3.2 Technology solutions to address the risk scenarios Step 4. Selling of the bars: The associate operating in the neighbouring country sells the gold bars though their distributors and receives payment including VAT. After a few transactions, the gold bars are exported, and the VAT is reclaimed. Risk scenario 3: Infiltration of the Legal Industrial Refining Process An organized crime group realizes that infiltrating the legal industrial refining process of precious metals would provide a high return on investment at a lower level of risk compared to other more “traditional” crime sectors. The criminal group implements the following business model: Step 1. Illegal acquisition of catalysts and scrap metals: The criminal group steals products containing PGMs (such as catalytic converters, chemical catalysts and others). Step 2. Exportation of the stolen material: The criminal group does not have a licence to refine precious metals and scrap (which is requested by the regulatory framework of the country where the group operates). Therefore, criminals use a front import/export company to export the stolen products containing precious metals to another front company that operates in a different country. The latter is a well-established company and is owned/controlled by an affiliate of the main criminal group and is specialized in metal smelting and refining, including industrial platinum, palladium and rhodium. Step 3. Extraction of precious metals: The front refinery company crushes and mixes the stolen (but legally exported) products with spent catalysts and other material containing precious metals. It then extracts the precious metals (rhodium, palladium and platinum). Step 4. Selling the precious metals: The front refinery company legally sells the precious metals (rhodium, palladium and platinum) which have been melted and poured into various forms (buttons/bars), thereby concealing their origin.
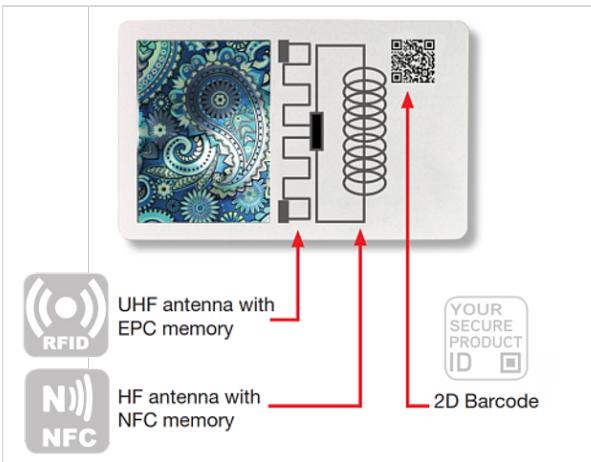
3.2 Technology solutions to address the risk scenarios The supply chain of precious metals has its own peculiarities and any activity aimed at securing it will have to take into account specific issues, such as the metals’ sourcing, their purity, weight, and tampering, among others. Supply chain security solutions in this field have been developed keeping these elements in consideration, in view of minimizing threats deriving from infiltration, counterfeiting and smuggling, also looking at the sourcing phase of the product. In this regard, for instance, some of the tools available to guarantee responsible sourcing include multilayer approaches that are based on track and trace systems to monitor precious metal provenance and their subsequent handling, transformation, distribution and sale. Frequently, track and trace systems are combined with other features such as blockchain technology and third-party based auditing and certification. In the case of metal purity, analytical techniques include magnetic tests, acid tests on stone, ultrasonic tests, testing electrical properties, X-ray fluorescence (XRF) and spectrography. These techniques are used by stakeholders to corroborate the quality of the products, since for end-users the cost of these techniques is quite high, making it hardly affordable. As mentioned, one additional element to consider in the field of precious metal supply chain security is weighing. However, even if traditionally this has been a widely used method to avoid the commercialization of counterfeit metals, it is currently relatively simple to maintain a specific weight for metals and still use counterfeit products. One of the threats that is directly related to weighing is tampering. Tampering precious metals is done to artificially increase the product weight by the addition of less expensive materials through different methods. To minimize this risk, analytical techniques to combat purity concerns are used by stakeholders. Finally, to improve security measures for the customer, new mobile apps are being designed to corroborate authenticity through the scanning of visible or invisible codes. The codes can be linked to a traceability system. This technology option is frequently combined with traditionally used serial numbers to facilitate the tracking of the product through the supply chain and with certificates to validate the authenticity and quality of the product.
94