THE RECORDS SIDE OF CYBER SECURITY EVALUATING THE TONE OF IG POLICIES
ARTIFICIAL INTELLIGENCE: THE NEXT FRONTIER FOR IG EXPERTS


Thank you to our 2024 Major Partner iQ ADVANCING AND CONNECTING THE RECORDS AND INFORMATION MANAGEMENT PROFESSION EXPLORING
TAPESTRY OF RIMPA's Communities of Practice THE RIMPA GLOBAL QUARTERLY MAGAZINE CAPTURING RECORDS AND INFORMATION MANAGEMENT NEWS SINCE 1984 VOL 40 / ISSUE 2 / JUNE 2024 Cybersecurity in the Digital Age
FEATURE:
THE RICH
SPECIAL
99% data extraction accuracy

Exedee was founded on our passionate recognition of the value and importance of every organisation’s information and how it contributes significantly to the effective and efficient running of each organisation. This passion led us to enthusiastically become the RIMPA Global 2024 Diamond Sponsor.
Our track record includes achieving market-leading 99% accuracy in data extraction and digitisation. Through our Diamond sponsorship, we will ensure that this, and our deep experience integrating the power of Artificial Intelligence into our innovative, automated business processing and Information Management software will provide many benefits to RIMPA members in the dynamic, ever-changing records and information landscape.
Exedee is looking forward to engaging with RIMPA members this year, to work together and enable improvements in your business processing and information management systems and processes. Our plans for the RIMPA 2024 Diamond Sponsorship engagement include:
Regular communications to RIMPA members through newsletters and eDMs
Networking and sharing our extensive experience and knowledge of the use of Artificial Intelligence in the areas of records and information management
Relevant webinars for RIMPA members to join and expand their knowledge
Scheduling workshop sessions that can show you how our software can help improve and streamline your work processes, so that you enjoy your work more!
Encouraging the use of “pilot projects” to RIMPA members to trial the use of AI driven software to help achieve excellent records and information management results.
Talk to the team of Exedee experts today, or visit our website at www.exedee.com
INDUSTRY NEWS 2 | iQ June 2024
2024 RIMPA Global Diamond
Exedee is excited and enthusiastic about our
Sponsorship!
EDITOR: Jo Kane
Chief Operating Officer
Email: editor.iq@rimpa.com.au
Post: Editor, iQ Magazine
1/43 Township Drive
Burleigh Waters Qld 4220
DESIGN: Amanda Hargreaves
Ole Creative - Graphic Design Agency
Web: www.olecreative.com.au
Email: amanda@olecreative.com.au
Stock images: Shutterstock
ADVERTISING
Jo Kane
jo.kane@rimpa.com.au
EDITORIAL COMMITTEE
Stephanie Ciempka (ACT)
Jo Kane (QLD)
Matt O’Mara (NZ)
David Pryde (NZ)
Philip Taylor (QLD)
Roger Buhlert (VIC)
CONTRIBUTIONS & EDITORIAL ENQUIRIES
Articles, reports, reviews, news releases, Letters to the Editor, and content suggestions are welcomed by the Editor, whose contact details are above.
COPYRIGHT & REPRODUCTION OF MATERIAL
Copyright in articles contained in iQ is vested in their authors. Most editorial material which appears in iQ may be reproduced in other publications with permission gained through iQ’s Editor.
ANNUAL SUBSCRIPTIONS
iQ HARDCOPY ANNUAL SUBSCRIPTION
$120.00 incl GST ($) per annum for 4 issues (excluding international postage).
iQ DIGITAL ANNUAL SUBSCRIPTION
$49.50 incl GST ($) per annum for 4 issues
RIMPA Global | Phone: 1800 242 611 International Phone: +61 7 32102171 To subscribe head to www.rimpa.com.au
iQ ONLINE ARCHIVE
Copies of articles published in iQ since 1984 are available at the Members Only section of the RIMPA Global website, in the iQ Article Archive. The Members Only section of the website can be accessed with RIMPA membership.
DISCLAIMERS
Acceptance of contributions and advertisements including inserts does not imply endorsement by RIMPA or the publishers. Unless otherwise stated, views and opinions expressed in iQ are those of individual contributors, and are not the views or opinions of the Editor or RIMPA. www.rimpa.com.au

























iQ | 3 Official Journal of Records and Information Management Practitioners Alliance - Global VOLUME 40 / ISSUE 2 / JUNE 2024 CONTENTS 30 44 RIMPA GLOBAL RIMPA QUARTERLY MAGAZINE 24 VIEW FROM THE CEO Anne Cornish, Life MRIM 4 MEMBER UPDATE Exploring the Rich Tapestry of RIMPA's Communities of Practice by Tynelle Spinner 5 Member Quarterly Update 6 INDUSTRY NEWS Public Records Office of Victoria (PROV) Update 7 Information Management Framework for Western Australian Government 8 RIMPA NEWS RIMPA Live 2024: Be the Navigator of Change. Be The Future of Information Management 12 Nominations Open for the Outstanding Achievements Award 39 LEADERSHIP & MANAGEMENT Understanding People and Bringing Out Their Best By Lindsay Adams OAM 14 SPECIAL FEATURE: CYBER SECURITY IN THE DIGITAL AGE The Records Side of Cyber Security By Xander Hunter ARIM 16 Professionalising Cybersecurity Professionals: Why It Needs To Happen By Tony Vizza 20 Cybersecurity in the Digital Age by Linda Shave, Life FRIM 24 INFORMATION MANAGEMENT A Case Study: Applying Information Security Classification By Uta Fox, MA, CRM, FAI 30 Records, Trust (And Lack Thereof) By Stephen Bedford 40 INFORMATION GOVERNANCE Evaluating the Tone of IG Policies By Lewis Eisen 43 Cultivating Ethical Governance Through Records Management: A Case Study By Jim Meyers 36 ARTIFICIAL INTELLIGENCE The Next Frontier for Information Governance Experts By Jim Merrifield, IGP, CIGO 42 What Can Artificial Intelligence Do for Content Management? By Gwendoline Huret 44 RIMPA Global Resources 49 Ability Works Partnership 50 Vendor Directory 52
iQ
 ANNE CORNISH LIFE MRIM CEO RIMPA GLOBAL
ANNE CORNISH LIFE MRIM CEO RIMPA GLOBAL
VIEW FROM THE CEO
It is now June, and we are all trying to work out where the first 6 months of the year have gone and we know Christmas will be here sooner than we know. But, not as soon as RIMPA Live.
September 3rd – 5th will see a congregation of information management practitioners, professionals, specialists and interested parties hit Adelaide SA to attend, present and network at what is considered the “must attend” event each year for information management – RIMPA LIVE.
If you haven’t already registered, you still have until the end of June to receive your member only early bird discount. Don’t miss out as your attendance is integral to your very own professional development, keeping up to date with new trends and meeting new people who also speak the language of information management.
I mentioned that the first six months of 2024 have gone quickly but that is not to say that RIMPA hasn’t been busy achieving results.
2024 has seen further enhancements in services and extending our global reach to achieve the bigger voice we have all been dreaming of. Members will soon see a transformation in educational delivery with the imminent implementation of RIMPA’s learning management system (LMS).
Members will be able to learn using selfpaced and on demand options providing further accessibility and opportunities for all members no matter what they do for a job or the time zone they live in.
RIMPA members have also been proudly represented at the newly formed Global Information Consortium in recent months with attendance at the inaugural GIC Global Council Strategy meeting in Palm Springs and a presentation to ISO TC46 SC/11 representatives in Berlin to over 60 countries on the value of working with the GIC. Bringing international IM bodies together to provide a bigger voice is a prime objective of the GIC.
RIMPA has also expanded their membership base with a pilot community of practice (CoP) commencing in India.
The Board required a minimum of 40 expressions of interest before they would consider supporting a CoP overseas and as you can imagine with the population in India at 1 billion plus, this figure was easily met and the formation commenced. The pilot provides RIMPA the opportunity to determine the resource requirements to support overseas CoP’s and provides us with a great sense of humanity and community by supporting an industry in another country that doesn’t have the luxury of a RIMPA in their own backyard. We hope you are able to meet some of CoP India members at RIMPA Live.
2024 has seen further enhancements in services and extending our global reach to achieve the bigger voice we have all been dreaming of.
The Roadshow series which is near completion has been a major success focusing on local and national trending topics. The theme of the year is “I’M the Next Wave” and the content at these events as well as what you will see at RIMPA Live easily fits the mark. The value of information assets, PII, data and records and of course the impact of AI are topics being discussed around the world and RIMPA lead the way in involving their members in how to solve the challenges associated with each new trend.
The next 6 months will also be busy and as a member you can expect more benefits for your membership dollars.
Have a great second half of the year and see you all at RIMPA Live 3rd – 5th September 2024.
Anne Cornish Life MRIM
4 | iQ June 2024
VIEW FROM THE CEO
Exploring the Rich Tapestry of RIMPA's Communities of Practice
In the dynamic world of records and information management, continuous learning and collaboration are key to professional growth and success. Recognising this, RIMPA offers several vibrant Communities of Practice (CoPs) that provide a ground for networking, knowledge sharing, and collective problem-solving. Whether you are looking to deepen your expertise, share your experiences, or explore innovative solutions, RIMPA's CoPs are designed to support your professional journey.
WHAT IS A COMMUNITY OF PRACTICE?
A Community of Practice is a collective of individuals united by a shared interest or profession. Members of a CoP come together to achieve both personal and communal goals through the exchange of knowledge, experiences, and tools. This collaborative environment not only fosters innovation and continuous learning but also enhances the individual growth of its members alongside the collective wisdom of the group.
Regular, creative interactions, whether faceto-face or online, are the backbone of these communities, making them a cornerstone for continuous improvement and shared success.
RIMPA'S
COMMUNITIES OF PRACTICE
TropiCoP (North Queensland)
TropiCoP serves as a vital community for records and information management professionals in North Queensland. Originating in Townsville, it has grown to include members from Mackay in the south to the Wujal Wujal region in the north. TropiCoP was founded on the recognition of the unique challenges faced by professionals in less urban areas, particularly in accessing training and networking opportunities. The community is dedicated to providing support, facilitating the exchange of expertise, and fostering connections among peers with similar interests.
VLGCoP
– Victorian Local Government
Focused on the specific needs and challenges of information management within Victorian local governments, this CoP helps professionals share best practices, legislative updates, and technological advancements pertinent to their roles in public service.
India
CoP
This newly formed community unites professionals from across India, offering a platform to explore both local challenges and global trends in records management. RIMPA has just launched this initiative, and we are eagerly anticipating the opportunities and developments that lie ahead in this space.
Joining a RIMPA CoP can significantly impact your professional development and career trajectory. Here’s how:
• Networking Opportunities: Connect with peers and industry leaders who can provide support, guidance, and opportunities to collaborate on projects or initiatives.
• Knowledge Sharing: Gain access to a wealth of information and experiences shared by community members, helping you stay updated with the latest trends and best practices.
• Skill Enhancement: Participate in workshops, seminars, and other learning opportunities that can help you acquire new skills and refine existing ones.
Innovation and Problem Solving: Work together with other professionals to devise solutions to common challenges, driving innovation in your field.
RIMPA's Communities of Practice are more than just groups; they are incubators for professional growth and innovation. Whether you are in North Queensland, India, or Victoria, there is a CoP waiting to welcome you. Join us today and be part of a thriving network committed to excellence and mutual success in the field of records and information management.
Interested in Starting Your Own CoP?
If you're inspired to start a new Community of Practice, reach out to us at admin@rimpa.com.au, and we will guide you through the process.
Starting a CoP can be a rewarding way to meet like-minded professionals and make a real impact in your field.
iQ | 5
NEWS MEMBER UPDATE
RIMPA GLOBAL: MEMBERSHIP
WHY JOIN A RIMPA CoP?
Member Quarterly Update
This quarter has been exceptionally busy and productive for our community. We're thrilled to welcome 38 new members who have joined us.
Additionally, we congratulate our recent professional upgrades:
• James Price to Associate
• Sharon Ipsen to Associate
• Stephen Clarke to Chartered SCHOLARSHIP PROGRAM SUCCESS
Our 2024 Scholarship Program has successfully closed, and we extend our thanks to all applicants for their hard work and dedication. A big congratulations to the following recipients:
• Matt O'Mara FRIM, Director i3 Ltd | Information | Imagination | Insights - Neil Granland International Convention Scholarship. Matt will be travelling to Houston, USA, to attend ARMA International’s InfoCon 2024.
• Toni-Lee Taylor, Information Management Advisor from Tas Networks, awarded the Marita Keenan RIMPA Live Scholarship. Toni-Lee will be travelling to Adelaide in September for RIMPA Live 2024.
• Kylie Greenhalgh, Project Officer Information Management from Murraylands and Riverland Landscape, awarded the Harry Haxton Certificate III in Business (R/IM) Scholarship. Kylie will begin their studies with the July intake.
• Mary Preston, System Governance Advisor and Privacy Officer from Tasmanian Catholic Education Office, awarded the Lisa McDonough Roadshow Scholarship.
CELEBRATING OUR TOP ONLINE CONTRIBUTOR: DR BETHANY SINCLAIR-GIARDINI MRIM
In every community, there are those who stand out by their enthusiasm and commitment, and it's time to shine a spotlight on one such remarkable individual in our RIMPA Community online forum—Bethany Sinclair-Giardini MRIM. This past quarter, Bethany has continued to reach new heights, emerging as our highest achiever in member engagement.
Not only has she initiated numerous fresh posts, but her contributions to ongoing threads have kept many of our discussions lively and informative. While there are too many threads to mention individually, some notable ones include:
• Personalisation and Records Management Obligations
• EDRMS Options / Information on Google Drive
• Identity Verification Processes
• IM Practitioners - Skills Base
• Content Manager with a M365 Connector
Her ability to weave in relevant articles enhances the quality and depth of our conversations, while her private chats with other users demonstrate a personal commitment to supporting and growing our community.
Apart from her online engagement, Bethany serves as a RIMPA Global Ambassador and Mentor and holds the position of Principal Consultant | Votar Partners. Her professional expertise and dedication are well respected within our community, making her contributions all the more valuable.
We look forward to her continued involvement and the innovative ideas she brings to the table.
Thank you, Bethany, for your dedication and for setting such a high standard of engagement within our RIMPA Community! Head to the RIMPA Community here: community.rimpa.com.au/home
LOOKING AHEAD
We eagerly anticipate hearing about our scholarship recipients' journeys and experiences. Stay tuned for their updates and stories in the upcoming issues. Thank you for being an integral part of our dynamic and ever-evolving community.

MEMBER UPDATE Become a RIMPA Global Member today! Visit rimpa.com.au or email admin@rimpa.com.au RIMPA GLOBAL: MEMBERSHIP NEWS
6 | iQ June 2024
Update from Public Record Office Victoria
New Operational Management Standard
Earlier this year we released a new Operational Management Standard (PROS 24/01), replacing the previous version (PROS 19/04), and an Implementation Guideline.
The Standard sets out the principles and requirements that Victorian public offices must comply with to ensure effective records management operations, and is relevant to every Victorian Government agency. It covers system planning and procurement, system maintenance, system transition, processes, training and awareness and contracting.
New principles and requirements within the Standard include the obligations that:
• Arrangements for any system transitions must ensure that records are protected and remain accessible and usable for their minimum required retention period.
• All staff must be trained in how to apply the recordkeeping requirements of the public office, upon induction and periodically throughout their tenure.
• And contractors and volunteers must also be trained in how to apply any recordkeeping requirements which are necessary for the tasks they are performing for the public office.
Changes to wording throughout the Standard strengthen and clarify the principles and requirements while also ensuring actions are realistic for public offices to achieve.
Visit prov.vic.gov.au to learn more about the Operational Management Standard and Guideline.

• Highlighting the role of AI, machine learning, and automation.
• Showcasing innovative tools and platforms for information management.
• Interviews with pioneers in developing transformative technologies.
• Case studies on successful integration of new technologies.

INDUSTRY NEWS iQ | 7 Want to contribute to iQ? Refer to iQ’s submission guidelines Visit rimpa.com.au/news/iq/iq-article-submission Submit your story to: editor.iq@rimpa.com.au
12 JULY NEXT
Innovative
Reshaping Information
COPY DUE:
EDITION: SEPTEMBER 2024
Technologies
Management
Aerial view of the State Library of Victoria
Information Management Framework for Western Australian Government
BY STATE RECORDS OFFICE OF WESTERN AUSTRALIA
The State Records Office of Western Australia has published a new Information Management Framework for WA Government. The Framework can be accessed via the Western Australian Government website at Information Management Framework for WA Government - www.wa.gov.au
The Framework will help our public sector colleagues across all levels of government navigate the information management requirements of various legislation, regulations, policies and strategies to support decision-making, deliver government services, drive innovation and be accountable.
The Framework highlights the dependence of information management and technology on each other for success. Technology is a critical enabler for effective information management – for example, Information Communication and Technology (ICT) staff maintain systems that hold information and manage security and backups for business continuity and disaster recovery. Information management deals with the content of the systems - managing access, retention and disposal, identifying and protecting vital records, and providing advice, information and training to staff.
OUR
APPROACH TO DEVELOPING THE FRAMEWORK.
Rather than reinvent the wheel, we started with the foundations already established through similar frameworks in other jurisdictions.
The State Records Office formed an interagency working group under WA Government ICT governance arrangements and engaged with a wide range of people - both within and outside government - to inform and refine the Framework.
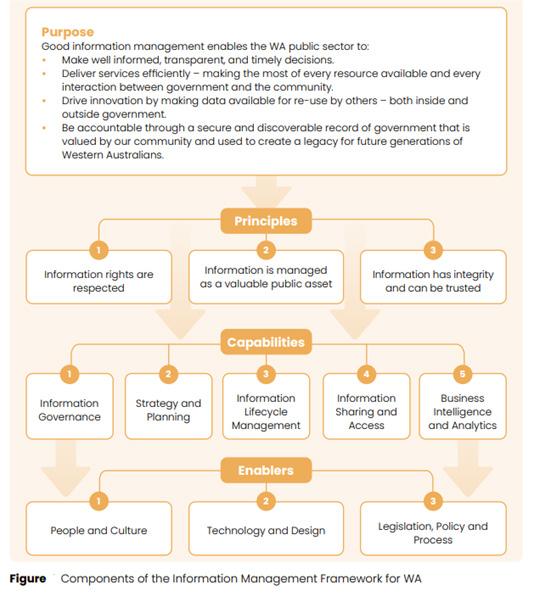
The group worked hard to keep the Framework very simple - resisting the temptation to add more principles where we could unify them. We used language that is meaningful to a wide audience, especially at executive level.
The Framework also leverages existing reporting and other compliance measures, rather than introducing new ones, so we have avoided adding to the compliance burden.
WHERE TO FROM HERE
The Framework is intended to be updated as needed over time, for example, as legislation and policies change, or as new requirements are developed.
The State Records Office facilitates communities of practice to help achieve this and will continue to engage with these experts and other groups locally and nationally to help make the Framework useful into the future.
INDUSTRY NEWS 8 | iQ June 2024
8
Strategies to Mitigate Cyber Security Incidents
There is no way to guarantee that your data is always going to be 100% safe from cyber threat, but there are acknowledged strategies that organisations can adopt to mitigate risk. The Australian Cyber Security Centre (ACSC) recommends organisations implement eight essential Strategies to Mitigate Cyber Security Incidents as a baseline making it harder for adversaries to compromise systems.
TIMG Australia has implemented the E8 Baseline across all services where we handle customer data. We are constantly updating and improving our processes and are now focused on rolling the standard out across all current back-office functions.
iQ | 9 INDUSTRY NEWS APPLICATION CONTROL 01 01 RESTRICT ADMINISTRATIVE PRIVILEGES 05 PATCH OPERATING SYSTEMS 06 MULTI-FACTOR AUTHENTICATION 07 REGULAR BACKUPS 08 PATCH APPLICATIONS 02 CONFIGURE MICROSOFT OFFICE MACRO SETTINGS 03 USER APPLICATION HARDENING 04 ESSENTIAL
Essential
Discover how TIMG can help your business. timg.com | sales@timg.com | 1800 464 360
RIMPA GLOBAL: BOOK REVIEW
FIFTH EDITION
Reference and Information Services: AN INTRODUCTION
Authors: Kay Ann Cassell, and Uma Hiremath
REVIEW BY ANDREW MCFADZEAN
Back to the Future: A New yet timehonoured trusted source
THE ESSENTIAL FEATURE OF THIS BOOK: FOUR-IN-ONE
Cassell and Hiremath have published a book for students, professional information managers and researchers that could be part of a set of professional “bibles.” These professional “bibles” are essential blends of basic descriptions of recordkeeping concepts, valuable lists of sources, catalogues of howto-guides and compact collections of resources created or used by reference librarians. These “bibles’ sit on the desks of reference librarians and information service managers reminding readers of much that was forgotten and is remembered about sources and ways of researching.

"These professional “bibles” are essential blends of basic descriptions of recordkeeping concepts, valuable lists of sources, catalogues of how-toguides and compact collections of resources created or used by reference librarians."
WHO ARE CASSELL AND HIREMATH?
Cassell is an academic-practitioner information manager who teaches a variety of courses, including references and information, services, collection development, public librarianship, and government information resources in the Department of Library and Information Science at Rutgers University. As a practicing professional Cassell was New York Public Library’s Associate Director of Collections and Services responsible for the development of the reference, collections, programs, and services for all the branches and initiated new programs and services.
Hiremath’s professional experience as a senior librarian covers a wide and diverse range of information management including Assistant Director of Public Services and Research at MacPhadin Library, Stonehill College, Massachusetts, Executive Director at the Ames Free Library, Massachusetts;

Assistant Director at the Thayer Public Library, Massachusetts and Supervising Librarian at the New York Public Library.
THE THEME
Cassell and Hiremath base their book on the assumption that “has consistently approached the reference transaction as an organic process. It is a process that requires contextual understanding of the text and subtext of a question, identifying best resources, and providing optimal answers in a format best suited to the information seeker (Cassell and Hiremath 2023, ix). Specifically, Cassell and Hiremath covered “an ongoing understanding of the fundamental concepts, essential resources, search techniques, communication platforms, and managerial tasks inherent to reference. In large part, these are underwritten by the wider social and educational patterns of information and research” (Cassell and Hiremath 2023, ix).
BOOK REVIEW 10 | iQ June 2024
THE SKILFUL BLENDING OF OLDER AND NEWER SOURCES
Cassell and Hiremath’s book should be seen as a blend of traditional, specific directories of diverse sources of information while referring to the braver world of Internet resources, WWW sources and access to social media platforms.
SUMMARY
OF KEY TAKEAWAYS:
Firstly, Cassell and Hiremath provide details of major sources ranging from basic search techniques, general reference books, magazines and newspapers, bibliographic networks, encyclopedias, dictionaries (many languages and specific subject), current events (geostrategic, geopolitical and national political almanacs) in databases or published indexes, legal, business studies, health, geographic information systems, maps, gazetteers and travel guides (including tourism), biographies and finally government documents, issues of governance and information databases covering administration (Cassell and Hiremath 2023, x-xii).
Secondly, Cassell and Hiremath’s special topics include “when and how to use the Internet as the primary reference tool, provides a succinct overview of the strengths and weaknesses of Internet reference. In an age of cyber security concerns, the chapter also includes a five-step guideline to using the Internet without falling easy prey to the ever-increasing reality of misinformation and fake facts” and “information literacy in the reference department, aims for clarity and understanding the dynamics of information, collection, organisation, and dispersal in different types of libraries. It provides an overview of the need for information literacy in reference department.” (Cassell and Hiremath 2023, xi)
Thirdly, in managing reference services, Cassell and Hiremath provide insights to staffing, defining the scope of services, identifying resources and guidelines for collection development (including cataloguing datasets). Cassell and Hiremath also cover the vexed issue of ethics (copyright, intellectual property rights, plagiarism, information security and access to information). Managing services includes the present and future of what Cassell and Hiremath call Reference 2.0 (Cassell and Hiremath 2023, xi-xii).
Cassell and Hiremath’s book should be seen as a blend of traditional, specific directories of diverse sources of information while referring to the braver world of Internet resources, WWW sources and access to social media platforms.
Fourthly, Cassell and Hiremath explore Reference 2.0 based on years of practice and observation. Cassell and Hiremath describe the four essential features of providing reference and information services through the Internet and the WWW. Reference librarians are working in an environment of creating answers through cooperation and collaboration. Cooperation is triggered and built across social media platforms and sites. The complex networks of the Internet allow information managers to rapidly reconfigure access to data and information sources and direct the results to clients, specifically and easily. The speed and diversity of the Internet allows data and information to be identified, harvested, curated and packaged as customised answers. This allows reference librarians to move from industriallogistical supply chains of data and information to finely-honed answers (Cassell and Hiremath 2023, 432)
Finally, Cassell and Hiremath reason five changes to refence and information services. Questions will evolve from the previously quicker, briefer ready-reference style to the more complex research issues. Reference librarians will focus on evaluating and selecting digital resources. Educating users in data and information literacy will occupy more time and resources, with exponential benefits for librarians and people seeking help. As noted in Reference 2.0 reference work will become collaborative based on networking which should produce more tailored, local results. Significantly, reference work supporting information services will become more interpersonal or as described by Kennedy as “high tech and high touch” (Cassell and Hiremath 2023, 461-465).
WOULD I RECOMMEND BUYING THIS BOOK?
Cassell and Hiremath’s book can be rated across three criteria: clarity, depth of research and practicality.
4/5 STARS OVERALL
4 out of 5 stars- **** Clarity: written as a business book, brief and to-the-point with enough context to make sense of the content but not waste the time of a reader. Remember, this is a survey of concepts not a detailed analysis.

5/5 stars - ***** Depth of research: extensively researched and anchored in numerous bibliographic references to substantiate their research and support their reasoning with evidence-based analysis.
4/5 stars - **** Practicality: written for working professionals as well as students of information management. The many examples of how-to guides and practical advice strengthen the value of this book as a reference.
RECOMMENDATION:
Worth its weight in gold for both students and long-time professionals. Students and practising reference librarians could buy and use this source for years, even through updated editions.
This book would make a significant contribution to a set of ‘professional bibles’ of sources and advice about reference-research skills covering American, British, European, Asian, Chinese and Pacific regions.
BOOK REVIEW
Be the Navigator of Change. Be the Future of Information Management.
JOIN US AND SURF THE NEXT WAVE INTO THE FUTURE OF IM.
From the 3rd to the 5th of September, the Adelaide Convention Centre will be the bustling hub for the Records and Information Management Practitioners Alliance (RIMPA) Live Convention.
Under the theme "I'M THE NEXT WAVE | LEADING THE FUTURE," this year's event promises to usher in the future of information management, equipping attendees to be navigators of change in an ever-evolving digital world.
The RIMPA Live Convention isn't just an event; it's a journey through the latest and most critical topics in the information management (IM) space. Whether you're looking to harness the power of artificial intelligence, navigate through the complexities of digital transformation, or master the standards of ISO30300, this convention has something to offer.
WHY ATTEND?
Access Unparalleled Expertise: Hear from leading domestic and international experts and keynote speakers as they share the most current insights and developments in the industry.
Interactive Learning Experiences: Participate in dynamic workshops led by top innovators. These sessions are designed to provide practical skills and knowledge that you can immediately apply to your work.
Explore Innovative Solutions: Discover the latest technologies designed to enhance your organisation’s growth and efficiency. See firsthand how these advancements can transform your operations.
Gain a Competitive Advantage: Stay at the forefront with critical updates, key statistics, and trends that will help you outpace the competition.
Expand Your Professional Circle: Network with industry leaders and influencers. Our events are crafted to facilitate new connections and collaborations that can lead to exciting opportunities.
Plus, so much more. See the full program via www.rimpa.com.au I'M THE NEXT WAVE LEADING THE FUTURE 3-5 September
Professional Development: Earn CPD points and collect valuable materials for ongoing education and reference.
Engage with Industry Leaders: Connect with key figures in the information management sector and participate in impactful discussions that could shape the future of the industry.
Celebrate and Connect: Enjoy the camaraderie of your peers at our Gala Awards Dinner and other social events, perfect for unwinding and strengthening professional bonds.
WHAT'S
ON THE AGENDA?
The three-day program is packed with sessions designed to tackle the hot topics of today and prepare you for the challenges of tomorrow. Highlights include:
Navigating the Digital Frontier: Explore the latest advancements and challenges in digital information management.
Harnessing AI for Superior Information and Records Management: Discover how artificial intelligence can transform the landscape of records management.
Information Governance: Delve into strategies for maintaining and improving the control of information, ensuring compliance and mitigating risks.
Leading with Agile Methodology: Learn how to implement agile practices in your management strategies to increase responsiveness and foster innovation.
Essentials for Communicating Change: Learn strategies to overcome disruption fatigue and effectively engage stakeholders in change initiatives.
Cybersecurity Incident Management: Gain insights into managing and mitigating risks in an increasingly vulnerable digital environment.
Harnessing Your Untapped Assets for Information Management in M365: Uncover the potential of Microsoft 365 in enhancing your information management practices.
Digital Transformation and Information Governance: Delve into the dynamics of digital transformation and its implications on governance.
12 | iQ June 2024 RIMPA NEWS
CENTRE
ANNUAL CONVENTION Records and Information Management Practitioners Alliance
ADELAIDE CONVENTION
39TH

MEET THE EXPERTS
This year, RIMPA Live is proud to feature a lineup of distinguished keynote speakers, including Andre Eikmeier, Dr. John Flackett and Dr. Neryl East, who will share their insights and experiences to inspire and guide you towards becoming a leader in information management.
VENUE AND ACCOMMODATIONS
Hosted at the state-of-the-art Adelaide Convention Centre, attendees will not only enjoy a world-class venue but also have a variety of accommodation options right at their doorstep. Special deals are available through the event's accommodation portal, offering something for every budget.
BE PART OF THE FUTURE
The RIMPA Live Convention is more than an opportunity to learn; it's a platform to network with peers, engage with industry leaders, and be part of a community driving the future of information management. Whether you are a seasoned professional or new to the field, this event is poised to spark inspiration, provoke thought, and empower you to lead in the IM domain.
Don't miss your chance to be the navigator of change at the RIMPA Live Convention. Register today and ready yourself to ride the next wave of information management innovation!





























iQ | 13 INFORMATION MANAGEMENT
RIMPA Live Exhibitors 2024 Keynotes Speakers
Andre Eikmeier
DIAMOND GOLD SILVER BRONZE PLATINUM MEMBER TYPE PRICE (INCLUDING GST) STUDENT (NO SOCIAL EVENTS) $500.00 RETIRED CERTIFIED $1,440.00 PROFESSIONAL (ARIM/MRIM/FRIM) $1,660.00 INDIVIDUAL/CORPORATE $1,860.00 ASA/ALIA/ARMA/ARANZ $1860.00 RIMPA ALLIED $2,060.00 NON MEMBER $2,560.00 Early Bird Prices Start From
Dr. Neryl East Dr. John Flackett
Industry Partners 2024
Understanding People and Bringing Out Their Best
BY LINDSAY ADAMS OAM

Understanding people is a cornerstone of effective leadership and interpersonal relationships. In the workplace, recognising and leveraging individual strengths is key to fostering a positive and productive environment. Behavioural analysis tools, such as the Enneagram, the Myers-Briggs Type Indicator (MBTI), and the DISC Model, offer valuable insights into the intricacies of human behaviour.
In this article, we will explore the benefits of understanding people and compare three prominent tools - the Enneagram, The Myer Briggs Type Indicator (MBTI), and the DISC Model - in order to make a compelling case for the latter as the most accessible and practical choice for enhancing workplace dynamics.
THE BENEFITS OF UNDERSTANDING PEOPLE
1. Enhanced Communication:
Understanding people allows for more effective communication. By recognising different communication styles, leaders can tailor their messages to resonate with individuals, minimizing misunderstandings and improving overall workplace communication.
2. Optimised Team Dynamics:
When team members understand each other's strengths and preferences, collaboration becomes more seamless. Leveraging diverse skills within a team enhances problem-solving and promotes a more inclusive and supportive work environment.
3. Increased Motivation:
Recognising what motivates individuals on a personal level enables leaders to tailor incentives and recognition. This targeted approach boosts morale, increases job satisfaction, and ultimately contributes to higher levels of productivity.
4. Conflict Resolution:
Understanding people's inherent differences helps navigate conflicts more effectively. Leaders equipped with insights into individual behavioural patterns can address conflicts proactively and find resolutions that align with the needs and preferences of those involved.
COMPARING SOME POPULAR BEHAVIOURAL ANALYSIS TOOLS
The Enneagram:
The Enneagram is a personality system that categorises individuals into nine distinct types, each characterised by a core motivation and worldview. While the Enneagram offers deep insights into personal motivations and fears, its complexity can be overwhelming for some. Additionally, its subjective nature relies heavily on selfreporting, which may lead to less reliable results.
The Myer Briggs Type Indicator (MBTI):
The MBTI classifies individuals into 16 personality types based on four dichotomies: extraversion/ introversion, sensing/intuition, thinking/feeling, and judging/perceiving. While widely used and respected, the MBTI has been criticised for its binary nature and lack of scientific validity. Moreover, the 16 types may oversimplify the intricacies of human personality, making it less nuanced for workplace applications.
The DISC Model:
The DISC Model categorizes individuals into four primary behavioural styles—Dominant (D), Influence (I), Steady (S), and Conscientious (C). This model is based on observable behaviour, making it more straightforward and applicable in the workplace. Its simplicity and ease of use set it apart, allowing for quick implementation and understanding among team members.
14 | iQ June 2024 MANAGEMENT & LEADERSHIP

CHOOSING THE RIGHT TOOL: DISC MODEL
While each tool has its merits, the DISC Model stands out for its practicality and ease of implementation in the workplace. Here's why:
Simplicity: The DISC Model is straightforward, using a simple framework that classifies individuals into four primary styles. This simplicity makes it accessible to a wide audience and facilitates quick comprehension and application.
Observable Behaviour: Unlike some other tools that rely on self-reported data, the DISC Model focuses on observable behaviour. This makes it more objective and less dependent on individuals accurately assessing their own characteristics.
Adaptability: The DISC Model is highly adaptable to various workplace scenarios. Whether it's team building, conflict resolution, or leadership development, the model provides actionable insights that can be readily applied in diverse situations.
Widespread Recognition: The DISC Model is widely recognised and utilised across industries. Its popularity ensures that team members are likely to have at least a basic understanding of the model, simplifying the integration of DISC insights into daily interactions.

ABOUT THE AUTHOR
By leveraging the insights gained through the DISC Model, organisations can create a more harmonious and productive work environment, fostering individual growth and collective success.
Understanding people is a fundamental aspect of effective leadership and collaboration. While various behavioural analysis tools provide valuable insights, the DISC Model stands out for its simplicity, practicality, and ease of implementation in the workplace.
The benefits of enhanced communication, optimised team dynamics, increased motivation, and improved conflict resolution make the DISC Model a valuable asset for leaders seeking to bring out the best in their teams. By leveraging the insights gained through the DISC Model, organisations can create a more harmonious and productive work environment, fostering individual growth and collective success.
Lindsay Adams is the CEO of 24x7 Assessments. He is an award-winning conference speaker and specialises in understanding people and bringing out the best in people. He has a wealth of experience in the assessment tool industry and has used thousands over the last 23 years in his own business. Today he teaches others how to harness the power of these tools for quality outcomes with their staff and stakeholders. In 2020 Lindsay was awarded a Medal in the Order of Australia, OAM for his services to the professional speaking industry. Contact Lindsay at lindsay@24x7assessments.com.au or www.24x7assessments.com.au
iQ | 15 MANAGEMENT & LEADERSHIP iQ | 15
The Records Side of Cyber Security
BY XANDER HUNTER ARIM
Aligning records management and cyber security strategies improves their impact and reach across the organisation. Cyber security specialists understand how to protect systems and networks from potential threats, and the actions which need to be taken should a cyber-attack occur.
Records management specialists understand the records the systems contain, including their risk, value, why they are being captured and kept, and how long they need to be retained.
Exploring how the two professional disciplines of cyber security and records management complement each other provides a road map for discussion and increased engagement. This in turn improves practices, strengthens desired outcomes, and maximises use of available resources.
Measures taken as part of cyber security programs are related to the confidentiality, integrity, and availability of records, information, and data (hereafter referred to as records). These measures protect the records and associated systems from external or internal threat. Records are at the centre of cyber-attacks, regardless of whether the attack seeks to steal records, or target an organisation’s infrastructure. Without records, the business of an organisation comes to a standstill. The organisation has no memory, cannot justify past actions or decisions made, and is severely limited in the business it can conduct.
INFORMATION
SECURITY
MANUAL ALIGNMENT
Preservation of confidentiality, integrity and availability of records aligns with cyber security in business continuity and/or disaster recovery plans. Records and cyber security programs need an understanding of the same space to do their work effectively, even though their area of focus and skill sets differ. It should come as no surprise then that recordkeeping practices align well with the four sets of principles under a key cyber security framework, the Information Security Manual (Australian Signals Directorate March 2024; hereafter referred to as ISM).
Some recordkeeping practices relate to having structures and processes in place that will aid a cyber security investigation, some diminish risk, some document the space to aid understanding, and some provide the means to commence recovery. For example, the set of principles under ‘Govern’ relate to identifying and managing security risk, and may include recordkeeping practices such as:
• Identifying and documenting highvalue high-risk records.
• Knowing and applying Retention and Disposal Authority coverage across all systems.
• Identifying risk to records and planning mitigation strategies.
• Developing and applying longevity and preservation strategies as needed.
• Documenting systems, technologies, and applications (including artificial intelligence (AI) technologies) and their integration.
Preservation of confidentiality, integrity and availability of records aligns with cyber security in business continuity and/or disaster recovery plans.
SPECIAL FEATURE 16 | iQ June 2024 CYBER SECURITY IN THE DIGITAL AGE

The set of principles under ‘Protect’ relate to implementing controls to reduce security risks, and may include recordkeeping practices such as:
• Recordkeeping by design and across the lifecycle of both systems and records.
• Systems functionality and control configurations matching recordkeeping requirements.
• Using archival systems rather than backups for archiving records or offline storage options.
• Managing evidential integrity – (for example, through implementing a digital preservation scheme, such as the Victorian Electronic Records Strategy or VERS).
• Addressing ongoing business and stakeholder recordkeeping needs through relevant and current business continuity and disaster recovery plans.
• Implementing disposal programs in a timely fashion.
The set of principles under ‘Detect’ relate to detecting and understanding cyber security events to identify cyber security incidents. They may include recordkeeping practices such as:
• Developing and implementing relevant metadata schemes
• Documenting systems, technologies, and applications (including AI technologies) and their integration.
The set of principles under ‘Respond’ relate to responding to and recovering from cyber security incidents. They may include recordkeeping practices such as:
• Implementing disaster recovery plans for records.
• Implementing preservation strategies for records.
• Locating and recovering high-value high-risk records.
CONFIDENTIALITY, INTEGRITY, AND AVAILABILITY
Relating recordkeeping practices to confidentiality, integrity and availability provides us with a different perspective of where the two areas of professional discipline overlap.
Confidentiality of records relates to what the records are, why they are being captured and kept (including associated legislative and regulatory contexts), who they have value for and why, and the consequences of unauthorised people having access to them. Confidential records and the systems they are located in are likely to be flagged as high risk when documenting the value and risk of records.
Cyber security specialists armed with this information will be able to determine areas of vulnerability so that suitable protections can be put in place. This fits within the ‘Govern’ and ‘Protect’ sets of principles as specified in the ISM.
Integrity of records relates to their value as evidence and includes factors that can be used to demonstrate a record is what it purports to be. For example, metadata, audit trails, lineage mapping, formats, classification schemes, process mapping, and relation to other records; all of which
iQ | 17 SPECIAL FEATURE CYBER SECURITY IN THE DIGITAL AGE
provide a record with meaning and context. Controls, such as levels of authorisation, audit trails, check-sum algorithms and other technical mechanisms can provide an indication that a record has been tampered with.
Cyber security specialists may use this information to determine and minimise the impact of a cyber-attack, and to put in places measures to prevent tampering. This fits within the ‘Govern’ and ‘Protect’ sets of principles as specified in the ISM. It is also required to achieve the ‘Detect’ set of principles.
Availability of records relates to whether records can be identified, located, retrieved, accessed, and used. It also relates to how long records are kept and their disposal sentence. Access policies for records need to balance being open and accessible so those who need it can locate, read, and use it, as well as being kept secure so those unauthorised to view or use it cannot do so. Locking down all records can result in people saving records outside of the systems, thereby placing the records at greater risk.
Cyber security specialists will need to understand how people access and use records in order to have protective measures in place and to plan for successful recovery from a cyber-attack. Different working environments, technologies, software, and business management systems will have different points of vulnerability and recovery. This fits within the ‘Govern’ and ‘Protect’ sets of principles as specified in the ISM. They also inform strategies needed to ‘Respond’.
STORAGE LOCATION AND DISPOSAL PRACTICES
The location of records may differ, depending on whether they are required for ongoing business operations, needed for more specialised occasions, or not needed at all. Some records will be on current systems, which may or may not be interconnected with other systems or cloud storage. Some may be held in nearline or offline systems, or physical storage vaults. Some may have been exported and held in separate archives facilities, such as a State Archive.
Cyber security specialists will have different prevention and recovery methods for different kinds of storage locations and situations. Integrated and online storage can be more at risk than nearline or offline storage.
For example, transferring permanent value and long-term temporary records to a separate archive can minimise security risks, improve preservation risks, as well as reduce overheads. This fits within the ‘Protect’ set of principles as specified in the ISM.
Some records will have been destroyed in line with authorised and lawful disposal practices. An effective disposal program prevents records from being kept unnecessarily, meaning they are not at risk during cyber security incidents. This is important when personal or sensitive information is held. For example, some records may contain credit card numbers or personal identifiers. Disposing of this information in a timely fashion in accordance with a relevant disposal instrument (such as PROS 22/07 Retention and Disposal Authority for Records of the Identity Verification Function) ensures that the information is less likely to exist in order to be compromised.
Cyber security specialists value timely and relevant disposal actions for time-expired records, as it means they are not in systems to be stolen or compromised during a successful attack. This fits within the ‘Govern’ and ‘Protect’ principles specified in the ISM.

LONGEVITY, PRESERVATION, AND BUSINESS CONTINUITY
Business continuity and/or disaster recovery plans will include records and are likely to be based around longevity and preservation strategies. Cyber security programs will also form part of or align with business continuity and disaster recovery plans. All the ISM principles will relate in some way to business continuity and/or disaster recovery.
Longevity and preservation strategies ensure records are captured in a long-term sustainable format, that threats to the record (such as loss of the record) can be prepared for, and that systems have sufficient functionality to manage records. For example, maintaining relationships between records and their relevant contextual metadata in a manner that enables them to be migrated from one system to another. A successful cyber-attack would be one of the risk scenarios considered (along with other threats to the record) so that preservation and recovery can be planned for.
Longevity strategies focus on ensuring the record is robust from the outset. That records will remain readable, accessible, useable, and locatable from the point of their creation and capture throughout the duration of their retention periods.
Longevity strategies may focus on factors such as:
• What long-term sustainable formats are used and why?
• How to ensure that the software and hardware required to keep, manage, open, access, read and understand the record are maintained for the duration of the records’ retention periods.
• Choosing storage options that don’t diminish the longevity of records.
Preservation strategies often include longevity and focus on the identification and mitigation of risks to the records across their lifespan.
Business continuity plans should include longevity and preservation strategies, along with information about high-value high-risk records.
SPECIAL FEATURE 18 | iQ June 2024
CYBER SECURITY IN THE DIGITAL AGE

Preservation strategies may include:
• Migration strategies to enable records to be moved from one system to another, complete with their context, while remaining accessible and useable.
• Ongoing management of decommissioned and offline systems so that the records on them are not lost to degradation and remain accessible and useable.
• The limitations, structures, and other aspects of technologies used (hardware and software) that impact on being able to identify, locate, retrieve, access, open, read, understand, and use records.
Business continuity plans are strategies, plans, and processes, to enable ongoing business in times of disaster or disruption (including cyber-attacks).
Business continuity plans should include longevity and preservation strategies, along with information about high-value high-risk records and what is needed in relation to them should disaster or disruption occur.
Preservation strategies and business continuity or disaster recovery plans should include:
• Where high-value high-risk records are located.
• How records may be recovered or restored under different disaster situations including cyber-attack.
• Whether there is sufficient provision for the recovery of records in budgets and resources.
• References to what records might be accessible and how they may be best obtained if the systems and infrastructure were suddenly unavailable (possibly due to cyber-attack, power outages, or internet being down). For example, what records are available offline and how are they accessed?
• A requirement to ensure that high-value high-risk records are created and maintained in long term sustainable formats where possible, and that they are part of actively managed digital preservation strategies.
• Transfer of permanent and long term temporary high value high risk records to a separate archive (such as a State Archive, for government records).
Reliance on backups to enable business to continue is not always possible. The backups held may also be compromised, and it may be difficult to detect or confirm that they have been compromised. Whether the backups are in the cloud or on tape may not make a difference if they contain undetected ransomware, or other malware.
CONCLUSION
Understanding where and how cyber security and records management overlap provides the common ground needed to build relationships, strengthen practices, and ensure that both areas are represented in relevant projects.
Cyber security programs can help maintain evidential integrity of records, while recordkeeping programs can enable cyber security efforts to focus on areas of high-value and high-risk. Recordkeeping and cyber security programs align well with each other and provide mutual support, especially regarding business continuity and disaster recovery. Perhaps this is why in Victoria we are seeing an increase in cyber security and recordkeeping specialists being part of the same work team.
References
• Cyber Security Topic Page (Public Record Office Victoria January 2024; https:// prov.vic.gov.au/recordkeeping-government/a-z-topics/cybersecurity)
• Information Security Manual (Australian Signals Directorate March 2024; https://www.cyber.gov.au/resources-business-and-government/essentialcyber-security/ism)
• PROS 22/07 RDA for Identity Verification Function; https://prov.vic.gov.au/ recordkeeping-government/document-library/pros-2207-identity-verificationfunction
• Victorian Electronic Records Strategy; https://prov.vic.gov.au/recordkeepinggovernment/vers

ABOUT THE AUTHOR
Xander Hunter, Standards and Policy, Public Record Office Victoria. Xander Hunter has worked in the records and information management profession for more than 20 years. Xander uses a multi-disciplined approach to developing policy and guidance across the Victorian public sector in their role as A/Manager, Standards and Policy at Public Record Office Victoria. Xander has a master’s degree of Information Management and Systems from Monash University with streams in Knowledge Management and Records and Information Management. Xander is also a member of the Australian Anthropological Society with a BA Hons from La Trobe University majoring in Anthropology.
SPECIAL FEATURE iQ | 19
CYBER SECURITY IN THE DIGITAL AGE

Professionalising Cybersecurity Professionals: Why It Needs to Happen
BY TONY VIZZA
Long-term cybersecurity practitioners tend to recognise cybersecurity solutions as involving a combination of people, process, and technology. However, most organisations see cybersecurity as mostly a technological problem. Inevitably, when organisations keep having cybersecurity incidents, they always throw more tech at the problem and continue to do so until they have an unwieldly stack of technology that inherently becomes a problem to manage.
But statistics keep illustrating that cybersecurity breaches most often happen because of human error. According to the Office of the Australian Information Commissioner, 96% of data breaches are a result of human error or deliberate (and malicious) human activity (the 2023 Jan/June report is available here). And according to cybersecurity vendor CrowdStrike, 75% of cybersecurity incident detections do not involve malware. This means that they
exploit an existing vulnerability in technology, or they manipulate people and processes to fall victim to cybercrime.
We know that human factors cause almost all cyber-related breaches. Hence, logic dictates that solving the cyber challenge rests not in more and more tech, but in ensuring that those who work in the sector are knowledgeable, skilled, experienced, and educated enough – and that they can competently follow the appropriate processes to prevent, detect, respond, recover and remediate cybersecurity risks.
Given that cybercrime is projected to become a $10 trillion black hole of criminal activity by 2025, you would be forgiven for thinking that cybersecurity practitioners belong to a professionalised industry governed by a code of practice, code of ethics, minimum acceptable levels of competency and a requirement to keep their knowledge, skills, and experience fresh.
20 | iQ June 2024 SPECIAL FEATURE CYBER SECURITY IN THE DIGITAL AGE

The same way doctors, lawyers, engineers, accountants, nurses, allied healthcare professionals, airline pilots, the trades and pretty much every single industry outside of IT does.
Not so. The Australian cybersecurity workforce today is completely unregulated. No industry-wide professional standards for cyber security practitioners are recognised formally by any Australian regulatory body or government entity.
What this means is that anyone can claim to be a cybersecurity professional. There are no barriers to entry. Employers and potential clients have no way to determine if an individual claiming to be a cybersecurity professional is legitimate.
On discovering this, a lawyer friend was speechless. Coming from a highly regulated profession with a clearly defined and regulated accreditation pathway for all practicing solicitors and barristers, he found it hard to believe that people working and protecting vast amounts of sensitive information had no way to legitimately claim to be 'professionals' in this field.
I get the same reaction when I discuss this with individuals in other well-established professions. Accountants. Engineers. Trades such as electricians, plumbers, and painters.
There is always a surprise. The response is often: 'Well, at least we know why there are all these data breaches in the news all the time.’
Professionalising the cyber security sector makes sense. Discussion continues around professionalisation in the cybersecurity space; why we need it; what it could look like and why it's important for national stability and security.
The Australian cybersecurity workforce today is completely unregulated... anyone can claim to be a cybersecurity professional.
While the vast majority of industry players in the space, including government, IT industry bodies and the academic sector recognise that the current laissez-faire approach is not an option going forward, a handful of vocal dissident’s express concern that any professionalisation scheme:
• It could serve as a 'barrier to entry.’
• It could 'worsen diversity.’
• It could 'drive up resourcing costs.’
• It will incur costs for individuals seeking professional status.
Let’s tackle each of these objections, one by one.
PROFESSIONALISATION WILL CREATE A BARRIER TO ENTRY INTO CYBERSECURITY.
Simply put, there is no evidence for this. Study after study shows there is a skills shortage in the sector. No one promoting professionalisation wants to prevent anyone from seeking a gainful career in cybersecurity. They know we need more people in the field.
Moreover, every individual who supports professionalisation believes strongly that anyone who refers to themselves as a 'cyber security professional' should have an adequately assessed and independently accredited, level of knowledge, skills, experience, current competency and should meet an industry code of conduct and code of ethics.
This might sound like an extensive list, but it's no different from the expectation of any other recognised profession. We all want the pilot flying the aircraft we are on to be an accredited pilot. We all want the doctor performing our surgery to be an accredited doctor. We all want the electrician doing electrical work on our homes to be an accredited electrician. Ditto for plumbers, builders, engineers, nurses, teachers, lawyers and so on.
SPECIAL FEATURE iQ | 21 CYBER SECURITY IN THE DIGITAL AGE
... it's hard to believe that people working and protecting vast amounts of sensitive information had no way to legitimately claim to be 'professionals' in this field.
A minimum level of professional standards should be expected of any individual in any industry looking to call themselves a 'professional' in that industry.
PROFESSIONALISATION WILL WORSEN DIVERSITY IN CYBERSECURITY.
It’s true that the cyber security sector suffers from chronically low levels of diversity today, in an environment where professionalisation does not exist. Female participation languishes somewhere between 15 and 30 percent, depending on the study and the methodology used. But claims that professionalisation could lead to worsening diversity have no credibility. The opposite may be true.
An official professionalisation scheme sponsored by government, accepted by industry and supported by academia would provide aspiring cyber professionals certainty as to what is required to be considered a 'professional', regardless of background. In fact, many women in cybersecurity report they are discriminated against via disparaging and/or untrue comments about their experience. Such a scheme would provide an objective assessment of the experience required for cybersecurity professionals to call themselves such.
PROFESSIONALISATION WILL DRIVE UP COSTS.
It may be true that attaining and retaining a professional designation would attract a fee. However, this is insignificant compared with the costs of lack of regulation.
For example, a multitude of socalled 'cyber security courses' in the market charge large fees with no standards-based approaches and exploit the current environment.
A good example of this is so-called ‘cybersecurity bootcamp’ courses from private providers ostensibly connected to universities, charging upwards of $15,000 for such a program which leaves students with minimal prospects of employment upon completion.
If anything, professionalisation will drive down these costs.
Salaries and remuneration in the cybersecurity sector already feature in the top 10 list of occupations by salary. Charging $100-$350 a year for individuals to be enrolled in a professionalisation scheme will not change this.
Sectors with a professionalisation scheme, by and large, are no more or less 'costly' than others. Consider the average salary paid to registered nurses ($80-90K), an occupation hugely vital for the well-being of everyday Australians. Nurses have a stringent accreditation scheme. The same goes for countless other regulated professions.
It is the lack of professionalisation that drives up cost. Consider remediating a cyber incident after an individual or company holding themselves out as 'a cyber security company' has completely botched the process? The clients pay the price. The ‘professionals’ concerned just find another unsuspecting client.
A VIABLE PROFESSIONALISATION PROPOSAL EXISTS.
I have been involved with the question of professionalisation for more than five years. In my previous role as the Director of Advocacy at ISC2, I devised a proposed professionalisation model for the U.K. cybersecurity workforce, based on the U.K. chartered accounting model. This lengthy paper contributed to the formation of the U.K. Cybersecurity Council, which developed a formal professional registration scheme for the U.K. cyber security sector.
After this, I developed a scheme to professionalise the Australian cybersecurity sector with Professor Jill Slay. This proposal incorporated concepts devised for the U.K. scheme, such as internationally accepted ISO-standards based recognition using ISO 17024, along with considerations and attributes required for an Australian context.
On the back of this proposal, the federal government funded the Australian Cyber Professionalisation Program. Phase 1 of this work was completed in 2023. The Federal Government 2030 Cybersecurity Strategy also references this issue and suggests that action to address a lack of professional standards in cybersecurity is warranted.
CONCLUSION
A lack of professional standards in the cybersecurity sector will continue to be a problem for the Australian economy. Developing and implementing a government-endorsed and promoted professionalisation scheme will help lift professional standards in the cybersecurity sector, address the skills and competency shortage in the sector, boost national resilience to cybersecurity threats and ensure a safer and more cyber secure Australia.

ABOUT THE AUTHOR
Tony Vizza brings extensive expertise in IT, cybersecurity, privacy and law. He has over 20 years of global experience in information security and risk strategy development, implementation and management. Tony engages with organisations on cybersecurity challenges, strategies and change management to reduce risk and enhance resilience. Prior to joining KordaMentha, Tony was the Director of Cybersecurity Advocacy for the largest global association of certified cybersecurity professionals and a board member of the peak body for the profession in Australia. He continues to advocate to government, industry and academia to improve cybersecurity on behalf of the profession.
SPECIAL FEATURE 22 | iQ June 2024
CYBER SECURITY IN THE DIGITAL AGE
STAY INFORMED; STAY COMPLIANT
EXPERIENCE MILA, YOUR COMPREHENSIVE COMPLIANCE COMPANION.

MILA provides a robust repository of act and regulation updates from all Australian jurisdictions, facilitating a clear understanding of what records need to be maintained, their retention period, and the consequences of non-compliance. WHAT IS MILA?
SHIELD YOUR BUSINESS AND PROTECT YOUR RECORDS
Recent breaches at Medibank, Latitude, and Optus highlight the vital role of robust record-keeping. Compliance and proper documentation could have lessened their impact. MILA offers comprehensive guidelines, empowering firms to establish secure information protocols, significantly reducing data breach risks.
WHY CHOOSE MILA:
Quarterly updates
In-depth guidance
Streamlined processes
Scan Here to Sign Up for a FREE 5-Day Trial:
Comprehensive coverage
Ongoing support



For more information please contact training@rimpa.com.au or call 1800 242 611
For more information please contact admin@rimpa.com.au or call 1800 244 611

Cybersecurity in the Digital Age
BY LINDA SHAVE, LIFE FRIM
Thanks to the internet and modern technology cybercriminals and hackers can reach across the globe and tap you on the shoulder with a digital finger, spreading malware, viruses and bad bots.
All such attacks are aimed at infecting your systems and stealing information as part of their cyberattacks. The value to these cybercriminals and hackers come from stealing information, compromising business operations or holding your data hostage.
24 | iQ June 2024 SPECIAL FEATURE CYBER SECURITY IN THE DIGITAL AGE
“Cybersecurity needs to be part of the fabric of every company and every industry, integrated into every business process and every employee action. And it begins and ends at the top. It is job number one.” - Charles W Scharf, President/CEO Wells Faroo & Company.
Interconnectivity between sensors, information sources, enterprises, individuals and the metaverse world is collecting gargantuan amounts of data daily and providing opportunities for cybercriminals and hackers. The exponential growth globally of macro-technology trends such as artificial intelligence, machine learning, generative AI, fake news, data analytics and algorithms has provided a ubiquitous amorphous landscape fuelled by the continued evolution of cybercriminals and hackers who engage in cybercrime.
We could say that cybercriminals are like spies who want government and business secrets, they are the organised criminals who want to steal our identities and money. Cybercriminals include hackers who want to make a political or social statement and terrorist who want to attack our infrastructure.
NAVIGATING THE EVOLVING LANDSCAPE OF CYBERSECURITY
Navigating the evolving landscape of cybersecurity requires agility, scalability and adaptability this is essential especially in areas such as national security where cyber threats continually mutate and evolve. Cybersecurity is not new and IT departments have been using Artificial Intelligence (AI) driven cybersecurity tools and solutions for some time. Original AI driven defence cybersecurity tools and solutions have been designed to protect business from cyberattacks and hackers and offered a significant advantage by automating routine security tasks that required considerable human effort. Activities such as continuous monitoring of network traffic, identifying vulnerabilities, and applying security patches have been handled competently and efficiently by AI driven defence cybersecurity tools.
In general, organisations have taken steps to protect their data and information assets from being accessed via vulnerabilities in its networks and/or business systems. Employees and business regularly changed passwords and understand their responsibilities for protecting business systems from unauthorised access.
However, there is a new and evolving threat on the cybersecurity horizon! AI driven defence cybersecurity tools are now being turned into potential weapons.
The arrival of Generative AI has provided a weapon to manipulate and control machines, provide erroneous information to human operators without their knowledge thus providing fake information, disinformation and malinformation which in turn can potentially harm individuals, citizens, government and business enterprises.
"...there is a new and evolving threat on the cybersecurity horizon! AI driven defence cybersecurity tools are now being turned into a potential weapon."
Cybercriminals and hackers are harnessing the power of generative AI to create more superior and evasive malware software that is specifically designed for cyberattacks. For example, generative AI malware explicitly designed to generate convincing phishing messages that are tailored to exploit network and individual vulnerabilities by creating deepfake. Deepfake and AI chatbots are both products of generative AI and have the potential to create something that does not exist. Generative AI poses not only a great risk to identity theft it is also a threat to cybersecurity.
SO, WHAT IS GENERATIVE AI? A BRIEF HISTORY.
Interestingly, the concept of Generative AI is not new. Around 1932 Georges Artsrouni invented a machine that he called the “mechanical brain” to translate languages. The mechanical translator was a multilingual dictionary which was encoded onto punch cards. In 2006, Data scientist Fei- Fei Li set up the ImageNet database that laid the foundation for visual object recognition. In 2011, Apple released Siri, a voice-powered personal assistant that generated responses and took actions in response to voice requests.
In 2014, Ian J. Goodfellow and colleagues published the first paper on Generative Adversarial Networks (GANs) which is a class of machine learning frameworks for approaching Generative AI, the aim being to determine if an image is real or fake and in 2022, we saw the arrival of ChatGPT.
It is hard to believe that the introduction in late 2022 of ChatGPT (which provided a chat-based interface to its GPT 3.5 language learning model (LLM)) could have had such an impact and start the race for the creation of generative tools. These generative tools have transformed how people search, use and assess information. Although tools such as ChatGPT can respond coherently the outcome is not always accurate.
The consequences could result in disinformation, malinformation and the possible generation of hate speech all of which could cause geopolitical crises.
Spanning the years 1932 to 2024 generative AI has excelled in recognising images, classifying articles and converting spoken words into written text. In essence generative AI can create synthetic images when given a description, generate papers about a particular topic or produce audio versions of written text as well as creating video images of a person and using their voice to create fake imposters and even write computer programs.
In the context of cybersecurity generative AI has the potential to enhance the ability of bad actors to flood us with fake content masquerading as truth and fake voices that sound eerily like those of our loved ones. Can we trust what we see or hear? The answer is probably not. In the wrong hands generative AI tools could cause even worse problems launching cyberattacks or causing havoc in energy grids, financial markets, information transmitting technologies and communication infrastructures. Generative AI language learning models continue to learn and thus the generative AI tool might become capable of making plans on their own and acting on them. Generative AI raises potential risk to infrastructure, data, people, applications and algorithmic risks.
SPECIAL FEATURE iQ | 25
CYBER SECURITY IN THE DIGITAL AGE
SO, WHAT IS THE METAVERSE?
The metaverse is a seamless convergence of our physical and digital lives, creating a unified, virtual community where we can work, play, relax, transact and socialise. An outcome of COVID-19 was the acceleration of digitisation, online engagement, communication and virtual experiences. The metaverse world continues to evolve with Augmented Reality (AR) and Virtual Reality (VR) headsets providing a powerful user experience. Use cases include online working and education which can now be conducted through video calls and virtual social events. The metaverse enables people to immerse themselves into education and learning, have access to remote healthcare, government services and shopping experiences without the geographical restrictions. However, in this metaverse world which is collecting gargantuan amounts of data daily there is the potential of vulnerability risks such as data privacy, user health and safety, secure identities, fraud and cybersecurity.
ADDRESSING EMERGING CYBER THREATS AND VULNERABILITIES
Addressing emerging cyber threats and vulnerabilities requires understanding that originally AI driven defence cybersecurity tools have been designed to protect business from cyberattacks and hackers. Times are now changing as AI driven defence cybersecurity tools are now being turned into a potential weapon with the rise of generative AI technologies. The arrival of generative AI has provided a means to manipulate and control machines, provide erroneous information to human operators without their knowledge thus providing fake information which, in turn, can potentially harm individuals, citizens, government and business enterprises. Another threat area for consideration might include ‘anonymisation’. Anonymisation or de-identification is
the process of removing as much data as possible that relates to individuals for example names, addresses and other identifying features that might identify an individual. This is particularly important in the era of government and business who are sharing large quantities of real time data. However, artificial intelligence, machine learning, algorithms and pattern recognition artificial intelligence tools can be effective at adding data features back into datasets, by for example, cross-referencing other available datasets. This in turn could pose a cybersecurity risk as well as exposing inadvertently information that might identify an individual.
It is interesting to note that governments and private enterprise services are asking customers to use voice recognition, thumb prints or biometrics as a safeguard to accessing customers services and their personal information. However, these blueprints of your biometrics and voice can now be used against you with the rise of generative AI technologies that can use your voice and features to create a fake ‘you’. One therefore needs to ask the questions how safe is your information?
And if stolen, how safe are you against being exploited or your identity, private information and any sensitive data being used against you? These are crucial questions for every citizen, government and private enterprises need to be able to answer how they will manage this superior and evolving cybersecurity mine field of cybercriminals, hackers and generative AI. Government and private enterprises need to convince every citizen and individual that they can be trusted to protect you from cybercriminal threats, fake news, disinformation, malinformation and identity theft.

SO, WHAT IS FAKE NEWS?
Fake news also sometimes referred to as the deepfake universe has escalated since the arrival of generative AI tools and the rise of disinformation and malinformation So what is disinformation and malinformation? What is Disinformation?
Disinformation is false or inaccurate information that is deliberately created and spread to harm a person, social group, organisation or country. What is Malinformation?
Malinformation is accurate information inappropriately spread with the intent to cause harm, particularly to the operation of democratic processes.
"In the wrong hands generative AI tools could cause even worse problems launching cyberattacks or causing havoc in energy grids, financial markets, information transmitting technologies and communication infrastructures."
Therefore, when addressing cybersecurity, emerging cyber threats and vulnerabilities in networks and business systems government and business need to consider in their cybersecurity strategies and policies:
• How do we identify fake from real information?
• How do we identify that data and information is trustworthy, ethical, non-bias, honest and righteous?
SPECIAL FEATURE 26 | iQ June 2024
CYBER SECURITY IN THE DIGITAL AGE
"...generative AI can be helpful in defending business systems from cybersecurity attacks as it is extremely adept to detecting patterns in huge unstructured datasets, thus enabling government and business to expedite threat analysis and troubleshooting."

BEST PRACTICES FOR SAFEGUARDING SENSITIVE INFORMATION
To address emerging cyber threats and vulnerabilities, record and information management professionals need to understand the difference between information security and cybersecurity. Information security and cybersecurity are terms used interchangeably because in their basic form they refer to the same things, which is protecting the availability, confidentiality and integrity of data. However, there is a crucial difference:
• Information is at the heart of the organisation, whether it is a business record, personal data or data collected as an outcome of a transaction. Information assets can be collected, secured, managed and kept in an electronic document and records management (EDRM) system or other business systems. Information security protocols are normally placed at the point of creation, capture or scanning and registering the information asset (data) into your EDRM systems or business systems. Information security focus is on protecting data from loss, unintended or unauthorised access, use or sharing.
• Cybersecurity on the other hand covers the steps an organisation takes to protect its data/ information assets that can be accessed via vulnerabilities in its networks and/or business systems. Cybersecurity focus is on safeguarding data from cyber-attacks, external malicious breaches, inadvertent internal breaches and/or thirdparty partner breaches.
The primary challenge and risks will be how to safeguard the omnipresent technology, networks, sensors and the Internet of Everything against generative AI cyber-attacks, data loss and privacy breaches. It maybe noteworthy to mention that every smart grid, sensor for smart streetlights, traffic lights, surveillance monitoring devices etcetera, all have their own Internet Protocol Address (IP) which uniquely identifies them just like your internet, mobile (cellular) phones, wireless-enabled laptops, smartphones and tablets IP addresses identify you.
If we consider that for every individual who is wirelessly connected and all the sensors across a city, state or the globe there are billions of discrete end points and IP addresses. In fact, one might ponder that over
time in the omnipresent wireless connected world there are now more sensor IP addresses in smart cities, smart devices and objects than IP addresses held by individual people.
Some best practices for safeguarding sensitive information might be to instigate a managed vulnerability rationalisation and business impact analysis by utilising cyber digital twins. A digital twin platform can help the business in identifying how they capture data, visualise business processes, simulate different scenarios, discover business operational critical assets and enable the organisation to analyse and secure their physical systems and infrastructure. Further, your cybersecurity and information security strategies, policies and procedures need to include how will you manage the risks, how do you measure the outcomes, steps for communicating, ongoing monitoring and reporting.
To err on the side of caution, there are many ISO standards and best practices for addressing cybersecurity. However, as outlined in the above generative AI discussion there is a new level of complexity, generative AI cyberattacks are using large language
iQ | 27 SPECIAL FEATURE CYBER SECURITY IN THE DIGITAL AGE
models including nefarious acts for sophisticated phishing incidents. The utilisation of third-party datasets, plug-ins and pre-trained models could increase vulnerabilities.
Generative AI may also inadvertently reveal confidential data in its responses, leading to unauthorised data access, privacy violations, and security breaches.
On the positive side of generative AI is that generative AI can be helpful in defending business systems from cybersecurity attacks as it is extremely adept to detecting patterns in huge unstructured datasets, thus enabling government and business to expedite threat analysis and troubleshooting. Government and business will need to consider new approaches for cybersecurity awareness and education for all employees.
INTERVIEWS WITH CYBERSECURITY EXPERTS AND THOUGHT LEADERS
I am deviating from interviews with cybersecurity experts and thought leaders to draw your attention to something much closer to home, the ransomware cyberattacks of a
Public Library. The public library was in Toronto where on 28th October 2023 100 branches and nearly 5,000 computers went down resulting in 1 million books piling up in storage.
The ransomware cyberattacks encrypted Toronto Public Library computer systems and stole staff information. The link to the CBA News article posted on 27th February 2024 is a great insight into what happened. It also reflects how staff rallied together by reverting to manual processes just to keep books circulating and services open to the public. The report indicates that Toronto Public Library did not pay a ransom to restore its system, instead they chose to rebuild it themselves. A great read and a real example of resilience in the face of hacker extremism.
See article www.cbc.ca/news/ canada/toronto/toronto-libraryransomware-recovery-1.7126412
In ending, there is indeed a lot of food for thought around cybersecurity in our digital world and how we continue to manage the changing landscape and moving goal posts of generative AI.
The topic around the good and bad of generative AI deserves future round table discussions, not only within information management circles but with our colleagues in IT, risk management, auditing and security.

ABOUT THE AUTHOR
Linda Shave FRIM, is acknowledged as a thought leader and architect of change. She is a researcher, consultant, educator and author on topic areas such as intelligent information management, artificial intelligence, robotic process automation, privacy, and security. Linda is a gold laureate winner for Government Innovation and has an interest in data science, robotics, and quantum computing. Linda is a member of numerous professional organisations. Linda can be contacted at linda.bizwyse@gmail.com


SPECIAL FEATURE 28 | iQ June 2024 CYBER SECURITY IN THE DIGITAL AGE 30 Years Young Records Solutions is turning 30 this year and we’re giving you a gift to celebrate! Use the QR code to send your enquiry and receive a 10% discount when you mention this ad* *valid until 31 July 2024
Discover our convenient workshop bundles designed to enhance your team's skills and expertise. Perfect for sharpening existing talents or expanding knowledge, these bundles offer flexibility and affordability.
Why Choose RIMPA Workshop Bundles?
• DISCOUNTED RATES: Affordable advanced learning options.
• EASE OF PLANNING: Pre-scheduled sessions fit seamlessly into your busy calendar.
• TAILORED WORKSHOPS: Customise workshops to suit your specific needs.
Boost performance, add value to your organisation, and stay ahead in the evolving world of records management. Invest in your future with our professional development programmes.
BOOK YOUR BUNDLES TODAY
CORPORATE BUNDLE
Exclusive online workshops just for your team!
3 Workshops
Up to 15 attendees
Discounted price Enquire Now
INDIVIDUAL BUNDLE
Pre-scheduled online workshops just for your need!
3 Workshops
Personal developments
Discounted price Enquire Now
PREPAID SESSIONS
Prepaid Scheduled online workshop sessions for you and your team
10 Workshop slots
Flexible attendees
Discounted price Enquire Now
CHOOSE FROM THESE CATEGORIES
We
iQ | 29 iQ | 29
DEVELOPMENT WITH
ELEVATE YOUR PROFESSIONAL
Workshop Bundles
Visit rimpa.com.au to find out more FOR MORE INFORMATION RIMPA GLOBAL RECORDS MANAGEMENT CLASSIFICATION & METADATA RISK & SECURITY ORGANISATION MANAGEMENT DIGITAL & AI ARCHIVING GOVERNANCE
provide exclusive corporate, individual, and prepaid workshop bundles designed for convenience, flexible and cost-effective professional development.
us and fast-track your professional development and learning journey.
Join

A
CASE STUDY:
Applying Information Security Classification
BY UTA FOX, MA, CRM, FAI
It’s no longer uncommon to hear of information breaches, or of unauthorized access to an organization’s information now reported widely in newspapers, television, and on social media.
Organizations are aware their information is an important asset and resource requiring protection from unauthorized access or disclosure, or inappropriate use or compromise. One method of attaining information security is by applying Information Security Classification (ISC).
ISC is defined as systematically categorizing an organization’s information based on that information’s sensitivity to the organization. The more sensitive the information, the higher the risks if that information is compromised or breached. Sensitivity means personal and/or business identifying information that if disclosed or accessed without authorization, could cause harm, damage, injury or worse to an individual, property, government or private sector. Protection of personal information is legislated in Canada both federally and in the province of Alberta:
Federally:
• Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) is applicable to the private sector.
• The Privacy Act protects the privacy of individuals and their personal information.
Alberta:
• Alberta’s Freedom of Information and Protection of Privacy Act is applicable to the provincial government and public sector agencies, boards and commissions.
• The Personal Information Protection Act (PIPA) relates to the private sector.
30 | iQ June 2024 INFORMATION MANAGEMENT
What types of personal and business information require protection?
Personal identifying information that may require protection include social insurance numbers, payroll information, medical and health information, etc. Business information that may require protection includes trade secrets, proprietary and or strategic information, customer / client information, legal information, contracts, intellectual property, etc.
APPLYING ISC – THE METHODOLOGY
In 2019, the Calgary Police Service (CPS) applied ISC to safeguard its information. This case study describes how CPS developed and implemented its ISC project and program. Beginning with the security classification model used, it discusses how CPS security classified its information and what that program entailed to mitigate the risks of unauthorized release or access to information.
From the security classification aspect, information must be identified and labeled according to its sensitivity. Handling strategies needed to be established addressing information sharing, labeling, storing, transmitting, printing/ copying and disposition. A policy was created to identify and standardize practices and processes; resources were developed, a training program implemented, and a communications strategy devised. Also addressed was the ‘Third Party Rule,’ (TPR) a rule that prohibits the disclosure of information without the consent of the original contributing agency. It is usually applied to criminal information shared with external partners but could also be applied internally.
The Project Team (Team) consisted of the Inspector, Technical Investigations Section, the Records and Evidence Management Section’s Director in collaboration with the Records and Information Management (R/IM) team. From the project’s beginning the Team specified a holistic approach to CPS’ records, documents, information, and data, collectively termed information.’ The ISC project and resulting ISC program addressed the protection of all of CPS’ information, regardless of format or media.
To avoid confusion with CPS’ robust R/IM program which classifies information according to CPS’ Records
TABLE 1: PROTECTED INFORMATION CATEGORIES
Protected Security Classification Protected Security Classifications Description
Unclassified if unclassified information was compromised no harm to individuals, government, or private sector; if there was any financial loss, it would be insignificant
Protected A sensitive information, if compromised may cause harm to individuals or an organization
Protected B personal and sensitive information; if compromised may cause serious injury to an individual, organization and may negatively impact public trust and the credibility of the organization
Protected C extremely sensitive and / or restricted information; if compromised may cause grievous bodily harm or severely jeopardize public safety
ISC is defined as systematically categorizing an organization’s information based on that information’s sensitivity to the organization.
Retention Schedule, and to differentiate RIM classification from ISC classification, classifying information from the ISC perspective was termed ‘security classifying.’
Benchmarking with other Canadian law enforcement agencies quickly determined the model that best reflected CPS operations was the Protected model (also used by the governments of Canada and Alberta). Protected information applies to safeguard information; if that information is compromised, it may cause harm to individuals, organizations or jeopardize public safety.
APPLYING INFORMATION SECURITY CLASSIFICATION - A CASE STUDY
Security Classification Process
To security classify CPS’ information the Team needed to differentiate between current and legacy information as it was not practical to physically security classify all of CPS’ information. A ‘go-forward’ approach was adopted based on when staff received ISC training. Once trained, employees were required to security classify the information they create. Legacy information is only security classified if it is subject to action. For instance, if a case file from 1982 was reopened, renewed or readdressed it requires security classification. But, if legacy information is not actioned, there is no requirement to physically label it with a security classification.
Using the Protected Security Classifications (Table 1) as the template, the Team approached security classifying CPS’ information by record series (Table 2). Job postings are security classified as Unclassified information as a published job posting should not create any harm. On the other hand, much of HR information is security classified as Protected B (personal and sensitive information) as harm could be caused if that information was compromised and made public.
TABLE 2:
EXAMPLES OF SECURITY CLASSIFIED RECORD SERIES
ISC Protected Category Examples of Applicable Record Series
Unclassified Annual reports; general crime reports; general public information; job postings, etc.
Protected A Policies and procedures; public relations information; general business plans; specific crime reports, etc.
Protected B
Human Resources (HR) information such as employee files, medical files, etc.; case files (operational and investigative files); finance and payroll; officer notebooks, etc.
Protected C Agent information, undercover officers, offender information, etc.
iQ | 31 INFORMATION MANAGEMENT
Once a security classification was assigned to a record series, the actual responsibility for applying it to created information was the responsibility of the creators or originators of the information. And, while employees creating the information are responsible for its security classification, their Inspector / Director (management) has authority to amend it.
The Team ensured employees were aware that CPS security classifications were a guideline, subject to change as there would be exceptions, especially as the information’s content determines the security classification. For example, according to Table 2, policies and procedures are security classified as Protected A, sensitive information. However, some policies and procedures may contain both personal and sensitive information which requires that security classification to increase to Protected B or higher, again depending on the content.
Information may also require reclassification as its protected status could change throughout its lifecycle. Some information may commence their lifecycle as Protected A, but could, once concluded, be reclassified. For instance, a 2015 report on crime analysis security classified as Protected A, could, by 2020, be reclassified as Unclassified as that information may no longer be sensitive.
A default status was also established. As Protected B and Protected C information required encryption if forwarded to external partners, the default was set at Protected A as it best reflected regular business operations. However, establishing a default setting could be misinterpreted to include all information was Protected A. The Team was aware of this misunderstanding, they ensured training and training resources addressed employee’s requirement to monitor their information’s content and increase / decrease the security classification default depending on the information’s content.
INFORMATION HANDLING
Non-compliance with the ISC policy could create harm. In establishing how Protected information could be shared, labeled, stored, transmitted, printed and/or copied and dispositioned, the Team considered the scenarios of working in the office, or from home or in the field in
terms of balancing the need to protect information while facilitating the work of the organization. As an example, choosing to encrypt all information shared externally could create a burden or jeopardize investigative success if recipients of encrypted information encountered difficulties unencrypting information immediately required.
Table 3 indicates the handling procedures and processes for Unclassified information; similar tables were created for Protected A, B and C reflecting the corresponding increase to the security of information as the security classification increased. For instance, Protected B information can be shared internally with authorized members and externally with other agencies for law enforcement and/or business purposes while Protected C information cannot be distributed, reclassified, copied, reproduced, used in whole or part, without the consent of the originator. Handling instructions are appended to the ISC policy. Refer to Table 3.
THE THIRD-PARTY RULE
The Alberta Provincial Policing Standard advises that police services are required to collect, analyze, evaluate, and exchange information relating to criminal activity. That criminal information can only be shared with authorized recipients. To control the release of that information, police services use the Third-Party Rule which states:
'This document is the property of the [name of police service] and is not to be reclassified, copied, reproduced, used in whole or in part or further disseminated without the consent of the originator.'
The TPR is labeled in red and inserted on the bottom of each page of applicable documents.
The purpose of the TPR is to prohibit the disclosure of information without the consent of the original contributing agency. It is not a security feature. The TPR can be difficult to comply with. For example, an employee receiving an email with a Third Party Ruled document can only ensure that information remains in their inbox as no actions, other than viewing it, can be made without any further consent. If any other actions were made on that document, apart from deletion, that would be non-compliant with the TPR.
Sharing:
Labeling:
Storing:
Transmitting:
Printing / copying:
Disposition
• Share unclassified information internally / externally as appropriate.
• Label documents, reports, spreadsheets, etc., in the upper right-hand corner as: | ‘ISC: Unclassified.’
• Label emails below the signature line.
• Physical information can be stored in desks, record boxes, in public areas, open shelving.
• Electronic information is stored according to the R/IM policy.
• May be emailed and mailed.
• May be printed and copied.
• Bring removable media to IT for disposal.
• Dispose physical and electronic information according to the R/IM policy.
32 | iQ June 2024 INFORMATION MANAGEMENT
ISC Category Handling Procedure Practice Unclassified
TABLE 3: HANDLING PROCEDURES AND PRACTICES:
Once a security classification was assigned to a record series, the actual responsibility for applying it to created information was the responsibility of the creators or originators of the information.
RESOURCES
Security classifying and sharing security classified information is complex and to assist employees with understanding and applying the ISC policy, practices and procedures the Team established a number of resources available on the intranet that includes:
• ISC Quick Guide – 1 page document encapsulating each Protected status, includes examples of each Protected records series and handling directions.
• Frequently Asked Questions (FAQs).
• Encrypting Information.
• Third Party Rule Guidelines. These resources are updated as processes and practices change.
SYSTEMS
CPS’ major systems were equipped with the security classification label at the time CPS implemented ISC, however, the label was not activated at the time of rollout and some systems required an upgrade prior to ISC deployment. In the interim, employees manually security classified any system generated documentation according to the ISC policy. Once systems were on-boarded, those storing case file information defaulted to Protected B. Microsoft 365 was a boost to ISC policy compliance as it contains the Sensitivity label that accommodated CPS’ four Protected status’ which IT defaulted to Protected A. Word, Excel, PowerPoint, and emails are now automatically inserting the default security classification into these documents in the upper right-hand corner. The ISC policy was updated to capture the automated function.
TRAINING
Once the ISC policy, handling instructions and resources were developed the Team was ready to launch ISC training. They crafted a PowerPoint presentation that addressed all components of the ISC program, why ISC was being implemented, its value and importance, how it was being implemented, the security classifications, which record series were applicable to each of the security classifications, the ThirdParty Rule, employee responsibilities, handling instructions, etc.
But, before rolling out the ISC training program Servicewide, the Team chose to pilot it first in their respective divisions. That strategy indicated improvements were required, for example, the Team initially took

ABOUT THE AUTHOR
responsibility for capturing employees attending ISC training but realized that was a management responsibility.
Throughout 2019 the Team provided ISC training sessions to each of CPS’ 150+ work areas delivering the interactive ISC presentation, recognizing ISC training was not a ‘one-time’ training event as some employees missed initial training (illness, vacations), some required refresher training and new employees needed ISC onboarding. Once the ISC project was completed, the ISC program commenced and ISC training became part of regular training the R/IM Team delivers along with R/IM training.
To reinforce ISC training and to ensure compliance the Team recently created an ISC e-learning course which CPS employees are required to complete. One of the many advantages of e-learning courses is that the Team can verify which employees successfully completed the course, advising management of those employees who still needed to complete the course.
LESSONS LEARNED
It took almost a year to implement ISC. Fortunately, the Team took a change management approach to deployment. They communicated with and kept senior management apprised of the project and had their full support. The Team’s solid implementation plan met its targets. The project easily transitioned to operations under the R/IM team’s jurisdiction.
Policy compliance is a continual path often caused by training gaps or forgetfulness. The training courses that were implemented improved compliance. R/IM updates the course content regularly so that employees experience a comprehensive and in-depth approach to ISC.
Information Systems support was flagged as an issue from the outset of policy development. Of note, it would have been almost impossible to implement ISC with full IT system compliance from day one. A decision was made to implement the policy and human aspects of ISC as an initial phase and follow with the upgrade and development of compliant systems. This allowed for a quicker project completion and increase in information security while avoiding significant cost and IT delays.
In terms of successes the Team awareness of the value of information and the significance of its protection increased exponentially. CPS implemented ISC to safeguard its information and while its ISC program is only applicable to its own information, the realization is that it regularly receives information from other police services, external agencies, citizens, etc., and that all information it receives, and stores must be protected and handled; accordingly, a concept the R/IM team now imparts into training.
Uta Fox is the Director of Records and Evidence Management Section at the Calgary Police Service, Calgary, AB, Canada. She holds a Master of Arts degree from the University of Calgary, is a certified records manager and a Fellow of ARMA International. Uta has been in the R/IM field for over 20 years.
iQ | 33 INFORMATION MANAGEMENT

Evaluating the Tone of IG Policies
BY LEWIS EISEN
This article advocates for a shift from authoritative language to a more respectful and collaborative approach in IG policy writing.
34 | iQ June 2024 INFORMATION GOVERNANCE
Securing stakeholder engagement at all levels of the organization remains a persistent challenge for Information Governance (IG) professionals. Within organizations, commitment to the various aspects of an IG program can vary widely, from robust compliance to near indifference. For IG practitioners, this engagement gap has long been a source of frustration. That situation is not optimal because comprehensive engagement is critical for the success of the program. Could part of the problem be the way the IG policies are worded?
Practitioners who belong to RIMPA pledge to uphold its values and principles, including Collegiality, which RIMPA defines as working together to willingly serve members, the profession and the community with diligence and respect. This value suggests that, as part of an enterprise IG program, its policies and standards will be developed in a manner that is inclusive, collaborative, and respectful, intending they are not merely adopted but also integrated into the organization's culture.
MISALIGNMENT OF TONE
Against this background, the tone employed in IG policies and directives often seems misaligned. Authoritative language in policy— for example, "Employees must keep personal information secure at all times" and “Employees must comply with all metadata standards” —can come across as dictatorial or patronizing. Even when the substance of the rule is defensible, the language and tone in those examples are decidedly heavy-handed, potentially alienating staff and hindering the cooperative spirit needed for effective IG on an enterprise-wide level.
The distinction between operating in a culture of trust versus one of distrust be determined by examining the language found an organization’s policies. You can tell that your organization is functioning in a culture of distrust when the overarching philosophy sounds something like this: “If we don't explicitly put a statement into the policy telling people not to steal company information, then somebody is going to do it and claim that they didn't know it wasn’t allowed.” That approach is overtly symptomatic of a defensive policy culture.
Sometimes, though, the symptoms are less conspicuous. Consider the tone of the following two statements addressing the same procedural requirement:
A) When requesting retrieval of boxes from storage, staff must complete the Box Request Form in full. Forms not filled out properly will be returned.”
B) Boxes are retrieved from storage upon receipt of a completed Box Request Form.
These statements convey the same factual request: the Records office wants the forms completed properly. So why the difference?
Looking at Statement A, it’s obvious that the office has received too many incomplete forms in the past. More seriously, what’s also apparent is the underlying emotion. Read between the lines and listen carefully to the language in Statement A and you will detect a subtle—but clearly perceptible—undertone of frustration: the people in the Records office are fed up with the lack of compliance with this rule and have no bones about sharing that sentiment.
Statement B is neutral. The requirement is still strict, yet it’s expressed in a helpful, rather than reproachful, manner.
“If we don't explicitly put a statement into the policy telling people not to steal company information, then somebody is going to do it and claim that they didn't know it wasn’t allowed.”
That approach is overtly symptomatic of a defensive policy culture.
While it's understandable that from time to time we all might experience a feeling of frustration around repeated rule violations, the salient question is whether it’s appropriate that emotions permeate policy documentation.
The presence of negativity within policy language not only reflects the tensions of the group internally, but then broadcasts those sentiments to the rest of the organization. That disclosure potentially undermines the professional reputation of the records office, diminishing trust between it and the rest of the organization.
The situation is even worse if your corporate policies are posted out on the Web in an effort to be more transparent. In that case, the entire world will find out about the low compliance level and the frustration of the Records staff. Not exactly a good image to project to the public.
MAKING RULES ENGAGING
Policies, done properly, are about getting clarity and setting targets. No matter what the field—Operations, HR, Finance, Security, and IG—rules are about helping people do the right thing. With well-crafted policy language, people don’t merely comply; they become advocates. They will encourage others to follow them, and often express a wish for such policies to be more widespread.
Achieving this level of endorsement requires rules are framed to sound positive and helpful, rather than negative or authoritarian. Consider this example:
C) You must be a metadata specialist to be given access to the Metadata Database. Why “must”? Why is someone issuing an order about this requirement?
iQ | 35 INFORMATION GOVERNANCE
No one talks to their employees in a condescending manner anymore. Yet a lot of people still write like that. As a result, too many policies today still sound like parents admonishing their children.

The access condition might be strict, but there’s no reason to make it a commandment, especially when there are many less aggressive ways to put it, such as:
D) Only metadata specialists are eligible to apply for the Metadata Database.
E) The Metadata Database is accessible exclusively by metadata specialists.
F) You qualify to use the Metadata Database if you are a metadata specialist.
Each of those alternatives communicates the same requirement without resorting to the ParentChild dynamic that is so toxic to good working relationships.
Whether intended or not, the message that Statement C delivers is, “Don’t try to get around this rule.” It's working from a defensive posture, revealing an underlying policy culture of distrust. It’s hard to build positive relationships with colleagues when your policies are loaded with negative messaging.
A HOLDOVER FROM THE PAST
Why is that dictatorial language there in the first place? More importantly, why is it still with us?
Think back. Our earliest encounters with rules were with our parents and our teachers, who constantly told us how to behave: Do this. Don’t do that. If you don’t do what I say, there will be consequences. Those interactions ingrained the belief that rules should sound forceful and unquestionable. That tone emphasized the power hierarchy: “I am in charge and you will obey me.”
To be fair, as children, we were only seeing part of the picture. What we were witnessing at the time was how caretakers instruct children. Wording rules directed at adults is a different skill altogether, and most of us weren’t taught how to do that.
In addition, for centuries up until only a couple of decades ago, that dictatorial tone of voice was reinforced by a too prevalent social dynamic in the office. In the past, it was not uncommon to hear bosses berating or verbally abusing their employees and, most unfortunately, there was
nothing the poor employees could do about it. Bosses spoke like that and they wrote like that, and that dynamic was the norm in the workplace.
Times have changed. Today the predominant trend is to maintain a respectful workplace. Management promotes awareness of issues around collaboration, diversity, and inclusion. <pull quote> No one talks to their employees in a condescending manner anymore. Yet a lot of people still write like that. As a result, too many policies today still sound like parents admonishing their children.
That relic of the past is a serious impediment to an optimally functioning workplace. Adults hear that heavy-handed tone of voice as disrespect and instinctively tend to resist. It’s called psychological reactance, and it’s well documented. Obviously, a range of factors affect compliance issues in the office, from practical impediments to dysfunctional enforcement mechanisms. The rules themselves may be weak and, in some cases, you might need to strengthen them; however, don’t confuse strict requirements with harsh language.
36 | iQ June 2024 INFORMATION GOVERNANCE


Making your requirements stricter has the power to effect changes in behaviour; in contrast, making your language harsher engenders more resistance.
AVOIDING THE PARENT–CHILD DYNAMIC
The easiest way to avoid sounding like a parent talking to a child in policies and directives is to leverage the power of the present tense. It’s plain and simple, conveying matter-of-fact information:
G) The office is open to the public from 8:00 to 16:00.
H) File inventory reports are due at the end of every fiscal year.
I) Expenses are reimbursed when submitted within one month of the trip.
"...don’t confuse strict requirements with harsh language."
The present tense informs you about the high-level executive decision that was made on the matter. There’s no “must,” “shall,” or “will” about it. It just is.
Not convinced that the present tense will be strong enough for you? Take a look at the world of legislation. The strictest rules anywhere are the criminal laws: the rules against murder, assault, kidnapping— you know, the nasty stuff.
Those rules are crafted very deliberately. They don’t say, “You must not murder other people” or “It is strictly prohibited to kidnap anyone.” They are much more dispassionate than that. Here’s the prohibition on destruction of properly from the Crimes Act of New South Wales:
A person who intentionally or recklessly destroys or damages property belonging to another or to that person and another, is liable— (a) to imprisonment for 5 years… Look at that! It’s drafted in the present tense. Look at the advantage of that formulation: there is no commanding, no finger wagging, no we-know-best or we-are-in-charge attitude. No Parent-Child dynamic. It's a simple, respectful statement of the decision on the topic.
iQ | 37 INFORMATION GOVERNANCE


As leaders, we cannot promote collaboration, inclusion, and respect, when a simple reading of the policies makes it clear that the real goal is old-fashioned obedience.
Here’s the same law in Western Australia:
Any person who wilfully and unlawfully destroys or damages any property is guilty of a crime and is liable — (b) if the property is not destroyed or damaged by fire, to imprisonment for 10 years…
And Queensland:
Any person who wilfully and unlawfully destroys or damages any property is guilty of an offence which, unless otherwise stated, is a misdemeanour, and the person is liable, if no other punishment is provided, to imprisonment for 5 years.
The same holds true for South Australia, New Zealand, Canada and the UK.
Victoria puts a subtle twist on it, using the present tense to describe the offence, but the future tense for the declaration of guilt. Tasmania is the sole outlier, using more antiquated language.
AN ABSURD SITUATION
What exists now is an absurd situation: the strictest laws for the most heinous crimes in the country are worded more respectfully than many of the IG policies in our organisations.
Ponder that for a moment. Going solely by the tone of voice, an employee could be forgiven for wondering if the office considers murdering one’s boss to be a less serious offence than putting documents on a C:\ drive. From a totally objective examination of the text, we speak more nicely to criminals than to our own colleagues. That’s just plain wrong.
There's no reason why IG policies can’t be worded more respectfully, and all practitioners need to be sensitive to the issue. As leaders, we cannot promote collaboration, inclusion, and respect, when a simple reading of the policies makes it clear that the real goal is old-fashioned obedience. The takeaway is clear: If organizations generally—and IG professionals specifically—are serious about supporting “respect” as a core, then we all need to walk the talk. Updating the tone in our organizational policies will encourage the engagement from others that is so critical to the success of the IG program.


ABOUT THE AUTHOR
Lewis S Eisen CIP, SIPC is the leading authority on the use of respectful language in policy drafting. He draws on over 25 years’ experience as a practising lawyer, business consultant, and federal civil servant. His Amazon international bestseller Rules: A Guide to Drafting Respectful Policies and Directives, is now in its third edition. Lewis has delivered two RIMPA webinars over the past year, and his approach to drafting policies using respectful language has been adopted at organizations around the world. Lewis Eisen, Ottawa, Ontario, Canada. Founder, Perfect Policies. Contact leisen@pfx.ca; www.lewiseisen.com/ www.linkedin.com/in/lewiseisen/
38 | iQ June 2024 INFORMATION GOVERNANCE



NOMINATIONS FOR THE Outstanding Achievements Awards are Officially Open




We are pleased to invite nominations for the Company Outstanding Achievement (COA) Awards, a prestigious accolade in the records and information management industry. These awards recognise trailblazers who have introduced innovative initiatives, authored insightful articles, and shown exceptional commitment to RIMPA Global.


Nominations Now Open! Submit your nominations between 3 June and 12 July 2024. The awards ceremony will take place at the elegant Black-Tie Gala Dinner and Awards Night during the RIMPA Live Convention in September 2024.
AWARD CATEGORIES INCLUDE:
J Eddis Linton Outstanding Individual of the Year is the highlight of the RIMPA Global award season, presented to an individual who has made a significant contribution to records and information management. As the pinnacle award bestowed upon an individual within the industry it recognises excellence to a superior standard. The recipients of this highly coveted award are role models from which we can all learn.

Join us in celebrating the outstanding achievements within our industry.

Pamela Hall Outstanding Group Award recognises remarkable contributions made by an organisation or group to their workplace practices, the RIMPA community or the records and information management industry.
Tom Lovett Outstanding Student Award is presented by RIMPA to recognise a student who has achieved excellence in their educational studies and this learning has impacted them and the RIMPA community and/or industry.
Julie Apps New Practitioner Award is presented by RIMPA to recognise the contribution an individual, who is new to the industry, has made either to their workplace practices or to the RIMPA community.
David Moldrich Outstanding Volunteer Award seeks to recognise Board Members, Ambassadors, RIMPA Committee and Working Group Members for their time and contributions to RIMPA Global in the year of the award and is a testament and thanks to the recipient's outstanding commitment to RIMPA Global. It demonstrates and recognises the importance of volunteering and giving back to the industry.
iQ Article of the Year rewards the author of an outstanding article from RIMPA's iQ Magazine.
Jim Shepherd Vendor of the Year recognises significant contributions to the records and information management industry and celebrates the vendor partners of RIMPA. Our vendor partners form the foundation of the opportunities provided to the RIMPA Global membership.
Whether it's a colleague, mentor, or professional team, your nominations will shine a spotlight on their dedication and accomplishments, reinforcing our commitment to excellence at RIMPA Global.
Let's make this awards season a memorable celebration of innovation and success. The BlackTie Gala will be a night to remember, honouring the exceptional talents and contributions in our community.
Together, we can celebrate the achievements that drive our industry forward! AWARD NOMINATIONS NOW OPEN!
RIMPA COMPANY AWARDS
Visit rimpa.com.au to nominate! NOMINATIONS NOW OPEN!

Records, Trust (And Lack Thereof)
BY STEPHEN BEDFORD
A discussion about duplicates, and why they are not always bad. Keeping records is a good way of building trust and mitigating against a lack of trust.
My first case story involved what I thought was an investigation into unnecessary duplication but turned into something else entirely.
CASE STORY 1
Late last century, I was conducting a recordkeeping survey for a business unit of the State Library of NSW. The library at that stage was keeping its records in paper.
I noticed that a moderate amount of storage space was taken up with copies of purchase orders. Taking a very “straight down the line” “single source of truth” and “storage and disposal approach”, I asked the record’s custodian why they needed to keep these copies. Why couldn’t they ask Finance for their copies if they needed to check something?
“Because we don’t trust Finance” was the response. “They keep allocating other branches purchases to our cost centre.”
The scales fell from my eyes.
40 | iQ June 2024 INFORMATION MANAGEMENT
Understanding record keeping requirements was very “trendy” in the profession in those days. The recordkeeping requirement for the central Finance copies was to meet the requirements of the Public Audit and Finance Act – this requirement expired after 6 years. The recordkeeping requirement for the local copy was to win arguments with Finance – this requirement expired 3 months after the end of the financial year (because you couldn’t re-journal mistakes after that).
The recordkeeping requirements were different – they were not duplicate records; they were different records.
BAD POETIC INTERLUDE - THE TAO OF RECORDS MANAGEMENT
During the 70s and 80s, Westerners often misappropriated Eastern philosophy, evident in works like "The Tao of Pooh" and "Zen and the Art of Motorcycle Maintenance." Here’s my attempt at a reinterpretation (inspired by Chapter 38 of the Tao Te Ching by Lao Tzu): "When the Tao is lost, there is goodness. When goodness is lost, there is kindness. When kindness is lost, there is trust. When trust is lost, there are records."
Records need to be kept by both sides of transactions and interactions between parties, partly to ensure that those parties agree with what happened, including any promises made and delivered. How many of us have been in the ultra-embarrassing situation of asking for a copy of a contract with a service provider because we have lost our own copy.
In larger organisations with competing priorities, cultures and ways of working, it may not be possible to have a “single source of truth”, where the custodian of that source has their own interests. Both “sides” need to keep records because of a lack of trust.
WHY ARE WE WORRIED ABOUT DUPLICATION IN THE FIRST PLACE?
This is the bit about duplicates if you haven’t already guessed.
Duplication has some positive features, redundancy in the face of loss or disasters is one of them. So, why are we so concerned about it? Why do many vendors offer identification and elimination of duplicates?
Storage /processing resources
This is a legitimate concern. In the physical environment I would contend that there is a more linear relationship between storage volumes and storage costs.
In the electronic environment, exponential growth has its own storage cost implications.
As well as costs, there are concerns about duplicates jamming up search results. Let’s investigate this concern in more detail.
• Partly this is caused by the “everything’s a record” approach which captures all documents into corporate records systems irrespective of their status (but that’s another discussion, see Problems with the Australian Approach to Records Management IQ December 2023).
• This also due to confusion about the status of duplicates – which is the authoritative version?
Whenever I see documents without business context in a recordkeeping system (e.g. documents saved into an EDRMS), I give a little sigh of disappointment.
Confusion about copies, versions and their status
When confronted with duplicate records, a common first thought is which is the “real” one? I would argue that if you need to ask that question, we have failed in our job as records managers. Why?
An important part of good recordkeeping is preserving the business context of the record.
This copy should have been captured with its business context (e.g. “this is the draft before it was submitted to the board”). The context can be through:
• The email which the copy is attached to.
• The MS Teams post linking to the document.
• The workflow step linked to the version in the business system.
• Or via some other means.
Records are overwhelmingly about communications.
Working in NSW, the requirements for business context about a communication come from s 71 of the Evidence Act 1995:
• The content of the message
• The origin
• The destination
• The date and time of sending.
Whenever I see documents without business context in a recordkeeping system (e.g. documents saved into an EDRMS), I give a little sigh of disappointment.
CASE STORY 2
Records management is often seen to be about legislative compliance.
This is not always the case, and I can prove it.
Let’s examine a form of enterprise where legal compliance is frankly the least of their motivations – a criminal enterprise.
One common trope in hardboiled detective stories, is that criminals maintain two sets of books: one to convince authorities they are legitimate, and a second set that reflects their true activities. If it's just about complying with legislation, why do they bother keeping the second set?
Again, it comes down to building (and enforcing) trust – in this case, honour amongst thieves.
No – this is not a personal case study, Officer.

ABOUT THE AUTHOR
Stephen Bedford spent 10 years as an archivist at the Archives Authority of NSW (now State Records), much of that time advising on records management matters. He then decided he probably should become a records manager, to understand what he was advising on. He has worked at the Reserve Bank of Australia, the NSW Department of Education and Training, the State Library of NSW, and the Australian Broadcasting Authority. He was the chair of the Records Management Classification Subcommittee IT21-09 of Standards Australia, and currently works for the NSW Department of Customer Service, Sydney, NSW.
iQ | 41 INFORMATION MANAGEMENT





































THANK YOU TO OUR INDUSTRY PARTNERS 2024 RIMPA GLOBAL Together We Succeed.
ARTIFICIAL INTELLIGENCE: The Next Frontier for Information Governance Experts
BY JIM MERRIFIELD, IGP, CIGO
In a world where data growth is exponential, and regulatory landscapes are constantly evolving, information governance stands as the backbone of a digitally resilient organization. For information governance professionals, mastering data management, compliance, and security has always been a complex jigsaw puzzle, but with the integration of Artificial Intelligence (AI), this intricate picture is becoming a bit more decipherable.
THE CRITICAL ROLE OF INFORMATION GOVERNANCE
Information governance is the strategic framework composed of policies, controlled objectives, and practices for managing information at an enterprise level, supporting an organization’s immediate and future regulatory, legal, risk, environmental, and operational requirements. Given its significance, integrating smarter tech like AI can redefine how this governance is conducted.
AI AS A CATALYST IN INFORMATION GOVERNANCE
AI is not just another tech buzzword; it’s a dynamic tool reshaping information governance. AI technologies, especially machine learning algorithms and natural language processing, are pivotal in streamlining data classification, proactively identifying compliance risks, enforcing policies, and enabling organizations to make more informed decisions. Not to mention, these tools are evolving to predict future governance needs based on unprecedented volumes and types of data analytics.

ABOUT THE AUTHOR
LEVERAGING AI FOR ENHANCED DATA MANAGEMENT
Imagine this: Through AI algorithms, information governance professionals can now automate the classification and tagging of data based on predefined criteria, which increases efficiency and reduces human error. Furthermore, AI-driven analytics can reveal insights into data usage and lifecycle, ensuring that data across all operation levels is harnessed responsibly.
As data continues to burgeon and legislative perimeters tighten, AI in information governance is not just an improvement; it's becoming essential.
SUCCESS STORIES OF AI-DRIVEN INFORMATION GOVERNANCE
It's not all theoretical; many organizations have already seen substantial advances through the marriage of AI with their information governance policies. A notable example is a healthcare provider that implemented AI to safeguard patient data and ensure HIPAA compliance. Through AI, they achieved greater control over sensitive information and improved auditing processes.
NAVIGATING CHALLENGES IN AI ADOPTION
Integrating AI undoubtedly can propel the information governance field forward, but it's not without its challenges. Governance professionals must consider accuracy, transparency, and ethical implications of AI.

There's also the task of keeping the human element in the loop for oversight and decision making, ensuring balance is maintained between human intuition and AI precision.
LOOKING AHEAD: AI IN THE FUTURE OF INFORMATION GOVERNANCE
The future sings tales of machine learning and predictive analytics becoming central to information governance. The predictive capabilities of AI could eventually forecast regulatory changes and suggest proactive alterations to compliance measures, maintaining a perpetual state of preparation against potential risks.
As data continues to burgeon and legislative perimeters tighten, AI in information governance is not just an improvement; it's becoming essential. While AI may bring its set of challenges, its benefits in cost-saving, risk reduction, and enhanced decision-making capabilities are too substantial to overlook. In this vein, it is incumbent upon information governance professionals to harness AI’s potential to steer organizations towards futuristic, data-driven growth.
CALL TO ACTION
For information governance professionals ready to leverage AI, now is the time to gear up and explore the full potential of this technology in transforming your data stewardship. Get in touch with solutions providers, invest in training for AI governance tools, and join forums to discuss strategies and share insights with your peers.
The future of data management is smarter and sharper with AI—are you prepared to be a part of it?
Jim Merrifield is a leading Information Governance Technology AI Influencer, Podcast Host, Keynote Speaker, and Data Privacy & Security Guru with nearly 20 years of experience. He currently serves as the Director of Information Governance & Business Intake at Robinson & Cole LLP and is the Vice Chair of the ARMA International Board of Directors. Jim hosts the "InfoGov Hot Seat" podcast, featuring insightful discussions on information governance challenges and trends. He is skilled in enterprise program deployment, policy development, and technology solution evaluation. Jim holds certifications as an Information Governance Officer (CIGO) and an Information Governance Professional (IGP).
iQ | 43 ARTIFICIAL INTELLIGENCE


What can Artificial Intelligence do for Content Management?
BY GWENDOLINE HURET



Trending Tech Topic of 2023 – at OpenText and Everywhere. With the New Year just in, it is a good opportunity to reflect on the past year and expected trends for 2024. You don’t get a prize for guessing the most obvious trending tech topic of 2023: Artificial Intelligence (AI).
At OpenText, AI has certainly become a constant buzzword, with our CEO Mark welcoming us to “the AI Revolution”. Mark believes that AI will dominate the tech industry going forward and is adapting OpenText strategy accordingly. It is important to highlight he is also focused on ethical AI, but that is another topic.
Whenever a trending tech topic becomes so big that even those outside the tech industry know about it, product managers expect only one thing: for all our customers to ask us where the technology fits into product roadmap. This year, the number one thing customers have wanted to discuss is Artificial Intelligence.


The use of trending technology within roadmaps and product releases reassures customers, as it shows both an investment in the product and a forwardthinking strategy. Concretely, a product with trending tech in the roadmap is more likely to deliver future value and still be around in a few years. Customers like innovation partly because it guarantees a better return on investment. Engineers like it because it’s fun.




The risk with a trending tech topic is that of innovation for the sake of innovation. A good product manager will know (and if they forget the engineers won’t fail to remind them) that everything comes at a cost. Most products have more ideas than resources, and effort invested in one feature means effort not invested in another. Furthermore, new tech often comes with significant performance and energy consumption impacts (cryptocurrency anyone?). That’s why product managers are taught to always convert features into value-add to the customer.
So, whilst customers are always eager to hear about artificial intelligence, we need to ensure we are directing the conversation in the right direction, by focusing on the value-add. This article aims to ask exactly this: What can artificial intelligence do for Content Management? What value can it bring, and what use cases make the investment worth the cost?

ARTIFICIAL INTELLIGENCE
44 | iQ June 2024














Whenever a trending tech topic becomes so big that even those outside the tech industry know about it, product managers expect only one thing: for all our customers to ask us where the technology fits into product roadmap.

iQ | 45 ARTIFICIAL INTELLIGENCE
















A NEW AI-TRANSFORMER TRAINED LARGE LANGUAGE MODELS
November 2023 marked the 1-year anniversary of the public release of ChatGPT. Chat GPT (an OpenAI product) showed the general public the capabilities of a large language model (LLM) trained to leverage context. Its ability to converse to appear human is what put artificial intelligence back in the spotlight.


If you are familiar with the Turing test (a test of a machine’s ability to pass as human, defined back in the infancy of artificial intelligence), you might be surprised to recall that the first software to pass the Turing test did so in 2014 . However, the test only requires 30% of those who converse with the chatbot to believe it to be human, and the 2014 software passed with a 33% score. Modern LLMs bring AI to another level, almost making the Turing test irrelevant.
For the anecdote, last year I was sent a birthday card filled with text generated by a large language model, as a joke from a friend. The card passed the Turing test with flying colours, and it was only after I’d finished complimenting how thoughtful the message was that I was informed it had been generated by AI (after submitting some facts to the algorithm of course).
Chatbots and artificial intelligence have been around for a long time, driven by neural network models. The strength of these new large language models is the “transformer” technology (the T in GPT for example) that allows a neural network to use the location of a word in a sentence to gain a deeper understanding of the word. In other words (neural network pun), leveraging context to achieve meaning. Transformers were invented in 2017 by Google researchers. It is transformer technology combined with unsupervised machine learning that makes modern AI generated content so human-like and credible.

When ChatGPT was released, it went viral, setting a record for the fastest growing user base linked to a consumer application in history. AI can now pass as human, and the benefits are overwhelming. The focus has now moved from using AI to solve single-context problems (such as building a machine capable of beating any human player at chess), to looking to build a “general purpose, multi-skilled” AI.
ChatGPT made transformer trained LLMs famous, and now tech companies worldwide are developing their own versions of such language models as well as tools to support the generation of AI models. OpenText has the “Aviator” series, Amazon is offering AWS “SageMaker” to help train large language models, and Microsoft Azure “DataBricks” supports LLM creators throughout the AI lifecycle.

With New AI now mainstream, how should software products in the Content Management space leverage this technology?
WHAT DOES THIS MEAN FOR CONTENT MANAGEMENT?
When using any technology, it is always important to ask what problem we are trying to solve.
Artificial Intelligence is currently adding value in many industries. In business and entertainment, content is being auto generated. In healthcare, diagnostics are being made. In Education, virtual teachers exist.
What value does artificial intelligence bring to the Content Management space?
If we ask ChatGPT 3.5, it provides an incredibly accurate summary of describing the advantages AI can bring to the Content Management space: See Figure 2 Screenshot from chat.openai.com
All the points raised above are great examples of use cases where AI can strengthen a Content Management roadmap.
In this article we will explore a few of these examples and raise others.
46 | iQ June 2024 ARTIFICIAL INTELLIGENCE




AUTO-CLASSIFICATION AND DATA-ENRICHMENT
One of the most common problems that customers with large quantities of data have been how to classify such data. Classification is essential, because it then allows you to apply data policies based on the classification. Policies could be security or lifecycle related, for example determining who has access to a document or when it will be automatically and safely deleted for compliance reasons. Content Management software does a great job of allowing for flexible configuration of classifications and from there defining security and lifecycle policies. However, the implementation and maintenance phase of such software projects always beg the question: how do I classify my content? How do I classify the large amount of data I’m going to first ingest into such a tool, and then as data gets created daily, how will it be input into the tool?
Some organisations still go for user-based manual classification, but the obvious answer is to automate the bulk of the data classification using technology. Userdependent classification systems almost always result in under-reported content (compliance is not usually top of mind in a business user’s daily priorities, and people are known to avoid extra tasks if they can). Not to mention the human errors: auto-classification will usually lead to higher amounts of content being correctly classified.
What benefits can AI offer in the way of content management?











This is an area where machine learning excels. Artificial intelligence can learn based on training, so it can take human-classified samples and from there classify the rest of your data. The standard procedure is to then mix that with some “simpler” classification rules, like looking for specific keywords or metadata values (ex: age of the file). The combination of simple rules and the machine learning classification that learns over iterations should lead to a classification with a lower margin of error than had it been classified by an end user.
Look for a solution that provides an intuitive interface for the training of the classification algorithm, such that even a non-technical or business user can feel comfortable using it. A good tip is to have the ability to test how a specific file would score for a specific category, or what category it would be classified into. Have the ability to tweak the confidence levels and the desired false positive rate. You may have a scenario where it is of extreme importance to detect any potential high-risk file, and the false-positive rate would then be higher in order to ensure nothing is missed. Alternatively, you may be filling in such large quantities of data that precision is of more importance. Just as important as the algorithm then, is the training interface, and the ability to modify the algorithm parameters in an intuitive manner from that interface.
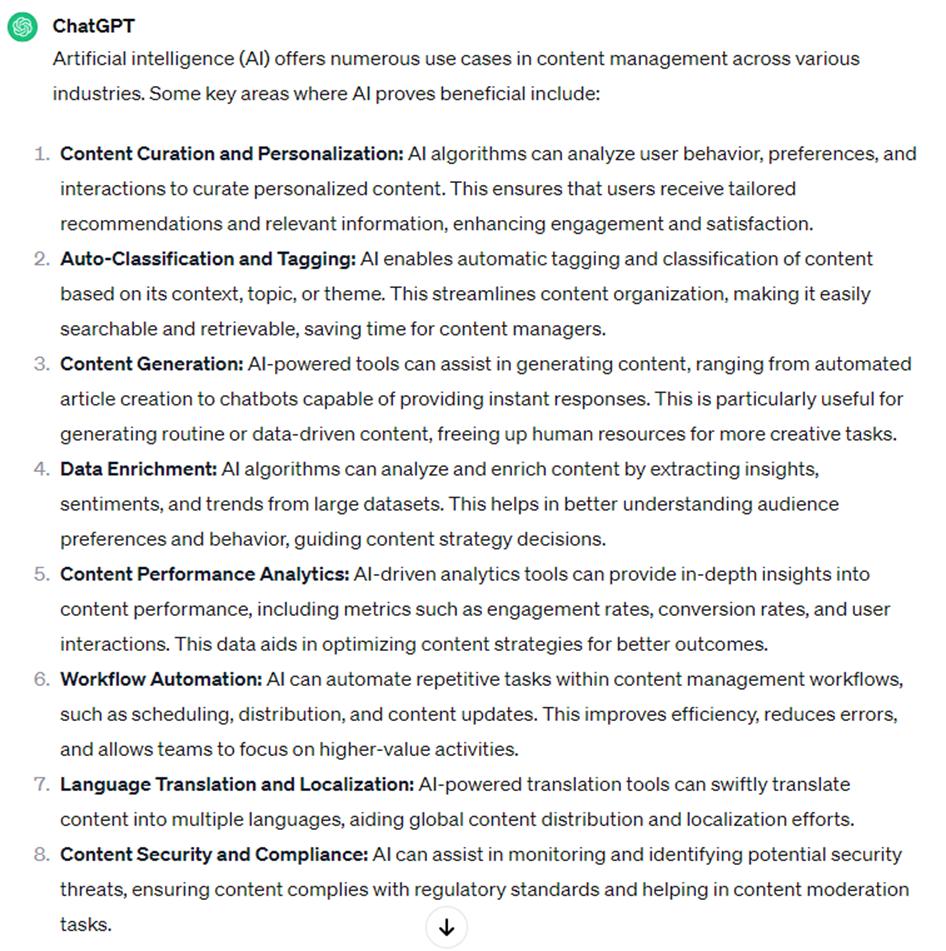












iQ | 47 ARTIFICIAL INTELLIGENCE
FIGURE 2 SCREENSHOT FROM CHAT.OPENAI.COM PROMPT:
Classification can also be taken a step further, leading us into the data-enrichment space. Data Enrichment is the ability to extract valuable information from a document and add this as metadata to the document. The metadata can then more easily be flagged or searched on. For example, doing data enrichment that extracts the name of organizations from a document, would then allow you to more quickly search for any content that references a specific company. IDOL is a great example of an auto-classification and data enrichment engine, which powers the software solution Content Manager.
WORKFLOW AUTOMATION
On the topic of artificial intelligence performing better than a human: another area where artificial intelligence should assist in document management is via suggestive actions. If a human user is planning on applying an action, or simply selecting an option from a dropdown that would determine an aspect of how content is managed, artificial intelligence could suggest which option is more suitable based on the user’s past behaviour, but also based on his colleague’s past behaviours. Most workflows still require human interaction, but artificial intelligence has a lot to offer in suggesting and changing the order of options available to the human reviewer. This could apply to various scenarios:
- Human inputting data into a content management system.
- Human creating a new record.
- Human configuring security settings.
BUSINESS INTELLIGENCE
The same technology behind auto-classification is capable of finding similar documents to the one you are working on. This “find similar” will obviously include basics like file format and metadata, but the more advanced options will also consider content. This is where artificial intelligence and the ability to understand context come into play. If you have a document discussing the effect of climate change on penguins, you don’t want this linked to a financial review of the Penguins editor company. The ability to understand words in context should be the strength of your auto-classify/find similar algorithm.
In general, a better understanding of your data will add to the business intelligence you extract from your data. This ability to find similar or relevant documents has many use cases:
- The case of duplicate cleanup or system cleanup. Find duplicates and delete them and find old versions of content and delete them or link them to the original. This use case traditionally can deliver large ROI to companies.
- Link related items together to gain business insight.
- Find related documents when creating content in order to increase document creation speed.
CHATBOT DIGITAL ASSISTANT: SEARCH, EXECUTE, REPORT, AND TRAIN
Artificial Intelligence can power chatbots capable of conversing like a human, and it can also help you to locate data by supporting natural language type of search queries. So, rather than build a Boolean search query using a complex search builder, you could ask your content management solution a question similarly to how you would talk to a colleague, and it will locate what you are asking for.
We could imagine “conversations” with your content management solution such as:
- “find me the document I was working on yesterday”
- “locate all records related to the Smith client matter”
- “Has this client previously filed a request for information”?
As you can see, these requests could go a stage further than searching for existing records, they could also provide general information for you about your content management strategies and statistics. This type of reporting is another area that AI can enhance. Reports can flag up anomalies in behaviour automatically, such as when an employee’s content creation rate is suddenly changing, or if certain metrics won’t be met.
Such a “chat-bot” would essentially be a digital assistant, capable of many actions.
A chatbot such as described above would also be invaluable for end user training and support. So often customers have a great tool but complain about uptake because the end user doesn’t have the time or inclination to learn a new software. These customers have spent money on a solution that could bring great value if it were properly used, but sometimes instead it causes pains to the IT and support department. Chatbots in a content management solution could suggest help, could answer questions, and suggest training videos or actions based on what the end user is asking.
THE FUTURE IS HERE
I couldn’t write an article on artificial intelligence without asking an AI powered chat-bot to conclude for me. Above you can see the conclusion generated by OpenAI’s ChatGPT 3.5. I could have fed my whole article into the command and gotten a sharper conclusion, but I had to be mindful with my sensitive data, because OpenAI is not my product.
When your Content Management tool uses AI, with authorized access to your sensitive data and your past behaviours, you can be sure the results will be even more impressive.

ABOUT THE AUTHOR
Gwendoline Huret has over 10 years of experience in Enterprise Software for Data Management and is now working as Product Manager at Opentext. She has specialized in privacy and cyber-security since the start of the GDPR in 2016. She has worked on data management projects across the globe, from coding to sales to product management. Gwendoline has a Masters in Mathematical Engineering and is based in Madrid, Spain. She has dual French and British nationality.
48 | iQ June 2024 ARTIFICIAL INTELLIGENCE
Content Chronicles
Your Quarterly Digest of Blogs, Newsletters, and Essential Links
This page will be a regular feature of iQ and is carefully curated by, and for, our community members. It's designed to boost our collective knowledge and efficiency by staying up-todate with the ever-evolving world of Records Management.
BULLETINS AND NEWSLETTERS
GAIN Australia (Government Agencies Information Network)
www.naa.gov.au/information-management/gain-australia
The Data Administration Letter www.tdan.com
Dataversity www.dataversity.net
State Records NSW www.staterecords.nsw.gov.au/guidance-and-resources/the-record-enewsletter
Public Records Office Victoria www.prov.vic.gov.au/explore-collection/publications/current-newsletters
WA State Records Office www.wa.gov.au/organisation/state-records-office-ofwestern-australia/state-records-office-newsletter
BLOGS
Digital Preservation Coalition www.dpconline.org
IRMS Blog - Information and Records Management Society UK www.irms.org.uk/blogpost/1576087/IRMS-Blog
Gaia Resources www.gaiaresources.com.au/blog
Think Clearly Blog | Lucidea www.lucidea.com/blog
Arkivum www.arkivum.com/blog
British Library Collection Care www.britishlibrary.typepad.co.uk/collectioncare www.britishlibrary.typepad.co.uk/endangeredarchives
Andrew Warland - Focus on Microsoft 365 www.andrewwarland.wordpress.com
NAA Records Search www.recordsearch.naa.gov.au/SearchNRetrieve/ Interface/SearchScreens/BasicSearch
Stories from the Archives www.blogs.archives.qld.gov.au
Trends in record Management www.restore.co.uk/Records/Resource-Hub/News/ category/document-storage-news
Database Trends and Applications (DBTA) www.dbta.com
KDnuggets on Data Management Crystal Ball www.kdnuggets.com
PODCASTS
Make Data Talk: Hosted by Dr Selena Fisk www.selenafisk.com/podcast
Making Data Simple: Hosted by Al Martin from IBM www.youtube.com/channel/UC5hGeG0Npnu7NOKzuajXm0w
Information Innovation: Hosted by M-Files www.podcasts.apple.com/us/podcast/informationinnovation-podcast/id1462958933
UNSECURITY - Information Security Podcast: Hosted by Evan France and Brad Nigh www.podcasts.apple.com/us/podcast/unsecurityinformation-security-podcast/id1442520920
iQ | 49 RIMPA NEWS RESOURCES
valuable contributions! Your expertise can help elevate our shared resource pool. Submit
suggestions to admin@rimpa.com.au.
GLOBAL
We're on the lookout for
your
RIMPA

Capability Statement
Social Enterprise solutions
Why use Ability Works?
RIMPA Global proudly partners with Ability Works Australia We are dedicated to fostering inclusivity in records and information management. Together, we're shaping a diverse community where everyone thrives professionally. Explore Ability Works' impactful initiatives at abilityworks.com.au and join us in building a more inclusive future for our profession.
At Ability Works we believe employment is the best way for people living with a disability or experiencing social disadvantage to achieve a sense of purpose, pride and belonging
Everyone deserves the same opportunities to work People living with a disability and/or who experience social disadvantage face significant barriers to employment.
Ability Works breaks down those barriers by offering our 180+ staff, training and employment alongside expert support that is tailored to their needs and the requirements of our customers





As a social enterprise, meeting our social mission of “Purpose through Employment” is as important to us as commercial outcomes
This is why we partner with organisations and companies that are equally committed to empowering lives at the same time as producing great quality products and generating business value and creating meaningful employment opportunities
87 075 933 612
www.abilityworks.com.au ABN:
Our Accreditations and Certifications
RIMPA GLOBAL 50 | iQ June 2024

Records Management
We are experts in this rapidly evolving commercial area Records management workflows require focus and repetition that align perfectly with the skills of our employees. We also embed the latest information technologies and tools into our processes to support our people and achieve the highest quality control and security standards for our clients.
Services include:
Digitisation of archives and records using our highspeed scanners and standalone data servers
Secure record destruction and disposal
Mail room services up to 1,200 items per day
Client benefits include:
Digitising records and files offers security, access and control for records on SharePoint or similar centralised corporate databases
Eliminating the cost of storing and maintaining records and files
Eliminating future degradation or loss of records
Lower fixed costs of mail room services
Creating social procurement credits
Over 500 hours of purposeful employment opportunities for every $10,000 spent with Ability Works
Talk to us about designing an effective records management plan for your business!
Customers include:
The Department of Defence record preparation, scanning, quality assurance, coding, digitising
“Ability Works has worked hard to meet the high standards we expect for our digitisation project. We look forward to continuing with this meaningful employment through our partnership” - Mardi Jarvis Assistant Secretary Regional Services, DOD
Transurban – mail receipt, sort, batch, scan and disposal of e-tags
“Transurban has successfully partnered with Ability Works for the past ten years. We’re extremely satisfied with the exemplary service and commitment delivered for our customers” – Darren Wallen, Head of Channel Management
Relationships Australia ( Victoria ) – record preparation, scanning, coding
iQ | 51
ACA PACIFIC
VENDOR DIRECTORY


ACA Pacific is a leading distributor of Document Scanners, Capture Software and Information Management solutions, designed to fast track your path to Digital Transformation. As the distributor for Kodak Alaris Scanners and Software, ABBYY solutions, Contex & Colortrac Wide-Format Scanners and GetSignature eSign solution, we can digitise just about any size and type of document, making it easy to store, share and manage business ready information. Deliver powerful benefits and real-world value to any job function and organisation.
Locations: Melbourne, Sydney, Brisbane, Perth, Auckland Ph: 1300 761 199 | E: imagingsales@acapacific.com.au | W: acapacific.com.au
AVEPOINT

Collaborate with confidence. AvePoint provides the most advanced platform for SaaS and data management to optime SaaS operations and secure collaboration. More than 8 million cloud users rely on our full suite of solutions including records & information management to make them more productive, compliant and secure. Locations: Sydney, Melbourne Ph: 03 3535 3200 | E: au_sales@avepoint.com | W: avepoint.com
COMPU-STOR
Compu-Stor is a family-owned Australian business specialising in information and records management solutions and services. From document, media & data storage to digital scanning, business process automation and consulting services, Compu-Stor provides a wide range of solutions using the latest technologies & methodologies to deliver secure & efficient services. Through its Digital Transformation Solutions, Compu-Stor helps maximise the accessibility of information within organisations. Compu-Stor works with its customers to provide costeffective solutions tailored to their needs. Locations: Across Australia Ph: 1300 559 778 |E: sales@compu-stor.com.au | W: compu-stor.com.au
CORPMEM

FUJI FILM
We see ourselves as your strategic business partner, not just another supplier. As the cost of running your business continues to rise and your customer’s preferred source of communication becomes digital, we have developed innovative solutions to help you adapt efficiently and effectively, not only in today’s environment but for the future. We recognise it is no longer viable to be just ‘another supplier’. Our focus is to truly understand your business challenges and strategic direction so we can support you as a trusted business partner.
Ph: 0481 009 779 | E: john.cox.ez@fujifilm.com | W: www.fujifilm.com/fbdms
GRACE INFORMATION MANAGEMENT

Grace ensures business information is managed as the high-value asset it is, throughout its lifecycle — Capture, Control, Storage, Access, and Secure Disposal. Established in 1911, Grace operates a national network of 28 branches across every capital city and major regional centre, each equipped to provide best-in-class secure physical records and specialist digital information management solutions. Partnering with Grace ensures information is expertly managed, whilst our digital specialists provide tailored transformation pathways to increase digital maturity. Locations: Across Australia Ph: 1800 057 567 | E: GIM-sales@grace.com.au | W: grace.com.au/information
ICOGNITION

iCognition is an Australian SME and the trusted advisor of choice to our clients for enterprise-wide information management and governance, consultancy and solutions implementation. We provide IMG services and software to government, not-forprofit, education and private sector enterprises across Australia and overseas. iCognition’s goal is to ensure enterprises maximise the value of their information, while minimising cost and risk. Locations: Canberra, Sydney, Adelaide and Brisbane Ph: 0434 364 517 | E: Nicholas.Fripp@icognition.com.au | W: icognition.com.au
IGNITE

CorpMem Business Solutions specialises in the MAGIQ Documents EDRMS and provides a wide range of services focused on improving your business by increasing the Return on Investment (ROI) made to deliver records management. InfoVantage is our flagship software designed to create a Records and Information Management Knowledge Platform that leverages off and integrates into whatever corporate EDRMS you have implemented. CorpMem converts their clients’ corporate memory into a knowledge asset. Location: Caloundra Ph: (07) 5438 0635 | E: hello@corpmem.com.au | W: corpmem.com.au
EZESCAN
EzeScan is one of Australia’s most popular production capture applications and software of choice for many Records and Information Managers. Solutions range from centralised production records capture, highly automated forms and invoice processing to decentralised enterprise digitisation platforms which uniquely align business processes with digitisation standards, compliance and governance requirements. Contact: Demos Gougoulas, Director Sales & Marketing | 1300 393 722
EXEDEE

Ignite has been assisting public and private sector organisations with talent services since 1984. We provide Specialist Recruitment (IT, Federal Government, Business Support & Engineering), On Demand (IT managed services) and Talent Solutions (RPO, Training, recruitment campaigns & talent management services). For four decades, we’ve been igniting the potential of people and have built a reputation as Australia’s trusted talent advisor. Locations: Sydney, Western Sydney, Canberra, Melbourne, Perth Ph: 02 9250 8000 | E: Catherine.hill@igniteco.com | W: igniteco.com
INFORMATION PROFICIENCY


Information Proficiency is a Records and Information Management specialist providing a full range of services and software. We cover everything IM; from strategy to daily operational processing practitioners, full managed services, technical support and helpdesk, training, software development, data migration, system design and implementations. We work with many IM products including MS365, e-signature, workflow, scanning, reporting and analytics. We also develop a range of productivity tools and connectors. We work hard to understand your requirements and implement solutions to match. Services available in all states and territories. Locations: Perth, Western Australia Ph: 08 6230 2213 | E: info@infoproficiency.com.au | W: infoproficiency.com.au

Make your business process more efficient and exact! Are process inefficiencies and data inaccuracies weighing your team down and causing errors? Do you currently achieve a data extraction accuracy of over 99%? Are you under pressure to improve outcomes while reducing costs and processing time? Are you looking for an easy, effective, and proven solution? Get the exact business process automation eSolution for your needs, with a team of dedicated experts supporting you. Talk to the Exedee team today! Ph: 1800 144 325 (Melb) | W: www.exedee.com
FYB
At FYB our customer promise is to provide secure, easy to use, leading edge technological solutions, to enable organisations to harness the power of their information so they can provide excellent services to the community. We’ve stayed true to our core beliefs—to deliver the best information governance, systems and solutions to our customers.
Ph: 1800 392 392 | E: info@fyb.com.au | W: fyb.com.au

IRON MOUNTAIN

Iron Mountain Incorporated (NYSE: IRM), founded in 1951, is the global leader for storage and information management services. Trusted by more than 225,000 organisations around the world, and with a real estate network of more than 85 million square feet across more than 1,400 facilities in over 50 countries, Iron Mountain stores and protects billions of valued assets, including critical business information, highly sensitive data, and cultural and historical artefacts. Ph: 02 9582 0122 | E: anita.pete@ironmountain.com | W: ironmountain.com
IPLATINUM
iFerret is a turnkey enterprise search solution developed by iPLATINUM that works like "google" over your corporate data. iFerret enables you to find information quickly across your enterprise. Location: Sydney, Melbourne Ph: 02 8986 9454 | E: info@iplatinum.com.au | W: iplatinum.com.au

52 | iQ June 2024
LTD

Leadership Through Data provide Microsoft 365 focused information and records management training that has been developed by information and records managers to Australian and New Zealand Records Standards. Our core offerings are designed to help Information and Records Managers make sense of Microsoft 365 so that strategy and policy can be developed with a true and accurate understanding of the platform’s capability. Our SharePoint Foundation offering helps with understanding the core of M365 before providing education in specific aspects – Records Management, Information Protection and Privacy Management, and Information Architecture. E: jacqueline@ leadershipthroughdata.co.uk | W: leadershipthroughdata.co.uk
OBJECTIVE

Objective Corporation - Powering digital transformation with trusted information. With a strong heritage in Enterprise Content Management, regulation and compliance, Objective extends governance capability throughout the modern workplace; across information, processes and collaborative workspaces with governance solutions that work with Objective ECM, Micro Focus Content Manager and Microsoft 365. Through a seamless user experience, people can access the information they need to make decisions or provide advice from wherever they choose to work. Locations: Australia: Sydney, Wollongong, Canberra, Brisbane, Melbourne, Adelaide, Perth; New Zealand: Wellington, Palmerston North Ph: 02 9955 2288 | E: enquiries@objective.com | W: objective.com.au
OPEN TEXT

OpenText, The Information Company™, enables organisations to gain insight through market leading information management solutions, powered by OpenText Cloud Editions. OpenText is one of the world’s largest global software providers, delivering mission critical technology to empower 125,000 customers across 180 countries. We believe that companies of all sizes can be smarter by bringing information and automation together and delivering smarter outcomes by helping customers BUILD, AUTOMATE, CONNECT, SECURE, PREDICT and ACT. Ph: 02 9026 3400 | W: opentext.com
PROFESSIONAL ADVANTAGE
Since 1989, Professional Advantage has excelled as a top IT solutions provider and Microsoft Solutions Partner in Australia, specializing in modern work, cloud, security, financial management, and business intelligence for various sectors. As an exclusive iWorkplace/ Information Leadership Partner, we leverage Microsoft 365 for effective digital workspaces, information management, and data governance. Our skilled team, boasting a high NPS and long client relationships, operates across 7 offices in 3 countries, serving over 1000 clients globally. Ph: 1800 126 499 | E: enquiries@pa.com.au | W: www.pa.com.au
RECORDPOINT
Founded in 2009, RecordPoint is a global leader in cloud-based information management and governance services. Our adaptable layer of intelligence offers complete insight and control over all in-place data, records, and content, enabling organisations to increase compliance and reduce costs. RecordPoint enables regulated companies and government agencies to reduce risk, achieve greater operational efficiency, and drive collaboration and innovation. Ph: 02 8006 9730 | E: salesapac@recordpoint.com | W: recordpoint.com
RECORDS SOLUTIONS

VENDOR DIRECTORY
TIMG - THE INFORMATION MANAGEMENT GROUP

TIMG (The Information Management Group) has been in the Information Management business for more than 20 years. We are known as a company that solves Information Management problems and, as such, we remain committed to providing innovative, smart and cost-effective information management solutions for our clients. As the digital world rapidly evolves, we remain committed to helping clients accurately store, track, access, retrieve and cull data. Some of the services we offer include document conversion and digitisation (including scanning, printing and data capture), document storage and archiving solutions, sentencing, secure document destruction, Ph: (02) 9305 9596 | E: info@timg.com | W: timg.com
VOTAR PARTNERS
Votar Partner's number one priority is our clients. Working independently of all software and IT vendors, we offer our proven and specialised expertise to empower our clients to achieve their goals. Our subject matter experts can help you develop and implement practical initiatives across each stage of the information management lifecycle, ensuring that your records and information management practices support and enable business improvements, and remain relevant.
Ph: (03) 9895 9600 | E: votar@votar.com.au | W: votar.com.au
WYLDLYNX


WyldLynx – We take your business personally. WyldLynx provides Information Management, Governance solutions and services using a unique blend of cutting-edge technology, real world experience and proven industry principles. This allows Organisations to manage their Information, Security, Privacy and Compliance across enterprise systems with reduced risk, complexity, and cost. WyldLynx has a reputation for delivering value through long term relationships built on trust, shared vision, and a continual investment in relevant innovation. Locations: Brisbane Ph: 1300 995 369 | E: contact@wyldlynx.com.au | W: wyldlynx.com.au
ZIRCODATA
A market leader in Records and Information Management, ZircoDATA provides secure document storage and records lifecycle solutions from information governance and digital conversion through to storage, translation services and destruction. With world class Record Centres nationally, we deliver superior service and solutions that reduce risk and inefficiencies, securely protecting and managing our customers’ records and information 24 hours a day, every day of the year. Locations: HQ Braeside, Victoria Ph: 13 ZIRCO (13 94 72) | E: services@zircodata.com.au | W: zircodata.com.au


Records Solutions is an Australian-owned company, founded in 1994. Created BY Information Managers FOR Information Managers, our team provide records and information management solutions to the industry. As a software neutral vendor, our only concern when working with you is what is best for you. With a Quality Management System developed in accordance with AS/NZS ISO 9001:2016, we aim to assist you in achieving the best outcome for your project. Locations: Brisbane Ph: 1300 253 060 | E: admin@rs.net.au | W: rs.net.au

iQ | 53
Connect with RIMPA’s Vendors




















54 | iQ June 2024
Lisa
Director 2022-2024 Strategic Pillar: Advocacy & Collaboration Nancy Taia MRIM Director 2022-2024 Strategic Pillar: Member Engagement
Moldrich Life FRIM Elected Board Director Strategic Pillar: Standards Meryl Bourke Life MRIM Elected Board Director Strategic Pillar: Member Engagement Paris Reddy Appointed Board Member 2024-2026 Director for Finance Ruth Edge ARIM Appointed Director 2023-2025 Strategic Pillar: Professional Development David Pryde Life MRIM Director 2022-2024 Strategic Pillar: Innovation and Standards
Bonita Kennedy Life ARIM Chair of the Board / Director
Read White Life FRIM
David
Anne Cornish MRIM Chief Executive Officer
Executive
and Finance
Sunshine Craig
Assistant
Officer
Khobi Ryan Member Relations and Services Officer
Membership
Tynelle Spinner
Engagement Manager
Joanne Kane Chief Operating Officer
Sarah Edwards Digital Marketing Coordinator Lisa Janell Marketing and Events Manager
Munaa Said Principal Trainer and Assessor
Vice Chair of the Board Strategic Pillar: Advocacy & Collaboration Peta Sweeney FRIM Content and Information Specialist Leadership and experience form the backbone of RIMPA's board. MEET THE
MEET THE TEAM BEHIND THE SCENES RIMPA GLOBAL CENTRAL OFFICE Contact the RIMPA Global team admin@rimpa.com.au RIMPA’s Board of Directors bring decades of industry insight and a wealth of experience, who formally represent the organisation.
Adil Afif Trainer and Assessor Otto Guardian of Information Officer
Jeremy Manford
BOARD

DO YOU GET 99% ACCURACY FROM YOUR DATA EXTRACTION?
In the dynamic records and information management landscape, it is crucial that you can trust any data that is imported during your business automation processes. We can deliver 99% accuracy to you.
Exedee software is driven by the “power of e” – we make anything to do with digitisation of records and business information processing easy, effortless, exact and efficient
Efficiently digitalises tens of thousands of documents in a short time
Effective governance demonstrated through complete and accurate metadata
Ensures you stay in control of information with a single source of truth for each document and a reliable search index
Enables increase in document transparency, accessibility and data quality
We put our energy and expertise into enabling all types of organisations to manage process automation and digitisation with ease – and with 99% accuracy
Talk to the Exedee team of experts today, and find out how we can help you.
Visit www.exedee.com and register your interest.

99% data extraction accuracy

















RECORDS AND INFORMATION MANAGEMENT PRACTITIONERS ALLIANCE PRESENTS: Elevate Your Expertise • Visit rimpa.com.au 3-5 September BOOK NOW! REGISTRATION OPEN I'M The Next Wave: Leading the Future Be the Navigator of Change. Be the Future of Information Management. 3- 5 September, Adelaide Convention Centre, South Australia Industry Partners 2024 DIAMOND GOLD SILVER BRONZE PLATINUM RIMPA Live 2024 Sponsors, Partners & Exhibitors EXHIBITORS EXECUTIVE SPONSOR PRINCIPLE PARTNERS




























 ANNE CORNISH LIFE MRIM CEO RIMPA GLOBAL
ANNE CORNISH LIFE MRIM CEO RIMPA GLOBAL