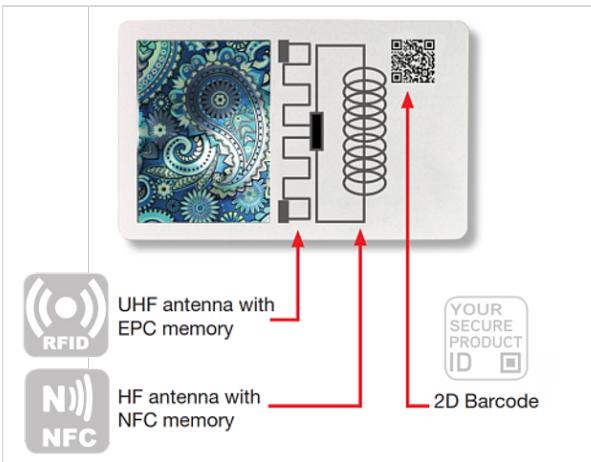
2.4 Examples of technology targeting e-commerce fraud
Step 5 – Building a parallel market for catering food supplies targeting small shops.
The same considerations described in step 3 apply to this step.
Step 6 – Distortion of competition.
Scenario 3: E-commerce: criminal infiltration of online supermarket chains for home delivery of fake food Step 1 – Control of legitimate e-operators. Step 2 – Selling fraudulent food as genuine through the controlled e-supermarkets.
The technology will be able to analyse the marketed products and determine if they are fraudulent, of low quality and whether they do not originate from the correct geographical location.
Step 3 – Expansion of e-commerce market through the creation of a Super E-food app. Step 4 – Creation of dedicated social network groups/ pages to sell fraudulent products to final customers.
2.4 Examples of technology targeting e-commerce fraud Technology option for e-commerce 1 The technology solution uses artificial intelligence to detect fraudulent product reviews and third-party sellers. Fraudulent reviews are used by sellers of counterfeit goods to create a false public image of consumer trust and exploit the fact that online consumers frequently use existing reviews as a reference point to base their purchases on, making them an important factor to consider in order to increase sales and consumer trust. Through the use of big data analytics and artificial intelligence, this technology option can identify fraudulent reviews supporting the selling of counterfeit products online. The solution consists in an online analyser bar where consumers can introduce the web address of a website in which the product they are interested in is being advertised. Another option is to install a browser extension in order to have a real-time analysis. As a result of the analysis, the technology displays relevant information related to the product, including: 1) A review grade that compares the review displayed on the website or app with the one generated by the analyser, 2) Highlights on the product (quality, packaging, competitiveness), its overview (reliability, deception level, total number of reviews), details about the reviews, insights, and review count and price graphs. In addition to the online analyser bar and the browser extension, the technology also gives consumers the possibility of downloading an app to perform the same check on a smartphone. This is a customer-centric solution that helps individuals to identify fraudulent products and providers through the detection of faults in the algorithms of the marketplace platforms, thus highlighting false reviews or suspicious low prices that can be the symptoms of counterfeit products and fraudulent sellers. Technology developed by Fakespot
83