
International Research Journal of Engineering and Technology (IRJET)
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net
e-ISSN:2395-0056
p-ISSN:2395-0072


International Research Journal of Engineering and Technology (IRJET)
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net
e-ISSN:2395-0056
p-ISSN:2395-0072
Abhishek Kumar Singh
Abstract: With strong machine learning, this examination reinforcescloudsecurity allthemoreparticularly,targets and lessens privilege escalation attacks for a more solid guard system. The gamble of privilege escalation assaults increments alongside the rising acknowledgment of mists. This task works on broad security by tending to shortcomings in worker access privileges inside cloud administrations. Utilizing ML, the venture distinguishes and lessens privilege escalation assault event progressively. Techniques such "LightGBM, Random Forest, Adaboost, and Xgboost" add to a powerful insurance against evolving dangers. Expanded information security experienced by clients and organizations fabricates confidence in cloud computing. The security enhancements of the task assist organizations and cloud with overhauling suppliers to get trust in a safe web-based climate. Moreover added a Voting Classifier that joins expectations from "Support Vector Machine, Random Forest, and Decision Tree" using a "soft" voting strategy to further develop framework execution in spotting and lessening privilege escalation occasions. Moreover, an easy to use Flask framework with SQLite coordination expands client testing through safe sign-in and close down highlights for commonsense application and assessment.
Index Terms –“Privilege escalation, insider attack, machine learning, random forest, adaboost, XGBoost, LightGBM, classification” .
Cloud computing is a clever way to deal with Web access conveyance. Current framework. Distributed storage suppliers use encryption, access control, and verification to get their frameworks and information. The cloud might storeanytypeofinformationinvariouscloudinformation capacity structures basically boundlessly relying upon information openness, speed, and recurrence. Because of the volume of information traded among associations and cloud specialist organizations, both unplanned and purposeful breaks might happen. The very includes that makeinternetprovidersadvantageous forlaborersand IT frameworks make it harder for firms to hinder unapproved access [2]. Cloud administrations open associations to new security chances including validation
and open points of interaction. High level programmers access Cloud frameworks. Machine learning utilizes numerous procedures to further develop information the executives and security. Numerous datasets are private and can't be dispersed because of protection concerns or needsignificantmeasurablehighlights[3],[4].
The quickly developing Cloud market presents protection and security issues directed by regulation. At the point whenCloudOrganizationworkersshiftjobs,theirentrance certifications may not change. Old honors are used awkwardlytotakeandharmsignificantinformation.Every PC talking account has authority. Server data sets, privilegedintel,anddifferentadministrationsarenormally restricted to allowed clients. By assuming control over a higherclientaccountandexpandinghonors,athreatening assailant can get to a delicate framework. Aggressors can advance evenly to control more frameworks or in an upwarddirectiontogetadministratorandrootadmittance to control the whole climate [1]. Even privilege escalation happens when a client acquires the entrance consents of one more client with a similar level. Flat privilege escalation allows an assailant to get to non-individual information. Gravely fabricated Web applications might permitanassailanttogettoothers'information[3],[5].A levelheightofhonorshackallowstheaggressortolookat, change,andduplicatedelicateinformation.
Assailants target information sources since they contain the most touchy and significant data. Each cloud client's protection and security are hurt by missing information. Insider dangers are approved harm. Many firms and associations have inward organizations because of organization extension. As indicated by current evaluations,90%ofassociationsdreadinsiderassaults[7]. Honor rise gives aggressors more ways of going after an objective framework. Privilege escalation is utilized by insider assailants to get sufficiently close to delicate frameworks. Insider attacks are difficult to identify and forestall on the grounds that they work underneath hierarchical security and frequently have advantaged networkaccess.Insiderdangerdetectionandclassification aretestingandtedious[8].

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net
In ongoing examinations, analysts recognized and arranged insider favored rise attacks. To conquer these deterrents, they recommended ML and DL strategies. Late examination used SVM, NB, CNN, LR, PCA, RF, and KNN methods. Because of the range of assaults, quick and compelling ML methods are esteemed. Detection, classification, and mitigation of insider assaults require a viableandproficientmethod.Wewantrefinedcalculations like ML calculations to arrange and gauge insider dangers tofurtherdevelopsecurity[17].
Knowing the presentation of ML calculations on recognizing insider dangers allows you to pick the best calculationforeverycircumstanceanddistinguishregions fordevelopment.Soyoucansupportsecurity. Toimprove and accelerate insider assault results, this examination applies powerful and productive ML calculations. ML calculations "Random Forest, AdaBoost, XGBoost, and LightGBM" were tried. By expanding order calculation forecast, the supporting method prepares an unfortunate classifier to be generally excellent. "Random Forest, AdaBoost, and XGBoost" grouped insider dangers quick andprecisely.
Cloud computing gives PC structure assets on request. Ability to store and deal with data without purchaser the board. It offers public and confidential figuring and information stockpiling on one Web stage. Also, security risks and weaknesses might frustrate distributed computing reception. [5] Cloud computing security concerns, difficulties, techniques, and arrangements are shroudedinthisarticle.Apastsurveyfoundafewsecurity issues. Security issues and arrangements are remembered for another distributed computing engineering model evaluation. All security issues, difficulties, techniques, and answersareinthisarticle.
Cloud computing gives information capacity and handling limit on request without client inclusion. People and gatheringssendandgetinformationutilizingemail.Credit reports, monetary information, and other touchy information are consistently traded on the web. [1] Fraudsters utilize phishing to take client information by seeming, by all accounts, to be dependable. Phishing messages could fool you into giving over delicate data. Email phishing endeavors while sending and getting are thecentralquestion.Atthepointwhenyouopenandread spammessages,theassailantgetsyourinformation.Lately, everybody has battled with it. This article distinguishes new messages, utilizes various qualities and calculations for arrangement, and utilizations different legitimate and
p-ISSN:2395-0072
phishing information amounts. Estimations of current strategies yield a changed dataset. “SVM [8, 10], Naive Bayes(NB),andLSTM”[1,27]wereappliedtoanelement removed CSV and mark record. This examination regards phishedemailacknowledgmentasagroupingissue. “SVM, NB, and LSTM” distinguish email phishing attacks better andall themoreprecisely,asindicated bycorrelationand execution. “SVM, NB, and LSTM classifiers order email attacksmostpreciselyat99.62%,97%,and98%” .
Progresses in science and innovation make cloud computing the following enormous thing. Cloud cryptographyencodesinformation[4].Cloudstorageisnot difficult to get to, has modest hardware, security, and upkeep costs, along these lines each organization utilizes it. Data is encoded to forestall undesirable access. Today, we need to shield our PC and web information from dangers. [4] Cryptography relies upon response time, mystery, transfer speed, and trustworthiness. To protect client information on the cloud, distributed computing security is urgent. We analyze cryptography calculations' proficiency, utilization, and utility in our review report. Assessmentdiscoveriesuncover whichstrategyisbestfor specificinformationandsetting.
With broad innovation use, security challenges have emerged. The general population and confidential areas burn through large chunk of change safeguarding their information against attacks. Insider attacks are more serious than outer assaults on the grounds that approved individuals have legitimate admittance to significant authoritativeresources[36].Manyexaminationhavebeen finished to make techniques and instruments to identify and alleviate insider dangers. This article talks about insider assault counteraction strategies. A solitary order model characterizes insider danger counteraction measures into biometric-based and resource based measurements. [36, 37] Resource measurements are classed as host, organization, and blended, while biometrics are physiological, social, and physical. This order organizes exactly affirmed methods involving grounded hypothesis for careful writing evaluation. The article likewise analyzes and talks about hypothetical and experimental variables that influence insider danger anticipation strategies (e.g., datasets, highlight spaces, characterization calculations, assessment measurements, genuine reproduction, dependability and adaptability). Sending true insider danger anticipation frameworks presentssignificant obstacles.Some explorationholesand potentialexaminationtargetsarelikewiseproposed.
The quick creating Internet of Things [34] utilizes organized processing gadgets and sensors to impart

International Research Journal of Engineering and Technology (IRJET)
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net
information across the organization to tackle issues and offernewtypesofassistance.SavvyhousesdependonIoT. Savvy home innovation offers temperature checking, smokedetection,robotizedlightcontrol,shrewdlocks,and so forth. Nonetheless, it likewise raises extra security and protection concerns, for example, getting to client information through reconnaissance hardware or misleadingalarms.Theseweaknessesrendersavvyhomes helpless against security attacks, accordingly many are reluctant to utilize this innovation. This review article [6] talks about IoT, its development, objects and their details, the layered IoT biological system, and shrewd home security issues for each layer. This article examines IoTbased savvy home security concerns and offers arrangements.
i) Proposed Work:
The proposed framework is a machine learning-based answer for cloud conditions' insider danger detection and classification. Further developing forecast execution with Random Forest, Adaboost, XGBoost, and LightGBM strategies utilizing many ML calculations including "Random Forest, Adaboost, XGBoost [35], and LightGBM" the proposed approach accomplishes upgraded accuracy in recognizing insider dangers. The framework coordinates the abilities of a few calculations utilizing ensemblelearningdrawsnear,thusfurtherdevelopingthe overallpredictionexecutionforinsiderdangerdetectionin cloud settings. To increment model execution, the framework utilizes solid information pretreatment techniques like information collection and normalizing, consequently handling issues such missing qualities, exceptions, and insignificant attributes. Learning rate, greatest profundity, and K-fold are among the boundaries thatare changedto boostthe exhibition oftheML models in this manner ensuring a more proficient and tweaked strategy for insider danger discovery. Moreover consolidated a Voting Classifier, which joins figures from "Decision Tree, Random Forest, and Support Vector Machine" [10] using a "soft" voting procedure, consequently working on the framework's viability in spotting and diminishing privilege escalation occasions. Besides, an easy to understand Flask framework with SQLite joining boosts client testing through safe sign-in and close down highlights for sober minded application andassessment.
Four fundamental stages portray the framework design: data collecting, data preparation, utilization of supervised
e-ISSN:2395-0056
p-ISSN:2395-0072
ML calculations, and results investigation. Tweaked dataset made from numerous CERT dataset documents is utilized in the information gathering stage. The accumulated information then, at that point, goes through preprocessing utilizing techniques including information collection,normalizing,andhighlightextractiontoworkon its quality and pertinence. Applying ML calculations “Random Forest, AdaBoost, XGBoost, and LightGBM” [31, 32] and a voting classifier as an expansion to the preprocessed information for the detection and classification of privilege escalation attacks characterizes the center of the framework. Finally, the framework completelyanalyzestheresults,surveyingtheexhibitionof each and every procedure and offering comprehension of the overall adequacy of the framework in spotting insider dangers.ThroughMLdrawsnear,thisengineeringensures acalculatedareasofstrengthforandtodealwithprivilege escalationassaults.
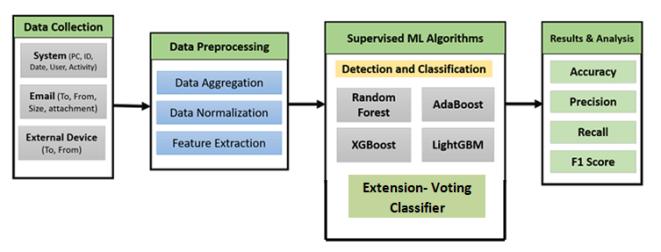
iii) Dataset collection:
Gotten from a few records inside the “CERT dataset” [13, 14], the dataset utilized in this trial centers particularly around email-related information. This painstakingly chosen assortment incorporates a few occasions relevant to email trades that fit insider danger circumstances. It coversafewviewpointsconnectedtoclientconduct,email content,andframeworkcooperations.
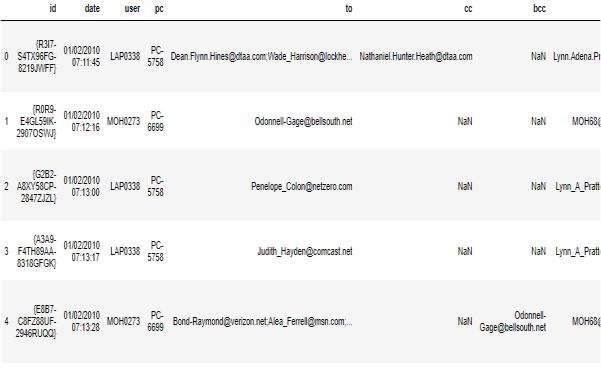
“Fig2CERTdataset”
iv) Data Processing:
Data processing begins with social event appropriate logs and movement information from cloud administrations to

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net p-ISSN:2395-0072
distinguish conceivable privilege escalation targets. This information is cleaned to oblige normalizing for predictable scaling, absent or strange qualities, and encoding of class attributes. Repetitive qualities are disposed of, and worldly information is organized. Client movement successions are arranged for setting; logs are timestamped.Training,approval,andtestingsubsetsofthe datasetgiveadjustedportrayalsothatMLmodelsmightbe preparedeffectively.
v) Feature selection:
Feature selection is to find significant variables driving increment of privilege in detection. Positioned highlights relying upon pertinence utilizing strategies including Recursive Feature Elimination (RFE) and Shared Data Examinesoflogshelptouncoversignificantpatternssuch access recurrence, honor levels, and uncommon action. Needisgiventohighlightsincludingclientjobs,endeavors atassetaccess,andtimesensitiveactiondesigns.PCA and other dimensionality decrease methods ensure low intricacy while protecting essential data for successful modelprojections.
vi) Algorithms:
LightGBM: In view of decision trees, the Train Utilizing AutoMLapparatusutilizesthegradientboostingensemble method known as LightGBM. LightGBM might be applied for both order and relapse, same as other decision treebased methods. LightGBM [31, 32] is tuned for brilliant executionutilizingcirculatedframeworks.
“Fig3LightGBM”
XGBoost: How XGBoost Works - Well-known and viable open-source gradient boosted tree execution accessible from Amazon SageMaker XGBoost Consolidating the evaluations of an assortment of more straightforward, more vulnerable models [35] gradient boosting is a supervisedlearningstrategyfocusingonexactlyforeseeing anobjectivevariable.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
“Fig4XGBoost”
AdaBoost: In ML, AdaBoost otherwise called Versatile Boosting is an Ensemble Strategy approach. With AdaBoost,themostfrequentlyutilizedassessorisdecision treeswithonelevel,inthismannermeaningonlyonesplit. OnefurthernamesforthesetreesareDecisionStumps.
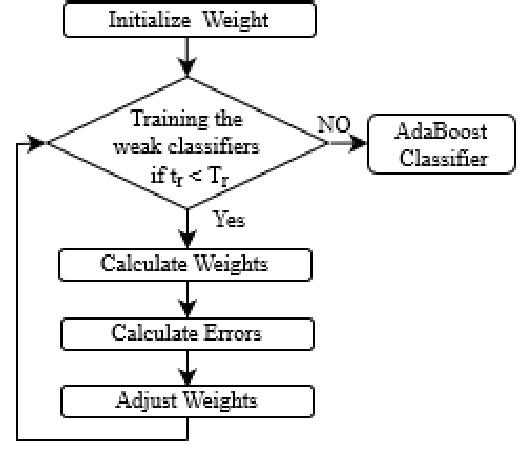
“Fig5Adaboost”
RF: The much utilized ML strategy Random Forest, which totals the result of numerous choice trees to create a solitaryresult.Itsstraightforwardnessandversatilityhave
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net p-ISSN:2395-0072 © 2024, IRJET | Impact Factor value: 8.315 | ISO 9001:2008 Certified Journal | Page387
assisted it with being embraced since it oversees both classificationandregressionissues[34].
“Fig6Randomforest”
VC: A voting classifier is an ML model prepared on an ensemble of a few models and figures a result (class) contingent upon their most prominent probability of chosenclass.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net p-ISSN:2395-0072
“Fig7Votingclassifier”
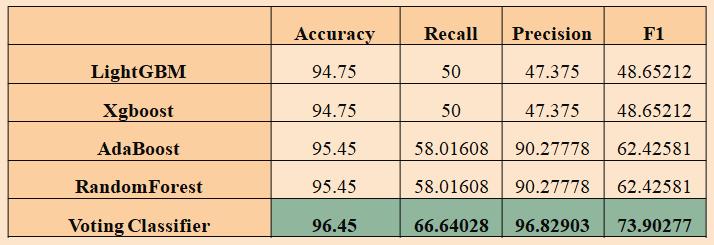
“Fig8Performanceevaluation”
This is subsequently the presentation estimates table. Furthermore, here we can track down the names of the calculationsalongwiththeiraccuracy,precision,recall,f1score, and particularity values got by them. In all the presentation measures, the augmentation voting classifier hassosurpassedanyremainingmodels.
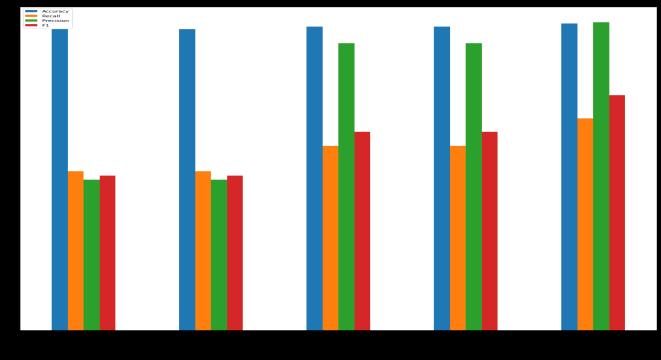
“Fig9Comparisongraph”
This is consequently the diagram of execution estimates examination.
Here, then, x pivot shows calculation names and y hub showsexecutionmeasures.
Blue color bar here shows accuracy; orange marks recall; greenmarksprecision;redisforf1score.
Precision: Underscoring the model's ability to forestall misleadingup-sides,precisionistheproportionofgenuine encouraging points to the all out of evident up-sides and wrongup-sides.
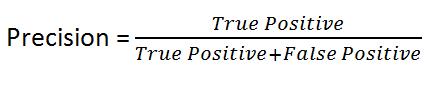
Recall: Recall checks the model's ability to track down all relevant occasions by figuring the genuine positive to misleadingnegativeproportion.
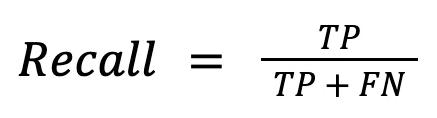
Accuracy: Accuracy assesses, among every one of the expectations,thelevelofpreciseestimates thatis,valid up-sides and genuine negatives giving an overall assessmentofthemodel'sexhibition.
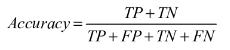
F1 Score: Particularlysupportivewhilemanagingunequal information, F1 score is the symphonious mean of accuracyandrecall,subsequentlyadjustingthetwo.

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net p-ISSN:2395-0072

Fig11SignupPage”


Since the unfriendly insider has more access and opportunities to cause significant harm, they comprise a seriousperiltotheorganization.Insidershaveadvantaged and suitable admittance to information and devices not at all like pariahs. This work introduced ML strategies to distinguish and sort an insider attack. [14] This approach utilizes a custom fitted dataset got from numerous CERT dataset documents. Improved results came from four ML procedures applied to that dataset. Among these are Random Forest, AdaBoost, XGBoost, and LightGBM. This work showed the effective exploratory outcomes with more noteworthy accuracy in the classification report utilizing these supervised machine learning strategies. With97%,theLightGBMcalculationhasthebestaccuracy among the recommended techniques; RF with 86%, AdaBoost with 88%, and XGBoost with 88.27% [31, 32] haveotheraccuracynumbers.Extendingthedatasetinsize and assortment as far as its credits and the new propensitiesofinsideraggressorstoexecutetheattackcan assist the recommended models with working on their exhibitionlateron.Thiscouldpromptnewreviewdesigns targeting recognizing and ordering insider attacks associated with various circles of business. Organizations use AI models to pursue decent business choices; better model discoveries convert into better decisions. Despite the fact that errors could have very significant costs, raising model exactness assists with bringing down this cost. Clients of ML-based examination can offer PC calculations with tremendous volumes of information, which they then, at that point, evaluate, recommend, and pursuechoicesupon.
Future upgrades ought to streamline the framework's adaptability to oversee more prominent jobs in enormous cloud establishments and guarantee smooth handling as information intricacy and volume extend. Dynamic response components that can rapidly recognize and go against new privilege escalation procedures ought to be

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net p-ISSN:2395-0072
executed in later headways to safeguard against creating insiderdangers.Incorporatingtechniquesthatmakesense ofmodelchoicesisvital.Thistransparencyassistssecurity examiners with understanding danger ID factors, supporting framework certainty [29, 30]. Making a framework for refreshing and broadening the model preparation dataset is fundamental. Persistent enhancement helps the framework recognize and relieve newattacksandinsiderdangerpatterns.
[1] U. A. Butt, R. Amin, H. Aldabbas, S. Mohan, B. Alouffi, and A. Ahmadian, ‘‘Cloud-based email phishing attack using machine and deep learning algorithm,’’ Complex Intell.Syst.,pp.1–28,Jun.2022.
[2] D. C. Le and A. N. Zincir-Heywood, ‘‘Machine learning based insider threat modelling and detection,’’ in Proc. IFIP/IEEE Symp. Integr. Netw. Service Manag. (IM), Apr. 2019,pp.1–6.
[3]P.Oberoi,‘‘Surveyofvarioussecurityattacksinclouds based environments,’’ Int. J. Adv. Res. Comput. Sci., vol. 8, no.9,pp.405–410,Sep.2017.
[4] A. Ajmal, S. Ibrar, and R. Amin, ‘‘Cloud computing platform: Performance analysis of prominent cryptographic algorithms,’’ Concurrency Comput., Pract. Exper.,vol.34,no.15,p.e6938,Jul.2022.
[5] U. A. Butt, R. Amin, M. Mehmood, H. Aldabbas, M. T. Alharbi, and N. Albaqami, ‘‘Cloud security threats and solutions:Asurvey,’’WirelessPers.Commun.,vol.128,no. 1,pp.387–413,Jan.2023.
[6] H. Touqeer, S. Zaman, R. Amin, M. Hussain, F. AlTurjman, and M. Bilal, ‘‘Smart home security: Challenges, issues and solutions at different IoT layers,’’ J. Supercomput.,vol.77,no.12,pp.14053–14089,Dec.2021.
[7] S. Zou, H. Sun, G. Xu, and R. Quan, ‘‘Ensemble strategy for insider threat detection from user activity logs,’’ Comput., Mater. Continua, vol. 65, no. 2, pp. 1321–1334, 2020.
[8]G.Apruzzese,M.Colajanni,L.Ferretti,A.Guido,and M. Marchetti, ‘‘On the effectiveness of machine and deep learning for cyber security,’’ in Proc. 10th Int. Conf. Cyber Conflict(CyCon),May2018,pp.371–390.
[9] D. C. Le, N. Zincir-Heywood, and M. I. Heywood, ‘‘Analyzing data granularity levels for insider threat
detection using machine learning,’’ IEEE Trans. Netw. ServiceManag.,vol.17,no.1,pp.30–44,Mar.2020.
[10] F. Janjua, A. Masood, H. Abbas, and I. Rashid, ‘‘Handling insider threat through supervised machine learning techniques,’’ Proc. Comput. Sci., vol. 177, pp. 64–71,Jan.2020.
[11]R.Kumar,K.Sethi,N.Prajapati,R.R.Rout,andP.Bera, ‘‘Machine learning based malware detection in cloud environmentusingclusteringapproach,’’in Proc.11thInt. Conf. Comput., Commun. Netw. Technol. (ICCCNT), Jul. 2020,pp.1–7.
[12] D. Tripathy, R. Gohil, and T. Halabi, ‘‘Detecting SQL injectionattacksincloudSaaSusingmachinelearning,’’ in Proc. IEEE 6th Int. Conf. Big Data Secur. Cloud (BigDataSecurity),Int.Conf. HighPerform.SmartComput., (HPSC),IEEEInt. Conf.Intell.Data Secur.(IDS),May2020, pp.145–150.
[13] X. Sun, Y. Wang, and Z. Shi, ‘‘Insider threat detection using an unsupervised learning method: COPOD,’’ in Proc. Int. Conf. Commun., Inf. Syst. Comput. Eng. (CISCE), May 2021,pp.749–754.
[14] J. Kim, M. Park, H. Kim, S. Cho, and P. Kang, ‘‘Insider threat detection based on user behavior modeling and anomaly detection algorithms,’’ Appl. Sci., vol. 9, no. 19, p. 4018,Sep.2019.
[15] L. Liu, O. de Vel, Q.-L. Han, J. Zhang, and Y. Xiang, ‘‘Detectingandpreventingcyberinsiderthreats:Asurvey,’’ IEEECommun.SurveysTuts.,vol.20,no.2,pp.1397–1417, 2ndQuart.,2018.
[16] P. Chattopadhyay, L. Wang, and Y.-P. Tan, ‘‘Scenariobased insider threat detection from cyber activities,’’ IEEE Trans. Computat. Social Syst., vol. 5, no. 3, pp. 660–675, Sep.2018.
[17] G. Ravikumar and M. Govindarasu, ‘‘Anomaly detection and mitigation for wide-area damping control using machine learning,’’ IEEE Trans. Smart Grid, early access,May18,2020,doi:10.1109/TSG.2020.2995313.
[18] M. I. Tariq, N. A. Memon, S. Ahmed, S. Tayyaba, M. T. Mushtaq,N.A.Mian,M.Imran,andM.W.Ashraf,‘‘Areview of deep learning security and privacy defensive techniques,’’ Mobile Inf. Syst., vol. 2020, pp. 1–18, Apr. 2020.
2024, IRJET | Impact Factor value: 8.315 | ISO 9001:2008

International Research Journal of Engineering and Technology (IRJET) e-ISSN:2395-0056
Volume: 11 Issue: 11 | Nov 2024 www.irjet.net p-ISSN:2395-0072
[19] D. S. Berman, A. L. Buczak, J. S. Chavis, and C. L. Corbett, ‘‘A survey of deep learning methods for cyber security,’’Information,vol.10,no.4,p.122,2019.
[20]N.T.VanandT.N.Thinh,‘‘Ananomaly-basednetwork intrusion detection system using deep learning,’’ in Proc. Int.Conf.Syst.Sci.Eng.(ICSSE),2017,pp.210–214.
[21] G. Pang, C. Shen, L. Cao, and A. V. D. Hengel, ‘‘Deep learning for anomaly detection: A review,’’ ACM Comput. Surv.,vol.54,no.2,pp.1–38,Mar.2021.
[22] R. A. Alsowail and T. Al-Shehari, ‘‘Techniques and countermeasures for preventing insider threats,’’ PeerJ Comput.Sci.,vol.8,p.e938,Apr.2022
[23]L.Coppolino,S. D’Antonio,G.Mazzeo,andL.Romano, ‘‘Cloud security: Emerging threats and current solutions,’’ Comput.Electr.Eng.,vol.59,pp.126–140,Apr.2017.
[24] M. Abdelsalam, R. Krishnan, Y. Huang, and R. Sandhu, ‘‘Malware detection in cloud infrastructures using convolutional neural networks,’’ in Proc. IEEE 11th Int. Conf.CloudComput.(CLOUD),Jul.2018,pp.162–169.
[25] F. Jaafar, G. Nicolescu, and C. Richard, ‘‘A systematic approach for privilege escalation prevention,’’ in Proc. IEEEInt.Conf.Softw.Quality,Rel.Secur.Companion(QRSC),Aug.2016,pp.101–108.
[26] N. Alhebaishi, L. Wang, S. Jajodia, and A. Singhal, ‘‘Modeling and mitigating the insider threat of remote administrators in clouds,’’ in Proc. IFIP Annu. Conf. Data Appl.Secur.Privacy.Bergamo,Italy:Springer,2018,pp.3–20.
[27] F. Yuan, Y. Cao, Y. Shang, Y. Liu, J. Tan, and B. Fang, ‘‘Insider threat detection with deep neural network,’’ in Proc. Int. Conf. Comput. Sci. Wuxi, China: Springer, 2018, pp.43–54.
[28] I. A. Mohammed, ‘‘Cloud identity and access management A model proposal,’’ Int. J. Innov. Eng. Res. Technol.,vol.6,no.10,pp.1–8,2019.
[29]F.M.Okikiola,A.M.Mustapha,A.F.Akinsola,andM.A. Sokunbi,‘‘Anewframeworkfordetectinginsiderattacksin cloud-basede-healthcaresystem,’’inProc.Int.Conf.Math., Comput.Eng.Comput.Sci.(ICMCECS),Mar.2020,pp.1–6.
[30] G. Li, S. X. Wu, S. Zhang, and Q. Li, ‘‘Neural networksaided insider attack detection for the average consensus algorithm,’’IEEEAccess,vol.8,pp.51871–51883,2020.
[31] A. R. Wani, Q. P. Rana, U. Saxena, and N. Pandey, ‘‘Analysis and detection of DDoS attacks on cloud computing environment using machine learning techniques,’’ in Proc. Amity Int. Conf. Artif. Intell. (AICAI), Feb.2019,pp.870–875.
[32] N. M. Sheykhkanloo and A. Hall, ‘‘Insider threat detection using supervised machine learning algorithms onanextremelyimbalanceddataset,’’Int.J.CyberWarfare Terrorism,vol.10,no.2,pp.1–26,Apr.2020.
[33] M. Idhammad, K. Afdel, and M. Belouch, ‘‘Distributed intrusion detection system for cloud environments based on data mining techniques,’’ Proc. Comput. Sci., vol. 127, pp.35–41,Jan.2018.
[34] P. Kaur, R. Kumar, and M. Kumar, ‘‘A healthcare monitoring system using random forest and Internet of Things (IoT),’’ Multimedia Tools Appl., vol. 78, no. 14, pp. 19905–19916,2019.
[35] J. L. Leevy, J. Hancock, R. Zuech, and T. M. Khoshgoftaar, ‘‘Detecting cybersecurity attacks using different network features with LightGBM and XGBoost learners,’’ in Proc. IEEE 2nd Int. Conf. Cognit. Mach. Intell. (CogMI),Oct.2020,pp.190–197.
[36] R. A. Alsowail and T. Al-Shehari, ‘‘Techniques and countermeasures for preventing insider threats,’’ PeerJ Comput.Sci.,vol.8,p.e938,Apr.2022.
[37] B. Alouffi, M. Hasnain, A. Alharbi, W. Alosaimi, H. Alyami, and M. Ayaz, ‘‘A systematic literature review on cloud computing security: Threats and mitigation strategies,’’IEEEAccess,vol.9,pp.57792–57807,2021.
2024, IRJET | Impact Factor value: 8.315 | ISO 9001:2008