





















































































































Protect critical data consistently against increasing cyberattacks! With the infodas SDoT Industry Gateway, you secure and control the data transfer between your sensitive networks! The Industry Gateway has been derived by our flagship military product to combine military grade security and flexibility for a maximum protection of critical infrastructures.































Since taking the helm at NCIA, I have had the opportunity to celebrate a number of milestones across the NATO Enterprise, but none bigger than the 75th anniversary of the Alliance itself. It has been my distinct pleasure to commemorate this historic occasion and look back on the triumphs and progress made as NATO has grown in both numbers and strength.
At its very core, different nations uniting under the shared determination to “safeguard the freedom, common heritage and civilization of their peoples” is an incredible feat of mutual support, partnership and compromise. Factor in 32 nations, spread across the Atlantic Ocean, and the success of NATO is truly something at which to marvel.
I am proud that NCIA makes interoperability possible by providing the digital solutions that connect the Alliance. Our services enable us to talk together, work together, train together, and – when necessary – fight together. We are evolving to ensure NATO can maintain its technological edge, and while the face of technology changes, those core principles established 75 years ago remain enduring: peace, security, liberty and the rule of law.
In this edition of NITECH magazine, we are commemorating the 75th anniversary by speaking to different stakeholders across the NATO Enterprise and industry. In her foreword, Assistant Secretary General for Public Diplomacy, Marie-Doha Besancenot, details why NATO is the most successful Alliance in history. You can learn more about said history in a number of special spreads found throughout this edition.
There is no better time in history to welcome another Ally to NATO, and this year we had the pleasure of adding Sweden to our Alliance, just one year after their neighbour Finland.



The role of NCIA has never been more apparent than in the work done to allow these nations to operate as full members from day one. Our experts have been preparing since summer 2023 to deliver communication and information systems (CIS) services to Sweden by conducting testing and ensuring compatibility and security.
Amid such a volatile time in the peace and security of our Nations and Partners, we are happy to have Sweden to bolster our collective deterrence and defence efforts, and I look forward to welcoming Swedish experts to NCIA’s impressive team. You can read an interesting account of how Sweden sees NATO’s role from their Minister of Defence, Pål Jonson.
Supporting NATO exercises, missions and operations is one of our core functions in NCIA, and this year that was put to the test in NATO’s largest military exercise since the Cold War, Steadfast Defender.
With more than 90,000 troops from all 32 NATO Allies, Steadfast Defender 24 (STDE24) was an extremely complex multi-domain, cross-continent operation. The success of the exercise demonstrates NATO’s ability to deploy, move and use reinforcements from North America and other parts of the Alliance to continental Europe.
Key areas of expertise within NCIA worked together to enable STDE24 by providing the necessary network and infrastructure to allow secure and efficient communications throughout the five months of the exercise.
Read Deputy Supreme Allied Commander Europe, Admiral Sir Keith Blount’s article to learn more about the who, what, when, where and why of this landmark event.
In the run up to the Washington Summit, all eyes are on our Allies in the West, as heads of state and government prepare to meet in North America for the first time in over 10 years.
Every year, the Summit provides NCIA with the opportunity to reaffirm our commitments to NATO’s ambitious agenda, and this year, highlight the transatlantic bonds among Allies. That’s why I am delighted to announce that NATO Edge, our flagship technology conference, will take place in Tampa, Florida in December.
The nature of our work at NCIA means we rely heavily on industry in order to stay at the forefront of technology and innovation, and over the past few years, we have been fostering strong partnerships with industry, not-for-profits and academia. NATO Edge 24 is a critical opportunity to strengthen these bonds with the North American and European private sectors, which is guaranteed to bring exciting opportunities in the near future.
We will be discussing topics such as artificial intelligence, cloud adoption and cyber security, and hearing from some of the most impactful voices in the industry. Our Technology Strategy, which provides the main directions for future investments in best-of-breed solutions for the Alliance, will also be presented at the conference. I look forward to facilitating captivating discussions and mutually beneficial partnerships between Europe and North America and hope to see many old and new faces there.
Without further ado, enjoy this edition of NITECH and happy 75th anniversary to all of us at NATO.





Is it just us or does it seem like every tech company this side of the Sierra Nevada is blindly rushing to launch the next AI doohickey, thingamabob, and whatchamacallit? Truth is, it’s starting to feel a lot like the Wild West ’round here. Making it difficult to know who to trust right now. That’s why we’re asking ourselves the all-important questions around how AI is being trained, how your company data is being protected, and how it’s all being governed. Which is precisely how we’re able to ensure that our own AI platform aligns with our #1 value: trust. If you have questions of your own, you’ll find us in the cloud at high noon. See you there, partner.






Combat-proven, state-of-the-art, and NATOregistered C4ISR products and solutions can change the game! Don’t solely rely on international suppliers but build your own in-country industrial capabilities.
Deployable, mobile tactical C4ISR, and unmanned aerial systems (UAS) in defense and security areas helped Slovak-Canadian company Aliter Technologies become one of the leaders in the NATO C4ISR defense and security community. Its defense product development domains include all platforms of hardware design, prototyping, manufacturing, testing and comprehensive software and hardware development engineering. The outsourcing of manufacturing, if required, allows manufacturing and industrial know-how transfer. The core efforts and services are oriented to the operational and tactical level of command and control, and they focus mainly on the field environments.
Aliter Technologies is a NATOregistered manufacturer and supplier (NCAGE #4127M). The company holds NATO and EU security clearances up to the SECRET level as well as ISO 9001 and AQAP 2110 quality management, ISO 14001 environmental management, ISO/ IEC 27001 information security management, ISO/IEC 20000-1 IT services management, ISO 45001 occupational health and safety management, and ISO 37001 antibribery management certificates.
The company’s unique in-house R&D capabilities, proprietary product portfolio, knowledge of military operational requirements, references from successfully implemented projects, ability to address customer requirements and maximize return on investment, the application of the most modern technologies and the provision of whole life cycle portfolio of services and solutions are the guarantee of the full
satisfaction of the customers.
The Aliter Technologies products and solutions are intended for use by armed forces including special operation forces, law enforcement agencies, fire brigades, rescue teams, civil protection, and crisis management personnel, in addition to other entities or organizations involved in missions of state defense and homeland security. The products and solutions are designed in accordance with both NATO, US and international standards. They are rapidly deployable, mobile, autonomous, simply operated, and capable of being used in severe geographic, climate and weather conditions. Individual products are available in the deployable or in-vehicle installed versions. They are MIL-STD compliant, and their typical features are impact resistance, temperature change stability, reliability, small dimensions, low weight, ease of use and simple maintenance. An important advantage of the products is usage of passive cooling technology, that predetermines long life cycle and low maintenance requirements. The products are of high quality and functionality which has been proven in real world military operations.
The company product portfolio includes COMTANET® tactical deployable ICT modules, COMTAG® tactical mobile communication system, ruggedized devices such as servers, routers, switches, power supply units, DC power distribution units, radio gateways, and Manet IP radios. An important part of the product portfolio is formed
By PAVOL GALIK Vice-Chairman of the Board of Directors, Aliter Technologies
by UAS solutions such as MMR mobile command post, and VIMA (VIrtual MAst) tethered drone system. The list of products is supplemented by the Laser Warning System, Simulation technologies and Tactical AVL system.
Aliter Technologies’ customers include multiple governments, enterprises, and international organizations. Aliter Technologies has also successfully delivered many contracts to NATO agencies and large defense contractors which includes but is not limited to Airbus Defense and Space, BAE Systems, Patria Land Oy and Ericsson.
Some notable examples of our portfolio include: MGCC (Mobile Ground Communication Component) IT Core HW and MBRs (Multiband Radios) for NATO AGS (Allied Ground Surveillance) Program; Deployable Area Communication System providing IP based voice, data and VTC services at the battalion and brigade command post level; Tactical communications system for self-propelled howitzers, rocket launchers including artillery command and control vehicles; Tactical C4ISR for SOF (Special Operations Forces); and Tactical communication systems for a number of different versions of the wheeled and tracked armored combat vehicles for the Slovak Armed Forces.
In conclusion, recent conflicts underscore the importance of advanced C4ISR solutions in modern warfare. Aliter Technologies stands at the forefront, offering innovative products and solutions to meet the evolving needs of defense and security operations.



NATO’s Assistant Secretary General for Public Diplomacy, Marie-Doha Besancenot, explains why after 75 years of NATO it is still crucial that the populations of the Member Countries understand the importance of NATO and its vital role in maintaining transatlantic security and stability
This year, we celebrate the 75th anniversary of the NATO Alliance. In all those years, NATO has prevented war and preserved peace throughout the Euro-Atlantic area. It has kept Europe and North America united, and helped to spread freedom, democracy and security across Central and Eastern Europe.
To this day, we keep our people safe and protect our shared values – democracy, freedom and rule of law. NATO truly is the most successful alliance in history.
NATO’s 75th anniversary is an opportunity to reflect on our successes and tell NATO’s story to a broader audience. We are using the momentum from this year’s milestone events – exercise Steadfast Defender, the 75th anniversary on 4 April, the Washington Summit in July, and more – to shape the narrative and give people accurate, credible information about who we are and what we do. In an alliance of democracies, our strength flows from the trust and support of our citizens. They are key to our success.
NATO’s story is much more than just a history lesson. In a dangerous world, NATO is more important and more relevant than ever to the one billion people who live in the Alliance.
We are in the midst of the most significant security crisis since the Second World War. Authoritarian states are challenging our security and our values. Russia’s war against Ukraine is the most immediate and direct challenge, but it is far from the only one. Authoritarian states such as Russia, China, North Korea and Iran are increasingly aligned. They are using all the tools at their disposal, not least disinformation and propaganda, to challenge and attempt to divide us. We also continue to face other persistent threats, including terrorism, sophisticated cyberattacks, the climate crisis and disruptive new technologies, each with important implications for our security.
As NATO has always done, we continue to adapt. One way we do this is by investing in the capabilities and technologies that help keep us safe now and in the future. These include state-of-the-art military capabilities to strengthen our deterrence and defence. We are also increasing our ability to respond to the relentless manipulation of the information environment.
In years past, our team would write summaries of the broadcast news and newspaper articles to inform NATO leadership about information trends. Today, we use sophisticated artificial intelligence-enabled tools for up-to-the-minute, global monitoring. We also share data and information with our military
colleagues, Allied capitals, and with like-minded partners, such as the European Union, the G7, Organization for Security and Co-operation in Europe, Organisation for Economic Co-operation and Development, and the United Nations. As a result, we are better able to identify and respond quickly to attempts to undermine our Alliance.
In the cyber domain, NATO’s Communications and Information Agency is on the front line 24/7, protecting our networks and ensuring we can fulfil our core tasks. Among other things, it provides the platforms we need to plan and execute complex missions involving Allied military forces, such as the integration of our air and missile defences.
There are many more actors in NATO’s ongoing story – from the Defence Investment Division’s work to develop our military capabilities, to the Office of the Chief Scientist’s strategic thinking on science and technology, and the incorporation of climate considerations into NATO’s core tasks.
NATO has an incredible story to tell, but our public diplomacy task is not easy. In a competitive information environment, we must be strategic and persistent in communicating our work to the world. We must also work with like-minded partners from business, academia and civil society, all of whom can speak with a unique level of credibility and reach broad and diverse audiences. By working together, I am confident the people we serve will know we are ready and able to defend their liberty and prosperity, and we will earn their trust and support for the next 75 years of this remarkable Alliance.



Simon: The 75th anniversary on 4 April 2024 was a truly auspicious moment for the NATO Alliance. Three quarters of a century is a very long time for any military alliance to endure, let alone continue to thrive and grow.
Lara: Indeed it is, Simon. Last year, we saw Finland join NATO, and this year Sweden finally joins the Alliance. In the previous issue of NITECH we were fortunate enough to have the Finnish Minister of Defence, Antti Häkkänen, offer a fascinating contribution on his nation’s ability to add value to NATO. This edition, Sweden’s Minister of Defence, Pål Jonson, has written an equally powerful piece about Sweden’s ambitions within the Alliance and how it sees the future for both NATO and Sweden.
Simon: The anniversary was an opportune moment for NATO to undertake one of its largest ever military exercises – Steadfast Defender 2024 (STDE24).
Without doubt, this was a massive undertaking, involving more than 90,000 troops from all 32 Member Countries.
Lara: Don’t forget that it also involved over 50 naval vessels and more than 80 aircraft, including fast jets such as the F-35 as well as helicopters and drones. Some of the warships and aircraft came across the Atlantic to take part, as did many of the land forces. It was incredibly impressive. It has not only honed the ability of the Alliance to conduct multi domain operations, but it has also shown the world how powerful the Alliance is as a partnership of nations able to integrate and interoperate.
Simon: That’s right, and in such a busy period we were extremely lucky for the Deputy Supreme Allied Commander Europe, Admiral Sir Keith Blount, to find time to explain what the exercise achieved and how the Alliance overcame some formidable challenges in successfully completing an incredibly ambitious training exercise spanning two continents and lasting several months.
Lara: Beyond those two momentous events, this edition has also helped to bear witness to two critical capability enhancements in the shape of a NATO strategy for quantum computing and the imminent completion of a
doctrine for countering unmanned aircraft systems, as they are now referred to. Both of these highlight how technology is accelerating the pace of military transformation. The Alliance now has a strategy for integrating quantum computing into its operations and capabilities. And, with DIANA (Defence Innovation Accelerator for the North Atlantic) now well and truly up and running, it will be able to grow the ecosystem to develop and deliver quantum-enabled systems. Cathal J. Mahon, Chief Business Officer at Deep Tech Lab –Quantum, is well placed to explain the implications of the strategy, and his interview is well worth a read.
Simon: Agreed, I thoroughly enjoyed learning about the new Quantum Strategy. The interview with Sean Bittick from the Alliance’s C-UAS Working Group also offers an insight into not only when we can expect the impending C-UAS doctrine to be published, but also how it was drafted and what benefits it will bring to the Alliance and the individual Member Countries as they seek to develop, test and field C-UAS systems.
Lara: NCIA has cause to celebrate too. The accreditation of the SANDI data science and AI sandbox last December is a key step forward in the ability of the Alliance to benefit from the vast volumes of data it gathers. For example, the data from the tools that NATO uses to plan and conduct operations can be brought into SANDI now that it has accreditation. That means new insights can be exposed in a secure fashion as part of NATO’s SECRET procedures.
Simon: That is not the only pioneering milestone that NCIA has achieved over the past six months. The first use of ‘Dynamic Sourcing’ in a NATO procurement will enhance NATO cyber security, and the speed in which it can be improved.
Lara: I am glad you brought that up as it gives me an opportunity to thank Mariana Antunes for writing that article. We were also lucky enough to have Talia Goode, Zainab Hashiru and Laura Danilas returning to NITECH with some engaging contributions. Sadly, Zainab and Laura have now left us to pursue their careers elsewhere, but we wish them the very best.
EMDYN Platform is our bespoke geospatial intelligence fusion application. It draws together location intelligence data from an array of sources in a single application to provide unparalleled insights into situations, events or patterns of movement. The technology behind EMDYN Platform delivers exceptional analytic and artificial intelligence capabilities, rapidly facilitating detailed analysis of a raft of sources including commercial and non-commercial data feeds. Learn more about EMDYN Platform: emdyn.com




Say goodbye to intelligence silos
Handle multiple Intelligence Sources from a single pane of glass
Build from the ground up for the Big Data era and process trillions of records near real-time
Highly Extensible and Customisable





Forewords
05 Marking 75 years of NATO
Ludwig Decamps, General Manager, NCIA
10 The most successful Alliance in history
Marie-Doha Besancenot, Assistant Secretary General for Public Diplomacy, NATO
12 Celebrating 75 years as an Alliance
Lara Vincent-Young and Simon Michell, co-Editors, NITECH
20 Key moments in NATO’s 75-year history
Since 1949, NATO has created an integrated military infrastructure second to none
22 Steadfast Defender 2024: enhancing Alliance unity and preparedness
Admiral Sir Keith Blount, Deputy Supreme Allied Commander Europe, NATO
28 Quantum-Ready NATO
Cathal J. Mahon, Chief Business Officer, Deep Tech Lab – Quantum
34 CCDCOE: keeping up with new technology
Mart Noorma, Director, Cooperative Cyber Defence Centre of Excellence (CCDCOE)
40 JFC Norfolk
Vice Admiral Douglas G. Perry, Commander of NATO’s Joint Force Command Norfolk

75 Years building a more secure NATO 44 NATO’s Secretaries General
A look at those who have filled this crucial position since the inception of NATO
C-UAS doctrine
Sean Bittick, Counter-UAS Working Group, NATO
54 View from the Nations: Canada
Bill Blair, Minister of National Defence, Canada
56 View from the Nations: Sweden
Pål Jonson, Defence Minister, Sweden
60 NATO’s evolution of NCIA
How NCIA (NATO Communications and Information Agency) came to be
62 Fighting anonymous threats – Northern Spirit/ Northern Challenge
Dr Cristian Coman, Principal Scientist, and Radu Cimpean, Senior Operations Specialist, NCIA
65 Enhancing network integration and interoperability
Matt Roper, Chief of Joint Intelligence Surveillance and Reconnaissance, NCIA
70 SANDI security accreditation
Dr Michael Street, Chief of Exploiting Data Science and AI, NCIA
73 Acquiring cyber security at speed –dynamic sourcing
Frederic Cloutier, Executive Advisor to the Chief of Staff, NCIA
76 NCIA: supporting cyber coalition
Tom Koolen, participant, NATO Cyber Coalition exercise
79 NATO ChatGPT
Dr Michael Street, Chief of Exploiting Data Science and AI, and Dr Sandro Bjelogrlic, Senior Data Scientist, NCIA
82 MN5G project
Luis Bastos, Head Innovating Team, Germano Capela, Senior Radio Engineer, and Alper Köprülü, Project Manager, MN5G, NCIA


86 Women in technology at NCIA
NITECH celebrates the contribution that women have made to NCIA’s technology development
89 Tech opportunities at NCIA
Daniel Sousa, former Data Science intern, NCIA
92 European Union’s Women TechEU
Martine van de Gaar, CEO and co-founder, Linksight
95 Farewell to John D. Patrick
Colonel John D. Patrick, founding Director, NATO Space Operations Centre (NSpOC) at Allied Air Command (AIRCOM)
Cloud services are the workhorse of digital transformation, but to achieve the best apps performance they must be weaved together using a new type of network

Joris van Oers
Managing Director, Global, BT
Digital technology is transforming how organizations operate by boosting the speed, effectiveness and resilience of their apps and business processes. By automating tasks, it can help organizations work more effectively but the latest wave of digital innovation powered by AI and machine learning goes further still.
With applications such as predictive analytics, organizations can strengthen the security and resilience of their systems and processes by spotting IT incidents before they can disrupt performance.
Cloud – the workhorse of digital transformation
The cloud is the workhorse of digital transformation. It offers capacity on tap to process and store the vast volumes of data organizations now create and consume and it helps turn it into actionable insight.
But when thinking about the cloud, it is important to realize that there isn’t just one type of cloud but many, and
there are several different cloud services providers.
The largest public cloud providers are known as hyperscalers. These include Microsoft Azure, AWS and Google Cloud. They offer services publicly and in many countries to organizations of all industries and sizes. They operate enormous data centres offering huge amounts of capacity on tap.
Many organizations continue to run their own data centres for a variety of reasons, from security or regulatory requirements to the need to maximise the return on capital invested. These are known as private clouds.
There’s edge cloud too – individual servers located on sites such as an organization’s offices, factories or depots. These might be used to aggregate data from local sensors before feeding it in bulk to central, large cloud facilities.
Many organizations now have a hybrid cloud estate, dispersing data and digital workloads across both private and public clouds and among various cloud service providers. This enables them to benefit from best-in-class capabilities but creates a complex mix of infrastructure for IT teams to manage as they try to strike the best balance of apps performance, cost, user experience, regulatory compliance and cyber security.
Traditional corporate networks were not built for this. They were designed at a time when almost all of an
organization’s people tended to be based in offices and other corporate buildings and all their applications and data were stored in a handful of their own privately operated data centres. This site-to-site connectivity – from office to data centre – was relatively simple.
Today, people and devices could be connecting from anywhere, accessing apps and data spread across multiple clouds.
Piling on pressure further still is the surge in data volumes expected from AI and the accelerating number of smart, Internet of Things (IoT) connected devices organizations now use.
Network-as-a-Service (NaaS) offers a new approach to connectivity. Designed specifically for multi-cloud, it makes it easy for organizations to view and control how their digital workloads move across multiple clouds, out to users and devices and then back again.
It’s like having a virtual toolbox that enables you to adapt your network to suit your needs, providing the flexibility and control to pick the best performing, most resilient and compliant routes for your digital workloads.
It makes use of AI and machine learning to offer unprecedented automation, meaning connections that previously could have taken weeks to provision can now be set up in an instant.

Like the public cloud, NaaS is pay-as-you-use, meaning costs can be tied directly to the organization’s demands.
Moreover, NaaS replaces expensive traditional network setups that require dedicated hardware – such as port, access and customer premise equipment (CPE) for each network service – with a shared, easily scalable infrastructure.
This network infrastructure enhances efficiency and reduces total cost of ownership by supporting automated provisioning and near real-time in-life management of services. It also allows multiple types and bandwidth of connectivity services on the same shared hardware, providing the flexibility to achieve the best total bandwidth allocation on demand.
Would you walk into unknown, possibly hostile territory with no idea of the risks you might face? I’m sure you wouldn’t, so why do it with your data?
NaaS is deterministic. This means you can choose the routes your workloads take as they move between clouds and out to users. For example, with standard internet connectivity, organizations have little control over the routes their
traffic takes. It could pass through national networks controlled by adversaries or where security is known to be lax
With NaaS, organizations can effectively geofence their traffic, keeping it within the borders of relevant jurisdictions and out of hostile territory.
NaaS can boost application performance and resilience too. With an end-to-end view of how each application’s workloads are moving between clouds, routes can be monitored and optimised in near real-time.
BT’s new NaaS, Global Fabric, seamlessly integrates global coverage, dense metro architecture – which means it has at least two Points of Presence (PoPs) in each metro zone boosting resilience – and software-defined intent-based routing. This combination delivers a resilient, high-performance network that easily adapts to changing conditions and optimises traffic flows to meet specific requirements.
Designed with a high-capacity core, with multiple 100 Gbps connections into major cloud locations globally, offering in-built resilience, Global Fabric handles large volumes of data or traffic easily.
It also provides real-time historical performance metrics that enable organizations to smoothly manage and optimise the performance and reliability of in-life mission-critical applications. By using continuous tracking, and analysing metrics such as latency, jitter and packet loss, it protects the health of an organization’s end-to-end application environment.
In the past, it’s been too easy for apps and clouds teams to overlook the importance of connectivity choices when deploying their new digital services. But, as digital transformation accelerates and workloads shift from private data centres into the cloud, this will no longer be the case. The networks team needs a seat at the table.
With the help of NaaS, they can help ensure your digital transformation is resilient and a success.
www.business.bt.com
Since 1949, NATO has expanded its membership from 12 to 32 Member Countries, creating an integrated military infrastructure and operational capability second to none. The Alliance has also added non-combat missions to its remit in support of nations overwhelmed by conflict or disaster
NATO was officially founded by 12 countries on 4 April 1949 with the signing of the North Atlantic Treaty (also known as the Washington Treaty). From the original 12 founder members, NATO has grown into an Alliance that now protects more than one billion people across Europe and North America.
The break-up of the Soviet Union in the final decade of the 20th Century paved the way for the most significant growth in the Alliance. Likewise, the subsequent disintegration of Yugoslavia ushered in a further period of expansion. Most recently, Russia’s illegal invasion of Ukraine in 2022 was the catalyst for Finland and Sweden to join the Alliance further raising the total of Member Countries to 32.

Originally created four years after the end of the Second World War to address the growing threat of the Soviet Union, NATO has steadily established a transatlantic military capability to safeguard the air, land, sea, space and cyber domains of its Member Countries. From its original deterrence focus during the Cold War, the Alliance has since taken on additional taskings such as peace-keeping, crisis-response and disaster-relief.
1950
NATO opens first headquarters in Belgravia Square, London
1968
1961
NATO establishes ‘Air Policing’ as an integral part of NATO’s Integrated Air and Missile Defence
1992 (October)
Operation Sky Monitor enforces no-fly zone over Bosnian airspace
1995
NATO conducts first major crisis response operation – the NATO Implementation Force (IFOR) in Bosnia and Herzegovina
1992 (July)
Operation Maritime Monitor establishes naval blockade to enforce UN sanctions on the former Yugoslavia
NATO establishes the Standing Naval Force Atlantic (STANAVFORLANT) to maintain permanent sea patrols. This was renamed SNMG1 in 2005


NATO replaces IFOR with the Stabilization Force (SFOR) to maintain peace and security in Bosnia and Herzegovina

1980
NATO establishes the NATO Airborne Early Warning and Control Force (NAEW&CF) to deliver airborne surveillance and C2
1992 (April)
STANAVFORMED formed to maintain maritime patrols in the Mediterranean Sea. Since renamed SNMG2 in 2005
1991
NATO develops partnerships with eastern European nations following the breakup of the Soviet Union
2014
NATO launches Enhanced Air Policing to bolster security of eastern European airspace
NCIA is established by merging NC3O, NCSA, NC3A, NACMA and ICTM

NATO launches Operation Sea Guardian to enhance stability and security in the Mediterranean Sea
1999
NATO establishes the NATO Kosovo Force (KFOR) to ensure a safe environment for entire Kosovan population
NATO airlifts more than 3,500 tons of disaster-relief supplies to Pakistan following a massive earthquake
2001
NATO invokes Article 5 of the Atlantic Treaty for the first time following the 9/11 terrorist attacks on the USA

NATO assumes command of the International Assistance Force (ISAF) in Afghanistan
NATO initiates the non-combat NATO Mission Iraq to help establish stable governance infrastructures and deter the return of ISIS/Daesh

2023
NATO coordinates airbridge to facilitate supplies to Türkiye following devastating earthquakes


Exercise Steadfast Defender is the largest series of military training events that NATO has undertaken in more than 30 years. Simon Michell asks Deputy Supreme Allied Commander Europe, Admiral Sir Keith Blount, how it will enhance NATO’s ability to conduct and sustain complex multi-domain operations (MDO) over a period of many months from the High North to Central and Eastern Europe


Why are exercises like Steadfast Defender so important to the Alliance preparedness?
Let me first underscore that NATO exercises are defensive, transparent and proportionate, and conducted in full respect of our international obligations.
Exercises are key to demonstrating the Alliance’s resolve and capability. Through exercises, we stress-test, adapt, streamline and improve our decision-making processes as well as the effectiveness of our alert and response system.
What is the overriding mission for Steadfast Defender 2024 series of activities?
Steadfast Defender 2024 was the biggest Alliance-wide effort for collective training in decades. It focused on promoting readiness across all domains and levels: tactical, operational and strategic. It was a series of NATO, national and multinational exercises under a single umbrella, with one clear message for all: we are ready! It was a clear demonstration of our unity, strength and determination to protect one another, our values and the rules-based international order.
The primary aim of the exercise was to train and demonstrate the ability of the Alliance to reinforce continental Europe via transatlantic movement of forces from North America and the UK.
Part 1 was a maritime-focused live exercise (LIVEX) led by Joint Force Command Norfolk that trained headquarters through rehearsing the strategic deployment of forces to continental Europe. This also included a demonstration of NATO’s ability to execute an amphibious assault in permissive and non-permissive environments.
Part 2 was a multi-domain demonstration of NATO, national and multinational military capabilities across continental Europe led by Joint Force Command Brunssum, in coordination with national exercise leads.
A focal point of Part 2 was the Very High Readiness Joint Task Force (VJTF) deploying to Poland, where the VJTF was integrated into the Polish Dragon 24 exercise.
The exercise demonstrated the enablement and employment of NATO and National Forces across all domains and across SACEUR’s Area of Responsibility. This reinforcement occurred during a simulated emerging conflict scenario against a near-peer adversary.
Steadfast Defender 2024 was the first large-scale NATO exercise where we put our new Regional Defence Plans, adopted at the Vilnius Summit, into action. This followed the stress-testing of the Defence and Deterrence of the Euro-Atlantic Area (DDA) family of plans in a complex exercise, Steadfast Jupiter, last autumn.
How have the participants been able to test their ability to sustain a complex multi-domain operation of this sort?
More than 90,000 forces, more than 50 ships, more than 80 air platforms flying hundreds of sorties, and more than 1,100 combat vehicles from all 32 NATO Allies have been exercising and testing their capabilities. Such a force has not been assembled since Exercise Reforger in 1988 with 125,000 participants, and Trident Juncture in 2018 with 50,000 participants.
In other words, every tank that rolls, every ship that sails, every aircraft that flies sends a message.
What, so far, have been the main challenges that have had to be overcome?
The challenges during Steadfast Defender 2024 were the fact that we had to coordinate, conduct and sustain complex multi-domain operations over several months,
across thousands of kilometres, from the High North to Central and Eastern Europe.
As the Alliance focuses on the principles of ‘Collective Defence’, the need to ensure the European continent is ready and ‘enabled’ has become an area of attention. This is complex and challenging, involving a multi-national and multi-agency approach that we are resolving through hard work, some investment and – of course – exercising.
What, so far, have been the key learning points from the exercise and how will they improve NATO’s ability to conduct MDO in the future?
Steadfast Defender 2024 has highlighted NATO’s ability to deploy forces rapidly from North America and other parts of the Alliance in order to reinforce the defence of Europe. The main lesson that we have observed is the same as always: complex exercises are essential to maintain and improve our operational coherence and expertise.


AWS provides a global infrastructure and secure, scalable, and mission-focused solutions that helps defence organisations globally outpace our adversaries, strengthen their mission advantage and rapidly adapt to shifting priorities.
The AWS Cloud powers national security and defence organisations through:
• Accelerating access to cutting-edge technologies
• Increasing the speed, impact and scalability of innovation
• Enabling rapid information analysis and collaboration
• Securing their most mission critical workloads.
Connect to our dedicated NATO Team ›



Reimagine the space domain and its missions with AWS Aerospace & Satellite
AWS helps customers reimagine how they design, launch, operate, and maintain space systems, derive insights to make better decisions faster, and accelerate innovation.
We bring together the most advanced, secure cloud infrastructure, broadest service portfolio, and extensive space industry expertise so you can simplify IT management and focus on your missions.
Kuiper
Whether on land, in air, or at sea, having connectivity and access to information in the field is critical for defence organisations.
Satellite communications systems provide critical capabilities – from delivering satellite imagery to enabling communications, that support military users operating around the globe.
Find out how AWS and Amazon’s Project Kuiper will help shape the future of global, ubiquitous, and secure internet connectivity throughout the space domain for the United States and its allies.
Learn more ›
A commercial alliance delivering decision-ready information for space domain awareness, maritime domain awareness, geospatial intelligence and beyond. Powered by AWS and the ARGUS Partner Alliance, ARGUS fuses best-in-class data with industry-leading infrastructure, analytics, visualization, security and compliance modules to deliver targeted insights for critical mission use cases.
ARGUS is from the ground up designed as an open architecture to:
• Deliver market leading tools and capabilities
• Access the right data to achieve critical insights
• Achieve instant interoperability and effortless integration.
Learn more ›


In January 2024, NATO published its first quantum strategy. But why does NATO need one and what challenges does it help to address? Former NCIA intern, Laura Danilas, spoke with Cathal J. Mahon, Chief Business Officer at Deep Tech Lab – Quantum, which is one of the official accelerator sites in NATO’s DIANA initiative, to answer these questions
Why does NATO need a quantum strategy?
To answer this question, I believe you need to go back to why the Defence Innovation Accelerator for the North Atlantic (DIANA) was set up initially. The purpose was to re-establish the technological edge that has been the fundamental rationale behind NATO’s strong defence posture since the end of the Second World War. That edge began to slowly wane around the end of the 1980s, and very recently NATO realized the need to re-establish it. Therefore, NATO identified nine emerging disruptive technologies (EDTs), with quantum being one of them.
Quantum is especially important as it truly is a disruptive technology, having huge implications for NATO’s defence posture, but also operational capabilities. For this reason, it is critical that NATO has a strategy for quantum. And the fact that it is one of the first of the nine EDTs to have its own strategy emphasizes its importance.

I think it would be very beneficial if every NATO Nation had its own quantum strategy. Many countries within the European Union either have one or are working towards developing one. NATO’s quantum strategy is a major step in the right direction, but national strategies are essential because they will be tailored to each country’s strengths and industrial bases.
What role do DIANA and the NATO Innovation Fund (NIF) play in the creation of a quantumready Alliance?
DIANA and the NIF are two stages in the value chain. At the initial stage we have DIANA, which operates the network of accelerators. The role of DIANA is to support tech companies that have EDTs for dual-use applications.
The main objective is to foster an ecosystem of quantum tech companies across the entire Alliance. Having a robust network of companies working in
varying technology areas is essential because they are dealing with civilian markets, where there is a wealth of opportunity and demand from a broad range of customers. This is a very diverse and dynamic ecosystem, driving continuous innovation in technology, applications and business models. At the same time, it enables companies to exploit the economies of scale, because the civilian market is considerably larger than the defence and security one. This is evident when looking at the history of the chip industry, whose first customers were the defence and security sector. Chip companies had to focus on generating demand from the civilian market, as this was the only way to scale the industry and ultimately, innovation.
DIANA does not only focus on technology, it also works to build effective teams and a better understanding of a product-market fit in civilian markets. And this is where the NIF comes in. Even though they have a
particular focus on dual-use technologies and companies coming through the programme, they also collaborate with various partners to syndicate investments. The companies emerging from DIANA need to attract different types of investors and therefore the civilian market component is vital in appealing to a broad range of investors.
Deep Tech Lab – Quantum is putting a lot of effort into supporting start-ups by giving them access to our knowledge, network, funding and infrastructure to help them commercialize their solutions. I have been visiting a lot of them on DIANA’s behalf to bring them into the NATO Quantum community.
What do you see as the main challenge right now regarding quantum and how can we overcome it? If we are discussing quantum technologies in the context of defence and security, we encounter challenges related to personnel, collaboration with


universities and engineering. These challenges are well known, but the primary focus within the context of DIANA should be to ensure that companies and researchers engaged in quantum technologies possess a comprehensive understanding of their applications. This is crucial to ensure they are able to develop something that meets the needs of the end users.
In the accelerator programme run at Deep Tech Lab –Quantum, the first module teaches companies how to identify your customer. Once the customer is defined, it is important to validate their interests, because often, initial assumptions do not align with actual needs. It is also an opportunity for the customer to express interest in something else the company could build for them; but they need to have that conversation. Therefore, from both the DIANA and NATO perspectives, it is crucial to facilitate dialogues
between quantum technology companies and end-users. If that is not done properly, a lot of resources would be wasted. It is also important to note here that determining a delicate level of disclosure that end users can provide is essential. This balance must be addressed to ensure that quantum technology is effectively tailored to specific applications.

Thorsten Ecke
Managing Director, INFODAS GmbH
What are the main threats that cyber criminals pose to critical infrastructures (CRITIS)?
Today, the threats to critical infrastructures are more complex and intricate than ever. They encompass way more than just cyber crime. Critical infrastructures have become the backbone of a complex information exchange of services and data that underpins the daily activities of entire communities – just think of energy, transport, healthcare and finance. A massive disruption of any one of these services could cause immediate panic on a huge scale. Not only that, it could have catastrophic economic consequences with billions of dollars potentially wiped out within a fraction of a second. This, in turn, could lead to major disruption to markets and international relationships. Last, but not least, it could result in severe consequences for the safety and security of entire populations.
Unfortunately, we are now living in an era of ‘unrestricted warfare’ where the boundaries between competition, rivalry and conflict is fluid and undefined and where the
areas of influence between conflicting powers are no longer limited to the activities of military forces. In line with the doctrines of multi domain operations (MDO), opposing forces are using all the instruments of soft and hard power to gain either supremacy or, at least, an advantage. We must therefore be aware that in this new MDO world, domains such as cyber and space make it easier for adversaries to operate horizontally across the legacy domains of land, sea and air and bring critical infrastructures into the realms of military overt and covert operations.
Recent unattributed attacks such as the one on the Danish electricity grid on 24 May 2023 or the infamous sabotage of the Nordstream 1 and 2 gas pipelines in the Baltic Sea on 26 September 2022 are merely two notorious examples of a new era of warfare that is only just beginning.
In this context, the ‘old Guard’ of cyber criminals, mainly motivated by financial gain, is being replaced by organized structures such as advanced persistent threats (APTs), which operate under, or act upon, a precise mandate. The strategies used by APTs are based on removing freedom of movement from an adversary, either as a direct act of aggression or as a deterrent according to the context of where and when the attack takes place. It is in this precise area that critical infrastructures come into the game. Operating in cyberspace (sometimes under a false flag), these APT entities are capable of producing tangible effects in the real world by cutting the primary lines of supply of a critical asset (power, water,
healthcare, finance) without any kinetic action. This is essentially no different from earlier forms of warfare where maritime traffic interdiction is an example of the same concept of cutting supply lines. That said, in historical terms, although the threat has not actually changed significantly, two factors have amplified the crisis around cyber resilience of critical infrastructures:
• today’s critical infrastructures are interconnected and interdependent and offer an almost infinite surface attack vector;
• the ease of operating in cyberspace in order to produce tangible effect on the physical world makes the threat persistent and ubiquitous.
How can these threats be mitigated in a comprehensive way?
Organizations need to understand that a well-orchestrated layered security (defence in depth) for a weaponized critical infrastructure should include military-grade components that ensure security in every situation. For many years, the protection of critical infrastructures has primarily relied on layers of general information technology (IT) security appliances like firewalls and IPS/IDS. While these solutions are certainly needed in a well-designed cyber resilience architecture, it is also vital that Data Loss Prevention (DLP) is taken into account. In fact, while firewalls and IPS/ IDS try to avoid malicious payloads from infiltrating the protected domains, they require constant monitoring and updating and they are often used as the stepping stones for the attacker to penetrate the network.
DLP solutions, like cross-domain solutions, work in a different way. They ensure that whatever happens (even if a threat vector is deployed in a protected network) the sensitive or mission-critical data sets are safeguarded, in every situation without any chance of them being compromised.
These solutions have been used for more than 20 years to protect the most critical information and assets in the military. In fact, infodas has been a pioneer in the field. Now, looking at the evolution of the hybrid battlefield, we are convinced that the time has come for other sectors beyond the military to embrace this paradigm of resilience and data protection.
What is the infodas SDoT Industry Gateway and how does it work?
The SDoT Industry Gateway is a security appliance that enables digital transformation in the industrial world. It works by allowing the interconnection of different domains such as IT and operational technology (OT), while preserving the security posture of the system.
The SDoT Industry Gateway is a derivative of our flagship product, the Security Gateway Express, which has been deployed in hundreds of military use cases around the world to enable, for example, command and control/machine-to-machine communication. As opposed to the military version, which is more focused on supporting tactical protocols and formats such as VMF and JREAP-C, the Industry Gateway enables the use of widely recognized industrial protocols such as MQTT and OPC-UA. As such, the SDoT Industry Gateway, which interconnects IT and OT, is an enabler of the industrial Internet of Things.
But, whereas many other products used in the industrial world are simple unidirectional optical diodes, the SDoT Industry Gateway can either be deployed as a diode (unidirectional gateway, which facilitates the monitoring of OT from IT), or as a fully bidirectional gateway that can enable command and control. Plus, it can be upgraded during its lifecycle. This means that the user can opt to start with a unidirectional gateway, and, at a later stage, decide to upgrade his appliance to a bidirectional gateway.
Knowing that the industrial world prefers OpEx to CapEx, the SDoT Industry Gateway is offered through a turnkey subscription model that includes every component the end user will need – from the hardware to the configuration, training, support and warranty.
What certifications does the SDoT Industry Gateway have across the world?
As I said, the SDoT Industry Gateway derives from our flagship product –Security Gateway Express. In this early stage of market entry, rather than going for a raft of certifications, we have decided to listen to our clients and concentrate on the certifications they deem most valuable and useful.
For example, the railway world may be interested in the ISO IEC 62443 certification, so we are currently assessing whether to include it in our product. In terms of our diode, we have achieved the important certification for the maritime sector relating to UR E26 and E27 and to the Bureau Veritas’ NR659.
Which CRITIS operators could benefit from the SDoT Industry Gateway and how?
There are a number of operators that might benefit from the SDoT Industry
Gateway, not only from the point of view of the Return on Security Investment (ROSI), but also from a compliance perspective.
We know that some industries, such as energy, transport and healthcare have specific obligations for the protection of the data they collect and/or for business continuity in provisioning services. The SDoT, a robust, reliable and proven cyber-resilience posture, ensures compliance without having to completely redesign the entire system to achieve the required levels of protection.
I would say that the infodas SDoT Industry Gateway is a must have for all operators who, according to a national or international regulatory framework, fall under the banner of national critical infrastructure with all the associated obligations and liabilities.

www.infodas.com



The Director of the Cooperative Cyber Defence Centre of Excellence (CCDCOE), Mart Noorma, offers an intriguing insight into how communications and network security has changed since the establishment of NATO and highlights how the CCDCOE embraces new technologies to support the Alliance. He also explains how NCIA adds value to the CCDCOE activities and technology adoption
How does the CCDCOE support NATO’s cyber security activities?
The CCDCOE serves as NATO’s accredited Center of Excellence specifically focused on fostering international cooperation in cyber defence among NATO and likeminded nations. We support the process of mainstreaming cyber security into NATO and national governance and capability within our focus areas of technology, strategy, operations and law. We offer NATO and Member Countries specialized expertise, doctrine, guidelines, research, education and training programmes. We also organize one-of-a-kind flagship exercises to address evolving and complex cyber threats.
As the custodian of the Allied Joint Doctrine for Cyberspace Operations (AJP 3.20), we bear the responsibility of continually updating and maintaining this doctrine to ensure its relevance and accuracy for the Alliance. Collaborating closely with Allied Command Transformation, we also undertake research projects aimed at further enhancing our understanding and response to emerging cyber challenges. The CCDCOE also acts as the Department Head for the cyberspace operations discipline and our experts participate in the planning and execution of NATO’s flagship cyber defence exercise Cyber Coalition.
What role does technology play in this effort and how has it changed since the establishment of the CCDCOE?
Digital connectivity and the adoption of new technology has elevated the importance of cyber security for all digital societies. The ongoing democratization of artificial intelligence (AI), notably large language models and generative AI, as well as other technologies, render the key role of cyber defenders in national security even more critical.
In recent years, the CCDCOE has embraced new technologies into our activities across research, experimentation, training and exercises. Each year, we keep innovating the annual iterations of our flagship cyber exercises Locked Shields and Crossed Swords. For example, in 2023 we used an AI Blue Team at Locked Shields and made the AI-generated exercise data available to the broader research community. This year, our industry partner Siemens provided an innovative industrial control system to the exercise, challenging its 4,000 participants.
We also conduct technical research and experimentation regarding the cyber security of the next-generation mobile communications network, 5G.
Our annual Cyber Conflict Conference convenes more than 600 experts and researchers from legal, technical and policy academic disciplines. This year’s conference, held in May, focused on emerging and disruptive
technologies (EDTs), and their implications to national security and cyber defence. It also discussed related opportunities and challenges.
What are the main challenges in keeping up with technology evolution? Who are the key players the CCDCOE must protect against and work with? As an international military organization, we rely on trusted partnerships that have supported our core competence areas and activities over the decades. One of the main challenges is the speed of technology development and adoption in the private sector, which outpaces the capabilities of national governments, academia and international organizations. We lean on our strengths – our people and partners – and continuously strive to offer them value and integrate technological innovation. Thus, the first challenge is to leverage opportunities for technological advancements and integrate them into our daily business.
The second challenge is broader. At the moment, despite malicious actors adopting generative AI and other tools to augment their techniques, tactics and procedures, cyber defence is prevailing. But we need to recognize that we are in an ever-accelerating game of cat and mouse and need to maintain our current technological edge and defender’s advantage. Steps, including larger investments into capabilities, must be taken and we need to speed up the efforts of integrating AI more rapidly into cyber security and cyber defence.
“
In everything we do, we bring together whole-of-society stakeholders with whom we have invested in strategic partnerships over many decades. These partnerships are our priority”

A third challenge is that, as the NATO Science and Technology Organization report highlights, EDTs will become increasingly intelligent, interconnected, decentralized and digital, and it is difficult to forecast how technologies will converge and what the specific effects through cyberspace will be. Cyber defenders must be fit to mitigate novel and converging risks from multi-domain operations, increased interconnectivity and networking, speed, autonomy and so on. In this regard, we support Allied Command Transformation with several research projects and workshops elucidating future cyberspace trends and their policy implications. Our research dissects legal, ethical, operational, policy and technical concerns related to new technologies.
Regarding malicious cyber actors, we are targeted by the same threat actors as Member Countries and the NATO Alliance, including nation-state threats, non-state threats and individuals.
In everything we do, we bring together whole-of-society stakeholders with whom we have invested in strategic partnerships over many decades. These partnerships are our priority. Our industry partners come from the traditional defence industry, cyber security companies, IT service providers, vendors of industrial control systems
and other operational technology. We work with international organizations, government agencies, academia and non-profit organizations. As a knowledge and talent hub for cyber defence, we integrate new technologies and corresponding procedures into our activities in education, training, exercises and research.
How do the CCDCOE and NCIA work together to enhance network and data security?
Cyber experts from NCIA’s NATO Cyber Security Centre have participated in the Locked Shields exercise for 13 years. As the cyber threat landscape evolves rapidly we welcome greater engagement and partnership, for example, through support to the exercise planning and assessment, or help integrating AI experimentation tools.
NCIA experts are welcome to our annual conference and we would like to contribute to the NATO Edge conference with our subject matter expertise.


Chief Security Strategist and Global VP Threat Intelligence, FortiGuard Labs, Fortinet
In the second half of 2023 (2H23), according to the semi-annual Global Threat Landscape Report by FortiGuard Labs, cyber adversaries are moving quicker than ever, exploiting new vulnerabilities 43% faster than during the first half of the year (1H23), with attacks starting on average just 4.76 days after new exploits were publicly disclosed.
In addition to this increased agility, there is strong evidence that attackers are targeting with increased precision
as they learn which kind of organizations are likely to yield the biggest returns and hone their tactics accordingly for optimal efficiency.
So, although the 70% drop in total ransomware detections seen in 2H23 (after surging by a factor 13 in 1H23) may sound like good news, this is almost certainly due to heightened targeting. This is supported by the data which showed that botnets, upon which many ransomware attacks depend, remained consistent, showing incredible resilience during the same period.
It is also in line with the FortiGuard Labs 2024 Threat Predictions Report, which forecast that in their search for bigger payouts, adversaries would turn their attention to critical industries such as healthcare, utilities, manufacturing and finance, which is now evidenced as what we are seeing based on FortiGuard Labs research.
In the case of ransomware and wipers (malware designed to erase victims’ data), the most notable targets in 2H23, accounting for 44% of all detections, were industrial and Operational Technology organizations, including energy, healthcare, manufacturing, transportation and automotive.
Unsurprisingly, due to their frequent lack of inherent security by design, some of the most targeted endpoints within this sector were Internet of Things (IoT) devices such as routers, cameras and industrial sensors, many of which may now be decades old and are often underprotected or entirely unprotected.
But even where security patches exist for common vulnerabilities and
exposures, 86% of the intrusions investigated by FortiGuard Labs in this period occurred through the exploitation of known vulnerabilities (an N-Day vulnerability) for which patches were readily available.
And while 41% of the organizations contributing to FortiGuard Labs’ telemetry detected exploits from signatures less than a month old, nearly all of these organizations (98%) detected N-Day vulnerabilities that have existed for five years or longer, suggesting that such dated attacks are still finding their mark. In fact, FortiGuard Labs is still detecting the exploitation of vulnerabilities more than 15 years after their initial disclosure.
In this climate, both vendors and customers have a role to play. Vendors must introduce robust security scrutiny at all stages of the product development life cycle and dedicate themselves to responsible radical transparency in their vulnerability disclosures. Organizations must remain vigilant about security hygiene and act quickly through a consistent patching and updating programme to reduce the risk of exploitation.
With threat groups adapting their tactics so rapidly and with new, ever-more sophisticated attacks appearing almost daily, we need a new, more unified approach to cyber security, with deeper integration and convergence of technology at a solution level, and a new culture of collaboration and transparency – not just within organizations – but across industries and borders, and
encompassing all parties – vendors, customers and government entities.
And while the idea of increasing security through alliance and collaboration should already be familiar to those of us within NATO, it hasn’t always been central to cyber security strategy. To turn the tide against bad cyber behaviours, it requires a culture of collaboration, transparency and accountability on a larger scale than from just individual organizations in the cyber security space. Every organization has a place in the chain of disruption against cyber threats.
Similarly, convergence of networking and security technology together with a Zero Trust approach can significantly reduce administrative complexity by unifying visibility and control of network security, regardless of user, device, location, mode of access or how applications are delivered.
Instead of implicitly trusting anything within a secure perimeter, Zero Trust takes the opposite approach – that no user or device transaction is trusted until identity and status has been confirmed.
By moving from implied trust based on network location to a model where trust is repeatedly evaluated on a per-transaction basis, the same access security policy can be applied everywhere – for users, whether they are in the office, on the road or working from home and for userindependent IoT devices. This not only strengthens the overall security posture for an organization but greatly simplifies its management.
But what about the accelerated attack time frame whereby for new exploits identified, attacks occurred in 4.76 days after discovery? With our adversaries targeting exploits within mere days of disclosure, how can we shrink the time taken to detect and respond to each new threat?
Organizations must remain vigilant about security hygiene, as attackers are not likely to stop exploiting older vulnerabilities and security practitioners need to act quickly through a consistent patching and updating programme when new vulnerabilities emerge.
As cyber threats continue to grow and evolve, so does the need for innovative solutions and reliable threat intelligence. Tapping into advanced threat intelligence can enable an organization to quickly evolve its security posture to address the latest threats and trends. It is critical to integrate advanced threat intelligence into threat response processes, so an organization can quickly understand an impending threat, what entry points may be vulnerable and what actions to take.
Additionally, artificial intelligence (AI) and machine learning can play an important role by automating key parts of the detection, analysis and response process, as can a well-integrated SecOps platform capable of unifying security across all environments.
The other key ingredients are transparency and collaboration. Through more proactive and responsible communications, findings reported are responded to appropriately. Timely and ongoing communications by vendors to proactively and responsibly disclose vulnerabilities and for victims of a cyber intrusion help protect and secure organizations across the global cyber-ecosystem.
New regulations such as the second European directive for network and information systems (NIS2) should help in this regard and includes the recommendation of heavy fines for failure to report new security incidents within vastly shortened time windows.
Every organization has a place in the chain of disruption against cyberthreats. Collaboration with high-profile, well-respected organizations from both the public and private sectors, including CERTs, government entities and academia, is a fundamental aspect of Fortinet’s commitment to enhance cyber resilience globally.
FortiGuard Labs will continue to monitor the worldwide attack surface through its millions of network sensors, employing AI to mine that data for new threats to get a better understanding of what is coming to offer actionable threat intelligence, such as in its 2H23 Global Threat Landscape Report.
In addition to this, collaboration with high-profile, well-respected organizations from both the public and private sectors, including CERTs, government entities and academia, is a fundamental aspect of Fortinet’s commitment to enhancing cyber resilience globally.
It is through constant technology innovation and collaboration across industries and working groups, such as Cyber Threat Alliance, Network Resilience Coalition, Interpol, the World Economic Forum (WEF) Partnership Against Cybercrime and WEF Cybercrime Atlas, that will collectively improve protections and aid in the fight against cyber crime globally.

fortinet.com/blog/threat-research/ key-findings-2h-2023-fortiguardlabs-threat-report
fortinet.com/blog/threatresearch/2024-threat-predictionschained-ai-and-caas-operations
fortinet.com/blog/industry-trends/ how-proactive-responsibletransparency-benefits-customers


Simon Michell asks the Commander of NATO’s Joint Force Command Norfolk, Vice Admiral Douglas G. Perry, how his organization plans, prepares and undertakes missions across its area of responsibility

What is JFC Norfolk’s current mission and how does it achieve it?
Joint Force Command Norfolk’s mission is to provide command and control to NATO Forces operating in peacetime, crisis or conflict to deter and, if required, defeat NATO’s potential adversaries. Our focus is defending the Strategic Lines of Communication between North America and Europe and reinforcing the transatlantic bond that has been the cornerstone of the NATO Alliance for 75 years, an anniversary NATO is celebrating this year. We deliver in our area of responsibility, on NATO’s three core tasks – collective defence, crisis management and cooperative security.
We achieve our mission through coordinating and synchronising multinational military operations across our area of responsibility. This involves daily contact with national authorities and other entities in NATO, both in North America and Europe to ensure Allied military operations are cohesive, efficient and achieve NATO’s aims and objectives.
What is JFC Norfolk’s area of responsibility and why?
Joint Force Command Norfolk is primarily responsible for the Atlantic and the Arctic, and we are responsible for the vast majority of Supreme Allied Commander Europe’s Area of Responsibility. The Strategic Lines of Communication that unite North America and Europe are vitally important to NATO and we were established to ensure their security in peacetime and, if necessary, defend them in crisis and conflict.
Joint Force Command Norfolk was re-established in 2019 due to the resurgence of Russian military activity in the Atlantic and Arctic. Russia’s maritime doctrine states that the Arctic is its primary focus for the Russian Navy and furthermore Russia has invested significant amounts of resources in expanding its Arctic presence. This has included the re-opening of Soviet-era military facilities and building new ones as well as re-organizing its Northern military district.
Russia’s ongoing, illegal war of aggression in Ukraine has entered its third year and this has only validated NATO’s decision to establish Joint Force Command Norfolk as well as establishing NATO’s Joint Strategic Enablement Command in Germany. Although Russia has suffered combat losses in Ukraine, the Russian Navy remains predominantly unaffected and continues to expand
with new surface combatants and submarines being brought into service. These platforms represent some of Russia’s most potent offensive capabilities.
Can you explain the role of emerging technologies in JFC Norfolk’s activities including in the domains of space and cybersecurity?
NATO as a whole is still actively integrating Space as a domain and is developing a Strategic Space Situational Awareness System at NATO HQ, increasing NATO’s space capabilities. Prior to this, NATO established the NATO Space Centre at Allied Air Command in Ramstein, Germany. The Alliance is not aiming to develop space capabilities of its own and will continue to rely on national space assets, though NATO is investing over €1 billion in procuring satellite communications services from 2020 until 2034.
At Joint Force Command Norfolk, while we don’t have integrated space and cyber capabilities, we work routinely with our fellow NATO entities to provide these capabilities on our behalf. Cyber security is provided and enabled by NCIA, NATO’s cyber subject matter experts. Our fellow North American Command, Allied Command Transformation pioneers NATO’s development on incorporating new technologies, including space and cyber, into NATO. They ensure NATO remains relevant and fit to address the challenges of the 21st century, looking ahead to understand, analyse and integrate new technologies into NATO.
How is JFC Norfolk enhancing the Alliance’s ability to conduct multi-domain operations (MDO)? MDO works by leveraging our supporting component commands alongside national capabilities in order to deliver effect as and where required. This is e ssential for Joint Force Command Norfolk as we need to be agile, responsive and resilient across our expansive area of responsibility. On a practical level we work to increase our coordination and efficiency while conducting MDO on a daily basis by deepening our partnerships, cooperation and communications with the nations in our area of responsibility across all domains.
We test our ability to conduct multi-domain operations through exercises, such as NATO’s Steadfast Defender, where we stress our command and control systems, working with real-world assets. Through exercises, we

test our processes and procedures learning from our mistakes, identifying the lessons and taking them forward with us. To our component commands we provide cohesion and focus for the multi domain requirements so that we can achieve SACEUR’s intent in our area of responsibility, which is the largest in NATO. Covering both the Northern Atlantic and the Arctic, Joint Force Command Norfolk has novel challenges covering such an expansive area and it is imperative that we optimise our ability to deliver on MDO in these vital areas.
How does NCIA support JFC Norfolk in achieving its mission?
NCIA helps not just Joint Force Command Norfolk but all other NATO entities, NATO allies and our partners communicate and share information together to fulfil our respective missions and tasks. Through federated mission networking from NATO to national gateways, NCIA enables communication – a critical component of
warfighting capability. In this modern world, the threat that cyber attacks pose to NATO is prominent and NCIA is NATO’s front line against the cyber threat defending NATO’s operations in cyber space. Working alongside industry and academia, NCIA leads the advancement of NATO’s CIS projects to look at delivery of communications abilities in the future and to ensure NATO’s communications remain robust, modern and efficient.
On a day-to-day basis, they are on-hand 24/7 to provide technical support and assistance to our operations ensuring our resilience, to allow us to focus on delivering operational outputs as well as providing cyber and technological advice as we require. Most importantly, they provide and maintain our Command and Control systems, which are absolutely essential for Joint Force Command Norfolk to deliver on operations on behalf of NATO.

The post of NATO Secretary General was established in 1952 and has been filled by a European civilian – usually a prominent politician or diplomat. Its first incumbent was the British politician, Lord Ismay, who was persuaded by Winston Churchill to take the position. Since then there have been 12 other Secretaries General from Belgium, Denmark, Germany, Italy, Norway, Spain, the Netherlands and the United Kingdom. The longest-serving Secretary General was the Dutch politician Joseph Luns, who served from 1971 to 1984

Lord Ismay, 1st Baron Ismay: British – 1952 to 1957
Former soldier and Secretary of State for Commonwealth Relations in Winston Churchill’s Government. Ismay is credited with laying the foundations for NATO’s key administrative functions.

Paul-Henri Spaak: Belgian –1957 to 1961
Nicknamed ‘Mr Europe’, Spaak was a prominent politician well-versed in international affairs, having presided over the first General Assembly of the United Nations in 1945.






Dirk Stikker: Dutch –1961 to 1964
Leading banker, diplomat, politician and industrialist. Having taken up the post in 1961 he resigned due to ill health two and a half years later.
Joseph Luns: Dutch –1971 to 1984
Highly influential politician, diplomat and jurist. Longestserving NATO Secretary General whose tenure was dominated by US/Soviet arms control talks and the Soviet invasion of Afghanistan.
Manfred Wörner: German –1988 to 1994
Politician and diplomat. He oversaw the fall of the Berlin Wall and NATO’s first use of force – the downing of four Bosnian Jastreb military jets.
Javier Solana: Spanish –1995 to 1999
Politician and skilful negotiator who presided over NATO’s peace-keeping efforts in Bosnia and Herzegovina and the accession of Czechia, Hungary and Poland.
Jaap de Hoop Scheffer: Dutch – 2004 to 2009
Politician, diplomat and jurist. His tenure witnessed further expansion of the Alliance as well as out-of-area operations in the Indian Ocean, Pakistan and Africa.
Jens Stoltenberg: Norwegian –2014 to 1 October 2024
Career politician and former Prime Minister of Norway. He has presided over the biggest reinforcement of NATO’s collective defence since the Cold War.






Manlio Brosio: Italian –1964 to 1971
Career diplomat who oversaw France’s departure from NATO’s military structure, tensions over Cyprus, the Cold War and the relocation of NATO HQ from Paris to Brussels.
Lord Carrington: British –1984 to 1988
Refined, cultured and personable politician. His tenure witnessed intense political tensions among Member Countries, including putative troop withdrawals from Europe.
Willem (Willy) Claes: Belgian –1994 to 1995
Politician and talented musician who served for 12 months as Secretary General. He resigned on 20 October 1995 just over one year into his tenure.
Lord Robertson: British –1999 to 2003
Politician who served as UK Secretary of State for Defence. His period in office as Secretary General witnessed NATO’s first use of Article 5 following terrorist attacks on the USA.
Anders Fogh Rasmussen: Danish – 2009 to 2014
Career politician and former Prime Minister of Denmark. He initiated the ‘New Strategic Concept’ document and became the first Secretary General to use social media.
Mark Rutte: Dutch – 1 October 2024 onwards
Former businessman and politician. He worked as a manager at Unilever before serving as Prime Minister of the Netherlands four times between 2010 and 2024.

Awadh Kapoor
Director, Digital Transformation, Worldwide Defense and Intelligence, Microsoft
What does Microsoft think about the ’digital advantage’ for future warfare?
Allied nations must prioritize increasing their tech intensity to gain a digital advantage over competitors. This involves developing digital capabilities, fostering a supportive environment and emphasizing digital transformation and innovation. Recent conflicts have shown that digital advantage cannot be accomplished with legacy isolated and disconnected ICT environments. The solution lies in the adoption of hyperscale cloud. Furthermore, as conflict moves increasingly to multidomain operations, nations and coalitions that have a digital backbone can support secure interoperability across all domains, enhance situational awareness, and facilitate alliance collaboration and data-driven decision making – and will have the advantage.
We see the digital transformation to achieve this advantage spanning five key pillars across the defence ecosystem:
First: Deploying a trusted and secure digital backbone, as well as modernization of IT and technology stacks.
Second: Empowering personnel to deliver missions and modernize facilities. We are enabling digital transformation to modernize the individual defence worker experience; everyone from the soldier serving on the front lines and the defence office worker at headquarters, to the engineer working at the industrial base. And, with respect to facility modernization, we are helping defence forces take a ’Smart City’ approach to facility modernization, including a big focus on sustainability initiatives.
Third: In parallel, it is fundamental to transform the capability lifecycle – this is all about transforming the way forces and the defence industrial base conceptualize, design, collaborate, deploy and sustain mission capability, with a focus on leveraging modern methodologies and digital capabilities such as digital engineering, agile systems and digital twins. The intent is to modernize the lifecycle and enable innovation at the speed of relevance.
Fourth: With the right foundations and the ecosystems brought to a good digital maturity, optimizing the decision advantage becomes inevitable. This is about helping forces harness their data as an asset and accelerate the OODA loop – Observe, Orient, Decide, Act.
Fifth: Enhancing interoperability. The focus is on enabling secure information exchange across partners, coalitions and with industry.
How does Microsoft see the evolution of generative AI in defence?
To address this, it is pivotal to understand the reasons behind the widespread adoption of generative AI or large language models (LLMs) in contrast to traditional AI frameworks. The conversational capabilities of LLMs in
natural language render them more accessible and user-friendly, even to those within an organization’s business operations, which may lack ability in data science or the deployment of AI models. Generative AI has the potential to integrate seamlessly into any scenario that involves human interaction. Consider the following examples:
AI-assisted personnel support –Commencing with recruitment, GenAI-powered chatbots can evaluate an individual’s readiness and interest in joining a specific defence force’s corps and offer suitable recommendations. Coupled with advanced cognitive image recognition and sentiment analysis, life-sized digital displays can be strategically positioned in public venues such as shopping centres, where these chatbots serve as an initial screening tool for recruitment. This support extends beyond service, aiding in the seamless transition of service members to civilian life as veterans. With a wealth of historical data on veterans’ transitions, the chatbot can proffer advice on post-service career paths.
Training and professional development – Post-recruitment, the task to expedite the readiness of forces for combat is formidable. With finite resources for training, particularly in equipment handling, new recruits often face protracted waiting periods. A training chatbot can optimise this interval, enabling personnel to interactively query archived doctrines and lessons learned using natural language. Generative AI can also synthesise training scenarios and content derived from antecedent war games and simulations, broadening the scope of training possibilities.
Asset maintenance – Once personnel are recruited and trained, equipping
them with the requisite assets is paramount. Whether it pertains to tanks, aircraft, naval vessels or other armaments, maintaining these assets with high reliability is crucial. In a setting constrained by resources, a digital maintenance assistant can be exceedingly beneficial. Envision the utility of an LLM meticulously fine-tuned on extensive aircraft maintenance manuals, amalgamated with historical maintenance logs. Such a ‘Maintenance Copilot’ could expedite the troubleshooting process for technicians and even proffer advanced recommendations for a proactive maintenance strategy.
The potential applications are indeed boundless. As defence organizations deepen their comprehension of generative AI models, they can progress towards strategic implementations. Such advances may include the generation of Operational Orders within the missionplanning phase. For example humanitarian aid and disaster recovery scenarios, adhering to the commander’s guidance, while always ensuring a human in the loop for all safety-critical situations. This approach ensures that while leveraging the efficiency of AI, the critical oversight and decision making remain firmly within human control. Another dimension of progress can be in the tactical edge environments, with the use of natural language for operational assets such as Remote Autonomous Systems (RAS), or for querying the C4ISR data received from sensors in the field.
How is Microsoft helping NATO to derive value out of generative AI?
We are steadfast in our commitment to safeguarding democratic principles and the foundational values of NATO. Microsoft stands as a strategic partner to NATO in both policy and technological spheres. Our offerings are aligned with the strategic objectives of NATO’s digital transformation, interoperability and resilience, mirroring our core mission of enabling every organization to accomplish more. Our leadership in
areas such as cyber security, AI, digital transformation and technological innovation is well established, and we are eager to exchange best practices with the Alliance. We have demonstrated how our solutions can bolster the Alliance’s interoperability while honouring the sovereignty aspirations of Member States. With recent engagements on developing a secure private Azure OpenAI-powered Chatbot for knowledge discovery and application of LLM’s to NATO standards and terminology, we have demonstrated the innovative capabilities for the needs of the NATO enterprise.
How do you define an AIready defence organization?
To effectively harness AI, defence organizations must cultivate an AI-ready culture, driving adoption and utilization. Such a culture champions ongoing learning, creativity across all roles and data-centric decision making. The first key element is this cultural shift. Secondly, a robust digital infrastructure combined with a clean and wellcatalogued data estate is crucial, enabling the use of data as a strategic asset and unlocking the cloud’s potential. Thirdly, AI democratisation equips the entire workforce, beyond technical specialists, to leverage data and enhance their roles, from headquarters to base to battlefront. Lastly, responsible innovation is paramount. AI’s significant impact necessitates adherence to the highest ethical standards in its research, development and application but also in defence operations, especially across mission-critical use cases.
What steps has Microsoft taken to ensure the responsible use of AI in safety critical applications in defence?
Microsoft provides actionable guidance for our teams and customers, going beyond high-level principles to create AI systems that uphold these values and earn society’s trust. We also have an Office of Responsible AI that sets governance policies, advises leadership
and ensures responsible practices across the company.
What guidelines can Microsoft provide to the broader defence community to ensure the responsible use of generative AI?
When starting, it is advisable to adopt a gradual approach and expand progressively. Ideal applications include text analysis, summarization, form processing and content creation. These areas represent the optimal use cases. Additionally, it facilitates information discovery and knowledge mining. It is crucial to note that generative AI models are not engineered for numerical computations, real-time data processing or to supplant intricate risk-assessment models. It is also not recommended to dispatch AI-generated advice or content directly to senior defence officials without human oversight. Initial prudence combined with a ’human in the loop’ approach can leverage value out of high-impact use cases, such as:
• The generative design of equipment where safety is of the utmost importance; for instance, ensuring the safety of flight operations.
• Analyses that influence the course of action and decisions that are critical to missions and safety on the battlefield.
At Microsoft, we are committed to partnering with Allied nations to help them use technology beneficially. This includes equipping defence organizations with the tools and capabilities needed to counter diverse and rapidly evolving global threats. Without doubt, AI is a crucial element of any future-ready defence force.


Sean Bittick from NATO’s Counter-UAS Working Group reveals the purpose and content of the Alliance’s Counter UAS doctrine, which is due for publication by the end of 2024
The proliferation of unmanned aircraft systems (UAS) poses a significant threat to NATO’s security. That is why it is hoped that the soon-to-be-published Counter-UAS (C-UAS) doctrine will provide a robust framework for NATO to efficiently detect, track and neutralize unauthorized UAS that pose a threat to its operations and personnel. This sounds like a very simple statement of fact, but, in reality, it is a very complex and challenging issue for everyone involved. In part, this complexity lies in the fact that there are myriad nuances associated with UAS. For example, they cannot all be corralled under the same categorization as they come in multiple different sizes with numerous diverse capabilities and operating characteristics. When it comes to countering them, there is no one-size-fits all panacea.
NATO has however, grasped the nettle and is on the cusp of publishing a doctrine for the smallest group of UAS – Class 1 – those of 150 kg or below. This will ensure NATO Member Countries are equipped with the necessary technology and training to effectively respond to the UAS threats that fall within this class. It is also hoped that it will enable NATO to coordinate with
other international organizations and countries, thereby facilitating a comprehensive response to Class 1 UAS threats at a global level.
One of the key protagonists behind the drafting of the new doctrine, Sean Bittick, C-UAS and Capability Development Officer for NATO’s Innovation, Hybrid & Cyber Division, is hopeful that the Class 1 C-UAS doctrine should be published before the end of 2024. As one of the authors of the doctrine, he has unparalleled insight as to its scope, purpose and schedule.
One of the first things he points out is that UAS now stands for unmanned aircraft systems as opposed to its former moniker – unmanned aerial systems. Next, he defines doctrine and puts it into context: “Policy relates to decisions made by civilians at the higher levels of military control as to what they require the military to achieve, and doctrine is a set of instructions and guidelines to support military organizations as they develop a modus operandi for achieving policy.” As such, doctrine seeks to understand the very essence of a problem and highlight the best practices for how to
solve it. In Bittick’s words, “It is a standardization and coherence effort to take all of the best information currently available to us and put it into a single source of information, such that whether you are an expert in C-UAS or if you are completely new to the subject, you should be able to understand the threat, plan how to counter it and then execute that plan.”
The effort to create the doctrine started about three years ago and was a recognition that despite the proliferation of UAS and the obvious game-changing impact they are having on, for example, conflicts in Ukraine and the Middle East, there is a lack of national-level C-UAS doctrines across the Alliance. “There are some service-level doctrines, but as far as I am aware there are no joint publications for C-UAS,” explains Bittick. This has led to a NATO-wide gap in the understanding of how to fight this threat, resulting in a level of uncertainty that is not addressed by existing doctrine. The C-UAS doctrine that is on the verge of being published answers many questions for
everyone, especially the air-defence and force protection communities – two segments of military operations that are both massively affected by the surge in UAS activity.
It will also have a wider impact. “I think that the doctrine itself will have a significant impact on Member Countries and NCIA in terms of materiel development, testing and fielding. We do not discuss specific items of equipment in the document; instead we promote a C-UAS system,” says Bittick. In fact, the recommendation is for a system of systems composed of a sensor (the look), an effector (the mitigate) and a command and control (C2) system to make sure the separate elements can talk to one another and cater for a human in, or on, the loop. When Member Countries and NCIA get access to the document it is going to help them understand what everyone is doing and what the common standards are. According to Bittick, “Having that same sheet of music – that similar way of understanding the challenge – should make it a little bit easier to focus on development, testing, scaling and fielding.”


Not surprisingly, the responsibility for drafting the C-UAS doctrine comes under NATO’s C-UAS Working Group’s (C-UAS WG) remit. Having been tasked to draft the doctrine, the C-UAS WG created a Tiger Team that held separate meetings outside of their regular activities. The Tiger Team was, and is, open to any NATO Member Country that wants to join it.
The document has been split into five chapters:
• Chapter 1: Introduction
• Chapter 2: Threat Environment
• Chapter 3: C-UAS Protection Function
• Chapter 4: Operational Guidance
• Chapter 5: Education, Training and Exercises
Bittick undertook the role of Working Group Secretary, which includes coordinating the efforts of the Tiger Team. His role was to ensure that each Nation was given an equal voice at the table and an opportunity to offer up their opinions and suggestions. The five chapters were allocated to individual Nations within the Tiger Team. Chapter Three, ‘C-UAS Protection Function’, was allocated to the United States, which in reality meant that Bittick had the opportunity to do much of the writing (he worked with the US Joint Counter-small Unmanned Aircraft Systems Office (JCO) prior to
assuming his post at NATO). He explains how the drafting process went. “We would write what we thought should be in the chapter, and then we would share it with the entire C-UAS community. They would provide their feedback, and then, at each Tiger Team meeting, we would either work on it together, based on the feedback from our nations, or we would try and tease out whatever we thought needed more attention or improving,” Bittick says.
This process continued until they collectively agreed they had something that would stand up to scrutiny from the NATO Standards Office (NSO) and the rest of the Alliance so that they could begin the process of ratification. Having entered the ratification process, the NATO Member Countries now have 180 days to raise any objections before it is ratified. “Once it is ratified it will be put under a period of silence for a week or two and once it clears the silence period we will send a request to promulgate to someone within NSO. Then it will hit the streets.” Bittick reveals.


Managing
Quantum technologies represent a growing sector with the potential to develop and shape new global industry value chains and defence operations. Based on these technologies, new ways of processing information (quantum computing), exchanging data (quantum communication) and exploring the environment (quantum sensing and metrology), among many other applications, are being developed.
What do you think are the advantages and risks of the use of quantum technology?
The current work by academic institutions and industry to develop quantum computers might enable the building of very powerful machines with the capacity to reshape industrial solutions. For example, they can potentially improve the simulation and optimisation of complex systems. However, they also impact the security of symmetric-key cryptography and break public-key cryptography.
Insecure cryptography threatens computer and communication systems, products and the supply chain for both industry and institutions. Adversaries could, for instance, tamper with critical data or gain access to confidential information. In addition, attackers can record secure communications today to decrypt them later using powerful quantum computers.
Two technologies are considered to be immune to this quantum threat: quantum key distribution (QKD) and post-quantum cryptography (PQC). QKD and PQC are two security technologies with complementary
characteristics that target different security requirements and are expected to work together to develop quantum-secure systems. While QKD is envisioned to cover some governments and industry security needs, PQC is expected to be used as the wider quantum-secure solution.
Can you share something about Airbus’ activities in quantum technologies?
Due to the strategic implications of quantum technologies, decisive action is crucial. Several years ago, Airbus identified quantum technologies as a key disruption for the future.
Airbus already uses quantum computing for problem optimisation, machine learning and simulation. These quantum computers encode information as quantum bits (qubits) and present enhanced processing capabilities due to the superposition and entanglement of quantum effects. Currently, different qubit technologies (for example, superconducting, photonic, ion trap) have different degrees of maturation and characteristics.
Airbus is indeed a pioneer in quantum computer benchmarking. In 2019, Airbus launched the quantum computer challenge, inviting the quantum and high-performance computing (HPC) communities to solve five aerospace problems with the potential of achieving a quantum advantage. This initiative brought together world-leading experts in the area to explore fast optimisation of aircraft loading. In 2024, Airbus is teaming up with a key player from the automobile industry to launch the
Quantum Mobility Quest and help shape the future of transportation.
Quantum sensing is another area that has a substantial impact on different industries. It uses quantum states to measure various properties, including acceleration, rotation, electromagnetic radiation, magnetic fields, time and frequencies. Quantum sensors can reshape a wide variety of services and they can outperform current traditional sensors in terms of accuracy, sensitivity and drift. This is the most mature quantum technology, with evolved commercial products such as quantum gravimeters already available. The first projects on the path to mass production are related to solid-state quantum sensors.
Regarding quantum sensing, Airbus is positioned as an integrator and developer of enhanced products and services. Airbus closely works with the quantum-sensing ecosystem, exploring various quantum sensors and evaluating their suitability for different aerospace applications. Since 2022, we have participated in the CARIOQA project, also known as the Cold Atom Rubidium Interferometer in Orbit for Quantum Accelerometry project. We are partnering with other European public and private entities to develop a technology demonstration mission to space-rate a quantum sensor capable of measuring accelerations using cold atoms. This project involves the testing of quantum accelerometers in space by 2030. One of the applications of these sensors is to measure the rise of sea level with unrivalled sensitivity, which is key for disaster management. This project will enable quantum sensors to mature and, therefore, prepare the ground for future high-precision gravimeter missions in space.
Airbus also has a strong footprint in the quantum-secure communication area, where the migration towards postquantum cryptography seems imminent. As the designer of the first European chip with post-quantum
capabilities, Airbus is pioneering the secure implementation and integration of post-quantum cryptography.
In addition, Airbus is leading the European system design initiatives of quantum communication, being the EuroQCI (European Quantum Communication Infrastructure) designer working together with the expert community towards the secure integration and interoperability of quantum communication.
The EuroQCI will integrate quantum technologies and systems into terrestrial optical fibre communication networks and will include a spacebased segment ensuring full coverage across the European Union and continents around the world. It aims to secure Europe’s encryption systems and critical infrastructures, such as government institutions, air traffic control, healthcare facilities, banks and power grids, against current and future cyber threats. Since 2023, the European Commission has been funding the deployment of the quantum network in the different member states. Airbus is contributing to the coordination of the various national deployments and participating in the French network deployment (FranceQCI).
Is Airbus also involved in projects using quantum technology for defence?
We are involved in different projects that explore quantum technologies for defence. Currently, Airbus is contributing to the European Defence Agency ANQUOR project (Advanced Networking with Quantum Communications with Operational Relevance), to explore and demonstrate the military relevance of quantum communication and determine specific military conditions using such technology. In quantumsecure communications, the aim is to achieve long-term security; for this, QKD and PQC are key. Airbus is exploring every single technology and their hybridisation (combination of
classical cryptography and PQC or PQC and QKD).
In QKD, users have a quantum channel to transfer a secret random key, making it impossible for an attacker to copy or read (measure) it without getting noticed.
In PQC, communication is protected through hard mathematical problems that are resistant to traditional and quantum attacks. We already have the in-house building blocks (software/ hardware) and capabilities for fast exploration and testing of PQC in different defence scenarios. Indeed, we have already been running successful tests using PQC since 2017 in different scenarios. Recent tests were run on secure drone connectivity, dynamic networks and secured blockchain.
Some of the areas specific to defence being explored at the moment, together with partners from industry and academia, are the use of quantum clouds for secure information sharing and computing. The exploration of quantum sensors and quantum communication is planned to continue with the aim of increasing the efficiency of tactical procedures as well as mission planning and execution. This work covers magnetic field sensors for anti-submarine warfare (ASW) and underwater mines as well as inertial sensors for precision firing and mass sensors for enhanced bunker/tunnel detection and mapping. Other areas include enhanced resolution and ultra-wideband with fused multi-band radar networks, secure communications between land, maritime and air assets, fibre links to fixed-quantum networks for secure communications and improved clock stability.
www.airbus.com/en/innovation/ disruptive-concepts/quantum-technologies


On 4 April 1949, Canada and 11 other nations founded NATO to promote the stability of the Euro-Atlantic area and to safeguard the freedom of its peoples. This year, Canada reaffirms its steadfast and longstanding commitment to the Alliance and celebrates NATO’s 75th anniversary alongside its 31 Allies.
The strong bond between North America and Europe is built on our commitment that an attack against one of us is an attack against all of us. This has made NATO the most successful military Alliance in history. Together with our Allies around the globe, we stand united in defence of freedom and democracy, and the rules-based international order.
Over the past 75 years, Canada has participated in nearly every NATO operation, and we are proud of our ongoing contributions to the Alliance. Currently, the Canadian Armed Forces (CAF) continue to support training in the Middle East under NATO Mission in Iraq; deploy ships on a near persistent basis to NATO’s Standing Naval Forces; and deploy personnel to Operation Kobold in Kosovo.
Most significantly, as part of the largest reinforcement of Alliance collective defence in a generation, Canada contributes to NATO’s deterrence and defence measures in Central and Eastern Europe through Operation Reassurance, Canada’s largest overseas mission. A Land Task Force with approximately 1,300 CAF members is currently based in Latvia. Further, we have committed to scaling up the Canada-led NATO Battle Group in Latvia to a Brigade, which will see as many as 2,200 Canadian personnel deployed on a persistent basis. Based in Prestwick, Scotland, a Canadian Air Task Force has delivered more than £16 million of Ukraine-bound military aid donated by Canada, Allies and Partners. A Canadian Maritime Task
Force is also deployed on a continuous, rotational basis, and contributes ships to the Standing NATO Maritime Groups.
Alongside our NATO Allies, we are also stepping up to support Ukraine. Canada has committed well over $13 billion in total assistance to Ukraine since February 2022, including $4 billion in military assistance – from tanks and artillery ammunition to F-16 training. Ukraine’s fight to defend itself is about the values that NATO was founded upon – and that is why Canada supports Ukraine’s NATO membership when conditions allow.
Although Canada makes significant contributions to the Alliance, we know that we need to do more.
In April 2024, Prime Minister Justin Trudeau and I released our plan to do so, titled ‘Our North, Strong and Free: A Renewed Vision for Canada’s Defence’. Through this policy, we will invest $8.1 billion over five years and $73 billion over 20 years in new funding, bringing our defence spending to 1.76% of gross domestic product by 2029–2030. This plan
invests in major new capabilities for the CAF that will increase our ability to defend our North, which is NATO’s Northern and Western flank. From new Airborne Early Warning aircraft to tactical helicopters and a long-range strike capability, these investments will significantly bolster the CAF’s ability to meet tomorrow’s challenges.
The policy update is a significant step toward reaching our commitment to spend at least 2% of GDP on defence, and it will see Canada meet the NATO commitment of spending 20% of defence expenditures on major equipment, starting next year.
This plan also confirms that Canada will participate in the newly established NATO Innovation Fund, which will offer additional funding streams for Canadian entrepreneurs. The Fund is the world’s first defencefocused multi-sovereign venture capital fund, providing investment in start-up firms developing dual-use, emerging and disruptive technologies (EDTs) critical to our defence. These include artificial intelligence (AI), big-data processing, quantum-enabled technologies, autonomy, biotechnology and human enhancement, novel materials, energy, propulsion and space capability.
In today’s unpredictable world, where technology is rapidly evolving, we must continue to adapt to the changing character of conflict, and its implications for Allied security and prosperity. Technologies such as AI, autonomous systems, and quantum technologies are changing the world and the way NATO operates, presenting risks and opportunities. Keeping pace with this evolution is critical to address threats from potential adversaries and to maintain our ability to operate as an Alliance.

That is why Canada continues to work closely with its Allies and Partners to help maintain NATO’s technological edge through innovation, and to seize the opportunities and address the challenges brought about by emerging and disruptive technologies. We continue to prioritize researching and developing key technologies such as AI, quantum technologies, advanced cyber, hypersonics and electronic warfare.
Canada remains committed to supporting the development of advanced defence capabilities and will continue to work with NATO and our Five Eyes partners on these key defence research and development areas. Canada fully supports initiatives to strengthen NATO’s deterrence and defence posture, to better understand the intent of adversaries’ tactics and approaches, and to retain NATO’s technological and warfighting superiority.
At home, Canada is taking action to address these new threats through its ongoing support of NATO’s Defence Innovation Accelerator for
the North Atlantic (DIANA), in addition to the establishment of support programmes aimed at enabling the research and development activities of Canadian innovators who participate in the NATO DIANA programme. With a North American Regional Office in Halifax, Nova Scotia, DIANA brings together industry leaders, leadingedge scientific minds and the brightest start-ups to help the Alliance maintain its technological edge.
Our Alliance is facing new and emerging challenges, from threats to the international rules that keep us all safe, to the changing character of conflict itself. But, our Alliance is also united, strong and growing, thanks to the addition of Sweden and Finland. I am more confident than ever in the future of NATO – and Canada is committed to doing its part to keep the Alliance strong and safe.

Sweden’s Defence Minister, Pål Jonson, highlights the importance of Sweden’s recent accession to the NATO Alliance and outlines how technology will help defend NATO and its territory

During this spring, Sweden has gone through a historic change within the defence and security arena. Becoming a member of NATO is the most significant move in Swedish security policy in over two centuries, abandoning neutrality and non-alignment.
We are also undertaking the largest military build-up in Sweden since the 1950s and this is set to continue. From 2020 to 2024, Sweden has doubled its defence budget to €12 billion.
The Swedish Defence Commission, consisting of representatives from all eight parties in parliament, recently stated in its final report a goal of defence spending reaching 2.6% of GDP by 2028. This year we are at 2.2% and we significantly exceed the
NATO 20% guideline for defence spending on major equipment and research and development (R&D). Innovations of tomorrow require engagement and investment today.
We contribute to the Alliance’s endeavour to maintain its technological edge. Sweden’s long-time and sustained focus on R&D spending, education and infrastructure sustains our vibrant and innovative industrial base. However, the key is transforming innovation power into military power.
Sweden’s unique industrial base combines innovation and technology to design, develop and produce world-class submarines, ships, anti-tank weapons and
armoured vehicles, as well as fighter aircraft and airborne early warning systems. This is rather unique for a country of 10 million people. We would never be able to accomplish this if we did not have a strong civilian R&D community in Sweden.
In the first half of 2023, the Ministry of Defence launched the Defence Innovation initiative to increase the capacity and pace of innovation in the defence industry. According to most innovation indexes, Sweden ranks among the top three in the world. However, we see opportunities for continued development by making even better use of civil-military synergies. Therefore, the government is establishing an innovation programme in a collaboration between the armed forces and the innovation agency, Vinnova.
This initiative aims to create added value through increased and enhanced collaboration within and between the business sector and government agencies in various sectors. The purpose is to strengthen Sweden’s security and national defence capability and boost competitiveness in the defence industry.
However, we can have all the strategies and plans in the world, but, as the saying goes, “culture eats strategies for breakfast”. We need to encourage a culture that is not afraid to make mistakes and is open to innovation and collaboration across traditional sectors.
LESSONS TO LEARN
This leads me to what we can learn from Ukraine.
First, supporting Ukraine is not only the right thing to do, but also the smart thing to do. It is an investment in our own security. Sweden will continue to support Ukraine until it
regains its freedom and territorial integrity. Russia’s full-scale invasion of Ukraine has shown us that war is as violent, as kinetic and as bloody as it always has been.
With the war being far from over, we have identified several initial observations, one of them being: we need a strong and robust defence industry in Europe. This has been a war of warehouses as well as a war of attrition. A strong defence industrial base is an indispensable part of credible deterrence.
Ramping up production is difficult. Nevertheless, it needs to be done. The willingness of industry to invest in production capacity must be met with long-term commitments from governments. The current rise in demand must remain at these high levels for many years to come if we want investments in production capacity.
We need to ensure that emerging and disruptive technologies are more quickly integrated into test beds and demonstrators, and then into the hands of the operators. On balance, in Europe, we are operating with acquisition cycles that are too long. It is crucial that we increase the pace of integration exponentially as the technology develops. The Defence Innovation initiative together with our newly created Defence Innovation Council will be a crucial driver in this work. We also look forward to actively contributing to NATO’s innovation initiatives in order to perpetuate and develop the Alliance’s technological edge. At the end of the day, we need to develop weapons that are more effective and advanced than those of our adversaries.


Many countries are experiencing a decline in democracy. Meanwhile, attacks on mobile devices are becoming more sophisticated, and advances in artificial intelligence (AI) technology have made it easier to monitor the vast amounts of data flowing through mobile networks. Today, it is more important than ever to protect the information you carry around in your pocket.
Mobile devices have become widely adopted and are integral to our lives, making them attractive targets for attackers. These devices often store sensitive data, creating opportunities for attackers to steal or exploit personal and financial information. Additionally, users are often less aware of security issues on mobile devices compared to computers, making it easier for attackers to take advantage of their vulnerabilities.
In regular use, mobile phones and other devices such as laptops and tablets are specifically designed to
connect to the internet and other networked devices as easily and quickly as possible. We expect to automatically get a prompt for free Wi-Fi connections when they are available, and these days we expect our phones to link up to our car to play our favourite songs over Bluetooth. If the automatic connection does not become immediately apparent, we assume that something is wrong. However, this ease of use can also create potential attack vectors.
Certain countries have gained notoriety for their extensive surveillance operations and their increasing disregard for international norms surrounding privacy and communications interception. This poses a significant threat when foreign, untrusted cellular operators collaborate with potential adversaries. Moreover, it raises concerns that sensitive information might be compromised as well as an individual’s rights violated.
If you connect your mobile device to a network in an unprotected way, it is possible for others to see what services you are connecting to, which in itself is a security risk even if the information you share with those services is not accessible to them. Additionally, the cellular operator can track your movements and geographical whereabouts within the country by closely monitoring your phone’s unique signature and position in the cellular
network. This allows for a comprehensive understanding of your travel patterns.
For instance, suppose you are a business traveller from Switzerland. The local cellular network operator can accurately identify your origin by analysing the network traffic directed towards your home country. By merging your geographical information with the network traffic, more advanced analysis becomes possible, potentially leading to informed speculation about the company you represent.
Network vulnerabilities and malicious applications can be used to attack networked devices. In addition, vulnerabilities in the devices you bring can lead to unauthorized access, data breaches and the potential compromise of sensitive information. And, so it goes on...
can someone protect themselves from these threats effectively?
The necessary protective measures for your work will of course vary depending on the type of tasks you perform and the information you regularly handle. Sectra provides solutions that cater to different security levels, ranging from low to the highest.
To ensure maximum security in these situations, it is crucial to use the appropriate products that safeguard both yourself and the information you share, particularly when accessing the internet or any open networks. First of all, you need to establish a secure and protected

connection between your mobile device, such as a phone, tablet or laptop, and your home network and services.
An absolutely key objective is to maintain anonymity within the network to make sure your activities are hard to detect and follow. Consequently, your online behaviours and geographical location should remain untraceable to ensure your data is secure from surveillance or potential shutdown. It is, therefore, important to use products that deliver an online presence that is both secure and difficult to detect, even in vulnerable and adverse network conditions. Crucially, when it comes to security, it is important that you have the right security solution for the right use case. If you are a journalist, diplomat or in the military and want to access the internet or any open network, you will need different solutions.
Can you describe Sectra’s portfolio of obfuscation products and explain how they protect people from network threats and ensure secure communications with anonymity?
Sectra has been developing a range of obfuscation tools for a few years
now to provide another layer of security that hides your mobile devices from hostile onlookers. We have different products depending on specific needs and use cases. There is no one-size-fits-all solution regarding security.
To start with, as a base protective measure we have the Stealth Connect solution, a new product, which is an innovative security gateway, designed to safeguard users in hostile network environments. The device functions as a robust network bridge and firewall, and establishes a secure connection between a mobile device, such as phone, tablet or laptop, and the home network or other attended services. The solution protects you from network-related threats and ensures that you are hard to detect and follow. This product has been frequently requested and we are delighted that we are now able to provide it.
Moving up into the cloud, we have the Network Protector system, which makes it very difficult to trace where information transmitted on public networks is coming from and where it is going to.
If you handle highly sensitive and classified information, you will most
likely need a Sectra Tiger/S secure phone. This is a quantum-resilient mobile phone that enables users to share classified information up to the classification level NATO SECRET, through encrypted speech, messaging and data transfer.
With Tiger/S, the user can call someone in their closed user group who has the same device using end-to-end encryption. In short, Tiger/S bypasses the threats I described earlier and enables the user to carry on their business in the knowledge that calls are not being intercepted, data on the phone is safe and any content being transferred is secure.
These two Sectra solutions I have just described, together with others in our portfolio, can be combined in different ways depending on the needs of the customer. As I mentioned before, you need to choose the right level of protection for your specific scenario.
Any closing words?
I have focused mainly on technical protection, such as how technology can protect your devices. We have not talked as much about what types of behaviour are safe, and how these can differ in different regions. Making smart decisions, following safe travel best practice and keeping a close eye on social engineering are also very important ways to keep yourself and your information protected.
Stay safe out there!
For more information, send an email to Dennis at dennis.buchinhoren@ sectra.com
communications.sectra.com


Since the signing of the North Atlantic Treaty (Washington Treaty) in 1949, the Alliance has steadily created and evolved organizations to jointly develop and support technology systems for its situational awareness and communication, consultation and control capabilities
The deployment of the 7th US Signal Brigade to SHAPE (Supreme Headquarters Allied Powers Europe) in 1951, underlined the critical role that communications and their networks played in the Alliance’s ability to consult with representatives of the Member Countries. This vital function enables the Alliance to make timely and effective decisions. Since then, NATO has created a number of organizations and agencies dedicated to the development and support of communications,
command and control and ISR (intelligence, surveillance and reconnaissance) systems.
In July 2012, the decision was made to streamline many of them into one overarching organization: NCIA (NATO Communications and Information Agency). Not only did this improve efficiency, it also enabled a more costeffective use of NATO communications and information technology investments.


1949 Signing of the North Atlantic Treaty
1951 7th US Signal Brigade is assigned to SHAPE
1955 SHAPE Air Defense Technical Centre (SADTC) opens
1963 SHAPE Technical Centre (STC) begins operations
1967 Creation of the SHAPE Signal Support Group (SSSG)
1971 NATO Integrated Communications Systems Management Agency (NICSMA) opens
1981 Establishment of the Service Support Group (SSG)
1985 Creation of the NATO Regional Signal Group SHAPE (RSGS)
1986 NATO Communications and Information Systems Agency (NACISA) opens
1987 Foundation of the NATO CIS Operating and Support Agency (NACOSA)
1991 Creation of the NATO ACCS Management Agency (NACMA)
1996 NATO Consultation Command and Control Agency (NC3A) opens (merging STC and NACISA)
2004 NATO CIS Services Agency (NCSA) begins operations
2005 Launch of NATO’s Programme office for Active Layered Theatre Ballistic Missile Defence (ALTBMD)
2007 Establishment of the Information Communications and Technology Management (ICTM) for NATO Headquarters
2012 Creation of the NATO Communications and Information Agency (NCIA)
2019 NCI Academy opens
2022 NCIA celebrates its 10th anniversary
2024 NCIA reaches 12 years since its establishment and NATO celebrates its 75th anniversary



Simon Michell asks NCIA’s Dr Cristian Coman and Radu Cimpean to explain how two simultaneous exercises in Iceland helped to enable the Alliance illuminate the identities of those who commit malicious acts against the Alliance and its Member Countries

In late autumn 2023, two NATO multinational exercises got under way in Keflavik, Iceland – Northern Spirit and Northern Challenge. The latter, hosted by the Icelandic Coast Guard, brought EOD (explosive ordnance disposal) and counter-IED (improvized explosive device) experts and practitioners from over a dozen Nations together to test and experiment with methods for safely disposing of bombs, missiles and similar weapon systems, as well as locating and deactivating deadly booby traps. These exercises are sponsored by the NATO Innovation, Hybrid and Cyber Division (IHCD) at NATO HQ through the Defence Against Terrorism Programme of Work (DAT POW).
The former, Northern Spirit (NOSP), was led by NCIA’s Dr Cristian Coman as Exercise Director, assisted by Radu Cimpean, Senior Operations Specialist (ISR) at NCIA and the NOSP Lead Planner. It was, according to Cimpean, “All about denying anonymity from those who prosecute terrorist acts such as planting bombs and boobytraps on NATO territory or elsewhere.” Specifically,
this exercise tested the operational interoperability of biometric and identity intelligence (I2) systems. Dr Coman explains, “The main aim was to test and exercise the interoperability of systems and people under the guidance of technical and operational objectives. We had technicians and industry representatives working together to try and attain our interoperability goal. On the flip side, we also had military training bodies who were there to apply operational processes using technical systems.” Cimpean adds, “We had a threefold objective within the overall goal. First, to execute biometric operations, second to produce identity intelligence, and third, related to Northern Challenge, to prove the utility of identity intelligence to the EOD and counter-IED community.”
The third objective explains why the two training events were held in the same place at the same time. In short, to show how I2 can help operational commanders make informed decisions about the next steps they should take after encountering a terrorist attack. To this end,

there was a training scenario where the two activities came together to practise and test how biometrics and I2 can enhance decision making in the field.
The art of biometrics and identity intelligence is being able to find traces of human presence (fingerprints, blood, sweat, hairs and so on) on items that have been left behind, discarded or scattered by other means at a location where a terrorist attack has taken place or was being planned. This could be a fingerprint on a water bottle or fragments of an IED. Once a trace element has been found, the next step is to try and match it to a person or eliminate a suspect. After a match has been confirmed, I2 systems are then used to put context around the person who has been identified. I2 can not only give details about the person – age, nationality, residence and so on, but also what circles they move in and who they are closely associated with. “Numerous techniques are used employing both open and classified sources to search for networks and nodes that connect the ‘matched’ person with other people and events,” says Cimpean.
NCIA has been working on biometrics for over a decade and has developed an operational system known as NABIS (NATO Automated Biometrics Identification System). This employs a ‘ping and ring’ system, whereby NABIS operators can ping a data source in search of relevant information and, once a likely source has been found, ring for more details. It was NABIS, among other systems and communications networks, that was being tested for its levels of interoperability at Northern Spirit.
The activities in Keflavik, Iceland, in October 2023 were very much focused on a counter-terrorism scenario and largely borne out of NATO’s activities in Afghanistan and Iraq. But, with a war in Ukraine now raging, the focus has
been shifted away from a hybrid asymmetrical conflict to a high-intensity conventional conflict. So, next October, Northern Spirit is going further afield to Canada so that it can support Exercise Ardent Defender, which, like Northern Challenge, is also an EOD/counter-IED exercise. The main difference being however, that at Ardent Defender there will be a sophisticated laboratory, which will facilitate the technical exploitation of captured materials and further enhance the I2 analysis.
Apart from that, there is not a huge amount of difference in the methodologies employed between asymmetric conflicts and conventional warfare.
“The tradecraft is the same,” explains Dr Coman. In both cases, the availability of an authoritative, reference biometric database is the key ingredient in conducting biometric operations. This prerequisite is achieved in NATO by connecting National Automated Biometrics Identification Systems (ABIS) into an enterprise network, where every participant can query information available in other databases without surrendering ownership of the data.
At Ardent Defender, as well as looking for the usual clues, they will also introduce additional elements, such as drones, which feature so prominently on both sides of the Ukraine conflict. There is another similarity to the nebulous world of counter terrorism. The war in Ukraine has shown that the Russians are relying on a host of different and often shadowy forces to assist them in their illegal invasion – private companies such as Wagner and quasi paramilitary organizations. In such circumstances, knowing exactly which organization a person is affiliated with, and what he or she might have previously been involved in, could prove invaluable. Denying these mysterious troublemakers anonymity would be equally as significant.


In response to Russia’s illegal invasion of Ukraine, NCIA’s Chief of Joint Intelligence Surveillance and Reconnaissance, Matt Roper , reveals how NCIA is helping speed up the integration and interoperability of NATO’s capabilities to enable multi-domain operations
In February 2022, the context of security and defence for the Alliance markedly transformed when Russia used military force against Ukraine. Consequently, the focus on speed and quality of decision making for NATO became increasingly critical for the Alliance. Within NCIA, the Joint Intelligence, Surveillance and Reconnaissance (JISR) Centre is directly supporting the current understanding of changes to NATO’s operational and strategic environments through an expanding number of key intelligence, surveillance and reconnaissance (ISR) focus areas.
The Russian invasion of Ukraine coincided with the publication of a number of NATO strategic papers that emphasised the need for increased situational awareness and the swift translation of decisions into action. For example, the NATO Strategic Concept 2022 highlighted the importance of multi-domain forces and warfighting, and an initial Alliance ‘Concept for Multi-Domain Operations (MDO)’ offered a working definition of MDO as the “the orchestration of military activities, across all domains and environments, synchronized with non-military activities, to enable the Alliance to deliver converging effects at the speed of relevance”.
Delivery of effects is directly dependent on an informed understanding of the environment through the collection of relevant data and information. The JISR Centre helps realize interoperability among a wide range of ISR capabilities and NATO systems through software

applications and architectures. This enables information collected by NATO and national ISR platforms to be integrated in, and accessible from, Alliance networks using NATO-approved standards.
With an increasingly diverse range of ISR sensors and information sources now available, the task of integration and interoperability continues to present challenges – some of which are being addressed through support to a number of current and future NATO intelligence capability projects.
Within the JISR Centre, the delivery of the Intelligence and ISR Functional Services (IIFS) programme will constitute a step change in the Alliance’s ability to utilize imagery and open-source intelligence, with implications across multiple areas within the Doctrine, Organization, Training, Material, Leadership and education, Personnel, Facilities and Interoperability (DOTMLPFI) spectrum. NATO’s Intelligence Functional Service (INTEL FS) is being upgraded (from Spiral 1 to Spiral 2) to provide a range of new and enhanced functionalities to better support Alliance INTEL operations. As part of the wider ISR architecture, the Coalition Shared Data (CSD) concept provides a secured mechanism via which ISR and INTEL products and services are stored, archived, retrieved and ultimately shared throughout the Alliance ISR enterprise.
Over the past few years, there has been a heavy JISR focus on supporting the successful delivery and integration of the Alliance Ground Surveillance (AGS) capability into operational service. This capability continues to evolve into NATO’s ISR Force and will become the hub for JISR data and services within the NATO Command Structure – and a critical node in the Alliance’s ambition for persistent surveillance.
Persistent surveillance is intrinsically linked to MDO and is fundamental for effective NATO deterrence and defence. With effective data management, persistent surveillance provides military and political leaders with the essential awareness to enable timely decision making and action. This ambition demands access to a multitude of data sources from the Alliance, Nations and commercial providers.
APSS – Alliance Persistent Surveillance from Space
The Alliance Persistent Surveillance from Space (APSS) programme will address an element of this challenge through increased access to relevant and timely data and services from space. Delivered through the JISR Centre, APSS uses JISR architectures and applications to ensure alignment with other strategic programmes and a common approach to shared data challenges.


Accessing commercially provided data is one of many challenges, which equally has an impact on operational processes and technical interoperability solutions. The strong partnerships developed between the JISR Centre and the operational community pays dividends in helping address these areas and ensures that any potential solution reflects the ‘users’ reality from the outset. These relationships are also evident in the continuous JISR support provided to the NATO Airborne Early Warning and Control Force (NAEW&CF), the extension in service of the E-3A aircraft and assistance to the programme, which will eventually provide the Alliance with an enduring replacement of the E-3A aircraft – the Alliance Future Surveillance, and Control (AFSC) Programme. The JISR Centre has also been supporting the assessment of industry proposals for AFSC with a focus on NATO JISR interoperability within the various concept proposals and feasibility studies provided by industry.
Supporting the delivery of MDO and the ambition of persistent surveillance constitutes an ongoing challenge of ISR data access across the electromagnetic spectrum. Here, the JISR Centre continues to expand support in considering how best to use technology to protect and defend Alliance activities. Electromagnetic operations, C-UAS (CounterUnmanned Aircraft Systems) activities, navigation warfare, C-IED (Counter-Improvised Explosive Devices), biometrics and identity intelligence are some of the many areas that are directly benefitting from the developed knowledge and understanding within the JISR Centre. Importantly, direct support of operational requirements is greatly enhanced through the combined blend of deep technology and engineering acumen and operational expertise within the JISR Centre staff. This expertise also includes research and application of advanced
technologies such as sensor fusion, machine learning and artificial intelligence – themes that crosscut many of the projects and activities within the JISR Centre portfolio.
All JISR data, products and services require geolocation in order to ensure that relevant information can be searched, retrieved, analysed and can directly contribute to decision effects. The JISR Centre capabilities within the areas of geospatial, meteorological and oceanographic (GeoMetOc) information systems, provide the ability to rapidly comprehend the multi-domain environment, ensuring the Alliance is basing key decisions and actions on common GeoMetOc frameworks.
The growing demand for integrated ISR data, products and services within NATO MDO activities requires a wide range of skills, knowledge and experience of the entire JISR Centre staff. Supporting the requirements of NATO analysts to meet the challenges of increasing volumes and complexities of data and a pressing need for rapid decision making, demands an agile approach and a focus on identifying commonalities between projects. In this regard, the JISR Centre works with NCIA’s Chief Technology Office to ensure that coherent technical solutions are applied across all NCIA products and services.
The realization of MDO represents a challenge for NATO JISR processes and personnel through a need to operate at an elevated tempo and intensity. Importantly, this requires an additional investment in the human capital of JISR (in addition to key technological advances). This is a core endeavour within NATO’s JISR vision and is also an important activity being directly supported by the JISR Centre.

NATO is undergoing a digital transformation. Can you describe what this means in terms of working with data in a digitized workflow? How will it revolutionize day-to-day operations?
information is the ultimate support. This is what we do at Hexagon.
What underpins this digital environment, and why is it so different to the former analogue environment?
EMEA Defence Lead, Hexagon’s Safety, Infrastructure & Geospatial Division

Richard Goodman Dr Uwe Jasnoch
EMEA Director of Government, Transportation and Defence, Hexagon’s Safety, Infrastructure & Geospatial Division
Richard Goodman: There is a difference between digitization and digitalization. Digitization captures or transforms a document or file into a digital entity. This offers undoubted benefits, such as ease of storage and cataloguing as well as increased speed of handling and sharing. The process of digitalization takes that a step further by enabling far more benefits, especially in the fields of access and control. Plus, digitalized workflows open the possibility of automation, which is one of the most important benefits. This is what will revolutionize NATO’s day-to-day operations. In fact, it has already started in many ways. At Hexagon, we recognize and leverage the benefits digitalization is bringing in terms of interoperability, enhanced communications, improved ability to share and greater levels of control and access available within digital workflows.
Uwe Jasnoch: Essentially, digitization speeds up processes. This is critical, as having the time to react and understand is key to achieving advantage over an adversary and eventually winning. That said, you need to convert the digitized data into information to draw out the essence of its meaning and value to enable better decision making. Lastly, help selecting the most relevant
RG: One of the major aspects of the digital environment is the huge volume of data that is being created by the innumerable, and frequently interconnected, digital sensors that have proliferated over the past decade or so. The introduction of multi-domain operations (MDO), which is underpinned by digital transformation, has also introduced a myriad of decision paths that need to be managed. Digital workflows, as opposed to the old analogue processes, enable you to handle and process these vast volumes of data and increased command chains in a way that is repeatable and consistently accurate. It removes the possibility of human error. This repeatability is vital. Once you capture a data workflow or human process in a digitalized form, you know that it will happen in the same way every time.
Added to that is the ability to secure data at the actual storage level rather than at the network perimeter level. This data-centric security also delivers ease of distribution and enhanced control. Further security is introduced through watermarking, which also enables different sharing rules embedded in the watermark.
UJ: Apart from the speed of action and reaction that the digital

transformation brings, it also enables you to break away from the old silos where operations were not necessarily connected or synchronized. That is making MDO much more achievable. The digital environment also enables commanders and planners to simulate and test various scenarios. As the MDO battlefield becomes ever more complicated, this is crucial.
Another element that is increasingly relevant is balancing the seemingly contradictory principles of ‘need to know’ with ‘need to share’. Neither of these can be applied optimally without the digital support relating to data creation, management and visualization.
Why is digitalization and digital transformation so important in terms of military capability and the ability to execute MDO?
RG: The speed of relevance has changed. In the digital world and with digitalization you can look for data, find it, share it and review the outcomes very quickly. This connectivity allied to interoperability are the foundations of MDO – not only within a single national force, but also within an alliance such as NATO.
UJ: To successfully execute MDO, you must have all the relevant data at your fingertips to make the best decisions. That said, if you are sharing data, it is the ability to coordinate successfully that is particularly important when it comes to MDO. In
addition, you need to be able to analyse and simulate.
How can Hexagon help, and could you describe a typical use case?
RG: Hexagon combines sensors, software and autonomous technologies, turning complex data about people, places and assets into meaningful information and capabilities for better, faster decision making. Take, for example, our geo-processing Spatial Modeller, which automates complex processes at the press of a button. If a commander wants to know where the narrowest point of a river is, or where the best and flattest ground for a campsite is, preferably close to water, the Spatial Modeller automates this task. These specialized workflows negate the need to refer to a geo-intelligence specialist as the knowledge is captured in the workflow and aggregated with the required data sources – terrain data that shows where the level ground is, vector data that shows the rivers, imagery that highlights objects and buildings and so on.
UJ: And for those that need a more bespoke facility, we have the Workflow Manager, which is designed for simplifying and supporting complicated tasks that are undertaken less often. It allows for more human interaction to guide it while the process of selecting parameters is made easier by a menu of options. This offers users a degree of freedom or flexibility while guaranteeing consistency and reliability.
What benefits does digitalization bring to workflows, catalogues and the visualization of geographic data, for example?
RG: The introduction of federated catalogues enables the user to query someone else’s data from the catalogue interface without duplicating data or having to move things around. This is very useful for checking your data against someone else’s. And, in terms of the explosion of data and data sources, it is now possible to visualize an environment that is dynamic through such things as real-time maps that have embedded analytics and predictive capabilities.
We recently undertook a proof-ofconcept trial using LiDAR geographic sensors, which pick up movement and time those movements/activities into blockchain. The result is that you can link multiple activities within a given area or areas into a master timeline giving you an authoritative, highly accurate sequence of events.
UJ: Blockchain is about the chronology of different things happening at simultaneous times, perhaps under different chains of command – as in MDO. If you are undertaking MDO, you have multiple command chains that need to synchronize and keep track of numerous complex activities. Our trials proved that blockchain is perfectly suited to that. Having that ability, it provides excellent information for debriefings, improving training exercises based on the insights and reduces poorly planned activities.


Having received its security accreditation in December 2023, NCIA’s SANDI Artificial Intelligence (AI) Platform provides a secure space for NATO AI specialists and data scientists to innovate. David Hayhurst asks NCIA’s Chief of Exploiting Data Science and AI, Dr Michael Street, to explain
December 2023 saw SANDI – NCIA’s Data Science and AI Sandbox – granted full security accreditation. It was created as a secure space for NATO’s AI specialists to work with classified data and ultrasophisticated software, based around a core of state-of-the-art graphics processing units (GPU)enabled servers. These are capable of processing vastly larger quantities of data, far faster than conventional processing units.
SANDI’s combination of hardware for computation and storage, software tools, and interfaces has been designed to support multiple NATO AI data science projects, where models can be trained, optimized and validated.
Naturally, SANDI is connected to NATO’s main SECRET Network, but is a separate entity. In the opinion of Dr Michael Street, NCIA’s Chief of Exploiting Data Science and AI, this is important for two reasons. The first is the sandbox’s flexibility: “In a carefully controlled way, we can bring in the latest open-source models from the outside world, thereby ensuring that the toolset within SANDI is kept current, and tracks the leading edge of the latest global AI developments.”
As a result, models created in the private sector or academia can swiftly be brought into SANDI, where they can be adapted – in an isolated, controlled, secure environment – to meet NATO’s specific needs.
The second reason concerns SANDI’s connectivity with the SECRET network, made possible since achieving full security accreditation in December, which followed interim approval in 2020. This allows SANDI to import
and use classified data from SECRET, and then disseminate results to other users on NATO’s classified networks. “SANDI can connect to the data that our data scientists and AI developers need to work with, and it also connects to the users who need to see the results,” explains Dr Street.
“The tools that our colleagues in NCIA are providing for the rest of NATO – the data from the tools that NATO uses to plan or conduct operations – can be brought into SANDI now that it has accreditation. Likewise, AI developments can be exposed to those users, or can be shared with those users. SANDI was always designed as a resource for the whole of the NATO enterprise. Having full accreditation means we can offer access to it to anyone within NATO.”
Bringing fresh insights
Clearly, SANDI is taking NATO into new territory in developing AI models with unprecedented levels of power and flexibility, while working with vast and exponentially growing quantities of data. Dr Street and his team have worked in close collaboration with the NATO Office of Security from the outset to ensure that work can be conducted securely and robustly, without inadvertently introducing vulnerabilities.
Meanwhile, the sandbox is serving a critical function in enhancing key NATO priorities through its demonstrable capabilities. “We can now take some of that classified data used elsewhere, including situational awareness and decision-making data, and we can apply new techniques to work with that data. We can help automate some activities and bring fresh insights.”
With colleagues throughout NATO now routinely having to process a lot more data, SANDI can analyse, process and visualize such datasets in ways that will still make sense to people. “They can continue to plan and achieve situational awareness, even while the quantity of data is increasing dramatically,” confirms Dr Street.
Recently, SANDI has worked in close collaboration with Allied Command Transformation (ACT) and Allied Command Operations (ACO) on developing a demonstrator capable of bringing the power of large language models to NATO’s extremely text-intensive TOPFAS operational planning tool.
Running this enhanced version of the TOPFAS tool in SANDI managed to combine the power of large-language model technology with information drawn from years’ worth of NATO’s operational plans, “and we can put that in front of the user at the time that they need it,” says Dr Street.
SANDI’s systemic flexibility also permits it to adapt open-source and commercial tools while maintaining a highly classified, secure environment. An example is a project with ACT, using IBM’s WatsonX AI platform operating on classified data.
IBM was able to install its tools in a NATO-classified environment that could be run, in a secure way, just as effectively as in its usual commercial manner, while meeting NATO security requirements. According to Dr Street, SANDI’s architecture, services and flexibility “makes it easy for industry to bring their tools into a classified environment, where we can put classified data through them, and we can address a lot of the complex issues when running these kinds of commercial tools, disconnected from the internet”.
Dr Michael Street (centre) joins in with the celebrations of the announcement of SANDI’s full security accreditation (PHOTO: NCIA)



Mariana Antunes asks Frederic Cloutier, NCIA Executive Advisor to the Chief of Staff, about the new agile procurement approach NCIA piloted to strengthen NATO’s cyber security posture
NCIA recently signed a contract with IBM to deliver a service for Enterprise Asset, Configuration and Patching for Vulnerability Management (E-ACPV). What made this procurement significant was the fact that NCIA successfully utilized a dynamic and competitive procurement process, which was designed to address the Alliance’s cyber security posture in a better, more collaborative way. The good news is that this new service will improve security visibility and asset management across all NATO enterprise networks. The achievement marks a significant milestone as it supports an innovative procurement process proposed as part of NATO’s acquisition reform.
According to Frederic Cloutier, NCIA Executive Advisor to the Chief of Staff, “NCIA, alongside the office of NATO’s Chief Information Officer, Manfred Boudreaux-Dehmer, identified a procurement concept called Dynamic Sourcing as a suitable process for complex service procurements. Subsequently, the NATO Budget Committee approved the E-ACPV as a pilot procurement for this new method.”
Cloutier explains that Dynamic Sourcing enables collaboration with industry on obtaining a desired service solution against NATO’s stated objectives, rather than

NATO prescribing a service with a fixed and detailed set of requirements. With this approach, the focus shifts from the traditional prescriptive solicitation package to an outcome-based effort. The process was adapted to adhere to NATO approved procurement procedures and ensures transparency, fairness, non-discrimination, integrity and accountability. “The idea is that industry can help us better address what we need for complex service objectives,” says Cloutier.
Dynamic Sourcing uses a competitive collaboration approach based on five agile stages, referred to as ’sprints’. These comprise an initial preparation sprint followed by three selection sprints, ending with a closing sprint for contract finalization. Companies can adjust their service solutions as they go through the second, third and fourth sprints, adapting their high-level service design solutions on the way. “This means that the service solution we obtain is more suitable for solving the problem at hand and delivers the service we need, as there is constant collaborative dialogue with industry throughout the process,” says Cloutier. “Using the old method, when we specified in detail what we wanted for complex services, we got exactly what we asked for – which might not have been what we really needed.”
The feedback gained from the recent E-ACPV process confirms that industry appreciated the dynamic, collaborative dialogue as opposed to the traditional
bidding process, particularly for complex services. The difference is that industry gets to understand the business context and problem more intimately and has the ability to offer and adapt their service solutions to solve the problem rather than respond to very tight customer technical requirements. “In essence, we get to harness industry’s expertise through a dynamic collaborative process at speed, while adhering to NATO competitive procurement procedures. They can ask questions during the sprints as they formulate their service solutions, which they cannot do as easily in traditional procurement methods. The latter is usually more bureaucratic while this method is very dynamic,” Cloutier says.
The main advantages of Dynamic Sourcing are optimizing service delivery to meet objectives and delivering the service at speed. It keeps NATO away from specifying detailed requirements, meaning it can rely more on industry expertise, ultimately providing service solutions that are geared to Alliance objectives and delivered at a faster pace. That said, Dynamic Sourcing is not a ‘one-sizefits-all’ procurement approach for every service, but, in terms of the delivery of more complex cyber security and IT services, it could be a game-changer.
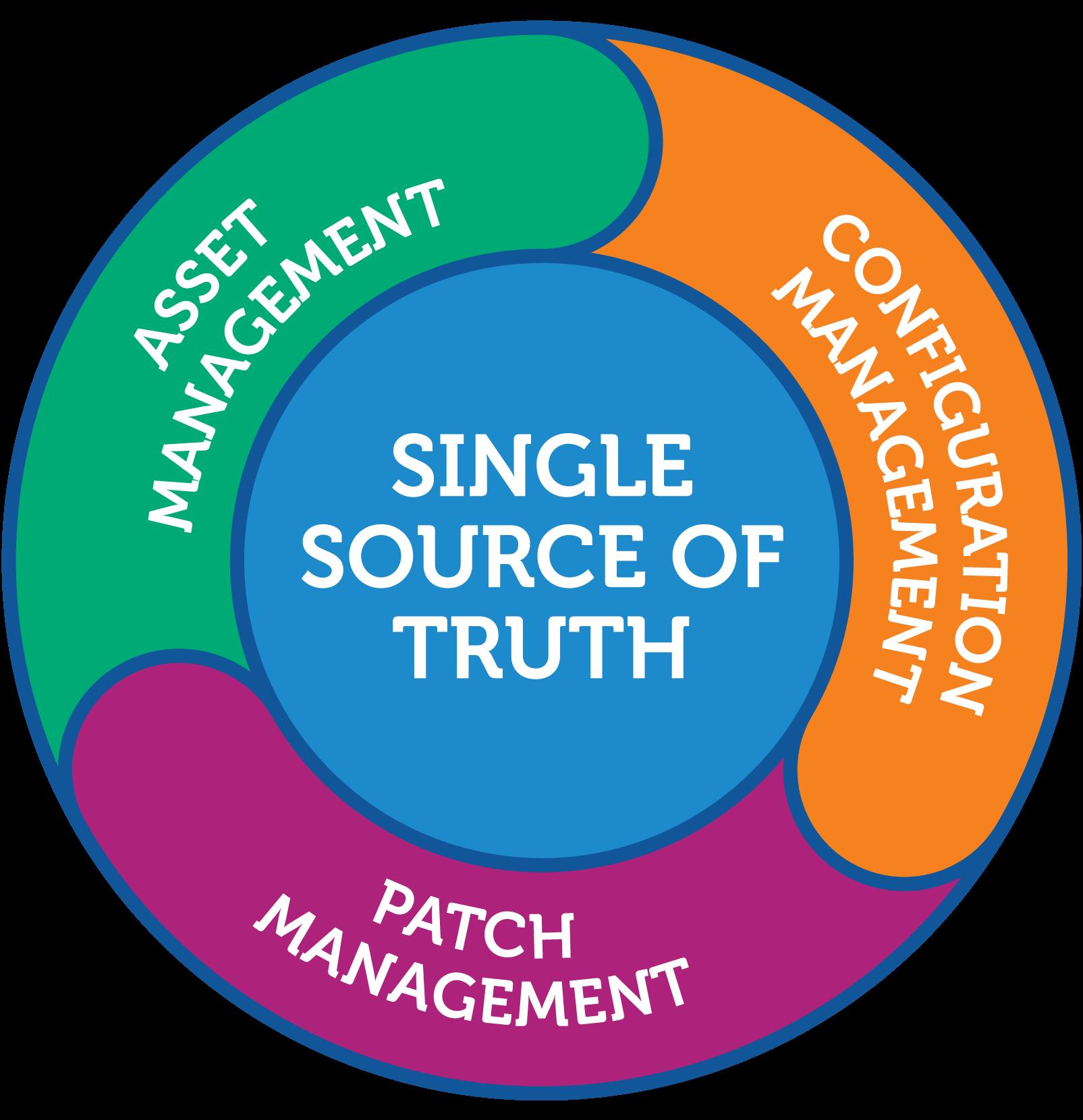
The E-ACPV service will provide a “single source of truth” across the NATO enterprise. It will support the required visibility of cyber security functions, with an initial focus on supporting a risk-informed vulnerability management function. In short, the service will improve the time to implement cyber security mitigation measures, reduce response times and increase NATO’s ability to prevent unwelcome intrusions.
It is the first NATO-wide Dynamic Sourcing initiative that the Alliance has piloted, and given its successful implementation, it will now feature in the acquisition reform dialogue happening across NATO.
The E-ACPV service will also create a NATO Enterprise framework that will eventually support the needs of other key functional areas that rely on asset, configuration and patch management information through a federated approach. These might include wider IT service management, finance, auditing and logistics.

In November 2023, more than 20 NCIA experts with cyber, legal and, for the first time, acquisition skills provided their expertise at the NATO Cyber Coalition exercise. NCIA’s Zainab Hashiru asks one of the participants, Tom Koolen, to detail the team’s experience

For 16 years, NATO Allies and Partners have assembled annually to train their cyber defence skills in one of the largest cyber exercises in the world. Cyber Coalition is NATO’s flagship collective cyber defence exercise led by NATO Allied Command Transformation (ACT).
During the 2023 iteration, a real-time scenario was created in which a fictitious NATO Nation was under attack. This enabled participating cyber defenders to protect NATO and national networks, systems and critical infrastructure against sophisticated incidents. Unlike other cyber exercises where participants compete against each other, Cyber Coalition prioritizes collaboration, cooperation and information-sharing to build collective resilience.
What does Cyber Coalition look like for exercise participants?
During Cyber Coalition, more than 30 Nations come together to investigate the cyber incidents launched against them by exercise organizers. The exercise lasts for five days, during which participants operate from within
their own national, military or civilian environments to conduct their investigations. They are contacted through various communication channels such as messages, emails and phone calls.
Once participants find indicators that the network has been compromised, it is up to them to determine which tools, processes and capabilities they should use to effectively address the incidents. Participants start their investigations from their respective nations, the results of which are shared in a multinational central cyber range. This enables teams to build a situational awareness picture of what is happening to other nations and determine how they will collaborate to find solutions using the means available. So, the exercise is unique in that it is always based on realistic, currently available tools and collaboration mechanisms.
How does NCIA support Cyber Coalition?
NCIA supports Cyber Coalition during the planning and execution phases. It does so through two tracks:

the technical cyberspace track, led by our NATO Cyber Security Centre (NCSC), and the non-technical track, led by the Collective Training and Exercise Branch. The NCSC approaches Cyber Coalition from a cyber-threat perspective, identifying the relevant day-to-day challenges that NATO faces and using those challenges to build the training requirements for the exercise and the incidents.
I am with NCIA’s Collective Training and Exercise Branch, and our role is to safeguard the learning perspective of the exercise. We ensure that the exercise makes sense to all the participants and that it has a coherent scenario that can effectively achieve the exercise objectives. Every Nation participating in Cyber Coalition has their own requirements, systems or things that they would like to get out of the exercise and my job as the Coherence Manager is to understand precisely what everyone wants to achieve. I collect information from all the participating nations and stakeholders in cyberspace, specifically within NATO, and combine all their inputs to create storylines that incorporate their training objectives into the exercise.
How has the format of Cyber Coalition evolved to keep pace with developments in the cyberspace domain?
It is worth noting that every edition of Cyber Coalition differs from the previous iteration. This is because it is tailored to the current context and structure of NATO. Cyberspace has evolved significantly over the past 16 years, and so has the Alliance. NATO has matured and adapted to these changes by continuously developing new operating procedures, collaboration mechanisms and insights on how to deal with cyber incidents. Within NATO, we are constantly developing new rules, responsibilities and entities to match the rate of change in the cyber domain.
When Cyber Coalition debuted, there were very few cyber commands in any of the Nations. There was no participation from Supreme Headquarters Allied Powers Europe (SHAPE), and the Office of the NATO Chief Information Officer did not yet exist. As a result of the developments in cyber, a lot of NATO’s current entities

and responsibilities have been created or have changed over time, and this further has an impact on Cyber Coalition. That is why the planning cycle for the exercise is challenging. We have to listen to the latest developments and make sure that they are incorporated into the exercise so that our Allies can test their capabilities and defences.
What role did NCIA’s non-technical experts play in Cyber Coalition 2023?
The challenges faced, once an incident is launched, are about information exchange, effective collaboration and having the necessary surge capacity to search for a solution. If an incident is significant and another Nation is confronted with similar issues, collaboration is necessary and should begin as soon as possible. However, before that collaboration can occur, there are national legal boundaries that need to be considered.
The job of our legal experts is to determine whether nations can access one another’s information without encroaching on any legal boundaries. If the incident happens on nationally owned equipment, then it is a national responsibility and classified as a protected environment, meaning external entities cannot interfere in that environment. So, there are a lot of legal issues that arise when trying to handle an incident collaboratively, and the same occurs with acquisition.
Cyber experts determine whether they have the required capacity or knowledge base needed to address a particular incident. If not, then they may have to outsource to industry and commercial companies to provide that capacity and knowledge. However, this adds another layer of complexity since time is of the essence during an incident and regular acquisition procedures do not move at the speed of relevance. The challenge for our acquisition experts is that they need to determine how to obtain the necessary support that cyber experts need within the required timeframe. They overcome that challenge by exploring all available options, including seeking assistance from other nations or companies that can provide the required assistance within the timeframe needed. These discussions are crucial and start happening within moments of detecting the incident.



In recent years, the technological world has been in the midst of a fourth industrial revolution, with the rise of big data and artificial intelligence (AI). Arguably, one of the most ground breaking and controversial applications to come out of this explosion of technological development is ChatGPT.
Developed by OpenAI, ChatGPT launched in November 2022 and uses a large language model (LLM) to have a humanlike conversational dialogue with users, by responding to questions and composing written content via a chatbot interface.
Since ChatGPT launched, many LLMs and generative AI tools have surfaced, and not only become an invaluable tool to a wide range of users, but threaten the future of certain industries such as media, market research, financial analysis and trading. However, just as the possibilities are endless, so too are the risks and grey areas – for example, encroaching on legal copyright and generating misinformation, unethical or dangerous content.
Lara Vincent-Young, Editor of NITECH, speaks to Dr Michael Street and Dr Sandro Bjelogrlic from NCIA’s Exploiting Data Science and AI team about the new NATO AI chatbot that is being piloted across the Enterprise
For an organization such as NATO, these threats are heightened when you consider the sensitive information environment and malicious intent by adversaries. Consequently, in the summer of 2023, the NATO Office of the Chief Information Officer (OCIO) issued a Directive on the use of Generative AI in NATO, and tasked NCIA to provide a NATO chatbot, providing access to ChatGPT functionality in a secure manner. One year after ChatGPT became available to the public, NCIA Chief Technology Office’s (CTO) Exploiting Data Science and AI team, together with the CTO Cloud Centre of Excellence and industry, delivered the first pilot service to a group of 200 users across the NATO Enterprise. The pilot user group covers NATO’s political, operational and management community.
Commercially available AI functions are developed using public information from the internet. However, the majority of NATO information is not readily available to the public; therefore, commercial AI is unable to provide
answers on NATO-specific topics. Sandro Bjelogrlic, Senior Data Scientist in the Exploiting Data Science and AI Team, explains, “Right now, if a NATO employee asked a ChatGPT model a question or for assistance with a piece of work, most likely it’s going to be wrong because it will make up an answer based on the information it has.”
In addition, commercial AI often uses users’ inputs to train the next iteration of the model. Therefore, if you ask a specific question about NATO, it may use this knowledge in the future, or simply sell data provided to third parties, leading to information leaks. Chief of Exploiting Data Science and AI, Dr Michael Street clarifies, “Our aim is to give NATO the same functionality and benefits of commercially available AI, but to do so in a controlled, secure way that protects our data and complies with NATO’s security requirements.”
USES OF NATO CHATGPT
The intent for NATO ChatGPT is for any person in any role within NATO to be able to gain value from the tool. A typical case could be summarising information or rewriting a concept. For technical users it can generate code, and it can even aid translators with translating complicated NATO documents.
The potential is evident, however the data science team is taking this one step further by enhancing the model with NATO unclassified information, allowing the model to retrieve information from NATO documents and provide an answer that is more relevant for end users.
NATO directives, policies, contracts and reports are all examples of information the model can be trained on. NCIA is working closely with the NATO Office of Security (NOS) to navigate this process.
NOS plays a critical role in making the NATO AI chatbot a viable service. Of course, LLMs are a new capability everywhere, but particularly for NATO, which often requires additional time to modify commercial technologies to comply with the strict security regulations. Despite the ability to manage the risks through NATO’s regular cyber security prevention mechanisms, the technology is so new that there are likely some threats that industry experts are still unaware of, so the unknown is the biggest concern.
In Bjelogrlic’s words, “The fact that this tool has access to NATO information can become another attack vector to extract information. Rightly so, there is a lot of scrutiny around how we need to implement the model, how it will be deployed, and where the information is flowing.”
The security challenges of creating an unclassified NATO ChatGPT do not even scratch the surface of those observed when considering a NATO SECRET version. These LLMs require very specific hardware to run efficiently, namely Graphical Power Units (GPUs). When working on an unclassified level, commercial cloud providers can be leveraged to solve this problem, however, NATO secret information must be stored
“ The security challenges of creating an unclassified NATO ChatGPT do not even scratch the surface of those observed when considering a NATO SECRET version”

in-house, which requires the computing hardware to be on-premise. Dr Street explains, “GPUs have not been a widespread commodity that we have in NATO, we have taken steps here, but widespread adoption will require significant investment, so this is a technical challenge that needs to be resolved.”
That being said, Dr Street elaborates that NATO already has ChatGPT-like technology which is hosted in the on-premise environment called SANDI. “We are using exactly the same kind of technology to feed large language models with data up to NATO SECRET in order to answer classified questions.” You can read more about SANDI in the article on page 70.
The NATO Office of the Chief Information Officer (OCIO), who is sponsoring this work, put out a request across the whole of NATO for volunteers to become what they term ‘AI champions’. These 200 volunteers make up the pilot group that have been given access to the first prototype. “It was up to each NATO organization to nominate the people they wanted to have access to it. NCIA decided on a top-down approach, including technical and non-technical staff, so it is great to have the General Manager as part of our pilot group,” says Dr Street. “We are in the phase of gathering feedback from the champions to see what needs to be improved; with the OCIO we will use that feedback to drive the next steps.”
The intention is that the service will be scaled up and rolled out as a NATO-wide service. To achieve this, the first step is to improve the application, second is augmenting the model with NATO unclassified data, and finally providing the scalable service. The latter will require collaboration with the Chief Operating Office, namely the NATO Infrastructure Service Centre. Dr Bjelogrlic acknowledges, “We have a very aggressive timeline. There are some slippery slopes on the way and some risks of course, but I am confident we will get there.”
Dr Bjelogrlic concludes, “At the pace that AI is moving these days, we need to be very proactive in on-boarding these technologies quickly, not only the Chief Technology Office, but the whole organization, because this is what is going to give us the edge, especially as we know these technologies are being adopted rapidly outside NATO too.”




With the upcoming establishment of the multinational 5G project (MN5G) by an initial number of participating Nations and NCIA, Luis Bastos, Head Innovating Team, Germano Capela, Senior Radio Engineer, and Alper Köprülü, Project Manager, provide an overview of the project and how it can leverage and complement related national and NATO activities in the area of military use of 5G
Multinational Collaboration on 5G, or MN5G, is the title of a new multinational project supported by NCIA aimed at exploiting the potential of International Mobile Telecommunications (IMT) technologies stemming from 5G standards and their evolutions. The effort to establish a multinational project combining efforts and creating a sizeable programme started in 2021, when a group of Nations and NCIA, in coordination with other NATO stakeholders, discussed the concept and developed an initial MN5G Reference Programme of Work (PoW) and a Memorandum of Understanding (MoU). We are now at a critical stage, where interested Nations are signing the MN5G MoU, and the last steps are being taken before formal project establishment.
The MN5G Reference PoW was developed by NCIA subject-matter experts (SMEs) and national representatives through a series of development meetings held in 2021. The primary aim of the PoW was to define the scope of the project and inform the development of its MoU. It was also aimed at providing inputs to medium and long-term NATO activities on 5G under NATO PoWs in different areas –Policy and Interoperability, Capability Development, and Science and Technology.
The reference PoW has a multi-year scope and was developed as an action plan to bridge the opportunities of specific 5G technologies for military application with the
end goal of implementing cost-effective interoperable military-grade solutions based on 5G technologies, as outlined in the diagram below. It is predicated on three main technical work packages:
• Awareness and Influence – To follow, influence and facilitate 5G standardization work, making sure that the military specificities are considered in future 5G/IMT standards. This includes technology watch activities, engaging with standardization stakeholders, liaising with other national or multinational stakeholders and programmes, and providing informed and unbiased technical advice to Nations.
• Capability Development – To develop future military communication and application systems based on 5G technologies addressing multiple national and multinational military application scenarios. This can address many topics, such as use case development and description, concept development, architecture development, technical design, prototyping, experimentation and analysis of 5G/IMT in different 5G application domains and utilization concepts.
• Security of 5G – To address the security concerns of 5G/IMT standards and infrastructure for military use in different 5G utilization concepts, subject to direction and priorities defined by participating Nations.
As a multinational project supported by NCIA, the project has a fourth non-technical work package called MN5G Project Office, addressing enabling work elements, such as project management, support to MN5G Project Board, liaison/coordination activities and development of new PoW activities.
Although the MN5G project has not been established yet and a formal MN5G PoW has not been defined by its Project Board, the initial MN5G Reference PoW has guided numerous 5G activities being conducted within NATO and NCIA, such as:
• Development of reference use cases for 5G technologies in military scenarios. This work consisted of developing initial reference use cases and associated technical concepts in multiple application domains and under different 5G utilization concepts. These use cases and associated high-level technical concepts were shared with the wider scientific community via conference papers. They also informed other national and NATO 5G activities, such as the scenarios picked by NATO STO IST-187 Research Task Group (RTG).
• Conducting background technical studies with support from industry and academia. Two examples are the NATO Sweet Spot on 5G study conducted by Bell Labs Consulting, and a detailed technical study conducted by the University of Aveiro, both under NCIA guidance. The former provided recommendations on priority areas for NATO focus, including how best to engage with 5G/IMT standardization organizations to address the military interests. The latter analysed the potential of Open-RAN architectures and concepts for military applications, including a high-level design for a NATO-owned 5G testbed based on Open-RAN and open-source software.
• NATO 5G/Next-Generation Networks vision and strategy. In 2023, the NATO Digital Policy Committee (DPC) published a vision and strategy for 5G (and
ensuing generations of IMT standards) as the main driver for New Generation (communication) Networks (NGN). The strategy notes the importance of identifying and prioritizing military use cases for the evaluation of the potential of 5G/NGN technologies to enhance NATO operations, IT infrastructure and national capabilities. It states the importance of investing in technology watch activities, conducting trials, and implementing prototypes and testbeds to acquire organic and independent knowledge and experience in the technology. The strategy also calls for the development of common standards, engagement with industry and academia for interoperability and integration of legacy systems, as well as the development of effective partnerships between national, industrial and academic stakeholders.
• Development and implementation of a NATO 5G testbed. NCIA is implementing a lab-environment 5G testbed with support from academia. The aim is for NATO to have an organic and independent test and development 5G capability based on Open-RAN and on open-source software implementing a full 5G stack (core and access networks, including basic services). The intent of this testbed is two-fold: (1) Implement and test 5G Air Interface features that are critical for military use cases and which are not being pursued in commercial civilian implementations (for example, Sidelink, Integrated Access Backhaul (IAB), Dynamic Spectrum Sharing, or use of specific frequency bands of military interest), and (2) Use it as a platform to test new applications and develop other technologies, such as autonomy, artificial intelligence, or mobile edge computing.
• Establishment of STO IST-220 NATO Wireless Communications Standardization RTG. IST-220 is a voluntary effort by NATO and national governmental and industrial representatives to collaboratively develop standardization profiles for military use cases and provide inputs to standardization forums (primarily 3GPP). This RTG aims at generating draft NATO standardization artefacts (for example, specifications, technical features, interoperability profiles, and so on) to ultimately enable interoperability of military 5G systems. That includes complementing 3GPP specifications to close gaps with military requirements, and contributing to future IMT/6G standards to stay ahead of the curve. This RTG leverages the fact that many of its industrial participants are active 3GPP delegates and are thus well placed to propose the inclusion of technical features of military interest in commercial standards. The RTG is co-chaired by NCIA, which ensures first-hand liaison with background NATO technical work on 5G and with Capability Panel 1
(CIS) of the DPC substructure in coordination with Nato Digital Staff.
• Participation in 6G-NTN specification for 2030 and beyond. NCIA SMEs are currently taking an advisory role in a multinational consortium with European industry, Horizon Europe 6G-NTN, which is investigating Non-Terrestrial Networking (NTN) evolutions for future IMT generations (6G and beyond). NTN deals with airborne and/or space-based components of 5G, and was long identified in reference use cases for military use of 5G by NCIA (for example, Land Tactical Operations). Through this long-lead activity, NCIA SMEs are contributing to the identification of functional and technical NTN requirements for defence applications in future IMT/6G standard development efforts.
• 5G Technology watch activities. Under NATO PoW funding, and to a limited extent, NCIA SMEs are monitoring latest developments of 5G and related technologies, with a particular attention to their military application. Since 2021, NCIA has been issuing a quarterly 5G technical newsletter to a wide community of interest. 5G/IMT is a complex topic prone to commercial hype and misunderstandings, and it is essential for NATO and national decision makers to be correctly informed by unbiased sources.
The MN5G MoU was developed in 2022 and was extensively discussed between Nations and NCIA throughout 2023. It sets the legal framework for the project, defining its high-level scope, project governance and management, roles and responsibilities, and so on.
As of end of Q2 2024, two Nations have signed the MoU and another is about to sign. Two additional Nations have confirmed their intention to initially join the project with observer status. MN5G will be formally established in Q3 2024 with at least three initial participating Nations, with others to join at a later stage via MoU amendments.
The first MN5G activities will be establishing the MN5G Project Board for governance and direction and defining the actual MN5G PoW to be executed by NCIA.
The development the actual MN5G PoW will be informed by the MN5G Reference PoW and coordinated with ongoing NATO and national work on military use of 5G, to avoid duplication of work, maximize potential synergies and address the priorities of MN5G participating Nations. In our view, the priorities for MN5G work should be the following:
• Embrace and leverage STO IST-220 standardization efforts. MN5G, as a funded project directed by national governmental representatives, can leverage IST-220 standardization efforts in
different forms: providing governmental inputs on multinational use cases and associated requirements and architectures, providing a forum for technical collaboration between nations (including their industry), and developing prototypes and reference platforms to support standardization development. MN5G and IST-220 should be aligned as symbiotic and complementary efforts.
• Develop mature reference use cases for military use of 5G and 6G technologies. Although use cases are well known and have been identified by both NATO and Nations, they are often defined at high level only. Credible reference use cases must include detailed scenario descriptions, clear functional and technical requirements, underlying 5G technical concepts, spectrum supportability aspects, and so on, to correctly inform ensuing standardization, architecture development, prototyping, testing and industrialization activities.
• Test non-standard 5G features critical for military use cases. Ongoing ‘military 5G’ experimentation efforts systematically consider mainstream 5G features typical of commercial civilian systems, failing to exploit and test optional features in 3GPP standards that are critical to military use cases, such as Dynamic Spectrum Sharing, Sidelink, Integrated Access Backhaul, or use of millimetre wave frequencies (mmWave) for contested environments.
• Develop target architectures and blueprint designs. MN5G can also develop target architectures and blueprint system designs to be used by Nations and NATO, to facilitate standardization efforts, multinational interoperability, and ultimately the creation of an enabling market of military off-the-shelf solutions. This work can also generate inputs to NATO innovation under DIANA challenge programmes.
• Implement test and development reference systems. In coordination with NATO standardization and capability development activities, MN5G can also develop, host and maintain 5G reference systems in support of multinational standardization and/or multinational testing, including the provision of an enabling interoperability testing service.
• Expand 5G technology watch and coordination activities. MN5G can also expand the scope of current technology watch activities conducted by NCIA in ambition and scope, such as active and in-depth engagements with relevant 5G stakeholders, such as industry associations, standardization entities, and industry. In addition, the project can also facilitate coordination with other relevant stakeholders involved in military 5G programmes (Nations, NATO, EU, industry, and so on), by virtue of its multinational dimension and the fact that it will have a funded PoW.

All the above possibilities for the actual MN5G PoW will be discussed between MN5G participating Nations and NCIA in coordination with NATO PoW entities, such as ACO, ACT, NDS and STO. These entities will likely be active observers in the project and will align and coordinate their PoWs with MN5G efforts (and vice-versa). Ultimately, participating Nations will decide on scope and level of ambition for MN5G PoW once the project is established, including future adjustments.
MN5G will leverage and complement ongoing NATO efforts in military use of 5G. The project will also bring new contributions to the table, not least due to two unique characteristics: (1) multinational scope and (2) national and commercial neutrality. Multinational scope is ensured by the fact that it is defined and funded only by the participating Nations, who want to complement their national programmes with concurrent activities under MN5G addressing multinational use cases (and/or common national use cases). National and commercial neutrality is ensured by the multinational nature of its governance (provided by governmental representatives) and by the fact that NCIA, which will execute the project, is nationally and commercially unbiased and is not a requirements holder in NATO Capability Development.
The establishment of the MN5G project will bring new prospects to military use of 5G/IMT technologies by participating Nations and their industry, NATO, and indirectly to other national and industrial stakeholders from non-participating Nations.

NITECH celebrates the contribution that women have made to NCIA’s technology development and how that has benefitted NATO and its Member Countries over the 75 years of the Alliance
IVANA ILIC MESTRIC, PRINCIPLE DATA SCIENTIST
What inspired you to pursue a career in STEM and how did you get started?
It was a combination of several factors. From an early age, I had a talent and a natural curiosity for mathematics and science. This created a strong foundation for my interest in STEM fields. But, I also wanted a challenge to explore and progress in an area where women are underrepresented, so that I could help break down barriers and prove that only hard work and persistence matters. These characteristics can open up many opportunities.
Can you share a significant project or innovation you’ve contributed to during your time at NCIA?
Whilst working in artificial intelligence (AI), which is still a very innovative area, I have made many valuable contributions and provided leadership to a variety of interesting and innovative projects. For example, I worked on STEAM (Science & Technology Ecosystem Analysis Model), which provides insights for NATO’s Office of the Chief Scientist by analysing millions of articles using AI.
I also contributed to Merlin - IEA (Information Environment Assessment), which promotes the use of AI to monitor information sources on behalf of NATO’s Strategic Communications Centre of Excellence.
In addition, I am very proud to be one of the initiators of an AI Masterclass for NATO senior leadership to help them become familiar with AI and deepen their understanding of AI technology.
In what ways do you believe your contributions have positively impacted NATO’s technological advancements?
Firstly by discovering the art of the possible, and then demonstrating technological value to the end users across the NATO enterprise. But, even more important is using my expertise in AI to help end users utilize AI technology. I have been fortunate enough to demonstrate this through many projects.
How have you seen the role of women in technology evolve since you’ve worked in STEM?
More women are pursuing STEM careers and demonstrating not just tech skills, but also a valuable balance between STEM and soft skills. Over the years, I’ve seen a gradual but steady shift towards greater inclusion and empowerment of women in STEM.
How do you think diversity, especially gender diversity, has influenced innovation within the organization?
Gender diversity brings new perspectives and different angles. These differing views and opinions inevitably open the door for innovative ideas.
MEGAN BROWN, SENIOR TECHNICIAN
What inspired you to pursue a career in STEM and how did you get started?
I did my Bachelor’s degree in criminology and psychology at University in London, only to find myself in a Communications and Information Systems (CIS) role with the Civil Service after graduating. Whilst there, I took advantage of the continued professional development and IT courses I was placed on to continue learning during full-time work. I was the first woman placed within my unit’s IT team at the UK Government’s Ministry of Defence. That’s when I first realized there was a place for women to grow and have equal opportunities within the technology field.
In what ways do you believe your contributions have positively impacted NATO’s technological advancements?
I am a Senior Technician within the Service Centre at the CIS Support Unit (CSU) in Brussels. Having been in the role for just over a year, I believe I have made a positive impact on diversity for the Service Desk and the streamlining of IT processes. Our team is critical to the everyday work of NATO, ensuring services are up and running and providing first-hand assistance and communication with customers whenever necessary. Many customers comment on their delight and pleasure of seeing more females on the team, which is always fantastic to hear and have acknowledged.
How have you seen the role of women in technology evolve since you’ve worked in STEM?
The ratio of women has slowly increased and I am now seeing women attain well-deserved influential and managerial positions.
However, within the past three CIS teams that I have been a part of I have always been one of only a few women. That said, each time, I have been accepted particularly well by both my colleagues and customers alike. They often emphasise the positive impact I am making.
How do you envision the future of women in tech in NATO and what steps can be taken to further support their advancement and inclusion within the field?
Inclusion of women should be a no-brainer, but we can help to achieve it by speaking out, championing diversity and making sure everyone has a seat at the table.
I have been one of very few women in each of the technical teams that I have been a member of throughout my career. I hope I have helped raise the visibility and strengthened the voice of women within the industry by challenging the status quo, and inspired others by breaking the stereotype and showcasing that women are capable in such roles.


What inspired you to pursue a career in STEM and how did you get started?
When I was younger I always enjoyed maths because of the logical thinking, the fun puzzles and the fact that there was only ever one correct answer. I found it a lot more satisfying and a lot less scary than English, history, or religion where you had to write convincing arguments and essays. After high school, and alongside college degrees in maths and computer science, I completed a lot of summer internship programmes as well as a semester abroad studying maths in Budapest, Hungary. This gave me not only a great foundation in STEM skills, but also a strong network of friends and colleagues who motivated me and made me feel passionate about continuing on to a maths and computer science career.
Have there been any particular mentors or role models who have influenced your journey in tech?
Working in STEM, specifically in technical roles for the public interest, runs in my family, so my parents were certainly my first role models. At university and graduate school, there was a particular college professor who has recently retired. He comes to mind. He had an infectious love of maths. Early in my career, I worked with, and for, a number of men and women that not only encouraged me, but pointed me towards interesting projects and new opportunities. I try to be a role model myself at this stage in my career, speaking at conferences, speaking to students and things like that.
Can you share a significant project or innovation you’ve contributed to during your time at the Agency?
I am very proud of the work I undertook when I was a part of the Cyber Adaptation project, which took place during Covid under the oversight of NATO’s Deputy
Secretary General’s office. I worked as part of an integrated team of people from across NATO, together with full-time on-site consultants. Our task was to examine how NATO could invest in, and mature, its cyber security programme.
Naturally, we investigated our cyber security technologies and teams, but it was so much more than that. It covered governance, asset management, procurement and understanding the external threat landscape. We also looked at how to manage issues that impact NATO at technical, political and military levels. It was an extremely rewarding project that led to many insights and improvements that are in place today.
In what ways do you believe your contributions have positively impacted NATO’s technological advancements?
The contributions that I believe make a difference in my work are my collaborative leadership style, my knowledge of the field, my ability to ask good questions and my wide network across NATO and the wider cyber security community.
How do you envision the future of women in tech in NATO and what steps can be taken to further support their advancement and inclusion within the field?
I hope the future involves many women working in the technology arena, including within NATO. When organizations create welcoming, fun, collaborative and safe environments to pursue challenging problems, both men and women will want to participate and, in my opinion, they will undoubtedly thrive.


NCIA offers excellent opportunities for young graduates and students to engage with technology at a very high level. Talia Goode asks former Data Science intern, Daniel Sousa , about the process of applying for an internship at NCIA and what to expect if your application is successful
How did you become aware that NCIA was recruiting interns?
I first learnt about the intern opportunities at NCIA during my final year of university; it popped up on my LinkedIn and immediately caught my attention. The job description seemed like a challenging role and I was very happy to find a position with the opportunity to live abroad despite the COVID-19 restrictions in place at the time. I had completed other internships in the private sector, which provided valuable experience, but the feeling of serving a bigger purpose was missing. Supporting NATO’s mission to protect nearly one billion citizens across the Atlantic motivates and inspires me daily.
What did you think of the process for applying and starting at NCIA?
The application process for NCIA was multi-staged. I underwent several rounds, including technical interviews with senior data scientists from the team I would potentially join. Despite its complexity, the onboarding process was well organized and I received great support and guidance from the hiring team, my direct team and especially from my internship sponsor. Their assistance was crucial in helping me understand the role of our team within NCIA and how to navigate the NATO ecosystem. They also provided advice to help me settle in a new city in a new country.
What sort of tasks and responsibilities did you have as a data science intern at NCIA?
During my internship, my primary responsibility revolved around a project on object detection using image data. This involved training machine learning (ML) models and developing an end-to-end solution for object detection. Additionally, I assisted with other team projects, including the development of solutions showcased at NATO exercises. The hands-on experience and exposure to real-world challenges were invaluable for improving my technical skills and problem-solving abilities. The way of working as a team was very dynamic and there was a lot of freedom to work on different projects and focus on personal areas of interest. As an intern at NCIA, I felt like a tangible asset to the team, and I was given real projects which contributed to the team.
What were the highlights from your NCIA internship?
My personal highlight from my internship was the content of my work, which was constantly evolving, keeping me on my toes and providing a continuous learning environment. One of the most rewarding aspects of my
work was being given the opportunity to actively contribute to the development of a prototype to support the Coalition Warrior Interoperability Exercise (CWIX), NATO’s biggest interoperability exercise. My task was to create an optimization algorithm to aid operatives in selecting how to decide which people should be attributed to which hospitals for example and in theory, maximize the amount of people that could be saved.
Another highlight was a project related to object detection and machine learning to process and analyse satellite imagery. This project involved collaboration from various teams across the organization and facilitated personal growth and development. In addition, introducing new tools and knowledge to the data science and artificial intelligence (AI) team emphasized the value of the fresh perspective that interns and graduates can bring.
Where did your NCIA internship take you next? Upon completing my internship, I transitioned back to industry and worked as a data scientist at a Portuguese bank. However, I kept an eye out for opportunities at NCIA.


When a vacancy caught my attention, I applied once again, and after roughly one year, I rejoined the Data Science and Artificial Intelligence team in a permanent capacity. In comparison to my internship role, my current role is more challenging, with harder deadlines and more responsibility, but I maintain a good work-life balance, which is an important NCIA principle. I continue to contribute to data science and AI projects, leveraging the experience and skills I gained in my previous roles to drive innovation and contribute to NCIA’s work supporting NATO’s mission.
What advice would you give others interested in or considering applying for a tech-focused internship? For individuals considering applying for a tech-focused role or internship at NCIA, I would advise them to be prepared for the application process. Like any international organization, it is thorough and lengthy but the aim is to get to know not only your professional skills, but also the interpersonal skills you will bring to the team. While the wait may be challenging, the experience and
knowledge gained during the internship are invaluable. Embrace the opportunity to learn not only about new technologies but also about the unique dynamics of an organization such as NATO. Additionally, investing in yourself by acquiring practical skills and familiarizing yourself with industry-standard tools can significantly enhance your chances of success. Remember, internships are not just about what you can learn; they are also about what you can bring to the table. So, bring fresh perspectives, innovative ideas and a willingness to collaborate to make a meaningful impact during your time at NCIA.


Martine van de Gaar, CEO and co-founder of Linksight, tells Simon Michell how the European Union’s Women TechEU scheme helped her company develop and launch a successful encryption-based data collaboration platform
What is Women TechEU and how did you become involved with it?
Women TechEU is an EU-funded scheme aimed at boosting the number of women in boardrooms and improving the gender balance in entrepreneurship. The vision behind it is to encourage and support women at the top of innovative tech companies. It has several benefits; not only does it help individual women, it also helps their companies, as research has shown that the more diverse a company’s workforce is, the more successful it can become.
Essentially, it is a grant scheme for women in leading positions (CEO, CTO or equivalent) in European deep tech startup companies. The programme offers grants of up to €75,000 as well as a range of support to help develop the company, in addition to a product that they can launch on the market.
My company, Linksight, was spun out of the Dutch applied research organization, TNO. That background gave us a familiarity with the grants and subsidies in the private and public sectors. In addition, we have an agency that specifically trawls the subsidy grant arena – local, national and international – to alert us to opportunities. They found the Women TechEU scheme and suggested we apply for it.
How has the scheme helped your company develop your data analytics platform?
The scheme gave us a terrific boost right from the beginning in a variety of ways. Many of the women that I met in the programme were first-time entrepreneurs. The programme helped us understand the various aspects involved in running a company. It is not just about the products and technology; it also covers a range of skills you need to run a company successfully.
Innovative tech start-ups always need to raise funding through the investment ecosystem, and so one crucial lesson I learned was the importance of being discerning when selecting investors, as severing ties with them can be challenging if things don’t go as planned or if you wish to change direction. In fact, the relationship with an investor can be extremely close, perhaps even closer than a partner. These kinds of takeaways, which help you build your company with strong foundations, are invaluable.
In terms of technology, we received the grant just six months after we established the company. At this point we still had not secured our first customer – the funding we got from Women TechEU enabled us to continue development. So, we managed to get a minimal viable product developed, which meant we could get started with clients. In other words, it was an early investment that helped us get on our feet.
How important is the network that the scheme nurtures?
The programme helps you create a network of like-minded people and organizations that can help you. When I started my career in 2007, there were female IT groups and bodies that I did not join as I was a bit wary of them and their perspective on the world. But I am really glad I have met the other women in the Women TechEU programme. Some of them are absolutely awesome. We really engage with each other and try to help each other along the way. On top of that, there is a wider international aspect to the scheme, which was a real eye-opener for me.
What does the Linksight data analytics offering do and why is it unique?
We develop technology at Linksight to support data collaborations. However, the unique aspect of our
“ I would definitely recommend other women to apply for the programme.
Besides the financial aspect, which is of course one of the main drivers, the mentoring sessions, the coaching and, of course, the network, make it so worthwhile”
offering is that it ensures that privacy is absolutely protected. That is important, because most current data collaboration tools typically copy data to bring various different data sets together in a single space in order for analysis to take place.
What makes our collaboration platform different is that we have a decentralized solution. The data stays at its original source, yet organizations can still gain insights from it thanks to our encryption tools, meaning they do not have to share sensitive data with each other nor with Linksight. Our solution has a second pillar related to data collaboration governance. This is a set of rules that enables organizations to add trusted partners to their network and operate according to an agreed set of principles, which allows organizations to keep control of their data and only share what they want to share.
Will Women TechEU continue to support you and your company, and if so, how?
The scheme was a one-off award. We could, of course, apply for another award if we met the criteria for any follow-on scheme. What is perhaps more significant is that the community we developed during the programme continues to exist. That network continues to help us. For example, it might alert us to any upcoming fundraising opportunities or exciting events we might want to attend.
The EU has several coaches in each EU country that you can select from. They have different skills and backgrounds so you are able to select one that will be best for your specific requirements and has the expertise you are looking for. I am still in contact with the coach that I selected for the programme.
What advice would you give other female technology leaders who are considering applying for Women TechEU support?
I would definitely recommend other women to apply for the programme. Besides the financial aspect, which is needless to say one of the main drivers, the mentoring sessions, the coaching and, of course, the network, make it so worthwhile. When I was on the programme, we covered about eight topics in the numerous sessions. These were not only to do with product development, but also more general topics related to building your company. They taught you how to deal with generic issues such as investments, setting up sales channels, putting a value on your sales leads – a whole host of business skills that have proven to be invaluable.



After five years as the founding Director of the NATO Space Operations Centre (NSpOC) at Allied Air Command (AIRCOM) in Ramstein, Germany, Colonel John D. Patrick is moving on. In recognition of his amazing accomplishment establishing the Centre and to celebrate the extremely close relationship between NCIA and NSpOC, we bid him farewell and wish him the very best for the future


Colonel John D. Patrick has been a hands-on space operator since the start of his career in the United States Air Force beginning in the late 1990s. He stepped on the scene as a Satellite Operations Officer at the 4th Space Operations Squadron at Schriever Air Force Base (AFB), Colorado, before becoming the 50th Space Operations Group Chief of Inspection Compliance. He then moved on to Vandenberg AFB California, where he was the Satellite Operations Lead Instructor charged with training officers and enlisted cadre to become satellite operators. He then undertook follow-on assignments to Colorado Springs Colorado, Maxwell Air Base Alabama and back to California where he ultimately took command of the 369th Air Force Recruiting Squadron.
Prior to his tour of duty at Ramstein Air Base in Germany, where NITECH caught up with him, he was stationed at Supreme Headquarters Allied Powers Europe (SHAPE) near Mons, Belgium. It was here, as the only space expert at the HQ, that he embarked on his eight-year journey to establish space as an operational domain, which then led to the NATO Space Operations Centre (NSpOC) being established.
At just under 20 people, the NSpOC is a relatively tight-knit organization. It is, however, still growing and gaining ever more influence across one of NATO’s newest operational domains. The fact that space has been recognized as one of NATO’s operating domains is in no small part down to Colonel Patrick, who led the effort – along with Commander Robert Kroeger from Allied Command Tranformation (ACT) – for its recognition while at SHAPE from 2016 to 2019. Together, they managed to get the policy adopted by the NATO North Atlantic
Council (NAC) – NATO’s principal decision-making body. It is a testament to what two OF-4s (Lt Col and equivalent ranks) can accomplish with grit and determination.
When Colonel Patrick arrived at AIRCOM in 2019 to establish the NSpOC, he was the only person there with a pedigree in space, “There was not a lot of space expertise at Ramstein in those days.” This meant that relationships with external organizations and agencies were key. “Space is a team sport. Space has to be collaborative. I worked a lot with Laryssa Patten at NCIA. She was a key NCIA space expert and has since gone on to become NCIA’s Head of Space Technology Adoption and Resilience (STAR) programme. Nowadays, we talk to NCIA on a routine daily basis. The relationship is very important to us.” But it was not just NCIA; Colonel Patrick also received a lot of support from the aforementioned Robert Kroeger, the Space Integrator at Allied Command Transformation, as well as from NATO HQ, national space entities and individuals who were genuinely interested in moving space forward in NATO and, in particular, standing up the NSpOC.
So what does the NSpOC actually do? “The NATO Space Operations Centre is the main hub for all NATO Force and Non-Force Components. All 32 NATO Member Countries are able to receive space products or services and Nations can collaborate on products. It also serves as the liaison office between all the Nations of the Alliance,” explains Colonel Patrick. A major task is keeping the NATO Member Countries informed of overall space activities. For example, they let everyone know when a rocket body or other large piece of space ‘junk’ is returning to earth after a satellite insertion mission.


The NSpOC saw an immediate uptake in its services and its day-to-day activities when Russia illegally invaded Ukraine. “I think the Ukrainian crisis really propelled us forward in a lot of different ways. When the illegal invasion took place we immediately began to provide more services to the Alliance members. These services are in essence about providing products to those who are experiencing such things as GPS or SATCOM jamming, for example, to help mitigate these effects.”
“When I look back at my five years as Director of NSpOC or, indeed, over the entire eight years we have been on this journey, my proudest moments are mostly related to the growth and successes of the individuals I have been on this journey with. I am very proud to have helped nurture and develop individuals to be the best they can be so that they can fulfil their ambitions in space,” Colonel Patrick says. He gives two specific examples. The first is NCIA’s Flavio Giudice, who was an intern at the NSpOC and who then joined NCIA, and is currently working for Laryssa Patten on the STAR programme. The other is Francisco Gallardo, one of his Spanish officers who was at the NSpOC from the beginning. “He was incredibly enthusiastic about space and everything related to it. The Spanish military has now reclaimed him and brought him back to Spain to work on their own domestic space agenda.” But these are just two examples – Colonel Patrick named more than 20 other members of the NSpOC team he had the pleasure of working with over the years. For Colonel Patrick it’s about the mission, and people are his mission.
Colonel Patrick is being somewhat modest. When he turned up at AIRCOM to establish the NSpOC, all he had was himself and an office. There were no staff members, no computers and in fact, no centre. Bit by bit Colonel
Patrick has had to navigate through a complex bureaucratic structure to piece together the puzzle to get where he is today. For everyone who helped him, and there were a lot of people keen to lend a hand, there is a bright light at the end of the tunnel. After a lot of trial and error, Colonel Patrick has finally managed to get his budget request across the finishing line. He is confident it will be granted soon. Once it is, everybody who lent him resources and equipment will be reimbursed – at least, that is his hope.
From the early days when it was just him at the NSpOC, he had to knock on doors at Ramstein to find people who wanted to join his team. Now, there are some 14 Nations integrated with the NSpOC. But Colonel Patrick is not satisfied with that. He has set the challenge for his successor to bring in the rest of the NATO family of Nations. He explains it like this: “Our relationship with some of the Nations is incredible. Within the past two years we have really brought Spain along with us to accelerate their programme. We are doing that now with Poland and Romania this year, but there are other NATO Nations that are only now beginning to develop a space programme. And so, that is my challenge for my successor. How can NSpOC get these Nations to develop quickly? NSpOC can help new Nations avoid the trials that we went through and bring them up to our level much more quickly. We can share best practices. We need to get every Nation up to speed with us and then they can go faster than us, which will make the Alliance even stronger.”
NATO INNOVATION AND TECHNOLOGY
ISSUE 11 | JULY 2024
Editors
Lara Vincent-Young and Simon Michell
Project Manager
Andrew Howard
Editorial Director
Emily Eastman
Art Direction
Errol Konat
Layout
Billy Odell
Contributing Photographers
Marcos Fernandez Marin, Conrad Dijkstra, Francesc Nogueras Sancho
Printed by Micropress Printers Ltd
Published by
Chantry House, Suite 10a High Street, Billericay, Essex CM12 9BQ
United Kingdom
Tel: +44 (0) 1277 655100
On behalf of
NATO Communications and Information Agency (NCIA) Oude Waalsdorperweg 61, 2597 AK The Hague, Netherlands
© 2024. The views and opinions, expressed by independent (non-NATO) authors, contributors and commentators in this publication, are provided in their personal capacities and are their sole responsibility. Publication thereof, does not imply that they represent the views or opinions of NCIA, NATO or Global Media Partners (GMP) and must neither be regarded as constituting advice on any matter whatsoever, nor be interpreted as such. References in this publication to any company or organization, as well as their products and services, do not constitute or imply any direct or indirect endorsement, recommendation or preference by NCIA, NATO or GMP. Furthermore, the reproduction of advertisements in this publication does not in any way imply endorsement by NCIA, NATO or GMP of products or services referred to therein.


