSATILITY
• FLEXIBLE DESIGN POSSIBILITIES WITH MODULAR & INTERCHANGEABLE OPTIONS

• ENHANCES LOOK AND FEEL WHILST BRINGING BIODIVERSITY TO URBAN LANDSCAPES
• BLENDS IN SEAMLESSLY WITH STANDARD STREET FURNITURE PACKAGES FROM BSFG bsfg.co.uk 01625 322 888
Offering security & protection to pedestrians and urban infrastructure while enhancing the aesthetic value of the space.






 TLR–7® sub
TLR® RM 1
TLR–8® G sub
TLR® RM 1 LASER. 500 LUMENS & 140m BEAM.
TLR–7® sub
TLR® RM 1
TLR–8® G sub
TLR® RM 1 LASER. 500 LUMENS & 140m BEAM.
WEAPON LIGHTS TACTICAL TOUGH, VERSATILE, DURABLE AND RELIABLE Made for situations when failure is not worth contemplating, Streamlight® has created the broadest range of professional torches and lighting tools that can be trusted for a lifetime. streamlight.com
TLR-7® SUB FEATURING AMBIDEXTROUS SWITCH

























 Polly Jones, editor
Polly Jones, editor


























































































































































































 TLR–7® sub
TLR® RM 1
TLR–8® G sub
TLR® RM 1 LASER. 500 LUMENS & 140m BEAM.
TLR–7® sub
TLR® RM 1
TLR–8® G sub
TLR® RM 1 LASER. 500 LUMENS & 140m BEAM.











