Institute's Technology and Digital Humanities Lab
Newcomb
Issue 6 | 2022-2023
The views and opinions contained herein by the various authors do not necessarily reflect the official views, opinions, or policy of Tulane University/Newcomb Institute administrators, staff, or faculty. All material contained herein are the views and opinions of the authors themselves.
THRIVINGWITH TECH
NEWCOMBINSTITUTE
CONTRIBUTORS
EDITOR
Jacquelyne Thoni Howard, Ph.D. Administrative Assistant Professor of Technology and Women’s History
GRADUATE ASSISTANT
DIGITAL RESEARCH INTERNS
Marisa Long & Wendy Yang (Product Developers)
Tess
Catherine
Rhea Majumdar Ifeoma Osakwe Ananya Anand Evan Hendrickson
Sam DeMarinis
INFORMATION TECHNOLOGY INTERNS
Naomi Stoner & Madeline Nellis (Product Developers)
GRACE HOPPER CELEBRATION ATTENDEES
Marisa
Ananya
ZINE LAYOUT & DESIGN
ZINE COVER
Rachel Tabor
M.S. Candidate in Biomedical Engineering
Kleanthous Izzy Blair Winna Xia Zoe Oboler
Hu Aaliyah Randall Claire Ramsay Meghan Nagia
Jingzhi Yang Kailen Mitchell Olivia Riess Izzy Blair
Long Olivia Riess Madeline Nellis Rhea Mujumdar
Anand Laya Kumar Wendy Yang Tess Kleanthous
Naomi Stoner Alyssa Bockman Kailen Mitchell Evan Hendrickson
Tess Kleanthous Rhea Majumdar Catherine Hu Zoe Oboler
Ifeoma Osakwe
Zoe Oboler Rhea Majumdar Ananya Anand (front cover) (front cover) (page dividers)
PROJECTS & PARTNERS
Project Name Project Partner
Maternal and Child Health Coalition
Website Administration and Interactive Map
Beautiful Sisterhood of Books
Feminist Pedagogy for Teaching Online
Clare Daniel Ph.D., Maeve Wallace Ph.D. & Danielle Houston
Kate Adams Ph.D., Jacquelyne Howard Ph.D. & Susan Tucker Ph.D.
Clare Daniel Ph.D. & Jacquelyne Howard Ph.D.
Frances Gaudet Legacy Project Nell Bolton & Rosanne Adderley Ph.D.
Newcomb Magazine
Deconstructing Rape Podcast
Transformative Preservation
Crime Survivors NOLA
Congo Sqaure Legacy Project
Scholars Lunch and Learns
The 50th Anniversary of 1975
Mellon Graduate Group
Nutrient Pollution
African Letters
Give Light
CONTACT
Becky Gipson & Lauren Gaines
Sally Kenney Ph.D.
Laura Blokker & Andrew Liles
Julie Ford & Rose Preston
Freddi Evans
Aidan Smith Ph.D.
Allison Truitt Ph.D.
Ryan McBride & Lucas Diaz
Isabel Englehart
Liz McMahon Ph.D.
Steph Smith
Newcomb Institute of Technology, Tulane University
The Commons, Suite 301
Website: https://newcomb.tulane.edu/technology-and-digital-humanities-lab/
US
Message from the Editors
April 2023
In the Technology and Digital Humanities Lab at Newcomb Institute, we are committed to promoting gender equity across technology fields and industries that are often dominated by patriarchal standards of representation, labor hierarchies, and design. As technology applications are integrated into the workplace and across society, entrenched inequities such as discrimination around race, class, gender, and sexual orientation pervade these digital spaces. In response to these growing inequities, the Lab equips undergraduate interns with the digital tools and essential skills to expand their technology portfolio in a low-stress caring environment that promotes learning, while also learning how technology can alter power structures in our society. We promote the philosophy that “everyone is a technologist,” which is shown by our diverse intern class of nineteen interns from fifteen different majors. We value our interdisciplinary lab community, as each brings valuable insight and skills that they can share with other interns.
This year, between our two internship programs, our interns surpassed past years in the breadth of our work portfolio. The growing Information Technology (IT) team completed 661 technology help tickets while supporting faculty, staff, students, and visitors using technology in the event spaces at the Commons. Our Digital Research (DRI) team worked on fifteen technological projects in partnership with faculty, staff, and community members. We also funded twelve of our students to attend the national Grace Hopper Convention (GHC) where many found impressive jobs, internships, and networking opportunities in the technology field. In addition to project work, we also focused on helping our interns feel confident to apply feminist practices in their future careers through curriculum and discussion. We integrated the reading and discussion of feminist scholarship into our meetings as part of our internship work. Interns completed training
on feminist technologies, feminist customer service, accessibility in the digital space, and more! We are proud that these feminist technologists took up the challenge to build their portfolio and also to engage in this holistic training!
In addition to the increased breadth of projects and service that the interns accomplished for external partners, we also introduced some new lab-grown initiatives this year. In March, we distributed our first edition of The Lab’s Newsletter. With the Newsletter, we aim to improve overall public engagement with the lab by sharing announcements, highlighting our interns and project partners, and sharing technology tips with our community. We have also been busy planning the return of our Feminist Technology Showcase as an in-person event in May 2023. The Tech Showcase provides an interactive opportunity for Lab interns to interact with the Tulane community interested in learning about The Lab and explore the projects that we have worked on with partners. We also started our first lab-grown digital project: Steminisms! Steminisms is a crowd-sourced digital humanities project that explores the intersections between gender equity and STEM (Science Technology Engineering and Math). This site will provide resources for scholars and general audiences to learn about these intersections. Interns have explored avenues for effectively communicating the resources as a database and have begun uploading content that will continue for years to come.
This zine serves as a portfolio of work for the interns, grantees, and affiliated student groups within the Lab. We hope this zine provides you with insight into our lab’s work and the personalities of our interns! The intern’s special interest articles illustrate the issues that matter to intersectional technologists. In addition to showcasing amazing digital research projects, the project posters demonstrate the range of technical skills that this lab is cultivating. As we work towards our goals, our lab continues to promote communities of care and feminist self-care values that students can use in our spaces and beyond. We hope you enjoy learning more about The Lab!
Sincerely,
Jacquelyne Thoni Howard, Administrative Assistant Professor of Technology and Women’s History
Rachel Tabor, Lab Manager and Graduate Assistant
TABLE OF CONTENTS Page 8 15 20 49 64 77 85 91 Content 2022–2023 Lab Interns Meet the Lab Digital Research Internship Program Articles Digital Research Internship Program Posters Information Technology Internship Program Articles Information Technology Internship Program Posters Grants Student Groups
ng in Cell & Molecular Biology and Computer Science. She is an international student from China and has been in the lab for two years. In addition to working as a Product Developer in the DRI team, Wendy is involved with Tulane International Society (TIS), Tulane Chinese Students and Scholars Association (TCSSA), and Tulane Equity in Tech (EIT). She also serves as a Global Ambassador, a TU Pal mentor, and a Newcomb Big. Her favorite part of the DRI program is working with the interdisciplinary and collaborative team. Outside of school, she loves camping, cooking, and playing board games!



Madeline Nellis is a Science and Music with a minor in Music, Science, & Technology. She is from Long Island, New York. In addition to being a Product Developer for the IT team she is also the president of the Equity In Tech club. For her senior capstone, Madeline is exploring technical solutions to provide students on Tulane's campus with Emergency contraceptives while protecting the privacy of both recipients and volunteers. Post graduation Madeline is pursuing a career in Data Analytics and visualizations and outside of school Madeline enjoys running, yoga, reading and playing the piano.







8
urth year studying Linguistics and Computer Science. She is originally from Columbus, Ohio and has been a part of the DRI team for three semesters, holding roles as a developer, team lead, and product developer. Participating in these different roles has allowed Marisa to deepen her understanding of feminism in a technology workplace and to contribute to growth in the digital humanities. Outside of DRI, Marisa is a TA for an introductory computer science course and is a member of the running club. In her free time, Marisa love to run, hike, read, and spend time with friends outdoors.



Naomi Stone





Cybersecurity and Theatre Performance with a minor in Russian. She is from Cincinnati, Ohio. In addition to being a Product Developer, Naomi has been a student worker for the School of Professional Development’s IT Department. Naomi is also active in the New Orleans and Atlanta theatre and film communities, and is happy to have worked on several student and independent films this past year. Outside of school, Naomi enjoys singing, altering clothing, and painting. Naomi hopes to pursue a career as both a cybersecurity analyst and actor post-graduation.
homore majoring in Economics and Computer Science with a minor in SLAM. She grew up in Bangalore, India. She had the pleasure of joining the Digital Research Internship and finding a community of like-minded students. Ananya also works as a Research Aide in the Economic Department at Tulane. Additionally, Ananya is involved with Tulane’s Bollywood Dance Team as the Manager and is part of the E-Board of the Cookies and Code Club. Outside of school and work, Ananya loves cooking, reading, and trying out different cuisines.

Sam DeMarinis is a sophomore majoring in Mathematics and Computer Science with minors in Psychology and Italian. He is from Morris Plains, New Jersey. In addition to being a Digital Research Intern, he is on the executive board for Tulane’s computer science club, Cookies & Code. He is also a member of the professional engineering fraternity, Theta Tau, where he is the chair of the General Majors Committee. Sam is interested in pursuing a career in data science and machine learning engineering. Outside of school, he enjoys playing music, learning Italian, and cooking.

udent majoring in Computer Science and Design. Zoe uses She/Her pronouns and was born and raised in Washington D.C. In addition to being a digital research intern, Zoe is a member of Theta Tau, where she is the chair of the website committee. She enjoys finding ways to explore her interests in both the arts and sciences, and often works in the intersection between computer science and graphic design. Out of School she enjoys travel, embroidery, oil painting, and baking.





Ifeoma Osakwe i and Molecular Biology on the Pre-Med track. She is an international student from Nigeria. As well as a Digital Research Intern, she is a Newcomb Scholar, a First Year Experience Peer Mentor, and Global and Green Wave Ambassador for the Office of Undergraduate Admission. She enjoys finding unexpected links between her academic interests, internships, and campus involvements and loves her positions in the Newcomb Institute because they allow her to explore such interdisciplinary curiosities. Outside of school and work, she likes to play board games, travel, and cook breakfast foods.


10
Tulane pursuing a B.S.E in Engineering Physics with a Certificate in Computational Engineering and a minor in French. Tess is originally from Westford, MA, but is excited to be moving to Littleton, CO at the end of the year. This year, Tess has had the privilege of joining the Digital Research Team as a Development Intern. Due to the fact that Tess has a background in both the arts and the sciences, she loves exploring the digital humanities or any subject that falls into that intersection. Outside of school and work, Tess’ primary hobbies include painting, reading, and paying for overpriced coffee simply for the aesthetic.








Meghan Nagia is a freshman from Atlanta, Georgia. She is majoring in Exercise Science with a minor in Strategy, Leadership, and Analytics (SLAM) on the Pre-Med Track. In addition to being a Digital Research Intern, she is a member of Phi Mu, the Current RLC, and the Tulane Orchestra. Meghan is also the secretary of the Indian Association at Tulane (IATU), vice president of the Kinesiology Club, and getting involved in other organizations. Outside of school, Meghan enjoys playing violin, working out, volunteering, drinking lots of coffee, and exploring New Orleans with her friends.
ing in Psychology and Design at Tulane University. Catherine is originally from Memphis, Tennessee. In addition to working as a Digital Research Intern, she is a Graphic Design Intern for the Newcomb-Tulane College’s Office of Undergraduate Enrichment. She also serves on the executive boards for a number of clubs, including the Asian American Student Union (AASU), Tulane University Ladies’ A Cappella (TULA), The Research Ambassadors, and Psi Chi. Outside of school, Catherine enjoys playing volleyball with her friends (unprofessionally) and painting with acrylics.




Aaliyah Randall


Neuroscience with a minor in Gender and Sexuality Studies. Aaliyah was born and raised in Lafayette, Louisiana. Along with the privilege of serving as a Digital Research Intern, she is an Ambassador of the Office of Gender and Sexual Diversity, a second-year Resident Advisor, former Vice President and member of the Tulane Women's Rugby team and a RoboRecovery Intern, where she teaches robotics to young students in New Orleans. Outside of academics, Aaliyah enjoys listening to and playing music, crafting original ceramic creations, exploring and photographing the wonders and foods of the world, a es.






undergraduate student pursuing a double major in Psychology and Design with a minor in Studio Art. She hai from Long Island, New York and re-joined the D team at Newcomb Institute this spring semester On campus, she works as a library research aid assistant editor for the Crescent Magazine's NOLA 360 section, and teaching assistant for a design studio. In her free time, she makes an excessive amount of Spotify playlists, dabbles in the kitchen, and gets lost while exploring New Orleans. She hopes to mesh her interests post-grad by entering the design industry, honing in on product design.
Winna Xia is a Neuroscience and History. Winna uses she, her, hers pronouns, and is originally from Lexington, MA. In addition to being a Digital Research Intern, she is also a Newcomb Scholar, TUPHE, service-learning assistant, and peer mentor. Winna is also involved with Tulane's Premedical Society and Walk n’ Talk NOLA. Outside of school, she likes to cook and do embroidery.

12
ear student from Mount Vernon, KY majoring in Public Health and Computer Science. Working as a Development Intern has allowed Evan to put the skills he learned during his four years at Tulane to use and learn about digital humanities and feminist pedagogy. In addition to working as a DRI Intern, Evan is the Outreach Chair for the Tulane Equity in Technology and a Tulane University Peer Health Educator. Evan plans on pursuing a career as a health/medical data scientist. In his free time, Evan enjoys spending time in Audubon Park, watching reality TV, listening to podcasts, and reading.
Clair University pursuing a BA in Economics with minors in Strategy, Leadership, and Analytics (SLAM) and Spanish. She is a member of the



Newcomb Scholars Program, an interdisciplinary







leadership development program focused on gender equity. In addition to working with the tech Lab, Claire works at Tulane’s Reily Recreation Center and handles Alumni Relations for Tulane DSP. She is excited to join the Digital Research Team and improve her technical and digital skills to help create projects that align with the project partners’ visions.
in Computer Science and Piano Performance. She is also minoring in Music, Science, and Technology. She is from Stuttgart, Arkansas. She is both a Digital Research and Information Technology Intern at the Newcomb Institute. She is both a classically trained pianist and composer. As a part of the WTUL radio station at Tulane, she is a DJ and hosts weekly radio shows. In her free time, she enjoys reading and rereading Jane Austen novels, learning new instruments, practicing yoga, and baking a ridiculous amount of cookies.
Jingzhi Yang is a senior majoring in chemical engineering, computer science, math, chemistry, econ and minoring in Information Technology. He is from Shanghai, China. In addition to being an IT intern at Newcomb Institute, he also works as an intern at Tulane IT cybersecurity. He holds multiple Comptia IT certifications and he is a certified ethical hacker. Outside of school, he enjoys cooking and running. He is also interested in credit card rewards program and he is currently holding ten credit cards to maxize the rewards. He will pursue Ph.D in chemical engineering at Georgia Tech starting 2023.


Olivia Riess is a senior majoring in Engineering Physics with a certificate in Mechanical Engineering, and minoring in Mathematics. She is from Wallingford, Pennsylvania. Outside of being an Information Technology Intern, Olivia is the president of Tulane’s Society of Women Engineers and is a tour guide for the university. She's so excited to be a part of the Newcomb team learning and applying feminist pedagogy in the Lab. In her spare time, you can find Olivia watching old horror movies, listening to the You're Wrong About podcast, or exploring New Orleans!


Kailen Mitchell is a So Mathematics and Computer Science with a minor in English. She is from San Francisco, California. Outside of the IT program, Kailen is part of the Women's Ultimate Frisbee team as well as the Equestrian Club. She has always been an avid problem solver and loves the opportunity to strengthen this skill through IT. She is extremely passionate about gender equity and is so grateful for the opportunity to be part of a feminist community while exploring her interests in technology. In her free time she enjoys reading fiction, creative writing, and hiking.







14








 Fall: Winna Xia, Ananya Anand, Izzy Blair, Evan Hendrickson, Ifeoma Osakwe, Marisa Long
Fall: Rachel Tabor, Zoe Oboler, Claire Ramsey, Meghan Nagia, Tess Kleanthous, Catherine Hu, Wendy Yang
Fall: Winna Xia, Ananya Anand, Izzy Blair, Evan Hendrickson, Ifeoma Osakwe, Marisa Long
Fall: Rachel Tabor, Zoe Oboler, Claire Ramsey, Meghan Nagia, Tess Kleanthous, Catherine Hu, Wendy Yang









 Fall: Zoe Oboler, Marisa Long, Winna Xia, Tess Kleanthous, Izzy Blair. Claire Ramsey, Evan Hendrickson
Fall: Madeline Nellis, Kailen Mitchell, Naomi Stoner, Olivia Riess, Izzy Blair
Fall: Zoe Oboler, Marisa Long, Winna Xia, Tess Kleanthous, Izzy Blair. Claire Ramsey, Evan Hendrickson
Fall: Madeline Nellis, Kailen Mitchell, Naomi Stoner, Olivia Riess, Izzy Blair
16
Spring: Evan Hendrickson, Meghan Nagia, Winna Xia, Sam DeMarinis, Tess Kleanthous, Wendy Yang
Q Q&&A A
with The Lab's Product Developers
ProductDevelopersareformerDevsandarechosenfromthe cohortsoftheInformationTechnologyandtheDigitalResearch Internshipteams.Theseinternshavestrongorganizational, projectmanagement,communication,andleadershipskillsand haveshownastrongcommitmenttothelab’sfeministethos DRI productdevelopersserveasprojectmanagersontheresearch projectofpartners/clients(facultyandcommunitymembers).IT productdevelopersserveasassistantfloormanagers,handling andinterveninginITinquiriesintheeventspaces,assistingthe GAsandAAPswithspecialprojects,andmanagingstudent workflowsandprojectsfortheITteam.
What’s your favorite part of being on the DRI/ITI team?
Naomi: "My favorite part of being on the ITI team is getting to work on both outside projects and on-site technical issues. I enjoy maintaining community partners’ websites because it allows me to engage with the community in a meaningful way while honing my software troubleshooting skills. On the other hand, troubleshooting on-site technical issues allows me to practice my customer service skills while learning about common hardware and system issues. In a nutshell, I enjoy working on both software and hardware issues while helping people both at Tulane and in the larger New Orleans community "




What’s your favorite project you have worked on?
Wendy: "My favorite project this year is the Nutrient Pollution project. Nutrient Pollution is the project I worked on last year as a DRI. It was great to finally meet the project partner Isabel in person and hear about her vision for the project. Nutrient pollution is such an important topic in environmental science and we always overlook it. While I worked as a PD, Nutrient Pollution was also the first project that we wrapped up, and it’s great to hear that the website is still sustainable since we handed the website back to the project partner."
 Naomi
Wendy
Madeline
Marisa
Naomi
Wendy
Madeline
Marisa
What’s your biggest lesson learned this year?
Madeline: "The biggest lesson I learned this year was confidence. This was my first year on the IT team and there was a big learning curve that came along with that. In the fall I was really nervous when asked to enter a classroom to try to troubleshoot and issue Now I can walk into classrooms with confidence; I know that I can figure out the issue, and if not I know how to escalate problems as well as explain issues to the professor This growth stemmed from experience but also the great community the lab facilitates; I know there are so many people who can help if I need assistance."
What skill did you improve the most working as a PD?
Marisa: "Working as a PD this year taught me a lot about professional communication. This was my first time working directly with our project partners, which was both inspiring and eyeopening. I learned to communicate efficiently inside and outside meetings to make sure that we kept projects on task and moving forward. I also got to practice communicating both the bigpicture idea and the broken-down steps of a project to the interns on my team."
What’s the best part of working as a PD?
Marisa: "My favorite part of working as a PD is getting to work with such amazing people I have a lot more one-on-one or small group meetings as a PD, so I feel as if I have gotten to know the people on my team and the other PDs better than I have been able to before having this role. Everyone has such unique and creative perspectives, which keeps our work fun and interesting "
Naomi: "My favorite part of working as a PD is getting to work with like-minded individuals with a strong sense of community. It is nice to be able to collaborate with other students and talk about daily life at work It is likewise refreshing to have a tech space that is committed to intersectionality and inclusivity."

Madeline: "My favorite part of working as a PD is getting to see the lab’s disciplinary values physically displayed in deliverables Interns in our lab come from all different backgrounds and areas of study. When assigning tasks, Naomi and I, try to keep everyone’s strengths in mind. I love seeing what our team produces especially when the deliverables are a different but better version of what I was expecting!"
Wendy: "My favorite part of working as a PD is meeting with project partners and seeing the bigger picture of each project. It is a pleasure to meet with project partners and hear about their passions, ideas, and goals for their projects Looking back at what we have done as a team, it gives me a sense of achievement seeing how we started from scratch and ended up having a sophisticated deliverable!"
18



20
CAN TECHNOLOGY HELP PRESERVE INDIGENOUS LANGUAGES?

WRITTENBYMARISALONG
Today,thereareover7,000languagesspokenworldwide,yetmorethan50percentofpeoplespeakthetop43ofthese languagesSincethemajorityoftheworldspeaksrelativelyfewlanguages,thereispressureonindigenouscommunities toraisetheirchildrentospeaktheofficiallanguage,astheyhopethiswillprovidethemwitheconomical,social,and professionaladvantagesinthefutureInmanycases,thereisalsopressurefromgoverningbodiesforlanguage conformitythrougheducationandlegislatureAsaresult,thenumberofpeoplespeakingminorityandindigenous languagesareeverdwindling,andwithit,preciousspecificknowledgethathasbeenencasedintheselanguagesWhen lookingatlinguisticdiversityontheInternet,minoritylanguagesaremarginalizedevenfurtherAccordingtoestimates fromW3Techs,Englishaloneaccountsforover50percentofthecontentEventhefifthmostwell-representedlanguage ontheinternet,Japanese,providesapproximately34percentofthecontentThelackoflinguisticdiversityontheInternet pointstoyetanotherinstanceoflinguisticandculturalerasure.
Despite technological barriers and rapidly dwindling numbers of speakers, many individualsarestillfightingtopreservebothindigenouslanguagesandcultures As languagetechnologieshavebecomemoreprevalentandavailable,somelinguistsare hopefulthatthesetoolswillbeabletoslowthecurrentrateoflanguagelossOneofthe primarywaysthattechnologymayaidlanguagepreservationisbyincreasingtherateand easeofdatacollectionHistorically,amajorchallengeinpreventinglanguagedeathis
creatingacorpus(acollectionoftexts)throughtranscriptiontocapture indigenouslanguageandknowledgewhiletherearestilllivingspeakers. Computerscientistsandlinguistshavebegunworkingtogethertobeginto automatethetranscriptionandtranslationfromlanguagesampleaudio files Thissaveslinguistsperformingfieldworkthetimeandenergythat normallywouldbespentcarefullylisteningandre-listeningtotranslate, whichisaslowprocessknownasthe“transcriptionbottleneck”However, thissolutionisstillaworkinprogressandcanonlybeusedincaseswhere therealreadyexistsenoughlinguisticdatatotraintheMLmodels This meansthatincasesofextremelyendangeredlanguageswherethereare onlyahandfulofspeakersleft,itisnearlyimpossibletobuildsuchamodel sinceeachindividual’slinguisticvariationmakesitdifficulttostandardizea formofthelanguage.Additionally,takingalanguagethatoriginallywas rootedinoraltraditionandplacingitintowrittenformriskslosingcultural aspectsassociatedwithstorytellingthatareencodedinbothsoundand movement
However,thereishopeonthehorizonduetoapushtoincludeindigenous leadersandcommunitiesintheprocessofdevelopingfurtherlinguistic technologies OneexampleinprogressistheSenecaProject,where linguists,computerscientists,andseveralSenecaleadersareworking together to develop deep learning speech recognition on resourceconstrainedindigenouslanguages Forthisproject,aninterdisciplinary teamisleveragingtheirfamiliaritywiththeSenecalanguagetotrainthe neuralnetworkusingindividualphonemes,andsofar,theireffortshave provensuccessful
AnotherexampleofinclusivelanguagetechnologyisWoolaroo,whichisanimage-based languageapplicationcreatedbyGoogleTheideabehindtheappistoplacelanguagelearningtoolsdirectlyinthehandsofindigenouspeoplethroughanopen-sourcecollection oflanguageworddefinitionsandaudiorecordingsEachentryisassociatedwithaphotoin anattempttoincludemorevisualculturalknowledgeinthelanguagedocumentationSo far,thereareonly10globallanguagesthatareincludedonWoolaroo,andaddingmore languagesmayremainachallengeduetolimitedaccesstotechnologygloballyHowever, theideaprovidesaninnovativewayforcommunitiestotakechargeofthewaytheir languagesarebeingsaved,documented,andtaught

Currently,thetechnologiesbeingusedforlanguagerevitalizationarenottranscribing languageatthesameratethatlanguageisbeinglostWithouturgentaction,thedigital spacewillcontinuetoexaggeratethegapsseeninourworldByprioritizingandfunding projectsthatallowforincreasedlanguagedocumentationanddecreasedbarrierstowards indigenousinvolvementinlanguagerevitalization,wecanchangethetrajectoryanduse technologyasatooltofightforindigenousinclusion
References Anand,P.,Chung,S.,&Wagers,M.(n.d.).WideningtheNet:ChallengesforGatheringLinguisticDataintheDigitalAge.ms,UniversityofSantaCruz.Retrievedfrom https://people.ucsc.edu/~schung/anandchungwagers.pdf. Anastasopoulos,A.,Cox,C.,Cruz,H.,&Neubig,G.(n.d.).EndangeredLanguagesmeetModernNLP.aclanthology.org.Retrievedfromhttps://aclanthology.org/2020.coling-tutorials.7.pdf Ebadi,B.(2018,June30).Technologyalonecan'tpreserveendangeredlanguages.CentreforInternationalGovernanceInnovation.RetrievedMarch8,2023,from https://www.cigionline.org/articles/technology-alone-cant-preserve-endangered-languages/ Howmanylanguagesarethereintheworld?|Ethnologue.(n.d.).RetrievedMarch6,2023,fromhttps://www.ethnologue.com/guides/how-many-languages Lin,E.(2021,September8).Theroleoftechnologyinpreservinglinguisticdiversity.ColumbiaUndergraduateScienceJournal.RetrievedMarch8,2023,from https://journals.library.columbia.edu/index.php/cusj/blog/view/378 ResearchersuseAItopreserveSenecalanguage.RIT.(n.d.).RetrievedMarch6,2023,fromhttps://www.rit.edu/news/researchers-use-ai-preserve-seneca-language ToppanDigitalLanguage.(2019,August15).ThechallengeofDisproportionateLanguageRepresentationOnline.ToppanDigitalLanguage.RetrievedMarch8,2023,from https://toppandigital.com/us/blog-us/the-challenge-of-disproportionate-language-representation-online/ UNSWArts,Design&ArchitectureLaunchesIndigenousStrategy.InsideUNSW.(n.d.).RetrievedMarch8,2023,fromhttps://www.inside.unsw.edu.au/campus-life/unsw-arts-designarchitecture-launches-indigenous-strategy
"Thevastarrayof knowledgeand culturecaptured byIndigenous languageswould belostifwefail torecognizethat languageismore thana successionof lettersand sounds."
-BushraEbadi
22
TECHNOLOGY'S AFTERTHOUGHT: TECHNOLOGY'S AFTERTHOUGHT: PEOPLE WITH DISABILITIES PEOPLE WITH DISABILITIES
 ByAaliyahRandall ByAaliyahRandall
ByAaliyahRandall ByAaliyahRandall
Technology is without a doubt an ever-changing and constantly growing field that greatly influences our experience on this earth. Because of technology, humans have been able to accomplish the unimaginable. We are able to instantly communicate with others who are thousands of miles away, we have created life-saving treatments for many health concerns, and we’ve even been able to put a man on the moon. Technology’s impact seems so endless and indisputable. However, technology doesn’t just make things easier for humans, it can actually create barriers for certain groups of people. More specifically, the people who create and develop technology invent barriers by not keeping in mind the needs of minority groups such as people with disabilities.
As technology has progressed throughout the years, we’ve been able to use its capabilities to improve the livelihoods of many people with disabilities in special ways. Devices such as prosthetics, hearing aids, scooters, braille keyboards, screen readers, etc. have proven to be very helpful to people with disabilities who are trying to navigate an ableist world. These technologies can make things such as the internet, the outdoors, and entertainment more accessible for the disabled community. Nevertheless, we must ask the question of why some of these technologies must exist and how compatible our world applications are to the necessary accommodative technologies used by people with disabilities.
Since the signing of The Americans with Disabilities Act (ADA) in 1990, people have had to think more intentionally about the treatment of the disabled community. The ADA prohibits “discrimination against people with disabilities in everyday activities” (Americans with Disabilities Act, 1990). Further, it “guarantees that people with disabilities have the same opportunities as everyone else to enjoy employment opportunities, purchase goods and services, and participate in state and local government programs” (Americans with Disabilities Act, 1990). The ADA legislation requires that employers, state and local governments, businesses that are open to the public, commercial facilities, transportation providers, and telecommunication companies comply with the standards set by the ADA to ensure accessibility.

With the passing of the ADA, many corporations set out to achieve the bare minimum in terms of accessibility by doing just enough to be ADA compliant. This can be very problematic as there is a lack of care for the true needs and experiences people with disabilities possess when interacting with certain products and programs. Because people with disabilities are not considered at the design level of products, barriers are created that make deceptively accessible products and applications difficult to use for people with disabilities. Some examples of these technological barriers include: website functions that
only work with clicking a mouse, inaccurate closed captioning, self-service kiosks without accessibility features, and touchscreens without screen reader software or tactile keyboards (Kovac, 2019). Additionally, there are other factors that contribute to these accessibility barriers, for example, lack of access to assistive computer hardware and software such as key guards, trackballs, large monitors, head-pointing systems, screen readers, screen magnification, or speech recognition programs (Kovac, 2019).

By centering the needs of those most marginalized at the first step of design, we can remove barriers before they are even created and make products that are more usable by not only people with disabilities, but those without disabilities as well. Tools such as speech recognition are useful for people with mobility issues and those who are effective multi-taskers. Websites that are designed to use keyboard commands also become easier for search engines to find and makes these websites more likely to be browsed. Companies like Microsoft are making strides in the right direction by including eye tracking features in their software and creating tools like Immersive Reader that reads out text, breaks words into syllables, and increases spacing between lines and letters (Daniel, 2019). A Hungarian company SignAll has developed the first automated sign language translator which translates sign language into text through the use of AI, allowing communication between deaf and hearing people with great potential (Daniel, 2019).
Going the extra mile and keeping people with disabilities as the priority user at the design level, we are able to create technology that is more usable for all. People with disabilities should not be a second-thought for designers, but the most valuable user to learn from. Ensuring accessibility needs to be prioritized because it makes a huge difference in the way many people experience life. The standards of accessibility should not stop at being ADA compliant. The standard should be above and beyond the stars, just like the man on the moon because it is the human thing to do.
References: Kovac,L (2019,November22) DisabilityandTechnologyBarriers AccessibilityforOntarianswithDisabilitiesAct(AODA) https://aodaca/disability-andtechnologybarriers/#:~:text=For%20instance%2C%20some%20technology%20barriers,magnification%2C%20or%20speech%20recognition%20programs Daniel,E (2019,June25) Howaccessibletechnologyisovercomingbarriersintheworkplace Verdict https://wwwverdictcouk/accessible-technologymicrosoft/ AmericansWithDisabilitiesActof1990,42U.S.C.§12101etseq.(1990).

24
Chat G to wri is an workfl have used AI for hiring, credit card applications, among other uses However, despite its amazing ability Ai has shown significant bias , often mirroring our own biases as well as the internet's rhetoric.

A recent Bloomberg article listed a number of racist and sexist comments made by chat gpt This is not the first time something like this has taken place The apple credit card used a complex AI system to approve and deny members as well as set their credit limits. Users noticed that women were continually given lower limits than their male counterparts Amazon recently had to stop using its ai recruiting tool when it began prioritizing men
So why are these AI’s so biased? In the end it comes down to the way Ai functions. Ai looks to find patterns in data, so for instance Amazon’s recruiting Ai was set to find patterns in resumes over the last 10 years Because the majority of those applications had been male, the Ai then believed that being male was part of the hiring criteria In Apple's case they defended themselves by saying that gender is not even a criteria in their applications in order to refute claims of bias. A recent Wired article titled The Apple Card Didn’t See Gender and That's the Problems refutes Apple's claims explaining “ , it is entirely possible for algorithms to discriminate on gender, even when they are programmed to be “blind” to that variable For another, imposing willful blindness to something as critical as gender only makes it harder for a company to detect, prevent, and reverse bias on exactly that variable.” The author goes on to explain that other data can be used as a proxy, for instance in past algorithms there has been evidence of home addresses being used as a proxy for race In this way not allowing input of information is not eliminating the bias, just making it harder to detect

So why is Chat Gpt, what is in many ways a glorified search engine, spitting out racist and sexist information? It all comes back to looking for patterns in data Tay microsoft’s twitter bot became incredibly racist and sexist less than a day after launching James Vinent in an article for the Guardian notes “But while it seems that some of the bad stuff Tay is being told is sinking in, it's not like the bot has a coherent ideology ” The crucial piece here is that although tay can repeat information, the bot has no real understanding of what it means Therefore her racism and sexism is simply a product of her input Chat GPT was simply mirroring the information it found online, much of which was biased.
What is the solution? The first may just be for us, as humans, to be better These AIs are simply reflecting back to us amalgamations of data we enter into them Without a prior gender bias in hiring Amazon’s Ai would never have discriminated against women. Without the hordes of twitter spamming Tay she wouldn’t have found her extreme views But this also brings us to one of the limits of AI Ai is not innovating, rather it is repackaging and recycling what it already knows Because of this Ai in its purest form will uphold the status quo Ask chat gpt to write a poem, and it will not elevate the field of poetry, instead it will just create a piece of work that is the same as what we already have. Using AI isn’t necessarily bad, but using it without understanding its limitations is incredibly dangerous Ai may be the pinnacle of technological progress but at the same time it may be stunting social progress As Ai becomes more prevalent we must make sure we continue moving forwards.
26
ComputerSaysNo
Devil's in the Detail: Design in Technology
by Rhea Majumdar
At the core of every great business, product and software is great design; it is the building block, the blueprint, the master plan. Design is that of empathetic utility -- it makes technology more human.
It is a broad discipline and spans across fields -fashion, technology, architecture, and so on. Within just technology, there are roles that have more prevalence now more than ever; they existed within broader roles for
quite some time, but demanded their own specialization. Some include, but are not limited to: web designers, visual designers, UI designers, UX designers, augmented reality designers, game designers, animators, interaction designers, product/packaging designers, etc.
Designers within technology are tasked with understanding business etiquette and common practices and use that knowledge to strategize to create user-centric

designs. Don Norman’s 'The Design of Everyday Things' summarizes the evolution of design’s role within technology well -- as he puts it, “The same technology that simplifies life by providing more functions in each device also complicates life by making the device harder to learn, harder to use. This is the paradox of technology… and the challenge for the designer” (Norman, 2021, p. 34). It is definitely paradoxical, but designers all work under the same principle -- despite the digital age accounting for drastic changes in how we

Carroll J M (nd) Human computer interaction - brief intro The Interaction Design Foundation https://wwwinteractiondesignorg/literature/book/the-encyclopedia-of-human-computerinteraction-2nd-ed/human-computer-interaction-brief-intro
Hasan, M S, & Yu, H (2016, December 29) Innovative developments in HCI and future trends Machine Intelligence Research https://wwwmiresearchnet/en/article/doi/101007/s1163301610396#: :text=It%20is%20now%20possible%20to,reality%2C%20wear able%20technology%2C%20etc
Mohan, M (2020, May 29) Council post: The growing importance of design in the tech world Forbes https://wwwforbescom/sites/forbesbusinesscouncil/2020/05/29/t he-growing-importance-of-design-in-the-tech-world/? sh=63d8f34f4bfc
Norman, D A (2021) The design of everyday things Basic Books
operate, “people are the same, and so design principles are the same” (Norman, 2021, p. 239).
28
Though often overlooked or thought of as an afterthought, successful development of anything is dependent on and begins with strong design culture -the devil is in the detail.
HOW THE METAVERSE CAN ADD VALUE TO ESG PROJECTS:
Waste Management and Employee Safety
While some see the term “metaverse” as a buzzword or fad, it is a technological platform that most firms are discussing or embracing. In a survey of 1,000 U.S. business executives, 66% reported that their companies are actively involved in the metaverse (PwC 2022). Many definitions of the metaverse exist, with various firms and individuals contributing to this evolving definition. William Burns III, who is listed in Forbes as an early contributor to the metaverse, defined it as “a collective virtual shared space, created by the convergence of virtually enhanced physical reality and physically persistent virtual space, including the sum of all virtual worlds, augmented reality, and the Internet” (Hackl 2021).

by Claire Ramsay
While virtual reality headsets and life-like gamified environments are commonly associated with the term metaverse, it can be broadly thought of as a future, more immersive iteration of the internet. However, for simplicity in this article, the metaverse will be thought of as an individual’s immersive visual experience in a digitally developed world, using virtual reality technology. In thinking about the metaverse, many questions persist, including: Will the metaverse be longlasting? Do consumers demand metaverse experiences? Can the metaverse transcend the gaming industry to drive value for environmental, social, or governance-related issues?

ESG Issues
ESG stands for Environmental, Social, and Governance. These terms are grouped together because they are all considerations that consumers and investors value that are not strictly profit-related. Duke Law Magazine summarizes: “ESG encompasses a broad range of concerns about the power of corporations, including their environmental impact, stance on social issues, employment practices, treatment of suppliers, diversity in governance, and ethics and transparency of operational practices” (Naujek 2021). ESG considerations emphasize maximizing shareholder value while simultaneously aligning with the firm’s values. With the U.S. Securities and Exchange Commission’s release of the Climate Related Disclosure Proposal in March 2021, many firms seem to be focused on the environmental (E) aspect of ESG, while Social (S) advances are also increasingly prioritized.
Waste Management
The metaverse’s virtual reality experiences can be implemented by companies to decrease waste and collect more accurate data while lessening their ecological footprints. The metaverse and virtual reality technologies could be used to predict the success or adoption of some items, buildings, apparel, or public projects and advise against the creation of others. For example, Have you ever heard a family member say: “I would go to that grocery store, but the layout is so hard to navigate”? What if targeted consumers’ preferences on grocery-store layouts could be considered prior to the construction and design of the store? When you walk into a sale section of a clothing store, how many of the items are the same color or style, meaning they were not popular enough to sell? Additionally, a city planner or official might say, ‘We should build a public park to increase the health and safety of our children, but where is the best location to put it? What are the best types of equipment to place in the park?’
When businesses or governments fail to utilize data to create accurate predictions, products and resources are wasted. The grocery store might close
30
or see lower customer retention, which could lead to food waste. In retail, the nonsold items are often thrown away, piling up in the landfill. A poorly placed park with unsafe or ‘boring’ equipment may be unattended, leading to wasted equipment, land, and potentially, crime. To lessen the quantity of waste in society, virtual reality software, including metaverse platforms, can be used to create randomized controlled experiments on a larger and more immersive scale, resulting in better data-driven or data-informed decisions, satisfied consumers, and less waste.
Industry Example
How often have you gone to the sale section in a store, and the remaining items have undesirable colors or styles in large quantities? The retail industry can use virtual reality software to better forecast trends, therefore, reducing waste. In 2017, the fashion industry was responsible for 85% of all textiles in landfills, according to the Environmental Protection Agency (Devaney 2017). Retailers have the option to donate unsold clothes, sell them to discount stores, or shred and deposit them in landfills However, most brands prefer to throw away unsold clothing rather than sell it for a discounted price: “The primary concern is the impact on the brand. We’ve spent all this time and money creating this image that we’re an upscale retailer, and now suddenly you can buy our products for 20 percent of the price” (Barrat 2014). As a solution, fashion retailers could introduce a metaverse platform to research which styles their consumers demand. For example, a sports apparel company deciding on which six colors to produce for their new line of leggings could randomly select a large group of previous customers to participate in a study with the goal of aligning the color choices with consumers’ preferences. Each storefront would ask participants to put on virtual reality headsets that immerse the consumers in a ‘metaverse showroom’ that displays six different types of people wearing 12 different color leggings, and then ask consumers to rank the colors. Furthermore, the metaverse platform could include an exercise class, virtually testing the garments. On larger scales, similar randomized controlled trials could be used to determine the design and location of a shopping mall, hotel chain, or line of resorts.
Safety Advances Through Metaverse Simulations
On a personal level, the first time I benefitted from a metaverse platform was in my college Genetics Lab during the COVID-19 pandemic. The virtual lab platform showed a digitally developed version of myself, moving around the lab, and completing various tasks. One day, I added an incorrect chemical to a solution, resulting in a virtual ‘explosion.’ My computer screen went fuzzy, mimicking blurred vision. The screen read, “press keys 1 and 2 ’to 'run' to the eyewash station”. Due to the virtual setting, I learned a lesson without potentially harming my vision. Many biology, chemistry, or pre-medical students must complete in-person labs, but, as an Economics major, I was glad to learn from this mistake without requiring medical attention or taking up space in a hospital needed by someone else.
Metaverse platforms can prevent dangerous situations and allow individuals to practice preliminary skills without physical consequences. On a graver note, school systems and teachers could benefit from metaverse active shooter drills, allowing teachers and administrators to be better prepared without their students’ presence and potential psychological harm. Metaverse simulations could help pilots practice landing planes in difficult areas or prepare for emergencies. Additionally, metaverse platforms could help in talent acquisition for any career. With the pilot example, a candidate considering enrolling in flight school could use virtual reality technology to test-fly a plane and decide if aviation is a career of interest. Prospective university students whose families cannot afford to travel and tour universities in-person could experience college tours in the metaverse, with the colleges and university recruiters lending virtual reality headsets to high schools. In politics or business, individuals preparing to give a speech or presentation to a large audience could practice in the metaverse with a crowd in front of them, improving their presentation quality and lessening their nerves.
Limitations and Remaining Questions
The main questions remaining are: Is the marginal benefit from implementing metaverse randomized trials and safety measures greater than the marginal cost of adding these initiatives? Which demographics are most likely to adopt or embrace these initiatives? Is virtual reality technology accessible in quantity and price to allow the implementation of these initiatives on a large scale? In my opinion, the main limitation of metaverse platforms is the shortage of metaverse software developers and engineers paired with researchers to create scenarios that are realistic, life-like, and safe. Additionally, metaverse training must be combined with nontechnologically immersive scenarios. Consumers would likely not trust a pilot who has only flown planes in the metaverse. However, it could be an introduction. Additionally, the metaverse creates safety concerns such as an increased sedentary lifestyle, potentially discriminatory depiction of individuals, and developer bias. Technology is only helpful when it is additive to society, and not negatively manipulated. Any technological advance will come with advantages and disadvantages, especially in the early stages If metaverse technologies are used to successfully improve ESG considerations, especially waste management, this controversial virtual platform would drive positive change for many members of society.
References
Ben-Achour,S (2014,March10) What do stores do with unsold merchandise? Marketplace RetrievedMarch2,2023,from https://wwwmarketplaceorg/2014/03/10/what-do-stores-do-unsold-merchandise/ Dalton,M (2020,August17) What happens to all of the unsold clothes? TheWallStreetJournal RetrievedMarch2,2023,from https://wwwwsjcom/articles/fashions-big-question-what-to-do-with-all-those-unsold-clothes-11597328695
Devaney,S (2017,May3) Here's why 235 million items of clothing will end up in landfill sites in the UK this year HuffPostUK RetrievedMarch2,2023,from https://wwwhuffingtonpostcouk/entry/235-million-items-of-clothing-landfill-sites-in-the-uk-this-year uk 58e62581e4b0917d34776259
ESG - Feature Story Fall 2021.DukeLawMagazine.(2022,March1).RetrievedMarch2,2023,fromhttps://magazine.law.duke.edu/esg-feature-story-fall2021/
Hackl,C (2022,November9) Defining the metaverse Today Forbes RetrievedMarch2,2023,from https://wwwforbescom/sites/cathyhackl/2021/05/02/defining-the-metaverse-today/ PricewaterhouseCoopers (nd) 2022 US metaverse survey PwC RetrievedMarch2,2023,fromhttps://wwwpwccom/us/en/tech-effect/emergingtech/metaverse-surveyhtml
32
DOES IT REALLY HELP US STAY FIT?
By Ifeoma Osakwe
My relationship with my Apple Watch is borderline worrisome. Once, with barely five minutes to make the tenminute walk to my cycling group exercise class, I walked the whole way back to my dorm just because I forgot to wear the watch. In today’s technology-saturated world, however, I can take comfort in knowing that other gym-goers share this reliance on wearable fitness technology. After all, as clinical research specialist Brittney McCrary asserted, “Apple Watch or it doesn’t count” (Brown). Such perceptions of exercise arise from the growing prevalence of wearable fitness and healthcare devices and raise concern about how beneficial these devices truly are.

[RenderofAppleWatchHealthElectrocardiogram].(n.d.).

https://www.apple.com/apple-watch-series-8/

When motivating lifestyle interventions like increasing daily physical activity or water intake, however, wearables can be useful. In a 2021 study on members of a college community, Browne et al. showed that incorporating personalized feedback and encouragement in wearable fitness trackers caused improvements in participants’ sleep quality and physical activity (12). The same study suggests that when such tailored features are present, wearables help users form persistent healthy habits (11). These findings seem reasonable, as some Apple Watch users—including myself— often eagerly anticipate the digital award and accompanying celebratory message that the device presents when its user achieves a new personal best or completes a fitness goal. In this sense, fitness devices are valuable, especially for people who adopt the technology with the goal of bettering their lifestyles due to health concerns.

These devices primarily quantify exercise and health, providing values for heart rate, calories burned and sleep quality, among several other fitness indicators. Often, people working toward their fitness goals base health decisions on the numbers these screens display each day. For example, a dedicated calorie counter might calculate that their dinner must not exceed 150 calories because their Apple Watch reports that they failed to ‘max their rings’ by reaching their daily 650 calorie goal. The issue with this lifestyle is recent research suggests that, despite their reliability and validity in controlled environments, such as rest, wearable activity trackers are undependable in more variable circumstances, such as high-intensity training (Shei 1983). So, the daily calorie report could be an over- or under-estimation of the calorie counter’s physical activity and cannot give an accurate prescription for caloric intake to achieve their fitness goals. Technological advancements in the wearable fitness industry will address this inaccuracy concern but for now, meticulously tracking fitness indicators with these devices offers no direct benefit. [RenderofAppleWatchCoaching].(n.d.). https://www.apple.com/watch/close-your-rings/
Yet, the question remains: are wearable fitness devices beneficial to regular gym-goers or the otherwise active population? Limited as it is, the existing research on this topic is conflicting. One research study on student athletes suggests that forming lasting habits may render wearable fitness trackers unimportant for maintaining health and fitness, thereby replacing them altogether (Bardus 13). In contrast, another study on older adults shows that even after forming good exercise habits, long-term wearable users did not abandon their devices (Kononova 9). Further study is necessary to draw a definite conclusion about the effectiveness of wearables for the active group but we can be certain that the “Apple Watch or it doesn’t count” mentality is flawed. The reality is that challenging oneself to reach fitness goals is fantastic and remains so even when one deserts their wearable device.
As technology penetrates the health and fitness industry, people must responsibly navigate the multitude of healthmarketed devices as they make consumer decisions. Some fully appreciate these devices and refuse to part with them, regardless of scientific findings that they are not as reliable as their manufacturers will admit. Still, with plenty of room to improve at measuring fitness indicators, wearables have some merit as they can help users create and maintain healthy habits through personalized feedback. Scholars must continue to investigate these devices to fully understand their effectiveness, especially since these devices will not leave the fitness industry soon.
[RenderofAppleWatchHealthTemperature].(n.d.). https://www.apple.com/apple-watch-series-8/

WORKS CITED
Bardus, Marco et al. "Exploring the Use of Mobile and Wearable Technology among University Student Athletes in Lebanon: Brown, Dalvin. “'Apple Watch or It Doesn't Count': How Tech Addiction Might Be Ruining Your Workout.” USA Today,
A Cross-Sectional Study." Sensors, vol. 21, no. 13, 2021, p. 4472, doi:10.3390/s21134472.
Gannett Satellite Information Network, 16 May 2019, https://www.usatoday.com/story/tech/2019/05/15/fitbitsapple-watches-and-smartphones-can-actually-hurt-your-workout/1186522001/.
Browne, Jonathan D. et al. "Lifestyle Modification Using a Wearable Biometric Ring and Guided Feedback Improve Sleep
and Exercise Behaviors: A 12-Month Randomized, Placebo-Controlled Study." Frontiers in Physiology, vol. 12, 2021, doi:10.3389/fphys.2021.777874.
Kononova, Anastasia et al. "The Use of Wearable Activity Trackers among Older Adults: Focus Group Study of Tracker
Perceptions, Motivators, and Barriers in the Maintenance Stage of Behavior Change." JMIR Mhealth Uhealth, vol. 7, no. 4, 2019, p. e9832, doi:10.2196/mhealth.9832.
Shei, Ren-Jay et al. "Wearable Activity Trackers–Advanced Technology or Advanced Marketing?" European Journal of
Applied Physiology, vol. 122, no. 9, 2022, pp. 1975-90, doi:10.1007/s00421-022-04951-1.
34
IZZYBLAIR
IInherentOppressionandBiasin InherentOppressionandBiasin nherentOppressionandBiasin ttheTiktokAlgorithm theTiktokAlgorithm heTiktokAlgorithm
With over one billion people using the app every month (a), Tiktok has become one of the world’smostpopularsocialmediaandvideosharingapps.Whiletherearemanyreasonsfor the app ’ s popularity, the most known reason is the app ’ s astoundingly efficient and controversial algorithm for user video curation Each user has their own “For You Page”, on which the algorithm chooses videos for you based on your interaction with previous videos. Each user can also allow their data and activity to be tracked across other apps they use, much like Facebook does. TikTok has its own Community Guidelines and that all user videos must follow, as well as “technology that identifies and flags potential policy violations, such as adult nudity and violent and graphic content” (b) to keep these rules in check However, withthistechnologycomesalotofbiasesthatusershavenoticed.

Thephenomenonofthe“echochamber”isonethatT users are familiar with. It describes the concept tha algorithm gives each user a video that perpetuate typeofcontenttheuserhasalreadyexpressedintere Ifauserrepeatedlylikes,comments,and/orsharesvi about knitting, they will get even more knitting video their For You Page This is why Tiktok is so popul rewards higher levels of activity with more conten userwillenjoy,thuscreatinganechochamber.
While this is great for users who enjoy knitting, there is a dark side to this echo chamber one that can perpetuate hateful ideas and videos One would think that the same technology that flags adult nudity and other visual content violations would also be able to flag these hateful ideologies as dangerous, but there is no such proof of any technology Of course, Tiktok has human reviewers who go through each flag, but there are still many cases of hateful ideologies not being flagged or punished in any way One user reported that his profile bio was flagged for using the word “black” in any capacity, whether it was “I am a black man ” to “Black Lives Matter” (c) However, the phrases “white supremacy ” and “I am a neo-Nazi" did not prompt the same flags for violations. The same algorithm that supposedly brings “ new content” into the user ’ s feed is the same one that narrows down the scope of what a user is actually consuming. In a country as politically, economically, and socially polarized as the United States, the creation of barriers between users with different viewpoints creates tension between a user and anyone who disagrees with them This brings up an important question: are these biases just simple errors in the algorithm, or was this intentional?

ThisechochamberideologyisperpetuatedindifferentalgorithmsonTiktok specifically, thealgorithmthatsuggestsnewaccountstofollow Inanonformalexperimentperformed byTwitteruserMarcFaddoul,anewTiktokaccountwascreatedforasinglepurpose:to follow random accounts and see what accounts would pop up on the suggested people bar Faddoul found that the physical features of the original account that he followed woulddeterminethesuggestionsforotheraccountstofollow IfFaddoulfollowedPerson A, who was a white woman with blonde hair, then he would get Person B and Person C, two other white women with blonde hair, recommended for him to follow This algorithm transcendsjustraceandgender Faddoulfoundthathairdye,bodytype,age,andvisible disabilityofuserswerealsofactors Heconcludedthatthisalgorithmassumesthatifone follows, say, an Asian teen with dyed hair, it is because the user is an Asian teen with dyed hair, and not for their humor, videos, or other aspects of their content Faddoul remarked that while it is not unusual for social media algorithms to create “bubbles” for things like political opinions, Tiktok seems to be the “first major platform to create such clearphysiognomicbubbles” (d)
Theseclearlybiasedalgorithmshaveanevenwiderrangeofimpact.Whiletheydoaffectvideo and profile curation for users, they also affect content creators in perhaps an even more devastating way When videos and profiles are so easily flagged for content violations and reliantonthe“physiognomicbubbles”togainmorefollowersandalargeraudience,creatorsin minoritygroupsareautomaticallydisadvantaged Notonlyaretheylesslikelytogainfame,but theyalsofallpreytoplagiarismandoutrightrobberyoftheircontent TheNewYorkTimeswrote anarticlein2020tellingthestoryoftheoriginalcreatorofthepopular“Renegade”danceon Tiktok.Thiscreator,JalaiahHarmon(picturedleft),sawherdancebeingreplicatedbysomeof the most popular and white creators on Tiktok, as her videos gained no more popularity and shereceivednocreditforherdance (e)
This story is one that BIPOC creators on Tiktok know well as they continue to experience algorithmic biases in this way. These same algorithms meant to be fair and unbiased have been the cause of the segregationandsilencingofBIPOCcreatorsandusersonTiktok Whileitwouldbeeasytojustblame theseproblemson“glitchesinthecode”,itisimportanttorecognizethatbiasedalgorithmsarecreated bybiasedhumans Thisiswhyitisimportanttoconductmoreformalresearchonracialbiaseswithinthe Tiktokalgorithminordertounderstandwhythisishappening.Furthermore,Tiktokisaperfectexample of why it is important that coding becomes more diverse A diverse array of people creating the algorithms would lead to less chance of biases like the ones on Tiktok. A more inclusive and safer Internet for everyone – one where diverse perspectives are cherished and users are encouraged to questionthingsandgrow-startswithdiversityatthesoftwarelevel.



Sources:
https://newsroomtiktokcom/en-us/1-billion-people-on-tiktok
https://wwwtiktokcom/community-guidelines?lang=en#38
https://www.nbcnews.com/news/us-news/tiktok-algorithm-prevents-user-declaring-support-black-lives-matter-n1273413
https://twittercom/MarcFaddoul/status/1232014908536938498?
ref src=twsrc%5Etfw%7Ctwcamp%5Etweetembed&ref url=https%3A%2F%2Fwwwbuzzfeednewscom%2Farticle%2Flaurenst rapagiel%2Ftiktok-algorithim-racial-bias
https://wwwnytimescom/2020/02/13/style/the-original-renegadehtml a b c. d e 36
AIANDTHE SUPPLYCHAIN REVOLUTION
By Ananya Anand
Nowmorethanever,allofushaveunlimited choices.Wecanchoosetobuyclothesfroma companyintheUKAfactorycanchooseto buyitsrawmaterialsfromChina.Countriescan importfoodsandbeveragesfromalmost anywherearoundtheglobe.Theprevalenceof suchextensivechoicesexistsasaresultofan invisiblegrid-ArtificialIntelligence.
Overtheyears,‘ArtificialIntelligence’moved frombeingjargoninSiliconValleytoeveryday vocabulary.ButwhatisArtificialIntelligence?
CommonlyknownasAI,ArtificialIntelligenceis thescienceofbuildingcomputerprogramsthat understandandbuildonhumanintelligence.AI requiresafoundationofspecializedhardwareand softwareforwritingandtrainingalgorithms I liketodefineAIasa“superbrain”thatmimicsa humanbrainbutwiththememory,storage,and speedofacomputer.
WiththenewdevelopmentsinAI,more companiesandcorporationsarelookingtoadopt differentmodelsofsupplychainmanagement OnesuchcompanyisAccenture,whichprides itselfonusingthelatesttechnologytoefficiently carryouttheprocessesofsupplychain management AsAccenturedefinesit,“Today’s supplychainsaremorecomplexthanlinear models they’resophisticatedsupplynetworks thataremoreflexibleandefficient.Thishelps meetcustomerexpectationsforawideselection ofcustomized,sustainableproductsandfast deliveriesthatmeetindividuals’specificneeds”
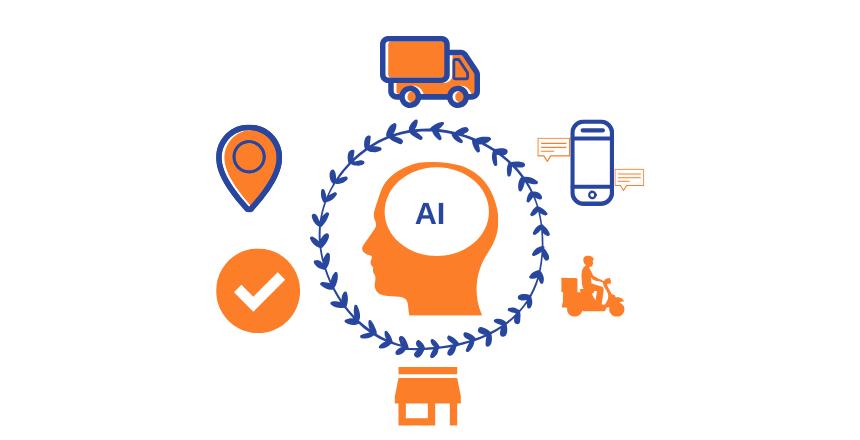
Supplychainmanagementcanbebrokendown intofivebroadprocesses-logistics,production, procurement,marketing,andsales.Thelogistical facetofsupplychainsinvolvesthemaintenance ofdata,servingasthebackboneoftheentire structure Thisconstitutesstoringaplethoraof informationrangingfrominventoryandlabor wagestoweatherconditionsandtransportation bottlenecks.Thisinformationprovidesthe frameworktoensurethesmoothrunningofall otherpartsofthesupplychain Immediateaccess todataandintelligenceallowsflexibilitywithin thebusinessandallowsthesupplychaintoadapt easilytovaryingsituations.Thismakessurethat boththesupplyanddemandsideoftheenterprise runscoherently
Next,productionandprocurement Anysupply chainworksonthemodelofmultipleiterative tasks,byautomatingsuchtasks,thecostoflabor decreasesandallthegoodsareconsistent.The intelligencecanalsobeusedtoidentify inefficiencyintheprocessofproduction, focusingthehumanworkforcetowardmore complexandstrategicallyimportanttasks.Data integrationwithsuppliersenablesthe optimizationofprocurementofrawmaterials basedonforecastedprices
Followingproductionandprocurement,thenext stageinthesupplychainismarketingandsales. Thisstageneedsdataandinformationthatbuilds onthepreviousstepsofthesupplychain The DeepNeuralNetwork(DNN)iscomposedof layersofnonlineartransformationnode functions,wheretheoutputofeachlayer becomesaninputtothenextlayerinthe network Makingtheintangiblefragmentsofthe supplychainjustaswellconnectedasthephysical fragmentsofthesupplychain Predictivedata fromthedifferentsegmentsofthenetworkcan beusedtomatchthemarketexpectationswith theproductionfromthesupplychain Andthus bringalltheprocessestogethertoformwhatwe knowasSupplyChainManagement
Sources
Accenture.“WhatIsSupplyChainManagement(SCM)?” Accenture,Accenture,30Mar2023, https://www.accenture.com/us-en/insights/supply-chainoperations/supply-chain-management-operations-index
Bajwa,Rumzz“HowAIIsEnhancingSupplyChain Performance”GlobalTradeMagazine,TheAuthorityFor USCompaniesDoingBusinessGlobally,29May2021, https://wwwglobaltrademagcom/how-ai-is-enhancingsupply-chain-performance/
Burns,Ed,etal“WhatIsArtificialIntelligence(AI)?-Ai DefinitionandHowItWorks”EnterpriseAI,TechTarget, 31Mar2023, https://wwwtechtargetcom/searchenterpriseai/definition/ AI-Artificial-Intelligence.
Meltzer,JoshuaP.“TheImpactofArtificialIntelligenceon InternationalTrade”Brookings,Brookings,9Mar2022, https://www.brookings.edu/research/the-impact-ofartificial-intelligence-on-international-trade/
“SucceedingintheAISupply-ChainRevolution”McKinsey &Company,McKinsey&Company,30Apr2021, https://wwwmckinseycom/industries/metals-andmining/our-insights/succeeding-in-the-ai-supply-chainrevolution
“WhatIsArtificialIntelligence(AI)?”IBM, https://wwwibmcom/topics/artificial-intelligence

38
CCLOUDCOMPUTING LOUDCOMPUTING AANDCLIMATE NDCLIMATE CCONSCIOUSNESS ONSCIOUSNESS
By:EvanHendrickson
TheblueprintforCloud Computingbeganina 1963projectinwhich researchers hoped to develop a way for multiple people to work simultaneously onthesamecomputer
ThisdevelopmentpromptedJCR Licklider,oneofthemostrevered computerscientistsofthe1900s,to envision the “Intergalactic ComputerNetwork”Thisnetwork wouldinterconnecttheentireglobe, make information readily accessible,andsoonbecomewhat weknowastheInternetBythelate 1990s, modern Cloud Computing infrastructurecametofruition,and manycompaniesbegantoseeitasa valuable business asset. Most notably, Salesforce became the global leader in harnessing the cloudforbusinessvaluebymaking itssoftwaredownloadabletoclients directlythroughtheInternet This allowed for the on-demand purchasingofsoftwarepackages,a muchmorefeasibleoptionforboth thevendorandtheclient.Bythe early 2000s, Amazon began capitalizing on Cloud Computing infrastructurewhenitlaunchedits online retail service and Amazon WebServices,andGooglelaunched Google Docs and Spreadsheets, bothofwhichpromptedotherlarge corporations to follow Today, Software-as-a-Service, made popularbyOracle,andapplication
developmenttoolsarethemostwidely usedformsofthecloudandcontinue tobetwoofthemostrapidlygrowing applicationsofthistechnologySimply put, Cloud Computing today is the rapiddeliveryofcomputingservices fromaremoteserverviatheInternet Bystoringtheseinthecloud,database storage/management, computing power, software, analytics, etc, can become more innovative, readily accessible,andlargerinscale.
Traditional data centers consume billions of kilowatt-hours of energy andemitmillionsoftonsofcarbon annuallytorunandcoolequipment, nottomentionthegreenhousegases produced to manufacture and transport these large pieces of hardware Public pressure to push majorcorporationstowardsoptingfor moresustainableenergysourcesand ultimately transition their business infrastructuretothecloudisbecoming
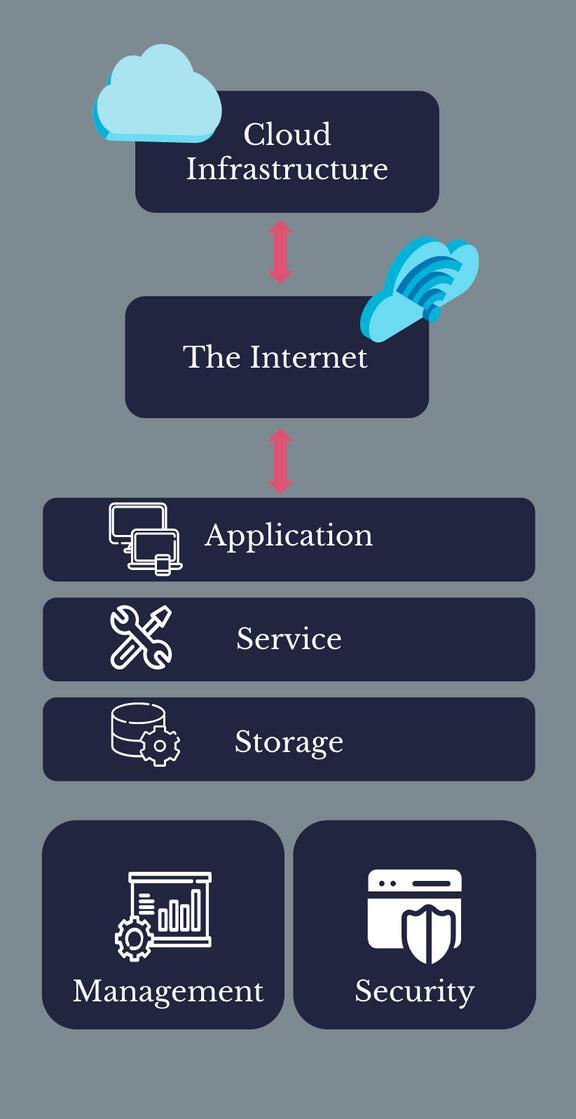
 AhighleveloverviewofCloudComputingArchitecture
AhighleveloverviewofCloudComputingArchitecture
moreintenseastheplanet’sclimate crisisworsensAmazon,Google,and Microsofthavepledgedtodeploy more sustainable energy sources andachievenet-zeroemissionsin the coming years, triggering an industry-widecompetitiontobethe firstBigTechcompanytoachievea net-zero carbon business infrastructure.
Research has shown that moving toward cloud-based alternatives would drastically reduce greenhouse gas emissions: more thanonebillionmetrictonsofCO2 emissionscouldbeeliminatedover athree-yearperiod,whichcanbe compared to the typical CO2 emissions of “35 commercial airliners, 216,000 passenger vehicles,and115,000homesinthe UnitedStates”overayear.Shared datacentersforCloudComputing also show the ability to run efficientlyusingrenewableenergy sources Mostofthesecentersare poweredusinggeothermal,hydro, solar, or wind power and save enoughenergytopowertheentire city of Los Angeles for one year compared to the non-Cloud Computing alternative Furthermore, Cloud Computing wouldhaltthegrowthofthe“ewaste mountain” of obsolete or broken electronic equipment in landfills that piles on 53 million metrictonsofwasteyearly Cloud Computing would significantly reduce the need to invest in hardware because Cloud Computing promotes dematerialization: the movement from physical hardware to cloud alternatives If the environmental benefitsarenotenticingenough,it is estimated that the largest US companies could save billions of dollars in energy expenditures if they adopted a cloud-based infrastructure
Although Cloud Computing is a promising step toward corporate carbon neutrality, this shift must occur with haste to avoid catastrophe for traditional and clouddatacentersalikeIn2009in both Turkey and Taiwan, data centers were decimated due to heavy rainfall In Turkey, this nearlycausedafourthofIkitelli’s localnetworktobecompromised. InTaiwan,thefloodingdeposited
somuchsedimentintotheocean that underwater landslides broke several communication cables buriedtwoandahalfmilesbelow the surface, compromising the Internetandtelecommunicationsof multiplecountriesintheregionAs sealevelscontinuetorise,undersea fiber optic cables--which handle almostallglobalcommunications-areatriskofbreakingastheseabed becomes more volatile. All major companies must prioritize the transitiontothecloudtoavoidthis moreclimateconsciousalternative falling victim to climate change’s effectsthatwouldrenderituseless Although damage to the environment cannot be reversed, this would be a significant step towardacleaner,moresustainable industryandearth
References
Bressler,RD(2021)Themortalitycost ofcarbonNatureCommunications, 12(1)https://doiorg/101038/s41467-02124487-w
Foster,P(2011,August18)Cloud computing–agreenopportunityor climatechangerisk?TheGuardian;The Guardian https://wwwtheguardiancom/sustainabl e-business/cloud-computing-climatechange
Foote,K.D.(2021,December17).ABrief HistoryofCloudComputingDATAVERSITYDATAVERSITY https://wwwdataversitynet/briefhistory-cloud-computing/
Francis,T(2021,September20)The nextbigcloudcompetitionistheraceto zeroemissionsWorldEconomic Forum https://wwwweforumorg/agenda/2021/ 09/the-next-big-cloud-competition-isthe-race-to-zero-emissions/
Gal,A(2022,July25)CouncilPost:The Power-ComputingWeaponThatIs FightingClimateChangeForbes https://wwwforbescom/sites/forbestech council/2022/07/22/the-powercomputing-weapon-that-is-fightingclimate-change/?sh=353bd8433dc4
Oberhaus,D(2019,December10) Amazon,Google,Microsoft:Here’sWho HastheGreenestCloudWIRED; WIRED https://wwwwiredcom/story/amazongoogle-microsoft-green-clouds-andhyperscale-data-centers/
ProdecNetworks(2021)5wayscloud computingcouldhelpsavetheplanet Prodeccouk https://wwwprodeccouk/insights/5ways-cloud-computing-could-helpsave-theplanet/#::text=In%20addition%20to%20 directly%20cutting,users%20to%20travel %20as%20much
Trueman,C(2019,August9)What impactaredatacentreshavingon climatechange?Computerworld https://wwwcomputerworldcom/article /3431148/why-data-centres-are-the-newfrontier-in-the-fight-against-climatechangehtml
40
Traumatic brain injury (TBI) is defined as a sudden trauma to the brain and is one of the leading causes of death worldwide (Ghajar 2000). At the same time, there continues to be no effective therapies to treat TBIs due to a limited understanding of the pathologies involved. Not only that, there is an imbalance in TBI research in regard to gender and sex differences. In 1993, the NIH put into law that women must be included in clinical research, but it was not until 2014 that the NIH stated that all funded research must use both male and female cells and test animals in pre-clinical studies (NIH 2022). However, research supported before 2014 can continue to operate studies involving only
RESEARCH ABOUT WOMEN'S BRAINS LOADING....
By Winna Xia
male pre-clinical studies. This leads to health professionals and scientists making dangerous assumptions about how similar peoples' bodies react to TBIs regardless of gender. Many past studies show that biologically female and male brains are very different from one another in size to the way neurons are wired (Brizendine 2006; Ingalhalikar 2014).
One of the main reasons women have not been historically included in the research is due to the 'complexity' of the ovarian cycle.
For many scientists, the ovarian cycle is another independent variable that is an annoyance to accommodate, and not a good representation of how the medication affects an individual (Castanon 2022).
Yet, even though past years have failed to accommodate this, half of the human population is affected by the ovarian cycle. Even though it is another independent variable, it is not one that can be brushed away.
In recent years, there have been efforts to level this inequity in research. In 2017, there was the “Understanding TBI in Women” workshop co-hosted by NIH, the Center for Neuroscience and Regenerative Medicine, and the Defense and Veterans Brain Injury Center in an effort to identify “knowledge gaps, best practices, and target populations relevant to research on sex differences and women with TBI." (Mollayeva and Colantonio 2020)
Additionally, there is new ongoing research (Armitage 2022, Valera 2021) focused on bridging these knowledge gaps and finding the why behind the differences between male and female responses to therapeutical treatments in intracranial injuries like TBI. TBI remains a consistent issue that has few therapeutic treatments for both males and females. However, with more equitable research and time, there is a possible therapeutic treatment that will work for everyone on the horizon.
Sources
Armitage, Hanae “Why Women Have a Tougher Time Recovering from Brain Injuries.” Stanford Medicine Magazine, 22 Sept. 2022, https://stanmed.stanford.edu/brain-injury-recovery-more-difficult-womenthan-men/
Brizendine, Louann. The Female Brain. United States, Morgan Road Books, 2006
Ingalhalikar, Madhura, et al. “Sex differences in the structural connectome of the human brain ” Proceedings of the National Academy of Sciences of the United States of America vol. 111,2(2014): 823-8. doi:10.1073/pnas.1316909110
Castanon, Laura “Most Biomedical Research Is Done on Male Animals That's a Public Health Problem.” Northeastern Global News, 30 Mar. 2022
Mollayeva, Tatyana, and Colantonio, Angela “Sex, Gender, and Traumatic Brain Injury: Implications for Better Science and Practice.” Brain Injury Association of America, 7 July 2020, https://www.biausa.org/publicaffairs/media/sex-gender-and-traumatic-brain-injury-implications- forbetter-science-and-practice.
Valera, Eve M et al “Understanding Traumatic Brain Injury in Females: A State-of-the-Art Summary and Future Directions.” The Journal of head trauma rehabilitation vol. 36,1 (2021):E1-E17. doi:10 1097/HTR 0000000000000652
hi
42
AFemale Recession


of2019,theSARS-CoV-2 virusemerged,launchingtheworldinto oneofthedeadliestpandemicsknown todateCovid-19,thediseasespreadby thisvirus,ischaracterizedbyquitea fewsymptomsrangingfromfeverand difficultybreathingallthewayto nauseaandvomitingThisdisease spreadsrapidlyasdropletsfroman infectedpersonspreadthroughtheir breathing,coughing,laughing,etc.In ordertopreventinfection,aquarantine periodalongwithmaskandvaccine mandateswereinstatedbymultipleUS states,municipalities,andprivate entities.





TessKleanthous 20222023



Thispandemic,whiledevastatingintermsofits physicalhealthimplications,changedeveryday life,evenforthosewhoremaineduninfectedThe quarantineperiodinstateddramaticallychanged workculture,somebusinessesevenpermanently shiftingtothepart-timeofficemodelafterquarantineandmaskmandateswereliftedIt’sno secretthatthisshiftintheworkenvironmentcausedaseveredisruptionineverydaydomestic life,buthowhasthisaffectedwomenintheworkforceastheyareforcedbackintothesamehome thattheywereonceconfinedtoduetoinequality?Nowwearehere,notbecauseofostracization fromprofessionallife,butbecauseofaneedforsurvival.However,womenarenottheonlyones throwndirectlybackintodomesticlifeastheirchildrenarenowalsoleft unattended.Thepandemichasseemedtostrikeadevastatingblowtothe childcaresector:4.5millionchildcareslotspotentiallybeinglostpermanently. Withnearly10millionworkingmothersintheUS,weneedtothink abouthowthisshiftintothehomecanaffectwomen’s work,wages,long-termeconomicoutcomes,aswellas whateconomicandprofessionalrecoverymayresemble Reportsaredetailingthatfourtimesasmanywomen droppedoutoftheworkforceinSeptember2020dueto inadequatechildcarecausedbythepandemic,the numberscomingouttoroughly865,000womencompared to216,000menThisstepbackfromprofessionallifeis


largelyfallenonwomenregardlessoftheprogressionswehavemadeinthegender equalityrealm:theindividualwithinthemorefeminineroleofthehousehold bearingtheresponsibilityformostifnotalloffamilycareAKFFWomen'sHealth

showingapotentialwagelossamountingtoapproximately$64.5billionper yearforwomenacrossthecountryFamilycaregivingresponsibilitieshave surveyconductedinearly2021hasfoundthatoneintenwomenhavereportedthat

theywerealreadytakingcareofafamilymemberwhoneededspecialassistancepriortothe pandemic.Whilethisisalreadysignificantlyhigherthanthepercentageofmencaringfora familymemberwithsimilarissues(14%vs9%respectively),women’sparentalrolesintheir familieslives’haveonlycontinuedtogrowfromtherewithoveroneintenwomenreporting thattheyhavegainednewcaregivingresponsibilitiesasaresultoftheCovid-19Pandemic Knowingthishasbeentheoutcomeofaglobalpandemicforwomenintheworkforce,whatcanwe dotocounteractthatharmthathasbeendone?It’stimeto“[Reinvent]theLeadershipJourneyfor WomeninTech.”Todothisthereareafewthingswemusttakeintoconsideration:thefactthat WomenofColordonothavethesameexperienceaswhitewomenandthefactthatseniorlevel womendonothavethesameexperienceasmidlevelwomen.AccordingtoaBCGsurvey,47%of WOCsaiditwasmoredifficulttocommunicatewithsupervisorsandmentorsasopposedto35%of whitewomen.Inadditiontothis,bothWOCandwhitewomenspentthesamenumberofhourson caregivingduties,however15%ofminorityrespondentsreportedthattheywerecaringforboth childrenandotherrelativesasopposedto8%ofwhiterespondentsIntermsofhowan authoritativeroleaffectedwomen'sexperience,33%ofwomeninseniorpositionspivotedtheir professionalidentityduringthepandemicwhereaswomenholdingmid-levelpositionswereless likelytodosoduetoadecreaseinflexibility.
Inordertosupportallwomenintech,regardlessoftheir identity,companiesmustkeepacloseeyeontheircompany culture.Forstarters,providingavarietyofpathwaysto leadershiptoaccommodatethosewhohavenothada traditionaljourneyandidentifyingwhataddsvaluetothe manager-employeerelationshiparegreatwaysthatemployerscan supporttheiremployeesinthesetimes.Supportingmentorship sponsorshipactivitiesinahybridenvironmentaswellasreassessing whatroutinesalignwiththenewworkmodelhavealsobecome increasinglypopularThiswilllookdifferentfordifferentcompanies, butmanagersmustlearntotakeintoconsiderationthenewwork-life balanceThismeansnormalizingthingssuchastemporaryleavefor bothcaregiversandnon-caregiversandensuringthatanysupport giventocaregiverssupportingchildrenextendstothosesupporting childrenandotherfamilymembersaccordingly.
https://wwwhopkinsmedicin eorg/health/conditions-anddiseases/coronavirus





https://www.americanprogre ssorg/article/covid-19-sentwomens-workforce-progressbackward/

https://www.kff.org/womenshealth-policy/issuebrief/women-work-andfamily-during-covid-19findings-from-the-kffwomens-health-survey/
https://wwwbcgcom/publica tions/2022/reinventing-theleadership-journey-forwomen-in-tech
44
Sources
WOMENAREHUNGRY FORCHANGE

THEGENDERGAPINFOODSECURITY
BY:MEGHANNAGIA
Foodinsecurityisreal Itisalsosexist Foodisabasichumanright However,genderinequalityplaysa prominentroleinpushingmorewomenintohungerthanmen Thenumberofwomensufferingfromhunger inanycountryisdirectlyproportionaltothenation’sgendergap Althoughhungerhasbeenanongoingglobal issue,in2021,59%ofthe828millionpeoplesufferingfromhungerwerewomen Since2021,150millionmore womenarefoodinsecurethanmenwiththegapcontinuouslywidening(Gilchrist).
Foodinsecurityisasocial,biological,nutritional,andeconomicphenomenon.Itcanbedefinedasthe uncertaintyofhavingortheinabilitytoacquireadequatefoodintakeforallhouseholdmembers(PublicHealth Nutrition).Womeninmanypartsoftheworldarelesslikelytohavethesameopportunitiesandresourcesas men;thisinequityisalsovisibleintheirlackofaccesstosufficientandnutritiousfoodtomeettheirfood preferencesanddietaryneeds,requiredforahealthylifestyle
AccordingtotheWorldFoodProgram(USA),innearlytwothirdsoftheworld’scountries,womenaremore likelytobehungrythanmen Womenalsosufferthemostfrommalnutritionandmacro-/micro-nutrient deficiencies Myriadfactors,aspresentedbelow,contributetothisgenderedhungergap:
Sexist norms, beliefs, and traditions
In some patriarchal cultures discriminatory social and cultural norms prevail even today. Sadly, some traditional societies treat women to be of an inferior status than men and expect them to sacrifice their food for their families. Women eat last, after the men or children in the household have been fed or they skip meals altogether
Lack of economic independence
In many parts of the world women are still dependent on their male counterparts for financial needs. They are not encouraged to be in the workforce or seek financial autonomy. Financial inequality is also visible among women working in agricultural farms under strenuous conditions who are not allowed to be landowners or paid the same wages as men. Furthermore, “there are 18 countries (e.g., Iran, Bahrain and Qatar) where husbands can legally prevent their wives from getting a job” (wfpusa). In several countries, females receive less, or no education compared to their male counterparts which decreases their chances to be gainfully employed and impacts their decision-making power. Whether toiling at home or on the farm, being “unpaid or underpaid” is normalized; this increases women’s likelihood of living in poverty more than men despite enduring hard work and physical labor.
Discriminatory laws and unequal rights
In many countries, women have fewer rights and power than men. For example, when men own land, women’s access to livestock, agriculture, and water rights decreases, resulting in lower crop yield and income. In several areas, females are subjected to gender-based domestic violence. The UN reports that 7090% of Pakistani women experience some form of physical or psychological abuse from their spouse or intimate partner. Lack of stringent laws or their effective enforcement powers men and boys to perpetuate disrespectful or abusive acts against women including denial of their basic right to a nutritious meal.
Disasters and conflicts
Extreme weather conditions, climate change, and man-made conflicts drive economic distress and famine. Several regions in the world are regularly hit by natural disasters such as droughts while other areas are vulnerable to devastating floods or typhoons. These unexpected catastrophes impair economic conditions and lead to poor water quality and food scarcity. Additionally, in countries ravaged by war, more often women and children are subjected to violence. They are forced to flee and live in overcrowded camps with unsanitary conditions, exposed to malnutrition or diseases such as HIV and AIDS, while having no access to a healthy and wholesome meal. At times they may also face famine which is the most extreme form of food insecurity.
Food insecurity has an adverse impact on the health and wellbeing of women and girls. Malnutrition, obesity, or depression are some of the health consequences suffered by women facing food insecurity. Pregnant women facing food insecurity are at a higher risk of gestational diabetes, iron deficiency, and low birth weight.
The four ‘pillars’ of food and nutrition security are availability, access, utilization, and stability. It is argued that food security for all will be achieved when these pillars are adequately realized. Many in developed nations take access to food for granted, when there are many “food deserts” or repressive regions and communities where women are denied proper nutrition and sufficient food.
With a hyper sense of urgency, the world must unite to eliminate food deserts and push for a shared global vision of gender-just food security where men and women have equal access to healthy and nutritious food. A few immediate interventions that can shrink the inequity in gender-based food insecurity include:
Empowering women through equal right to education will enhance their knowledge and decision making power
Breaking down antiquated social norms and dismantling unjust laws including women’s land ownership
Offering economic independence by creating more jobs for women
Closing the gender wage gap to increase affordability of food and other necessities of life.
Food is an essential ingredient for survival. Not knowing where the next meal will come from can be stressful and daunting. Hunger stifles proper functioning of the body. However, many women are enduring this crisis every day. Let us come together to amplify our voices against gender-driven food insecurity and aspire for a zero-hunger world where neither women nor men are starved for food.
Sources Bapolisi,WyvineAnsima,etal.“GenderedDeterminantsofFoodInsecurityinOngoingRegionalConflicts,NorthandSouthKivu,theDemocraticRepublicofCongo-Agriculture& FoodSecurity.”BioMedCentral,BioMedCentral,28Apr.2021,https://agricultureandfoodsecurity.biomedcentral.com/articles/10.1186/s40066-021-0028
Botreau,Hélène,andMarcJ.Cohen.“GenderInequalityandFoodInsecurity:ADozenYearsaftertheFoodPriceCrisis,RuralWomenStillBeartheBruntofPovertyandHunger.” AdvancesinFoodSecurityandSustainability,ElsevierInc.,2020,https://www.ncbi.nlm.nih.gov/pmc/articles/PMC7526640/.5-x. FoodSecurityandGender-OECD.https://www.oecd.org/dac/gender-development/46460857.pdf.
“GenderInequalityCausesMoreWomentoSufferfromHunger&Poverty.”WorldFoodProgramUSA,8Mar.2022,https://www.wfpusa.org/articles/women-in-crisis-top-wayswomen-are-hungrier/.
Gilchrist,Karen.“GlobalFoodCrisisSees150MillionMoreWomenthanMenGoingHungry-and'It'sGoingtoGetWorse'.”CNBC,CNBC,30Aug.2022, https://www.cnbc.com/2022/08/30/global-food-crisis-sees-150-million-more-women-than-men-going-hungry.html.
Jung,NatáliaMiranda,etal.“GenderDifferencesinthePrevalenceofHouseholdFoodInsecurity:ASystematicReviewandMeta-Analysis:PublicHealthNutrition.”Cambridge Core,CambridgeUniversityPress,10Nov.2016,https://www.cambridge.org/core/journals/public-health-nutrition/article/gender-differences-in-the-prevalence-of-householdfood-insecurity-a-systematic-review-and-metaanalysis/B3B0DE2E04C0413E48267E63B400EC36.
“WomenAreHungrier.”WorldFoodProgramUSA,https://www.wfpusa.org/women-are-hungrier-infographic/.
46
ARTIFICIAL INTELLIGENCE & ARTIFICIAL INTELLIGENCE & ARTIFICIAL INTELLIGENCE &
MACHINE LEARNING: MACHINE LEARNING: MACHINE LEARNING:
HOW IT WORKS, AND HOW IT FAILS HOW IT WORKS, AND HOW IT FAILS HOW IT WORKS, AND HOW IT FAILS
The rise of machine learning and artificial intelligence has led to mind-boggling technological developments that have impacted our lives immensely From viral videos of Boston Dynamics robots doing backflips to Netflix recommendations on what to watch next, we cannot go a day without AI trying to make our lives easier. But for underrepresented individuals––LGBTQ+, racial minorities, etc ––there is significant harm being done instead How do these artificial intelligence models work? What are the basic processes happening to make them? A computer is only as smart as we make it––how could they be discriminating against these individuals, and is it possible to stop this?
WHAT IS ML? WHAT IS ML? WHAT IS ML?
Machine learning (ML), a subgenre of artificial intelligence, is truly a fascinating and innovative technological advancement. The idea behind this process is to, quite literally, teach a machine how to learn so that it can make logical predictions based on data it has already analyzed before To those unfamiliar with machine learning (and even to those who are), it really does seem like magic. But to understand how and why underrepresented individuals are being harmed by some of these algorithms, it is important to understand how a basic machine learning algorithm works. Though there are many different algorithms out there, the main process occurring in all of them stems from a common idea: calculating distances between data points For example, the number of streams of a song would be quantitative data, while the genre that a song fits into would be categorical data. It is important to understand what kind of data we are working with when it comes to implementing ML algorithms because we will need to adjust them accordingly.
One of the most common algorithms, knearest neighbors (KNN) regression/ classification, generates a predicted value for a particular label based on a set of features. For example, given sufficient data, one could generate a predicted temperature value for a specific day based on factors such as wind, humidity, distance from the ocean, and more But how does the algorithm really work?
Let’s continue with our example of predicting temperature. Say that we have a dataset of 730 rows where each row corresponds to a day over the past 2 years. There are several columns to describe these rows, such as the factors described above (wind, humidity, distance from the ocean, and more). Using this preconstructed dataset, we can iterate through each observation (day) in the dataset and generate a predicted temperature value by looking at the k nearest neighbors in the dataset, where the value of k is up to us. We can find the mean of these k neighbors’ temperature values and use that as our prediction. This is a very basic machine learning algorithm, but this idea of extrapolating based on averaged distance or error between points is a common idea that shows up in all machine learning algorithms But what if the dataset we used to build this predictive model only contained weather data from, say, Antarctica?
This data would not extrapolate well to a different environment, such as Jamaica in the summertime. Since a model only learns based off the data we supply, it would likely make inaccurate predictions for new, different data In order to combat this, we would need to feed the model diverse data that contains many different kinds of weather observations.
WRITTEN BY SAM DEMARINIS
KNN ALGORITHM KNN ALGORITHM KNN ALGORITHM
WHAT COULD GO WRONG? WHAT COULD GO WRONG? WHAT COULD GO WRONG?
Unfortunately, ML will inherently misunderstand and mislabel members of the LGBTQ+ community, racial minorities, and disabled people. Let’s start by examining how the LGBTQ+ community is being hurt. As cited in the article, “Why Artificial Intelligence Is Set Up to Fail LGBTQ People,” anthropologist Mary L Gray states that LGBTQ+ people are “constantly remaking” their community For algorithms that are built upon previous observed data, this raises concerns Individuals who identify as LGBTQ+ will go through a life-long journey with their identity, and as they evolve and change, algorithms will not be able to keep up. They will continue to calculate data points with the least amount of distance to a new data point to make ‘logical’ predictions. But when data points represent people, with unique and extensive identities, this does not lead to accurate predictions Instead, it results in misclassification that can be harmful to an individual’s security in their identity. Take Automatic Gender Recognition, for example, that is built on training data of mostly cisgendered males and females. To classify a new person’s gender, the algorithm compares their physical facial features to those in the training data to make a logical classification.
Many transgender individuals are being harmed by these superficial assumptions
When it comes to racial minorities, we are seeing significant biases especially in the medical field. Algorithms that predict which patients need care have been unintentionally discriminating against black people. In their study entitled “Dissecting racial bias in an algorithm used to manage the health of populations”, Obermeyer et al. examined a commonly used medical ML algorithm and found that black patients needed to be significantly sicker than white patients to be recommended for the same type of care The reason that we see such biases in this algorithm is because the model was built on “past data on health care spending, which reflects a history in which Black patients had less to spend on their health care compared to white patients, due to longstanding wealth and income disparities” (Grant). Since the data has been strongly impacted by such racial issues, the model reflects this and
results in more recommendations for white people to receive care This is a major issue because black patients may require care but not receive it due to the model’s biases
SSOLUTIONS SOLUTIONS OLUTIONS
The main solution that many people suggest is to build ML models on data that is unbiased. For the example of racist models in the medical field, this would look like building a model on data that does not strictly contain healthcare spending history for white and black Americans, but rather includes other factors that don’t misrepresent black Americans. The reason is that ML models try to make predictions based on data points that are most like the new, unlabeled data point. If a model is built on data that is not accurate or representative of a population, we see these kinds of problems. For issues involving the labeling of LGBTQ+ individuals, it is likely not enough to build a model on unbiased data Groups that are constantly evolving will continue to be hurt by algorithms that are based on previously seen data While these predictions may be accurate at times, they may not hold up in the future, so it is likely that AI will never be successful in trying to classify LGBTQ+ individuals. Overall, it is difficult to determine the exact solution to the issues raised by ML and AI. While there are countless benefits of these phenomena that we are experiencing in our daily lives, we must be aware of the social issues that come with it, as well as why they are there in the first place From there, we can work towards rectifying these problems and preventing them from happening again in the future.
Sources
Grant, Crystal “Algorithms Are Making Decisions About Health Care, Which May Only Worsen Medical Racism ” American Civil Liberties Union, 24 Feb 2023, www aclu org/news/privacy-technology/algorithms-in-health-care-may-worsen-medicalracism
Keyes, Os The Misgendering Machines: Trans/HCI Implications of Automatic Gender Recognition ironholds org/resources/papers/agr paper pdf
Obermeyer, Ziad, et al “Dissecting Racial Bias in an Algorithm Used to Manage the Health of Populations Science, 25 Oct 2019, www science org/doi/10 1126/science aax2342
Rangnekar, Priti “Decoding the ‘Encoding’ of Ableism in Technology and Artificial Intelligence ” Medium 27 July 2021 medium com/@scienceconnectorg/decoding-theencoding-of-ableism-in-technology-and-artificial-intelligence-a4f33bcccc85
Wareham, Jamie “Why Artificial Intelligence Is Set up to Fail LGBTQ People ” Forbes, 26 Mar 2021, www forbes com/sites/jamiewareham/2021/03/21/why-artificial-intelligencewill-always-fail-lgbtq-people/?sh=3e81a6d2301e
48


This paid internship provides students with tangible experience in technology and feminist leadership while working on the digital scholarship projects of Tulane faculty in the humanities, social sciences, and sciences. Technical areas include: digital media, digital archiving, web design, database development, coding, design thinking, UX/UI, and audio/visual editing.

g
50










AresourceusedtodocumentthelifeofFrancesJoseph-Gaudetan Americanactivist,educator,andsocialworkerwhofocusedoncauses suchasprisonreform.Thegoalofthisprojectistoguideandinspire similarworkinthepresenttimes.

ProjectPartners:NellBoltonandRosanneAdderleyPh.D.
Required:WebsiteandDigitalArchive Software:Omeka

Contributions:
Buildofwebsiteinfrastructure
Websitemaintenance
Digitalarchivingofresources
52
Goals:Awebsite&activesocialmedia
Software:wordpress,LinkedIn,Twitter,Canva

Project:Anonlinecollectionwhosepurposeistomaintainthe legacyofCongoSquare,anareainthesoutherncornerof ArmstrongParkwherebothenslavedandfreepeopleofcolor wouldgatherthroughoutthe19thcentury.

CongoSquareInterview
Views 2monthsago

PROJECT PROMOTION SOCIALMEDIA MAINTENANCE WEBSITE DEVELOPMENT
Join Subscribed
Partner:FreddiEvans





54
GIVE LIGHT
PROJECT PARTNER
 Steph Smith
Steph Smith
OUTCOMES
We spread awareness about the lives and professions of Indigenous Midwives. In addition, we helped inform student groups and feminist organizations about the film.
DEVELOPMENTS
"Give Light: Stories from Indigenous Midwives" is a documentary film highlighting the experiences and perspectives of Indigenous midwives. Throughout the year, we have marketed the film screenings to local and national audiences through the use of social media platforms, Eventbrite, and emails. We also brainstormed educational toolkit examples for viewers and developed an interactive toolkit on SquareSpace.
STORIES FROM INDIGENOUS MIDWIVES

Software:WordPressandArcGIS






Developments:
websiteconstruction databasebuildandmaintenance searchengineoptimization automationresearch

56
This project aims to help organizations and the general public remain updated on upstream developmental that may affect downstream water quality with an informational tracker of water quality for several states within the Mississpi River Basin
Project Partners: Isabel Englehart, Mark Davis, Chris Dalbom

So far this project has tracked data from:
Technology Used:
N U T R I E N T P O L L U T I O N N U T R I E N T P O L L U T I O N C A S E T R A C K E R C A S E T R A C K E R
Iowa Kentucky Louisiana Minnesota
WordPress
Mississippi Missouri Wisconsin
Transformative Preservation
Purpose
This project supports efforts to preserve the legacies of African American educational excellence and community pride through preserving and repurposing mid-century African American school campuses. Additionally, it is hoped that this website will also serve as a conduit for networking among alumni hoping to preserve their alma maters and supporters of this work in the South.

Our Work
SOFTWARE:
This year our team worked on developing and updating the African American School Building Revival website. In this process, we redesigned the homepage, designed a new logo for the site, created mockup timelines to be implemented in the future, and added more schools to the school page.


2022 - 2023
PROJECT OWNER: Laura Blokker & Andrew Liles
-ARCGIS -VISME
-UCRAFT
58
50TH ANNIVERSARY OF 1975
PROJECT OWNER: ALLISON TRUITT PH.D.

PROJECT GOAL:
To gain a better understanding and increase the visibility of the presence and contributions of people with Southeast Asian heritage who resettled in the New Orleans area due to the Vietnam War

WHAT WE HAVE DONE SO FAR:
THE TECHNOLOGY: Set up the Scalar website Integrated Knight Lab timeline into the Scalar website
Scalar Knight Lab

MELLONGRADUATE COMMUNITYPROGRAM
PROJECTOWNERS:TULANEMELLONGRADUATE COMMUNITY-ENGAGEDSCHOLARSHIP(CES)PROGRAM


ProjectGoals:Thedigitalexhibitionallowsforauniquelookinto12 studentcommunity-engagedscholarshipprojects
Divi!
TechnologyUsed:WordPress,WordPressplug-ins(i.eWPtouch MobilePlugin,WPGoMaps,DiviBuilder,PDFEmbedder)
Developments:websitedesign,websitemanagement,digital archivecreationwithpdfsandvideos,createdtutorialsforfuture websitedevelopment
60
Ryan Hugo & Lucas Diaz
Maternal and Child Health Coalition
Project Owner: Dr. Clare Daniel
Project Mission
To improve outcomes, experiences, and access to quality, respectful care during pregnancy, birth, and the postpartum period by centering the experiences of Black birthing people and their infants in New Orleans




Our Project Goal
To create an abortion access map that compares state abortion access to maternal mortality rates.
What We Achieved
Created the abortion access map that will be integrated into the site

Performed general website clean up and updating


Software Used WordPress Tableau SCAN TO VISIT
FEMINISM, SCIENCE, AND TECHNOLOGY STUDIES

PROJECT EXPLORES THE INTERSECTIONS OF GENDER EQUITY AND SOCIAL JUSTICE WITH SCIENCE AND TECHNOLOGY STUDIES USING HISTORICAL PERSPECTIVES. IT INTENTIONALLY USES INTERDISCIPLINARY APPROACHES OF SCIENCE AND TECHNOLOGY STUDIES, INCLUDING HISTORY, POLITICS, ARTS, CULTURE, PUBLIC HEALTH, SOCIAL SCIENCES, WRITING AND RESEARCH TO MAKE EXPLORING STEM (SCIENCE, TECHNOLOGY, ENGINEERING, MATH) TOPICS MORE ACCESSIBLE. THE SITE’S TITLE, “STEMINISMS” REFERS TO DIFFERENT VARIETIES OF FEMINIST THINKING BUT THE SITE FOCUSES ON INTERSECTIONAL PRACTICES. WE HAVE DESIGNED THIS SITE USING FEMINIST TENETS TO SERVE BOTH ACADEMIC AUDIENCES AND ENTHUSIASTS. WE USE A PEER-REVIEWED CROWDSOURCE PROCESS TO GATHER SOURCES THAT ALLOWS ANYONE THE OPPORTUNITY TO CONTRIBUTE AS A RESEARCHER.

62



64
THE TECHNOLOGYTRAFFICKING NEXUS
EMERGING TECHNOLOGIES AND THEIR RELATIONSHIP TO HUMAN TRAFFICKING
 By Olivia Riess
By Olivia Riess
CONTEXTUALIZINGHUMANTRAFFICKING

Human trafficking is one of the most prominent humanitarian crises that exist today. It is an intersectional issue that is defined in two instances: sex trafficking and forced labor. In addition to race, gender, disability, age, and class, other factors, such as migration status and economic instability, can increase vulnerability to human trafficking Therefore, ending human trafficking requires addressing the root causes, such as poverty, discrimination, and lack of access to education and opportunities. It also requires a comprehensive approach that involves law enforcement, civil society, governments, and the private sector to prevent trafficking, protect victims, and prosecute perpetrators.
Sex trafficking victims are disproportionately women of color, many under the age of 18. In Louisiana alone, we can see this as an intersectional issue as “black girls represent 49% of child sex trafficking victims, even though they comprise only 19% of Louisiana’s population of youth.” [1] There is a range of misconceptions surrounding human trafficking that can hinder efforts to address this issue Common misconceptions may include the notion that human trafficking only happens in developing countries or in certain industries, such as the sex industry, however, human trafficking is a global issue that can occur in any industry, including agriculture, domestic work, and manufacturing and can happen in any country, including developed countries.
COMBATTINGHUMANTRAFFICKINGWITHTECHNOLOGY
Unfortunately, many advancements in technology have been exploited to aid perpetrators of human trafficking. New tech such as instant and secure communication, remote control of victims using GPS location apps, and the use of cryptocurrency or receiving and moving illegitimate profits through cryptocurrency have all been employed as a tactic to maintain HT operations. However, new technologies also have the potential to play a critical role in the fight against human trafficking by helping to identify and prevent trafficking activity, and by providing support and resources to victims. [2]
REFRAMINGTHECONVERSATION
While there is much to celebrate regarding these advancements that have allowed for new methods in combat human trafficking, it is important to address the root causes of the issue. The way that the traffickingtechnology connection is often portrayed simplifies the issue into a good vs. evil framework This narrative focuses on punishing the perpetrators and rescuing the victims, while absolving nation-states and businesses from responsibility for creating the conditions that enable exploitation, and relying solely on technology to address human trafficking risks distracts from the standard operating practices of businesses that may contribute to exploitation. [3] In order to effectively address human trafficking, we must actively and intentionally work to address the underlying problems and hold all stakeholders accountable.
References:
TECH USE & EXAMPLES
1 Social Media can be used to raise awareness about human trafficking and connect victims with resources
ex Polaris and the National Human Trafficking Hotline
2. Data Analysis can be used to identify patterns and trends in human trafficking, helping to better understand and respond ex. Human Trafficking Hotline
3. Mobile apps have been developed to help people identify and report suspected instances of human trafficking ex STOP-IT app
4 Blockchain technology can be used to create secure and transparent systems for tracking supply chains and financial transactions, which can help to prevent human trafficking

ex World Food Programme has used blockchain technology to track the distribution of aid in refugee camps, help to prevent aid from being diverted to traffickers
5. Artificial Intelligence (AI) has been used to identify potential trafficking activity and assist law enforcement in investigations.
ex Thorn's AI tool 'Safer'
[1]LouisianaDepartmentofChildrenandFamilyServices,HumanTrafficking,TraffickingofChildrenforSexualPurposesandCommercialSexualExploitation:AnnualReport6(2018);C Puzzanchera,A SladkyandW Kang, EasyAccesstoJuvenilePopulations:1990-2017(2018), https://wwwojjdpgov/ojstatbb/ezapop/asp/profile displayasp
[2]Montasari,R,Jahankhani,H (2021) TheApplicationofTechnologyinCombatingHumanTrafficking In:Jahankhani,H,Jamal,A,Lawson,S (eds)Cybersecurity,PrivacyandFreedomProtectionintheConnectedWorld AdvancedSciencesandTechnologiesforSecurityApplications Springer,Cham https://doiorg/101007/978-3-030-68534-8 10
[3] Milivojevic, S, Moore, H, & Segrave, M (2020) Freeing the modern slaves, one click at a time: Theorising human trafficking, modern slavery, and technology Anti-Trafficking Review, 14, 16-32 https://doiorg/1014197/atr201220142
66
GENDER EQUITY IN THE HOME: PROOF WE’VE DONE LITTLE IN CLOSING THE GENDER GAP

KAILEN MITCHELL
Genderdisparitiesexistallaroundus,andifyouhaven’tbeenlivingunderarock,you mightrecognizegenderequalityeffortsassolvingthewagegaporencouragingmore womentoworkinSTEMfields.InthisarticleI’mgoingtolookpasttheseissuesand insteadmorecloselyatanothertypeofgenderdisparity:theonewithinthehome.I’m goingtoexaminethegenderingofhouseholdlaborandwhythelittleprogresswe’ve madeinsidethehomeisproofofamuchlargerissue:ourselectiveandmasculineorientedgenderequitystrategies.Additionally,I'llcoverhowthislackofprogressis affectingwomen’slivesnegatively,andthereforeourworldasawhole.
Despitealleffortsforgenderequalityinthemodernage,womencontinuetocarrythe burdenofdomesticlaborandchildcareatdisproportionateratescomparedtotheir malepartners.Infact,womendomorethan75%oftheunpaidcareworkintheworld. Researchalsofindsthatdespitethefactthatwomennowoutnumbermeninthepaid workforce,theycontinuetodo60%morehouseholdlaborastheirpartners.Whilethe genderpaygapissteadilynarrowing,thehouseworkgapstoppednarrowinginthe 1980s.Intermsofmendoingtheirfairshareofunpaidlabor,we’restillstuckinthe80s. Onereasonwomenmaybetakingonthisworkisduetoafeartheirpartnerswillnot performtheworktoasufficientstandard,aGuardianarticlesuggests.Thearticlestates thismeansthisissueisn’tsimplesexismoflazymen,butratheramuchmorecomplex issuewhereinternalizedsexismreiteratestowomenthatthestateofherhomeisasign ofherworth.Womenaretoldtheirentirelivesthattheirvaluerestsontheirabilitytobe a“goodwoman,”meaningsheperformsallherwifelyandmotherlyduties.Aclean,tidy houseisasignof“succeeding”asawoman,andthereforeinternalizedsexismforces womentohavehighstandards.It’sclearwe’veprogressedlittleintermsofclosingthe gendergapwithinthehome,andwhenweexaminewhythisistrue,itrevealsanintegral issuewithourapproachtosolvinggenderinequalities.
Themainreasonwe’resofocusedonissueslikewomenenteringmaledominated workplacesandthepaygapisbecausethesearemasculine-centricissues.Insteadof focusingonvaluingwomen’sworkorevengettingmentocontributetowomen’swork, weasasocietyareobsessedwithgettingwomentobemorelikemen,andthinkthat oncewomenhavebecomelikemenourworldwillhaveachievedgenderequality.
Butthisisfarfromthetruth.Thestrategiesandareaswehavepouredeffortsintoare inherentlypartoftheproblem:wecontinuetobeasocietythatvaluesthemasculine. Theveryfactthatwearenotfocusedonsolvingthisissueproveshowlittlewevaluethis unpaidworkwomendobehindthescenes.Thisundervaluingisextremelyharmfulto women ’slives.
Notonlyarewomen53%morestressedthanmen,butalsowomenconsistentlyexceed therecommendednumberofhoursoneshouldworkperweekbeforeit’sdetrimentalto yourhealth.Researchshowsyoushouldn’tbeworkingmorethan40hoursaweek,but womendoworkoverthisamountduetotheirlaborinandoutsideofthehome.This imbalanceoflaborinsidethehomeisliterallykillingwomen.Additionally,meninthe UnitedStatesreporthaving,onaverage,anextrahourperdayofpersonalleisuretime. That’sanhourwomenlosetotheirhouseholdburdensthattheycouldbespendingon personalactivitiestoimprovetheirmentalhealth.It’snowonderwomenaresomuch morestressedthanmen,andaretwiceaslikelytobediagnosedwithdepression.
ExtremelypoormaternitylawsintheUnitedStatesalsomeanthatwomenareforced intoquittingtheirjobsormovingintoparttimework,whereasmendonotfacethesame issue.Whenweholdwomenback,weholdback50%ofthelaborforceandreducethe poolofqualified,intelligentworkers.Ontopofthis,theworkplaceitselfisbuilttonot accommodatesomeonewhohaschildcareresponsibilities.Womenfaceavarietyof issuesthatmenjustdon’thavetothinkabout,forexample,lastminuteshiftschedules beingstandard,pregnantwomennothavingproperworkplaceaccommodations,and babysittersnotbeingconsideredabusinessexpenseforwomenparticipatinginwork trips.Theseexamplesarejustthesurfaceofwhatwomenfaceday-to-dayand throughouttheircareers.Thedisadvantagesthatstartinthehomeleavewomen impairedcomparedtotheirmalecounterparts.Ifwewantwomentohaveequal opportunitieswithintheworkplaceandinlife,wemuststartbyreducingtheirhomely burdens.
Thelittleprogresswe’vemadeinsidethehomeandourfocusontheissuesoutsideofit showsthatourapproachtosolvinggenderinequalitiesisamalecentricone.Weare failingwomenwithgenderequityinthehome,andit’sadireissue.Wemustdismantle thevaluesweholdsurroundingworkinsideandoutsideofthehometoeitheraccountfor women ’sburdenorcarework,orwemustcreateanenvironmentwherebothmenand womencontributeequallytohouseholdtasks.Findingasolutiontothisproblemnotonly benefitswomen,buteveryoneaswomen'sinvisibleworkisthebackboneofourworld.
Sources:
- https://sociologyiresearchnetcom/sociology-of-family/division-of-household-labor/
- https://wwwtheguardiancom/inequality/2018/feb/17/dirty-secret-why-housework-gender-gap
- https://wwwpewresearchorg/fact-tank/2021/01/25/for-american-couples-gender-gapsin-sharing-household-responsibilities-persist-amid-pandemic/
- https://hbrorg/2020/05/gender-equity-starts-in-the-home
- https://wwwmayoclinicorg/diseases-conditions/depression/in-depth/depression/art20047725#: :text=Women%20are%20nearly%20twice%20as,occur%20with%20normal%20hormonal%20changes

68
- Invisible Women by Caroline Criado Perez
ComputerScienceas"Women'sWork"
Themodernconsensusona“computerscientist”iswellknown—one imaginesascruffywhitemanwhospendstoomuchtimeonhis computerandnotenoughbeingoutsideorsociallyactive This sentiment,however,ofwhatacomputerscientistlookslikehaschanged alotsincethebirthoftheprofessionofcomputerscience Infact, computersciencewasconsidered“women’swork”beforeanythingelse, especiallysointhemid-twentiethcentury Thebeginningsofcomputer scienceasa“pinkcollar”jobcanbeattributedtomanyreasons,butthe mainonewasthatcomputerengineeringandhardwarewasconsidered muchmoreimportantanddifficultthananyworkrelatedtosoftwareor mathematicalcalculations.Despitethesesomewhatcondescending categorizationsofcomputerscience,thefieldopenedmanydoorsfor womeninscience,astherewere“sofewotheropportunitiesforwomen, otherthanteaching”(1)
ByIzzy Blair
Themostinterestingthingaboutthewaysinwhichwomen incomputersciencewereperceivedandjudgedisseenin howthesesameperceptionsweremirroredbythe perceptionsofcomputersingeneral.Littlewasknownabout thetrajectoryofcomputersoftwareandallthevaryingways inwhichitcouldbeusedtosolveproblems.Furthermore, therewasageneralsensethat“thecomputeritselfwas doingthework,andbuildingthecomputerwasthereally importantthing”(2).Becauseofthisperception,themath andcalculationsthatservedastheinputintotheseearly computerswereseenastrivial,easy,andmuchless importantwork
Thisworkwasfarfromeasy,however:pagesandpagesof calculationsthathadtobeflawlesswentintoeachproblem,and manymorehoursofworkputintothesepages However,afterthe PearlHarborattacks,calculationsforflightsandotherwarfare tacticsbecamemorepertinent.Malescientiststhrewtheworkof calculatingontowomenevenmoreheavilyduringthistime.Thisis whyearlyfemalecomputerscientistswerecalled“humancomputers” --theycomputedmathematicalproblemsallday,fillingupnotebook afternotebookwiththeirwork.Humancomputersbecameso importantthattherewereentiredepartmentsdevotedtothem, headedandrunbywomencomputerscientists.Somewomenwould evenbehiredstraightoutofcollegeastheimportanceofhiring young,brightmindsbecameapriority(3).
Notonlydidtheemersionofcomputerscienceasa“pinkcollar”field allowwomenpositionsinscience-relatedjobs,butitalsokickstartedawaveofwomen’sworkerrightsbeingrecognizedand implemented.Forexample,whenNASAbeganhiringwomenstraight outofcollege,theyallowedthemtohavematernityleavewitha guaranteedreturntotheirjobiftheyprovedvaluabletotheteam. dedanewsortofjobsecuritythatwomeninscience eriencedbefore.Anotherbenefitthatarosefromthis kcollar”workerswastheincreaseinhiringwomenof mancomputers.Asmoreandmorehumancomputers NASAandothercomputer-techcompaniesbeganto basedontheircomputationalskillsandnottheirskin So,thesamesystemthatwassupposedtosuppress omputersciencewasthesameonethatallowedmore mdiversebackgroundstothriveandgrowthefield.
putersciencebeganasa“pinkcollar”field,howdidit male-dominated?Theanswerissimple:ascomputers memorecomplex,theworkofmaintainingthemcame redmorecomplexandimportant,andtherefore“unfit” n.Thefieldofcomputersciencebegantobepaidand edmoreasitbecamemoremale-dominated Software ng,likecomputerengineering,formedamorerevered reputationandthereforepositionswerefilledwithmenwherebefore theywerefilledbywomen.Thisisn’ttosaythatthereweren’t womenstillinthesepositions—forexample,SueFinley,now80 yearsold,isNASA’slongest-servingemployeeandstartedworking asahumancomputerin1958(3) However,itisclearthatgender diversityhasbecomeanissueinthefieldofcomputerscience. Lookingbackatthebeginningsofthefieldshowsnotonlythe importantrolewomenhaveplayedinfurtheringtechnologyscience, butalsothetrivialityofimposedgenderrolesontechnological careers
Sources:
https://www.smithsonianmag.com/smart-news/computerprogramming-used-to-be-womens-work-718061/ http://www.history.com/news/coding-used-to-be-a-womansjob-so-it-was-paid-less-and-undervalued https://www.history.com/news/human-computers-women-atnasa

70
a. b. c.
Digital Privacy Post-Roe: A How-To Guide By Madeline Nellis
In the wake of Roe vs. Wade being overturned, we must make sure our bodily autonomy is protected as much as possible. Digital surveillance, and understanding what is being tracked, is increasingly important as states have banned abortions and pregnant people turn to out-of-state options. The following is a guide to digital privacy post-Roe. Know your tools, and obstacles, and how they work.
Step 1: DON’T use period tracking apps. DO use a calendar to track menstruation.
Menstruation apps store data that a user inputs in order to predict when the user will get their period as well as ovulation dates and to show the user where they are in their cycle. Records of having a period, missing a period, sexual activity, and other things such as mood swings and menstruation symptoms can be tracked within the apps. This can be evidence that can make or break a criminal case.
Data that is streamed through third-party systems can be subjected to warrants if a user is being accused of illegally terminating a pregnancy. The apps themselves can be subjected to data demands if their information is not legally protected. Post Roe is a world with a new legal environment. Data gathered by apps such as smoking and alcohol intake could also find its way into the courtroom depending on how criminality is defined for healthcare providers and patients (Planned Parenthood Federation of America Inc.) We must proceed with the utmost precaution.
Calendar tracking can be a useful tool to predict menstruation, when one is fertile, and when it is safe to have sex. When starting to calendar track you should follow your cycle for at least six cycles by marking the first day of each period on the calendar. The total number of days between marks, from the first day of one period to the first day of the next, is the length of your cycle.
To keep track of your fertile days you first need to detect the shortest cycle you have in your record. Then you subtract 18 from the total number of days in the cycle, count that number from day 1 of your current cycle, and that day is your first fertile day. In order to find your last fertile day, find the longest cycle in your records. Then you subtract 11 from the total number of days in the longest cycle, and count that number from day 1 of your current cycle, marking that as your last fertile day (What’s the calendar method of FAMs?). (What’sthecalendarmethodofFAMs?)

Of course, calendar tracking is not 100% accurate and you should always use other preventative measures if you are not trying to become pregnant, but it provides the same information an app would supply.
Step 2: Know the weaknesses in your defenses: VPN, encryption, private browser
There are a few different measures you can take to browse the web in a saferless trackable way. You must know how to use them and their weaknesses- what is protected and what is not.
VPN stands for virtual private network. They protect browsing information from internet service providers. When using VPNs, your device connects to the VPN servers and internet connection. While they limit service providers from tracking and recording your data, they do not disguise device location from cellular networks.
Encryption scrambles messages when sent so that they are indecipherable when passing through application servers. Messaging apps like apple message and whatsapp use encryption. Although these messages are difficult for law enforcement to decode, they can gain access with a court order through the application.
Private Browsers search the internet in private mode- stopping devices from making records of web searches/visits. Private Browsers do not hide browsing data from internet providers (NYT.) Overall, when searching the internet, a VPN is your best option, as long as you are in a location that does not need to be concealed (Singer).
Step 3: Leave your phone at home.
You cannot escape digital surveillance. Every piece of technology can be a way for law enforcement to gain data. In the event that you need an abortion, and are able to get to a clinic that can perform one, you should leave your phone at home. Keep it turned on so that local cell towers track its location and there is no trace of you leaving your residence.
References
Osborne, C (n d ) Period tracking apps are no longer safe delete them ZDNET Retrieved February 23, 2023, from https://www zdnet com/article/period-tracking-apps-are-no-longer-safe-delete-them/
Planned Parenthood Federation of America Inc. (n.d.). What is the calendar method?: Fertility Calendar Info. Planned Parenthood. Retrieved February 23, 2023, from https://www plannedparenthood org/learn/birth-control/fertility-awareness/whats-calendar-methodfams#: :text=You%20can%20do%20this%20with,first%20days%20of%20each%20period
Singer, N., & Chen, B. X. (2022, July 13). In a post-roe world, the future of Digital Privacy Looks Even Grimmer. The New York Times. Retrieved February 23, 2023, from https://www nytimes com/2022/07/13/technology/personaltech/abortion-privacy-roe-surveillance html
72
IntrusionDetectionOverview
By Jingzhi Yang
IDS is a type of detection system that plays a key role in protecting cyber security by monitoring the states of software and hardware running in a network. The first intrusion detection system was proposed in 1980. Generally speaking, there are two types of IDS classification methods: the detection-based method and the data source-based method Detection-based methods are also sub-classified into misuse-based and anomaly-based detection
Misuse-basedDetection
The idea behind misuse-based detection method is keeping the known or seen attack behaviors as signatures in a database. These specification-based techniques have been shown to produce a low rate of false alarms but are not as effective as anomaly detection in detecting novel attacks. Researchers realized hackers can easily find their ways to bypass the obstacles. For example, a system might have handcrafted rules such as if login time is in the non-business hours and there are 5 continuous failed attempts then suspend the account for 24 hours. After some experiments, hackers will get to know this rule and try to log in at a different time or implement a ‘cooling’ time before his next try to bypass the rule. Rule-based systems can be effective, but they require constant manual updates, and they can be easily defeated by a knowledgeable adversary It is very time consuming and inaccurate
Anomaly-baseddetection
Anomaly detection can be defined as a key element of intrusion detection and other detection systems in which perturbations of normal behavior suggest the presence of intentionally or unintentionally induced attacks, faults, defects, etc. The keyword in this definition is ‘normal behavior’ or as somebody prefers ‘baseline’. The baseline represents how the system normally behaves, and then all network activity is compared to that baseline.
The baseline represents how the system normally behaves, and then all network activity is compared to that baseline Rather than searching for known IOC (indicator of compromise), anomaly-based IDS simply identifies any out-of-theordinary behavior to trigger alerts. For example, if a user usually uses MacOS and logs in from New Orleans but all of a sudden he is using a Windows machine to log in from Russia, it is very unlikely that this log in attempt is coming from the user. Because anomaly-based systems can detect misuse based on network and system behavior, the type of misuse does not need to be previously known.
Machine Learning is an intuitive way to implement anomaly-based detection. The most common supervised algorithms are, Supervised Neural Networks, Support Vector Machines (SVM), k-Nearest Neighbors, Bayesian Networks and Decision Tree. The most common unsupervised algorithms are, K-Means, Self-organizing maps (SOM), C-means, ExpectationMaximization Meta algorithm (EM), Adaptive resonance theory (ART), Unsupervised Niche Clustering (UNC) and One-Class Support Vector Machine.
Anomaly detection and misused based methods have their advantages and disadvantages Is it possible to devise a system that utilizes both methods to achieve better performance? The answer is yes Depren proposed a novel Intrusion Detection System (IDS) architecture utilizing both anomaly and misuse detection approaches to find anomaly connections in network traffic (Depren et al., 2005). In his implementation, anomaly and misuse detection are two separate modules that make independent predictions, and then a rule-based decision support system (DSS) will make a final decision. In his implementation decision-making is a straightforward process. The logic of decision-making can be divided into three parts: 1. if the misused approach predicts it is an attack, then the final decision will be an attack regardless of anomaly approach prediction. 2. If the misused approach predicts it is benign, but the anomaly approach predicts it is an attack then the final decision is unclassified. 3. If both the misused and anomaly approach predicts it is benign then the final decision is benign Using the KDD Cup 99 Data Set which is raw packet network traffic data (e g 0, TCP, HTTP, SF, 181, 5450, 0, 0, 0, 0, 0, 1, normal), Depren achieved a detection rate of 99 90%, a classification rate of 99 84%, and a false positive rate of 1.25%, which overall outperformed both anomaly-based and misused-based detection methods where for anomaly detection, the detection rate is 98.96% and the false positive rate is 1.01%, and for misuse detection, the classification rate is 99.61% and false positive is 0.2% (Depren et al., 2005).
Although there is much literature using raw packet network traffic as a dataset to develop their IDS like Depren’s work, there are very few using user sign-in logs as the dataset. This is because the user sign-in log is sensitive data that is normally only available to each organization’s IT department. However, user authentication is a serious issue right now in the cybersecurity field. Many organizations rely on Microsoft Azure Active Directory to authenticate users to allow them to use resources within the organization such as email services Unfortunately, Microsoft Azure Active Directory authentication is not as effective as expected What makes it worse is that since the implementation is a black-box, there is no way for users to improve the detection. Hopefully in the future there is an open-sourced solution that can address the issue.

74
TheCyberGenderGap
Naomi Stoner
Today,womenrepresentabout50%oftheworld’sworkforce,butonlyabout11%of thecybersecurityworkforce(Maryville 2022) Thereasonsforthisdisparityare multifaceted Forexample,thenarrowsocietalperceptionofwhat“hackers”are maycontributetothelackofwomenrepresentedincyber Themostcommon imagepopularizedbyHollywoodandmediagenerallyisthatofawhiteyoung manwearingahoodiesittingbehindadeskcrampedwithnumerousoversized monitors Thiscommonarchetypemayleadtoanassumptionthatcybersecurityis agenderedjob orsomethingthatonlymendo Theseassumptionscanleadto hiringbiasthatcompelscompaniestohiremenoverwomen(Townsend,2022)
Furthermore,womenmaybediscouragedfromapplyingtojobadswithgender biasedlanguage,andmanyjobadsforcybersecuritypositionslackgenderneutral language(Kshetri,2021)
Thelackofgenderdiversityoncybersecurity teamspresentsseveralissues First,diverseteams precipitatemorecomprehensivesecurity For example,womengenerallyplacemoreemphasison internaltrainingasameanstoensuresecurity, whereasmentendtofavortechnicalcontrols (Kshetri,2021) Neitherusertrainingnortechnical controlsaresufficienttosecureanorganization; theymustbeusedinconcertwithoneanother Therefore teamswithmembersthatemphasize bothfacetsofsecuritywillofferbettersecurity solutions meaninggender-diverseteamswilloffer morecomprehensivesecurityoverall Morebroadly researchhasshownthatgenderdiverse cybersecurityteamsincreaseteamperformanceby 12%andcompanyretentionby20%(Barekas,2021)
Whatcanbedone?
Therearemanyavenuesthatcanbetakentoimprovethe representationofwomenincybersecurity Usinggender neutrallanguageinjobadvertisementsisonewayto increasetheamountofwomenapplyingtocybersecurity jobs Specificinitiativesdesignedtopromotecybersecurity interestinschool-agedgirlscanalsohelpdecreasethe gendergap,especiallysincemostwomenhaveruledout cybersecurityasapossiblecareerbyage15 Severalof theseinitiativesalreadyexistandservetopromotethe inclusionofwomeninthecyberworkforce Forexample PaloAltoNetworkshaspartneredwiththeGirlScoutsof Americatodevelopcybersecuritytrainingcurricula and WomeninCybersecurityofSpainhasbegunoffering early-careermentoringprogramstowomenincyber (Kshetri,2021)
Overall,increasingthegender diversityinthefieldof cybersecuritywillleadtoboth improvedsecurityoutcomes as wellasincreasedcompany performanceandretention Itis thereforeimportanttosupport initiativespromotingtheinclusion ofwomenincyber
References:
https://online.maryville.edu/blog/women-in-cyber-security-closing-the-gender-gap/ https://www.cyber-insights.org/gender-gap-in-cybersecurity-is-a-concern/ https://www.uscybersecurity.net/gender-gap-cybersecurity/ https://nordvpn.com/blog/gender-gap-in-cybersecurity/
76


This paid internship employs undergraduates to support technical operations within a nonprofit research and education center using feminist technology customer support ethos. Technical areas include: asset management, IT help desk, web maintenance, project management, classroom/AV support, and instructional technology training.

g
78
NewcombInstitutethroughtrainingstaff,respondingtohelp tickets,andservicinganysystems.Internsalsoupkeeptechnology withinthelabandperformwebsitemaintenance.
TechFixes UserError 34.2% System 272% Hardware 254% Software 132% 926 taskscompleted 326 shiftchecklists 64 softwareupdates Information Technology internship OurProject 2022-2023 overview Quickstats
checkoutthe differenttechfixes wedid!
Many of the issues we encounter can be categorized as hardware (laptops, microphones, projector), software (glitches, updates), user error, or system (network, conntection). We completed 114techfixes this year!
InformationTechnologyInternsprovidetechnicalsupportto
Ourwork
Checkoutthebreakdownof someofthetaskswe've completedthisyear: TheITteamhashelpedmaintain 8differentwebsitesincluding: CongoSquareConnection,Nutrient Pollution,FeministPedagogyfor TeachingOnline,&more!
Wedon'tjustlearnandapplyITpractices-wealsoteachthem!TheITI teamisresponsiblefordesigningtheinstructioncardsonpodiumswith easilyunderstoodoperatingandtroubleshootingprocedures,creating techhelpflyersforthestaff,anddevelopingworkshopsforundergraduate students.WehavealsotakenonaprojectasDigitalTAwherewehelpa graduateclassturntheirresearchintoonlineexhibitsaswellasteachthem aboutthedigitalhumanities!
Helptickets
Emailusat
ncitech@wave.tulane.edufor techwalk-throughsbeforeyour bigpresentation,troubleshooting advice,andanyotherquestions regardingtechnologyat NewcombInstititue!
LabMaintenanceTechAdmin ClassroomSupportWebsiteMaintenanceTeachingSupport 400 300 200 100 0
# o f t a s k s
80
Whenindoubt... comefindanIT interninablue nametag!
Lunch&Learn
MicrosoftOfficeTrainings

ProjectPartner:Dr.AidenSmith
TopicsCovered
Excel
Transposing data, filters, short cuts, formulas, tables
Word
Researcher mode, outlines, Microsoft editor
Powerpoint
Editing images, speaker coach, saving time
Outlook
Gendered communication, calendar automatic replies, signature For all: ADA accessibility and best feminist practices
HowWeDidIt
Graduate Assistant and Interns led and developed four in-person trainings

Students experienced class led tutorials as well as selfguided tutorials to solidify topics
Take home worksheets provided for ll i f d
OurPurpose
Help students use these tech tools
Help students incorporate the of use ADA accessibility and feminist practices to uphold community values
leadingthefirstLunch&Learn
RachelTabor,GraduateAssistant,
NEWCOMBMAGAZINE

WEBSITE
Awebsitetohouseinformation abouttheNewcombInstitute's Magazine,aswellasitstemporary andpermanentcontributors.
Whatwedid:Implementedblog feature,updatedarchivesofpast issues,addeddonationfeature,and implementedvariousnewdesign developments.
ProjectPartners:
BeckyGibson
LaurenGaines
REALLYGREATSITECOM
82




TheTechnologyand DigitalHumanitiesLab atNewcombInstitute
FEMINISTPEDAGOGYFOR TEACHINGONLINE
ProjectPartners
ClareDanielandJacquelyneThoniHoward
Background
Adigitalguidethatprovidesresourcesfor integratingfeministpedagogyandtechnology intoonline,hybrid,andtraditional undergraduatecourses.Thisguideisdesigned tosupportinterdisciplinarytopicsandfields.It focusesonactivelearningpracticesinthesocial sciences,theliberalarts,andthehumanities.

ProjectDevelopment
Thiswebsitewasbuiltonthesoftware WordPress.Weupkeepthewebsiteanddothe overallwebmaintenance.Wealsocontributed tothisprojectbydoingtheliteraturereview, postingupdatesaboutthesiteonSocial Media,troubleshootingHTMLissues,and editinginterviewvideos.
84


Grace Hopper Celebration is a conference for technologists who care about equity. Named after computer scientist Grace Hopper, this conference brings together students, companies, educators, and professionals.
g
The Gender and Technology grant program offers undergraduates the opportunity to conduct research on topics relating to gender and technology. Students will receive a grant to produce a digital research project that will be published digitally. Students may receive sponsorship to apply to the national HASTAC Scholar program. Ainsely Anderson was accepted as a HASTAC Scholar in 2022.
g

86
GraceHopper Celebration
GraceHopper(GHC)isacareerfairandconferencetobringwomenand non-binarytechnologiststogether.It'stheworld'slargestgatheringfor womenincomputing!Fromcareerboothstoinsiprationalspeakersto collaborativeworkshops,GHChassomethingforeveryone.


THISYEAR'SATTENDEES
AnanyaAnand(she/her)
AlyssaBockman(she/her)
EvanHendrickson(he/him)
TessKleanthous(she/her)
LayaKumar(she/her)
MarisaLong(she/her)
KailenMitchell(she/her)
MadelineNellis(she/her)
NaomiStoner(she/her)
OliviaRiess(she/her)
WendyYang(she/her)
Thisyear,NewcombInstitutesent11atendeestoGHC! Overthecourseoftheevent...
18
joboffersreceived
Interviewswerecompleted 9 15 11 11 11
differentcompaniesinterviewedourstudents
studentshadameaningfulencounterwithatleast onecompany
attendeesfeltadequatelypreparedbyNewcomb attendeesfeltGHCenhancedtheirprofessionalskills
AttendeesinterviewedwithcompanieslikeUnitedAirlines,Chevron,American Express,MorganStanley,NorthropGrumman,WellsFargo,Genentech,and more!
GraceHopper Celebration

TESTIMONIALS
Reflectonwhatwasthemostmeaningfulexperienceyougotfrom GraceHopper.
"GraceHopperCelebrationwasaninspiringadventureforme,asIwassurroundedby peoplededicatedtoinnovationandinclusioninthetechnologyindustryIwasableto connectwithotherundergraduatewomenfromotheruniversitiesandbondoverourshared experiencesbeingawomanintech.Welaughedandwelearnedfromoneanother,and formedacommunitywherepeoplefeltheard"-Olivia
"OneofthemeaningfulmomentsofGHCtomewasfeelingthesupport ofmyfellowlabmembersoutsideoftheconferencehoursIremember thenightandmorningbeforethreeofushadinterviews,wespenttime togethersharingexperiencesandliftingeachotherup.Ithoughtthat thesemomentsweregreatrepresentationsofhowourlabandGHC buildscommunitythatextendsbeyondjustcreatingefficient coworkers.NotonlydidGHCserveasaprofessionaldevelopment experience,butitdoubleasateambuildingtrip."-Marisa
"ThemostmeaningfulexperiencetomeduringGHC2022 wasbeingabletospeaktowomeninSoftwareEngineering rolesatcompanieslikeGoogleandAdobe.Bothofthe SeniorSoftwareEngineersthatIspoketowereableto,not onlytellmehowtheygotintotheirfield,buttheywereable todosobyrelatingtheirstoriestomeandwhereIamatin myprofessionaljourney.Ifoundthatthisreallyinspiredme andhelpedsteermeintherightdirectionformy educationalandprofessionalfuture"-Tess

"OneofthemostmeaningfultakeawaysIgotfromattending GHCwasthatimpostersyndrometrulyaffectseveryoneAtalk thatIattendeddiscussedovercomingimpostersyndrome,and plentyofthepeopleintheroomwereestablishedintheir careerIwentintothisconferencefeelingprettyunconfident aboutmyoddsofgettingjoboffersthatweekTalkingto recruitersandobservingtheirreactionsgavemealotmore confidencegoingforwardthatevenifIfeeloutofplace,I deservetobeintheroomasmuchasanybody."-Marisa

88
The Lab’s HASTAC Scholar: Ainsley Anderson!
Ainsley Anderson is a sophomore at Tulane University, pursuing a double major in economics and environmental studies. As a member of the Newcomb Scholars feminist research cohort, she is passionate about exploring ways to incorporate feminist perspectives into her work. She is fascinated by the connections between economics, the environment, and social justice, and hopes to use her education to make a positive impact in these areas. When not studying or conducting research, you can find her roaming New Orleans or listening to some live music.
Her dome project is being funded by the HASTAC grant! Read more about the fellowship program here:
https://hastac.hcommons.org/about/hastac-scholars/


90


Society of Women Engineers is an organization that inspires students to achieve their full potential as engineers. Tulane's chapter focuses on supporting, encouraging, and providing women engineers, and members of the STEM community, with the means to succeed throughout their college career and beyond. The SWE chapter provides outreach opportunities within the greater New Orleans community. The executive board has bi-weekly meetings where they discuss, plan, and coordinate future general body meetings, study help, professional development, and more.
Equity in Technology acts as a dynamic resource for the campus by providing space for feminist-minded technologists of all majors and interests to connect with an interdisciplinary community of like-minded peers. Students are welcome from all majors and those with all levels of technology abilities. Within this group, students are encouraged to explore social and cultural issues involving technology and interdisciplinary applications of technology innovation through curriculum and service.

92 g
g
SOCIETY OF WOMEN ENGINEERS
who we are: by women. for women.
The Society of Women Engineers is a international organization founded on principles of advancing and empowering women in engineering and other STEM fields.

Tulane's collegiate SWE section is a community of undergraduate students united in supporting women in engineering and other STEM disciplines on campus and beyond.

13% ofengineersinthe workforcearewomen
>32% ofwomenleaveSTEM programsincollege
10% lesspayearnedby femaleengineers thanmale
45.5% of engineering degrees at Tulane are awarded to women







professional development community participate in outreach at Tulane and throughout New Orleans outreach build a community among undergraduate women in engineering programs provide professional development opportunities through SWE's national conference and workshops what we do: @tulaneswe facebook.com/tulaneswe/ @tulaneswe 94
TULANE EQUITY IN TECHNOLOGY (Formerly Women in tech)
EQUITYINTEC
OURCEFORTHE
CAMPUSBYPROVIDINGSPACEFORFEMINIST-MINDED TECHNOLOGISTSOFALLMAJORSANDINTERESTSTOCONNECT WITHANINTERDISCIPLINARYCOMMUNITYOFLIKE-MINDED PEERS


STUDENTSAREENCOURAGEDTOEXPLORESOCIALANDCULTURAL ISSUESINVOLVINGTECHNOLOGYANDINTERDISCIPLINARY APPLICATIONSOFTECHNOLOGYINNOVATIONTHROUGH CURRICULUMANDSERVICE
EITPROVIDESOPEN-ACCESSSKILLS-BUILDINGWORKSHOPS,COSPONSORSSPEAKERS,ORGANIZESSCREENINGSANDREADING GROUPS,ADVOCATESFORPOLICYCHANGE,ANDPROVIDES OUTREACHANDNETWORKINGOPPORTUNITIES
OUR E-BOARD THIS YEAR






MADELINENELLIS'23 PRESIDENT EMILYPOWERS'23 TREASURER EVANHENDRICKSON'23 VICEPRESIDENT
WENDYYANG'23 SECRETARY RHEAMAJUMAR'23 OUTREACHCHAIR 96
VOLUME6 2022-2023
NEWCOMB INSTITUTE












































































 Fall: Winna Xia, Ananya Anand, Izzy Blair, Evan Hendrickson, Ifeoma Osakwe, Marisa Long
Fall: Rachel Tabor, Zoe Oboler, Claire Ramsey, Meghan Nagia, Tess Kleanthous, Catherine Hu, Wendy Yang
Fall: Winna Xia, Ananya Anand, Izzy Blair, Evan Hendrickson, Ifeoma Osakwe, Marisa Long
Fall: Rachel Tabor, Zoe Oboler, Claire Ramsey, Meghan Nagia, Tess Kleanthous, Catherine Hu, Wendy Yang












 Naomi
Wendy
Madeline
Marisa
Naomi
Wendy
Madeline
Marisa




 ByAaliyahRandall ByAaliyahRandall
ByAaliyahRandall ByAaliyahRandall






















 AhighleveloverviewofCloudComputingArchitecture
AhighleveloverviewofCloudComputingArchitecture






































 Steph Smith
Steph Smith























 By Olivia Riess
By Olivia Riess