
UnitCSEC03:DatabaseSecurityand Computer Programming
QUALIFI Level 5 Extended Diploma in Networkingand Cyber Security


QUALIFI Level 5 Extended Diploma in Networkingand Cyber Security
• The main purpose of this workbook is to supportyou as you study for the Qualifi Level4 diplomain CyberSecurity, so itspecifically focuses on the contentof the syllabus forthe Unit CSEC03: Database Security and Computer Programming.
• This workbook provides underpinning knowledgeand develops understandingto improve yourskills as wellas to prepare you for future assessment. If you are studyingtowards the Qualifi Level 4diplomain CyberSecurity then, if you choose to do so, you will be assessed on yourknowledge and understandingof the learningoutcomes.

• Database security concerns the use of a broad range of information security controls to protectdatabases (potentially includingthe data, the database applications orstored functions, the database systems, the database servers and the associated network links) againstcompromises of theirconfidentiality, integrity and availability. Itinvolves various types or categories of controls, such as technical, procedural/administrative and physical. Databasesecurity is a specialisttopic within the broaderrealms of computersecurity, information security and risk management.
• In this unitthe learners willexploresecurity risks to database systems and mitigation techniques. Understandingthe function of computerprogrammingis essential to understandingthe dark arts of ‘Black Hat Hackers’.
• Learners will also examine (as arollingcase study) Python as a popularcontemporary programminglanguage. The symbiotic link between developments in computerprogrammingand vulnerabilities to hackingwillbe examined and explored.

1. Understand the broad range of information security controls to protect databases.
2. Understand types of database categories of control.
3. Understand the underpinning concepts and models of cloud-based storage solutions.
4. Understand the relationship between computer programming and computer hacking.
5. Understand the ‘interpreted’ general-purpose programming language, Python.
Learning Outcome 1:

Understand the broad range of information security controls to protect databases
Assessment Criteria
1.1 Explain security risks in database systems.
1.2 Assess the effectiveness of information security concepts and tools in protecting databases.
• A database is an organized collection of structured information, or data, typically stored electronically in a computer system.
• A database is usually controlled by a database management system (DBMS). Together, the data and the DBMS, along with the applications that are associated with them, are referred to as a database system, often shortened to just database.
• Data within the most common types of databases in operation today is typically modeled in rows and columns in a series of tables to make processing and data querying efficient.
• The data can then be easily accessed, managed, modified, updated, controlled, and organized. Most databases use structured query language (SQL) for writing and querying data.


SQL is a programming language used by nearly all relational databases to query, manipulate, and define data, and to provide access control.
SQL was first developed at IBM in the 1970s with Oracle as a major contributor, which led to implementation of the SQL ANSI standard, SQL has spurred many extensions from companies such as IBM, Oracle, and Microsoft.
Although SQL is still widely used today, new programming languages are beginning to appear.

Databases have evolved dramaticallysince their inception in the early1960s.
Navigational databases such as the hierarchical database (which relied on a tree-like model and allowed onlya one-to-many relationship), and the network database (a more flexible model that allowed multiple relationships), were the original systems used to store and manipulate data.
Although simple, these earlysystems were inflexible.
In the 1980s, relational databases became popular, followed byobject-oriented databases in the 1990s.
More recently, NoSQL databases came about as a response to the growth ofthe internet and the need for faster speed and processingof unstructured data.
Today, cloud databases and self-driving databases are breakingnew ground when it comes to howdata is collected, stored, managed, and utilized.
(www.oracle.com, 2020)

Informationstored in a database management system can be either highly structured (such as accounting records or customer information) or unstructured (such as digital images or spreadsheets).
The data may be accessed directly by customers and employees, or indirectly through enterprise software, websites, or mobile apps. Additionally, many types of software such as business intelligence, customer relationshipmanagement, and supply chain applications use information storedin databases.
• There are many different types of databases. The best database for a specific organization depends on how the organization intends to use the data.
• Relational databases. Relational databases became dominant in the 1980s. Items in a relational database are organized as a set of tables with columns and rows. Relational database technology provides the most efficient and flexible way to access structured information.
• Object-oriented databases. Information in an object-oriented database is represented in the form of objects, as in object-oriented programming.
• Distributed databases. A distributed database consists of two or more files located in different sites. The database may be stored on multiple computers, located in the same physical location, or scattered over different networks.
• Data warehouses. A central repository for data, a data warehouse is a type of database specifically designed for fast query and analysis.
NoSQL databases. A NoSQL, or no relational database, allows unstructured and semi structured data to be stored and manipulated (in contrastto a relational database, which defines how all data inserted into the databasemustbe composed). NoSQL databases grew popular as web applications becamemore common and more complex.
Graph databases. A graph databasestores data in terms of entities and the relationships between entities.
OLTP databases. An OLTP databaseis a speedy, analytic databasedesigned for largenumbers of transactions performed by multipleusers.
These are only a few of the several dozen types of databases in usetoday. Other, less common databases aretailored to very specific scientific, financial, or other functions.

In addition to the differentdatabasetypes, changes in technology developmentapproaches and dramaticadvances such as the cloud and automation are propellingdatabases in entirely new directions. Some of the latestdatabases include:
• Opensource databases. An open source database system is one whose source code is open source;such databases could be SQL or NoSQLdatabases.
• Clouddatabases. A cloud database is a collection of data, either structured or unstructured, thatresides on aprivate, public, or hybrid cloud computingplatform. There are two types ofcloud database models:traditionaland database as a service (DBaaS). With DBaaS, administrative tasks and maintenanceare performed by a service provider.
• Multimodel database. Multimodel databases combine different types of database models into asingle, integrated back end. This means they can accommodate various datatypes.

Document/JSON database. Designed for storing, retrieving, and managingdocument-oriented information, documentdatabasesare a modern way to store data in JSON format rather than rows and columns.
Self-driving databases. The newest and most groundbreakingtype of database, self-driving databases (also known as autonomous databases) are cloud-based and use machine learningto automate database tuning, security, backups, updates, and other routine management tasks traditionally performed by database administrators.

• A database typically requires acomprehensivedatabase software program known as a database managementsystem (DBMS).
• A DBMS serves as an interface between the database and its end users or programs, allowingusers to retrieve, update, and manage how the information is organized and optimized.
• A DBMS also facilitates oversightand control of databases, enablinga variety of administrative operations such as performance monitoring, tuning, and backup and recovery.
• Some examples of populardatabase software orDBMSs include MySQL, MicrosoftAccess, MicrosoftSQLServer, FileMakerPro, Oracle Database, and dBASE.

Today’s large enterprise databases often support very complex queries and are expectedto deliver nearly instantresponses to those queries.
As a result, database administrators are constantly calleduponto employ a wide varietyof methods to help improve performance.Some common challenges that theyface include:
Absorbing significant increases in data volume. The explosion of data coming in from sensors, connected machines, and dozens of other sources keeps database administrators scrambling to manage andorganize their companies’ data efficiently.
Ensuring data security. Data breaches are happening everywhere these days, andhackers are getting more inventive.It’s more important than everto ensure thatdata is secure but also easily accessible to users.
• Keeping up with demand. In today’s fast-moving business environment, companies need real-time access to their data to support timely decision-making and to take advantage of new opportunities.
• Managing and maintaining the database and infrastructure. Database administrators must continually watch the database for problems and perform preventative maintenance, as well as apply software upgrades and patches. As databases become more complex and data volumes grow, companies are faced with the expense of hiring additional talent to monitor and tune their databases.
• Removing limits on scalability. A business needs to grow if it’s going to survive, and its data management must grow along with it. But it’s very difficult for database administrators to predict how much capacity the company will need, particularly with onpremises databases.
• Addressing all of these challenges can be time-consuming and can prevent database administrators from performing more strategic functions.
Keeping up with demand. In today’s fast-moving business environment, companies need real-time access to their data to support timely decision-making and to take advantage of new opportunities.

Managing and maintaining the database and infrastructure. Database administrators mustcontinually watch the databasefor problems and perform preventative maintenance, as well as apply softwareupgrades and patches. As databases become more complex and data volumes grow, companies are faced with the expense of hiring additional talentto monitor and tune their databases.
Removing limits on scalability. A business needs to grow if it’s going to survive, and its data management must grow along with it. But it’s very difficultfor databaseadministrators to predicthow much capacity thecompany will need, particularly with on-premises databases.
Addressing all of these challenges can be time-consuming and can prevent databaseadministrators fromperforming more strategic functions.

• Every day, hackers unleash attacks designed to steal confidential data, and an organization’s databaseservers are often the primary targets of these attacks.
• Databases are one of the mostcompromised assets accordingto the 2015 Verizon DataBreach Investigations Report.
• “The reason databases are targeted so often is quite simple, they are at the heartof any organization, storingcustomerrecords and otherconfidential business data,”said Morgan Gerhart, vice presidentof productmarketingat cybersecurity firm Imperva. Organizations are notprotectingthesecrucial assets well enough, he added.
• “When hackers and malicious insiders gain access to sensitive data, they can quickly extractvalue, inflictdamage orimpact business operations. In addition to financialloss orreputation damage, breaches can resultin regulatory violations, fines and legal fees,”he said.
• The threats identified over the years are the same that continue to plague businesses today.
• The most common databasethreats include:
• Excessive privileges
• Legitimate privilege abuse
• Database injection attacks
• Malware
• Storagemedia exposure
• Exploitation of vulnerable databases
• Unmanaged sensitive data
• The human factor
• Denial of service attack
• Database users may have different privileges.
• When workers are granted default database privileges that exceed the requirements of their job functions, these privileges can be abused,
• Excessive privileges always create unnecessary risks. According to statistics 80% of the attacks on company databases are executed by current company employees or ex-employees.
• Some companies fail to update access privileges for employees who change roles within an organization or leave altogether.
Legitimate privilege abuse
• Users may abuse legitimate database privileges for unauthorized purposes
• It is advised to deploy and uphold a strict access and privileges control policy.
• Don’t grant excessive privileges to company employees and revoke outdated privileges in time.
• The two major types of database injection attacksare SQL injections that target traditionaldatabase systems and NoSQL injections that target “big data” platforms.
• This is a type of attackwhen a malicious code is embedded in frontend (web) applications and then passed to the backend database
• As the result of database injections cybercriminals get unrestrictedaccess to any data being stored in a database.
• Stored procedure shall be used instead of direct queries.
• MVC Architecture shall be implemented.
A perennial threat, malwareis used to steal sensitivedata via legitimate users using infected devices.

• It’s a good practiceto make backups of proprietary databases atdefined periods of time.
• However, surprisingly databaseback-up files areoften left completely unprotected from attack.
• As a result, there are numerous security breaches happening through databasebackup leaks.
• Failureto auditand monitor the activities of administrators who have low-level access to sensitiveinformation can putthe data at risk.
• Encrypt both databases and backups. Storing data in encrypted form allows secureboth production and back-up copies of databases.
• Audit both the databaseand backups.Doing this helps to see who has been trying to get access to sensitivedata.

Exploitation of vulnerable databases
• It often happens that databases are found totally unprotected due to misconfiguration.
• Some databases have default accounts and configuration parameters.
• One should remember that hackers are often highly professional IT specialists who surely know how to exploit database vulnerabilities and misconfigurations and use them to attack the databases.
Countermeasures for Exploitation of vulnerable databases
• Databases shouldn’t have any default accounts.
• IT personnel should be highly qualified and experienced.
• Many companies store alotof sensitive information and fail to keep an accurate inventory of it.
• Forgotten and unattended datamay fall prey to hackers.
• In addition, new sensitive datais added daily and it’s noteasy to keep track of itall.
• It means thatnewly added datamay be exposed to threats.
• These type of data will be exposed to threats if the required controls and permissions are notimplemented
• Encrypt all sensitive datain yourdatabase(s).
• Apply required controls and permissions to the database.
• Run periodicsearch fornew sensitivedataon yourdatabases. You can do this very effectively with the PeriodicDataDiscovery tool and Compliance Managerthatwill automatically discovernewly added sensitive dataand protectit.
• Databases get breached and leaked due to insufficient level of IT security expertise and education of non-technicalemployees who may break basic database security rules and put databases at risk.
• IT security personnel may also lack the expertise required to implement security controls, enforce policies, or conduct incident response processes.
• Database users shall be educated in database security.
• IT security specialists shall be urged to raise their professionallevel and qualification.
• This type of attacks slows down a database server and can even make it unavailable to all users.
• Even though a DoS attack doesn’t disclose the contents of a database, it may cost the victims a lot of time and money.
• What’s the use of a database if you can’t use or access it.
• Harden the TCP/IP stack by applyingthe appropriate registry settings to increase the size of the TCPconnection queue.
• Decrease the connection establishment period.
• Employ dynamicbacklog mechanisms to ensure that the connection queue is never exhausted.
• Use a network Intrusion Detection System (IDS).
(www.ibm.com, 2020)
•
Learning Outcome 2:
• Understand types of database categories of control.
• Assessment Criteria
• 2.1 Explain database terminology and categories of control.

• A database is a structure that organizes and stores data electronically.
• The data is stored using a database management system (DBMS) such as Microsoft Access, MySQL or Microsoft SQL Server.
• Data is organized into rows, columns, and tables, so that it can be easily accessed, managed and updated.
• Tables
• A table is a set of data represented by columns and rows.
• A column is referred to as a field and a row is a combination of column values and is referred to as a record.
www.sum-it.nl
www.lankelma.nl
• Tables Cont.
• Tables contain a uniqueset of characteristics and they store data of the same type in each row.
• A tablein a databaselooks likea simplespreadsheet.
• Row
• A row (= tuple, entry) is a group of related data, for example the data of one subscription. Onerow can not contain lists.
• Column
• One column (data element) contains data of one and the same kind.
The example above has 3 rows and 2 columns.
• Data Fields
• A data field which is onepiece of information you track in your database.
• Each data field in the table can define the characteristics of its data as a string value, numeric value, date and/or time values.
• Relationships
• A relational databasecontains tables thatrelateto another tableby using a relationship.
• The tables areconnected by a common field.
• The relationships aredefined as:
• One to Many: this is the most common type of a tablerelationship. For every record in TableA, there aremultiplerecords in TableB.
• Example: There is a one to many relationship between the Customers table and Orders table. A customer may have many orders in the Order table.
Many to Many: For every record in Table A, there are multiple records in Table B, and vice versa. In this case, a third table called a Join Table is created to which will contain only unique values
Example: Many to Many relationship between Orders and Products with the table ProductsOrders functioning as the Join Table. The table ProductsOrders holds all the details about each order and what products it contains. Its primary key is a combination of the primary key of the Orders and Products table.
One to One – the rarest type of a table relationship. It is used for security and organization to avoid empty fields that only apply to some records in a table.

• Keys
• Key fields are used to build the relationships between datain different tables.
• Primary Key: Usually auto-numbered, unique IDforinternal trackingand for matchingrecords between related tables. Each value is unique to the table and cannotbe null. There is only one Primary Key pertable
• ForeignKey:A field in arelated table pointingback to the Primary Key in anothertable. Forauto-numbered fields itis defined as anumbervalue.
• Index
• An index in a database resembles an indexatthe back of a book.
• Usinga keyword you can find the rightpage numberof rows, within atable.
• Referential Integrity
• Referential Integrity makes sure that a foreign key value always points to an existing row.
• A "dead" link can not happen anymore.
• Several rules can enforce referential integrity.
• When creating or updating a row the system checks whether the foreign keys have valid values.
• In addition the database designer chooses an action for delete:
• It's only possible to delete a row in the one-table when there a no more related many-rows.
• When deleting a row the RDBMS automatically deletes the related data in the many table. This is called a cascaded delete.
• When deleting the last 'many' the RDBMS automatically deletes the related 'one' row.

• Professor Ross Anderson of Cambridge university have been arguing that by their nature large databases will never be free of abuse.
• Anderson's Rule means you cannot construct a databasewith scale, functionality and security because if you design a large system for ease of access it becomes insecure, while if you make it watertight it becomes impossible to use. (Anderson, 2008)
Database control refers to the task of enforcing regulations to provide correct data to authentic users and applications of a database.
In order that correct data is available to users, all data should conform to the integrity constraints defined in the database. Besides, data should be screened away from unauthorized users so as to maintain security and privacy of the database.
Database control is one of the primary tasks of the database administrator(DBA).
The three dimensions of database control are:
Authentication
Access rights
Integrity constraint

• Authentication
• In a distributed database system, authentication is the process through which onlylegitimate users can gain access to the data resources.
• Authentication can be enforced in two levels:
• Controlling Access to Client Computer − At this level, user access is restricted while login to the client computer that provides userinterface to the database server.
• The most common method is a username/password combination. However, more sophisticated methods like biometric authentication maybe used for high securitydata.
• Controlling Access to the Database Software − At this level, the database software/administrator assigns some credentialsto the user.
• The user gains accessto the database using these credentials. One of the methods is to create a login account within the database server.
A user’s access rights refers to the privileges that the user is given regarding DBMS operations such as the rights to create a table, drop a table, add/delete/update tuples in a table or query upon the table.
In distributed environments, sincethere are large number of tables and yet larger number of users, it is not feasible to assign individual access rights to users. So, DDBMS defines certain roles.
A role is a construct with certain privileges within a database system. Once the different roles are defined, the individual users are assigned one of these roles. Often a hierarchy of roles are defined according to the organization’s hierarchy of authority and responsibility.
• Integrity constraint
• Semantic Integrity Control
• Semantic integrity control defines and enforces the integrity constraints of the database system.
• The integrity constraints are as follows:
• Data type integrity constraint
• Entity integrity constraint
• Referential integrity constraint
• Data Type Integrity Constraint
• A data type constraint restricts the range of values and the type of operations that can be applied to the field with the specified data type.
• For example, let us consider that a table "HOSTEL" has three fields - the hostel number, hostel name and capacity. The hostel number should start with capital letter "H" and cannot be NULL, and the capacity should not be more than 150.

• Integrityconstraint Cont.
• Semantic IntegrityControl Cont.
• Entity Integrity Control
• Entity integrity control enforces the rules so thateach tuple can be uniquely identified from othertuples. Forthis aprimary key is defined. A primary key is a setof minimal fields thatcan uniquely identify atuple.
• Entity integrity constraintstates thatno two tuples in atable can have identical values forprimary keys and thatno field which is apart of the primary key can have NULL value.
• Integrity constraint Cont.

• Semantic Integrity Control Cont.
• Referential Integrity Constraint
• Referential integrity constraint lays down the rules of foreign keys.
• A foreign key is a field in a data table that is the primary key of a related table. The referential integrity constraint lays down the rule that the value of the foreign key field should either be among the values of the primary key of the referenced table or be entirely NULL.
In addition to implementing layered security controls across the entire network environment, database security requires to establish the correct controls and policies for access to the database itself.
These include:
Administrative controls to govern installation, change, and configuration management for the database.
Preventativecontrols to govern access, encryption, tokenization, and masking.
Detective controls to monitor database activity monitoring and data loss prevention tools. These solutions make it possible to identify and alert on anomalous or suspicious activities.
• Database security policies should be integratedwith and support the overall business goals, such as protection of critical intellectual property and cyber security policies and cloud security policies.
• Ensure to designated responsibility for maintaining and auditing security controls within the organizationand that the policies complement those of the cloud provider in shared responsibility agreements.
• Security controls, security awareness training and education programs, and penetration testing and vulnerability assessment strategies should all be established in support of the formal security policies. (www.ibm.com, 2020)
• Sina Weibo
• Date: March 2020
Impact: 538 million accounts
Details: With over 500 million users, Sina Weibo is China’s answer to Twitter. However, in March 2020 it was reported that the real names, site usernames, gender, location, and -- for 172 million users -- phone numbers had been posted for sale on dark web markets. Passwords were not included, which may indicate why the data was available for just ¥1,799 ($250).
• Weibo acknowledged the data for sale was from the company, but claimed the data was obtained by matching contacts against its address book API. It also said that since doesn't store passwords in plaintext, users should have nothing to worry about. This, however, doesn’t tally as some of the information being offered such as location data, isn’t available via the API. The social media giant said it had notified authorities about the incident and China’s Cyber Security Administration of the Ministry of Industry and Information Technology said it is investigating.
• Marriott International
• Date: 2014-18
Impact: 500 million customers
Details:Marriott International announced in November2018 that attackers had stolen data on approximately 500million customers. The breach initially occurred on systems supporting Starwood hotel brands startingin 2014. The attackers remained in the systemafterMarriottacquired Starwood in 2016 and were not discovered until September2018.
• The attackers were able to take some combination of contact information, passportnumber, Starwood Preferred Guestnumbers, travel information, and otherpersonal information. The creditcard numbers and expiration dates of more than 100 million customers were believed to be stolen, butMarriottis uncertain whetherthe attackers were able to decryptthe creditcard numbers. The breach was eventually attributed to aChinese intelligencegroup seekingto gatherdata on US citizens, accordingto a New York Times article.
• MySpace
• Date: 2013
Impact: 360 million user accounts
Details: Though it had long stopped being the powerhouse that it once was, social media site
MySpacehit the headlines in 2016 after 360 million user accounts were leaked onto both
LeakedSource(a searchable database of stolen accounts) and put up for sale on dark web market
The Real Deal with an asking price of 6 bitcoin (around $3,000 at the time).
• According to the company, lost data included email addresses, passwords and usernames for “a portion of accounts that were created prior to June 11, 2013, on the old Myspaceplatform.”
According to Troy Hunt of HaveIBeenPwned, the passwords were stored as SHA-1 hashes of the first 10 characters of the password converted to lowercase.
• eBay
• Date: May 2014
Impact: 145 million users
Details: eBay reported that an attack exposed its entire account list of 145 million users in May 2014, including names, addresses, dates of birth and encrypted passwords. The online auction giant said hackers used the credentials of three corporate employees to access its network and had complete access for 229 days—more than enough time to compromise the user database.
• The company asked customers to change their passwords. Financial information, such as credit card numbers, was stored separately and was not compromised. The company was criticized at the time for a lack of communication with its users and poor implementation of the password-renewal process.
• (www.csoonline.com, 2020)
Understandthe underpinningconcepts and models of cloud-based storage solutions.
3.1 Explore the functionality of database tools available to Data Owners, Custodians, Incident Responders and Investigators.
Today, a wide array of vendors offerdataprotection tools and platforms. A fullscale solution should include all the followingcapabilities:
Look fora tool that can scan for and classify vulnerabilities across all the databases, whetherthey’re hosted in the cloud or on-premise and offer recommendations for remediatingany vulnerabilities identified.
Discovery capabilities are often required to conformto regulatory compliance mandates.
• The solutionshouldbe able to monitor and audit all data activities across all databases, regardless of whether the deployment is on-premise, in the cloud, or in a container.
• It should alert the suspicious activities in real-time so that the companies can respond to threats more quickly.
• Database administratorswant a solution thatcan enforce rules, policies, and separation of duties and that offers visibility into the status of the data through a comprehensive and unified user interface.
• Make sure that any solution that choose can generate the reports which shall need to meet compliance requirements.
• In case of a breach, encryption offers a final line of defense against compromise.
• Any tool that choose should include flexible encryption capabilitiesthat can safeguard datain on-premise, cloud, hybrid, or multicloud environments.
• Look for a tool with file, volume, and application encryption capabilities thatconform to the industry’s compliance requirements, which may demand tokenization (datamasking) or advanced security key management capabilities.
Data security optimization and risk analysis
A tool that can generate contextual insights by combining data security information with advanced analytics will enable to accomplish optimization, risk analysis, and reporting with ease.
Choose a solution that can retain and synthesize large quantities of historical and recent data about the status and security of the databases, and look for one that offers data exploration, auditing, and reporting capabilities through a comprehensive but user-friendly self-service dashboard.
Amongthe most significantdatabase tools, we can find the following:
With database visualization, organizations obtain visual representation and graphics of data that help them understand it and make better, more informed business decisions.
Through database visualization tools, database admins can fully understand the raw data that lives in databases and gain value fromitby identifyingpatterns or trends.
By visualizinga database, users getto explore datain a more effectivemannerthat allows fordeeper analysis.
• Databases typically include complex sets of data that can create performance issues if not thoroughly examined.
• With database performance testing, users can take preemptive actions that can help correct any issue that is identified during the testing process.
• By simulating real-life load for databases, administrators can pinpoint how the database will react under the specific circumstances when multiple users use the database simultaneously.
• Database backup and recovery are strategies and proceduresthat help ensure the databaseis protectedagainst data loss and the associated problems of reconstruction.
• By backing up a database, users create a duplicate database for use in case of a crash, data corruption, or any type of data loss.
• In essence, databasebackups help recover data easily and reconstruct it in case of loss.
The method of ‘Grandfather-Father-Son’ backup scheme belongs to the most widely used schemes.
This scheme uses daily (Son), weekly (Father) and monthly (Grandfather) medium sets.
Four medium sets are titled everyday backup of workweek (i.e. Monday to Thursday).
On these medium sets (titled as Son in the scheme of GFS) the incremental backups take place.
These medium sets (Son) are repeatedly rewritten during the next week.


Database Backup Cont.
Grandfather-Father-Son (GFS)
• Another group of five medium sets, which is included in the GFS scheme, are medium sets titled as Week 1, Week 2, and so on (Father).
Refer the figure:
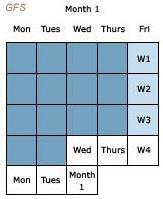
On these mediumsets (Father) the full backups take place every week, the Son mediumsets are notused, and the expiration time of ‘Father’ group is one month.
Then theirrewritingfollows. The final mediumset‘Grandfather’ consists of 3 mediumsets (medium setmay be composed of one ormany tapes) and itis titled as ‘Month 1, Month 2, Month 3, and so on’.
On these mediumsets the follow-up rewritingtakes place once perthree months and more (depends on how many sets are devoted to ‘Grandfather’ group.
The expiration of these sets (itis the possibility of anotherrewriting) is adjusted accordingto the numberof mediumsets in GrandfatherGroup.
Database Backup Cont.
Each ‘medium set’ of tape groups (Son, Father or Grandfather) is either individual or a set of tapes. That is dependent on the size of backed-up data.
The total number of used medium sets in the GFS backup scheme is twelve. By reason of tape wear and by reason of keeping a longer history (archiving) it is recommended to change the medium sets for new ones in a certain time period. (Anderson, 2008)
• It is the movement of data from one platform to another.
• Through several stages and iterations, database migration takes into consideration the current state of the database as well as the future needs of the organization, migratingthe schema and movingthe data simultaneously.
• One of the main benefits associated with database migration is cost as it enables companies to move from an on-premise database to a cloud database in a cost-effective manner.
It is the duplication of data in different places, whether by accident or done deliberately for backup and recovery purposes.
DBMS software provides control over data redundancy and saves storage space by doing so.
Typically, DBMS solutions use data normalization techniques to avoid unnecessary redundancy and duplicate data.
Understand the relationship between computer programming and computer hacking.
4.1 Explain various popularcomputer programming languages.
4.2 Analyse the relationship between programming skills and the abilityto hack into systems.

• Computer programming languages allow us to give instructions to a computer in a language the computer understands.
• Such instructions can be executed directly when they are in the computer manufacturer-specific numerical form known as machine language, after a simple substitution process when expressed in a corresponding assembly language, or after translation from some “higher-level” language.
• Machine and assembly languages are “low-level,” requiring a programmer to manage explicitly all of a computer’s idiosyncratic features of data storage and operation.
• In contrast, high-level languages shield a programmer from worrying about such considerations and provide a notation that is more easily written and read by programmers.
Although there are many computer languages, relatively few are widely used.
Just as many human-based languages exist, there are an array of computer programming languages that programmers can use to communicate with a computer.
Just as many human-based languages exist, there are an array of computer programming languages that programmers can use to communicate with a computer.
The portion of the language that a computer can understand is called a “binary.”
Translating programming language into binary is known as “compiling.”

• Each language, from C Language to Python, has its own distinct features, though many times there are commonalities between programming languages.
• These languages allow computers to quickly and efficiently process large and complex swaths of information.
• For example, if a person is given a list of randomized numbers ranging from one to ten thousand and is asked to place them in ascending order, chances are that it will take a sizable amount of time and include some errors.
• There are dozens of programming languages used in the industry today. Here we've compiled overviews of the most important, relevant and in-demand of these languages.

• Python was developed in the late 1980s at CWI in the Netherlands and first released to the publicin 1991.
• Python is an easy to learn, powerful programming language. It has efficient high-level data structures and a simple but effective approach to object-oriented programming.
• Python’s elegant syntax and dynamic typing, together with its interpreted nature, make it an ideal language for scripting and rapid application development in many areas on most platforms.
• The Python interpreter and the extensive standard library are freely available in source or binary form for all major platforms from the Python Web site, https://www.python.org/, and may be freely distributed.
(www.python.org, 2020)
• The same site also contains distributions of and pointers to many free third-party Python modules, programs and tools, and additional documentation.
• The Python interpreter is easily extended with new functions and data types implementedin C or C++ (or other languages callable from C).
• Python is also suitable as an extension language for customizable applications.

• Professions and Industries:
• Python developers, software engineers, back end developers, Python programmers
• Used by employers in information technology, engineering, professional services and design
• Major Organizations: Google, Pinterest, Instagram, YouTube, DropBox, NASA, ESRI
• Specializations and Industries: Weband Internet development (frameworks, micro-frameworks and advanced content management systems); scientific and numeric computing; desktop graphical user interfaces (GUIs)

• Python lets you work quickly to integrate systems as a scripting or glue language. It’s also suited for Rapid Application Develop (RAD).
• The game Civilization 4 has all its inner logic, including AI, implemented in Python.
• NASA uses Python in its Integrated Planning System as a standard scripting language.
Features:
• Simple to learn and easily read
• Associated web frameworks for developing web-based applications
• Free interpreter and standard library available in source or binary on major platforms
(www.python.org, 2020)

• Java is a general-purpose, object-oriented, high-levelprogramminglanguagewith several features thatmake itideal forweb-based development.
• Originally known as Oak, Javawas developed in 1990 at Sun Microsystems to add capabilities to the C++ language. Javawas developed accordingto the principleof WORA (Write Once Run Anywhere). The language was introduced to the publicin 1995 and is now owned by Oracle.
Whouse it?
• Professions andIndustries:
• Software engineers, Javadevelopers
• Used by employers in communications, education, finance, health sciences, hospitality, retail and utilities
• Major Organizations:V2COM, Eclipse Information Technologies, eBay, Eurotech
• Specializations andIndustries: Internet of Things (IoT), Enterprise Architecture, Cloud Computing

• Java is used to develop enterprise-level applications for video games and mobile apps, as well as to create web-based applications with JSP (Java Server Pages). When used online, Java allows applets to be downloaded and used through a browser, which can then perform a function not normally available.
• Programs that use or are written in Java include Adobe Creative Suite, Eclipse, Lotus Notes, Minecraft and OpenOffice.
• Java is the core foundation for developing Android apps.
Features:
• Application portability
• Robust and interpreted language
• Extensive network library

• Ruby is an open-sourced, object-oriented scripting languagethatcan be used independently or as partof the Ruby on Rails web framework.
• Designed in 1995, Ruby’s creator described itas “simplein appearance, but it is very complex inside, justlikeour human body.”
• Ruby is used for simulations, 3D modeling, and to manage and track information.
• Basecamp, Amazon, Twitter and Groupon were all created using Ruby on Rails.
• NASA uses Ruby to conduct simulations.
Features:
• Free to use, copy, modify and distribute
• Intuitiveand flexiblelanguage
• Completely object-oriented (ability to use method chaining)

• Professions and Industries:
• Ruby on Rails developers, software engineers, data science engineers
• Used by employers in technology, engineering, professional services, design, science and quality control
• Major Organizations: Github, Scribd, Groupon, NASA Langley Research Center, Blue Sequence (part of Toyota Motor Manufacturing), Motorola, Google (SketchUp)
• Specializations and Industries: Web App Development, Robotics, Networking, System Administration and Security

• JavaScript is a client-side programming language that runs inside a client browser and processes commands on a computer rather than a server. It is commonly placed into an HTML or ASP file. Despite its name, JavaScript is not related to Java.
• JavaScript was designed by Netscape and originally known as LiveScript, before becoming JavaScript in 1995.
• JavaScript is used primarily in Web development to manipulate various page elements and make them more dynamic, including scrolling abilities, printing the time and date, creating a calendar and other tasks not possible through plain HTML. It can also be used to create games and APIs.
• The agency Cyber-Duck in Britain uses public APIs, createdwith JavaScript, to pull in data about crime and enables users to review a local area.
• Tweetmap, created by Pete Smart and Rob Hawkes using JavaScript, represents a world map that is proportionally sized according to the number of tweets.
Features:
• Basic features are easy to learn
• Multiple frameworks
• Users can reference JQuery, a comprehensive Javascript library


• Professions and Industries:
• JavaScript developers, Web developers, software engineers
• Used by employers in Information Technology, Engineering, Design, Marketing, Finance and Healthcare
• Major Organizations: WordPress, Soundcloud, Khan Academy, Linkedin, Groupon, Yahooand many others
• Specializations and Industries Where JavaScript is Used Most: Front End Website Development, Gaming Development

• Professions andIndustries:
• SwiftPlatformDevelopers, iOS Mobile Application Developers, Software Developers, SeniorProgrammers, Data Engineers
• Information Technology, Engineering, Design, Managementand Professional Services
• Major Organizations:Apple, Getty Images, Slack, Dow Jones, Playlist Media
• Specializations Where Swiftis Used
Most: Software development

• C++ is a general purpose, object-oriented, middle-level programming language and is an extension of C language, which makes it possible to code C++ in a “C style”. In some situations, coding can be done in either format, making C++ an example of a hybrid language.
• Released in 1983 and often considered an object-oriented version of C language, C++ was created to compile lean, efficient code, while providing high-level abstractions to better manage large development projects.
• The C++ language is used to create computer programs and packaged software, such as games, office applications, graphics and video editors and operating systems.
• The Blackberry OS is developed using C++.
• The newest Microsoft Office suite was developed using C++.
Features:
• Often the first programming language taught at college level
• Quick processing and compilation mechanism
• Robust standard library (STL)

• Professions andIndustries:
• C++ software engineers, C++software developers, embedded engineers, programmeranalysts
• Used by employers in Information Technology, Engineering, Professional Services, Design, Quality Control and Management
• Major Company and Organization Users: Google, Mozilla, Firefox, Winamp, Adobe Software, Amazon, Lockheed Martin
• Specializations:System/Application Software, Drivers, Client-ServerApplications, Embedded Firmware

• HTML is the standard markup language used to create web pages; it ensures proper formatting of text and images (using tags) so that Internet browsers can display them in the ways they were intended to look.
• HTML was created by physicist Tim Berners-Lee in 1990 to allow scientists to share documents online. Before then, all communication was sent using plain text. HTML made “rich” text possible (i.e. text formatting and visual images).
• HTML is used to create electronic documents (pages) displayed online. Visit any page and you will see an example of HTML in action.
• The diversity and complexity in the structure and appearance of today’s sites is made possible with HTML.
Features:
• Easy to use and learn the basics of HTML
• Free and accessible
• Multiple versions available



• Professions and Industries:
• Web developers, technical editors, email designers, software engineers
• Used by employers in Information Technology, Engineering, Design, Professional Services, Management, Marketing, Customer Services and Sales
• Major Organizations:Apple, CyberCoders, Apex Systems, CareerBuilder
• Specializationsand Industries Where HTML is Used Most: Web Development, Email Programming
We generally write a computer program using a high-level language. A high-level language is one that is understandable by us, humans. This is called source code. However, a computer does not understand high-level language. It only understands the program written in 0's and 1's in binary, called the machine code.
To convert source code into machine code, we use either a compiler or an interpreter.
Both compilers and interpreters are used to convert a program written in a high-level language into machine code understood by computers.
However, there are differences between how an interpreter and a compiler works.
Compiled Languages
• Compiled languages are converted directly into machine code that the processor can execute. As a result, they tend to be faster and more efficient to execute than interpreted languages. They also give the developer more control over hardware aspects, like memory management and CPU usage.
• Compiled languages need a “build” step – they need to be manually compiled first. You need to “rebuild” the program every time you need to make a change.
• Examples of pure compiled languages are C, C++, Erlang, Haskell, Rust, and Go.
Programs that are compiled into native machine code tend to be fasterthan interpreted code. This is because the process of translatingcode at run time adds to the overhead and can cause the program to be sloweroverall.
The most notable disadvantages are:
•Additional timeneeded to complete the entire compilation step before testing
•Platformdependenceof the generated binary code

• Interpretersrun through a programline by line and execute each command.
• Interpretedlanguages were once significantly slower than compiled languages. But, with the development of just-in-time compilation, that gap is shrinking.
• Examples of common interpreted languages are PHP, Ruby, Python, and JavaScript.
Advantagesof interpretedlanguages
• Interpretedlanguages tend to be more flexible, and often offer features like dynamic typing and smaller program size. Also, because interpretersexecute the source program code themselves, the code itself is platform independent.
Disadvantagesof interpretedlanguages
• The most notable disadvantageis typical execution speed compared to compiled languages.
Compiled Language
A compiled language is a programming language whose implementations are typically compilers and not interpreters.
Interpreted Language
An interpreted languageis a programming languagewhose implementations execute instructions directly and freely, without previously compiling a programinto machinelanguageinstructions.

Once the program is compiled it is expressed in the instructions of the target machine.
The instructions are not directly executed by the target machine.
Error are displayed after the entire program is compiled
Memory requirement is more due to the creation of object code.
Error are displayed for every single instruction.
Memory requirement is less.
There are at leasttwo steps to get from sourcecode to execution.
There is only one steps to get from sourcecode to execution. Source code ---Compiler ---
CompiledLanguage

InterpretedLanguage
Compiled programsrun faster than interpreted programs. Interpretedprograms can be modified while the program is running.
Compilation errors prevent the code from compiling. All the debugging occursat runtime.
The code of compiled language can be executed directly by the computer’sCPU.
A program written in an interpreted language is not compiled, it is interpreted.
Delivers better performance. Delivers relatively slower performance.
e.g: C,C++, Java e.g: Perl, Python, Ruby
Difference between Compiled and Interpreted Language
Cont.
• Programmers solve problems using code, a Hacker is a creator/tinkerer, and a Developer is a formally trained programmer who doesn’t just solve problems but does so in a structured and disciplined way that was probably learned formally.
• A Programmer is someone who can solve problems by manipulating computer code. They can have a wide range of skill levels—from just being “ok” with basic scripting to being an absolute sorcerer with any language.
• A Hacker is someone who makes things. In this context, it’s someone who makes things by programming computers. This is the original, and purest definition of the term, i.e., that you have an idea and you “hack” something together to make it work. It also applies to people who tinker with things in a way that extends or changes their functionality, or otherwise uses them in ways that weren’t originally intended.

A Developer is a formally trained programmer. They don’t just solve problems or create things but do so in accordance with a set of design and implementation principles. These include things like performance, maintainability, scale, robustness, and (ideally) security.
What developers, hackers, and programmers all have in common is that they solve problems using code.

• People can be any combination of Developer, Programmer or a hacker. Here’s how they relate to each other
• All hackers and developers are programmers.
• Some people started out as programmers and became hackers. They typically become very good at their job, as they can understand the code and how to patch it.
• Many programmers, and even developers, are not creative enough to be considered hackers.
• Many programmers, and even hackers, are not educated or experienced enough to be considered developers.
• Ideally, one would strive to be all three, i.e., creative enough to be considered a hacker, but with enough formal training and experience to design software rather than simply, hacking it together.
• But even if someone aren’t very creative, and/or lack the education and/or experience to properly build massive applications, shouldstill be proud to be a programmer.
• Solvingproblems usingcode is a superpower by itself.
• While the programmer may be good at writingprograms, that are also secure, the hacker’s job is to understandthe code and find bugs in it, and generally suggest patches too.
• A hacker may not be able to write a big program from scratch, but they are generally able to review source code in most languages and find security issues that the programmer missed.
• The programmer’s job is generally to create an application.
• The hacker’s job is to use that application in an unintendedway, and in some cases, the hacker will need to know some programmingin order to make the program execute his or her own code perhaps
A programmer is one who writes code. A hacker is one who exploits vulnerabilities on a system or a network.
Someone who can solve problems by manipulatingcomputer code is known as a programmer.
Someone who makes things. In this context, it’s someone who makes things by programming computers is known as a hacker.
The programmer is a problem solver.
Many programmers are not creative enough to be considered hackers.
The Hacker is the creator.
All hackers are programmers.
LEARNING OUTCOME 5:
INVESTIGATE WHERE NON-MALICIOUS AND MALICIOUS HACKERS HAVE UTILISED PYTHON.
5.1 INVESTIGATE WHERE NON-MALICIOUS AND MALICIOUS HACKERS HAVE UTILISED PYTHON.

• Python is one of the fastest-growing programming languages than any other language and playing a major role in Ethical hacking & cyber security industries that mainly used to develop the various penetration testing and hacking tools.
• Python is one of the well-known programming languages that can help crack into the big databases.
• It is one of the desired code-cracker for hackers all over the world.
Why is Python language used for Hacking?
• Its 3-5 times shorter than Java programs, as Python not just presents excellent ease for Python developers, but the programmer can be more fruitful in Python.
• With a mere and simple syntax and a code style guideline that promotes the usage of formatting of codes, it’s all recommendation for beginners. It’s just the best programming language to nail it.
• Python is a dynamic language with high-level inbuilt data standards. Thus it enables developers to maintain multiple variables at the equivalent time, thus limiting any loss of time.
• It’s a simple language for hackers that utilize simple functions and variables.


• Python is evaluated as a general-purpose programming language, and not only this, it is also known as a scripting language.
• Python is a vast language, not just because it is extensively used in software development, web frameworks, and applications.
• Still, the effective programming language can be utilized for everything that is created on the Java platform.
• However, the fact is that Python is a high-level scripting language that can promptly join existing elements together.
• The most exciting feature of python regarding hackers is that there are a lot of python-modules that can encourage hackers to reproduce exploit scripts.
• Hacking, as an object, needs utilizing libraries that can do the language reversal task.
• Python library consolidates built-in modules (written in C) that present a free hand over system functionality just as file I/O that would contrarily be unavailable to Python programmers.
• Python has a tremendous rebuilt and a very conventional library that can make hacking a kid’s play for an already well-knowledged person for hacking.
• It has great third-party libraries that assist hackers in getting the job done
• As it encourages the hacker to do away with existing tracked by Anti-viruses (AV), invasion detection system, and many more, so, it has to be a chosen language between hackers.
Noticeably Python, continued to be the weapon of choice for most hackers.
Next, we can see Google’s Go, WinHttp library, which is mainly used by .net and CPP running on Windows, followed by Shell tools such as cURL, wget and others. The rest of the top tools were more.
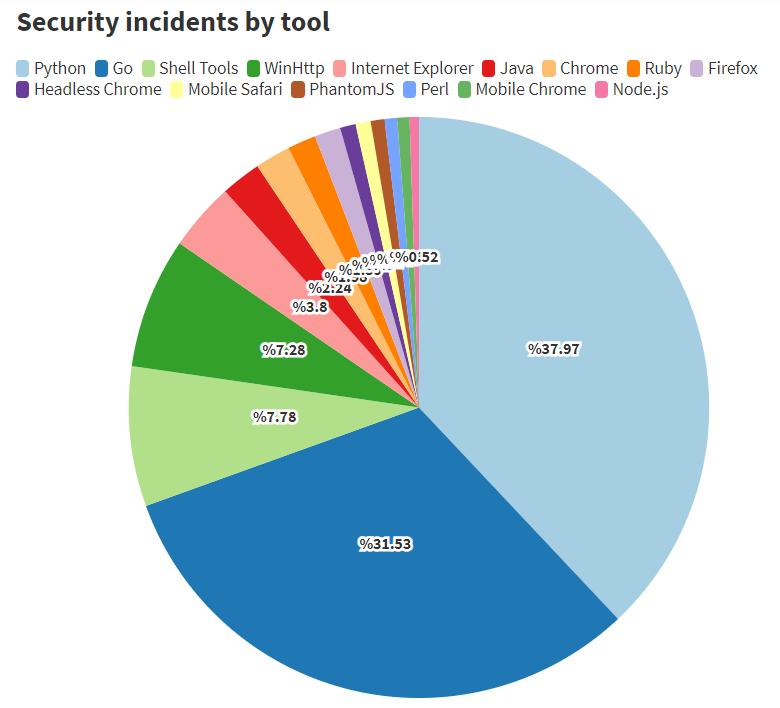

• As illustratedbelow, Python was the strongest tool in RCE/RFI, File Upload and Data Leakage attacks duringthe year 2019. China used Python way more than any other country. It’s hard to say why but given how wellknown these countries are for their cyber activity, it’s possible that new hackers joiningthe market chose modern tools for their nefarious activities. (www.imperva.com, 2020)
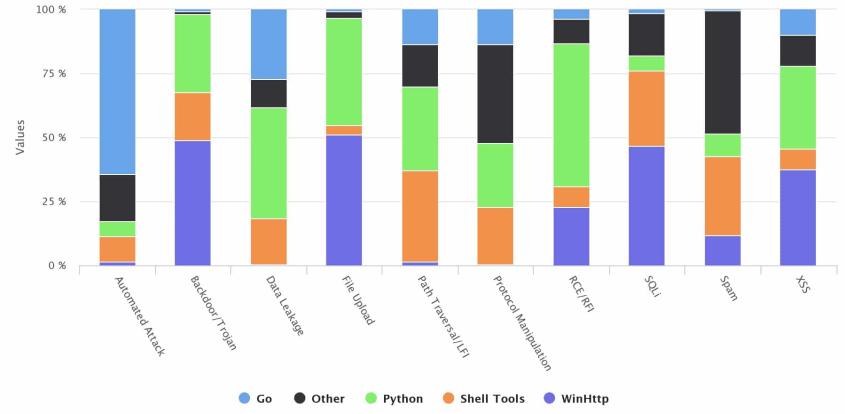
As stated above that Python is the most desired programming language employed by hackers since it’s an open-source language, which means that hackers can manage the stuff that other hackers have earlier made.
Not only this as being free and high-level language, but it also occurs with a group of genius support as well.
Though unethical hacking isn’t an apprehended thing to do, ethical hacking and re-coding in phases of upgrading and adjustment is an attached advantage that Python has in store to attempt.

• Alfred Basta& Melissa Zgola (2011)
Database Security, Boston: USA: Cengage Learning
• Mark Lutz (2013)Learning Python (5th Ed.) Newton: USA, O’Reilly Media
