2.2 Supply Chain Security Solutions to address the risk scenarios
Scenario 3: E-commerce: criminal infiltration of online supermarket chains for home delivery of fake food Step 1 – Control of legitimate e-operators. Step 2 – Selling fraudulent food as genuine through the controlled e-supermarkets.
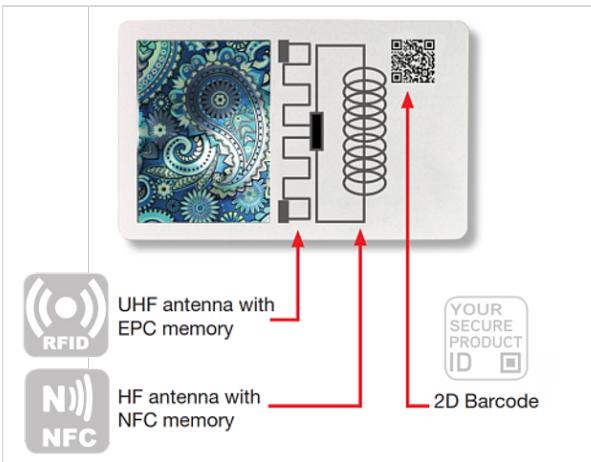
Through the use of strong authentication measures in the product and then the control of its movements. The code provides an important security layer, which can be improved in the future if it includes encrypted information about the characteristics of the specific product that is linked to the blockchain protected traceability system. However, since in many cases the product is directly sold to the final consumer, avoiding any other intermediary passages, consumers may also have a role to play in this case. This requires the consumer to be fully aware of the authentication method and of how to identify a counterfeit.
Step 3 – Expansion of e-commerce market through the creation of a Super E-food app. Step 4 – Creation of dedicated social network groups/pages to sell fraudulent products to final customers.
2.2.6 Focus on authenticating, tracking and tracing ingredients Technology submission 6 One of the submissions received focuses on the application of an advanced Manufacturing Execution System (MES) that provides the ability to track the manufacturing of products and their movement through the supply chain anywhere in the world via a web-based tracking data management system. The solution secures products through tamper-proof labelling solutions that assign unique, serialized identities to each crop, ingredient, product, and batch. This is combined with total traceability and control throughout the food and beverage supply chain—from seed, to harvest, production, distribution, sale, and after sale. This technology option is based on assigning serialized identities to every product, starting in the field, providing stakeholders with a highly detailed record of every product’s genealogy. With a single scan, this detail can be instantly accessed by key stakeholders throughout the supply chain, providing insight into where a product came from, what ingredients were used, and who interacted with it at every stage of the supply chain. The solution creates and assigns unique codes (paired with security labelling). The codes are associated with all aspects of the process and items used in the process. It starts with the codes that are associated with raw materials and ingredients, product, and materials produced. The raw material and ingredient codes are embedded in the product along with other process data such as user information, operational data, and specific intrinsic data such as temperatures, pressures, and dwell times, among others. These codes are aggregated to pallets, skids, and cartons, allowing the solution to easily track the shipping information. By using the system, stakeholders can have a complete overview of what is produced, where it came from, and where it went.
54