p1, Is Cyber Security Training Really Necessary?
p2, Making the most of your Microsoft 365 apps requires you to adopt appropriate security measures.
p4, How ZOOM is the Life-Saving Tool for Business During Pandemic?
p5, Enhance Your Server Management with these 8 Tips

2022 FEBRUARY VOLUME
14


TEKNOLOGY INSIDER
Business gadget p7 of the month


February Webinars with p8 Sergey - Getting Hacked New in Microsoft 365, p9 Do your part #becybersmart, MS Outlook Tip - Search p11 by category,
YOUR MONTHLY NEWSLETTER, WRITTEN FOR HUMANS, NOT GEEKS
ISCYBERSECURITYTRAINING REALLYNECESSARY?

Getting Hacked: What You Need to Know to Protect Yourself
Feb. 10 at 11 AM, see page 8 for more details
Making the most of your Microsoft 365 apps requires you to adopt appropriate security measures.
Read page 2 for full story
TOOLS AND SOFTWARE
DIGITAL INTEREST
MAKING THE MOST OF YOUR MICROSOFT 365 APPS REQUIRES YOU TO ADOPT APPROPRIATE SECURITY MEASURES.
Microsoft 365 is one of the best collaboration and productivity tools around. It provides users with seamless communication, scalability and supports remote work with various features. The security is also solid due to a wide array of defense mechanisms.
But this doesn't mean you're impervious to cyber attacks.
Data leakage, unauthorized access, and malware can still jeopardize your system and offer ideal entry points for hackers. Should your business fall victim, the consequences can be dire, ranging from operational disruptions to severe reputational damage.
The only way to fend off hackers is to take your Microsoft 365 data protection to the next level. And this article will list the 11 most effective security measures to help shield your data in Microsoft 365.
THE 11 EFFECTIVE SECURITY MEASURES
Security Measure #1 - Activate Multi-Factor Authentication

Microsoft 365 users have just one method of verifying their identity when using a username
and password. Unfortunately, many people don't follow robust password protocols. If you’re doing the same, you’re exposing your organization to intrusions.
That's where multi-factor authentication (MFA) comes into play.
It can boost your Microsoft 365 security with one-time passphrases or other factors to verify user identity. Best of all, this measure is easy to apply.
However, enabling MFA should only be your first step. The next one is to activate Security Defaults, a Microsoft feature that enforces MFA in each administrator account.


Another great idea is to implement MFA in all accounts without administrator permissions. It’s because these accounts can still endanger services and apps in your ecosystem.
Security Measure #1 - Use Session Timeouts
Many employees fail to log out of their accounts and lock their mobile devices or computers. This can grant hackers unlimited access to enterprise accounts, enabling them to compromise
your data.
Incorporating session timeouts into internal networks and accounts automatically logs users out after a certain inactivity period. That means hackers can't take over their devices and access sensitive information.
Security Measure #3 - Refrain from Public Calendar Sharing
Calendar sharing enables your employees to synchronize and share schedules with colleagues. While this facilitates team collaboration, it can also give hackers insight into your operations and vulnerable users.
For example, if your security administrator is on vacation and this information is publicly available, attackers can use this window to launch malware.
Security Measure #4 - Employ Advanced Threat Protection
Advanced threat protection (ATP) is a robust solution that recognizes and prevents advanced threats that usually bypass antivirus and firewall defenses.

It grants access to a database that receives real-time updates, allowing users to understand the
(Continued on next page)
2 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca LIFESTYLE | MICROSOFT OFFICE TIPS/GUIDES
(Continued from page 2
threats and integrate the data into their analysis.
ATP notifies you about attacks, the severity, and the method that stopped them, regardless of the source. It's especially effective at preventing phishing.
It relies on machine learning and a massive database of suspicious sites notorious for malware delivery or phishing attempts.
Security Measure #5Leverage Policy Alerts
Microsoft 365 lets you establish your policy notifications in the compliance center to meet your company's security needs. For example, they send your employees tips on sending sensitive information whenever they're about to send a message to a contact outside your network.
These warnings can safeguard against data leaks while educating your team on safe data sharing methods.
Security Measure #6 - Secure Your Mobile Access
Your tea

email, contacts, documents, and calendars, especially if they work remotely. So, securing their devices should be your top priority when protecting data.
The best way to do so is to install Microsoft 365 mobile management features. They can let you manage your security policy, permissions, restrictions, and wipe crucial information from stolen or lost devices.
Security Measure #7Deactivate Legacy Protocol Authentication
It’s worth noting that legacy protocols don't support several security features in Microsoft 365 that reduce the chances of intrusion, such as MFA. This can make them perfect gateways for adversaries who want to target your organization.
That said, your best bet is to deactivate legacy protocols to mitigate risks.
However, you may not want to disable legacy authentication if your team needs it for older email accounts. The good news is that you can still make your network safer by restricting access to users who don't need this
Security Measure #8 - Integrate Role-Based Access Control

Access management is a convenient security feature that can limit the flow of private information across your business. It allows you to establish the users who can access data in your company.
For instance, you can minimize data leaks by preventing rankand-file team members from reading and editing executivelevel files.

Security Measure #9 - Rely on Unified Audit Log
Unified audit log (UAL) includes logs from several Microsoft 365 services, such as Azure AD, SharePoint Online, OneDrive, and Microsoft Teams. Enabling it can give the administrator insight into malicious activity and actions that violate organizational policies.
You may also want to incorporate your logs into an existing SIEM (Security Information and Event Management) tool Doing so enables you to connect logs with current log monitoring and management solutions to reveal abnormal activity. Plus, it can improve the overall security of your Microsoft 365 suite.
(Continued on next page)
LIFESTYLE | MICROSOFT OFFICE TIPS/GUIDES
)
TECHNOLOGY | ZOOM & SERVER MANAGEMENT

(Continued from page 3 )
Security Measure #10Encrypt Emails

Encrypting sensitive data is often the last resort when dealing with data breaches. But if cyberattackers access your emails, robust encryption tools can make them unreadable. That’s why email encryption is something worth looking into.
Security Measure #11 - Train and Educate Your Employees
The above measures are undoubtedly effective, but they may amount to nothing if you leave your employees out of the picture. In fact, human error is the leading cause of most data breaches.
One of the best ways to prevent security breaches in your business is to schedule employee it t i i d d ti

This feature is essential for Microsoft 365 users who share il d fil l l through our computers and cellular devices.
As we found many new and previously used tool, Zoom was the life-saving tool for small and large businesses during the pandemic. Zoom enables employees to communicate and perform tasks to achieve business goals. Below, you will find some benefits of using Zoom as a conferencing tool during a pandemic:


It can raise their awareness of potential threats and guide them on how to address them.
This is especially important when recruiting employees. Make sure they undergo in-depth security training before granting them access to sensitive data and organizational devices.
meetings.
Employees can share files and communicate through video and chat that encourages businesses to grow despite pandemic situations.
Meetings can be recorded for easy and convenient review at a later time, and with services like Rev.com you can get them easily transcribed as well.
(Continued on next page)
4 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca
(Continued from page 4)
You can install Zoom on any device, so people do not invest in expensive devices and computers.
Zoom is not only facilitating small and large businesses to enable communication after COVID-19, but many educational departments, health sectors, and governmental organizations are communicating through this tool as well.
ENHANCE YOUR SERVER MANAGEMENT WITH THESE 8 TIPS
You may have state-of-the-art servers, but their efficiency can diminish over time. Managing them is key to optimizing your business operations.
Numerous organizations rely on servers for various IT functions, such as applications, emails, hosting websites, and data storage

Although many companies have turned to cloud-based services using remote data centers, many enterprises still depend on in-house servers As such, they need to ensure their devices remain in tip-top condition
That’s where server management comes into play

Managing your servers can streamline the performance of your team by allowing them to


complete complex tasks faster. Plus, it can enable them to detect problems early on before they get out of hand and compromise your business. As a result, the risk of experiencing operational setbacks is drastically lower.
But the only way to make the most of your server management is to perform it correctly And to help you do so, this article will share nine tips on improving your server management
THE 8 TIPS
TIP #1 - Mount the Servers Properly

Small businesses often need to prioritize immediate concerns over long-term plans because they need to work on tight budgets This is particularly evident in terms of server management
When you first set up your servers, it might be tempting to connect them near your workstations. However, this can harm your hardware.
Mounting your servers in racks is a much better solution. It can shield them from accidents in high-traffic areas, tripping hazards, spills, and dirt
Furthermore, server racks can help keep the hardware safe by organizing it in an accessible area that facilitates management and cleaning They also limit the exposure to regular wear and tear in the office
Another critical consideration is to plan for the future when installing your servers
When selecting a rack mount, be sure there’s enough room to expand your hardware Unless your office is tiny, having half
(Continued on next page)
5 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca TECHNOLOGY | ZOOM & SERVER MANAGEMENT
(Continued from page 5)
empty racks is preferred to tearing them down and redesigning them a few years down the line.
TIP #2 - Separate Your Servers from Your Main Area


Depending on the type of servers, they can get quite noisy when in operation. On top of that, they can comprise valuable hardware. So, you’ll want to separate them physically from the working premises.
If you can’t afford a designated server room, invest in secure rack mounts with integrated sound reduction
TIP #3 - Take Care of Your Hardware
Hardware maintenance plays a pivotal role in server management. Without dependable hardware, your productivity can plunge.
To avoid this scenario, you need to monitor the essential components of your server:
CPU (Central Processing Unit)
– Your CPU is the core of your servers, performing all calculations for running programs. You need to constantly monitor it to prevent overuse.


If it operates near 100% of its power, your team members can’t carry out additional tasks due to slowdowns. It may require chip upgrades or performance tuning to alleviate the stress.
RAM (Random Access Memory) – This is the working memory of your server, as it runs faster than hard disks. The more RAM you have, the higher the performance of your device. Closely monitor its usage and add more memory when it gets close to its full capacity.

Hard drive – The hard drive is the permanent storage of your servers. It saves your data and programs, but its performance can diminish with overuse. Proper hard disk management entails keeping track of the available space, deleting unnecessary files, installing new drives, or including cloud-based solutions.
TIP #4 - Employ Frequent Cooling
You expect your servers to perform fast, but the only way to ensure this is to provide optimal conditions. That said, you should primarily focus on cooling the servers. Excess heat can dramatically decrease their lifespan.
The best practice here is to make sure your cooling device operates outside your building.
Additionally, if you experience a power outage or central air doesn’t work at night, you need a cooling solution that can run on backup power.
TIP #5 - Manage and Maintain Your Software
Software used for your server requires regular maintenance, too The key is to perform regular updates and delete old software to enhance performance Your servers will operate better, and there will be fewer vulnerabilities cybercriminals can exploit to access your network
TIP #6 - Arrange the Wiring Neatly
The amount of wiring in your server setup can be overwhelming, especially if you have no technical experience. Sorting out the mess doesn’t only improve cleanliness, but it can also help boost the performance of your server viability for future upgrades.
Keep in mind that whenever you’re removing, rearranging, or installing your cables, label and group them neatly. Doing so helps prevent clutter.
(Continued on next page)
6 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca
TIP #7 - Pay Special Attention to Security
As previously mentioned, servers can be susceptible to cyberattacks. That’s why it’s crucial to maintain a secure system. Here’s what you should do:
Install and update antivirus software.
Repel unauthorized traffic with firewalls.

Use robust access control software or sound password policies and instruct your users to change them regularly.
Encrypt external networks and data storage.
Incorporate SIEM (Security Information and Event Management) tools.
Analyze and implement security logging measures to understand potential threats.
TIP #8 - Back Up Your Data
The final part of robust server management is backing up your data regularly After all, loss of information can be disastrous, harming your reputation and losing your customers
Besides backing up server software and hardware, you should also have a backup for your power supply to prevent data losses during power outages. Moreover, you can integrate with various tools to expedite backups, recoveries, and status monitoring.
Look for software that covers both your IT architecture and operating system.
BUSINESS GADGET OF THE MONTH
Now that many of us are working remotely, safe and secure transport for our devices is a must.
The Nordace Siena smart backpack is perfect.

Not only does it look good, but it has a padded laptop compartment, a USB charging point, and a secret pocket for valuables.
It even has a fleece-lined sunglasses pocket.
It needs to work across systems and applications you currently have or plan on installing. Additionally, it should diagnose server issues efficiently with powerful analytic capabilities.
SERVER MANAGEMENT AT ITS FINEST


Managing effective server operation involves several key considerations, from monitoring system temperature to updates and data backups. Even though this can be an arduous process, it’s integral to optimizing your server performance and eliminating security concerns.
If you need help in optimum server management in your business, we’d love to help you out. Contact us and let’s have a quick, no-obligation chat about it.
(Continued from page 6)
Staff highlight: Darwin


I have been passionate about everything electronic since I was a kid - most especially computers. My dad was the one who introduced me to it. In my younger days, I break apart almost anything to learn how it works. Sadly, most of them I wasn't able to put back. This taught me that some things you can't learn from books.
I began my career as a Helpdesk Support Agent for BellSouthhelping customers with their DSL connection.



After a year I landed an office job at a local university.
For more than 8 years, I worked as an IT System Administrator. So it was a big switch for me when I joined CapitalTek since I was used to doing everything hands-on. And I am very happy that I made that decision.


Technology fascinates me, especially how it makes things more convenient for everyone. And my goal is to let our clients have that privilege.

8 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca MEDIA & ARTS | UPCOMING WEBINAR SCAN the QR Code to REGISTER for FREE
Network and Server Engineer darwin@capitaltek ca GettingHacked:WhatYouNeedtoKnow toProtectYourself 1. Thursday,February10,2022·11AMEST 2.MS365vsGoogleWorkspace Thursday,February24,2022·11AMEST
RegisterforFREE:capitaltek.ca/webinar
NEW IN MICROSOFT 365

Chat with yourself in Teams
This idea isn’t as mad as it seems…
You know those times you’re in a Teams meeting and you think to yourself, ‘Oh, I’ll remember that for later’… but you never do?
Or when someone mentions a file and you plan to take a look after the call… but then you forget for a few weeks?
Later this month Teams will give you a new power to send things to yourself. Notes, messages, files, photos, and other things to help you to stay more organized.
Who knew talking to yourself could be so productive?!
DID YOU KNOW?
Safari's busy protecting you
If you use Safari, maybe you’ve noticed its boasts about blocking “x” number of trackers from profiling you. But what does that really mean?

It has nothing to do with malware or being hacked. Instead, it means the browser has stopped the websites you visit from tracking:
Your movements across the web
Your IP address

And even your location
DO YOUR PART #BECYBERSMART
Do you part, #becybersmart. When you make cybersecurity a priority, it becomes easier to see where others can make smarter decisions in their own cyber life.
It does this by blocking third-party cookies from being stored on your device.
You’ll might notice that the number is usually high. That means there’s still a way to go to get more privacy online.
The Dark Web gets a bad rap for being a community where cybercrime can thrive. But many good-intentioned people use the tool for communication purposes outside of their controlling countries.

Charity scams increase in volume after natural disasters and during holiday seasons. Do your homework on any charity before dipping into your wallet for a donation.

9 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca TECHNOLOGY UPDATE | MICROSOFT 365
The Funnies



Q&As Tech Quiz


Which tech whizz invented the term ‘metaverse’?
Which part of the US, famous for internet companies, is named after the mineral used in transistors and computer chips?

What was the first handheld game console to be played in space?
What does the ‘CC’ in an email stand for?

What year was YouTube started?
Q: Can I print straight from my Android device?
A: Yes, if your printer has Bluetooth or Wi-Fi. On your phone switch on Default Print Service in the settings Open the file you want to print Tap the menu (the three dots), print, and select your printer

Q: How do I see how much space apps are taking up?
A: In Windows 10 and 11 go to Settings> System -> Storage. Tap on Cleanup recommendations to see what software you’re not using and could remove
CapitalTek Teknology Insider 613-227 ENTERTAINMENT
| PUZZLES AND CROSSWORDS
g em yoB ni .3991 dnA eht emag deyalp saw sirteT nobraC ypoC 5002 .4 5
1. 2
3.
4. 5. The answers are below.
Search by Category
SEARCH BY CATEGORY
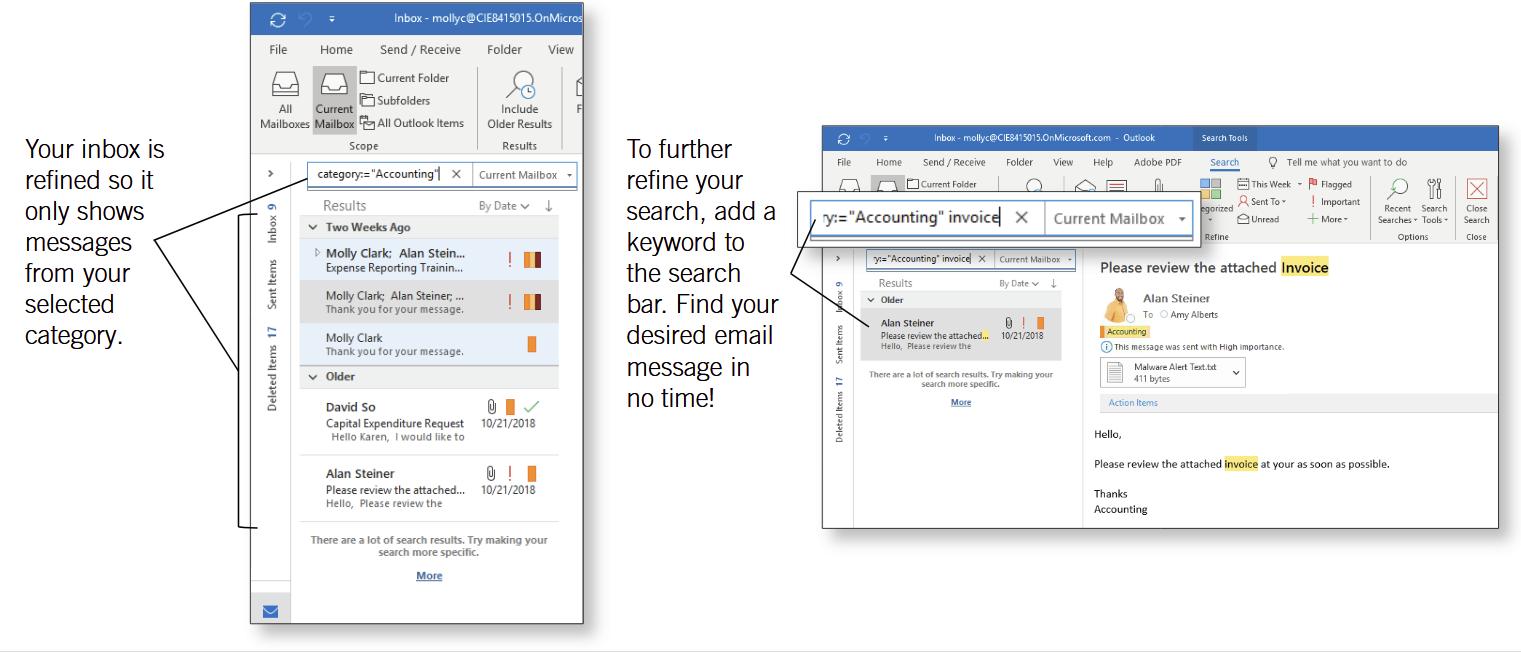
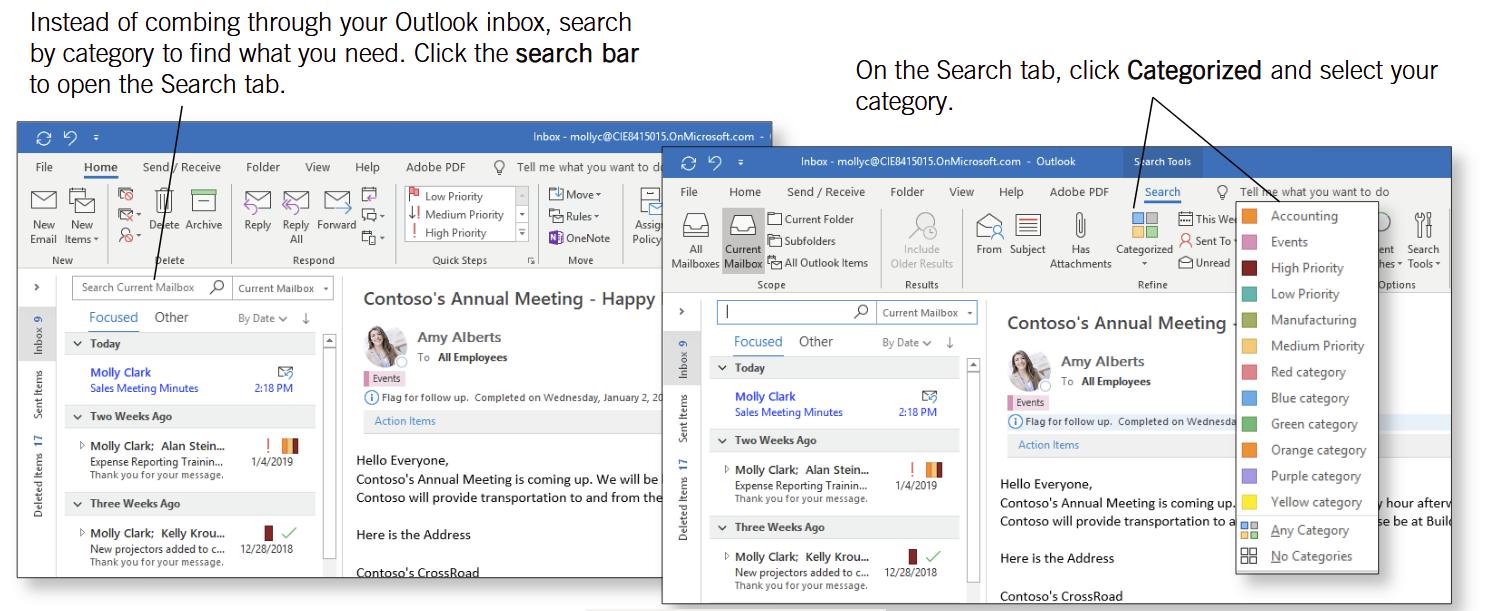



REFINE WITH KEYWORDS

11 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek ca FEATURE | MS OUTLOOK 365
NATURE CANADA
Nature Canada is one of the oldest national nature conservation charities in Canada



For 80 years, Nature Canada has helped protect over 110 million acres of parks and wildlife areas in Canada and countless species.
Today, Nature Canada represents a network of over 130,000 members and supporters and more than 1,000 nature organizations.
"Our expe en very positive so far. Sergey and this staff are very responsive, knowledgeable and patient. They have set up systems that quickly allow our whole team to access the day to day IT support they need and have helped us navigate through some big projects such as transitioning file management systems."



ABOUT FOUNDER & CEO, SERGEY POLTEV



Award-winning managed IT services for small to medium-sized companies in Ottawa. We combine essentials with a comprehensive platform to keep you running worry-free 24/7.






Founder and CEO Sergey Poltev, has been fixing computers since he was a kid. He immigrated to Canada to seek new opportunities, where he launched CALLGEEK (later renamed to CAPITALTEK) in 2008. Sergey was recognized in 2021 with a Forty Under 40 Awards from the Ottawa Board of Trade & Ottawa Business Journal.

COMPUTER MAINTENANCE MANAGED NETWORK BUSINESS PHONE BUSINESS EMAIL DATA BACKUP WEB HOSTING 12 CapitalTek Teknology Insider 613-227-HELP (4357) help@capitaltek ca capitaltek c FEATURE | CUSTOMER HIGHLIGHT P (4357) ltek ca capitaltek ca We're now taking on new clients! Set up a 30 minute explanatory video call at www.capitaltek.ca/talk-to-an-expert
Canada| naturecanada.ca
Nature

































