2.5 Conclusions
Step 3 – Expansion of e-commerce market through the creation of a Super E-food app.
Big data analytics can be used to monitor apps, allowing the user to obtain an alert if an app is selling counterfeit goods.
Step 4 – Creation of dedicated social network groups/pages to sell fraudulent products to final customers.
Big data analytics can target social media as part of the constant monitoring of the e-commerce platforms. Groups and users selling fraudulent products can be eliminated or reported.
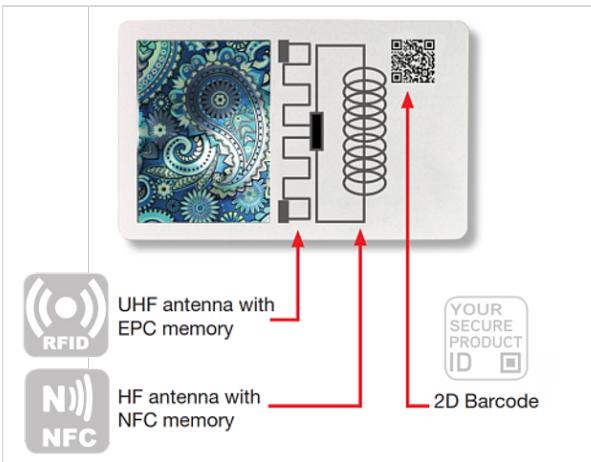
2.5 Conclusions The agro-food mafia risk scenarios presented some of the threats that can affect the integrity of the supply chain. Thanks to research conducted by UNICRI and the submissions we received from technology experts; it has been possible to assess how technology solutions may contribute to increase the security of the supply chain of these products while limiting related criminal activities. Existing technology solutions usually encompass one or several of these elements to protect the flow of products in the supply chain: Authentication technology: This option is defined by specific characteristics that allow the differentiation of a product to help the different stakeholders of the supply chain, which could possibly include consumers, to identify original products and, consequently, the presence of counterfeits. To define what an original product is, it is possible to refer to certain intrinsic features of the product itself or to apply specific technology on the product, which will provide for the distinction between original and counterfeit (a hologram or a code, for instance). The solutions can be overt (using the sensorial capability of the individual) or covert (that require a device or an additional tool to be revealed) or a combination of both. Track and trace systems: Frequently, authentication technology on the products is coupled with the implementation of track and trace systems that allow the monitoring of the authenticated goods throughout the different stages of the supply chain and secure the latter from infiltration of unauthorized products. This grants visibility to identify illicit activities related to the deviation of the products from the supply chain, including the use of expired or low-quality products that are repacked and relabelled with falsified dates, dosage and brand information. Traceability options can also use space technologies as a proof of origin as well as for monitoring purposes. Blockchain technology: This solution has been integrated to traceability systems. It can connect the different parties in the supply chain that have not established trusted relationships with each other, by ensuring transparency. Blockchain stores every transaction or exchange of data that occurs in the network, reducing the need for intermediaries by providing a means by which all the actors in the network may share access to the same information, including what is added to the data, by whom, and the date and time of the submission.2 Forensics: A product resulting from the supply chain process can be seen as the culmination of certain contingencies (nodes in the supply chain) and continuities (production methods) intrinsic in its manufacture. Forensics can be used to analyse a product which has already reached the market to verify if it is counterfeit or not. This evidence can even be brought in court to support allegations of counterfeiting since it may also serve as a tool to trace back the origin of the incident and to compare other counterfeits to verify if they have the same origin. In the case of food fraud, the following techniques can be used: stable isotope 2
Accenture. (2019, January 15). Tracing the Supply Chain. Retrieved August 23, 2020, from https://www.accenture.com/_acnmedia/ pdf-93/accenture-tracing-supply-chain-blockchain-study-pov.p
87