29 minute read
Editorial Calendar
Install the image created by appliance-creator using virt-manager. You will probably need 3 GB of memory to successfully install OpenStack.
Now you are ready to follow the RDO ‘quick start’ instructions (http://openstack.redhat.com/Quickstart).
Advertisement
The following commands are fairly quick:
# yum install -y http://rdo.fedorapeople.org/rdo-release.rpm # yum install -y openstack-packstack
The packstack command makes it simple to install OpenStack and the dependencies. It uses Puppet. However, the packstack command may take a long time, depending on the network and download speeds (I usually find it better to add ‘&country=us,ca’ to Fedora and update repositories for the Indian environment).
# packstack --allinone
You may find that the above command fails to run the remote script after setting up the ssh keys. If so, you need to set up authorised keys.
# cat /root/.ssh/id_rsa.pub >> /root/.ssh/authorized_keys
The first time Packstack is run, it creates an answer file with a name like packstack-answers-X-Y.txt. You will need to reuse the same answers in case you have to rerun Packstack.
# packstack –answer-file packstack-answers-X-Y.txt Figure 1: OpenStack
After Packstack completes successfully, the local cloud is ready. You can browse the site http://$VM-IPADDRESS/dashboard.
Some things to think about
What do you do with the local cloud you have set up? How do you create and manage the virtual machines that you need?
By: Dr Anil Seth
The author has earned the right to do what interests him. You can find him online at http://sethanil.com, http://sethanil. blogspot.com, and reach him via email at anil@sethanil.com
osFy Magazine attractions during 2014-15
Month theMe Featured List buyers guide
March 2014 Network monitoring Security -------------------
April 2014 May 2014 June 2014 Android Special Backup and Data Storage Open Source on Windows
July 2014 Firewall and Network security
August 2014
Kernel Development September 2014 Open Source for Start-ups Anti Virus
Certification
Mobile Apps Wifi Hotspot devices External Storage UTMs fo SME
Web hosting Solutions Providers MFD Printers for SMEs Big Data Solution Providers SSD for servers
Cloud Android devices
October 2014 Mobile App Development November 2014 Cloud special Training on Programming Languages Projectors Virtualisation Solutions Provider Network Switches and Routers
December 2014 Web Development January 2015 Programming Languages A list of leading Ecommerce sites AV Conferencing IT Consultancy Laser Printers for SMEs
February 2015 Top 10 of Everything on Open Source Storage Solution Providers Wireless routers
Admin How To
Wireshark: Essential for a Network Professional’s Toolbox
Wireshark, a free and open source tool, is a packet analyser. It is used for network troubleshooting, software-analysis, protocol development, and education. In this and the following few articles, the author will help readers gain in depth understanding of using wireshark for network troubleshooting.

In order to troubleshoot computer network related problems effectively and efficiently, an in-depth understanding of TCP/IP is absolutely necessary, but along with that, you also need to ‘see’ TCP/IP traffic. There are various open source and commercial tools available to capture and display network traffic for further analysis.
Let us consider the essential features of effective traffic analysis and network troubleshooting tools: The ability to capture traffic from various networks such as wired, wireless, etc Layer-wise representation of captured traffic for easy readability Ability to save the packets in standard format Ability to drill down packets for traffic analysis
All these features are an inherent part of Wireshark. Over and above this, the tool is available under GNU GPL (read, free). So Wireshark is an absolute must for any networking professional!
This series of articles on Wireshark will familiarise readers with the Wireshark GUI and analysing various TCP/IP protocols by means of captured packets, explaining the features of Wireshark and discuss various scenarios to locate network related problems.
The basics: Wireshark modules
To provide the desired functions, Wireshark uses a number of different modules integrated together by the Wireshark core.
Module Function
GTK (GIMP Toolkit) GUI and handling of all user inputs/ outputs Dumpcap Packet capture engine Pcap libraries Actual packet capturing. The Linux version uses libpcap developed by the Tcpdump team (available under the BSD licence), while the Windows version uses winpcap developed by Riverbed Technologies, which is available as freeware
Dissector(s) Detects the packet’s type and gets the maximum information out of it – you can also write custom dissectors Wiretap libraries Reading and writing captured files from and to various file formats
Here, I have taken the liberty of mentioning only the important or relevant modules and their functions for easy understanding. For more details, please refer to wireshark.org.
Installation
Wireshark installation is very simple and straightforward.
Windows: Download the latest 32- or 64-bit version installable, which is compatible with your Windows version; double-click on it and follow the instructions.
During this installation, you will be asked to confirm installation of winpcap libraries. Here is an interesting point to remember for those paranoid about security: some of the websites, such as McAfee SiteAdvisor, rate winpcap libraries as security risk. This is primarily due to the ability of winpcap to capture network packets. So go ahead and install the libraries, which are a must to run Wireshark.
Ubuntu: Search for Wireshark under Ubuntu Software Centre, and click to install or use the command line:
sudo apt-get install wireshark
That’s it. Your system is ready for the first capture. Welcome to the exciting world of network troubleshooting and protocol analysis.
Capturing packets
Windows: Start Wireshark by clicking its icon.
Linux: Use the command wireshark. You may require administrative privileges. The recommended way to do so is to use gksudo wireshark.
Wireshark also has various command line options, which will be covered in a separate article. Optionally, you can capture packets using dumpcap (the packet capture engine), save them and use Wireshark for further analysis. This ensures minimum administrative privileges, limited only to the capture engine and not the entire Wireshark software.
Select the capture interface on the first screen. Go through Figure 1; did you notice something interesting under the Interface List? You can capture traffic on USB ports as well!
Click on the desired interface and Wireshark starts capturing and displaying packets, which are represented in three panes.

Figure 1: Wireshark interface selection
The three Wireshark panes
The topmost pane is called the ‘Packet List Pane’ and displays the captured packet’s number, its time stamps, source and destination addresses, protocol, length and other information about it.
The middle pane displays ‘Packet details’ of the current packet as viewed from various layers. The captured data could be viewed as Frame – Physical, Ethernet – Data Link, IP – Network, UDP (or TCP) – Transport, and DNS (or any other application) – Application layers. (For more details about these layers, there is ample material, including excellent videos, on the Web to get a better understanding.)
‘Packet Bytes’ are displayed in the bottom most pane.
If this sounds very simple, here is one interesting difficulty.
Capturing packets in a switched environment
Capturing traffic towards and from Wireshark PC is simple enough; however, for network troubleshooting you require to capture various kinds of network traffic, such as what originates from any of the systems in the network, the entire network traffic from your network towards the Internet, etc.
Capturing traffic in a switched environment is not easy. And here’s why. Let me start with the difference between an Ethernet hub and an Ethernet switch. The hub sends all packets received on a particular port to all the other ports. The switch forwards traffic only to the designated port. To achieve this, the switch maintains a table of MAC addresses (Layer 2 address corresponding to the port binding), and forwards the packet to the interface to which the device with the destination MAC address is connected. If the destination MAC is not known, it broadcasts to all ports (except the sender port), asking for the port that has the device with the destination MAC. Once a confirmatory reply is received, the actual packet is forwarded to the corresponding port only.
From a security perspective, an Ethernet switch is definitely better (than the hub). However, the feature ensuring security poses a challenge while capturing network traffic. In a switched network, the default capture will contain packets to and from the Wireshark machine and broadcast traffic only.
There are several ways to overcome this: 1. Hubbing out: Replace the switch with a hub and capture traffic by connecting the Wireshark system to the hub. 2. Using Wiretap: A‘tap’ is used to capture communication between two end points. The primary concern while inserting Wiretap is that it should not disturb any traffic between two hosts. Wiretap achieves this by sitting between two end points (the switch and device) and providing two Ethernet outputs. These are connected to the Wireshark computer system with dual Ethernet. This system captures all traffic between two nodes without disturbing existing traffic. If this tap is inserted between the firewall and the switch, it will capture all Internet traffic. Typically, this box can be constructed by wiring four information outlets. See the wiring diagram for more details (Figure 2).
Wiretap Wiring Diagram
2
1
3
H O S T
7
8
6
5
A
4 2
1
3
H O S T
7
8
6
5
B
4
2

1
3
5
T A P
A
7
8
6
4 2
1
3
5
T A P
B
7
8
6
4
omegasystems.co.in
Figure 2: Wiretap

Figure 3: DNS query and ICMP echo request
3. Using Switched Port ANalyzer (SPAN), also called port mirroring: SPAN ports are available with some of the managed switches. Once enabled, this feature copies traffic from the defined ports to the SPAN port. The
Wireshark system is connected to this SPAN port to capture the traffic. The disadvantage of this system is that the SPAN port can get overloaded since it receives all traffic from many ports. This results in loss of packets. 4. Using ARP spoofing: This requires using the ARP spoofing tool such as ettercap-NG, which is tricky and may result in network disruption if sufficient care is not taken.
The first capture
Let us start by capturing packets for the DNS (Domain Name Service) protocol. As you must be aware, DNS resolves URLs to IP addresses. It is a very simple UDP protocol (works on TCP as well). It sends out a DNS query and gets a DNS query response.
To capture DNS, start Wireshark and select the desired interface to start packet capture. Go to the command prompt under Windows (or the terminal, in the case of Linux) and ping any URL—the associated screenshot (Figure 3) is for omegasystems.co.in. You will see several captured packets on the screen. Stop packet capture.
The command line request to ‘PING’ omegasystems. co.in triggered a 78-byte UDP DNS query from the computer system 192.168.1.2 (IP address in your capture will be the same as the TCP/IP configuration of your capture system) towards DNS server 208.67.222.222. A 94-byte reply was received with the IP address of omegasystems.co.in as 23.91.123.124.
A 74-byte ICMP Echo Request is now sent to the resolved IP address of omegasystems.co.in, for which a 74-byte ICMP Echo reply is received.
Please view the Time column, and you will notice that approximately 0.3 seconds were required to receive replies for both these queries.
Background information on Wireshark.org
In May 2006, Gerald Combs (the original author of Ethereal) went to work for CACE Technologies (best known for winpcap). Unfortunately, he had to leave the Ethereal trademarks behind. This left the project in an awkward position. The only reasonable way to ensure the continued success of the project was to change the name. This is how Wireshark was born. Wireshark is a network protocol analyser. It lets you capture and interactively browse the traffic running on a computer network. It runs on most computing platforms including Windows, OS X, Linux and UNIX.
Wireshark's Sectools rating
Sectools.org, maintained by the Nmap Project, has been cataloguing the network security community’s favourite tools for more than a decade. It ranks Wireshark as the No 1 among network security tools and describes it as follows: “Wireshark (known as Ethereal until a trademark dispute in Summer 2006) is a fantastic open source multi-platform network protocol analyser. It allows you to examine data from a live network or from a capture file on disk. You can interactively browse the capture data, delving down into just the level of packet detail you need. Wireshark has several powerful features, including a rich display filter language and the ability to view the reconstructed stream of a TCP session. It also supports hundreds of protocols and media types.”
A word of caution
The test scenarios described in this series of articles are capable of revealing sensitive information such as login names and passwords. Some scenarios, such as using ARP spoofing, will disturb the network temporarily. Make sure to use these techniques only in a test environment or avail explicit written permission before using them in a live environment.
By: Rajesh Deodhar
The author is an IS auditor and network security trainerconsultant for the last two decades. He is a BE in industrial electronics, as well as a CISA, CISSP, CCNA and DCL. He can be contacted at rajesh@omegasystems.co.in

Admin How To
Ghost: A Powerful Blogging Platform
If you are on the lookout for a blogging platform, give Ghost a try. It’s a simple yet powerful publishing platform that opens up the world of online journalism to you. Ghost is used by thousands of people and companies.

My encounter with Ghost, not the one from the horror stories, started when I was wandering through the Internet looking for a blogging platform for my college group, which focused more on writing rather than the several options that offer plugins to do simple things. When I navigated to the official page of Ghost (https://ghost.org/), all it said was, “Just a blogging platform.” Ghost aims to be a simple, open source blogging platform focused on offering a good user experience.
Installation
Though it aims to be a simple platform, installation is not so simple for the average user. For a seasoned command line user, it’s a cakewalk. For this demonstration, I’ll be using Linux, so some of the steps will be Linux-specific. Ghost is built on node.js, and requires version 0.10.* (the latest stable version). For Linux, the easiest way to install node.js is via the available package manager, but it may or may not be the latest version. Therefore, the best way to install node. js is to download the latest tar.gz archive from http://nodejs. org/download/ to install the latest binaries from the section ‘Linux Binaries’ (if you like compiling), and then download the source code and compile. Before compiling, make sure Python is installed.
wget http://nodejs.org/dist/v0.10.28/node-v0.10.28.tar.gz
Version number may vary.
tar xzvf node-latest.tar.gz && cd node-v* ./configure make sudo make install
For Mac, Windows or other OSs, download the respective installer from http://nodejs.org/download/.
If you still face any difficulties, refer to the wiki page https://github.com/joyent/node/wiki/Installing-Node.js-viapackage-manager
After installing node.js, it’s time to download and set up Ghost. Before downloading, make sure you have the recommended version of node.js:
nodejs -v
Download the latest version https://ghost. org/download/ and extract it to a folder named ‘ghost’. But if you have a terminal opening right in front of you, then the following commands will do the trick:

curl -L https://ghost.org/zip/ghost-latest.zip -o ghost.zip unzip -uo ghost.zip -d ghost Figure 1: Ghost sign-up page
coNtENt NEw PoSt SEttINGS Full Name
Email Address
Password
SIGN UP
JAtIN DHANKHAR
Now cd to the folder named ‘ghost’ that you created earlier. cd to the correct folder and run the npm commands as follows:
cd path/to/ghost
In my case it was in the Downloads folder:

cd Downloads/ghost
Then install Ghost with:
SETTINGS
General
User GENERAL
Display a cover image on your site
Email Address
Posts per pgae
Dated Permalinks
Theme
dhankhar.jatin@gmail.com
Address to use for admin notifications
6
How many posts should be displayed on each page
Include the date in your post URLs
froyo - 0.1.0
Select a theme for your blog
SAVE
npm install -- production Figure 2: Dashboard theme section
After installation, type the following command to start Ghost:
npm start
Mac and Windows users can refer to the respective documentation for installation instructions (http://docs.ghost. org/installation/). Ghost will be up and running on Port number 2368. Point your browser to http://127.0.0.1:2368/ to see your Ghost blog in action. Now it’s time to create an admin user. Change the URL to http://127.0.0.1:2368/ghost, and create your admin user to log in to the Ghost admin.
For now, Ghost allows only one user per blog; multi-user support will be available in version 0.5, which is expected to be out early in July 2014. If you still want multiple user support, there are some hacks available like the one at http://lifewiththemacks. com/multi-user-support/. After signing in successfully, you may encounter a warning related to email configuration, which you can leave for now, as it will be used for resetting the password.
Writing
Writing a post in Ghost is simple. When you install it, there already is a post made for you which explains everything about writing. To put it simply, the writing is done in Markdown format.
Theming and customisation
Theming and customisation are simple and straightforward. To add a new theme, just copy the folder that has theme files to the Themes folder, which is inside the Content folder section and update the theme in the dashboard. Here is an example of the installation of a new theme named Froyo, which is available at https://github.com/adriannorman/froyo-ghost-theme. Download the zip file and extract it to ghost_folder ->content ->themes and restart Ghost. You can browse the themes at marketplace.ghost. org and then update them in the dashboard by navigating to / ghost/settings/general/.
Deployment
Now we are ready with a blog and, hopefully, can begin writing some interesting posts. But how do we share them? We can’t host our blog on our computer because of security reasons and also considering the fact that electricity is not cheap. So we need to deploy our Ghost blog, for which we have many options. But for now, we are interested only in free options, with custom domains also for free. This brings our options down to two places: Openshift and Github pages.
Openshift
Openshift allows easy deployment of Ghost blogs. Before getting started, get an account on Openshift and install the necessary tools from https://www.openshift.com/developers/rhc-clienttools-install. To create the app, type the following command:
rhc app create ghost nodejs-0.10 --env NODE_ENV=production --from-code https://github.com/openshift-quickstart/openshiftghost-quickstart.git
…or follow the guide available at https://www.openshift. com/quickstarts/ghost-on-openshift. Whenever you want to add a new theme or edit some configuration, use the following command:
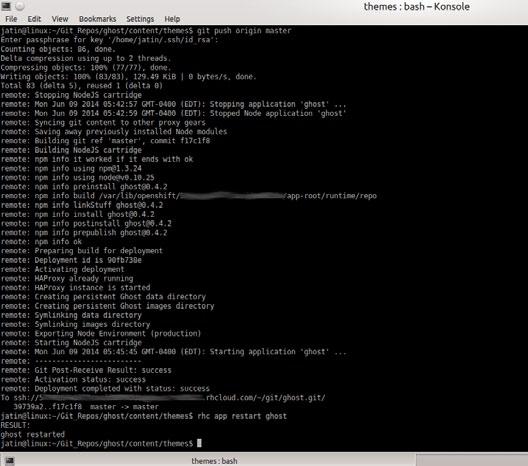
Figure 3: Deployment messages
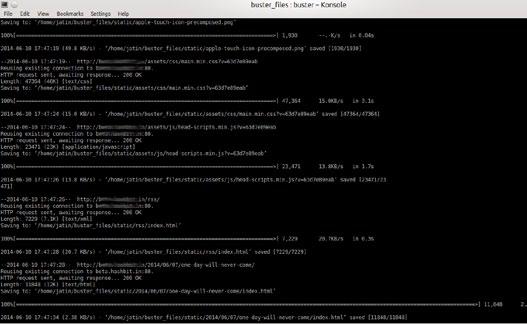
Figure 4: Buster generating static files site live on Github and you don’t want to alter it, make a new repo and name it ‘ghost’, and it will be available at username. github.io/ghost. Installing Buster is easy; just issue the following command:
pip install buster # prefix with sudo, if following command fails
Also make sure you have wget installed. To store the static content, create a separate folder for proper management, which I will name as buster_files:
mkdir buster_files cd buster_files
From the folder, run the following command:
buster setup
…and enter the address of the Github repo you created above. In my case, I was deploying to a repo named ghost, so it was https://github.com/jatindhankhar/ghost.git. Once you are done with this, run the following code:
buster generate -- domain=http://127.0.0.1:2368 # If ghost is running locally # or if you already have a ghost running somewhere else, use buster generate – domain=http://address-to.ghost.blog # Run it only on the ghost you own, otherwise you may violate some data mining laws
After Buster is done, it will store all the files in a folder named static. Switch to the static folder and add, commit and push the files to the repo using Git.
git add file_name_to_be_added git commit -m “Commit Message” git push origion master
rhc app restart ghost # Replace ghost with the name of app cd static git add. git commit -m “Your commit message here” git push origin gh-pages
After this, you will see something similar to what is shown in Figure 3.
Github pages
Github provides an excellent service to serve static pages. But Ghost requires node.js on the server side; so let’s look at a workaround. The solution lies in Buster, a brute force static site generator for Ghost. Buster can be pointed at any Ghost blog—a blog hosted on an external website or one running locally on your own computer—and output a directory with the static content of the site. Before this, create a repo on Github with the name username.github.io (replace username with your Github username) if you don’t have one already. If you already have a
If you have some money to spare, I would recommend that you go in for hosted ghost blogs.
References
[1] http://docs.ghost.org/ [2] https://ledtechnica.com/free-ghost-hosting-on-github-pages/ [3] https://github.com/axitkhurana/buster [4] http://ghost-chops.rhcloud.com/hosting-ghost-on-openshift/
By: Jatin Dhankhar
The author, who is currently doing his B. Tech in computer science from Ramanujan College, University of Delhi, is crazy about computers and loves to learn about anything related to them. He can be reached at jatin@jatindhankhar.in

Admin Insight
Make Your Network Secure with PCAP and Snort
PCAP is an application programming interface (API) for capturing network traffic (packets). Snort is a tool for detecting network intrusion. This article explains how they can be used in tandem to analyse network traffic and detect any attacks on the network.
Packet capture is a classic, frequently performed task carried out by network administrators. This is done to detect any suspicious activity in the network. Any out-of-the-way or abnormal activity is analysed by intrusion detection system (IDS) tools in order to classify the attack or the type of traffic. There are numerous IDS tools available, including open source products, that classify the attacks or traffic based on information gathered from the PCAP (packet capture) files fetched from honey pots or servers.
PCAP (packet capture)
Issues of intrusion in the network by different media can be tackled by making use of PCAP (packet capture), which has an application programming interface (API) for capturing network traffic from ports, IP addresses and associated parameters. In the case of UNIX-like systems, PCAP is implemented in the Libpcap library. In Windows, it is implemented through WinPcap, which is the Windows version of Libpcap.
The base API of PCAP is in the C programming language. To implement PCAP in other programming languages such as Java, .NET and Web-based scripting languages, a wrapper is used, but remember that neither Libpcap nor WinPcap provide these wrappers by default. In the case of C++, the programs can link directly to the C API or make use of an object-oriented wrapper.
The MIME type for the file format that is created and read by Libpcap is application/vnd.tcpdump.pcap. The classical file extension for PCAP is .pcap. In some tools, .cap and .dmp file extensions are also used.
Libpcap and WinPcap are associated, in terms of packet capturing as well as filtering engines, with many open source and commercial network tools. These include protocol analysers (packet sniffers), network investigators, network IDEs, traffic generators and network analysers.
A feature of Libpcap is that the captured files can be exported and saved to a file. A captured file that is saved in the format that Libpcap and WinPcap use can be easily analysed by applications that understand this format, including tcpdump, Wireshark, NetworkMiner and many others.

Tools for reading Libpcap
Here is a list of network analysis tools that make use of Libpcap. Tcpdump: A tool to capture and dump packets for forensics and investigation. ngrep (Network Grep): Shows packet data in a userfriendly output scenario.
Wireshark (earlier called Ethereal): A GUI-based packetcapturing and protocol forensic tool. Snort: An open source network intrusion detection system. Nmap: A port-scanning and fingerprinting network utility. Bro IDS: An IDS and network analysis tool. URL Snooper: Locates the addresses of audio and video files to enable recording them. Iftop: Displays the usage of bandwidth in the network. EtherApe: GUI-based tool for monitoring network traffic and bandwidth usage in real time. Bit-Twist: Ethernet packet generator. Pirni: Network security tool used with jailbroken iOS devices. Firesheep: An extension for the Mozilla Firefox Web browser. It intercepts the unencrypted cookies from different websites. It is also used for session hijacking and network vulnerabilities. Suricata: A network intrusion analysis and prevention platform. WhatPulse: A statistical measurement tool (input, network, uptime, etc) in the network. Xplico: A network forensics analysis tool (NFAT).
Snort
Snort is an open source tool developed by Sourcefire and written in C. It is used as a network intrusion prevention as well as a network intrusion detection system. It is an excellent combination of signature, protocol and anomaly-based inspection. Snort’s user statistics are impressive with millions of downloads and nearly 400,000 registered users. It is not only an IDS but is also used as an IPS (Intrusion Prevention System) to avoid any unwanted activity or unauthorised access to resources. Snort can easily implement protocol analysis and content investigation with a number of other features. The excellent features of the tool include detection of a variety of attacks and probes such as buffer overflows, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts and many others.
The main configuration file is /etc/snort/snort.conf. In this, the actual information about the network or system under investigation is specified. All values and parameters are commented in the file so that the changes can be made very easily.
Other free intrusion detection systems (IDS)
Other free intrusion detection systems are given below: ACARM-ng AIDE Bro NIDS OSSEC HIDS Prelude Hybrid IDS Samhain Suricata
Different modes for Snort network forensics
Snort can be configured in three different modes.
Sniffer mode: Sniffer mode is used to read the packets of the network and display them to the user in a continuous stream on the system.
Packet logger mode: Packet logger mode is used to log the packets to the disk.
Network IDS mode: Network IDS mode is associated with configurable parameters that allow the tool to analyse network traffic by matching it against specific user-defined rules. Finally, it performs several actions based on what the tool investigates at the time of execution.
Sniffer mode
To view only the TCP/IP packet headers to the screen, the following command is used:
./snort -v
This will execute Snort and show the IP and TCP/UDP/ ICMP headers.
To display the application data in transit, the following command is used:
./snort -vd
With this, Snort displays the packet data as well as the headers.
To view a detailed analysis or description, showing the data link layer headers, use the following command:
./snort -vde
This command, with different switches, can also be executed
as:
./snort -d -v –e
Packet logger mode
To record the packets to a disk, we need to specify the directory for logging. Snort will automatically execute the packet logger mode:
./snort -dev -l ./log
Running in this mode, Snort will collect every data packet that it encounters and place it in a directory hierarchy that is based upon the IP address of one of the hosts in the datagram.
If you specify a switch ‘-l’, you will see that Snort uses the address of the remote computer as the directory in which it places packets. In some scenarios, it makes use of the local host address. For the logging of packets relative to the home network, you have to specify this network with the following command:
./snort -dev -l ./log -h 192.168.1.0/24
This command and rule will specify that you want to view the data link and TCP/IP headers as well as application data
into the directory ./log, and log the packets relative to the 192.168.1.0 class C network. All incoming data packets will be recorded in the sub-directories of the main directory log with the names of the directory based on the address of the remote host. If you are working on a high speed network or want to log the packets in a compressed form for later analysis, consider logging in ‘binary mode’.
In the binary mode, the logging of the packets is done in the ‘tcpdump format’ to a single binary file in the logging directory:
./snort -l ./log -b
We should note that we have not specified a home network in the command above because the binary mode logs everything to a single file, in which there is no need to specify how to format the output directory structure.
Network intrusion detection mode
To run the tool in network intrusion detection (NIDS) mode, execute the following command:
./snort -dev -l ./log -h 192.168.1.0/24 -c snort. conf
snort.conf is the name of the file that has different rules. The rules set is applied from the snort.conf file to each packet to finally decide whether or not to take a particular action based upon the rule type in the file. If we do not specify the output directory for the program, it will be /var/log/snort by default.
Reading PCAP using Snort and alert files
PCAP files can be analysed very easily using Snort. The PCAP file is passed with a Snort command. Once the command is executed, Snort generates the alert file from that specific PCAP file.
To read a single PCAP file, use the following commands:
$ snort -r mynetwork.pcap $ snort --pcap-single= mynetwork.pcap
To read multiple PCAPS from a file, use the following:
$ cat mypcaps.txt pcap1.pcap pcap2.pcap $ snort --pcap-file=mypcaps.txt
This command will read pcap1.pcap, pcap2.pcap and all files under /home/mynetwork/pcaps. Snort will not attempt to check whether the files under that directory are really PCAP files or not.
To read PCAPS from a command line list, use the following command:
$ snort --pcap-list=“MyNetwork1.pcap MyNetwork2. pcap MyNetwork3.pcap”
This will read MyNetwork1.pcap, MyNetwork2.pcap and MyNetwork3.pcap.
To read PCAPS under a directory, type:
$ snort --pcap-dir=”/home/MyNetwork/pcaps”
This will include all of the files under /home/MyNetwork/ pcaps.
You can also use filters to read a PCAP file:
$ cat MyNetwork.txt MyNetwork1.pcap MyNetwork2.pcap
Here, the current directory is /home/MyNetwork/pcaps
$ snort --pcap-filter=”*.pcap” --pcapfile=MyNetwork.txt $ snort --pcap-filter=”*.pcap” --pcap-dir=/home/ MyNetwork/pcaps
The above will only include files that match the shell pattern ‘*.pcap’; in other words, any file ending in ‘.pcap’.
$ snort --pcap-filter=”*.pcap --pcapfile=MyNetwork.txt \ > --pcap-filter=”*.cap” --pcap-dir=/home/ MyNetwork/pcaps
In the above, the first filter ‘*.pcap’ will only be applied to PCAP files in the file ‘MyNetwork.txt’ (and any directories that are recursed in that file). The addition of the second filter ‘*.cap’ will cause the first filter to be forgotten and then be applied to the directory /home/MyNetwork/pcaps; so only files ending in ‘.cap’ will be included from that directory.
$ snort --pcap-filter=”*.pcap --pcapfile=MyNetwork.txt \ > --pcap-no-filter --pcap-dir=/home/MyNetwork/ pcaps
In this example, the first filter will be applied to MyNetwork.txt. Subsequently, no filter will be applied to the files found under /home/MyNetwork/pcaps; so all the files found under it will be included.
$ snort --pcap-filter=”*.pcap --pcapfile=MyNetwork.txt \ > --pcap-no-filter --pcap-dir=/home/MyNetwork/ pcaps \ > --pcap-filter=”*.cap” --pcap-dir=/home/

Figure 1: Bookmark the line

Figure 2: Segregating bookmarked lines
MyNetwork/pcaps2
In this example, the first filter will be applied to MyNetwork.txt. Subsequently, no filter will be applied to the files found under /home/MyNetwork/pcaps; so all files found under it will be included. Then, the filter ‘*.cap’ will be applied to files found under /home/MyNetwork/pcaps2.
Printing the PCAPS
$ snort --pcap-dir=/home/MyNetwork/pcaps --pcap-show
The above example will read all the files under /home/ MyNetwork/pcaps and will print a line indicating which PCAP is currently being read.
Snort’s full file format
From the specified alert file given below that is fetched by Snort, we can plot the graphs/charts or any other pattern related to data mining.
[**] [1:2010935:2] ET POLICY Suspicious inbound to MSSQL port 1433 [**] [Classification: Potentially Bad Traffic] [Priority: 2] 07/25-20:31:31.817217 232.11.237.105:1000 -> 233.29.20.24:1433 TCP TTL:102 TOS:0x0 ID:256 IpLen:20 DgmLen:40 ******S* Seq: 0x43EE0000 Ack: 0x0 Win: 0x4000 TcpLen: 20 [Xref => http://doc.emergingthreats.net/2010935]
[**] [1:2010935:2] ET POLICY Suspicious inbound to MSSQL port 1433 [**] [Classification: Potentially Bad Traffic] [Priority: 2] 07/25-20:31:31.838622 17.1.27.05:6000 -> 23.12.20.17:1433 TCP TTL:103 TOS:0x0 ID:256 IpLen:20 DgmLen:40 ******S* Seq: 0x6D5F0000 Ack: 0x0 Win: 0x4000 TcpLen: 20 [Xref => http://doc.emergingthreats.net/2010935]
[**] [1:2010935:2] ET POLICY Suspicious inbound to MSSQL port 1433 [**] [Classification: Potentially Bad Traffic] [Priority: 2] 07/25-20:31:31.898603 17.1.27.5:6000 -> 23.19.20.22:1433 TCP TTL:103 TOS:0x0 ID:256 IpLen:20 DgmLen:40 ******S* Seq: 0x262F0000 Ack: 0x0 Win: 0x4000 TcpLen: 20 [Xref => http://doc.emergingthreats.net/2010935]
Extraction of relevant patterns and data from Alert files using Notepad++
Once the alert file is generated, it can be opened in Notepad++, which has the unique feature of bookmarking specific lines. To separate the lines that have Classification, Priority and IPLen from the Alert file, the Find and bookmark feature can be used.
Once the lines are marked with bookmarks, you can easily cut these selected lines.
Finally, let’s paste these lines to a separate file, and the following file will be generated:
[Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 233 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 233 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 234 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 232 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 234 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 231 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen: 232 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen : 231 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen : 232 [Classification: Potentially Bad Traffic] [Priority: 2] Dgmlen : 230
The extracted alert file can be moved to a spreadsheet package to plot graphs or apply any formula using the following steps: 1. In MS-Word => Use Find-Replace for replacing every paragraph with a tab 2. For this, simply replace SPACE with ^t 3. It will generate the file with fields separated by tabs 4. Copy the full file with the tab to MS-Excel 5. MS-Excel will place all tab fields in different columns 6. Now, you can easily apply any formula
Using this method, you can get the following type of output in the Spreadsheet Package:
Classification Priority IPLen dgmLen
Attempted Administrator Privilege Gain 1 20 231 Potentially Bad Traffic 1 20 231 Attempted Administrator Privilege Gain 1 20 231 Potentially Bad Traffic 2 20 231 Attempted Administrator Privilege Gain 1 20 231 Attempted Administrator Privilege Gain 1 20 231 Potentially Bad Traffic 2 20 231 Attempted Administrator Privilege Gain 1 20 23 Attempted Administrator Privilege Gain 1 20 23 Potentially Bad Traffic 2 20 24
This method can be used to analyse any network traffic captured by APIs like PCAP, enabling detailed investigation of the packets and associated parameters.
By: Dr Gaurav Kumar
The author is associated with various academic and research institutes, where he delivers lectures and conducts technical workshops on the latest technologies and tools. You can contact him at kumargaurav.in@gmail.com











