KNOWLEDGE NEXUS
Enjoy the highlights from the 2024 Security Middle East Conference
GATEWAY TO THE GULF
Unveiling seamless security with mobile access control


Enjoy the highlights from the 2024 Security Middle East Conference
Unveiling seamless security with mobile access control

Shahnawaz Siddiqui of Allied Telesis Middle East explores the security needs of the smart networks powering the region’s smart buildings






EDITORIAL
Publisher
Barry Bebbington
+44 1708 229354 barry@pubint.co.uk
Editor
Cora Lydon +44 7834 244613
cora.lydon@securitymiddleeastonline.com
ADVERTISING
Worldwide
Mike Dingle
+44 1752 267330
mike@securitymiddleeastonline.com
Gareth Driscoll
+44 1752 260603 gareth@securitymiddleeastonline.com
Ryan Bickerton +44 1752 265802 ryan@securitymiddleeastonline.com
Rahul Vara +44 1752 604352 rahul@securitymiddleeastonline.com
Marketing Manager
Paul Riglar
+44 7496 377630 paul@securitymiddleeastonline.com
Digital Editor
Britt Jones
brit@securitymiddleeastonline.com
PUBLISHED BY
Publications International Ltd +44 1708 229354
166 Front Lane, Upminster, Essex, RM14 1LN, UK
This publication may not be reproduced or transmitted in any form in whole or in part without the written consent of the publishers.
©Publications International Ltd. 2024
For subscriptions and advertising enquires, or for further information on the magazine visit our website at: securitymiddleeastmagazine.com

It may have only been a matter of weeks since we wrapped the Security Middle East Conference 2024, but already we’re busy making plans for next year’s conference with some exciting new developments that will be unveiled in the coming months. This year’s May event was a huge success and demonstrated the collaborative spirit our industry is known for. We had the brightest and the best minds in the security sector generously share their expertise with our delegates, and our audience engage with our panel discussions to help advance the sector’s future. Turn to page 15 to find out more about how the day unfolded and on page 20 you can read our chairperson’s reflections on the event.
As always, this issue is packed to the brim with insightful reads to ensure you stay on top of your role. On page 37, Luke Wilkinson, MD at Mobile Tornado covers how the future of real-time communications for the security and
safety sector is Push-to-talk Over Cellular, while if you want to be sure your disaster recovery plan is water-tight, Nazy Fouladirad, President of Tevora, has the strategies for you (page 28).
Allied Telesis is also discussing the need for the smart networks responsible for powering the next generation of smart buildings to prioritise security – take a closer look at what its Regional Sales Manager, Shahnawaz Siddiqui has to say on the topic on page 12.
Until next issue…
Cora Lydon Editor
cora.lydon@securitymiddleeastonline.com
Middle East Magazine
138 JULY 2024
03 Up front
Foreword from the Editor
06 News Monitor
The latest regional and international security news
09 Market Monitor
A roundup of the latest security products and solutions
12 Cover story: Allied Telesis
Shahnawaz Siddiqui, Regional Sales Manager at Allied Telesis Middle East discusses the need for smart networks powering smart buildings to prioritise security
15 Security Middle East Conference 2024
May’s Security Middle East Conference 2024 was a resounding success –find out more about the strategic discussions, keynote speakers and networking opportunities that were had
20 Chairperson’s reflections
Daniel Norman, Regional Director, EMEA of the ISF, and Chairperson for the Security Middle East Conference looks back at our recent event and the key take-aways our audience gained
22 Security Middle East Conference Gallery
Take a look at some of the pictures from this year’s events

24 Navigating the cloud opportunity
Firas Jadalla, Regional Director META at Genetec says the cloud is facilitating faster, easier physical security deployments
28 Tactics for recovery readiness
Find out the strategies needed to ensure you have an effective disaster recovery plan, by Nazy Fouladirad, President and COO of Tevora
31 Mobile access for the hyper-digital GCC
Mobile access powers and secures a sustainable future of work in the hyper-digital GCC, says Sam Cherif, Senior Director, Regional Business Head, MEA at HID
37 The future of real-time communications
Luke Wilkinson, Managing Director at Mobile Tornado, explores how push-to-talk over cellular is improving operational efficiencies for the public safety and security sectors
40 The urgency of integrated security in banking
The banking and finance sectors must adopt a layered security approach to tackle risk, according to Matt Tengwall, SVP and Global GM, Verint

44 Zebra Technologies’ stripes of security
Security Middle East magazine spoke with Oliver Ledgard, EMEA Government and Aviation Vertical Lead at Zebra Technologies to explore asset management tech for the defence industry
46 Case study: border security agency
Powered by ClanTect technology we look at how a border security agency was able to improve its operations
49 Interview: Hospitality
Meshal Aljohani of Aramco, talks to Vitthal Teli, Area Security Specialist for Hyatt Hotels Corporation about tourism and hospitality security
50 Diary
Diary dates for forthcoming security exhibitions, conferences and events

SAFE — The National Security Services Company is owned by The Public Investment Fund and was established in 2019. Its mission is to lead the transformation of the security services ecosystem and to promote and transform the security services sector through a consultative approach and by offering best-in-class security solutions. Its vision is to be the ultimate security partner leading the transformation of the security ecosystem. SAFE joined the Security Middle East Conference as Strategic Partner.



Regional Sales Manager at Allied Telesis Middle East
Shahnawaz Siddiqui works for Allied Telesis Middle East as Regional Sales Manager, and has worked for the company for over a decade.
Dan Norman
Regional Director, EMEA, Information Security Forum (ISF)
Dan Norman’s role at the ISF is to help organisations manage their current and emerging cyber risks.
President and COO of Tevora
President and COO of Tevora, a global cybersecurity consultancy, where she has worked for two decades.


















Cloudflare announced its 2024 Q1 DDoS report that shares insights through its global Cloudflare network, which is one of the largest in the world.
It found that Cloudflare’s defence systems automatically mitigated 4.5 million DDoS attacks during the first quarter — representing a 50 per cent year-on-year (YoY) increase.

Within the data, DNS-based DDoS attacks were found to have increased by 80 per cent YoY and remain the most prominent attack vector.
Globally, the gaming and gambling industry was the number one most targeted by HTTP DDoS attacks with just over seven of every 100 DDoS requests that Cloudflare mitigated being aimed at this industry.
Cequence, a leading company in API security and bot management, announced it signed a Memorandum of Understanding (MoU) with Aramco Digital Company to establish plans for a strategic collaboration to enhance and localise API security within the Kingdom of Saudi Arabia.
The collaboration aims to enhance the digital transformation of Saudi Arabia’s industrial sectors by implementing Unified API Protection (UAP) that will safeguard critical data and functionality exposed through APIs.
Ameya Talwalkar, CEO of Cequence said: “The digital landscape’s expansion, especially with the advent of generative AI and its reliance on APIs, has made APIs the number one target for attackers. As APIs become the backbone of digital transformation, securing them is paramount. This partnership underscores our commitment to providing best-in-class API security solutions that shield sensitive data and guarantee seamless and secure adoption of AI in enterprises.” cequence.ai
EllisDon has finalised a new partnership between its Infrastructure Services & Technology (IST) Division and J2 Innovations.
The collaboration will see EllisDon utilise J2 Innovations’ FIN Framework, which enables original equipment manufacturers (OEMs) to create automation and IoT applications quickly and efficiently.
In second place was the information technology and internet industry.
Bashar Bashaireh, Managing Director & Head of Sales — Middle East and Türkiye at Cloudflare said: “Cloudflare’s mission is to help build a better internet, a vision where it remains secure, performant, and accessible to everyone. With four out of every 10 HTTP DDoS attacks lasting over 10 minutes and approximately three out of 10 extending beyond an hour, the challenge is substantial. Yet, whether an attack involves over 100,000 requests per second, as is the case in one out of every 10 attacks, or even exceeds a million requests per second — a rarity seen in only four out of every 1,000 attacks — Cloudflare’s defences remain impenetrable.” cloudflare.com

Home security provider, Ring has released its smart solution for pet owners in the Middle East who want to ensure their furry friends are looked after.
With advanced motion detection, live view and two-way talk, Ring devices allow owners to check in on their pets to make sure they are safe.
Mohammad Meraj Hoda,
The partnership will allow EllisDon’s IST Division to further develop its digital twin application, EKO, focusing on integrating all data points within a facility to optimise the built environment and enhance the end user’s experience.
Robert Barnes, Senior Vice President, Energy & Digital Services at EllisDon said: “We are excited to collaborate and enhance industry standards by utilising
Vice President – Emerging Markets at Ring said:
“Homeowners can ensure their peace of mind knowing that they can check in on their pets at any time if they have to run out for a quick errand.
“With Ring, homeowners can check on their pets remotely, reducing anxiety for owners, and allowing them to stay connected even while they’re away.” ae-en.ring.com
J2 Innovations’ expertise in FIN Framework, as it will be an important component of our digital twin application, EKO. This partnership will leverage the strengths of both companies by exploring new opportunities, strengthening product offerings, and providing cutting-edge solutions to meet the evolving needs of the market.” ellisdon.com
INTERNATIONAL NEWS
WSO2 has signed a definitive agreement to be acquired by EQT, to deliver innovative solutions across integration, API management, identity & access management (IAM) and application development.
With EQT as its new partner, WSO2 is “focused on driving customer success, fostering community collaboration, and delivering innovative software that unlocks new value creation opportunities.”
Dr Sanjiva Weerawarana, CEO and Founder of WSO2 said: “We are thrilled to partner with EQT as we embark on the next phase of WSO2’s journey. With EQT’s support and expertise, we are wellpositioned to accelerate our innovation agenda, expand our global footprint,

and continue empowering enterprises to thrive in the digital economy.”
Hari Gopalakrishnan, Partner in the EQT Private Capital Asia advisory team, added: “We’re excited to partner with WSO2 as it helps customers across industries drive their digital transformation and enhance operational resilience. We believe that WSO2 is well-positioned to capitalise on long-term trends such as digital transformation and rising generative AI adoption and are confident of drawing on EQT’s proven software value creation playbook to further accelerate WSO2’s strong growth.” wso2.com

INTERNATIONAL NEWS
Ian Dyson QPM DL is the new Chair of the Chartered Security Professionals’ Registration Authority (CSPRA), according to the Worshipful Company of Security Professionals. Dyson replaced Baroness
Ruth Henig and will help oversee the admission, governance and maintenance of the Register of Chartered Security Professionals.
He said: “It is a huge privilege to be taking on the role of Chair of CSPRA and in doing so I pay tribute to Ruth Henig, who was an exemplary chair and widely respected both inside and outside the industry. During my time in the City of London police I saw the impressive work of the Security Institute and the Worshipful Company, in helping to professionalise the security industry and I hope to continue to build on the excellent work done to date.” security-institute.org/csyp
INTERNATIONAL NEWS
The SDoT Industry Gateway combines the same level of security and performance as the military and public sector and incorporates flexibility and straightforward integration into existing industrial environments.
It enables fully secure and controlled data exchange between operational technology (OT) and information
technology (IT). By providing highly secure data communication, the SDoT Industry Gateway is based on an enhancement of the architecture of the infodas SDoT Data Diode, which is certified by Bureau Veritas. The product mitigates the threat of potential cyberattacks and ensures a high profitability with an attractive, turnkey and subscription-based model. infodas.com/en
BAHRAIN AND BRITAIN SIGN SECURITY AGREEMENT
Bahrain announced a military agreement with Britain which will provide military facilities at the Mina Salman Bahrain Defence Force base as part of a strategy to build relations with major nations. This relates to bolstering regional and energy security in the Arabian Gulf gas and oil exportation market.
SAUDI ARABIA CREATES NEW SECURITY AUTHORITY
Saudi Arabia has created a new authority for cybersecurity with its Minister of State, Musaed al-Aiban, as its Chairman. According to a royal decree, the National Authority for Cyber Security is set on strengthening security in the world’s largest oil exporter, and will include the heads of state security, intelligence, and the deputy interior minister and assistant to the minister of defense.
KUWAIT’S DIRECTOR GENERAL OF STATE SECURITY SUSPENDED
Kuwait’s Minister of Interior Anas al-Saleh suspended the Director General of State Security and the former director of the money laundering department and a number of officers after investigations into 2018 recordings found the Interior Ministry allegedly spying on citizens.
The UAE Cyber Security Council urged iPhone users to install the latest software in a social media post which cited: “Apple has released a security update to address several critical security vulnerabilities for its various products, that could potentially allow attackers to gain unauthorised access to devices, steal data, or execute malicious code.”
The United States and the Sultanate of Oman have agreed to a strategic partnership on regional security.


INTERNATIONAL NEWS
Veeam Software has announced new technical training and certification programmes through Veeam University.
The new online offering is the result of a global partnership with Tsunati, a Veeam Accredited Service Partner.
The education provider offers maximum flexibility and an immersive, engaging learning experience in a self-paced format. This approach includes clickable labs that can be accessed at any hour and any day, video-based demos and technical deep
INTERNATIONAL NEWS
ATERMES will establish a new MENA headquarters in Dubai, UAE to accommodate growing demands in these strategic industries.
dives allowing students to effectively absorb concepts and prepare for realworld cybersecurity and disaster recovery scenarios.
Mike Blanchette, Vice President, Global Sales Acceleration at Veeam said: “Knowledge is critical in a world where every organisation is facing cyber threats. “Cyber resilience is the marriage of the right technology to protect and recover your systems and data should the worst happen, with the skills and knowledge to configure, build, and run that technology safely. Through these new investments

The announcement — made on the same day ATERMES confirmed its participation at ISNR Abu Dhabi, the region’s largest national security, cybersecurity, and civil protection event — illustrates the company’s vision for expanding its Middle Eastern operational presence and partnership ecosystem.

in Veeam University, we are preparing people to tackle any cybersecurity challenge they face and enabling cyber resiliency. Our partnership with Tsunati enables us to provide innovative technical training and certification programmes in a flexible format that best suits the learner.” veeam.com
Elaborating on the upcoming MENA office and the positive implications this entails for customers, Walid Lahoud, Head of Operations MENA, ATERMES, said: “Our regional HQ in Dubai will represent the beginning of a vibrant new era of robust relationships with those we serve. From partners we’ve accommodated for many years to organisations we’ve just begun working with and alongside, this facility will embody our forward-facing commitment to fostering even greater degrees of trust and transparency.
“Ultimately, it will empower us in our mission to provide more personalised support and expertise to customers –individually and collectively. With enhanced intimacy by bringing our operations closer to home, we’ve no doubt that we’ll succeed in ensuring that all receive the tailored solutions and unconditional duty of care that they need, expect and deserve.” atermes.fr/en
INTERNATIONAL NEWS
Defendis has announced the launch of its AI-powered platform. The newlylaunched platform was unveiled at GITEX Africa and will enable organisations to proactively contain data leaks and neutralise cyberattacks.
The platform taps into AI to identify credentials and payment card leaks, asset vulnerabilities, phishing attacks, fraudulent domains and online brand impersonation attempts.
Amine Bajeddi, Co-founder and CEO of Defendis said of the company’s goals: “Our mission is to provide
organisations, especially those with limited resources and capabilities, with advanced cybersecurity solutions to adapt to the ever-changing threat landscape and regulatory requirements.” defendis.ai
Heriot-Watt University and Mohamed bin Zayed
Heriot-Watt University and Mohamed bin Zayed University of Artificial Intelligence (MBZUAI) have announced a collaboration to establish an international Centre for Doctoral Training (CDT) in Robotics and Artificial Intelligence in the UAE.
The collaboration will allow students access to support and supervision across both universities and the opportunity to align with the world-leading faculty, facilities and courses at MBZUAI as well as at Heriot-Watt University in Dubai and Edinburgh.
The new centre will be capable of supporting up to 60 doctoral students at any one time, and the CDT aims to build capability and intellectual property in the UAE in alignment with the National Artificial Intelligence Strategy 2031.
The CDT will enable Heriot-Watt University to bring its Scottish expertise to the UAE and position the country as a leader in AI.


The four-year programme will include taught courses and an industrial placement in the first year of study, along with annual conferences and workshops in both the UAE and Scotland.
Provost and Vice Principal of Heriot-Watt University Dubai, Professor Dame Heather McGregor, said: “Heriot-Watt University in the UK hosts National Robotarium, an acknowledged international centre for robotics teaching and research. We are delighted to be partnering with the prestigious MBZUAI and bringing together leading faculty to support the UAE’s National Artificial Intelligence Strategy, which aims to position the UAE as a global leader in artificial intelligence by 2031, this collaboration with MBZUAI will allow us to jointly contribute to advancing the country as a leader in AI technologies.” hw.ac.uk/dubai.htm
Orange Business has signed an agreement with EdgeConn to support in establishing the AWS Outposts in Egypt.
EdgeConn’s strategic customer, the Egypt Ministry of Education is currently targeting the transformation of the educational content delivery for 22 million students and teachers in the K-12 segment.
Orange Business was able to roll out in a number of days an initial connectivity service for EdgeConn to meet the project needs.
With the signing of this agreement, Orange Business is now providing the cloud connectivity network service through its strategic partnership with AWS. Orange Business will provide end-to-end, fully managed services including hardware, design, implementation and operation.
These include connectivity (Business VPN Galerie service to privately connect to AWS); professional services (Network Consultant for design phase); technical management to provide end-to-end configuration; project management during the implementation phase; service management (Service Manage - 24X7 Service Support Orange Business helpdesk and remote proactive service monitoring); and dedicated customer service manager during the operation phase. orange-business.com
It also provides server redundancy through its failover service which allows on-site
AxxonSoft is gearing up to launch Axxon Air, a unified cloud security solution that reshapes the field of video surveillance through cloud-managed VMS.
Incorporating a health monitoring service that collects data from all connected locations about camera operation, network utilisation, server hardware and software condition and storage space, the administrator can monitor system health and receive notifications when the controlled parameters go out of norm.
Axxon Air servers to be organised into failover clusters, with standby servers that automatically take over all functions from the off-line or malfunctioning servers.
In addition, Axxon Air offers auto-backup of server configurations in the cloud, which minimises the system downtime by quickly deploying the same configuration on another server when one of the servers goes down or you need a hardware upgrade.
Further cybersecurity features implemented in Axxon Air include:
n Two-factor authentication.
n reCAPTCHA v3 on the web client login screen.
n User password hashing.
n Password expiry and password history.
n Setting the lockout time/number of failed login attempts.
n Auto-logout after a set period of inactivity.
n Inactive account locking after a set period, with reactivation by email.
n System integrity checks at server startup. axxonsoft.com
Sunray is the specifiers choice for Steel Security, Fire and Blast Doors, Louvre Panels/Facades and Steel/GRP Platforms and Walkways. Our comprehensive Steel Door Range and associated products provides Fire Ratings for up to 4 Hours plus overrun and Security Ratings from SR1-SR6.
We lead the industry with our Door Size Ratios, which enables the Architect, Designer or Specifier to maximise infill without overpanel and creating clean sight lines, as well as practical ease of access for plant, machinery, and general use. With an extensive list of hardware and locking options, electro-mechanical access, vision panels, finishes etc. we tailor your criteria to deliver the required performance and practical solution.
● UTILITY

● TRANSPORT
● POLICE
● EMBASSY & CONSULATE
● PETROCHEM
● RETAIL
- sub-stations, transformer chambers, plant & pump rooms.
- rail, including underground, airport & ferry terminals.
- government & military, armouries, ranges, sensitive & secure buildings.
- UK & abroad.
- UK & abroad.
- staff / safe & stock rooms & financial institutions.
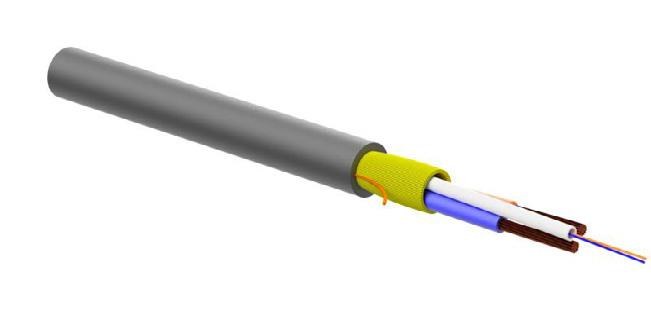
Find out more about how the smart networks that power smart buildings must prioritise security, to deliver the best possible user experience
Today’s buildings can do more for us than ever before, and they should. By improving satisfaction for tenants or employees, smart buildings can increase staff retention and maximise occupancy, helping ensure ROI for landlords. Add the role that smart buildings play in the reduction of greenhouse emissions, and the case for them is strong.
According to Gartner, IoT expenditures in smart buildings were $53 billion in 2020 and are expected to reach $108 billion by 2030. So, it’s worth looking at the drivers behind the development of smart buildings and recognising that there is a common denominator that underpins them all; which is that smart buildings need smart networks.
In a smart building, occupancy patterns allow for smart comfort levels in both open spaces and meeting rooms, and this can be extended to individual preferences by making adjustments before meetings start or at a simpler level controlling temperature in meeting rooms only when they are booked and occupied. This extends to lighting levels and fast start meeting rooms.
Flexibility to allow changes, the ability to accommodate personal preferences and to monitor for individual health and workplace security are reasons why tenants remain for longer. According to research from CMS, renters are willing to pay 20 per cent more on average to live in a smart building. Energy efficient buildings also sell for as
much as 17 per cent more than standard building stock, generate 35 per cent more rental income, and have 18 per cent higher occupancy rates, according to JLL.
But smart buildings don’t have to be created from scratch. Retrofitting existing buildings increases return on investment with payback taking less than two years and delivering 25 per cent energy savings annually.
Blurring of the line between Information Technology (IT) and Operational Technology (OT) has been happening for many years. In telephony, IP has been the norm for 15 years and during this time other technologies have been repackaged as IP applications and moved from the facilities department to IT; with electronic security in the form of CCTV and access control soon following telephony’s lead.
The smartest buildings run a centralised Building Management System (BMS) made up of IT and OT over a single converged IP network. A BMS on a converged IP network further interlinks Facilities Management and Property Management and enables instant notifications about issues which reduce downtime.
Shahnawaz Siddiqui, Regional Sales Manager at Allied Telesis Middle East, commented: “The benefits of data flowing across a converged network are that it can easily be presented to a single pane of glass dashboard, allowing intelligent


rule-based changes to a building’s settings as well as allowing predictive maintenance decisions to be made from real-world live data. This has a major benefit in smart enabled buildings as integrations between systems are predominately made at the network level.”
‘‘This has a major benefit in smart enabled buildings as integrations between systems are predominately made at the network level’’
The danger for OT equipment relying on IT is that they can become more easily exposed to security breaches. IT, however, is experienced in keeping its network safe, which is another way that the convergence of OT and IT allows for better use of resources while delivering a single IP network that is well protected and is accessible to all building and business systems. The best converged IP networks for smart buildings also enable a network security system that watches for unusual activity such as repeated failed user logins, user logins at unusual terminals or devices, unusual user movements, data leaks, and unusual network activity. AMF-Sec, from Allied Telesis, can isolate the resources in real-time, giving IT or management time to investigate and remediate.
The intelligent services that make a building smart, such as layout and user flexibility, access control, heating and lighting, security and more, require 24/7 connectivity to the BMS for operational efficiency and to provide the best user experience. A converged data network that delivers a wealth of information reliably from the many end devices and systems to the BMS is essential for optimal building performance. Look for a network partner experienced in providing secure, resilient, always-on networks that underpin smart building operations.
With a converged IP network architecture from Allied Telesis, our smart building solutions are efficient, agile and secure. Combined with our intelligent monitoring and network automation tools for complete control, you spend less and get more.
A converged end-to-end integrated systems architecture reduces your network cost and complexity and minimises your environmental impact. Your customers enjoy a range of benefits too. alliedtelesis.com

Safety and security for now and whatever’s next.
With the world’s #1 OEM Solutions Provider * a safer and more secure future is all by design. *Global Share based on 2023 Revenue, VDC Research, Worldwide OEM Solutions Provider



The sun beat down on Saudi Arabia this May as the second annual Security Middle East Conference (SMEC) unfolded. Building on the triumphs of its inaugural year, the conference cemented its place as the premier security summit in the region. From engaging panel sessions to unparalleled networking opportunities, the conference delivered a powerful combination of knowledge, connection and inspiration.
The conference commenced with a thought-provoking address by Fahad Alghamdi, Chief Operations Officer at The National Security Services Company – SAFE, and a prominent figure in the industry. Alghamdi’s speech underscored the conference’s commitment to fostering a collaborative approach to security across the Middle East. And of course, his own extensive contributions to the sector and his passion and dedication to advancing security in the region helped set the tone for an event brimming with expert-led discussions and a strong sense of community.
The beating heart of the Security Middle East Conference 2024 was undoubtedly its panel sessions. These lively forums brought together a diverse range of security professionals, each offering their unique perspectives on some of the most pressing security challenges facing the region. These sessions weren’t dry, one-sided presentations – they were vibrant exchanges of ideas, experiences and best practices. Delegates had the opportunity
to actively participate, posing questions and engaging in discussions on a range of demanding security issues.
The first session, Preparing Security Professionals for Major Events and Increased Tourism, explored the security considerations that arise alongside booming tourism sectors. Panellists tackled the delicate balance between ensuring safety and fostering a welcoming environment for visitors. Attendees gained valuable insights into best practices for securing major events, from crowd control strategies to implementing cutting-edge security technologies. Sharing insightful and informative discussions with us were: Tawfeeq Alsadoon, Group Head of Security, Red Sea Global; Konstantin Turuntcev, Managing Partner, Event Concept Consultancy; Trevor Sinden, Regional Director, March Networks; Andrew Long, Principal Security Risk Management Consultant, WSP Middle East, alongside moderator Luke Bencie, Managing Director at Security Management International.
Another excellent session, Building Resilient Cities: Future-proofing the Region’s Giga Projects, delved into the ever-evolving
concept of urban resilience. Panelists Firas Beiruti, Regional Manager, Dell Technologies; Joe Stanley, Riyadh Council Chairman, Overseas Security Advisory Council; Abdulaziz Alqahtani, Manager Security Operations, Saudi Aramco; Mohamad Saad, KSA and Bahrain Country Manager, Genetec and Issam Shibany, Director of Presales and Business Development, Convergint, were joined by our moderator, Craig Ross, Associate Director, Safety and Security, Diriyah Company. Our experts discussed how cities can prepare for and respond to various security threats, from natural disasters to cyberattacks. The session offered attendees a roadmap for building robust urban security frameworks, fostering a sense of safety and well-being for residents and businesses alike.
Sustainability in the security sector was another key theme explored in a dedicated panel session, How Can the Industry Create a Green and Secure Future? Our panelists were Saeed Ba-Dugaish, Manager of Security Operations, Saudi Aramco;

Dr Ahmed Sakalla, Chief Operations Manager, Wafrat Al Kheer Group; Farah Ghanem, Head of Climate Change and Policy, Alpin Limited and moderator Muttahir Salim, Associate Director Security, Buro Happold. They explored the oftenoverlooked connection between environmental well-being and security. Discussions centred on the need to build sustainable security solutions that not only protect people and assets but also safeguard the environment for future generations. Attendees learned about innovative solutions and best practices for minimising the environmental footprint of security operations.
One of the liveliest panels of the day saw four women take to the stage to debate the session: Challenging the Normal: Improving Inclusivity, Equality and Diversity in Security. We were delighted to welcome Hayley Van Loon, Deputy CEO, Crimestoppers International and CEO of Magnolia Intelligence; Sumaiyah Alotaibi, Manager of Security Operations, Saudi Aramco; Uliana Barbysheva, Managing Partner, Event Concept Consultancy, and our moderator Betania Allo, ex-United Nations and NEOM and a cyber law and policy expert. Discussions came thick and fast and covered everything from looking outside of the usual hiring pools and exploring transferrable skills, through to cultural aspects, the role of men in championing diversity and how to tackle unconscious biases.
The final panel discussion to engage our audience focused on cybersecurity, and more specifically the topic of artificial intelligence (AI). Our speakers discussed how to guard against ever-evolving threats that arise due to advances in AI technology, and what all security professionals should be aware of. Up on stage we were lucky enough to have global information technology expert, Ian Keller; Dr Nasser Alamri, Cybersecurity Executive Director for the Institute of Public Administration Saudi Arabia; Khalid Almedbel, CISO within government and Daniel Norman, from the ISF as our moderator. One important thing the audience took away with them was that a resilient business, can only be resilient to the threats it is facing. It was clear that the experts were in agreement that AI poses a significant threat to businesses globally.
While our discussion panels facilitated debate, our keynotes were all about sharing knowledge from some of the sector’s


brightest and best.
Our opening keynote was delivered by Bader Alsubaey, the Director of Industrial Security Operations at Saudi Aramco. Alsubaey explored smart cities and giga projects through the lens of high-tech security and the people working within Aramco. His address was a great springboard to start discussions for the day and served as food for thought for anyone involved with smart city planning and beyond.
Later in the day we heard from Nadeem Iqbal, Meshari Al Suwanea and Nojoud Al Subaie who shared with our delegates information about the training academy that is a key part of the National Security Services Company (SAFE)’s foundation. SAFE places a huge amount of emphasis on learning from all sources as well as working to its employees’ strengths. Iqbal confirmed the value of events such as this conference by sharing that while 10 per cent of learning happens in lectures, and a further 20 per cent of learning comes from social platforms – it is conferences,




seminars and workshops that contribute a massive 70 per cent to all learning.
Our final keynote was delivered by Mohsan Tanvir, Senior Enterprise Executive at Magnet Forensics. He delved into the use of digital forensics and how they can be leveraged to help professionals better understand incidents. After discussing how regular forensics work for incidents, he then went on to compare this to the use of digital forensics. And while we may not have the same breadth of knowledge and experience as Tanvir, he did point out that we are all involved with digital forensics in ways we may not even realise: after all, we all go home to WiFi and computers and other digital devices.
The Security Middle East Conference wasn’t just about lectures and presentations; it was also about building connections that extend far beyond the confines of the venue. The conference provided numerous opportunities for attendees to network with peers,



industry leaders and potential partners. Dedicated networking events, breakout sessions, and casual gatherings fostered a collaborative atmosphere where attendees could exchange ideas, share challenges and explore potential avenues for collaboration.
Imagine yourself mingling with security professionals from across the Middle East, exchanging contact details, and forging valuable connections that could propel your career or business forward. This is the kind of environment that the Security Middle East Conference 2024 cultivated.
In addition, we were delighted to have Icon Training Company and Luke Bencie provide a workshop to some of our delegates focused on Cognizant Security Strategy for Vision 2030. This was about encouraging our delegates to think differently – as Bencie said: “We always say, think outside the box. Well, I’m here to say, there is no box.” Attendees gained excellent insights into strategies they can implement in their roles and a look into the innovations that can make an impact.



By participating in Security Middle East Conference 2024, attendees walked away with a wealth of knowledge and practical takeaways. This was more than just a conference – it was a time investment in their professional development and the future of security in the region.
They gained insights into the latest security trends, discovered innovative technologies and learned best practices from industry experts. Attendees also built valuable connections with security professionals from across the region, opening doors to potential collaborations and partnerships. They also left with a renewed sense of purpose, equipped with new ideas and strategies to take back to the office with them.
Exposure to cutting-edge security strategies: Through the diverse range of panel discussions, attendees gained valuable insights into the latest security trends, technologies and best practice.
Enhanced networking opportunities:
The conference provided a platform to connect with a wide-range of security leaders and professionals, fostering new collaborations and partnerships. Direct access to industry leaders: Attendees gained the unique opportunity to engage with renowned security experts, pose questions and gain firsthand knowledge from the top minds in the field. A platform for knowledge sharing: The interactive nature of the panel sessions and insightful keynotes allowed delegates to actively participate in discussions, share their own experiences and contribute to the collective knowledge base of the regional security community.
Perhaps most importantly, Security Middle East Conference 2024 served as a source of inspiration. The conference showcased the dedication, innovation and collaborative spirit that define the security industry in the Middle East. It left attendees feeling empowered to tackle the challenges of tomorrow and contribute to a safer, more secure region.



The resounding success of this year’s conference leaves only one question: why miss out on Security Middle East Conference 2025? We’re delighted to announce we’ll be back next year, bigger and better, raising the bar even higher to deliver an enriching and engaging experience. So if you’re a security professional in the Middle East, looking to elevate your career, here’s why you should mark your calendar for next year’s event.

Unparalleled learning: Stay ahead of the curve by gaining insights into the latest security trends and technologies, ensuring you’re equipped to tackle emerging challenges.
Expert insights: Learn from industry leaders and security professionals who are shaping the future of security in the Middle East.
Networking opportunities: Forge valuable connections with peers and potential partners from across the region.
Collaboration: Be part of a vibrant community dedicated to creating a safer








and more secure Middle East. Plus: We’ll be bringing a new feel and format to the 2025 event to make sure we can address the needs of all of our audience, and deliver a more personalised experience.
Security Middle East Conference 2025 promises to be an even more enriching experience. Don’t miss out on this opportunity to elevate your knowledge, network with industry leaders, and be part of the conversation that’s shaping the future of security in the Middle East.





Secure your checkpoint with our industry-leading X-ray inspection, optical inspection, and radiation detection technologies that help to uncover threats and identify and authenticate vehicles and occupants. Further enhance inspection capabilities and operational efficiencies with our analyst assist tools and data integration platform that automates manual processes, controls workflows, and delivers actionable intelligence. With our comprehensive checkpoint security solutions, we can help you maximize threat detection and operational success. rapiscan-ase.com







Find out more about the second Security Middle East Conference which took place in May this year, from our chairperson for the event, Daniel Norman, Regional Director, EMEA, of the ISF
The second Security Middle East Conference did not disappoint… I had the honour of shaping the event, alongside the planning committee and Board to design an event that covered a variety of topics: from addressing the talent gap in the Middle East, to smart city security, to resilience in the age of digitalisation, to increasing the number of women in the security industry. The event provided attendees with direct access to Middle Eastern security titans; their insights and perspectives on current and emerging security challenges were enriching for everyone involved. As chairperson for the conference, I was provided with a unique opportunity to network and learn from senior leaders, and became immersed in all of the discussions directly. Here are my reflections on what we heard and the key messages to takeaway.
The focus on security, both physical and digital, has emerged as a critical proponent to ensuring the successful implementation of all elements of Vision 2030. In order to keep pace with the tremendous investment in GIGA projects, critical infrastructure, manufacturing, retail and especially tourism, the region must continue to prioritise security and safety, of both people and technology. What became clear was the Saudi government has a clear roadmap to significantly increase the number of tourists in the region to over 100 million in 2030, which would outperform the major tourist locations around the world, from London, to Paris to even Disney World… There is billions of dollars of investment in hotels, entertainment facilities, accommodation, sanitation, public transportation, etc.
This focus on the entertainment and tourism industry shifts attention to ensuring safety at all times, whether that is with effective crowd management, safe hotel zones, secure and seamless travel, data protection for international clientele and usability of technology.
The talent gap remains to be an area of focus, as it was in 2023. Many jobs continue to go unfulfilled, such as security guards, cyber security, data protection, policing and government. Building a platform for security practitioners to improve their knowledge and skills in a professional manner will add tremendous value for the individual and the collective. Having a clear roadmap and escalation pathway between roles and departments will provide security practitioners with the inspiration they



need to take ownership of their careers and livelihood. Events like the Security Middle East Conference, and the development of regional Chapters, such as the ISF Middle Eastern Chapter, provide security leaders from all parts of the security arena with access to world-class training, networking opportunities and a mechanism to share best practices. There is still work to be done in this space, but the focus is crystal clear.
As Saudi Arabia digitises and expands its technological footprint, the focus on managing cybersecurity and minimising cyber risk has significantly increased. The geopolitical environment in the Middle East is on a knife-edge. Threat actors are seemingly constantly trying to disrupt critical infrastructure, steal intellectual property and distort the perspectives of citizens and create further turbulence in the region. The cybersecurity focus is not just simply on digital assets and IP, but on operational technologies, undersea cables, physical infrastructure and beyond. It is clear that investment in cybersecurity tooling and frameworks is crucial for effectively staying ahead of

these threat actors. The focus and desire from many practitioners was to share best practices and intelligence amongst trusted partners in the region – having access to other likeminded individuals and institutions can empower organisations to overcome a variety of security challenges, such as cyber risk management, compliance, governance, navigating future technologies like AI, and so on.
In this year’s edition of the conference, it was imperative to provide the women in our Middle Eastern security community with a platform to demonstrate their value


and highlight the incredible contributions women have been making. It is clear that the typically male-dominated security industry has lacked female voices and representation historically – however, it was clear the value women have brought over the last few years, both in physical security and cyber: from providing unique and fresh perspectives to managing security crises, to talking down and calming physical situations that could have escalated further if met with male aggression, to providing nurturing leadership styles to the workplace. Training opportunities have been opened to women across police, government, cybersecurity and beyond, and in many cases in leadership roles. There is clearly still work to be done to balance the male/female percentages in terms of professionals across all security domains, but the progression has been admirable.
The 2024 event was bigger and better in so many ways than 2023 – passionate speakers exploring a spectrum of security topics, and attended by a variety of progressive security leaders. The conference has set the bar incredibly high for 2025 and I am very much looking forward to being involved once again.















The advent of cloud technology has facilitated faster, easier physical security deployments, according to Firas Jadalla, Regional Director META at Genetec
Recent research conducted by Genetec shows that 44 per cent of end users reported that more than 25 per cent of their physical security setups are now either in the cloud or use a combination of cloud and on-premises solutions. Organisations of all sizes have come to expect a hosted option as an alternative or addition to their on-prem physical security infrastructure. For systems integrators, this signals a new era of opportunity and adaptation.
The best of all worlds
As businesses rationalise their costs, concerns and approach to migrating to the cloud, hybrid-cloud deployments are gaining traction across the physical security industry. Preliminary data from Novaira Insight’s latest annual report on the market for video surveillance hardware and software shows the rapid pace of this transition to the cloud. It estimates that the market for cloud video management software will have grown by almost 50 per cent in the world, excluding China, in 2023.
According to Josh Woodhouse,Lead Analyst at Novaira Insights: “Most of these deployments use a hybrid architecture combining a primary tier of local storage with cloud-based video management and system administration.” Hybrid-cloud deployments enable organisations to keep their existing infrastructure and systems and deploy cloud applications in sites or applications where it makes sense. This allows them to transition to the cloud gradually, at their own pace, without having to rip and replace everything.
Technology should serve as a tool to achieve objectives rather than dictate strategies. Businesses ought to retain full autonomy in deploying their systems across different locations. Rather than being constrained by the limitations of a singular technological approach, deployments should be in line with business goals. With an open ecosystem that allows them to implement solutions based on their needs rather than location (either on-prem or in the cloud), organisations can unify, upgrade, scale and deploy systems faster, streamline processes, and strengthen their cybersecurity in new ways.
For example, businesses with numerous locations need to consider each site’s unique requirements. They might run all their physical security systems on local servers and networks at their headquarters locations. Yet, they might choose a full-cloud deployment for smaller remote sites, while another location might require cloud connectivity with additional storage on site. With a flexible hybrid-cloud deployment, there are always options. No matter how many systems are running on local servers or connected to the cloud, organisations should be able to bring them all back to a central head end and enjoy a seamless experience with all systems accessed from one platform.
As the purchase process and technical integration of on-prem, cloud and hybridcloud systems come together, security systems integrators need to consider a new approach. Reconfiguring their business models to support subscription services may initially seem daunting, but the benefits can be substantial.
Offering long-term contracts for hosted services provides integrators with a stable and predictable monthly recurring revenue that helps complement income from project sales. Costs associated with customer
monitoring, system integrations to expand your customers’ ecosystem and more.
Having a solid stable of clients delivering recurring monthly revenue can also increase the valuation of your business. Whether you’re looking for growth financing, planning for the future sale of your business, or looking to reinforce your financial footing, there’s no question that building a new stream of predictable, repeatable and reliable income offers financial value.
While selling and deploying security systems is essential, the real future opportunities lie in helping to enhance customer operations. Systems integrators can become trusted advisors, offering insights into productivity gains and operational efficiencies. By focusing on customer needs and tailoring services, integrators elevate their role from service providers to strategic partners.
No matter how savvy the user, it’s the systems integrators and their trusted software partners who do this work, day in and day out, who have the knowledge and expertise that comes from having built systems that protect hundreds of thousands of customers daily.
Hosted systems can help reshape your customer relationships from transactional or commoditised to monetising your expertise beyond your ability to repair cameras, wire doors, or update software to increase customer engagement. It’s the kind of value that isn’t so easily replaceable, and that sets you apart from competitors, creating differentiation so
‘‘Most of these deployments use a hybrid architecture combining a primary tier of local storage with cloudbased video management and system administration.’’
acquisition and setup are reduced while building ongoing revenue streams. This can give you the freedom to expand your service offering and capture new opportunities by selling new value-added services that go beyond the traditional ways of selling on-prem systems. Visibility into user adoption can allow you to sell more and help users close the consumption gap. Customers remain satisfied and loyal over the long-term, helping you further expand their use of the solution. But you can also cross- or up-sell services such as user training and enablement, system health
that you don’t only have to compete on price. With a hosted solution that’s easy and fast to deploy and managed and maintained by the provider, you can reduce overhead costs, staff training and truck rolls via remote customer support. As a result, you can allocate more time to new business possibilities, including new projects, services, consultation and customer engagement. These benefits also allow you to spend time developing greater expertise in your customers’ processes. Using this newfound knowledge, you can tailor your services
towards potential productivity gains for your customers and turn them into additional sales. This way, you make sure your customers get the most out of the technology that is available and that they have already purchased.
In a cloud-based system, fixes and upgrades are pushed continuously by the software provider as soon as they are ready for release. You can control the update and upgrade schedule that best suits your customer to ensure a seamless and unintrusive experience. Deployment time can be much more flexible, and there is no need to go from machine to machine to update each server or device individually. It’s a more fluid and nimble approach that also enables rapid break/fix response and facilitates system resiliency.
What’s more, it’s easier to practice good cyber hygiene on hosted systems. System hardening, cybersecurity configuration and data management are critical but time-consuming, and keeping on top of the latest threats is a job in itself. With hosted solutions, the manufacturer helps alleviate some of this burden.
In a growing number of companies, the responsibility for purchasing security systems no longer rests solely on a security or facilities team. Increasingly, stakeholders from IT and senior management are involved in making the purchase decision. Usually, they come to the table already familiar with the mechanics of SaaS. Systems integrators who don’t adjust to respond to this demand risk being left behind.
Luckily, you don’t need to do this alone. A reliable and supportive SaaS manufacturer partner can help you
‘Increasingly, stakeholders from IT and senior management are involved in making the purchase decision.’
evaluate whether a fully hosted or hybrid model is the best solution for a particular customer. This means choosing a software partner that offers unified, open-architecture and scalable solutions. Your ideal partner will also allow you to choose the cloud deployment that works
best for your clients. It will give you the option of selecting either a true cloud system, with no servers on-premises, or a hybrid model that helps you move clients to the cloud at their own pace.
It is also critical to ensure your SaaS partner has a proven track record of building cyber-resilient solutions with multiple lines of defence. This demonstrates: a commitment to proactive risk identification and mitigation; promotes transparent communications; and works exclusively with a network of trusted partners.
As the physical security industry undergoes this profound shift, systems integrators must adapt to thrive in this new landscape. By embracing cloud and hybrid solutions, integrators can unlock new revenue streams, enhance customer relationships and stay ahead of technological advancements. With the right partnerships and a forward-thinking mindset, systems integrators can navigate this transformation and take advantage of new opportunities being presented by evolving technology. genetec.com

Securing your organization requires more than video surveillance. To be successful, you need access control, intercom, analytics, and other systems too. This is why our Security Center platform excels. It delivers a cohesive operating picture through modules that were built as one system. So, whether you’re securing an airport, a parking structure, a multi-site enterprise, public transit, or an entire city, you can access all the information you need in one place.

Nazy Fouladirad, President and COO of Tevora, shares the strategies you need to ensure your disaster recovery plan is effective
As more organisations rely on digitising their operations to help them scale, there is more pressure placed on their ability to keep their systems from suffering from too much downtime. However, unexpected events like natural disasters or cybersecurity breaches can be a potential source of disruption for businesses when they least expect them.
In order to minimise the extent of disruption these situations can cause, having a well-designed disaster recovery plan is essential. Disaster recovery plans are an important documented approach to rapidly responding to major operational disruptions. However, to keep these recovery plans effective, there are some important steps you should take.
As a rule of thumb, disaster recovery plans should never be considered a static set of procedures. It’s important to regularly review and update plan components as the organisation scales and evolves.
Organisations should thoroughly examine the steps used to restore their systems during an outage, as well as keep all the contact information of primary stakeholders in the plans up-to-date.
While regularly reviewing recovery plans is vital, it’s also important to test the plan whenever possible. This can include conducting tabletop exercises with red and blue teams as well as working with outside penetration testing services to
test the capabilities of various security controls as well as how the business can respond to them.
While you can take the time necessary to make sure your disaster recovery plan is as up-to-date as it can be, unless you test the strategy, you’ll never know if it’s capable of supporting the organisation when it’s needed most. Creating a testing strategy helps validate the effectiveness of your disaster recovery plan and gives the business confidence that it can be relied on in the future.
To create a reliable testing strategy, the first step is to define all of the testing objectives. Once clear objectives are set, you can then implement the right testing procedures and frequency needed as well as having the ability to provision enough resources to make the testing scenarios a success.
There is no one-size-fits-all approach to creating a successful disaster recovery plan testing scenario. There are a variety of different formal and informal testing procedures that organisations can plan for — all of which help to verify the impact and effectiveness of various planning initiatives.
Many organisations benefit from incorporating functional testing procedures when testing their plans. This involves
testing specific components of a drafted plan like data backup and restoration procedures or noting the time it takes to complete certain tasks. These functional tests can be helpful when trying to verify compliance capabilities in regulated industries that need to maintain certifications like HITRUST or PCI DSS.
When an organisation experiences a major disaster, effective communication can make all the difference when executing a disaster recovery plan. All disaster recovery plans must have clear and consistent communication protocols assigned to them. This includes making sure that all relevant parties that have a role in disaster recovery understand the frequency of plan testing and their responsibilities during the process.
The first thing to do is to establish a detailed testing schedule that can be distributed to internal and external stakeholders. The schedule that’s been
decided on should have a clear outline of any dates or times for each of the testing cycles as well as any systems or processes that will be affected. It’s also important that all stakeholders are notified well in advance of the test that’s taking place to give them enough time to prepare.
in either the planning or execution phase of the test, everyone involved should be notified so they understand any specific actions they should take.
During the test, all necessary participants should have communication channels established in a unified
‘‘The purpose of disaster recovery plan testing is to be able to analyse and improve based on the results.’’
Disaster recovery plan testing can require considerable resources to manage effectively. Careful planning and coordination are essential to getting the most out of the process. Businesses should clearly define the scope of the test and the departments responsible for conducting it.
Before executing the test, there should be a final review of all of the testing procedures that will take place and any necessary scripts that should be used. If there are any potential issues that arise,
environment where all parties can share and receive important updates during the process and coordinate any necessary responses to key issues developing.
The whole purpose of disaster recovery plan testing is to be able to analyse and improve based on the results. After each test is completed, it’s important to take the time to thoroughly analyse any data that was collected – including review logs, reports, or important feedback –
to help you create some actionable improvement initiatives.
Businesses should identify different areas where the organisation performed well during the test as well as areas that may cause bottlenecks during the recovery process. Based on the data the analysis gives, organisations have the vital information needed to keep their disaster recovery plan effective long-term.
Maintaining a disaster recovery plan for your business is the smart thing to do. However, unless you regularly test the effectiveness of your plans, it’s hard to know if you’ll be able to depend on them when you need them most.
By following the guidelines discussed, you’ll ensure that your business is ready for the unexpected and can minimise downtime while successfully bouncing back during a major operational incident. tevora.com



Mobile access powers and secures a sustainable future of work in the hyper-digital GCC, says Sam Cherif, Senior Director, Regional Business Head, MEA at HID
It’s no secret that citizens in the GCC have been increasingly embracing mobile technology: according to Statista, in 2023, smartphone penetration rates in the region exceeded 96%. And with governments in the United Arab Emirates and Saudi Arabia prioritising digital expenditure on technology such as 5G, mobile will be truly ubiquitous.
This surge in mobile phone usage, coupled with the growing adoption of hybrid work models, has ignited a pressing need for digital solutions, particularly in the smart building sector. At an industry summit in Dubai in January 2024, it emerged that the global smart buildings market was worth around US$96 billion in 2023 and could rise to as much as US$408 billion by 2030. Additionally, given the relatively high
contribution of the construction and real estate sectors to carbon emissions (40%), some US$4.8 trillion could be saved around the world over a three-year period.
For the security industry, the changing requirements of access control systems have been more dramatic than ever before. Digitisation has brought convenience and security closer, but hybrid work models have also added prominence to building efficiencies and contactless solutions.
There are many security complexities in the hybrid work model and organisations are now challenged with bringing disparate identity sources and access management systems together so they can centrally manage physical and digital access efficiently and easily.
And that’s where mobile access shines.
Because of their convenience, advanced security and flexibility, mobile access control systems represent the confluence of all these drivers, with the added benefits of enhanced touchless experiences and broader read ranges. In addition, the ability to provide and revoke credentials over the air further limits physical contact and improves access control administration with a digital, cloud-based platform.
The use cases for mobile access are vast and exciting, going beyond simply opening doors to include providing contactless, seamless access to a wide range of devices and services such as time-and-attendance terminals, cashless vending machines, printers, computers, workstations and other applications.
In fact, according to the 2024 State of Security and Identity Survey, published annually by HID, two-thirds of the 2,600 surveyed organisations (64%) reported some level of mobile ID deployment, with that number expected to increase
while achieving cost savings. As a result, consultants and integrators are moving away from proprietary models and embracing open standards-based technology where software upgrades can be securely managed through the cloud.
‘Industry partners are optimistic in their outlook, stating that 94% of their customers will have deployed mobile IDs’
to 79% within the next five years.
Industry partners are optimistic in their outlook, stating that 94% of their customers will have deployed mobile IDs. Among all survey respondents, 59% say it’s more convenient for users, 45% laud its added security and 35% say it’s more convenient for administrators. So, building on the momentum of a mobile-first population and a growing hybrid work environment, the GCC has a significant opportunity to capitalise on the advantages of mobile access control systems, particularly those that leverage mobile ID technology. These include:
1. Robust security: Mobile access eliminates reliance on physical cards or badges, supports multiple security protocols and includes additional layers of security on top of the card encryption, making it more secure than traditional plastic credentials.
2. Convenience: Users can access buildings using their mobile devices, such as smartphones and wearables, eliminating the need for traditional key fobs and badges. Tenants can easily manage and update credentials securely through the cloud. Integration with digital wallet apps improves the user experience.
3. Threat prevention: Real-time access to data allows organisations to quickly detect and mitigate threats, such as the ability to instantly revoke credentials, allowing for sustained growth and continuous improvement of their security systems.
4. Mobile access and touchless capabilities: It’s no surprise then, that demand for mobile access is growing. While security system administrators benefit from increased operational efficiency, employees and visitors may find mobile access more convenient and secure since they are more likely to have their mobile devices at hand than their access cards.
5. System interoperability: Future-proof support is also a growing concern as users are pushing for long-term convenience
6. Improved efficiency and scalability:
Remote management and updating of credentials are possible through cloud platforms. For example, the HID Origo cloud platform’s modular, multilayered secure infrastructure is validated by industry-leading certifications and fully committed to via HID’s service level agreements and support. Using Origo’s cloud-connected access control devices, applications, and trusted mobile identities, organisations can enhance security, improve workplace efficiency, and scale their access control infrastructure.
7. Sustainability: Organisations across all regions are making a clear effort to understand how new purchases and upgrades in access control technology can have an impact on sustainable practices, with 74% of end users saying they’ve seen the importance of sustainability increasing over the past year, and 80% of partners reporting
the trend growing in importance among their customers.
Access control readers that have Environmental Product Declarations and intelligent power management, for example, support green building ratings such as LEED. Additionally, deploying mobile access and virtual credentials removes the need for plastic cards, sparing the carbon footprint associated with their lifecycle. Integration with a building management platform allows for continuous adjustment of building resources based on occupancy. And as consumers urge businesses to demonstrate their sustainability footprint with information like energy use, waste reduction and resource optimisation, organisations can clearly benefit from mobile access. Wireless readers and controllers, for instance, can significantly reduce the amount of cable infrastructure required in a building, while upgrading to mobile or biometric credentials reduces single-use plastics and printing since access is done via a mobile device and the data is securely stored in the cloud.
The value of mobile access is unquestionable — and any size organisation from any sector can benefit from the digital transformation angles when it comes to security and convenience. hidglobal.com


With practical and innovative solutions that adapt to fit any current and future needs, March Networks® IP video surveillance and data analytics help organizations of every size enhance their security — and their competitive advantage.
Our comprehensive Cloud Suite of intelligent video solutions delivers operational efficiencies, business intelligence, streamlined sharing and enhanced customer service capabilities.
Protect your business with a solution that gives you real-time visibility into your stores and branches without the hassle of maintaining your own surveillance network. We help retailers and banks cut losses from theft, oversee operations, improve service, and drive profitability with video-based business intelligence.

One of Türkiye’s leading banks, Garanti BBVA is transitioning to an all-digital video surveillance platform including over 22,000 IP cameras and 5,000 Network Video Recorders, all managed seamlessly and centrally using March Networks enterprise-grade video management software. It provides advanced system-wide monitoring for real-time visibility, and offsite backup storage.
eXtra, the largest electronic retail and home appliance store in Saudi Arabia, opted for March Networks due to its high security standards and reliable products. They are implementing March Networks' NVRs and cameras, aiming for easy deployment and management using Command Enterprise for centralized control and health reporting. Once their initial stores are deployed with March Networks systems, eXtra plans to explore March Networks Searchlight for Retail, for business intelligence and operational advantages.
Qatari Banking
March Networks have dominated the Qatari Bank sector since 2011, powering 3 of the top 4 banks, including the largest bank in Qatar which is also regarded as the largest, by asset, in the Middle East. Over and above our end-to-end video solutions, the banks also use our Searchlight for Banking solution to flag suspicious ATM transactions and to speed up investigations.
The island-inspired clothing and home furnishing retailer selected March Networks’ comprehensive retail solution to gain faster, more robust loss prevention capabilities, improve recovery and apprehension rates with higher-quality video evidence, and better safeguard customers and employees at its stores worldwide. It has reduced investigation times by over 90 percent.
See why March Networks is trusted by over 1000 financial institutions and over 300 retailers worldwide.

Carl Fenger, LEGIC Identsystems, discusses letting your smartphone represent you in the physical world
People use mobile credentials on almost a daily basis. When opening your office door using your smartphone or entering a metro station using an e-Ticket, you are presenting information via NFC or Bluetooth that is relevant to you that is stored on your mobile device to gain access to areas and services that you are authorised to use. The infrastructure grants you rights based on mobile credentials stored on your phone.
Mobile credentials enable mobile devices to become a form of Digital Twin that can store and selectively share data such as your identity, authorisations, preferences, credit card numbers, clothing size, shopping and location etc. with infrastructure such as doors, public transportation, vehicles, shops, vending machines, parking garages, hotels, even your own living room. Mobile credentials are typically encrypted, and can be as
simple (such as an anonymised token) or content rich as an application requires. When combined with meta-data such as your location, preferences, time, weather, vicinity of friends and family, or your personal calendar, apps or digital wallets that share mobile credentials with infrastructure make a great leap towards making your surrounding world more friendly, informative, customised and convenient.
Three technologies are converging to enable a variety of service possibilities that will soon be commonplace. By leveraging mobile credentials with Ultra-Wideband (UWB) indoor positioning (a short-range radio technology that determines your precise location even inside buildings) and Bluetooth advertising (the ability for any device within Bluetooth range to broadcast

their availability, even while ‘asleep’), the connection between who you are, where you are, and what’s available around you is made. This can be illustrated in a variety of use cases.
Guiding people as well as machines to their destination indoors as well as outside is the next evolutionary step for access control. Add in the demand for touchless


entry due to covid, the scenario made famous by Star Trek is finally becoming reality: doors that recognise your intent and automatically open when authorised persons approach.
As UWB real-time locating systems (RTLS) can determine where you are (in front of a door and not behind it) and in what direction you are moving and how fast, smart doors can intelligently open and close as you freely walk through an office building, airport, or campus.
Your mobile credentials make sure that only the right doors open, and each door’s Bluetooth advertising informs your app of its identity and presence.
With shared vehicles and mobility services, registering in-person and entering credit card details is bypassed with mobile credentials. By simply approaching it (guided by indoor navigation), your desired vehicle activates via Bluetooth wake-up, unlocks and even adjusts to your personal preferences such as seat position, climate control, destinations, preferred restaurants and points of interest. Credentials can be wirelessly shared with parking facilities and fuelling/charging stations to provide a seamless driving experience where you never pull-out keys or your wallet.
In IIoT deployments such as logistics supply chains, millions of interactions take place per day between vehicles, infrastructure, containers and the like, and employees, contractors and partners. Ensuring that only authorised persons are interacting with industrial assets, and at the right time and place, requires automated recognition of a person’s (or robot’s) mobile credentials. Only then can interactions be allowed to take place including logging of when and where it occurred.
Unmanned stores meet consumer demand for fast check-out, while reducing costs for retailers. This shopping trend leverages mobile credentials, a smartphone equivalent to the customer loyalty card, with digital wallets.
‘Just walk out’ stores such as Amazon Go implement AI with computer vision, sensors and RFID to detect items taken from the shelf. As there is no staff, UWB navigation can further enhance the experience with indoor navigation to guide consumers to desired products, and Bluetooth wake-up can advertise specials or new products as shoppers come within range as they walk around.
To enable these scenarios, an end-to-end platform is needed that facilitates creating, storing, updating, distributing and protecting mobile credentials as they are distributed over the internet, or broadcast via NFC or Bluetooth.
LEGIC Connect is a mobile credentialling platform that securely distributes credentials to registered mobile devices anytime, anywhere, instantly, automatically or at the touch of a button. The system provides a globally available, secure, end-to-end credentialling service that is the backbone of establishing trust and accountability in user/infrastructure interactions. The platform gives service providers the ability to manage user credentials and permissions, plus send and receive data securely to smartphones and infrastructure devices. The system is compatible with UWB positioning systems and supports discovery of devices equipped with Bluetooth advertising.
LEGIC Connect supports Android and iOS devices, and a mobile SDK is provided for easy development of mobile apps or wallet-based service based on mobile credentialling.
For details about LEGIC Connect, see: legic.com/connect
Venue:

Venue:





Time: 11am to 8pm






















Luke
Wilkinson, Managing
Director
at Mobile Tornado, explores how push-to-talk over cellular is tackling challenges and improving operational efficiencies for the public safety and security sectors
Effective and secure communication is the backbone of services provided by public safety and security sectors. While the stereotypical ‘Roger, Roger’ may be a familiar phrase, the reality is that we all rely heavily on the expertise and swift actions of security personnel and first
responders to ensure our safety in both routine and spontaneous situations. But who safeguards the well-being of these essential workers? The answer is their dispatch controllers, whose ability to communicate in real-time is a vital component in protecting those on the
frontlines. Effective real-time communication enables dispatch controllers to coordinate efforts, disseminate crucial information, and make informed decisions.
Unfortunately, three key issues still affect workforces in public safety and
security sectors, limiting their own safety. They are: poor communication quality and timeliness; dispersed and separated teams; and cybersecurity vulnerabilities. To combat these issues, public safety and security organisations need secure and dependable real-time communication solutions. Push-to-talk over cellular (PTToC) has emerged as a popular real-time communication method, surpassing two-way radios, as it offers improved voice quality, range and advanced features such as live video, GPS tracking and data encryption. But how exactly is PTToC helping the public safety and security sectors tackle their current challenges and improving operational efficiency?
Overcoming poor communication quality and timeliness
The public safety and security sectors have long relied on effective real-time communication to coordinate responses and ensure the safety of both personnel and the public. The need for instantaneous communication in these time-sensitive industries has contributed to the rise of PTToC technology. It’s no surprise then
that Polaris Market Research forecasts the global market to hit US$61.28bn by 2030.
This market boom can be attributed to the significant advantages PTToC offers over traditional radio systems, including broader coverage, higher reliability and seamless network switching without dropped calls. In particular, rail companies, security providers, airport operators and emergency medical services are embracing the enhanced capabilities and superior
For example, footage from an officer’s body camera can provide invaluable visual context, allowing a workforce to make more informed decisions and coordinate an effective response plan. With live video, responders can get a head start on assessing the situation before arriving – identifying immediate threats, the number of people needing assistance and the best route to take.
Personnel in the public safety and security sectors often operate with limited cellular coverage – from remote construction sites to overcrowded events. In such situations, PTToC’s ability to leverage different cellular network generations, from 2G to 5G, ensures remote workers can stay connected and access critical information in real-time, without relying on traditional radio systems with unstable coverage and poor audio quality.
Not only are security and public safety workforces often dispersed, but the number of lone workers is continuing to rise in these sectors. In fact, the Lone Worker Safety Expo found that the number of lone workers in the UK has increased by 25% over the past five years, leaving these professionals more vulnerable to potential threats or accidents and the picture is likely to be similar globally. Ensuring the safety of lone, remote workers has encouraged many organisations in critical sectors to utilise the dispatch console included in most PTToC platforms. The dispatch console serves as a command-and-control centre for management of workers in the field. It allows the dispatcher to track and speak to workers, coordinating support if needed.
To combat risks associated with lone working, many PTToC platforms offer recording features and one-touch SOS
‘‘In critical situations, push-to-video at the scene of an incident allows command centres to get a clear, real-time understanding of what is unfolding.’’
user experience offered by PTToC solutions, surpassing the limitations of traditional radio systems.
A standout feature of PTToC is its ability to integrate with other digital communication tools, including video. In critical situations, push-to-video at the scene of an incident allows command centres to get a clear, real-time understanding of what is unfolding.
alerts. Lone workers can instantly send an SOS alert or recording to their team, providing location and context for an immediate response. Workforce management solutions often include checking features, requiring workers to respond to regular alerts, allowing quick support dispatch if needed. PTToC ensures remote workers feel secure and supported, knowing help is just a click away.
Harness the power of automation to unlock lab capacity, empower your experts, and finish digital investigations faster.

Ready to see Magnet Automate in action? Get a free trial. Scan to learn more.

As reliance on digital communication technologies increases for first responders and lone workers, the threat of cyber-attacks has grown significantly.
The Zayo report revealed a substantial number of DDoS attacks targeting telecoms in 2023, with nearly 13,000 attacks in the second half of 2023: 40% of the attack volume.
With sensitive information transmitted over wireless and cellular networks, hackers actively seek vulnerabilities to exploit security systems. The rollout of 5G technology, while offering enhanced capabilities, also increases the attack surface for cyber threats.
To combat these risks, public safety and security sectors are fortifying their communication systems. PTToC solutions incorporate encryption protocols and can be deployed through a SaaS model, enabling seamless security updates and real-time threat protection. This proactive approach helps organisations stay ahead of cyber threats.
‘‘Traditional two-way radios are no longer sufficient to address current communication challenges of poor audio quality, dispersed workforces, and cybersecurity vulnerabilities.’’
Additionally, PTToC platforms often include Mobile Device Management (MDM) capabilities, granting dispatch controllers comprehensive control over device features, settings, applications and user permissions. Devices can be configured for single application mode (PTToC only) or multi-application mode with whitelisted third-party apps, ensuring absolute security and proper usage.
As the public safety and security sectors face increasingly complex challenges, advanced communication and collaboration tools are becoming more crucial. Traditional two-way radios are no longer sufficient to address current communication challenges of poor audio quality, dispersed workforces, and cybersecurity vulnerabilities. PTToC
provides these critical sectors with the capabilities and tools they need, including real-time video communication for enhanced situational awareness, lone worker safety features for remote personnel, and robust security measures against cyber threats.
Looking ahead, the future of public safety and security will be defined by the continued adoption and seamless integration of transformative technologies like PTToC. As these solutions become more widespread, they will drive improvements in real-time communications, operational agility, and ultimately, the ability to protect lives and safeguard communities more effectively.
mobiletornado.com

It’s time to create a unified landscape in the banking and finance world that is adaptable to myriad risks, says Matt Tengwall, SVP and Global GM, Verint
There is a significant need to change siloed security operations within banks. Financial services providers must adopt layered security measures to protect against modern threats. Leveraging the power of video surveillance, AI and cloud technology, along with integrating physical and cybersecurity, has never been more urgent.
Banks face numerous challenges, from safeguarding data and assets to ensuring business continuity. An integrated security approach streamlines risk management and supports real-time risk detection and an agile security infrastructure. By combining new technologies, processes and strategies, financial institutions can better protect themselves and their customers in an increasingly complex landscape.
Cloud technology is becoming more critical in this modern world, offering scalable, cost-effective and secure video surveillance and data-sharing services. While adopting the cloud in the banking market is still in its infancy, it provides significant advantages. Banks can adjust video security resources based on demand, scale operations easily, and ensure sensitive footage is protected and accessible to authorised personnel only. This approach improves incident response times and helps banks comply with regulatory requirements.
The ongoing digital transformation of banks supports the seamless integration
of video surveillance technologies and security measures. Networked video can be integrated with access controls and AI software, allowing banks to manage security solutions centrally. As the market evolves, a well-planned and integrated approach to security is necessary and a strategic imperative for safeguarding assets, data and reputation in an era of a changing world.
The emergence of AI is also playing a massive part in the financial services industry. The banking sector can use AI-driven tools to transform its physical security and combat cyber threats. AI solutions offer strong capabilities to keep banks one step ahead, including real-time video monitoring, predictive threat analysis and advanced fraud detection. These technologies are key for combating the growing risk landscape and fraud schemes targeting banks.
Additionally, AI can rapidly filter through vast amounts of data to detect unusual patterns that can point to a security risk. This enables fast responses to possible security incidents, reducing the likelihood of significant harm. AI improves security systems by predicting and correcting issues before they become serious. AI, for example, can identify anomalies in transactions that can indicate fraudulent activity, enabling organisations to take swift and immediate action and prevent further losses.
Financial organisations must manage a constantly evolving risk environment that includes physical and cyber threats. Traditional threats, such as robbery and card skimming, remain prevalent, as do newer ones, such as identity theft and data breaches. This evolving landscape emphasises the need for comprehensive security solutions.
The convergence of digital and physical security measures is essential in dealing with these potential threats. As banks expand into new territories and integrate operations, the risk of security breaches rises. A proactive approach combining IT and traditional security activities is needed to mitigate these dangers. This involves protecting the branch network and ensuring that all technological infrastructure is secure and up-to-date.
infrastructure capable of identifying and responding to threats in real-time. This comprehensive strategy increases security and operational efficiency by decreasing manual monitoring and intervention.
A well-integrated security programme safeguards a bank’s assets while increasing client trust.
‘This allowed the newly developed system to only generate an alarm when internally generated vehicle’
Working together is critical for ensuring financial stability. The industry must establish robust connections with regulatory authorities, law enforcement agencies and cybersecurity professionals. Banks can tackle intricate security concerns by engaging in concerted efforts and keeping lines of communication open. Together, they can identify gaps and increase the sector’s response capabilities by carrying out simulated attack drills and working together on threat assessments.
Financial institutions always work to improve their technological capabilities to remain ahead of the constantly changing risk environment and handle problems such as data breaches, identity theft and ATM skimming. Strong security measures must be in place at banks to successfully detect and address a variety of threats.
It’s important to remember that these security systems must receive regular updates and upgrades to remain effective. For equipment like networked video recorders and surveillance cameras to remain secure, firmware updates are essential. Modern features like ATM loitering detection and facial recognition depend on current firmware to function at their best and provide insightful data. Comprehensive protection is also further achieved by merging multiple security technologies into a single system. For example, combining video surveillance, access control systems and AI-driven analytics can result in a strong
In an era of data breaches, customers want to know that their financial institution is taking every precaution to protect their personal and financial information. Transparent communication regarding security measures and timely and effective reactions to occurrences can help a bank’s reputation and customer loyalty. Sophisticated security technologies like AI and cloud solutions will provide customers with a more seamless and secure banking experience. Real-time transaction alerts, secure online banking platforms and powerful fraud detection systems all help customers feel more secure and confident while utilising digital banking services. Adding a visible focus on physical safety and branch protection further enhances a client’s positive experience with the financial brand.
The urgency of incorporating security into banking cannot be emphasised enough. The demand for an effective and reliable security approach grows as banks head for an increasingly complicated landscape. Leveraging technology like AI and cloud computing and fostering communication with regulatory authorities can help build a strong security infrastructure.
In this world of rapid technological advancement, prioritising security integration is essential for protecting a bank’s assets, data and reputation. A well-thought-out, comprehensive security strategy will secure financial institutions while also improving their ability to serve and protect customers in a rapidly evolving landscape. The time to act is now, and the strategies implemented will have a lasting impact on banking security. verint.com
In countries all over the world, the financial sector is fundamental to economic growth and social prosperity. Unfortunately, financial institutions face many challenges that curtail their productivity, innovation, and profitability, and ultimately, limit hinder their ability to make tangible contributions to national progress and growth.
Fortunately, financial organisations can mitigate these challenges. They can also deliver better financial services, and even promote financial inclusion and economic growth. The key is to leverage the right technologies in the right way - which is easily done with the support of an expert technology partner. A partner like MVP Tech - Convergint MEA.
At MVP Tech, we understand the challenges that financial organisations grapple with, from a complex regulatory landscape, to operational and market risks, economic and geopolitical volatility, fraud, and the persistent threats of cyberattacks. More importantly, we understand that these organisations can mitigate these challenges and successfully tap into new opportunities for innovation, growth, customer satisfaction, and profitability - with technology.
As an engineering-driven organisation, we deliver comprehensive and innovative solutions powered by the latest, most cutting-edge technologies. Our 300 strong team - 80% of which is comprised of engineers and other technologists - has executed hundreds of diverse and highly complex projects for financial

institutions all over the Middle East and Africa. Each project is carefully planned and meticulously executed to empower our clients to successfully overcome their challenges and achieve their goals in the high-stakes environment they operate in.
MVP Tech builds and integrates a wide range of tailored solutions for financial organisations. One of our specialities, advanced surveillance solutions, play a vital role in strengthening their security posture. These solutions harness high-resolution cameras and realtime AI analytics, allowing banks and other financial institutions to continuously monitor their premises. AI-enabled cameras help officials make informed decisions by analysing events and data captured by these cameras and security systems. In doing so, they can secure their business-critical assets and people, curtail fraudulent activities, and reduce the potential for financial or reputational loss.
Over the years, MVP Tech has also designed and implemented access control systems that have helped all kinds of financial businesses to effortlessly manage and control who can access their systems and resources. By implementing these systems, they are able to safeguard their environments from unauthorised, suspicious, and malicious parties, and protect sensitive data and customer privacy.
In addition to AI-powered analytics, advanced surveillance systems, access control systems, and fraud prevention systems, our expertise extends

to audio-visual (AV) solutions and dynamic digital signage/display systems. These offerings enhance communication and collaboration in financial organisations, while also helping them to boost operational efficiency, improve service delivery, and enhance customer experiences and satisfaction.
MVP Tech’s solutions strengthen financial institutions’ technological infrastructures, ultimately transforming the way they operate and serve their customers and nations. By implementing our bespoke solutions, financial businesses have successfully streamlined operations and enhanced operational efficiency in a rapidly evolving financial landscape. Many have enhanced their security environments or improved their ability to take better decisions. Others have harnessed our technologies to reduce costs, remove informational siloes, or enhance customer relationships.
Moreover, every offering is customised to each organisation’s unique needs, challenges, and goals, providing high value and ROI right from the get-go. Also, as expert systems integrators, we ensure that our installations can be seamlessly integrated into the institution’s existing infrastructure. In building tailored, well-integrated solutions, we help to create secure, efficient, and compliant operational environments for modern-day challenges - and opportunities.
MVP Tech - Convergint empowers financial institutions to enhance operational efficiency, security and compliance with our comprehensive range of cuttingedge, tailored, and integrated solutions. We also offer business-friendly maintenance contracts to ensure that every solution delivers consistent performance and desired results for every client.
Contact MVP Tech - Convergint if you are looking to boost the security and efficiency of your operational environment. Our experts will build a tailored and integrated technology solution that augments your current infrastructure and positions you for success in a challenging business landscape.


Oliver Ledgard, the EMEA Government and Aviation Vertical Lead of Zebra Technologies sat down with Security Middle East magazine’s Britt Jones to explore the role of security within asset management technology and the defence sector in the region
Zebra Technologies is a leader in asset management, mobile and industrial print and mobile computing, with recent acquisitions around machine vision and workforce software. The company works exclusively with channel partners in the Middle East to fulfil customers’ needs for operational efficiency, using Zebra Technologies’ portfolio.
Prominent within the Middle Eastern government space, the mobile computing provider is seeing change to areas for growth which call for investment.
Ledgard explained: “We can leverage a lot of our experience from other markets to really demonstrate to our government customers how they can drive efficiency within their separate workflows, whether it be e-citation, RFID tracking within large locations, such as defence, or simply improving operations for emergency services like front line responders.”
What are the three pillars of tech solutions Zebra Technologies work within?
For government, we break it down into three different pillars of mobile digitisation, asset management and critical communications. For mobile digitisation, we’ve got a range of different handheld tablets.
Zebra Technologies is driving efficiencies and giving visibility to large locations, but also in critical communications where we’ve got devices that can be used for frontline responders, whether they’re used in-vehicle or in-person.
In asset tracking, we have RFID technologies that can be used to gain real-time awareness of assets such
as equipment, personnel, supplies and more. This helps emergency services know what assets they have, where they’re deployed and what condition they’re in.
Do you have many channel partners in the Middle East?
In the Middle East we work exclusively with our channel partners. We leverage our partner capabilities to bring our hardware solutions and software to regions such as the Middle East.
Our Middle East team has a large channel programme, where we send solutions into different industries — for government work it’s vital.
How do you enhance the acceleration of the digitisation process within security operations?
As an example, a Fire and Rescue Service in the UK is utilising our RFID fixed reader and mobile computing to optimise the distribution, management and use of personal protective equipment (PPE).
What we found is that putting this simple technology in place is saving them more than $600,000 over the 10-year lifespan of the PPE. So, you’re looking at the consumables and having to be much
more forward-thinking as opposed to looking at a yearly budget.
We’re seeing a lot more focus and a lot more strain on the end user because of challenges with recruiting workers, so we’re giving them more time back to do the job they’re employed to do rather than the admin.
How does Zebra Technologies help governments in the Middle East meet their various objectives?
For the Middle East, we’re working really closely with government agencies to ensure we are offering devices that can be utilised in the field for a longer period of time, ensuring they don’t have to buy twice.
In terms of that software element as well, we find when we’re talking to our customers, it’s really imperative for them, because they can utilise a rugged device for five years, but it may not be supported via software.
So, it always feeds into our conversation with the customer that you don’t need to be buying twice over a five-year period. Instead, buy once and we will support you through our local service centre, and also in an Android enterprise software sense.


Are your defence channels using your handheld devices?
Yes, we have our RFID technology being utilised by the defence sector.
One of the big transformation projects for us was in the UK. We had the military services utilising a handheld mobile computer, as well as our software and services which resulted in an 83 per cent reduction in time taken to conduct daily equipment account checks across hundreds of locations in the UK, and a 93 per cent decrease in the time taken to receive pallets.
So again, just giving time back to the workers, rather than having to do a lot of the back-end checks, which can be very admin-heavy.
the site of an incident. The broadband connectivity we supply, whether on a handheld device or tablet, is giving frontline responders better visibility in the field.
Over the next five to 10 years, there’s going to be a transition away from Tetra to broadband. We see this happening already in France with the Olympics and Paralympics, and we’re seeing opportunity in Spain, Germany and Finland. So, there are lots of countries looking at transitioning away from Tetra, which is going to give their users greater visibility, greater use cases for one device in the field.
We talked to customers at the show from the Middle East and the topic of Tetra to broadband migration is hot right now.
‘‘Over the next five to 10 years, there’s going to be a transition away from Tetra to broadband’’
How do you enhance the decision-making process for emergency services?
For us, it’s giving that operational visibility. So, coming from Critical Communications World, we can see the start of a migration away from Tetra to broadband technology.
It’s giving better visibility for those staff at HQ to see what’s going on in the field and it’s giving visibility for everyone at
They saw how Zebra could help them, whether it’s a frontline responder device or it’s for asset management and how that can help drive efficiencies.
Do you have anything that you want to expand upon in that sector in the future?
We’re always looking at how we can improve operations. I think we’ve seen
more and more stories from the customer coming out about how we’re helping them drive efficiencies. One of those outcomes is the sustainability angle.
Is there anything currently being developed that could be rolled out to the region?
There are lots of new exciting things, nothing I can talk about at the moment, but we’re constantly looking at our portfolio.
We’re looking at trends in the market. We’re talking to a number of different users and partners and we spend a huge amount every year to see how we can improve or look at new products and technologies to bring out.
A new product from Zebra Technologies is called Identity Guardian and it allows a shared device ecosystem to be utilised and enhances security. It uses an individual’s face profile, and then Identity Guardian will create a personal profile, depending on what level of authority and access is required.
So, if you were a frontline responder, you may get a very different set of apps than a commander may see, but you can all use the same shared device.
You don’t have to buy different device portfolios, for different users. You can buy one device that fits all but then you can simply change the applications and accessibility. zebra.com
A major border security agency was able to minimise ‘false positives’ by installing a new human detection system from ClanTect, which incorporated proprietary ‘signal processing’ algorithms

The border security agency was originally using CO2 detectors for vehicle search operations at the seaports under its jurisdiction, before 15 years ago moving to multiple human detection systems (HDS). The agency was carrying out thousands of searches every single week.
There had been a significant increase in the number of people attempting to cross borders illegally. A key factor was the impact of conflicts and economic upheaval, across the Middle East, which was causing many thousands of people to flee and seek a safer and better life.
Tens of thousands took the risk of boarding trucks to transport them across the European borders. Many of the border crossings across Europe were inadequately equipped to cope with the
However, it had to halt the use of the systems within weeks of installation as almost every vehicle search generated a false alarm (false positive). So the company reverted to the sole use of CO2 detection technology instead. Keen to find a reliable alternative they turned to the expertise of ClanTect founder, Professor Daley.
increase of people attempting to cross. Thousands of migrants survived and made it undetected into Europe.
The failure of the legacy HDS machines meant reverting to CO2 detection technology to detect illegal border crossings, which could only be used to search soft-sided vehicles and caused significant delays at busy ports.
The technology was also producing a high number of false alarms and the situation quickly became unmanageable.
The border security agency called on the expertise of Professor Steve Daley, regarded as one of the world’s leading experts in the field of sound and vibration technology, which underpins HDS technology. Professor Daley was able to identify the reason for the ‘false positives’ in the original HDS system – the legacy machines were incapable of differentiating between the effects of disturbance sources that were external to the trucks, (e.g. passing traffic, general port operations such as crane movement and nearby machinery operation) and the ‘internal’ excitation sources which were caused by hidden human presence within the vehicle.
Working with his team, Professor Daley developed a prototype of a new human presence detection system, which was installed for evaluation at one of the ports.
The key differential of the prototype was the incorporation of proprietary ‘signal processing’ algorithms, which enabled clear differentiation between the effects of ‘external’ and ‘internal’ disturbance sources.
This allowed the newly developed system to only generate an alarm when internally generated vehicle motion (i.e. caused by people inside the truck) was identified. The border security agency operated the prototype system continuously for several weeks, which performed with exceptionally high detection accuracy removing the occurrence of both false positive and false negative results, thereby confirming the flaw in the legacy machines.
While the agency waited a couple of years to secure funds, they had to revert to manual operations for most of their search operations at each of their port locations.
‘This allowed the newly developed system to only generate an alarm when internally generated vehicle motion was identified’
However, once funding was approved, Professor Daley, with colleagues from the Institute of Sound and Vibration Research (ISVR) at the University of Southampton, developed a commercialstandard machine to participate in the tender competition.
The evaluation included months of onsite comparative trials on-site at the busy ports, which involved exposure to the different sources of external excitation. The trials confirmed the exceptional accuracy of the machine developed at the ISVR even in the most demanding environment.
The tender was subsequently awarded to the entity that shortly after was incorporated as ClanTect Ltd.
Following the contract award the border security agency installed the new ClanTect systems at all of the ports under its jurisdiction.
The deployment of the ClanTect system resulted in an unprecedented number of people being detected and detained (many thousands) at the border crossings over a relatively short period of time. The impact of the ClanTect roll out was huge, effectively stopping the illegal transit of people through those ports and, importantly, saving the lives of very many migrants.

ClanTect technology includes wireless systems with multi-vehicle search capabilities, enabling several vehicles to be searched simultaneously. This has significantly sped up the search process, meaning two or more vehicles can be searched within 60 seconds.
The wireless systems are cable-free and the wireless sensors have advanced in-built health diagnostics and battery management, for accuracy and extended battery life. Border agencies can use ClanTect’s highly mobile tablet-based system. This can easily be set up in open environments (e.g., for ad-hoc roadside check points) in a few minutes.
ClanTect’s motion detection technology utilises a proprietary tuned ‘Wind Frame’, which together with unique advanced signal processing algorithms, enables accurate search results to be obtained even in continuous wind excitation.
ClanTect’s ClanConnect high-speed remote and secure access software provides global remote access to any ClanTect device. Daily search data for every vehicle is automatically uploaded to a central server and the agency’s operations centre can access ClanTect devices at any time, for support, diagnostics and software upgrades.
The systems are passive and completely harmless for both search staff and any people that are hiding inside the vehicles.



Can you tell us about your journey in the security industry?
I embarked on my professional journey with Marriott International as a Security Officer. Driven by a relentless pursuit of personal growth, I swiftly ascended to the role of Security Supervisor at Renaissance Hotels, overseeing security operations for Mumbai’s busiest hotel.
Seeking new challenges and broader horizons, I ventured into the passenger cruise industry after months of intensive preparation. In 2006, my perseverance paid off as I secured a position with Carnival Cruise Lines in Miami, USA.
In January 2008, I returned to Mumbai and I embarked on a new chapter with Accor Hotels India, where I contributed to the security operations at Novotel Hotel in Juhu, Mumbai, catering to a highprofile clientele. My journey again took an international turn with a compelling opportunity to be part of the pre-opening team at a Hyatt property in Dubai. Here, I played a pivotal role in crafting and implementing security programmes across multiple hotel properties.
In 2022, I embraced a leadership role managing security for Park Hyatt Hotel in Doha, Qatar, where I successfully orchestrated security operations during the Soccer World Cup 2022, a landmark event that underscored my expertise and leadership in the field.
Throughout, I continued my learning journey to achieve various certifications like CLSD, CPP, IFE Level3 Certificate, CCNS, PSP, PCI, LA 27001, LI 31000 and Certificate in Cybersecurity.
How have hospitality security protocols, systems and technology in the UAE evolved in recent years?
There are constant review and feedback sessions with law enforcement authorities to improve and develop a strong security culture in Dubai Emirate. Dubai has
excelled in looking for and accepting advanced technological systems when it comes to CCTV, Access Control Systems and other technical security systems.

The hospitality industry faces several security challenges that can impact the safety, security and well-being of guests, staff, and the overall operation of hotels and related establishments. Some of these challenges include:
Theft & fraud: Hotels are susceptible to various forms of theft, including theft of personal belongings, identity theft, credit card fraud and employee theft.
Cybersecurity threats: Protecting guest information and ensuring secure online transactions are critical concerns. Terrorism & violence: Security measures must be in place to mitigate the risk of terrorist attacks, as well as incidents of violence.
Unauthorised access & intrusions: Implementing access control measures, such as door lock, access control on key
cards and surveillance cameras, can help prevent unauthorised entry.
Privacy concerns: Maintaining guest privacy and confidentiality is crucial in the hospitality industry.
Employee safety: Providing adequate training and support to employees can help mitigate and manage such risks.
Natural disasters & emergencies: Proper emergency preparedness plans, including evacuation procedures and communication protocols, are essential to ensure the safety of guests and staff.
How would you like to see hospitality security develop in the UAE within the coming years?
The UAE presents significant opportunities for the development of hospitality security due to its ever-booming tourism industry and the importance of maintaining safety and security in the region.
There is a growing emphasis on leveraging cutting-edge technologies, such as AI-based surveillance systems, biometric authentication and cybersecurity solutions, to enhance hospitality security and guest experiences.
The UAE government has prioritised security and safety in the hospitality sector and has implemented stringent regulations and standards to ensure compliance which includes licensing requirements for security personnel and building codes for hotels.
Hotels and hospitality establishments often work in partnership with local police and security forces to share information, coordinate responses to incidents and deter criminal activity.
The UAE’s hospitality industry is undergoing significant development due to its thriving tourism sector, technological advancement and stringent regulatory framework. By embracing innovation and collaboration, the UAE can enhance security standards, ensuring a safe and memorable tourism experience.
28 June
Prevent 2024
New World Makati Hotel, Philippines
leverageinternational.com/ events

14 August
Secutech Vietnam SECC, Ho Chi Minh City
secutechvietnam.tw. messefrankfurt.com
Please check the event websites for the most up-to-date details as dates can change all the time.
2–5 September
Special Operations Forces Exhibition and Conference (SOFEX)
Aqaba International Exhibition & Convention Center, Jordan sofexjordan.com
17–18 September
MENA Information Security Conference Riyadh, Saudi Arabia
menaisc.com
24–25 September
International Security Expo Olympia, London
internationalsecurityexpo.com
1–3 October
Intersec
Saudi Arabia
Riyadh International Convention and Exhibition Center
intersec-ksa.ae. messefrankfurt.com
22–26 October
SAHA Expo Istanbul Fair Central, Türkiye
sahaexpo.com
29–31 October
Milipol Qatar
Doha Exhibition and Convention Center
milipolqatar.com
30 Oct–1 Nov
Secutech Thailand BITEC, Bangkok
secutechthailand.tw. messefrankfurt.com
2–4 December
Security & Fire Excellence Awards
JW Marriott Grosvenor House, London
securityandfireawards.com
14–16 January
Intersec Dubai World Trade Centre
intersec.ae. messefrankfurt.com


Expanding security innovations with AI and IoT, Wesco Anixter offers expertise you can count on alongside a global ecosystem of strategic partners. Together with Corning, we empower transformative digital security for organisations through reliable, high-performance connectivity.


Scan to learn more about Corning’s fibre and connectivity solutions.
We build, connect, power and protect the world.
Wesco.com/security-emea