
10 minute read
New age’ risk frameworks in a post-pandemic world by Kristen Gantt
‘new age’ risk frameworks in a post-pandemic world
by Kristen Gantt
Advertisement
In this unprecedented time of uncertainty caused by COVID-19, we are moving from ‘sheltering in place’ to slowly re-opening both our businesses and personal lives. We’ve launched into a surreal and futuristic world almost overnight with rapid change in business models, delivery channels and ways to interact with customers and stakeholders. Looking back, some organizations have used this time as an opportunity to bounce forward by reinventing the way they do business, while others struggled to bounce back and maintain relevance.
In either scenario, this new world raised the bar high on adaptability. During the disruption, both previously known and unanticipated risks are prevalent. What’s clear is that resiliency through change requires vast increase in the speed and quality of intelligence from the owned business operations and extended enterprises on which the business depends. Known risks changed the degree of ‘heat’ based on new operating models and processes that run them. Unanticipated risk scenarios presented themselves and required quick understanding of the new underlying processes, fast assessment of potential threats, and rapid design of risk treatment to reduce the potential for significant loss.
How then do risk frameworks adapt to the new normal? This article, exploring a variety of useful techniques aimed to vastly improve the quality of risk intelligence, beyond core GRC and risk data structures. Some of these methods are borrowed and re-invented from other business operations and/ or industries, and each is designed to help risk frameworks ‘bounce forward’ in this new era.
‘new age’ risk assessment: a focus on process discovery
The interconnectedness between traditional risk ‘domains’ has become undeniable. The common denominator between risk categories, or ‘domains’, and the Lines-of-defense (“LoD”) who manage these risks, is clearly the end-to-end (“E2E”) processes used to deliver critical goods / services through defined products.
What the COVID-19 experience has reinforced is that the extended enterprise including third-party, its people, processes, technologies used to deliver quality goods / services are inextricably entwined to sustain delivery of these products and services. At the same time, a significant proportion of regulatory obligations directly link to how the organization decides and processes transactions. To enable compliance, processes and control activities need to be well-designed. Ultimately, siloed risk assessments based on siloed views of E2E process can no longer survive the new era.
Current approaches challenge the value of risk assessments. Typical risk assessments start with an assessor formulating a risk profile for each Line of Business (“LoB”) by developing top-down risk statements, tying risk appetite to the business objectives. The assessor then shifts to create a bottom-up operational view of various risk scenarios, ultimately to compare results with the top-down risk profile. The frailty in this approach lies within the incomplete, inaccurate and potentially biased view of actual processes operating in the business. While an assessor may takes weeks or months to discover and document the underlying processes, the actual processes may have: a) changed significantly, making the documented understanding immediately outdated and/or incomplete; and b) represent only the assessor’s divisional view of the E2E flow.
Exhibit A in the diagram below illustrates the drivers in obtaining disparate E2E process understanding, based on the activity drivers for each risk domain.
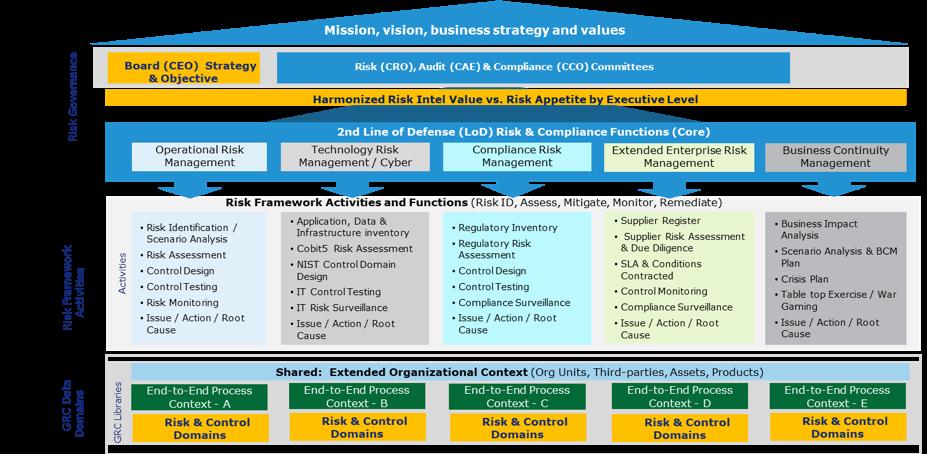
Exhibit A – Siloed LoD E2E Process Context (green) documented separately in static visual based on point of view of each LoD
Let’s use a hypothetical scenario that illustrates the frailty of current risk assessment methods:
The Compliance group of a US FSI is performing a risk assessment. After identifying the regulatory inventory, the compliance risk assessor maps the parts of the process where risk non-compliance can occur and included third parties in their assessment with compliance risk ‘in-scope’. Results are entered into their GRC system of record and tests of controls designed.
At the same time, the IT risk folks are looking at the same processes where the IT asset is linked, assessing risk of program and data breaches, including third parties where IT risks are deemed most relevant. IT risk group created a separate data flow diagram depicting the same process documented by the Compliance group.
Each of these risk groups’ E2E process maps took weeks or months to create a static view say, using MS Visio™. Methods used to create the E2E visual included separate management interviews and observation to piece together these disparate views.
At the same time, the COVID-19 pandemic hit, and the FSI had to rapidly respond by changing its operating model – in fact, depending on the location (NYC hotspot vs. non-hotspot area), new variations in process had been created ‘on the fly’. The controls designed to mitigate risks within the current Visio understanding of E2E process flow were fit for purpose for each LoD group; however, not knowing the actual process changes, the same controls may be unfit for purpose, inefficient or ineffective at mitigating exposure to the risks.
As a result, with the new WFH environment and process changes, this organization bypassed several internal controls used to ensure compliance to the regulations. The regulators received complaints, and infractions were identified in the WSJ and regulatory publications.
This hypothetical case study illustrates a risk framework that produced disjointed views of the extended enterprise, processes, technologies and related controls embedded in the process. In this case, the organizational risk framework was not able to change its views quickly enough to manage the new risk profile, making it difficult to adequately designed or collaborate on risk responses -- even with a mature integrated GRC system of record in place.
What does a ‘new age’ risk framework look like and how is it different? The short answer is the ‘devil is in [knowing] the [real] details’ – which are perpetually changing. If we turn the current risk assessment framework operating model upside down (or right-side up!) by starting with a closer-to-real-time shared view of E2E process, we can then use our collective domain expertise and risk lenses within the LoD to cull-out the risks and a coordinated risk response.
Today, most siloed LoD areas create their own views of process, highlighting the area of process most pertinent to the LoD’s own risk lens as they alone are the consumers of their view of the business.
This hypothetical case study illustrates a risk framework that produced disjointed views of the extended enterprise, processes, technologies and related controls embedded in the process. In this case, the organizational risk framework was not able to change its views quickly enough to manage the new risk profile, making it difficult to adequately design or collaborate on risk responses - even with a mature integrated GRC system of record in place.

Exhibit B – Shared E2E Process Context (green) using process mining AI – each LoD attains transparent visibility into E2E Processes closer-to-real-time
Consider a ‘new age’ process discovery using process mining AI tools. Now, let’s consider a new scenario. Say all LoD had access to a single, centralized view of truth of the actual E2E processes and data flows operating real-time? Further, using this approach it took 3 or 4 days to create an E2E visual of the actual process flow, including all variations across multiple geographic units. Further, the Visio previously created was converted into a machine readable BPMN format and compared to this ‘real-time’ view of E2E process.
We’ll now replay the above hypothetical scenario using advanced process mining techniques:
The Compliance group of a US FSI is performing a risk assessment. After identifying the regulatory inventory, the compliance risk assessor accesses the central E2E process flow view recently uploaded to the central Process Visualization system – all third parties and IT systems are identified on this map.
After executing a ‘Conformance Check’ against the current Compliance Process Visio (after converting into a BPMN), the Compliance risk assessor identifies the following:
• New processes are identified in the central E2E view, not shown on the reference Visio – the Compliance Risk Assessor considers the appropriateness of the process, introduction of new risk scenarios, and updates the reference Visio as needed.
• Control processes shown in the reference Visio are not shown in the central E2E view. The Compliance risk assessor collaborates with the IT Risk group to innovate the design of a new control with utility properties that reduce both Compliance and other risks.
• Using data flow analysis tools in the central E2E view, the risk assessor notes 22% of the transaction flow skips over the established control(s). The assessor immediately identifies transactions to be tested to ‘Discovery’ testing.
• New Processes and controls are added to the GRC system of record to link to refreshed RCSA and Testing record.
• The Compliance Risk assessor observes several other control steps in the central E2E view not considered ‘key’ in the reference Visio. These control steps are shown in the central E2E view to be manual, and the cycle time to process through the controls adds 5 extra days to throughput. The Compliance Risk assessor innovates an RPA use case to replace the manual controls to work in conjunction with the key control
At the same time, the IT risk folks are looking at the same central E2E process where the IT assets are all identified. Since dataflows and applications are shown in the central E2E process visual, the IT risk group proceeds in focusing on mapping shared services of Info Security processes.
• The IT Risk Assessor noticed a significant increase in volume of transactions moving through an application that is designed to handle a small number of transactions. Throughput times were also noted to have increased by 3 business days.
• The IT Risk Assessor-observed transactions are moving through a process supported by a new application provided by a new vendor, not included in earlier IT Asset inventories – a new risk assessment was created immediately.
As the COVID-19 pandemic changes the ‘return to work’ and ‘social distancing’ guidelines naturally over the next few weeks, these changes required the FSI to modify the process two more times. Each week, the central E2E process tool has current data uploaded to create new process analyses. As new processes are compared to prior versions, new insights are captured close-to-the-speedof-business.
As a result of being able to stay ahead of business and risk landscape changes, risk management alleviated time to focus on proactive customer and stakeholder communications, increase the efficiency of the control processes, and reduce compliance infractions in the operations.
Benefits using process discovery. With process discovery tools, each risk assessor was able to leverage the same current version of truth and perform analysis that met the needs of the LoD domain expert focus (e.g., Compliance or IT Risk). Each was able to focus more time and talent on identifying new risks and designing efficient and effective controls and develop closer-to-real-time monitoring metrics tied to business performance and risk reduction.
Risk managers have also become innovators by identifying areas where controls may be transformed using AI, RPA and other advanced analytics by analyzing throughput time reduction opportunities where bottlenecks or rework occurs where manual controls are ineffective or bypassed.
author
Kristen Gantt
Kristen Gantt is Managing Director ATS Solutions LLC, a risk advisory firm while also serving as an advisory council member of the Risk Management Association (RMA) Internal Auditors Society. Kristen recently held a Specialist Leader GRC Solutions role within Financial & Risk Advisory at Deloitte & Touche, LLP in U.S., responsible for developing service strategy and advising clients seeking to mature their integrated risk management programs and platforms. Prior to Deloitte, Kristen was regional vice president industry solutions at MetricStream, Inc. for five years, and responsible for establishing integrated risk management capabilities at key US Financial Services industry (FSI) and manufacturing industry clients. Prior to MetricStream, Kristen held a U.S. operational risk management leadership role at Natixis Corporate & Investment Bank as well as having over fifteen years expertise in the Internal Audit discipline as a senior manager / director for several major FSIs, including J.P. Morgan.






