Abstract
Cyber threats are a constant in our networked world. Infrastructure such as electrical power and telecommunications are often cited as targets of cyberattacks but in the post-COVID world, health and economic systems have been increasingly targeted by malicious actors. In this paper, I will define cyber intelligence and provide examples for how it is collected and used by governments and the private sector and what traits, core competencies and skills are required by the workforce. Examples of how cybersecurity, information security, cyber intelligence, and intelligence are taught in academia will be highlighted. Reasons why cyber intelligence is more important than ever in a post-pandemic world will be delineated.
Cyber Intelligence
Sun Tzu’s adage from 2,500 years ago is just as relevant today and applies to cyber intelligence: “Know the enemy and know yourself; in a hundred battles you will never be in peril. When you are ignorant of the enemy, but know yourself, your chances of winning and losing are equal. If ignorant both of the enemy and of yourself, you are certain in every battle to be in peril” (Tzu, 1971, p. 84).
I realized early in my military intelligence career the importance of cyber intelligence. I knew then that cyber intelligence would be the intelligence of the future, which is today. Before I begin discussing the importance of teaching cyber intelligence, we must first understand what cyber intelligence is.
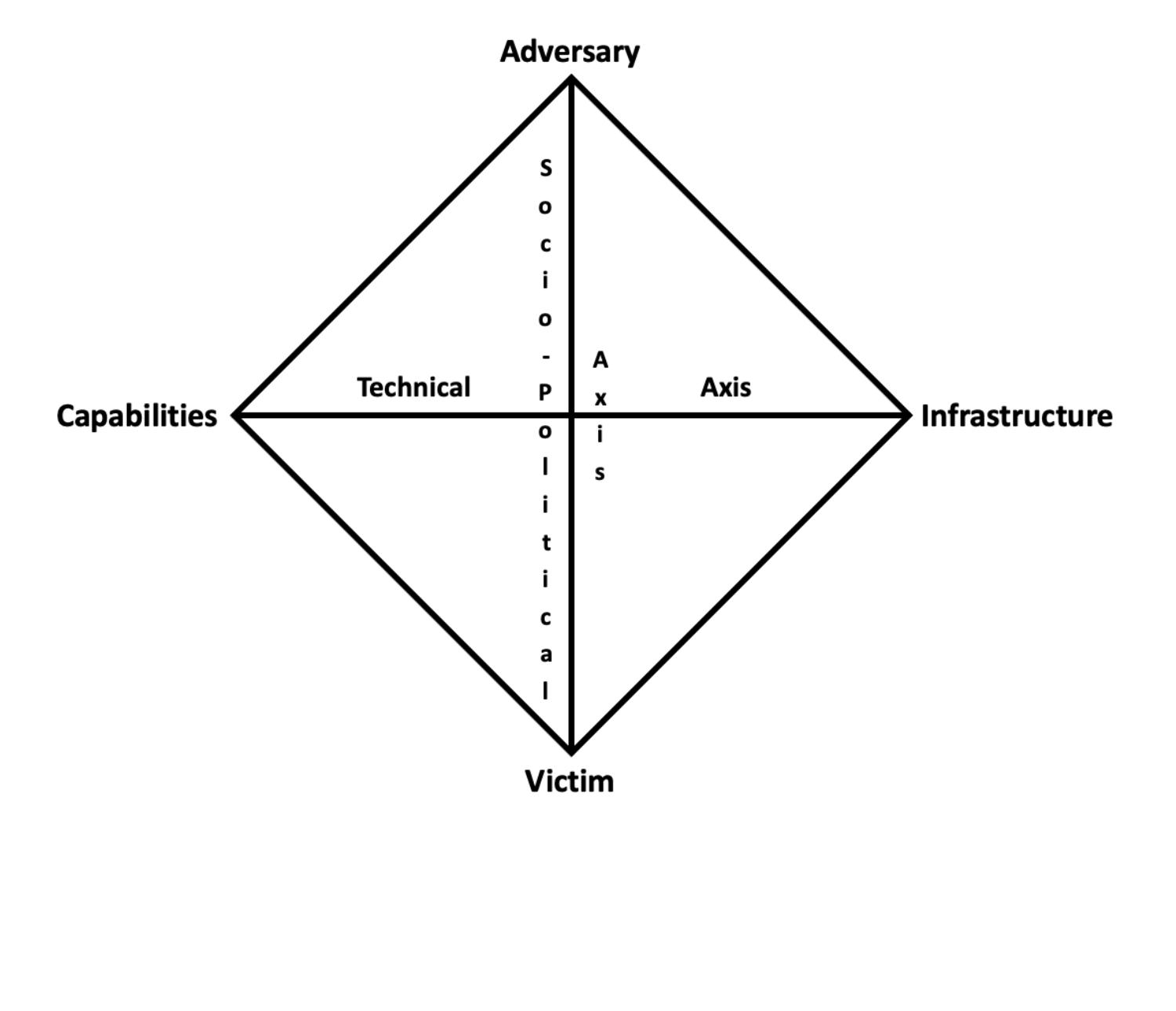
There are many definitions for cyber intelligence. I define cyber intelligence as intelligence (the intelligence function) conducted in, through, and for cyberspace (“the online world of computer networks and especially the Internet” (Merriam-Webster, 2022)). The primary focus should be on the cyber threat actors (CTAs), the person behind the keyboard, and their intentions, capabilities, tools, tactics, techniques, and procedures. From the existing definitions of cyber intelligence I prefer the 2014 National Intelligence Strategy definition, “the collection, processing, analysis, and dissemination of information from all sources of intelligence on foreign actors’ cyber programs, intentions, capabilities, research and development, tactics, and operational activities and indicators; their impact or potential effects on national security, information systems, infrastructure, and data; and network characterization, or insight into the components, structures, use, and vulnerabilities of foreign information systems” (ODNI, 2014, p.8). Cyber intelligence is represented across the three levels of intelligence: strategic, operational, and tactical. Some have included a fourth level of cyber intelligence, technical (Mavroeidis, 2021), but I consider technical intelligence as part of tactical intelligence. Cyber threat intelligence and (CTI) and cyber counterintelligence (CCI) are two main subcomponents of cyber intelligence.
Cyber threat intelligence (CTI). CTI is a main subcomponent of cyber intelligence and is “actionable and provides relevant, accurate, contextual, and timely knowledge regarding an organization’s attack surface, including defensive measures” (Mavroeidis, 2021). CTI usually consists of identifying indicators of compromise (IOCs), which are signatures identified as malicious that should be blocked, quarantined, or monitored to secure the network. The one thing missing from the cyber intelligence definition and not clearly delineated in the CTI definition is that we must know and understand our networks, systems, information, and data as well as the cyber threat actors’ networks, systems, information, data, intentions, capabilities, tactics, techniques, and procedures (TTPs).
Cyber counterintelligence (CCI). CCI is another main subcomponent of cyber intelligence. CCI is “measures to identify, penetrate, or neutralize foreign operations that use cyber means as the primary tradecraft methodology, as well as foreign intelligence service collection efforts that use traditional methods to gauge cyber capabilities and intentions” (Busch, 2018). Cyber espionage is a major concern, whether it is stealing government secrets or theft of intellectual property.
Cyber intelligence is relatively a new field of study and career path. Although it is often considered a subcomponent of cybersecurity, it is also a standalone field of study and career path. Cyber intelligence has three primary functions: It can be conducted for 1) Defensive purposes, e.g., cybersecurity and defensive cyber operations,
2) Offensive purposes, e.g., offensive cyber operations and cyberattacks, and 3) Intelligence purposes, e.g., intelligence collection and cyber espionage. Some confuse cyber intelligence with open-source intelligence (OSINT) (collecting and analyzing publicly available data) or signals intelligence (SIGINT) (collecting and analyzing digital and other electronic signals). There is overlap between cyber intelligence and these two intelligence disciplines, but the goals and therefore the products are different for these three intelligence disciplines.
Cyber intelligence in cyberspace is conducted the same way it is conducted in the other domains: air, land, sea, and space. In other words, the intelligence cycle is the same for all five domains (“intelligence is intelligence”). Unlike the other domains, the cyber domain, cyberspace, is manmade. Inherently, this means we have more control over this domain and therefore should be able conduct more intelligence in this domain. Although conducting intelligence in the domains of air, land, sea, and space is important, cyberspace has quickly become the most important domain for conducting intelligence.
Cyber intelligence is collected by a variety of means. One method that every entity can employ is collecting intelligence from their own network. Data and information on networks such as phishing emails, network and log anomalies, IOCs, malware, viruses, etc. can be collected for cyber intelligence purposes. The private sector primarily collects cyber intelligence outside of their own network by conducting OSINT. Governments have other means besides OSINT, such as SIGINT, and other “INTs”, to collect cyber intelligence. Many organizations subscribe to CTI feeds, which usually consist of IOCs and other technical threat information, to assist with their cyber intelligence.
Why Cyber Intelligence is Important

Now that we understand what cyber intelligence is (and is not), we must appreciate why cyber intelligence is important. You need to look no further than the daily news to realize the importance of cyber intelligence. On a regular basis there is a cyberattack that makes international news. Whether the cyberattack is against a nation, e.g., Ukraine (2022), or an entity, e.g., International Committee of the Red Cross (ICRC) (2022), and this trend has increased during the COVID-era. Not only have the cyberattacks increased (30,000 cyberattacks between December 31, 2019 and April 14, 2020) (Fichtenkamm et al, 2022), but the proportion of unseen malware (“zero days” or novel attacks) increased from 20% before the pandemic to 35% during the pandemic (Nabe, 2022). This increase in number of attacks using “zero days” infers that cybercriminals will exploit pandemics when they occur. Health and economic systems have increasingly become targets of cybercriminals and nation states. Fichtenkamm et al (2002, p.2) stated, “cybercriminals may have been the only decision makers who believed the early pandemic environment provided them with any chance to shape the future with their actions.” Below I identified some of the major cyberattacks that occurred since the pandemic began.
Some of the cyberattacks listed were directly because of the COVID-era we have experienced. Several of those cyberattacks were conducted to steal COVID-related data, e.g., vaccine data, or to take advantage of the pandemic work situation, e.g., the switch to virtual/remote work (“work from home”), which exposed many new cybersecurity vulnerabilities. Most organizations were not prepared for transitioning work to employees’ homes, especially for an extended period of time (Fichtenkamm et al, 2022).
From 2019, some of the major international cyberattacks include:
Adobe Inc.
• Ancestry.com
• Android
Apple
• Capital One
• Cognyte
• Crypto firm Bitmart
ElasticSearch
• Instagram International Committee of the Red Cross
• Log4j
Marriott International
• Microsoft
• Microsoft Exchange servers
Mobile TeleSystems
MongoDB
• NEC Networks, LLC
Nintendo
• Ransomware
• Socialarks server
• SolarWinds
Stripchat database
• TikTok
• View Media
YouTube
• Zynga
From 2019, some of the major country-specific cyberattacks include:
Ministry of Health (Brazil)
• Personnel database (Brazil)
• Revenue agency (Bulgaria)
• Saskatchewan Liquor & Gaming Authority (Canada)
• Vastaamo (Finland)
• Government email infrastructure (India)
• Raychat (Iran)
• Health Service Executive (Ireland)
Luas (Ireland)
• Local Government (Italy)
• Panasonic (Japan) Media companies (Norway) Bykea (Pakistan)
• Khyber Pakhtunkhwa police (Pakistan)
National Health Information Center (Slovakia)
• Public websites (Sri Lanka) Visitor database (Thailand) Government websites (Ukraine)
• Harris Federation (UK)
Colonial Pipeline (US)
• Quest Diagnostics (US)
• T-Mobile (US)
WaWa (US)
Below is a list of some of the topics that currently affect and will affect cyber intelligence into the future: 5G/6G and Beyond
• Artificial Intelligence (AI)
• Autonomous Vehicles
• Biotechnology
Climate Change
• “Computer Analysts” (e.g., Augmenting Intelligence Using Machines (AIM))
• Cryptocurrency
• Deep Fakes
• Drones/ Unmanned Arial Vehicles/Systems (UAVs/Ss)
Emerging Technologies
• Fake News
Global Warming
• Industrial Control Systems (ICS)
• Internet of Things (IoT) Machine Learning (ML)
• Pandemics
• Quantum Computing Space Activities
Virtual Reality (VR)/Augmented Reality (AR)
Why Teaching Cyber Intelligence is Important
The importance of teaching cyber intelligence cannot be overstated. The current cyber threat landscape, partially described above, justifies the need for teaching cyber intelligence. Cyber intelligence is utilized to produce an accurate cyber threat landscape, which assists with cybersecurity, preventing and mitigating cyberattacks, and to support offensive actions and intelligence collection.

The cyber intelligence job market also is a major indicator of the need for cyber intelligence education. There are hundreds of thousands of cyber intelligence-related job openings worldwide. A simple job search for terms such as cyber intelligence, cyber threat intelligence, cyber threat analyst, cyber analyst, cybersecurity analyst, infosec analyst, IT analyst, data analyst, security analyst, etc. results in thousands of job openings. According to CyberSeek.org, an online site that provides real-time supply and demand of the US cybersecurity job market, as of August 22, 2022, there were 194,017 cybersecurity-related analyst (cyber intelligence-related) positions available in the US (NICE, 2022).
As stated, the international community needs more intelligence professionals who understand cyberspace. We have three primary options to accomplish this feat: 1) teach current intelligence professionals about cyberspace, e.g., networks, systems, information, data, and how they work together; 2) teach cyber professionals, e.g., cybersecurity and IT personnel, how to conduct intelligence; or 3) teach non-intelligence and non-cyber professionals about cyberspace and intelligence together, i.e., cyber intelligence. Teaching cyber intelligence should be applied in all three options. The cyber intelligence analyst traits, core competencies and skills desired are provided in Figure 1 below.