2.2 Supply Chain Security Solutions to address the risk scenarios In order to achieve this goal, the criminal group implemented the following criminal business model: Step 7.
Control of legitimate e-operators: through one of the companies that it partially controls, the criminal group infiltrates two popular e-supermarkets which fall under its control. The well-established reputation of these two e-supermarkets will help the group to gain competitive advantage in the e-market of food, given that customers are becoming increasingly concerned by the risk of online fraud, especially with the smaller online shops.
Step 8. Selling fraudulent food as genuine: the criminal group uses the e-supermarkets to sell fraudulent products. First, it copies the design, packaging and trademark of well-known producers. Then it replaces the authentic products with low-cost products that disregard any food safety standards; or with food products that have expired or nearly expired. Step 9. Expansion of e-commerce market: the criminal group develops a Super E-food app, which is encrypted to the highest level. Customers believe that the app (awarded with the Invincible App Certificate) will protect them from online fraud. Unbeknownst to them, they use a secure app to purchase fraudulent food. Step 10. Creation of dedicated social network groups/pages: the group creates dedicated pages and groups on social media to promote and sell their products, leveraging on the reputation of the acquired e-supermarkets. In one year, the infiltration of the e-food sector reached a market share of nearly 5%, 10% of the sales are related to fraudulent food and they generate profits of several million euros. In the same period, a sudden wave of food poisoning cases starts affecting the country.
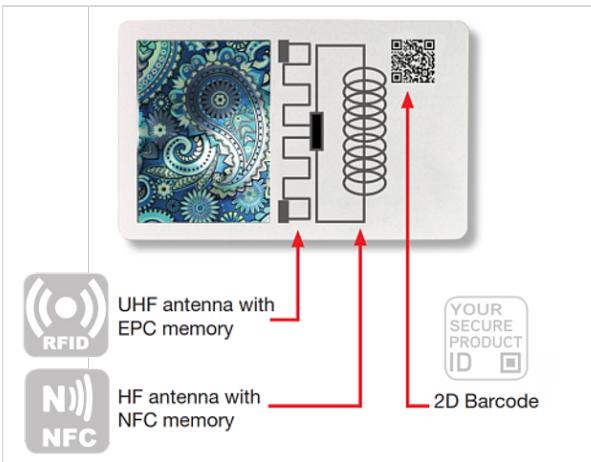
2.2 Supply Chain Security Solutions to address the risk scenarios This part of the report presents possible solutions to the challenges posed by the three risk scenarios described in the previous section. It describes the main aspects of the technology submissions, their relevance to the risk scenarios and possible advantages and limitations. Advantages and limitations in the use of supply chain security technology are also discussed in this section. They usually refer to the technology categories in general (authentication and track and trace). However, in some cases, reference will be made to some of the specific submissions we received; this will be done solely in view of providing a specific example of technology application. The issue of supply chain security in the area of food fraud is fundamentally framed by the notion that these traded products are consumed by humans, posing a significant threat to human health and safety and the existing food system. Security in the food supply chain is widely based on overt and covert security authentication solutions, that are incorporated into layered protection systems, which incorporate additional levels of security such as traceability mechanisms and sample testing. In general terms, by analysing the various submissions received, it can be observed that technology solutions applied to combat supply chain related threats have been developed to be flexible and easily adaptable to different products and various stages of the supply chain. Available technology options can be integrated to enhance the protection of the production and distribution process, especially since technology can be adapted to multiple approaches such as the authentication of the package, the monitoring of the product through the supply chain, the chemical composition of the goods, or the combination of several techniques. Several available technology options are based on tagging or modifying the package by using stamps, seals or labels that are attached to the products and that are usually tamper evident. The authentication technology can also be embedded in the material, in microtaggants or nano-structured security features such as holograms and codes, which make the solution non-removable. The information to validate the authenticity of the product is frequently read with machines developed to specifically perform this task and work in combination with the authentication and track and trace technology. The codification and decodification of the data that is saved in the product provides stakeholders of the supply chain with a secure mechanism to corroborate the authenticity of the merchandise.
23