

: Levitating, contactless, intelligent!
Free 2D product movement with up to 6 degrees of freedom
www.beckhoff.com/xplanar

XPlanar enables new degrees of freedom in product handling: Levitating planar movers float over individually arranged planar tiles on freely programmable tracks.
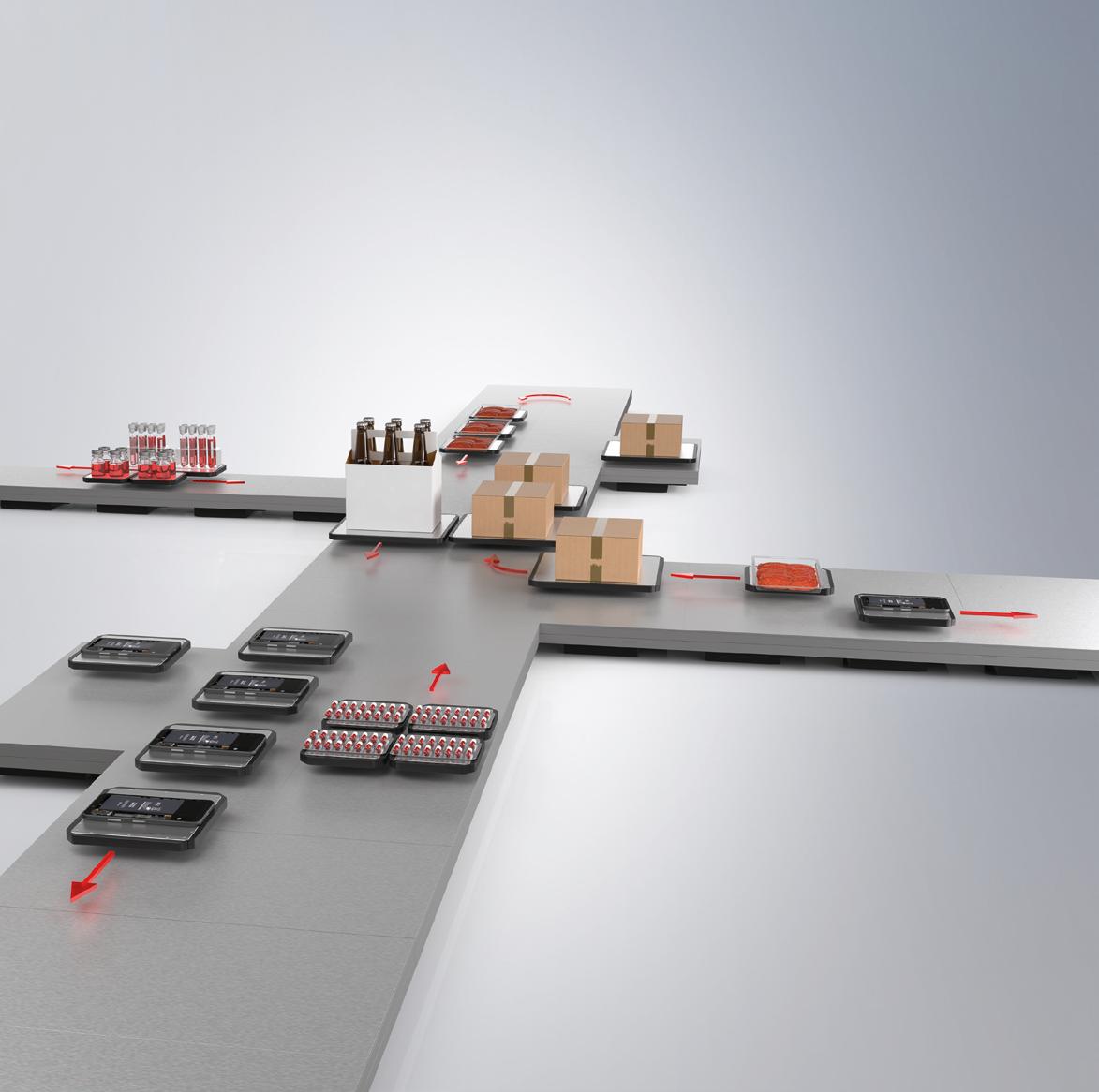
Individual 2D transport at up to 2 m/s
Processing with up to 6 degrees of freedom
Transport and processing in one system
Wear-free, hygienic and easy to clean
Free arrangement of planar tiles enabling customized machine layout
Multi-mover control allowing parallel and individual product handling
Fully integrated into the powerful PC-based Beckhoff control system
(TwinCAT, PLC IEC 61131, Motion, Measurement, Machine Learning, Vision, Communication, HMI)
For use across all industries: assembly, food, pharma, laboratory, entertainment, …
Iain
Safety and security are explored in depth in this issue – we are looking at the cybersecurity implications of greater IT/OT convergence, getting advice from a variety of cybersecurity experts; we also offer advice on what companies at different stages in their IT/OT convergence journey need to consider. When it comes to process safety we are looking at t he benefits of digital-twin technology when applied to safety instrumented systems.
Wireless technology is also a focus this month, with features looking at trends and considerations when looking at the technology; offering advice on selecting the right wireless networks for your application; and also looking at the beneficial relationship that IO-Link Wireless and 5G might offer.
Suzanne GillINDUSTRY REPORTS
4 The IPC requirements of complex control; Building a roadmap to remote maintenance
EDITOR’S CHOICE
6 Compact and energy saving decentralised drive package; graphic operation terminals
NETWORK SECURITY
8 Suzanne Gill poses some IT/OT security questions to a panel of experts


14 IT/OT convergence – what do you need to do?
16 We highlight the importance of locking down your OT networks
PROCESS SAFETY
18 An exploration of the benefits of digitally-twinning safety instrumented systems
20 Digital transformation and process safety do not have to be mutually exclusive
WIRELESS TECHNOLOGY
22 Will well-engineered systems help make wireless control the new normal in factories and plants?
24 Advice on selecting the right wireless sensor network
26 We take a look at the beneficial relationship of IO-Link Wireless and 5G for the industrial sector
SUSTAINABILITY
28 Find out how the application of digital capabilities can push the energy and resource transition
TEST & MEASUREMENT
30 Testing the physical structure of Ethernet systems PG
THE IPC REQUIREMENTS OF COMPLEX CONTROL
As automation technologies and the Industrial Internet of Things (IIoT) become more commonplace in modern manufacturing, the requirements of control hardware have increased. However, according to Stephen Hayes, managing director at Beckhoff UK, the importance of this is often overshadowed by the focus on new sophisticated software. He believes that manufacturers should take a holistic approach to complex control.
Countless reports in recent years have reinforced the imminent arrival of the IIoT. In 2019, Microsoft’s IoT Signals report stated that, by the end of 2021, 94% of businesses will use IoT in some capacity. Yet fast-forward to the fateful year and a survey by Ubisense identifies that 43% of manufacturers no longer understand the value of IoT.
Unquestionably, a contributing factor to this uncertainty around the value of IoT is how the concept has been presented in recent years. Whereas IoT and connected devices are new ideas in some markets, they are a long-established norm for many manufacturers. When we consider IIoT simply as connected industrial systems and advanced
automation technologies, more manufacturers are aware of the intrinsic value to their operations – and this is reflected in how well these technologies have been adopted in recent years.
However, the implied distinction between automation technology and IIoT has led some business leaders down a route of believing that software is the core focus for digitising their operations. While software certainly plays an integral role, it’s vital that hardware – in particular, industrial PCs (IPCs) – are considered.
For example, the right software package can allow plant managers to ensure that data is communicated and managed in the right way, or that complex control programs can be run. However, if the IPCs at the field-level are unable to provide the computing capacity required to process control or system data, the software package is unable to provide the best value.
Steven Hayes believes that this is where the conversation around IIoT has gone awry in recent years. The intangible concepts of the IIoT and industrial digitalisation place the core focus on software functionality, rather than looking at hardware and software as a
Handbook helps build a roadmap to remote industrial maintenance
SKF has published a handbook to help organisations through the process of introducing remote industrial maintenance.
The global pandemic has raised the profile of remote industrial maintenance from simply being an element of operational planning to being strategically important.
The SKF handbook draws on the company’s experience of providing ‘Rotation as a Service’ and includes benchmark data from research conducted at more than 1,400 organisations globally.
As well as a cross-industry guide, there are specific versions for the pulp & paper, steel and chemical sectors.
Each guide explains the elements of remote industrial maintenance, identifies ways in which it can be introduced, assesses risks and estimates financial benefits. These subjects are dealt with in separate chapters.

The guide also helps to estimate financial benefits. Moving forward with one or more components of remote industrial maintenance must be based on a specific business
holistic solution for industrial control.
Fortunately, hardware capabilities have kept pace with the demands placed on them by more sophisticated software. Looking within Beckhoff’s IPC portfolio for example, there is everything from cost-effective and compact units to IP65 rated units with multi-core processing for harsher environments with demanding computing requirements.
Each range consists of units with various processors, making them able to accommodate different levels of data intensity and software requirements. Yet every IPC is designed with flexibility in mind: whether in a control cabinet or machine-mounted, there is a range of form factors to fit most footprints. This is important because it allows manufacturers with legacy machines to upgrade the control system IPCs without requiring extensive redesigns or delays.
Perhaps it is time that manufacturers swap the concept of the IIoT with the idea of advanced automation instead, giving ample focus to the hardware level that keeps data flowing throughout operations. In doing so, we may find manufacturers once more fully understanding how these technologies can add value and making the intangible idea of IIoT seem far more tangible.
consideration so guidance is also offered on estimating the benefit of reduced unplanned downtime.
For more information go to: https://skf.li/zh7yrx
Applying ISO/IEC 27001/2 and ISA/IEC 62443 for OT environments
Many organisations have established ISO/IEC 27001/2-based policies and procedures governing the IT security in their office environment. Some have attempted to address their operational technology (OT) infrastructure under the same management system and have leveraged many IT/OT commonalities. The ISA/IEC 62443 series explicitly addresses issues such as these, helping organisations to maintain conformance with ISO/IEC 27001 through common approaches wherever feasible, while highlighting differences in IT versus OT approaches where needed.
A new ISA white paper offers guidance for familiar with ISO/IEC 27001 and interested in protecting the OT infrastructure of their operating facilities based on the ISA/IEC 62443 series. It describes the relationship between the ISA/IEC 62443 series and ISO/IEC 27001/2 and how both standards may be effectively used within one organisation to protect both IT and OT. https://bit.ly/3ilsTWS
Partnership offers end-to-end cloud-based industrial traceability
Rockwell Automation is partnering with Kezzler AS, a cloudbased product digitisation and traceability platform, to help manufacturers capture the journey of their products from raw material sources to point-of-sale or beyond, using cloud-based supply chain solutions that focus on product traceability.
The combined offering is well suited to industries such as life sciences, food and beverage, and consumer packaged goods, which are focused on complying with regulatory requirements and meeting consumer expectations.
Rockwell’s supply chain capabilities will combine with Kezzler’s traceability technologies to help customers connect suppliers, manufacturing, logistics, and consumers into one real-time traceability platform.
Kezzler’s cloud-based solution provides integration flexibility and ease of access to existing systems of record that incorporate a range of technologies from immutable ledgers (blockchain) to traditional databases.
The two companies can also create unique identities that can be used to digitally identify and track products from creation to consumption. For example, they can provide the data needed to aggregate total environmental footprint per manufactured product. This data can then be used for evidence and improvement or be shared directly with consumers.
Rockwell and Kezzler have already created traceability solutions for FrieslandCampina, one of the world’s largest dairy companies. By creating unique QR codes on each of its Friso infant formula products, the company can now track its products from farmer to consumer. Consumers can also scan the codes to check authenticity and learn more about the product and its origin.
.Human touch. .Industrial performance.
The latest generation of collaborative industrial robot, MELFA ASSISTA brings high accuracy with a delicate touch to a wide range of manufacturing applications.

Able to complete complex assembly tasks to the highest levels of precision and repeatability, ASSISTA is easy to set up and fast to program, enabling rapid production changeovers. Independently tested to international safety standards, ASSISTA is proven to be a safe co-worker, that delivers next level industrial performance.
Scan the QR code to register for our white paper and learn more on cooperative manufacturing with industrial cobots and robots.
Precise control valve lightens up
Schubert & Salzer Control Systems has introduced what it believes is the smallest sliding gate control valve with diaphragm actuator and integrated digital positioner on the market.

The compact, lightweight and energyefficient type 8028 sliding gate valve is designed for use in all areas of the process industry. In addition, with a pneumatic 80mm diaphragm actuator and digital positioner, the control valve is said to be very fast, almost wear and maintenance-free as well as offering low-noise operation.
Its small size and a space-saving intermediate flange design makes the valve suitable for use in confined spaces.
The sliding gate technology used in the type 8028 controls the flow in milliseconds – two slotted discs
arranged vertically to the direction of flow slide over each another in a linear movement. The actuator must therefore only overcome the sliding friction between both discs. The required actuating force is 90% lower than for globe valves with the same nominal size at the same differential pressure.
Short actuator travels of between 6 to 9mm also reduce the wear from the packing and drive of the control valve. Even when difficult media get stuck to the piston rod, the tightness remains permanently unimpaired because the piston rod barely moves into the packing. For the actuator diaphragm too, the short stroke and low control pressures mean much lower stress and hence a long service life with many million switch cycles.
Graphic operation terminals
Mitsubishi Electric has added two new Graphic Operation Terminals (GOTs to its GOT2000 Series Wide model lineup.
The 12.1in narrow bezel widescreen models are designed to meet the need for wider screens to show more information in factory, process, utility and other automation applications. The widescreen GOTs are also ready to support remote connection in cases where user access may be restricted. Remote connection functions such as SoftGOT enable remote maintenance via access to the local GOT
screen while operators can obtain live data using GOT Mobile.
The range is also now available with new antibacterial, antiviral protection sheets as options for standard GT27 and GT25 GOTs. The sheets help reduce disinfection. They work by adopting ‘SIAA’ certified sheets with anti-virus and antibacterial features. They are proven to inactivate 99.99% of viruses and reduce bacterial growth to less than 1/100, with 10+ years of performance in typical environments.
Compact and energy saving decentralised drive package
WEG has introduced a decentralised drive package, consisting of WG20-series gear units, EUSAS motors and a MW500 variable speed drive (VSD). Compared with traditional drives, this compact package is said to provide lower energy consumption and a compact footprint, as well as improved flexibility.

The decentralised drive package can be used for a range of applications, including machines in intralogistics, such as warehouse systems and conveyor belts. Other potential applications include speed-controlled fans, pumps and filling systems.
Members of the MW500 VSD family can be used for a range of applications
in the 0.12 to 9.2 kW range for line voltages of 380 - 480 V. The equipment is available in three frame sizes (A, B and C), and from 0.12 to 1.5kW for 200 - 240V with WEG’s WG20 geared motor series – which are available as helical, parallel shaft or helical bevel gear units.
When the WG20 gear unit in this setup is connected to a WEG EUSAS integral motor from WEG, it offers a wide range of advantages as the EUSAS motor operated in frequency inverter mode (100/120 Hz characteristics) offers double the power at a constant torque.
The heavy-duty housing design for
the MW500 with an IP66 and NEMA 4X rating means the VSD can be used outdoors and can be attached directly to the motor terminal box frame or to the wall.
Variable speed drives are commonly used in applications like fans, pumps and compressors. The “WEG guide to Variable Speed Drive applications” explains how using a VSD can help decrease greenhouse gases by lowering energy consumption, leading to a reduction in the total cost of ownership.

Download the free guide at www.weg-automation.com

VARIABLE SPEED DRIVES HELP SAVE THE ENVIRONMENT AND REDUCE COSTS.
CONVERGENCE QUESTIONS
Q. What do you believe are the biggest security risks and challenges of IT/OT convergence?
Prof Dr Tobias Heer, senior architect at Belden believes that the biggest issue is the heterogeneity and complexity created by mixing IT and OT systems, resulting in systems that are hard to understand from a security perspective. The result, he says, is a lack of control over what’s happening in the network. Especially when less restrictive networks grow over the years it becomes difficult to know what’s going on. Getting rid of the heterogeneity is not always possible since we have vastly different device classes (control systems on the one hand and IT servers on the other hand). So, making sure you stay on top of what’s happening is key.
Heer says that recent ransomware attacks have often used the fact that communication was too liberal in industrial networks and that known vulnerabilities existed in the connected systems. That’s exactly the result of an open and possibly unknown network

structure. The result of complex and unorganised networks can get worse if multiple groups manage the network and can attach devices to it. Of course, work gets done if everything has a network that just works. However, critical security controls are hard to implement in such a situation. On the other hand, starting from the point of knowing what’s happening in the network enables one to implement a whole chain of security controls. Asset management enables you to find vulnerabilities and outdated software versions. Knowing the software in use enables you to implement patch management to always have your devices up to date. Knowing all devices and their peers helps you to segment the network into different zones to restrict attacker communication. Knowing the permitted communication patterns allows you to detect deviations and to ultimately identify attacker behavior. It all starts with a network in which you have full visibility and control. Then suddenly other core tasks become manageable.
Andrew Bullock, industrial automation and network cyber security specialist at Rockwell Automation, believes that one of the biggest security risks and challenges of IT/OT convergence is poor leadership. It is not having a defined hierarchy of responsibility for the security lifecycle process. Offering an example he points out that, where there is no security responsibility, people with the good intention of improving operational visibility, and insight and hence performance and operating efficiency allow the proliferation of unmanaged devices on to the network, particularly open IoT. However, by doing so, they increase the attack surface by increasing the number of unprotected entry points to the network.
Creating a structured hierarchy of security responsibilities enables organisations to establish a culture of good security practices and confirm that appropriate security procedures and technologies are used. Leaders must actively get involved and sponsor the development of programs and working groups as diverse as, the education of an > p10
OF APPLICATIONS. YOUR GLOBAL RESOURCE.

Your Source for Industrial Electronics & Automation
Finding the right part for the job has never been easier. Galco carries more than 3 million electrical products, with free technical support to help you find the part you need and get it quickly.

IT professional, or IT department, to help them understand the differing priorities between IT and OT networks, or an engineering manager to understand the risks associated with unmonitored and unsecure external remote connectivity to allow ‘ease of modification’, to operator awareness of unexpected behavioUr of an operating screen or machine.
Aengus Gorey, a security systems engineer at Analog Devices, says that OT asset management is a critical challenge to a converged network. He says that, typically, an OT network does not have a live device map with rich profile data, which allows the devices access to the network to be controlled & managed. In a converged network, such a feature allows rogue devices to attach to the network and interact more easily inside the network, creating security holes for observation or malicious actions on the network.
How security concepts are applied and managed in the converged network become increasingly important. Equipment manufacture, commissioning and servicing processes need to be designed with a security mindset. Without a security lifecycle process, it will expose devices in an OT network to threats created by poor security hygiene.
Gorey believes that, as we move towards an Industry 5.0 model with greater human/ machine dynamic, the interfaces to an OT network will look much more like an IT network than previously and consequently this may expose OT networks to a greater degree of social engineering threats.
Phillip J Corner, industrial cyber security engineer at Thales UK, says that interconnection of process systems and business systems can offer benefits to enterprises not only operationally, but also for cyber resilience. Endpoint protection, patch management, monitoring systems, backup and recovery, and other key components underpinning cyber resilience are likely to be more advanced in business systems and can be efficiently expanded to serve process security needs.
Additionally, the majority of current
state-of-the-art solutions have a vendor-hosted cloud component for configuration, management, and monitoring. However, Corner says that the benefits of connectivity compared with isolated systems must be carefully planned and managed throughout the lifecycle of the system and its component assets to balance the risk posed by that same connectivity lest it also present a significant cyber security risk. Particularly in existing systems with legacy assets which may not have robust built-in security.
Interconnection may also be to the public Internet providing external access to ICS assets. The recent pandemic saw a sharp rise in remote access technologies being rapidly implemented for both business and process systems. Without continual management, boundary systems like these become insecure and can essentially leave the front door open to attackers.
Studies of vulnerability disclosures in several popular remote access products revealed a worrying number of vulnerable systems publicly detectable on the Internet, sometimes years after the vendor had released updates indicating that some organisations are failing to understand and address even basic best practice in their high-risk assets.
Q. What advice can you offer about securing converged IT/ OT networks?
Heer points out that converged IT/OT networks are often a mix of different systems with different communication protocols and software. Attackers can choose the weakest link in the chain and pick the most vulnerable devices if their communication is not restricted. Hence, converged networks require a restrictive planning of communication capabilities and access. Having just one big connected component almost guarantees security problems. Introducing additional zones and firewall rules between these is key to creating a resilient industrial network. By segmenting a network into
different zones, Heers says that the possible communication peers of a compromised device are limited. Having tightly controlled passages between the zones, for example by using restrictive firewall rules, also helps to block malware from spilling over from the more IT-friendly and open parts of the network.
Keeping the attacker away from the vulnerable parts of the plant is much easier if there is a good zones-andconduit concept. This has been the most important countermeasure against the current rampage of ransomware that caused havoc at numerous industrial sites. Keeping devices apart that don’t need to communicate means keeping existing known or unknown vulnerabilities inaccessible from each other.
This concept of zones-and-conduits is so important that it has become a core part of ISO/IEC 62443 which provides guidance to operators, integrators and vendors on how to shape a secure industrial site. Heer’s advice is to embrace this standard. If you don’t intend to use or implement it, then at least implement the concept of zones and conduit by segmenting your network into different independent zones to block or slow down attackers that get an initial foothold in the network.
Bullock points out that industrial security must be holistic. It should extend from the enterprise through the plant level and even out to end devices, and address risks across people, processes, and technologies. It should involve collaboration between IT and OT personnel. Both sides have vital roles to play in establishing a secure network architecture. He says that a fully connected enterprise requires a comprehensive approach to security. A complex, interconnected system includes challenges. It is critical to understand the potential risks and start building security into industrial automation control systems. However, before any security can be defined, it is important to establish responsibility. Knowing who
Securing converged IT/OT networks
Martin Jenker, head of cybersecurity at MOXA, offers advice about securing converged IT/OT networks.
The gap between the IT and OT domains has to be bridged. To enhance operational resilience, OT networks must ensure their cybersecurity measures are as mature as those utilised in IT networks.
Step 1: Manage your OT networks
You cannot protect assets you do not know you have. So, the first step to enhance operation resilience requires OT operators to monitor everything on their networks in a similar way to how IT network administrators often have complete visibility. Is everything that should be on your OT network there? Is there anything on your network that should not be there?
For example, OT operators can start to determine who can and cannot access the network by leveraging ACL or other authentication mechanisms. Furthermore, there are simple mechanisms that OT operators can set up to define which PLC can be connected to the network by port access control or sticky MAC. In other words, everything on the trusted list is allowed to go through the network, and anything not specified on the trusted list is blocked. Managing your OT network, instead of relying on the IT department, also allows OT operators to respond more quickly to downtime and troubleshoot issues more rapidly.
Step 2: Segment your OT networks
Unlike IT networks that can be segmented by dividing the network into different departments with their own set of permissions, OT networks are essentially one giant Intranet where everything is connected. This makes OT networks more difficult but still not impossible to segment. There are two ways for segmenting an OT network:
• Vertical segmentation involves adding an Industrial Demilitarised Zone between the IT network and OT network. Although this separation should be
has responsibility is key to starting the process of securing converged IT/OT networks. Whether that be individuals, job roles or departments, having that ‘chain of command’ in place means that the overall security program will be correctly structured and defined.
Bullock goes on to point out that developing and implementing an effective industrial security program first requires an understanding of the risks and areas of vulnerability
mandatory, many companies still have not segmented their OT networks from their IT networks.
• Horizontal or lateral segmentation involves creating and separating cells, zones, and sites on the OT network. A cell is essentially a tiny place where all equipment is stored, such as a cabinet. Several cells can form a zone, and multiple zones can form a site.
Segmenting OT networks using either method, or both, allows operators to prevent cyberthreats from spreading to other parts of the network.
Step 3: Patch vulnerabilities
As equipment and devices running on OT networks cannot be upgraded or replaced as frequently as endpoints on IT networks, OT networks still have many legacy devices. Some of them may even be running on obsolete operating systems like Windows 95. Many legacy OT devices remain unpatched and are relatively easy for hackers to exploit. If no patch is available from the original equipment vendor, consider inserting compact industrial IPS devices in front of legacy devices. This creates a ‘virtual patch’ protecting unpatched devices against known exploits.
Step 4: Secure remote connections
Protecting the data that is transmitted from the plant or remote site back to the monitoring and control center is crucial. Ensure that each remote connection to the OT network is authenticated and encrypted. Authentication verifies the identity of the user requesting access whereas encryption ensures that the data transmitted is securely encoded and cannot be easily deciphered by prying eyes. Besides managing and segmenting OT networks, OT operators also need to ensure their systems are properly patched and remote connections are secure. These steps not only help reduce the gap between OT and IT departments, but also protect industrial control systems, which are increasingly being connected to the Internet, from cyberattacks.
that exist within the organisation. A security assessment’s deliverables should include at a minimum: An inventory of authorised and unauthorised devices and software; Detailed observation and documentation of system performance; Identification of tolerance thresholds and risk/vulnerability indications; Prioritisation of each vulnerability, based on impact and exploitation potential.
Corner says that, when interconnecting a system it is crucial that operators
ensure they have a suitably detailed and clearly documented understanding of that system, its functional requirements, components, and their behaviour. Some vendors offer products to assist in this process which can be helpful at a large scale, but its equally practical for experienced persons to conduct a deep dive using common free tools, like Wireshark, to establish an accurate record of the physical and logical topology of the system, its
configuration, and ‘as fitted’ behaviour from a network communications perspective.
It is important to survey physical and logical aspects, this forms a basis for identifying and addressing cyber risk and often also identifies potential operational resilience deficiencies, this can include damaged communication cables, failed power supplies, lack of configuration backups, and incorrect configurations.
Using this data it is then possible to create a baseline of the required core functionality and then implement controls that restrict access to the minimum required, this can includes segmenting the system to control the logical flow of data (an IEC 62443 aligned zoning approach) and also implementing robust identification and authentication of individuals, allocating the least privilege possible. For external facing systems like remote access, multifactor authentication is an absolute must.
Q. Can you offer an overview of OT security best practices for control engineers?
There is a plethora of security best practices to follow, says Heer. They can be best categorised as IT-like or OT-like security best practices. Overall, this is a set of important measures to keep everything clean, simple and to avoid complexity. This must be done
regardless of having a converged IT/OT network or not.
The technological push and innovation in security is coming from the IT side, though, explained Heer. In recent years we have seen more successful applications of security information event management (SIEM) systems, log management solutions, network access control and intrusion detection systems to identify attackers and efficiently manage the flood of available data that could or could not hint at the existence of an attacker. These technologies have benefits and disadvantages. As a benefit, many systems make managing security more efficient.
However, they are often complex and require special skills. So, choosing the tools carefully is important to avoid headaches.
Making sure that security can be checked and improved is probably even more important than any of the technical systems and this starts with someone who is responsible for taking care of security. Assign someone the task and make sure they have the time and the knowledge to really do it.
Next, Heer recommends taking one of the relevant security standards appropriate to the sector. A good standard provides enough abstract advice on security best practices so that you can get the actual work going. Get accustomed to what’s required to fulfill it even if you don’t plan to implement it.
Finally, he says, decide what makes sense for you. Focus on responsibilities and process first, instead of prioritising a technical solution. When starting out, working with processes and with humans provides the best leverage. Also, be sure to formalise and document these processes. The more precise you can describe what’s intended to happen in a plant in policies and procedures, the better you can defend the site or detect dangerous misbehaviour.
According to Bullock, industrial security is best implemented as a complete system across all operations. Defense-in-Depth (DiD) security supports this approach. Based on the notion that any one point of protection can and likely will be defeated, DiD security establishes multiple layers of protection through a combination of physical, electronic and procedural safeguards.
A DiD security approach should consist of six main components – policies and procedures, physical, network, computer, application and device.
Policies and procedures play a critical role in shaping cultural behaviours to follow good security practices and confirming the appropriate security technologies are used.
Physical security should limit personnel access to not only areas of a facility but also to entry points on the physical network infrastructure, such as control panels, cabling, and devices. At the facility level, access control technology

such as networked key cards can help restrict access to the plant floor, control rooms and other areas to authorised personnel only.
A network security framework should be established to help safeguard the network infrastructure against cyberattacks. This requires close cooperation between IT and OT, including a robust discussion about the technologies and policies needed to best protect the assets and ability to innovate. One of the technologies discussed should be an industrial demilitarized zone (IDMZ), which creates a critical barrier of protection between the enterprise and industrial zones. Segmenting areas of the plant floor into virtual local area networks (VLANs) is a good security practice at the network level. Firewalls with intrusion detection and prevention systems (IDS/IPS) should be deployed within and around the industrial network to manage and limit network traffic.
Security patch management should be established to track, evaluate, test, and install cybersecurity software patches. Authentication, authorisation, and accounting (AAA) software can restrict and monitor application access and changes. Antivirus software, application whitelisting and host intrusion-detection systems can further harden computer assets.
Security devices should also be incorporated at the manufacturing

or industrial application level as part of a DiD approach. A role-based access control system can restrict access to critical process functions or require operators to enter log-in information before they access applications.

Device authentication and unauthorised device identification can help make sure only trusted devices are used. Additionally, changing the outof-the-box default configurations for embedded devices can help make them more secure in areas such as restrictive access and change management.
Corner’s advice is to look closely at maximising the use of built in security features of components before augmenting them with additional controls to provide DiD. This requires an appreciation that commodity components are likely to exhibit insecure characteristics by default. Integrators and operators are increasingly looking to accredited vendors showing a ‘secure by design’ principle, but do not necessarily appreciate the limitations. Accreditations are often achieved by a product disabling all features by default. This doesn’t mean that insecure features cannot be configured, so it’s vital to
ensure these products are also used in a way that is ‘secure by integration’ and ‘secure by operation’.
There needs to be a commitment to build and maintain a deep understanding of the operation of components in use and their technical principles, achieved through training and experience.
Organisations should maximise the use of specialists from both business and process teams where possible. Their ICA engineers will have an innate understanding of the process requirements but even at their most capable are unlikely to be as experienced in communications networks or servers as their IT counterparts. Fostering cooperation and collaboration at all levels is crucial. Bilateral peer mentoring is an effective approach to achieve though pairing up enthusiastic individuals from different specialisms to share their knowledge and experience. plus-circle
THE CONVERGENCE CONUNDRUM

What does OT/IT convergence mean? In the OT/IT cyber workspace there are two types of company – those seeking to converge and those that have never diverged. Both must change and both must face similar risks. But their circumstances and their means of addressing the risks may be vastly different as the following examples illustrate.
What sort of companies are they?
Company A, which is seeking to converge, is a large company operating multiple sites and with multiple complex manufacturing processes. The network is currently segmented to provide complete segregation between OT and IT – theoretically ‘air gapped’, or at least with one or more firewalls between OT and IT. Perhaps 20 years ago the company reviewed OT/IT security and decided that this was the safest approach. However, today it is no longer the case. For this business model it makes sense to have a complete overview of the chain of manufacturing from order placement for goods-in to order fulfilment for ‘widgets’ or ‘gloop’ -out.
Company B has never diverged OT and IT, being medium sized, it has embraced technical innovation through greater use of IT, which spills over into use of smarter machines and sensors in the manufacturing environment. For this company it makes sense to connect machines to the IT network to extend control and monitoring to a remote location or to make use of maintenance tools. The company has a flat and undivided network because it grew that way. It has a firewall where its Internet Service
Provider (ISP) provides service, so all is good (or so it seems). But it isn’t.
The threats
The threat landscape has changed so much in recent years that the probability of attack is essentially random and high. That means that it is now necessary to create as many barriers to attack as possible.
Company B needs to be aware that the firewall at the ISP access point has very limited capabilities and is only fit to protect the IT environment – it has no knowledge of the protocols used by OT equipment. As if that were not bad enough, the defenders need to be aware that if their perimeter defences are penetrated – due to a phishing e-mail – any malware installed would be free to attack the OT equipment which is generally not robust to attack. Divergence is needed! At least to the extent of getting an extra firewall to separate IT and OT. It would be wise to start monitoring network traffic too.
Company A has a ‘convergence’ project to migrate much of the IT and OT infrastructure to the cloud, which is fine if done with appropriate safeguards. Those safeguards, for both supplier and user physical assets and management processes, include providing adequate
diversity and redundancy, avoiding single points of failure, minimising pinch points, and wargaming some realistic scenarios. These things should be done before placing contracts! If the service provider – a high value ransomware target – is attacked and cannot provide service at any level then what is the fallback position?
Problem areas
Although the solutions are different there are some points of common difficulty. What have they got that they actually want to change? It is easy to overlook that a complete, thorough, as built inventory is needed, including all connections (physical and logical) and data flows with the reasons for them. Many organisations struggle with this – it is not a small task. Some of it can be automated – the ‘What’. ‘How’ is a little harder, ‘Why’ is harder still. There is no shortage of guidance about what a target secured network design should look like for various cases but it doesn’t tell you how to get there from where you are now. The problem is that no one but those intimately involved can define that journey. plus-circle
Although a lot is being said about the pro’s and con’s of Operational Technology/ Information Technology (OT/IT) convergence, there is often little appreciation of what companies at different stages in their evolution may need to do, argues Edward Kessler.HART-IP Packet Structure.
Physical Event








SECURING YOUR OT NETWORK
In December of 2015, at 3:30pm, workers of the Prykarpattyaoblenergo control centre – an electricity distribution outlet for the Ivano-Frankivsk region of Western Ukraine – were preparing to wrap up their day and head home for the evening. That was until one worker noticed his cursor jump across his screen of its own volition. He then watched helplessly, as his mouse was unresponsive to any of his own inputs, as whoever was operating it clicked to take one of the substation circuit breakers offline, instantly dropping electricity distribution to an area just outside the city, home to around a thousand residents.
Then they switched off another and another. And then another 27. In total the hackers switched off 30 circuit
breakers at the control centre, but they didn’t stop there. They hit two other distribution centres in the city until more than 23,000 residents were left without power.
It wasn’t that the control centre’s operational technology security was more lax than others, nor was it particularly substandard. It could even be classed as a little more robust than that of some centres in the UK and the US, but in the end, it simply wasn’t secure enough.
The term Operational Technology (OT) defines a setup of both hardware and software used to monitor and administer physical devices, processes and events. SCADA systems are one of the archetypes of these systems, and one of the most popular, which are used to operate machinery and
monitor temperatures and outputs in industrial environments.
It’s clear that if hackers can gain access to these systems, they gain access to any machinery connected to them.
When hacks affect physical machinery things can become dangerous. Imagine a metal pressing factory, with numerous stations of heavy machinery slamming and punching thick metal into useful shapes. Even in the hands of a skilled labourer these machines are dangerous. In the hands of a remote hacker, with intent known only to themselves, they can become deadly.
Halting production by shutting down a robot on a production line is costly and inconvenient to the company. But should the hacker take control of and

disable something like a pressure release valve on a gas tank installed on an offshore oil rig, the consequences could be disastrous.
Securing your OT network?
There are many aspects to an OT network that don’t just fall under the hardware/software umbrella. Physical security and policies and procedures are just as important.

For instance, it’s great to have a stringent password policy but if a person can simply walk up to a device and pull the power cable, or insert a USB containing malicious code, passwords and security policies become redundant in an instant.
Having policies in place for access rights, encryption policies, passwords, and having procedures for hardware configuration and network segmentation, all contribute to securing the network. The IEC 62443 standard sets some minimum configuration parameters with regards to password complexity, encryption, disabling unsecure protocols etc, which many networking products are certified to.
But, if anyone has physical access to these systems, they do no good at all.
Locking devices up behind some form of physical barrier removes the threat of these simple denial-ofservice attacks. It seems simple, but it is surprising how many companies are blasé about the physical protection of their most vulnerable computing assets when the solution is so cheap and simple to implement.
Firewalls are another mainstay of OT and IT security, but as more physical devices are connected to the internet, the need for more robust security measures has pushed the possibilities of what can be locked down, and how. We now see Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) make headway into the OT networks — systems that continuously analyse the packets flowing through the network and scan for malicious activity. Depending on the security policies of the network, this malicious activity can either prompt a notification to network engineers or be ceased completely.
In summary
As industrial systems become more connected – be it to the cloud or otherwise – the need for all these elements to work together becomes more important. Where we can never be 100% secure, due to the constant evolution of hackers and their tools, we can at least secure our OT networks to the point where they are highly locked down and a deterrent to hackers. plus-circle
robots
Designed for use with our single-arm YuMi®, GoFa™ and SWIFTI™ collaborative robots and IRB 1100 industrial robot, Wizard Easy Programming makes setting up and operating your robot easier than you can imagine. Featuring a block-based easy graphical interface, the Wizard software enables even total beginners to get a robot up and running in minutes, helping your company to find new ways to grow with robots.
To find out more visit http://bit.ly/ABB_Wizard or scan the QR code
Take your first steps to robotic automation –no coding skills needed Introducing Wizard Easy Programming – the simple way to grow with
DIGITAL TWINNING OF THE SAFETY LIFECYCLE
Engineering designs for functional safety instrumented systems (SIS) used in the process industry are typically thorough, detailed, and are prepared following a safety life-cycle process. This standard is internationally known as IEC 61511.

In a non-digitised execution model, a great deal of valuable information becomes stranded. Traditionally, different teams create the documents, using separate tools with varying formats, to produce the required functional safety basis of design.
The hypothetical scenario that follows illustrates a common challenge:
A chemical company has had an unplanned trip in one of its process units and the team is trying to understand the root cause. Upon investigation, the team observes the activation of a high-temperature interlock in one of the distillation columns, but the root cause is not yet clear.
Plant management requires a restart to production as soon as possible. However, to do that the operations team needs to review the latest Process Hazard Analysis (PHA) report to understand what the associated risks are due to high temperature (HT) and they need to assess the options available to restart production in a safe manner.
The operations team does not have immediate access to the latest PHA report. In order to make a timely decision, the operations team would want to consider the following:
• Was the process unit trip based on a real demand or a spurious trip?
• If they bypass the safety interlock, what is the risk gap that will be created?
• When was the last time a similar demand occurred?
• When was the last time the inputs to this safety interlock were bypassed and why?
• When was the last time all the instruments related to the safety interlock were calibrated?
Many operators frequently wrestle with these challenges and, when the situation is further considered, senior management may also want to know:
• How safe is the process unit?
• How many of the safety interlocks are in good working condition, and how many have been bypassed?
• Are there recurring demands of safety interlocks which were not accounted for and if so, why?
All the above questions can be answered using traditional methods and techniques, but it often is time consuming.
Objective
Functional Safety standards recommend a safety life-cycle to analyse process risks, design and implement Independent Protection Layers (IPLs) to mitigate the risks and maintain the IPLs during plant operations to manage potentially unmitigated risks. The objective of the IEC 61511 standard is to manage functional safety throughout the life-cycle. Historically the engineering and operational data would be within disconnected software tools or documents. The aim of digitalisation is to
simplify the ability to manage the data, and not to produce stranded deliverables only reused every revalidation cycle. The benefit of digitising data management is to enable an evergreen design basis through which compliance to local and industry regulations can be quickly demonstrated at any given time. Further benefits include the ability to access the data regardless of geographic location.
Recommended solution
A digital twin can provide a comprehensive software package that can import existing engineering documentation for any of the phases of the safety life-cycle as well as having the capability to execute the steps of the safety life-cycle. Using the previous HT scenario, a digital twin would facilitate safety life-cycle implementation using features such as:
• Analysis modules like Hazard and Operability (HAZOP) and Layer of Protection Analysis (LOPA) to examine the process unit’s risk and recommend
Prasad Goteti and Steve Lindsay explore the benefits of digitally-twinning safety instrumented systems which are responsible for the operating safety in the process industry.
IPLs to reduce the risk to acceptable levels.
• Engineering modules to design and implement IPLs like Safety Integrity Level (SIL) calculation engine, cause and effect chart generation and functional test plans to validate the Safety Instrumented Functions (SIF).
• Operational modules to consolidate relevant operational data related to the IPLs on a real-time basis like IPL demands with timestamps, stroke time of valves during a demand, time in bypass for each IPL and others.
• Maintenance and inspection modules to record test results and ‘as found and as left’ information for IPL components.
The digital twin produces a centralised platform to digitise the data, execute the life-cycle steps while providing user/rolebased access for process safety, functional safety, operations and maintenance engineers and management.

Why use a digital twin?

The digital twin provides a simplified and consistent method to realise the following benefits:
• It produces dashboards by comparing design assumptions with operational data to generate relevant KPIs. These KPIs can be used to repair bad actors either in the running plant or on the drawing board. KPIs can be developed for normal plant operation and maintenance, management reporting as well as incident investigation.
• All phases of the safety life-cycle are digitised and easily available for user access. Digitised and evergreen data also means that all the steps of the safety life-cycle are current.
• It creates and models offline ‘whatif’ scenarios in any part of the safety life-cycle and sees the effect of a modification ripple down.
• It provides an automated interface to other industry design packages such as Computer Maintenance

Management System (CMMS). Automated interfacing helps reduce both systematic and human error in data transfer.
• It enables digitised data entry which creates potential cost savings through all phases of the life-cycle.

• It continually validates design assumptions to actual performance, which leads to enhanced confidence among all users for risk management.
The digital twin creates an ability to focus on the design rather than creating design deliverables. It seamlessly connects the basis of design to the source of truth (the operational performance of the IPLs) on a continuous basis allowing generation of real-time KPIs. plus-circle
Prasad Goteti is safety engineering consultant at Honeywell Process Solutions and Steve Lindsay is a business development director at Honeywell Process Solutions.
Turck Banner’s wireless part counting solutions enable our customers to deploy intelligent lean initiatives by providing the means to accurately measure, analyse and optimise their OEE performance
HAVING IT ALL!
While digital transformation sounds great on paper it isn’t always straightforward in practice. When it comes to process safety – the discipline for safe operating systems and processes of hazardous substances and environments – it is more complex.

In many industrial settings, going digital can pay huge dividends – helping to improve productivity, encourage collaboration, streamline workflows and enable better asset management thanks to faster, more accurate monitoring. Above all, it paves the way for Industrial Internet of Things (IIoT) technology, big data analytics and improved operational efficiency across entire facilities.
According to McKinsey & Company, the Covid-19 pandemic caused consumer and business digital adoption to leap forward by more than five years in a matter of weeks at the beginning of 2020.
However, many industrial and manufacturing plants were not built with digitisation in mind. Many deal with hazardous substances or contain restricted zones with dangerous explosive atmospheres. As a result, these areas have long been designated ‘pen and paper’ zones. But, as more organisations look to achieve true digital transformation, there is a need to find a way to accommodate devices in such locations without putting employees in danger.
Every explosive atmosphere is unique and must be treated accordingly. Under the ATEX classification, no two explosive atmospheres are the same. Zones containing gases/vapours are assigned a rating between 0 (an explosive mixture is continuously present or present for long
periods) and 2 (an explosive mixture is not likely to occur in normal operation and if it occurs, will exist only for a short time). Similarly, zones containing combustible dust or fibres are rated between 20 and 22, based on the same criteria.
Each ATEX level has guidelines around the safety measures that electronic equipment must meet. For example, a zone 0/20 device requires more stringent safety features than those in zone 2/22. Organisations must ensure that only devices with the corresponding ATEX certification enter that zone.
Meeting the challenge
In response to growing demand, mobile device technology has evolved significantly in terms of design, manufacturing and testing in recent years. Today it is possible to choose from a range of versatile and cost-effective ATEX certified commercial off-the-shelf (COTS) solutions with inbuilt intrinsic safety technology.
Features required for ATEX zone 2/22 certification – such as temperature control, port protection, and double fault circuitry – are also much more readily available on devices from rugged manufacturers now, either as standard or as optional extras. This makes it easier to meet the standards required within budget.
Functionality has also improved
significantly. In the past, many ATEX certified devices were cumbersome and outdated right out of the box. Today, the biggest trade-offs tend to be a slightly dimmer screen (due to lower energy output), lack of interchangeable battery (because the device is completely sealed), and a small weight penalty (caused by the addition of intrinsic safety features). Even devices specifically designed for more stringent ATEX zones 0/1 are now incredibly capable, offering a wealth of productivity features alongside strict safety requirements.
As the need for digital transformation continues to gather pace digital devices are finding their way into a wide array of locations where previously they were forbidden. While this represents a positive step, in terms of productivity and operational efficiency, it also introduces a level of risk that must be properly addressed in order to ensure worker safety and regulatory compliance. The growth of ATEX certified, intrinsically safe devices has taken much of the pain out of workflow and procurement processes. However, with so many options now available, it is crucial that organisations take the time to research the right devices for their needs before making a purchasing decision. plus-circle
Digital transformation and process safety don’t have to be mutually exclusive argues Sophie Silk.





WIRELESS CONNECTIVITY: TRENDS AND CONSIDERATIONS
Advances in wireless network speed and reductions in latency over the past couple of decades have fundamentally altered communication globally. Wireless cellular technology has moved from 3G at 20 Mbit/sec speed in the 2000s to 5G at up to 20 Gbit/sec speed today, with generational advances taking place approximately every decade. The past three WiFi specifications have been released about five years apart, with WiFi 4 allowing download speeds of 600 Mbit/sec and WiFi 6 enabling speeds of up to 9.6 Gbit/sec.
While the generation advancements for both of these technologies have taken place at a constant linear rate, the speed has increased at an exponential rate. This dramatic decrease in communication time has enabled remote connectivity of machines such as palletisers in packaging facilities and isolated instrumentation in oil and gas fields to allow remote monitoring for maintenance support as well as plant wide networks in automotive for advanced diagnostic analysis.
Wireless communication initially enabled voice for business, then grew in capability to transport data for business and automation, including video, and finally is poised to be a viable solution for control in automation, especially with private and hybrid network option availability for 5G. The next frontier in the continued progression of wireless networks is widespread control in both discrete and process environments, which will get a significant jumpstart from the new 5G and WiFi 6 technologies.
Automation considerations
Wireless communication in an automation environment brings a host of additional opportunities and challenges. Some of the benefits include potential savings in installation cost due to not having to install physical cable, increased connectivity of devices and instrumentation, and decreased challenges in routing cables in environments with a high degree of movement. However, challenges such as safety, security, and physical location must be addressed in order for wireless to be truly viable in automation control applications. Security is a critical concern since a new exploitation opportunity can open up from outside the walls of a factory or gates of a plant with wireless. Stray signals can be mitigated with radiating cable and smart placement of the antennae. However, it is important to authenticate transmitting nodes, to encrypt traffic, and to ensure that configurations cannot be changed without a password or key. As part of a defense-in-depth solution, device and edge control level automation traffic can be further protected via solutions such as the CIP Security network extension for EtherNet/IP.
Safety is another critical aspect for wireless, especially for mobile vehicles, machinery with motion, and locations where workers can come into contact with potentially dangerous movement. Safety design for electronics is guided by IEC 61508 and IEC 62061, which specify how to apply failure mode analysis, continuous diagnostics, and other robust design practices for electronic system safety. Additionally, IEC 13849 covers the
same design safety approach for electromechanical systems. To meet these standards, many industrial safety systems leverage the black channel approach. This concept requires safety devices to have enough compute, intelligence, and diagnostic capability that the entire communication network has zero impact on the ability of the safety devices to detect communication errors. This means that the physical transmission medium is just another part of the black channel. Application layer safety solutions, such as the CIP Safety network extension for EtherNet/IP, can provide fail-safe communication between nodes such as safety I/O blocks, safety interlock switches, safety light curtains and safety controllers in both machine and process automation safety applications up to Safety Integrity Level (SIL) 3, according to IEC 61508. Finally, distance, obstacles, and interference must be considered for wireless control applications. It is important to ensure that distance is minimised, that line of sight is maintained, and that interference from high voltage and other sources of high frequency signals are minimised. Interference can result in wireless networks having higher packet error rates and reconfiguring themselves more frequently than wired networks, which can create delayed and lost packets as well as connection timeouts. These transitions can potentially disrupt automation applications, depending on the speed that is required. Wireless repeaters are an option to help increase signal strength and overcome potential interference.
Well designed systems, which take into account the physical environment, safety, and security, will help make wireless control the new normal in factories and plants around the globe.
Wireless application examples
A clear example of the value of wireless control is for Automated Guided Vehicles (AGVs) that transport materials around a factory or warehouse. It is costly to create a physical track on the floor for an AGV to travel on and this cost multiplies when process changes require new layouts. Welding cells within automotive plants have also adopted wireless control in order to remove some of the challenges of running cables in tight spaces with a high degree of movement. Process automation has long leveraged wireless control for connectivity between remotely located and spread-out instrumentation that are a part of wind farms or oil and gas fields. Additional possibilities include using less cable for hygienic design in food and beverage applications, modular and flexible plant design to prepare for Industry 4.0, and adding data collection sensors to legacy devices for IIoT analysis.
EtherNet/IP over wireless
The EtherNet/IP industrial communication network communicates data between devices and instruments at the application layer of the ISO/OSI model, using the Common Industrial Protocol (CIP). CIP information is then encapsulated in the transport layer, which uses either TCP for larger data packets such as diagnostics or UDP for smaller, more time sensitive data packets such as I/O for EtherNet/IP. At the network layer, logical addressing Internet Protocol (IP) information is added to make the packet ready for network access. In the datalink layer and the physical layer, the packets are converted to the transmission media. This approach of communicating data via CIP, independent of the transport, network, datalink or physical layers, makes use of different transmission media possible. Therefore, EtherNet/IP can be used across copper, fibre, and wireless to provide users with a high
flexibility for use across numerous industrial applications.
The path forward
The industrial space has already been experiencing the advantages of diagnostic information via wireless for some time and is now set to engage in a significant shift to using wireless for control. Technologies such as 5G and WiFi 6, among others, will help drive the increased speed and reduced latency that industrial applications demand. EtherNet/IP will be one of the key industrial communication protocols that will enable this change due to its media independence enabled by CIP communication. plus-circle
Read the ‘CIP Safety: Wireless Functional Safety’ whitepaper at: https://www.odva.org/technologystandards/document-library/ to learn more about CIP, EtherNet/IP, and CIP Safety over wireless.
SELECTING THE RIGHT WIRELESS SENSOR NETWORK
Jonas Berge outlines the importance of selecting a wireless sensor network that can meet the demands of your process application.
In 2009, NAMUR, the international association and standards body for automation technology users in the process industry, produced the NAMUR NE124 recommendations, which define requirements for wireless standards technologies, the technology employed, and solutions from different manufacturers to ensure the necessary functions for sustainable use to be practical in the process industry is provided.
Probably the most important requirement for data networks is reliability. Although a figure is not stated in NAMUR NE124, from my experience, greater than 99% reliability is needed to ensure data is available when required. Most wireless technologies do not provide a reliability figure, probably because it is much lower than 99%. The reason for this is that plants present challenging environments for wireless, with permanent steel infrastructure, such as furnaces and storage tanks, and heavy vehicles and shipping containers that change position, all preventing radio transmission.
Most wireless sensor network (WSN) technologies use a star topology, with point-to-point communications and a clear `line-of-sight’ required between the gateway and every sensor. In a typical plant, this is problematic, requiring additional gateways that add cost. Some WSN technologies use a star topology, but with a backbone to create many sub-networks, each with an intermediate backbone router. The drawback here is that the backbone network and power may need to be installed in a hazardous area, increasing project complexity and cost.
WirelessHART uses a mesh topology,
whereby a sensor without line of sight with the gateway communicates with a neighbouring sensor, which then relays the communication to the next sensor and so on until it reaches the gateway. This enables data to be routed around metal obstacles. If there is a weak spot in the mesh topology, a repeater is used, with no need to install additional gateways, a network backbone or power cabling. Sensors communicate to many neighbouring sensors and this forms a mesh of connections, with multiple paths from each sensor to the gateway. Data path redundancy is the key to maximising reliability.
WirelessHART is also self-organising, with no need for manual configuration of communication paths between sensors. The mesh network forms automatically. Moreover, the selforganising mesh adapts dynamically. If a sensor is moved, runs out of battery or is obstructed, the system dynamically chooses an alternative path to route data. As a result, WirelessHART achieves 99% reliability. NAMUR NE124 does not specify the need for a specific range from a sensor to gateway. Rather than the range from gateway to sensor, what matters is the depth – the maximum number of hops in one communication path. WirelessHART can perform seven hops or more which allows it to reach sensors installed deeper inside plant units than other technologies can. As a result, this gives WirelessHART the longest effective range and greatest coverage inside a plant.
Real-time performance
Wireless sensors are mostly used in applications that are not time-critical – such as to help eliminate manual data collection. For these applications,
an update period of one minute, one hour or even one day are fine, but for other use cases an update period of one second may be required. Many WSN technologies only support update periods of one minute or longer, which means they are unsuitable for these applications. WirelessHART offers realtime capability, with update periods of one second for applicable sensor types.
WirelessHART helps to maximise battery life with time-synchronised communication. The sensor sleeps to conserve battery, wakes up briefly to make a measurement, then goes back to sleep again. As a result, it is possible to achieve a battery life of between 5 and 10 years for sensors, helping to lower total cost of ownership.
Security
The various WSN technologies all have similar security mechanisms, but differ in terms of ease of commissioning sensors. For several WSN technologies, configuring the security credentials is very time-consuming and involves multiple steps and special tools. Even for sensors using the same technology, the tools and procedures differ from one sensor manufacturer to the next. For WirelessHART, commissioning is simplified using HART field communicators or HART modems. Instrument technicians will be very familiar with these tools used for existing 4-20 mA/HART instruments.
Multi-vendor interoperability
There are WSN technologies that look open, licensed to several manufacturers, but in fact are not an IEEE or IEC standard, instead being owned by a single company. Proprietary technologies always have associated
risk. WirelessHART is an international standard, IEC62591. Standardisation dramatically reduces risk, which is why instrumentation and control engineers specify IEC standards for all electrical and electronic equipment including WSNs. WirelessHART is supported by multiple vendors, with interoperability ensuring products from different vendors will work together. It also has universal and common practice commands used by all vendors. Interchangeability allows failed sensors to be replaced with sensors from another vendor and to work without system reconfiguration.
Users need to monitor the selfdiagnostics in the sensors. Most WSN technologies do not have a common backhaul network application protocol for sensor configuration and advanced diagnostic data. As a result, sensors cannot be integrated into a plant’s existing intelligent device management (IDM) software. WirelessHART solves this with the HART-IP application protocol over Ethernet. HART-IP is used for the backhaul network to bring sensor configuration and advanced diagnostics data into the plant’s existing IDM software. HART-IP supports EDDL (electronic device description language) and FDI (field device integration). This means that all types of WirelessHART sensors can be managed from the same software used for the plant’s existing wired devices. Even IDM
software, based on FDT/DTM (field device tool/device type manager), can be used to manage WirelessHART sensors.
Portable tools
Several WSN technologies have no common method of bench or field configuration and calibration. Even for the same technology, manufacturers have different ways of configuring their sensors. Managing a variety of portable tools in such a heterogenous environment causes delays. A direct interface for a portable calibrator is not supported. In addition, some sensors cannot be calibrated or `trimmed’ to correct for long-term drift, and once no longer accurate, they must simply be thrown away. WirelessHART solves this with a wired HART console port. HART tools widely used in plants, including HART field communicators, HART modems and portable calibrators, can all be used.
To achieve the desired operational improvements, wireless sensors and applications cannot be isolated islands of automation and must integrate with the existing automation systems. Because many WSN technologies don’t define a standard application protocol with a common message format or data types, the wireless gateway does not convert sensor measurement data to Modbus or OPC and cannot be easily integrated. This makes it hard
to put that data to good use. Some WSN solutions are for a single use-case, which creates the situation where you have multiple heterogenous systems with multiple software to monitor each application.

WirelessHART uses the standard HART application protocol, which has a common message format and common data types for all WirelessHART sensors, regardless of manufacturer and sensor type. This enables WirelessHART gateways to convert standard data, from a mix of sensors from multiple vendors, to common industrial protocols, such as Modbus, EtherNet/IP and OPC. As a result, data can be integrated with existing systems like the plant historian or control system, without custom programming or scripting. It is then available to produce analytics, dashboards, reports and notifications.
Some WSN technologies only transmit measurement and status data, no detailed diagnostics like a vibration spectrum or waveform is available, or requires scripting to be decoded. WirelessHART provides advanced diagnostics communicated by requestresponse as a non-real-time `second channel’. This enables advanced diagnostics like a vibration spectrum or waveform to be analysed centrally. plus-circle
WIRELESS TO THE LAST MILE
Alexander Weber discusses the beneficial relationship that IO-Link Wireless and 5G can offer in industrial applications.
Wireless applications have become an indispensable part of our everyday lives with users no longer being concerned about how these wireless connections are established and whether they are stable. It is only when the connection is interrupted that we take a closer look at the technology.
In industrial environments, however, wireless technology is still met with some reservations, primarily due to the need for high machine availability.
However, with wired solutions machine communications cannot be physically tested, which means that a potential failure quickly becomes a challenge. Collision of the packets with relevant information from other packets in the same frequency band, as well as shielding/reflection of the nodes by components in the immediate vicinity, for example, can occur. This can result in a communication breakdown
and a possible control malfunction. Traditionally, such problems have been difficult to prevent using, often proprietary, wireless technologies. This has also hindered the adoption of wireless components in industrial automation.
However, it is in precisely these situations where the call for wireless applications is getting louder today. What is needed are industrial standards that offer users the greatest possible flexibility, diversity and scalability. Many wireless networks cannot meet the requirements for reliability, device density, installation effort and physical dimensions, which is why they are rarely used.
A recently study from HMS Networks, with a representative survey of 50 international industry professionals, (https://www.hms-networks.com/ industrial-iot-solutions/5G/ready) found that wireless applications for remote
monitoring and remote control of equipment are already being used by over 54% of the respondents to the study, while 48% of respondents also claimed that they are positive about 5G and would like to use this technology instead of the unreliable Wi-Fi and its various industrial derivatives.
In the context of 5G (Ultra Reliable and Low Latency Communication), however, another standardised wireless technology – called IO-Link Wireless – should also be mentioned. Both standards in coexistence create a great added value and potentiate each other’s respective areas of application.
IO-Link Wireless is a standard that was defined specifically for factory automation. It provides a reliable, real-time and deterministic protocol for control systems in industrial factory automation. It adds wireless transmission links to the classic wired cables in industrial control applications,

increasing mobility and flexibility and elevating plant communications to the master level of automation.
In parallel, companies are starting to market various 5G-based products and services as part of the fourth industrial revolution. In this context, the 5G transformation is designed to take several years, as production deployments require stable specifications, production-grade implementation, and supportive ecosystems before widespread availability can be achieved.
Implementation considerations
If a wireless communication solution is to be implemented for a machine, several key factors must be taken into consideration:

• Output
• Latency
• Application
• Physical dimensions
• Range
• Costs
• Availability of the frequency spectrum
Indeed, both technologies have their justifications. They cover various application areas within industrial automation technology. As a glance at the automation pyramid shows, they also address very different types of nodes in each case.
IO-Link Wireless (IOLW) is primarily intended for field devices in factory automation that already communicate via IO-Link. It is therefore also a solution that can be spatially limited – used selectively and scaled to transmit the signals of switching and measuring sensors, but also of simpler actuators. Process data of < 2 bytes are processed and forwarded. Since these devices are often lower cost and used in large numbers, the total cost of a system often determines the success of the new technology. In addition, the devices communicate directly with the controller via a node (IO-Link master), which makes a stable and continuous connection from master to device essential. This is also a high requirement for timecritical applications. IOLW is based on the standardised IO-Link technology (IEC 61131-9) and therefore meets these requirements while offering the same high communication stability (Packet Error Rate 10-9) as the wired version. In addition, it is a flexible and cost-efficient solution that can be embedded in an existing infrastructure with the previously used sensors and actuators with little effort.
5G, on the other hand, was designed as a communication medium for field nodes with greater bandwidth. It is a comprehensive network infrastructure designed for a higher level of communication. For example, this
technology is not designed to serve a selective application area due to the licensing costs and the investment in infrastructure. It will typically be found within the automation pyramid at the higher field level, where Ethernetbased nodes are also used, involving, for example, communication between the controller and camera systems, servo motors, fieldbus modules or even data transmission from robots to a gateway. These devices are typically installed in smaller quantities and, due to their complexity, are also in a different price range, which is why the additional costs for the 5G infrastructure of a complete manufacturing environment are less significant.
Because both technologies serve different use cases, they are very well suited to be used within a combined system. The different frequency bands are also not expected to interfere with each other, even if they are not directly compatible. A fieldbus module could act as the hub of both technologies, communicating downward via IOLW and upward via 5G. IOLW can therefore fully coexist with any 5G network. These networks do not contradict each other as 5G focusses on high-end applications with higher data throughput. plus-circle
Good Practice Guidance for Electrical, Control and Cyber Security in Industrial Engineering – Improving efficiency and safety




• Practical guidance for everyday and irregular situations and tasks
• Verified and developed from contributions by the industry, for the industry

• Readily accessible for all in the industry – wherever they are, whatever time they have
• FREE task and procedure checklists

• E-learning for professional development
• Active guidance
CONTROL AND IMPROVE FLUCTUATING PROCESSES
TThe project outcome may solve two challenges – to reduce the release of carbon-rich gases to the atmosphere and to substitute fossil raw materials as a carbon source. To achieve these goals partners from science and industry are developing solutions for the sustainable management of energy and raw materials.

The Kyoto Protocol pinpoints carbon dioxide as a greenhouse gas which heavily influences global warming. This odourless and colourless gas emerges, for example, while burning fossil energy carriers as coal, oil, or natural gas and it is the main contributor to the human-intensified greenhouse effect (anthropogenic carbon dioxide). Various estimates assume a residence time (i.e. the time until natural processes finally remove the CO2 molecule from the
circular economy is the subject of the Carbon2Chem project. Partners from science and industry are collaborating to develop solutions, funded by the Germany Ministry of Education and Research. The aim is to use renewable energies to convert carbon-containing gases from steelworks into chemical raw materials such as methanol. The process needs to be designed so as to flexibly manage changes in loads. At the end, the exhaust gas from furnaces serves as input material for fuels, plastics or fertilisers.
The challenges of these new processes lies in the fact that exhaust gas flows vary – in terms of both their volume and chemical composition. What is more, renewable energies – and the hydrogen they are used to produce – are not uniformly available. However, the
safe, optimal control of these fluctuating
Reliable basis for AI
“In this project, we collect data from multiple temperature measurements and gas analysers and use AI tools to develop a multivariable control system. This leads to a more energy-efficient process, a longer service life for the catalyst as well as improved selectivity and yields,” said Dr. Andreas Menne, head of Low Carbon Technologies department at Fraunhofer UMSICHT. “The data also helps to improve existing process-simulations and kinetic models. Both affect the cost-effectiveness and sustainability of the overall process due to model-based predictive control, predictive maintenance or co-simulation to enable far-reaching optimisation.”
Instrumentation and control systems from Siemens are effectively supporting the progress of developing the
methanol synthesis out of gas streams, which fluctuate in terms of quantity and composition.
Siemens’ scalable and flexible Simatic PCS 7 process control system is installed for process control and visualisation in the project. The data collection of temperature and exhaust gas compositions forms the basis for a downstream, multivariable control solution that is being developed by Siemens together with the Fraunhofer Institute UMSICHT, within the framework of Carbon2Chem. Thanks to its scalable system architecture, Simatic PCS 7 enables cost-effective implementation of dedicated automation solutions and economic operation of processes.
The scalability applies to all parts of the system. The architecture is designed in a way that allows instrumentation and control to perfectly fit requirements. As Dörte Sack, head of Technical Concepts for the Chemical Industry at Siemens in Karlsruhe, explains: “Our technology is very flexible in this respect. The instrumentation and control can be expanded at any time if the plant is scaled up or if there are technological modifications. At the control level alone, multiple compatible automation systems, with appropriate price/
performance ratios, are available to the user. The performance can therefore be optimally adapted to the tasks of the process.”
Accurate temperature profiles
The Sitrans TO500 system uses fibreoptic methods to determine the temperature profiles in a reactor. It enables many temperature measurements to be captured and evaluated simultaneously. Therefore several sensors – Fibre Bragg grating (FBG) – are arranged on a very slim fibre-optic measuring lance.
A FBG is a microstructure typically a few millimeters in length that is inscribed in the core of a standard single-mode fibre. It acts as a resonance structure for the selective reflection of wave lengths: it is a narrow-band filter. Changes in temperature and pressure cause a change in wavelength. To eliminate the influence of pressure, the FBG must not be subjected to strain when used as a temperature sensor. For this reason, the individual optical fibres, which are referred to as lances, are installed in protective tubes (metal capillaries). Due to the measured value transmission (reflection of light) in the same fibre, no additional cables are necessary. This means the cross-
section of the protective tubes for the measurement setup can be substantially reduced.
The transmitter emits light in a range of 1500 to 1600 nm. Based on the reflections of the individual FBG sensors, the system calculates the temperature profile and provides the values via a Profibus interface for evaluation in the control system. This information forms the basis for implementation and optimisation of the processes control as well as for management of the installed assets. Reliable information is vital for realising innovative processes which meet the goals of the Paris climate agreement without jeopardising the competitiveness of energy-intensive sectors such as the chemical, steel or cement industries in Europe. Precise data evaluation in dedicated applications and implementation of the results into improved control algorithms enable economical and sustainable process control. The digitalised plant thus enables industrial applications that advance defossilisation and modernisation in line with the EU Commission’s Green Deal. plus-circle

TESTING THE PHYSICAL INFRASTRUCTURE
The role of Ethernet continues to expand, supporting the high speed transfer of data. Mark Mullins describes some simple cable testing options.
When it comes to deploying Ethernet network infrastructure to support data transmission, certification testing is the key to ensuring that the supporting cable plant is installed correctly, complies with industry standards, and will support applications.
Certification testing measures key performance parameters and compares them to industry standards set by TIA or ISO/IEC, with results indicating compliance with the standard and/ or a specific category or class of cable. This, in turn indicates which industrial Ethernet applications the cable plant can support – a critical piece of information needed to leverage Industrial Internet of Things (lloT) technologies.
It is recommended that certification testing is a requirement on any cabling project specification. Indeed, it is often required for obtaining vendor warranty on the cabling system.

Unfortunately, network problems can arise after successful installation. Some of the most common causes include accidental damage to cables and connectors from workers and machinery; electromagnetic interference; miswiring or improper terminations; or dirty fibre optic connector end faces caused by exposure to dust. There are some inexpensive tools that can help Operations Technology (OT) staff identify and locate problems.
Copper troubleshooting
A non-functioning copper link is often a result of a lack of continuity caused by a cut or break in the cable or a bad termination process. Testing
for continuity is accomplished with wiremap testing that looks for opens, shorts, reversed pairs, cross pairs, and split pairs.
While the certification tester used for initial testing will conduct wiremap testing, few OT departments own these complex, expensive tools. Fortunately, verification testing using a simple, lowcost wiremap tool is an ideal solution.
Identifying the actual location of a fault along a length of copper cable can be easily achieved with an inexpensive tone and probe, which works by injecting a high harmonic signal onto a conductor that generates an audible noise at the fault location. Somewhat more sophisticated verification tools include a Time Domain Reflectometer (TDR), which indicates the distance to a cabling fault, greatly reducing troubleshooting time.
While verification is the first line of defence, if it is found that continuity is not the problem, qualification testing may be needed. A qualification tester includes alI of the verification functionality but is more sophisticated and can qualify cabling bandwidth on live Ethernet networks to determine if the cable supports the intended application. A good qualification tester will indicate if the problem is related to noise issues.
Fibre troubleshooting
The most common cause of fibre optic failures is contamination caused by dust or dirt on the endface of a fibre connector. Some inexpensive tools exist for dealing with typical problems. One tool to have on hand is a basic fibre inspection camera that can reveal a dirty fibre end face at a connection point. If dirt is visible the connector end face can
be cleaned using wipes and solvents. There is also a chance that the fibre is bent or broken somewhere along the link. A simple visual fault locator (VFL) will illuminate a fibre with a visible laser that will leak out where the fibre is broken or bent.
It may make sense to invest in a more sophisticated fault locator that bridges the gap between a VFL and an expensive OpticaI Time Domain Reflectometer (OTDR), which is a more complex troubleshooting tool that requires more skill to operate. There are fault locators available that locally display the location of events such as severe bends, highloss splices, breaks, and dirty connectors that can impact transmission.
The key to a worry-free cable plant starts with quality components and installation by a qualified installer, followed by certification testing. But if something goes wrong down the road, troubleshooting the problem can be your first line of defence. It may allow OT teams to fix the problem or at least cut down on the cost of repairs by eliminating the need to pay for diagnosis. plus-circle
Mark Mullins is global communications manager at Fluke Networks.Alarm systems management
Complex industrial systems require complex control systems – but carefully thought out alarms systems
EEMUA is the acknowledged leader in the field, with EEMUA 191, ‘Alarm systems - a guide to design, management and procurement’, being regarded as the benchmark in alarm systems management.


The EEMUA Alarm Systems e-learning module provides an introduction to EEMUA 191 and is positioned at the awareness level. It offers simple and practical guidance to managers, designers, supervisors and operators on how to recognise and deal with typical human-factor problems involving alarm systems. Its
scope covers many sectors, including the energy, process and utilities industries.
The e-learning is recommended
Creating a successful control environment
Know what you want, plan what you’ll get, check that you’ve got it!
The EEMUA Control Rooms e-learning module provides guidance to engineers and the wider teams involved in the design of control rooms, control desks and consoles. It will help during newbuild and modification projects, as well as evaluating existing set ups where people operate industrial processes and activities on facilities such as chemical plants, power stations and oil refineries.
The e-learning will benefit anyone with an interest in process plant control rooms and control desks using Human Machine Interfaces.
It is especially relevant to control
engineers, control room console (and HMI) designers and vendors, control room operators, engineering consultants, engineering contractors,
for both discipline and projectfocused engineers from a variety of backgrounds who want to gain an introduction to the fundamental principles for design, management and procurement of alarm systems. The course is also relevant to engineers and managers from operating companies as well as specialist contractors and equipment suppliers.
Visit the EEMUA website for further details.
www.eemua.org
engineering managers, facilities managers, graduate engineers, plant operations managers, process safety managers, SCADA engineers and systems support managers.
The e-learning is positioned at the awareness/introductory level and is an optional precursor to working through EEMUA 201, ‘Control rooms: A guide to their specification, design, commissioning and operation’.
Visit the EEMUA website for further details.
www.eemua.org
Maximum performance with minimum footprint

The C6030/C6032 ultra-compact Industrial PCs: with reduced space requirements for highly complex and demanding applications Intel® Core™-i processors of the highest performance class up to the ninth generation maximum computing power up to Intel® Core™ i7 with 8 cores at 2.6 GHz each almost any automation and visualization task can be realized the C6032 variant offers modular interface extension for increased flexibility

Ultra-compact
Ultra-powerful
