2.2 Supply Chain Security Solutions to address the risk scenarios
Step 3 – Expansion of e-commerce market through the creation of a Super E-food app. Step 4 – Creation of dedicated social network groups/pages to sell fraudulent products to final customers.
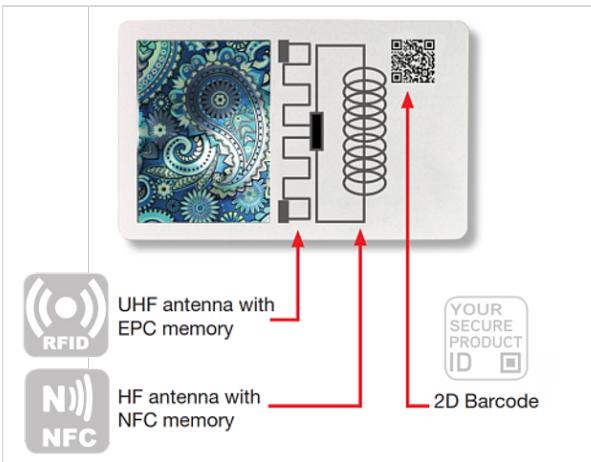
2.2.3 Focus on labels – the “all in one label” Technology submission 3 One of the submissions received combines the initial unique identification of the product with a traceability system that is protected by blockchain technology. Multilayer security is presented as a combination of authentication, tamper evidence and digital security. In the specific case of food traded online, this multilayer security technology starts at the basic protection element, using VOID labels for packaging. A VOID label is type of security label that is designed to indicate that a label has been tampered with by displaying a “VOID” message on the substrate (total transfer), on the back of the label (non-transfer), or both (partial transfer) when the label is removed. These seals can use covert, overt or semi-covert authentication and anti-tampering technology and can consequently also be used to create the digital identity of the product in the track and trace database to follow its movements along the supply chain. There is a wide range of proprietary VOID effects that can be applied, for example, three-colour VOID, integrated micro texts, variable codes, VOID effects visible on light and dark backgrounds. With transparent VOID tapes, underlying texts remain legible. If no transparency is required, a VOID effect can also be created from a multi-coloured image. These labels are also “consumer friendly”, since the VOID effect reveals a previously invisible, irreversible pattern as soon as the tape is removed or peeled off. VOID labels for packaging can be customized for each customer. In the case in which food is packaged in reusable packaging, returned by the consumer, this submission takes into consideration that there will be specific issues to solve. The standard VOID label with different security features could not be used in this case, since it would be difficult to remove from the packaging in view of its new use. For this reason, the submission is proposing to use a special dry-peel VOID that has been developed. This label is a 2-layer construction, allowing both identification of tampering and reusability of packaging after usage. When an attempt is made to remove the label, a VOID effect is triggered between two layers. The bottom layer of the label remains on the returnable packaging. The bottom layer can be removed without leaving residues, since if the label is peeled off again, a security punch is triggered, and the label is destroyed into individual parts. In case of legitimate reuse of the packaging, the supply chain operator will affix a new VOID label while in the case of criminal manipulation, the label will be destroyed and further actors of the supply chain, including consumers, will be alerted by its absence. As in the case of the traditional VOID labels, these dry-peel labels can also be equipped with different authentication measures that allow each of them to have its own ID and consequently to be followed and checked along the supply chain. In addition to the physical product security, a dry-peel VOID can be equipped with serialised ID and a related traceability function. That means that each label has its own ID and can be managed and tracked individually. The main features include the online authentication of each code, personalisation at item level, creating response pages driven by algorithms, GEO tracking with full track and trace for the entire supply chain and global distribution chain, management of packaging aggregation, consumer engagement. The solution can be divided into:
36