
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
Vijay Santosh Tawar1, Dr. Nafees Ahmed M. Kazi2
1 Assistant Professor, Electronics & Telecommunication Engineering, SSVPS’ B. S. Deore COE, Dhule, MS, India
2 Associate Professor, Electronics & Telecommunication Engineering, SSBT’ COET, Bambhori, Jalgaon, MS, India
Giventhefastpaceofthedevelopmentofwirelesscommunicationtechnologiesandcorrespondingdemandsforsecuredata transmissionduetothesensitivityofinformationbeingtransmitted,FPGAshavegarneredmuchinterestasagatewayfor implementingencryptiontechniquesbecauseoftheirflexibilityandhigh-speedprocessingwithenergyefficiencycomparedto otherconventionalhardwaretechnologies.Inthisregard,thepaperwouldliketopresentacomprehensivereviewofthelatest FPGAimplementationsofvariousdataencryptiontechniquesusedinwirelesscommunicationsystems[4,5].Inthisdiscussion, varioustraditionalencryptionalgorithms,namelyAES,RSA,andDES,alongwiththeirFPGAimplementationswillbeexplored. Later,recenttrendsofellipticcurvecryptography,quantum-resistantcryptosystem,andrelatedperformancemetricslike throughput,latency,resourceutilization,andpowerefficiencyfortheseimplementationswillalsobediscussed,givinginsights intotheirapplicabilityinreal-timewirelesscommunicationsystems.
Keywords: FPGA, data encryption, wireless communication, AES, RSA, DES, elliptic curve cryptography, quantum cryptography
Theproliferationofwirelesscommunicationsystemsinvariousdomains,suchascellularnetworksmilitaryapplicationsand IoT,hasonlyraisedconcernsoverthesecurityofthetransmitteddata[1].
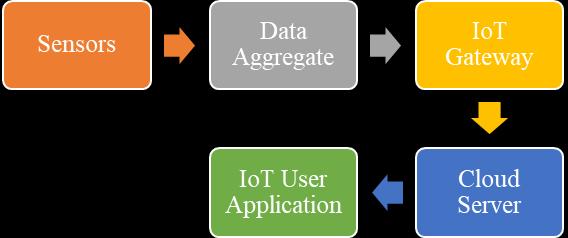
Theneedforsecureandefficientencryptiontechniqueshasneverbeenmorecritical,especiallyasthewirelesscommunication systemcontinuestoexpandintosensitivefieldslikefinanceandhealthcare,defense,etc.[2]Figure1showsgeneralpurpose illustrationofflowinnormalIoTsystem.
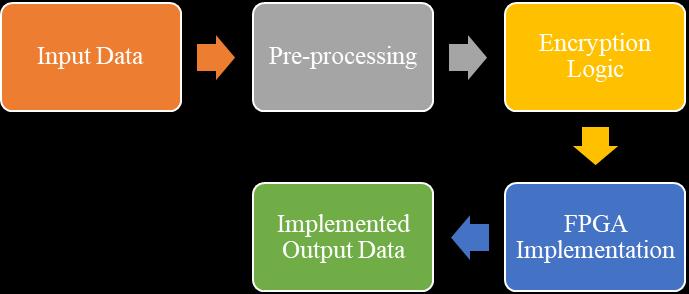
FPGAswillprovideaconcreteplatforminthedesignofcryptographytechniquesduetotheirintrinsiccapabilityinparallel processing, re-configurability, and high performance. On the contrary, conventional microprocessors and the supported conventional software-based encryption schemes are flexible but not capable to present solutions to modern wireless communicationsystemswiththeirhighdemandingreal-timeprocessingrequirements[2].FPGAscanbereprogrammedfor intendedapplications,henceensuringthattheyoutperforminspeed,powerconsumption,andbetteruseofresources[1].In figure2implementationofFPGAsystemwithblocklevelworkingisindicated.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
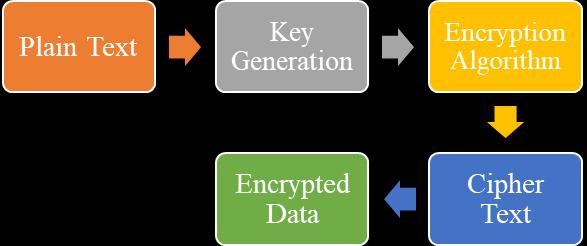
TheaimofthisworkistoreviewrecentFPGAimplementationsofdataencryptiontechniquesinwirelesscommunication.The paperwillstudytraditionalalgorithmslikeAES,RSA,andDES,alongwithnewertechniquesofencryptionlikeellipticcurve cryptographyandquantum-resistantcryptography.ThechallengesandfuturetrendsinimplementingencryptionusingFPGA inthefieldofwirelesscommunicationsystemsarealsoproposedinthiswork.Infigure3,theflowofencryptionalgorithmfor generalpurposesystemisshown.
2.1 Overview of FPGA Technology
FPGAsaresemiconductordeviceswhoseconfigurationsbytheusercanbedonepost-manufacturingforimplementingawide rangeoffunctions.AnimmediateandoverwhelmingadvantageofthisabilitytoprogramFPGAsforcertaintasksisoverthe ASICsandanyformofsoftwareprocessing.
XilinxandIntel-seven,formerlyAltera-dominantfamiliesofFPGAsarewidelyusedfortherealizationofvariousencryption algorithms. Logic blocks, interconnections, and memory elements form programmable FPGA devices that are capable of carryingoutmostcryptographicfunctionsinparallelwithhighthroughput/lowlatency[10].
2.2 Why FPGA for Encryption?
SomeoftheadvantagesofimplementingFPGAsforvariousencryptiontechniquesincludethefollowing:
Parallel Processing: FPGAs can process different cryptographic operations simultaneously, making them better suitedforhigh-speedencryption.
Flexibility: FPGAscanbereprogrammedincaseoftheintroductionofnewencryptionalgorithmsorupdatesthat mightbecarriedoutinawirelesscommunicationsystemwhentheprotocolschange[15].
Energy Efficiency: FPGAsfeaturelowpowerusecomparedtogeneral-purposeprocessors,hencetheywouldbevery suitableformobileandIoTapplications[1].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
3.1.1 Advanced Encryption Standard (AES)
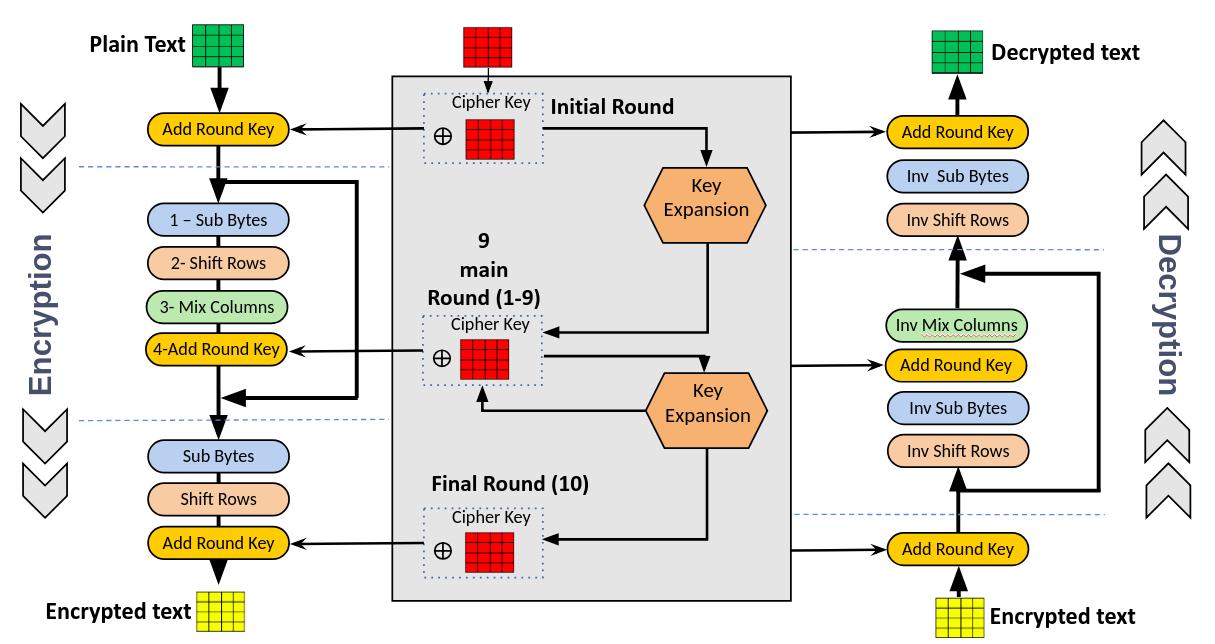
One of the most deployed encryption standards for secure communication is AES. The FPGA implementation has shown prominentimprovementinspeedandefficiencycomparedtoasoftware-basedsolution.InherentparallelismofAESrounds allowsexecutionofroundssimultaneouslyonFPGAs,henceenhancingthethroughputtoagreatextent.Generalizedflow diagram for AES algorithm is as shown in figure 4. Several architectures concerning AES encryption on FPGA have been proposedbyvariousresearchers.Mostofthemworktowardsthereductionofthenumberoflogicelementsusedand,atthe sametime,reducepowerconsumption[7].Forexample,afullypipelinedAESimplementationiscapableofproducingseveral Gbpsthroughputwithveryminimallatency[5].
3.1.2 Data Encryption Standard (DES) and Triple DES (3DES)
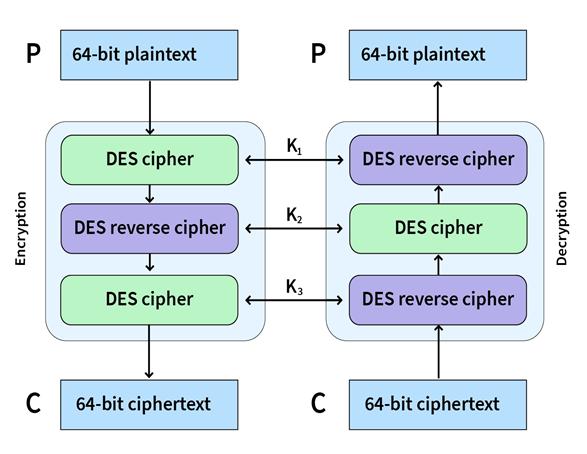
DES,thoughreplacedbyAESinmostapplications,stillfindsitsusageinsomelegacysystems[1,7].Themainconcentrationin theFPGA-basedimplementationsofDEShasbeentowardenhancingtheperformanceoftheencryptionprocess.3DES,which appliestheDESencryptionthreetimes,ismoreresource-intensiveandhencemuchbenefitsfromtheparallelismofFPGA.In figure5shownbelowusingDESalgorithm64bitplaintextcanbeconvertedin64bitciphertextusingroundkeygeneration andencryptionmethodwhereasdecryptionprocessisexactlyoppositetoencryptioni.e.itworksinreverseorder.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
3.1.3 RSA Encryption
RSAisapublic-keyencryptionalgorithmbasedonthecomputationalintoleranceoffactorizinglargeprimenumbers.Previous FPGAimplementationsofRSAareallbasedonefficientmoduloexponentiation,asthisphaseisusuallyregardedasthemost computation-intensive part of the whole RSA algorithm [12]. Using methods like Montgomery multiplication, an RSA implementationbasedonFPGAcanbehighlyacceleratedcomparedwithatraditionalmicroprocessor-basedimplementation.
3.2 Recent Trends in Encryption
3.2.1 Elliptic Curve Cryptography (ECC)
SomewouldconsiderECCmoresecurethanRSA,sinceRSAbases itskeystrengthonfactoringlargenumbers,whichisa problemcomputershavebeenabletosolve.Ontheotherhand,theproblemsthatellipticcurvecryptographyuses-namelythe discretelogarithmproblem-aremuchhardertosolve[14].ECCisanalternativepublic-keyencryptiontechniquethatfinds favorbecausekeylengthsaresomewhatshortercomparedtothoseofRSAforsimilarlevelsofsecuritybutfarmoremoderate intheircomputationalresourcerequirements.Infact,FPGAimplementationsofECCalsoshowprettysuperiorperformancein constrainedresourceplatformssuchasmobilesandIoTdevices.Mostrecently,severalworkshaveconcentratedonimproving theperformanceofthepointmultiplicationoperationlyingattheheartofECConFPGAplatforms.
3.2.2 Quantum-Resistant Cryptosystems
Whilequantumcomputingreplacestraditionalencryptionmethods,vulnerabilitiesinattacksarealsogrowing.Lattice-based cryptographyandhash-basedcryptographyhaveabigpotentialfordevelopingnovelmethodsofquantumresistance[13,15].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
FPGAs are a flexible platform for implementing such new cryptographic algorithms, which enables real-time testing and performanceevaluationinawirelesscommunicationenvironment[11].
Table-1belowsummarizesafewpointsofdifferencebetweensomecommonlyusedencryptionmethodsonFPGAsappliedfor differentwirelesscommunicationsystems.Eachencryptiontechniqueisassessedbasedonperformance,powerefficiencyon FPGA,anditstypicalapplications[1,7].
Table 1 Comparative highlights of Encryption Methods used for FPGA Implementation
Encryption Method Key Features FPGA Implementation
AES (Advanced Encryption Standard)
DES (Data Encryption Standard)
RSA (Rivest-ShamirAdleman)
ECC (Elliptic Curve Cryptography)
QuantumResistant Cryptography
High security, 128/192/25 6-bitkeys
Fully pipelined architectures
Performance (Throughput/La tency)
High throughput (several Gbps) withlowlatency
Outdated, 56-bit key, vulnerable Requires additional layers(TripleDES)
Public-key, key lengths of 10244096bits
Optimized through modular exponentiation on FPGA
Shorter keys, same security as RSA Efficient implementation with reduced FPGA resourceusage
Resistant to quantum computing attacks FPGAs provide flexible testing for newalgorithms
Lower throughput comparedtoAES
High latency due to complex key processing
Higher performance in constrained devices
Power Efficiency Applications
Moderate, depending on pipelining
Secure wireless communications, IoT,5G
Higher power consumption Legacy systems, still in use for specificindustries
Moderate efficiency
High power efficiency due to shortkeys
Varies by algorithm, ongoingresearch Varies, still in development
4.1 Real-Time Encryption in 4G/5G Networks
Secure key exchange, VPNs, DigitalSignatures
Mobile devices, IoT, low-power applications
Future wireless communication systems, postquantumsecurity
ThesearealsotheencryptiontechniquescarriedoutbyFPGAs,widelyadoptedinmodern4Gand5Gwirelesscommunication networks[3].Allthesewirelesscommunicationnetworksrequiresecuredatatransmissionamongdifferentnodes.Inthis regard, FPGA-based AES and ECC techniques showed paramount performances. These platforms can execute different encryptionanddecryptionprocessesbyexploitingparallelismandre-configurabilitywithlowlatencyforachievingsecureand real-timecommunications[6].
4.2
NewchallengesfordatasecurityhavebeenposedbytherapidemergenceofIoTdevices.Ingeneral,suchdevicespossessvery limitedprocessingpowerandsuppliesofenergy,soFPGA-basedencryptionseemstobetherightanswer[3].SeveralIoT deviceshaveintroducedPRESENTandSPECKasFPGAimplementationsoflight-weightcryptographicalgorithmscapableof offeringatrade-offbetweensecurityandenergyefficiency[6,9].

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
Whiletheadvantagesarenotlimitedtotheaforementioned,therearestillseveralchallengesinFPGA-basedencryption.These includebutarenotlimitedto:
Power Consumption: Although FPGAs are efficient and consume less power compared to general-purpose processors,thepowerconsumptioninbattery-powereddevices,suchasmobilephonesandIoTdevices,isoneofthe topconcerns.
Resource Utilization: Allheavycryptographicalgorithms,forinstance,RSAandECC,requireheavyresourcesonan FPGA,whichmaybeprohibitedinresource-constrainedenvironments[3,9].
Futureresearchislikelytoconcentrateon:
Integration with AI and Machine Learning: FPGA-basedencryptioncouldalsobecombinedwithAIalgorithmsin developingadaptivesecuritysystemsthatcanresponddynamicallytonewemergingthreats[2,3,4,6,8].
Post-Quantum Cryptography: Oncequantumcomputersbecomereality,attentionwillbeturnedtoimplementing quantum-resistantcryptographicalgorithmsonFPGAs.
6. CONCLUSION
This work has identified the key role of FPGAs in implementing wireless communication data encryption techniques. Its flexibility,speed,andenergyefficiencycurrentlymakeFPGAahotchoiceforvariousreal-worldapplicationsinthefieldsof5G, IoT,andsecuremilitarycommunication. To this end, even asnew methods of encryption are beginningto be developed, includingthedevelopmentofquantum-resistantalgorithms,FPGAswillstillbeconsideredacentralplayerinensuringsecure communicationinanincreasinglyconnectedworld.
REFERENCES:
[1] NRShetty,NHPrasad,HCNagaraj,“AdvancesinCommunicationandApplications,” Proceedings of ERCICA,2023.
[2] SMoradian,SGharbia,AIOlbert,“Enhancingtheaccuracyofwindpowerprojectionsunderclimatechangeusing geospatialmachinelearningmodels,” Energy Reports,2024-Elsevier.
[3] SBAkinpelu,SAAbolade,EOkafor,“Interpretablemachinelearningmethodstopredictthemechanicalpropertiesof ABX3perovskites,” Results in Physics,2024-Elsevier.
[4] JFinkelstein,AGabriel,SSchmer,“IdentifyingFacilitatorsandBarrierstoImplementationofAI-AssistedClinical DecisionSupportinanElectronicHealthRecordSystem,” Journal of Medical Systems,2024-Springer.
[5] A Chierici, F Lareyre, “Vascular liver segmentation: a narrative review on methods and new insights brought by artificialintelligence,” Journal of Medical Case Reports,2024.
[6] SShahpouri,DGordon,“TransientNOxemissionmodelingofahydrogen-dieselengineusinghybridmachinelearning methods,” International Journal of Engine Research,2024.
[7] J Yang, J Yu, D Tang, “An interpretable precursor-driven hierarchical model for predictive aircraft safety,” Expert Systems with Applications,2024-Elsevier.
[8] DFreedman,BBagga,“QualityassessmentofexpeditedAIgeneratedreformattedimagesforEDacquiredCTabdomen andpelvisimaging,” Abdominal Radiology,2024.
[9] MKattih,MBressler,“ArtificialIntelligence-PromptedExplanationsofCommonPrimaryCareDiagnoses,” PRiMER, 2024.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 09 | Sep 2024 www.irjet.net p-ISSN: 2395-0072
[10] A Sarajlić, I Plaščak, “The use of acoustic technology for monitoring biodiversity in the Kopački Rit Nature park (projectWatchOut),” Proceedings of Croatian Conference on Plant Protection,2024-Croris.
[11] R Saed, “The impact of artificial intelligence on the jurisprudential research industry between prohibition and permissibility,” Annals of the Faculty of Arts, Ain Shams University,2024.
[12] JFRamírez-Vasquez,EJCarlock-Acevedo,“Inversekinematicsusingneuralnetworksandrandomforestsfortrajectory trackingofathree-degree-of-freedomroboticarm,” BUAP Institutional Repository,2024.
[13] KAEinarson,“Molecularrepresentationsincomputationaldrugdesign-fromearlystageproteinfunctionstomachine learningbasedpredictionofpharmacokineticparameters,” Technical University of Denmark,2024.
[14] JMirabetHerranz,“ApplicationofmachinelearningtechniquestodetectmalwareonAndroiddevices,” Universitat Politècnica de València,2024.
[15] SMinoo,FGhasemi,“AutomatedTeethDiseaseClassificationusingDeepLearningModels,” International Journal of Applied Data Science,2024.
BIOGRAPHIES


Mr. Vijay Santosh Tawar has experience of 13 Years in Teaching, currently working as Assistant Professor Approved by KBCNMU, Jalgaon and DBATU, Lonere, in Department of Electronics & Telecommunication EngineeringinSSVPS’BapusahebShivajiraoDeoreCollege ofEngineering,Dhule(MS).HeperceivedM.Tech.inDigital Communication in 2015. His domain of research is VLSI Design,DateEncryption&DecryptionandCommunication.
Dr.NafeesAhmedM.Kazihasvastexperienceof25Years inTeaching,currentlyworkingasAssociateProfessor,in Department of Electronics & Telecommunication Engineering in SSBT’ SSBTs College of Engineering and TechnologyBambhoriJalgaon(MS).HeperceivedPhDin ElectronicsEngineeringfromKBCNMU,Jalgaonin2022.His domainofresearchisSoftwareDefinedNetwork,Computer Networking, Satellite Communication, CMOS Design, AutomotiveElectronicsandElectricVehicle