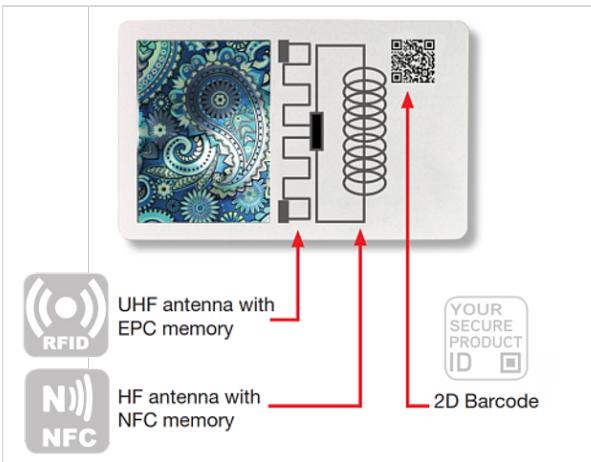
1.2 An introduction to the evolution of technology solutions for securing the products’ supply chain ‘Covert’ security elements were traditionally restricted to authorized stakeholders such as producers, brand owners, or enforcement officials, yet an increasing number of security elements can be authenticated by smartphones (for example, digital watermarks, copy detection patterns, Near Field Communication (NFC)). As a result, it has become common practice to let consumers, as well as other supply chain intermediaries and retailers, verify the authenticity of covert authentication elements. The above technologies mainly serve the purpose of authenticating a product or, more often, its packaging, telling if it is genuine or not. To control products’ movements along the supply chain, track and trace technologies are needed and the combination of authentication and track and trace may serve as a more effective barrier to the infiltration of fake and illegitimate products within the legal supply chain. Several types of authentication elements can be used to distinguish authentic goods from phony items, including holograms, colour-shifting inks, security threads, QR codes, data matrix codes, micro-printing, anti-forgery inks, bar-code technology, digital watermarks and copy detection patterns, to mention a few. On the other hand, tracking and tracing mainly relies on two identification methods: optical barcodes (e.g. QR codes, data matrix) and radio frequency identification (RFID), which can be applied either separately or jointly and with optical identification methods being more widespread. QR codes and data matrix codes may however be used for authentication if used in combination with an authentication element which is verified simultaneously.11 Operationally, and for both optical and RFID technology, the process of securing and controlling the movement of products with authentication and track and trace may start as early as the manufacturing stage and may continue in the distribution and retail phases, depending on the type of product, the producer/government’s requirements, and the relevant regulations in place12.
1.2 An introduction to the evolution of technology solutions for securing the products’ supply chain The technological evolution in supply chain security mechanisms has been combined with the progressive transformation of industries which were facing the need to quickly circulate mass market products globally while controlling their location and protecting from a series of evolving threats posed by criminals to the integrity of the supply chain. Two examples can be briefly mentioned to show how technology evolved in the area of supply chain security. The first one relates to rapid technology evolution in relation to tools to authenticate and subsequently track and trace products. The second one refers to the possibility of adapting tools initially created for specific purposes (tax collection in this specific case) to a modified criminal environment, where the purpose of collecting taxes progressively met the purpose of protecting the integrity of the supply chain.
11
For more information see: The European Observatory on Infringements of Intellectual Property Rights (EUIPO). (2021). AntiCounterfeiting Technology Guide. Retrieved from https://euipo.europa.eu/tunnel-web/secure/webdav/guest/document_library/ observatory/documents/reports/2021_Anti_Counterfeiting_Technology_Guide/2021_Anti_Counterfeiting_Technology_Guide_en.pdf
12
A complete overview of these elements can be found in the 2016 report “Ensuring supply chain security: the role of anticounterfeiting technologies”. The report was published in 2016, consequently, the information presented might not consider the latest developments in technology. The present report focuses on current risks and possible responses, including the presentation of innovative submissions based on up-to-date technology solutions. To access the previous report, see: UNICRI (2016), “Ensuring supply chain security: the role of anti-counterfeiting technologies”, http://www.unicri.it/index.php/ensuring-supply-chains-securityrole-anti-counterfeiting-technologies
10