
International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072


International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
Ayush Wardhan sahu1 , Prof. Satendra Sonare2
1Reseacrh Scholar, Department of CSE, Gyan Ganga Institute of Technology and sciences, Jabalpur, M.P.
2Professor, Departmet of CSE, Gyan Ganga Institute of Technology and Sciences, Jabalpur, M.P.
***
Abstract – Android'spopularitymakesitalucrativetarget forcybercriminals.Malwarewithdifferentbehaviorpatterns thatspecificallytargetuserroutinesisconstantlyentering the market. For this reason, knowing how to identify different forms of malware is essential to anti-malware protection.Androidmalwarehasbecomeaseriousthreatto our daily lives, so it is urgently necessary to effectively mitigate or defend against it. Recently, many Android malwareanalysisapproachesandtoolshavebeenproposed toprotectlegitimateusersfromthethreat.However,most approaches focus on malware detection, while only a few considermalwareclassificationormalwarecharacterization. This paper proposes the use of ECLAT-based machine learning and deep learning methods to classify malware familiesandcategoriesbasedonmanydifferentdatasetsin ordertoevaluateandselectappropriatemethodsforeach dataset.
Keywords: Android malware, Malware Features, Deep Learning,ECLAT,SequentialNeuralNetwork,Accuracy.
Toprotectcomputersystems,weneedtodetectmalwareas soonasitinfectssystems.Malwaredetectionistheprocess of analyzing a suspicious file and identifying whether it is malwareorbenign.Malwareclassificationisastepfurther. Afterafileisidentifiedasmalware,byenteringacategoryor group of malware known as a malware classification. Malwaredetectionrequires3-stepoperations:
1. Malware files are analyzed using appropriate tools. 2. Staticanddynamicelementsareextractedfromtheanalyzed files.
3. Functions are grouped in certain ways to separate malicioussoftwarefrombenignsoftware.Varioussciences andtechniquesincludingdatascience,machinelearning,and heuristics,aswellastechnologiessuchascloudcomputing, big data, and blockchain, are used in these processes to increasedetectionrates.Therearedifferentapproachesto detect malware using the above techniques and technologies. These approaches are mainly signature, behavior, model checking and heuristic detection [1], [2]. The names of these approaches vary according to the techniques and technologies used. The signature-based approachiseffectiveforknownandsimilarversionsofthe
same malware. However, it failed to detect previously unseenmalware.Althoughdetectionapproachesbasedon behavior, heuristics, and model checking are effective in detecting some parts of unknown malware, they cannot showthesameperformanceindetectingcomplexmalware variantsthatuseobfuscationandpackagingtechniques. A deep learning approach is starting to be used as a new paradigmtoovercometheshortcomingsofexistingmalware detectionandclassificationapproaches.Deeplearninghas been widely used in various fields including image processing,computervision,humanactivityrecognition[3], drivingsafety[4],facialemotionrecognition[5],andnatural languageprocessing.However,itislittleusedinthefieldof cyber security, especially in malware detection. Deep learningisasubsetofartificialintelligencethatoperateson artificial neural networks (ANNs). Deep learning uses multiplehiddenlayersandlearnsfromexamples.Recently, several deep learning architectures such as deep neural networks(DNNs),deepbeliefnetworks(DBNs),recurrent neuralnetworks(RNNs),andconvolutionalneuralnetworks (CNNs) have been used to improve model performance. Deeplearningbringsmanyadvantagesoverthetraditional learningscheme:
1. The DL model can automatically generate high-level elementsfromexistingelements.
2.DLreducestheneedforfeatureengineering.
3.DLcanhandleunstructureddataefficiently.
4.DLcanhandleverylargedatasets.
5.DLreducestheelementspace.
6.DLcaneffectivelyperformunsupervised,semi-supervised andsupervisedlearning.
7.DLreducescostsandincreasesaccuracy.
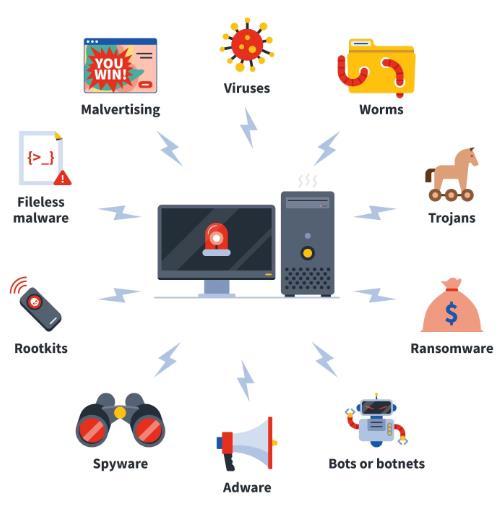
Malware,ShortForMaliciousSoftware,IsSoftwareDesigned by Cyber Attackers to Access or Harm a Computer or Network without the Victim’s Knowledge. Malware Is DefinedAsAnySoftware DesignedToCause DirectHarm. DespiteA39%DecreaseInGlobalMalwareVolumeIn2020, MalwareAttacksContinue.AtTheSameTime,SomeTypes

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
OfMalwareAreLinkedToTheUseOfSimilarAttacks,Such As The Use Of Explosives, Meaning That Some Ideas Are Created By The Victims Themselves, Phishing And Social EngineeringTacticsAreUsedToDistributeMalwareDirectly To Victims; ; Or Mobile Malware, Which Is Malware That Targets Mobile Devices. The Most Common Types of MalwareAre:
1. Malware viruses [6]
Malware Is A Type Of Malicious Software, Usually In The FormOfCodeThatIsAddedToAnApplication,Program,Or System And Distributed By Its Victims. Most Types Of MalwareAreSimilarToVirusesInThatTheyRequireAHost (SuchAsADevice)ToSurvive.TheyRemainActiveUntilAn AttackOccurs,ProbablyCausedByAUserDownloadingAn EmailLink(UsuallyAn.ExeFile,MeaningAn"Executable" File). Documents Are Copied From One Computer To Another,CausingtheMostDamage.Finally,malwarecan:
•Captureapplications.
•Sendinfectedfilestoindividuals
•Stealdata
•EliminateDDoSattacks
•Attackransomwaresoftwareattacks.
Example: iloveyouvirus,2000.
2. Worm malware [6]
Ultimately,wormmalwarecan:
Deleteormodifyfiles
Stealdata
Installbackdoorsforhackers
LaunchDDoSattacks
Launchransomwareattacks
Createbotnets
Infectmanycomputersatonce.
Examples: Sqlslammer,2003:consideredoneofthefastest growingmalwareever,sqlslammerexploitsvulnerabilityin Microsoftsqlserversoftware.Theattacklastedonly10minutes andaffectedthousandsofservers.
3. Trojan malware [6]
Atrojanhorseisa typeofmalwarethatdisguisesitselfas real software, applications, or files, causing users to downloadandlosecontroloftheirdevices.Onceinstalled, trojans can do what they were designed to do, such as damage,destroy,steal,orcauseotherproblemswithyour data or network. Download websites or direct messages from email links. Like viruses, these must be done by the
2024, IRJET | Impact Factor value: 8.315 |
user.Thedifferencewhencomparingmalwareandtrojansis that viruses are host-dependent, while trojans are not. Trojansdonotreplicatethemselveslikeviruses.
Ultimately,trojanmalwarecan:
Delete,modify,orstealdata
Spyonusers
Accessnetworks
LaunchDDoSattacks
Takeremotecontrolofdevices
Examples: Zeus/Zbot, 2011: This bankingTrojan leveragedkeystrokelogging tosteal credentials andalso accountbalances.
4. Ransomware [6]: As the name suggests, ransomware is malware that carries a ransom. It locks and encrypts the victim’sdeviceordataanddemandsaransomtoregainaccess. This usually occurs when the victim has downloaded the malware through an email link or a link from an unknown source.Onceinstalled,themalwarecancreateabackdoorthat allowshackerstoaccessthedeviceandthenbeginencrypting thedata,thuslockingtheentireowneroutofthedeviceuntil theypayaransomtoregainownership.Itisworthnotingthat ransomware is increasingly being paid in crypto currency, sometimescalledcrypto-malware.
Ultimately,ransomwarecan:
Holddeviceshostage
Makedatainaccessiblethroughencryption
Resultinfinancialloss
Examples: WannaCry, 2017: this ransomware attack targeted thousands of computers running the windows operating system worldwide and spread to corporate partnersworldwide.Victimsareaskedtopayabitcoinfee togettheirdataback.
5. Bots or botnets [6]
Othertimes,botscanactas"spiders,"meaningtheprogram ischeckingthenetworktoseewhenhackersareusingthe siteandusingasecuritysite,orifyouprefer,abottodoso. Malware. In some cases, botnets attack devices directly, allowingcybercriminalstocontrolthemremotely.
Finally,botnetsorbotnetscan:
•LaunchDDoSattacks
• Record activities including keystrokes, webcams, and screenshots
•Emailthroughyourdevicecansendphishingemails
•Hackerscanusedeviceremotely

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
Examples:Mirai,2016:ThisbotnetattacktargetedInternetof Thingsdevicesand,fromthere,leveragedDDoSattacks.
6. Adware malware
As the name suggests, adware is advertising-related malware.Alsoknownasadware,adwaredisplaysunwanted advertisementsonyourcomputer,sometimesintheformof pop-upadsthattracktheuser'sbrowsingexperience.Where adware can go wrong is when these ads can distort your messages;downloadtospread.
Finally,adwarecan:
•beannoying
•redirectuserstomaliciouswebsites
•installspyware
•shareuserinformationwithus.
For example: fireball, 2017: this adware infected approximately 250 million devices by tracking victims' onlinegamingthroughbrowserhijacking.
7. Spyware [6]
As the name suggests, adware is advertising-related malware.Alsoknownasadware,adwaredisplaysunwanted advertisementsonyourcomputer,sometimesintheformof pop-upadsthattracktheuser'sbrowsingexperience.Where adware can go wrong is when these ads can distort your messages;downloadtospread.Finally,spywarecan:
•invadeaperson'sprivacy
• collect confidential information, including recording keystrokes
•stealinformation
•causetheftorcreditcardfraud
Example:darkhotel,2014:thiskeyloggingspywaretargets governmentandcorporateexecutivesusinghotelwi-fi.
8. Rootkits [6]
Arootkitisatypeofmalwarethatallowscybercriminalstotake control of a victim's device, usually without the victim's knowledge.Becauserootkitsaredesignedtoremainsilent,they canstealorreplacesecuritysoftware,allowingthemalwareto persistonyourcomputerforlongperiodsoftimeandcause seriousdamage,accordingtothereport.
Finally,rootkitscan:
•Controldevicesremotely
•providecybercriminalswithcontrolledaccesstodevices
•Monitoruseractivity
Examples:zacinlo,2012:this rootkit remainedhiddenuntil: firstdiscoveredaround2017,thisvirusofteninfectsadwareon windowsdevicesanddisablesantivirussoftware.
9. Fileless malware [6]
Arootkitisatypeofmalwarethatallowscybercriminalsto takecontrolofavictim'sdevice,usuallywithoutthevictim's knowledge.Becauserootkitsaredesignedtoremainsilent, they can steal or replace security software, allowing the malware to persist on your computer for long periods of timeandcauseseriousdamage,accordingtothereport.
Finally,Filelessmalwarecan:
•breakantivirussoftware
•stealdata
Example:astaroth,2019:thisFilelessmalwareisarealdata stealer and mostly attacks windows devices and targets specificcountriesincludingBrazil.
10. Malvertising [6]
Nottobeconfusedwithadware,adwareismalwarethatcomes fromadvertisementsonlegitimatewebsites.However,adware isatypeofmalwarethatisalreadypresentonthedevice.Both attacksrelyononlineadvertisementstocauseharm.Youcan fallvictimtoanadvirusbyclickingonit(whichcybercriminals may pay to have on the website), or you can fall victim to downloadsbyvisitingawebsitewithfakeadvertisements.
Finally,malvertisingcan:
Leadtoransomwareattacks
Leadtodatatheft
Leadtocreditcardfraud
Examplesofmaliciousadvertising:media,2016:theNewYork Times, the BBC, aol and other unknown news sites target readers with the aim of hacking computers and demanding ransoms.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
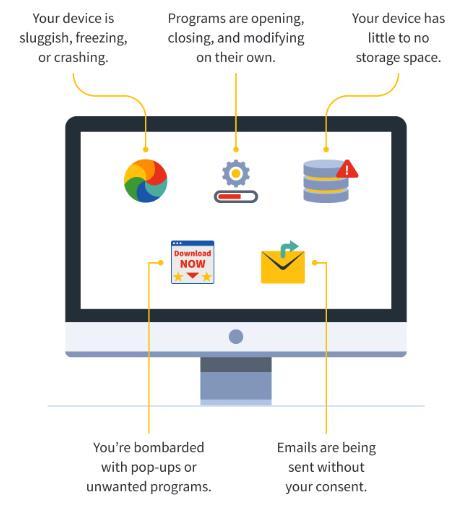
Malwareisoftenspreadviaemail.Accordingtostatistics,94% ofthemaresentviaemail.However,cybercriminalsstilluse differentmethodstoattackmalware.Thesearejustafewof theircommonideas,somearemixed.
Aman-in-the-browserattackoccurswhenanattackerplaces malwareonacomputertocollectinformationsenttovictims and specific websites, and then installs the malware in the browserwithouttheuser'sknowledge.
•Securityexploitationiswhencybercriminalsmanuallysearch for vulnerabilities in devices and networks and then inject malwareintothem.
™ Electronic Devices are an alternative to exploiting vulnerabilities.Thesearepre-writtenscripts thatsearchfor vulnerabilities indevices andultimatelyinjectmalwareinto thatsecuritysystem.
Drive-by downloading is when a user accesses a malicious website that hosts a malware attack. Phishing can include phishingorSMSscams.
1.2:
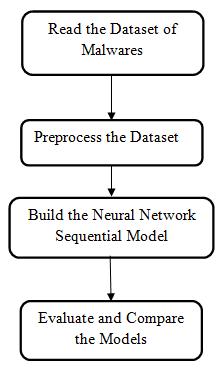
2.1 Malware Detection and Classification: Malware detection and classification is a long process. Many techniquesandmethodsareusedinthesestages.Toidentify malware, you must first use the relevant analysis tools. Secondly, the results of the device are closed and the features are manually extracted or cut. At this stage, the informationisonlyusedtogetgoodresultsintheprocess. After that, the extraction process is selected according to certain rules. Finally, the selected features are trained by
machinelearningalgorithmsorformallearningtechniques to distinguish bad software from good software. Malware identification, detection, and classification are shown in figure2.1[7].Inordertobetterunderstandthecontentand purpose of malware, further classification can be done by determiningthetypeandcategoryofmalwareitbelongsto. Thissectionisdividedintofoursections:malwaredetection tools and platforms, malware analysis, malware feature extraction,anddetectionandclassification.
1.Desktopsandlaptops.
2.Mobiledevices
3.Internetofthingsdevices.
4. Cloud computing platform. Other devices such as smartphones,personalassistants(pdas),andtheinternetof things(iot)havealsobecomeknownovertime.Computer viruses became very popular in the 1990s and 2000s [8]. From 2000 to 2010, the first computer viruses appeared, followedbyTrojanhorses.Ransomwarehasbecomeavery popularmalwaresince2010[9].From1990to2010,most types of malware were written for regular computers, as well as for the windows operating system (os), as well as otheroperatingsystemsotherthanwindows(suchasunix, different versions of linux, and MacOS). Therefore, a malwaredetectionmethodforcomputersisready.However, after2010,mobiledevicessuchassmartphones,tablets,and pdas became popular. After that, cloud computing environments and iot devices became quite popular. Accordingto recentresearch,thenumberofsmartphones has surpassed computers, and the difference is increasing day by day. People use mobile apps more than the web version of the program. The number of iot devices is also increasing. As the use of smartphones and iot devices is more popular than regular computers, cybercriminals’ attention has also shifted from regular computers to smartphonesandiotdevices.Cybercriminalsmodifyexisting malwareandcreatedifferentversionsofthesamemalware thatcanrunonthesedevices.Accordingtomcafee’sreport, there has been an increase in banking trojans, backdoors, and fake apps targeting mobile platforms [10]. Also, maliciousattacksinvolvingcryptocurrencies,socialmedia, iot devices, and cloud computing environments are increasing. These reasons are that malware detection is moving from computers to mobile iot devices and cloud environments. Cloud computing has many advantages for malwaredetection,includingeasyaccess,morepower,and larger data [11]. Therefore, up-to-date information on malwaredetectionanddistributionformobilephonesand iot is collected using deep learning and used in the cloud environment.
Data mining and machine learning techniques identify malware based on features obtained from static analysis,

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
negative analysis, visualization-based analysis, or a combinationofanalyses.Dataminingclassifiersaretrained usingvariousfeaturestoclassifyunknownmalware.Some studies use feature ranking [12] to perform effective malwareclassificationusing machinelearningalgorithms. Theframeworkproposedby[13]isbasedonstaticfeatures that can be applied to three learning algorithms, namely inductive student rule, probabilistic method, and multiple classifiersystems.Theirapproachislimitedtotheworld’s largest models. Reference [14] uses machine learning techniques such as naive Bayes, decision trees, support vector machines, and n-gram feature-based boosting. The authorstheorizethatboosteddecisiontreesaresuperiorto othermethods.Theirapproachislimitedtocrimedetection andidentifyingmalwareexecutioncharacteristics.StaticPE archivefeatureswereextractedbytestingwithexecutables [15]andmachinelearningclassifiers(suchasNaiveBayes, Bagged J48, KNN, multilayer perceptron (MLP), and J48 decision trees using entropy thresholding and unbagged examples for classification). Reference [16] constructed vectorsfromopcodesequencesofexecutablesandtraineda machinelearningclassifier.Theirapproachisusedonlyfor packing. The phrase sequences are extracted from PE archives [17] and negative examples are created to represent them. The authors perform malware detection usingeachnearestneighbor(ANN)classifier.However,the success of machine learning-based measurement tools dependsontheextractedfeaturesandthecapabilitiesofthe selected machine learning model. A classifier may fail if it cannotprovidecluesduetopacking,obfuscation,andminor changes in the order of features made by the malware author. It is also used to identify and isolate malware to augmentmalwareanalysismethodsformalwareanalysis.A combination of static and dynamic features improves detection [18], [19]. The implementation [20] combines staticfeaturessuchaslongfrequencyvectorsandprintdata vectors with dynamic API features into a single vector. It extractsopcodesequencesandsystemcallsignaturesfrom binaryarchivesusingdynamicanalysis.Thesefeatures[21], [22]areseenlaterintheimage.Asimilarpredictionmethod [22],[23]consistsofstaticanddynamicfeaturesbasedon image matrix vector representation. The model is represented using a new method [24] by creating groups basedonsimilaroperationsforeachtypeofresource(e.g., Filenames,names,mutexes,andnameregister).Theyuse machine learning classifiers to classify malware and cleanware. This technique is not capable of providing general visibility for malware detection because new malwareanddifferenttypesofexistingmalwarearealways present in the network. Automatic Android Malware Detection (AAMD-OELAC) technology integrates learning. ThemaingoalofAAMD-OELACtechnologyistheautomatic classification and identification of Android malware. To achievethis,theAAMD-OELACsystemprocessesthedatain a preliminary stage. For the Android malware detection process,theAAMD-OELACtechnologybasedonthelearning process using three ML models, namely Least Squares
SupportVectorMachine(LS-SVM),KernelExtremeLearning Machine (KELM), and Regularized Random Vector FunctionalConnectionNeuralNetwork(RRVFLN).Finally, theav-avoptimization(HPO)methodisusedtocorrectthe disadvantagesofourdeeplearning,whichhelpstoimprove the malware detection results. An experimental test was conducted to demonstrate the effectiveness of the AAMDOELAC method. The simulation results demonstrate the superiority of the AAMD-OELAC technology over other existingmachinelearning-basedantimalwaresolutions.The proposedsystemisbasedonhierarchicalintegration,which followsthebasicfeaturesofdeeplearningbutwillbemore efficient in the future. The proposed method does not requirehyperparameterstuningorBackpropagationandcan reducemodelcomplexity.Theproposedmodeloutperforms other state-of-the-art methods, achieving 98.65%, 97.2%, and 97.43% detection rate for Malimg, BIG 2015, and MaleVis malware datasets, respectively. The results show thatthesolutionisabletodetectnewandadvancedmalware due to its different capabilities. Find framework. The frameworkusesmultipleregressionmethods.Authorization isoneofthemostimportantaspectsofAndroidOSsecurity; applicationauthorizationis extractedfromstaticanalysis, and application security analysis is performed through machinelearning.Accordingtodifferenthorizontalmalware types, permissions are requested from two distributions basedonAndroidmalwaredetection.Theseclassifications arecomparedwithsimplemachinelearningmethodssuchas supportvectormachine,k-nearestneighbors,naiveBayes, and decision trees on four different datasets. In addition, bagging, one of the hybrid learning methods, is used to generatedifferentdistributionstoimprovetheclassification efficiency. Therefore, classification algorithms based on linear regression models can achieve high performance withouttheneedforverycomplexclassificationalgorithms. Engineering,decompiling,ordisassemblingtheevaluation applicationinawaythatviolatestheapplicationlicenseand termsofuse.Moreover,thesesolutionsoftenusethesame machinelearning(ML)modeltoidentifydifferenttypesof malware,whichleadstomanyvulnerabilities.Inthiscontext, wepropose a method for detecting Android malware that includesasetofdedicateddetectiontools,allbasedonrules andMLtechniques,atthesamelevel.Differentapplication cycles(Pre-andPost-)Performseveralanalysisphases.Our method[25]alsodiffersfromthecasesolutionsinthatitis not affected by using a method that does not violate the application form and terms to obtain the application function.
The proposed model will have two stages: analysis and deployment stage. During the analysis, each signature is checked for malware and data quality. Both static and dynamicfeatureswillbeconsidered.Forbetterresults,the numberoffeatureswill increaseto215. Thesecondstage involvesclassifyingmalwareintosimilarcategoriesbasedon

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
theirstaticanddynamicfeatures.Inthisstage,deeplearning is used for malware detection and classification. The scanning stage, inspired by the concept of convolutional neural networks (CNN), will be used to preserve the relationshipbetweentheoriginalpixels.Eachprofileinthe training process is an input-level classification. The first stage starts with the analysis of input data from parallel processing. The following diagram shows the proposed workingmodel.
4.5FeatureSelectionandDimensionalityReduction
Feature Selection and Dimensionality Reduction are important methods to improve model performance in machine learning by removing unnecessary features and focusing on data features, reducing overfitting to highdimensionaldatasetsandimprovingperformance.Theyalso contributetomodelinterpretation,solvingmulticollinearity problems, handling cases with little or no data, and improvingmodelcapabilitiesbymakingmodelconstruction easier. These ideas also help create good and effective beautifuldesignsbyguidingthearchitectureandhelpingto understandhowfeaturesaffectdifferenttargets.ECLATwas selectedforspecialselectioninAndroidmalwaredetection duetoitsefficiencyandeffectivenessintheproblem.These techniquesareknowntoimprovemodelperformanceand interpretationandarefrequentlyusedinmachinelearning, makingthemasuitablechoiceforthisstudy.
In machine learning and data science, a technique called training-testsplitisusedtoevaluatetheperformanceofa model.Training-testsplitisaprocessthatsplitstheexisting dataintotwogroups:atrainingsampleandatestsample.A percentageofthedataissplitbetweentrainingandtesting.A ratio provides 70-80% of the material for the training process and the remaining 20-30% for testing. But the
percentagewillvary.Ourmodel'sdataisdividedintotwo parts: training and testing. 90% Of the dataset is used for training and 10% for testing. These are two new record stores with a total of 41 entries. The final result is the answer,whichhastwopossibleanswers:1or0.Thefirst40 itemsarefeatures,thelastitemsareresponses.-Trainsize= 13528-testsize=1503.ModelDesign
The proposed model is designed to study classification problemsusingsmalldata,whichisaspecialtypeofneural in our work. The network is usually used as a link. As a result, the implementation of the planning function has proven to be very effective because it aims to study the similaritiesratherthanstatisticsbetweentwoproposals.
Aftertraining,thenetworkcancomparetwodatasamples. The first query sample uses the training network embeddings and then compares using the same ECLAT algorithm.Usedistancescorestogeneratebinaryoptions. Trainingmodels
Design models commonly used to solve Android malware problems were used to train our models. Using a set of pointsasinput,themodellearnstopredictwhethertwodata pointsbelongtothesamecategory.Thetwo-layerstructure isthefirstpartofthedesign,followedbythelayerstructure, distance layer and sigmoid release layer, each with 64 hiddenholes.Themodelusingstochasticgradientdescentis optimized after training with binary cross-entropy loss. Training was conducted in 10 sessions with a group of 8 people.Inaddition,afunctiongeneratorisusedinthisstudy togeneratedatapairsforeachdataset;80%ofthedata is usedfortrainingand20%foruse.Toensurethatthemodel doesnotconformtotrainingmaterials,trainingandmisuse, andisfollowedduringtraining.Twoeffectivemethodsare usedtoreducetheeffectsofclassinequalityduringmodel training:stratifiedsamplingandclassweighting.
Malware detection often faces the problem of class inequality, where the number of examples in one class greatlyexceedsthenumberofexamplesinanotherclass.By usingundersampling,youensurethateachmini-batchused fortraininghasaproportionalrepresentationofeachclass, thus controlling the class distribution of the original data. This strategy ensures that the minority group receives sufficientattentionduringtrainingandpreventsthemodel frombiasingtowardsthedominantgroup.Weightingunits are also included in the optimization process. This model focuses more on analyzing data from a small class by assigninghigherweightstofewerclasses,thussolvingthe problemofunder-classification.Thisprocessimprovesthe model’sabilitytoperformandcorrectclassificationofmost andleastclasses,makingAndroidmalwaredetectionmore efficientandreliable.Trainingandtestingaccuracyshould betakenintoaccountinafullevaluationofmachinelearning models. It has many features that will help increase the

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
usabilityandreliabilityofyourmodel.First,ithelpsidentify over-fitting,whichoccurswhenamodelfocusestoomuchon memorizing information and underperforms when presentedwithnewinformation.Overfittingcanbedetected bycomparingtheaccuracyofthetrainingandtestdata,and appropriatemeasurescanbetakentocorrectit.
Amodelaccuracyrateabove99%indicatesthatthemodelis abletopredictpatternswellinthetestdata.However,the model will become training data, which will cause performancetodegradeonnewdata.Validationdropsand accuracy are monitored during training to prevent overfitting.Monitoringredundancyisimportantbecauseit providesinformationaboutthemodel’sabilitytogeneralize andintegrate.InFigure6.42,boththetrainingandvalidation lossesshowadecreasingtrendindicatingthattheweightsof the model are optimized and the model is learning new information from the data sheet. This model successfully reducesthebinarycrossentropylossofthetrainingdataas canbeseenfromthedecreaseinlearninglossandthisalso showshowgoodthemodelisforthestudymaterials.Thisis supportedbythefactthatthevalidationlossalsodecreases asthemodelgeneralizestothevalidationdata.
The data we use in our paper is the well-known Drebin malware dataset. To use this data, we need to select individualfeaturesandthenspecifyourmodelaroundthem. Tofindthebestfeaturesforourusecase,weuseaselection processtosearchforthemostimportantfeaturesthatdetect malware.
ThelistofAndroidappsclassifiedasdangerousormalicious is publicly available and is called the Drebin dataset. The data was generated from a 2014 study by researchers at Northeastern University to identify malware on Android devices[37].Theresearchersseparatedeachprograminthe dataset into bad and not-so-bad projects using static and dynamic analysis. The database contains 5,560 apps from 179differentmalwarefamilies.Thecollectionalsoincludes 13,106 samples from other sources, including Android websites, malware forums, and security blogs, as well as 96,150appsfromtheGooglePlayStore,19,545appsfrom variousotherstoresinChina,2,810appsfromotherRussian app stores, and more. The five main stages of its implementationarepreprocessing,datapartitioning,model architecture,training,andevaluation.Theresearchersused two methods to find the suspected malware, and then analyzed the results. The Drebin dataset has become a favoriteofmobilesecurityresearchersinmanystudiesand research initiatives. The document is available for public downloadfromtheNortheasternUniversitywebsite.
Chart
Afterpre-processing,counttheoccurrenceofeachclass.For counting,firstseparatethefeaturesandlabels.Calculatethe
majorityandminorityclasslabels.Separatethemajorityand minorityclass.TheresultsareshownbelowIfigures.
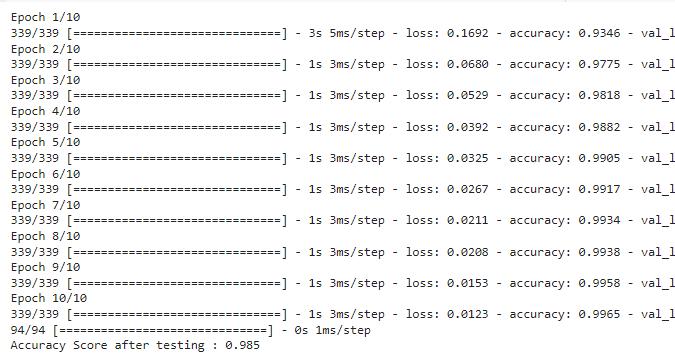
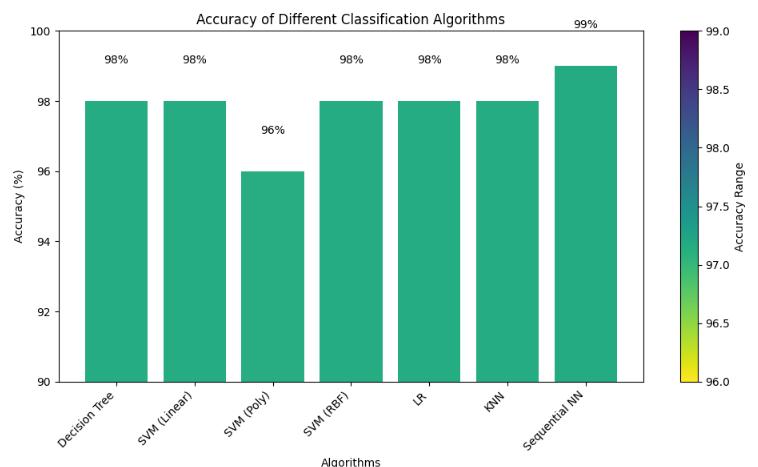
Insummary,thestudy,classweightsandstratifiedsampling areusedduringmodeloptimizationtoaddressissueswith class imbalance that are frequently present in malware detection. The effectiveness of the model is thoroughly assessed,accountingforbothtestingandtrainingaccuracy. Notably, the model outperforms earlier techniques like LogisticRegression,randomforestclassifier,KNN,XGBoost by achieving an impressive accuracy rate of 99% on the Drebin dataset and other dataset. The performance of the model is fully analyzed using a set of evaluation metrics, includingaccuracy,recall,precision,F1score,andconfusion matrix.

International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 11 Issue: 9 | Sep-2024 www.irjet.net p-ISSN: 2395-0072
[1] O.AslanandR.Samet,“Acomprehensivereviewon malware detection approaches,’’ IEEE Access, vol. 8, pp. 6249–6271,Jan.2020.
[2] R.KomatwarandM.Kokare,‘‘Asurveyonmalware detectionandclassification,’’J.Appl.Secur.Res.,pp.1–31, Aug.2020.
[3] A. A. Yilmaz, M. S. Guzel, E. Bostanci, and I. Askerzade,‘‘Anovelactionrecognitionframeworkbasedon deep-learningandgeneticalgorithms,’’IEEEAccess,vol.8, pp.100631–100644,2020.
[4] A. A. Yilmaz, M. S. Guzel, I. Askerbeyli, and E. Bostanci,‘‘Avehicledetectionapproachusingdeeplearning methodologies,’’inProc.Int.Conf.Theor.Appl.Comput.Sci. Eng.,Nov.2018,pp.64–71.
[5] A. A. Yılmaz, M. S. Guzel, I. Askerbeyli, and E. Bostancı, ‘‘A hybrid facial emotion recognition framework using deep learning methodologies,’’ in Human-Computer Interaction, T. Ozseven, Eds. Hauppauge, NY, USA: Nova SciencePublishers,2020.
[6] https://us.norton.com/blog/malware/types-ofmalware
[7] O. Aslan and A. A. Yilmaz, "A New Malware Classification Framework Based on Deep Learning Algorithms,"inIEEEAccess,vol.9,pp.87936-87951,2021, doi:10.1109/ACCESS.2021.3089586.
[8] J. Love. (2018). A Brief History of Malware Its Evolution and Impact. Accessed: Mar. 20, 2021. [Online]. Available: https://www.lastline. Com/blog/history-ofmalware-its’s-evolution-and-impact.
[9] D. Palmer. (2017). Ransomware: Security Researchers Spot Emerging New Strain of Malware. Accessed: Mar. 20, 2021. [Online]. Available: https://www.zdnet.com/article/ransomware-securityresearchers-spotemerging-new-strain-of-malware [10] (2020).McAfeeMobileThreatReportQ1.Accessed: Mar. 21, 2021. [Online]. Available: https://www.mcafee.com/content/dam/consumer/enus/do cs/2020-Mobile-Threat-Report.pdf
[11] O.Aslan,M.Ozkan-Okay,andD.Gupta,‘‘Areviewof cloud-based malware detection system: Opportunities, advancesandchallenges,’’Eur.J.Eng.Technol.Res.,vol.6, no.3,pp.1–8,Mar.2021.
[12] M. Wadkar, F. Di Troia, and M. Stamp, ‘‘Detecting malwareevolutionusingsupportvectormachines,’’Expert Syst. Appl., vol. 143, Apr. 2020, Art. no. 113022, doi: 10.1016/j.eswa.2019.113022.
[13] M.G.Schultz,E.Eskin,F.Zadok,andS.J.Stolfo,‘‘Data miningmethodsfordetectionofnewmaliciousexecutables,’’ inProc.IEEESymp.Secur.Privacy.(S&P),May2000,pp.38–49.
[14] J. Z. Kolter and M. A. Maloof, ‘‘Learning to detect maliciousexecutablesinthewild,’’inProc.ACMSIGKDDInt. Conf.Knowl.DiscoveryDataMining(KDD),2004,pp.470–478.
[15] R.Perdisci,A.Lanzi, and W. Lee, “Classificationof packedexecutablesforaccuratecomputervirusdetection,” PatternRecognit.Lett,vol.29,no.14,pp.1941–1946,Oct. 2008,doi:10.1016/j.patrec.2008.06.016.
[16] I. Santos, F. Brezo, X. Ugarte-Pedrero, and P. G. Bringas,‘‘Opcodesequencesasrepresentationofexecutables fordata-mining-basedunknownmalwaredetection,”Inf.Sci., vol. 231, pp. 64–82, May 2013, doi: 10.1016/j.ins.2011.08.020.
[17] Y. Fan, Y. Ye, and L. Chen, “Malicious sequential pattern mining for automatic malware detection,’’ Expert Syst. Appl., vol. 52, pp. 16–25, Jun. 2016, doi: 10.1016/j.eswa.2016.01.002.
[18] J. Z. Kolter and M. A. Maloof, ‘‘Learning to detect maliciousexecutablesinthewild,’’inProc.ACMSIGKDDInt. Conf.Knowl.DiscoveryDataMining(KDD),2004,pp.470–478.
[19] H.-J.Li,Z. Wang,J.Pei, J.Cao,and Y. Shi, ‘‘Optimal estimationoflow-rankfactorsviafeatureleveldatafusionof multiplex signal systems,’’ IEEE Trans. Knowl. Data Eng., early access, Aug. 13, 2020, doi: 10.1109/TKDE.2020.3015914.
[20] R. Islam, R. Tian, L. M. Batten, and S. Versteeg, ‘‘Classification of malware based on integrated static and dynamicfeatures,’’J.Netw.Comput.Appl.,vol.36,no.2,pp. 646–656,Mar.2013,doi:10.1016/j.jnca.2012.10.004.
[21] J. Zhang, Z. Qin, H. Yin, L. Ou, S. Xiao, and Y. Hu, ‘‘Malwarevariantdetectionusingopcodeimagerecognition with small training sets,’’ in Proc. 25th Int. Conf. Comput. Commun.Netw.(ICCCN),Aug.2016,pp.1–9.
[22] K. Han, B. Kang, and E. G. Im, ‘‘Malware analysis usingvisualizedimagematrices,’’Sci.WorldJ.,vol.2014,pp. 1–15,Jul.2014,doi:10.1155/2014/132713.
[23] H.-J. Li, L. Wang, Y. Zhang, and M. Perc, ‘‘Optimization of identifiability for efficient community detection,’’ New J. Phys., vol. 22, no. 6, Jun. 2020, Art. no. 063035,doi:10.1088/1367-2630/ab8e5e.
[24] J. Stiborek, T. Pevný, and M. Rehák, ‘‘multiple instanceslearningformalwareclassification,’’ExpertSyst. Appl., vol. 93, pp. 346–357, Mar. 2018, doi: 10.1016/j.eswa.2017.10.036.
[25] L.d.Costa andV.Moia,"ALightweightandMultiStageApproachforAndroidMalwareDetectionUsingNonInvasiveMachineLearningTechniques,"inIEEEAccess,vol. 11, pp. 73127-73144, 2023, doi: 10.1109/ACCESS.2023.3296606.